
Information Warfare At Bay – The Dangers of Russian Menace to Underwater Internet Critical Infrastructure
19.12.2017 securityaffairs BigBrothers
British Armed Forces chief has warned that Russia could compromise underwater communication cables causing severe damage to the financial global economy
It came as silently as a fatal heart stroke, and now the dangers of Russian Cyber Warfare materializes into reality.
Join us to uncover this cripple and stealth threat to our global community.
As defined by the Briefing European Parliamentary Research Service, “Hybrid conflict is a situation in which parties to the conflict refrain from the overt use of armed forces against each other, relying instead on a combination of military intimidation (falling short of an attack), exploitation of economic and political vulnerabilities, and diplomatic or technological means to pursue their objectives.”
In this regard, we take a special account in Russia development of Electronic Warfare and Navy developments to further advance conventional and unconventional threats to US and Allies.
As reported in many media outlets, Air Chief Marshal Sir Stuart Peach, who heads the British Armed Forces, in a speech to the Royal United Services Institute, has warned that Russia could compromise underwater communication cables causing severe damage to the financial global economy. As reported by BBC, “Russia is upgrading and advancing it’s use of conventional and unconventional warfare,” especially in the fifth domain: The Cyberspace.
Russian ships have been spotted regularly near the Atlantic cables and according to Marshal Peach, it is due to the lack of investments in upgrading UK Navy to match the developments of Russia Navy. The Marshal also notice that there are not enough UK ships to monitor the activities of Russia Navy. It is important to notice that since the annexation of Crimea, Russia is developing new technologies of Electronic Warfare which is putting in danger the global security.

Besides the economic danger to UK and US economies, Russian ships can also try to wiretapping and disrupt communications that could cause great danger to the intelligence community and national security of many countries.
The news comes in the midst of scandals involving Russian meddling in US election and the use of Kaspersky software, recently banned from US Government use, to spy on US Government Data. This brings some serious concerns about how secure we are in this interconnected world we live in. A new Theater of Operations is presented were rogue nations can seriously damage our way of live.
It is a serious concern since that Russia is not alone trying to undermine the world, as it has a partnership with Iran, North Korea, Syria, China and Brazil trying to destabilize the global security and economy. We must notice that to China and Brazil had contributed to Russia Cyber Upgrade since this two countries are the leading source of software piracy that causes serious economic losses and exposures to organizations around the world. In Brazil, for example, a copy of Microsoft Windows is sold for 3 dollars on the streets of Santa Ifigênia.
The US and Europe must take a firm stance with sanctions against those rogue nations and maintain an up to date investment in Navy to continuously monitor any activity that could lead to dangers to the global security. Also according to BBC, it is estimated that 97% of global communications are transmitted by underwater cables, and approximately 10 trillion of financial transaction is negotiated on a daily basis through these cables. Any scenario involving an attack to this critical infrastructure could lead not only to an enormous loss of money but also to an enormous loss of life and the collapse of modern society due to its implications on supply chain and product delivery.
Sources:
http://www.natolibguides.info/hybridwarfare/reports
https://www.icds.ee/fileadmin/media/icds.ee/doc/ICDS_Report_Russias_Electronic_Warfare_to_2025.pdf
Russia’s Neighbors Respond to Putin’s ‘Hybrid War’
http://www.armyupress.army.mil/Journals/Military-Review/Online-Exclusive/2017-Online-Exclusive-Articles/Russian-Actions-and-Methods/
[1]http://www.europarl.europa.eu/RegData/etudes/BRIE/2017/599315/EPRS_BRI(2017)599315_EN.pdf
https://rusi.org/event/annual-chief-defence-staff-lecture-2017
https://www.theregister.co.uk/2017/12/15/russia_cable_chop_warning_chief_of_defence_staff/
https://www.washingtontimes.com/news/2017/dec/15/britain-warns-russian-threat-undersea-internet-cab/
Networked Printers are Some of the Oldest IoT Devices, and over 1,000 Lexmark Printers Are Vulnerable Today
19.12.2017 securityaffairs Vulnerebility
Experts at NewSky Security scanned the Internet and discovered that “out of 1,475 unique IPs, 1,123 Lexmark printers had no security.”
We think of Internet of Things (IoT) as all the “new” devices added to networks like webcams, Internet-connected toys, smarthome devices, etc. But we have been connecting unattended things to networks for a very long time with office printers being some of the earliest. With new IoT threats emerging every day, network-connected printers are once again increasing cyber risk for organizations. This week we learn that more than one thousand Lexmark printers are connected to the Internet with no security.
NewSky Security performed a search for Internet-connected Lexmark printers through the search engine for the Internet of Things, Shodan. They were able to determine that, “out of 1,475 unique IPs, 1,123 Lexmark printers had no security.“ That means that anyone on the Internet can access the printer’s admin setup at hxxp://example.ip/cgi-bin/dynamic/printer/config/secure/authsetup.htmlwhere example.ip is the IP address of the printer as identified in Shodan. Once at this page, the visitor can set up a new password and proceed to reconfigure the printer as they wish.
You might wonder what is going on here. Why are printers added to networks with no security? This is the same situation that leads to every IoT compromise and things like the Mirai botnet. Vendors make it simple to get their equipment up and running. In most cases, it is plugged into the network and it starts working. If the person performing the installation is satisfied with the minimum requirements, their work is complete. Anticipating that some users will want to configure their devices once they are on the network, vendors allow remote access through common web interfaces. Without a firewall between the device and the Internet, anyone with a web browser can access the admin pages. We have seen this same scenario played out on webcams, routers, DVRs, and now Lexmark printers.
NewSky Security determined that at least one of the insecure Lexmark printers was in use by Lafayette Consolidate Government and several others are in use by universities. They also identified vulnerable Lexmark printers in many different countries with the majority in the United States.
The problem isn’t with IoT devices in general or Lexmark printers specifically. As long as the devices can be secured, the vendors are doing the right thing. It is up to users to understand the implications of installing equipment on Internet-connected networks and taking the appropriate steps to secure that equipment. There is rarely a reason for a physical device like a printer to be accessible directly from the Internet. A firewall takes care of the basics and then make sure you change default passwords. It isn’t difficult to secure these devices, but it takes a little more than plugging it in and turning it on.
Kaspersky Lab files Lawsuit over DHS Ban of its products and services
19.12.2017 securityaffairs BigBrothers
Kaspersky Lab sues the U.S. Government over product ban, it’s appeal was filed in the U.S. District Court for the District of Columbia.
Last week, the US President Donald Trump signed a bill that bans the use of Kaspersky Lab products and services in federal agencies.
Section 1634 of the bill prohibits the use of security software and services provided by security giant, the ban will start from October 1, 2018.
Below the details of the ban included in the section 1634 of the National Defense Authorization Act for Fiscal Year 2018.
“SEC. 1634. Prohibition on use of products and services developed or provided by Kaspersky Lab.
(a) Prohibition.—No department, agency, organization, or other element of the Federal Government may use, whether directly or through work with or on behalf of another department, agency, organization, or element of the Federal Government, any hardware, software, or services developed or provided, in whole or in part, by—
(1) Kaspersky Lab (or any successor entity);
(2) any entity that controls, is controlled by, or is under common control with Kaspersky Lab; or
(3) any entity of which Kaspersky Lab has majority ownership.
(b) Effective date.—The prohibition in subsection (a) shall take effect on October 1, 2018.”
Now the security firm sues the U.S. Government over product ban, it’s appeal was filed in the U.S. District Court for the District of Columbia and targets the DHS’s Binding Operational Directive 17-01.
Kaspersky considers the ban as unconstitutional, according to the company the US Government took the decision to prohibit its products based on reports citing anonymous sources without strong evidence of its involvement in cyber espionage activities.
Kaspersky claims to have offered its support to the DHS for its investigation, but the agency issued the 17-01 directive, banning its security software and services without any warning.
The company sustains the DHS should have given it the opportunity to view the information before the directive was issued.
On the other side, Eugene Kaspersky was invited to testify before Congress in September, but he was unable to travel to the U.S. in time for the hearing due to visa problems.
A second hearing was announced for October, but Kaspersky was not invited to testify.
kaspersky
The decision of the US Government is having a significant impact on the brand reputation with a consequent effect on the sales in almost any sector and any country.
“Through Binding Operational Directive 17-01, DHS has harmed Kaspersky Lab’s reputation, negatively affected the livelihoods of its U.S.-based employees and U.S.-based business partners, and undermined the company’s contributions to the broader cybersecurity community,” said Eugene Kaspersky, CEO and co-founder of Kaspersky Lab.

Eugene Kaspersky
✔
@e_kaspersky
What to do when banned without evidence and the right to be heard? Well, we’re securing our rights by taking this to the courts. Why? We’ve done nothing wrong. https://kas.pr/nj7j
#SecurityWithoutBorders
7:40 PM - Dec 18, 2017
8 8 Replies 81 81 Retweets 114 114 likes
Twitter Ads info and privacy
“Dissuading consumers and businesses in the United States and abroad from using Kaspersky Lab products solely because of its geographic origins and without any credible evidence does not constitute a risk-based approach to cybersecurity and does little to address information security concerns related to government networks,” Eugene Kaspersky added.
The security firm also announced a new transparency initiative that involves giving partners access to source code to exclude the presence of backdoors, it also proposed to pay huge bug bounties for vulnerabilities found in its security solutions.
Kaspersky Sues U.S. Government Over Product Ban
19.12.2017 securityweek BigBrothers
Kaspersky Lab has filed a lawsuit against the U.S. government in response to the decision of the Department of Homeland Security (DHS) to ban the use of the company’s products in federal agencies.
The Russia-based cybersecurity firm’s appeal, filed in the U.S. District Court for the District of Columbia, targets the DHS’s Binding Operational Directive 17-01, which the agency issued in mid-September. President Donald Trump reinforced the ban last week when he signed the National Defense Authorization Act for FY2018.
Kaspersky says the ban is unconstitutional as it infringes the company’s due process rights. Kaspersky believes the DHS should have given it the opportunity to view the information and contest it before the directive was issued.
The company’s lawsuit also alleges that the decision to prohibit its products in federal agencies is largely based on rumors and media reports citing anonymous sources. While some believe the U.S. government may have actual evidence that Kaspersky Lab has been aiding Russia’s espionage efforts, no proof has been presented and even some officials appear to base their accusations on news reports.
Kaspersky claims that it voluntarily reached out to the DHS in July and offered to assist with any investigation into the company and its products. While the agency seemed to appreciate the offer and promised to get it touch, it did not do so, and instead it issued the 17-01 directive, banning the company’s software and services without warning.
The security firm says that while only a relatively small percentage of its revenue comes from the U.S. government, the DHS’s actions have had a negative impact on sales in other sectors, in both the United States and other countries.
“Through Binding Operational Directive 17-01, DHS has harmed Kaspersky Lab’s reputation, negatively affected the livelihoods of its U.S.-based employees and U.S.-based business partners, and undermined the company’s contributions to the broader cybersecurity community,” said Eugene Kaspersky, CEO and co-founder of Kaspersky Lab.
A majority of the accusations against Kaspersky Lab stem from its founder’s former ties to Russian intelligence. However, the CEO pointed out that most of the intelligence reports published by the company in the past years targeted Russian-speaking espionage groups.
In response to claims by U.S. officials that Kaspersky’s software is dangerous due to the deep level of access and privileges it requires, the Russian businessman highlighted that these capabilities are present in all security products and it’s unfair to single out his company without any evidence of wrongdoing.
“Dissuading consumers and businesses in the United States and abroad from using Kaspersky Lab products solely because of its geographic origins and without any credible evidence does not constitute a risk-based approach to cybersecurity and does little to address information security concerns related to government networks,” Eugene Kaspersky said.
Kaspersky has attempted to clear its name by launching a new transparency initiative that involves giving partners access to source code and paying significantly larger bug bounties for vulnerabilities found in the firm’s products.
Eugene Kaspersky was invited to testify before Congress in September, but he was unable to travel to the U.S. in time for the hearing due to visa problems. A second hearing was announced for October, but the cyber security tycoon was not invited.
Barclays Bank Employee Jailed for Role in Malware Scheme
18.12.2017 securityweek Virus
A Barclays bank employee in London has been sentenced to six years and four months in jail for his role in a scheme to launder money stolen using the Dridex banking Trojan.
Jinal Pethad, 29, worked with money launderers Pavel Gincota and Ion Turcan to set up 105 fraudulent bank accounts for them, in an attempt to launder over £2.5 million ($3.34 million).
To ensure that the bank’s security processes didn’t block the stolen funds, Pethad was managing the accounts personally, the UK’s National Crime Agency says.
The individual was arrested in November 2016, one month after Gincota and Turcan were jailed for the conspiracy. Pethad pleaded guilty last week to conspiring to launder money between 2014 and 2016.
When searching Pethad’s home, NCA officers found over £4,000 ($5,300) in cash, 7 luxury watches, and 3 mobile phones that had been used to communicate with Gincota. Text messages on one of the phones revealed that Gincota and Pethad were making arrangements to open fraudulent accounts.
“Jinal Pethad abused his position of trust at the bank to knowingly set up sham accounts for Gincota and Turcan, providing a vital service which enabled them to launder millions. Using his knowledge of the financial system, he made sure the stolen money was not blocked before entering these accounts, and provided the pair with reports to evidence his efforts and maintain the criminal relationship,” Mark Cains from the NCA’s National Cyber Crime Unit, said.
Dridex, the malware used to steal the laundered funds, is a successor of the Cridex Trojan, has been around for several years and is currently one of the most prolific banking Trojans out there.
Not only did Dridex survive a takedown attempt in October 2015, but its activity has increased since. Last year, the actors behind Dridex launched the Locky ransomware and have been operating both ever since.
California Voter Data Stolen from Insecure MongoDB Database
18.12.2017 securityweek Incindent
An improperly secured MongoDB database has provided cybercriminals with the possibility to steal information on the entire voting population of California, Kromtech security researchers reported.
The information was taken from an unprotected instance of a MongoDB database that was exposed to the Internet, meaning that anyone connected to the web could have accessed, viewed, or edited the database’s content.
Named 'cool_db', the database contained two collections, one being a manually crafted set of voter registration data for a local district, while the other apparently including data on the voting population from the entire state of California: a total of 19,264,123 records.
Bob Diachenko, head of communications, Kromtech Security Center, explains that the security firm was “unable to identify the owner of the database or conduct a detailed analysis.” It appears that the database has been erased by cybercriminals who dropped a ransom note demanding 0.2 Bitcoin for the data.
Given the presence of said ransom note, the incident is believed to be related to the MongoDB ransack campaign that resulted in tens of thousands of databases being erased in January 2017. Similar attacks were observed in September as well, when MongoDB decided to implement new data security measures.
“We were able to analyze the stats data we saw in our report (metadata on total number of records, uptime, names of the collection etc.), as well as 20-records sample extracted from the database shortly before it has been wiped out and ransom note appeared,” Diachenko says.
Kromtech's security researchers haven’t determined who compiled the voter database but believe that a political action committee might have been behind it, given the unofficial name the repository had.
The miscreants behind the attack used ransomware to wipe out the voter data, but are believed to have copied the database to their server first. “Once in the hands of cyber criminals this voter data could end up for sale on the Dark Web. If this were an official database, deleting parts of that data could affect someone’s voting process,” the security researchers note.
The first, smaller collection (4GB) contained data structured with rows containing many fields that included home address, phone number, date of birth, and many more.
Based on EstractDate information, the database appears to have been created on May 31, 2017.
The second, much larger collection (22GB) in the database, which appears to be the complete California voter registration records, contains a total of 409,449,416 records.
The data in the larger collection includes: District, RegistrantId, CountyCode, DistrictName and ObjectId.
“This is a massive amount of data and a wakeup call for millions citizens of California who have done nothing more than fulfil the civic duty to vote. This discovery highlights how a simple human error of failing to enact the basic security measures can result in a serious risk to stored data. The MongoDB was left publically available and was later discovered by cyber criminals who seemed to steal the data, which origin is still unknown,” Diachenko concludes.
The researchers note that the database has been taken down after being initially discovered in early December. The Secretary of State of California was aware of the leak and “looking into it,” Diachenko said.
Pentagon Hacked in New U.S. Air Force Bug Bounty Program
18.12.2017 securityweek BigBrothers
The Hack the Air Force 2.0 bug bounty program kicked off earlier this month with researchers finding a critical vulnerability that could have been exploited to gain access to a network of the U.S. Department of Defense.
Hack the Air Force 2.0 started on December 9 with a live hacking competition hosted by the HackerOne platform at the WeWork Fulton Center inside the Fulton Center subway station in New York City.
During the event, Mathias Karlsson and Brett Buerhaus demonstrated how malicious actors could have breached an unclassified DoD network by exploiting a vulnerability in the Air Force’s website. They earned $10,650 for their findings, which is the largest single payout coming from any bug bounty program run by the U.S. government.
Seven U.S. Airmen and 25 civilian white hat hackers discovered a total of 55 vulnerabilities during the event, for which they earned $26,883.Hack the Air Force 2.0 bug bounty program
Hack the Air Force 2.0 will run until January 1, 2018 and anyone can apply as long as they are a citizen or a permanent resident of Five Eyes countries, NATO countries, or Sweden. People from 31 countries can take part in the initiative, which makes it the most open government bug bounty program to date. Members of the U.S. military can also participate, but they are not eligible for bounties.
While anyone from these countries can apply, not everyone will be invited to actually take part. The Air Force will invite 600 people, 70 percent of which based on their HackerOne reputation score and the other 30 percent will be selected randomly.
“Hack the Air Force allowed us to look outward and leverage the range of talent in our country and partner nations to secure our defenses,” said Air Force CISO Peter Kim. “We're greatly expanding on the tremendous success of the first challenge by opening up approximately 300 public facing AF websites. The cost-benefit of this partnership is invaluable.”
Hack the Air Force 2.0 was announced following the success of the first Hack the Air Force program, which resulted in more than $130,000 being paid out for over 200 valid vulnerability reports.
Previous DoD bug bounty projects included Hack the Pentagon, which resulted in payouts of roughly $75,000, and Hack the Army, with rewards totaling approximately $100,000. The Pentagon has paid more than $300,000 for over 3,000 flaws discovered in its public-facing systems, but the organization estimates that it saved millions of dollars by running these programs.
Roughly one year ago, the Pentagon announced a vulnerability disclosure policy that aims to provide guidance to researchers on how to disclose security holes found in the organization’s public-facing websites. While no monetary rewards are being offered, the policy provides a legal avenue for reporting flaws.
"Zealot" Apache Struts Attacks Abuses NSA Exploits
18.12.2017 securityweek BigBrothers
A sophisticated multi-staged Apache Struts cyber attack campaign is abusing NSA-linked exploits to target internal networks, researchers from F5 Networks have discovered.
Dubbed Zealot, the highly obfuscated attack uses the EternalBlue and EternalSynergy exploits to target Windows and Linux systems. The newly uncovered campaign employs a PowerShell agent to compromise Windows systems and a Python agent to target Linux/OS X. The scripts appear based on the EmpireProject post-exploitation framework, F5 says.
The attack is targeting servers vulnerable to CVE-2017-5638 (Apache Struts Jakarta Multipart Parser attack) and CVE-2017-9822 (a flaw in the DotNetNuke (DNN) content management system). The main purpose of the campaign is to mine for the Monero cryptocurrency.
“The Zealot campaign aggressively targets both Windows and Linux systems, with the DNN and Struts exploits together. When looking more closely at the unusually high obfuscated payload, we discovered a much more sophisticated multi-staged attack, with lateral movement capabilities, leveraging the leaked NSA-attributed EternalBlue and EternalSynergy exploits,” the researchers reveal.
The attack starts with two HTTP requests, one of which is the notorious Apache Struts exploit via the Content-Type header. Java code is executed to determine the underlying OS on the targeted system.
On Linux, shell commands are executed in the background to download and execute a spearhead bash script that checks whether the machine is already infected and then fetches and runs a crypto-miner file named “mule”.
The Python code checks whether a firewall solution is running and fetches more code from the command and control (C&C) server. The received response is encrypted so that it cannot be detected by typical network inspection devices.
“When sending the request to the C&C, specific User-Agent and Cookie headers are added. This technique means that anyone (like us researchers) who tries to access the C&C from their own browser or a tool won’t get the same response as the malware,” F5 explains.
On Windows systems, the Struts payload runs a PowerShell interpreter in a hidden mode, which in turn executes a base64-encoded script pointing to a file on a different domain. Even more heavily obfuscated, the file is “scv.ps1,” a PowerShell script that downloads the miner and runs it. It can also download the malware as a DLL and inject it into the PowerShell process using reflective DLL injection.
The malicious code also downloads the Python installer and deploys it if Python 2.7 is not present on the targeted Windows system. It then downloads the main Python module to initiate propagation over the internal network.
Two more files are downloaded onto the machine, namely “zealot.zip” and “raven64.exe.” The former includes several Python scripts and libraries, including a script designed to execute the EternalBlue and EternalSynergy exploits, an SMB protocol wrapper, and a series of known Python packages.
The “raven64.exe” file scans the internal network for port 445 and calls the main script to inject three different shellcodes for Windows 7 and Windows 8 systems to exploit EternalSynergy and EternalBlue. After execution, a PowerShell downloads the “scv.ps1” agent, but from a different server.
“The “mule” malware is a cryptocurrency malware mining for the Monero currency. Monero has become the cybercrime currency of choice due to its high anonymity. The amount that was paid for this specific miner address was approximately $8,500. It is not known how much profit the threat actor has overall,” F5 says.
The security researchers also determined that the Zealot attackers used the public EmpireProject, a PowerShell and Python post-exploitation agent.
The second HTTP request observed in this campaign is attempting to exploit the ASP.NET-based content management system DotNetNuke by sending a serialized object via a vulnerable DNNPersonalization cookie. The goal is to obtain arbitrary code execution to run the same PowerShell script delivered via the Apache Struts exploit.
The NSA exploits have been abused in previous campaigns, including NotPetya and WannaCry ransomware, along with the Adylkuzz cryptominer, but Zealot seems to be the first Struts campaign using these exploits.
The new attack also opens “new attack vector doors, automatically delivering malware on internal networks via web application vulnerabilities. The level of sophistication we are currently observing in the Zealot campaign is leading us to believe that the campaign was developed and is being run by threat actors several levels above common bot herders,” F5 concludes.
Firewall Bursting: A New Approach to Better Branch Security
18.12.2017 thehackernews Safety
One of the most common network security solutions is the branch firewall. Branch firewall appliances can pack into a single device a wide range of security capabilities including a stateful or next-generation firewall, anti-virus, URL filtering, and IDS/IPS.
But the reality is that most of these edge devices lack the processing power to apply the full scope of capabilities on all of the necessary traffic.
If the firewall deployed in the branch cannot scale to address critical security needs, an alternative strategy must be used. Wholesale appliance upgrades are easy but expensive. Regional security hubs are complex and also costly.
A new approach, called firewall bursting, leverages cloud scalability to offer an easier, more cost-effective alternative to branch office security. (You can find a great table comparing the different Firewall approaches here.)
Costly Appliance Upgrades and Secure Hub Architectures
The existing methods of evolving branch security force IT into a tough trade-off: the cost and complexity of managing appliance sprawl or the complexities of a two-tier network security architecture.
Upgrading all branch firewalls to high-performance, next-generation branch firewalls improve network security, no doubt. Branch offices gain more in-depth packet inspection and more protections to be applied on more traffic. This is a relatively straightforward, but very costly, solution to achieving stronger security.
Aside from the obvious, the firewall upgrade cost, there are also the costs of operating and maintaining the appliance, which includes forced upgrades. Sizing branch firewall appliances correctly can be tricky.
The appliance needs enough power to support the mix of security services across all traffic—encrypted and unencrypted—for the next three to five years.
Alone that would be complex, but the constantly growing traffic volumes only complicate that forecast. And encrypted traffic, which has become the new norm of virtually all Internet traffic, is not only growing but must be first decrypted, exacting a heavy processing toll on the appliance.
All of which means that IT ends up either paying more than necessary to accommodate growth or under provision and risk compromising the company’s security posture.
Regional hubs avoid the problems with upgrading all branch firewalls. Instead, organizations continue with their branch routers and firewalls, but backhaul all traffic to a larger firewall with public Internet access, typically hosted in a regional co-location hub.
The regional hub enables IT to maintain minimal branch security capabilities while benefitting from advanced security.
However, regional hubs bring their own problems. Deployment costs increase as regional hubs must be built out at significant hosting expense and equipment cost. And we’re not just speaking about throwing up an appliance in some low-grade hosting facility.
Hub outages impact not just one small office but the entire region. They need to be highly available, resilient, run the up-to-date software, and maintained by expert staff.
Even then, there are still the same problems of forced upgrades due to increased traffic volume and encrypted traffic share, this time, though, of only the hub firewall appliances.
The network architecture is also made far more complex, particularly for global organizations. Not only must they rollout multiple regional hubs, but multiple hubs must be deployed in geographically dispersed regions or those regions with a high concentration of branches.
In short, while the number of firewall instances can be reduced, regional hubs introduce a level of complexity and cost often too excessive for many organizations.
Firewall Bursting: Stretching your Firewalls to the Cloud
Cloud computing offers a new way to solve the edge firewall dilemma. With "cloud bursting," enterprises seamlessly extend physical data center capacity to a cloud datacenter when traffic spikes or they exhaust resources of their physical datacenter.
Firewall bursting does something similar to under-capacity, branch firewalls. Edge security processing is minimized where firewall capacity is constrained, and advanced security is applied in the cloud, where resources are scalable and elastic.
The on-premise firewall handles basic packet forwarding, but anything requiring "heavy lifting," such as decryption, anti-malware or IPS, is sent to the cloud. This avoids forced branch firewall upgrades.
Firewall bursting is similar to the regional hub approach, but with a key difference: the IT team isn't responsible for building and running the hubs. Hubs are created, scaled, and maintained by the cloud service provider.
Who Delivers Firewall Bursting Capabilities?
Secure web gateways (SWGs) delivered as cloud services, can provide firewall bursting for Internet traffic. However, since firewalls need to apply the same inspection to WAN traffic, SWGs only offer a partial solution.
Purpose-built, global Firewall as a Service (FWaaS) is another option. FWaaS providers, such as Cato Networks, create a global network of Points of Presence (PoPs), providing a full network security stack specifically built for cloud scalability.
While the PoPs are distributed, they act "together" as a single logical firewall instance. The PoPs are highly redundant and resilient, and in case of outages, processing capacity seamlessly shifts inside or across PoPs, so firewall services are always available.
The PoPs are capable of processing very large volumes of WAN and Internet traffic. Because adding processing capacity either within PoPs or by adding new PoPs is transparent to customers, you don't have to adjust policies or reconfigure your environment to accommodate changes in load or traffic mix.
Summary
With firewall bursting customers can keep their current edge firewalls and still improve security. If you are running out of gas on your edge firewalls, you have options.
Beyond the obvious approaches of firewall upgrades and hub-and-branches set up, new innovations like FWaaS are now available.
FWaaS leverages cloud elasticity and scalability to globally extend network security with minimal impact on current network design.
Firewall refresh, capacity upgrades, mergers and acquisition, all represent a great opportunity to look at firewall bursting and FWaaS to evolve your network security beyond the edge.
Two Critical 0-Day Remote Exploits for vBulletin Forum Disclosed Publicly
18.12.2017 thehackernews Vulnerebility
Security researchers have discovered and disclosed details of two unpatched critical vulnerabilities in a popular internet forum software—vBulletin—one of which could allow a remote attacker to execute malicious code on the latest version of vBulletin application server.
vBulletin is a widely used proprietary Internet forum software package based on PHP and MySQL database server. It powers more than 100,000 websites on the Internet, including Fortune 500 and Alexa Top 1 million companies websites and forums.
The vulnerabilities were discovered by a security researcher from Italy-based security firm TRUEL IT and an unknown independent security researcher, who disclosed the details of the vulnerabilities by Beyond Security's SecuriTeam Secure Disclosure program.
The vulnerabilities affect version 5 of the vBulletin forum software and are currently unpatched. Beyond Security claims, it tried to contact vBulletin since November 21, 2017, but received no response from the company.
vBulletin Remote Code Execution Vulnerability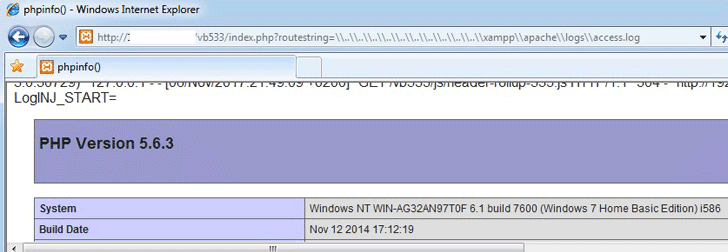
The first vulnerability discovered in vBulletin is a file inclusion issue that leads to remote code execution, allowing a remote attacker to include any file from the vBulletin server and execute arbitrary PHP code.
An unauthenticated attacker can trigger the file inclusion vulnerability by sending a GET request to index.php with the routestring= parameter in the request, eventually allowing the attacker to "create a crafted request to Vbulletin server installed on Windows OS and include any file on the web server."
The researcher has also provided Proof-of-Concept (PoC) exploit code to show the exploitation of the vulnerability. A Common Vulnerabilities and Exposures (CVE) number has not been assigned to this particular vulnerability.
vBulletin Remote Arbitrary File Deletion Vulnerability
The second vulnerability discovered in the vBulletin forum software version 5 has been assigned CVE-2017-17672 and described as a deserialization issue that an unauthenticated attacker can exploit to delete arbitrary files and even execute malicious code "under certain circumstances."
The vulnerability is due to unsafe usage of PHP's unserialize() on user-supplied input, which allows an unauthenticated hacker to delete arbitrary files and possibly execute arbitrary code on a vBulletin installation.
A publicly exposed API, called vB_Library_Template's cacheTemplates() function, allows fetching information on a set of given templates from the database to store them inside a cache variable.
"$temnplateidlist variable, which can come directly from user-input, is directly supplied to unserialize(), resulting in an arbitrary deserialization primitive," the advisory explains.
Besides technical details, the advisory also includes Proof-of-Concept (PoC) exploit code to explain the severity of this vulnerability.
We expect the vendor to release the patch for both the security flaws before hackers started exploiting them to target vBulletin installations.
Expert found critical issues in Palo Alto PAN-OS Networks Security Platform
18.12.2017 securityaffairs Vulnerebility
Palo Alto Networks released security updates for its PAN-OS security platform that address critical and high severity vulnerabilities
Last week, Palo Alto Networks released security updates for its PAN-OS security platform that address critical and high severity vulnerabilities that can be exploited by a remote and unauthenticated for remote code execution and command injection.
The critical issue, tracked as CVE-2017-15944, is a combination of flaws that affect the management interface.
PAN-OS 6.1.18, 7.0.18, 7.1.13, 8.0.5 and earlier versions are affected by the issue that was addressed by security updates included in PAN-OS 6.1.19, 7.0.19, 7.1.14 and 8.0.6.
Palo Alto Network also released vulnerability signatures to block the attacks that exploit this issue.
The set of vulnerability was discovered in July by Philip Pettersson that published a security advisory on SecList. Pettersson has found three vulnerabilities (a partial authentication bypass, an arbitrary directory creation issue, and a command injection bug) that can be chained to allow an unauthenticated attacker to execute arbitrary code with root privileges through the vulnerable web interface.
“This is a public advisory for CVE-2017-15944 which is a remote root code execution bug in Palo Alto Networks firewalls. Three separate bugs can be used together to remotely execute commands as root through the web management interface without authentication on: PAN-OS 6.1.18 and earlier, PAN-OS 7.0.18 and earlier, PAN-OS 7.1.13 and earlier, PAN-OS 8.0.5 and earlier.” reads the advisory.
Palo Alto Networks notified customers the vulnerability informing them to avoid exposing the web interface of its devices to the Internet.

The security updated for PAN-OS also address a high severity flaw in the web interface packet capture management component tracked as CVE-2017-15940.
The flaw can be exploited by an authenticated attacker to inject arbitrary commands.
Affected products are PAN-OS 6.1.18 and earlier, PAN-OS 7.0.18 and earlier, PAN-OS 7.1.13 and earlier, PAN-OS 8.0.6 and earlier.
“This issue affects the management interface of the device and is strongly mitigated by following best practices for the isolation of management interfaces for security appliances. We recommend that the management interface be isolated and strictly limited only to security administration personnel through either network segmentation or using the IP access control list restriction feature within PAN-OS.” reads the advisory.
Researchers discovered two serious code execution flaws in vBulletin not yet unpatched
18.12.2017 securityaffairs Vulnerebility
Two code execution vulnerabilities affecting version 5 of the vBulletin forum software were disclosed by researchers last week.
Two code execution vulnerabilities affecting version 5 of the popular vBulletin forum CMS were disclosed by researchers last week via Beyond Security’s SecuriTeam Secure Disclosure program.
vBulletin is currently used by over 100,000 sites, including Fortune 500 and Alexa Top 1M companies websites and forums.
The flaws were discovered by an expert at the Italy-based security firm TRUEL IT and an expert who has not been named.
The vulnerabilities are still unpatched, but the vBulletin development team is going to fix them as soon as possible.
The first vulnerability was reported by an independent security researcher, it is described as an unauthenticated file inclusion issue and could lead to remote code execution.
An attacker can include malicious PHP code into a file on the server, for example the access.log, and then include that file by manipulating the routestring= parameter in a specifically crafted request that can result in the attacker’s code getting executed.
“vBulletin contains a vulnerability that can allow a remote attacker to include any file from the vBulletin server and execute arbitrary PHP code.
An unauthenticated user is able to send a GET request to /index.php which can then trigger the file inclusion vulnerability with parameter routestring=.” reads the security advisory.
“The request allows an attacker to create a crafted request to Vbulletin server installed on Windows OS and include any file on the web server.”
The second vulnerability, tracked as CVE-2017-17672, has been described as an unauthenticated deserialization flaw.
The flaw, reported by a security researcher from, TRUEL IT ( @truel_it ), can be exploited by an unauthenticated attacker to delete arbitrary files and possibly even execute arbitrary code.
“Unsafe usage of PHP’s unserialize() on user-supplied input allows an unauthenticated attacker to delete arbitrary files and, under certain circumstances, execute arbitrary code on a vBulletin installation.” states the security advisory.
“vB_Library_Template’s cacheTemplates() function, which is an publicly exposed API which allows to fetch information on a set of given templates from the database in order to store them inside a cache variable.”
For both vulnerabilities, the researchers released proof-of-concept (PoC) codes.
Beyond Security claims it has first reported the issues to the vBulletin development team on November 21, but has not received any response.
According to SecurityWeek, the development team has already developed a patchand it is testing it.
“vBulletin, on the other hand, told SecurityWeek that it received no email into its ticket system regarding the vulnerabilities until last week. A patch has already been developed and it will be released once it’s tested.” reported SecurityWeek.