
Malware is Pervasive Across Cloud Platforms: Report
8.2.2018 securityweek Virus
Leading Cloud Service Providers and Majority of AV Engines Failed to Detect New Ransomware Variant
Cloud Access Security Brokers (CASBs) provide visibility into the cloud. Some CASBs provide malware protection. Some clouds provide malware protection. Bitglass analyzed the efficacy of cloud-only protection by scanning the files of its customers that had not implemented its own Advanced Threat Protection (actually Cylance).
Bitglass scanned tens of millions of customer files and found (PDF) a remarkably high number of infections: 44% of organizations had at least one piece of malware in their cloud applications; and nearly one-in-three SaaS app instances contained at least one threat. Among the SaaS apps, 54.4% of OneDrive and 42.9% of Google Drive instances were infected. Dropbox and Box followed, both at 33%.
The research discovered that the average company had nearly 450,000 files held in the cloud, with more than 20 of the files containing malware. Forty-two percent of the infected file types were script and executable files, 21% were Office documents, 10% were Windows system files, and 8% were compressed formats. The other 19% were in various different file formats.
Among the infections it discovered a malware that Cylance confirmed as a zero-day ransomware -- which it calls ShurL0ckr. ShurL0ckr is ransomware-as-a-service , "meaning," says Bitglass, "the hacker generates a ransomware payload and distributes it via phishing or drive-by-download to encrypt files on disk in a background process until a Bitcoin ransom is paid." No analysis of the malware and its inner workings is provided.
It is, however, undetected by either Microsoft's or Google's cloud offerings.
"The sad truth," comments Meni Farjon, co-founder and CTO at SoleBIT Labs, "is that today, most cloud services providers still do not supply advanced malware detection capabilities, thus making this vector a perfect choice for attackers who aim to infect corporate users on a massive scale. I believe we will definitely see more ransomware variants targeting cloud application in the coming months, at least until the major cloud services providers offer malware detection capabilities to those services."
Bitglass checked whether mainstream anti-malware would detect the ShurL0ckr ransomware. "The team," writes Bitglass, "then leveraged VirusTotal to scrutinize a file containing the ransomware across dozens of antivirus engines. Only 7% of said engines (five in sixty-seven) detected the malware - one of these engines was Cylance, a Bitglass technology partner."
VirusTotal was acquired by Google in 2012.
The key takeaways from this research are that security teams' concerns about cloud security are valid, and there's a new ransomware that goes largely undetected. That last point is, however, not clear cut. The purpose of VirusTotal (VT) is to allow concerned users to gain insight into a suspect file -- could it be, or is it likely not, malicious? It is not an anti-malware comparative tool.
VirusTotal itself says, "Antivirus engines can be sophisticated tools that have additional detection features that may not function within the VirusTotal scanning environment. Because of this, VirusTotal scan results aren't intended to be used for the comparison of the effectiveness of antivirus products."
"In other words," comments ESET senior research fellow David Harley, "a VirusTotal report is not a reliable indicator as to whether a product detects or blocks a given sample out in the field, because VirusTotal doesnít necessarily make use of all the layers of protection made available by a specific product in the real world. To draw any conclusions about the efficacy of any product based on one sample isnít testing at all," he added; "itís just marketing."
Lenny Zeltser, VP of products at Minerva Labs, isn't surprised by the VT engines' low detection rate. "Attackers continually find ways of getting around AV tools, due to the inherent weaknesses of any approach to detecting malicious software on the basis of previously-seen patterns. This is a reality for all types of AV solutions," he told SecurityWeek, "regardless of whether they employ AI or not."
He believes that it is reasonable for Bitglass to quote a low VT detection rate because "this research focused on the way in which files stored on cloud services are identified as malware. I believe the providers of such services rely on static scans, which makes VirusTotal a reasonable approximation of AV efficacy in such scenarios. The findings show that organizations cannot rely solely on the scans performed by these providers, and should deploy anti-malware protection to their endpoints as well.î
What we now know is that there is another ransomware to worry about. We know that Cylance can detect it, but we don't know whether other anti-malware products deployed in the field will also catch it -- we do not know that only 7% will detect it. Bitglass hasn't provided any IOCs in its report, so it will be difficult for security teams to check for themselves.
However, since Bitglass uploaded an infected file to VirusTotal, VT will have shared details with its partner AV companies. They will now be making sure that they will detect it in the future -- so it might be useful for security teams to check directly with their own anti-malware provider to make sure they are already covered.
Silicon Valley-based Bitglass raised $45 million in a Series C funding round in January 2017, adding to the $25 million Series B round in 2014.
Swisscom Breach Hits 800,000 Customers
8.2.2018 securityweek Crime
Swiss telecoms giant Swisscom on Wednesday said it had tightened security controls after suffering a data breach that affected roughly 800,000 of its customers.
The company said unauthorized parties gained access to customer data by leveraging the access privileges of a sales partner. The attackers somehow obtained the partner’s credentials and used them to access contact information, including names, physical addresses, phone numbers, and dates of birth.
Swisscom pointed out that it collects this type of data legally from customers when they enter a subscription agreement, and sales partners are given limited access to records for identification and contracting purposes.
The company noted that this type of information is not considered sensitive under data protection laws, and it’s mostly either already in the public domain or in the hands of list brokers.
The data breach has affected approximately 800,000 Swisscom customers, mostly mobile services subscribers. The company said it had detected the incident during a routine check, but an in-depth investigation was launched following its discovery.
“Swisscom stresses that the system was not hacked and no sensitive data, such as passwords, conversation or payment data, was affected by the incident,” Swisscom stated. “Rigorous long-established security mechanisms are already in place in this case.”
While the compromised data is non-sensitive, Swisscom has reported the incident to the Swiss Federal Data Protection and Information Commissioner (FDPIC).
In response to the breach, the company has revoked access for the firm whose credentials were stolen and implemented tighter controls for partners. In the future, Swisscom wants to ensure that high-volume queries for customer information can no longer be run, and introduce two-factor authentication for sales partners when accessing its systems.
The company says it is not aware of any schemes leveraging the stolen data, but it has advised customers to be wary of any suspicious calls.
Joomla 3.8.4 release addresses three XSS and SQL Injection vulnerabilities
8.2.2018 securityaffairs Vulnerebility
Joomla development team has released the Joomla 3.8.4 that addresses many issues, including an SQL injection bug and three cross-site scripting (XSS) flaws.
Joomla development team has released the Joomla 3.8.4 that addresses a large number of issues, including an SQL injection bug and three cross-site scripting (XSS) vulnerabilities. The latest release also includes several improvements.
The XSS and SQL injection vulnerabilities have been classified as “low priority”
“Joomla 3.8.4 is now available. This is a security release for the 3.x series of Joomla addressing four security vulnerabilities and including over 100 bug fixes and improvements.” reads the announcement.
The most severe issue is the SQL injection vulnerability tracked as CVE-2018-6376 due to its high impact.
The issue was reported by the researcher Karim Ouerghemmi from RIPS Technologies (ripstech.com), it affects Joomla! CMS versions 3.7.0 through 3.8.3.
“The lack of type casting of a variable in SQL statement leads to a SQL injection vulnerability in the Hathor postinstall message.” states the security advisory published by Joomla.
“Recent updates to our analysis engine lead to the discovery of a new vulnerability in the Joomla! core affecting versions prior to 3.8.4. RIPS discovered a second-order SQL injection that could be used by attackers to leverage lower permissions and to escalate them into full admin permissions.” reads the analysis published by RIPS.
The experts explained that the flaw could be exploited to gain admin privileges and take over the Joomla installs.
“An attacker exploiting this vulnerability can read arbitrary data from the database. This data can be used to further extend the permissions of the attacker. By gaining full administrative privileges she can take over the Joomla! installation by executing arbitrary PHP code.” continues the post.
The researchers discovered the vulnerability by using their static code analyzer, an attacker can first inject arbitrary content into the targeted install’s database and then create a specially crafted query to gain admin privileges.

The XSS flaws affect the Uri class (versions 1.5.0 through 3.8.3), the com_fields component (versions 3.7.0 through 3.8.3), and the Module chrome (versions 3.0.0 through 3.8.3).
According to the development team, the Uri class (formerly JUri) fails to properly filter the input opening to XSS attacks.
Cyber Espionage Group Targets Asian Countries With Bitcoin Mining Malware
8.2.2018 thehahckernews CyberSpy CoinMine
Security researchers have discovered a custom-built piece of malware that's wreaking havoc in Asia for past several months and is capable of performing nasty tasks, like password stealing, bitcoin mining, and providing hackers complete remote access to compromised systems.
Dubbed Operation PZChao, the attack campaign discovered by the security researchers at Bitdefender have been targeting organizations in the government, technology, education, and telecommunications sectors in Asia and the United States.
Researchers believe nature, infrastructure, and payloads, including variants of the Gh0stRAT trojan, used in the PZChao attacks are reminiscent of the notorious Chinese hacker group—Iron Tiger.
However, this campaign has evolved its payloads to drop trojan, conduct cyber espionage and mine Bitcoin cryptocurrency.
The PZChao campaign is attacking targets across Asia and the U.S. by using similar attack tactics as of Iron Tiger, which, according to the researchers, signifies the possible return of the notorious Chinese APT group.
Since at least July last year, the PZChao campaign has been targeting organizations with a malicious VBS file attachment that delivers via highly-targeted phishing emails.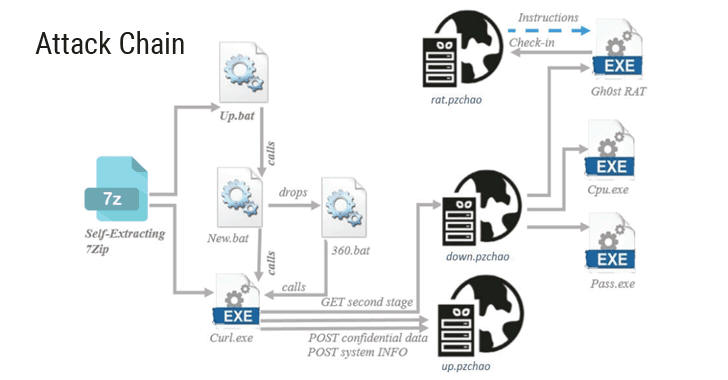
If executed, the VBS script downloads additional payloads to an affected Windows machine from a distribution server hosting "down.pzchao.com," which resolved to an IP address (125.7.152.55) in South Korea at the time of the investigation.
The threat actors behind the attack campaign have control over at least five malicious subdomains of the "pzchao.com" domain, and each one is used to serve specific tasks, like download, upload, RAT related actions, malware DLL delivery.
The payloads deployed by the threat actors are "diversified and include capabilities to download and execute additional binary files, collect private information and remotely execute commands on the system," researchers noted.
The first payload dropped on the compromised machines is a Bitcoin miner, disguised as a 'java.exe' file, that mines cryptocurrency every three weeks at 3 AM, when most people are not in front of their systems.
For password stealing, the malware also deploys one of two versions of the Mimikatz password-scraping utility (depending on the operating architecture of the affected machine) to harvest passwords and upload them to the command and control server.
PZChao's final payload includes a slightly modified version of Gh0st remote access trojan (RAT) which is designed to act as a backdoor implant and behaves very similar to the versions detected in cyber attacks associated with the Iron Tiger APT group.
The Gh0st RAT is equipped with massive cyber-espionage capabilities, including:
Real-time and offline remote keystroke logging
Listing of all active processes and opened windows
Listening in on conversations via microphone
Eavesdropping on webcams' live video feed
Allowing for remote shutdown and reboot of the system
Downloading binaries from the Internet to remote host
Modifying and stealing files and more.
All of the above capabilities allows a remote attacker to take full control of the compromised system, spy on the victims and exfiltrate confidential data easily.
While the tools used in the PZChao campaign are a few years old, "they are battle-tested and more than suitable for future attacks," researchers say.
Active since 2010, Iron Tiger, also known as "Emissary Panda" or "Threat Group-3390," is a Chinese advanced persistent threat (APT) group that was behind previous campaigns resulting in the theft of massive amounts of data from the directors and managers of US-based defense contractors.
Similar to the PZChao campaign, the group also carried out attacks against entities in China, the Philippines, and Tibet, besides attacking targets in the U.S.
For further insights, you can read the detailed technical paper published by Bitdefender.
Critical Flaw in Grammarly Spell Checker Could Let Attackers Steal Your Data
8.2.2018 thehahckernews Vulnerebility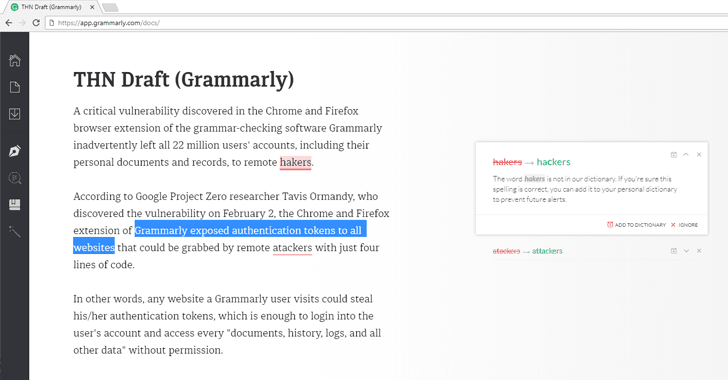
A critical vulnerability discovered in the Chrome and Firefox browser extension of the grammar-checking software Grammarly inadvertently left all 22 million users' accounts, including their personal documents and records, vulnerable to remote hackers.
According to Google Project Zero researcher Tavis Ormandy, who discovered the vulnerability on February 2, the Chrome and Firefox extension of Grammarly exposed authentication tokens to all websites that could be grabbed by remote attackers with just 4 lines of JavaScript code.
In other words, any website a Grammarly user visits could steal his/her authentication tokens, which is enough to login into the user's account and access every "documents, history, logs, and all other data" without permission.
"I'm calling this a high severity bug, because it seems like a pretty severe violation of user expectations," Ormandy said in a vulnerability report. "Users would not expect that visiting a website gives it permission to access documents or data they've typed into other websites."
Ormandy has also provided a proof-of-concept (PoC) exploit, which explains how one can easily trigger this serious bug to steal Grammarly user's access token with just four lines of code.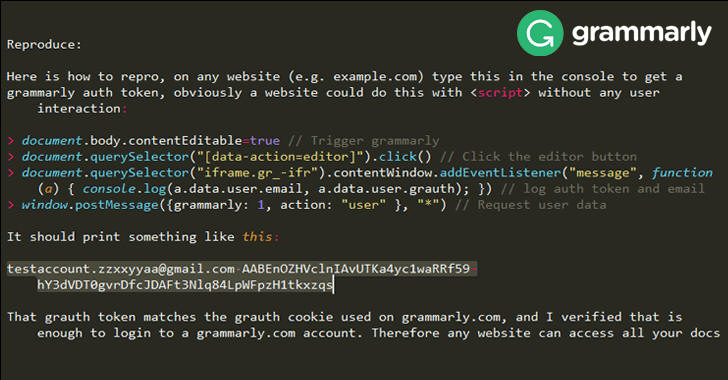
This high-severity flaw was discovered on Friday and fixed early Monday morning by the Grammarly team, which, according to the researcher, is "a really impressive response time" for addressing such bugs.
Security updates are now available for both Chrome and Firefox browser extensions, which should get automatically updated without requiring any action by Grammarly users.
A Grammarly spokesperson also told in an email that the company has no evidence of users being compromised by this vulnerability.
"Grammarly resolved a security bug reported by Google's Project Zero security researcher, Tavis Ormandy, within hours of its discovery. At this time, Grammarly has no evidence that any user information was compromised by this issue," the spokesperson said.
"We're continuing to monitor actively for any unusual activity. The security issue potentially affected text saved in the Grammarly Editor. This bug did not affect the Grammarly Keyboard, the Grammarly Microsoft Office add-in, or any text typed on websites while using the Grammarly browser extension. The bug is fixed, and there is no action required by Grammarly users."
Stay tuned for more updates.
Watch Out! New Cryptocurrency-Mining Android Malware is Spreading Rapidly
8.2.2018 thehahckernews Android CoinMine
Due to the recent surge in cryptocurrency prices, threat actors are increasingly targeting every platform, including IoT, Android, and Windows, with malware that leverages the CPU power of victims' devices to mine cryptocurrency.
Just last month, Kaspersky researchers spotted fake antivirus and porn Android apps infected with malware that mines Monero cryptocurrency, launches DDoS attacks, and performs several other malicious tasks, causing the phone's battery to bulge out of its cover.
Now, security researchers at Chinese IT security firm Qihoo 360 Netlab discovered a new piece of wormable Android malware, dubbed ADB.Miner, that scans wide-range of IP addresses to find vulnerable devices and infect them to mine digital cryptocurrency.
According to the researchers, ADB.Miner is the first Android worm to reuse the scanning code programmed in Mirai—the infamous IoT botnet malware that knocked major Internet companies offline last year by launching massive DDoS attacks against Dyndns.
ADB.Miner scans for Android devices—including smartphones, smart TVs, and TV set-top boxes—with publicly accessible ADB debug interface running over port 5555 and then infects them with a malware that mines Monero cryptocurrency for its operators.
Android Debug Bridge (ADB) is a command-line tool that helps developers debug Android code on the emulator and grants access to some of the operating system’s most sensitive features.
It should be noted that almost all Android devices by default come with the ADB port disabled, so botnet would target only those devices that have manually been configured to enable port 5555.
Besides mining Monero cryptocurrency, ADB.Miner installed on an infected device also attempts to propagate itself by scanning for more targets on the Internet.
Researchers did not reveal exactly how or by exploiting which ADB flaw hackers are installing malware onto Android devices.
However, the researchers believed hackers are not exploiting any vulnerability that targets any specific device vendor since they found devices from a wide range of manufacturers impacted.
According to the researchers, the infection started on January 21, and the number of attacks has increased recently. As of Sunday, the researchers detected 7,400 unique IP addresses using the Monero mining code—that's more than 5,000 impacted devices in just 24 hours.
Based on the scanning IP addresses, the highest number of infection has been noticed in China (40%) and South Korea (31%), the researchers estimated.
In order to fight against such malware Android users are advised not to install unnecessary and untrusted applications from the app store, even from Google Play Store, and keep your devices behind a firewall or a VPN.
Researcher Claims Hotspot Shield VPN Service Exposes You on the Internet
8.2.2018 thehahckernews Vulnerebility
Virtual Private Network (VPN) is one of the best solutions you can have to protect your privacy and data on the Internet, but you should be more vigilant while choosing a VPN service which truly respects your privacy.
If you are using the popular VPN service Hotspot Shield for online anonymity and privacy, you may inadvertently be leaking your real IP address and other sensitive information.
Developed by AnchorFree GmbH, Hotspot Shield is a VPN service available for free on Google Play Store and Apple Mac App Store with an estimated 500 million users around the world.
The service promises to "secure all online activities," hide users' IP addresses and their identities and protect them from tracking by transferring their internet and browsing traffic through its encrypted channel.
However, an 'alleged' information disclosure vulnerability discovered in Hotspot Shield results in the exposure of users data, like the name of Wi-Fi network name (if connected), their real IP addresses, which could reveal their location, and other sensitive information.
The vulnerability, assigned CVE-2018-6460, has been discovered and reported to the company by an independent security researcher, Paulos Yibelo, but he made details of the vulnerability to the public on Monday after not receiving a response from the company.
According to the researcher claims, the flaw resides in the local web server (runs on a hardcoded host 127.0.0.1 and port 895) that Hotspot Shield installs on the user's machine.
This server hosts multiple JSONP endpoints, which are surprisingly accessible to unauthenticated requests as well that in response could reveal sensitive information about the active VPN service, including its configuration details.
"http://localhost:895/status.js generates a sensitive JSON response that reveals whether the user is connected to VPN, to which VPN he/she is connected to what and what their real IP address is & other system juicy information. There are other multiple endpoints that return sensitive data including configuration details," Yibelo claims.
"User-controlled input is not sufficiently filtered: an unauthenticated attacker can send a POST request to /status.js with the parameter func=$_APPLOG.Rfunc and extract sensitive information about the machine," the vulnerability description reads.
Yibelo has also publicly released a proof-of-concept (PoC) exploit code—just a few lines of JavaScript code—that could allow an unauthenticated, remote attacker to extract sensitive information and configuration data.
However, ZDNet reporter Zack Whittaker tries to verify researcher's claim and found that the PoC code only revealed the Wi-Fi network name and country, but not the real IP address.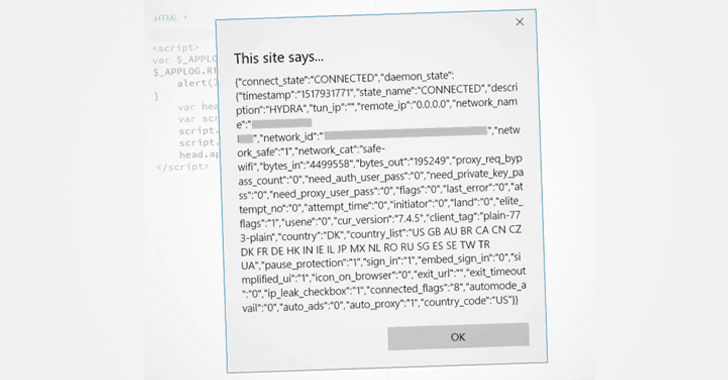
In a statement, AnchorFree spokesperson acknowledged the vulnerability but denied the disclosure of real IP address as claimed by Yibelo.
"We have found that this vulnerability does not leak the user's real IP address or any personal information, but may expose some generic information such as the user's country," the spokesperson told ZDNet.
The researcher also claims that he was able to leverage this vulnerability to achieve remote code execution.
Hotspot Shield also made headlines in August last year, when the Centre for Democracy and Technology (CDT), a US non-profit advocacy group for digital rights, accused the service of allegedly tracking, intercepting and collecting its customers' data.
Intel Releases New Spectre Patches for Skylake CPUs
8.2.2018 securityweek Vulnerebility
Intel has started releasing new microcode updates that should address one of the Spectre vulnerabilities after the first round of patches caused significant problems for many users.
The company has so far released new firmware updates only for its Skylake processors, but expects updates to become available for other platforms as well in the coming days. Customers and partners have been provided beta updates to ensure that they can be extensively tested before being moved into production.
The chipmaker started releasing microcode patches for the Spectre and Meltdown vulnerabilities shortly after the attack methods were disclosed by researchers. However, the company was forced to suspend updates due to frequent reboots and other unpredictable system behavior. Microsoft and other vendors also disabled mitigations or stopped providing firmware updates due to Intel’s buggy patches.Intel provides new microcode updates for Skylake CPUs
Intel claims to have identified the root of an issue that caused systems to reboot more frequently after the patches were installed.
The company initially said only systems running Broadwell and Haswell CPUs experienced more frequent reboots, but similar behavior was later observed on Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms as well.
The problem appears to be related to the fix for CVE-2017-5715, one of the flaws that allows Spectre attacks, specifically Spectre Variant 2. Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Both Intel and AMD announced recently that they are working on processors that will have built-in protections against exploits such as Spectre and Meltdown.
In the meantime, Intel has urged customers to always install updates as soon as they become available. On the other hand, many users might decide to take a risk and not immediately apply fixes in order to avoid potential problems such as the ones introduced by the first round of Spectre and Meltdown patches.
Intel has admitted that researchers or malicious actors will likely find new variants of the Spectre and Meltdown attacks.
Security firms have already spotted more than 100 malware samples exploiting the Spectre and Meltdown vulnerabilities. While a majority appeared to be in the testing phase, we could soon start seeing attacks in the wild, especially since the samples analyzed by experts are designed to work on major operating systems and browsers.
Intel, AMD and Apple face class action lawsuits over the Spectre and Meltdown vulnerabilities.
U.S. Announces Takedown of Global Cyber Theft Ring
8.2.2018 securityweek IT
The US Justice Department announced indictments Wednesday for 36 people accused of running a transnational ring stealing and selling credit card and personal identity data, causing $530 million in losses.
Thirteen members of the "Infraud Organization" were arrested in the United States, Australia, Britain, France, Italy, Kosovo and Serbia, it said.
Created in Ukraine in 2010 by Svyatoslav Bondarenko, Infraud was a key hub for card fraud, touting itself with the motto "In Fraud We Trust."
It was "the premier one-stop shop for cybercriminals worldwide," said Deputy Assistant Attorney General David Rybicki.
Members could buy and sell card and personal data for use to buy goods on the internet, defrauding the card owners, card issuers and vendors.
Infraud operated automated vending sites to make it easy for someone to buy card and identity data from them. It had 10,901 approved "members" registered to buy and sell with them in early 2017, and maintained a rating and feedback system for members.
The senior administrators continuously screened the products and services of vendors "to ensure quality products," said the indictment.
The group operated moderated web forums to share advice among customers, and operated an "escrow" service for payments in digital currencies like Bitcoin, the Justice Department said.
"As alleged in the indictment, Infraud operated like a business to facilitate cyberfraud on a global scale," said Acting Assistant Attorney General John Cronan.
The network of indicted Infraud leaders included people from the United States, France, Britain, Egypt, Pakistan, Kosovo, Serbia, Bangladesh, Canada and Australia.
Bondarenko remains at large, but the number two figure in the organization, Russian co-founder Sergey Medvedev has been arrested, according to US officials.