
Pyeongchang – Olympic Destroyer Unleashed to Embarrass Pyeongchang 2018 Games
13.2.2018 securityaffairs Cyber
Shortly before the Pyeongchang opening ceremonies on Friday, televisions at the main press centre, wifi at the Olympic Stadium and the official website were taken down.
It is well known that big events attract the attention of hackers. The biggest event right now is the 2018 Winter Olympics in Pyeongchang, South Korea and it looks like the hackers have arrived. Shortly before the opening ceremonies on Friday, televisions at the main press centre, wifi at the Olympic Stadium and the official website were taken down. All systems were restored by 8AM on the following Saturday, and although individuals were unable to print event tickets during the outage, the organizing committee described the event as affecting only “noncritical systems.” Given the high profile of the games, the rumor mill immediately began spreading whispers that the outage was the result of a cyberattack.
After restoring services and investigating the cause, Sunday evening Pyeongchang 2018 spokesperson Sung Baik-you issued an official statement confirming that the outage resulted from a cyber attack.
“There was a cyber-attack and the server was updated yesterday during the day and we have the cause of the problem”, Sung Baik-you said.
Leading up to the Olympic Games there was a lot of speculation whether North Korea would attempt to disrupt the games. Along with China and Russia, North Korean cyberwarfare teams are often suspected in large-scale attack such as these. In this case, the International Olympics Committee (IOC) is refusing to participate in any speculation as to the source of the attacks.
“We wouldn’t start giving you the details of an investigation before it has come to an end, particularly because it involves security which at these games is incredibly important. I am sure you appreciate we need to maintain the security of our systems,” said Mark Adams, head of communications for the IOC.
While the IOC and Pyeongchang spokespeople are being cautious about releasing details to focus on ensuring security and safety of the games, Cisco Talos has been forthcoming with technical details of the attack. While they haven’t pointed fingers at specific attackers, but in a Talos blog post on February 12, they have stated, “[samples identified] are not from adversaries looking for information from the games but instead they are aimed to disrupt the games.”

According to their research, there are many similarities between the Pyeongchang attack, which they are dubbing “Olympic Destroyer”, and earlier attacks such as BadRabbit and NotPetya. All of these attacks are focused on destruction and disruption of equipment not exfiltration of data or other, more subtle attacks. Using legitimate tools such as PsExec and WMI the attackers are specifically targeting the pyeongchang2018.com domain attempting to steal browser and system credentials to move laterally in the network and then wiping the victim computer to make it unusable.
While the source of the attacks is uncertain, the Cisco Talos blog post is clear in identifying motivation, “Disruption is the clear objective in this type of attack and it leaves us confident in thinking that the actors behind this were after embarrassment of the Olympic committee during the opening ceremony.”
Victims of some versions of the Cryakl ransomware can decrypt their files for free
13.2.2018 securityaffairs Ransomware
Free decryption keys for the Cryakl ransomware were added to the free Rakhni Decryptor that could be downloaded on the NoMoreRansom website.
The Belgian Federal Police has located the command and control server used by a criminal organization behind the Cryakl ransomware. The server was located in an unspecified neighboring country, law enforcement seized it and shared the decryption keys found on the machine with the No More Ransom project.
“The Belgian Federal Police is releasing free decryption keys for the Cryakl ransomware today, after working in close cooperation with Kaspersky Lab. The keys were obtained during an ongoing investigation; by sharing the keys with No More Ransom the Belgian Federal Police becomes a new associated partner of the project – the second law enforcement agency after the Dutch National Police.” reads the statement published by the Europol.
“Led by the federal prosecutor’s office, the Belgian authorities seized this and other servers while forensic analysis worked to retrieve the decryption keys. Kaspersky Lab provided technical expertise to the Belgian federal prosecutor and has now added these keys to the No More Ransom portal on behalf of the Belgian federal police. This will allow victims to regain access to their encrypted files without having to pay to the criminals.”
The “exponential” rise in Ransomware threat represents a serious problem for users online and it is a profitable business for cyber criminals. The operation NO More Ransom is the response of the Europol of the growing threat.

Victims of Cryakl ransomware can recover encrypted files using the Rakhni Decryptor available for free from Kaspersky Lab or NoMoreRansom at the following URL.
The tool works with most versions of the Cryakl ransomware, but researchers at MalwareHunterTeam confirmed that it doesn’t work with CL 1.4.0 and newer (so 1.4.0 is included in what can’t be decrypted).
It has been estimated that the tool has helped more than 35,000 victims of ransomware to decrypt their files for free, an overall loss for crooks of over €10m.
“There are now 52 free decryption tools on www.nomoreransom.org, which can be used to decrypt 84 ransomware families. CryptXXX, CrySIS and Dharma are the most detected infections.” continues the statement.
The Belgian authorities are still investigating the case.
Lenovo Patches Critical Wi-Fi Vulnerabilities
12.2.2018 securityweek Vulnerebility
Lenovo has released patches for two critical vulnerabilities that were found last year in certain Broadcom Wi-Fi controllers.
Identified as CVE-2017-11120 and CVE-2017-11121, the two issues were discovered by Google Project Zero and were publicly disclosed in September 2017.
Both vulnerabilities affect Broadcom Wi-Fi chips found in many mobile devices, thus having an industry-wide impact. Both were addressed in the Android and iOS operating systems in September last year.
When disclosing the bugs, Gal Beniamini of Google Project Zero explained that an attacker within Wi-Fi range could exploit CVE-2017-11120, an out-of-bounds write issue, to achieve arbitrary code execution on an impacted device.
“Upon successful execution of the exploit, a backdoor is inserted into the firmware, allowing remote read/write commands to be issued to the firmware via crafted action frames (thus allowing easy remote control over the Wi-Fi chip),” the researcher said.
CVE-2017-11121 can be abused by means of malicious over-the-air Fast Transition frames designed to trigger internal Wi-Fi firmware heap and/or stack overflows. This could lead to remote code execution as well.
“Broadcom has issued an advisory for certain Broadcom WiFi controllers used by many computer and device makers, which contain buffer overflow vulnerabilities on the adapter (not the system CPU),” Lenovo noted in an advisory last week.
The computer maker also notes that, while it “initially did not plan to remediate these issues,” Broadcom released patches after the WPA2 KRACK vulnerability became public, to address both bugs.
“Lenovo received the first of these near the end of 2017, and continues releasing fixes as integration and testing is completed,” the company says.
Lenovo explains that only its ThinkPad products pack the affected Broadcom WiFi controllers. The computer maker also published a list of all impacted ThinkPad devices and recommends users to update to the WiFi driver version (or newer) indicated for their models.
IBM Releases Spectre, Meltdown Patches for Power Systems
12.2.2018 securityweek Vulnerebility
IBM has released firmware and operating system updates to address the Meltdown and Spectre vulnerabilities in the company’s Power Systems servers.
IBM started releasing firmware patches for its POWER processors within a week after the Spectre and Meltdown attack methods were disclosed. Firmware updates were first released for the POWER7+ and POWER8 processors, but customers would have to wait another month for operating system patches.
The company announced late last week the availability of patches for remaining POWER processors, along with updates for its AIX and IBM i operating systems.
Firmware patches are now available for POWER7, POWER7+, POWER8 and POWER9 processors. Earlier versions will not receive updates as they have reached end of service and IBM recommends migrating to a supported generation.
The vulnerabilities that allow Meltdown and Spectre attacks (CVE-2017-5753, CVE-2017-5715 and CVE-2017-5754) have also been patched in IBM i with the release of program temporary fixes (PTFs) for versions 7.1, 7.2 and 7.3. Fixes have also been released for AIX 5.3, 6.1, 7.1 and 7.2, and VIOS 2.2.x.
Both firmware and operating system updates must be installed for efficient protection against Meltdown and Spectre attacks. However, it’s recommended that the firmware patches are applied prior to operating system updates.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data. Billions of devices using Intel, AMD, ARM, Qualcomm and IBM processors are affected.
Impacted vendors started releasing software and firmware patches shortly after the methods were disclosed, but both types of fixes caused problems.
A few weeks after it started releasing microcode patches, Intel decided to halt updates due to frequent reboots and unpredictable system behavior. The company now says it has identified the root cause of the problem and started releasing a new round of patches.
Intel and AMD told customers that their future products will include built-in protections for exploits such as Specter and Meltdown.
Crypto Mining Malware Infects Thousands of Websites
12.2.2018 securityweek CoinMine
Hacked Script Infects Several Government Sites with Cryptominer
The websites of numerous government, health and education organizations worldwide were infected with a crypto-currency miner over the weekend, after a script running on all of them was maliciously modified.
The culprit was Browsealoud, a script developed by Texthelp to add “speech, reading, and translation to websites.” The software was designed to provide access and participation to people with Dyslexia, Low Literacy, English as a Second Language, and to those with mild visual impairments, the company says.
Over the weekend, Texthelp was the target of a cyber-attack that resulted in a JavaScript file, part of the Browsealoud script, being modified. Because of that, Browsealoud would inject a Coinhive cryptojacking script into the visitors’ browsers, to turn them into crypto-currency mining machines.
“At 11:14 am GMT on Sunday 11th February 2018, a JavaScript file which is part of the Texthelp Browsealoud product was compromised during a cyber-attack. The attacker added malicious code to the file to use the browser CPU in an attempt to illegally generate cryptocurrency. This was a criminal act and a thorough investigation is currently underway,” the company revealed in a blog post.
As a result of this attack, numerous government websites in the United Kingdom, the United States, and Australia were infected with the crypto-mining software.
As Scott Helme, the researcher who noticed the malicious script quickly discovered, a total of 4275 websites were impacted in this attack, including prominent sites such as UK's Information Commissioner's Office, the NHS, the General Medical Council, U.S. Courts, academic websites, and many others.
“The ba.js had been altered to include a document.write call that added a CoinHive crypto miner to any page it was loaded in to. The sheer number of sites affected by this is huge and some of them are really prominent government websites,” Helme points out.
The reason so many websites were impacted isn’t only the ease of use Browsealoud promises, as admins only need to copy and paste one script to take advantage of it, but also regulatory requirements around accessibility that many sites need to comply with, especially government sites.
Soon after realizing the cause of the infection, Helme notified Texthelp, which decided to take Browsealoud offline, thus removing it from all of their customer sites immediately. The company claims that taking the product down allowed them to address the issue without requiring customers to take action.
“Texthelp can report that no customer data has been accessed or lost. The company has examined the affected file thoroughly and can confirm that it did not redirect any data, it simply used the computers CPUs to attempt to generate cryptocurrency. The exploit was active for a period of four hours on Sunday,” Martin McKay, CTO and Data Security Officer, Texthelp, says.
McKay also noted that, although the issue has been addressed, Browsealoud will remain offline until Tuesday, so that customers could be informed on the issue. He also pointed out that no other Texthelp products have been affected.
“A security review will be conducted by an independent security consultancy. The investigation is ongoing, and customers will receive a further update when the security investigated has been completed,” McKay concluded.
UK’s National Cyber Security Centre also said they were examining the incident.
“The affected service has been taken offline, largely mitigating the issue. Government websites continue to operate securely. At this stage there is nothing to suggest that members of the public are at risk,” the NCSC said.
However, it appears that the issue might have not been completely resolved, as Helme points out on Twitter. The researcher claims that even today the malicious script attempts to load when accessing the UK's Information Commissioner's Office website, likely from cache. This means that returning visitors might still be impacted.
NoMoreRansom: Free Decryption for Latest Cryakl Ransomware
12.2.2018 securityweek Ransomware
Decryption keys for a current version of Cryakl ransomware have been obtained and uploaded to the NoMoreRansom website. Victims of Cryakl can potentially recover encrypted files with the Rakhni Decryptor available for free from Kaspersky Lab or NoMoreRansom.
NoMoreRansom is a collaborative public/private project launched by Europol, the Dutch National Police, Kaspersky Lab and McAfee in July 2016. Its purpose is to help ransomware victims recover encrypted files through the use of decryptors. Since its launch, other national law enforcement agencies and additional private companies have joined the project. There are now 52 decryption tools available on the site, able to recover files from 84 ransomware families.
The project now comprises more than 120 partners, including more than 75 private organizations. The Cypriot and Estonian police are the most recent law enforcement agencies to join, while KPN, Telenor and The College of Professionals in Information and Computing (CPIC) have joined as new private sector partners. Europol claims that the site has enabled more than 35,000 ransomware victims to recover their files without paying a ransom – preventing criminals from profiting from more than €10 million.
The Rakhni Decryptor, developed by Kaspersky Lab, could already decrypt older versions of Cryakl – which first appeared in 2015. It could not, however, decrypt the latest version – which it now does.
The Belgian Federal Computer Crime Unit (FCCU) learned that Belgian citizens had been victims of this new version of Cryakl. It was able to locate a C2 server in an unspecified neighboring country. The Netherlands is one neighbor state that is often used by criminals to host their malicious servers.
“Led by the federal prosecutor's office,” announced Europol Thursday, “the Belgian authorities seized this and other servers while forensic analysis worked to retrieve the decryption keys.” Kaspersky Lab provided technical expertise, and has now included the recovered keys in its Rakhni Decryptor, uploaded on behalf of the Belgian authorities.
The Rakhni Decryptor, says Kaspersky Lab, “Decrypts files affected by Rakhni, Agent.iih, Aura, Autoit, Pletor, Rotor, Lamer, Cryptokluchen, Lortok, Democry, Bitman (TeslaCrypt) version 3 and 4, Chimera, Crysis (versions 2 and 3), Jaff, Dharma and new versions of Cryakl ransomware.”
The Belgian authorities are continuing their investigation into the operators of the seized C2 servers, but decided not to wait before making the recovered keys available to victims. It is, says Europol, “another successful example of how cooperation between law enforcement and internet security companies can lead to great results.”
CSE CybSec ZLAB Malware Analysis Report: Dark Caracal and the Pallas malware family
12.2.2018 securityaffairs Android
Dark Caracal APT – The Pallas Family
Researchers from CSE ZLAB malware Analysis Laboratory analyzed a set of samples of the Pallas malware family used by the Dark Caracal APT in its hacking operations.
The malware researchers from ZLab analyzed a collection of samples related to a new APT tracked as Dark Caracal, which was discovered by Electronic Frontier Foundation in collaboration with Lookout Mobile Security.
Dark Caracal has been active at least since 2012, but only recently it was identified as a powerful threat actor in the cyber arena.
The first analysis of the APT linked it to Lebanese General Directorate of General Security.
Dark Caracal is behind a number of stealth hacking campaigns that in the last six years, aimed to steal text messages, call logs, and files from journalists, military staff, corporations, and other targets in 21 countries worldwide.
One of their most powerful campaigns started in the first months of last year, using a series of trojanized Android applications to steal sensitive data from the victim’s mobile device. The trojan injected in these applications is known in the threat landscape with the name Pallas.
Threat actors use the “repackaging” technique to generate its samples, they start from a legitimate application and inject the malicious code before rebuilding the apk.
The target applications belongs to specific categories, such as social chat app (Whatsapp, Telegram, Primo), secure chat app (Signal, Threema), or software related to secure navigation (Orbot, Psiphon).
The attackers used social engineering techniques to trick victims into installing the malware. Attackers use SMS, a Facebook message or a Facebook post, which invites the victim to download a new version of the popular app through from a specific URL
http://secureandroid[.]info,
All the trojanized app are hosted at the same URL.

Figure 1 – Dark Caracal Repository – Malicious site
This malware is able to collect a large amount of data and to send it to a C&C through an encrypted URL that is decrypted at runtime. The capabilities of the trojan are:
Read SMS
Send SMS
Record calls
Read calls log
Retrieve account and contacts information
Gather all stored media and send them to C2C
Download and install other malicious software
Display a phishing window in order to try to steal credentials
Retrieve the list of all devices connected to the same network
Further details are included in the complete report published by CSE.
Thousands More Personal Records Exposed via Misconfigurations
12.2.2018 securityweek Incindent
Two more misconfigured databases exposing the personal details of thousands of people were disclosed late last week.
The Maryland Joint Insurance Association (MDJIA, with offices in Ellicott City, MD) left internet access to a data repository of customer files containing information such as customer names, addresses, phone numbers, birth dates, and full Social Security numbers; together with financial data such as check images, full bank account numbers, and insurance policy numbers. Also exposed were MDJIA access credentials for ISO ClaimSearch, a third-party insurance database containing ‘tens of millions of reports on individual insurance claims’ for industry professionals. The problem was a NAS server with an open port 9000.
Paris-based Octoly, a brand marketing firm, left open internet access to an AWS S3 bucket. This contained details of its IT operations, including sensitive personal details of more than 12,000 social media influencers used in its marketing campaigns. The details include the real names, addresses, phone numbers, email addresses – including those specified for use with PayPal – and birth dates, together with thousands of hashed passwords.
Both misconfigurations were discovered by Chris Vickery, the director of cyber risk research at UpGuard. Researcher Vickery has discovered numerous misconfigurations providing open access to sensitive, often personal, information over the last few years. Examples include details of 191 million U.S. voters, nearly 1.4 billion user records exposed by known spammers, and sensitive military data belonging to the U.S. National Geospatial-Intelligence Agency (NGA) left exposed by contractor Booz Allen Hamilton.
None of these misconfigurations require any hacking effort or skill to exploit, merely a computer with internet access. If a white hat researcher such as Vickery can find them, potentially any malicious actor could also find them with disastrous results. The question then is, why do misconfigurations, rated #6 in the OWASP top ten threats list, happen so frequently – and what should organizations do to prevent them?
Bryce Carlen; CIO at Washington State Department of Commerce, notes that MDJIA is a small organization with minimal – if any – dedicated IT staff. He warns that there may be many more small organizations in a similar position. “If this is as small an organization as it appears to be, then all of this is no real surprise. If you only have the budget for one or two IT staff or contractors, it's likely you're not going to have dedicated security staff or deep security expertise in the generalists you have working for you.” The problem, he added, is that small organizations don't understand the risks until after a cybersecurity event, because protecting data is not part of the core business based around using that data.
The Octoly incident is similar to many other examples of exposed AWS S3 buckets. “Every time I look at the AWS control panel, it seems like there are new services available, each of which comes with new settings and configuration switches. It's especially tough when you layer that on top of the constantly evolving job of securing your on-prem environment against shifting threats,” Carlen said.
He fears that the cloud is simply increasing 'security fatigue', leading to simple errors. “It's one of the things that frightens me about the cloud. There are a bunch of what appear to be otherwise competent organizations making a big mess with cloud configuration settings.”
Randy Potts, information security leader at Real Time Resolutions, Inc, believes the problem is still a missing 'culture of security' in many organizations. “Both of these incidents [last week] happened because the person that deployed them did not think about the bad actors. They only think about giving access to the people that need it, not preventing access from those that should not have it.”
He believes that it is the continuing point of tension between IT and information security. “IT is measured by uptime and functionality, but information security is measured by controlling access to data. From the IT perspective, information security risks breaking access and harming functionality.” He believes that IT personnel need to understand security better: “They need to respect that while not taking that extra step may save time now, it can have a serious impact to the organization later.”
But the problem goes beyond just IT and security into the entire corporate culture; that is, “the moral obligation that everyone handling sensitive information has to the people that correspond to that PII.” That includes the business owners as well as the IT staff and the security team.
This is a theme agreed by Graham Mann, managing director at CyberSpace Defence Ltd. “Management must shoulder their portion of the blame because they simply do not attach sufficient importance to security,” he says. He believes it is an area that can be addressed by legislation – indeed, it has already been addressed by the EU's General Data Protection Regulation (GDPR).
“GDPR specifically addresses the issues outlined in these so-called misconfiguration problems,” he told SecurityWeek; “and had Octoly happened five months later, they would now be facing a significant fine. Moreover, given the closeness of GDPR, it’s somewhat amazing that Octoly hasn't yet put measures in place to avoid such catastrophes.
“Misconfigurations are entirely feasible and easy to make when you are rushing to implement a device or making seemingly innocuous modifications to existing devices,” he continued. “Most IT administrators probably never consider the implications or consequences of making such errors. That’s why you need to consider the potential repercussions in advance (as specified in GDPR); you need to undertake a risk analysis on everything you do -- what could go wrong and what can we do to ensure any errors are mitigated. This is where management are critical: the involvement of security must be supported from above.”
Security researcher and consultant, Stewart Twynham, goes one step further. He believes the gaps between IT and security can be closed by treating both as aspects of corporate governance. “Professional IT people are under constant pressure to get things done, which is why security should be treated as a governance issue as well as an IT one,” he suggests. “Without those checks and balances (have we carried out the due diligence? do we fully understand the technology? do we understand the risks? do we have a process in place to continuously review what weíve set up?) mistakes like this will continue to happen.”
In short, misconfigurations will continue to occur while the pressure on IT to react instantly to business requirements goes unabated. Any alteration to the IT infrastructure should involve the security team before implementation. But this will require senior management to own the problem under an overarching corporate governance regime – and when that happens, misconfigurations will be less common.
New Details Surface on Equifax Breach
12.2.2018 securityweek Incindent
Documents provided recently by Equifax to senators revealed that the breach suffered by the company last year may have involved types of data not mentioned in the initial disclosure of the incident.
In mid-May 2017, malicious actors exploited a known vulnerability in the Apache Struts development framework to gain unauthorized access to Equifax systems. The company said the breach affected roughly 145 million customers – mostly in the U.S., but also in Canada and the United Kingdom – including their social security numbers, dates of birth, addresses, and in some cases driver’s license numbers, payment cards, and dispute documents.
Confidential documents sent by Equifax to the Senate Banking Committee, copies of which were seen by CNN and The Wall Street Journal, show that hackers may have also stolen tax identification numbers, email addresses, and driver’s license information other than just license numbers.
In response to news reports, Equifax said its initial disclosure was never intended to include all the types of information that may have been compromised.
U.S. Senator Elizabeth Warren has called on Equifax to provide clarifications on what she has described as “conflicting, confusing and incomplete information” provided by the company to the public and Congress.
According to Sen. Warren, Equifax told the Banking Committee in early October that passport numbers had also been included in the database tables possibly accessed by the attackers, but now the credit reporting agency claims passports were not compromised.
“As your company continues to issue incomplete, confusing and contradictory statements and hide information from Congress and the public, it is clear that five months after the breach was publicly announced, Equifax has yet to answer this simple question in full: what was the precise extent of the breach?” Sen. Warren wroten in a letter to Equifax.
The senator has given Equifax one week to provide a full and complete list of data elements confirmed or believed to have been compromised in the breach, along with a timeline of its efforts to determine the full extent of the intrusion.
Sen. Warren last week published a 15-page report containing the findings of her own four-month investigation into Equifax’s failures. The lawmaker’s investigation found that the company had set up a flawed system to prevent data security incidents, it ignored numerous warning of risks to customer data, it failed to disclose the breach to stakeholders in a timely manner, and provided inadequate assistance and information to consumers. The report also said Equifax had taken advantage of federal contracting loopholes to force the IRS into signing a contract.
Earlier this year, senators Warren and Mark Warner introduced a bill that would provide the Federal Trade Commission (FTC) with punitive powers over the credit reporting industry for poor cybersecurity practices. The bill came in response to the Equifax breach.
Reuters reported earlier this month that Mick Mulvaney, the head of the Consumer Financial Protection Bureau (CFPB), had halted the probe into the Equifax breach. Following the news, 32 senators sent a letter CFPB asking for additional information on its investigation.
49% of crypto mining scripts are deployed on pornographic related websites
12.2.2018 securityaffairs CoinMine
The number of crypto mining scripts discovered by security experts continues to increase, especially those ones illegally deployed by hacking servers online.
The experts from Qihoo 360’s Netlab analyzed crypto mining scripts online by analyzing DNS traffic with its DNSMon system. The experts were able to determine which sites load the scripts from domains associated with in-browser mining services.
According to the researchers, 49% of crypto mining scripts are deployed on pornographic related websites.
The study revealed that cryptocurrency mining scripts are also deployed on fraud sites (8%), advertising domains (7%), and cryptocurrency mining (7%).
“0.2% of websites have web mining code embedded in the homepage : 241 (0.24%) in Alexa Top 100,000 websites, 629 (0.21%) in Alexa Top 300,000 websites” reads the analysis published by NetLab.
“Pornographic related websites are the main body , accounting for 49% of these websites. Others include fraud (8%), advertising (7%), mining (7%), film and television (6%) and other categories”
The most used crypto mining script is Coinhive (68%+10%), followed by JSEcoin (9%). 
The fact that cryptocurrency mining scripts are most deployed on porn websites is not a surprise because they have a large number of visitors that used to spend a lot of time watching their content.
Mining activities online are rapidly increasing, the following graph shows the mining site DNS traffic trends:

Below the categories of new actors most involved in mining activities:
Advertisers : The mining activity of some websites is introduced by the advertisers’ external chains
Shell link : Some websites will use a “shell link” to obscure the mining site link in the source code
Short domain name service provider : goobo . COM .br Brazil is a short domain name service provider, the website home page, including a short domain name through the service generated when access to the link will be loaded coinhive mining
Supply chain contamination : the WWW . Midijs . NET is a JS-based MIDI file player, website source code used in mining to coinhive
Self-built pool : Some people in github open source code , can be used to build from the pool
Web users informed mining : authedmine . COM is emerging of a mining site, the site claims that only a clear case of known and authorized users, began mining
Thousands of websites worldwide hijacked by cryptocurrency mining code due Browsealoud plugin hack
12.2.2018 securityaffairs CoinMine
Thousands of websites worldwide hijacked by a cryptocurrency mining code due to the hack of the popular Browsealoud plugin.
A massive attack hit thousands of websites around the world, crooks deployed Coinhive scripts forcing them to secretly mine cryptocurrencies on visitors’ browsers.
The list of compromised websites (4275) includes the UK’s NHS, Information Commissioner’s Office (ICO) (ico.org.uk), the UK’s Student Loans Company (slc.co.uk), The City University of New York (cuny.edu), and the US government’s court system.
Once discovered the hack some sites web down, the ICO also took its website down.
The compromised websites use the Browsealoud plugin which makes their content accessible for blind or partially sighted people by reading it.
In a time-window of roughly seven hours (between 0300 and 1145 UTC), all the websites using Browsealoud inadvertently ran the Monero cryptocurrency mining code.
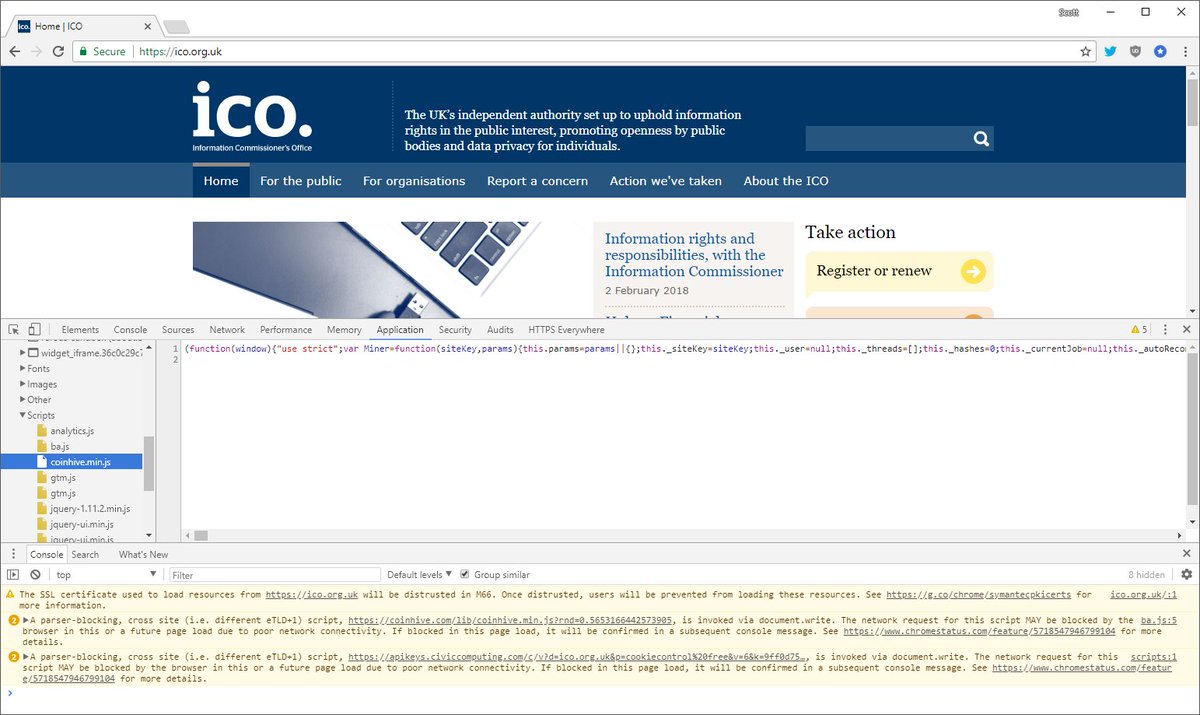
The attackers injected an obfuscated version of the mining code in the plugin that once converted from hexadecimal back to ASCII allowed to load the mining code in the webpage.

The alarm was thrown by the security expert Scott Helme who was contacted by a friend who sent him antivirus software warnings received after visiting a UK ICO website.
“This type of attack isn’t new – but this is the biggest I’ve seen. A single company being hacked has meant thousands of sites impacted across the UK, Ireland and the United States.” said Helme.
“Someone just messaged me to say their local government website in Australia is using the software as well.”
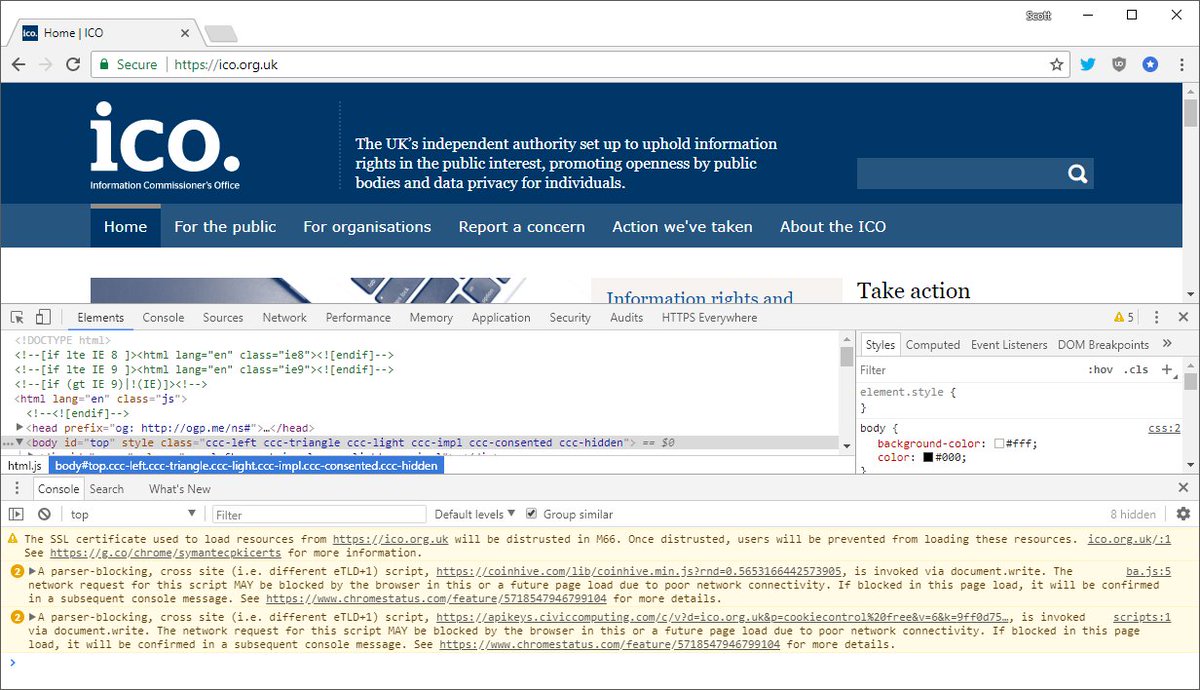
Scott Helme
✔
@Scott_Helme
Ummm, so yeah, this is *bad*. I just had @phat_hobbit point out that @ICOnews has a cryptominer installed on their site... 😮
2:46 PM - Feb 11, 2018
739
789 people are talking about this
Twitter Ads info and privacy
The expert suggests using the Subresource Integrity (SRI) technique to block unwanted code injected in affected websites.
Texthelp, the company that developed the Browsealoud plugin, has removed its Browsealoud code from the web to stop the cryptocurrency mining operation.
“In light of other recent cyber attacks all over the world, we have been preparing for such an incident for the last year and our data security action plan was actioned straight away,” said Texthelp’s chief technology officer Martin McKay in a statement.
“Texthelp has in place continuous automated security tests for Browsealoud, and these detected the modified file and as a result the product was taken offline.”
Texthelp confirmed that “no customer data has been accessed or lost,” and “customers will receive a further update when the security investigation has been completed.”
Texthelp for Edu
@texthelp
Our Data security investigation underway at Texthelp, statement on our website: http://okt.to/EtJobI
Browsealoud was automatically removed from all our customers' websites in response. No action needed by our customers.
10:20 PM - Feb 11, 2018
3
See Texthelp for Edu's other Tweets
Twitter Ads info and privacy
The malicious code was removed by 1600 UTC today, the UK’s ICO is currently in a minimal “maintenance” mode as a precaution.
U.S. Spies Bilked for $100,000 by Russian Peddling Trump Secrets: Report
11.2.2018 securityweek BigBrothers
A Russian man promising stolen hacking tools and compromising information on President Donald Trump fleeced American spies for $100,000 last year, The New York Times reported Friday.
In a story worthy of a John le Carre novel that included secret USB-drive handovers in a small West Berlin bar and coded messages delivered over the National Security Agency's Twitter account, CIA agents reportedly spent much of last year trying to buy back from the Russian hacking programs stolen from the NSA.
The seller, who was not identified but had links to both cyber criminals and Russian intelligence, tantalized the US spies with an offer of the NSA hacking tools that had been advertised for sale online by a shady group called the Shadow Brokers.
Some of the tools, developed by the NSA to break into the computers of US rivals, were used by other hackers last year to break into computer systems around the world, including the global malware attack last May.
The seller, reached through a chain of intermediaries, wanted $1 million.
The $100,000, delivered in a cash-stuffed suitcase handed over in a Berlin hotel room, was an initial payment by US agents still dubious he really had what he was promising.
- Trump kompromat -
The seller also repeatedly pressed US agents with offers of compromising materials, or kompromat, on Trump, the Times said, citing US and European intelligence officials.
Although an investigation was already underway back in Washington on the link between Moscow and the Trump campaign, the agents did not want to get involved in anything that smelled of the politics back home.
The story -- which was also reported by The Intercept, an online magazine on nationals security matters -- paints a classic spy versus spy story where the US agents aren't ever certain about who they are dealing with and whether or not they are being baited and played by their Russian counterparts.
US intelligence officials say Russia interfered with the 2016 election to help elect Trump, and continues to use disinformation to sow confusion in the American political system.
The Intercept reported that the operation created rifts in the CIA, which is led by Trump loyalist Mike Pompeo but has many staffers still smarting over the president's repeated harsh comments about the intelligence community's role in the Russia meddling investigation.
The Russian's first delivery turned out to be hacking tools the Shadow Brokers had already released.
And he kept pushing his offer of kompromat on Trump, including shady financial records and a sex video that the US spies didn't really want.
In the end, the deal broke down last month -- the Russian did not come up with any of the unreleased NSA materials, and the Trump-related materials were either already known or untrustworthy.
The Russian was told by the Americans to leave Western Europe and not return, according to the Times.