(Unpatched) Adobe Flash Player Zero-Day Exploit Spotted in the Wild
2.2.2018 thehackernews Vulnerebility
Another reason to uninstall Adobe Flash Player—a new zero-day Flash Player exploit has reportedly been spotted in the wild by North Korean hackers.
South Korea's Computer Emergency Response Team (KR-CERT) issued an alert Wednesday for a new Flash Player zero-day vulnerability that's being actively exploited in the wild by North Korean hackers to target Windows users in South Korea.
Simon Choi of South Korea-based cybersecurity firm Hauri first reported the campaign on Twitter, saying the North Korean hackers have been using the Flash zero-day against South Koreans since mid-November 2017.
Although Choi did not share any malware sample or details about the vulnerability, the researcher said the attacks using the new Flash zero-day is aimed at South Korean individuals who focus on researching North Korea.
Adobe also released an advisory on Wednesday, which said the zero-day is exploiting a critical 'use-after-free' vulnerability (CVE-2018-4878) in its Flash media software that leads to remote code execution.
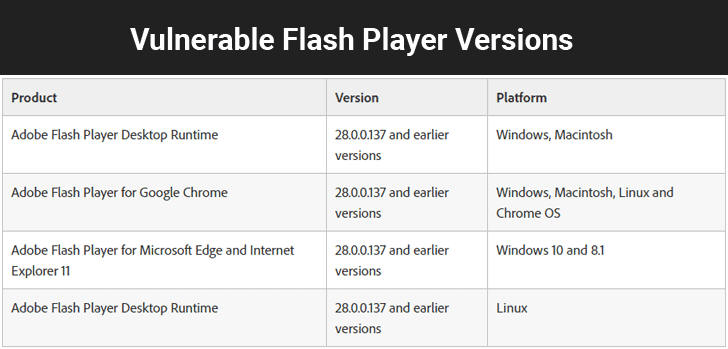
The critical vulnerability affects Adobe Flash Player version 28.0.0.137 and earlier versions for:
Desktop Runtime (Win/Mac/Linux)
Google Chrome (Win/Mac/Linux/Chrome OS)
Microsoft Edge and Internet Explorer 11 (Win 10 & 8.1)
"Adobe is aware of a report that an exploit for CVE-2018-4878 exists in the wild, and is being used in limited, targeted attacks against Windows users," the advisory said. "These attacks leverage Office documents with embedded malicious Flash content distributed via email. Adobe will address this vulnerability in a release planned for the week of February 5."
To exploit the vulnerability, all an attacker need to do is trick victims into opening Microsoft Office documents, web pages, or spam messages that contain a maliciously crafted Adobe Flash file.
The vulnerability can be leveraged by hackers to take control of an affected computer.
Choi also posted a screenshot to show that the Flash Player zero-day exploit has been delivered via malicious Microsoft Excel files.
Adobe said in its advisory that the company has planned to address this vulnerability in a "release planned for the week of February 5," through KR-CERT advises users to disable or completely remove the buggy software.
Meltdown/Specter-based Malware Coming Soon to Devices Near You, Are You Ready?
2.2.2018 thehackernews Safety

It has been few weeks since the details of the Spectre, and Meltdown processor vulnerabilities came out in public and researchers have discovered more than 130 malware samples trying to exploit these chip flaws.
Spectre and Meltdown are security vulnerabilities disclosed by security researchers earlier this month in many processors from Intel, ARM and AMD used in modern PCs, servers and smartphones, among other devices.
These CPU vulnerabilities could enable attackers to bypass memory isolation mechanisms and access everything, including memory allocated for the kernel containing sensitive data like passwords, encryption keys and other private information.
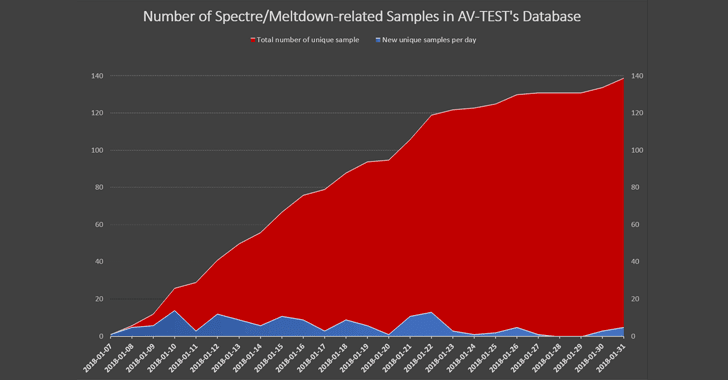
Researchers from independent antivirus testing firm AV-TEST detected at least 139 malware samples, as of today, which are related to these CPU vulnerabilities, as shown in the growth graph.
You can find SHA256 hashes for all malware samples here.
Meanwhile, cybersecurity firm Fortinet also tracked and analyzed many malware samples 'trying to exploit' recently disclosed CPU vulnerabilities, most of which includes re-compiled or extended version of the JavaScript-based proof-of-concept (PoC) exploit released last month.
"The rate at which the cybercriminal community is targeting known vulnerabilities is clearly accelerating, with the WannaCry and NotPetya exploits serving as perfect examples of the need to patch vulnerable systems as soon as possible," Fortinet said.
"Which is why our concerns were raised when we recently learned about some of the largest vulnerabilities ever reported—ones that affect virtually every processor developed since 1995 by chip manufacturers Intel, AMD, and ARM."
Another news makes this situation, even more, worse—Intel halted all its CPU firmware patches for the Meltdown and Spectre flaws last week after it caused issues like spontaneous reboots and other 'unpredictable' system behaviour on affected PCs.
So, until Intel and other vendors do not come up with stable security patches for the Meltdown and Spectre attacks that don’t cause systems to break, users are recommended to keep their operating system, web browsers, antivirus and other software up-to-date.
Increasing Number of Industrial Systems Accessible From Web: Study
2.2.2018 securityweek ICS
The number of industrial control systems (ICS) accessible from the Internet has increased significantly in the past year, reaching more than 175,000 components, according to a new report from Positive Technologies.
Using the Shodan, Censys and Google search engines, researchers identified 175,632 ICS components accessible from the Web. In comparison, similar searches conducted in the previous year uncovered just over 162,000 systems.
Of all the systems identified in 2017, more than 66,000 were accessible via HTTP, followed by the Fox building automation protocol associated with Honeywell’s Niagara framework (39,000), Ethernet/IP (25,000), BACnet (13,000), and the Lantronix discovery protocol (10,000).
The highest percentage of exposed devices, representing 42% of the total, was spotted in the United States. The number of Internet-accessible ICS components in the U.S. increased by 10% compared to 2016, from roughly 50,000 to 64,000. The U.S. is followed at a distance by Germany (13,000 accessible systems), France (7,000), and Canada (7,000).
Many of the industrial systems connected to the Web come from Honeywell (26,000), Lantronix (12,000), SMA (9,000), Beck IPC (9,000), Siemens (6,000) and Rockwell Automation (5,000).
The distribution of Internet-exposed components by type has remained largely the same compared to 2016. 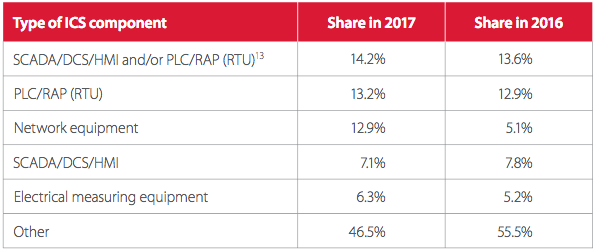
John Matherly, CEO of the search engine Shodan, has confirmed for SecurityWeek that there has been an increase of roughly 10% year-over-year in terms of ICS exposure on the Internet.
“The increase is mostly in building automation protocols and despite the news coverage we haven't seen any decrease in devices,” Matherly said.
According to Positive Technologies, a total of nearly 200 new vulnerabilities were disclosed in 2017, compared to 115 in 2016. Worryingly, 61% of the flaws whose existence was made public last year were rated critical and high severity.
The most common types of vulnerabilities were remote code execution (24%), information disclosure (17%), and buffer overflows (12%). “Most vulnerabilities detected in 2017 can be exploited remotely without needing to obtain any privileges in advance,” Positive Technologies said in its report.
A report published in October by CyberX revealed that one-third of industrial and critical infrastructure systems had been connected to the Internet, based on data obtained by the industrial security firm by passively monitoring traffic from hundreds of operational technology (OT) networks.
AutoSploit: Automated Hacking Tool Set to Wreak Havoc or a Tempest in a Teapot?
2.2.2018 securityweek Virus
AutoSploit Automatically Finds Vulnerable Targets via Shodan and Uses Metasploit Exploits to Compromise Hosts
AutoSploit is a tool designed to automate the use of Metasploit exploits. It was announced on Twitter on Wednesday.
"I just released AutoSploit on #Github. #Python based mass #exploit #tool. Gathers targets via #Shodan and automatically invokes selected #Metasploit modules to facilitate #RCE," announced Twitter user VectorSEC, Wednesday. Just to be clear, this tool automatically finds vulnerable targets and uses Metasploit exploits to provide remote code execution for the user.
No great skill is necessary: all that is required is AutoSploit (available from GitHub), Python Blessings, Shodan, and Metasploit. Shodan locates the targets, Metasploit provides the exploits, and AutoSploit actions them. Since new vulnerability exploits are added to Metasploit faster than many companies can apply vulnerability patches, the immediate concern is whether this new tool will further commoditize cybercrime by facilitating a new army of unskilled, wannabee, skiddie, hackers able to hack computers automatically.
Just how dangerous is this? Opinions are varied. "[AutoSploit] makes being a script kiddie infinitely easier," comments Chris Morales, head of security analytics at Vectra Networks. "It is combining a whole set of automated tools for identifying exposed hosts and then executing exploits. Where I think this will have the most dramatic effect, and what scares me most, is with IoT. I’m predicting a rash of new IoT DOS, cryptocurrency mining, and general debauchery."
But he notes that it will simply lead to a compromised host -- something security teams have to handle every day. There is still time for incident response. "We cannot rely on prevention and need to be vigilant in finding attackers once they infect systems and before they can cause real damage.”
Chris Roberts, chief security architect at Acalvio, agrees that it will attract the wannabees. “Good to know we’ve weaponized for the masses. Everyone can now be a script kiddie simply by plugging, playing and attacking." But he points out that attack tools with 'very nice interfaces' are not new, and only exist because the root problem is the bad products, code, systems and infrastructures used by everyone.
"The kids are not more dangerous," he says. "They already were dangerous. We’ve simply given them a newer, simpler, shinier way to exploit everything that’s broken. Maybe we should fix the ROOT problem.”
"The basic functionalities [of AutoSploit] were already accessible," says ESET senior research fellow, David Harley, "but AutoSploit lowers the level of knowledge and competence necessary to take advantage of them. So, I guess there could be more skiddies snapping at the heels of companies and individuals whose patching isn’t up to scratch."
He warns that companies cannot rely on prevention technologies to neutralize AutoSploit. "Security companies watch Metasploit with the intention of remediating where they can, so some (at least) of the modules used will be less effective on well-protected systems. Sadly, not every exploit can be 100% defended against by third-party security software. Not every system out there is well-protected. And it sounds as if AutoSploit will make it easier to find and probe systems that are less likely to be properly patched or defended with security software. Like the Internet-of-unnecessarily-interconnected-things…"

There are others who simply dismiss AutoSploit. Jerry Gamblin, lead security analyst at Carfax, tweeted, "While everyone is freaking out I hacked together antiautosploit to stop autosploit from sploiting you (This just blocks Shodan from scanning you)."
The general consensus from the security industry seems to be that AutoSploit will attract the kiddies but won't change the current threat landscape -- beyond perhaps making existing good practice (patching, incident response) more important and urgent.
"This doesn't really change anything from way things are already," says F-Secure principal researcher Jarno Niemela. "My 11-year-old son learned Metasploit when he was 10 years old, and there is a ton of tradecraft videos in YouTube for anyone who is interested... This tool simply makes something that was already very easy just a bit easier."
But he also has a word of warning for wannabees attracted by AutoSploit. "The fact that something is really easy, does not make unauthorized computer access any less a crime. And tools like this leave a forensic footprint that is miles wide. Yes, you can compromise poorly protected systems very easily with this tool, but you can also end up in a lot of trouble."
Legacy Malware and Legacy Systems Are Not a Legacy Problem
2.2.2018 securityweek Virus
Companies must be wary of chasing shiny new threats with shiny new defenses, while leaving legacy systems vulnerable to legacy malware.
Trend Micro calls the legacy threat 'Throwhack'; after the more benign 'Throwback Thursday' social media trend; but, says principal security strategist Bharat Mistry in a blog published today, "there’s nothing entertaining about this list of legacy security challenges."
Mistry points to Conficker (dating back to 2008). "Throughout 2017 we saw monthly detections of around 20,000; meaning it’s still highly active." In conversation with SecurityWeek, he agreed that the majority of detections were in the Far East with few appearing in the U.S. or Europe; but warned that Far East breaches could get into the supply chain of Western organizations.
Heartbleed is another old threat that hasn't gone away. "Despite surfacing and being patched in 2014, nearly 200,000 servers and devices were reported as exposed last year."
The problem goes deeper than just old malware -- it is exacerbated by the continued use of old and unsupported systems. "Spiceworks has claimed that 68% of US, Canadian and US firms still run Office 2007, while it has also been reported that around 20% of US and UK healthcare organizations still run Windows XP. It doesn’t take much to understand the dangers of running unsupported systems," he writes.
One of the problems, he told SecurityWeek, is that new security products are not always old problem aware. "Machine learning systems," he said, "often 'learn' to detect malware based on current threats. They simply aren't taught to detect old behaviors; and can miss them."
To be fair, he isn't advocating abandoning new machine learning detection products or methods, only pointing out that on their own they aren't enough. "Wherever possible," he said, "organizations should employ traditional anti-malware products as well as new machine learning products." He added that the challenge of the smaller processing overhead from ML systems has spurred traditional anti-malware into designing and implementing new approaches that reduce their own overhead.
Nevertheless, he stresses that one of the best solutions to legacy malware is to update or upgrade legacy systems: newer versions of old operating systems are no longer susceptible to old vulnerabilities.
"If updating your OS is not possible, for whatever reason, use vulnerability shielding/virtual patching on the endpoint or intrusion prevention at the network level. It’s ideal for mitigating the impact of older malware like Conficker which exploits vulnerabilities. It protects legacy systems by providing convenient and automatic updates, allowing organizations to maintain protection while minimizing their patch management costs."





