
Industry Reactions to U.S. Blaming North Korea for WannaCry
22.12.2017 securityweek BigBrothers
The United States, Canada, Japan, Australia and New Zealand have all officially accused North Korea this week of being behind the WannaCry campaign. They join the United Kingdom, which blamed Pyongyang for the attack back in October.
While some security firms pointed the finger at North Korea shortly after the attack, Japan and the Five Eyes countries claim their intelligence agencies reached the same conclusion after conducting their own investigations and sharing data with each other.
North Korea has once again denied the accusations, claiming that Washington was demonising it.
Industry Reactions to U.S. Blaming North Korea for WannaCry
Some industry professionals point to evidence showing that these governments’ assessment is accurate, while others highlight that attribution is a difficult task, and warn that the world is not ready for the next WannaCry.
And the feedback begins...
Benjamin Read, Manager, Cyber Espionage Analysis, FireEye:
“FireEye has found the WannaCry malware shares unique code with WHITEOUT malware that we have previously attributed to suspected North Korean actors. While we have not verified other experts’ observation of known DPRK tools being used to drop early versions of WannaCry, we have not observed other groups use the code present in both WannaCry and WHITEOUT and we do not believe it is available in open source. This indicates a connection between the two.
Our analysis has found this unique code shared across additional North Korean malware, including NESTEGG and MACTRUCK. Significantly, while this code is present in the MACTRUCK malware, it is not used. The shared code likely means that, at a minimum, WannaCry operators share software development resources with North Korean espionage operators.
In addition to the WannaCry activity, we believe that North Korean actors are using multiple vectors to engage in cyber-criminal actively, including, most prominently, the targeting of Bitcoin exchanges. FireEye assess that North Korea will continue to pursue financially motivated cyber intrusion to supplement the government's income.”
Tim Erlin, VP of Product Management and Strategy, Tripwire:
“Accurate attribution for cyber attacks is almost always a difficult task, and it’s doubly so when the evidence leading to the conclusion can’t be shared.
With global public trust in the US government at a low point, it’s not surprising that there’s skepticism. If we’re going to have national security organizations delivering these types of conclusions on attribution to the public, we need to find a way to develop trusted output. The mantra of ‘trust us’ doesn’t cut it here.
This conclusion about North Korea’s culpability isn’t new. The UK discussed the very same conclusion in October, with the very same caveats about sharing the actual evidence. You can’t arrest a nation-state, which inevitably prevents any real closure on an incident like WannaCry.”
Chris Doman, Threat Engineer, AlienVault:
“WannaCry was linked to a group known as Lazarus, which others have linked to North Korea. There were two data points linking WannaCry to Lazarus - a number of rare code overlaps between WannaCry and Lazarus malware, and Symantec saw an early version of WannaCry manually deployed by Lazarus on one of their clients. The US government may have additional information, but the evidence provided at the time by the private sector was pretty strong.
The evidence linking Lazarus to North Korea is similarly strong. There are a very small number of publicly assigned internet addresses assigned to North Korea, and they pop up in Lazarus attacks. The attacks have been dated back to at least 2007, and often contain other clues such as North Korean fonts.
Things take time to come out of the government - but the timing today may have to do with other events. Lazarus have been particularly active recently - I’m seeing numerous new malware samples from them daily. A lot of their current activity involves stealing bitcoin and credit card numbers.”
Dmitri Alperovitch, CTO and Co-founder, CrowdStrike:
“[The US Government’s announcement] of its official public attribution of the WannaCry attack to North Korea regime is another step in establishing the importance for regularly attributing significant attacks to nation-states and criminal groups. It also raises public awareness about North Korea’s growing offensive cyber capabilities. CrowdStrike has tracked DPRK’s cyber activities going back to the mid-2000s, which started with espionage, then half a decade later evolved into destructive attacks and in the last few years delved into cybercrime such as ransomware and bank heists. They are a very capable actor that is known to have developed 0-day exploits and their own unique malware code. As such, they pose a major threat to organizations globally, especially as tensions between the US and North Korea over the nuclear and missile programs continue to escalate.”
Joseph Carson, Chief Security Scientist, Thycotic:
"Cyber attribution is one of the most difficult tasks in cybersecurity today. Unless the devices are persistent, it is almost impossible to identify who was sitting behind the keyboard, let alone who was instructing that person to carry out the malicious activity without any advanced cyber forensics tools. When attribution is pointing to a nation state, it is crucial that the attribution is communicated by the impacted government and not any private company or entity. Private companies should focus on getting back to a secure and operational state and assist in evidence that assist the government in accordance to any compliance requirements. In my experience, when cybercrime crosses international borders, it is difficult to claim attribution without cooperation of the country to where the evidence leads.
The challenge with calling out a group like Lazarus, which is widely believed to be associated with North Korea and several previous cyber-attacks, is that it is important to be clear that this is a group and motives can change depending on who is paying. I have found when researching hacking groups they can one day be working for one government under one alias and another using a different alias. This means that association in cyberspace means nothing. In my experience in digital forensics, I have always followed two rules when analyzing a cyber-crime: follow the motive or follow the money — either one will lead to the criminal.
In both WannaCry and NotPetya it looks like the motive was not financial. To me, it is clear that multiple bad actors played a part in the creation and malicious use of the ransomware. The payload and financial portion of the crime appears to be constructed by two different groups of cybercriminals. Remember, the real purpose of ransomware can be a combination of motives, or involve multiple threat actors with different motives. It is always important to step back and think: if this was your crime how would you have done it? It’s crucial to be able to think and look at the world through the eyes a hacker or cyber-criminal.”
Michael Daly, CTO, Raytheon Cybersecurity and Special Missions:
“The message for any company doing business on the internet is that North Korea sees you as a target. So do other rogue nation-states, and so do transnational crime organizations. For them, ransomware is an irresistible crime. It keeps hundreds of millions of dollars in untraceable cryptocurrency flowing in, all the while causing chaos in places like hospitals, power plants, train stations, financial institutions and telecommunications companies.
It's no coincidence the administration announced its findings in a publication they knew would reach the people who have the power and influence to strengthen networks in the commercial sector. Stronger networks are more expensive to attack, and when we increase the cost of cybercrime, we undermine the incentive for the attack.”
Travis Farral, Director of Security Strategy, Anomali:
“Attributing certain attacks or specific malware to an actor, group, or nation-state is difficult in the cyber world. Often, attribution is made as a best-guess based on available evidence. In the case of WannaCry, a handful of prominent security companies noted clues that pointed to the Lazarus Group, a North Korea associated actor group, as the potential culprits behind the malware. The cited links connecting North Korea to WannaCry have been far from conclusive, however. The U.S. Government claims to have evidence indicating that North Korea was indeed behind WannaCry. They may have such evidence, but because they have not shared the details with the public, it is a case of trusting their judgment on the matter.”
Atif Mushtaq, CEO, SlashNext:
“The interesting thing about malware is that, like any other product that works effectively, it can become widely-adopted. We recently blocked an exploit called “EternalBlue” which takes advantage of a Microsoft Windows Security flaw to gain entry using the network file sharing protocol (TCP ports: 139, 445). Similarities, including infection vectors, code sequences, infrastructure and exploitation techniques, link this to the APT called “Unit 180,” as well as a backdoor program called Contopee, originating from Lazarus, a North Korean hacking group. The core malware gets used but each hacking group modifies their attack strategy in order to evade signature- or sandbox-based detection mechanisms.”
Chris Morales, Head of Security Analytics, Vectra:
“Most industry experts believe that North Korea is engaged in finding alternative means for funding their efforts as they have been cut off from traditional financial channels. When WannaCry was first detected, we saw similarities in the code used for that ransomware attack with previous attacks attributed to North Korea, like the Sony hack. North Korea has been targeting banks directly with banking malware while using ransomware against other organizations to acquire a large volume of Bitcoin. North Korea has benefited greatly from with the meteoric rise in bitcoin over the past year. With the success in financial gain they have received from cybercrime, we can expect to see more.
We anticipate that many more ransomware attacks will continue to occur. They will have different names and use different exploits. What won’t change is the nature of the attacks and their associated behavior. While we don’t know when the next big attack will occur, enterprises need to be ready for it. Ongoing advances in AI have allowed technology to augment the efforts of cybersecurity teams. And there must be a seismic shift in the cybersecurity industry to identify attacker behaviors fast and early to stop ransomware attacks.”
Eddie Habibi, Founder and CEO, PAS:
“While attribution is an important question to answer, the real question is are we prepared for the next WannaCry? The lifeblood of critical infrastructure plants – where electricity is generated, fuel is produced, and drinking water is cleaned – are industrial control systems. They are responsible for process safety, production uptime, and environmental protection. Attacks on these systems have increased seven-fold since 2010, and the bad guys are achieving greater success with every attack.
Even after WannaCry initially hit, many plants had systems that remained unpatched. Just last week, attackers were successful taking control of safety systems in a plant with malware called TRITON/TRISIS. They did not need a vulnerability to assert control; they only needed specific process knowledge and an unprepared plant environment.
The threat landscape is fluid, and risk is increasing for critical infrastructure companies. Traditional IT security controls are not keeping pace with the requirements of operational technology systems, and industries need better methods to increase visibility into their most critical cyber assets – eighty percent of which are largely invisible to security personnel today. The basic fact is, you cannot protect what you cannot see.”
Nissan Finance Canada hacked, 1.13 million customers may have been exposed
22.12.2017 securityaffairs Incindent
Nissan Finance Canada announced on Thursday that the personal information of 1.13 million customers may have been exposed as a result of a data breach.
Nissan Finance Canada has been hacked, personal information of 1.13 million customers may have been exposed as a result of a data breach discovered by the company on December 11 (The biz took 10 days to disclose the incident).
The company notified customers via email the incident, it confirmed that its systems were compromised, with “unauthorized person(s) gaining access to the personal information of some customers that have financed their vehicles through Nissan Canada Finance or Infiniti Financial Services Canada.”
“We apologize for any frustration and anxiety this may cause our customers, and we thank you for your patience and support as we work through this issue.”
Nissan published a quite similar message on its website too, it added that at this time, there is no indication that customers who financed vehicles outside of Canada are affected. According to Nissan Canada, compromised data includes customer names, addresses, vehicle makes and models, vehicle identification numbers (VINs), credit scores, loan amounts and monthly payment figures.
Financial information belonging to the customers, such as payment card data was not affected.
“Nissan Canada Finance (NCF) is notifying its customers in Canada that it is a victim of a data breach that may have involved unauthorized person(s) gaining access to the personal information of some customers that have financed their vehicles through Nissan Canada Finance and INFINITI Financial Services Canada.” states the message published on the company website.
“On December 11, 2017, NCF became aware of unauthorized access to personal information.” “While the precise number of customers affected by the data breach is not yet known, NCF is contacting all of our current and past customers – approximately 1.13 million customers – who have financed their vehicles through Nissan Canada Finance and INFINITI Financial Services Canada.”

The company is investigating the attack with the help of law enforcement trying to figure out the extension of the incident and potential impact on its customers.
“We are still investigating precisely what personal information has been impacted,” the company added.
Nissan is offering 12 months of credit monitoring services through TransUnion at no cost.
Chinese crime group targets database servers for mining cryptocurrency
22.12.2017 securityaffairs CyberCrime
Security researchers discovered multiple hacking campaigns conducted by a Chinese criminal gang targeting database servers.
The researchers from the security firm GuardiCore Labs Security have discovered multiple hacking campaigns conducted by a Chinese criminal gang targeting database servers. The attackers targeted systems worldwide for mining cryptocurrencies, exfiltrating sensitive data and building a DDoS botnet.
The experts observed thousands of cyber attacks in recent months and identified at least three attack scheme, Hex, Hanako, and Taylor, targeting MS SQL and MySQL servers running on both Windows and Linux machines.
“In the last few months GuardiCore Labs has been investigating multiple attack campaigns conducted by an established Chinese crime group that operates worldwide.” reads the analysis published by Guardicore.
“The campaigns are launched from a large coordinated infrastructure and are mostly targeting servers running database services. By now we were able to identify three attack variants – Hex, Hanako and Taylor – targeting different SQL Servers, each with its own goals, scale and target services.”

The experts pointed out that the three malware are used for different purposes by the criminal group, below are described the attack scenarios:
Hex installs cryptocurrency miners and remote access trojans (RATs) on infected machines;
Taylor installs a keylogger and a backdoor;
Hanako is used to infect systems and recruit them in a DDoS botnet;
The experts observed threat actors mainly launching Taylor attacks, they recorded hundreds of Hex and Hanako attacks and tens of thousands of Taylor attacks each month.
The vast majority of compromised machines are mostly based in China, other infections were discovered in Thailand, the United States, Japan, and others.
Similarly to the Bondnet botnet, victims are re-purposed to help the attackers, making impossible analyzing the source of the attacks.
The researchers noticed that attackers used nearly all the machine for one month before rotate out of use, evidence they collected suggests that the attack group is based in China. The code includes comments in Chinese, the Trojan RAT disguises itself as a popular Chinese program and configuration files list email addresses from popular Chinese providers.
“Determining the scope of the campaign was quite a challenge. The group has shown an ability to generate over 300 unique binaries per each attack and to constantly rotate their attacking machines and domains, while manipulating thousands of victims as part of their attack infrastructure.” continues the analysis.
The hackers powered brute force attacks to gain unauthorized access to the targeted database servers, then run a series of predefined SQL commands to gain persistence and evade audit logs.
The hackers used a network of already compromised systems to power the brute force attacks against the database servers and deliver the malware, in this way they prevented takedown of their infrastructure.
All the malware variants create backdoor users in the database and open the Remote Desktop port, with this technique the attackers can remotely download and install their payloads (i.e. Cryptocurrency miner, Remote Access Trojan (RAT) or a DDoS malware).
“Later in the attack, the attacker stops or disables a variety of anti-virus and monitoring applications by running shell commands.” continues the post.
“The anti-virus targeted is a mixture of well known products such as Avira and Panda Security and niche software such as Quick Heal and BullGuard. As a final step, the attackers attempt to cover their tracks by deleting any unnecessary registry, file and folder entries using batch files and VB scripts.” the researchers wrote in their blog post published Tuesday.”
The attackers use to cover their tracks deleting any unnecessary Windows registry, file, and folder entry using pre-defined batch files and Visual Basic scripts.
Administrators should check for the existence of the following usernames in their database or systems in order to identify if they have been compromised by the Chinese criminal hackers.
Further info is available in the report, including Indicators of Compromise (IoCs).
After US, also Lithuania bans Kaspersky Software due to its alleged link to the Kremlin
22.12.2017 securityaffairs BigBrothers
Lithuania announced it will ban the products of the cyber security giant Kaspersky from computers in critical infrastructure.
After the decision of the US Government for banning Kaspersky software, Lithuania announced it will ban the products of the security giant from computers in critical infrastructure (energy, finance, and transport).
Lithuania is member of the EU and also component of the NATO alliance, it is very critics of Russia, especially after its 2014 annexation of the Crimea peninsula from Ukraine.
“The government… recognised that Kaspersky Lab software is a potential national security threat,” the Lithuanian’s defence ministry said in a statement.
The government will prohibit agencies responsible for “critical infrastructure” from using Kaspersky products and will force them to replace the anti-virus software in “a short while.”
The Russian security software was banned from US government agencies because it was blamed by US intelligence of helping Russian intelligence steal top-secret information.
The Lithuanian intelligence has the same opinion as of the US peers, the Lithuanian intelligence chief Darius Jauniskis recently said Kaspersky “was sometimes acting as a toy in the hands of (Russian President Vladimir) Putin’s administration”.
Kaspersky denied any involvement in cyber espionage activity, the company sued the U.S. Government over product ban, it’s appeal was filed in the U.S. District Court for the District of Columbia.
Kaspersky considers the ban as unconstitutional, according to the company the US Government took the decision to prohibit its products based on reports citing anonymous sources without strong evidence of its involvement in cyber espionage activities.
Kaspersky claims to have offered its support to the DHS for its investigation, but the agency issued the 17-01 directive, banning its security software and services without any warning.

The decision of the US Government is having a significant impact on the brand reputation with a consequent effect on the sales in almost any sector and any country.
“Through Binding Operational Directive 17-01, DHS has harmed Kaspersky Lab’s reputation, negatively affected the livelihoods of its U.S.-based employees and U.S.-based business partners, and undermined the company’s contributions to the broader cybersecurity community,” said Eugene Kaspersky, CEO and co-founder of Kaspersky Lab.
In December 2016, Lithuania announced to have found Russian spyware on its government computers, the government blamed Moscow for cyber espionage campaigns.
According to the Lithuanian intelligence, Russia powered cyber attacks that hit government networks over the last two years. According to the Reuters, the head of cyber security Rimtautas Cerniauskas confirmed the discovery of at least three Russian spyware on government computers since 2015.
Apple Admits Deliberately Slowing Older iPhones — Here’s Why
21.12.2017 thehackernews Apple

Why is my iPhone slow?
Do you also ask this question again and again?
Well, the biggest conspiracy theory floating around from years that Apple deliberately slows down performance on your older iPhones whenever the company is about to launch the next version of its flagship to push its sale is TRUE (at least partially).
Apple has finally admitted that it does indeed intentionally slow down older iPhone models, without notifying its customers, though the company claims the move is not intended to encourage customers to upgrade to newer iPhone models.
Instead, Apple says it is a feature—implemented on the iPhone 6, 6S and SE last year during a software update, and on the iPhone 7 in December with the release of iOS 11.2—to protect against unexpectedly shutting down of older iPhones due to aging batteries and prolong their lifespan.
"Last year we released a feature for iPhone 6, iPhone 6s and iPhone SE to smooth out the instantaneous peaks only when needed to prevent the device from unexpectedly shutting down during these conditions," the company said in an official statement to Reuters.
"We've now extended that feature to iPhone 7 with iOS 11.2, and plan to add support for other products in the future."
According to Apple, the issue resides in iPhone's battery, and not in its processor. The performance of lithium-ion battery used in iPhones degrades over time, which could result in damaging the internal components of the device.
Therefore, Apple intentionally throttles the performance of iPhones that have older batteries, batteries with low charge or that are cold, in an attempt to protect their components.
The above statement by Apple came in response to a blog post published earlier this week by Toronto-based firm Geekbench developer John Poole, who analyzed the performance of iPhone 6S and iPhone 7 over time.
Poole expected the battery capacity to decrease as they age, but processor performance to stay the same. He found that an iOS update rolled out to fix a 'sudden shutdown' issue was to blame for the decreased performance.
"Users expect either full performance or reduced performance with a notification that their phone is in low-power mode," Poole wrote in a blog post published Monday (18th December).
"This fix creates a third, unexpected state. While this state is created to mask a deficiency in battery power, users may believe that the slow down is due to CPU performance, instead of battery performance, which is triggering an Apple introduced CPU slow-down."
Apparently, this latest Apple's revelation sparked an outcry among Apple fans.
Although the company was not playing a bad trick to push the sale of newer iPhone models by slowing older ones, Apple should show a bit more honesty in a relationship with its customers who call themselves Apple fans.
Hidden Backdoor Found In WordPress Captcha Plugin Affects Over 300,000 Sites
21.12.2017 thehackernews Vulnerebility
Buying popular plugins with a large user-base and using it for effortless malicious campaigns have become a new trend for bad actors.
One such incident happened recently when the renowned developer BestWebSoft sold a popular Captcha WordPress plugin to an undisclosed buyer, who then modified the plugin to download and install a hidden backdoor.
In a blog post published on Tuesday, WordFence security firm revealed why WordPress recently kicked a popular Captcha plugin with more than 300,000 active installations out of its official plugin store.
While reviewing the source code of the Captcha plugin, WordFence folks found a severe backdoor that could allow the plugin author or attackers to remotely gain administrative access to WordPress websites without requiring any authentication.
The plugin was configured to automatically pull an updated "backdoored" version from a remote URL — https[://]simplywordpress[dot]net/captcha/captcha_pro_update.php — after installation from the official Wordpress repository without site admin consent.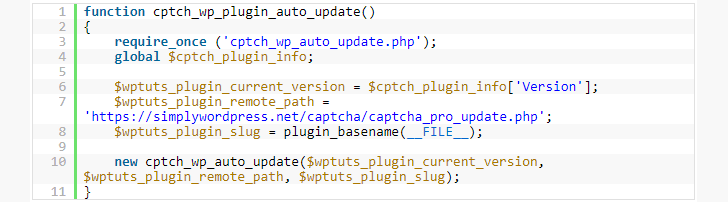
This backdoor code was designed to create a login session for the attacker, who is the plugin author in this case, with administrative privileges, allowing them to gain access to any of the 300,000 websites (using this plugin) remotely without requiring any authentication.
"This backdoor creates a session with user ID 1 (the default admin user that WordPress creates when you first install it), sets authentication cookies, and then deletes itself’" reads the WordFence blog post. "The backdoor installation code is unauthenticated, meaning anyone can trigger it."
Also, the modified code pulled from the remote server is almost identical to the code in legitimate plugin repository, therefore "triggering the same automatic update process removes all file system traces of the backdoor," making it look as if it was never there and helping the attacker avoid detection.
The reason behind the adding a backdoor is unclear at this moment, but if someone pays a handsome amount to buy a popular plugin with a large user base, there must be a strong motive behind.
In similar cases, we have seen how organized cyber gangs acquire popular plugins and applications to stealthy infect their large user base with malware, adware, and spyware.
While figuring out the actual identity of the Captcha plugin buyer, WordFence researchers found that the simplywordpress[dot]net domain serving the backdoor file was registered to someone named "Stacy Wellington" using the email address "scwellington[at]hotmail.co.uk."
Using reverse whois lookup, the researchers found a large number of other domains registered to the same user, including Convert me Popup, Death To Comments, Human Captcha, Smart Recaptcha, and Social Exchange.
What's interesting? All of the above-mentioned domains booked under the user contained the same backdoor code that the WordFence researchers found in Captcha.
WordFence has teamed up with WordPress to patch the affected version of Captcha plug-in and blocked the author from publishing updates, so websites administrators are highly recommended to replace their plugin with the latest official Captcha version 4.4.5.
WordFence has promised to release in-depth technical details on how the backdoor installation and execution works, along with a proof-of-concept exploit after 30 days so that admins get enough time to patch their websites.
Greedy North Korean Hackers Targeting Cryptocurrencies and Point-of-Sale Terminals
21.12.2017 thehackernews BigBrothers
The North Korean hacking group has turned greedy.
Security researchers have uncovered a new widespread malware campaign targeting cryptocurrency users, believed to be originated from Lazarus Group, a state-sponsored hacking group linked to the North Korean government.
Active since 2009, Lazarus Group has been attributed to many high profile attacks, including Sony Pictures Hack, $81 million heists from the Bangladesh Bank, and the latest — WannaCry.
The United States has officially blamed North Korea for global WannaCry ransomware attack that infected hundreds of thousands of computers across more than 150 countries earlier this year.
In separate news, security experts have blamed Lazarus group for stealing bitcoins worth millions from the South Korean exchange Youbit, forcing it to shut down and file for bankruptcy after losing 17% of its assets.
Researchers from security firm Proofpoint have published a new report, revealing a connection between Lazarus Group and a number of multistage cyber attacks against cryptocurrency users and point-of-sale systems.
"The group has increasingly focused on financially motivated attacks and appears to be capitalizing on both the increasing interest and skyrocketing prices for cryptocurrencies," the researchers said. "The Lazarus Group’s arsenal of tools, implants, and exploits is extensive and under constant development."
After analyzing a large number of spear phishing emails with different attack vectors from multiple spear phishing campaigns, researchers discovered a new PowerShell-based reconnaissance implant from Lazarus Group arsenal, dubbed PowerRatankba.
Encryption, obfuscation, functionality, decoys, and command-and-control servers used by PowerRatankba closely resembles the original Ratankba implant developed by Lazarus Group.
The PowerRatankba implant is being spread using a massive email campaign through the following attack vectors:
Windows executable downloader dubbed PowerSpritz
Malicious Windows Shortcut (LNK) files
Several malicious Microsoft Compiled HTML Help (CHM) files
Multiple JavaScript (JS) downloaders
Macro-based Microsoft Office documents
Backdoored popular cryptocurrency applications hosted on fake websites
PowerRatankba, with at least two variants in the wild, acts as a first-stage malware that delivers a fully-featured backdoor (in this case, Gh0st RAT) only to those targeted companies, organizations, and individuals that have interest in cryptocurrency.
"During our research, we discovered that long-term sandboxing detonations of PowerRatankba not running cryptocurrency related applications were never infected with a Stage2 implant. This may indicate that the PowerRatankba operator(s) were only interested in infecting device owners with an obvious interest in various cryptocurrencies," reads the 38-page-long report [PDF] published by Proofpoint.
Once installed, Gh0st RAT allows cybercriminals to steal credentials for cryptocurrency wallets and exchanges.
It's notable that PowerRatankba and Gh0st RAT don't exploit any zero-day vulnerability; instead, Lazarus Group relies on mixed programming practices, like C&C communication over HTTP, use of Spritz encryption algorithm and the Base64-encoded custom encryptor.
"It is already well-known that Lazarus Group has targeted and successfully breached several prominent cryptocurrency companies and exchanges," the researchers say. "From these breaches, law enforcement agencies suspect that the group has amassed nearly $100 million worth of cryptocurrencies based on their value today."
Besides stealing cryptocurrencies, the group was also found infecting SoftCamp point-of-sale (POS) terminals, largely deployed in South Korea, using RatankbaPOS malware for stealing credit card data.
Since RatankbaPOS was sharing same C&C server as the PowerRatankba implant, it is believed that both the implants are linked to Lazarus Group.
The explosive growth in cryptocurrency values has motivated not only traders but also hackers to invest all their time and resources in making digital wealth.
More details about the new malware campaigns run by Lazarus Group can be found in the in-depth report [PDF], titled "North Korea Bitten by Bitcoin Bug—Financially motivated campaigns reveal a new dimension of the Lazarus Group," published by PowerPoint on Wednesday.
Romanian Police Arrest 5 People for Spreading CTB Locker and Cerber Ransomware
21.12.2017 thehackernews Ransomware Crime
Romanian police have arrested five individuals suspected of infecting tens of thousands of computers across Europe and the United States in recent years by spreading two infamous ransomware families—Cerber and CTB Locker.
Under Operation Bakovia—a major global police operation conducted by Europol, the FBI and law enforcement agencies from Romanian, Dutch, and the UK—raided six houses in East Romania and made five arrests, Europol said on Wednesday.
Authorities have seized a significant amount of hard drives, external storage, laptops, cryptocurrency mining devices, numerous documents and hundreds of SIM cards during the raid.
One thing to note is that all of the five suspects were not arrested for developing or maintaining the infamous ransomware strains, but for allegedly spreading CTB Locker and Cerber.
Based on CryptoLocker, CTB Locker, aka Critroni, was the most widely spread ransomware families in 2016 and was the first ransomware to use the Tor anonymizing network to hide its command and control servers.
Emerged in March 2016, Cerber ransomware works on ransomware-as-a-service (RaaS) model that helped it to gain widespread distribution, allowing any would-be hacker to spread the malware in exchange for 40% of each ransom amount paid.
While CTB Locker helped criminals made $27 million in ransom, Cerber was ranked by Google as the most criminally profitable ransomware that helped them earned $6.9 million up in July 2017.
As with most ransomware, CTB Locker and Cerber distributors were using the most common attack vectors, such as phishing emails and exploit kits.
"In early 2017, the Romanian authorities received detailed information from the Dutch High Tech Crime Unit and other authorities that a group of Romanian nationals was involved in sending spam messages," Europol said in its press release.
"The spam messages intended to infect computer systems and encrypt their data with the CTB-Locker ransomware aka Critroni. Each email had an attachment, often in the form of an archived invoice, which contained a malicious file. Once this attachment was opened on a Windows system, the malware encrypted files on the infected device."
Although the authorities did not release the actual identities of the arrested individuals yet, Europol released a dramatic video of the arrests, where you can see how armed officers stormed the suspects' residence.
Hackers Targeting Servers Running Database Services for Mining Cryptocurrency
21.12.2017 thehackernews Hacking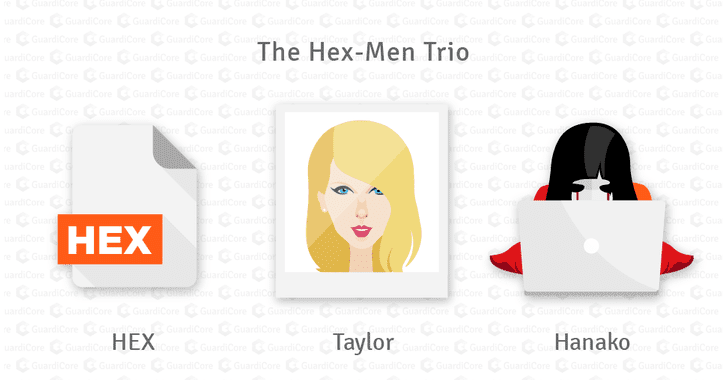
Security researchers have discovered multiple attack campaigns conducted by an established Chinese criminal group that operates worldwide, targeting database servers for mining cryptocurrencies, exfiltrating sensitive data and building a DDoS botnet.
The researchers from security firm GuardiCore Labs have analyzed thousands of attacks launched in recent months and identified at least three attack variants—Hex, Hanako, and Taylor—targeting different MS SQL and MySQL servers for both Windows and Linux.
The goals of all the three variants are different—Hex installs cryptocurrency miners and remote access trojans (RATs) on infected machines, Taylor installs a keylogger and a backdoor, and Hanako uses infected devices to build a DDoS botnet.
So far, researchers have recorded hundreds of Hex and Hanako attacks and tens of thousands of Taylor attacks each month and found that most compromised machines are based in China, and some in Thailand, the United States, Japan and others.
To gain unauthorized access to the targeted database servers, the attackers use brute force attacks and then run a series of predefined SQL commands to gain persistent access and evade audit logs.
What's interesting? To launch the attacks against database servers and serve malicious files, attackers use a network of already compromised systems, making their attack infrastructure modular and preventing takedown of their malicious activities.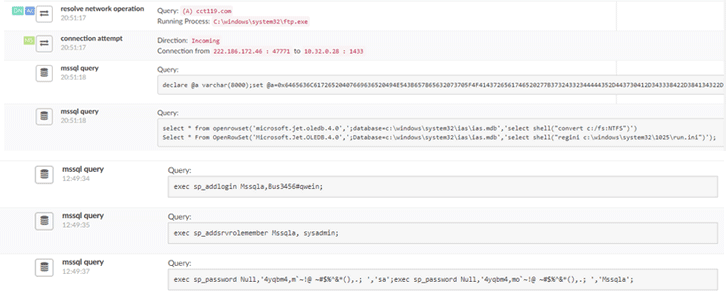
For achieving persistent access to the victim's database, all three variants (Hex, Hanko, and Taylor) create backdoor users in the database and open the Remote Desktop port, allowing attackers to remotely download and install their next stage attack—a cryptocurrency miner, Remote Access Trojan (RAT) or a DDoS bot.
"Later in the attack, the attacker stops or disables a variety of anti-virus and monitoring applications by running shell commands," the researchers wrote in their blog post published Tuesday.
"The anti-virus targeted is a mixture of well-known products such as Avira and Panda Security and niche software such as Quick Heal and BullGuard."
Finally, to cover their tracks, the attackers deletes any unnecessary Windows registry, file, and folder entry using pre-defined batch files and Visual Basic scripts.
Administrators should check for the existence of the following usernames in their database or systems in order to identify if they have been compromised by the Chinese criminal hackers.
hanako
kisadminnew1
401hk$
Guest
Huazhongdiguo110
To prevent compromise of your systems, researchers advised administrators to always follow the databases hardening guides (provided by both MySQL and Microsoft), rather than just having a strong password for your databases.
"While defending against this type of attacks may sound easy or trivial—'patch your servers and use strong passwords'—we know that 'in real life' things are much more complicated. The best way to minimize your exposure to campaigns targeting databases is to control the machines that have access to the database," the researchers advised.
"Routinely review the list of machines that have access to your databases, keep this list to a minimum and pay special attention to machines that are accessible directly from the internet. Every connection attempt from an IP or domain that does not belong to this list should be blocked and investigated."
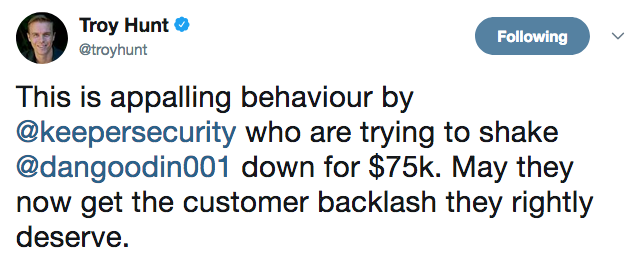
Keeper Sues Ars Technica Over Reporting on Critical Flaw
21.12.2017 securityweek Vulnerebility
Keeper Security has filed a lawsuit against Ars Technica and reporter Dan Goodin over an article covering a serious vulnerability found by a Google researcher in the company’s password manager.
Google Project Zero researcher Tavis Ormandy revealed last week that he had identified a critical vulnerability in the browser extension for the Keeper password manager.
The flaw, very similar to one discovered by the expert just over one year ago in the same application, could have been exploited by hackers to steal passwords stored by the extension if they could convince an authenticated user to access a malicious website.
Keeper Security released a patch within 24 hours of the flaw being reported and there had been no evidence of exploitation in the wild. The vendor highlighted that the security hole only impacted the browser extension and not the Keeper desktop application.
These types of vulnerabilities are often covered by the media, particularly ones found by Ormandy, who is known for discovering critical, easy-to-exploit weaknesses in popular software. However, Keeper Security does not like the article written by Ars Technica Security Editor Dan Goodin on this story and filed a lawsuit against him and his employer.
Goodin’s initial article, titled “Microsoft is forcing users to install a critically flawed password manager,” claimed the application had a 16-month-old bug, but it was later updated after Keeper clarified that only a version released this month had been impacted. Despite at least two other updates made to the story, Keeper is still not happy with it and has filed a lawsuit in an effort to get the article removed.
It its complaint, Keeper claims the article “was intended to and did cause harm” to the company by making “false and misleading statements.” The suit covers three counts: defamation, violation of the Uniform Deceptive Trade Practices Act, and commercial disparagement.
Keeper, which requested a jury trial, wants Ars and Goodin not only to remove the story, but also to be awarded damages and have legal costs covered.
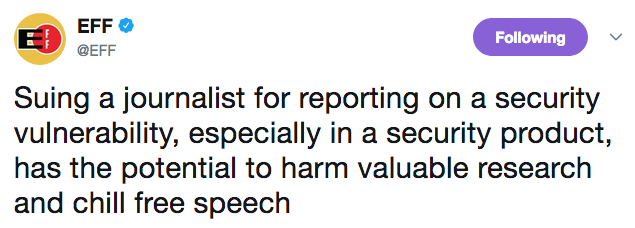
While some members of the cybersecurity industry have taken Keeper Security’s side, saying that many of Goodin’s stories are sensationalized, most have sided with the reporter and believe the lawsuit will cause more damage to the company than the article. Several people believe it will have a so-called “Streisand effect.”
This is not the first time Keeper Security has resorted to legal action over vulnerability disclosures. Back in 2013, it threatened to sue Netherlands-based security firm Fox-IT after it had discovered a critical flaw in one of its products.
Pepperl+Fuchs Ecom Rugged Devices Exposed to KRACK Attacks
21.12.2017 securityweek ICS
Rugged tablets, phones and PDAs made by Ecom Instruments use Wi-Fi components that are vulnerable to a recently disclosed attack method named KRACK.
Ecom Instruments, acquired last year by Germany-based factory automation solutions provider Pepperl+Fuchs, specializes in developing mobile devices designed for use in hazardous areas, including in the chemical and petrochemical, oil and gas exploration, mining, and energy sectors.
According to ICS-CERT and its German counterpart CERT@VDE, several Windows- and Android-based mobile devices from Ecom are affected by the KRACK flaws.
The list of vulnerable products includes Android-based Tab-Ex 01 tablets, Ex-Handy 09 and 209 phones, and Smart-Ex 01 and 201 smartphones, and Windows-based Pad-Ex 01 tablets, and i.roc Ci70-Ex, CK70A-ATEX, CK71A-ATEX, CN70A-ATEX and CN70E-ATEX PDAs.ecom mobile devices vulnerable to KRACK attacks

“ecom instruments devices are in theory attackable by replay, decryption and forging of packets,” CERT@VDE said in an advisory. “However, to perform the attack, the attacker must be significantly closer to the ecom device than to the access point. The WPA2 password cannot be compromised using a KRACK attack. Note if WPA-TKIP is used instead of AES-CCMP, an attacker can easily forge and inject packets directly into the WLAN.”
Pepperl+Fuchs and Ecom are working on addressing the vulnerabilities in the impacted Android products. As for the Windows-based devices, users have been advised to apply the patches provided by Microsoft and switch to using AES-CCMP encryption instead of WPA-TKIP.
KRACK, or Key Reinstallation Attack, is the name assigned to a series of vulnerabilities in the WPA2 protocol. The flaws can allow an attacker within range of the targeted device to read information that the user believes is encrypted and, in some cases, even inject and manipulate data.
The vulnerabilities affect millions of devices from tens or possibly hundreds of vendors. Pepperl+Fuchs is not the first industrial solutions provider to inform customers that its products are impacted by KRACK.
Days after the vulnerabilities were disclosed, Cisco, Rockwell Automation and Sierra Wireless admitted that their industrial networking devices had been vulnerable. A few weeks later, Siemens, ABB, Phoenix Contact, Lantronix and Johnson Controls also warned customers.
Experts believe the risk of attacks against the industrial devices themselves is not as big as the risk to systems used by ICS engineers and operators for remote access, such as smartphones, tablets, and network communication devices.