
Russia-Linked Attacks on Political Organizations Continue
19.1.2018 securityweek APT
The cyber-espionage group known as Fancy Bear was highly active in the second half of 2017, hitting political organizations worldwide, Trend Micro said this week.
Also known as APT28, Pawn Storm, Sofacy, Group 74, Sednit, Tsar Team, and Strontium, the group is said to have ties with the Russian government. Since 2015, the group has been associated with attacks on political organizations in France, Germany, Montenegro, Turkey, Ukraine, and the United States.
During the second half of 2017, such attacks continued, without revealing much technical innovation over time. However, the attacks are well prepared, persistent, and often hard to defend against, the security researchers say.
“Pawn Storm has a large toolset full of social engineering tricks, malware and exploits, and therefore doesn’t need much innovation apart from occasionally using their own zero-days and quickly abusing software vulnerabilities shortly after a security patch is released,” Trend Micro points out.
During the second half of 2017, the group was observed targeting organizations with credential phishing and spear phishing attacks. In August and September, the hackers used tabnabbing against Yahoo! users, a method that involves changing a browser tab to point to a phishing site after distracting the target.
In attacks observed in October and November 2017, the group used credential phishing emails to target specific organizations. One incident employed an email claiming to inform the target of an expired password, while the other claimed a new file was present on the company’s OneDrive system.
During the past six months, Pawn Storm also targeted several International Olympic Wintersport Federations, including the European Ice Hockey Federation, the International Ski Federation, the International Biathlon Union, the International Bobsleigh and Skeleton Federation, and the International Luge Federation.
The attacks appear to be related to several Russian Olympic players being banned for life in fall 2017. A recent incident involving the leak of emails exchanged between officials of the International Olympic Committee (IOC) and other individuals involved with the Olympics also appears to be related to the state-sponsored actor.
Some of the group’s political targets included chmail.ir webmail users, who received credential phishing emails on May 18, 2017, one day before the presidential elections in Iran. Similar incidents were observed targeting political organizations globally, Trend Micro says.
In June 2017, the actor set up phishing sites mimicking the ADFS (Active Directory Federation Services) of the U.S. Senate. In attacks observed during fall 2017, the group was abusing Google’s Blogspot service to target Bellingcat, a group of investigative journalists that uses open source information to report on various events taking place around the world.
Individuals interested in the CyCon U.S. conference organized by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) in collaboration with the Army Cyber Institute at West Point were also targeted by Pawn Storm last year.
Moving forth, the group is expected to continue targeting political organizations, while also likely focusing on influencing public opinion via social media, given that social media algorithms are “susceptible to abuse by various actors with bad intentions.”
“Publishing stolen data together with spreading fake news and rumors on social media gives malicious actors powerful tools. While a successful influence campaign might seem relatively easy to do, it needs a lot of planning, persistence, and resources to be successful. Some of the basic tools and services, like ones used to spread fake news on social media, are already being offered as a service in the underground economy,” Trend Micro notes.
Other actors too might start campaigns attempting to influence politics and issues of interest domestically and abroad, the researchers say. Pawn Storm, however, is expected to continue to be highly active, especially with the Olympics and several significant global elections taking place in 2018.
Booby-Trapped Messaging Apps Used for Spying: Researchers
19.1.2018 securityweek Mobil
An espionage campaign using malware-infected messaging apps has been stealing smartphone data from activists, soldiers, lawyers, journalists and others in more than 20 countries, researchers said in a report Thursday.
A report authored by digital rights group Electronic Frontier Foundation and mobile security firm Lookout detailed discovery of "a prolific actor" with nation-state capabilities "exploiting targets globally across multiple platforms."
Desktop computers were also targeted, but getting into data-rich mobile devices was a primary objective, according to the report.
With fake versions of secure messaging services like WhatsApp and Signal, the scheme has enabled attackers to take pictures, capture audio, pinpoint locations, and mine handsets for private data.
EFF and Lookout researchers dubbed the threat "Dark Caracal."
People in the US, Canada, Germany, Lebanon, and France have been hit by Dark Caracal, according to EFF director of cybersecurity Eva Galperin.
"This is a very large, global campaign, focused on mobile devices," Galperin said.
"Mobile is the future of spying, because phones are full of so much data about a person's day-to-day life."
Hundreds of gigabytes of data have been taken from thousands of victims in more than 21 countries, according to Lookout and the EFF.
There were indications that Dark Caracal might be an infrastructure hosting a number of widespread, global cyberespionage campaigns, some of which date back years, the report said.
Because the apps fool people into thinking they are legitimate, users give them access to cameras, microphones and data.
"All Dark Caracal needed was application permissions that users themselves granted when they downloaded the apps, not realizing that they contained malware," said EFF staff technologist Cooper Quintin.
"This research shows it's not difficult to create a strategy allowing people and governments spy to on targets around the world."
Researchers reported that they tracked Dark Caracal to a building in Beirut belonging to the Lebanese General Security Directorate.
Analysis showed that devices of military personnel, businesses, journalists, lawyers, educators, and medical professionals have been compromised, according to the report.
"Not only was Dark Caracal able to cast its net wide, it was also able to gain deep insight into each of the victim's lives," the report concluded.
Cyber security professionals consistently warn people to be wary when downloading software, avoiding programs shared through links or email and instead relying on trusted sources.
Cloudflare Launches Remote Access to Replace Corporate VPNs
19.1.2018 securityweek Security
Mobile and cloud computing have challenged the concept of perimeter security. There is no longer an easily definable perimeter to defend. VPNs are a traditional, but not ideal solution. Neither approach addresses the attacker who gets through the perimeter or into the VPN. Google long ago recognized the problems and introduced BeyondCorp as an alternative to perimeters and VPNs for its own worldwide employees.
BeyondCorp replaces the need for VPNs. Instead it focuses on authenticating the device (which it provides and identifies with a device certificate) and its user, and then imposes tiered authentication around its applications. In effect, it removes the distinction between a trusted network and an untrusted network, and focuses on authenticated access from any location.
It is a good security model, but one that is beyond the reach of companies that don't have Google's resources. Now Cloudflare has announced a new service for its customers that it calls Cloudflare Access and describes as 'democratizing' the BeyondCorp model. It allows employees to operate outside of the corporate network without requiring them to use a VPN, "which," writes Cloudflare engineer Venkat Viswanathan in an associated blog post Wednesday, "slows down work because every page load makes extra round trips to the VPN server. After all this hassle, users on the VPN are still highly susceptible to phishing, man-in-the-middle and SQL injection attacks."
"VPNs are slow, and clunky, and frankly, don't make sense for an increasingly mobile workforce accessing increasingly cloudified apps," said Matthew Prince, co-founder and CEO of Cloudflare. "Cloudflare Access gives centralized application access control for legacy or cloud apps without slowing down connections, regardless of where someone is working around the world."
Unlike BeyondCorp, however, Cloudflare cannot provide corporate devices for the users. Customers remain responsible for the security of the remote devices. "We don't insist on clients providing company devices to employees," Prince told SecurityWeek, "but we recommend that they tick some sort of identity provider. That could be Google, Microsoft Active Directory, Okta or something they've built themselves. How much they use that service and lock down the individual devices is up to them, but we would recommend that they use multi-factor authentication on those devices."
Cloudflare's role in this model is to protect the customer's individual applications within separate authentication wrappers. "While perimeter defense is based on the idea of a moat around the castle," said Prince, "this new model puts each application (the castle's individual crown jewels) into separate safes. We don't care whether the customer uses a combination lock safe, or a physical key safe or an electronic keypad safe. We'll support any of the different mechanisms for unlocking the safe -- but what we provide is the safe itself. We provide the thing that wraps around wherever the crown jewels are located and protects them. It is the customers that decide how they want to verify if the device and user are legitimate and authorized to open the door that we provide."
Cloudflare's Access product does not defend the user's device, but it does defend the company's applications. "Even if an attacker manages to get into a device, every access to the company network is logged by Cloudflare. The customer can monitor for anomalies. So, the model of wrapping authentication around each application not only adds friction to any attack, it also provides a central repository where the security team can look for anomalies, track bad behavior and quickly respond accordingly. The customer's administrator for the Cloudflare service would have a single view of every employee's device -- when it logged into and used each of the different services -- on a service by service basis. If anything anomalous happens, the administrator can withdraw the user's Access instantly."
The logs are accessible through a Cloudflare API, so anomaly detection can be automated using anomaly detection tools in-house. "Over time," said Prince, "as Access matures, there will be additional tools that we provide to allow customers to look for things that might be anomalous. For example, if a device has only logged into three services in its entire history, and then suddenly logs into five new services, we would surface that in the logs and show it to the admins. This is not currently available," he added. "You could build it through our APIs, but it's something we are likely to make available in future versions of our product."
Cloudflare's new Access product is a replacement for corporate VPNs using much of Google's BeyondCorp model.
"When a user accesses an individual application," explained Prince, "it would be like passing through a VPN on a per application basis. Users would hit a Cloudflare data center which prompts for proof of identity and authorization to access a particular application. If that authorization proves 'true', then the user gets a fast lane back to the actual application, which could be running anywhere on the internet, whether in-house or a third-party such as Salesforce. The user gets a much faster experience through not having to back haul everything through some centralized VPN server." Like a VPN, all traffic is protected by encryption.
"If you think of the problems that VPNs are trying to solve, they're simply trying to let the good guys in and keep the bad guys out. Access solves that exact same problem, but does it in a way that is more robust. It supports cloud environments, it supports remote workers without slowing down their connection, and it actually provides a better security model where you have individuals being logged as they pass through authentication checkpoints to use each different application."
Cloudflare Access is being sold on a per seat basis: $3 per person, per month. There is no limit to the number of applications that can be accessed by each user via the service. Volume discounts are available for large deployments.
San Francisco, CA-based Cloudflare was founded in 2009. It has raised a total funding amount of $182,050,000 -- the most recent being $110 million Series D funding led by Fidelity Investments in September 2015. It routes traffic through its own global network, blocking DoS attacks, reducing spam and improving performance.
Meltdown and Spectre patches have a variable impact and can cause unwanted reboots, Intel warns
19.1.2018 securityaffairs Vulnerebility
Intel has published the results of the test conducted on the Meltdown and Spectre patches and their impact on performance confirming serious problems.
According to the tech giant systems with several types of processors running Meltdown and Spectre patches may experience more frequent reboots.
A few days ago Intel reported that extensive test conducted on home and business PCs demonstrated a negligible performance impact on these types of systems (from 2 up to 14%).
Now the vendor has conducted some performance tests on data centers and results show that the impact on the performance depends on the system configuration and the workload.
“As expected, our testing results to date show performance impact that ranges depending on specific workloads and configurations. Generally speaking, the workloads that incorporate a larger number of user/kernel privilege changes and spend a significant amount of time in privileged mode will be more adversely impacted.” reads the analysis conducted by Intel.
Impacts ranging from 0-2% on industry-standard measures of integer and floating point throughput, Linpack, STREAM, server-side Java and energy efficiency benchmarks. The tests are related to benchmarks that cover typical workloads for enterprise and cloud customers.
Intel also evaluated the impact on online transaction processing (OLTP), estimating it at roughly 4%.
Benchmarks for storage demonstrated a strict dependence on the benchmark, test setup, and system configuration.
For FlexibleIO, which simulates various I/O workloads, throughput performance decreased by 18% when the CPU was stressed, but there was no impact when CPU usage was low.
The tests for FlexibleIO were conducted using different benchmark simulating different types of I/O loads, the results depend on many factors, including read/write mix, block size, drives and CPU utilization.
“For FlexibleIO, a benchmark simulating different types of I/O loads, results depend on many factors, including read/write mix, block size, drives and CPU utilization. When we conducted testing to stress the CPU (100% write case), we saw an 18% decrease in throughput performance because there was not CPU utilization headroom.” continues the analysis. “When we used a 70/30 read/write model, we saw a 2% decrease in throughput performance. When CPU utilization was low (100% read case), as is the case with common storage provisioning, we saw an increase in CPU utilization, but no throughput performance impact.”
The most severe degradation of the performance was observed during Storage Performance Development Kit (SPDK) tests, using iSCSI the degradation reached 25% when only a single core was used. Fortunately, there was no degradation of the performance when SPDK vHost was used.

Intel also reported that Meltdown and Spectre patches are causing more frequent reboots, this behavior was observed for systems running Broadwell, Haswell, Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms.
“We have reproduced these issues internally and are making progress toward identifying the root cause. In parallel, we will be providing beta microcode to vendors for validation by next week,” said Navin Shenoy, executive vice president and general manager of Intel’s Data Center Group.
Only the newest Intel 8th-gen CPUs Coffee Lake seems to be not affected by reboots.
North Korea Group 123 involved in at least 6 different hacking campaigns in 2017
19.1.2018 securityaffairs APT
North Korean hackers belonging to the North Korea Group 123 have conducted at least six different massive malware campaigns during 2017.
North Korean hackers have conducted at least six different massive malware campaigns during 2017, most of them against targets in South Korea. Security researchers from Cisco’s Talos group who have monitored the situation for 12 months have identified a North Korean threat actor tracked by the experts as Group 123 that conducted numerous malware attacks against entities in the South.
In three differed phishing campaigns tracked as “Golden Time”, “Evil New Year” and “North Korean Human Rights” South Korean victims were specifically infected with the Remote Access Trojan ROKRAT.
“On January 2nd of 2018, the “Evil New Year 2018” was started. This campaign copies the approach of the 2017 “Evil New Year” campaign.
The links between the different campaigns include shared code and compiler artifacts such as PDB (Program DataBase) patterns which were present throughout these campaigns.” reads the analysis published by Talos.
“Based on our analysis, the “Golden Time”, both “Evil New Year” and the “North Korean Human Rights” campaigns specifically targeted South Korean users.”
The ROKRAT RAT was used to target Korean targets using the popular Korean Microsoft Word alternative Hangul Word Processor (HWP). In the past, we saw other attacks against people using the HWP application.

The three campaigns leveraged on a payload in the Hancom Hangul Office Suite, North Korean hackers exploited vulnerabilities such as the CVE-2013-0808 EPS viewer bug to deliver the RAT.
The attackers also used specially crafted files to trigger the arbitrary code execution vulnerability CVE-2017-0199. Group 123 also launched the FreeMilk campaign against financial institutions outside South Korea.
The hackers in this campaign used phishing message with a weaponized Microsoft Office document that was able to trigger the vulnerability CVE-2017-0199.
“Group 123 used this vulnerability less than one month after its public disclosure. During this campaign, the attackers used 2 different malicious binaries: PoohMilk and Freenki.” continues the analysis.”PoohMilk exists only to launch Freenki. Freenki is used to gather information about the infected system and to download a subsequent stage payload. This malware was used in several campaigns in 2016 and has some code overlap with ROKRAT.”
The last campaign analyzed by Talos group was tracked as “Are You Happy,” it is a sabotage campaign that targeted the victims using a module from ROKRAT designed to wipe the first sectors of the victim’s hard drive.
According to Talos, this actor was very active in 2017, and likely will continue its campaigns in the next months, especially against targets in the South.
“The actor has the following demonstrated capabilities:
To include exploits (for Hangul and Microsoft Office) in its workflows.
To modify its campaigns by splitting the payload in to multiple stages
To use compromised web servers or legitimate cloud based platforms.
To use HTTPS communications to make it harder to perform traffic analysis.
To compromise third parties to forge realistic spear phishing campaigns (i.e. Yonsei university in the “Golden Time” campaign).
To constantly evolve, the new fileless capability included in 2018 is a proof.” concluded Talos.
The report includes the IoCs for each campaign.
Hackers Exploiting Three Microsoft Office Flaws to Spread Zyklon Malware
18.1.2018 thehackernews Virus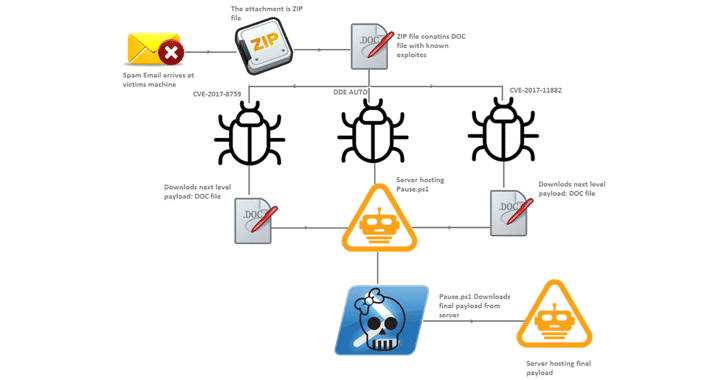
Security researchers have spotted a new malware campaign in the wild that spreads an advanced botnet malware by leveraging at least three recently disclosed vulnerabilities in Microsoft Office.
Dubbed Zyklon, the fully-featured malware has resurfaced after almost two years and primarily found targeting telecommunications, insurance and financial services.
Active since early 2016, Zyklon is an HTTP botnet malware that communicates with its command-and-control servers over Tor anonymising network and allows attackers to remotely steal keylogs, sensitive data, like passwords stored in web browsers and email clients.
Zyklon malware is also capable of executing additional plugins, including secretly using infected systems for DDoS attacks and cryptocurrency mining.
Different versions of the Zyklon malware has previously been found being advertised on a popular underground marketplace for $75 (normal build) and $125 ( Tor-enabled build).
According to a recently published report by FireEye, the attackers behind the campaign are leveraging three following vulnerabilities in Microsoft Office that execute a PowerShell script on the targeted computers to download the final payload from its C&C server.
1) .NET Framework RCE Vulnerability (CVE-2017-8759)—this remote code execution vulnerability exists when Microsoft .NET Framework processes untrusted input, allowing an attacker to take control of an affected system by tricking victims into opening a specially crafted malicious document file sent over an email. Microsoft already released a security patch for this flaw in September updates.
2) Microsoft Office RCE Vulnerability (CVE-2017-11882)—it’s a 17-year-old memory corruption flaw that Microsoft patched in November patch update allows a remote attacker to execute malicious code on the targeted systems without requiring any user interaction after opening a malicious document.
3) Dynamic Data Exchange Protocol (DDE Exploit)—this technique allows attackers to leverage a built-in feature of Microsoft Office, called DDE, to perform code execution on the targeted device without requiring Macros to be enabled or memory corruption.
As explained by the researchers, attackers are actively exploiting these three vulnerabilities to deliver Zyklon malware using spear phishing emails, which typically arrives with an attached ZIP file containing a malicious Office doc file.
Once opened, the malicious doc file equipped with one of these vulnerabilities immediately runs a PowerShell script, which eventually downloads the final payload, i.e., Zyklon HTTP malware, onto the infected computer.
"In all these techniques, the same domain is used to download the next level payload (Pause.ps1), which is another PowerShell script that is Base64 encoded," the FireEye researchers said.
"The Pause.ps1 script is responsible for resolving the APIs required for code injection. It also contains the injectable shellcode."
"The injected code is responsible for downloading the final payload from the server. The final stage payload is a PE executable compiled with .Net framework."
Interestingly, the PowerShell script connects to a dotless IP address (example: http://3627732942) to download the final payload.
What is Dotless IP Address? If you are unaware, dotless IP addresses, sometimes referred as 'Decimal Address,' are decimal values of IPv4 addresses (represented as dotted-quad notation). Almost all modern web browsers resolve decimal IP address to its equivalent IPV4 address when opened with "http://" following the decimal value.
For example, Google's IP address 216.58.207.206 can also be represented as http://3627732942 in decimal values (Try this online converter).
The best way to protect yourself and your organisation from such malware attacks are always to be suspicious of any uninvited document sent via an email and never click on links inside those documents unless adequately verifying the source.
Most importantly, always keep your software and systems up-to-date, as threat actors incorporate recently discovered, but patched, vulnerabilities in popular software—Microsoft Office, in this case—to increase the potential for successful infections.
Threat actors are delivering the Zyklon Malware exploiting three Office vulnerabilities
18.1.2018 securityaffairs Vulnerebility
Security experts from FireEye have spotted a new strain of the Zyklon malware that has been delivered by using new vulnerabilities in Microsoft Office.
Researchers at FireEye reported the malware was used in attacks against organizations in the telecommunications, financial, and insurance sectors.
Zyklon has been spotted for the first time in 2016, it is a publicly available malware that could be used for multiple purposes such as espionage campaigns, DDoS attacks or to mine cryptocurrency.
“FireEye researchers recently observed threat actors leveraging relatively new vulnerabilities in Microsoft Office to spread Zyklon HTTP malware.” reads the analysis published by FireEye.
“Zyklon is a publicly available, full-featured backdoor capable of keylogging, password harvesting, downloading and executing additional plugins, conducting distributed denial-of-service (DDoS) attacks, and self-updating and self-removal.”
The malware is modular, it can download several plugins to implement different features, it may communicate with C&C server over The Onion Router (Tor) network.
In this last campaign, the malicious code has been delivered via spam emails using as a ZIP archive that contains a specially crafted Word document.
The document exploits one of three vulnerabilities in Microsoft Office to deliver a PowerShell script that downloads the final Zyklon payload from a remote server.
Zyklon malware
One of the flaws exploited by the attackers is CVE-2017-8759, a flaw that was fixed by Microsoft in September 2017 after it was exploited by threat actors such as the Cobalt group to deliver malware in attacks wild.
A second triggered by the documents used in the campaign spotted by FireEye is CVE-2017-11882, a 17-year-old vulnerability in MS Office that could be exploited by remote attackers to install a malware without user interaction.
The flaw is a memory-corruption issue that affects all versions of Microsoft Office released in the past 17 years, including the latest Microsoft Office 365. The vulnerability could be triggered on all versions of Windows operating system, including the latest Microsoft Windows 10 Creators Update.
The vulnerability affects the MS Office component EQNEDT32.EXE that is responsible for insertion and editing of equations (OLE objects) in documents.
This flaw was used by differed APT groups, including the Cobalt group and Iran-linked hackers.
The attackers also exploited the Dynamic Data Exchange (DDE) feature in Office to deliver the malicious code, the same feature was abused by at least one Russian APT group in cyber espionage campaigns and by the powerful Necurs botnet to deliver ransomware.
Once the malware has successfully exploited one of these flaws, it will download a PowerShell script that injects code and fetches the final payload from a remote server.
FireEye highlighted the fact that attackers are exploiting recently discovered flaws in widely adopted software such as the Office suite to increase the likelihood of infecting the victims’ machines.
“Threat actors incorporating recently discovered vulnerabilities in popular software – Microsoft Office, in this case – only increases the potential for successful infections. These types of threats show why it is very important to ensure that all software is fully updated. Additionally, all industries should be on alert, as it is highly likely that the threat actors will eventually move outside the scope of their current targeting.” concludes FireEye.
Technical details about the threat, including the Indicators of Compromise, are available in the report published by FireEye.
Internet Systems Consortium rolled out a patch for a BIND security flaw caused DNS Servers Crash
18.1.2018 securityaffairs Vulnerebility
The Internet Systems Consortium (ISC) has issued security updates for BIND to address a high severity vulnerability that could cause DNS servers crash.
The Internet Systems Consortium (ISC) has rolled out security updates for BIND to address a high severity vulnerability that could be remotely exploited to crash DNS servers.
The flaw discovered by Jayachandran Palanisamy of Cygate AB and tracked as CVE-2017-3145, is caused by a use-after-free bug that can lead to an assertion failure and crash of the BIND name server (named) process.
“BIND was improperly sequencing cleanup operations on upstream recursion fetch contexts, leading in some cases to a use-after-free error that can trigger an assertion failure and crash in named.” reads the security advisory published by ISC.
According to the ISC there is no evidence that the flaw has been exploited in attacks in the wild, but the ISC states that many crashes caused by the bug have been reported by “multiple parties.”
The issue impacted systems that operate as DNSSEC validating resolvers, the experts suggest to temporarily disable DNSSEC validation as a workaround.
“While this bug has existed in BIND since 9.0.0, there are no known code paths leading to it in ISC releases prior to those containing the fix for CVE-2017-3137. Thus while all instances of BIND ought to be patched, only ISC versions [9.9.9-P8 to 9.9.11, 9.10.4-P8 to 9.10.6, 9.11.0-P5 to 9.11.2, 9.9.9-S10 to 9.9.11-S1, 9.10.5-S1 to 9.10.6-S1, and 9.12.0a1 to 9.12.0rc1] acting as DNSSEC validating resolvers are currently known to crash due to this bug. The known crash is an assertion failure in netaddr.c.” continues the advisory.
The ISC also disclosed a medium severity DHCP flaw tracked as CVE-2017-3144 that affect versions 4.1.0 to 4.1-ESV-R15, 4.2.0 to 4.2.8, and 4.3.0 to 4.3.6.
“A vulnerability stemming from failure to properly clean up closed OMAPI connections can lead to exhaustion of the pool of socket descriptors available to the DHCP server. ” reads the ISC advisory.
“By intentionally exploiting this vulnerability an attacker who is permitted to establish connections to the OMAPI control port can exhaust the pool of socket descriptors available to the DHCP server. Once exhausted, the server will not accept additional connections, potentially denying access to legitimate connections from the server operator. While the server will continue to receive and service DHCP client requests, the operator can be blocked from the ability to use OMAPI to control server state, add new lease reservations, etc.,”
ISC has already developed a patch that will be rolled out in the future DHCP releases, as a workaround it is possible to disallow access to the OMAPI control port from unauthorized clients.