
U.S. Energy Department Unveils Multiyear Cybersecurity Plan
18.5.2018 securityweek Cyber
The U.S. Department of Energy this week announced its strategy to reduce cyber risks in the energy sector and outlined its goals, objectives and activities for the next five years.
With the energy sector increasingly targeted by threat actors, the Energy Department is concerned that attackers may be able to cause a large and prolonged energy disruption. In an effort to improve the cybersecurity and resilience of energy services, the agency has created the DOE Multiyear Plan for Energy Sector Cybersecurity, which is meant to provide a foundation for the recently launched Office of Cybersecurity, Energy Security, and Emergency Response (CESER).US Energy Department announces multiyear plan for cybersecurity in the energy sector
The plan focuses on three main goals: strengthening cybersecurity preparedness, coordinating incident response and recovery, and accelerating research, development and demonstration (RD&D) for resilient energy delivery systems (EDS).
When it comes to strengthening preparedness, the DOE’s objectives include enhancing information sharing and situational awareness capabilities, strengthening risk management capabilities, reducing supply chain vulnerabilities, and developing and improving information sharing tools. This last objective includes the development of a virtual crowdsourced malware forensic analysis platform.
As for incident response and recovery, the Energy Department wants to establish a coordinated national incident response capability, conduct training for emergency responders and improve the incident reporting process, and conduct exercises.
The DOE’s third goal is to accelerate “game-changing RD&D” of resilient EDS, including for detecting, preventing and mitigating cyber incidents. The organization also wants tools and technologies that can anticipate future attack scenarios, and the development of systems and components that are cybersecurity-aware and capable of automatically handling cyberattacks.
“The DOE will be updating the Cybersecurity Capability Maturity Model (C2M2). The market has changed since it was published in February 2014,” commented Michael Magrath, director of global regulations & standards at VASCO Data Security. “We anticipate DOE will incorporate NIST’s Digital Identity Guidelines (SP 800-63-3), refreshed in 2017 and advance risk-based, biometric adaptive authentication technologies to protect the nation’s energy sector.”
“We welcome the DOE raising awareness around critical threats to the energy sector and laying out a strategy,” said Ray DeMeo, COO at Virsec. “While the strategy pillars are sound, making them actionable will be challenging - largely in view of the inertia behind legacy systems. It's critical that we invest with speed and agility, and the roadmap’s goal to accelerate game-changing RD&D of resilient systems stands out. The administration’s funding request for $96 million is hopefully just a down payment, because protecting our infrastructure adequately will cost billions.”
Critical Flaws in Cisco DNA Center Allow Unauthorized Access
18.5.2018 securityweek Vulnerebility
Cisco has found and patched three critical unauthorized access vulnerabilities in its Digital Network Architecture (DNA) platform.
Cisco DNA is a solution that helps enterprises automate network operations, making it easy to design, provision and apply policies across their environments.
Cisco discovered that the DNA Center is impacted by three serious flaws. One of them, CVE-2018-0222, is related to the existence of undocumented static credentials for the default admin account.
A remote attacker could leverage these credentials to gain access to the affected system and execute commands with root privileges. The issue has been addressed with the release of Cisco DNA Center software version 1.1.3.
The second vulnerability, CVE-2018-0271, allows a remote attacker to bypass authentication and obtain privileged access to critical services in the DNA Center. This flaw has been patched with the release of Cisco DNA Center software version 1.1.2.
“The vulnerability is due to a failure to normalize URLs prior to servicing requests. An attacker could exploit this vulnerability by submitting a crafted URL designed to exploit the issue,” Cisco explained in an advisory.
The third critical security hole in DNA Center, CVE-2018-0268, also allows a remote attacker to bypass authentication and obtain elevated privileges. A patch is included in version 1.1.3.
“This vulnerability is due to an insecure default configuration of the Kubernetes container management subsystem within DNA Center,” Cisco said. “An attacker who has the ability to access the Kubernetes service port could execute commands with elevated privileges within provisioned containers. A successful exploit could result in a complete compromise of affected containers.”
All the vulnerabilities were discovered by Cisco itself and there is no evidence of malicious exploitation.
Cisco published more than a dozen security advisories on Wednesday, including four that describe high severity vulnerabilities.
The list includes a cross-site request forgery (CSRF) flaw in IoT Field Network Director (IoT-FND), a denial-of-service (DoS) bug in the Identity Services Engine (ISE), a shell access vulnerability in Enterprise NFV Infrastructure Software (NFVIS), and a DoS problem in Meeting Server.
DHS Publishes New Cybersecurity Strategy
18.5.2018 securityweek BigBrothers
The U.S. Department of Homeland Security (DHS) this week published its long-delayed Cybersecurity Strategy. It had been mandated by Congress to deliver a strategy by March 2017, and did so on May 15, 2018.
The strategy is defined in a high-level document (PDF) of 35 pages. Its scope is to provide "the Department with a framework to execute our cybersecurity responsibilities during the next five years to keep pace with the evolving cyber risk landscape by reducing vulnerabilities and building resilience; countering malicious actors in cyberspace; responding to incidents; and making the cyber ecosystem more secure and resilient."
This framework comprises five pillars containing seven separate goals. The pillars are risk identification; vulnerability reduction Including the twin goals of protecting federal systems and critical industries); threat reduction by proactive means; consequence mitigation (that is, improved incident response); and to enable cybersecurity outcomes. The last pillar comprises the twin goals of strengthening the security and reliability of the cyber ecosystem, and improving the management of its own activities.
"The cyber threat landscape is shifting in real-time, and we have reached a historic turning point," said DHS Secretary Kirstjen Nielsen. "Digital security is now converging with personal and physical security, and it is clear that our cyber adversaries can now threaten the very fabric of our republic itself. That is why DHS is rethinking its approach by adopting a more comprehensive cybersecurity strategy. In an age of brand-name breaches, we must think beyond the defense of specific assets -- and confront systemic risks that affect everyone from tech giants to homeowners. Our strategy outlines how DHS will leverage its unique capabilities on the digital battlefield to defend American networks and get ahead of emerging cyber threats."
Of necessity, however, the five pillars and seven goals are defined in very basic terms. They define objectives, sub-objectives and outcomes -- but with little on methods. For example, goal #1 (the risk identification pillar) is to assess evolving cybersecurity risks. This will be achieved by working with "stakeholders, including sector-specific agencies, nonfederal cybersecurity firms, and other federal and nonfederal entities, to gain an adequate understanding of the national cybersecurity risk posture, analyze evolving interdependencies and systemic risk, and assess changing techniques of malicious actors."
However, nobody was able to predict, detect or prevent Russian meddling in the 2016 presidential election, nor the WannaCry and NotPetya outbreaks. The implication is that something new and beyond just increased interagency cooperation needs to be done to achieve genuine risk identification.
The third pillar, threat reduction together with goal #4 (prevent and disrupt criminal use of cyberspace) is also interesting. The strategy states, "We will reduce cyber threats by countering transnational criminal organizations and sophisticated cyber criminals." Again, the obvious question is, 'How?'. The strategy states, "our law enforcement jurisdiction is broad". But it does not reach into those countries that are generally considered to be the prime movers of serious cyber criminality: Russia, China, Iran and North Korea.
Indeed, the U.S. government has so far failed to repatriate Edward Snowden from Russia, nor even to apprehend Julian Assange in the European Union. It is difficult to see how the DHS will be able to prevent and disrupt advanced foreign criminal use of cyberspace without resorting to new tactics -- such as a more aggressive active defense verging on hacking back. Neither 'active defense' nor 'hack back' are mentioned in the strategy document.
Ray DeMeo, COO at Virsec, has similar concerns. "Cybersecurity is an inherently global issue and it's good that the DHS strategy recognizes the need for a 'global approach with robust international engagement'," he told SecurityWeek. "But it's yet unclear how an agency with a domestic mandate is going to effectively engage globally. The reality is that a large portion of internet crime is driven from the international "wild west" from areas with lax law enforcement, or actual nation-state sponsorship. This problem is as much diplomatic as it is technological."
These caveats aside, it is good to see a formal strategy to cover the DHS' entire theater of responsibility with a clearly stated objective: "By 2023, the Department of Homeland Security will have improved national cybersecurity risk management by increasing security and resilience across government networks and critical infrastructure; decreasing illicit cyber activity; improving responses to cyber incidents; and fostering a more secure and reliable cyber ecosystem through a unified departmental approach, strong leadership, and close partnership with other federal and nonfederal entities."
"The strategy put forth by DHS is very comprehensive and well thought out," says Rishi Bhargava, co-founder at Demisto. "The inclusion of response plan coordination under the Consequence Mitigation section is a critical piece to be able to contain damage from an attack. Any strategy is as good as it's execution. I look forward to seeing this put in action across different departments and policies."
It is reassuring that the organization is not seeking to develop its own new framework, but to encourage the use of existing relevant frameworks. "DHS," says the document, "must expand efforts to encourage adoption of applicable cybersecurity best practices, including NIST's Framework for Improving Critical Infrastructure Cybersecurity."
It is a little surprising, however, that while NIST is specified, the Domain Message Authentication Reporting & Conformance (DMARC) protocol is not mentioned. In October 2017, DHS issued a binding operational directive requiring that all federal agencies start to use DMARC. By January 2018 it was reported that about half of the agencies had implemented DMARC, but only at its lowest level.
It is easy to be critical of a high-level strategy document -- it is the detail of implementation that will decide on the effectiveness of this strategy. For the moment, this document marks a valuable and important approach to unifying and strengthening the domestic cybersecurity remit of the DHS. "The DHS approach to managing cybersecurity risk on the national level," comments Brajesh Goyal, VP of engineering at Cavirin, "is a good analogy for what organizations need to do to manage their cyber-posture. A good framework for this is the NIST Cybersecurity Framework (CSF). This can serve as a foundation for other security in-depth actions."
"It's important that the DHS has finally published its cybersecurity strategy," explains DeMeo; "but by definition, this is high-level. For the most part, these are sensible recommendations. What's critical now is making this strategy actionable. One of the document's guiding principles is to foster innovation and agility -- this is a big ask, where existing time horizons must be reduced from years down to months. We need to dramatically accelerate collaboration with the private sector, where meaningful security innovation is happening daily, if we are going to change the asymmetric nature of today's threat landscape."
CISCO issued security updates to address three critical flaws in Cisco DNA Center
18.5.2018 securityaffairs Vulnerebility
Cisco has issued security updates to address three critical vulnerabilities in its DNA Center appliance, admins need to update their installs as soon as possible.
Cisco has issued security updates to address three critical vulnerabilities in its Digital Network Architecture (DNA) Center appliance.
The DNA Center is a network management and administration tool, experts discovered three vulnerabilities that could be exploited by remote unauthenticated attackers to take over the appliance.
The most severe issue is a static credentials vulnerability (CVE-2018-0222) affecting the DNA Center, the attacker can use them to completely take over the targeted appliance.
“A vulnerability in Cisco Digital Network Architecture (DNA) Center could allow an unauthenticated, remote attacker to log in to an affected system by using an administrative account that has default, static user credentials.” reads the security advisory published by Cisco.
The experts found undocumented, static user credentials for the default administrative account in the affected software.
“The vulnerability is due to the presence of undocumented, static user credentials for the default administrative account for the affected software. An attacker could exploit this vulnerability by using the account to log in to an affected system.” continues the advisory.
“A successful exploit could allow the attacker to log in to the affected system and execute arbitrary commands with root privileges.”
The second vulnerability tracked as CVE-2018-0271 affects the API gateway of the Cisco Digital Network Architecture (DNA) Center.
The flaw could be exploited by a remote unauthenticated attacker to bypass authentication and gain a privileged access to critical services in the DNA Center.
“A vulnerability in the API gateway of the Cisco Digital Network Architecture (DNA) Center could allow an unauthenticated, remote attacker to bypass authentication and access critical services.” reads the Cisco advisory.
“The vulnerability is due to a failure to normalize URLs prior to servicing requests. An attacker could exploit this vulnerability by submitting a crafted URL designed to exploit the issue,”
The third critical flaw in DNA Center fixed by Cisco tracked as CVE-2018-0268 could be exploited by an attacker to bypass authentication within the container instances and obtain elevated privileges.
“This vulnerability is due to an insecure default configuration of the Kubernetes container management subsystem within DNA Center,” states the Cisco security advisory. “An attacker who has the ability to access the Kubernetes service port could execute commands with elevated privileges within provisioned containers. A successful exploit could result in a complete compromise of affected containers.”
Cisco rolled out a security update to DNA Center via its System Updates tool, admins need to install the version 1.1.3 as soon as possible.
Nethammer – Exploiting Rowhammer attack through network without a single attacker-controlled line of code
18.5.2018 securityaffairs Exploit
Nethammer attack technique is the first truly remote Rowhammer attack that doesn’t require a single attacker-controlled line of code on the targeted system.
A few days ago security experts announced the first network-based remote Rowhammer attack, dubbed Throwhammer. The attack exploits a known vulnerability in DRAM through network cards using remote direct memory access (RDMA) channels.
Rowhammer is classified as a problem affecting some recent DRAM devices in which repeatedly accessing a row of memory can cause bit flips in adjacent rows, this means that theoretically, an attacker can change any value of the bit in the memory.
The issue has been known at least since 2012, the first attack was demonstrated in 2015 by white hat hackers at Google Project Zero team.
To better understand the Rowhammer flaw, let’s remember that a DDR memory is arranged in an array of rows and columns. Blocks of memory are assigned to various services and applications. To avoid that an application accesses the memory space reserved by another application, it implements a “sandbox” protection mechanism.
Bit flipping technique caused by the Rowhammer problems could be exploited to evade the sandbox.
A separate group of security researchers has now demonstrated another network-based remote Rowhammer attack dubbed Nethammert, that leverages uncached memory or flush instruction while processing the network requests.
“Nethammer is the first truly remote Rowhammer attack, without a single attacker-controlled line of code on the targeted system. Systems that use uncached memory or flush instructions while handling network requests, e.g., for interaction with the network device, can be attacked using Nethammer” reads the research paper published by the experts.
The research team was composed of academics from the Graz University of Technology, the University of Michigan and Univ Rennes.
The Nethammer technique can be exploited by attackers to execute arbitrary code on the targeted system by rapidly writing and rewriting memory used for packet processing.
The attack is feasible only with a fast network connection between the attacker and victim.
“We demonstrate that the frequency of the cache misses is in all three cases high enough to induce bit flips. We evaluated different bit flip scenarios.” continues the paper.
“Depending on the location, the bit flip compromises either the security and integrity of the system and the data of its users, or it can leave persistent damage on the system, i.e., persistent denial of service.”
This process results in a high number of memory accesses to the same set of memory locations, which could induce disturbance errors in DRAM and causes memory corruption by unintentionally flipping the DRAM bit-value.
Nethammer attack
Data corruption resulting from the operations can be exploited by the attackers to gain control over the victim’s system.
“To mount a Rowhammer attack, memory accesses need to be directly served by the main memory. Thus, an attacker needs to make sure that the data is not stored in the cache.” continues the attacker.
“An attacker can use the unprivileged clflush instruction to invalidate the cache line or use uncached memory if available.”
The experts highlighted that caching makes the attack more difficult, so they devised some techniques to bypass the cache and direct access to the DRAM to cause the interference.
The experts successfully demonstrated three different cache bypasses for Nethammer technique:
A kernel driver that flushes (and reloads) an address whenever a packet is received.
Intel Xeon CPUs with Intel CAT for fast cache eviction
Uncached memory on an ARM-based mobile device.
The experts observed a bit flip every 350 ms demonstrating that it is possible to hammer over the network if at least two memory accesses are served from main memory, they successfully induced the interference by sending a stream of UDP packets with up to 500 Mbit/s to the target system.
The Nethammer attack technique does not require any attack code differently from the original Rowhammer attack.
Unfortunately, any attack technique based on the Rowhammer attack is not possible to mitigate with software patched, to solve the issues, it is necessary to re-design the architecture of the flawed components, meantime threat actors can start exploiting the Rowhammer technique in the wild.
Further details on the Rowhammer attack are reported in my post titled “The Rowhammer: the Evolution of a Dangerous Attack”
The new Wicked Mirai botnet leverages at least three new exploits
18.5.2018 securityaffairs BotNet
Security experts from Fortinet have spotted a new variant of the Mirai botnet dubbed ‘Wicked Mirai’, it includes new exploits and spread a new bot.
The name Wicked Mirai comes from the strings in the code, the experts discovered that this new variant includes at least three new exploits compared to the original one.
“The FortiGuard Labs team has seen an increasing number of Mirai variants, thanks to the source code being made public two years ago.” reads the analysis published by Fortinet.
“Some made significant modifications, such as adding the capability to turn infected devices into swarms of malware proxies and cryptominers. Others integrated Mirai code with multiple exploits targeting both known and unknown vulnerabilities, similar to a new variant recently discovered by FortiGuard Labs, which we now call WICKED.”

The Mirai botnet was first spotted in 2016 by the experts at MalwareMustDie, at the time it was used to power massive DDoS attacks in the wild. The Mirai’s source code was leaked online in October 2016, since then many other variants emerged in the wild, including Satori, Masuta, and Okiru.
According to Fortinet, the author of the Wicked Mirai is the same as the other variants.
Mirai botnets are usually composed of three main modules: Attack, Killer, and Scanner. Fortinet focused its analysis on the Scanner module that is responsible for the propagation of the malware.
The original Mirai leveraged brute force attempts to compromise other IOT devices, while the WICKED Mirai uses known exploits.
The Wicked Mirai would scan ports 8080, 8443, 80, and 81 by initiating a raw socket SYN connection to IoT devices. Once it has established a connection, the bot will attempt to exploit the device and download its payload by writing the exploit strings to the socket through the write() syscall.
The experts discovered that the exploit to be used depends on the specific port the bot was able to connect to. Below the list of devices targeted by the Wicked Mirai
Port 8080: Netgear DGN1000 and DGN2200 v1 routers (also used by Reaper botnet)
Port 81: CCTV-DVR Remote Code Execution
Port 8443: Netgear R7000 and R6400 Command Injection (CVE-2016-6277)
Port 80: Invoker shell in compromised web servers
The analysis of the code revealed the presence of the string SoraLOADER, which suggested it might attempt to distribute the Sora botnet. Further investigation allowed the researchers to contradict this hypothesis and confirmed the bot would actually connect to a malicious domain to download the Owari Mirai bot.
“After a successful exploit, this bot then downloads its payload from a malicious web site, in this case, hxxp://185[.]246[.]152[.]173/exploit/owari.{extension}. This makes it obvious that it aims to download the Owari bot, another Mirai variant, instead of the previously hinted at Sora bot.” reads the analysis.
“However, at the time of analysis, the Owari bot samples could no longer be found in the website directory. In another turn of events, it turns out that they have been replaced by the samples shown below, which were later found to be the Omni bot.”
The analysis of the website’s /bins directory revealed other Omni samples, which were apparently delivered using the GPON vulnerability CVE-2018-10561.

Searching for a link between Wicked, Sora, Owari, and Omni, the security researchers at Fortinet found a conversation with Owari/Sora IoT Botnet author dated back to April.
The vxer, who goes by the online handle of “Wicked,” that at the time said he abandoned the Sora botnet and was working on Owari one.
The conversation suggests the author abandoned both Sora and Owari bots and he is currently working on the Omni project.
“Based on the author’s statements in the above-mentioned interview as to the different botnets being hosted in the same host, we can essentially confirm that the author of the botnets Wicked, Sora, Owari, and Omni are one and the same. This also leads us to the conclusion that while the WICKED bot was originally meant to deliver the Sora botnet, it was later repurposed to serve the author’s succeeding projects,” Fortinet concludes.
Google Offers Free DDoS Protection for U.S. Political Organizations
17.5.2018 securityweek Attack
Jigsaw, an incubator run by Google parent Alphabet, this week announced the availability of Project Shield – which offers free distributed denial of service (DDoS) protections – for the U.S. political community.
Opened in February 2016 to independent, under-resourced news sites, Project Shield helps protect free speech by fending off crippling DDoS assaults. The service, which leverages Google technology, was launched only weeks after Google Ideas became Jigsaw.
In March last year, Google and Jigsaw announced a partnership to offer Protect Your Election, tools that would help news organizations, human rights groups, and election monitoring sites fend off not only DDoS assaults, but also phishing and account takeover attempts.
This week, Jigsaw revealed that Project Shield is now available for free to “U.S. political organizations registered with the appropriate electoral authorities, including candidates, campaigns, section 527 organizations, and political action committees.”
“These organizations are critical parts of the democratic process, and they deserve the same defenses against cyber-attacks that we’ve offered to news organizations around the world,” George Conard, Product Manager, Jigsaw, says.
The free service is offered in response to an increase in the frequency and intensity of digital attacks against democratic institutions in the United States and globally. Threat actors flood computer systems and servers with traffic to silence political speech and prevent voters from accessing the information they need.
Not only is the number of DDoS attacks increasing overall, but so does the number of attacks the same target faces, recent reports have revealed. The cost of launching a DDoS attack has decreased as well: one can hire a DDoS-launching service for only $10 per hour.
DDoS attacks increasingly target political parties, campaigns, and organizations, Conard notes. The most recent example is a Tennessee county website displaying election results being disrupted earlier this month for an hour on the night of the Tennessee congressional primary elections.
“Any political organization, regardless of size or significance, is potentially at risk. It’s critical to provide support to those smaller, more vulnerable political groups that don’t have the financial or technical resources to do it themselves. Project Shield helps ensure that any eligible organization can be protected from a range of digital attacks — for free,” Conard says.
While Project Shield can protect websites against DDoS attacks, the Protect Your Election initiative can help political organizations defend against other attacks as well. The goal remains the same as when Project Shield was launched: to protect freedom of expression and access to information.
Project Shield leverages Google’s infrastructure to protect from DDoS attacks using “a reverse proxy multi-layer defense system.” Basically, requests from end users first come through the Shield, which filters malicious traffic and only allows legitimate requests to pass through.
Not only is the tool free, but it is also easy to set up and doesn’t require maintenance, to keep a website safe from DDoS attacks, Conard says.
“Protecting critical infrastructure and institutions from cyber-attacks is more important than ever. With the U.S. midterm elections approaching, it’s crucial to make sure that private information is protected and public information is accessible,” he points out.
Jigsaw is committed to working with U.S. political organizations of all sizes to ensure that every one of them, regardless of their resources, can stay safe online. In the coming months, the protections will be expanded to international political organizations as well.
Hackers Steal '$15.3 Million' From Mexico Financial System
17.5.2018 securityweek Incindent
Hackers who targeted Mexico's interbank payment system made off with more than $15 million in the past several weeks, the Bank of Mexico said Wednesday.
The amount of funds involved in the irregular activity totaled "approximately 300 million pesos ($15.3 million)," central bank governor Alejandro Diaz de Leon told reporters.
He said commercial bank customers' accounts were never in danger.
An investigation is under way, the governor said, without indicating if the suspected hackers were domestic or international.
The interbank payments system allows banks to make real-time transfers to each other.
They connect via their own computer systems or an external provider -- the point where the attacks appear to have taken place, Lorenza Martinez, director general of the corporate payments and services system at the central bank, said on Monday.
Martinez revealed that at least five attacks had occurred but, at that time, said the amount taken was still being analyzed.
After the attacks were detected, banks switched to a slower but more secure method.
IT threat evolution Q1 2018. Statistics
17.5.2018 Kaspersky Analysis
Q1 figures
According to KSN:
Kaspersky Lab solutions blocked 796,806,112 attacks launched from online resources located in 194 countries across the globe.
282,807,433 unique URLs were recognized as malicious by Web Anti-Virus components.
Attempted infections by malware designed to steal money via online access to bank accounts were logged on the computers of 204,448 users.
Ransomware attacks were registered on the computers of 179,934 unique users.
Our File Anti-Virus logged 187,597,494 unique malicious and potentially unwanted objects.
Kaspersky Lab products for mobile devices detected:
1,322,578 malicious installation packages
18,912 installation packages for mobile banking Trojans
8,787 installation packages for mobile ransomware Trojans
Mobile threats
Q1 events
In Q1 2018, DNS-hijacking, a new in-the-wild method for spreading mobile malware on Android devices, was identified. As a result of hacked routers and modified DNS settings, users were redirected to IP addresses belonging to the cybercriminals, where they were prompted to download malware disguised, for example, as browser updates. That is how the Korean banking Trojan Wroba was distributed.
This malicious resource shows a fake window while displaying the legitimate site in the address bar
It wasn’t a drive-by-download case, since the success of the attack largely depended on actions by the victim, such as installing and running the Trojan. But it’s interesting to note that some devices (routers) were used to attack other devices (smartphones), all sprinkled with social engineering to make it more effective.
However, a far greater splash in Q1 was caused by the creators of a seemingly legitimate app called GetContact.
Some backstory to begin with. Various families and classes of malicious apps are known to gather data from infected devices: it could be a relatively harmless IMEI number, phone book contents, SMS correspondence, or even WhatsApp chats. All the above (and much more besides) is personal information that only the mobile phone owner should have control over. However, the creators of GetContact concocted a license agreement giving them the right to download the user’s phone book to their servers and grant all their subscribers access to it. As a result, anyone could find out what name GetContact users had saved their phone number under, often with sad consequences. Let’s hope that the app creators had the noble intention of protecting users from telephone spam and fraudulent calls, but simply chose the wrong means to do so.
Mobile threat statistics
In Q1 2018, Kaspersky Lab detected 1,322,578 malicious installation packages, down 11% against the previous quarter.
Number of detected malicious installation packages, Q2 2017 – Q1 2018

Distribution of newly detected mobile apps by type, Q4 2017 and Q1 2018
Among all the threats detected in Q1 2018, the lion’s share belonged to potentially unwanted RiskTool apps (49.3%); compared to the previous quarter, their share fell by 5.5%. Members of the RiskTool.AndroidOS.SMSreg family contributed most to this indicator.
Second place was taken by Trojan-Dropper threats (21%), whose share doubled. Most detected files of this type came from the Trojan-Dropper.AndroidOS.Piom family.
Advertising apps, which ranked second in Q4 2017, dropped a place—their share decreased by 8%, accounting for 11% of all detected threats.
On a separate note, Q1 saw a rise in the share of mobile banking threats. This was due to the mass distribution of Trojan-Banker.AndroidOS.Faketoken.z.
TOP 20 mobile malware
Note that this malware rating does not include potentially dangerous or unwanted programs such as RiskTool and Adware.
Verdict %*
1 DangerousObject.Multi.Generic 70.17
2 Trojan.AndroidOS.Boogr.gsh 12.92
3 Trojan.AndroidOS.Agent.rx 5.55
4 Trojan-Dropper.AndroidOS.Lezok.p 5.23
5 Trojan-Dropper.AndroidOS.Hqwar.ba 2.95
6 Trojan.AndroidOS.Triada.dl 2.94
7 Trojan-Dropper.AndroidOS.Hqwar.i 2.51
8 Trojan.AndroidOS.Piom.rfw 2.13
9 Trojan-Dropper.AndroidOS.Lezok.t 2.06
10 Trojan.AndroidOS.Piom.pnl 1.78
11 Trojan-Dropper.AndroidOS.Agent.ii 1.76
12 Trojan-SMS.AndroidOS.FakeInst.ei 1.64
13 Trojan-Dropper.AndroidOS.Hqwar.gen 1.50
14 Trojan-Ransom.AndroidOS.Zebt.a 1.48
15 Trojan.AndroidOS.Piom.qmx 1.47
16 Trojan.AndroidOS.Dvmap.a 1.40
17 Trojan-SMS.AndroidOS.Agent.xk 1.35
18 Trojan.AndroidOS.Triada.snt 1.24
19 Trojan-Dropper.AndroidOS.Lezok.b 1.22
20 Trojan-Dropper.AndroidOS.Tiny.d 1.22
* Unique users attacked by the relevant malware as a percentage of all users of Kaspersky Lab’s mobile antivirus that were attacked.
As before, first place in our TOP 20 went to DangerousObject.Multi.Generic (70.17%), the verdict we use for malware detected using cloud technologies. Cloud technologies work when the anti-virus databases lack data for detecting a piece of malware, but the cloud of the anti-virus company already contains information about the object. This is basically how the latest malicious programs are detected.
In second place was Trojan.AndroidOS.Boogr.gsh (12.92%). This verdict is given to files recognized as malicious by our system based on machine learning.
Third was Trojan.AndroidOS.Agent.rx (5.55%). Operating in background mode, this Trojan’s task is to covertly visit web pages as instructed by its C&C.
Fourth and fifth places went to the Trojan matryoshkas Trojan-Dropper.AndroidOS.Lezok.p (5.2%) and Trojan-Dropper.AndroidOS.Hqwar.ba (2.95%), respectively. Note that in Q1 threats like Trojan-Dropper effectively owned the TOP 20, occupying eight positions in the rating. The main tasks of such droppers are to drop a payload on the victim, avoid detection by security software, and complicate the reverse engineering process. In the case of Lezok, an aggressive advertising app acts as the payload, while Hqwar can conceal a banking Trojan or ransomware.
Sixth place in the rating was taken by the unusual Trojan Triada.dl (2.94%) from the Trojan.AndroidOS.Triada family of modular-designed malware, which we have written about many times. The Trojan was notable for its highly sophisticated attack vector: it modified the main system library libandroid_runtime.so so that malicious code started when any debugging output was written to the system event log. Devices with the modified library ended up on store shelves, thus ensuring that the infection began early. The capabilities of Triada.dl are almost limitless: it can be embedded in apps already installed and pinch data from them, and it can show the user fake data in “clean” apps.
The Trojan ransomware Trojan-Trojan-Ransom.AndroidOS.Zebt.a (1.48%) finished 14th. It features a quaint set of functions, including hiding the icon at startup and requesting device administrator rights to counteract deletion. Like other such mobile ransomware, the malware is distributed under the guise of a porn app.
Another interesting resident in the TOP 20 is Trojan-SMS.AndroidOS.Agent.xk (1.35%), which operates like the SMS Trojans of 2011. The malware displays a welcome screen offering various services, generally access to content. At the bottom in fine print it is written that the services are fee-based and subscription to them is via SMS.
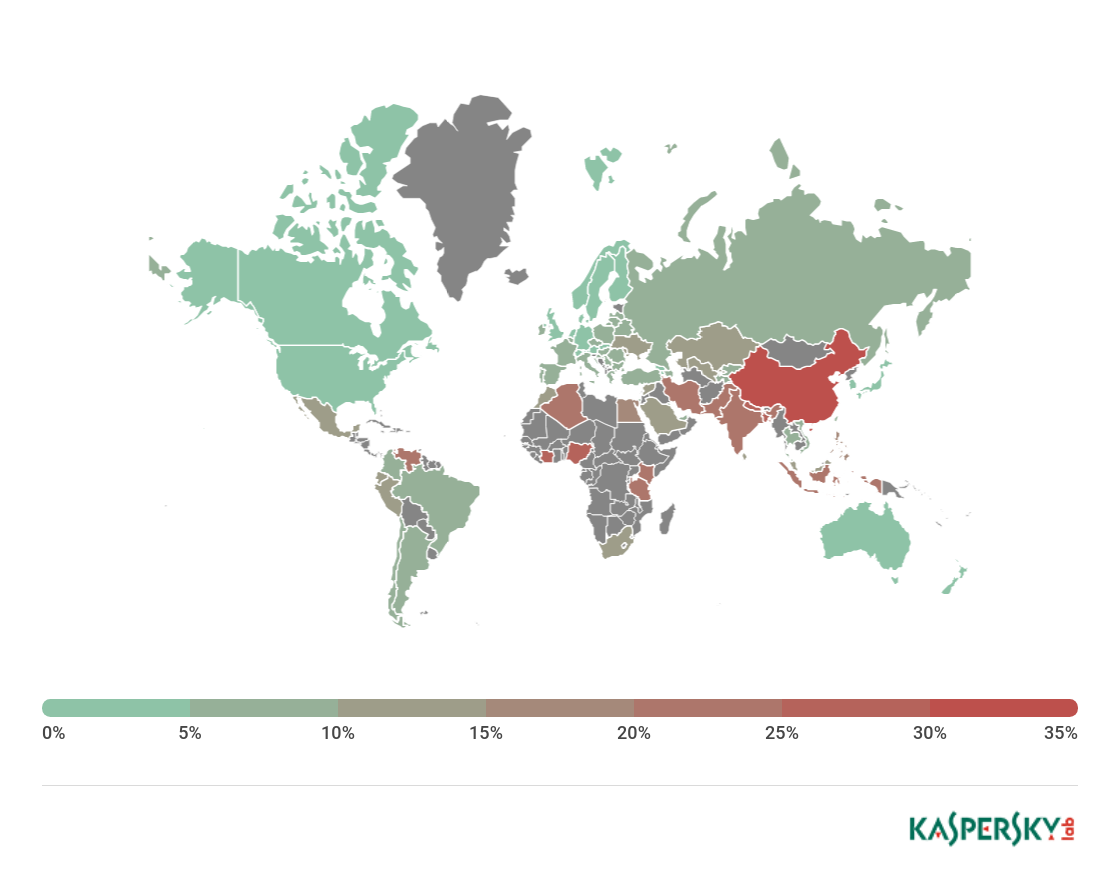
Map of attempted infections using mobile malware in Q1 2018 (percentage of attacked users in the country)
TOP 10 countries by share of users attacked by mobile malware:
Country* %**
1 China 34.43
2 Bangladesh 27.53
3 Nepal 27.37
4 Ivory Coast 27.16
5 Nigeria 25.36
6 Algeria 24.13
7 Tanzania 23.61
8 India 23.27
9 Indonesia 22.01
10 Kenya 21.45
* Excluded from the rating are countries with relatively few users of Kaspersky Lab’s mobile antivirus (under 10,000).
** Unique users attacked in the country as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
In Q1 2018, China (34.43%) topped the list by share of mobile users attacked. Note that China is a regular fixture in the TOP 10 rating by number of attacked users: It came sixth in 2017, and fourth in 2016. As in 2017, second place was claimed by Bangladesh (27.53%). The biggest climber was Nepal (27.37%), rising from ninth place last year to third.
Russia (8.18%) this quarter was down in 39th spot, behind Qatar (8.22%) and Vietnam (8.48%).
The safest countries (based on proportion of mobile users attacked) are Denmark (1.85%) and Japan (1%).
Mobile banking Trojans
In the reporting period, we detected 18,912 installation packages for mobile banking Trojans, which is 1.3 times more than in Q4 2017.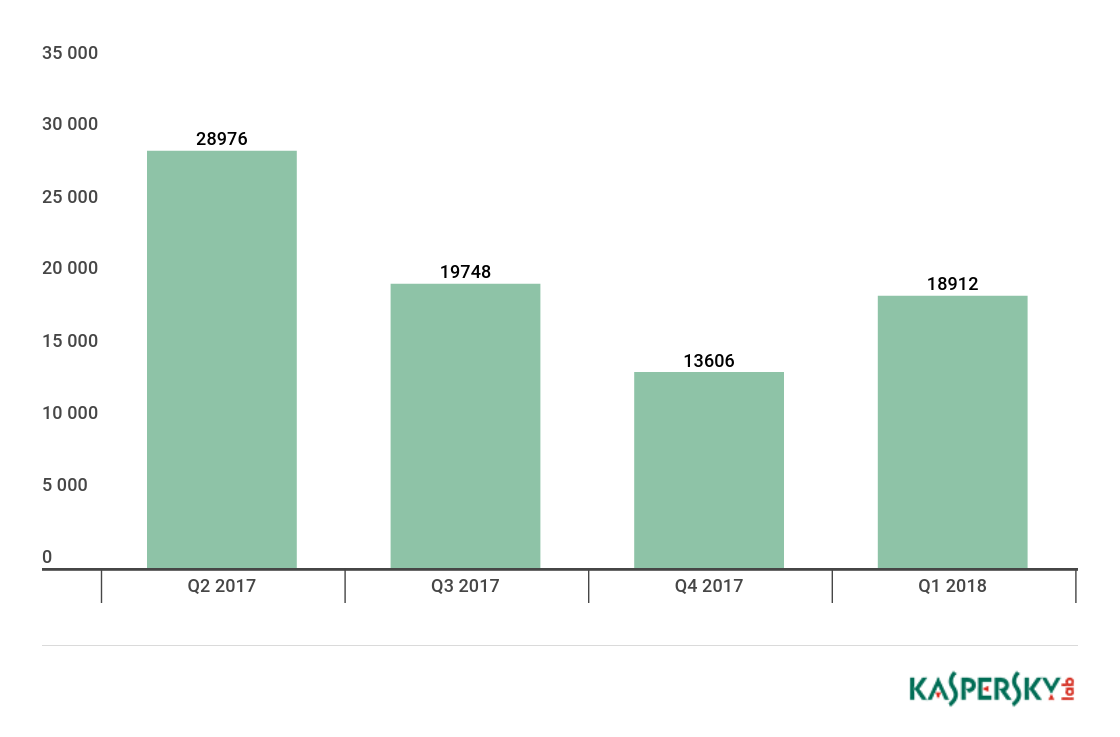
Number of installation packages for mobile banking Trojans detected by Kaspersky Lab, Q2 2017 – Q1 2018
Verdict %*
1 Trojan-Banker.AndroidOS.Asacub.bj 12.36
2 Trojan-Banker.AndroidOS.Svpeng.q 9.17
3 Trojan-Banker.AndroidOS.Asacub.bk 7.82
4 Trojan-Banker.AndroidOS.Svpeng.aj 6.63
5 Trojan-Banker.AndroidOS.Asacub.e 5.93
6 Trojan-Banker.AndroidOS.Hqwar.t 5.38
7 Trojan-Banker.AndroidOS.Faketoken.z 5.15
8 Trojan-Banker.AndroidOS.Svpeng.ai 4.54
9 Trojan-Banker.AndroidOS.Agent.di 4.31
10 Trojan-Banker.AndroidOS.Asacub.ar 3.52
* Unique users attacked by the relevant malware as a percentage of all users of Kaspersky Lab’s mobile antivirus that were attacked by banking threats.
The most popular mobile banking Trojan in Q1 was Asacub.bj (12.36%), nudging ahead of second-place Svpeng.q (9.17%). Both these Trojans use phishing windows to steal bank card and authentication data for online banking. They also steal money through SMS services, including mobile banking.
Note that the TOP 10 mobile banking threats in Q1 is largely made up of members of the Asacub (4 out of 10) and Svpeng (3 out of 10) families. However, Trojan-Banker.AndroidOS.Faketoken.z also entered the list. This Trojan has extensive spy capabilities: it can install other apps, intercept incoming messages (or create them on command), make calls and USSD requests, and, of course, open links to phishing pages.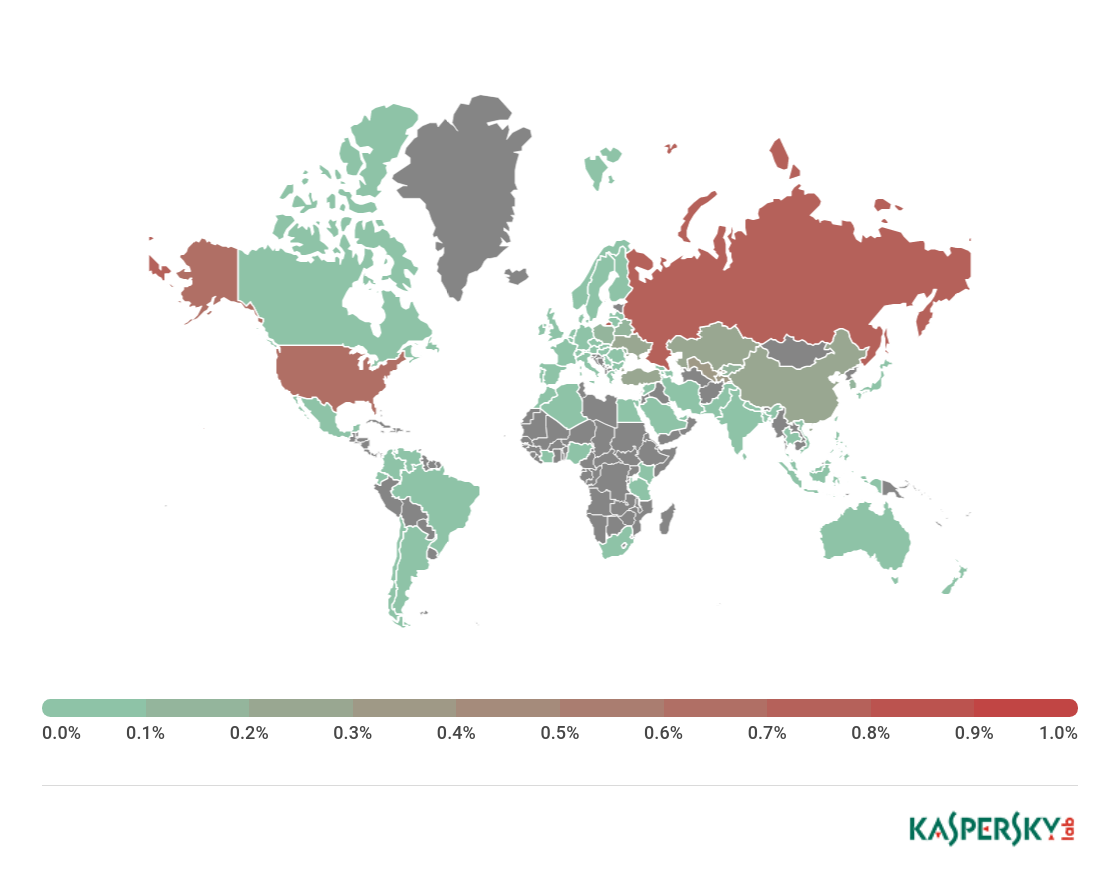
Geography of mobile banking threats in Q1 2018 (percentage of attacked users)
TOP 10 countries by share of users attacked by mobile banking Trojans
Country* %**
1 Russia 0.74
2 USA 0.65
3 Tajikistan 0.31
4 Uzbekistan 0.30
5 China 0.26
6 Turkey 0.22
7 Ukraine 0.22
8 Kazakhstan 0.22
9 Poland 0.17
10 Moldova 0.16
* Excluded from the rating are countries with relatively few users of Kaspersky Lab’s mobile antivirus (under 10,000).
** Unique users attacked by mobile banking Trojans in the country as a percentage of all users of Kaspersky Lab’s mobile antivirus in this country.
The Q1 2018 rating was much the same as the situation observed throughout 2017: Russia (0.74%) remained top.
The US (0.65%) and Tajikistan (0.31%) took silver and bronze, respectively. The most popular mobile banking Trojans in these countries were various modifications of the Trojan-Banker.AndroidOS.Svpeng family, as well Trojan-Banker.AndroidOS.Faketoken.z.
Mobile ransomware Trojans
In Q1 2018, we detected 8,787 installation packages for mobile ransomware Trojans, which is just over half the amount seen in the previous quarter and 22 times less than in Q2 2017. This significant drop is largely because attackers began to make more use of droppers in an attempt to hinder detection and hide the payload. As a result, such malware is detected as a dropper (for example, from the Trojan-Dropper.AndroidOS.Hqwar family), even though it may contain mobile ransomware or a “banker.”
Number of installation packages for mobile ransomware Trojans detected by Kaspersky Lab (Q2 2017 – Q1 2018)
Note that despite the decline in their total number, ransomware Trojans remain a serious threat — technically they are now far more advanced and dangerous. For instance, Trojan-Trojan-Ransom.AndroidOS.Svpeng acquires device administrator rights and locks the smartphone screen with a PIN if an attempt is made to remove them. If no PIN is set (could also be a graphic, numeric, or biometric lock), the device is locked. In this case, the only way to restore the smartphone to working order is to reset the factory settings.
The most widespread mobile ransomware in Q1 was Trojan-Ransom.AndroidOS.Zebt.a — it was encountered by more than half of all users. In second place was Trojan-Ransom.AndroidOS.Fusob.h, having held pole position for a long time. The once popular Trojan-Ransom.AndroidOS.Svpeng.ab only managed fifth place, behind Trojan-Ransom.AndroidOS.Egat.d and Trojan-Ransom.AndroidOS.Small.snt. Incidentally, Egat.d is a pared-down version of Zebt.a, both have the same creators.
Geography of mobile ransomware Trojans in Q1 2018 (percentage of attacked users)
TOP 10 countries by share of users attacked by mobile ransomware Trojans:
Country* %**
1 Kazakhstan 0.99
2 Italy 0.64
3 Ireland 0.63
4 Poland 0.61
5 Belgium 0.56
6 Austria 0.38
7 Romania 0.37
8 Hungary 0.34
9 Germany 0.33
10 Switzerland 0.29
* Excluded from the rating are countries where the number of users of Kaspersky Lab’s mobile antivirus is relatively small (fewer than 10,000)
** Unique users in the country attacked by mobile ransomware Trojans as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
First place in the TOP 10 again went to Kazakhstan (0.99%); the most active family in this country was Trojan-Ransom.AndroidOS.Small. Second came Italy (0.64%), where most attacks were the work of Trojan-Ransom.AndroidOS.Zebt.a, which is also the most popular mobile ransomware in third-place Ireland (0.63%).
Vulnerable apps used by cybercriminals
In Q1 2018, we observed some major changes in the distribution of exploits launched against users. The share of Microsoft Office exploits (47.15%) more than doubled compared with the average for 2017. This is also twice the quarterly score of the permanent leader in recent years — browser exploits (23.47%). The reason behind the sharp increase is clear: over the past year, so many different vulnerabilities have been found and exploited in Office applications, that it can only be compared to amount of Adobe Flash vulnerabilities found in the past. But lately the share of Flash exploits has been decreasing (2.57% in Q1), since Adobe and Microsoft are doing all they can to hinder the exploitation of Flash Player.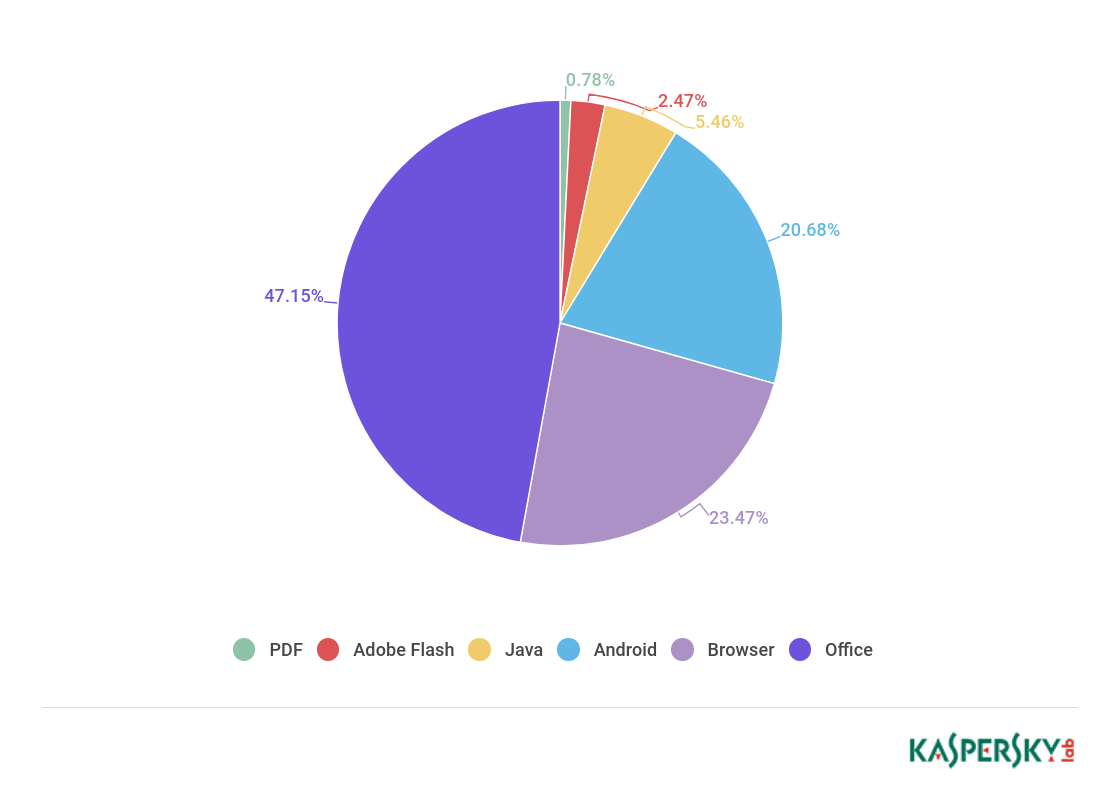
Distribution of exploits used in attacks by type of application attacked, Q1 2018
The most frequently used vulnerability in Microsoft Office in Q1 was CVE-2017-11882 — a stack overflow-type vulnerability in Equation Editor, a rather old component in the Office suite. Attacks using this vulnerability make up approximately one-sixth of all exploit-based attacks. This is presumably because CVE-2017-11882 exploitation is fairly reliable. Plus, the bytecode processed by Equation Editor allows the use of various obfuscations, which increases the chances of bypassing the protection and launching a successful attack (Kaspersky Lab’s Equation file format parser easily handles all currently known obfuscations). Another vulnerability found in Equation Editor this quarter was CVE-2018-0802. It too is exploited, but less actively. The following exploits for logical vulnerabilities in Office found in 2017 were also encountered: CVE-2017-8570, CVE-2017-8759, CVE-2017-0199. But even their combined number of attacks does not rival CVE-2017-11882.
As for zero-day exploits in Q1, CVE-2018-4878 was reported by a South Korean CERT and several other sources in late January. This is an Adobe Flash vulnerability originally used in targeted attacks (supposedly by the Scarcruft group). At the end of the quarter, an exploit for it appeared in the widespread GreenFlash Sundown, Magnitude, and RIG exploit kits. In targeted attacks, a Flash object with the exploit was embedded in a Word document, while exploit kits distribute it via web pages.
Large-scale use of network exploits using vulnerabilities patched by the MS17-010 update (those that exploited EternalBlue and other vulnerabilities from the Shadow Brokers leak) also continued throughout the quarter. MS17-010 exploits account for more than 25% of all network attacks that we registered.
Malicious programs online (attacks via web resources)
The statistics in this chapter are based on Web Anti-Virus, which protects users when malicious objects are downloaded from malicious/infected web pages. Malicious websites are specially created by cybercriminals; web resources with user-created content (for example, forums), as well as hacked legitimate resources, can be infected.
Online threats in the financial sector
Q1 events
In early 2018, the owners of the Trojan Dridex were particularly active. Throughout its years-long existence, this malware has acquired a solid infrastructure. Today, its main line of activity is compromising credentials for online banking services with subsequent theft of funds from bank accounts. Its accomplice is fellow banking Trojan Emotet. Discovered in 2014, this malware also belongs to a new breed of banking Trojans developed from scratch. However, it was located on the same network infrastructure as Dridex, suggesting a close link between the two families. But now Emotet has lost its banking functions and is used by attackers as a spam bot and loader with Dridex as the payload. Early this year, it was reported that the encryptor BitPaymer (discovered last year) was developed by the same group behind Dridex. As a result, the malware was rebranded FriedEx.
Q1 saw the arrest of the head of the criminal group responsible for the Carbanak and Cobalt malware attacks, it was reported by Europol. Starting in 2013, the criminal group attacked more than 40 organizations, causing damage to the financial industry estimated at more than EUR 1 billion. The main attack vector was to penetrate the target organization’s network by sending employees spear-phishing messages with malicious attachments. Having penetrated the internal network via the infected computers, the cybercriminals gained access to the ATM control servers, and through them to the ATMs themselves. Access to the infrastructure, servers, and ATMs allowed the cybercriminals to dispense cash without the use of bank cards, transfer money from the organisation to criminal accounts, and inflate bank balances with money mules being used to collect the proceeds.
Financial threat statistics
These statistics are based on detection verdicts of Kaspersky Lab products received from users who consented to provide statistical data. As of Q1 2017, the statistics include malicious programs for ATMs and POS terminals, but do not include mobile threats.
In Q1 2018, Kaspersky Lab solutions blocked attempts to launch one or more malicious programs designed to steal money from bank accounts on the computers of 204,448 users.
Number of unique users attacked by financial malware, Q1 2018
Geography of attacks
To evaluate and compare the risk of being infected by banking Trojans and ATM/POS malware worldwide, for each country we calculated the share of users of Kaspersky Lab products that faced this threat during the reporting period out of all users of our products in that country.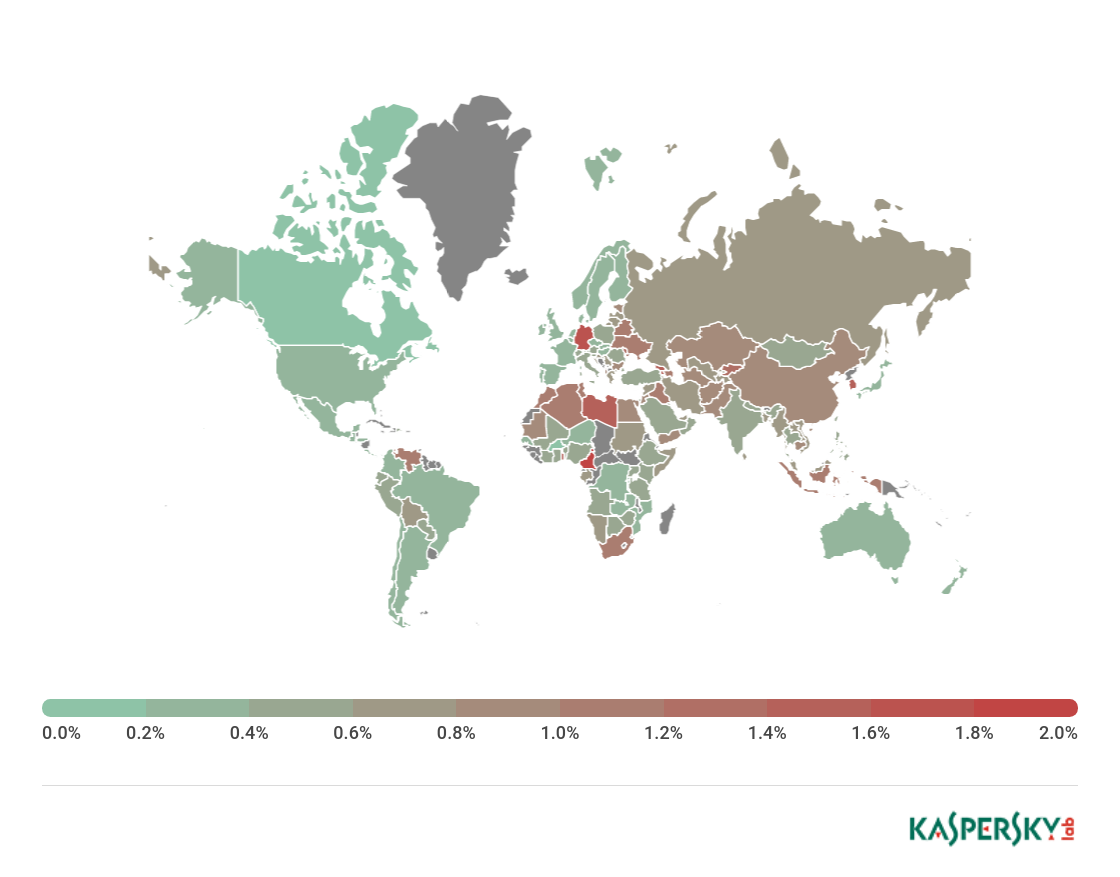
Geography of banking malware attacks in Q1 2018 (percentage of attacked users)
TOP 10 countries by percentage of attacked users
Country* % of users attacked**
1 Cameroon 2.1
2 Germany 1.7
3 South Korea 1.5
4 Libya 1.5
5 Togo 1.5
6 Armenia 1.4
7 Georgia 1.4
8 Moldova 1.2
9 Kyrgyzstan 1.2
10 Indonesia 1.1
These statistics are based on Anti-Virus detection verdicts received from users of Kaspersky Lab products who consented to provide statistical data.
Excluded are countries with relatively few Kaspersky Lab’ product users (under 10,000).
** Unique users whose computers were targeted by banking Trojans as a percentage of all unique users of Kaspersky Lab products in the country.
TOP 10 banking malware families
TOP 10 malware families used to attack online banking users in Q1 2018 (by share of attacked users):
Name Verdicts* % of attacked users**
1 Zbot Trojan.Win32. Zbot 28.0%
2 Nymaim Trojan.Win32. Nymaim 20.3%
3 Caphaw Backdoor.Win32. Caphaw 15.2%
4 SpyEye Backdoor.Win32. SpyEye 11.9%
5 NeutrinoPOS Trojan-Banker.Win32.NeutrinoPOS 4.5%
6 Emotet Backdoor.Win32. Emotet 2.4%
7 Neurevt Trojan.Win32. Neurevt 2.3%
8 Shiz Backdoor.Win32. Shiz 2.1%
9 Gozi Trojan.Win32. Gozi 1.9%
10 ZAccess Backdoor.Win32. ZAccess 1.3%
* Detection verdicts of Kaspersky Lab products. The information was provided by Kaspersky Lab product users who consented to provide statistical data.
** Unique users attacked by this malware as a percentage of all users attacked by financial malware.
In Q1 2018, TrickBot departed the rating to be replaced by Emotet (2.4%), also known as Heodo. Trojan.Win32.Zbot (28%) and Trojan.Win32.Nymaim (20.3%) remain in the lead, while Trojan.Win32.Neurevt (2.3%), also known as Betabot, suffered a major slide. Meanwhile, Caphaw (15.2%) and NeutrinoPOS (4.5%) climbed significantly, as did their Q1 activity.
Cryptoware programs
Q1 events
Q1 2018 passed without major incidents or mass cryptoware epidemics. The highlight was perhaps the emergence and widespread occurrence of a new Trojan called GandCrab. Notable features of the malware include:
Use of C&C servers in the .bit domain zone (this top-level domain is supported by an alternative decentralized DNS system based on Namecoin technology)
Ransom demand in the cryptocurrency Dash
GandCrab was first detected in January. The cybercriminals behind it used spam emails and exploit kits to deliver the cryptoware to victim computers.
The RaaS (ransomware as a service) distribution model continues to attract malware developers. In February, for example, there appeared a new piece of ransomware called Data Keeper, able to be distributed by any cybercriminal who so desired. Via a special resource on the Tor network, the creators of Data Keeper made it possible to generate executable files of the Trojan for subsequent distribution by “affilate program” participants. A dangerous feature of this malware is its ability to automatically propagate inside a local network. Despite this, Data Keeper did not achieve widespread distribution in Q1.
One notable success in the fight against cryptoware came from Europe: with the assistance of Kaspersky Lab, Belgian police managed to locate and confiscate a server used by the masterminds behind the Trojan Cryakl. Following the operation, Kaspersky Lab was given several private RSA keys required to decrypt files encrypted with certain versions of the Trojan. As a result, we were able to develop a tool to assist victims.
Number of new modifications
In Q1 2018, there appeared several new cryptors, but only one, GandCrab, was assigned a new family in our classification. The rest, which are not widely spread, continue to be detected with generic verdicts.
Number of new cryptoware modifications, Q2 2017 – Q1 2018
The number of new modifications fell sharply against previous quarters. The trend indicates that cybercriminals using this type of malware are becoming less active.
Number of users attacked by Trojan cryptors
During the reporting period, Kaspersky Lab products blocked cryptoware attacks on the computers of 179,934 unique users. Despite fewer new Trojan modifications, the number of attacked users did not fall against Q3.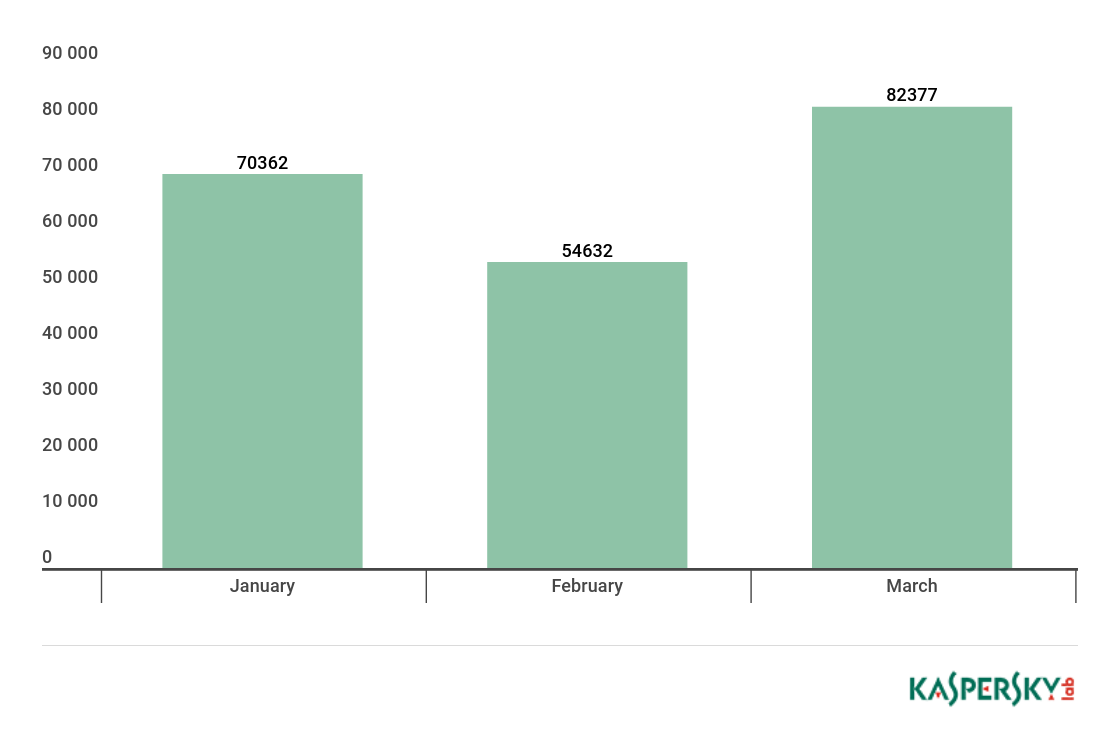
Number of unique users attacked by cryptors, Q1 2018
Geography of attacks
TOP 10 countries attacked by Trojan cryptors
Country* % of users attacked by cryptors**
1 Uzbekistan 1.12
2 Angola 1.11
3 Vietnam 1.04
4 Venezuela 0.95
5 Indonesia 0.95
6 Pakistan 0.93
7 China 0.87
8 Azerbaijan 0.75
9 Bangladesh 0.70
10 Mongolia 0.64
* Excluded are countries with relatively few Kaspersky Lab users (under 50,000).
** Unique users whose computers were attacked by Trojan cryptors as a percentage of all unique users of Kaspersky Lab products in the country.
The makeup of the rating differs markedly from 2017. That said, most positions were again filled by Asian countries, while Europe did not have a single representative in the TOP 10 countries attacked by cryptors.
Despite not making the TOP 10 last year, Uzbekistan (1.12%) and Angola (1.11%) came first and second. Vietnam (1.04%) moved from second to third, Indonesia (0.95%) from third to fifth, and China (0.87%) from fifth to seventh, while Venezuela (0.95%) climbed from eighth to fourth.
TOP 10 most widespread cryptor families
Name Verdicts* % of attacked users**
1 WannaCry Trojan-Ransom.Win32.Wanna 38.33
2 PolyRansom/VirLock Virus.Win32.PolyRansom 4.07
3 Cerber Trojan-Ransom.Win32.Zerber 4.06
4 Cryakl Trojan-Ransom.Win32.Cryakl 2.99
5 (generic verdict) Trojan-Ransom.Win32.Crypren 2.77
6 Shade Trojan-Ransom.Win32.Shade 2.61
7 Purgen/GlobeImposter Trojan-Ransom.Win32.Purgen 1.64
8 Crysis Trojan-Ransom.Win32.Crusis 1.62
9 Locky Trojan-Ransom.Win32.Locky 1.23
10 (generic verdict) Trojan-Ransom.Win32.Gen 1.15
* Statistics are based on detection verdicts of Kaspersky Lab products. The information was provided by Kaspersky Lab product users who consented to provide statistical data.
** Unique Kaspersky Lab users attacked by a particular family of Trojan cryptors as a percentage of all users attacked by Trojan cryptors.
This quarter, the rating is again topped by WannaCry (38.33%), extending its already impressive lead. Second place was claimed by PolyRansom (4.07%), also known as VirLock, a worm that’s been around for a while. This malware substitutes user files with modified instances of its own body, and places victim data inside these copies in an encrypted format. Statistics show that a new modification detected in December immediately began to attack user computers.
The remaining TOP 10 positions are taken by Trojans already known from previous reports: Cerber, Cryakl, Purgen, Crysis, Locky, and Shade.
Countries that are sources of web-based attacks: TOP 10
The following statistics show the distribution by country of the sources of Internet attacks blocked by Kaspersky Lab products on user computers (web pages with redirects to exploits, sites containing exploits and other malicious programs, botnet C&C centers, etc.). Any unique host could be the source of one or more web-based attacks.
To determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q1 2018, Kaspersky Lab solutions blocked 796,806,112 attacks launched from Internet resources located in 194 countries worldwide. 282,807,433 unique URLs were recognized as malicious by Web Anti-Virus components. These indicators are significantly higher than in previous quarters. This is largely explained by the large number of triggers in response to attempts to download web miners, which came to prominence towards the end of last year and continue to outweigh other web threats.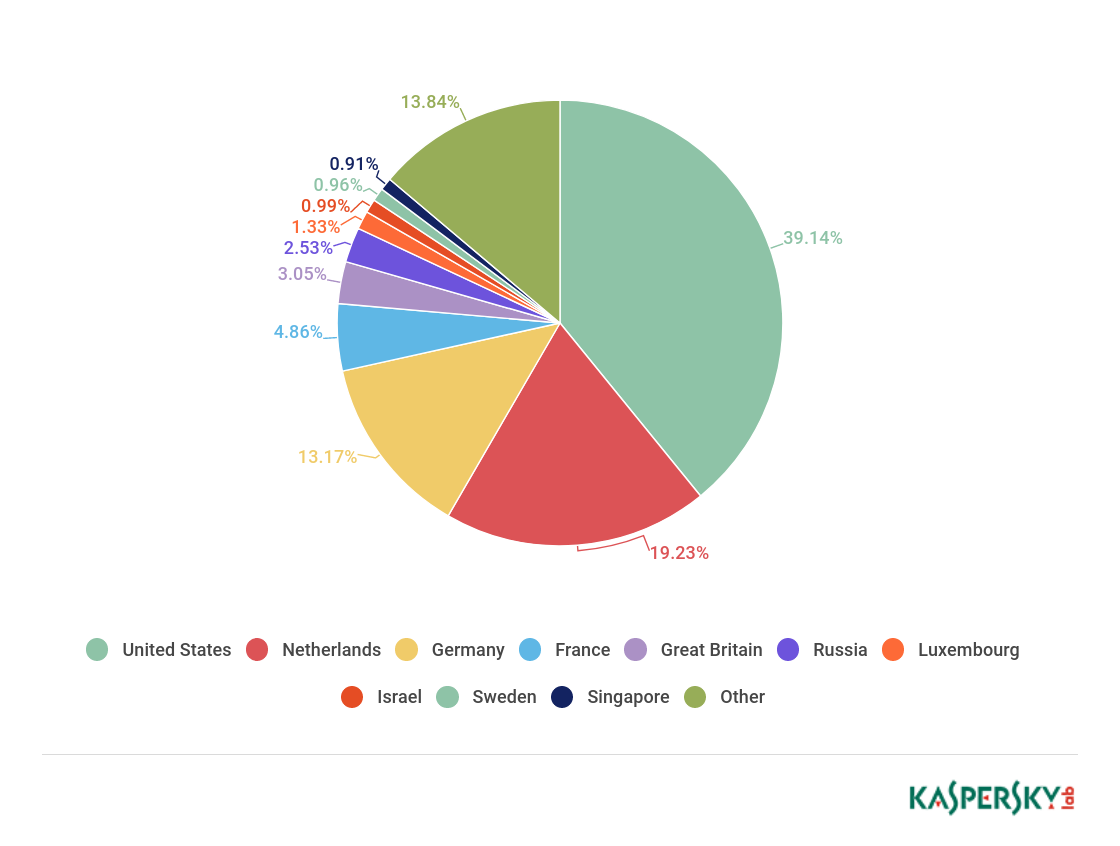
Distribution of web attack sources by country, Q1 2018
This quarter, Web Anti-Virus was most active on resources located in the US (39.14%). Canada, China, Ireland, and Ukraine dropped out of TOP 10 to be replaced by Luxembourg (1.33%), Israel (0.99%), Sweden (0.96%), and Singapore (0.91%).
Countries where users faced the greatest risk of online infection
To assess the risk of online infection faced by users in different countries, for each country we calculated the percentage of Kaspersky Lab users on whose computers Web Anti-Virus was triggered during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers operate in different countries.
This rating only includes attacks by malicious programs that fall under the Malware class; it does not include Web Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of attacked users**
1 Belarus 40.90
2 Ukraine 40.32
3 Algeria 39.69
4 Albania 37.33
5 Moldova 37.17
6 Greece 36.83
7 Armenia 36.78
8 Azerbaijan 35.13
9 Kazakhstan 34.64
10 Russia 34.56
11 Kyrgyzstan 33.77
12 Venezuela 33.10
13 Uzbekistan 31.52
14 Georgia 31.40
15 Latvia 29.85
16 Tunisia 29.77
17 Romania 29.09
18 Qatar 28.71
19 Vietnam 28.66
20 Serbia 28.55
These statistics are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky Lab products who consented to provide statistical data.
* Excluded are countries with relatively few Kaspersky Lab users (under 10,000).
** Unique users targeted by Malware-class attacks as a percentage of all unique users of Kaspersky Lab products in the country.
On average, 23.69% of Internet user computers worldwide experienced at least one Malware-class attack.
Geography of malicious web attacks in Q1 2018 (percentage of attacked users)
The countries with the safest surfing environments included Iran (9.06%), Singapore (8.94%), Puerto Rico (6.67%), Niger (5.14%), and Cuba (4.44%).
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems by infecting files or removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.).
Data in this section is based on analyzing statistics produced by Anti-Virus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media.
In Q1 2018, our File Anti-Virus detected 187,597,494 malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky Lab product users on whose computers File Anti-Virus was triggered during the reporting period. These statistics reflect the level of personal computer infection in different countries.
The rating includes only Malware-class attacks. It does not include File Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of attacked users**
1 Uzbekistan 57.03
2 Afghanistan 56.02
3 Yemen 54.99
4 Tajikistan 53.08
5 Algeria 49.07
6 Turkmenistan 48.68
7 Ethiopia 48.21
8 Mongolia 46.84
9 Kyrgyzstan 46.53
10 Sudan 46.44
11 Vietnam 46.38
12 Syria 46.12
13 Rwanda 46.09
14 Laos 45.66
15 Libya 45.50
16 Djibouti 44.96
17 Iraq 44.65
18 Mauritania 44.55
19 Kazakhstan 44.19
20 Bangladesh 44.15
These statistics are based on detection verdicts returned by OAS and ODS Anti-Virus modules received from users of Kaspersky Lab products who consented to provide statistical data. The data include detections of malicious programs located on user computers or removable media connected to computers, such as flash drives, camera and phone memory cards, or external hard drives.
* Excluded are countries with relatively few Kaspersky Lab users (under 10,000).
** Unique users on whose computers Malware-class local threats were blocked, as a percentage of all unique users of Kaspersky Lab products in the country.
On average, 23.39% of computers globally faced at least one Malware-class local threat in Q1.
The figure for Russia was 30.92%.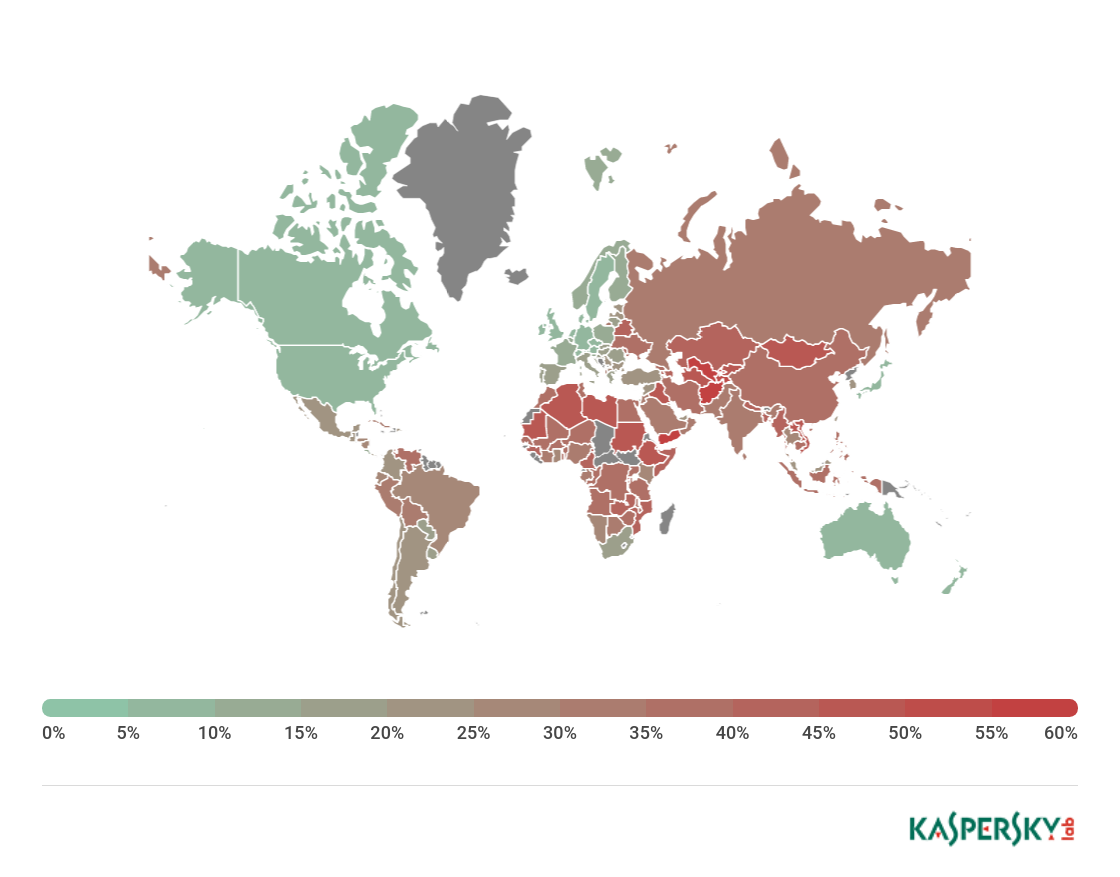
The safest countries in terms of infection risk included Estonia (15.86%), Singapore (11.97%), New Zealand (9.24%), Czech Republic (7.89%), Ireland (6.86%), and Japan (5.79%).
U.S. Jury Convicts Operator of Counter AV Service Scan4You
17.5.2018 securityweek Crime
A 37-year-old Latvian resident was convicted by a U.S. jury on Wednesday for his role in the operation of a counter antivirus service named Scan4You. Sentencing is scheduled for September 21.
Ruslans Bondars, a citizen of the former USSR, had been residing in Riga, Latvia, when he was arrested in May 2017 along with Russian national Jurijs Martisevs. Martisevs was on a trip to Latvia when he was taken into custody.
Bondars and Martisevs were accused of running the Scan4You service, which helped cybercriminals test their malware to ensure that it would not be detected by cybersecurity products.
Bondars was convicted on Wednesday on one count of conspiracy to violate the Computer Fraud and Abuse Act (CFAA), one count of conspiracy to commit wire fraud, and one count of computer intrusion with intent to cause damage and aiding and abetting.
Martisevs pleaded guilty in March to conspiracy, for which he faces up to 5 years in prison, and aiding and abetting computer intrusions, for which he faces 10 years in prison. His sentencing is scheduled for July.
According to Trend Micro, whose experts helped authorities investigate Scan4You, the service was launched in 2009 and was active until the arrests of its operators. An unnamed individual from Great Falls, Virginia, was also allegedly involved.
Bondars (known online as b0rland and Borland) and Martisevs (known online as Garrik) started their cybercrime career in at least 2006, and they managed to turn Scan4You into one of the largest counter antivirus services, with thousands of customers.
Scan4You allowed cybercriminals to conduct 100,000 scans per month for $30 and $0.15 for single scans. The service was also popular among counter antivirus resellers such as Indetectables, RazorScanner and reFUD.me.
Trend Micro says Bondars and Martisevs were also involved with a shady online pharmacy and launched their own banking malware campaigns.
However, they did a poor job at hiding their identity. Bondars, for instance, used the same Gmail account to register command and control (C&C) domains for his banking malware and to create a Facebook account. The Gmail account contained his real name and profile photo.
According to authorities, Scan4You was used to test the malware involved in the massive 2013 breach at the U.S. retailer Target. The service was also used in the development of Citadel, a banking trojan that infected over 11 million computers worldwide, which resulted in over $500 million in fraud-related losses.
U.S. Senate Votes to Restore 'Net Neutrality' Rules
17.5.2018 securityweek BigBrothers
The US Senate voted Wednesday to restore so-called "net neutrality" rules aimed at requiring all online data to be treated equally, the latest step in a years-long battle on internet regulation.
The 52-47 vote is likely to be symbolic, however, since the measure faces an uphill battle in the House of Representatives and would need enough lawmaker support to overturn a probable presidential veto.
The vote marked the latest step in a contentious fight over rules governing online access over the past decade including court challenges and various moves by regulators.
Related: Security Implications of the End of Net Neutrality
In December, the Federal Communications Commission voted 3-2 along party lines to reverse a 2015 order which established net neutrality and which itself had faced court challenges and intense partisan debate.
In the Senate, three Republicans joined Democrats in the vote under the Congressional Review Act, which allows lawmakers to overturn a regulatory body.
FCC chairman Ajit Pai, appointed by President Donald Trump, has argued that the 2015 rules were "heavy-handed" and failed to take into account the rapidly changing landscape for online services and were discouraging investment in advanced networks.
Net neutrality backers have argued that clear rules are needed to prevent internet service providers from blocking or throttling services or websites for competitive reasons.
Some activists fear internet service providers will seek to extract higher fees from services that are heavy data users, like Netflix or other streaming services, with these costs passed on to consumers.
The battle has been largely along party lines, and has also been split with large tech firms supporting neutrality and telecom operators backing more flexible rules.
Although the Senate vote may not succeed in restoring neutrality rules, backers said it would allow voters to know where their lawmakers stand.
Democratic Senator Ed Markey said on Twitter the vote would "show the American people who sides with them, and who sides with the powerful special interests and corporate donors who are thriving under the @realDonaldTrump administration."
Ferras Vinh of the Center for Democracy & Technology, a digital rights group, welcomed the vote.
"Without net neutrality protections, internet service providers will have an explicit license to block, slow, or levy tolls on content, which will limit choices for internet users and suffocate small businesses looking to enter the market," Vinh said.
"These protections are the guiding principles of the open internet, facilitating innovation and enabling the spread of new ideas."
But USTelecom, an industry group representing major broadband carriers, expressed disappointment.
"This vote throws into reverse our shared goal of maintaining an open, thriving internet," said association president Jonathan Spalter.
"Consumers want permanent, comprehensive online protections, not half measures or election-year posturing from our representatives in Congress."
Mexican central bank confirmed that SWIFT hackers stole millions of dollars from Mexican Banks
17.5.2018 securityaffairs Hacking
The head of the Mexican central bank, Alejandro Diaz de Leon announced this week that hackers were involved in shadowy transfers of between $18 million and $20 million.
Mexican central bank is the last victim of the SWIFT hackers, officials at the bank confirmed this week that hackers hit the payments system and stole millions of dollars from domestic banks.
The attack was discovered in late April and presents many similarities with past attacks against the SWIFT systems.
The Mexican central bank did not disclose the name of the banks that were hit by the cyber attack and did not detail the overall amount of money that crooks have stolen.
According to Alejandro Diaz de Leon, head of Mexico’s central bank, crooks were able to complete illicit transactions of $18 million to $20 million.
“Central bank Governor Alejandro Diaz de Leon said on Monday that the country had seen an unprecedented attack on payment system connections and that he hoped that measures being taken would stop future incidents.” reported the Reuters.
“A source close to the government’s investigation said more than 300 million had been siphoned out of banks, but it was not clear how much had subsequently been taken out in cash withdrawals.”

According to reports, Mexico’s central following the latest cyber attacks has created a cybersecurity division, and it has instituted a one-day waiting period on electronic funds transfers of more than $2,500.
“Perhaps, some financial institutions perceived the attacks in Bangladesh as something very distant,” said Alejandro Diaz de Leon who believes that some Mexican banks may not have invested in sufficient security measures.
“But criminals look for vulnerability and once they see it they are going to exploit it.”
Mexican depositors won’t be affected, but the overall losses for the local banks could be greater than initially thought.
Critical Code Execution Flaws Patched in Advantech WebAccess
16.5.2018 securityweek Vulnerebility
Taiwan-based industrial automation company Advantech has released an update for its WebAccess product to address nearly a dozen vulnerabilities, including critical flaws that allow arbitrary code execution.
Advantech WebAccess is a browser-based software package for human-machine interfaces (HMI) and supervisory control and data acquisition (SCADA) systems. The product is used in the United States, Europe and East Asia in the energy, critical manufacturing, and water and wastewater sectors.
The list of security holes rated critical includes unrestricted file upload, path traversal, stack-based buffer overflow, and untrusted pointer dereference issues, all of which can be exploited for arbitrary code execution.
Advantech has also fixed high severity vulnerabilities that can be exploited to obtain sensitive information, modify files, and delete files. There are also a couple of medium severity issues that can be leveraged to steal session cookies and obtain potentially sensitive data through SQL injection.
According to ICS-CERT, the flaws affect WebAccess versions V8.2_20170817 and prior, WebAccess V8.3.0 and prior, WebAccess Dashboard V.2.0.15 and prior, WebAccess Scada Node versions prior to 8.3.1, and WebAccess/NMS 2.0.3 and prior. The vendor patched them with the release of version 8.3.1 last week.
ICS-CERT has credited researchers Mat Powell, Andrea Micalizzi (rgod), Steven Seeley, Donato Onofri and Simone Onofri for discovering the security bugs. Many of the weaknesses were reported through Trend Micro’s Zero Day Initiative (ZDI), which will publish advisories in the coming weeks.
Seeley has identified tens of vulnerabilities in WebAccess this year, and some of them, affecting WebAccess HMI Designer, were disclosed in April before Advantech released patches.
ICS-CERT has published a total of four advisories for Advantech WebAccess vulnerabilities this year, including two in January.
A report published last year by Trend Micro’s Zero Day Initiative (ZDI) showed that it had taken Advantech, on average, 131 days to patch vulnerabilities, which was significantly better compared to many other major ICS vendors. ZDI published more than 50 advisories for Advantech vulnerabilities in 2017, which was roughly half the number published in the previous year.
Facebook Suspends 200 Apps Over Data Misuse
16.5.2018 securityweek Social
Facebook said Monday it has suspended "around 200" apps on its platform as part of an investigation into misuse of private user data.
The investigation was launched after revelations that political consulting firm Cambridge Analytica hijacked data on some 87 million Facebook users as it worked on Donald Trump's 2016 campaign.
"The investigation process is in full swing," said an online statement from Facebook product partnerships vice president Ime Archibong.
"We have large teams of internal and external experts working hard to investigate these apps as quickly as possible. To date thousands of apps have been investigated and around 200 have been suspended -- pending a thorough investigation into whether they did in fact misuse any data."
Archibong added that "where we find evidence that these or other apps did misuse data, we will ban them and notify people via this website."
The revelations over Cambridge Analytica have prompted investigations on both sides of the Atlantic and led Facebook to tighten its policies on how personal data is shared and accessed.
Facebook made a policy change in 2014 limiting access to user data but noted that some applications still had data it had obtained prior to the revision.
"There is a lot more work to be done to find all the apps that may have misused people's Facebook data -- and it will take time," Archibong said.
Behind the Scenes in the Deceptive App Wars
16.5.2018 securityweek Security
All is not well in the app ecosphere. That ecosphere comprises a large number of useful apps that benefit users, and an unknown number of apps that deceive users. The latter are sometimes described potentially unwanted programs, or PUPs. Both categories need to make money: good apps are upfront with how this is achieved; deceptive apps hide the process.
In recent years there has been an increasing effort to cleanse the ecosphere of deceptive apps. The anti-virus (AV) industry has taken a more aggressive stance in flagging and sometimes removing what it calls PUPs; the Clean Software Alliance (CSA) was founded to help guide app developers away from the dark side; and a new firm, AppEsteem, certifies good apps and calls out bad apps in its ‘Deceptor’ program.
One name figures throughout: Dennis Batchelder. He is currently president of the AV-dominated Anti-Malware Testing Standards Organization (AMTSO); was a leading light in the formation, and until recently a member of the advisory board, of the CSA; and is the founder of AppEsteem.
But there has been a falling out between the CSA and AppEsteem.
The CSA
The CSA was officially launched in the Fall of 2015, although it had already been on the drawing board for over a year. Batchelder was instrumental in getting it started while he was working for Microsoft, where he was director, program management until April 2016.
The CSA was introduced during VB2015 with a joint presentation from Microsoft and Google, demonstrating early support from the industry’s big-hitters.
“As a 501(c)(6) nonprofit trade association,” writes the CSA on its website, “the CSA works to advance the interests of the software development community through the establishment and enforcement of guidelines, policies and technology tools that balance the software industry’s needs while preserving user choice and user control.”
In other words, it seeks to develop an app ecosphere where honest developers can be fairly recompensed, via monetization, for their labor. However, it provides very little information on its website. It does not, for example, list the members of the trade association, nor give any indication on how it will enforce its guidelines and policies on recalcitrant apps.
AppEsteem
Founded by Batchelder in 2016, AppEsteem is primarily an app certification organization – it certifies clean apps. However, since a carrot works best when supported by a stick, AppEsteem also calls out those apps it considers to be deceptive and therefore potentially harmful to users.
Batchelder hoped that the CSA and AppEsteem could work together (he was on the advisory board of the former and is president of the latter). The CSA could provide recommendations and industry support on classification criteria, and AppEsteem – at one step removed – could provide the enforcement element apparently missing in the CSA.
AppEsteem maintains what it calls the ‘deceptor list’; a list of apps that in its own judgement use deceptive means to increase their monetization potential. At the time of writing, there are more than 300 apps on the deceptor list. It also actively encourages AV firms to use this list in their own attempts at blocking PUPs.
There is a difficult balance. Deceptive app developers will object to being included on a public shaming list. Apps that get clean need to be removed in a timely fashion. New methods of deception need to be recognized and included in the bad behavior criteria.
It is, in short, a process wide open for criticism from app developers who are called out.
CSA criticizes AppEsteem
Criticism came last week from an unexpected source – from the CSA. On 10 May 2018, the CSA published a remarkably negative report on AppEsteem’s ‘deceptor’ program titled, CSA Review of AppEsteem Programs. It was, said the CSA, “triggered by a groundswell of complaints and expressions of concern received by the CSA from industry members regarding this program.”
The report is largely – although not entirely – negative. It raises some interesting points. The ‘groundswell of complaints’ is to be expected; particularly from the apps and the app developers called out for being deceptive.
However, concern over some other elements seem valid. AppEsteem does not seem keen to call out AV products, even when they appear to use ‘deceptive’ practices (consider, for example, the ease with which the user can download one product and find that McAfee has also been downloaded).
Furthermore, if certification is annual, a certified app could introduce deceptive practices immediately after certification that would go undetected (would effectively be allowed) for 12 months. “There is no more deceptive or risky behavior than that,” notes the report.
The CSA report makes four proposals. AppEsteem should: refocus efforts on certification; work with the CSA to devise consensus‐built ‘minbar’ criteria; balance violator identification and remediation; and embrace oversight and dispute resolution.
‘Oversight’ implies external management. Refocusing on certification implies abandoning the deceptor app listing. And ‘work with the CSA’ implies that AppEsteem should take its direction from the CSA. If not quite a power grab, the report attempts to neutralize the enforcement element of AppEsteem.
AppEsteem’s response
AppEsteem’s first response was for Batchelder to resign from the CSA advisory board. “I unable to figure out how to remain on the CSA Advisory Board in good conscience,” he wrote to the CSA. “Which sucks, as I’ve pushed for CSA to get operational and remain relevant, sent potential members its way, and worked hard to help it succeed. But being an advisor of an incorporator-status organization who is conducting a ‘confidential’ investigation into AppEsteem’s certification program without involving AppEsteem makes no sense at all.”
AppEsteem’s second response was to establish CleanApps.org; which is effectively an alternative to the CSA. “AppEsteem needs CSA,” comments one source who asked to be anonymous, “or at least some organization that can provide guidelines and some kind of oversight of what AppEsteem is doing… It seems that this new player is in fact a company created by Dennis trying to get rid of CSA.”
That partly makes sense. If AppEsteem cannot work with the CSA, it must find a similar organization it can work with. “After I disengaged from CSA, Batchelder told SecurityWeek, “we realized that AppEsteem had to find a way to get the vendor voice and to reassure them that we’re doing things fairly (the stuff we had hoped CSA would do). So, I incorporated CleanApps.org and recruited its first board from some of our customers (I know, it’s like a soap opera), and then resigned/handed it over once the board launched. Our goal is that once CleanApps.org launches, we’ll give them insight into our operations.”
To the CSA, he wrote in February, “I wanted to let you know that we have determined that it’s in best interests of both ourselves, our customers, and the vendor community if we had oversight and a ‘voice’ specifically representing the vendor community… We won’t become a member or hold any position in CleanApps.org; they will self-govern.” (He has since made it clear that he does not mean ‘oversight’ in any controlling manner.)
AppEsteem’s position seems to be that the app ecosphere requires three organizations: AppEsteem to enforce good behavior among the app developers; the CSA to represent the market in which apps operate; and CleanApps to represent the apps and app developers.
But it is clearly concerned over the current relevance of the CSA. “I think the biggest hole with CSA,” Batchelder told SecurityWeek, “is that they never finished forming: it’s still just… as the only member, and what we felt was that when [that member] had an issue with us, CSA went negative… it’s problematic to us that they’re not formed after four years.”
If AppEsteem needs something like the CSA to be effective, the CSA needs something like AppEsteem to be relevant.
AppEsteem’s third response is a short blog posted on the same day as CSA published its report – Thursday, 10 May 2018. There is no indication of any rapprochement with the CSA. “But we also want to be clear,” writes the author: “if you think it’s fine to treat consumers as exploitable targets for deceptive and aggressive software, we totally understand your desire for us to leave you alone. We strongly suggest you either get on board or find something else to do with your time, as we’re going to continue to tune our Deceptor program to find even more effective ways to disrupt your ability to hurt consumers.”
The way forward
It is hard to see how any outright deceptive app produced by developers simply out to get as much money as possible will ever be persuaded by force of argument alone to abandon deceptive practices. This seems to be the approach of the CSA; and it appears – on the evidence of its website – to have achieved little in its three to four years of existence.
Indeed, the one and only report the CSA has published is the report criticizing AppEsteem. Before that, the previous publication seems to be ‘update #7’, probably written around March 2016.
If the CSA has achieved anything, it is not saying so. At the very least, it could be urged to be more transparent in its operations and achievements – even a list of members would be useful.
Meantime, if the new CleanApps.org gathers pace and support, the CSA itself will become increasingly irrelevant in the battle against deceptive apps; that is, potentially unwanted programs.
Security Gaps Remain as OT, IT Converge
16.5.2018 securityweek Cyber
The accelerating digitization of business, driven by compelling commercial arguments, is driving the integration of new information technology (IT) networks with older operational technology (OT) networks. This is introducing new security risks to old technology and old technology practices -- and where the OT is driving a critical manufacturing plant, the new risk is from nation-state actors as well as traditional cyber criminals.
The good news is that many organizations understand the risks and are actively engaged in mitigating those risks. The bad news is the risk mitigation process is far from complete.
Network and content security firm Fortinet commissioned Forrester Consulting to survey the state of converging IT / OT network security. In an associated blog, Fortinet's senior director of product marketing, Peter Newton, explains the cultural difference between IT and OT security: "IT teams have a tendency to just want to throw security technology at the network and call it good. But these networks can be very different, and what works well in one environment can have devastating consequences in the other. For example, an error that opens a port on a switch can have a very different result from one that opens a valve on a boiler."
In January 2018, Forrester queried 429 global decision-makers responsible for the security of their organization’s critical infrastructure from a range of different industries, asking about their IT / OT convergence (PDF) and the security challenges being faced. The result suggests that awareness is high, and steps are in progress (SCADA / ICS security spending is planned to increase by 77%) -- but there is much yet to be done (45% of respondents do not used privileged account management (PAM) for their administrators).
The last issue is particularly relevant given the extent to which converged networks are being opened to third-party suppliers. Sixty-four percent of the companies surveyed provide either complete or high-level access to their SCADA / ICS, including to outsourced suppliers, business partners and government agencies. This seems to be changing, with respondents taking steps to reduce the number of vendors used to provide security functions for IPS, NAC and IoT.
"The number of organizations that now rely on a single vendor to provide a full range of outsourced solutions has jumped from 38% to 47% between 2016 and 2018," comments John Maddison, Fortinet's SVP products and solutions, in a separate blog post.
Coupled with the lack of a PAM solution, the report highlights that 45% of the respondents do not use role-based access control, which provides openings for insider threats. Indeed, internal hackers are considered a greater threat (77% of respondents are extremely or very concerned) than external hackers (70%). The greatest concern is reserved for malware at 77%, with leakage of sensitive or confidential data at 70%.
The security threat is not hypothetical. While there have already been severaal highly-publicized incidents (such as the Ukraine power outages in December 2015, and the U.S. water utility incident in March 2016) the majority of respondents have also experienced a breach. Fifty-six percent of organizations using SCADA / ICS reported a breach in the past year, and only 11% indicated they have never been breached.
SCADA / ICS breaches can have serious consequences. "Sixty-three percent of organizations say the safety of their employees was highly or critically impacted by a SCADA / ICS security breach," notes the report. "Another 58% report major impacts to their organization’s financial stability, and 63% note a serious drag on their ability to operate at a sufficient level."
Solutions to the growing SCADA / ICS risk exist, but require a new approach beyond the traditional IT security approach. IT and OT teams speak different languages for security, comments Newton. Existing OT systems may be running on an obsolete operating system on hardware that is ten or more years old. "But that may be because it only has one job," he explains: "for example, monitoring a thermostat and then throwing a switch when it reaches a critical temperature. That doesn’t require the latest technology, and if it is doing the job it was designed to do, then there is no reason to change it. But because so many of these systems run on proprietary software and use delicate instrumentation, even something as benign as scanning a device for malware can cause it to malfunction."
Solutions do exist, but must be chosen with care. "When considering a security vendor for their SCADA / ICS environments," suggests Newton, "the ability to meet compliance standards and provide end-to-end solutions, along with a reputation for reliability are the most important attributes [the respondents] look for. These organizations are looking for solutions from a variety of vendors, from systems integrators to security manufacturers."
Hackers Divert Funds From Mexico Banks, Amount Unclear: Official
16.5.2018 securityweek Hacking
Hackers have stolen an unknown amount of money from banks in Mexico in a series of cyber attacks on the country's interbank payments system, an official said Monday.
At least five attacks on the Mexican central bank's Interbank Electronic Payments System (SPEI) were carried out in April and May, said Lorenza Martinez, director general of the corporate payments and services system at the central bank.
"Some transactions were introduced that were not recognized by the issuing bank," she told Radio Centro.
"In some cases these transfers made it through to the destination bank and were withdrawn in cash."
She declined to reveal which banks were targeted.
Some Mexican media outlets have put the amount stolen at 400 million pesos ($20.4 million), but Martinez denied those reports.
"The amount is currently being analyzed. Some of the transfers were stopped, and the funds are currently being returned," she said.
She said the money stolen belonged to the banks themselves and that clients' funds were never affected.
The interbank payments system allows banks to make real-time transfers to each other.
They connect via their own computer systems or an external provider -- the point where the attacks appear to have taken place, Martinez said.
After the attacks were detected, banks switched to a slower but more secure method.
No new attacks have been registered since.
Adobe Patches Two Dozen Critical Flaws in Acrobat, Reader
16.5.2018 securityweek Vulnerebility
Updates released on Monday by Adobe for its Acrobat, Reader and Photoshop products patch nearly 50 vulnerabilities, including a remote code execution flaw that has been exploited in the wild.
A total of 47 security holes have been addressed in the Windows and macOS versions of Acrobat DC (Consumer and Classic 2015), Acrobat Reader DC (Consumer and Classic 2015), Acrobat 2017, and Acrobat Reader 2017. The flaws have been resolved with the release of versions 2018.011.20040, 2017.011.30080 and 2015.006.30418.
The vulnerabilities include 24 critical memory corruptions that allow arbitrary code execution in the context of the targeted user, and various types of “important” issues that can lead to information disclosure or security bypasses.
The most serious of the flaws is CVE-2018-4990, which has been exploited in the wild in combination with CVE-2018-8120, a zero-day vulnerability affecting Windows. CVE-2018-8120 was fixed by Microsoft with the May 2018 Patch Tuesday updates.
Independent experts and researchers from Cisco Talos, ESET, Kaspersky, Check Point, Palo Alto Networks, Tencent, Knownsec 404 Security Team, Cybellum and Cure53 have been credited for responsibly disclosing the flaws patched with the latest Acrobat and Reader releases. Many of the security bugs were reported to Adobe through Trend Micro’s Zero Day Initiative (ZDI).
Adobe also informed customers that support for Acrobat and Reader 11.x ended on October 15, 2017, and that version 11.0.23 is the final release for these branches. Users have been advised to update to the latest versions of Acrobat DC and Acrobat Reader DC.
Adobe has also released security updates for the Windows and macOS versions of Photoshop CC to address a flaw reported by researcher Giwan Go.
Photoshop CC 2018 version 19.1.4 and Photoshop CC 2017 version 18.1.4 fix a critical out-of-bounds write issue that can be exploited for arbitrary code execution in the context of the targeted user.
Earlier this month, Adobe patched several vulnerabilities in its Flash Player, Creative Cloud and Connect products with the company’s Patch Tuesday updates.
The previous round of security updates for Acrobat and Reader resolved 39 vulnerabilities. However, those updates had been assigned a priority rating of “2,” which makes them less likely to be exploited, while the latest patches have been given a priority rating of “1,” which means exploitation is more likely and users should update as soon as possible.
*Updated with information on CVE-2018-4990
Symantec Shares More Information on Internal Investigation
16.5.2018 securityweek IT
Symantec shares gained nearly 10 percent on Monday in anticipation of a conference call that promised to provide more information regarding the internal investigation announced by the company last week.
Along with its financial results for the fourth quarter and full year, Symantec told investors last week that the Audit Committee of the Board of Directors had launched an investigation as a result of concerns raised by a former employee.
The company initially did not share any additional information, except that the Securities and Exchange Commission (SEC) had been notified and that the probe would likely prevent it from filing its annual 10-K report with the SEC in a timely manner.
Symantec shares dropped roughly 20 percent to less than $24 after the announcement was made on Thursday, and on Friday shares dove 33 percent, reaching just over $19.
A conference call announced for Monday afternoon helped the company gain nearly 10 percent, closing at $21.40.
While many expected Symantec to provide details on its internal probe, the company did not answer any questions on the matter. A statement published by the company does, however, reveal that the investigation is related to “concerns raised by a former employee regarding the Company’s public disclosures including commentary on historical financial results, its reporting of certain Non-GAAP measures including those that could impact executive compensation programs, certain forward-looking statements, stock trading plans and retaliation.”
The company says it cannot predict the duration of the investigation or the outcome, which could have an impact on financial results and guidance.
The cybersecurity firm says it does not anticipate a material adverse impact on its historical financial statements.
In response to news of the internal probe, investor rights law firm Rosen Law Firm announced the preparation of a class action to recover losses suffered by Symantec investors. Rosen says it’s investigating allegations that Symantec “may have issued materially misleading business information to the investing public.”
Kaspersky Lab to Move Core Infrastructure to Switzerland
16.5.2018 securityweek BigBrothers
Swiss Data Storage
Company Will Open Transparency Center in Zurich by 2019; Data From Customers in North America Will be Stored and Processed in Switzerland
As part of its Global Transparency Initiative, Russia-based Kaspersky Lab today announced that it will adjust its infrastructure to move a number of "core processes" from Russia to Switzerland.
The security firm has had problems with the U.S. government. In September 2017, the U.S. Department of Homeland Security (DHS) instructed government departments and agencies to stop using products from the Russia-based firm.
There is no hard evidence that Kaspersky has ever colluded with the Russian government; and the lost U.S. government market is small in global terms. The bigger problem, however, is the knock-on effect that U.S. government criticism has on trust levels in the wider market.
In December 2017, Lithuania banned the use of Kaspersky Lab software within certain critical national industries. In April 2018, Twitter stopped accepting ads From Kaspersky Lab; and now, on May 15, 2018, the Dutch government announced it will phase out Kaspersky Lab anti-virus software 'as a precautionary measure'.
Justice Minister Ferdinand Grapperhaus told the Dutch parliament, “The (Dutch) cabinet has carried out an independent review and analysis and made a careful decision on that basis. Although there are no concrete cases of misuse known in the Netherlands, it cannot be excluded.”
Kaspersky Lab Logo
In December 2017, the UK's National Cyber Security Center published a letter it had sent to government permanent secretaries. It included, "In practical terms, this means that for systems processing information classified SECRET and above, a Russia-based provider should never be used."
It is to maintain or regain trust that is behind Kaspersky's Global Transparency Initiative, announced in October 2017.
"The new measures," the firm announced, "comprise the move of data storage and processing for a number of regions, the relocation of software assembly and the opening of the first Transparency Center," which will be in Zurich.
The measures in question include customer data storage and processing for most regions; and software assembly including threat detection updates. Transparency will be provided by making the source code available for review by responsible stakeholders in a dedicated Transparency Center.
The company said that by the end of 2018, its products and threat detection rule databases (AV databases) "will start to be assembled and signed with a digital signature in Switzerland, before being distributed to the endpoints of customers worldwide."
The firm is going further by making plans for its processes and source code to be independently supervised by a qualified third-party. To this end, it is supporting the creation of a new, non-profit organization able to assume this responsibility not just for itself, but for other partners and members who wish to join.
“The third-party organization is a non-profit organization to be established independently for the purpose of producing professional technical reviews of the trustworthiness of the security products of its members (including Kaspersky Lab)," the firm told SecurityWeek.
“Since transparency and trust are becoming universal requirements across the cybersecurity industry, Kaspersky Lab is supporting the creation of a new, non-profit organization to take on this responsibility, not just for the company, but for other partners and members who wish to join. The details of the new organization are currently being discussed and will be shared as soon as they are available.”
Switzerland has been chosen as the site of the Center as much for its symbolic importance as anything else. “We considered several locations for our first Transparency Center, and Switzerland most closely met our criteria as well as our policy of complete neutrality," Kaspersky Lab told SecurityWeek.
"We detect and remediate any malware, regardless of its source or purpose, while Switzerland has a long and famous history of neutrality. We also value Switzerland’s robust approach to data protection legislation.” Noticeably, Switzerland is one of just a handful of non-EU companies that has been recognized by Europe as having 'adequate' privacy controls.
Noticeably, Kaspersky Lab does not link the move specifically to the effects of the U.S. ban, but sees wider issues of global trust emerging. “We are implementing these measures first and foremost in response to the evolving, ultra-connected global landscape and the challenges the cyber-world is currently facing," it said.
"This is not exclusive to Kaspersky Lab, and we believe other organizations will in future also choose to adapt to these trends. Having said that, the overall aim of these measures is transparency, verified and proven, which means that anyone with concerns will now be able to see the integrity and trustworthiness of our solutions.”
Exploiting People Instead of Software: Report Shows Attacker Love for Human Interaction
16.5.2018 securityweek Exploit
Cybercriminals Continue to Rely on Human Interaction to Conduct Wide Range of Attacks
Cybercriminals have been scaling up people-centered threats, increasingly using social engineering rather than automated exploits even in web attacks, a recent report from Proofpoint report reveals.
Humans have been long said to be the best exploits in the eyes of cybecriminals, with social engineering becoming the most used attack method years back, when almost all attached documents and URLs in malicious emails required human interaction.
Now, Proofpoint’s The Human Factor 2018 report (PDF) reveals that both cybercriminals and threat actors have found new ways to trick victims into becoming their unwitting accomplices. Email remained the most popular attack vector, while the rise of crypto-currency drove innovations in phishing and cybercrime.
Proofpoint saw attacks that include both large, multimillion-message malicious campaigns distributing malware such as ransomware (the biggest email-borne threat of 2017) and highly targeted assaults orchestrated by state-sponsored groups and financially motivated fraudsters.
“Whether they are broad-based or targeted; whether delivered via email, social media, the web, cloud apps, or other vectors; whether they are motivated by financial gain or national interests, the social engineering tactics used in these attacks work time and time again. Victims clicked malicious links, downloaded unsafe files, installed malware, transferred funds, and disclosed sensitive information at scale,” Proofpoint notes.
Last year, suspiciously registered domains of large enterprises outnumbered brand-registered domains 20 to 1, according to the report. Furthermore, 95% of observed web-based attacks used social engineering to trick users into installing malware, 55% of social media attacks impersonating customer-support accounts targeted customers of financial services companies, and 35% of social media scams using links took users to video streaming and movie download sites.
Dropbox phishing was the top lure for phishing attacks, but click rates for Docusign lures were the highest. Network traffic of coin mining bots jumped almost 90% between September and November, while ransomware and banking Trojans accounted for more than 82% of all malicious email messages. Although used often in email campaigns, Microsoft Office exploits usually came in short bursts.
The largest numbers of email fraud attacks hit education, management consulting, entertainment, and media firms, while construction, manufacturing, and technology were the most phished industries. Manufacturing, healthcare, and technology firms were targeted the most by crimeware.
Although ransomware predominated worldwide, banking Trojans were highly popular in Europe and Japan, accounting for 36% and 37% of all malicious mail in those regions, respectively.
Proofpoint has examined hundreds of thousands of SaaS accounts during risk assessments conducted across industries and says that around 1% of all cloud service credentials have been leaked. Furthermore, the security firm discovered that 25% of all suspicious login attempts to cloud services were successful (24% of all logins to cloud services were suspicious).
Attackers are increasingly using cloud services that users are accustomed to receive email notifications from to send malicious messages and host malware. While no major cloud services avoided abuse, services such as G Suite and Evernote were used to send phishing emails and malware.
“Most cloud platforms are extensible. Third-party add-ons open up new features, but they also create possibilities for abuse. We found a vulnerability in Google Apps Script, for example, that allowed attackers to send malware through legitimate emails that came from G Suite accounts,” the security researchers report.
Looking at how people behave in response to these threats, Proofpoint discovered that North American employees tended to click at the beginning of the work day, at lunch, and the end of the work day. South America followed a similar pattern, but Australian employees were more likely to click in the morning.
Half of all clicks (52%), however occurred within one hour of the message being delivered, with 11% of recipients clicking on the malicious URL within the first minute and a quarter within 5 minutes.
Usually focused on high-profile targets, state-sponsored attackers and established cyber criminals switched to targeting smaller targets in 2017.
The North Korea- affiliated Lazarus Group launched multistage attacks against individuals and point-of-sale (POS) infrastructure to steal cryptocurrency and consumer credit card data. The financially-motivated FIN7 started targeting individuals within restaurant chains using a new backdoor and malicious macros.
The Cobalt Group used new malware and document exploits in attacks against financial institutions and used anti-sandbox features to make detection more difficult.
The security firm also observed cryptocurrency phishing campaigns and identified sophisticated phishing templates targeting wallets and exchanges, including one attack that used malicious Office documents to install a banking Trojan. As of January, the researchers discovered over 100,000 Bitcoin-related domains, some supposedly registered for nefarious purposes.
“Social engineering is at the heart of most attacks today. It can come through something as simple as a bogus invoice lure in a multimillion message malicious spam campaign. It may appear as an intricate fake chain of emails and out-of-band communications in email fraud. Even web-based attacks—which once depended almost exclusively on exploit kits and drive-by downloads—are now built around social engineering templates. People willingly download bogus software updates or fake anti-malware software,” Proofpoint notes.
New DDoS Attack Method Obfuscates Source Port Data
16.5.2018 securityweek Attack
Recent distributed denial of service (DDoS) attacks showed evidence of a new method being used to bypass existing defenses by obfuscating source port data, Imperva says.
In addition to commonly encountered amplification methods, the observed attacks used payloads with irregular source port data, a vector that only few DDoS defenders considered possible, Imperva claims. The attack method abuses a well-known, unpatched UPnP (Universal Plug and Play) protocol exploit.
The UPnP networking protocol allows for device discovery over UDP port 1900, and for device control over an arbitrarily chosen TCP port. Because of that, many Internet of Things devices use the protocol to discover and communicate to one another over LAN.
However, default settings leaving devices open to remote access, the lack of an authentication mechanism, and UPnP-specific remote code execution vulnerabilities have shown the protocol to pose security risks.
In addition to revealing UPnP related vulnerabilities for nearly two decades, security researchers have also shown how SOAP API calls could be used to remotely reconfigure insecure devices over WAN. SOAP API calls can also be used to remotely execute AddPortMapping commands, which govern port forwarding rules.
While mitigating a SSDP amplification assault on April 11, 2018, Imperva noticed that some of the payloads were arriving from an unexpected source port, and not UDP/1900. The same technique was used in another attack a couple of weeks later.
The investigation into these incidents led to the creation of a “PoC for an UPnP-integrated attack method that could be used to obfuscate source port information for any type of amplification payload,” the security firm says.
To perform DNS amplification attacks using this PoC, one would first have to locate an open UPnP router, which can be done by running a wide-scale scan with SSDP requests using a publicly available online service such as Shodan.
There are over 1.3 million devices that appear in such a search, although not all are vulnerable. Locating an exploitable one is still easy, as scripts can be used to automate the process.
Next, the attacker would need to access the device XML file (rootDesc.xml) via HTTP, which can be done by replacing the ‘Location’ IP with the actual device IP in Shodan.
With the rootDesc.xml file listing all of the available UPnP services and devices, the next step is to modify the device’s port forwarding rules, which can be done via the AddPortMapping command, which is the first on the said list.
“Using the scheme within the file, a SOAP request can be crafted to create a forwarding rule that reroutes all UDP packets sent to port 1337 to an external DNS server (3.3.3.3) via port UDP/53,” Imperva notes.
This works because, although port forwarding should only be used for mapping traffic from external IPs to internal IPs and vice versa, most routers don’t verify that a provided internal IP is actually internal, this allowing proxy requests from external IPs to another external IP.
To use this for port-obfuscated DNS amplification, a DNS request issued to the device and received by the UPnP device on port UDP/1337 is proxied to a DNS resolver over destination port UDP/53. The resolver responds to the device over source port UDP/53, and the device forwards the DNS response back to the original requestor after changing the source port back to UDP/1337.
“In an actual attack scenario, however, the initial DNS request would have been issued from a spoofed victim’s IP, meaning that the response would have been bounced back to the victim,” Imperva notes.
The device could be used to launch a DNS amplification DDoS assault with evasive ports, as the payloads would originate from irregular source ports, thus being able to bypass commonplace defenses that identify amplification payloads by looking for source port data. The evasion method can also be used for SSDP and NTP attacks and could work with other amplification vectors as well, including Memcached.
“With source IP and port information no longer serving as reliable filtering factors, the most likely answer is to perform deep packet inspection (DPI) to identify amplification payloads—a more resource-intensive process, which is challenging to perform at an inline rate without access to dedicated mitigation equipment,” Imperva notes.
Signal Flaw Allowed Code Execution With No User Interaction
16.5.2018 securityweek Vulnerebility
An update released over the weekend for the desktop version of the privacy-focused communications app Signal patches a critical vulnerability that could have been exploited for remote code execution with no user interaction required.
Several researchers were looking at an unrelated cross-site scripting (XSS) vulnerability when they noticed that the XSS payload was triggered in the Signal desktop application.
The white hat hackers discovered that they could execute arbitrary code in the app simply by sending a specially crafted message containing specific HTML elements to the targeted user.
“The Signal-desktop software fails to sanitize specific html-encoded HTML tags that can be used to inject HTML code into remote chat windows. Specifically the <img> and <iframe> tags can be used to include remote or local resources,” the researchers explained in an advisory.
They created proof-of-concept (PoC) payloads that could be used to crash Signal, obtain data from the targeted device’s /etc/passwd file, execute a remote JavaScript file, display a message in an iframe, play audio and video files, display a phishing page, and exfiltrate conversations.
“The critical thing here was that it didn’t required any interaction form the victim, other than simply being in the conversation. Anyone can initiate a conversation in Signal, so the attacker just needs to send a specially crafted URL to pwn the victim without further action,” Iván Ariel Barrera Oro, one of the researchers involved in finding the vulnerability, wrote in a blog post.
The vulnerability affects versions 1.7.1, 1.8.0, 1.9.0 and 1.10.0 on Windows, Linux and likely macOS. Signal developers patched the issue within a couple of hours with the release of version 1.10.1 on Saturday.
Based on an analysis of the source code, researchers determined that the flaw had been previously patched but the fix was removed – likely by accident – with a change made on April 10.
Serbia Arrests FBI-sought Cybercrime Suspect
16.5.2018 securityweek BigBrothers
Serbian police said Wednesday they had arrested a man sought by the FBI under suspicion of being part of a group of cybercriminals who called themselves "The Dark Overlord".
The arrest of the 38-year-old Serbian from Belgrade, identified only by his initials S.S., was carried out as part of an "international operation conducted by the FBI," a police statement said.
The goal was to identify and arrest hackers who used the name "The Dark Overlord" and had been committing cyberattacks since June 2016, the statement added.
Members of the group were "stealing information and personal data from US citizens, including property and intellectual property data, sensitive health insurance and medical treatment data," it said.
At least 50 people were victims of attacks, the investigation found.
Police said the arrested man is accused of "illegal access to protected computers, computer networks and extorsion".
In late April, a British and Dutch-led operation brought down a website linked to more than four million cyberattacks around the world, with banking giants among the victims.
Two people, suspected of being administrators of the webstresser(.)org website were arrested in Serbia at the time.
Some Firefox Screenshots End Up Publicly Accessible
16.5.2018 securityweek Security
Mozilla’s Firefox browser allows users to take screenshots of entire pages or sections of pages and save them to the cloud, and these could end up accessible to everyone, an ethical hacker has discovered.
Introduced in the browser last fall, Firefox Screenshots was meant to make it easy for users to “take, download, collect and share screenshots.” To access it, one would have to click on the Page actions menu in the address bar (or simply right-click on a web page) and select Take a Screenshot.
This allows users to save a screenshot of the entire page, of the visible section of the page, or use a selection tool to save only a region they consider important. Next, they can dismiss the action, copy the screenshot, download it, or click a “Save” button that sends the screenshot to the cloud.
All saved screenshots go to https://screenshots.firefox.com, a default setting in the browser. Furthermore, all screenshots that have been previously shared to public forums are indexed by search engines such as Google and could be discovered and accessed by anyone.
Screenshots are sent to the public server only when the user clicks the “Save” button. Many users, however, might have been long doing so without realizing that they were actually sending them to the cloud.
Mozilla issued a fix for the issue yesterday, soon after details on it emerged on Twitter. Apparently, this is not the first time the organization attempts to address this, but the previous implementation was flawed.
Specifically, in its attempt to avoid shot pages being indexed by search engines, Mozilla replaced robots.txt with <meta name=robots value=noindex>, but the fix was “only put in place for expired pages instead of all pages as intended.”
“So this is being deployed and now we're talking to DDG/Google etc to strip the domains,” John Gruen, UX-focused Product Manager at Mozilla, told the ethical hacker who discovered the flaw.
Updated: A previous version of this article incorrectly stated that all screenshots end up being publicly accessible.