Windows 10 Ransomware Protection Easily Bypassed, Researcher Says
6.2.2018 securityweek Ransomware
It’s rather trivial to bypass the anti-ransomware feature that Microsoft introduced in its Windows 10 Fall Creators Update, a security researcher claims.
Dubbed Controlled folder access, the anti-ransomware feature was announced as part of Windows Defender Exploit Guard, a new set of host intrusion prevention capabilities in Microsoft’s latest platform iteration.
When announcing the feature, Microsoft described it as a layer of real-time protection that would allow users to prevent ransomware from accessing their data by defining what programs have access to certain folders. Thus, malware and other unauthorized apps would not be able to touch the files in those directories.
According to Yago Jesus, however, this added protection can be easily bypassed by using an authorized application such as Office to access the data.
This would be possible because Office executables are by default whitelisted and allowed to make changes to files placed in protected folders, without restrictions, even when a malicious actor uses OLE/COM objects to control Office executables programmatically.
“So, a ransomware developer could adapt their software to use OLE objects to change / delete / encrypt files invisibly for the files owner,” the researcher explains.
Thus, an attacker capable of creating code leveraging OLE Word Object for execution would be able to bypass the anti-ransomware feature in Windows 10. Windows Defender would do nothing to stop the code from execution, because the entire operation would rely on the native encryption feature in Microsoft Office.
This technique, the researcher argues, renders Windows Defender Exploit Guard’s Controlled folder access functionality useless in an environment where both Office and Windows are employed. In addition to documents, the method can also be used to target PDFs, images, and other file types that Office can edit.
“While this capability is designed to protect against ransomware, it’s not surprising that it’s unable to handle all ransomware scenarios. The use of Microsoft Office files, which is described in the recent documented bypass, has been an effective way for attackers to get around AV tools,” Lenny Zeltser, Vice President of Products at Israel-based Minerva Labs, told SecurityWeek via email.
Another exploitation scenario, Jesus reveals, would involve the use of Selection.Copy / Selection.Paste methods to copy the content of a protected file to another file located outside the protected folder, delete the content of the original file or replace it with a ransom note, and then encrypt the new file normally.
The researcher says he informed Microsoft on his findings and that the company confirmed that they would resolve the issue “through an improvement to the Controlled Folder Access functionality.” However, it appears that the tech giant doesn’t see the bug as a security vulnerability, “because Defender Exploit Guard isn't meant to be a security boundary.”
According to Joseph Carson, chief security scientist at Washington D.C. based Thycotic, such a response from Microsoft is unacceptable.
"Frankly, this is a classic example of being misleading,” he told SecurityWeek via email. “It's like a security guard at the door of a building checking to ensure that anyone entering has the correct access, when you've left the backdoor wide open. It is a false sense of protection as you are purely relying on cybercriminals being honest.”
“When you call a product ‘Windows Defender’, or use terms such as ‘Defender Exploit Guard’, and when notified by a security researcher on a security bypass, the response of course is legally correct stating ‘we aren't classifying this as a security vulnerability because Defender Exploit Guard isn't meant to be a security boundary’,” Carson said.
He also pointed out that this bypass technique might have been already exploited in attacks against businesses and that companies should not simply rely on Windows Defender as the only security control, especially if Microsoft themselves say it isn’t even a security boundary.
“Immediately change the name to what it is rather than misleading consumers into a false sense of security and protection,” Carson concluded.
Meni Farjon, Co-Founder and CTO at Israel-based SoleBIT Labs, also believes that attackers are bound to leverage Office capabilities to bypass Microsoft’s ransomware protection. The main vulnerability, he told SecurityWeek, is that there’s a whitelist of programs such as Office that are allowed to make changes to protected folders without restrictions.
“Today we see an increase in macro-based malware, leveraging Office active-content capabilities to deliver ransomware. Generally speaking, I believe Windows Defender’s ransomware protection should not be considered a fully functional anti-ransomware feature, but more like a data protection feature. I would advise users to augment such defenses with vulnerability and active content detection solutions to combat ransomware on the network level, before it even reaches the endpoint,” Farjon concluded.
Microsoft hasn’t responded yet to SecurityWeek’s request for a comment on the matter.
One Computer Can Knock Almost Any WordPress Site Offline
6.2.2018 securityweek Vulnerebility
As if there aren't enough ways to attack a WordPress site, an Israeli researcher has published details of how almost anyone can launch a denial of service (DoS) attack against almost any WordPress with just one computer. That, he suggests, is almost 30% of all websites on the internet.
The attack uses the vulnerability associated with CVE-2018-6389. The CVE database, at the time of writing, has no details, marking it only as 'reserved' for future use. Details, however, can be found in a Barak Tawily blog post published Monday. It is an abuse of the WordPress load-scripts.php function, which exists to allow administrators/web designers to improve website performance by combining multiple JavaScript files into a single request at the server end.
Tawily's DoS methodology makes use of two elements. Firstly, use of load-scripts.php requires no user authentication -- it can be invoked by anyone. The second element is that load-scripts.php receives a parameter called 'load[]', which is an array. The purpose of the array is to be able to specify which scripts should be combined and loaded to improve performance. Since it is also used to improve performance of the wp-login.php page, it can be invoked before any user authorization is required.
Within WordPress there is a wp_scripts list containing defined paths for all the 181 script files. The intention is that the administrator or web designer can include the path for specific scripts within the load[] parameter, and improve performance according to the supplied value from the user. The wp_scripts list is hard-coded in the script-loader.php file.
"I wondered," writes Tawily "what would happen if I sent the server a request to supply me every JS module that it stored? A single request would cause the server to perform 181 I/O actions and provide the file contents in the response. I did so..."
The result took 2.2 seconds and was almost 4 Mb of data -- making the server work hard to comply.
Tawily's next step was to use a python script he had written himself to send repeated identical requests to the server. And this time it worked. "As long as I kept sending those requests to the server, it was too busy to handle any other request, and I had effectively (and easily) caused DoS."
He used HackerOne to report the issue to WordPress, even though DoS is outside the scope of WordPress bounties. Nevertheless, it is a vulnerability that needed to be reported. The response, however, was muted: "This kind of thing should really be mitigated at the server or network level rather than the application level, which is outside of WordPress's control," said WordPress.
That's debatable on two counts. First, many WordPress sites are blogs and micro-business sites run cheaply on shared servers with the respective service providers, and with little technical skill among the owners. There is simply no way that such sites can be mitigated at the server or network level.
Second, Tawily goes on to show that mitigation isn't really that difficult if you know what to do (which many WordPress users do not). He "forked WordPress project and patched it so no one but authenticated users can access the load-*.php files, without actually harming the wp-login.php file functionality." He goes further to provide a bash script that modifies the relevant files to mitigate the vulnerability.
SSL Increasingly Abused by Malware, Phishing: Report
6.2.2018 securityweek Phishing
There has been a significant increase in the number of phishing and malware attacks abusing SSL and TLS technology, according to Zscaler’s SSL Threat Report for the second half of 2017.
In the first half of 2017, Zscaler’s products blocked roughly 600,000 threats hidden in encrypted traffic every day, but that number grew to 800,000 in the second half of the year, which represents an increase of 30 percent.
Malicious actors have used SSL-encrypted channels for the initial delivery of malvertising, phishing and compromised websites, to distribute malware payloads and exploits, and for communications between the infected host and command and control (C&C) servers.
In the case of phishing attempts, Zscaler saw a 400 percent increase in the first half of 2017 compared to 2016. Overall, in 2017, phishing activity jumped by nearly 300 percent.
Phishing pages served over HTTPS are either hosted on a compromised website that has an SSL certificate, or they are hosted on malicious sites that imitate well-known brands and rely on certificates obtained by the cybercriminals themselves. Services such as Let’s Encrypt make it easier for malicious actors to obtain free certificates that they can use in their operations.

In the case of malware attacks, Zscaler said SSL/TLS channels were used 60 percent of the time to deliver banking Trojans throughout 2017, and ransomware was spotted in one-quarter of attempts. Many attackers obtained an encrypted distribution channel for their malware by hosting it on legitimate services such as Box, Dropbox, Google and AWS.
An analysis of roughly 6,700 SSL transactions blocked by Zscaler showed that a majority of abused certificates belonged to legitimate sites that had been compromised.
The security firm also found that the types of certificates that are most abused by cybercriminals are domain validated (DV) certificates, which have a validity of three months and are obtained more easily. DV certificates, particularly ones obtained for free, were spotted in 75 percent of cases.
More than half of certificates were valid for less than one year, and roughly one-third of those had a validity period of three months or less.
Adobe Patches Flash Zero-Day Exploited by North Korean Hackers
6.2.2018 securityweek Vulnerebility
Adobe updated Flash Player on Tuesday to address a zero-day vulnerability exploited by what experts believe to be a North Korean hacker group in attacks aimed at individuals in South Korea.
The existence of the vulnerability, tracked as CVE-2018-4878, came to light on January 31 when South Korea’s Internet & Security Agency (KISA) issued an alert. Cybersecurity experts based in the country said the flaw had been used by North Korean threat actors against South Koreans who focus on North Korea research.
Adobe has promised to release a patch sometime this week and it has kept its promise. Flash Player version 28.0.0.161 should fix the vulnerability, which the company has described as a use-after-free bug that allows remote code execution.
The security hole, which affects Flash Player 28.0.0.137 and earlier, was brought to the company’s attention by South Korea's KrCERT/CC.
The latest Flash release also patches CVE-2018-4877, which is also a use-after-free vulnerability that allows remote code execution. The flaw was reported to Adobe by bo13oy of Qihoo 360 Vulcan Team via Trend Micro’s Zero Day Initiative (ZDI). Adobe does not appear to be aware of any attacks exploiting CVE-2018-4877.
FireEye has analyzed the attacks involving CVE-2018-4878 and believes the zero-day has been used by a group it tracks as TEMP.Reaper. The security firm determined that these hackers are likely based in North Korea based on IP addresses used to access command and control (C&C) servers.
“The majority of their targeting has been South Korea focused, targeting the government, military, and defense industrial base as well as other industry,” FireEye said. “They have also taken an interest in predictable North Korean interests such as unification efforts and defectors.”
The attacks observed by FireEye involved malicious Office documents and spreadsheets designed to exploit the Flash Player zero-day in an effort to deliver a piece of malware tracked by the company as DOGCALL.
Cisco Talos has also analyzed the campaign and attributed it to an actor it tracks as Group 123. While Cisco has not explicitly blamed North Korea for attacks launched by Group 123, the company has detailed several campaigns aimed at South Korea that often use North Korea-related topics as a lure when delivering malware.
Researchers pointed out that the addition of a zero-day exploit to its arsenal shows that the group has become highly motivated and sophisticated.
Crime ring linked to Luminosity RAT dismantled by an international law enforcement operation
6.2.2018 securityaffairs Virus
The Europol’s European Cybercrime Centre along with the UK NSA disclosed the details of an international law enforcement operation that dismantled a crime ring linked to Luminosity RAT.
The Europol’s European Cybercrime Centre (EC3) along with the UK National Crime Agency (NCA) disclosed the details of an international law enforcement operation that targeted the criminal ecosystem around the Luminosity RAT (aka LuminosityLink).
According to the EC3, the joint operation was conducted in September 2017, it involved more than a dozen law enforcement agencies from Europe, the US, and Australia.
The Luminosity RAT was first spotted in 2015 but it became very popular in 2016.
The malware was offered for sale in the criminal underground for as little as $40, it allows attackers to take complete control over the infected system.

In September 2016, the UK law enforcement arrested a man that was linked to the threat. The arrest triggered a new investigation that resulted in several arrests, search warrants, and cease and desist notifications across Europe, America, and Australia.
Law enforcement agencies target both sellers and users of Luminosity Trojan. According to the NCA, a small crime ring in the UK distributed Luminosity RAT to more than 8,600 buyers across 78 countries.
“The Luminosity Link RAT (a Remote Access Trojan) enabled hackers to connect to a victim’s machine undetected. They could then disable anti-virus and anti-malware software, carry out commands such as monitoring and recording keystrokes, steal data and passwords, and watch victims via their webcams.” states the press release published by NCA.
“The RAT cost as little as £30 and users needed little technical knowledge to deploy it.
A small network of UK individuals supported the distribution and use of the RAT across 78 countries and sold it to more than 8,600 buyers via a website dedicated to hacking and the use of criminal malware.”
The Luminosity RAT was one of the malicious code used in Business Email Compromise attacks and was also used Nigerian gangs in attacks aimed at industrial firms.
Law enforcement believes that thousands of individuals were infected with the RAT.
“Victims are believed to be in the thousands, with investigators having already identified evidence of stolen personal details, passwords, private photographs, video footage and data. Forensic analysis on the large number of computers and internet accounts seized continues.” reads the announcement published by the Europol.
“Through such strong, coordinated actions across national boundaries, criminals across the world are finding out that committing crimes remotely offers no protection from arrests. Nobody wants their personal details or photographs of loved ones to be stolen by criminals. We continue to urge everybody to ensure their operating systems and security software are up to date”. said Steven Wilson, Head of Europol’s European Cybercrime Centre.
Abusing X.509 Digital Certificates to establish a covert data exchange channel
6.2.2018 securityaffairs Security
Researcher at Fidelis Cybersecurity devised a new technique that abuses X.509 Digital Certificates to establish a covert data exchange channel
Last year, during the Bsides conference in July 2017, the security researcher at Fidelis Cybersecurity Jason Reaves demonstrated how to covertly exchange data using X.509 digital certificates, now the same expert published the proof-of-concept code.
The X.509 is a standard that defines the format of public key certificates currently used in many Internet protocols, including TLS/SS. TLS, for example, uses X.509 for certificate exchange, during the handshake process that establishes an encrypted communication.
The covert channel devised by Reaves uses fields in X.509 extensions to carry data, it could be exploited by an attacker to exfiltrate data from a target organization without being detected.
“The research demonstrates that a sufficiently motivated attacker can utilize technologies outside of their intended purposes to not only accomplish their goals but also end up bypassing common security measures in the process.” reads the paper published by the expert.
“In brief, TLS X.509 certificates have many fields where strings can be stored. You can see them in this image[16]. The fields include version, serial number, Issuer Name, validity period and so on. The certificate abuse described in our research takes advantage of this fact to hide data transfer inside one of these fields. Since the certificate exchange happens before the TLS session is established there appears to never be data transfer, when in reality the data was transferred within the certificate exchange itself. “
The proof-of-concept code published by Reaves uses the field ‘class=wrap_text>SubjectKeyIdentifier‘
Digital certificate extensions were added in version 3 of the X.509 protocol and allow the CAs to add descriptions to a certificate, unfortunately, they can be abused to embed malicious data.
Attackers can send small amounts of data to an external server without being noticed.
Anyway, these extensions can be very large, for this reason, many libraries attempt to limit the ultimate handshake packet size. The expert noticed that the extension in the certificate itself can be created to a length that appears to only be limited by memory.
Data hidden in the X.509 metadata are impossible to detect, the PoC code published transfers the Mimikatz post-exploit attack tool in the TLS negotiation:

As possible mitigations, Reaves suggests to block self-signed certificates such the ones used in the PoC and check for executables in certificates.
British Hacker 'Lauri Love' will not be extradited to US, Court Rules
6.2.2018 thehackernews BigBrothers
British citizen and hacker Lauri Love, who was accused of hacking into United States government websites, will not be extradited to stand trial in the U.S., the High Court of England and Wales ruled today.
Love, 33, is facing a 99-year prison sentence in the United States for allegedly carrying out series of cyber attacks against the FBI, US Army, US Missile Defence Agency, National Aeronautics and Space Administration (NASA), and New York's Federal Reserve Bank between 2012 and 2013.
The High Court ruled Monday that Love should be tried in U.K. after Lord Chief Justice Lord Burnett of Maldon and Justice Ouseley heard he suffered severe mental illness like Asperger syndrome, eczema, asthma, and depression, and may kill himself if extradited.
At Westminster Magistrates' Court in London in late 2016, District Judge Nina Tempia ordered Love to be extradited to the U.S. to stand trial, although his lawyers appealed the decision, arguing that he should be tried for his alleged crimes in the UK.
The court accepted both of the arguments advanced by Love's lawyers and ruled that extradition would be "oppressive" due to his serious health conditions and it would be likely that he would be kept in solitary confinement in the American prison system if extradited.
The court burst in applause and cheering when the judgment was handed down by Lord Burnett, who asked Love supporters to be quiet, saying "This is a court, not a theatre."
The Crown Prosecution Service (CPS), which acts on behalf of the US authorities, said it would read the judgment before deciding whether to appeal the high court decision to the supreme court.
According to US Prosecutors, Love was allegedly involved in #OpLastResort, an online protest linked with the Anonymous collective following the persecution and untimely death of hacktivist Aaron Swartz, who committed suicide in 2013 while under federal charges for data theft.
Love, who lives near Newmarket, was arrested from his home in Stradishall, England in October 2013, when the British police seized his encrypted laptops and hard drives.
Britain's National Crime Agency (NCA) also asked the courts to force Love to turn over keys to decrypt his encrypted computer's hard drives, but Love won the case against the agency in early 2016.
If extradited to the United States and found guilty, Love could have sentenced to up to 99 years in prison and a potential fine of up to $9 million (£6.3 million).
Speaking outside the Royal Courts of Justice, Love expressed his thanks to the judges and said: "I'm thankful for all the support we've had, without which I'm not sure I would have made it this far."
WikiLeaks founder Julian Assange, who is also fighting US extradition, congratulate Love in a Tweet, saying: "VICTORY: @LauriLove wins UK appeal against US extradition. Congratulations to Lauri, his lawyers & family, @CourageFound and many supporters on an excellent campaign."
Right now, it is not clear if Love, who denies all wrongdoings, would face a prison sentence in the UK following his five years of legal battle.
Unpatched DoS Flaw Could Help Anyone Take Down WordPress Websites
6.2.2018 thehackernews Vulnerebility
A simple yet serious application-level denial of service (DoS) vulnerability has been discovered in WordPress CMS platform that could allow anyone to take down most WordPress websites even with a single machine—without hitting with a massive amount of bandwidth, as required in network-level DDoS attacks to achieve the same.
Since the company has denied patching the issue, the vulnerability (CVE-2018-6389) remains unpatched and affects almost all versions of WordPress released in last nine years, including the latest stable release of WordPress (Version 4.9.2).
Discovered by Israeli security researcher Barak Tawily, the vulnerability resides in the way "load-scripts.php," a built-in script in WordPress CMS, processes user-defined requests.
For those unaware, load-scripts.php file has only been designed for admin users to help a website improve performance and load page faster by combining (on the server end) multiple JavaScript files into a single request.
However, to make "load-scripts.php" work on the admin login page (wp-login.php) before login, WordPress authors did not keep any authentication in place, eventually making the feature accessible to anyone.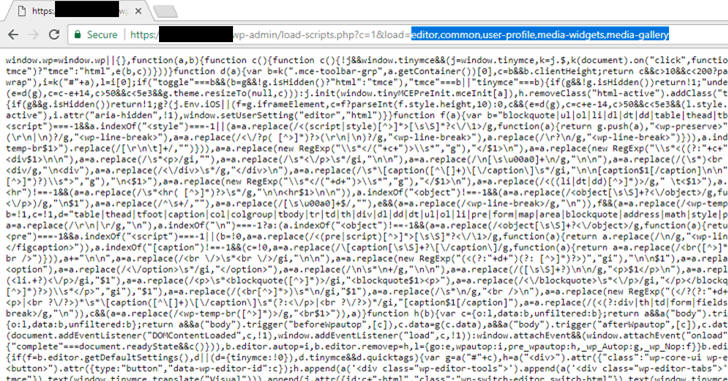
Depending upon the plugins and modules you have installed, the load-scripts.php file selectively calls required JavaScript files by passing their names into the "load" parameter, separated by a comma, like in the following URL:
https://your-wordpress-site.com/wp-admin/load-scripts.php?c=1&load=editor,common,user-profile,media-widgets,media-gallery
While loading the website, the 'load-scripts.php' (mentioned in the head of the page) tries to find each JavaScript file name given in the URL, append their content into a single file and then send back it to the user's web browser.
How WordPress DoS Attack Works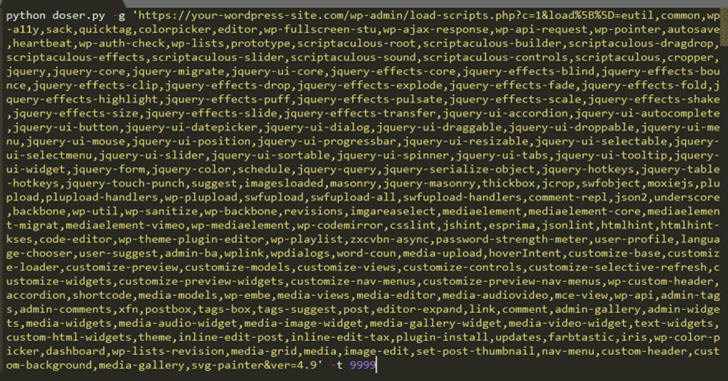
According to the researcher, one can simply force load-scripts.php to call all possible JavaScript files (i.e., 181 scripts) in one go by passing their names into the above URL, making the targeted website slightly slow by consuming high CPU and server memory.
"There is a well-defined list ($wp_scripts), that can be requested by users as part of the load[] parameter. If the requested value exists, the server will perform an I/O read action for a well-defined path associated with the supplied value from the user," Tawily says.
Although a single request would not be enough to take down the whole website for its visitors, Tawily used a proof-of-concept (PoC) python script, doser.py, which makes large numbers of concurrent requests to the same URL in an attempt to use up as much of the target servers CPU resources as possible and bring it down.
The Hacker News has verified the authenticity of the DoS exploit that successfully took down one of our demo WordPress websites running on a medium-sized VPS server.
"It is time to mention again that load-scripts.php does not require any authentication, an anonymous user can do so. After ~500 requests, the server didn't respond at all any more, or returned 502/503/504 status code errors," Tawily says.
However, attack from a single machine, with some 40 Mbps connection, was not enough to take down another demo website running on a dedicated server with high processing power and memory.
But that doesn't mean the flaw is not effective against WordPress websites running over a heavy-server, as application-level attack generally requires a lot fewer packets and bandwidth to achieve the same goal—to take down a site.
So attackers with more bandwidth or a few bots can exploit this flaw to target big and popular WordPress websites as well.
No Patch Available – Mitigation Guide
Along with the full disclosure, Tawily has also provided a video demonstration for the WordPress Denial of Service attack. You can watch the video to see the attack in action.
Knowing that DoS vulnerabilities are out-of-scope from the WordPress bug bounty program, Tawily responsibly reported this DoS vulnerability to the WordPress team through HackerOne platform.
However, the company refused to acknowledge the issue, saying that this kind of bug "should really get mitigated at the server end or network level rather than the application level," which is outside of WordPress's control.
The vulnerability seems to be serious because WordPress powers nearly 29 percent of the Web, placing millions of websites vulnerable to hackers and making them unavailable for their legitimate users.
For websites that can't afford services offering DDoS protection against application-layer attacks, the researcher has provided a forked version of WordPress, which includes mitigation against this vulnerability.
However, I personally wouldn't recommend users to install modified CMS, even if it is from a trusted source other than the original author.
Besides this, the researcher has also released a simple bash script that fixes the issue, in case you have already installed WordPress.
How to Mitigate the Threat Cryptocurrency Mining Poses to Enterprise Security
6.2.2018 thehackernews CoinMine
The growing popularity of Bitcoin and other cryptocurrencies is generating curiosity—and concern—among security specialists. Crypto mining software has been found on user machines, often installed by botnets. Organizations need to understand the risks posed by this software and what actions, if any, should be taken.
To better advise our readers, we reached out to the security researchers at Cato Networks. Cato provides a cloud-based SD-WAN that includes FireWall as a Service (FWaaS). Its research team, Cato Research Labs, maintains the company's Cloud IPS, and today released a list of crypto mining pool addresses that you can use as a blacklist in your firewall. (To download the list, visit this page.)
Cato Research Labs determined crypto mining represents a moderate threat to the organization. Immediate disruption of the organization infrastructure or loss of sensitive data is not likely to be a direct outcome of crypto mining.
However, there are significant risks of increased facility cost that must be addressed.
Understanding Blockchain and Crypto Mining
Crypto mining is the process of validating cryptocurrency transactions and adding encrypted blocks to the blockchain. Miners solve a hash to establish a valid block, receiving a reward for their efforts. The more blocks mined, the more difficult and resource-intensive becomes solving the hash to mine a new block.
Today, the mining process can require years with an off-the-shelf computer. To get around the problem, miners use custom hardware to accelerate the mining process, as well as forming "mining pools" where collections of computers work together to calculate the hash.
The more compute resources contributed to the pool, the greater the chance of mining a new block and collecting the reward. It's this search for more compute resources that have led some miners to exploit enterprise and cloud networks.
Participating in mining pools requires computers run native or JavaScript-based mining software (see Figure 1). Both will use the Stratum protocol to distribute computational tasks among the computers in the mining pool using TCP or HTTP/S (technically, WebSockets over HTTP/S).
Figure 1: An example of a website running JavaScript-based mining software. Typically, websites do not ask for permission.
Native mining software will typically use long-lasting TCP connections, running Stratum over TCP; JavaScript-based software will usually rely on shorter-lived connections and run Stratum over HTTP/S.
The Risk Crypto Mining Poses to the Enterprise
Mining software poses a risk to the organization on two accounts. In all cases, mining software is highly compute-intensive, which can slow down an employee’s machine. Running CPUs with a “high-load” for an extended period of time will increase electricity costs and may also shorten the life of the processor or the battery within laptops.
Mining software is also being distributed by some botnets. Native mining software accesses the underlying operating system in a way similar to how botnet-delivered malware exploits a victim’s machine. As such, the presence of native mining software may indicate a compromised device.
How To Protect Against Crypto Mining
Cato Research Labs recommends blocking crypto mining on your network. This can be done by disrupting the process of joining and communicating with the mining pool.
The deep packet inspection (DPI) engine in many firewalls can be used to detect and block Stratum over TCP. Alternatively, you can block the addresses and domains for joining public mining pools.
Approach 1: Blocking Unencrypted Stratum Sessions with DPI
DPI engines can disrupt blockchain communications by blocking Stratum over TCP. Stratum uses a publish/subscribe architecture where servers send messages (publish) to subscribed clients. Blocking the subscription or publishing process will prevent Stratum from operating across the network.
DPI rules should be configured for JSON. Stratum payloads are simple, readable JSON-RPC messages (see Figure 2).
Stratum uses a request/response over JSON-RPC: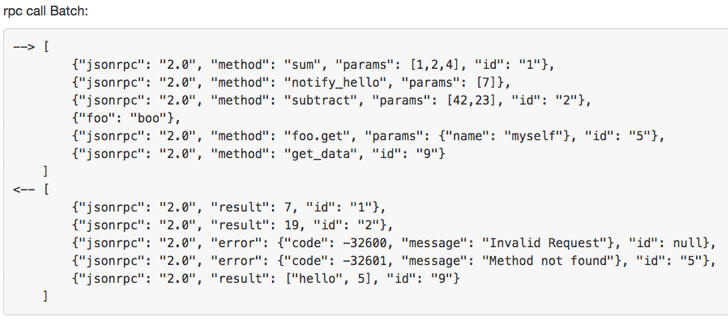
Figure 2: Detail of a JSON-RPC batch call (reference: http://www.jsonrpc.org/specification)
A subscription request to join a pool will have the following entities: id, method, and params (see Figure 3). Configure DPI rules to look for these parameters to block Stratum over unencrypted TCP.
{"id": 1, "method": "mining.subscribe", "params": []}
Three parameters are used in a subscription request message when joining a pool.
Approach 2: Blocking Public Mining Pool Addresses
However, some mining pools create secure, Stratum channels. This is particularly true for JavaScript-based applications that often run Stratum over HTTPS.
Detecting Stratum, in that case, will be difficult for DPI engines who do not decrypt TLS traffic at scale. (For the record, Cato IPS can decrypt TLS sessions at scale.) In those cases, organizations should block the IP addresses and domains that form the public blockchain pools.
To determine the IP addresses to block, look at the configuration information needed to join a mining pool. Mining software requires miners to fill in the following details:
the appropriate pool address (domain or IP)
a wallet address to receive equity
the password for joining the pool
The configuration information is usually passed via JSON or via command-line arguments (see Figure 3).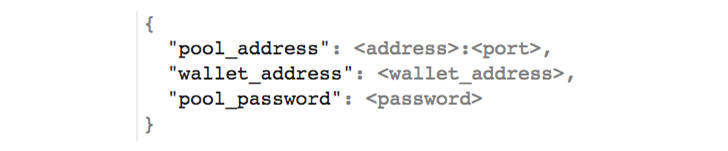
Figure 3: A JSON file providing the necessary miner pool configuration
Organizations could configure firewall rules to use a blacklist and block the relevant addresses. In theory, such a list should be easy to create as the necessary information is publicly available. Most mining pools publish their details over the Internet in order to attract miners to their networks (see Figure 4).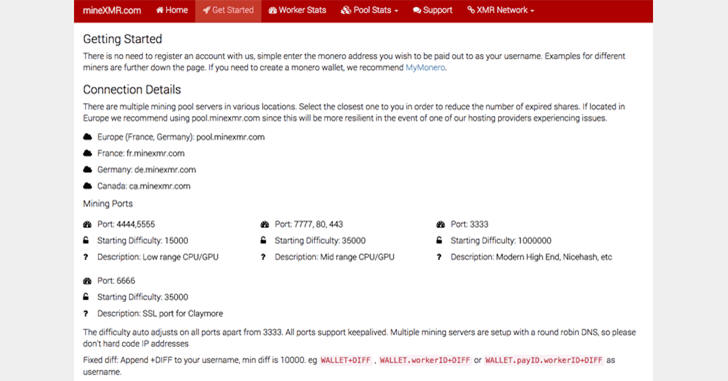
Figure 4: Public addresses for mining pools are well advertised as demonstrated by mineXMR.com’s “Getting Started” page
Despite extensive research, though, Cato Research Labs could not find a reliable feed of mining pool addresses. Without such a list, collecting the target mining pool addresses for blocking would be time-consuming.
IT professionals would be forced to manually enter in public addresses, which will likely change or increase, requiring constant maintenance and updates.
Cato Research Labs Publishes List of Mining Pool Addresses
To address the issue, Cato Research Labs generated its own list of mining pool addresses for use by the greater community. Using Google to identify sites and then employing scraping techniques, Cato researchers were able to extract pool addresses for many mining pools.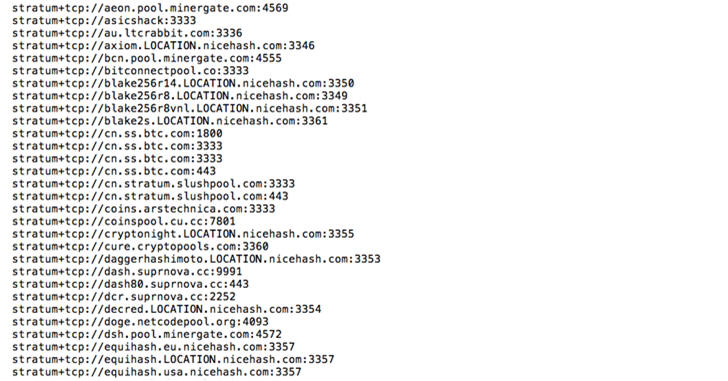
Figure 5: Partial list of mining pool addresses compiled by Cato Research Labs
Cato researchers wrote code that leveraged those results to develop a mining-pool address feed. Today, the list identifies hundreds of pool addresses (see Figure 5) and should be suitable for most DPI rule engines. See here for the full list.
Final Thoughts
The combined risk of impairing devices, increasing costs, and botnet infections led Cato Research Labs to strongly recommend IT prevent and remove crypto mining from enterprise networks.
Should software-mining applications be found on the network, Cato Research Labs strongly recommends investigating active malware infections and cleaning those machines to reduce any risk to organization's data.
Cato Research Labs provided a list of address that can be used towards that goal, blocking access to public blockchain pools. But there's always a chance of new pools or addresses, which is why Cato Research Labs strongly recommend constructing rules using a DPI engine with sufficient encrypted-session capacity.
Grammarly Rushes to Patch Flaw Exposing User Data
6.2.2018 securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy discovered a vulnerability in the online grammar checker Grammarly that could have been exploited by malicious websites to access user data. The app’s developers quickly patched the flaw after learning of its existence.
Ormandy found that the Grammarly browser extension, which has roughly 20 million users on Chrome and 645,000 on Firefox, exposed authentication tokens to third-party websites.
An attacker could have obtained authentication tokens and used them to access the target’s Grammarly.com account simply by getting them to visit a specially crafted website. This was a serious flaw considering that some Grammarly accounts could contain highly sensitive information.
“I'm calling this a high severity bug, because it seems like a pretty severe violation of user expectations,” Ormandy said in an advisory. “Users would not expect that visiting a website gives it permission to access documents or data they've typed into other websites.”
In a blog post covering the Google researcher’s findings, Sophos expert Paul Ducklin explained how authentication tokens work.
“An authentication token is a one-time cryptographic string that is set by a server as a browser cookie after you’ve successfully logged into a website. Your browser sends that cookie back to the site with every subsequent web transaction, thus signalling to the server that it’s you coming back for more,” Ducklin said. “Without this sort of arrangement, you’d have to supply your username and password for every web request you wanted to make.”
Ducklin highlighted that online services should protect these tokens by using HTTPS, and by enforcing the same-origin policy (SOP), which prevents websites from interacting with each other.
Ormandy reported the vulnerability to Grammarly on Friday and the company said it rolled out a fix within hours. Users are not required to take any action as the affected browser extensions should be updated automatically.
Grammarly pointed out that the security hole only affected text saved in the Grammarly Editor, and it did not impact Grammarly Keyboard, the Microsoft Office add-in, or any text typed in websites while using the extension.
“At this time, Grammarly has no evidence that any user information was compromised by this issue,” Grammarly said. “We’re continuing to monitor actively for any unusual activity.”
This is not the first vulnerability disclosed by Ormandy this year. He has also reported finding a critical remote code execution vulnerability in the Transmission BitTorrent client, and a code execution flaw affecting all games from Blizzard.
Crypto-mining Botnet Targets Android Devices
6.2.2018 securityweek Android
A new crypto-mining botnet has been growing and targeting Android devices with an open ADB port, Qihoo 360's NetLab researchers reveal.
The attacks started last week, targeting port 5555, which is the working port for the adb debug interface on Android devices. While this port should be normally closed on all devices, sometimes it could remain open, thus allowing devices to be compromised.
Courtesy of scanning code borrowed from the infamous Mirai botnet – which targets Internet of Things (IoT) devices – the new threat can spread as a worm, NetLab reports. Each of the infected bots would continue to scan for open 5555 adb ports to spread further.
This is the first time the Mirai code has been reused to target Android devices, the researchers point out.
The infection appears to have started on January 21, 2018, and the researchers say that the number of attacks has increased recently.
As of February 4, between 2,700 and 5,500 devices had been affected by the botnet, with most of them located in China (40%) and South Korea (31%) – based on the scanning IP addresses targeted devices include smartphones and smart TVs (TV set-top boxes), the security researchers say.
It appears that the botnet isn’t targeting vulnerabilities affecting only specific devices, mainly because models from a broad range of manufacturers have been already impacted. However, the security firm hasn’t provided details on the impacted device models.
The purpose of the newly created botnet, NetLab reports, is to mine for the Monero crypto-currency. The malware’s configuration shows the use of two mining pools, but both groups of devices are using the same wallet address.
The researchers revealed that no payment had been made to the used wallet by the time of their report, but also said they would continue watching and analyzing the threat to provide additional details.
Popular British hacktivist Lauri Love will not be extradited to US, UK Court Ruled
6.2.2018 securityaffairs Crime
The popular British hacker Lauri Love (33) will not be extradited to stand trial in the US, the High Court of England and Wales ruled.
Lauri Love was accused of hacking into United States government websites, will not be extradited to stand trial in the U.S., the High Court of England and Wales ruled today.
The list of victims of the hacker includes the FBI, the Federal Reserve Bank, US Missile Defence Agency, National Aeronautics and Space Administration (NASA), and the US Missile Defence Agency.
The decision of the Lauri Love’s extradition was taken at Westminster Magistrates’ Court in London in 2016, by District Judge Nina Tempia. If extradited, Love risks a sentence to up to 99 years in prison and a potential fine of up to $9 million.
Actually, the man would face a prison sentence in the UK following his five years of legal battle.
US Prosecutors believe that Lauri Love is a member of a hacker crew, they sustain that he was also involved in the OpLastResort campaign launched by Anonymous against the US Government.

Lord Chief Justice Lord Burnett of Maldon and Justice Ouseley halted the extradition after heard Lauri Love suffered severe mental illness, including Asperger syndrome, and depression, they fear the man should commit suicide if extradited.
“There have not been any incidents of self-harm in the past but I accept Mr Love has experienced suicidal thoughts intermittently, both in the past and now. Mr Love denied any suggestion that he had exaggerated his symptoms and his suicide risk which I accept given the medical evidence.” the High Court ruled on Monday.
“I also accept Professor Baron-Cohen and Professor Kopelman’s evidence that he would attempt suicide before extradition to the United States. Both are of the opinion he would be at high risk of suicide. I accept Professor BaronCohen’s oral evidence that Mr Love’s intention is not a reflection of a voluntary plan or act but due to his mental health being dependant on him being at home with his parents and not being detained for an indefinite period.”
The court recognized that extradition would be “oppressive” due to the man’s health conditions. Love supporters that were present in the court applauded the judgment.
The Crown Prosecution Service (CPS), which acts on behalf of the US authorities, would examine the judgment before deciding whether to appeal the high court decision to the supreme court.
“I’m thankful for all the support we’ve had, without which I’m not sure I would have made it this far.” commented Love expressing gratitude to the judges.
The judgment was accepted with joy in the hacking community and by human rights advocates.
ADB.Miner, the Android mining botnet that targets devices with ADB interface open
6.2.2018 securityaffairs BotNet
Security researchers at Qihoo 360’s Netlab have spotted a new Android mining botnet that targets devices with ADB interface open.
Security researchers at Qihoo 360’s Netlab have spotted a new Android mining botnet over the weekend. The malicious code ADB.Miner targets Android devices by scanning for open ADB debugging interface (port 5555) and infects them with a Monero cryptocurrency miner.
The port 5555 is the working port ADB debug interface on Android device that should be shut down normally. The devices infected by ADB.miner are devices where users or vendors have voluntary enabled the debugging port 5555.
“Spread of time : the earliest time of infection can be traced back to near January 31. This current wave of helminthic infections has been detected by our system from around 15:00 on the afternoon of 2018-02-03 and is still on the rise.” reads the analysis published by Netlab.
“Infected port : 5555, is the working port adb debug interface on Android device, the port should be shut down normally, but unknown part of the cause led to the wrong port opened.”
Starting from February 3, the expert noticed a rapid growth of the volume of scan traffic on port 5555 associated with the ADB.Miner:

Once the ADB.Miner has infected a device, the compromised system start scanning the Internet for other devices to infect.
According to the experts, ADB.miner borrowed the scanning code implemented by the Mirai botnet, this is the first time that the Mirai code is used by an Android threat.
The researchers did not reveal the way the malware infects the Android devices, it is likely it exploits a flaw in the ADB interface.
The number of infected devices is rapidly growing, according to different caliber statistics, there are 2.75 ~ 5.5k, and this figure is rapidly growing.
The two sources reported by Netlab are:
Statistics from scanmon : 2.75k, mainly from China (40%) and South Korea (31%).
Statistics from our botnet tracking system: 5.5k
At the time of writing the number of ADB.miner scans reached 75,900 unique IP addresses.

Most IP addresses scanning the port 5555 are located in China (~40%) and South Korea (~30%).
The operators of the botnet are using the following Monero wallet address:
44XT4KvmobTQfeWa6PCQF5RDosr2MLWm43AsaE3o5iNRXXTfDbYk2VPHTVedTQHZyfXNzMn8YYF2466d3FSDT7gJS8gdHAr
That still has not received the first payment for the mine.