2 ---
3 > $wptuts_plugin_remote_path = 'https://simplywordpress.net/captcha/captcha_free_update.php';

Backdoor in Captcha Plugin poses serious risks to 300K WordPress sites
20.12.2017 securityaffairs Hacking
Experts discovered that the popular WordPress Captcha plugin installed on over 300,000 sites was recently updated to deliver a hidden backdoor.
Security experts at WordFence have discovered that the popular WordPress Captcha plugin installed on over 300,000 sites was recently updated to deliver a hidden backdoor. The WordPress team promptly removed the plugin from the official WordPress Plugins repository and provided sanitized versions for affected customers.
WordPress also blocked the author of the plug-in from publishing updates without the review of its development team, WordFence now includes firewall rules to block Captcha and five other plugins from the same author.
WordFence has worked with the WordPress plug-in team to patch pre-4.4.5 versions of the plug-in.
The WordPress team noticed something of strange in September, when the plug-in changed hands. Just three months later the new team distributed the backdoored version Captcha 4.3.7.
Experts found a code triggering an automatic update process that downloads a ZIP file from:
https://simplywordpress[dot]net/captcha/captcha_pro_update.php
then extracts and installs itself modifying the install of the Captcha plugin running on WordPress site.
“Whenever the WordPress repository removes a plugin with a large user base, we check to see if it was possibly due to something security-related. Wordfence alerts users when any plugin they are running is removed from WordPress repo as well. At the time of its removal, Captcha had over 300,000 active installs, so its removal significantly impacts many users.” states the analysis published by WordPress.
“A backdoor file allows an attacker, or in this case, a plugin author, to gain unauthorized administrative access to your website. This backdoor creates a session with user ID 1 (the default admin user that WordPress creates when you first install it), sets authentication cookies, and then deletes itself.”
1 < $wptuts_plugin_remote_path = 'https://simplywordpress.net/captcha/captcha_pro_update.php';
2 ---
3 > $wptuts_plugin_remote_path = 'https://simplywordpress.net/captcha/captcha_free_update.php';
WordFence investigated the new ownership of the plugin, it noticed that the domain used to deliver the ZIP file containing the backdoor is simplywordpress[.]net that is registered to someone named Stacy Wellington using the email address scwellington@hotmail.co.uk.
It was easy to discover that the same email address was used to register a large number of other domains and the footer of one of them referenced Martin Soiza.
In September, around 200,000 WordPress websites using the Display Widgets Plugin were impacted after it was updated to include malicious code. Further investigation allowed the experts at WordFence to discover that the man behind plugin spam was the Briton Mason Soiza (23) who bought the plugin in late May.
WordFence discovered that also other plug-ins from the simplywordpress domain ( Convert me Popup, Death To Comments, Human Captcha, Smart Recaptcha, and Social Exchange) contain the same backdoor code.
According to the researchers, the backdoor was used to create cloaked backlinks to various payday loan businesses in order to boost their Google rankings.
“If you have not read our previous post on Mason Soiza, I’d suggest you read that first, since he has a long history of buying WordPress plugins in order to place cloaked backlinks on his users’ sites. He then uses these backlinks to increase page rank in SERPs (Search Engine Results Pages) since only web crawlers such as Googlebot can read them.” states WordPress.
“The hostmaster email address is the same for both simplywordpress.net and unsecuredloans4u.co.uk (Stacy Wellington scwellington@hotmail.co.uk).”
Let me close with simple recommendation provided by the experts, hurry up,uninstall the Captcha plugin immediately from your site.
Singapore Issues Cryptocurrency Warning
19.12.2017 securityweek Security
Singapore Tuesday issued a warning about cryptocurrencies after a recent surge in prices sent investors flocking to bitcoin.
"The Monetary Authority of Singapore advises the public to act with extreme caution and understand the significant risks they take on if they choose to invest in cryptocurrencies," the city-state's central bank said in a statement.
"MAS is concerned that members of the public may be attracted to invest in cryptocurrencies, such as Bitcoin, due to the recent escalation in their prices."
It said the recent spike in bitcoin prices comes from speculation, and cautioned that the bubble may burst.
Singapore's central bank joins a number of regulators who have warned about cryptocurrency investments, including the US Federal Reserve, which said bitcoin could threaten financial stability.
Regulators in Seoul have banned South Korean financial institutions from dealing in virtual currencies.
The MAS, which also acts as a financial regulator in the city-state, noted that cryptocurrencies are not backed by any central bank and are unregulated, which means those who lose money after investing in them have no room for redress under Singapore law.
"There is also a risk of loss should the cryptocurrency intermediary be hacked, as it may not have sufficiently robust security features," the regulator said.
Earlier on Tuesday, a South Korean virtual currency exchange declared itself bankrupt after being hacked for the second time in a year.
The closure comes eight months after nearly 4,000 bitcoin -- then valued at 5.5 billion won ($5 million), nearly 40 percent of the exchange's total assets -- were stolen in a cyber-attack blamed on North Korea.
Global bitcoin prices have soared around 20-fold this year, with the cryptocurrency trading above $18,000 on Tuesday.
Created in 2009 as a piece of encrypted software, bitcoin been used to buy everything from beer to pizza, and is increasingly accepted by major companies such as online travel giant Expedia.
Analysts have put the surge down to growing acceptance among traditional investors and a decision by US regulators to allow bitcoin futures to trade on major exchanges.
Previously only traded on specialist platforms, bitcoin started trading on the Cboe Futures Exchange earlier this month before hitting the major Chicago Mercantile Exchange (CME) on Monday.
Loapi Android Trojan Does All Sorts of Bad
19.12.2017 securityweek Android
A recently discovered Android malware features a modular architecture that allows it to perform a broad range of nefarious activities, Kaspersky Lab researchers warn.
Detected by Kaspersky as Trojan.AndroidOS.Loapi, the malicious program was found masquerading as antivirus solutions or adult content apps. Its capabilities, the security researchers say, range from mining for cryptocurrencies to displaying a constant stream of ads and to launching distributed denial of service (DDoS) attacks, among others.
The mobile threat was observed distributed via advertising campaigns that redirected users to the attackers’ malicious websites. After installation, the malware attempts to gain device administrator rights, continuously requesting them in a loop. Although it checks whether the device is rooted, the Trojan doesn’t use root privileges.
If the user gives in and grants the malicious app admin privileges, Loapi either hides its icon in the menu or simulates antivirus activity. The displayed behavior depends on the type of application it masquerades as, Kaspersky has discovered.
The Trojan can prevent users from revoking its device manager permissions by locking the screen and closing the window with device manager settings. Moreover, the malware receives from the command and control (C&C) server a list of apps that could pose a danger and uses it to monitor the installation and launch of those apps.
When such an app is installed or launched, the Trojan displays a fake message claiming it has detected malware, prompting the user to delete it. The message is displayed in a loop, thus preventing the user from dismissing it until the application is deleted.
At installation, Loapi receives from the C&C lists of modules to install or remove, a list of domains that serve as C&C, an additional reserved list of domains, the list of “dangerous” apps, and a flag whether to hide its app icon. At a third stage during the process, the necessary modules are downloaded and initialized.
An advertisement module is used to aggressively display ads on the device, but can also be used to open URLs, create shortcuts, show notifications, open pages in popular social network apps (including Facebook, Instagram, VK), and download and install other applications.
An SMS module can perform various text message manipulation operations. Based on C&C commands, it can send inbox SMS messages to attackers’ server, reply to incoming messages, send SMS messages with specified text to specified number, delete SMS messages from inbox and sent folder, and execute requests to URL and run specified JavaScript code in the page received as response.
A Web crawling module can subscribe users to services by covertly executing JavaScript code on web pages with WAP billing, in addition to performing web page crawling. Should operators send text messages asking for confirmation, the SMS module is employed to reply with the required text. Together with the ad module, it was observed attempting to open 28,000 unique URLs on a single device during a 24-hour experiment.
The Trojan also packs a proxy module that allows attackers to send HTTP requests from the victims’ devices via an HTTP proxy server. This feature allows the malware authors to organize DDoS attacks against specified resources or to change the Internet connection type on a device, the security researchers warn.
Another module uses the Android version of minerd to mine for the Monero (XMR) cryptocurrency.
According to Kaspersky, Loapi might be related to the Podec malware (Trojan.AndroidOS.Podec), as both threats use the same C&C server IP address, both use the same obfuscation, and feature similar ways of detecting superuser on the device. Moreover, both collect information with similar structure and content and send it in JSON format to the C&C during the initial stage.
“Loapi is an interesting representative from the world of malicious Android apps. Its creators have implemented almost the entire spectrum of techniques for attacking devices […]. The only thing missing is user espionage, but the modular architecture of this Trojan means it’s possible to add this sort of functionality at any time,” Kaspersky concludes.
Successor to NetTraveler Malware Dissected
19.12.2017 securityweek Virus
A recently observed backdoor could be intended as the successor of the NetTraveler malware, Kaspersky Lab security researchers report.
NetTraveler has been around for more than a decade, but has recently resurfaced in a series of cyber-espionage attacks launched against victims in Russia and neighboring European countries. Several years ago, the malware was associated with a campaign that hit targets in over 40 countries.
The malware was designed for surveillance purposes, and a new variant referred to as Travle or PYLOT appears to have emerged earlier this year. Supposedly the offspring of a Chinese-speaking actor, the new threat gets its name from a typo in a string in one of the analyzed samples: “Travle Path Failed!” (the typo has been corrected in newer releases).
The malware was observed being deployed using malicious documents delivered via spear-phishing attacks on Russian-speaking targets. The executables were maintained in encrypted form using a technique previously used to conceal Enfal, and then the Microcin APT family.
Travle command and control (C&C) domains often overlap with those of Enfal, which in turn was observed using the same encryption method for maintaining the C&C URL as NetTraveler. Thus, Kaspersky believes that Enfal, NetTraveler, Travle and Microcin are related to each other and that the Travle backdoor is the successor of NetTraveler.
Upon initializing communication with its C&C server, the malware sends information about the target operating system in an HTTP POST request. Sent information includes UserID (based on the computer name and IP-address), Computer name, Keyboard layout, OS version, IP-addresses, and MAC address.
The server responds by sending URL paths for receiving commands, for reporting on command execution results, and for downloading and uploading files from C&C. The server also provides the first and second RC4 key, and an ID. After receiving the packet, the backdoor waits for additional commands.
All communication with the server is encrypted, with the ciphering algorithm depending on the type of transmitted object. The bot can send technical messages, which contain information about the OS or about the performed commands, and operational messages, which contain lists of files in a directory or the content of a specific file.
Based on commands received from the C&C, the malware can scan the file system, can execute specified batch file or application with passed arguments, can check if a specified file exists, can delete/rename/move/create files, can download and execute files (scripts or BAT-files), can download DLLs and launch them using the LoadLibrary API function, and can load/unload a library to/from memory.
According to Kaspersky, the actor behind the Travle backdoor has been active during the last few years but doesn’t appear worried about being tracked by security companies. In fact, all of the modifications and new additions they made to their tools have been discovered and detected quite quickly.
“Still, the fact that they didn´t really need to change their TTPs during all these years seems to suggest that they don´t need to increase their sophistication level in order to fulfill their goals. What’s worse, according to subjects of decoy documents these backdoors are used primarily in the CIS region against government organizations, military entities and companies engaged in high-tech research, which indicates that even high-profile targets still have a long way to go to implement IT-sec best practices which efficiently resist targeted attacks,” Kaspersky concludes.
South Korea cryptocurrency exchange Youbit shuts down after second hack in 2017
19.12.2017 securityaffairs Hacking
The South Korea Cryptocurrency Exchange Youbit has gone bankrupt.after suffering a major cyber attack for the second time this year.
The South Korea Cryptocurrency Exchange Youbit shuts down after suffering a major cyber attack for the second time this year. The company announced bankrupt on Tuesday after being hacked for the second time in the last eight months, the company declared it had lost 17 percent of its assets in the last attack.
This is the first time that a cryptocurrency exchange based in South Korean has gone bankrupt.
Eight months ago hackers stole nearly 4,000 bitcoin (5.5 billion won ($5 million) at the time of the hack) that accounted for nearly 40 percent of the Youbit exchange’s total assets.Lazarus targets Bitcoin company

“We will close all trades, suspend all deposits or withdrawals and take steps for bankruptcy,” reads the statement issued by the company after the last attack.
In order to minimize the economic impact of the customers, all the clients will have their cryptocurrency assets marked down by 25 percent, in this way Youbit wants to cover the losses selling the remaining assets and using insurance.
The South Korean market for virtual currencies has become one of the most active, considering that whose trades account for some 20 percent of global Bitcoin transactions. More than one million South Koreans already invested in Bitcoin.
Analysts observed that the demand is very high, for this reason, prices for the unit are around 20 percent higher than in the US.
While global bitcoin prices continue to increase, threat actors are focusing their interests on the virtual currencies.
Recently security experts from Secureworks revealed the Lazarus APT group launched a spearphishing campaign against a London cryptocurrency company.
U.S. blames North Korea for the massive WannaCry ransomware attack
19.12.2017 securityaffairs Ransomware
It’s official, according to Tom Bossert, homeland security adviser, the US Government attributes the massive ransomware attack Wannacry to North Korea.
It’s official, the US Government attributes the massive attack Wannacry to North Korea.
The news of the attribution was first reported by The Wall Street Journal, according to the US Government, the WannaCry attack infected millions of computers worldwide in May is an act of Information Warfare.
WannaCry infected 200,000 computers across 150 countries in a matter of hours last week, it took advantage of a tool named “Eternal Blue”, originally created by the NSA, which exploited a vulnerability present inside the earlier versions of Microsoft Windows. This tool was soon stolen by a hacking group named “Shadow Brokers” which leaked it to the world in April 2017.
The ransomware infected systems in any industry and also targeted critical infrastructures such as hospitals and banks.

WannaCry ransomware on a Bayer radiology system – Source Forbes
In October, the UK Government linked the WannaCry attack that crippled NHS to North Korea.
“This attack, we believe quite strongly that it came from a foreign state,” Ben Wallace, a junior minister for security, told BBC Radio 4’s Today programme.
“North Korea was the state that we believe was involved in this worldwide attack,” he said, adding that the government was “as sure as possible”.
The attack caused billions of dollars damages, now the United States Homeland Security Advisor Tom Bossert officially blamed Noth Korea for the attack declaring that the US Government has collected evidence that Link Pyongyang to the massive WannaCry attack.
“The attack was widespread and cost billions, and North Korea is directly responsible,” Tom Bossert, homeland security adviser to President Donald Trump, wrote in an article published by the Wall Street Journal.
“North Korea has acted especially badly, largely unchecked, for more than a decade, and its malicious behavior is growing more egregious,” “WannaCry was indiscriminately reckless.”
The US government was expected to follow up with an official statement blaming North Korea for the attack.
The US Government has collected irrefutable proofs that link the North Korea APT Lazarus Group to WannaCry, with a “very high level of confidence” the APT carried out the WannaCry attack.
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. Security researchers discovered that North Korean Lazarus APT group was behind recent attacks on banks, including the Bangladesh cyber heist.
According to security experts, the group was behind, other large-scale cyber espionage campaigns against targets worldwide, including the Troy Operation, the DarkSeoul Operation, and the Sony Picture hack.
The North Korean government hasn’t yet commented the allegation.
New TelegramRAT Exploits Recently Patched Office Vulnerability
19.12.2017 securityweek Vulnerebility
A recently discovered Remote Access Trojan (RAT) is being distributed via documents that exploit a 17-year old Office vulnerability patched in November 2017, Netskope warns.
Dubbed TelegramRAT, the malware leverages the Telegram Messenger application for command and control (C&C), and abuses a cloud storage platform to store its payload. This approach allows the threat to evade some traditional security scanners.
Attacks involving TelegramRAT start with a malicious Office document exploiting CVE-2017-11882, a vulnerability that was introduced in the Microsoft Equation Editor (EQNEDT32.EXE) in November 2000. The bug remained unnoticed for 17 years, until Microsoft manually patched it last month, but it didn’t take long for malicious actors to start abusing it.
As part of the newly observed attack, the Bit.ly URL redirection service is used to conceal the TelegramRAT payload hosted on Dropbox. The malware uses the Telegram BOT API to receive commands and send responses to the attacker. By employing SSL cloud applications for infection and C&C operations, the malware can keep communication hidden from security applications.
“The payload executable strings contained lots of references to Python files. After a quick analysis, the payload looked to be a Python program converted into a standalone binary executable that contained everything needed to run the application,” Netskope says.
Because the Python interpreter, the application code, and all the required libraries are packaged, the executable is large in size, which also makes it less suspicious.
Within the extracted directory, the researchers found PYD files, DLL files, and an out00-PYZ.pyz_extracted folder containing .pyc files. They also discovered a file called “RATAttack” which points to an open-source “RAT-via-Telegram” on GitHub.
The attackers used almost the exact code from GitHub when compiling their Python executable, the security researchers have discovered.
By using Telegram, which supports encrypted communication, the attackers ensure that they can easily communicate with the target without anyone snooping into the communication. The RAT’s authors create a Telegram bot and embed the bot’s Telegram token into the TelegramRAT’s configuration file. The malware then connects to the bot’s Telegram channel, where the attacker can issue commands for the infected machines.
Based on the received commands, the malware can take screenshots, execute shell commands, copy files, delete files/folders, download file from target, encode local files and decode them, enable/disable keyboard freeze, get Google Chrome’s login/passwords, record microphone, get keylogs, get PC information, open a proxy server, reboot/shut down the machine, run a file, schedule a command to run at specific time, display services and processes running, and update executable.
“TelegramRAT offers another unfortunate instance of attackers recognizing that the cloud can be leveraged to evade many traditional security scanners. By making itself cloud native, TelegramRAT uses one cloud application for its payload host, and another for its C&C operation. This cloud application splicing offers resilience to the attack, and requires security scanners to be able to discern cloud application instances, and to inspect SSL traffic to be effective,” Netskope concludes.
Australia Police Accidentally Broadcast Arrest Plans on Social Media
19.12.2017 securityweek BigBrothers
Australian police accidentally broadcast on social media details of an operation to arrest a suspected North Korean agent -- three days before he was taken into custody, media reported Wednesday.
The Sydney-based man, described by authorities as a "loyal agent of North Korea", was arrested on Saturday and charged with trying to sell missile parts and technology on the black market to raise money for Pyongyang in breach of international sanctions.
But a minute of conversation about the case between federal police officers, including the timing of the arrest, was broadcast on Periscope Wednesday and linked to on Twitter, The West Australian reported Tuesday.
The newspaper said it had listened to the discussion, which included a suggestion that officers are "not going in all guns blazing, it's only half-a-dozen people and a forensic van".
The paper added that while the tweet was deleted, the broadcast remained live -- and was watched by 40 people -- before it was also removed after the publication alerted federal police.
It was only by luck that no details of the identity of the target were revealed, the West Australian added.
Federal police confirmed part of a conversation was mistakenly broadcast via its Periscope account while "testing a piece of social media broadcasting equipment".
"Steps have been taken to ensure such incidents will not occur again," the force said in a statement.
"The matter has been referred to the AFP's security area for review."
AFP [Australian Federal Police] Assistant Commissioner Neil Gaughan told reporters on Sunday that the case involving the alleged agent was "like nothing we have ever seen on Australian soil".
He added that the 59-year-old suspect, named in local media as Chan Han Choi, was a "loyal agent of North Korea, believing he was acting to serve some higher patriotic purpose".
Choi, who is in custody, is due back in court this week.
South Korea Cryptocurrency Exchange Shuts Down After Hacking
19.12.2017 securityweek Hacking
A South Korean exchange trading bitcoin and other virtual currencies declared itself bankrupt on Tuesday after being hacked for the second time this year, highlighting the risk over cryptocurrencies as they soar in popularity.
The Youbit exchange said it had lost 17 percent of its assets in the attack on Tuesday.
It came eight months after nearly 4,000 bitcoin -- then valued at 5.5 billion won ($5 million) and nearly 40 percent of the exchange's total assets -- were stolen in a cyber attack blamed on North Korea.
"We will close all trades, suspend all deposits or withdrawals and take steps for bankruptcy," the exchange said in a statement which did not assign blame for the latest attack.
All its customers will have their cryptocurrency assets marked down by 25 percent, it said, adding it would do its best to "minimise" their losses by using insurance and selling the remains of the firm.
The exchange -- founded in 2013 -- brokered trades of multiple virtual currencies including bitcoin and ethereum.
It is the first time that a South Korean cryptocurrency exchange has gone bankrupt.
Investing in virtual currencies has become hugely popular in the hyper-wired South, whose trades account for some 20 percent of global bitcoin transactions.
About one million South Koreans, many of them small-time investors, are estimated to own bitcoin. Demand is so high that prices for the unit are around 20 percent higher than in the US, its biggest market.
Global bitcoin prices have soared around 20-fold this year.
Concerns over a potential bubble have unnerved Seoul's financial regulators, who last week banned its financial institutions from dealing in virtual currencies.
U.S. Declares North Korea Led Huge WannaCry Cyberattack
19.12.2017 securityweek BigBrothers
The United States officially accused North Korea late Monday of carrying out the massive WannaCry attack that infected some 300,000 computers in 150 countries earlier this year.
North Korea was widely suspected of being behind the computer virus and ransomware, which demanded payment to restore access. It has been denounced as such by Britain, but the United States had yet to follow suit.
Homeland Security Advisor Tom Bossert made the announcement in a Wall Street Journal op-ed, and was expected to provide more details in a briefing with reporters early Tuesday.
"The attack was widespread and cost billions, and North Korea is directly responsible," he wrote.
"We do not make this allegation lightly. It is based on evidence."
Among the infected computers were those at Britain's National Health Service (NHS), Spanish telecoms company Telefonica and US logistics company FedEx.
"These disruptions put lives at risk," Bossert wrote.
"North Korea has acted especially badly, largely unchecked, for more than a decade, and its malicious behavior is growing more egregious. WannaCry was indiscriminately reckless."
He said Washington must lead efforts to cooperate with other governments and businesses to "mitigate cyber risk and increase the cost to hackers," and thus improve internet security and resilience.
"When we must, the US will act alone to impose costs and consequences for cyber malfeasance," Bossert added.
President Donald Trump "has already pulled many levers of pressure to address North Korea's unacceptable nuclear and missile developments, and we will continue to use our maximum pressure strategy to curb Pyongyang's ability to mount attacks, cyber or otherwise."
The WannaCry attack spread rapidly around the globe using a security flaw in Microsoft's Windows XP operating system, an older version that is no longer given mainstream tech support by the US giant.
Ransomware, which can be used on PCs as well as tablets and smartphones, is malicious software which locks computer files and forces users to pay the attackers a designated sum in the virtual Bitcoin currency to regain access to the files.
The Washington Post cited a US official as saying Trump's administration would be urging allies to counter North Korea's cyberattack capabilities and implement all "relevant" UN Security Council sanctions.
It said the CIA had already laid blame on North Korea for the attack in November, though the assessment was classified and had not yet been previously reported.
Cambium Wireless Networking Devices Vulnerable to Attacks
19.12.2017 securityweek Vulnerebility
A researcher has discovered nearly a dozen security issues in ePMP and cnPilot wireless networking products from Cambium, including vulnerabilities that can be exploited to take control of devices and the networks they serve.
Cambium’s ePMP and cnPilot wireless broadband solutions are used by managed services providers, governments, retailers, ISPs, hotels, schools, enterprises, and industrial organizations.
Researcher Karn Ganeshen discovered that ePMP 1000, 2000 and Force wireless broadband devices, and cnPilot R190, R200 and R201 Wi-Fi access points are affected by potentially serious vulnerabilities. The flaws were reported to Cambium in September via Rapid7 and a majority of them were patched last month.
While exploitation of the flaws normally requires access to the network, Rapid7’s Project Sonar uncovered more than 36,000 ePMP devices and 133 cnPilot systems accessible from the Internet, and many of them could be vulnerable. The highest number of exposed systems has been seen in Serbia (9,600), the United States (8.200), Italy (5,000), Brazil (3,000), Spain (2,700), Colombia (2,500) and South Africa (1,100).
Several of the vulnerabilities have been rated critical with a CVSS score of 9.0. One of them is CVE-2017-5254, a privilege escalation flaw affecting ePMP devices. These systems are shipped with several default accounts with default credentials, including admin/admin, installer/installer, home/home and readonly/readonly. The home and installer accounts don’t have admin privileges, but Ganeshen discovered that they can be used to change the admin account password.
The admin password normally cannot be changed by a installer or home user as the password field is not editable. However, an attacker who has access to the web interface with one of these low-privileged accounts can use the Inspect Element feature in their browser and delete the disabled=”” property, which makes the password field editable. The password set by the attacker for the admin account can then be used to access the web interface with administrator privileges.
Another critical privilege escalation flaw in ePMP is CVE-2017-5255. It allows an authenticated attacker – even one with a readonly account – to execute OS-level commands as root by sending a specially crafted request to a function named get_chart.
A hacker can also escalate privileges on an ePMP device by exploiting persistent cross-site scripting (XSS) vulnerabilities in the Device Name and System Description fields. An attacker with access to a device’s web interface can insert JavaScript code into these fields and the code will get executed both when the login page is accessed and after the user has logged in.
There are also a couple of other XSS flaws in the ePMP product, but these are more difficult to exploit. The XSS vulnerabilities can allow an attacker to hijack a user’s session, hook the browser, or conduct other activities that can lead to privilege escalation.
The most serious flaw affecting the cnPilot product is related to an undocumented root web shell that can be accessed by any user (CVE-2017-5259). Another critical issue in cnPilot allows privilege escalation via a direct object reference vulnerability (CVE-2017-5260).
cnPilot is also affected by information disclosure and privilege escalation flaws that have been rated medium severity.
The vulnerabilities affect ePMP products running version 3.5 and earlier of the firmware and cnPilot devices running version 4.3.2-R4 and earlier. Fixes have been introduced with the release of versions 3.5.1 and 4.4, respectively. Two issues involving the lack of cross-site request forgery (CSRF) protections and some suspicious binaries have not been patched.
This New Android Malware Can Physically Damage Your Phone
19.12.2017 thehackernews Android

Due to the recent surge in cryptocurrency prices, not only hackers but also legitimate website administrators are increasingly using JavaScript-based cryptocurrency miners to monetize by levying the CPU power of your PC to mine Bitcoin or other cryptocurrencies.
Just last week, researchers from AdGuard discovered that some popular video streaming and ripper sites including openload, Streamango, Rapidvideo, and OnlineVideoConverter hijacks CPU cycles from their over hundreds of millions of visitors for mining Monero cryptocurrency.
Now, researchers from Moscow-based cyber security firm Kaspersky Lab have uncovered a new strain of Android malware lurking in fake anti-virus and porn applications, which is capable of performing a plethora of nefarious activities—from mining cryptocurrencies to launching Distributed Denial of Service (DDoS) attacks.
Dubbed Loapi, the new Android Trojan can perform so many more malicious activities at a time that can exploit a handset to the extent that within just two days of infection it can cause the phone's battery to bulge out of its cover.
Described as a "jack-of-all-trades" by the researchers, Loapi has a modular architecture that lets it conduct a variety of malicious activities, including mining the Monero cryptocurrency, launching DDoS attacks, bombarding infected users with constant ads, redirecting web traffic, sending text messages, and downloading and installing other apps.
Loapi Destroyed An Android Phone In Just 2 Days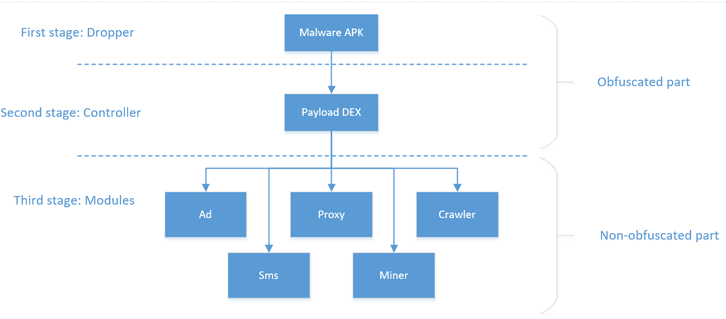
When analyzed a Loapi sample, Kaspersky's researchers discovered that the malware mines the Monero cryptocurrency so intensely that it destroyed an Android phone after two days of testing, causing the battery to bulge and deforming the phone cover.
According to researchers, the cybercriminals behind Loapi are the same responsible for the 2015 Android malware Podec. They are distributing the malware through third-party app stores and online advertisements that pose as apps for "popular antivirus solutions and even a famous porn site."
A screenshot in the Kaspersky blog suggests that Loapi impersonates as at least 20 variations of adult-content apps and legitimate antivirus software from AVG, Psafe DFNDR, Kaspersky Lab, Norton, Avira, Dr. Web and CM Security, among others.
Upon installation, Loapi forces the user to grant it 'device administrator' permissions by looping a pop-up until a victim clicks yes, which gives the malicious app the same power over your smartphone that you have.
This highest level privilege on a device would also make the Loapi malware ideal for user espionage, though this capability is not yet present in the malware, the Kaspersky researchers think this can be included in the future.
Loapi Malware Aggressively Fights to Protect Itself
Researchers also said the malware "aggressively fights any attempts to revoke device manager permissions" by locking the screen and closing phone windows by itself.
Loapi communicates with the module-specific command and control (C&C) servers, including advertisement module, SMS module and mining module, web crawler, and proxy module, for different functions to be performed on the infected device.
By connecting with one of the above-mentioned C&C servers, Loapi sends a list of legitimate antivirus apps that pose it danger and claims the real app as malware and urges the user to delete it by showing the pop-up in a loop until the user finally deletes the app.
"Loapi is an interesting representative from the world of malicious Android apps. It’s creators have implemented almost the entire spectrum of techniques for attacking devices: the Trojan can subscribe users to paid services, send SMS messages to any number, generate traffic and make money from showing advertisements, use the computing power of a device to mine cryptocurrencies, as well as perform a variety of actions on the internet on behalf of the user/device," the researchers concluded.
Fortunately, Loapi failed to make its ways to Google Play Store, so users who stick to downloads from the official app store are not affected by the malware. But you are advised to remain vigilant even when downloading apps from Play Store as malware often makes its ways to infect Android users.
Kaspersky Lab Sues U.S. Government Over Software Ban
19.12.2017 thehackernews BigBrothers
Moscow-based cyber security firm Kaspersky Lab has taken the United States government to a U.S. federal court for its decision to ban the use of Kaspersky products in federal agencies and departments.
In September 2017, the United States Department of Homeland Security (DHS) issued a Binding Operational Directive (BOD) ordering civilian government agencies to remove Kaspersky Lab software from their computers and networks within 90 days.
The order came amid mounting concern among United States officials that the Kaspersky antivirus software could be helping Russian government spy on their activities, which may threaten the U.S. national security.
U.S. President Donald Trump also signed into law last week legislation that bans the use of Kaspersky products within the U.S. government, capping a months-long effort to purge Kaspersky from federal agencies amid concerns it's vulnerable to Kremlin influence.
The Kaspersky's appeal is part of an ongoing campaign by the company to refute allegations that the company is vulnerable to Russian influence.
Moreover, there's no substantial evidence yet available which can prove these allegations, but an article published by US media WSJ in October claimed that Kaspersky software helped Russian spies steal highly classified documents and hacking tools belonging to the NSA in 2015 from a staffer's home PC.
Just last month, Kaspersky claimed that its antivirus package running on the staffer's PC detected the copies of the NSA exploits as malware and uploaded them to its cloud for analysis, but its analysts immediately deleted them.
Earlier this month, the NSA staffer, identified as Nghia Hoang Pho, a 67-year-old of Ellicott City, Maryland, pleaded guilty to illegally taking classified documents home, which were later stolen by Russian hackers.
Kaspersky Lab Challenges DHS's Ban on its Software in U.S. Court
Underlining that U.S. authorities have not provided any substantial evidence of wrongdoing by the company, CEO Eugene Kaspersky wrote in an open letter to the Homeland Security agency on Monday, stressing that the "DHS's decision is unconstitutional" and based purely on "subjective, non-technical public sources."
"One of the foundational principles enshrined in the U.S. Constitution, which I deeply respect, is due process: the opportunity to contest any evidence and defend oneself before the government takes adverse action," Kaspersky wrote.
"Unfortunately, in the case of Binding Operational Directive 17-01, DHS did not provide Kaspersky Lab with a meaningful opportunity to be heard before the Directive's issuance, and therefore, Kaspersky Lab's due process rights were infringed."
Kaspersky argues that the company was not given enough time to contest allegations before the DHS issued a ban, and that the documents available at the time of the ban were based more on references than a technical threat that the company could analyze and respond to.
The company also said that it wrote to DHS in mid-July to address any concerns the U.S. agency had, and DHS even acknowledged receipt of the communication in mid-August, appreciating the company's offer to provide information on the matter.
Kaspersky: DHS Harmed Kaspersky Lab's Reputation
However, Kaspersky said the agency did not follow up with the company "until the notification regarding the issuance of Binding Operational Directive 17-01" and accusing Kaspersky products of causing infosec risks on federal information systems.
"DHS has harmed Kaspersky Lab's reputation, negatively affected the livelihoods of its U.S.-based employees and U.S.-based business partners, and undermined the company’s contributions to the broader cybersecurity community," Kaspersky wrote.
"In filing this appeal, Kaspersky Lab hopes to protect its due process rights under the US Constitution and federal law and repair the harm caused to its commercial operations, its US-based employees, and its US-based business partners."
CEO Eugene Kaspersky has repeatedly denied the company's ties to any government and said it would not help a government with cyber espionage, adding that "If the Russian government comes to me and asks me to anything wrong, or my employees, I will move the business out of Russia."
In October, it was also reported that Israeli government hackers hacked into Kaspersky's network in 2015 and caught Russian hackers red-handed hacking United States government with the help of Kaspersky software.
In the wake of this incident, Kaspersky Lab also launched a transparency initiative late October, giving partners access to its antivirus source code and paying large bug bounties for security issues discovered in its products.
The thin line between BlackEnergy, DragonFly and TeamSpy attacks
19.12.2017 securityaffairs APT
Experts from McAfee Labs collected evidence that links DragonFly malware to other hacking campaigns, like BlackEnergy and TeamSpy attacks.
On September 6, Symantec published a detailed analysis of the Dragonfly 2.0 campaign that targeted dozens of energy companies this year. Threat actor is the same behind the Dragonfly campaign observed in 2014.
Further analysis conducted by McAfee Labs lead the experts into believing that the Operation Dragonfly is linked to earlier attacks.
The investigation conducted by McAfee Labs and the Advanced Threat Research team uncovered related attacks targeting the pharmaceutical, financial, and accounting industries.
The experts noticed the same techniques, tactics, and procedures (i.e. spear phishing, watering holes, and exploits of supply-chain technologies) were the same used in previous campaigns.
“By compromising well-established software vulnerabilities and embedding within them “backdoor” malware, the victims think they are installing software from a trusted vendor, while unaware of the supply-side compromise.” reads the analysis published by McAfee Labs.
Once compromised the target network, attackers used remote-desktop protocol to hop among internal or external systems, they connect either to a control server or use an internal compromised server to conduct operations.
Researchers observed threat actors using several backdoors and utilities, in one case a Trojan used in 2017 attacks was also used in a July 2013 attack.
Experts correlated the malware by analyzing their hashes, both contained the same TeamViewer that was spotted by the Hungarian security company Crysys in a report about the TeamSpy malware.
The TeamSpy hackers hit a large variety of high-level subjects including Russia-based Embassy for a not revealed undisclosed country belonging to both NATO and the European Union, multiple research and educational organizations in France and Belgium, an electronics company located in Iran and an industrial manufacturer located in Russia
Crysys researchers mentioned the same hash used in the recent attacks and correlated it to a sample that was compiled on 2011:09:07 – 09:27:58+01:00.
“Although the report attributes the attacks to a threat actor or actors and shared tactics and procedures, the motivations behind TeamSpy appear similar to those of the Dragonfly group. With identical code reuse, could the TeamSpy campaign be the work of Dragonfly?” continues McAfee Labs.
The experts discovered that the 2017 sample contained code blocks associated with BlackEnergy malware.

BlackEnergy sample from 2016 (at left) alongside a Dragonfly sample from 2017. (Source McAfee)
“Self-deleting code is very common in malware, but it is usually implemented by creating a batch file and executing the batch instead of directly calling the delete command, as we see in the preceding examples.” continues the analysis.
“The BlackEnergy sample used in our comparison was captured in the Ukraine on October 31, 2015, and was mentioned in our post on the evolution of the BlackEnergy Trojan. It is remarkable that this piece of code is almost identical in both samples, and suggests a correlation between the BlackEnergy and Dragonfly campaigns.”

The experts pointed out an evolution of the code in the backdoors developed by the threat actors and the reuse of code in their campaigns.
The malicious code is fairly sophisticated in hiding details of their attacks, making hard the attribution through the use of false flags.