South Korea Warns of Flash Zero-Day Exploited by North Korea
2.2.2018 securityweek BigBrothers
South Korea’s Internet & Security Agency (KISA) has issued an alert for a zero-day vulnerability in Flash Player that has reportedly been exploited in attacks by North Korean hackers.
Few details have been provided, but KISA says the vulnerability affects Flash Player 28.0.0.137 and earlier. Version 28.0.0.137 is the latest, released by Adobe in January as part of the Patch Tuesday updates.
The security hole can be exploited by getting a user to open a document, web page or email containing a specially crafted Flash file, KISA said on Wednesday.
Simon Choi of South Korea-based cybersecurity firm Hauri said on Twitter the Flash Player zero-day has been exploited by North Korea since mid-November 2017 in attacks aimed at South Korean individuals who focus on researching North Korea.
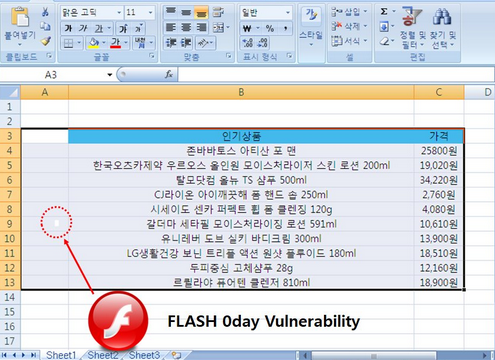
According to the expert, the flaw has been leveraged to distribute malware. A screenshot he posted appears to show that the exploit has been delivered via malicious Microsoft Excel files. 
Flash zero-day exploited by North Korea - credits: Simon Choi (@issuemakerslab)
SecurityWeek has reached out to Adobe for comment and will update this article once the company responds. Since the activities of North Korean threat actors have been closely monitored by several security firms, it’s possible that Adobe has already been made aware of the zero-day and is working on a patch.
UPDATE. Adobe says it's aware of a report that an exploit for a vulnerability it tracks as CVE-2018-4878 exists in the wild, and is being used in limited, targeted attacks against Windows users. The company says it will address the flaw with an update planned for the week of February 5.
In an advisory, Adobe said the vulnerability is a critical use-after-free that allows remote code execution. Until a patch becomes available, the company has provided some mitigations.
"Beginning with Flash Player 27, administrators have the ability to change Flash Player's behavior when running on Internet Explorer on Windows 7 and below by prompting the user before playing SWF content," Adobe said. "Administrators may also consider implementing Protected View for Office. Protected View opens a file marked as potentially unsafe in Read-only mode."
Kaspersky Launches New Security Product for Exchange Online
2.2.2018 securityweek Safety
Kaspersky Lab has expanded its small and medium-sized business (SMB) offering with a new cloud-based product designed to provide an extra layer of security for the Exchange Online email service in Microsoft Office 365.
The new product, Kaspersky Security for Microsoft Office 365, is designed to protect users against malware, phishing, spam, and other email-borne threats.
Exchange Online includes built-in anti-malware and anti-spam features, but Kaspersky says its own product – part of the company’s Business Hub offering – works in conjunction with Microsoft’s protections and offers native integration.
Kaspersky says its product relies on various security technologies, including machine learning-based detection, an anti-phishing engine that uses neural networks, sandboxing, attachment filtering mechanisms, and data from the company’s threat intelligence network.
The new product analyzes incoming emails and places suspicious messages in quarantine. Administrators are informed of the potential threats via a central console shared with the Kaspersky Endpoint Security Cloud product. The console allows customers to view each potentially malicious email and restore them in case of false positives.
According to the security firm, Kaspersky Security for Microsoft Office 365 is capable of recognizing if a file attached to an email is the type it claims to be, and it can detect malicious macros hidden in harmless-looking Office documents.
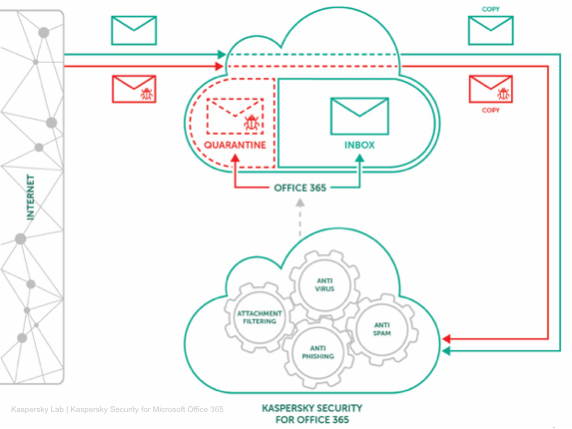
Since there has been a lot of debate recently on the implications of the physical location of data stored in the cloud, Kaspersky allows users to specify which data center they want to use for processing emails.
Furthermore, given the recent controversy regarding the company uploading sensitive files from an NSA contractor’s computer to its own servers, Kaspersky has highlighted that the new product does not upload any files to its systems. Instead, quarantined emails are stored in the customer’s Exchange Online account.
Watch out, cyber criminals are using fake FBI emails to infect your computer
2.2.2018 securityaffairs BigBrothers
The FBI Internet Crime Complaint Center (IC3) is warning of a new malware campaign aimed at infecting victims with weaponized attachments.
The Feds’ Internet Crime Complaint Center (IC3) is warning of a new spam campaign aimed at infecting victims with a ransomware. According to an alert issued on Wednesday by the IC3, numerous citizens filled complaints after received emails purporting to be from IC3. The message pretends to be the compensation from a cyber attack and asks the victims to fill the attached document, but the file is laced with malware.
The story is interesting, the email reports that a Nigerian cyber criminal had been arrested and feds have found the recipient’s email address of the alleged scammer’s PC. The email asks victims to return the document with recipient info and wait for the refund to arrive. Once the victim has opened the document, the infection process will start.

The FBI has identified at least three other versions of the IC3 impersonation scam:
“The first involved a fake IC3 social media page, which advertised itself as the FBI Cyber Crime Department (IC3) and requested recipients provide personal information in order to report an internet crime.” states the alert issued by the FBI. “
“The second involved an email which stated the recipient was treated unfairly by various banks and courier companies. The email claimed the recipient’s name was found in a financial company’s database and that they will be compensated for this unfair treatment.”
“The third example involved an email from the Internet Crime Investigation Center/Cyber Division and provided an address in Minneapolis, Minnesota. The email also included a case reference number in the subject line. The email informed the recipient that their IP address was referred to the IC3 as a possible victim of a federal cyber-crime. The email then requests the recipient to contact the sender via telephone.”
FBI is currently investigating the cases, victims of an online scam can file a complaint with the IC3 at www.ic3.gov.
WannaMine, the sophisticated crypto miner that spreads via NSA EternalBlue exploit
2.2.2018 securityaffairs Virus
Researchers from security firm CrowdStrike spotted a new Monero crypto-mining worm dubbed WannaMine that spreads leveraging the NSA-linked EternalBlue exploit.
This morning I wrote about the Smominru botnet that used NSA exploit to infect more than 526,000 systems, and I explained that other threat actors are using similar techniques to mine cryptocurrency.
This is the case of a strain of the Monero crypto-mining worm dubbed WannaMine that spreads leveraging the EternalBlue exploit.
ETERNALBLUE is the alleged NSA exploit that made the headlines with DOUBLEPULSAR in the WannaCry attack, it targets the SMBv1 protocol and has become widely adopted in the community of malware developers.
In June, following the WannaCry attacks experts discovered that there were at least other 3 different groups have been leveraging the NSA EternalBlue exploit,
Back to the present, WannaMine was developed to mine the Monero cryptocurrency abusing victims’ resources. According to security researchers at CrowdStrike, the malicious code is very sophisticated, it implements a spreading mechanism and persistence model similar to those used by state-sponsored APT groups.
“CrowdStrike has recently seen several cases where mining has impacted business operations, rendering some companies unable to operate for days and weeks at a time. The tools have caused systems and applications to crash due to such high CPU utilization speeds.” reads the analysis published by CrowdStrike.
“CrowdStrike has observed more sophisticated capabilities built into a cryptomining worm dubbed WannaMine. This tool leverages persistence mechanisms and propagation techniques similar to those used by nation-state actors, demonstrating a trend highlighted in the recent CrowdStrike Cyber Intrusion Services Casebook 2017, which states that “contemporary attacks continue to blur the lines between nation-state and eCrime tactics.”
WannaMine is a fileless that was first reported by researchers at Panda Security.

The malicious code implements so-called “living off the land” techniques to gain persistence on the infected system leveraging Windows Management Instrumentation (WMI) permanent event subscriptions. WannaMine registers a permanent event subscription that would execute every 90 minutes a PowerShell command located in the Event Consumer.
Experts noticed that the malware uses credential harvester Mimikatz to collect users’ credentials that could be used for lateral movements. It also relies on the EternalBlue exploit in case it is not able to move laterally with the above technique.
WannaMine is able to infect systems running all Windows versions starting with Windows 2000, including 64-bit versions and Windows Server 2003.
“While the tactics, techniques, and procedures (TTPs) displayed in WannaMine did not require a high degree of sophistication, the attack clearly stands on the shoulders of more innovative and enterprising nation-state and eCrime threat actors. CrowdStrike anticipates that these threat actors will continue to evolve their capabilities to go undetected,” CrowdStrike concluded.
WannaMine would degrade the performance of the infected machines, in case of laptops the malicious code could cause damages if it runs continuously for several hours.
Sophos experts published an interesting post containing Q&A on WannaMine.
WannaMine Malware Spreads via NSA-Linked Exploit
1.2.2018 securityweek Virus Exploit
A piece of crypto-mining malware is using sophisticated tools for its operations, including a Windows exploit linked to the National Security Agency, security researchers warn.
Dubbed WannaMine, the crypto-mining worm spreads using EternalBlue, the NSA-linked tool that became public in April 2017, just one month after Microsoft released a patch for it.
Leveraging a vulnerability in Windows’ Server Message Block (SMB) on port 445, the exploit became famous after the WannaCry ransomware was found exploiting it for distribution. Other malware families abused it as well, including botnets, backdoors, NotPetya, and banking Trojans.
Now, the same exploit is being used to spread WannaMine, a piece of malware focused on mining for the Monero crypto-currency, but which uses sophisticated capabilities, such as persistence and distribution mechanisms similar to those used by nation-state actors, CrowdStrike says.
WannaMine, the security researchers explain, employs “living off the land” techniques for persistence, such as Windows Management Instrumentation (WMI) permanent event subscriptions. The malware has a fileless nature, leveraging PowerShell for infection, which makes it difficult to block without the appropriate security tools.
The malware uses credential harvester Mimikatz to acquire legitimate credentials that would allow it to propagate and move laterally. If that fails, however, the worm attempts to exploit the remote system via EternalBlue.
To achieve persistence, WannaMine sets a permanent event subscription that would execute a PowerShell command located in the Event Consumer every 90 minutes.
The malware targets all Windows versions starting with Windows 2000, including 64-bit versions and Windows Server 2003. However, it uses different files and commands for Windows Vista and newer platform iterations.
“While the tactics, techniques, and procedures (TTPs) displayed in WannaMine did not require a high degree of sophistication, the attack clearly stands on the shoulders of more innovative and enterprising nation-state and eCrime threat actors. CrowdStrike anticipates that these threat actors will continue to evolve their capabilities to go undetected,” the security company notes.
As Sophos points out, organizations that find the WannaMine malware in their network are also at risk of other malware, including ransomware. It is not uncommon to find multiple malware families on machines that have been compromised once.
Designed to mine for Monero, not to steal user information or crypto-coins, WannaMine would still slow down the infected machines. Laptops could even be damaged, if the malware runs on them continuously for several hours, as the device gets hotter. Also, the battery is drained faster than usual, Sophos points out.
An antivirus application should keep users protected from this malware family. Keeping systems up to date at all times and using strong passwords should also help avoiding a WannaMine infection.
Google Adds Custom Roles Feature to Cloud IAM
1.2.2018 securityweek IT
The Identity & Access Management (IAM) service in the Google Cloud Platform (GCP) now includes a feature that allows users to assign custom roles for finer-grained security.
The custom roles feature was first announced back in October when the beta version was introduced. The tech giant announced on Wednesday that nearly all permissions can now be customized.
Granting users excessive privileges to services, applications and data can introduce serious security risks, which is why it’s crucial for administrators to ensure that users only have the permissions needed to perform their jobs.
Customers of Google’s cloud platform now have full control over more than 1,200 public permissions, providing them fine-grained access control for enforcing the principle of least privilege. The principle of least privilege is a concept that promotes minimal user profile privileges based on job necessities.
In the case of GCP, administrators can rely on the IAM service to assign a predefined role to users - for example, allow them to view or modify data stored in the cloud. However, these predefined roles are sometimes not enough for implementing the principle of least privilege.
Custom roles, on the other hand, can be used to remix permissions across all services to ensure that users do not receive privileges other than ones required to do their job.
“Consider a tool that needs access to multiple GCP services to inventory Cloud Storage buckets, BigQuery tables and Cloud Spanner databases. Enumerating data doesn’t require privileges to decrypt that data. While predefined roles to view an entire project may grant .query,.decrypt and .get as a set, custom roles make it possible to grant .get permission on its own,” Google’s Rohit Khare and Pradeep Madhavarapu explained in a blog post.
Except for certain permissions that are only supported in predefined roles, all permissions are now customizable. A list of all supported permissions has been made available and users can keep track of changes via a central change log.
In the future, Google wants to further enhance its IAM service, including by using research from the company’s Forseti open source initiative to help explain why a specific permission has been granted or denied.
Siemens fixed three flaws in plant management product Siemens TeleControl Basic system
1.2.2018 securityaffairs Vulnerebility
Siemens has patched three security vulnerabilities in its Plant Management Product, the Siemens TeleControl Basic system.
The system is used in water treatment facilities, traffic monitoring systems, and energy distribution plants. The TeleControl Basic control center runs the TeleControl Server Basic software. The Siemens TeleControl Basic system allows organizations to monitor and control processes in industrial environment and operation of municipal facilities.

The TeleControl Server Basic system is affected by three vulnerabilities that could be exploited by an attacker to conduct different types of attacks, including privilege escalation, bypass authentication, and denial-of-service (DoS) attacks.
“The latest update for TeleControl Server Basic resolves three vulnerabilities. One of these vulnerabilities could allow an authenticated attacker with network access to escalate his privileges and perform administrative actions.” reads the security advisory published by Siemens.
“Siemens recommends updating to the new version.”
This is the first time that Siemens publishes a security advisory released by Siemens and ICS-CERT for a vulnerability that affects TeleControl products
The flaws affect TeleControl Server Basic versions prior to V3.1, the most severe one is tracked as CVE-2018-4836 and rated high severity.
Below the list of the vulnerabilities and related descriptions:
Vulnerability (CVE-2018-4835) [CVSS v3.0 Base Score 5.3] – It could be exploited by an attacker with network access to the TeleControl Server Basic’s port 8000/tcp to bypass the authentication mechanism and access limited information.
Vulnerability (CVE-2018-4836) [CVSS v3.0 Base Score 8.8] – It could be exploited by an authenticated attacker with a low-privileged account to the TeleControl Server Basic’s port 8000/tcp to escalate privileges and perform administrative operations.
Vulnerability (CVE-2018-4837) [CVSS v3.0 Base Score 5.3] – It could be exploited by an attacker with access to the TeleControl Server Basic’s webserver (port 80/tcp or 443/tcp) to cause a DoS condition on the web server.
Siemens also provided some workarounds to mitigate the risk of attacks, including the blocking of TCP port 8000 through the Windows firewall for both CVE-2018-4835, CVE-2018-4836 and the blocking of the ports 80 and 443 for the CVE-2018-4837.
The US ICS-CERT also published a detailed advisory for the vulnerabilities in the Siemens TeleControl Basic.
Cryptocurrency Mining Malware Infected Over Half-Million PCs Using NSA Exploit
1.2.2018 thehackernews Virus

2017 was the year of high profile data breaches and ransomware attacks, but from the beginning of this year, we are noticing a faster-paced shift in the cyber threat landscape, as cryptocurrency-related malware is becoming a popular and profitable choice of cyber criminals.
Several cybersecurity firms are reporting of new cryptocurrency mining viruses that are being spread using EternalBlue—the same NSA exploit that was leaked by the hacking group Shadow Brokers and responsible for the devastating widespread ransomware threat WannaCry.
Researchers from Proofpoint discovered a massive global botnet dubbed "Smominru," a.k.a Ismo, that is using EternalBlue SMB exploit (CVE-2017-0144) to infect Windows computers to secretly mine Monero cryptocurrency, worth millions of dollars, for its master.
Active since at least May 2017, Smominru botnet has already infected more than 526,000 Windows computers, most of which are believed to be servers running unpatched versions of Windows, according to the researchers.
"Based on the hash power associated with the Monero payment address for this operation, it appeared that this botnet was likely twice the size of Adylkuzz," the researchers said.
The botnet operators have already mined approximately 8,900 Monero, valued at up to $3.6 million, at the rate of roughly 24 Monero per day ($8,500) by stealing computing resources of millions of systems.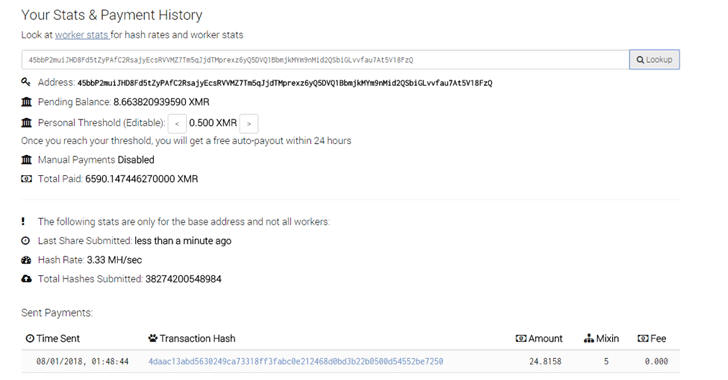
The highest number of Smominru infection has been observed in Russia, India, and Taiwan, the researchers said.
The command and control infrastructure of Smominru botnet is hosted on DDoS protection service SharkTech, which was notified of the abuse but the firm reportedly ignored the abuse notifications.
According to the Proofpoint researchers, cybercriminals are using at least 25 machines to scan the internet to find vulnerable Windows computers and also using leaked NSA's RDP protocol exploit, EsteemAudit (CVE-2017-0176), for infection.
"As Bitcoin has become prohibitively resource-intensive to mine outside of dedicated mining farms, interest in Monero has increased dramatically. While Monero can no longer be mined effectively on desktop computers, a distributed botnet like that described here can prove quite lucrative for its operators," the researchers concluded.
"The operators of this botnet are persistent, use all available exploits to expand their botnet, and have found multiple ways to recover after sinkhole operations. Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes."
Another security firm CrowdStrike recently published a blog post, reporting another widespread cryptocurrency fileless malware, dubbed WannaMine, using EternalBlue exploit to infect computers to mine Monero cryptocurrency.
Since it does not download any application to an infected computer, WannaMine infections are harder to detect by antivirus programs. CrowdStrike researchers observed the malware has rendered "some companies unable to operate for days and weeks at a time."
Besides infecting systems, cybercriminals are also widely adopting cryptojacking attacks, wherein browser-based JavaScript miners utilise website visitors' CPUs power to mine cryptocurrencies for monetisation.
Since recently observed cryptocurrency mining malware attacks have been found leveraging EternalBlue, which had already been patched by Microsoft last year, users are advised to keep their systems and software updated to avoid being a victim of such threats.
Siemens Patches Flaws in Plant Management Product
1.2.2018 securityweek Vulnerebility
Siemens has informed customers that a component of its TeleControl Basic product is affected by several vulnerabilities that can be exploited by an attacker to escalate privileges, bypass authentication, and launch denial-of-service (DoS) attacks.
Siemens’ TeleControl Basic system allows organizations to monitor and control plant processes. The solution can also be used to optimize the operation of municipal facilities, including water treatment, traffic monitoring, and energy distribution. TeleControl Server Basic is the software used for the TeleControl Basic control center.
According to advisories published by Siemens and ICS-CERT, the TeleControl Server Basic system is affected by a total of three vulnerabilities. The most serious of them, tracked as CVE-2018-4836 and rated high severity, allows an attacker with a low privileged account and access to TCP port 8000 to escalate privileges and perform administrative tasks.
Another flaw, CVE-2018-4835, allows an attacker with network access to port 8000 to bypass the system’s authentication mechanism and obtain limited information.
The last security hole, CVE-2018-4837, can be exploited by an attacker with access to the TeleControl web server on TCP ports 80 or 443 to cause the web server to enter a DoS condition. However, Siemens pointed out that the DoS condition does not affect other functionality.
CVE-2018-4835 and CVE-2018-4837 have been classified as medium severity with a CVSS score of 5.3.
Siemens has patched the vulnerabilities with the release of TeleControl Server Basic 3.1. In addition, the company has identified some workarounds and mitigations that can be used to reduce the risk of attacks.
These include blocking TCP port 8000 using the Windows firewall to mitigate CVE-2018-4835 and CVE-2018-4836, and blocking ports 80 and 443 to prevent attacks involving CVE-2018-4837.
While this is the first advisory released by Siemens and ICS-CERT for a vulnerability specific to TeleControl products, a privilege escalation flaw disclosed in November 2016 had been found to impact TeleControl Server Basic – among many other industrial solutions from Siemens. That security hole was addressed in TeleControl Server Basic with the release of version 3.0.
Mining Smominru botnet used NSA exploit to infect more than 526,000 systems
1.2.2018 securityaffairs BigBrothers
Researchers from Proofpoint discovered a huge botnet dubbed ‘Smominru’ that is using the EternalBlue exploit to infect Windows computers and recruit them in Monero cryptocurrency mining activities.
The number of cyber attacks against the cryptocurrency sector continues, vxers are focusing their efforts on the development of cryptocurrency/miner malware.
Recently security experts observed cryptocurrency miners leveraging the NSA EternalBlue SMB exploit (CVE-2017-0144) as spreading mechanism.
On August 2017, a new fileless miner dubbed CoinMiner appeared in the wild, it uses NSA EternalBlue exploit and WMI tool to spread.
Now researchers Researchers from Proofpoint discovered a huge botnet dubbed ‘Smominru’ (aka Ismo) that is using the EternalBlue exploit (CVE-2017-0144) to infect Windows computers and recruit them in Monero cryptocurrency mining activities.
” Because obtaining these cryptocurrencies through legitimate mining mechanisms is quite resource-intensive, cybercriminals are stealing them, demanding ransomware payments in them, and harnessing other computers to mine them for free. Recently, Proofpoint researchers have been tracking the massive Smominru botnet, the combined computing power of which had earned millions of dollars for its operators.” states the analysis published by Proofpoint
With the help of Abuse.CH and the ShadowServer Foundation, Proofpoint conducted a sinkholing operation that allowed to profile the botnet.
The command and control infrastructure of the Smominru botnet is hosted on DDoS protection service SharkTech, Proofpoint promptly notified the abuse to the service provider without receiving any response.
According to the researchers, the Smominru botnet has been active at least since May 2017 and has already infected more than 526,000 Windows computers.
Most of the infected systems are servers distributed worldwide, most of them in Russia, India, and Taiwan. It is a profitable business, the operators had already mined approximately 8,900 Monero ($2,346,271 at the current rate).
“Based on the hash power associated with the Monero payment address for this operation, it appeared that this botnet was likely twice the size of Adylkuzz,” the researchers said. “The operators had already mined approximately 8,900 Monero (valued this week between $2.8M and $3.6M). Each day, the botnet mined roughly 24 Monero, worth an average of $8,500 this week (Figure 2).”

The researchers at Proofpoint discovered that crooks are using at least 25 hosts to scan the Internet for EternalBlue vulnerable Windows computers and also leveraging the NSA EsteemAudit (CVE-2017-0176) for compromising the target machines.
The machines all appear to sit behind the network autonomous system AS63199, further technical details and the IoCs are included in the analysis published by Proofpoint.
“Because most of the nodes in this botnet appear to be Windows servers, the performance impact on potentially critical business infrastructure may be high, as can the cost of increased energy usage by servers running much closer to capacity. The operators of this botnet are persistent, use all available exploits to expand their botnet, and have found multiple ways to recover after sinkhole operations.” concluded the Proofpoint.
“Given the significant profits available to the botnet operators and the resilience of the botnet and its infrastructure, we expect these activities to continue, along with their potential impacts on infected nodes. We also expect botnets like that described here to become more common and to continue growing in size.”
Every little bitcoin helps
1.2.2018 Kaspersky Spam
It often happens that inventions and technologies that start out good end up turning into dangerous tools in the hands of criminals. Blockchain is no exception to this rule, especially in its most common cryptocurrency incarnation. Cryptocurrencies crop up in all kinds of spam: from traditional advertising (courses about investment and trade) to more fraudulent and malicious varieties. Quite often, cryptocurrencies are used by attackers as originally intended — as a means of payment (albeit from victims). We found and delved into several spam mailings in which cybercrooks exploited user paranoia about information threats and took bitcoins as payment for peace of mind. The attacks targeted employees of small companies, but such emails could be sent to any user’s personal mail.
In the first email, the attacker claimed to have installed malware on a porn site visited by the victim, and to be in possession of several videos recorded from both the device screen and cameras; not only that, a keylogger had supposedly provided access to the user’s IM, email, and social media contacts. To get the attacker off their back, the victim was asked to transfer the equivalent of $320 to the bitcoin wallet specified in the email. It was also mentioned that a built-in tracking pixel would inform the attacker that the email had been seen. And if the recipient wanted proof of that, they should reply to the message, whereupon the compromising info would be sent out to five of their contacts. As a postscript, the scammer warned against going to the police: he allegedly lived in Belarus, so the investigation would drag on for years.
The next email was wordy but imaginative, written by a hacker by the name of Andrey. The attacker informed the recipient that he had studied the latter’s company, together with its employees and their relatives, found weaknesses, and was planning to ruin it. The author listed no fewer than seven ways to achieve this goal, from simply writing negative reviews on various websites to creating fake company reports in his garage(!) and sending them to government departments. However, the hacker’s preferred outcome was for the company to see sense and transfer 3 bitcoins to his wallet. Like the previous email, it specifically mentioned not going to the cops, since “Andrey” lived in Ukraine.
Another email was the work of not one hacker, but an entire chain gang. The attackers allegedly had hacked the company’s server and got hold of information about its clients, bank accounts, tax payments, etc. Now they were threatening to damage the company’s reputation by publishing this information online. It was also stated that at some unspecified moment they would launch an attack on the company’s servers and computers, encrypting all data. To call off the attack, the blackmailers demanded 0.5 bitcoin. If the cryptopayment was not made before the start of the attack, the amount would rise to 2 bitcoins.
Sadly and (perhaps) surprisingly, some people still fall for such concoctions. The targets of these mailings are usually small companies that lack the resources for decent anti-spam protection and basic information security training for staff. So let us reiterate: be vigilant, stay calm, and take anonymous threats of this kind with a pinch of salt.
Cybercriminals target early IRS 2018 refunds now
1.2.2018 Kaspersky CyberCrime
Where is my tax refund? Wait! What are that fraud charges on my credit card??
On Monday, Jan 29th, IRS officially opened its 2018 season. Some taxpayers already filed their taxes and cybercriminals know it too. So, right after two days of the official 2018 season opening, we got phishing messages with a fake refund status Websites:
The link in the email leads to a hacked Brazilian restaurant, redirecting to Website with Australian domain zone.
So, the whole scheme is to steal credit card information of the taxpayers expecting a tax refund from IRS. Both URLs are blocked by Kaspersky Anti-Phishing now.
The mentioned Website was hacked and includes an old Webshell uploaded back to 2016.
Should we expect more campaigns like this? Definitely yes. Stay watchful and don’t lose your refunds!