
Hackers can remotely access adult sex toys compromising at least 50.000 users
7.2.2018 securityaffairs Hacking
Researchers discovered that sex toys from German company Amor Gummiwaren GmbH and its cloud platform are affected by critical security flaws.
As a result for Master Thesis by Werner Schober in cooperation with SEC Consult and the University of Applied Sciences St. Pölten, it was discovered that sex toys from German company Amor Gummiwaren GmbH and its cloud platform are affected by critical security flaws.
In an astonishing revelation, multiple vulnerabilities were discovered in “Vibratissimo” secy toys and in its cloud platform that compromised not only the privacy and data protection but also physical safety of owners.
The database pertaining all customers data was accessible via internet in such a way that explicit images, chat logs, sexual orientation, email addresses and passwords in clear text were compromised.
A total lack of security measures had caused the enumeration of all explicit images of users compromising their identities due to the utilization of predictable numbers and absence of authorization verification. Hackers could even give pleasure to users without their consent using the internet or standing nearby the address within the range of Bluetooth. These are only a few dangers users are exposed once connected to the world of the Internet of Things (IoT).
The Internet of Things (IoT) is a technology that comprises a myriad of devices connected to the internet and has evolved in such way that is present in many products used in a daily basis, from cars to home utilities. Once taking this into account we see the arising of a new sub-category within the Internet of Things (IoT) named Internet of Dildos (IoD). The Internet of Dildos (IoD) comprehends every device connected to networks that give mankind pleasure. According to the article, the term from 1975 given to this area of research is the following: “Teledildonics (also known as “cyberdildonics”) is technology for remote sex (or, at least, remote mutual masturbation), where tactile sensations are communicated over a data link between the participants”.
The products from Amor Gummiwaren GmbH that are vulnerable are the following: Vibratissimo Panty Buster, MagicMotion Flamingo, and Realov Lydia. The analysis of researchers focused on Vibratissimo Panty Buster. The panty buster is a sex toy that can be controlled remotely with mobile applications (Android, iOS), but the mobile application, the backend server, hardware, and firmware are developed by third-party company. The application presents many interactive features that enable extensive communication and sharing capabilities, in such a manner that creates a social network where users can expand their experience. Some features are: Search for other users, the creation of friends lists, video chat, message board and sharing of image galleries that can be stored across its social network.
The vulnerabilities found were: Customer Database Credential Disclosure, Exposed administrative interfaces on the internet, Cleartext Storage of Passwords, Unauthenticated Bluetooth LE Connections, Insufficient Authentication Mechanism, Insecure Direct Object Reference, Missing Authentication in Remote Control and Reflected Cross-Site Scripting. As we start taking a glimpse at the vulnerabilities discovered we can consider the following: All credentials of Vibratissimo database environment were leaked on the internet, alongside with the PHPMyAdmin interface that can have allowed hackers to access the database and dump all content.
The PHPMyAdmin interface was accessible throughout the URL http://www.vibratissimo.com/phpmyadmin/ with the stored passwords without encryption in clear text format. The content pertained to the database might have the following data: Usernames, Session Tokens, Cleartext passwords, chat histories and explicit image galleries created by the users themselves. The DS_STORE file and config.ini.php was found on the web server of Vibratissimo in such way that hackers could exploit attack vector like directory listing and discover the operating system which in this case is a MAC OSX.
Also, as disclosed by the researchers, there are great dangers to users in the remote control of the vibrator. The first is related to the connection between the Bluetooth LE of the vibrator and the smartphone application that could lead to eavesdropping, replay and MitM attacks. Although the equipment offers several pairing methods the most dangerous is “no pairing” as noted in the report. This method can allow hackers to search for information on the device as well as write data. If a hacker is in range, he could take control of the device. Also, a man in the middle attack is possible due to the lack of authentication, where a hacker can create a link for itself and then decrement or increment the ID to get direct access to the link used by the person. Due to the lack of authentication, a reflected cross-site scripting is also possible, but as noticed by the researchers it is not as dangerous as the other security issues.
Last but not least the researchers recommend a complete update in the software and mobile application used by the devices. It is highly recommended for all users to change their login information as well as their passwords for greater protection. Not all security flaws were addressed and corrected, therefore there are some dangers loaming around that can be exploited by tools like Shodan and autosploit. It is a social security concern these vulnerabilities since they pose a grave danger to user’s reputation, that can lead to suicide.
Sources:
http://www.securitynewspaper.com/2018/02/03/internet-dildos-long-way-vibrant-future-iot-iod/
https://www.sec-consult.com/en/blog/2018/02/internet-of-dildos-a-long-way-to-a-vibrant-future-from-iot-to-iod/index.html
https://www.sec-consult.com/en/blog/advisories/multiple-critical-vulnerabilities-in-whole-vibratissimo-smart-sex-toy-product-range/index.html
https://www.theregister.co.uk/2018/02/02/adult_fun_toy_security_fail/
http://www.zdnet.com/article/this-smart-vibrator-can-be-easily-hacked-and-remotely-controlled-by-anyone
https://mashable.com/2018/02/01/internet-of-dildos-hackers-teledildonics
https://www.cnet.com/news/beware-the-vibratissimo-smart-vibrator-is-vulnerable-to-hacks/
http://www.wired.co.uk/article/sex-toy-bluetooth-hacks-security-fix
https://www.forbes.com/sites/thomasbrewster/2018/02/01/vibratissimo-panty-buster-sex-toy-multiple-vulnerabilities/#37ec1d25a944
9 Tips to Prevent WordPress Hacks in this Dangerous Digital World
7.2.2018 securityaffairs Hacking
WordPress hacks are increasingly common. Whether it’s for malicious reasons, to harm a site or to just insert backlinks, WordPress can be very vulnerable if not cared for and updated regularly. How to Prevent hacks?
So, how do you prevent these security blips – this post aims to show how.
Backup
Regular data backup can save you lots of frustration and headache, and especially after a hack. Taking the necessary measures to ensure information on your WordPress site or blog is backed up before making any significant changes, and doing the same after updates are recommended.
Although most people prefer to backup their data manually, using a plugin can make your work much more manageable. Plugins provide a convenient way to handle data backups at set times or intervals. Backup buddy (a plugin) is pretty good at this.
Although a paid option, this plugin exports everything on your WP from settings, files, images, and content on the database. You could also opt for free plugins as well.
Update the WordPress Version as Quickly as the New Comes
Updating your blog/site to the latest WP version can also save you lots of trouble. The regular updates are not only meant to make your experience much better but also patches security loopholes that could otherwise be manipulated by hackers.
You can simply follow WordPress feeds to find out about new updates, or just log in to the blog as admin. Be sure to follow WordPress Development blogs to get the latest updates on when the next patch or fixed will be released.
Check Themes and Plugins for Continued Support
Only used plugins and themes with continuous support and updates. It is through the continued support that developers of the same can release patches to make their plugins hacker-proof.
Any outdated or plugins/themes that no longer receive updates should be avoided, or uninstalled altogether. Most developers only provide support for about a year or two, then discontinue support for the same.
Be sure to look for themes or plugins with active support, receives frequent updates, well-rated, and customer support. You will be surprised to know most of the top-selling themes are outdated or longer receive updates. Look at the comment section for red flags and other indicators of flaws in the same before making an order.
Most of the premium WordPress themes will come bundled with third-party plugins. Some of the plugins bundled with the theme may or may not receive frequent updates.
Revolution Slider is an excellent example of plugins that come bundled with lots of themes on ThemeForest. This plugin had a major vulnerability back in 2014.
The thousands of sites that used this plugin were hacked with most of the hacks redirecting traffic to malicious sites. Although the developers of the same were pushing out updates for their themes, one loophole cost many websites a fortune.
As a precaution, consider investing in plugins that aren’t bundled with extra ‘freebies’. If need be, buy each plugin individually to reduce vulnerabilities to your site. You also need to turn on updates on these plugins to keep your site safe as well.
Keep the WP Admin Directory Protected
The admin directory in WP should always be password protected at all times. It holds the key to every function and security of the site. Password protecting the WP-admin directory helps keep hackers and other malicious people at bay.
This also means the admin will be required to enter two passwords to access the admin directory. The first password gives access to the login page with the WP-Admin directory still protected. The fun part about password-protecting this directory is that you get to control all aspects of the site, including unlocking various parts for access to authorized users only.
One way to protect the WP-admin directory is by installing the AskApache Password Protect plugin. The plugin configures enhanced security file permissions and encrypts the directory with a .htpasswd file.
Encrypt Data with Secure Socket Layer (SSL) Certificate
Using the SSL certificate to secure the Admin panel is not only wise but a smart move. This certification ensures data transfer between the server and user browsers is encrypted and almost impossible to breach.
This enhances data security on the site. Getting an SSL certificate is easy too. You can have your hosting firm for one, or just buy the certificate from a dedicated company.
The Let’s Encrypt SSL certificate is available for free and is an open source product as well. This means it does a pretty good job of keeping your site and data secure. Using an SSL certificate on your WP site can also help boost the site’s rankings on Google
Rename the Login URL
Changing the default WP login address to a different one gives your site an extra layer of security. You can do this by accessing the site’s admin URL.
Renaming the URL makes it hard for hackers to brute force their way into the site. Test the new login details with GWDb to see if anyone can guess your login details.
Although a simple maneuver, this trick helps restrict unauthorized entry to your login page. Only individuals with the login URL and details can access the dashboard. You could also use the iThemes Security plugin to rename your login address.
Never use Public Wi-Fi to Log In
Although public Wi-Fi may seem convenient, it poses multiple threats to your devices, sites, and online activity. Any malicious person on the same network or running packet sniffing software can sniff out any personal data you send via the same. If you have to log in to your WP site admin panel, then ensure you have an SSL certificate installed, or better still, use a virtual private network (VPN).
Have a VPN service installed on your computer or any other device just in case you need to log in to your site. It would also be a good habit to have the VPN running even with the SSL certificate installed. Never underestimate the skills of a black hat hacker targeting your site.
Disable File Editing
Users with admin access to your WP site or dashboard can edit or even change files on the site. This includes themes and plugins already installed in the same.
Disabling file editing on the site means only you can make changes to the site, and also helps make it almost impossible for hackers to change anything on the site. Any hacker that gains access to the WP dashboard will find it hard to change or modify files already on the site. Consider disallowing other users adding content and scripts to the site as well.
To do this, add these commands to the wp-config.php file located at the very end.
Define (‘DISALLOW_FILE_EDIT’, true);
Use the Right Server Configurations and Connections
According to matthewwoodward.co.uk you should only connect the server through SSH or SFTP when setting up the site for the first time. SFTP has more security features enabled as compared to the traditional FTP protocol. These security features are also not attributed to FTP, thus enhanced security.
Connecting the server via SFTP and SSH guarantees secure file transfer. Most web hosting providers can provide this service on request, with some offering it as a part of their packages. You can also enable these features manually too. Some expert knowledge may be needed to connect such safety and without much struggle.
BSides NYC, a volunteer organized event put on by and for the community
7.2.2018 Kaspersky Congress
Another edition of BSides NYC has passed, and as first time attendee and presenter, I was genuinely impressed with the impeccable organization, the content shared, and the interesting conversations that took place among enthusiasts and professionals from all over the world. I’ve been a long time follower and supporter of BSides events in Latin America, mainly due to the fact that they offer a relaxed venue for sharing and learning about the newest topics in information security, all while bringing together people from different backgrounds in a community-driven event.
This year’s edition of BSides NYC took place at the John Jay College of Criminal Justice, with faculty member and the deputy CISO of the City of New York opening the event along some additional memorable keynotes given by Runa Sandvik from the New York Times, and Amber Baldet from JP Morgan. Once the initial kick-off was done, each attendee was able to choose from two technical tracks, an entrepreneur track, or any of the available villages and workshops. It was certainly tough for everyone how to decide where to spend their time, taking a coffee break here and there to meet and greet colleagues, friends, and keep enjoying all the activities happening around.
After lunch, I began my presentation on “Threat hunting .NET malware with YARA”, giving some examples of how to use YARA and the newly added .NET module, particularly useful for tracking the growing number of malware relying on Microsoft’s flagship framework. For learning purposes I chose a very popular malware targeting Latin American ATMs named Ploutus, which has landed in US territory just recently. It was quite an experience to fit an entire day of YARA content in less than an hour, but fortunately everyone at the presentation was extremely supportive, whether they have been using the tool since the beginning or never heard about it before.
From https://twitter.com/mathmare_/status/954786901621387264
Then it was the turn for Dmitry Bestuzhev, Director of Kaspersky Lab’s Global Research and Analysis Team in Latin America, who gave an astonishing presentation titled “Moving like a Spook through Walls Or how to be only a shadow for APT detectors”. It’s always interesting to observe how the community sees the Latin American threat landscape, which sometimes would seem as it’s not getting the attention it deserves. There wasn’t enough room in the auditorium to fit all the people interested in the talk, however since coffee and pastries were waiting for us after the presentation, the conversation could be continued with all of those that were eager to keep the debate open.
From https://twitter.com/pentest_it/status/954789778528096256
The biggest surprise for me was the addition of an entrepreneur track, something that undoubtedly every attendee was thankful for. Sometimes we are guilty of getting lost in the technical side of things, forgetting about the business and how to actually make our idea reach the audience we want it to. There were presentations from different startups, and remarkable information on how to grow your business, monetize it, and ultimately how not to lose sight of your original concept or idea even when dealing with venture capitals and external pressures.
It’s one of those events that you can’t miss, whether it’s playing the custom capture the flag game with your team, building weird antennas in the hacking village, or participating in any of the tracks, you’ll find something in BSides NYC for you. Oh, and don’t forget, there’s always conference swag!
Proofpoint to Acquire Security Awareness Training Firm Wombat Security for $225 Million
7.2.2018 securityweek IT
Cybersecurity firm Proofpoint on Tuesday announced that it has agreed to acquire Wombat Security Technologies for $255 million in cash.
Wombat, which helps companies educate employees on the dangers of phishing attacks and how to avoid them, grew out of a research project at Carnegie Mellon University in 2008.
The purchase of Wombat is the second acquisition north of $100 million by Proofpoint in recent months. Proofpoint also acquired messaging security firm Cloudmark in November 2017 for $110 million in cash.
Proofpoint LogoBest known for its email security offerings, Proofpoint says the acquisition will help its customers use data from active phishing campaigns for simulations.
The company explains that by integrating Wombat’s technology with Proofpoint’s threat detection and intelligence, enterprises will have insights into their employees’ vulnerability to the real phishing attacks that strike every day.
“Because threat actors target employees as the weakest link, companies need to continuously train employees and arm them with real-time threat data,” said Gary Steele, Proofpoint CEO. “The acquisition of Wombat gives us greater ability to help protect our customers from today’s people-centric cyberattacks, as cybercriminals look for new ways to exploit the human factor. We are thrilled to welcome Wombat’s employees to the Proofpoint team.”
The integrated solution will become part of Proofpoint's advanced email solution suite, and is scheduled to be available in the first half of 2018.
The agreement is subject to customary closing conditions and is expected to close in the first quarter of 2018, Proofpoint said.
Following the acquisition, Proofpoint expects Wombat will increase its 2018 revenue range by $30 – $32 million, and increase the free cash flow range by $2 million for the year.
Business Wire Hit by Ongoing DDoS Attack
7.2.2018 securityweek Attack
Newswire service Business Wire said Tuesday that it has been under a sustained Distributed Denial of Service (DDoS) attack for almost a week.
The company said that since last Wednesday, January 31, the attack has been attempting to render the newswire service portal unavailable.
As a frequent user of Business Wire services, SecurityWeek can confirm that the web-based service has been often unresponsive or seen performance being extremely degraded in recent days.
In a customer advisory, Richard DeLeo, Chief Operating Officer at Business Wire, said there is no evidence that any systems or client information have been compromised.
DeLeo said the company is working closely with unnamed partners to mitigate and resolve the attacks and stabilize the environment, but did not share any details, other than calling it a “directed and persistent” attack.
A traceroute shows that the company utilizes Akamai as a content delivery network to handle web requests to www.businesswire.com.
In August 2015, Berkshire Hathaway-owned Business Wire was victim of a cyberattack that allowed malicious actors to gain unauthorized access to non-public, market-moving information stored on its news distribution platform. Soon after, the Securities and Exchange Commission (SEC) announced that a cybercriminal group allegedly hacked into multiple newswire services to steal non-public information about corporate earnings announcements that were used to make financial trades that generated more than $100 million in illegal profits.
According to Arbor Networks’ 13th Annual Worldwide Infrastructure Security Report (WISR), 57% of enterprise, government and education (EGE) respondents and 45% of data center operators had their network resources depleted due to DDoS attacks in 2017. Arbor observed 7.5 million DDoS attacks in 2017.
Arbor also found that attack durations surged in 2017, with 29% of service providers saying they experienced attacks of over 12 hours. 45% of respondents said they experienced more than 21 attacks per month, while 17% were hit more than 500 times per month.
Adobe rolled out an emergency patch that fixed CVE-2018-4878 flaw exploited by North Korea
7.2.2018 securityaffairs Vulnerebility
Adobe rolled out an emergency patch that fixed two critical remote execution vulnerabilities, including the CVE-2018-4878 flaw exploited by North Korea.
Adobe has rolled out an emergency patch to address two Flash player vulnerabilities after North Korea’s APT group was spotted exploiting one of them in targeted attacks.
Last week, South Korea’s Internet & Security Agency (KISA) warned of a Flash zero-day vulnerability (CVE-2018-4878) that has reportedly been exploited in attacks by North Korea’s hackers.
According to the alert published by the KISA, the vulnerability affects the latest Flash Player version 28.0.0.137 and earlier.
The zero-day vulnerability could be exploited by an attack by tricking victims into opening a document, web page or email containing a specially crafted Flash file.
“A zero-day vulnerability has been found in Adobe Flash Player. An attacker may be able to convince a user to open a Microsoft Office document, web page, or spam mail containing a Flash file,” reads the advisory published by the Korean CERT.
According to the researcher Simon Choi the Flash Player zero-day has been exploited by North Korea since mid-November 2017. The attackers exploited the zero-day vulnerability in attacks aimed at South Korean individuals involved in research activity on North Korea.
Hackers exploited the vulnerability to deliver a malware, in the image shared by Choi on Twitter shows that the exploit has been delivered via malicious Microsoft Excel files.
Simon Choi
@issuemakerslab
Flash 0day vulnerability that made by North Korea used from mid-November 2017. They attacked South Koreans who mainly do research on North Korea. (no patch yet)
11:11 AM - Feb 1, 2018
208
234 people are talking about this
Twitter Ads info and privacy
Cisco and FireEye have both been investigating, and warn that a North Korean group that they have been following for a while are likely behind this latest attack. Called TEMP.Reaper by FireEye and Group 123 by Cisco, the group with ties to North Korea was very active in 2017.
Adobe addressed the bug with an emergency patch that also fixed another remote code execution vulnerability, tracked as CVE-2018-4877, that was discovered by researchers at Qihoo 360 Vulcan Team.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could lead to remote code execution in Adobe Flash Player 28.0.0.137 and earlier versions. Successful exploitation could potentially allow an attacker to take control of the affected system.” reads the security advisory published by Adobe.
“Adobe is aware of a report that an exploit for CVE-2018-4878 exists in the wild, and is being used in limited, targeted attacks against Windows users. These attacks leverage Office documents with embedded malicious Flash content distributed via email.”
The two vulnerabilities are rated critical for all supported operating systems, the unique exception is the Linux build of Adobe Flash Player Desktop Runtime.
There have been over 1,000 Adobe Flash vulnerabilities since it was released. Designed to make website development easier and providing additional features not supported by standard web browsers, it also adds complexity and a much broader attack surface. Web browsers no longer support Flash by default, but users often re-enable it for convenience. And just having it installed on your system may be enough for vulnerabilities like these ones to be exploited.
Researchers ported the NSA EternalSynergy, EternalRomance, and EternalChampion to Metasploit
7.2.2018 securityaffairs BigBrothers
Security researcher Sean Dillon ported three NSA-linked exploits, EternalSynergy, EternalRomance, and EternalChampion, to the Metasploit platform.
The security researcher at RiskSense Sean Dillon (@zerosum0x0) ported the Rapid7 Metasploit three hacking tools supposedly stolen from the NSA-linked Equation Group.
The researcher modified the exploits to use them also against latest windows versions and merged them into the Metasploit Framework, they should work on all unpatched versions of Windows based on x86 and x64 architectures.
The three exploits are EternalSynergy, EternalRomance, and EternalChampion that were leaked by the hacker crew Shadow Brokers in April 2017.

The tools were later used in several attacks in the wild, for example, the EternalRomance exploit was used in the massive Bad Rabbit ransomware attack.
The versions ported to Metasploit could be used to target all Windows versions since Windows 2000.


zǝɹosum0x0🦉
@zerosum0x0
MS17-010 #EternalSynergy #EternalRomance #EternalChampion exploit and auxiliary modules for @Metasploit. Support for Windows 2000 through 2016. I basically bolted MSF psexec onto @sleepya_ zzz_exploit. https://github.com/rapid7/metasploit-framework/pull/9473 …
5:54 AM - Jan 29, 2018
655
503 people are talking about this
Twitter Ads info and privacy
The EternalChampion and EternalSynergy exploits trigger a race condition with Transaction requests tracked as CVE-2017-0146, while the EternalRomance and EternalSynergy exploits trigger the CVE-2017-0143, a type confusion between WriteAndX and Transaction requests.
The expert explained that the tool can be used to run any command as System or to stage Meterpreter.
“You can run any command as SYSTEM, or stage Meterpreter. Note: unlike EternalBlue, kernel shellcode is not used to stage Meterpreter, so you might have to evade your payloads.” Dillon explained.
“This module is highly reliable and preferred over EternalBlue where a Named Pipe is accessible for anonymous logins (generally, everything pre-Vista, and relatively common for domain computers in the wild).”
The Metasploit module does not implement shellcode execution, instead, it overwrites the SMB connection session structures instead to obtain Admin/SYSTEM session.
“The exploit chain is an almost 1:1 skid port of @worawit awesome zzz_exploit adaptation, which brings a few improvements over the original Eternal exploits. Instead of going for shellcode execution, it overwrites the SMB connection session structures to gain Admin/SYSTEM session.” wrote the expert.
“The MSF module is leaner (stripped down packet count/padding), checks extra named pipes, sprinkles randomness where possible, and has Metasploit’s psexec DCERPC implementation bolted onto it. For the last reason, Rex is used and not RubySMB,”
Further info and the “MS17-010 EternalSynergy / EternalRomance / EternalChampion aux+exploit modules” are available on GitHub.
TLS-Abusing Covert Data Channel Bypasses Network Defenses
6.2.2018 securityweek Krypto
Researchers from Fidelis Cybersecurity have discovered a new method of abusing the X.509 public key certificates standard for covert channel data exchange following initial system compromise.
The standard is used in both Transport Layer Security (TLS) and Secure Sockets Layer (SSL) cryptographic Internet protocol implementations, but the manner in which the certificates are exchanged can be abused to hijack them for command and control (C&C) communication, the researchers say.
The X.509 extensions can be used for covert channel data transfer to bypass network protection methods that do not inspect certificate values, the researchers say. To date, no confirmed cases of this technique being abused have been observed, but the widespread use of certificates could put many organizations at risk, Fidelis researchers argue.
To demonstrate their theory, Fidelis Cybersecurity revealed a custom-built framework that serves as proof of concept. However, the researchers point out that detection is possible and that the community can implement protections to identify possible abuse of the covert channel data transfer mechanism.
The use of covert channels for data transfer across the network is not new, and the possible abuse of X.509 certificates for covert network communication was demonstrated before. In fact, the use of the TLS protocol to establish hidden communication channels was detailed a decade ago.
The new research (PDF) by Fidelis’ Jason Reaves into the use of X.509 extensions for covert channel purposes expands on the previous findings to describe a system that could be used to send or receive data from both a client and a server perspective.
Using previous demonstrations that arbitrary data can be placed into X.509 certificates and that these certs can be used as a covert channel, the researcher argues that a sufficiently motivated attacker could “utilize technologies outside of their intended purposes to not only accomplish their goals but also end up bypassing common security measures in the process.”
Reaves analyzed X.509 certificate extensions, which “provide methods for associating additional attributes with users or public keys and for managing relationships between CAs,” but which can be abused for malicious purposes due to ambiguity in the language, which led to relaxed implementations.
Because TLS X.509 certificates have a large number of fields where strings can be stored, actors can take advantage of this to hide data transfer inside one of these fields. The certificates are exchanged before the TLS session is established, meaning that the data transfer doesn’t show up, although it was performed within the certificate exchange itself.
“Testing shows that using this methodology for communication and control in malware will not result in anything beyond an SSL negotiation which could bypass common security mechanisms that are not looking for abnormal data being passed in X.509 certificates,” Reaves says.
Fidelis also came up with a proof of concept to show that file transfer using the X.509 covert channel would be possible. For their demonstration, they chose to simulate a threat actor transferring the password stealing tool Mimikatz to a compromised system.
Cisco Reissues Patches for Critical Firewall Flaw
6.2.2018 securityweek Vulnerebility
Cisco has reissued patches for a critical vulnerability affecting some of the company’s security appliances after identifying new attack vectors and additional affected features, and determining that the original fix had been incomplete.
The networking giant informed customers in late January that its Adaptive Security Appliance (ASA) software is affected by a serious flaw that can be exploited by a remote and unauthenticated attacker to execute arbitrary code or cause a denial-of-service (DoS) condition.
The vulnerability, tracked as CVE-2018-0101, affects several products running ASA software, including Firepower firewalls, 3000 series industrial security appliances, ASA 5000 and 5500 series appliances, 1000V cloud firewalls, ASA service modules for routers and switches, and Firepower Threat Defense (FTD) software.
The details of the security hole were disclosed on February 2 at a conference by Cedric Halbronn, an NCC Group researcher who reported the bug to Cisco.
“When exploited, this vulnerability known as CVE-2018-0101 allows the attacker to see all of the data passing through the system and provides them with administrative privileges, enabling them to remotely gain access to the network behind it,” NCC Group said in a blog post. “Targeting the vulnerability without a specially-crafted exploit would cause the firewall to crash and would potentially disrupt the connectivity to the network.”
Cisco initially told customers that the vulnerability is related to the webvpn feature, but further analysis revealed additional attack vectors and impacted features.
In an updated advisory published on Monday, the company said the flaw affects more than a dozen features, including Adaptive Security Device Manager (ASDM), AnyConnect IKEv2 Remote Access and SSL VPN, Cisco Security Manager, Clientless SSL VPN, Cut-Through Proxy, Local Certificate Authority, Mobile Device Manager Proxy, Mobile User Security, Proxy Bypass, the REST API, and Security Assertion Markup Language (SAML) Single Sign-on (SSO).
A specific configuration for each of these features introduces the vulnerability, but some of the configurations are reportedly common for the affected firewalls.
Cisco has now released a new set of patches after discovering that the initial fixes were vulnerable to additional DoS attacks.
“While Cisco PSIRT is not aware of any malicious use of this vulnerability, Cisco highly recommends all customers upgrade to a fixed software version,” said Omar Santos, principal engineer in the Cisco Product Security Incident Response Team (PSIRT). “This proactive patching is especially important for those customers whose devices and configurations include potential exposure through the expanded attack surface.”
Cato Networks reported that there are roughly 120,000 ASA devices with the webvpn feature enabled accessible from the Internet. Furthermore, some system administrators have complained about the availability of patches and the time it takes to apply them.
System admin Colin Edwards posted a blog post suggesting that Cisco may have started patching the vulnerability 80 days before publishing a security advisory to warn customers.
“I can understand some of the challenges that Cisco and their peers are up against. But even with that, I’m not sure that customers should be willing to accept that an advisory like this can be withheld for eighty days after some fixes are already available,” Edwards said. “Eighty days is a long time, and it’s a particularly long time for a vulnerability with a CVSS Score of 10 that affects devices that are usually directly connected to the internet.”
Santos said the company published the advisory shortly after learning that there had been public knowledge of the vulnerability.
NSA-Linked Hacking Tools Ported to Metasploit
6.2.2018 securityweek BigBrothers
Three hacking tools supposedly stolen from the National Security Agency-linked Equation Group and made public last year were recently ported to Rapid7’s Metasploit Framework.
The three exploits – EternalSynergy, EternalRomance, and EternalChampion – were released publicly in April 2017 alongside the more popular EternalBlue, one month after Microsoft patched them.
The tools could previously be used only on several, older Windows releases, although EternalSynergy was modified to target recent Windows versions as well. Last year, EternalRomance was used in the global Bad Rabbit ransomware attack.
All three exploits can now be used to target all Windows versions since Windows 2000, Sean Dillon, a security researcher with RiskSense who goes by the online handle of @zerosum0x0, reveals. The researcher modified the exploits and merged them into the open-source Metasploit Framework.
The three tools target two vulnerabilities in Microsoft’s platform, namely CVE-2017-0146, a race condition with Transaction requests exploited by EternalChampion and EternalSynergy, and CVE-2017-0143, a type confusion between WriteAndX and Transaction requests exploited by EternalRomance and EternalSynergy.
The researcher explains that the module does not use kernel shellcode to stage Meterpreter, meaning that those interested in leveraging it would need to use evasion for their payloads. However, the tool can be used to run any command as System or to stage Meterpreter.
“This module is highly reliable and preferred over EternalBlue where a Named Pipe is accessible for anonymous logins (generally, everything pre-Vista, and relatively common for domain computers in the wild),” the researcher says.
The module does not attempt shellcode execution, but overwrites the SMB connection session structures instead, thus achieving Admin/SYSTEM session.
“The MSF module is leaner (stripped down packet count/padding), checks extra named pipes, sprinkles randomness where possible, and has Metasploit's psexec DCERPC implementation bolted onto it. For the last reason, Rex is used and not RubySMB,” the researcher explains.
The exploits can be used on both 32-bit and 64-bit architectures and target all platform iterations from Windows 2000 to Windows 10 and Windows Server 2016.
The module is available on GitHub. As Dillon points out, it has been created for academic research and the development of defenses, not to be used in attacks, except where explicitly authorized.
Duo Charged Over ATM "Jackpotting" Attacks
6.2.2018 securityweek Attack
Two men were charged in the United States with bank fraud from their involvement an alleged ATM "jackpotting" operation.
Alex Alberto Fajin-Diaz, 31, a citizen of Spain, and Argenys Rodriguez, 21, of Springfield, Massachusetts, were both arrested on related state charges on January 27 and are currently detained.
ATM jackpotting is an attack technique targeting automated teller machines (ATMs), where criminals connect to these devices and install malware or use specialized hardware to control the operations of the machine and cause them to dispense cash.
While the attack method hasn’t been seen in the United States until recently, ATM makers and the U.S. Secret Service issued alerts last month on the technique being used in attacks in the U.S. as well. The alerts warned that ATMs located in pharmacies, big box retailers, and drive thru ATMs were being targeted by jackpotting attacks.
A Department of Justice announcement on Monday revealed that ATM jackpotting incidents recently occurred in Hamden, Guilford, and Providence, Rhode Island, and that federal, state and local law enforcement agencies have been investigating the attacks.
According to the criminal complaint, on January 27, 2018, Fajin-Diaz and Rodriguez were found near an ATM compromised with jackpotting malware and which “was in the process of dispensing $20 bills,” the DoJ announcement reads. On the same date, Citizens Bank investigators had contacted police after an apparent attack on an ATM in Cromwell.
“A search of Fajin-Diaz and Rodriguez’s vehicle, which had a license plate that was assigned to another vehicle, revealed tools and electronic devices consistent with items needed to compromise an ATM machine to dispense its cash contents. Faji-Diaz and Rodriguez also possessed more than $9,000 in $20 bills,” the DoJ says.
If found guilty of bank fraud, the two face a maximum sentence of 30 years in prison.
Although widely reported on only last week, ATM jackpotting attacks in the U.S. appear to have started several months ago, with the first suspects arrested in November 2017, as Oil City News reported at the time.
Cisco, Apple Launch Cyber Risk Offering With Insurance Giant Allianz
6.2.2018 securityweek Cyber
Cisco, Apple, Aon, Allianz Partner to Help Businesses Protect Against Common Malware Threats
Munich, Germany-based Allianz -- named by Forbes as the world's second largest insurance firm -- is offering cyber insurance at competitive premiums with reduced deductibles; but only if the insured is risk-assessed by Aon and uses certain Cisco and Apple products.
Over the last few years, information security has increasingly been seen as a risk management issue. One of the traditional options for risk management is risk transfer; that is, insurance. But while the cyber insurance option has increased in visibility, its adoption remains relatively low. In 2016, US cyber insurance premiums were reported to be $1.35 billion. This is just 3.3% of the total premiums for U.S. commercial line insurers. Clearly, there is an opportunity for insurance companies to increase their own share of a potentially large market.
At the same time, product vendors are always looking for new opportunities to sell their products. The potential for linking specific product to reduced insurance premiums could help both industries to increase market share.
This has been slow to materialize because insurance works on detailed statistics between risk and premiums. It has decades of statistics for motor vehicles, and perhaps hundreds of years for shipping -- but only a few years' experience of a continuously changing and worsening infosecurity world. The natural effect of this is that premiums have to be set at the higher end of the possible scale simply because nobody really understands the full risk.
Apple and Cisco have been working to change this. In June 2017, Cisco's David Ulevitch (VP, security business group) announced, "We’re collaborating with insurance industry heavyweights to lead the way in developing the architecture that enables cyber insurance providers to offer more robust policies to our customers."
This collaboration surfaced yesterday in the announcement of a deal with Allianz: "a new cyber risk management solution for businesses, comprised of cyber resilience evaluation services from Aon, the most secure technology from Cisco and Apple, and options for enhanced cyber insurance coverage from Allianz," said Apple. However, it should be noted that this is not a general cyber insurance offering, but one specifically related to "cyber risk associated with ransomware and other malware-related threats, which are the most common threats faced by organizations today."
There are three elements that could lead to the insurance deal. The first is that the candidate company is risk assessed by Aon, who will examine the company's existing cyber security posture and make recommendations on how to improve existing defenses.
The second is that the candidate company should use Cisco Ransomware Defense and/or qualified Apple products iPhone, iPad and Mac. The third is that insured companies will then have access to Cisco and Aon incident response teams in the event of a malware attack.
With any contract, and an insurance policy is just a contract, the devil is always in the detail. It isn't clear from the current announcement whether the insurance will go beyond just a malware attack -- into, for example, data manipulation or theft because of the malware attack. That may vary from contract to contract depending on the result of the Aon assessment.
For the moment, there is just the bald statement that if a company uses certain Cisco and Apple product, and presumably 'passes' a risk assessment by Aon, that company might possibly qualify for lower deductibles in a malware-related cyber insurance policy underwritten by Allianz.
Windows 10 Ransomware Protection Easily Bypassed, Researcher Says
6.2.2018 securityweek Ransomware
It’s rather trivial to bypass the anti-ransomware feature that Microsoft introduced in its Windows 10 Fall Creators Update, a security researcher claims.
Dubbed Controlled folder access, the anti-ransomware feature was announced as part of Windows Defender Exploit Guard, a new set of host intrusion prevention capabilities in Microsoft’s latest platform iteration.
When announcing the feature, Microsoft described it as a layer of real-time protection that would allow users to prevent ransomware from accessing their data by defining what programs have access to certain folders. Thus, malware and other unauthorized apps would not be able to touch the files in those directories.
According to Yago Jesus, however, this added protection can be easily bypassed by using an authorized application such as Office to access the data.
This would be possible because Office executables are by default whitelisted and allowed to make changes to files placed in protected folders, without restrictions, even when a malicious actor uses OLE/COM objects to control Office executables programmatically.
“So, a ransomware developer could adapt their software to use OLE objects to change / delete / encrypt files invisibly for the files owner,” the researcher explains.
Thus, an attacker capable of creating code leveraging OLE Word Object for execution would be able to bypass the anti-ransomware feature in Windows 10. Windows Defender would do nothing to stop the code from execution, because the entire operation would rely on the native encryption feature in Microsoft Office.
This technique, the researcher argues, renders Windows Defender Exploit Guard’s Controlled folder access functionality useless in an environment where both Office and Windows are employed. In addition to documents, the method can also be used to target PDFs, images, and other file types that Office can edit.
“While this capability is designed to protect against ransomware, it’s not surprising that it’s unable to handle all ransomware scenarios. The use of Microsoft Office files, which is described in the recent documented bypass, has been an effective way for attackers to get around AV tools,” Lenny Zeltser, Vice President of Products at Israel-based Minerva Labs, told SecurityWeek via email.
Another exploitation scenario, Jesus reveals, would involve the use of Selection.Copy / Selection.Paste methods to copy the content of a protected file to another file located outside the protected folder, delete the content of the original file or replace it with a ransom note, and then encrypt the new file normally.
The researcher says he informed Microsoft on his findings and that the company confirmed that they would resolve the issue “through an improvement to the Controlled Folder Access functionality.” However, it appears that the tech giant doesn’t see the bug as a security vulnerability, “because Defender Exploit Guard isn't meant to be a security boundary.”
According to Joseph Carson, chief security scientist at Washington D.C. based Thycotic, such a response from Microsoft is unacceptable.
"Frankly, this is a classic example of being misleading,” he told SecurityWeek via email. “It's like a security guard at the door of a building checking to ensure that anyone entering has the correct access, when you've left the backdoor wide open. It is a false sense of protection as you are purely relying on cybercriminals being honest.”
“When you call a product ‘Windows Defender’, or use terms such as ‘Defender Exploit Guard’, and when notified by a security researcher on a security bypass, the response of course is legally correct stating ‘we aren't classifying this as a security vulnerability because Defender Exploit Guard isn't meant to be a security boundary’,” Carson said.
He also pointed out that this bypass technique might have been already exploited in attacks against businesses and that companies should not simply rely on Windows Defender as the only security control, especially if Microsoft themselves say it isn’t even a security boundary.
“Immediately change the name to what it is rather than misleading consumers into a false sense of security and protection,” Carson concluded.
Meni Farjon, Co-Founder and CTO at Israel-based SoleBIT Labs, also believes that attackers are bound to leverage Office capabilities to bypass Microsoft’s ransomware protection. The main vulnerability, he told SecurityWeek, is that there’s a whitelist of programs such as Office that are allowed to make changes to protected folders without restrictions.
“Today we see an increase in macro-based malware, leveraging Office active-content capabilities to deliver ransomware. Generally speaking, I believe Windows Defender’s ransomware protection should not be considered a fully functional anti-ransomware feature, but more like a data protection feature. I would advise users to augment such defenses with vulnerability and active content detection solutions to combat ransomware on the network level, before it even reaches the endpoint,” Farjon concluded.
Microsoft hasn’t responded yet to SecurityWeek’s request for a comment on the matter.
One Computer Can Knock Almost Any WordPress Site Offline
6.2.2018 securityweek Vulnerebility
As if there aren't enough ways to attack a WordPress site, an Israeli researcher has published details of how almost anyone can launch a denial of service (DoS) attack against almost any WordPress with just one computer. That, he suggests, is almost 30% of all websites on the internet.
The attack uses the vulnerability associated with CVE-2018-6389. The CVE database, at the time of writing, has no details, marking it only as 'reserved' for future use. Details, however, can be found in a Barak Tawily blog post published Monday. It is an abuse of the WordPress load-scripts.php function, which exists to allow administrators/web designers to improve website performance by combining multiple JavaScript files into a single request at the server end.
Tawily's DoS methodology makes use of two elements. Firstly, use of load-scripts.php requires no user authentication -- it can be invoked by anyone. The second element is that load-scripts.php receives a parameter called 'load[]', which is an array. The purpose of the array is to be able to specify which scripts should be combined and loaded to improve performance. Since it is also used to improve performance of the wp-login.php page, it can be invoked before any user authorization is required.
Within WordPress there is a wp_scripts list containing defined paths for all the 181 script files. The intention is that the administrator or web designer can include the path for specific scripts within the load[] parameter, and improve performance according to the supplied value from the user. The wp_scripts list is hard-coded in the script-loader.php file.
"I wondered," writes Tawily "what would happen if I sent the server a request to supply me every JS module that it stored? A single request would cause the server to perform 181 I/O actions and provide the file contents in the response. I did so..."
The result took 2.2 seconds and was almost 4 Mb of data -- making the server work hard to comply.
Tawily's next step was to use a python script he had written himself to send repeated identical requests to the server. And this time it worked. "As long as I kept sending those requests to the server, it was too busy to handle any other request, and I had effectively (and easily) caused DoS."
He used HackerOne to report the issue to WordPress, even though DoS is outside the scope of WordPress bounties. Nevertheless, it is a vulnerability that needed to be reported. The response, however, was muted: "This kind of thing should really be mitigated at the server or network level rather than the application level, which is outside of WordPress's control," said WordPress.
That's debatable on two counts. First, many WordPress sites are blogs and micro-business sites run cheaply on shared servers with the respective service providers, and with little technical skill among the owners. There is simply no way that such sites can be mitigated at the server or network level.
Second, Tawily goes on to show that mitigation isn't really that difficult if you know what to do (which many WordPress users do not). He "forked WordPress project and patched it so no one but authenticated users can access the load-*.php files, without actually harming the wp-login.php file functionality." He goes further to provide a bash script that modifies the relevant files to mitigate the vulnerability.
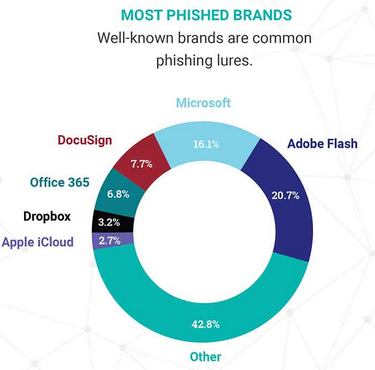
SSL Increasingly Abused by Malware, Phishing: Report
6.2.2018 securityweek Phishing
There has been a significant increase in the number of phishing and malware attacks abusing SSL and TLS technology, according to Zscaler’s SSL Threat Report for the second half of 2017.
In the first half of 2017, Zscaler’s products blocked roughly 600,000 threats hidden in encrypted traffic every day, but that number grew to 800,000 in the second half of the year, which represents an increase of 30 percent.
Malicious actors have used SSL-encrypted channels for the initial delivery of malvertising, phishing and compromised websites, to distribute malware payloads and exploits, and for communications between the infected host and command and control (C&C) servers.
In the case of phishing attempts, Zscaler saw a 400 percent increase in the first half of 2017 compared to 2016. Overall, in 2017, phishing activity jumped by nearly 300 percent.
Phishing pages served over HTTPS are either hosted on a compromised website that has an SSL certificate, or they are hosted on malicious sites that imitate well-known brands and rely on certificates obtained by the cybercriminals themselves. Services such as Let’s Encrypt make it easier for malicious actors to obtain free certificates that they can use in their operations.
In the case of malware attacks, Zscaler said SSL/TLS channels were used 60 percent of the time to deliver banking Trojans throughout 2017, and ransomware was spotted in one-quarter of attempts. Many attackers obtained an encrypted distribution channel for their malware by hosting it on legitimate services such as Box, Dropbox, Google and AWS.
An analysis of roughly 6,700 SSL transactions blocked by Zscaler showed that a majority of abused certificates belonged to legitimate sites that had been compromised.
The security firm also found that the types of certificates that are most abused by cybercriminals are domain validated (DV) certificates, which have a validity of three months and are obtained more easily. DV certificates, particularly ones obtained for free, were spotted in 75 percent of cases.
More than half of certificates were valid for less than one year, and roughly one-third of those had a validity period of three months or less.
Adobe Patches Flash Zero-Day Exploited by North Korean Hackers
6.2.2018 securityweek Vulnerebility
Adobe updated Flash Player on Tuesday to address a zero-day vulnerability exploited by what experts believe to be a North Korean hacker group in attacks aimed at individuals in South Korea.
The existence of the vulnerability, tracked as CVE-2018-4878, came to light on January 31 when South Korea’s Internet & Security Agency (KISA) issued an alert. Cybersecurity experts based in the country said the flaw had been used by North Korean threat actors against South Koreans who focus on North Korea research.
Adobe has promised to release a patch sometime this week and it has kept its promise. Flash Player version 28.0.0.161 should fix the vulnerability, which the company has described as a use-after-free bug that allows remote code execution.
The security hole, which affects Flash Player 28.0.0.137 and earlier, was brought to the company’s attention by South Korea's KrCERT/CC.
The latest Flash release also patches CVE-2018-4877, which is also a use-after-free vulnerability that allows remote code execution. The flaw was reported to Adobe by bo13oy of Qihoo 360 Vulcan Team via Trend Micro’s Zero Day Initiative (ZDI). Adobe does not appear to be aware of any attacks exploiting CVE-2018-4877.
FireEye has analyzed the attacks involving CVE-2018-4878 and believes the zero-day has been used by a group it tracks as TEMP.Reaper. The security firm determined that these hackers are likely based in North Korea based on IP addresses used to access command and control (C&C) servers.
“The majority of their targeting has been South Korea focused, targeting the government, military, and defense industrial base as well as other industry,” FireEye said. “They have also taken an interest in predictable North Korean interests such as unification efforts and defectors.”
The attacks observed by FireEye involved malicious Office documents and spreadsheets designed to exploit the Flash Player zero-day in an effort to deliver a piece of malware tracked by the company as DOGCALL.
Cisco Talos has also analyzed the campaign and attributed it to an actor it tracks as Group 123. While Cisco has not explicitly blamed North Korea for attacks launched by Group 123, the company has detailed several campaigns aimed at South Korea that often use North Korea-related topics as a lure when delivering malware.
Researchers pointed out that the addition of a zero-day exploit to its arsenal shows that the group has become highly motivated and sophisticated.