
South Korea Probes Cyber Shutdown During Olympics Ceremony
11.2.2018 securityweek BigBrothers
South Korea on Saturday investigated a mysterious internet shutdown during the Winter Olympics opening ceremony, which follows warnings of possible cyberattacks during the Pyeongchang Games.
Internal internet and wifi systems crashed at about 7:15 pm (1015 GMT) on Friday and were still not back to normal at midday on Saturday, Games organizers said.
Cyber-security teams and experts from South Korea's defence ministry, plus four other ministries, formed part of a taskforce investigating the shutdown, they said, adding that it didn't affect the high-tech opening ceremony.
Kim Yo Jong, the sister of North Korean leader Kim Jong Un, South Korean President Moon Jae-in and US Vice-President Mike Pence were among the VIPs at Pyeongchang Olympic Stadium late on Friday.
The outage follows warnings of malware phishing attacks targeting organizations working at the Olympics, and allegations of cyberattacks from Russia -- which has denied any involvement.
North Korea has also blamed for a series of cyber incidents including the WannaCry global ransomware attack, which infected 300,000 computers worldwide last May.
"We don't want to speculate because we're still trying to find out what the root source is," said Nancy Park, a spokeswoman for the Games organisers.
"We have some reports, we've been working all night trying to find out and working with our partners."
- WannaCry -
South Korea showed off its technical expertise with a dazzling gala opening ceremony on Friday which included state-of-the-art special effects and augmented reality to add extra impact for TV viewers.
While internet and wifi were affected across the Olympic site -- spread over two main venues in mountainous eastern South Korea -- organisers said there was no impact on competition, which got into full swing on Saturday.
"There were some issues that impacted some of our non-critical systems last night for a few hours," Games organizers said in a statement.
"These have not disrupted any events, or had any effect on the safety and security of any athletes or spectators," they added.
"All competitions are running as planned and the systems are working at the expected level."
Last month, cyber-security firm McAfee said it had uncovered an attack targeting organisations involved with the Olympics, using a malicious email attachment.
North Korea has been accused of involvement in a number of cyber incidents, including WannaCry -- although it has slammed that accusation as "absurd".
Russia has also denied launching any hacking attacks on the Pyeongchang Olympics, where its team is formally banned following the revelation of systemic doping.
While organizers wouldn't comment on the possibility that an attack was behind the shutdown, experts believe disrupting the Games would be seen as a coup for many hackers.
"The whole world’s watching. It's one of the largest stages you can possibly have to get a message out there," Ross Rustici, senior director for intelligence Boston-based Cybereason told the Tribune News Service.
"You got a lot of lower-tier guys going after these games. It's head-hunting, bragging rights," Rustici was quoted as saying.
Hackers are exploiting the CVE-2018-0101 CISCO ASA flaw in attacks in the wild
11.2.2018 securityaffairs Vulnerebility
Hackers are exploiting the CVE-2018-0101 CISCO ASA flaw in attacks in the wild and a Proof-of-concept exploit code is available online.
This week, Cisco has rolled out new security patches for a critical vulnerability, tracked as CVE-2018-0101, in its CISCO ASA (Adaptive Security Appliance) software.
This is the second the tech giant issued a security patch to fix the critical vulnerability in CISCO ASA, the first one released in January. The vulnerability could be exploited by a remote and unauthenticated attacker to execute arbitrary code or trigger a denial-of-service (DoS) condition causing the reload of the system.
The affected models are:
3000 Series Industrial Security Appliance (ISA)
ASA 5500 Series Adaptive Security Appliances
ASA 5500-X Series Next-Generation Firewalls
ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
ASA 1000V Cloud Firewall
Adaptive Security Virtual Appliance (ASAv)
Firepower 2100 Series Security Appliance
Firepower 4110 Security Appliance
Firepower 9300 ASA Security Module
Firepower Threat Defense Software (FTD)
Now the company confirmed that attackers are trying to exploit the vulnerability CVE-2018-0101 in attacks in the wild.
“The Cisco Product Security Incident Response Team (PSIRT) is aware of public knowledge of the vulnerability that is described in this advisory,” reads the security advisory published by CISCO. the update states. “Cisco PSIRT is aware of attempted malicious use of the vulnerability described in this advisory.”
The vulnerability was discovered by Cedric Halbronn and received a CVSS base score of 10.0, the highest one.
This week Halbronn presented its findings at the REcon conference in Brussels, in its speech titled ‘Robin Hood vs CISCO ASA Anyconnect.’ he highlighted that the vulnerability could be present up to seven years old because the AnyConnect Host Scan is available since 2011.
The new attack scenario covered with the new update sees an attacker exploiting the vulnerability by sending specially crafted XML packets to a webvpn-configured interface.

A “Cisco ASA CVE-2018-0101 Crash PoC” was already published by some users on Pastebin.
FSB arrested researchers at the Russian Federation Nuclear Center for using a supercomputer to mine Bitcoins
11.2.2018 securityaffairs CoinMine
Russian authorities have arrested some employees at the Russian Federation Nuclear Center facility because they are suspected for trying to using a supercomputer at the plant to mine Bitcoin.
The peaks reached by the values of principal cryptocurrencies is attracting criminal organizations, the number of cyber-attacks against the sector continues to increase, and VXers are focusing their efforts on the development of cryptocurrency/miner malware.
In a few days, security firms have spotted several huge botnets that were used by crooks to mine cryptocurrencies.
This week, security experts at Radiflow, a provider of cybersecurity solutions for critical infrastructure, have discovered in a water utility the first case of a SCADA network infected with a Monero cryptocurrency-mining malware.
“Radiflow, a provider of cybersecurity solutions for critical infrastructure, today announced that the company has revealed the first documented cryptocurrency malware attack on a SCADA network of a critical infrastructure operator.” reads the press release published by the company.
The Radiflow revealed that the cryptocurrency malware was designed to run in a stealth mode on a target system and even disable security software.
“Cryptocurrency malware attacks involve extremely high CPU processing and network bandwidth consumption, which can threaten the stability and availability of the physical processes of a critical infrastructure operator,” explained Yehonatan Kfir, CTO at Radiflow. “While it is known that ransomware attacks have been launched on OT networks, this new case of a cryptocurrency malware attack on an OT network poses new threats as it runs in stealth mode and can remain undetected over time.”
A cryptocurrency malware infection could have e dramatic impact on ICS and SCADA systems because it could increase resources consumption affecting the response times of the systems used to control processes in the environments.
While the story was making the headlines, the Russian Interfax News Agency reported that several scientists at the Russian Federation Nuclear Center facility (aka All-Russian Research Institute of Experimental Physics) had been arrested by authorities charged for mining cryptocurrency with “office computing resources.”
The nuclear research plant is located in Sarov, in 2011, the Russian Federation Nuclear Center deployed on a new petaflop-supercomputer.
The scientists are accused to have abused the computing power of one of Russia’s most powerful supercomputers located in the Federal Nuclear Center to mine Bitcoins.

The supercomputer normally isolated from the Internet, but the researchers were discovered while attempting to connect it online. the Federal Security Service (FSB) has arrested the researchers.
“There has been an unsanctioned attempt to use computer facilities for private purposes including so-called mining,” Tatyana Zalesskaya, head of the Institute’s press service, told Interfax news agency.
“Their activities were stopped in time. The bungling miners have been detained by the competent authorities. As far as I know, a criminal case has been opened regarding them,”
Online Auction Safety Tips for Buyers and Sellers
11.2.2018 securityaffairs Security
Buying or selling goods through online auctions is more popular than ever. Which are the best practices to follow for buyers and sellers for an online auction?
Buying or selling goods through online auctions is more popular than ever. Today, there are a number of different auctions sites available where sellers can post new and used items for sale.
Buyers often flock to these marketplaces, largely because auction prices tend to be quite low. Additionally, buying through online auctions is a great way to find unique items or collectibles that you simply can’t buy through traditional retail stores.
The vast majority of transactions that take place through these sites go off without a hitch. Occasionally, however, problems do occur.
There are instances where unscrupulous buyers or sellers try to take advantage of other people on the auction site.
By following a few simple online auction safety tips, you can ensure that you don’t fall victim to a scam.
A good place to start is by familiarizing yourself with some of the common risks including the following:
Sellers sometimes try to scam buyers by failing to send out items after they have already been paid for. Buyers, on the other hand, sometimes take advantage of sellers by failing to pay for the item after the seller has already sent it to them or claiming that they never received the item in order to get a refund.
Hackers or online thieves can take control of your account if they get access to your password. Not only can they use your account to make purchases but they can also steal your identity.
Buyers or sellers can sometimes use the personal information that is exchanged during a sale to steal your identity. For instance, if you use a personal check to pay for an item, and unscrupulous seller may try to steal your identity based on the information printed on your check.
Sellers sometimes may try to sell you a knockoff or copy rather than the actual item you are interested in purchasing.
Phishing scams may try to get you to share your information by posing as the auction site or as your payment processor. In most cases, these scams are designed to try to gain access to your banking information or to your password so that the perpetrators can steal your identity.
online auction
Now that you have a better idea of all of the things that can go wrong when buying through an online auction, you can take steps to prepare yourself. A good place to start is by familiarizing yourself with how each auction site is set up. Before posting an item for sale or placing a bid, spend some time performing the following tasks:
Try to get a sense of how the auction site works by watching several items. Pay particular attention to what happens at the end of the auction to see if there is a lot of last-minute bidding. You can then put auction software to work for you on bidding and selling.
Familiarize yourself with the website’s Terms of Use. Make sure you have a clear understanding of the various fees that are charged to both sellers and buyers.
Additionally, find out what steps they take to help protect users in the event that something goes awry with a transaction. Make sure that you fully understand the site’s rules before buying or selling items through their platform.
Find out what forms of payment the website recommends. In most cases, the best option is to use a service like PayPal rather than relying on other payment methods. Personal checks, wire transfers, money orders, cash, and credit or debit cards can be risky for both buyers and sellers. Services such as PayPal provide protection against problems that are commonly experienced online.
Protect your identity when creating your profile. Avoid including personally identifiable information in your profile. Try to keep your screen name and user account as anonymous as possible.
Choose your password carefully. The last thing that you want is for someone to be able to guess your password or to break it easily using software tools. Make sure your password is a minimum of 10 characters long. Include upper and lowercase letters along with symbols and numbers. Avoid including personal information such as your birthdate, age, or name in your password. Additionally, choose a different password for every site that you are on.
That way, even if hackers figure out your password on one site, they won’t be able to access your profiles on other sites.
Online auction – Before making a purchase or listing an item for sale, be sure to do careful research.
Start by taking a closer look at the reputation of the seller or buyer. Typically, the best option is to buy from sellers who have been selling through the platform for a long period of time and who have good feedback from buyers. Make sure all the transactions are completed through the auction site. Don’t fall for the scam where a seller tries to offer you a lower price if you buy the item from them directly rather than buying through the auction site.
Learn as much as you can about the item you are selling or buying. Find out how much the item is currently worth. Make sure that it is authentic and figure out what type of condition it is in. Buyers may want to consider saving a screenshot of the description so that they have proof that they can turn to if the item doesn’t live up to the seller’s promises.
Facebook Increases Bug Bounty Payout After Audit
10.2.2018 securityweek Social
Facebook decided to increase a researcher’s bug bounty payout after discovering that that a bug he reported could lead to account takeover.
In September 2017, security researcher Josip Franjkoviæ discovered an issue with Facebook’s partners portal, which leaked users’ email addresses. The bug was discovered after one of the researcher’s sites was approved to participate in the Free Basics project by Facebook.
What the researcher discovered was a medium-high impact privacy bug where adding a new admin user would leak their email address in subsequent notification emails.
Basically, for a newly added admin, the notifications emails would contain the admin's primary Facebook email through a parameter in one of the links, the security researcher discovered.
To reproduce the bug, one would simply head to the Settings section at https://partners.facebook.com/fbs/settings/, add a name, and enter an email they control in the email field.
Next, they should simply hit the “Add” button, intercept the POST request to /mobile/settings/requirements/save/, and modify the values [settings.users.userstablecontainer.user_id] GET parameter to the ID of the victim whose email they would like to reveal, then forward the request.
Thus, the email Facebook sends to the user’s controlled address contains the victim's primary mail as part of <a href link >, the security researcher found.
Franjkoviæ reported the discovery on September 30, 2017, and Facebook informed him a couple of days later that they fixed an account takeover vulnerability in their platform. The original privacy leak bug, however, was resolved only in late October, after the researcher informed the company the exploit would still work.
After requesting more information from Facebook, the researcher found that the bug he discovered could result in the leaking of login codes. One other parameter in the email link could “potentially be used to login to the user's account (with some restrictions),” the researcher explains.
The feature, however, wasn’t enabled for the researcher’s account, so he could not notice it in the first place.
“Thank you Facebook's security team for being (more than) fair - they could have awarded only the email leak bug, and I would never know this was an account takeover,” the researcher notes.
Facebook too has confirmed that, after analyzing the bug reported by Franjkoviæ internally, the security team discovered that it could potentially allow an attacker to gain access to another account.
“We did a complete review and we determined that there is no evidence that these tactics were used or that personal information was exposed,” a post by the Facebook Bug Bounty team reads.
Franjkoviæ confirmed in an email discussion with SecurityWeek that Facebook increased the paid bounty to reward him for the more important vulnerability. While he wouldn’t reveal the exact amount he received, he did say it was his biggest bounty to date.
Lenovo patches critical flaws that affect Broadcom’s chipsets in dozens of Lenovo ThinkPad
10.2.2018 securityaffairs Vulnerebility
According to a security advisory issued by Lenovo, two critical vulnerabilities in Broadcom chipsets affects at least 25 models of Lenovo ThinkPad.
The affected models are ThinkPad 10, ThinkPad L460, ThinkPad P50s, ThinkPad T460, ThinkPad T460p, ThinkPad T460s, ThinkPad T560, ThinkPad X260 and ThinkPad Yoga 260.
One of the flaws was discovered in June by Google that publicly disclosed it in September. Google also published a proof-of-concept exploit for a Wi-Fi firmware vulnerability affecting Broadcom chipsets in iOS 10 and earlier.
The flaw tracked as CVE-2017-11120, is a memory corruption vulnerability that could be exploited by attackers to execute code and establish a backdoor on a targeted device. T
The flaw initially reported affecting specific Broadcom chipsets used in Apple iPhones, Apple TV, and Android devices was patched in the same month.
The vulnerability, tracked as CVE-2017-11120, is a memory corruption vulnerability, Apple addressed it in the security update for the release of iOS 11.
Now Lenovo warns of the presence of the flaw in two dozen ThinkPad models that use Broadcom’s BCM4356 Wireless LAN Driver for Windows 10.
The Broadcom Wi-Fi chipsets used by Lenovo ThinkPad devices are affected by the CVE-2017-11120 flaw and also by the CVE-2017-11121 vulnerability, both issue are rated as “critical” and received a CVSS 10 score.
“Broadcom has issued an advisory for certain Broadcom WiFi controllers used by many computer and device makers, which contain buffer overflow vulnerabilities on the adapter (not the system CPU).“reads the security advisory.” Broadcom initially did not plan to remediate these issues, but when the WPA2 KRACK issue also emerged, Broadcom combined both fixes in to a single set of driver updates. Lenovo received the first of these near the end of 2017, and continues releasing fixes as integration and testing is completed.”
The flaws can be exploited by remote attackers to execute arbitrary code on the adapter (not the system’s CPU) of the target system.
The CVE-2017-11121 vulnerability was also discovered by Google experts, it is a buffer overflow vulnerability caused by improper validation of Wi-Fi signals.
“Properly crafted malicious over-the-air Fast Transition frames can potentially trigger internal Wi-Fi firmware heap and/or stack overflows, leading to denial of service or other effects,” reads the description for the flaw.
Lenovo users urge to update the Wi-Fi driver for their ThinkPad models.
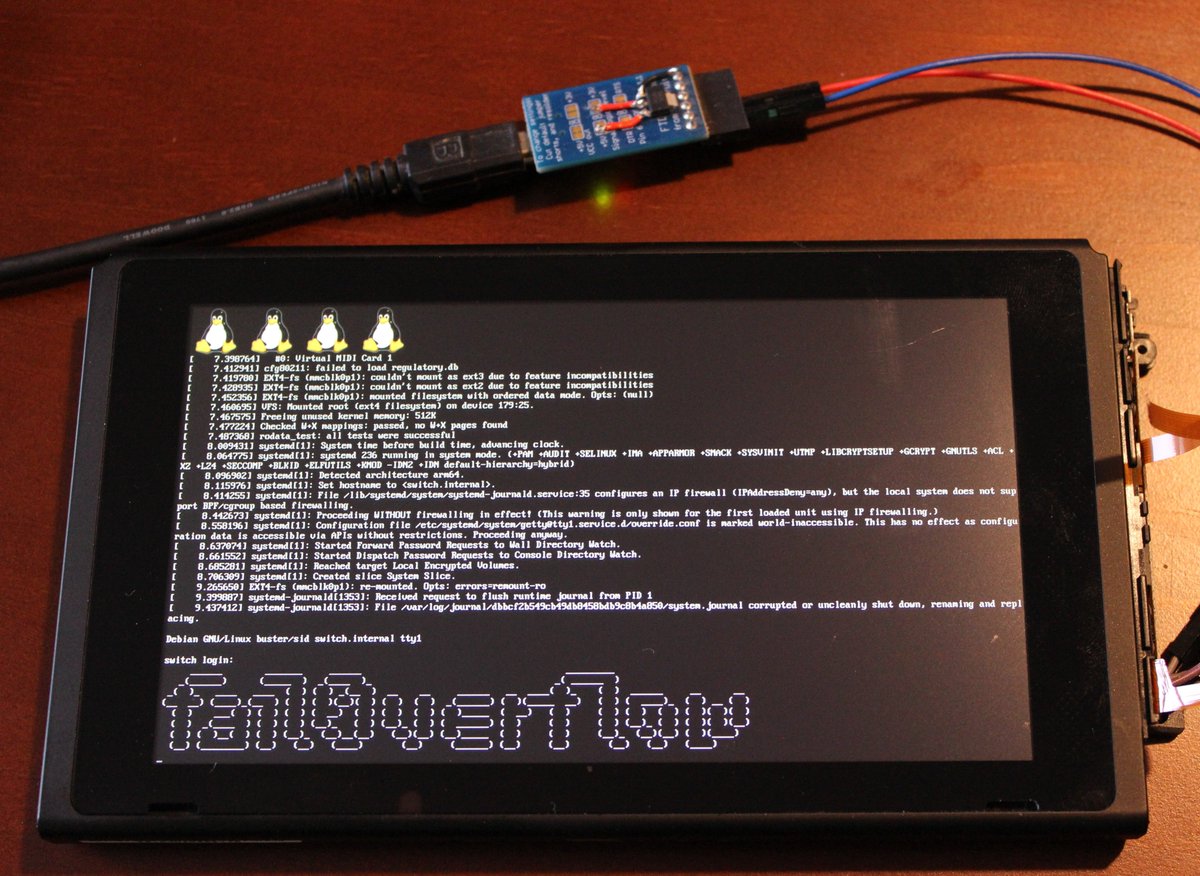
fail0verflow hackers found an unpatchable flaw in Nintendo Switch bootROM and runs Linux OS
10.2.2018 securityaffairs Hacking
The group of hackers known as ‘fail0verflow’ has discovered a vulnerability in the gaming console Nintendo Switch that could be exploited to install a Linux distro.
The hackers announced their discovery in a post on Twitter, the published an image of a console running the Debian Linux distro after the hack.
fail0verflow
@fail0verflow
🐧🐧🐧🐧 #switch
4:16 PM - Feb 6, 2018
4,917
2,269 people are talking about this
Twitter Ads info and privacy
The fail0verflow group revealed that the exploit triggers a flaw in the boot ROM process of the Nvidia Tegra X1 chip that powers the console, if confirmed the issue cannot be solved with a software o firmware update.
When asked if they have built the hack on nvtboot the group No closed-source boot chain components were involved.
Discovery of a flaw in the Boot ROM opens the door to the hack of the console for other purposes, for example to the piracy.

In a next future, hackers could find a way to install homebrew apps and pirated games on the Nintendo Switch.
On the other side, Nintendo could work with Nvidia on new secure Tegra X1 chips, as a temporary solution it could ban users with hacked consoles to ban these users from online play.
VMware releases temporary mitigations for Meltdown and Spectre flaws
10.2.2018 securityaffairs Vulnerebility
VMware has provided detailed instruction on how to mitigate the Meltdown and Spectre vulnerabilities in several of its products.
VMware is releasing patches and workarounds for its Virtual Appliance products affected by the Meltdown and Spectre vulnerabilities.
The Meltdown and Spectre attacks could be exploited by attackers to bypass memory isolation mechanisms and access target sensitive data.
The mitigations measures could be applied to vCloud Usage Meter, Identity Manager (vIDM), vCenter Server, vSphere Data Protection, vSphere Integrated Containers and vRealize Automation (vRA).
“VMware Virtual Appliance updates address side-channel analysis due to speculative execution” states the advisory published by the company.
The company acknowledged problems for its virtual appliances and opted to release workarounds to protect its customers. The proposed solutions are only temporary waiting for a permanent fix that will be released as soon as they are available.
The complete list of workarounds is available here, in some cases, admins can mitigate the issue by launching a few commands as a privileged user, in other cases the procedure to deploy mitigations is more complex.
DDoS attacks in Q4 2017
10.2.2018 Kaspersky Analysis Attack
News overview
In terms of news about DDoS attacks, the last quarter of 2017 was livelier than the previous one. Some major botnets were discovered and destroyed. For instance, early December saw the FBI, Microsoft, and Europol team up to knock out the Andromeda botnet, in operation since 2011. In late October, the Indian Computer Emergency Response Team (CERT) issued a warning about a massive botnet being assembled by a hacker group using the Reaper and IoTroop malware; earlier that same month, the spread of Sockbot through infected Google Play apps was detected and terminated.
Besides the various battles with Trojan-infested botnets, the last three months of 2017 were dominated by three main DDoS trends: politically motivated attacks, attempts to cash in on the soaring price of Bitcoin, and tougher law enforcement.
Politically motivated DDoS attacks remain eye-catching, but fairly ineffective. In late October again, during parliamentary elections in the Czech Republic, the country’s statistical office was hit by a DDoS attack in the middle of the vote count. The attack was a nuisance, but nothing more, and the results of the elections were duly announced on time.
Another DDoS-based political protest was aimed at the Spanish government in connection with the Catalan question. Hacktivists from the Anonymous group managed to take down the website of Spain’s Constitutional Court, and defaced the Ministry of Public Works and Transport’s website with the message “Free Catalonia.”
But politics is politics, and business is, well, just that. As we noted in the previous quarter, Bitcoin and everything associated with it has hit peak commercial popularity — not surprising, considering the explosive growth in its value. No sooner had Bitcoin spawned a new kind of cryptocurrency in the shape of Bitcoin Gold (BTG) than BTG sites immediately came under DDoS fire. After the price of the cryptocurrency took off in November, DDoS attacks rained down on the Bitfinex exchange — apparently with the aim of profiting from Bitcoin price fluctuations caused by denial of service. Still punch-drunk from the November attack, Bitfinex was paralyzed by two more onslaughts in early December.
On the topic of total failure, it would be amiss not to mention the shutdown of four shadow markets in the deep web used for all kinds of illegal trade: Trade Route, Tochka, Wall Street Market, and Dream Market. They have been operating erratically ever since October. It wasn’t clear at first what was behind these massive, well-coordinated attacks: the law enforcement agencies (as in the recent destruction of AlphaBay and Hansa) or competitors attempting to encroach on their territory. The subsequent attacks on all other trading platforms in early December dispelled most analysts’ doubts that it was a full-scale cyberwar between drug cartels.
However, the law — in particular, the judicial system — is not sitting idly by. Q4 saw a whole host of charges and sentences handed down in DDoS-related cases. The US judicial system was the most active: in mid-December, three defendants, Paras Jha, Josiah White, and Dalton Norman, confessed to being the brains behind the Mirai botnet.
And in late December, the founders of the notorious hacker groups Lizard Squad and PoodleCorp — Zachary Buchta of the U.S. and Bradley Jan Willem van Rooy of the Netherlands — were convicted.
In Britain, the high-profile case of young hacker Alex Bessell from Liverpool went to trial. Bessell was recently jailed for having launched a series of major cyber attacks in the period 2011-2013 against such giants as Skype, Google, and Pokemon. An even younger British hacker who targeted NatWest Bank, the National Crime Agency, Vodafone, the BBC, and Amazon was handed 16 months’ detention, suspended for two years.
A curious incident concerned 46-year-old John Gammell of Minnesota, who was charged with hiring three hacking services to create problems for his former employers, the websites of the judicial system of the district where he lived, and several other companies where he was once a contractor. The sponsors of DDoS attacks are often hard to track down, but Gammel couldn’t resist the temptation to tease his targets with emails — which led to his capture. As the investigators reported, the hacking services dealt with Gammel very professionally and cordially, thanking him for procuring their services and even upgrading his membership.
Quarter trends
Q4 demonstrated that DDoS attacks can be categorized as persistent online “crosstalk.” Junk traffic has become so widespread that server failure from too many requests might not be attack-related, but the accidental result of botnet side activities. For instance, in December we logged a huge number of requests to non-existent 2nd and 3rd level domains, which created an abnormal load on DNS servers in the RU zone. A modification of the Lethic Trojan turned out to be the culprit. This long-known malware comes in many different flavors, its main task being to allow spam traffic to pass through infected devices, basically like a proxy server.
The version we discovered was unlike most modifications in that it operates in multiple threads to create a huge number of requests to non-existent domains. The study found that this behavior was an attempt to mask the command-and-control (C&C) server addresses behind numerous junk requests, and the excessive load on the DNS servers was simply the result of the malware’s poor design. Nevertheless, DDoS attacks on DNS servers using junk requests are quite common and easy to implement. Our experts have assisted clients in many such instances. What’s interesting here is the method employed, as well as the perhaps unintended effect.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience of combating cyber threats, including DDoS attacks of various complexity types and ranges. Company experts track the actions of botnets by using the DDoS Intelligence system.
Being part of the Kaspersky DDoS Prevention solution, the DDoS Intelligence system intercepts and analyzes commands sent to bots from C&C servers and requires neither the infection of any user devices, nor the actual execution of cybercriminals’ commands.
This report contains DDoS Intelligence statistics for Q4 2017.
In the context of this report, it is assumed that an incident is a separate (single) DDoS-attack if the interval between botnet activity periods does not exceed 24 hours. For example, if the same web resource was attacked by the same botnet with an interval of 24 hours or more, then this incident is considered as two attacks. Also, bot requests originating from different botnets but directed at one resource count as separate attacks.
The geographical locations of DDoS-attack victims and C&C servers used to send commands are determined by their respective IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
DDoS Intelligence statistics are limited only to those botnets detected and analyzed by Kaspersky Lab. It should also be noted that botnets are just one of the tools for performing DDoS attacks; thus, the data presented in this report do not cover every single DDoS attack that occurred during the specified period.
Quarter results
In Q4 2017, DDoS attacks were registered against targets in 84 countries (98 in Q3). However, as in the previous quarter, the overwhelming majority of attacks occurred in the top ten countries in the list (94.48% vs. 93.56%).
More than half of all attacks in Q4 (51.84%) were aimed at targets in China — almost unchanged since Q3 (51.56%).
In terms of both number of attacks and number of targets, South Korea, China, and the US remain out in front. But in terms of number of botnet C&C servers, Russia pulled alongside this trio: its relative share matched China’s.
The longest DDoS attack of Q4 2017 lasted 146 hours (just over six days). This is significantly shorter than the previous quarter’s record of 215 hours (almost nine days). 2017’s longest attack (277 hours) was registered in Q2.
The days before and after Black Friday and Cyber Monday saw increased activity on dummy Linux servers (honeypot traps), which lasted right up until the beginning of December.
SYN DDoS remains the most common attack method, while the least popular is ICMP DDoS. According to Kaspersky DDoS Protection data, the frequency of multi-method attacks rose.
In Q4 2017, the share of Linux botnets climbed slightly to 71.19% of all attacks.
Geography of attacks
In Q4 2017, DDoS attacks affected 84 countries, which represents a slight improvement over the previous quarter, when 98 countries were hit. Traditionally, China is most in the firing line, although the country’s share of attacks decreased slightly (from 63.30% to 59.18%), approaching the Q2 level. The figures for the US and South Korea, which retained second and third place, went up slightly to 16.00% and 10.21%, respectively.
Fourth place went to Britain (2.70%), which climbed 1.4% to overtake Russia. Although Russia’s share of attacks dropped insignificantly (by 0.3%), that was enough to push it into sixth place behind Vietnam (1.26%), which made a return to the leaderboard, squeezing Hong Kong out of the top ten.
The percentage of attacks directed against targets in the top ten countries grew in the last quarter (but not by much) to almost 92.90% vs. 91.27% in Q3 2017. The landscape is much the same as before.
About half of all targets are still in China (51.84%), followed by the US (19.32%), where the number of targets is again nearing 20% after a slight dip in Q3; South Korea is third with 10.37%. Vietnam again ousted Hong Kong from the top ten, taking ninth place with a 1.13% share, while Russia (1.21%) came seventh with a loss of 1%, making way for Britain (3.93%), France (1.60%), Canada (1.24%), and the Netherlands (1.22%), whose figures did not change much against the previous quarter.
Dynamics of the number of DDoS attacks
Statistical analysis of specially prepared Linux servers — so-called honeypot traps — shows that peak botnet activity this quarter occurred during the pre- and post-holiday sales. Feverish cybercriminal activity was clearly observed around Black Friday and Cyber Monday, dying down by the second third of December.
The most significant peaks occurred on November 24 and 29, when the number of individual IPs storming our resources doubled. Some increase in activity was also observed in late October — most likely Halloween-related.
Such fluctuations point to attempts by cybercriminals to boost their botnets in the run-up to major sales. Pre-holiday periods are incubators of cybercriminal growth for two reasons: first, users are less discerning and more likely to “surrender” their devices to intruders; second, the prospect of a fast buck makes it possible to blackmail Internet companies with lost profits or to offer one’s services in the cut-throat struggle online.
Dynamics of the number of Linux-based attacks in Q4 in 2017*
*Shows changes in the number of unique IPs per 24 hours
Types and duration of DDoS attacks
In Q4, the share of SYN DDoS attacks decreased (from 60.43% to 55.63%) due to less activity by the Linux-based Xor DDoS botnet. These attacks still rank first, however. The percentage of ICMP attacks (3.37%), still the least common, also fell. The relative frequency of other types of attacks increased, but whereas in the previous quarter TCP attacks ranked second after SYN, UDP overshadowed both these types, rising from second-to-last to second-from-top (in Q4 UDP DDoS accounted for 15.24% of all attacks).
Kaspersky DDoS Protection annual statistics show a decline in the popularity of DDoS attacks involving only pure HTTP and HTTPS flooding. The frequency of multi-method attacks rose accordingly. Nevertheless, one in three mixed attacks contained an HTTP or HTTPS flood. This may be due to the fact that HTTP(S) attacks are quite expensive and complex, while in a mixed attack they can be used by cybercriminals to increase the overall effectiveness without additional costs.
Correlation between attack types according to Kaspersky DDoS Protection, 2016 and 2017
The longest attack in Q4 was significantly shorter than its Q3 counterpart: 146 hours (about 6 days) vs. 215 (about 9). That’s barely half the Q2 and 2017 record of 277 hours. Overall, the share of longish attacks continues to decline, albeit insignificantly. This also applies to attacks lasting 100-139 hours and 50-99 hours (the shares of these categories are so small that even a change of 0.01% is news). The most common are still micro-attacks, lasting no more than four hours: their share rose slightly to 76.76% (vs. 76.09% in Q3). Also up was the proportion of attacks lasting 10-49 hours, but again not by much — about 1.5%.
Distribution of DDoS attacks by duration (hours), Q3 and Q4 2017
C&C servers and botnet types
The top three countries by number of C&C servers remained as before: South Korea (46.63%), the US (17.26%), China (5.95%). Yet although the figures for the latter two climbed slightly against Q3, China had to share third place with Russia, which gained 2%, the reason being that despite the fact that the leaders’ share changed insignificantly percentage-wise, in absolute terms the number of C&C servers detected in all three countries almost halved. This is at least partially due to the termination of many Nitol botnet admin servers and the less active Xor botnet. On a separate note, this category’s top ten welcomed Canada, Turkey, and Lithuania (1.19% each), while Italy, Hong Kong, and Britain departed the list.
Distribution of botnet C&C servers by country, Q4 2017
The steady increase in the number of Linux-based botnets continued this quarter: their share now stands at 71.19% against Q3’s 69.62%. Accordingly, the share of Windows-based botnets fell from 30.38% to 28.81%.
Correlation between Windows- and Linux-based botnet attacks, Q4 2017
Conclusion
Q4 2017 represented something of a lull: both the number and duration of DDoS attacks were down against the previous quarter. The final three months of 2017 were even calmer than the first three. Alongside the rising number of multicomponent attacks involving various combinations of SYN, TCP Connect, HTTP flooding, and UDP flooding techniques, the emerging pattern suggests a backsliding for DDoS botnets in general. Perhaps the economic climate or tougher law enforcement has made it harder to maintain large botnets, causing their operators to switch tactics and start combining components from a range of botnets.
At the same time, the increase in the number of attacks on honeypot traps in the runup to holiday sales indicates that cybercriminals are keen to expand their botnets at the most opportune moment, looking to grab a slice of the pie by pressuring owners of online resources and preventing them from making a profit. In any event, the DDoS spikes around Black Friday and Cyber Monday were a salient feature of this quarter.
Another aspect of the late fall/early winter period was the continued attacks on cryptocurrency exchanges in line with the trends of the past months. Such fervor on the part of cybercriminals is not surprising given the explosive growth in the price of Bitcoin and Monero. Barring a collapse in the exchange rate (short-term fluctuations that only encourage speculators do not count), these exchanges are set to remain a prime target throughout 2018.
What’s more, the last quarter showed that not only are DDoS attacks a means to make financial or political gain, but can produce accidental side effects, as we saw last December with the junk traffic generated by the Lethic spam bot. Clearly, the Internet is now so saturated with digital noise that an arbitrary resource can be hit by botnet activity without being the target of the attack or representing any value whatsoever to the attackers.
WordPress Update Breaks Automatic Update Feature—Apply Manual Update
9.2.2018 thehackernews Vulnerebility
WordPress administrators are once again in trouble.
WordPress version 4.9.3 was released earlier this week with patches for a total 34 vulnerabilities, but unfortunately, the new version broke the automatic update mechanism for millions of WordPress websites.
WordPress team has now issued a new maintenance update, WordPress 4.9.4, to patch this severe bug, which WordPress admins have to install manually.
According to security site WordFence, when WordPress CMS tries to determine whether the site needs to install an updated version, if available, a PHP error interrupts the auto-update process.
If not updated manually to the latest 4.9.4 version, the bug would leave your website on WordPress 4.9.3 forever, leaving it vulnerable to future security issues.
Here's what WordPress lead developer Dion Hulse explained about the bug:
"#43103-core aimed to reduce the number of API calls which get made when the auto-update cron task is run. Unfortunately, due to human error, the final commit didn't have the intended effect and instead triggers a fatal error as not all of the dependencies of find_core_auto_update() are met. For whatever reason, the fatal error was not discovered before 4.9.3's release—it was a few hours after release when discovered."
The issue has since been fixed, but as reported, the fix will not be installed automatically.
Thus, WordPress administrators are being urged to update to the latest WordPress release manually to make sure they'll be protected against future vulnerabilities.
To manually update their WordPress installations, admin users can sign into their WordPress website and visit Dashboard→Updates and then click "Update Now."
After the update, make sure that your core WordPress version is 4.9.4.
However, not all websites being updated to the faulty update have reported seeing this bug. Some users have seen their website installed both updates (4.9.3 and 4.9.4) automatically.
Moreover, the company released two new maintenance updates this week, but none of them includes a security patch for a severe application-level DoS vulnerability disclosed last week that could allow anyone to take down most WordPress websites even with a single machine.
Since WordPress sites are often under hackers target due to its wide popularity in the content management system (CMS) market, administrators are advised to always keep their software and plugins up-to-date.
New Point-of-Sale Malware Steals Credit Card Data via DNS Queries
9.2.2018 thehackernews Virus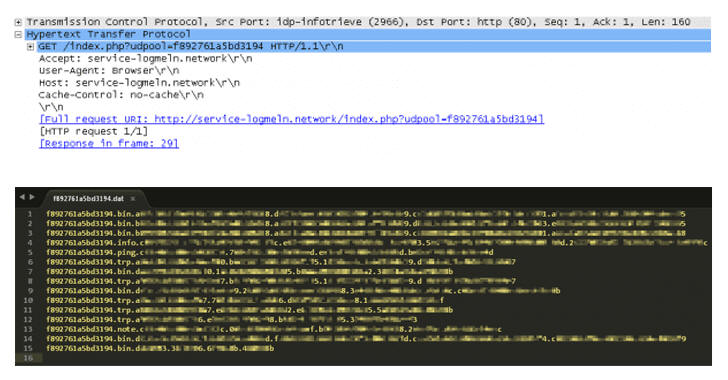
Cybercriminals are becoming more adept, innovative, and stealthy with each passing day. They are now adopting more clandestine techniques that come with limitless attack vectors and are harder to detect.
A new strain of malware has now been discovered that relies on a unique technique to steal payment card information from point-of-sale (PoS) systems.
Since the new POS malware relies upon User Datagram Protocol (UDP) DNS traffic for the exfiltration of credit card information, security researchers at Forcepoint Labs, who have uncovered the malware, dubbed it UDPoS.
Yes, UDPoS uses Domain Name System (DNS) queries to exfiltrate stolen data, instead of HTTP that has been used by most POS malware in the past. This malware is also thought to be first of its kind.
Besides using 'unusual' DNS requests to exfiltrate data, the UDPoS malware disguises itself as an update from LogMeIn—a legitimate remote desktop control service used to manage computers and other systems remotely—in an attempt to avoid detection while transferring stolen payment card data pass firewalls and other security controls.
"We recently came across a sample apparently disguised as a LogMeIn service pack which generated notable amounts of 'unusual' DNS requests," Forcepoint researchers said in a blogpost published Thursday.
"Deeper investigation revealed something of a flawed gem, ultimately designed to steal magnetic stripe payment card data: a hallmark of PoS malware."
The malware sample analyzed by the researchers links to a command and control (C&C) server hosted in Switzerland rather than the usual suspects of the United States, China, Korea, Turkey or Russia. The server hosts a dropper file, which is a self-extracting archive containing the actual malware.
It should be noted that the UDPoS malware can only target older POS systems that use LogMeIn.
Like most malware, UDPoS also actively searches for antivirus software and virtual machines and disable if find any. The researchers say it's unclear "at present whether this is a reflection of the malware still being in a relatively early stage of development/testing."
Although there is no evidence of the UDPoS malware currently being in use to steal credit or debit card data, the Forcepoint's tests have shown that the malware is indeed capable of doing so successfully.
Moreover, one of the C&C servers with which the UDPoS malware sample communicates was active and responsive during the investigation of the threat, suggesting the authors were at least prepared to deploy this malware in the wild.
It should be noted that the attackers behind the malware have not been compromised the LogMeIn service itself—it's just impersonated. LogMeIn itself published a blogpost this week, warning its customers not to fall for the scam.
"According to our investigation, the malware is intended to deceive an unsuspecting user into executing a malicious email, link or file, possibly containing the LogMeIn name," LogMeIn noted.
"This link, file or executable isn't provided by LogMeIn and updates for LogMeIn products, including patches, updates, etc., will always be delivered securely in-product. You'll never be contacted by us with a request to update your software that also includes either an attachment or a link to a new version or update."
According to Forcepoint researchers, protecting against such threat could be a tricky proposition, as "nearly all companies have firewalls and other protections in place to monitor and filter TCP- and UDP-based communications," but DNS is still often treated differently, providing a golden opportunity for hackers to leak data.
Last year, we came across a Remote Access Trojan (RAT), dubbed DNSMessenger, that uses DNS queries to conduct malicious PowerShell commands on compromised computers, making the malware difficult to detect onto targeted systems.
A vulnerable driver: lesson almost learned
9.2.2018 Kaspersky Vulnerebility
How not to use a driver to execute code with kernel privileges
Recently, we started receiving suspicious events from our internal sandbox Exploit Checker plugin. Our heuristics for supervisor mode code execution in the user address space were constantly being triggered, and an executable file was being flagged for further analysis. At first, it looked like we’d found a zero-day local privilege escalation vulnerability for Windows, but the sample that was triggering Exploit Checker events turned out to be the clean signed executable GundamOnline.exe, part of the multiplayer online game Mobile Suit Gundam Online from BANDAI NAMCO Online Inc.
The initial sample is packed using a custom packer and contains anti-analysis techniques that complicate static analysis. For example, it tries to detect if it’s being launched inside a virtual machine by performing a well-known VMware hypervisor detection routine. It first loads the EAX register with the hypervisor magic value VMXh, and the ECX register with the value 0x0A, which is a special command to receive the hypervisor version. Then it performs an ‘in’ command to the VMware hypervisor I\O port 0x5658. If the EBX register is overwritten with VMXh as a result of that operation, it means the executable file is running on the VMware machine.
Our sandbox execution logs showed that the user space memory page is called from the driver bandainamcoonline.sys immediately after IOCTL request 0xAA012044 to device object \\.\Htsysm7838 that is created by the driver. The driver itself is installed just before that. It is first dropped to the directory C:\Windows\SysWOW64\ by a GundamOnline executable, loaded using NtLoadDriver() and deleted immediately afterwards.
Normally, this kind of behavior should not be allowed due to SMEP (Supervisor Mode Execution Prevention). This is a security feature present on the latest Intel processors that restricts supervisor mode execution on user memory pages. Page type is determined using the User/Supervisor flag in the page table entry. If a user memory page is called while in supervisor execution mode, SMEP generates an access violation exception and, as a result, the system will trigger a bug check and halt. This is commonly referred to as a BSOD.
The dropped driver itself is a legitimate driver, signed with a certificate issued to NAMCO BANDAI Online Inc.
The certificate validity period tells us two things. First, this certificate has been valid since 2012, which could mean that the first vulnerable version of the driver was released around the same time. However, we were unable to find one; the earliest sample of bandainamcoonline.sys that we found dates back to November 2015. Secondly, because it expired more than three years ago, you could be forgiven for thinking it’s impossible to install a driver signed with this certificate in a system. Actually, there’s nothing stopping you from installing and loading a driver with an expired certificate validity period.
In order to find the cause of the heuristics trigger, we need to do a static analysis of the driver itself. In the DriverEntry function it first decodes the device object name string in memory, and then creates the device \\.\Htsysm7838. The other two encoded strings – bandainamcoonline and bandainamcoonline.sys – are not used in the driver.
The driver itself is very small and contains only three registered major functions. Function IRP_MJ_DEVICE_CONTROL, which handles requests, accepts only two IOCTLs: 0xAA012044 and 0xAA013044. When called, it checks the size of the input and output buffers and eventually calls the ExecuteUserspaceCode function, passing on the contents of the input buffer to it.
The function ExecuteUserspaceCode performs a single check on the input buffer, which contains a pointer to a user space function or a shellcode, and disables SMEP while saving old CR4 register values. It then calls that function, passing it a pointer to the MmGetSystemRoutineAddress as an argument. After that it restores the original register state, re-enabling SMEP.
To be able to directly call the user function from the provided pointer driver it is necessary to remove a specific bit in the CR4 register first to temporarily stop SMEP, which is what the DisableSMEP function does. The original CR4 values are then restored by the EnableSMEP function.
The vulnerability in this case is that other than the basic checks on the format of the input buffer, no additional checks are done. Therefore, any user on the system can use this driver to elevate their privileges and execute arbitrary code in the Ring 0 of the OS. Even if the driver is not present in the system, an attacker can register it with Windows API functions and exploit the flaw.
We realized that this vulnerability looks exactly like the one found in Capcom’s driver last year.
Binary diffing bandainamcoonline.sys and capcom.sys proves exactly that, showing there are almost no differences between the two drivers. The only slight variations are the encoded strings and digital signatures. Because the earliest sample of the vulnerable driver that we’ve been able to find dates to November 2015, it can be assumed that this vulnerability first appeared in the bandainamcoonline.sys driver – almost a year before a similar driver was used by Capcom.
We believe both drivers were almost certainly compiled from the same source code, as a part of an anti-hacking solution to prevent users from cheating in the game. The presence of functions that implicitly disable and re-enable SMEP show that this design decision was intentional. But because the driver makes no additional security checks, any user can call and exploit the vulnerable IO control code by using Windows APIs such as DeviceIoControl(). This essentially makes the driver a rootkit, allowing anyone to interact with the operating system at the highest privilege level. In fact, we found multiple malware samples (already detected by our products) using a previously known vulnerability in capcom.sys to elevate their privileges to System level.
After finding the vulnerability we contacted BANDAI NAMCO Online Inc. The vendor responded promptly and released a patch three days later. They removed the driver altogether, and it is no longer loaded by the game executable. This is very similar to what Capcom did, and is perfectly acceptable in this case.
Finding this vulnerability wouldn’t have been possible without our Exploit Checker technology, which is a plugin for our sandbox, and can be also found in KATA (Kaspersky Anti Targeted Attack Platform). The technology was designed to monitor suspicious events that occur at the earliest post-exploitation phases and can detect common techniques used in exploits, such as ROP, Heap Spray, Stack Pivot, and so on. In this particular case, multiple heuristics for executing code in supervisor mode in the user address space were triggered, and the sample was flagged for further analysis. If a token-swapping attempt was performed to elevate process privileges, a technique that’s widely used in LPE exploits, it would have been automatically detected by Exploit Checker heuristics.
Kaspersky Lab solutions detect the vulnerable drivers mentioned in this article as HEUR:HackTool.Win32.Banco.a and HEUR:HackTool.Win32.Capco.a.
Zerodium Offers $45,000 for Linux 0-Days
9.2.2018 securityweek IT
Hackers willing to find unpatched vulnerabilities in the Linux operating system and report them to exploit acquisition firm Zerodium can earn up to $45,000 for their findings, the company announced on Thursday.
The company has been long acquiring vulnerabilities in Linux as part of its normal payouts program, but it would normally pay only up to $30,000 for Local Privilege Escalation flaws in the operating system. Until March 31, 2018, however, such flaws can earn hackers up to 50% more, Zerodium said on Twitter.
Zerodium
✔
@Zerodium
Got a Linux LPE? Working with default installations of Ubuntu, Debian, CentOS/RHEL/Fedora? We are increasing our payouts to $45,000 per #0day exploit until March 31st, 2018. To submit, please check: https://zerodium.com/submit.html
4:03 PM - Feb 8, 2018
46
43 people are talking about this
Twitter Ads info and privacy
Zerodium claims that hackers who submit valid zero-day vulnerabilities in products of interest would receive payment for their efforts within a week after the initial submission.
The exploit acquisition firm is targeting vulnerabilities in the most commonly used Linux distributions and interested hackers can head over to its website to learn specific information on what is considered an eligible submission.
The payments promised for Linux vulnerabilities, however, aren’t the highest the company offers.
On desktop platforms, remote code execution flaws in Windows can earn the reporting hacker up to $300,000. Those who discover unpatched vulnerabilities in mobile operating systems can make up to $1,500,000, if the bug affects Apple’s iOS platform.
In fact, Zerodium is already known to have paid a group of hackers $1 million for a zero-day in iOS.
In August 2017, Zerodium announced it was prepared to pay up to $500,000 for unpatched vulnerabilities in popular instant messaging and email applications. The offer remains active in its current program.
In September last year, the company announced it was willing to pay up to $1 million for zero-day flaws in the Tor Browser. The “bounty” program ended in December 2017, but Zerodium wouldn’t provide information on the results of the operation.
Once in the possession of vulnerabilities it considers of interest, the company sells them to its customers as part of the Zerodium Zero-Day Research Feed. The company also says it analyzes, aggregates, and documents the acquired security intelligence before offering it, along with protective measures and security recommendations, to its clients.
New PoS Malware Family Discovered
9.2.2018 securityweek Virus
Researchers have discovered a new Point of Sale (POS) malware. They cannot tell yet whether it is new code still being developed, or already used -- complete with coding errors -- in an undetected campaign. They suspect the latter.
PoS malware has been responsible for a number of high profile data breaches over the last few years, including Hyatt Hotels, Chipotle Mexican Grill, Avanti Markets, and Sonic Drive-In. The growing use of EMV (chip & pin) payment cards in the U.S. makes card-present fraud more difficult. It was always expected that this would drive criminals towards card-not-present (that is, online) fraud; making the online theft of card details more attractive.
Forcepoint researchers Robert Neumann and Luke Somerville described the malware in a blog analysis posted today. "This appears to be a new family which we are currently calling 'UDPoS' owing to its heavy use of UDP-based DNS traffic." The researchers are not overly impressed by the quality of the coding, describing it as 'a flawed gem' -- where 'flawed' refers to the coding and 'gem' to the excitement of discovering a new needle in the haystack of old malware.
The malware uses a 'LogMeIn' theme as camouflage. The C2 server is service-logmeln.network (with an 'L' rather than an 'I') hosting the dropper file, update.exe. This is a self-extracting 7-Zip archive containing LogmeinServicePack_5.115.22.001.exe and logmeinumon.exe. The former, the service component of the malware, is run automatically by 7-Zip on extraction.
This service component is responsible for setting up its own folder, and establishing persistence. It then passes control to the second, or monitoring, component by launching logmeinumon.exe. The two components have a similar structure, and use the same string encoding technique to hide the name of the C" server, filenames and hard-coded process names.
The monitor component creates five different threads after attempting an anti-AV and virtual machine check and either creating or loading an existing ‘Machine ID'. The Machine ID is used in all the malware's DNS queries. The anti-AV/VM process is flawed, attempting to open only one of several modules.
When first run, the malware generates a batch file (infobat.bat) to fingerprint the infected device, with details written to a local file before being sent to the C2 server via DNS. The precise reason for this is unclear, but the researchers note, "The network map, list of running processes and list of installed security updates is highly valuable information."
Deeper analysis of the malware revealed a process designed to collect Track 1 and Track 2 payment card data by scraping the memory of running processes. "These processes," say the researchers, "are checked against an embedded and pre-defined blacklist of common system process and browser names with only ones not present on the list being scanned."
If any Track 1/2 data is found, it is sent to the C2 server. A log is also created and stored, "presumably," say the researchers, "for the purpose of keeping track of what has already been submitted to the C2 server."
When the researchers attempted to find additional samples of the same malware family, all they found was a different service component but without a corresponding monitor component. This one had an 'Intel' theme rather than a 'LogMeIn' theme. It was compiled at the end of September 2017, two weeks before the compilation stamp of October 11, 2017 for the LogMeIn components.
"Whether this is a sign that authors of the malware were not successful in deploying it at first or whether these are two different campaigns cannot be fully determined at this time due to the lack of additional executables," note the authors.
They warn that legacy PoS systems -- which can number thousands in large retailers -- are often based on variations of the Windows XP kernel. "While Windows POSReady is in extended support until January 2019, it is still fundamentally an operating system which is seventeen years old this year."
They urge sysadmins to monitor unusual activity patterns; in this case, DNS traffic. "By identifying and reacting to these patterns, businesses -- both PoS terminal owners and suppliers -- can close down this sort of attack sooner."
Austin, Texas based Forcepoint, originally known as Raytheon/Websense, was created in a $1.9 billion deal involving Raytheon, Websense and Vista Equity Partners in April 2015. It was renamed to Forcepoint in January 2016.
Actor Targeting Middle East Shows Excellent OPSEC
9.2.2018 securityweek Krypto
An actor making extensive use of scripting languages in attacks on targets in the Middle East demonstrates excellent operational security (OPSEC), researchers from Talos say.
As part of these targeted attacks allegedly confidential decoy documents supposedly written by the Jordanian publishing and research house Dar El-Jaleel were used, as well as VBScript, PowerShell, and VBA scripts that would dynamically load and execute functions retrieved from a command and control (C&C) server.
The threat actor(s) was particularly careful to camouflage the infrastructure and used several reconnaissance scripts to check the validity of victim machines. The actor was observed blocking systems that didn't meet their criteria, filtering connections based on their User-Agent strings, and hosting the infrastructure on CloudFlare.
Attacks start with a VBScript designed to create a second stage PowerShell script that would create a Microsoft Office document and to open it. The document was purportedly written by Dar El-Jaleel, an institute well-known for their research of the Palestinian-Israeli conflict and the Sunni-Shia conflict in Iran.
Supposedly a confidential analysis report on Iranian activities within the Syrian civil war, the document contains a macro designed to create a WSF (Windows Script File) file and to execute it. The WSF script, Talos discovered, is the main part of the infection and contains a User-Agent used to identify the targets.
The script first registers the infected system with a command and control server and executes an infinite loop, trying to contact the /search URI every 5 seconds to download and execute payloads.
These payloads are of three types, but all are VBScript functions loaded and executed on the fly using the ExecuteGlobal() and GetRef() APIs, differentiated by the number of arguments supplied: none, one, or two. The security researchers received five different functions, all obfuscated.
A reconnaissance function was received a few minutes after the initial compromise, meant to retrieve information from the infected system: disk volume serial number, installed anti-virus software, Internet IP address, computer name, username, Operating System, and architecture. All data is sent to the C&C. A second reconnaissance function was used to list the drives of the system and their type.
Two functions meant to achieve persistence for the WSF script were received as well: one script was used to persist, while the second was meant to clean the infected system.
The system also received a pivot function, which was meant to execute a PowerShell script. In turn, the script would execute a second base64 encoded script.
One last PowerShell script served to the system was meant to download shellcode from 176[.]107[.]185[.]246 IP, map it in memory, and execute it. While the shellcode wasn’t retrieved during investigation, the process revealed the many precautions the attacker takes before delivering the payload.
The attacker’s C&C is protected by CloudFlare, which makes it difficult to track and analyze the campaign. The researchers noticed that the actor was active during the morning (Central European Time zone), and that payloads were only sent during that time.
Furthermore, the attacker’s server becomes unreachable after serving the shellcode (the firewall is disabled for a few minutes to allow the download to go through). The actor was also observed blacklisting some of the researchers’ specific User-Agent strings and IP addresses.
“This high level of OPSEC is exceptional even among presumed state sponsored threat actors,” Talos notes.
The VBScript used during this campaign shows similarities to Jenxcus (also known as Houdini/H-Worm), but the researchers are not sure whether the actor used “new version of Jenxcus or if this malware served as the inspiration for their own malicious code.”
While Jenxcus’ source code is available on the Internet, the adaptation observed in these attacks is more advanced, with the functions loaded on demand and the initial script including only parts of the code, not all of it.
The security researchers were also able to identify different targets based on the User-Agent and say that targeted campaigns using Dar El-Jaleel decoy documents were observed before. In fact, the same decoy documents were observed in several attacks in 2017, but it is not clear if the same actor is behind all of them.
“These campaigns show us that at least one threat actor is interested in and targeting the Middle East. Due to the nature of the decoy documents, we can conclude that the intended targets have an interest in the geopolitical context of the region,” Talos notes.
Philippine Bank Threatens Counter-Suit Over World's Biggest Cyber-Heist
9.2.2018 securityweek Cyber
The Philippine bank used by hackers to transfer money in the world's biggest cyber heist warned of tit-for-tat legal action Thursday, after Bangladeshi officials said they would sue the lender.
Unidentified hackers stole $81 million from the Bangladesh central bank's account with the US Federal Reserve in New York two years ago, then transferred it to a Manila branch of the Rizal Commercial Banking Corp (RCBC).
The funds were then swiftly withdrawn and laundered through local casinos.
Bangladeshi officials said Wednesday they are readying a case against RCBC for its alleged role in the heist.
One of the officials, Bangladesh's Finance Minister A.M.A Muhith, said last year he wanted to "wipe out" RCBC.
But RCBC maintained the February 2016 cyber-heist was an "inside job" and that the Philippine bank was being used as a scapegoat to hide the real culprits.
RCBC, one of the Philippines' largest banks, charged that Bangladeshi officials were hiding their own findings into the crime, possibly to conceal the involvement of their own officials in the heist.
"RCBC has had it and will consider a lawsuit against Bangladesh Central Bank officials for claiming the bank had a hand in the $81M cyber-heist," the Philippine lender said in a statement.
"They are perpetuating the cover-up and using RCBC as a scapegoat to keep their people in the dark," the RCBC statement said.
The Philippine central bank imposed a record $21 million fine on RCBC after the discovery of the heist as it investigated the lender's alleged role in the theft.
Only a small amount of the stolen money has been recovered.
Money-laundering charges were also filed against the RCBC branch manager.
The US reserve bank, which manages the Bangladesh Bank reserve account, has denied its own systems were breached.
Flaws Affecting Top-Selling Netgear Routers Disclosed
9.2.2018 securityweek Vulnerebility
Security firm Trustwave has disclosed the details of several vulnerabilities affecting Netgear routers, including devices that are top-selling products on Amazon and Best Buy.
The flaws were discovered by researchers in March 2017 and they were patched by Netgear in August, September and October.
One of the high severity vulnerabilities has been described as a password recovery and file access issue affecting 17 Netgear routers and modem routers, including best-sellers such as R6400, R7000 (Nighthawk), R8000 (Nighthawk X6), and R7300DST (Nighthawk DST).Vulnerabilities in Netgear Nighthawk routers
According to Trustwave, the web server shipped with these and other Netgear routers has a resource that can be abused to access files in the device’s root directory and other locations if the path is known. The exposed files can store administrator usernames and passwords, which can be leveraged to gain complete control of the device.
An unauthenticated attacker can exploit the flaw remotely if the remote management feature is enabled on the targeted device. Improperly implemented cross-site request forgery (CSRF) protections may also allow remote attacks.
Another high severity flaw affecting 17 Netgear routers, including the aforementioned best-sellers, can be exploited by an attacker to bypass authentication using a specially crafted request. Trustwave said the vulnerability can be easily exploited.

A flaw that can be exploited to execute arbitrary OS commands with root privileges without authentication has also been classified as high severity. Trustwave said command injection is possible through a chained attack that involves a CSRF token recovery vulnerability and other weaknesses.
Two other command injection vulnerabilities have been found by Trustwave researchers, but they have been rated medium severity and they only affect six Netgear router models.
One of the flaws requires authentication, but experts pointed out that an attacker can execute arbitrary commands after bypassing authentication using the aforementioned authentication bypass vulnerability.
The other medium severity command injection is related to the Wi-Fi Protected Setup (WPS). When a user presses the WPS button on a Netgear router, a bug causes WPS clients to be allowed to execute arbitrary code on the device with root privileges during the setup process.
“In other words, if an attacker can press the WPS button on the router, the router is completely compromised,” Trustwave said in an advisory.
Netgear has put a lot of effort into securing its products, especially since the launch of its bug bounty program one year ago. In 2017, the company published more than 180 security advisories describing vulnerabilities in its routers, gateways, extenders, access points, managed switches, and network-attached storage (NAS) products.
VMware Addresses Meltdown, Spectre Flaws in Virtual Appliances
9.2.2018 securityweek Vulnerebility
VMware has started releasing patches and workarounds for the Virtual Appliance products affected by the recently disclosed CPU vulnerabilities known as Meltdown and Spectre.
According to an advisory published on Thursday, Meltdown and Spectre impact several VMware Virtual Appliances, including vCloud Usage Meter (UM), Identity Manager (vIDM), vCenter Server (vCSA), vSphere Data Protection (VDP), vSphere Integrated Containers (VIC) and vRealize Automation (vRA).
VMware has so far released a patch only for its VIC product, and workarounds have been made available for UM, vIDM, vCSA, and vRA. vCSA 5.5 is not affected, and neither patches nor workarounds have been released for VDP.
VMware has released separate advisories describing the specific workarounds for each product. The company advised users not to apply workarounds to other products than the one they are intended for, and pointed out that the workarounds are only meant to be a temporary solution until permanent fixes become available.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data. Billions of devices using Intel, AMD, ARM, Qualcomm and IBM processors are affected.
Intel started releasing microcode updates for its processors shortly after the flaws were disclosed, but the company decided to halt updates due to frequent reboots and unpredictable system behavior.
Following Intel’s announcement, VMware informed customers that it had decided to delay new releases of microcode updates for its ESXi hypervisor until the chipmaker addresses problems.
Intel announced this week that it has identified the root of an issue that caused systems to reboot more frequently and started releasing a new round of patches.
Intel and AMD told customers that their future products will include built-in protections for exploits such as Specter and Meltdown.