
90% of the SAP customers exposed to hack due to 13 Year-Old configuration flaw
29.4.2018 securityaffairs Vulnerebility
Many companies using SAP systems ignore to be impacted by a 13-year-old security configuration that could expose their architecture to cyber attacks.
According to the security firm Onapsis, 90 percent SAP systems were impacted by the vulnerability that affects SAP Netweaver and that can be exploited by a remote unauthenticated attacker who has network access to the system.
Because SAP Netweaver technology is the pillar for SAP solutions, including the SAP ERP and S/4 HANA, at least 378,000 users worldwide are affected.
“How critical is this vulnerability? SAP Netweaver installations, if not properly secured, could be compromised by a remote unauthenticated attacker having only network access to the system.” reads the report published by Onapsis says
“Attackers can obtain unrestricted access to SAP systems, enabling them to compromise the platform along with all of its information, modify or extract this information or shut the system down. It affects all SAP Netweaver versions and still exists within the default security settings on every Netweaver-based SAP product such as the SAP ERP, including the latest versions such as S/4HANA.”
The configuration relates to how components of the SAP infrastructure communicate, with a specific focus on Application Servers, SAP Message Servers, and the SAP Central Instance.

Every time a new app is created, the sysadmin must register the new app (Application Server) with the SAP Message Server, the registration is performed via internal port 39<xx> (3900 by default).
The SAP Message Servers implements an access control list (ACL) mechanism for the access to the registration port.
“The SAP Message Server implements a protection mechanism, also known as ACL or access control list, to check which IP addresses can register an application server and which ones cannot.” continues the report.
“This ACL is controlled by the profile parameter “ms/acl_info”. This parameter should contain a path to a file with the following format:
HOST=[*| ip-adr | hostname | Subnet-mask | Domin ] [, …]”
SAP published details on how to properly configure this access file in 2005 through SAP Security Note #8218752 ‘security settings in the message server.’
“Nevertheless, this parameter is set with default configuration, as well as the ACL contents open, allowing any host with network access to the SAP Message Server to register an application server in the SAP system.” continues the Onapsis’s report.
An attacker can exploit improper configuration of a secure Message Server ACL to register a fake Application Server that could be abused to gain full control of the SAP install.
The experts highlighted that the issue could be mitigated by properly configuring the SAP Message Server ACL.
Below the Step by step remediation provided by Onapsis:
Properly configure SAP Message Server ACL. SAP published instructions for this more than ten years ago, which confirms the need for more investment and education in SAP cybersecurity if this vulnerability is still present in your systems.
Implement continuous monitoring and compliance checks to validate that security-relevant configurations such as the Message Server ACL files do not change the security posture of the entire system.
Implement an SAP cybersecurity program that helps bridge the gap between teams: Align IT Security, Internal Audit, BASIS and SAP Security teams towards the unified goal of running secure SAP applications.
DDoS attacks in Q1 2018
29.4.2018 Kaspersky Attack
News overview
In early January, it was reported that an amateur hacker had come close to pulling off a botnet attack using “improvised” materials. Armed with information gleaned from hacker forums, the DIYer created a Trojan using a zero-day exploit in Huawei routers and released it online. The attack was soon nipped in the bud, but the wannabe cybercriminal could not be traced.
Other slightly weightier news: first, experts reported growth in the Reaper (or IoTroop) botnet (not to be confused with North Korean hacker group The Reaper), first discovered last quarter; second, IT security resources hinted at the emergence of new “strains” of Mirai and Satori (the latter, known as Okiru, is intended for ARC processors), but so far without details. Moreover, in early February a platform selling JenX botnet services was detected and neutralized. JenX was found to be using a fan server for the video game GTA: San Andreas as its C&C. In terms of power, JenX was nothing to write home about, but the originality of its creators deserves a mention. On the topic of original botnets, another worth noting is DoubleDoor: the first known piece of “wild” malware to bundle two IoT vulnerabilities together.
As for new methods and vulnerabilities, besides the multiget hole in Memcached, last quarter news broke of a vulnerability in WordPress that makes it easy to down a web server. Fortunately, no in-the-wild attacks were observed.
The attack targets for this new weaponry remained largely the same. Profit is still the main motive behind DDoS attacks (the number of attacks on business in Russia alone doubled in 2017), although high-profile “commercial” attacks in the last three months were not so numerous. Within the space of three days in early February, players of Final Fantasy encountered problems signing into certain services. At roughly the same time, BusinessWire experienced similar difficulties lasting more than a week, during which period neither editors nor readers could access the news portal. There was no reported ransom demand, so the motive behind the attack can be assumed to be competition-related.
It would be amiss not to mention a series of attacks that hit GitHub and an unknown service provider in early March, which produced record volumes of garbage traffic — over 1 TB/s. This capacity was achieved by leveraging Memcached, a popular caching service for Linux servers. Interestingly, in some of these attacks the garbage traffic itself contained ransom demands in Monero.
Political motives are less common, but often more visible due to their topicality. The most headlining incident of late was, of course, the threat to sabotage the opening ceremony of the Winter Olympics in early February, most likely through a DDoS offensive. Even before that, in late January, the US Department of Defense repelled an influx of spam, and in late March their Russian counterparts had to survive a DDOS attack. In addition, experts reported that North Korean group The Reaper was extending its reach. Despite not showing any DDoS activity, it could soon start moving in that direction.
Another hard-hitting DDoS attack on major financial institutions in the Netherlands was initially thought to be political, but on closer inspection turned out to be pure hooliganism: Dutch police arrested a teen suspect for causing week-long mayhem at several banks simply to prove that it was possible.
DDoS is also becoming more popular as a means of personal revenge. California, for instance, witnessed the case of David Goodyear, who was found guilty of trying to launch a DDoS attack against an amateur astronomy forum when it blacklisted him for using bad language. True, he can’t be accused of not trying other methods before turning his hand to cybercrime: Goodyear repeatedly registered on the forum under different chat names, but each time earned himself a ban for boorish behavior.
Quarter trends
Due to its capacity and relative accessibility, Memcached was the springboard for last quarter’s most sensational attacks. However, it could prove to be a short-lived trend, and here’s why.
In late February, Kaspersky DDoS Protection support was contacted by a company reporting an unusually high load on its communications channel in what it suspected to be a DDoS attack.
At first glance, the picture did indeed resemble a typical DDoS attack: the channel was clogged up, and users couldn’t access the company’s services. However, our investigation revealed that a CentOS Linux server with a vulnerable Memcached service was installed on one of the client servers. This service, used by the cybercriminals during the attack, generated large amounts of outgoing traffic, overloading the channel. In other words, the client was not the target, but an unwitting accomplice in the DDoS attack: the attackers used its server as an amplifier. After Kaspersky Lab’s recommendations were implemented, the malicious parasitic traffic stopped.
This situation is typical for Memcached attacks: owners of vulnerable servers hijacked during attacks notice the load increase and rush to patch any vulnerabilities not to suffer even more downtime losses. As a result, the number of vulnerable servers that can be utilized for this type of attack is rapidly declining, for which reason Memcached attacks will likely dry up soon.
Still, the picture in Q1 shows that “amplified” attacks, which were on the wane, have again picked up momentum. NTP and DNS-based boosting has practically disappeared, since most vulnerable services have already been patched. Cybercriminals will likely seek out other non-standard amplification methods besides Memcached. Last quarter, for instance, we registered a quite rare (yet effective) type of amplification attack, in which the LDAP service was used as an amplifier. Alongside Memcached, NTP, and DNS, this service has one of the biggest amplification factors. Despite the relatively small number of LDAP servers available, this type of attack could be a hit on the shadow Internet in the coming months.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience of combating cyber threats, including DDoS attacks of various complexity types and ranges. Company experts track the actions of botnets by using the DDoS Intelligence system.
As part of the Kaspersky DDoS Protection solution, the DDoS Intelligence system intercepts and analyzes commands sent to bots from C&C servers; it does not require any user devices to be infected or cybercriminals to execute any actual commands.
This report contains DDoS Intelligence statistics for Q1 2018.
In the context of this report, it is assumed that an incident is a separate (single) DDoS-attack if the interval between botnet activity periods does not exceed 24 hours. For example, if one particular web resource was attacked by the same botnet in two waves with an interval of 24 hours or more, the incident is considered as two attacks. Bot requests originating from different botnets but directed at one resource also count as separate attacks.
The geographical locations of DDoS-attack victims and C&C servers used to send commands are determined by their respective IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
DDoS Intelligence statistics are limited to botnets detected and analyzed by Kaspersky Lab. Note that botnets are just one of the tools for performing DDoS attacks, and that the data presented in this report do not cover every single DDoS attack that occurred during the period under review.
Quarter results
In Q1 2018, DDoS attacks were registered against targets in 79 countries (84 in the previous quarter). As ever, the vast majority (95.14%) occurred in the top ten countries.
As for attack targets, as usual about half were located in China (47.53%), although the share was somewhat lower against the previous quarter.
The number of attacks and targets rose significantly, as did the number of long-duration attacks. The most sustained DDoS attack lasted 297 hours (more than 12 days), making it one of the longest in recent years.
The share of Linux botnets fell slightly to 66% against the previous quarter’s 71%.
Significant peaks in the number and power of cyberattacks were observed in mid-January and early March, while the mid-quarter period was relatively calm.
Geography of attacks
China easily retained pole position by number of attacks: its share remained almost unchanged, up from 59.18% to 59.42%. The US share (17.83%), the second largest, increased by a more noticeable 1.83%. South Korea again took bronze, but its share fell by more than 2%, from 10.21% to 8%.
Britain (1.30%) moved from fourth to fifth. Tenth place in Q1 2018 went to Russia, whose share decreased from 1.25% to 0.76%. The Netherlands and Vietnam dropped out of the top ten, but Hong Kong (with a solid 3.67% against 0.67% in Q4 2017) and Japan (1.16%) reappeared.
Distribution of DDoS attacks by country, Q1 2018 and Q4 2017
As regards the distribution of attack targets, top spot again belongs to China, although its share declined from 51.84% to 47.53%. Meanwhile, the still second-place US saw its share increase from 19.32% to 24.10%. Third position was taken by South Korea (9.62%). France’s ranking changed significantly: shedding just 0.65% this quarter, it dropped from fifth to ninth place.
The list of top ten most attacked countries said goodbye to Russia and the Netherlands, but welcomed Hong Kong (4.76%) straight into fourth place, and Japan (1.6%) into sixth. Overall this quarter, the total share of top ten countries increased slightly to 94.17% against 92.9% at the end of 2017.
Distribution of unique DDoS-attack targets by country, Q4 2017 and Q1 2018
Dynamics of the number of DDoS attacks
Most Q1 activity occurred in the first and last third. The number of attacks peaked on January 19 (666) and March 7 (687 attacks). This is probably linked to the end of the New Year holidays (the number of attacks began to rise around the second week of January) and the March sales (in connection with International Women’s Day). The quietest days were observed at roughly the same time: January 16 and March 11. The mid-quarter period passed relatively smoothly without significant peaks or noticeable declines.
The calmest day of the week in the latest quarter was Sunday, accounting for just 11.35% of all attacks.
Distribution of DDoS attacks by day of the week, Q4 2017 and Q1 2018
Types and duration of DDoS attacks
The share of SYN-DDOS attacks increased slightly (from 55.63% to 57.3%), but there was no repeat of the situation seen in previous quarters. The share of ICMP attacks almost doubled, from 3.4% to 6.1%. Accordingly, UDP, TCP and HTTP floods were forced to cede some ground: their shares dropped by 1-2% against the previous quarter.
Distribution of DDoS attacks by type, Q1 2018
After some respite at the end of 2017, we saw a return of sustained attacks: the longest lasted 297 hours (12.4 days). And although that falls short of the world record, the magnitude is still considerable. We have to go back to late 2015 for a longer attack.
The share of all other sustained attacks (50 hours or more) increased by more than six times, from 0.10% to 0.63%. At the other end of the spectrum, the share of the shortest attacks (9 hours or less) also grew: if last quarter they accounted for 85.5% of all attacks, now the figure stands at 91.47%. Meanwhile, the number of attacks lasting between 10 hours and three days in the latest quarter almost halved from 14.85% to 7.76%.
Distribution of DDoS attacks by duration (hours), Q4 2017 and Q1 2018
The top ten countries by number of C&C servers last quarter underwent a major reshuffle: Canada, Turkey, Lithuania, and Denmark dropped out, while Italy, Hong Kong, Germany, and Britain climbed upwards. The top three remained practically unchanged: South Korea (30.92%), the US (29.32%), China (8.03%). Only Russia (2.01%), having shared bronze with China in late 2017, slid down to ninth place.
The US share almost doubled, bringing it within touching distance of this ranking’s perennial leader South Korea. In addition, the shares of Italy (6.83%), which last quarter did not even make the top ten, the Netherlands (5.62%), and France (3.61%) increased significantly. This jump was due to a sharp rise in the number of C&C accounts for Darkai (in the US, Italy, the Netherlands, and France) and AESDDoS (in China) bots.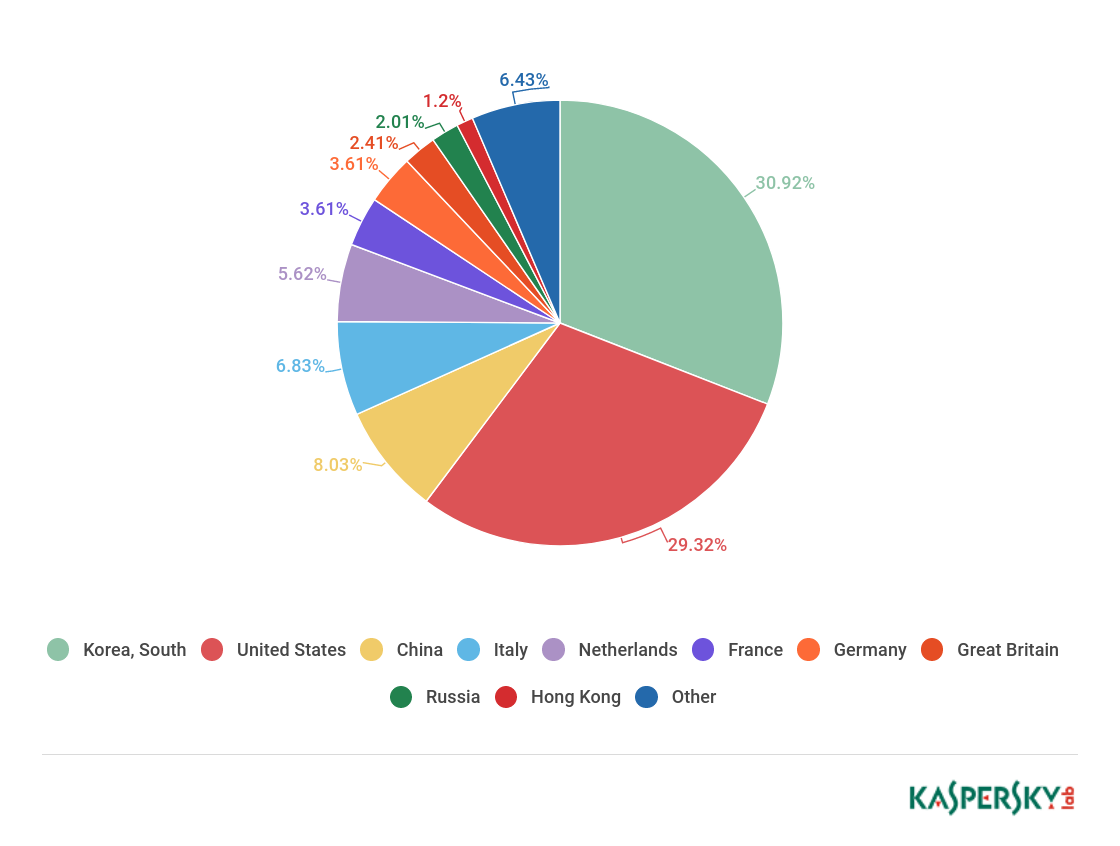
Distribution of botnet C&C servers by country, Q1 2018
The share of Linux botnets last quarter fell slightly compared to the end of 2017, down to 66% from 71%. Accordingly, the share of Windows-based botnets climbed from 29% to 34%.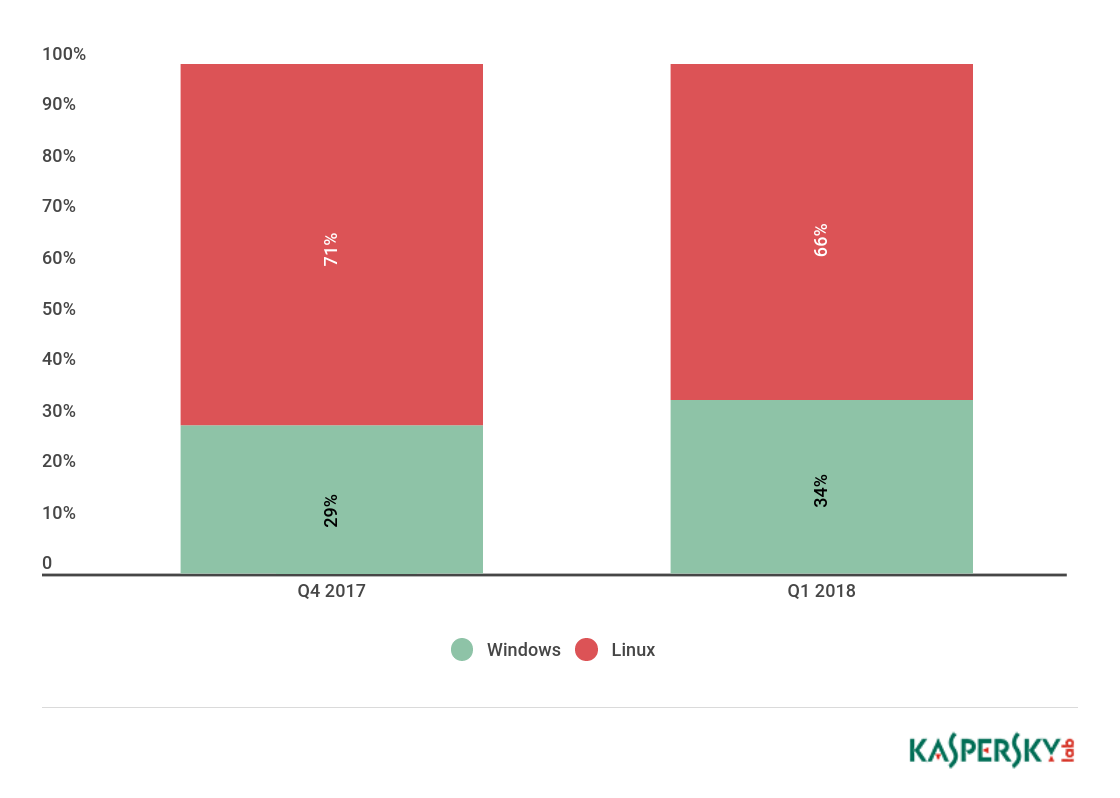
Correlation between Windows- and Linux-based botnet attacks, Q1 2018
Conclusion
In Q1 2018, we observed a significant increase in both the total number and duration of DDoS attacks against Q4 2017. The new Linux-based botnets Darkai (a Mirai clone) and AESDDoS are largely responsible for this hike. The number of now familiar Xor attacks also rose. Neither did Windows-based botnets remain idle, making some headway against Linux in the total number of attacks. The old Yoyo botnet was particularly lively, almost five times as active.
The number of mixed attacks involving several botnet families also increased. This is a clear continuation of the trend that we spoke about at the end of last year: to optimize outlays, attackers utilize unused parts of botnets to generate garbage traffic, redeploying them across targets.
Amplified attacks returned to the cyber arena, particularly through the Memcached service. However, we expect that server owners will quickly spot the abundance of garbage traffic and patch up the vulnerabilities, which will dent the popularity of attacks of this type. That being the case, DDoS masterminds will likely seek out other amplification methods, one of which could be LDAP services.
Researchers Dissect Tool Used by Infamous Russian Hacker Group
28.4.2018 securityweek APT
Sofacy’s First-Stage Malware Zebrocy Analyzed
ESET security researchers have taken a deep dive into one of the tools heavily used by the Russian threat actor Sofacy over the past couple of years.
Dubbed Zebrocy, the tool serves as a first-stage malware in attacks and is comprised of a Delphi downloader, an AutoIt downloader and a Delphi backdoor. Used in multiple attacks, the malicious program often acts as a downloader for the actor’s main backdoor, Xagent.
Also referred to as APT28, Fancy Bear, Pawn Storm, Sednit, and Strontium, and active since around 2007, the group is focused on cyber espionage and has hit government, military, and defense organizations worldwide.
Supposedly the actor behind attacks targeting the 2016 presidential election in the United States, Sofacy has been known to target Ukraine and NATO countries, and has recently switched focus to targets in Asia.
Coexisting with another Sofacy first-stage tool, Seduploader, the Zebrocy malware has been used in attacks against victims in Azerbaijan, Bosnia and Herzegovina, Egypt, Georgia, Iran, Kazakhstan, Korea, Kyrgyzstan, Russia, Saudi Arabia, Serbia, Switzerland, Tajikistan, Turkey, Turkmenistan, Ukraine, Uruguay and Zimbabwe, ESET reveals.
Zebrocy is usually delivered via emails carrying malicious attachments and users are lured into opening them. These are either Microsoft Office documents that deliver the payload via VBA macros, exploits, or Dynamic Data Exchange (DDE), or archives containing executables with an icon and a document-like filename.
Once the malicious attachment is executed, the first stage of the Zebrocy family is delivered: a Delphi downloader (in some attacks the AutoIt stage was used directly). The downloader is usually masked using document or Windows library icons and some samples are packed with UPX.
When launched, the malware displays a splash window with a bogus error message to distract the user. In the background, however, the malware drops a file under %TEMP% and adds a Windows registry to achieve persistence. It also gathers information on the compromised system and sends it to the command and control (C&C) server via a HTTP POST request.
If the target is considered of interest, the C&C responds with the next stage, the AutoIt downloader, which acts as another layer of the reconnaissance phase. Packing all of the functionality of the Delphi downloader and even more, the AutoIt downloader is sometimes used as the first stage instead.
The tool can detect sandbox and virtual environments and retrieve system information such as: a list of installed software, Windows version (32-bit or 64-bit), process list, hard drive information, and screenshots, along with various details about the computer, gathered using Windows Management Instrumentation (WMI) objects.
The Delphi backdoor, which is the last stage of the Zebrocy chain of components, has an internal versioning number, unrelated to the campaign it is used in. It embeds configuration data such as: AES keys for C&C communication, URLs, malware version, persistence windows registry key/value, path to store temporary files, and the names of hidden directories to be created to store temporary files.
Once set up, the malware executes callback functions via the Windows API function SetTimer, allowing the attackers to handle features and commands: take a screenshot of the desktop, capture keystrokes, list drives/network resources, read/write into Windows registry, copy/move/delete a file system object, and execute files or create scheduled tasks.
The backdoor supports around 30 commands, which differ from one version to another. For communication purposes, the malware stores the report of these functions on a temp file, then reds the file content and sends it to the C&C.
Zebrocy might be the successor of another malware components written in Delphi that Sofacy is known have used, namely Downdelph. The tool was last seen in September 2015, two months before Zebrocy emerged and both malware families also use a similar deployment method, the researchers note.
“We have seen Zebrocy being heavily used by the Sednit group over the last two years. Our analysis of the many new variants that appeared on a regular basis since 2017 clearly indicates that Zebrocy is being actively maintained and improved by its author(s). We can consider it as one of the stable, mature tools in Sednit’s arsenal, a tool that deserves to be monitored closely,” ESET concludes.
Amazon Alexa Can Be Used for Snooping, Researchers Say
28.4.2018 securityweek Privacy
Amazon's Alexa cloud-based virtual assistant for Amazon Echo can be abused to eavesdrop on users, Checkmarx security researchers have discovered.
Present on more than 31 million devices around the world, Alexa enables user interaction after a wake-up word (specifically, “Alexa”) activates it. Next, the Intelligent Personal Assistant (IPA) launches the requested capability or application – called skill, it either comes built-in or is installed from the Alexa Skills Store.
Checkmarx researchers built a malicious skill application capable of recording user’s speech in the background and then exfiltrating the recording, all without alerting the user.
Because of the required wake-up word, the recording would have to be performed after the activation. However, the listening session would normally end after a response is delivered to the user, to protect privacy, yet the researchers found a way to keep the session alive and to hide that from the user.
A shouldEndSession flag allows a session to stay alive for another cycle, after reading back the service’s text as a response. However, reading back the text would reveal to the user that the device is still listening.
To overcome this issue, the researchers used a re-prompt feature, which works in a similar manner, but accepts “empty re-prompts.” Thus, they could start a new listening cycle without alerting the user on the matter.
Finally, the researchers also focused on being able to accurately transcribe the voice received by the skill application. For that, they added a new slot-type to capture any single word, not limited to a defined list of words. They also built a formatted string for each possible length.
Of course, users would still be alerted on a device listening to them because the blue light on Amazon Echo lights-up when a session is alive. However, some Alexa Voice Services (AVS) vendors would embed Alexa capabilities into their devices without providing the visual indicator, and it’s also highly likely that users would not pay attention to that light.
“While the shining blue light discloses that Alexa is still listening, much of the point of an IPA device is that, unlike a smartphone or tablet, you do not have to look at it to operate it. In fact, these IPAs are made to be placed in a corner where users simply speak to a device without actively looking in its direction,” the researchers say.
As long as speech is recognized and words picked up, the malicious skill can continue to eavesdrop in the background, without the user noticing it. In case of silence, Alexa closes the session after 8 seconds, but a silence re-prompt (defined with an empty output-speech that the user cannot hear) can double the grace period to 16 seconds, the security researchers say.
Checkmarx informed Amazon on their findings and worked with the company to mitigate the risks. Specific criteria to identify (and reject) eavesdropping skills during certification were put in place, along with measures to detect both empty-reprompts and longer-than-usual sessions, and take appropriate actions in both cases.
The security researchers also published a video demonstration of how the attack works.
Expert shows how to trigger blue-screen-of-death on Windows by triggering NTFS flaw
28.4.2018 securityaffairs Vulnerebility
Bitdefender researcher Marius Tivadar has developed a dodgy NTFS file system image that could trigger a blue-screen-of-death when a mount is attempted on Windows 7 and 10 systems.
The Bitdefender expert Marius Tivadar has discovered a vulnerability tied the way Microsoft handles of NTFS filesystem images, he also published a proof-of-concept code on GitHub that could be used to cause Blue Screen of Death within seconds on most Windows computers.
“One can generate blue-screen-of-death using a handcrafted NTFS image. This Denial of Service type of attack, can be driven from user mode, limited user account or Administrator. It can even crash the system if it is in locked state.” wrote Tivadar.
The PoC code includes a malformed NTFS image can be stored on a USB thumb drive. Once the user will insert the USB thumb drive in a Windows PC it will crash the system within a few seconds causing a Blue Screen of Death.
Tivadar highlighted that auto-play is activated by default and even disabling it the system will crash when the NTFS image is accessed.
The expert noticed that some security tools like Windows Defender scans the USB stick triggering the flaw.
NTFS hack
Tivadar reported the NTFS issue to Microsoft in July 2017, but the tech giant did not recognize it as a security bug so the expert opted to disclose the flaw.
Microsoft pointed out that the exploitation of the issue requires either physical access, but Tivadar explained that an attacker could use a malware to exploit the PoC code.
Tivadar noticed that the NTFS bug also works while the PC is locked, this is an anomaly because there is no need to mount a USB stick/volume when the system is locked.
“Generally speaking, no driver should be loaded, no code should get executed when the system is locked and external peripherals are inserted into the machine.” the researcher explained.
Tivadar published two PoC videos on his personal Google Photos account and on his Google Drive account.
Necurs Spam Botnet operators adopt a new technique to avoid detection
28.4.2018 securityaffairs BotNet
Operators behind the Necurs botnet, the world’s largest spam botnet, are currently using a new evasion technique attempting to surprise the unprepared defenses.
Necurs is the world’s largest spam botnet, it is composed of millions of infected computers worldwide.
Necurs was not active for a long period at the beginning of 2017 and resumed its activity in April 2017. The Necurs botnet was used in the past months to push some malware, including Locky, Jaff, GlobeImposter, Dridex , Scarab and the Trickbot.
In February security experts observed the Necurs botnet was used to send out an amazing number of messages offering companionship waiting for Valentine’s day.
According to the IBM X-Force team, the campaign started in mid-January, it leveraged the overall Necurs botnet that has been estimated as composed of 6 million bots.
Now the botnet made the headlines again, the author implemented a new evasion technique. Crooks are sending out an email to a potential victim containing an archive file that once unzipped will present a file with the extension of .URL.
The .URL extension is associated with Windows shortcut file that opens an URL into a browser, in the campaign observed by the experts it points to a remote script file that downloads and executes a final payload.
In this last campaign, Necurs is delivering the Quant Loader to the victims to download another malware.
“As security vendors are wise to Necurs’s traditional infection chain (a script, a macro, or archives containing certain file formats), the malware has started using an internet shortcut or .URL file to bypass detection.” reads the analysis published by Trend Micro.
“Previously, Necurs’s JavaScript downloader downloads the final payload. But in its latest iteration, the remote script downloads QUANTLOADER (detected by Trend Micro as TROJ_QUANT) – a different downloader – which then downloads the final payload. This is another layer added to Necurs’s infection chain.”
The abuse of .URL files is a novelty for Necurs operators. according to the researchers, this technique implements a simplified infection chain compared to spam techniques used in the past.
“Last year, we also saw how Necurs pushed double-zipped attachments that either contained JavaScript, Visual Basic scripts, or macro files with the capability to download its final payload.” continues the analysis.
“In an attempt to evade spam detection through its attachments, Necurs used archives that included .ZIP files to disguise the script downloader, which was later enclosed in another .ZIP to hide itself.”

This simple infection chain allows avoiding anti-malware solutions that scan emails, looking for malicious links, boobytrapped attachments or other malicious patterns associated with an attack.
Of course, once uncovered the new campaign, the security firms will update existing detection rules to rapidly discovers attacks and neutralize the spam campaign.
Malware researchers added that crooks are using the standard folder icon to hide .URL files to deceive victims on their malicious nature.
Once the victim has clicked on the archive it extracts a file that appears to the victims as a new folder on their PC. When the victims click on the folder to explore its content they will start the infection chain.
“Notice that aside from the icons disguised as folders, the filenames were also crafted to resemble typical folder names such as IMG-20180404-9AC4DD, SCN-20180404-268CC1, and PIC-20180404-ADEEEE shown in Figure 2, to name a few.” states Trend Micro.

Now that you know this new technique … open the eyes and remain vigilant.
European and US police hit the Islamic State propaganda machine
28.4.2018 securityaffairs BigBrothers
A coordinated effort of law enforcement agencies (law enforcement authorities of the European Union Member States, Canada, and the USA) hit the Islamic State propaganda machine.
European law enforcement agencies coordinated by Europol conducted an unprecedented multinational cyber operation against the Islamic State’propaganda machine.
Authorities have “punched a big hole” in Islamic State’s propaganda machine, they targeted news agencies and radio stations in a two-day takedown operation.
“On 25 April 2018 law enforcement authorities of the European Union Member States, Canada and the USA launched a joint action against the so-called Islamic State (IS) propaganda machine in order to severely disrupt their propaganda flow.” read the press release published by Europol.
“The takedown operation was coordinated by the European Union Internet Referral Unit (EU IRU) within the European Counter Terrorism Centre (ECTC) at the Europol headquarters.”
View image on Twitter
View image on Twitter
Europol
✔
@Europol
#BREAKING: Takedown of Islamic State propaganda machine in international operation coordinated by Europol. Amaq – the main mouthpiece of the terrorist organisation – among those knocked down offline https://www.europol.europa.eu/newsroom/news/islamic-state-propaganda-machine-hit-law-enforcement-in-coordinated-takedown-action … #IS #terrorism
10:02 AM - Apr 27, 2018
189
232 people are talking about this
Twitter Ads info and privacy
The operation hit Islamic State media outlets, including the Amaq and Nashir news agencies and al-Bayan radio.
The authorities seized the servers and are analyzing data to identify the administrators behind principal media outlets.
“With this groundbreaking operation we have punched a big hole in the capability of IS [Isis] to spread propaganda online and radicalise young people in Europe.” said Rob Wainwright, executive director of Europol.
Europol hit Islamic State
This isn’t the first time Europol and other agencies target Islamic State propaganda machine since 2015 they have conducted numerous operations to shut down the infrastructure used by the terrorists.
In August 2016, an international joint operation conducted by the police hit the Amaq’s mobile application and web infrastructure, another operation was conducted in June 2017 and led to the identification of radicalised individuals in more than 100 countries.
Commissioner Dimitris Avramopoulos said: “Today’s international take-down action, with the support of Europol, shows our global strength and our unwavering resolve to fight against terrorist content online. Daesh is no longer just losing territory on the ground – but also online. We will not stop until their propaganda is entirely eradicated from the Internet.”
“This shows that by working together we can stamp out the poisonous propaganda Daesh [Isis] has used to fuel many of the recent terror attacks in Europe. For too long the internet has been open to terrorists and those who seek to do us harm. Those days are coming to an end thanks to this type of co-ordinated global work.” said the EU security commissioner, Julian King.
How to use weaponized PDF documents to steal Windows credentials
28.4.2018 securityaffairs Hacking
Weaponized documents are the main ingredient for almost any spam and spear-phishing campaign, let’s see how to steal windows credentials with specially crafted PDF files.
Weaponized documents are the main ingredient for almost any spam and spear-phishing campaign.
Weaponized PDF files can be used by threat actors to steal Windows credentials, precisely the associated NTLM hashes, without any user interaction.
According to a research published by Assaf Baharav, a security expert at Check Point, the attackers just need to trick victims into opening a file.
According to Check Point researchers, rather than exploiting the vulnerability in Microsoft Word files or Outlook’s handling of RTF files, attackers take advantage of a feature that allows embedding remote documents and files inside a PDF file.
Baharav explained that attackers could take advantage of features natively found in the PDF standard to steal NTLM hashes, rather than exploiting a flaw in Microsoft Word files or RTF files.
“The attacker can then use this to inject malicious content into a PDF and so when that PDF is opened, the target automatically leaks credentials in the form of NTLM hashes.” wrote Baharav.
The researcher used a specially crafted PDF document for his proof-of-concept.
When a victim would open the PDF document it would automatically contact a remote SMB server controlled by the attacker, but don’t forget that SMB requests include the NTLM hash for the authentication process.
“The NTLM details are leaked through the SMB traffic and sent to the attacker’s server which can be further used to cause various SMB relay attacks.” continues the expert.

Using this trick the attacker can obtain the NTLM hash and use tools available online to recover the original password.
Such kind of attack is stealth, it is impossible for the victims to notice any abnormal behavior.
Similar techniques leveraging SMB requests were used in the past by several threat actors, but with other types of documents or OS features (i.e. Office documents, shared folders authentication, Outlook)
According to Check Point, almost any Windows PDF-viewer is affected by this security flaw and will reveal the NTLM credentials.
Baharav successfully tested the attack on Adobe Acrobat and FoxIT Reader.
The experts followed a 90 days disclosure policy by notifying both Adobe and Foxit the vulnerability.
Adobe replied that will not fix the issue because it considers the flaw linked to the OS, meanwhile FoxIT still has not responded.
Adobe experts are referring to Microsoft Security Advisory ADV170014, released in October 2017 that implements a mechanism and provides instructions on how users could disable NTLM SSO authentication on Windows operating systems.
Below the reply from Adobe:
“Thank you for checking in on this case. Microsoft issued an optional security enhancement [0] late last year that provides customers with the ability to disable NTLM SSO authentication as a method for public resources. With this mitigation available to customers, we are not planning to make changes in Acrobat.“
Mozilla Adding New CSRF Protection to Firefox
27.4.2018 securityweek Safety
Mozilla announced this week that the upcoming Firefox 60 will introduce support for the same-site cookie attribute in an effort to protect users against cross-site request forgery (CSRF) attacks.
CSRF attacks allow malicious actors to perform unauthorized activities on a website on behalf of authenticated users by getting them to visit a specially crafted webpage. These types of attacks leverage the fact that every request to a website includes cookies and many sites rely on these cookies for authentication purposes.
Mozilla has pointed out that the current web architecture does not allow websites to reliably determine if a request has been initiated legitimately by the user or if it comes from a third-party script.
“To compensate, the same-site cookie attribute allows a web application to advise the browser that cookies should only be sent if the request originates from the website the cookie came from,” members of the Mozilla Security Team explained in a blog post. “Requests triggered from a URL different than the one that appears in the URL bar will not include any of the cookies tagged with this new attribute.”
Firefox 60, currently scheduled for release on May 9, will attempt to protect users against CSRF attacks with same-site attributes that can have one of two values: strict or lax.
In strict mode, when users click on an inbound link from an external site, they will be treated as unauthenticated even if they have an active session as cookies will not be sent.
In lax mode, cookies will be sent when users navigate safely from an external website (e.g. by following a link), but they will not be sent on cross-domain subrequests, such as the ones made for images or frames. The lax mode is designed for applications that may be incompatible with the strict mode.
Microsoft Releases More Microcode Patches for Spectre Flaw
27.4.2018 securityweek Vulnerebility
Microsoft this week released another round of software and microcode updates designed to address the CPU vulnerability known as Spectre Variant 2.
Microsoft has been releasing software mitigations for the Spectre and Meltdown vulnerabilities since January, shortly after researchers disclosed the flaws.
A new standalone security update (4078407) enables by default the mitigations against Spectre Variant 2 in all supported versions of Windows 10 and Windows Server 2016. Alternatively, advanced users can manually enable these mitigations through registry settings.
The company announced in early March that microcode updates from Intel will be delivered to Windows 10 and Windows Server 2016 users through the Microsoft Update Catalog. The first round of updates covered devices with Intel Skylake processors and the list was later expanded to include Coffee Lake and Kaby Lake CPUs.
Broadwell and Haswell processors have now also been added to the list, which currently includes tens of Intel CPUs across roughly 30 microarchitecture categories. Intel announced the availability of microcode updates for Broadwell and Haswell CPUs in late February.
Meltdown and Spectre allow malicious applications to bypass memory isolation and access sensitive data. Meltdown attacks are possible due to CVE-2017-5754, while Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). Meltdown and Spectre Variant 1 can be resolved with software updates, but Spectre Variant 2 requires microcode patches as well.
Last month, Microsoft released out-of-band updates for Windows 7 and Windows Server 2008 R2 to address a serious privilege escalation vulnerability introduced by the Meltdown mitigations.
Dutch Police Shut Notorious 'Revenge Porn' Site, Three Arrested
27.4.2018 securityweek Crime
Dutch police said Thursday they have arrested three men for stealing explicit pictures of girls and young women from their cloud data, and shut down a globally notorious "revenge porn" site.
After a year-long complex cyber-crime investigation following a complaint by a woman in March 2017, the police and prosecution service said they had found "enormous amounts of women's personal data and images" on the three men's phones and computers.
"With the confiscation of a server, the police have taken a hackers forum offline," they said in a statement identifying the forum as Anon-IB.
The hackers were mainly interested "in nude photographs and videos of girls and young women, which they stole from the clouds of their victims and shared with one another in other, more hidden locations on the internet," it added.
Those arrested are aged 28 to 35 and come from the Dutch cities of Heerlen, Culemborg and Groningen. Data from two other suspects has also been seized, but the other two men have not yet been arrested.
They had all been "able to access email boxes, social media accounts and repositories, such as clouds, belonging to hundreds of women" which had not been properly secured, the Dutch police said in a statement.
They procured "sexual images of a few hundred women without the victims noticing," they added.
The suspects had all got to know each other through using Anon-IB, where they "asked for help in obtaining images of specific girls," the police said in a statement.
Once the images were found, they retreated to smaller groups "in hidden places in the web to share the stolen footage."
Police spokesman Joep Patijn told the NOS broadcaster that the crime "involves a lot of women who have been hacked, hundreds or even thousands."
Women from other countries such as Belgium and New Zealand may also be involved, and police will now seek to inform all those whose data may have been stolen if they can identify them.
Anon-IB is notorious for being an image board where tens thousands of exploitative images are shared often anonymously and without the owners' consent.
It had been implicated in the 2014 "Celebgate" scandal when nude photos of actresses including Jennifer Lawrence and model Kate Upton were posted on line.
13 Year-Old Configuration Flaw Impacts Most SAP Deployments
27.4.2018 securityweek Vulnerebility
Most SAP implementations continue to be impacted by a security configuration flaw initially documented in 2005, Onapsis warns.
Neglected security configurations and unintentional configuration drifts of previously secured systems render SAP implementations vulnerable despite the release of several Security Notes designed to address the issues. According to Onapsis, a firm that specializes in securing SAP and Oracle applications, 9 out of 10 SAP systems were found vulnerable to the bug.
The security bug impacts SAP Netweaver and can be exploited by a remote unauthenticated attacker who has network access to the system. By targeting the bug, an attacker could gain unrestricted access to the system, thus being able to compromise the platform and all of the information on it, extract data, or shut the system down.
The vulnerability impacts all SAP Netweaver versions. Because SAP Netweaver is the foundation of all SAP deployments, 378,000 customers worldwide are affected, Onapsis says. The vulnerability exists within the default security settings on every Netweaver-based SAP product. Even the next generation digital business suite S/4HANA is impacted.
In a report detailing the vulnerability, Onapsis explains that a protection scheme through ACL (access control list) ensures that SAP Application Servers are registered within the SAP Message Server to work. Registration is performed using internal port 39<xx> (3900 by default), and SAP explained in a Security Note in 2010 that the port should be secured and only accessible by trusted application IP addresses.
The Message Server ACL, designed to check “which IP addresses can register an application server and which ones cannot,” is controlled by a profile parameter (ms/acl_info) that should contain a path to a file with a specific format. SAP published details on how to properly configure this access file in a Security Note in 2015.
“Nevertheless, this parameter is set with default configuration, as well as the ACL contents open, allowing any host with network access to the SAP Message Server to register an application server in the SAP system,” Onapsis explains.
By exploiting the lack of a secure Message Server ACL configuration on a SAP System, an attacker can register a fake Application Server, which could then be abused to achieve full system compromise through more complex attacks.
For a successful attack, however, an actor needs to take advantage of this misconfiguration: access to the Message Server internal port with a default configuration in the ACL. This means that proper configuration of SAP Message Server ACL should mitigate the risks associated with the attack.
Organizations are also advised to implement continuous monitoring and compliance checks to ensure relevant configurations don’t affect the security posture of the system, as well as to implement a SAP cybersecurity program that helps bridge the gap between teams.
“While much attention this year will go to new vulnerabilities, such as IoT, Meltdown and Spectre, there is a more silent threat lurking behind the scenes that may be as serious and certainly as broad. Many SAP landscapes are so interconnected and complex that taking a system offline to implement a secure configuration can be very disruptive to the organization. That being said, it is critical that organizations ensure that they make the time to implement the configuration. These upgrades must be planned out and timed to have the lowest impact on the organization,” said JP Perez-Etchegoyen, CTO at Onapsis.
Western Digital Cloud Storage Device Exposes Files to All LAN Users
27.4.2018 securityweek Security
The default configuration on the new Western Digital My Cloud EX2 storage device allows any users on the network to retrieve files via HTTP requests, Trustwave has discovered.
WD’s My Cloud represents a highly popular storage/backup device option, allowing users to easily backup important data (including documents, photos, and media files) and store it on removable media.
The new drive, however, exposes data to any unauthenticated local network user, because of a Universal Plug and Play (UPnP) media server that the device automatically starts when powered on.
By default, it allows any users capable of sending HTTP requests to the drive to grab any files from the device. Thus, any permissions or restrictions set by the owner or administrator are completely bypassed, Trustwave’s security researchers warn.
“It is possible to access files on the storage even when Public shares are disabled. Specifically, anyone can issue HTTP requests to TMSContentDirectory/Control on port 9000 passing various actions. The Browse action returns XML with URLs to individual files on the device,” the security firm explains in an advisory.
The researchers also published a proof-of-concept, explaining that an attacker needs to include XML with Browse action in the HTTP request to port 9000 asking for the TMSContentDirectory/Control resource. This will result in the UPnP server responding with a list of files on the device.
Next, the attacker can use HTTP requests to fetch the actual files from the device, given that they are already in the possession of the URLs leading to those files (from the response collected at the previous step).
Unfortunately, there is no official fix to address the vulnerability. WD was informed on the issue in January, but the company said they wouldn’t release a patch.
The My Cloud content can be accessed from the local network when Twonky DLNA Media Server is enabled because the server does not support authentication and is broadcast to any DLNA client without any authentication mechanism.
To ensure their data remains protected, users should keep sensitive data in a Password protected My Cloud Share. They are also advised to disable Twonky DLNA Media Server for the entire My Cloud or to disable Media Serving for Shares containing sensitive data.
Instructions on how to disable Twonky DLNA Media Server are available in this knowledge base article.
Dutch Police shut down the Anon-IB revenge porn forum
27.4.2018 securityweek Crime
The Dutch National Police shut down the anonymous revenge-porn sharing site Anon-IB, an aggregator website for revenge and child pornography.
Dutch Police shut down a Notorious ‘Revenge Porn’ Site Anon-IB, the authorities have arrested three men for stealing explicit pictures of girls and young women from their cloud data.
The men are aged 28 to 35 and live in the Netherlands, in the cities of Heerlen, Culemborg, and Groningen.
Anon-IB has first appeared in the criminal underground in 2014, it had more than 2,000 registered users and hosted links to tens of thousands of images and videos.
The operation lasted at least one year, the investigation started with a complaint by a woman in March 2017.
Unfortunately, the number of the victims is high, the police had found “enormous amounts of women’s personal data and images” on the smartphones and computers of the suspects. The police also seized data from two other suspects that have not yet been arrested, a 19-year-old from Terneuzen, and a 26-year-old from Geleen.
“With the confiscation of a server, the police have taken a hackers forum offline,” reads a statement shared by the police.
The crooks targeted the women searching for nude pictures and video on their cloud storage and shared them on the Anon-IB site and on hidden forums on the web.
[Crooks were interested] “in nude photographs and videos of girls and young women, which they stole from the clouds of their victims and shared with one another in other, more hidden locations on the internet,” continues the statement.
They obtained “sexual images of a few hundred women without the victims noticing,”
Those arrested are aged 28 to 35 and come from the Dutch cities of Heerlen, Culemborg, and Groningen.
The hackers exploited the lack of proper security hygiene of the victims to access their email accounts, social media accounts, and cloud storages.
“The suspects were able to access the e-mail accounts, social media profiles and cloud storage services of many hundreds of women. The suspects met these women on the street, tried to get their name out and then hack them, the police told RTL Nieuws.” reported the RTL Nieuws.
According to the Dutch police, suspects had all been “able to access email boxes, social media accounts, and repositories, such as clouds, belonging to hundreds of women” which had not been properly protected by the victims.
RTL Nieuws reported Anon-IB users would talk about extorting hacked victims.
According to the law enforcement, the suspects were all Anon-IB users, in some cases, they “asked for help in obtaining images of specific girls,” then shared them within smaller groups “in hidden places in the web to share the stolen footage.”

Source RTL Nieuws
The crime “involves a lot of women who have been hacked, hundreds or even thousands,” Police spokesman Joep Patijn told the NOS broadcaster.
According to the police, women from other countries may also be involved, and authorities are working to identify the victims.
CVE-2018-7602 – Drupal addressed a new vulnerability associated with Drupalgeddon2 flaw
27.4.2018 securityweek Vulnerebility
The new flaw tracked as CVE-2018-7602, is a highly critical remote code execution issue, Drupal team fixed it with the release of versions 7.59, 8.4.8 and 8.5.3.
Drupal team has released updates for versions 7 and 8 of the popular content management system (CMS) to address the recently disclosed CVE-2018-7600 Drupalgeddon2 flaw.
The new flaw tracked as CVE-2018-7602, is a highly critical remote code execution issue, Drupal team fixed it with the release of versions 7.59, 8.4.8 and 8.5.3.
“A remote code execution vulnerability exists within multiple subsystems of Drupal 7.x and 8.x. This potentially allows attackers to exploit multiple attack vectors on a Drupal site, which could result in the site being compromised. This vulnerability is related to Drupal core – Highly critical – Remote Code Execution – SA-CORE-2018-002. Both SA-CORE-2018-002 and this vulnerability are being exploited in the wild.“reads the security advisory published by Drupal.
Administrators of websites running the Drupal CMS who cannot immediately update their version can apply a patch, but it only works if the fix for the original Drupalgeddon2 flaw is present. If the previous patch was not installed, the website may already be compromised, Drupal developers warned.
Both CVE-2018-7600 and CVE-2018-7602 have been exploited in the wild.
A week after the release of the security update for the CVE-2018-7600 flaw, a proof-of-concept (PoC) exploit was publicly disclosed.
The experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
“In brief, Drupal had insufficient input sanitation on Form API (FAPI) AJAX requests. As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication.” reads the analysis.
“By exploiting this vulnerability an attacker would have been able to carry out a full site takeover of any Drupal customer.”
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw.
The new CVE-2018-7602 vulnerability was discovered while members of the Drupal Security Team with the help of the Drupal developer Jasper Mattsson were analyzing the original Drupalgeddon2 flaw.
Security experts speculate the vulnerability may have been exploited to launch the ransomware-based attack on the website of the Ukrainian energy ministry.

Unfortunately, several threat actors are exploiting the Drupalgeddon2 flaw in the wild, security experts observed crooks using the exploit to deliver cryptocurrency miners such as XMRig and CGMiner.
According to the analysis published by experts at security firm Volexity, threat actors are exploiting the Drupalgeddon2 flaw to deliver malicious scripts cryptocurrency miners and backdoors.
The experts associated one of the observed campaigns aimed to deliver XMRig with a cybercriminal gang that exploited the vulnerability (CVE-2017-10271) in Oracle WebLogic servers to deliver cryptocurrency miners in late 2017.
According to security experts at Imperva, 90% of the Drupalgeddon2 attacks are scanning activities, 3% are backdoor infection attempts, and 2% are attempting to run drop cryptocurrency miners on the vulnerable systems.
F-Secure experts devised a Master Key that unlocks millions of hotel rooms
27.4.2018 securityaffairs Hacking
A security duo has built a master key that could be used to unlock doors of hotel rooms using the Vision by VingCard digital lock technology.
Do you travel often? Probably you don’t know that hackers can unlock your room door without using the master key due to a critical design vulnerability in a popular and widely used electronic lock system.
The affected locking system is the Vision by VingCard manufactured by Assa Abloy, the flaw can be exploited to unlock hotel rooms worldwide.
The Vision by VingCard locking system is currently deployed in more than 42,000 facilities in 166 different countries.
The vulnerability was discovered by Tomi Tuominen and Timo Hirvonen, security researchers at F-Secure researchers. The security duo has built a master key that could be used to unlock doors of the hotel rooms using the Vision by VingCard digital lock technology.
“You can imagine what a malicious person could do with the power to enter any hotel room, with a master key created basically out of thin air,” says Tomi Tuominen, Practice Leader at F-Secure Cyber Security Services.
“He worked side by side with F-Secure’s Timo Hirvonen, Senior Security Consultant, to devise a way to exploit the software system, known as Vision by VingCard.”
Let’s see how hackers have built their ‘Master Key,’ step by step. First, the attacker needs to get access to an electronic keycard used in the target facility, no matter it is currently active, experts noticed that even an expired key from a stay five years ago will work.
“An attacker will read the key and use a small hardware device to derive more keys to the facility. These derived keys can be tested against any lock in the same building. Within minutes the device is able to generate a master key to the facility.” continues the post published by F-Secure.
“The device can then be used instead of a key to bypass any lock in the facility, or alternatively, to overwrite an existing key with the newly created master key.”
The attacker can read the electronic key (RFID or magstripe) remotely by standing close to a hotel guest or employee having a keycard in his pocket. Another option consists of booking a room and then use that card as the source.
At this point, the attacker would need to write the electronic key and to do it he can use a portable programmer. Such kind of device is very cheap, it can be bought online for a few hundred dollars.
Tomi and Timo developed a custom software that allows creating a master key within minutes. The experts devised a custom-tailored device (actually an RFID reader/writer) that they held close to the VingCard locking system, it then tries different keys in less than one minute and finds the master key to unlock the door.
“An attacker will read the key and use a small hardware device to derive more keys to the facility. These derived keys can be tested against any lock in the same building. Within minutes the device is able to generate a master key to the facility. The device can then be used instead of a key to bypass any lock in the facility, or alternatively, to overwrite an existing key with the newly created master key.” continues the post published by F-Secure.
“The needed hardware is available online for a few hundred euros. However, it is the custom software developed by Tomi and Timo that makes the attack possible.”
The researchers notified Assa Abloy of their discovery in April 2017, since then the experts helped the manufacturer in fixing the issue.
Assa Abloy has recently issued a security update to address the vulnerability.

The experts will not publish the technical details of the attack nor will they make any the custom-hardware available.
The good news is that to date, the experts are not aware of any attacks in the wild exploiting the flaw they discovered.
Below a video PoC of the hack.
In addition, the two experts also discovered that the Vision software could be exploited within the same network to get access to sensitive customer data.
Hacking the Amazon Alexa virtual assistant to spy on unaware users
27.4.2018 securityaffairs Security
Checkmarx experts created a proof-of-concept Amazon Echo Skill for Alexa that instructs the device to eavesdrop on users’ conversations and then sends the transcripts to a website controlled by the attackers.
The Alexa virtual assistant could be abused by attackers to spy on consumers with smart devices.
Researchers at security firm Checkmarx created a proof-of-concept Amazon Echo Skill for Alexa that instructs the device to indefinitely record surround voice to secretly eavesdrop on users’ conversations and then sends the transcripts to a website controlled by the attackers.
Amazon allows developers to build custom Skills that can control voice-activated smart devices such as Amazon Echo Show, Echo Dot, and Amazon Tap.
The rogue Echo Skill for Alexa is disguised as a simple math calculator, once installed it will be activated in the background after a user says “Alexa, open calculator.”
“The Echo is continuously listening for the user’s voice. So when the user says “Alexa, open calculator”, the calculator skill is initialized and the API\Lambda-function that’s associated with the skill receives a launch request as an input.” reads the report published by Checkmarx.

The experts at Checkmarx were able to build a feature that kept the Alexa session up so Alexa would continue listening and customers were not able to detect Alexa’s activity.
The experts manipulated the code used in a built-in JavaScript library (ShouldEndSession) that is used to halt the device from listening if it doesn’t receive voice commands.
“The combination of a session that is still open (shouldEndSession=false) and an un-noticeable (empty) reprompt with a record intent as described above is that even after the user ends the regular functionality of the skill (math calculation within the calculator), the skill will continue to record, will capture the spoken words and send them to a log.” continues the report.
“As long as it will recognize speech and will pick up words, the eavesdropping will continue. Even the default 8-second grace of Alexa prior to closing the skill (in case of silence) will be doubled to 16 seconds due to a silence re-prompt.”
Checkmarx published a video proof-of-concept to show that Alexa can spy on users once they have opened up a session with the calculator app. A second session is created without prompting the user that the microphone is still active.
Any recorded audio is transcribed and transcripts are then sent to the attackers. Checkmarx reported his findings to Amazon that addressed the problem on April 10.
In November 2017, researchers at security firm Armis reported that millions of AI-based voice-activated personal assistants, including Google Home and Amazon Echo, were affected by the Blueborne vulnerabilities.
Virtual assistants are powerful technologies by dramatically enlarge our surface of attack, for this reason, it is essential to develop them with a security-by-design approach.
Microsoft releases new software and microcode updates to address Spectre flaw (Variant 2).
27.4.2018 securityaffairs Vulnerebility
Microsoft has released a new batch of software and microcode updates to address the Spectre flaw (Variant 2).
The IT giant has rolled out a new batch of software and microcode security updates to address the Spectre flaw (Variant 2).
The Spectre Variant 2, aka CVE-2017-5715, is a branch target injection vulnerability, while the Meltdown and Variant 1 of the Spectre attacks can be mitigated efficiently with software updates, the Spectre Variant 2 requires microcode updates to be fully addressed.
Microsoft is one of the companies that first released security patched to address the Meltdown and Spectre vulnerabilities in Intel chips, has been releasing software mitigations for the Spectre and Meltdown flaws since January.
Now Microsoft issued the security update 4078407 that enables by default the mitigations against Spectre Variant 2 for all Windows 10 and Windows Server 2016 versions.
Microsoft anyway allows advanced users to manually enable the mitigations through registry settings.
“Applying this update will enable the Spectre Variant 2 mitigation CVE-2017-5715 – “Branch target injection vulnerability.”” reads the security advisory published by Microsoft.
Advanced users can also manually enable mitigation against Spectre, Variant 2 through the registry settings documented in the following articles:
Windows Client Guidance for IT Pros to protect against speculative execution side-channel vulnerabilities
Windows Server Guidance to protect against speculative execution side-channel vulnerabilities“
In March, Microsoft released the first set of security updates for Windows systems running on Intel Skylake processors and later the tech giant also covered Coffee Lake and Kaby Lake CPUs.
Microsoft also provided updates for Broadwell and Haswell processors.
In April, Microsoft released out-of-band updates for Windows 7 and Windows Server 2008 R2 to fix a severe privilege escalation flaw introduced by the Meltdown security patches.
Rubella Macro Builder Crimeware Kit gains popularity on cybercrime underground
27.4.2018 securityaffairs CyberCrime
A new crimeware kit dubbed the Rubella Macro Builder is rapidly gaining popularity in the cybercriminal underground, experts already spotted its malware in the wild.
A new crimeware kit dubbed the Rubella Macro Builder is rapidly gaining popularity in the cybercriminal underground. The Rubella Macro Builder allows crooks to generate a malicious payload for social-engineering spam campaigns, crooks are offering it as a service for a three-month license of $120.
“While newer versions of the builder are significantly cheaper—as of April, a three-month license is $120 USD—they also come with enhanced features including various encryption algorithm choices ( XOR and Base64), download methods (PowerShell, Bitsadmin, Microsoft.XMLHTTP, MSXML2.XMLHTTP, custom PowerShell payload), payload execution methods (executable, JavaScript, Visual Basic Script), and the ability to easily deploy social engineering decoy themes with an Enable Content feature turned on to run the macro.” reads the analysis published by Flashpoint.
According to Flashpoint researches, Rubella is not particularly sophisticated, the builder is used to create Microsoft Word or Excel weaponized documents to use in spam email. The Rubella-generated malware acts as a first-stage loader for other malware.
The Rubella Macro Builder is cheap, fast and easy to use, the malware it generated can evade antivirus detection.

According to Flashpoint experts, also popular criminal gangs are using Rubella malware in their campaign, for example, the criminal crews behind the Panda and Gootkit banking malware.
“The macro junk and substitution method appears to be relatively primitive, relying on basic string substitutions. Additionally, its copy/paste implementation of the Base64 algorithm is displayed in Visual Basic Script (VBS) code implementation. The code is obfuscated through general Chr ASCII values.” continues the analysis.
Crooks continues to use weaponized documents for their campaigns, builders for Microsoft Office-based loader malware are a precious commodity in the underground.
Flashpoint also published the indicators of compromise (IOCs) for the Rubella macro builder here.
Western Digital MY CLOUD EX2 storage devices leak files
26.4.2018 securityaffairs Vulnerebility
Researchers at Trustwave have discovered that Western Digital My Cloud EX2 storage devices leak files.
Security experts at Trustwave have discovered that Western Digital My Cloud EX2 storage devices leak files on a local network by default. The situation gets worse if users configure the device for remote access and expose them online, in this scenario the My Cloud EX2 storage devices also leak files via an HTTP request on port 9000.
“unfortunately the default configuration of a new My Cloud EX2 drive allows any unauthenticated local network user to grab any files from the device using HTTP requests,” states Trustwave.
According to the experts, the problem tied the embedded UPnP media server that is automatically started when the device is powered on.
“By default, unauthenticated users can grab any files from the device completely bypassing any permissions or restrictions set by the owner or administrator,” continues Trustwave.
Trustwave revealed they found the vulnerability on January 26.
Trustwave reported the vulnerabilities to Western Digital that initially downplayed them, and only recommended users to disable the DLNA.
Trustwave published a Proof-of-Concept code for the vulnerabilities, the attack scenario sees the attackers issuing an HTTP request to port 9000 asking for the “TMSContentDirectory/Control” resource, the UPnP server, in turn, will respond with a list of files on the storage. Then the attacker uses subsequent HTTP requests to fetch files from the storage using URLs from the response collected.
“It doesn’t matter that you can set permissions and credentials on the My Cloud EX2 to make sure that your children’s photos are locked down and only available to somebody that’s actually authenticated with the device. By knowing how the traffic works with the My Cloud (EX2) appliance, you can actually get it to feed you any file on the device, regardless of the permissions. That is something new specific to this device.” continues Trustwave.
In February, researchers at Trustwave disclosed other two vulnerabilities in Western Digital My Cloud network storage devices could be exploited by a local attacker to gain root access to the NAS devices.
Police shut down the biggest DDoS-for-hire service (webstresser.org) and arrested its administrators
26.4.2018 securityaffairs BigBrothers
The European police have shut down webstresser.org, the world’s biggest DDoS-for-hire service, that allowed crooks to launch over 4 million attacks.
An international operation dubbed conducted by the European law enforcement agencies led by the UK’s National Crime Agency (NCA) and the Dutch Police, with the help of Europol, has taken down the world’s biggest DDoS-for-hire service.
The operation dubbed Power Off allowed to shut down the biggest DDoS-for-hire service (webstresser.org) and arrest its administrators, according to the investigators the platform was involved in over 4 million attacks and arrested its administrators.
The police arrested 6 members of the crime group behind the ‘webstresser.org‘ website in Scotland, Croatia, Canada, and Serbia on Tuesday.
The Europol confirmed that Webstresser.org had 136,000 registered users and was used to target online services from banks, government institutions, police forces and the gaming world.
“The administrators of the DDoS marketplace webstresser.org were arrested on 24 April 2018 as a result of Operation Power Off, a complex investigation led by the Dutch Police and the UK’s National Crime Agency with the support of Europol and a dozen law enforcement agencies from around the world.” reads the press release published by the Europol.
“Webstresser.org was considered the world’s biggest marketplace to hire Distributed Denial of Service (DDoS) services, with over 136 000 registered users and 4 million attacks measured by April 2018.”
DDoS-for-hire service allows criminals without specific technical skills to launch powerful cyber attacks by renting their service.

“Stressed websites make powerful weapons in the hands of cybercriminals,” said Jaap van Oss, Dutch chairman of the Joint Cybercrime Action Taskforce.
“International law enforcement will not tolerate these illegal services and will continue to pursue its admins and users,”
The service was shuttered and the police seized the hacking platform, the Europol announced “further measures” were also taken against the top users in the above four countries, as well as in Italy, Australia, Hong Kong and Spain.
Registered user on Webstresser.org could access the DDoS-for-hire service an entry fee of €15 per month.
“We have a trend where the sophistication of certain professional hackers to provide resources is allowing individuals – and not just experienced ones – to conduct DDoS attacks and other kind of malicious activities online”, said Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3). “It’s a growing problem, and one we take very seriously. Criminals are very good at collaborating, victimising millions of users in a moment form anywhere in the world. We need to collaborate as good as them with our international partners to turn the table on these criminals and shut down their malicious cyberattacks.”
Abusing legitimate booter services or using a DDoS-for-hire service is a crime, the Europol remarked that penalties can be severe.
“DDoS attacks are illegal. Many IT enthusiasts get involved in seemingly low-level fringe cybercrime activities, unaware of the consequences that such crimes carry. The penalties can be severe: if you conduct a DDoS attack, or make, supply or obtain stresser or booter services, you could receive a prison sentence, a fine or both.” concluded the Europol.
Do Not Disturb app will protect your device from evil maid attacks
26.4.2018 securityaffairs Hacking
Former NSA expert and white hat hacker Patrick Wardle has released an app named Do Not Disturb app that can be used to detect attacks powered by attackers with physical access to the device (so-called “evil maid” attacks).
Patrick Wardle app Version 1.0.0 was built explicitly to protect unattended laptops continually monitors the system for events that may indicate a precursor of “evil maid” attack. According to Wardle, the Not Disturb app watches for ‘lid open’ events, the expert credited @thegrugq for the idea.
“If you’ve shut your laptop (and thus triggered sleep mode), the majority of physical access attacks may require the lid to be opened in order for the attack to succeed.” wrote Wardle.
“Such attacks could include:
Logging in locally as root, by exploiting a bug such as ‘#iamroot’
Locally logging in via credentials captured by a hidden camera
Inserting a malicious device into a USB or Thunderbolt port.
Again, most of these attacks require a closed laptop to be opened…either to awake it (i.e. to process a malicious device) or for the attacker to interact with the laptop!”
Once the Do Not Disturb app has detected a lid open event, it will take a series of actions. The app is able to display a local alert, send an alert to a remote Apple device (iPhone or iPad), log the attacker’s actions (creation of new processes, USB insertions, etc.), run custom scripts that could wipe sensitive data, disable the USB interfaces, or automatically re-lock the device every few seconds.

Wardle’s company Digita Security, has also released an iOS companion app for Do Not Disturb (available on the Apple Store) that allows users to associate their devices with the Do Not Disturb app, an operation that is necessary to receive alerts and notifications in case of attack.
“While the iOS companion application is free, after the first week of remote alerts/tasking, one will have to subscribe to a monthly ($0.99) or yearly ($9.99) to maintain this functionality. The Mac application, is and will always be 100% free 🙂 ” added Wardle.
“The iOS companion application is completely optional, and only required if one is interested in receiving remote DND alerts.”
Wardle plans to introduce new features in the future versions of the Do Not Disturb app that will include the management of more “lid open” events.
Drupal Patches New Flaw Related to Drupalgeddon2
26.4.2018 securityweek Vulnerebility
Drupal developers have released updates for versions 7 and 8 of the content management system (CMS) to address a new vulnerability related to the recently patched flaw known as Drupalgeddon2.
The new vulnerability, tracked as CVE-2018-7602, has been described as a highly critical issue that can be exploited for remote code execution. The flaw has been patched with the release of versions 7.59, 8.4.8 and 8.5.3.
Drupal website administrators who cannot immediately install the updates can apply a patch, but the patch only works if the fix for the original Drupalgeddon2 vulnerability (CVE-2018-7600) is present. If the previous patch was not installed, the website may already be compromised, Drupal developers warned.
CVE-2018-7602 was discovered by members of the Drupal Security Team, which consists of 34 volunteers from around the world, along with Finland-based Drupal developer Jasper Mattsson, who also reported the original vulnerability. The new flaw was identified during an investigation into CVE-2018-7600.New variant found for Drupalgeddon2 Drupal vulnerability
Drupal developers warn that similar to CVE-2018-7600, CVE-2018-7602 has also been exploited in the wild.
Drupalgeddon2 was patched in late March and the first attacks were seen roughly two weeks later, shortly after technical details and a proof-of-concept (PoC) exploit were made public.
While many of the exploitation attempts are designed to identify vulnerable systems, some cybercriminals have leveraged the flaw to deliver cryptocurrency miners, backdoors and other types of malware.
Some experts believe the security hole may have been exploited to deliver ransomware to the website of the Ukrainian energy ministry.
There are several groups exploiting Drupalgeddon2, including one that leverages a relatively large botnet named Muhstik, which is related to the old Tsunami botnet.
The botnet has helped cybercriminals make a profit by delivering cryptocurrency miners such as XMRig and CGMiner, and by launching distributed denial-of-service (DDoS) attacks.
Two security firms have independently confirmed that one of the Drupalgeddon2 campaigns delivering a Monero cryptocurrency miner is linked to a cybercriminal group that last year exploited a vulnerability in Oracle WebLogic Server (CVE-2017-10271) to infect systems with cryptocurrency malware.
Drupal powers more than one million websites, including nine percent of the top 10,000 most popular websites running a known CMS, making it a tempting target for malicious actors.
Apple Patches macOS, iOS, Safari
26.4.2018 securityweek Apple
Apple this week released patches to address a handful of security vulnerabilities in macOS, iOS, and Safari.
Available for macOS High Sierra 10.13.4, Security Update 2018-001 addresses two vulnerabilities impacting Crash Reporter and LinkPresentation, respectively.
The first is a memory corruption issue that could allow an application to gain elevated privileges. Tracked as CVE-2018-4206, the security flaw was reported by Ian Beer of Google Project Zero. Apple addressed the bug with improved error handling.
The tech company also resolved a spoofing issue in the handling of URLs, which could result in UI spoofing when processing a maliciously crafted text message. Tracked as CVE-2018-4187 and reported by Zhiyang Zeng, of Tencent Security Platform Department, and Roman Mueller, the issue was addressed with improved input validation.
In a blog post in March, Mueller explained that the vulnerability was introduced when Apple added QR code reading capabilities to the camera app and that it resides in the application being unable to correctly detect the hostname in a URL.
Thus, a malicious actor could craft a QR code that, when read with the camera app, would display a different hostname in the notification shown to the user compared to the domain Safari would actually access.
Both of these issues were resolved in iOS 11.3.1 as well, which is now available for iPhone 5s and later, iPad Air and later, and iPod touch 6th generation. Additionally, the iOS update patches two bugs in WebKit.
Both of these bugs are memory corruption issues that could lead to arbitrary code execution when processing maliciously crafted web content. To resolve these vulnerabilities, Apple improved state management and memory handling, respectively.
The first of these bugs is tracked as CVE-2018-4200 and was found by Ivan Fratric of Google Project Zero. Tracked as CVE-2018-4204, the second issue was reported by Richard Zhu, working with Trend Micro's Zero Day Initiative.
Now available for OS X El Capitan 10.11.6, macOS Sierra 10.12.6, and macOS High Sierra 10.13.4, the newly released Safari 11.1 includes patches for both WebKit vulnerabilities.
Hotel Rooms Around the World Susceptible to Silent Breach
26.4.2018 securityweek Hacking
Vision by VingCard
In 2003, researchers from F-Secure were attending a security conference in Berlin -- specifically, the ph-neutral hacker conference -- when a laptop was stolen from a locked hotel room. They reported the theft to the hotel staff, but felt they weren't taken too seriously because, dressed in typical hacker gear, "We kinda looked like a bunch of hippies."
More to the point, however, there was no sign of the door being forced, nor any indication from the electronic locking system's logs that anyone had entered the room in their absence.
The locking system was Assa Abloy's Vision by VingCard -- a state-of-the-art system from one of the world's most trusted and widely-used facilities security firms. In short, the laptop was stolen by a ghost that could pass through locked doors and leave no trace.
Vision by VingCard is deployed in 166 different countries, 40,000 facilities, and millions of doors.
F-Secure researchers told SecurityWeek, "Our guy was working on some really interesting and specific stuff; and, yes, it would absolutely have been of interest to any 3, 4 or 5 letter agency in many different nation-states." Without naming their victim researcher, they added, "This was not some Joe-average researcher, and we have always been 100% sure that the laptop was stolen."
With this background it is not surprising that the researchers started to investigate the locking system. Specifically, they were looking for a Vision by VingCard vulnerability that could be exploited without trace -- and eventually they found one. It took thousands of hours work over the last 15 years examining the system and looking for the tiniest errors of logic.
"We wanted to find out if it's possible to bypass the electronic lock without leaving a trace," said Timo Hirvonen, senior security consultant at F-Secure. "Building a secure access control system is very difficult because there are so many things you need to get right. Only after we thoroughly understood how it was designed were we able to identify seemingly innocuous shortcomings. We creatively combined these shortcomings to come up with a method for creating master keys."
In summary, with any existing, old or expired keycard to any room on the system, it is possible to generate a master key that can be used to gain entry to any of the hotel rooms without leaving a trace on the system. An attacker could book a room and then use that keycard as the source; or could even read the data remotely by standing close to someone who has a card in a pocket -- in a hotel elevator, for example.
"You can imagine what a malicious person could do with the power to enter any hotel room, with a master key created basically out of thin air," commented Tomi Tuominen, practice leader at F-Secure Cyber Security Services. Property, such as F-Secure's laptop, could be physically removed; or an evil maid attack on any discovered laptop could deliver malware or perhaps prepare the device for remote control by usurping the Intel Management Engine BIOS Extension (MEBx).
Hirvonen explained the process of developing a master card to access a room. The first requirement is to obtain any keycard, current or expired, to any door in the target facility. A custom-tailored device (actually a Proxmark RFID token reader/writer) is then held close to the target lock. The device tries different keys, and in an average of less than one minute, locates the master key and unlocks the door. "The final step is that you either use the device as the master key, or you write the master key back to your keycard. This only has to be done once. You have found the master key and you can access any room in the hotel."
The basic Proxmark can be bought online for around 300 euros; but, added Hirvonen, "It is our custom software that does the work. It emulates different keys, and one of those will be the master key." He explained further. "On paper, it looks as if the keyspace is too big to crack so quickly using brute force. But we were able to combine small technical design flaws with a process vulnerability that allowed us to reduce the keyspace from a gazillion to something that could be brute forced in an average of 20 tries."
The capacity of the card is 64 bytes; and of those some 48 bytes are usable. It includes multiple different data fields on the card. "Once we identified the eleven different data fields," continued Hirvonen, "we realized that what remained could feasibly be attacked."
F-Secure reported its findings to Assa Abloy in April 2017, and for the last year the two firms have worked on a solution. At first, Assa Abloy thought the solution would simply be to increase the keyspace on the cards -- a theoretical solution that F-Secure repeatedly demonstrated didn't work in practice. The real solution has included effective randomization of the whole keyspace; and Assa Abloy has now released an update for its systems.
"Because of Assa Abloy's diligence and willingness to address the problems identified by our research," says Tuominen in an associated blog published today, "the hospitality world is now a safer place. We urge any establishment using this software to apply the update as soon as possible."
Full technical details of the attack will not be released by F-Secure, and Tuominen and Hirvonen have stressed that they are unaware of this exploit ever being used in the wild. But then, how would you detect the phantom use of a forged master keycard that leaves no trace on the system logs?
New Advanced Phishing Kit Targets eCommerce
26.4.2018 securityweek Phishing
A new advanced phishing kit has surfaced, which provides miscreants with more than the usual one or two pages used to collect personal and financial data from victims, Check Point warns.
The phishing kit is currently being advertised on the Dark Web at $100-$300 and has been designed to target online users looking to shop at popular retailers, in an attempt to steal their personal details and credit card information.
Advertised by a certain [A]pache, the kit doesn’t only display a login page with a prompt for personal and financial information. Instead, it incorporates entire replicas of retail sites, Check Point's security researchers have discovered.
Through the kit’s backend interface, cybercriminals can create convincing fake retail product pages, in addition to being able to manage their entire phishing campaign. The [A]pache Next Generation Advanced Phishing Kit is mainly targeting users in Brazil with convincing replicas of Walmart, Americanas, Ponto Frio, Casas Bahia, Submarino, Shoptime and Extra.
“By preparing a site with discounted products that appear to be sold by a legitimate retailer, the threat actor can then lure victims into making a ‘purchase’, at which point they surrender their personal and financial information,” Check Point notes.
Miscreants downloading [A]pache’s multi-functioning phishing kit don’t need advanced technical abilities to get started with their own cyber-attacks. The kit comes with installation instructions that allows any actor to launch a campaign fast.
Packing a full suite of tools to carry out an attack, the kit seems aimed at those with a good knowledge of Portuguese, but the security researchers discovered that some U.S. brands were targeted as well.
To trick victims, the attackers use domain names similar to those of the legitimate sites. Once the fake domains have been registered, the miscreants deploy the kit to a PHP and MySQL supported web host, and then log in to the admin panel to configure the campaign.
Actors can select an email address to receive notifications; to enter the URL of the phishing site; to choose to disable ‘Boleto Bancário’ (and force victims to enter their credit card data); to insert legitimate product URLs from the retailer’s website for automatic import; and to manage the phished victim information.
“[A]pache has made a simple user interface within the admin panel where the threat actor can paste the product URL of the legitimate retailer and the kit will automatically import the product information into the phishing page. They can then view their ‘products’ and change their original prices,” Check Point explains.
The phishing sites also claim to be offering competitive prices, in an attempt to motivate potential ‘customers’ into clicking on items and proceeding to checkout. However, prices aren’t reduced by much, as that would raise suspicions. Highly valued and desired items are listed first, to entice potential victims.
Not only does the fake website look exactly like the target site, but an automated post-code look-up function for added conviction is also included in the phishing kit. Thus, unsuspecting victims would easily reveal their payment details, including the card’s CVV, and the attacker can view the stolen details in the admin panel.
The victim is instead notified that the payment process has failed, so as to avoid arising suspicion when the purchased fake products do not arrive. The attackers would often take down the fake sites after successful attacks, to avoid being caught.
In one case, the researchers found a custom built ‘error 404’ site in use, which makes reference to a non-existent ‘Blue World Electronicos’ company. An English version of the page was found being used online on a few domains serving PayPal phishing scams.
Thus, the researchers discovered that the author of the Brazilian phishing kit appears to be behind kits targeting US victims as well. After finding the handle ‘Douglas Zedn’ in the control panel of the Walmart phishing site, the researchers managed to link it to the individual’s Steam account and then to their Twitter account.
“With some reports claiming that 91% of cyberattacks and data breaches begin with a phishing email, phishing remains a constant threat for stealing financial information, intellectual property, and even interfering with elections. For this reason, consumers and businesses alike must ensure they have the latest protections for safeguarding against such threats,” Check Point concludes.
Ransomware Hits Ukrainian Energy Ministry Website
26.4.2018 securityweek Ransomware
Hackers managed to compromise the Ukrainian energy ministry website, encrypt files, and post a ransom demand.
Although Ukraine has been heavily hit by global malware outbreaks over the last year, including WannaCry, NotPetya, and Bad Rabbit, the recent incident appears isolated and by no means the work of state-sponsored actors, security experts say.
In fact, the assault is believed to have been orchestrated by amateur hackers, who possibly didn’t even know what website they compromised.
“It appears that this attack was from someone (or a group) who uses automation to mass scan and then compromise vulnerable websites with ransomware. It is likely that the operators of this did not know that they were going to compromise this website going into it,” James Lerud, head of the Behavioural Research Team at Verodin, told SecurityWeek in an emailed comment.
After gaining access to the website, the attackers encrypted resources and posted a message demanding a 0.1 Bitcoin (around $930 at today's exchange rate) payment to decrypt the files.
Matt Walmsley, EMEA Director at Vectra, pointed out to SecurityWeek that there’s no evidence that the ministry’s internal systems or data has been breached. Only the web-facing service has been compromised in what appears to have been cyber-vandalism or low-level cybercrime unlikely to generate any significant monetary gain, Walmsley said.
According to Chris Doman, security researcher at AlienVault, who provided SecurityWeek with a screenshot of the compromised website, multiple miscreants appear to have hit the domain as part of the attack.
“What has probably happened here is that a hacktivist has hacked the site for fun, then the criminal ransomware attacker has used their backdoor (which you can see at the bottom of the page) to try and make some money. They appear to have done the same with a Russian website,” Doman said.
The payment address included in the ransom note has already received some payments, supposedly from the owners of previously compromised sites in 2017. However, it appears that the attackers only made a bit over $100 for their efforts.
Joseph Carson, chief security scientist at Thycotic, suggests that the attackers might be currently testing their abilities, likely in preparation for a larger campaign.
“It’s very likely that the cybercriminals behind this recent cyberattack against the Ukrainian Energy Ministry are testing their new skills in order to improve for a bigger cyberattack later or to get acceptance into a new underground cyber group that requires showing a display of skills and ability,” he said.
The security experts agree that the attack wasn’t the work of sophisticated actors, but the manner in which the website was compromised in the first place remains a mystery.
The website was using Drupal 7 and Lerud suggests that the site admins didn’t take the necessary precautions to lock down the site.
“Drupal 7 also had a massive vulnerability known as ‘Drupalgeddon 2’ which was announced March 28th; if the website owners did not patch it is entirely possible this is how the ransomware got in,” Lerud said.
Google Ramps Up Gmail Privacy Controls in Major Update
26.4.2018 securityweek IT
Google on Wednesday ramped up privacy controls in a Gmail overhaul, aiming first at businesses that use its suite of workplace tools hosted in the internet cloud.
The "all new" Gmail is available to the more than four million businesses that pay for G Suite services.
People who use the email service personally for free can opt in by making the choice in settings, vice president of product management David Thacker said in a blog post.
Revamped Gmail has "a brand new look on the web, advanced security features, new applications of Google's artificial intelligence and even more integrations with other G Suite apps," according to Thacker.
A confidential mode added to Gmail promises to let people sending messages set expiration dates and block them from being forwarded, copied, downloaded or printed.
Messages can be revoked after being sent, Thacker said.
Senders of mail can also require that a code delivered by text message be entered before an email can be viewed, in an added layer of security.
"Because you can require additional authentication via text message to view an email, it's also possible to protect data even if a recipient's email account has been hijacked while the message is active," Thacker said.
Confidential mode will begin to roll out to personal Gmail users and a limited number of G Suite customers in coming weeks, according to Google.
Artificial intelligence is being put to work in new Gmail features including "nudging" people to tend to neglected messages and automated reply suggestions along the lines of those added to a mobile version of the email service last year.
"Gmail can also recommend when to unsubscribe from mailing lists," Thacker said.
"Using intelligence, unsubscribe suggestions appear based on cues like how many emails you get from a sender and how many of them you actually read."
Google and rival technology titans such as Apple, Amazon, and Microsoft have followed people into the internet cloud with services, digital content, and software hosted online at data centers but accessed from the gamut of devices.
Authorities Take Down Largest DDoS Services Marketplace
26.4.2018 securityweek Attack
The world’s largest marketplace for selling Distributed Denial of Service (DDoS) attacks, was taken down this week following a complex joint operation, authorities announced.
The site, Webstresser.org, offered DDoS for hire services for as little as $14.99 per month, and had over 136,000 egistered users and 4 million attacks measured as of April 2018. The service was available to any wannabe criminal, and didn’t require technical knowledge to launch crippling DDoS attacks across the world.
Critical online services of banks, government institutions, and police forces, as well as gaming organizations fell victim to attacks, Europol said.
Such for-hire services rely on botnets – networks of malware-infected systems under the attacker’s control – to launch high volumes of Internet traffic at the target machines to paralyze them. By depleting the resources of a targeted server, they can either slow it down or completely knock it offline.
Published earlier this year, Arbor Networks’ 13th Annual Worldwide Infrastructure Security Report (WISR) revealed that over half of enterprise, government and education (EGE) organizations faced a crippling DDoS attack in 2017. The security firm observed 7.5 million assaults last year.
On April 24, as part of an investigation called Operation Power Off, the Dutch Police and the UK’s National Crime Agency, with support from Europol and law enforcement agencies worldwide, targeted six administrators of Webstresser.org in the United Kingdom, Croatia, Canada and Serbia.
Today, the Dutch police, with assistance from Germany and the United States, seized infrastructure and effectively took down the webstresser.org website.
Furthermore, the authorities took measures against the top users of the marketplace, in the Netherlands, Italy, Spain, Croatia, the United Kingdom, Australia, Canada and Hong Kong.
In the UK, NCA officers searched an address in Bradford, supposedly linked to an individual who used the DDoS service to target seven of the UK’s biggest banks in attacks in November 2017, forcing them to shut down entire systems.
“We have a trend where the sophistication of certain professional hackers to provide resources is allowing individuals – and not just experienced ones – to conduct DDoS attacks and other kind of malicious activities online. It’s a growing problem, and one we take very seriously,” Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3), said.
DDoS attacks are illegal, Europol underlines. Anyone who gets involved could face severe penalties: conducting a DDoS attack or creating (supplying or obtaining) stresser or booter services could result in a prison sentence, a fine or both.
“Stresser websites make powerful weapons in the hands of cybercriminals. International law enforcement will not tolerate these illegal services and will continue to pursue its admins and users,” Jaap van Oss, Dutch Chairman of the Joint Cybercrime Action Taskforce (J-CAT), said.
According to Europol, many IT enthusiasts become involved in low-level fringe cybercrime activities, unaware of consequences. IT-related skills – either coding, gaming, computer programming, or cyber security – are in high demand and could be put to a positive use instead.
Internet Exposure, Flaws Put Industrial Safety Controllers at Risk of Attacks
26.4.2018 securityweek ICS
Applied Risk details safety controller flaws at ICS Cyber Security Conference Singapore
SINGAPORE — SECURITYWEEK 2018 ICS CYBER SECURITY CONFERENCE | SINGAPORE — Researchers have discovered a potentially serious vulnerability in industrial safety controllers and a significant number of the impacted devices are directly exposed to the Internet, making it easy for malicious actors to launch attacks and possibly cause damage.
Safety systems are designed to prevent incidents in industrial environments by restoring processes to a safe state or shut them down if parameters indicate a potentially hazardous situation. While these devices play an important role in ensuring physical safety, they can and have been targeted by malicious hackers. The best example is the Triton/Trisis/Hatman attack, which leveraged a zero-day vulnerability in Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers.
Researchers at industrial cybersecurity firm Applied Risk have analyzed safety controllers from several major vendors, including Siemens, ABB, Rockwell Automation’s Allen Bradley, Pilz, and Phoenix Contact.
The research is ongoing, but they have identified a denial-of-service (DoS) flaw that may affect several products. Details of the vulnerability were disclosed on Wednesday at SecurityWeek’s ICS Cyber Security Conference in Singapore by Gjoko Krstic, senior ICS security researcher at Applied Risk.
The vulnerability allows a remote attacker to cause a safety controller to reboot and enter faulted mode. Manual intervention is required to restore the device, Krstic told SecurityWeek in an interview.
The security hole can be leveraged to cause the device to enter a DoS condition by sending it a specially crafted TCP packet. Specifically, the attack relies on EtherNet/IP, one of the most widely used industrial network protocols.
Applied Risk researchers discovered that an attacker can cause safety controllers to fail by sending them a TCP packet that starts with the No Operation (NOP) option. Experts determined that, for some reason, safety controllers cannot handle incorrect TCP options.
Krstic says there is no other requirement for the attack to work. An attacker with access to the targeted controller, either from the Internet or the local network, can cause the device to become inoperable simply by sending it a packet.
An exploit has been tested by Applied Risk on Rockwell Automation’s Allen Bradley 1769 Compact GuardLogix 5370 controllers, but since the underlying issue is related to Ethernet/IP, researchers believe products from other vendors are likely affected as well.
All impacted vendors have been informed. Rockwell Automation, which has assigned CVE-2017-9312 to this vulnerability, is expected to release a patch and an advisory sometime in May.
Applied Risk has identified nearly a dozen Allen Bradley 1769 Compact GuardLogix 5370 controllers exposed directly to the Internet. However, the total number of safety controllers accessible from the Web is much higher. A Shodan search for the popular Siemens Simatic S7 devices, which include safety controllers, reveals nearly 900 results.
Given the significant role of safety controllers in industrial environments, causing a device to enter a DoS condition could have serious consequences, including physical damage to equipment and physical harm to people.
As the Triton/Trisis attack on Schneider Electric devices showed, writing malicious programs to a controller requires that the device’s key switch is set to “Program” mode. As part of its research into safety controllers, Applied Risk has been trying to find a way to remotely bypass the key switch and, while they have yet to succeed, experts are optimistic based on their progress so far.
Over 20 Million Users Installed Malicious Ad Blockers From Chrome Store
25.4.2018 thehackernews Virus
If you have installed any of the below-mentioned Ad blocker extension in your Chrome browser, you could have been hacked.
A security researcher has spotted five malicious ad blockers extension in the Google Chrome Store that had already been installed by at least 20 million users.
Unfortunately, malicious browser extensions are nothing new. They often have access to everything you do online and could allow its creators to steal any information victims enter into any website they visit, including passwords, web browsing history and credit card details.
Discovered by Andrey Meshkov, co-founder of Adguard, these five malicious extensions are copycat versions of some legitimate, well-known Ad Blockers.
Creators of these extensions also used popular keywords in their names and descriptions to rank top in the search results, increasing the possibility of getting more users to download them.
"All the extensions I've highlighted are simple rip-offs with a few lines of code and some analytics code added by the authors," Meshkov says.
After Meshkov reported his findings to Google on Tuesday, the tech giant immediately removed all of the following mentioned malicious ad blockers extension from its Chrome Store:
AdRemover for Google Chrome™ (10 million+ users)
uBlock Plus (8 million+ users)
[Fake] Adblock Pro (2 million+ users)
HD for YouTube™ (400,000+ users)
Webutation (30,000+ users)
Meshkov downloaded the ‘AdRemover’ extension for Chrome, and after analyzing it, he discovered that malicious code hidden inside the modified version of jQuery, a well-known JavaScript library, sends information about some websites a user visits back to a remote server.
Also Read: Someone Hijacks A Popular Chrome Extension to Push Malware
The malicious extension then receives commands from the remote server, which are executed in the extension 'background page' and can change your browser's behavior in any way.
To avoid detection, these commands send by the remote server are hidden inside a harmless-looking image.
"These commands are scripts which are then executed in the privileged context (extension's background page) and can change your browser behavior in any way," Meshkov says.
"Basically, this is a botnet composed of browsers infected with the fake Adblock extensions," Meshkov says. "The browser will do whatever the command center server owner orders it to do."
The researcher also analyzed other extensions on the Chrome Store and found four more extensions using similar tactics.
Also Read: Malicious Chrome Extension Hijacks CryptoCurrencies and Wallets
Since browser extension takes permission to access to all the web pages you visit, it can do practically anything.
So, you are advised to install as few extensions as possible and only from companies you trust.
Facebook Plans to Build Its Own Chips For Hardware Devices
25.4.2018 thehackernews Social 
A new job opening post on Facebook suggests that the social network is forming a team to build its own hardware chips, joining other tech titans like Google, Apple, and Amazon in becoming more self-reliant.
According to the post, Facebook is looking for an expert in ASIC and FPGA—two custom silicon designs to help it evaluate, develop and drive next-generation technologies within Facebook—particularly in artificial intelligence and machine learning.
The social media company is seeking to hire an expert who can "an end-to-end SoC/ASIC, firmware and driver development organization, including all aspects of front-end and back-end standard cell ASIC development," reads the job listing on Facebook's corporate website.
SoC (system-on-a-chip) is a processor typically used in mobile devices with all the components required to power a device, while ASIC (application-specific integrated circuit) is a customized piece of silicon designed for a narrow purpose that companies can gear toward something specific, like mining cryptocurrency.
FPGA (field programmable gate array) is an adaptable chip designed to be a more flexible and modular design that can be tuned to speed up specific jobs by running a particular piece of software.
First reported by Bloomberg, building its own processors would help the social media giant reduce dependency on companies such as Qualcomm and Intel, who hold the lion's share of the processor market.
Reportedly Apple, who already makes its own A-series custom chips for iPhones, iPads and other iThings, has planned to use its custom-designed ARM chips in Mac computers starting as early as 2020, replacing the Intel processors running on its desktop and laptop hardware.
Google has also developed its own artificial intelligence chip, and Amazon is reportedly designing its custom hardware to improve Alexa-equipped devices.
The plan to invest in building its own processors could help Facebook to power its artificial intelligence software, servers in its data centers, as well as its future hardware devices, like Oculus virtual reality headsets and smart speakers (similar to Amazon Echo and Google Home).
Using its custom chips would also allow the social media company to gain more control over its own hardware roadmap better and eventual feature set to offer better performance to its users.
Facebook has not commented on the news yet, so at this time, it is hard to say where the company will deploy its in-house chips.
'iTunes Wi-Fi Sync' Feature Could Let Attackers Hijack Your iPhone, iPad Remotely
25.4.2018 thehackernews Apple
Be careful while plugging your iPhone into a friend's laptop for a quick charge or sharing selected files.
Researchers at Symantec have issued a security warning for iPhone and iPad users about a new attack, which they named "TrustJacking," that could allow someone you trust to remotely take persistent control of, and extract data from your Apple device.
Apple provides an iTunes Wi-Fi sync feature in iOS that allows users to sync their iPhones to a computer wirelessly. To enable this feature, users have to grant one-time permission to a trusted computer (with iTunes) over a USB cable.
Once enabled, the feature allows the computer owner to secretly spy on your iPhone over the Wi-Fi network without requiring any authentication, even when your phone is no longer physically connected to that computer.
"Reading the text, the user is led to believe that this is only relevant while the device is physically connected to the computer, so assumes that disconnecting it will prevent any access to his private data," Symantec said.
Since there is no noticeable indication on the victim's device, Symantec believes the feature could exploit the "relation of trust the victim has between his iOS device and a computer."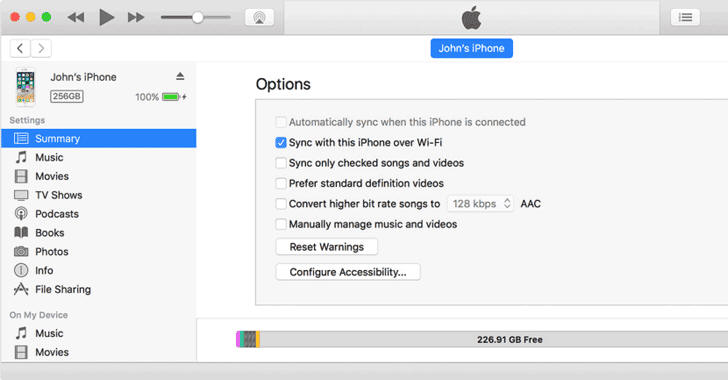
Researchers suggest following scenarios where TrustJacking attack can be successfully performed, especially when you trust a wrong computer:
Connecting your phone to a free charger at an airport, and mistakenly approving the pop-up permission message to trust the connected station.
A remote attacker, not in the same Wi-Fi network can also access iPhone data if the device owner's own "trusted" PC or Mac has been compromised by malware.
Moreover, iTunes Wi-Fi sync feature could also be used to remotely install malware apps on your iPhone, as well as to download a backup and steal all your photos, SMS / iMessage chats history, and application data.
"An attacker can also use this access to the device to install malicious apps, and even replace existing apps with a modified wrapped version that looks exactly like the original app, but is able to spy on the user while using the app and even leverage private APIs to spy on other activities all the time," Symantec said.
The TrustJacking attack could also allow trusted computers to watch your device's screen in real-time by repeatedly taking remote screenshots, observing and recording your every action.
Apple has now introduced another security layer in iOS 11, asking users to enter their iPhone's passcode while pairing their iPhone with a computer, after getting notified by the Symantec researchers.
However, Symantec says the loophole remains open, as the patch does not address the primary concern, i.e., the absence of noticeable indication or mandatory re-authentication between the user's device and the trusted computer after a given interval of time.
"While we appreciate the mitigation that Apple has taken, we’d like to highlight that it does not address Trustjacking in a holistic manner," Symantec's Roy Iarchy said. "Once the user has chosen to trust the compromised computer, the rest of the exploit continues to work as described above."
The best and simple way to protect yourself is to ensure that no unwanted computers are being trusted by your iOS device. For this, you can remove the trusted computers list by going to Settings → General → Reset → Reset Location & Privacy.
Also, most important, always deny the access when asked to trust the computer while charging your iOS device. Your device would still charge using the computer, without exposing your data.
Another Critical Flaw Found In Drupal Core—Patch Your Sites Immediately
25.4.2018 thehackernews Vulnerebility

It's time to update your Drupal websites, once again.
For the second time within a month, Drupal has been found vulnerable to another critical vulnerability that could allow remote attackers to pull off advanced attacks including cookie theft, keylogging, phishing and identity theft.
Discovered by the Drupal security team, the open source content management framework is vulnerable to cross-site scripting (XSS) vulnerability that resides in a third-party plugin CKEditor which comes pre-integrated in Drupal core to help site administrators and users create interactive content.
CKEditor is a popular JavaScript-based WYSIWYG rich text editor which is being used by many websites, as well as comes pre-installed with some popular web projects.
According to a security advisory released by CKEditor, the XSS vulnerability stems from the improper validation of "img" tag in Enhanced Image plugin for CKEditor 4.5.11 and later versions.
This could allow an attacker to execute arbitrary HTML and JavaScript code in the victim's browser and gain access to sensitive information.
Enhanced Image plugin was introduced in CKEditor 4.3 and supports an advanced way of inserting images into the content using an editor.
"The vulnerability stemmed from the fact that it was possible to execute XSS inside CKEditor when using the image2 plugin (which Drupal 8 core also uses)," the Drupal security team said.
CKEditor has patched the vulnerability with the release of CKEditor version 4.9.2, which has also been patched in the CMS by the Drupal security team with the release of Drupal version 8.5.2 and Drupal 8.4.7.
Since CKEditor plugin in Drupal 7.x is configured to load from the CDN servers, it is not affected by the flaw.
However, if you have installed the CKEditor plugin manually, you are advised to download and upgrade your plugin to the latest version from its official website.
Drupal recently patched another critical vulnerability, dubbed Drupalgeddon2, a remote code execution bug that allows an unauthenticated, remote attacker to execute malicious code on default or common Drupal installations under the privileges of the user, affecting all versions of Drupal from 6 to 8.
However, due to people's laziness of patching their systems and websites timely, the Drupalgeddon2 vulnerability has been found exploiting in the wild by hackers to deliver cryptocurrency miners, backdoors, and other malware.
Therefore, users are highly recommended always to take security advisories seriously and keep their systems and software up-to-date in order to avoid become victims of any cyber attack.
Cybercriminals Hijack Router DNS to Distribute Android Banking Trojan
25.4.2018 thehackernews Android
Security researchers have been warning about an ongoing malware campaign hijacking Internet routers to distribute Android banking malware that steals users' sensitive information, login credentials and the secret code for two-factor authentication.
In order to trick victims into installing the Android malware, dubbed Roaming Mantis, hackers have been hijacking DNS settings on vulnerable and poorly secured routers.
DNS hijacking attack allows hackers to intercept traffic, inject rogue ads on web-pages and redirect users to phishing pages designed to trick them into sharing their sensitive information like login credentials, bank account details, and more.
Hijacking routers' DNS for a malicious purpose is not new. Previously we reported about widespread DNSChanger and Switcher—both the malware worked by changing the DNS settings of the wireless routers to redirect traffic to malicious websites controlled by attackers.
Discovered by security researchers at Kaspersky Lab, the new malware campaign has primarily been targeting users in Asian countries, including South Korea, China Bangladesh, and Japan, since February this year.
Once modified, the rogue DNS settings configured by hackers redirect victims to fake versions of legitimate websites they try to visit and displays a pop-up warning message, which says—"To better experience the browsing, update to the latest chrome version."
It then downloads the Roaming Mantis malware app masquerading as Chrome browser app for Android, which takes permission to collect device’ account information, manage SMS/MMS and making calls, record audio, control external storage, check packages, work with file systems, draw overlay windows and so on.
"The redirection led to the installation of Trojanized applications named facebook.apk and chrome.apk that contained Android Trojan-Banker."
If installed, the malicious app overlays all other windows immediately to show a fake warning message (in broken English), which reads, "Account No.exists risks, use after certification."
Roaming Mantis then starts a local web server on the device and launches the web browser to open a fake version of Google website, asking users to fill up their names and date of births.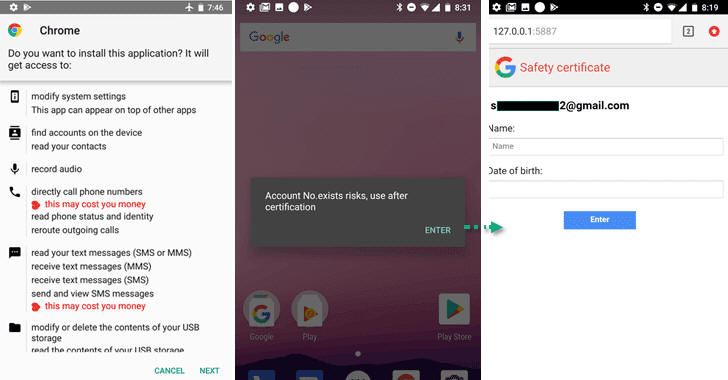
To convince users into believing that they are handing over this information to Google itself, the fake page displays users' Gmail email ID configured on their infected Android device, as shown in the screenshots.
"After the user enters their name and date of birth, the browser is redirected to a blank page at http://127.0.0.1:${random_port}/submit," researchers said. "Just like the distribution page, the malware supports four locales: Korean, Traditional Chinese, Japanese and English."
Since Roaming Mantis malware app has already gained permission to read and write SMS on the device, it allows attackers to steal the secret verification code for the two-factor authentication for victims' accounts.
While analysing the malware code, Researchers found reference to popular South Korean mobile banking and gaming applications, as well as a function that tries to detect if the infected device is rooted.
"For attackers, this may indicate that a device is owned by an advanced Android user (a signal to stop messing with the device) or, alternatively, a chance to leverage root access to gain access to the whole system," the researchers said.
What's interesting about this malware is that it uses one of the leading Chinese social media websites (my.tv.sohu.com) as its command-and-control server and sends commands to infected devices just via updating the attacker-controlled user profiles.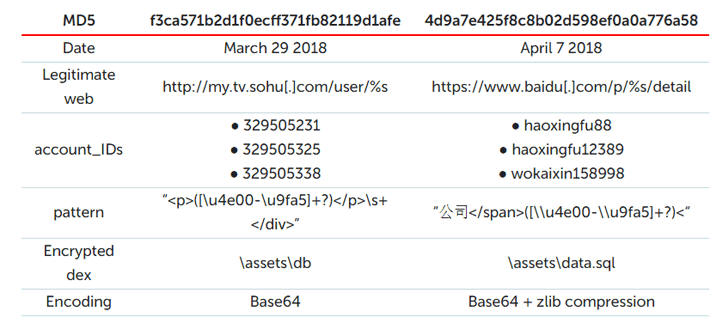
According to Kaspersky's Telemetry data, the Roaming Mantis malware was detected more than 6,000 times, though the reports came from just 150 unique users.
You are advised to ensure your router is running the latest version of the firmware and protected with a strong password.
You should also disable router's remote administration feature and hardcode a trusted DNS server into the operating system network settings.
Microsoft built its own custom Linux OS to secure IoT devices
25.4.2018 thehackernews IoT
Finally, it's happening.
Microsoft has built its own custom Linux kernel to power "Azure Sphere," a newly launched technology that aims to better secure billions of "Internet of things" devices by combining the custom Linux kernel with new chip design, and its cloud security service.
Project Azure Sphere focuses on protecting microcontroller-based IoT devices, including smart appliances, connected toys, and other smart gadgets, Microsoft announced during the security-focused RSA Conference in San Francisco Monday.
It is basically a security package consists of three main components:
Azure Sphere-certified microcontrollers (MCUs)
Azure Sphere OS
Azure Sphere Security Service
"Azure Sphere provides security that starts in the hardware and extends to the cloud, delivering holistic security that protects, detects, and responds to threats—so they're always prepared," Microsoft said.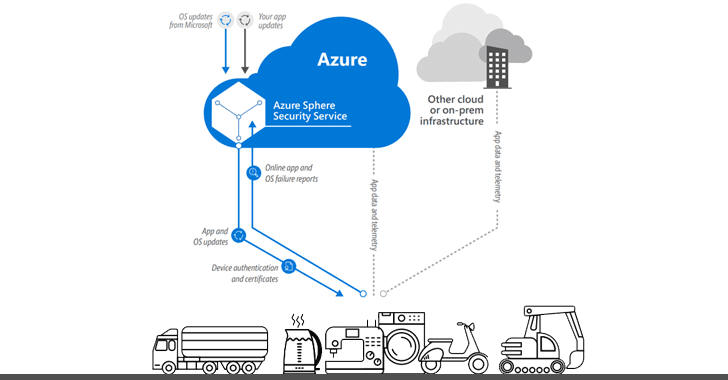
Internet of Things (IoT) devices are 'ridiculously' vulnerable to remote hacking, because they are not originally manufactured keeping security in mind.
One innocent looking insecure IoT device connected to your 'secured network' would be enough to cause security nightmares. In the past, we have seen how lack of security by design led to massive DDoS attacks powered by Mirai IoT botnet.
To address such issues, Azure Sphere offers a full-fledged solution that provides the best-in-class security and a trustworthy environment for future IoT devices, and at the same time makes the life of IoT device manufactures a lot easier.
Azure Sphere Certified Microcontrollers (MCUs)
Designed by Microsoft Research, the Azure Sphere Certified Microcontrollers is a new cross-over class of fixed-functional microcontroller chips that will be licensed to manufacturing partners for free, which comes with built-in connectivity, networking and Pluton security subsystems to ensure the security of future IoT devices.
These MCUs "combines both real-time and application processors with built-in Microsoft security technology and connectivity," Microsoft explains.
"The Pluton Security Subsystem creates a hardware root of trust, stores private keys, and executes complex cryptographic operations," Microsoft said. "A new crossover MCU combines the versatility and power of a Cortex-A processor with the low overhead and real-time guarantees of a Cortex-M class processor."
"Each chip includes custom silicon security technology from Microsoft, inspired by 15 years of experience and learnings from Xbox, to secure this new class of MCUs and the devices they power," the company adds.
According to Microsoft president Brad Smith, the first Azure Sphere chip, called the "MT3620," will be made by Taiwan-based MediaTek and to be available in stores worldwide by the end of the year.
The Azure Sphere chips will also be compatible with other cloud services like Google Cloud, Amazon Web Services, and Oracle Cloud.
Azure Sphere OS (Linux-based)
The second component of the solution, called Azure Sphere OS, is a "defense-in-depth" operating system that comes with a security monitor and Microsoft's custom Linux kernel to offer multiple layers of security.
"Each Azure Sphere chip will include our Microsoft Pluton security subsystem, run the Azure Sphere OS, and connect to the Azure Sphere Security Service for simple and secure updates, failure reporting, and authentication," Microsoft says.
It is the first time when Microsoft created hardware that is designed to run only Linux, rather than its Windows operating system.
"We are a Windows company, but what we recognized is that the best solution for a computer of this size in a toy is not a full-blown version of Windows," Smith said. "It is a custom Linux Kernel, and it is an important step for us and the industry."
Azure Sphere Security Service (Cloud-based)
On top of everything, Azure Sphere Security Service is a cloud-based service that handles security and management of microcontroller chips.
The service offers device-to-device and device-to-cloud communication through certificate-based authentication to guards every Azure Sphere device.
It detects emerging security threats across the entire Azure Sphere ecosystem and also takes care of software updates.
Azure Sphere is now available in private preview, and the company will distribute software development kits to everyone interested in hacking Azure Sphere by the middle of this year. To find more details about Azure Sphere, you can head on to Microsoft Azure Sphere's blog.
Intel Processors Now Allows Antivirus to Use Built-in GPUs for Malware Scanning
25.4.2018 thehackernews Safety
Global chip-maker Intel on Tuesday announced two new technologies—Threat Detection Technology (TDT) and Security Essentials—that not only offer hardware-based built-in security features across Intel processors but also improve threat detection without compromising system performance.
Intel's Threat Detection Technology (TDT) offers a new set of features that leverage hardware-level telemetry to help security products detect new classes of threats and exploits.
It includes two main capabilities—Accelerated Memory Scanning and Advanced Platform Telemetry.
Accelerated Memory Scanning allows antivirus programs to use Intel's integrated GPU to scan and detect memory-based malware attacks while reducing the impact on performance and power consumption.
"Current scanning technologies can detect system memory-based cyber-attacks, but at the cost of CPU performance," says Rick Echevarria, Intel security division Vice President.
"With Accelerated Memory Scanning, the scanning is handled by Intel's integrated graphics processor, enabling more scanning, while reducing the impact on performance and power consumption."
According to Intel, early tests using the new GPU-accelerated scanning technique suggest that CPU utilization for malware threat scans "dropped from 20 percent to as little as 2 percent"—that's obviously a massive increase in efficiency.
The other TDT feature is Intel Advanced Platform Telemetry that incorporates cloud-based machine learning and endpoint data collection to better identify potential security threats, "while reducing false positives and minimizing performance impact."
Intel's new Thread Detection Technology solution will be available for computers with 6th, 7th, and 8th generation Intel processors, though it's up to third-party antivirus vendors to actually utilize the feature.
Microsoft and Cisco are the first ones to make use of Intel's Threat Detection Technology (TDT), with the Intel TDT coming to Windows Defender Advanced Protection Threat (ATP) this month.
The second security solution launched by the chip maker is Intel Security Essentials—a built-in toolkit which includes a bunch of different hardware-based security features available across Intel Core, Xeon, and Atom processors.
Intel Security Essentials has following properties that offer a chain of trust to protect against a wide range of attacks:
Hardware Root of Trust—Cryptographic keys protected by hardware
Small Trusted Computing Base—Protecting keys, IDs, and data using hardware trusted platform module (TPM)
Defence in Depth—Hardware and software protection
Compartmentalization—Hardware-enforced barriers between software components
Direct Anonymous Authentication—Cryptographic schemes to offer anonymous authentication of a device for privacy (especially for IoT devices)
HW Security escalation—Enabling hardware acceleration of cryptographic calculation, antivirus scanning, and key generation
The announcement comes after serious security vulnerabilities—Meltdown and Spectre—badly hit Intel CPUs and chips from other companies earlier this year, and the security patches rolled out by the companies increased load for the CPU, affecting device performance.
CCleaner Attack Timeline—Here's How Hackers Infected 2.3 Million PCs
25.4.2018 thehackernews Attack
Last year, the popular system cleanup software CCleaner suffered a massive supply-chain malware attack of all times, wherein hackers compromised the company's servers for more than a month and replaced the original version of the software with the malicious one.
The malware attack infected over 2.3 million users who downloaded or updated their CCleaner app between August and September last year from the official website with the backdoored version of the software.
Now, it turns out that the hackers managed to infiltrate the company's network almost five months before they first replaced the official CCleaner build with the backdoored version, revealed Avast executive VP and CTO Ondrej Vlcek at the RSA security conference in San Francisco on Tuesday.
6-Months Timeline of CCleaner Supply Chain Attack
Vlcek shared a brief timeline of the last year's incident that came out to be the worst nightmare for the company, detailing how and when unknown hackers breached Piriform, the company that created CCleaner and was acquired by Avast in July 2017.
March 11, 2017 (5 AM local time)—Attackers first accessed an unattended workstation of one of the CCleaner developers, which was connected to Piriform network, using remote support software TeamViewer.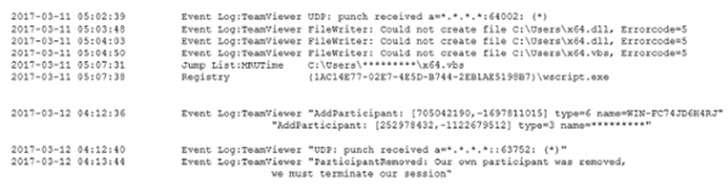
The company believes attackers reused the developer's credentials obtained from previous data breaches to access the TeamViewer account and managed to install malware using VBScript on the third attempt.
March 12, 2017 (4 AM local time)—Using the first machine, attackers penetrated into the second unattended computer connected to the same network and opened a backdoor through Windows RDP (Remote Desktop Service) protocol.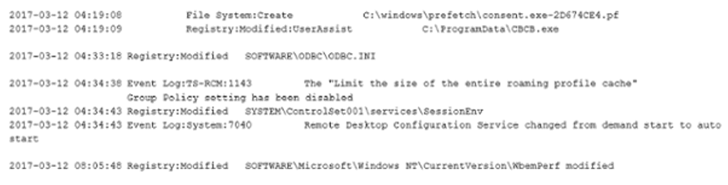
Using RDP access, the attackers dropped a binary and a malicious payload—a second stage malware (older version) that was later delivered to 40 CCleaner users—on the target computer's registry.
March 14, 2017—Attackers infected the first computer with the older version of the second stage malware as well.
April 4, 2017—Attackers compiled a customised version of ShadowPad, an infamous backdoor that allows attackers to download further malicious modules or steal data, and this payload the company believes was the third stage of the CCleaner attack.
April 12, 2017—A few days later, attackers installed the 3rd stage payload on four computers in the Piriform network (as a mscoree.dll library) and a build server (as a .NET runtime library).
Between mid-April and July—During this period, the attackers prepared the malicious version of CCleaner, and tried to infiltrate other computers in the internal network by installing a keylogger on already compromised systems to steal credentials, and logging in with administrative privileges through RDP.
July 18, 2017—Security company Avast acquired Piriform, the UK-based software development company behind CCleaner with more than 2 billion downloads.
August 2, 2017—Attackers replaced the original version of CCleaner software from its official website with their backdoored version of CCleaner, which was distributed to millions of users.
September 13, 2017—Researchers at Cisco Talos detected the malicious version of the software, which was being distributed through the company's official website for more than a month, and notified Avast immediately.
The malicious version of CCleaner had a multi-stage malware payload designed to steal data from infected computers and send it back to an attacker-controlled command-and-control server.
Although Avast, with the help of the FBI, was able to shut down the attackers' command-and-control server within three days of being notified of the incident, the malicious CCleaner software had already been downloaded by 2.27 million users.
Moreover, it was found that the attackers were then able to install a second-stage payload on 40 selected computers operated by major international technology companies, including Google, Microsoft, Cisco, Intel, Samsung, Sony, HTC, Linksys, D-Link, Akamai and VMware.
However, the company has no proofs if the third stage payload with ShadowPad was distributed to any of these targets.
"Our investigation revealed that ShadowPad had been previously used in South Korea, and in Russia, where attackers intruded a computer, observing a money transfer." Avast said.
"The oldest malicious executable used in the Russian attack was built in 2014, which means the group behind it might have been spying for years."
Based on their analysis of the ShadowPad executable from the Piriform network, Avast believes that the malicious attackers behind the malware have been active for a long time, spying on institutions and organizations so thoroughly.