
Mirai Variant "Satori" Targets Huawei Routers
23.12.2017 securityweek BotNet
Hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers have been observed over the past month, Check Point security researchers warn.
The attacks were trying to drop Satori, an updated variant of the notorious Mirai botnet that managed to wreak havoc in late 2016. Targeting port 37215 on Huawei HG532 devices, the assaults were observed all around the world, including the USA, Italy, Germany and Egypt, the researchers say.
Common to these incidents was the attempt to exploit CVE-2017-17215, a zero-day vulnerability in the Huawei home router residing in the fact that the TR-064 technical report standard, which was designed and intended for local network configuration, was exposed to WAN through port 37215 (UPnP - Universal Plug and Play).
The affected device supports a service type named `DeviceUpgrade`, which is supposedly carrying out firmware upgrade actions. By injecting shell meta-characters “$()” in two elements with which the upgrade is carried out, a remote administrator could execute arbitrary code on the affected devices.
By successfully exploiting the flaw, an attacker could download and execute a malicious payload onto the impacted devices. In this case, the payload was the Satori botnet, Check Point notes.
Huawei was informed on the vulnerability on November 27. Within days, the company published an advisory to confirm the vulnerability and inform users on available measures to circumvent or prevent the exploit: using the built-in firewall function, changing default passwords, deploying a firewall at the carrier side.
“The customers can deploy Huawei NGFWs (Next Generation Firewall) or data center firewalls, and upgrade the IPS signature database to the latest version IPS_H20011000_2017120100 released on December 1, 2017 to detect and defend against this vulnerability exploits initiated from the Internet.” Huawei notes.
In this Satori attack, each bot is used to flood targets with manually crafted UDP or TCP packets. The bot first attempts to resolve the IP address of a command and control (C&C) server using DNS request with the hardcoded domain name, then gets the addresses from the DNS response and tries to connect via TCP on the hardcoded target port (7645).
The C&C server provides the number of packets used for the flooding action and their corresponding parameters, and can also pass an individual IP for attack or a subnet.
The bot’s binary, the researchers discovered, contains a lot of unused text strings, supposedly inherited from another bot or a previous version.
A custom protocol is used for C&C communication, which includes two hardcoded requests to check in with the server, which in turn responds with the parameters for launching distributed denial of service attacks.
While analyzing the incident, which involved the use of a zero-day and numerous servers to attack Huawei devices, the security researchers discovered that the actor behind the Satori botnet might be using the online handle of NexusZeta.
They were able to track the actor’s activity across several hacking forums and also discovered that NexusZeta is active on social media, most notably Twitter and Github, and has Skype and SoundCloud accounts under the name of Caleb Wilson (caleb.wilson37 / Caleb Wilson 37), but couldn’t determine if this is the attacker's real name.
Based on forum posts attributed to the actor, the researchers concluded that he isn’t an advanced actor, “but rather an amateur with lots of motivation, looking for the crowd’s wisdom.” What the security researchers couldn’t determine, however, was how the zero-day vulnerability arrived in the individual’s possession.
“Nonetheless, as seen in this case as well as others over the past year, it is clear that a combination of leaked malware code together with exploitable and poor IoT security, when used by unskilled hackers, can lead to disastrous results,” Check Point concludes.
Digmine Cryptocurrency Miner spreads via Facebook messenger
23.12.2017 securityaffairs Social
Researchers from security firm Trend Micro observed crooks spreading a new cryptocurrency mining bot dubbed Digmine via Facebook Messenger.
Watch out for video file (packed in zip archive) sent by your friends via Facebook messenger, according to the researchers from security firm Trend Micro crooks are using this technique to spread a new cryptocurrency mining bot dubbed Digmine.
The bot was first observed in South Korea, experts named it Digmine based on the moniker (비트코인 채굴기 bot) referred to in a report of recent related incidents in South Korea. Digmine infections were observed in other countries such as Vietnam, Azerbaijan, Ukraine, Vietnam, Philippines, Thailand, and Venezuela.
Attackers are targeting Google Chrome desktop users to take advantage of the recent spike in the price of cryptocurrencies.
Digmine is a Monero-cryptocurrency mining bot disguises as a non-embedded video file, under the name video_xxxx.zip, but is actually includes an AutoIt script.
The infection starts after the victims click on the file, the malicious code compromise the system and downloads its components and related configuration files from a command-and-control server.
Digmine first installs a miner (i.e. miner.exe—a modified version of an open-source Monero miner known as XMRig) that silently mines the Monero cryptocurrency in the background. The bot also installs an autostart mechanism and launch Chrome with a malicious extension that allows attackers to control the victims’ Facebook profile and used it to spread the malware to the victim’s Messenger friends list.
“Facebook Messenger works across different platforms, but Digmine only affects Facebook Messenger’s desktop/web browser (Chrome) version. If the file is opened on other platforms (e.g., mobile), the malware will not work as intended.” reads the analysis published by TrendMicro.
“Digmine is coded in AutoIt, and sent to would-be victims posing as a video file but is actually an AutoIt executable script. If the user’s Facebook account is set to log in automatically, Digmine will manipulate Facebook Messenger in order to send a link to the file to the account’s friends. “
Researchers observed that since Chrome extensions can only be installed via official Chrome Web Store, crooks launch Chrome (loaded with the malicious extension) via command line.
“The extension will read its own configuration from the C&C server. It can instruct the extension to either proceed with logging in to Facebook or open a fake page that will play a video” Trend Micro continues.
“The decoy website that plays the video also serves as part of their C&C structure. This site pretends to be a video streaming site but also holds a lot of the configurations for the malware’s components.”

The technique doesn’t work when users open the malicious video file through the Messenger app on their mobile devices.
“The abuse of Facebook is limited to propagation for now, but it wouldn’t be implausible for attackers to hijack the Facebook account itself down the line. This functionality’s code is pushed from the command-and-control (C&C) server, which means it can be updated.” continues the analysis.
Facebook had taken down most of the malware files from the social networking site.
Further info, including the IoCs are included in the report.
Satori is the latest Mirai botnet variant that is targeting Huawei HG532 home routers
23.12.2017 securityaffairs BotNet
Satori botnet, Mirai variant, is responsible for hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers.
The Mirai botnet makes the headlines once again, a new variant dubbed Satori is responsible for hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers.
The activity of the Satori botnet has been observed over the past month by researchers from Check Point security.
“A Zero-Day vulnerability (CVE-2017-17215) in the Huawei home router HG532 has been discovered by Check Point Researchers, and hundreds of thousands of attempts to exploit it have already been found in the wild.
The delivered payload has been identified as OKIRU/SATORI, an updated variant of Mirai.
The suspected threat actor behind the attack has been identified by his nickname, ‘Nexus Zeta’.” states the report published by Check Point security.
Satori is an updated variant of the notorious Mirai botnet that was first spotted by the malware researchers MalwareMustDie in August 2016. The malicious code was developed to target IoT devices, the Sartori version targets port 37215 on Huawei HG532 devices.
The attacks against Huawei HG532 devices were observed in several countries, including the USA, Italy, Germany, and Egypt.

Experts observed that attacks attempt to exploit the CVE-2017-17215 zero-day vulnerability in the Huawei home router residing in the fact that the TR-064 technical report standard, which was designed for local network configuration, was exposed to WAN through port 37215 (UPnP – Universal Plug and Play).
“In this case though, the TR-064 implementation in the Huawei devices was exposed to WAN through port 37215 (UPnP).
From looking into the UPnP description of the device, it can be seen that it supports a service type named `DeviceUpgrade`. This service is supposedly carrying out a firmware upgrade action by sending a request to “/ctrlt/DeviceUpgrade_1” (referred to as controlURL ) and is carried out with two elements named `NewStatusURL` and `NewDownloadURL`.” continues the analysis.
“The vulnerability allows remote administrators to execute arbitrary commands by injecting shell meta-characters “$()” in the NewStatusURL and NewDownloadURL”

The successful exploitation of the vulnerability could allow an attacker to download and execute the Satori bot.
The flaw was reported to Huawei on November 27, after a few days, the company published a security advisory that notifies the vulnerability to the users and provides recommendations to prevent the exploitation of the flaw.
Customers can take the following measures to circumvent or prevent the exploit of this vulnerability. For details, consult the local service provider or Huawei TAC.
Configure the built-in firewall function.
Change the default password.
Deploy a firewall at the carrier side.
“The customers can deploy Huawei NGFWs (Next Generation Firewall) or data center firewalls, and upgrade the IPS signature database to the latest version IPS_H20011000_2017120100 released on December 1, 2017 to detect and defend against this vulnerability exploits initiated from the Internet.” reads the andisory published by Huawei.
Each Satori bot floods targets with manually crafted UDP or TCP packets, they first attempt to resolve the IP address of a C&C server using DNS request with the hardcoded domain name, then gets the addresses from the DNS response and tries to connect via TCP on the hardcoded target port (7645).
The C&C server, in turn, provides the number of packets used for the flooding action and their corresponding parameters, and can also pass an individual IP for attack or a subnet.
The bot uses a custom protocol to communicate with the C&C, it includes two hardcoded requests to check in with the server that responds with the DDoS attack parameters.
The researchers that investigated the case determined that the actor behind the Satori botnet might be using the online handle of NexusZeta.
NexusZeta is very active on social media such as Twitter and Github, and has Skype and SoundCloud accounts under the name of Caleb Wilson (caleb.wilson37 / Caleb Wilson 37).
While the actor described himself as a novice (“an amateur with lots of motivation, looking for the crowd’s wisdom.”), it is unclear how he discovered the zero-day vulnerability .
“Nonetheless, as seen in this case as well as others over the past year, it is clear that a combination of leaked malware code together with exploitable and poor IoT security, when used by unskilled hackers, can lead to disastrous results,” Check Point concludes.
Travle aka PYLOT backdoor hits Russian-speaking targets
22.12.2017 Kaspersky Virus
At the end of September, Palo Alto released a report on Unit42 activity where they – among other things – talked about PYLOT malware. We have been detecting attacks that have employed the use of this backdoor since at least 2015 and refer to it as Travle. Coincidentally, KL was recently involved in an investigation of a successful attack where Travle was detected, during which we conducted a deep analysis of this malware. So, with this intelligence ready we are sharing our findings in this blog to supplement Palo Alto’s research with additional details.
Technical Details
MD5 SIZE LINKER COMPILED ON
7643335D06BAEC5A14C95A393592EA3F 164352 11.0 2016-10-14 06:21:07
The Travle sample found during our investigation was a DLL with a single exported function (MSOProtect). The malware name Travle was chosen given a string found in early samples of this family: “Travle Path Failed!”. This typo was replaced with correct word “Travel” in newer releases. We believe that Travle could be a successor to the NetTraveler family.
First of all, we detected numerous malicious documents being used in spear-phishing attacks with file names suggesting Russian-speaking targets with executables maintained in encrypted form:
This encryption method has been well known for a long time – it was first used in exploit documents to conceal Enfal, then we discovered this backdoor – Travle. Later documents with such encryption started maintaining another one APT family – Microcin. Travle C2 domains often overlap with those of Enfal. In regard to NetTraveler, at some point Enfal samples started using the same encryption method for maintaining the C2 URL as was used in NetTraveler:
Enfal sample with NetTraveler-like C2 string encryption
So, clearly these backdoors – Enfal, NetTraveler, Travle and Microcin – are all related to each other and are believed to have Chinese-speaking origins. And after finding the string “Travel path failed!” we believe that the Travle backdoor could be intended as a successor to the NetTraveler malware.
The malware starts by initializing the following variables:
%TEMP%\KB287640\ – local malware drop-zone
%TEMP%\KB887209\ – plugins storage
<malware install path>\~KB178495.DAT – configuration file path
Surprisingly, these paths remain the same in all samples of this family. If no configuration file is found, Travle reads the default settings from its resource “RAW_DATA“. Settings are maintained in an encrypted form. Here is the code for decryption:
for (i = size – 1; i > 1; –i)
buf[i] ^= buf[i – 2]
The storage format for the configuration block is as follows:
Offset Size Value
0 0x81 C2 domain
0x102 0x81 C2 URL path
0x204 2 C2 port (not used)
0x206 0xB not used
0x21C 0xB Sample ID
0x232 0x401 Bot’s first RC4 key
0xA34 0x401 Bot’s second RC4 key
0x1238 2 not used
The described sample maintains the following configuration data:
Field Value
C2 domain remember123321.com
C2 URL path /zzw/ash.py
Sample ID MjdfS0584
1st RC4 key mffAFe4bgaadbAzpoYRf
2nd RC4 key mffAFe4bgaadbAzpoYRf
The Travle backdoor starts its communication with the C2 by sending gathered information about the target operating system in an HTTP POST request to a URL built using the C2 domain and the path specified in the settings. The information sent includes the following data:
UserID – based on the computer name and IP-address
Computer name
Keyboard layout
OS version
IP-addresses
MAC-address
Once the C2 receives the first packet, it responds with a block of data containing the following information:
URL path for receiving commands
URL path for reporting on command execution results
URL path for downloading files from C2
URL path for uploading files to C2
C2 second RC4 key
C2 first RC4 key
C2 ID
After this packet has been received, Travle waits for additional commands from the server.
Communication encryption
The ciphering algorithm depends on the type of transmitted object. There are three possible variants:
Data
Data is ciphered with Base64
The resulting string is appended to the header with a size of 0x58 bytes
The resulting buffer is ciphered by RC4 with the C2 first RC4 key
The resulting buffer is ciphered with Base64
List of strings
Each line is ciphered by RC4 with the C2 second RC4 key
The resulting buffer is ciphered with Base64
All the previously Base64-ciphered strings are merged in one delimited with \r\n”
The resulting string is appended to the header with a size of 0x54 bytes
The resulting buffer is ciphered by RC4 with the C2 first RC4 key
The resulting buffer is ciphered with Base64
File
Compressed with LZO
The resulting archive is ciphered with the C2 second RC4 key
Messages format
The header for the transmitted data is as follows:
Offset (bytes) Size (bytes) Description
0 0x14 Random set of bytes
0x14 4 Data type / Command ordinal
0x18 4 NULL / Command ID
0x1C 4 Size of data
0x20 0x14 Sample ID
0x34 0x24 User ID
0x58 Size of data Data
The file is transferred to the C2 in a POST request as a multipart content type with boundary “kdncia987231875123nnm“. All samples of Travle we have discovered use this value.
Message types – from bot to C2
The command ID is specified at offset 0x18 in the header.
Technical messages are as follows:
ID Description Data content
1 Information about OS Information about OS
2 Request for the first command NULL
3 Request for the list of commands NULL
4 Command is successfully executed Information about command execution or the name of transmitted file
5 Command execution failed Information about an error
Operational messages are as follows:
ID Description Data content
1 Bot sends the list of files in the requested directory The list of files
11 Bot sends the content of the requested file The content of the file
Message types – from C2 to bot
In case of bot sending POST request C2 responses with data of following format:
ID Description Data content
0 Information about C2 The list of C2 parameters
1 Commands The list of commands
Bot also may send GET request for retrieving a specific file from the server. In this case, C2 responses with the requested file.
General communication between bot and C2
Interaction with C2 includes two stages:
1st (automatic – carried out with no operator actions). It consists of:
Sending information about the OS
Receiving information about C2
Sending a request for the first command
Receiving the command with ordinal 1 and first argument “*”
Sending the request for the next command
2nd (carried out by operators). It consists of:
Sending commands to the bot
Sending files to the bot
Sending results of the executed commands to the C2
Commands – general bot functionality
Ordinal Arguments Action
Scan File System
1 Path In case of “Path” is not “*”, the bot collects the list of files and folders in the specified directory with creation date between specified values and files with an “Encrypted” attribute.
If the “Path” is “*”, the search for files and folders is done in complete file system.
In any case, the search is recursive.
Minimum date
Maximum date
Run Process
2 Path to the batch or executable file The bot executes specified batch file or application with passed arguments.
Command line arguments
File Presence Test
4 File name The bot examines if specified file exists.
Delete File
3 File name File deletion.
Rename File
5 Old file name File renaming.
New file name
Move File
6 Old path File moving.
New path
Create New Config
7 Content of the new configuration The bot creates the file with new configuration.
Process File With Batch
48 Batch script The bot sends GET request to the C2 for downloading a file specified in one command argument. Batch script received in another command argument is saved in the file and executed with a parameter – file name of the downloaded file.
File path
Run Batch
49 Batch script The bot receives a BAT-file and executes it.
Download File
16 File path The bot sends a GET request for downloading a file. The file is saved with the specified name and location.
Upload File
17 File path The bot sends the content of a requested file in a POST message.
Download And Run Plugin
32 Plugin name The bot sends a GET request for downloading Plugin (DLL). Plugin is saved in the file system and launched with the use of the LoadLibrary API function.
Plugin argument
Unload Plugin
33 Plugin name The bot unloads a plugin library from memory.
Delete Plugin
34 Plugin name The bot unloads a plugin from memory and deletes the plugin file.
Load And Run Plugin
35 Plugin name The bot loads a plugin in memory with a specified parameter.
Plugin argument
Plugins
Unfortunately, we have been unable to receive plugins from any C2 found in examined Travle samples, but after analyzing the code of Travle we can briefly describe how they are handled.
Plugins are handled with the use of commands 32-35. From all the analyzed Travle samples, we found out that not every Travle sample is able to work with plugins.
Each plugin DLL is saved in a file and loaded with the use of the LoadLibrary API function. The DLL should export three functions: GetPluginInfo, Starting and FreeMemory. These functions are invoked one-by-one at the plugin DLL loading stage. When Travle has to unload the plugin DLL it calls the FreeLibrary API function.
In all analyzed Travle samples, plugins are saved in the same location: %TEMP%\KB887209\.
Conclusion
The actor or actors responsible for the Travle attack has been active during the last few years, apparently not worried about being tracked by AV companies. Usually, modifications and new additions to their arsenal are discovered and detected quite quickly. Still, the fact that they didn´t really need to change their TTPs during all these years seems to suggest that they don´t need to increase their sophistication level in order to fulfill their goals. What’s worse, according to subjects of decoy documents these backdoors are used primarily in the CIS region against government organizations, military entities and companies engaged in high-tech research, which indicates that even high-profile targets still have a long way to go to implement IT-sec best practices which efficiently resist targeted attacks.
We detect Travle samples with the following verdicts:
Trojan.Win32.Tpyn.*
Trojan.Win32.TravNet.*
Trojan-Spy.Win32.TravNet.*
HEUR:Trojan.Win32.Generic
HEUR:Trojan.Win32.TravNet.gen
HEUR:Backdoor.Win32.NetTraveler.gen
Nhash: petty pranks with big finances
22.12.2017 Kaspersky Security
According to our data, cryptocurrency miners are rapidly gaining in popularity. In an earlier publication we noted that cybercriminals were making use of social engineering to install this sort of software on users’ computers. This time, we’d like to dwell more on how exactly the computers of gullible users start working for cybercriminals.
Beware freebies
We detected a number of similar websites with offers to download various types of free software. Some of them really were free applications (such as OpenOffice), while others attempted to entice users with “free” software packages of Adobe Premiere Pro, CorelDraw, PowerPoint, etc. From the victim’s point of view, the software was indeed free – it didn’t ask for activation keys and could be used immediately. Moreover, the cybercriminals used domain names resembling those of recognized legitimate products, such as thefinereader.ru, theopenoffice.ru, etc. There was one thing all these apps had in common – they were installed on the victim computer along with a custom-configured version of cryptocurrency mining software from the NiceHash project.
All sites followed the same design template, differing only in their product descriptions and download links
Mining coins at any price
Kaspersky Lab’s products detect the NiceHash miner with the verdict not-a-virus:RiskTool.Win64.BitCoinMiner.cgi; it is not malicious according to Kaspersky Lab’s classification. According to KSN data, around 200 files are detected with this verdict. We chose the file FineReader-12.0.101.382.exe for analysis. It was obtained from the website thefinereader.ru which is no longer available; at this website, it was presented as a “free full version” of ABBYY FineReader. It should be noted that this hacked version, minus the miner component, has long been available on the internet via Torrent file distribution systems:
The executable file contains the installation package Inno Setup; unpacking it will produce a number of folders containing the actual software and its resources, as well as an installation guide script. The installer’s root folder looks like this:
The {app} folder is of interest to us; it contains the software that is installed. This folder contains a ‘portable’ version of FineReader:
The lib folder contains some suspicious-looking files:
Among these files is the NiceHash miner that we mentioned above. There are also text files in this folder that contain the information required to initialize the miner – namely the wallet details and the mining pool’s address. This folder will be installed stealthily to the victim computer while FineReader is installing.
A shortcut will also be created in the autorun folder:
The shortcut reveals the path to the miner’s work directory on the C drive:
That leaves the tskmgr.exe and system.exe files of interest for analysis. Both files are BAT scripts compiled into PE files. Let’s look at the contents of system.exe after extracting the BAT script:
It ensures the wallet’s address is up to date and initializes the miner’s operation. It contacts the following addresses:
http://176.9.42.149/tmp1.txt
http://176.9.42.149/tmp3.txt?user=default&idurl=3
http://176.9.42.149/tmp2.txt?user=3id170927143302
After the third query, the following response is received:
This is a PowerShell script that assigns a unique ID to the infected computer and launches mining with the correct wallet details (in this specific case, the zcash cryptocurrency is mined). IDs are generated following a specific algorithm based on the mining start time. For example, the ID 4v09v2017v03v24v26 is made up of the date (14.09.2017) and time (03:24:26).
We have also identified other types of covert miners with a slightly different logic. Below is the same Inno Setup installation package, but if we take a look at its contents, we can see lots of shortcuts:
Let’s take a look inside:
This is a classic case – the shortcuts are scattered across the system; when opened by the user, they launch the miner. The package includes the TrayIt! utility that hides the miner’s window from the user by minimizing it to the system tray. This miner doesn’t receive any data from the server, but instead operates using the wallet and pool details that were hardwired into it.
Finances
Among the mining pools used by cybercriminals, we detected some that provided statistics about the wallets and the number of miners. At the time of our analysis, total revenue from all wallets was nearly US$3400.
The t1WSaZQxqBLLtGMKsGT6t9WGHom8LcE8Ng5 wallet
The t1JA25kJrAaUw9xe6TzGiC8BU5pZRhgL4Ho wallet
The t1N7sapDRuYdqzKgPwet8L31Z9Aa96i7hy4 wallet
The 3MR6WuGkuPDqPZgibV6gi4DaC7qMabEFks wallet
Conclusion
This small piece of research once again demonstrates that no one should ignore protection measures and get lulled into a false sense of security, believing cybercriminals are only interested in financial organizations; practice shows that regular users are also targeted. The mining software that we analyzed, albeit incapable of inflicting any damage, can seriously impair your workstation’s performance by hijacking its resources and making it work for somebody else.
Indicators of Compromise
C&C
176.9.42.149
MD5
a9510e8f59a34a17ca47df9f78173291
19cdaf36a4bafd84c9f7b2cfff09ca50
613bd514f42e7cc78d6e0e267fc706d0
ab31d1cbed96114f2ea9797030fb608f
0a571873a125c846861127729fcf41bb
fd8f89a437bcb5490a92dc1609f190d1
dd639dc20f62393827c2067021b7fd50
6b567d817b94f714c0005e183ffb6d47
11e66ac4c9e7e3d0b341bdb51f5f8740
58c7db74c6ce306037f22984dd758362
f38b5a31eee2fd8c97249cefbc5fa19f
f378951994051bf90dc561457c88c69f
fb9c1f949f95caeada09c0fd70fb5416
b017f2836988f93b80f4322dbd488e00
211c6c52527b8c1029d64bb75a9a39d8
57cda2f33fce912f4f5eecbc66a27fa6
URLs
thefinereader[.]ru
abby-finereader[.]ru
thexpadder[.]ru
theteamspeak[.]ru
thecoreldraw[.]ru
the-powerpoint[.]ru
theoutlook[.]ru
picturemanager[.]ru
furmark[.]ru
thedxtory[.]ru
thevisio[.]ru
kmp-pleer[.]ru
theadobepremiere[.]ru
cdburner-xp[.]ru
theopenoffice[.]ru
iobit-uninstaller[.]ru
Jack of all trades
22.12.2017 Kaspersky Android
Nowadays, it’s all too easy to end up with malicious apps on your smartphone, even if you’re using the official Google Play app store. The situation gets even worse when you go somewhere other than the official store – fake applications, limited security checks, and so on. However, the spread of malware targeting Android OS is not limited to unofficial stores – advertising, SMS-spam campaigns and other techniques are also used. Among this array of threats we found a rather interesting sample – Trojan.AndroidOS.Loapi. This Trojan boasts a complicated modular architecture that means it can conduct a variety of malicious activities: mine cryptocurrencies, annoy users with constant ads, launch DDoS attacks from the affected device and much more. We’ve never seen such a ‘jack of all trades’ before.
Distribution and infection
Samples of the Loapi family are distributed via advertising campaigns. Malicious files are downloaded after the user is redirected to the attackers’ malicious web resource. We found more than 20 such resources, whose domains refer to popular antivirus solutions and even a famous porn site. As we can see from the image below, Loapi mainly hides behind the mask of antivirus solutions or adult content apps:
After the installation process is finished, the application tries to obtain device administrator permissions, asking for them in a loop until the user agrees. Trojan.AndroidOS.Loapi also checks if the device is rooted, but never subsequently uses root privileges – no doubt they will be used in some new module in the future.
After acquiring admin privileges, the malicious app either hides its icon in the menu or simulates various antivirus activity, depending on the type of application it masquerades as:
Self-protection
Loapi aggressively fights any attempts to revoke device manager permissions. If the user tries to take away these permissions, the malicious app locks the screen and closes the window with device manager settings, executing the following code:
As well as this fairly standard technique to prevent removal, we also found an interesting feature in the self-protection mechanism. The Trojan is capable of receiving from its C&C server a list of apps that pose a danger. This list is used to monitor the installation and launch of those dangerous apps. If one of the apps is installed or launched, then the Trojan shows a fake message claiming it has detected some malware and, of course, prompts the user to delete it:
This message is shown in a loop, so even if the user rejects the offer, the message will be shown again and again until the user finally agrees and deletes the application.
Layered architecture
Let’s take a look at the Trojan’s architecture in more detail:
At the initial stage, the malicious app loads a file from the “assets” folder, decodes it using Base64 and afterwards decrypts it using XOR operations and the app signature hash as a key. A DEX file with payload, which was retrieved after these operations, is loaded with ClassLoader.
At the second stage, the malicious app sends JSON with information about the device to the central C&C server hxxps://api-profit.com:
A command in the following format is received as a response from the server:
Where “installs” is a list of module IDs that have to be downloaded and launched; “removes” is a list of module IDs that have to be deleted; “domains” is a list of domains to be used as C&C servers; “reservedDomains” is an additional reserved list of domains; “hic” is a flag that shows that the app icon should be hidden from the user; and “dangerousPackages” is a list of apps that must be prevented from launching and installing for self-protection purposes.
At the third stage, the modules are downloaded and initialized. All the malicious functionality is concealed inside them. Let’s take a closer look at the modules we received from the cybercriminals’ server.
Advertisement module
Purpose and functionality: this module is used for the aggressive display of advertisements on the user’s device. It can also be used for secretly boosting ratings. Functionality:
Display video ads and banners
Open specified URL
Create shortcuts on the device
Show notifications
Open pages in popular social networks, including Facebook, Instagram, VK
Download and install other applications
Example of task to show ads received from the server:
While handling this task, the application sends a hidden request with a specific User-Agent and Referrer to the web page hxxps://ronesio.xyz/advert/api/interim, which in turn redirects to a page with the ads.
SMS module
Purpose and functionality: this module is used for different manipulations with text messages. Periodically sends requests to the C&C server to obtain relevant settings and commands. Functionality:
Send inbox SMS messages to attackers’ server
Reply to incoming messages according to specified masks (masks are received from C&C server)
Send SMS messages with specified text to specified number (all information is received from C&C server)
Delete SMS messages from inbox and sent folder according to specified masks (masks are received from C&C server)
Execute requests to URL and run specified Javascript code in the page received as a response (legacy functionality that was later moved to a separate module)
Web crawling module
Purpose and functionality: this module is used for hidden Javascript code execution on web pages with WAP billing in order to subscribe the user to various services. Sometimes mobile operators send a text message asking for confirmation of a subscription. In such cases the Trojan uses SMS module functionality to send a reply with the required text. Also, this module can be used for web page crawling. An example of a web page crawling task received from the server is shown below:
This module together with the advertisement module tried to open about 28,000 unique URLs on one device during our 24-hour experiment.
Proxy module
Purpose and functionality: this module is an implementation of an HTTP proxy server that allows the attackers to send HTTP requests from the victim’s device. This can be used to organize DDoS attacks against specified resources. This module can also change the internet connection type on a device (from mobile traffic to Wi-Fi and vice versa).
Mining Monero
Purpose and functionality: this module uses the Android version of minerd to perform Monero (XMR) cryptocurrency mining. Mining is initiated using the code below:
The code uses the following arguments:
url – mining pool address, “stratum+tcp://xmr.pool.minergate.com:45560”
this.user – username, value randomly selected from the following list: “lukasjeromemi@gmail.com”, “jjopajopaa@gmail.com”, “grishaobskyy@mail.ru”, “kimzheng@yandex.ru”, “hirt.brown@gmx.de”, “swiftjobs@rambler.ru”, “highboot1@mail333.com”, “jahram.abdi@yandex.com”, “goodearglen@inbox.ru”, girlfool@bk.ru
password – constant value, “qwe”
Old ties
During our investigation we found a potential connection between Loapi and Trojan.AndroidOS.Podec. We gathered some evidence to support this theory:
Matching C&C server IP addresses. The current address of the active Loapi C&C server is resolved with DNS to 5.101.40.6 and 5.101.40.7. But if we take a look at the history, we can see other IP addresses to which this URL resolved before:
At first, this URL was resolved to the IP address 91.202.62.38. If we analyze the history of DNS records that resolved to this address, we see the following:
As we can see from the records, in 2015 (when Podec was active), this IP address was resolved from various generated domains, and many of them were used in Podec (for example, obiparujudyritow.biz, in the 0AF37F5F07BBF85AFC9D3502C45B81F2 sample).
Matching unique fields at the initial information collection stage. Both Trojans collect information with similar structure and content and send it in JSON format to the attackers’ server during the initial stage. Both JSON objects have the fields “Param1”, “Param2” and “PseudoId”. We performed a search in our internal ElasticSearch clusters – where we store information about clean and malicious applications – and found these fields were only used in Podec and Loapi.
Similar obfuscation.
Similar ways of detecting SU on a device.
Similar functionality (both can subscribe users to paid services).
None of these arguments can be considered conclusive proof of our theory, but taken together they suggest there’s a high probability that the malicious applications Podec and Loapi were created by the same group of cybercriminals.
Conclusion
Loapi is an interesting representative from the world of malicious Android apps. It’s creators have implemented almost the entire spectrum of techniques for attacking devices: the Trojan can subscribe users to paid services, send SMS messages to any number, generate traffic and make money from showing advertisements, use the computing power of a device to mine cryptocurrencies, as well as perform a variety of actions on the internet on behalf of the user/device. The only thing missing is user espionage, but the modular architecture of this Trojan means it’s possible to add this sort of functionality at any time.
P.S.
As part of our dynamic malware analysis we installed the malicious application on a test device. The images below show what happened to it after two days:
Because of the constant load caused by the mining module and generated traffic, the battery bulged and deformed the phone cover.
C&C
ronesio.xyz (advertisement module)
api-profit.com:5210 (SMS module and mining module)
mnfioew.info (web crawler)
mp-app.info (proxy module)
Domains
List of web resources from which the malicious application was downloaded:
Domain IP
a2017-security.com 91.202.62.45
alert.com–securitynotice.us 104.18.47.240,104.18.46.240
alibabadownload.org 91.202.62.45
antivirus-out.net 91.202.62.45
antivirus360.ru 91.202.62.45,31.31.204.59,95.213.165.247,
194.58.56.226,194.58.56.50
clean-application.com 91.202.62.45
defenderdevicebiz.biz 104.27.178.88,104.27.179.88
fixdevice.biz 104.18.45.199,104.18.44.199
highspeard.eu 91.202.62.45
hoxdownload.eu 91.202.62.45
lilybrook.ru 104.24.113.21,104.24.112.21
nootracks.eu 91.202.62.45
noxrow.eu 91.202.62.45
s4.pornolub.xyz 91.202.62.45
sidsidebottom.com 9.56.163.55,104.27.128.72
titangelx.com 104.27.171.112,104.27.170.112
trust.com-mobilehealth.biz 04.27.157.60,104.27.156.60
trust.com-securitynotice.biz 104.31.68.110,104.31.69.110
violetataylor.ru 104.31.88.236,104.31.89.236
Beware of Cryptocurrency Mining Virus Spreading Through Facebook Messenger
22.12.2017 thehackernews Social
If you receive a video file (packed in zip archive) sent by someone (or your friends) on your Facebook messenger — just don’t click on it.
Researchers from security firm Trend Micro are warning users of a new cryptocurrency mining bot which is spreading through Facebook Messenger and targeting Google Chrome desktop users to take advantage of the recent surge in cryptocurrency prices.
Dubbed Digmine, the Monero-cryptocurrency mining bot disguises as a non-embedded video file, under the name video_xxxx.zip (as shown in the screenshot), but is actually contains an AutoIt executable script.
Once clicked, the malware infects victim’s computer and downloads its components and related configuration files from a remote command-and-control (C&C) server.
Digimine primarily installs a cryptocurrency miner, i.e. miner.exe—a modified version of an open-source Monero miner known as XMRig—which silently mines the Monero cryptocurrency in the background for hackers using the CPU power of the infected computers.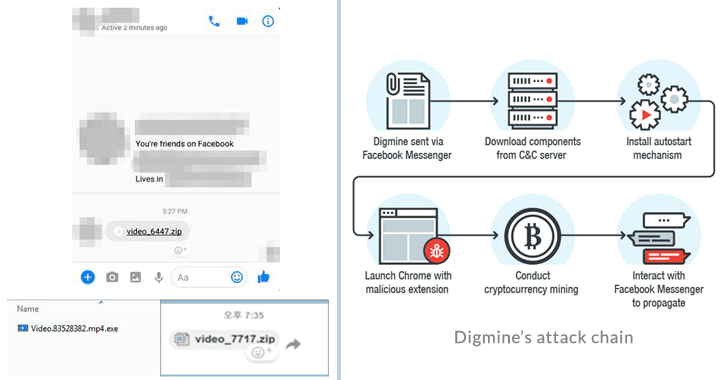
Besides the cryptocurrency miner, Digimine bot also installs an autostart mechanism and launch Chrome with a malicious extension that allows attackers to access the victims’ Facebook profile and spread the same malware file to their friends' list via Messenger.
Since Chrome extensions can only be installed via official Chrome Web Store, "the attackers bypassed this by launching Chrome (loaded with the malicious extension) via command line."
"The extension will read its own configuration from the C&C server. It can instruct the extension to either proceed with logging in to Facebook or open a fake page that will play a video" Trend Micro researchers say.
"The decoy website that plays the video also serves as part of their C&C structure. This site pretends to be a video streaming site but also holds a lot of the configurations for the malware’s components."
It's noteworthy that users opening the malicious video file through the Messenger app on their mobile devices are not affected.
Since the miner is controlled from a C&C server, the authors behind Digiminer can upgrade their malware to add different functionalities overnight.
Digmine was first spotted infecting users in South Korea and has since spread its activities to Vietnam, Azerbaijan, Ukraine, Philippines, Thailand, and Venezuela. But since Facebook Messenger is used worldwide, there are more chances of the bot being spread globally.
When notified by Researchers, Facebook told it had taken down most of the malware files from the social networking site.
Facebook Spam campaigns are quite common. So users are advised to be vigilant when clicking on links and files provided via the social media site platform.
Nissan Finance Canada Suffers Data Breach — Notifies 1.13 Million Customers
22.12.2017 thehackernews Incindent
It's the last month of this year, but possibly not the last data breach report.
Nissan warns of a possible data breach of personal information on its customers who financed their vehicles through Nissan Canada Finance and INFINITI Financial Services Canada.
Although the company says it does not know precisely how many customers were affected by the data breach, Nissan is contacting all of its roughly 1.13 million current and previous customers.
In a statement released Thursday, Nissan Canada said the company became aware of an "unauthorized access to personal information" of some customers on December 11.
"Nissan Canada Finance recently became aware it was the victim of a data breach that may have involved an unauthorized person(s) gaining access to the personal information of some customers that have financed their vehicles through Nissan Canada Finance and INFINITI Financial Services Canada," the company said.
It's believed that the unknown hacker(s) may have had access to the following information:
Customers' names
Home addresses
Vehicle makes and models
Vehicle identification numbers (VIN)
Credit scores
Loan amounts
Monthly payments
The company says there no indication, at least at this moment, that if the data breach also includes payment information and contactable information like email addresses or phone numbers.
The company offers 12 months of free credit monitoring services through TransUnion to all of its financed customers.
Since the investigation into the data breach incident is still ongoing, it is not clear if the hack also impacts customers outside of Canada and customers who did not obtain financing through NCF.
"We sincerely apologize to the customers whose personal information may have been illegally accessed and for any frustration or inconvenience that this may cause," Nissan Canada president Alain Ballu said. "We are focused on supporting our customers and ensuring the security of our systems."
Nissan Canada has contacted Canadian privacy regulators, law enforcement, and data security experts to help rapidly investigate the matter.
Chinese Hackers Target Servers With Three Types of Malware
22.12.2017 securityweek BigBrothers
An established Chinese crime group uses a large coordinated infrastructure to target servers running database services with three different types of malware, GuardiCore security researchers say.
The group is operating worldwide and has been observed launching multiple attacks over the past several months. Each of the three malware families employed – Hex, Hanako and Taylor – is targeting different SQL servers and has its own goals, scale and target services.
According to GuardiCore, a campaign targeting a single server has started in March of this year and evolved into thousands of attacks per day during summer, hitting numerous MS SQL Server and MySQL services. The compromised machines were used for various activities, including cryptocurrency mining, distributed denial of service (DDoS), and for implanting Remote Access Trojans (RATs).
While most of the compromised machines are located in China, some were observed in Thailand, the U.S., Japan, and other countries. Database services on both Windows and Linux machines are targeted.
The three campaigns launched from this infrastructure differ mostly in target goals: Hex focuses on cryptocurrency miners and RATs; Hanako builds a DDoS botnet; and Taylor installs a keylogger and a backdoor. To date, the security firm has observed hundreds of Hex and Hanako attacks and tens of thousands of Taylor incidents each month.
“From what we’ve seen, the attackers often compromise public and private cloud deployments without chasing any specific domain. This is shown in their frequent scanning of Azure and AWS public IP ranges (which are publicly available) while looking for potential victims,” GuardiCore says.
Compromised machines aren’t used for long
To fly under the radar, the actors use each machine to attack only a small number of IPs. The security researchers discovered that victims are re-purposed to make tracing as difficult as possible: every compromised machine is used for about a month and then rotated out of use.
The infected systems are used for scanning, launching attacks, hosting malware executables and as command and control (C&C) servers. Most of the attacks feature three simple steps: scanning, attacking and initial implant.
The scan machines search for subnets and create ‘hit lists’ of IPs and credentials. The attackers, the researchers say, start from a large set of IP ranges and look for machines running services such as HTTP web servers, MS SQL Server, ElasticSearch, and more.
Based on said ‘hit lists’, the attacker machines attempt to gain an initial foothold on the servers through brute forcing MS SQL and MySQL databases. Next, they execute predefined SQL commands to gain full control of the victim machine, such as creating new users for persistency.
Parts of the campaign, such as the RATs, are hosted on separate file servers, to ensure attacks aren’t dependent on a single server. In addition to this modular approach, the infrastructure features both FTP and HFS (HTTP File Server) servers and is used to deliver additional attack tools after the initial dropper runs.
While the Tylor attacks were observed downloading the files from two domains down@mys2016@info and js@mys2016@info, both registered in March 2017, Hex and Hanako were observed using a unique file server per attack.
Attack flow
After brute forcing their way onto the target servers (an operation possible because many admins don’t harden the database beyond the use of a password), the attackers use xp_cmshell, a variety of stored procedures and OLE automation, to upload their first set of tools.
The droppers employed by the group usually establish persistency by creating a backdoor user and opening the Remote Desktop port. Next, malware is downloaded from a short lived FTP or HTTP server.
Later on, the attackers also stop or disable anti-virus and monitoring applications and attempt to cover tracks by deleting any unnecessary registry, file, and folder entries. The downloaded malware attempts to trick detection by using a fake MFC user interface and abnormally sized binaries containing large quantities of junk data.
Hex and Hanako, the security researchers discovered, use the same MS SQL Server attack flow and download unique attack configuration files. They create an identical scheduled task to run the same unique binary and target the same antivirus products.
Hanako gets its name after the backdoor user added to targeted databases.
Written in C++, Hex (it uses name variations of Hex.exe) can log key strokes and capture the screen and microphone to extract information from the victim machines and can download and execute additional modules.
The malware masquerades as Kugou Player, a popular Chinese music streaming service. Along with comments in Chinese found in the code, targets’ location, and configuration files showing email addresses from popular Chinese providers, this suggests that the actor behind the campaign is of Chinese origin, the researchers say.
Taylor (named after an image of Taylor Swift used to hide the keylogger) has been observed in over 80,000 attack attempts since March. As part of the attack, a backdoor related to the 2016 Mirai botnet is also downloaded onto the compromised servers, the researchers say.
Although it uses the same domain names over time and does not change IP addresses often, Taylor uses a more cautious attack script, where the hackers send most of the queries encoded in hex. They also store references to the servers in HTML pages downloaded during the attack.
“The best way to minimize your exposure to campaigns targeting databases is to control the machines that have access to the database. Routinely review the list of machines that have access to your databases, keep this list to a minimum and pay special attention to machines that are accessible directly from the internet. Every connection attempt from an IP or domain that does not belong to this list should be blocked and investigated,” GuardiCore concludes.
“There isn’t a server out there that is connected to a LAN which isn’t vulnerable to malware. If the LAN is connected to the Internet, bad actors can get in. Since infection is inevitable, it is important to watch for the telltale signs of an infection. Behaviors such as abnormal traffic to another host can be an indicator and this could be in the form of excessive connections (E.g. DDoS), bytes, or other metric. Even light scanning behaviors can be detected. Leveraging flow data for network traffic analytics is one of the best resources for monitoring and malware incident response,” Michael Patterson, CEO of Plixer, told SecurityWeek in an emailed comment.
Lithuania Bans Kaspersky Software as 'Potential' Threat
22.12.2017 securityweek BigBrothers
Lithuania will ban Moscow-based cyber security firm Kaspersky Lab's products from computers managing key energy, finance and transport systems due to security concerns, authorities said Thursday.
The Russian firm's software was banned from US government networks earlier this year amid allegations that it helped Russian intelligence steal top secret information.
"The government... recognised that Kaspersky Lab software is a potential national security threat," the Baltic EU state's defence ministry said in a statement.
The government agencies responsible for "critical infrastructure" must replace the popular anti-virus software in "a short while", it added.
Lithuanian intelligence chief Darius Jauniskis recently said the cyberfirm "was sometimes acting as a toy in the hands of (Russian President Vladimir) Putin's administration".
Kaspersky has repeatedly denied having any inappropriate ties with the Kremlin and said that malware-infected Microsoft Office software and not its own was to blame for the hacking theft of American intelligence materials.
Kaspersky told Russian media on Thursday it was "disappointed" and assured customers they "do not have to worry because they have not been subjected to any violation from our company."
"The Kaspersky laboratory has never helped nor will it ever assist any state in the world to engage in cyber-espionage or to conduct cyber-attacks," the company said. "The Kaspersky laboratory has no political connection or affiliation with any government."
Lithuania, a NATO and EU member of 2.8 million people, has been one of the most vocal critics of Russia, notably after its 2014 annexation of the Crimea peninsula from Ukraine.
Google Warns DoubleClick Customers of XSS Flaws
22.12.2017 securityweek Vulnerebility
Google has warned DoubleClick customers that some of the files provided by third-party vendors through its advertising platform can introduce cross-site scripting (XSS) vulnerabilities.
The tech giant has shared a list of more than a dozen advertising firms whose files are vulnerable to XSS attacks. The company has advised website owners and administrators to check if the files are present on their server – they are typically hosted in the root domain – and remove them.
“We have disabled these vendors where possible for all DoubleClick for Publishers and DoubleClick Ad Exchange customers. However, any of the mentioned files hosted on your site may still pose a risk and should be taken down. We will notify you as we learn more,” Google said.
Google’s DoubleClick for Publishers (DFP) and DoubleClick Ad Exchange advertising services allow customers to display ads outside an iframe, the inline frame used for embedding content within an HTML page. In order to expand ads outside the iframe, Google and third-party ad firms provide what is called an “iframe buster kit,” which includes several HTML and JavaScript files that need to be hosted on the customer’s domain.
Some of these files contain XSS vulnerabilities that allow attackers to execute arbitrary JavaScript code in the context of a user’s browser by getting the victim to click on a specially crafted link.
The issue was brought to light earlier this week by a researcher who uses the online monikers “Zmx” and “Tr4L.” He is an employee of IDM, a company that specializes in solutions for managing, delivering and monetizing content. The firm uses the problematic iframe buster kit, which led to the discovery of the vulnerabilities.
A proof-of-concept (PoC) provided by Zmx shows how these XSS bugs can be triggered:
https://www.jobisjob.ch/predicta/predicta_bf.html?dm=bgtian.life
Zmx told SecurityWeek that he disclosed his findings via the Full Disclosure mailing list on Tuesday without notifying Google “because he is lazy.” It’s unclear if Google’s alert to customers comes in response to the researcher’s post or if it learned about the flaws from other sources. We have reached out to Google for clarifications and will update this article if the company responds.
Zmx also pointed out that there are several other problematic iframe buster kits for expandable ads that may not be provided by Google. The vulnerable kits identified by the researcher and not included in Google’s list come from Undertone, Interpolls and IgnitionOne (netmng.com).
UPDATE. Google has provided the following statement to SecurityWeek:
"We have disabled these vendors, removed these files, and added instructions in our help center to help publishers manage any additional steps to help ensure their users are secure."
North Korean Hackers Targeting Individuals: Report
22.12.2017 securityweek BigBrothers
North Korea Bitten by Bitcoin Bug
North Korean state-sponsored hacking group Lazarus has started targeting individuals and organizations directly, instead of focusing exclusively on spying on financial institutions, Proofpoint reports.
Active since at least 2009, the Lazarus Group is considered one of the most disruptive nation-state sponsored actors, accused of being involved in numerous high-profile attacks. Some of these include the 2014 Sony Pictures hack, last year’s theft of $81 million from the Bangladesh Bank, and this year’s WannaCry ransomware attack.
The group was recently observed to be increasingly focused on financially motivated attacks and was named as the most serious threat against banks earlier this year. More recently, the group also started showing high interest in the skyrocketing prices of cryptocurrencies.
The multistage attacks that Proofpoint has uncovered rely on cryptocurrency-related lures to spread sophisticated backdoors and reconnaissance malware. In some cases, the hackers deploy additional malware, including the Gh0st remote access Trojan (RAT), in an attempt to steal credentials for cryptocurrency wallets and exchanges.
What’s more, Proofpoint's security researchers discovered that the nation-state actor also started targeting a point-of-sale (PoS) related framework to steal credit card data. These PoS attacks can potentially incur high financial losses given their timing near the holiday shopping season.
In a new report (PDF), Proofpoint details a new toolset associated with the Lazarus Group. Dubbed PowerRatankba, the toolset has been targeting individuals, companies, and organizations with interests in cryptocurrency via spear-phishing and phishing campaigns.
The hackers were observed using a total of six different attack vectors to deliver PowerRatankba, including a new Windows executable downloader called PowerSpritz, a malicious Windows Shortcut (LNK) file, malicious Compiled HTML Help (CHM) files, JavaScript (JS) downloaders, two macro-based Microsoft Office documents, and backdoored popular cryptocurrency applications hosted on internationalized domain (IDN) infrastructure, thus appearing as legitimate.
The campaigns started on or around June 30, 2017 and included highly targeted spear-phishing attacks focused on at least one executive at a cryptocurrency organization. While a PowerRatankba.A variant was used in these attacks, the rest of the campaigns used PowerRatankba.B, Proofpoint says.
Attack vectors
The PowerSpritz downloader hides both its legitimate payload and malicious PowerShell command using the Spritz encryption algorithm. The downloader has been delivered via spear-phishing attacks using the TinyCC link shortener service to hide the malicious link.
Posing as Telegram or Skype updates, PowerSpritz would first launch a legitimate installer to trick the user into believing they downloaded a working application installer or update. In the background, however, a PowerShell command is executed to download the first stage of PowerRatankba.
A malicious LNK file was observed using a known AppLocker bypass to retrieve the payload from a TinyURL shortener link. The CHM files abuse a well-known technique to create a shortcut object capable of executing malicious code and to cause the object to be automatically clicked.
The JavaScript (JS) downloaders are hosted on supposedly attacker-controlled servers and have been designed to retrieve decoy PDF documents featuring themes such as cryptocurrency exchanges Coinbase and Bithumb, the Falcon Coin ICO, and a list of Bitcoin transactions.
The researchers also associated two VBScript macro-laden Microsoft Office documents with this activity, namely one Word document and one Excel spreadsheet. The former uses an Internal Revenue Service (IRS) theme, while the latter uses a Bithumb lure.
New first-stage implant
Recent attacks involved the use of phishing emails to direct users to fake webpages in an attempt to trick them into downloading or updating cryptocurrency applications. A backdoor in the PyInstaller executables, however, was meant to download PowerRatankba.
The implant, supposedly a successor of Ratankba, which was publicly detailed earlier this year, is a first stage reconnaissance tool used for the deployment of further stage implants. Using HTTP for command and control (C&C) communication, PowerRatankba first sends information about the machine, including computer name, IP address, OS boot time and installation date, language, info on ports 139/3389/445, a process list, and output from two WMIC commands (PowerRatankba.B only).
After initial contact with the C&C, PowerRatankba.A sends a request to receive commands from the server. This malware variant can download a payload and execute it via memory injection; can download the payload, save it to disk, and then execute it; can sleep and send request after sleep; and exit.
For persistence, PowerRatankba.A saves a JS file to the Startup folder. Depending on whether it runs under an admin account or not, PowerRatankba.B either downloads a PowerShell script, saves it to disk, and creates a scheduled task to execute it on system startup, or downloads a VBScript file and saves it to the Startup folder.
PowerRatankba.B was observed delivering a custom variant of the Gh0st RAT to several devices, but only to victims with obvious interest in cryptocurrencies. An attack involving the RAT revealed immediate interest in taking full remote control of the infected device to interact with a password-protected Bitcoin wallet, among other applications.
POS malware
The North Korean state-sponsored hackers appear to be interested in other financially motivated actions as well, beyond stealing millions in cryptocurrency. Thus, Proofpoint has discovered what appears to be a Lazarus operation focused on targeting PoS terminals of businesses operating in South Korea.
Dubbed RatankbaPOS, this might be “the first publicly documented nation-state sponsored campaign to steal PoS data from a PoS-related framework,” the security researchers note.
Although it’s unclear how the new malware variant is distributed, Proofpoint believes that PowerRatankba is used to deploy later stage implants that would ultimately infect systems with RatankbaPOS. The file was found on a C&C in plaintext, suggesting that it wasn’t deployed using the reconnaissance tool.
Deployment is achieved through a process injection dropper that can also achieve persistence by creating a registry key. The malware first checks with the server for an update and then starts the process injection search.
RatankbaPOS would hook a KSNETADSL.dll module “which appears to be the handling of encrypted and decrypted credit card numbers for a KSNET-related POS framework system.” According to Proofpoint, however, the module (two of them, actually) isn’t the correct target for the malware.
The security researchers believe that the malware might be targeting an encrypted form of the track data, suggesting that the actor is focused on a SoftCamp POS-related software application, framework, or device. The researchers believe “with high confidence” that the attacks are primarily targeting devices in South Korea.
Attribution
“Attribution is a controversial topic and arguably one of the most difficult tasks threat intelligence analysts face. However, based on our research, we assess with a high level of confidence given the information available to us that the operations and activity discussed in this research are attributed to Lazarus Group and ultimately North Korea,” Proofpoint says.
The security firm notes that the use of a specific implementation of the Spritz encryption cipher to encrypt PowerSpritz’ legitimate installer payload and malicious PowerShell commands is one clear indicator that this hacking group is behind the attacks. Furthermore, obfuscation techniques used in these campaigns overlap with those attributed to the Lazarus Group before.
The fact that PowerRatankba and RatankbaPOS include similar or identical features previously observed in the original Ratankba implants are another indicator of correct attribution, the researchers say. To that, the researchers add the use of a common directory for storing implants and logs, seen across the group’s toolset, as well as the initial POST request to C&C to deliver system information.
The researchers also discovered instances of code overlap between the RatankbaPOS dropper and the spreader implant used in the attack on the Far Eastern International Bank (FEIB) in Taiwan in October. The implants use the same directory and set up persistence in almost precisely the same way.
Additionally, Proofpoint discovered that content found in a PowerRatankba JS downloader decoy PDF file was previously used in Lazarus campaigns focused on espionage rather than for financial gain.
According to the security researchers, the detailed campaigns and tools belong to a financially motivated arm of the state actor, which should be differentiated from the espionage and disruption teams. The group is following the money, stealing directly from individuals and organizations instead of targeting financial institutions for espionage, as “traditional” threat actors do.
“This group now appears to be targeting individuals rather than just organizations: individuals are softer targets, often lacking resources and knowledge to defend themselves and providing new avenues of monetization for a state-sponsored threat actor’s toolkit,” Proofpoint concludes.
Nissan Canada Informs 1.1 Million Customers of Data Breach
22.12.2017 securityweek Incindent
Nissan Canada revealed on Thursday that the personal information of some customers may have been compromised as a result of a data breach discovered by the company on December 11.
The incident affects individuals who have financed their vehicles through Nissan Canada Finance (NCF) and INFINITI Financial Services Canada. The exact number of impacted customers has yet to be determined, but Nissan is notifying all 1.13 million current and past customers.
While the company believes not all customers are affected, it has decided to offer all of them free credit monitoring services through TransUnion for a period of 12 months. NCF is in the process of sending out emails and letters to individuals whose information may have been compromised.
The attacker could have stolen names, addresses, vehicle details, vehicle identification numbers (VINs), credit scores, loan amounts, and information on monthly payments. Nissan Canada says the incident does not appear to involve payment card information.
There is no indication that Nissan or Infiniti customers in Canada who did not obtain financing through NCF or customers outside of Canada are impacted.
The company is working with law enforcement and data security experts to investigate the incident and has not made any comments on who might be behind the attack. Canadian privacy regulators have also been informed of the breach.
This is not the first time Nissan has been targeted by hackers. Back in 2012, the company reported finding malware on its global information systems network. Last year, the company was forced to shut down its global websites due to a cyberattack apparently motivated by anger over Japan's controversial whale and dolphin hunts.
Schneider Electric Patches Flaws in Pelco Video Management System
22.12.2017 securityweek ICS
Schneider Electric recently developed a firmware update for its Pelco VideoXpert Enterprise product to address several vulnerabilities, including a high severity code execution flaw.
Pelco VideoXpert Enterprise is a video management system used in commercial facilities worldwide. Researcher Gjoko Krstic discovered that the product is affected by two directory traversal bugs and an improper access control issue that can allow arbitrary code execution.
The most serious of the flaws is CVE-2017-9966, which allows an attacker to replace certain files and execute malicious code with system privileges, Schneider Electric and ICS-CERT said in their advisories.Schneider fixes vulnerabilities in Pelco video management system

The directory traversal vulnerabilities are tracked as CVE-2017-9964 and CVE-2017-9965, and they have been classified as medium severity. The first security hole allows an attacker to bypass authentication or hijack sessions by “sniffing communications.”
The second directory traversal can be exploited by an unauthorized user to access web server files that could contain sensitive information.
These Pelco VideoXpert Enterprise vulnerabilities have been patched with the release of firmware version 2.1. All prior versions are affected.
This is the third round of Pelco product vulnerabilities covered in advisories published by ICS-CERT. The organization also released an advisory in June 2016 for a serious vulnerability in the Digital Sentry video management system, and in March 2015 for a high severity flaw in the DS-NVs software package.
Intelligence Committee Outlines UK's Offensive and Defensive Cyber Posture
22.12.2017 securityweek BigBrothers
The UK Intelligence and Security Committee, which has oversight of the UK intelligence community, published its 2016-2017 annual report (PDF) on Wednesday. With the rider that the report was written prior to April 2017, but delayed in publication, it provides insight into the UK perspective on global cyber threats. Its discussion includes commentary on nation state adversaries, the potential impact of the Trump administration on UKUSA, and the effect of Brexit on GCHQ operations.
The primary cyber threats are perceived to come from state actors, organized criminals and terrorist groups. State actors are the most advanced, with objectives including traditional espionage, commercial secrets and geopolitical instability. Organized crime occupies the next level of sophistication, becoming increasingly competent and targeted, and concentrating on financial gain. Terrorist groups have the intent to use cyber techniques, but are currently thought to lack the requisite capabilities (although this is likely to change).
There is additional threat from hacktivists and less competent criminals. Hacktivists are often politically motivated and primarily use DDoS for publicity or to inflict reputational damage. The entry level for less-skilled criminals is lowering, and financial gain is the main motivation.
The impact from cyber threats is primarily economic, although the reports notes, "increasingly there is a risk of physical damage in the 'real world'." This is magnified by the growing insecure internet of things (IoT) usage within the critical infrastructure. "Manufacturers," says the report, "are likely to side-line cyber security considerations, given their potential impact on time to market and, therefore, profits." The Committee urges the government to work with industry internationally "to promote the use of modern and secure operating systems in all smart devices connected to the internet."
The report describes the UK's new (since November 2016) National Cyber Security Strategy. It revolves around 'Defend' (which is typical cyber security mitigation); 'Deter' (which includes the specific warning, "We have the means to take offensive action in cyberspace, should we choose to do so"); and 'Develop' (based on "an innovative, growing cyber security industry").
GCHQ is tasked with implementing this policy; and it is leading to a change in GCHQ's traditional posture -- it is coming out of the shadows and promises to be more proactive in UK commercial cyber defense.
"We're spending too much time shouting at users and telling them they're too stupid to do the right thing frankly, and that hasn't worked and we need to get away from that," GCHQ told the Committee. The new approach has been called 'active cyber defense', and "includes GCHQ assisting private companies in developing automated technological solutions to operate on the underlying internet infrastructure that would prevent a large proportion of cyber attacks from ever reaching end-users."
Part of this process can be seen in the National Cyber Security Center (NCSC) which is both GCHQ (still covert) and partly an advice center backed by the skills and knowledge of GCHQ. It's aim, says GCHQ, is "to fuse powerful covert capabilities, accesses, data and skills to help provide cyber defense at scale to the UK."
The Committee asked whether GCHQ should have legal cyber security enforcement powers. GCHQ welcomes the tendency for existing regulatory organizations (such as the Bank of England and the Office of the Nuclear Regulator) to consult with and take advice from the organization; but it is not a supporter of general 'cyber regulatory legislation'. While it is a political decision, it says it is hard to do, difficult to keep up with technology, and problematic across different industry sectors.
The UK has a well-established offensive cyber capability program. GCHQ's ultimate position on the use of offensive capabilities is clear: "International law applies to state acts in cyberspace in the same way as anywhere else." If international law allows a response to kinetic activity, it will allow a response to cyber activity. The committee says that GCHQ's offensive capabilities are "an effective deterrent".
The problem remains 'attribution'. "Further work will be required to develop a better international consensus on the rules of engagement for offensive cyber. GCHQ told us that it supported this concept in principle, but held some concerns, for example about others' adherence to such agreements."
The report highlights four specific cyber adversary states: Russia, China, Iran and North Korea. Russia is the primary concern. "It is possible that Russia is ostentatiously flexing its muscles towards the West under a deliberately thin blanket of deniability, or these may simply be providing a useful public cover for the Russian agencies' practice runs," suggests the report.
The intelligence community is more forthright. "The [Russian] risk appetite is quite different and they are quite prepared to use the world as a range, [saying] 'we will give it a go and see what happens', said Defense Intelligence. "They clearly are operating to risk thresholds which are nothing like those that the West operates," said MI5. Despite this increasing level of mistrust between Russia and the West, the Committee urges "that limited lines of communication should be maintained, although a delicate balance is needed."
China remains a serious cyber threat, attempting to steal data for economic purposes and to acquire classified government and military data. GCHQ notes that since the UK and the U.S. both signed cyber security accords with China (where all sides agreed not to engage in commercial cyber espionage), China is taking more care to disguise attribution.
Iran gets relatively little coverage in the report. "Iranian motivations against the UK are more obscure than those of Russia and China. GCHQ has suggested that Iran is primarily attempting a show of strength."
North Korea is different. Its 'recklessness and unpredictability' is difficult to defend against. "It is prepared to use its capabilities without any concern for attribution, and for ideological motives which are alien to other countries," warns the report.
In international cyber relations, the report unsurprisingly highlights the Five Eyes (the UK, USA, Canada, Australia and New Zealand) as "the closest international intelligence partnership in the world." Bearing in mind that much of the report was compiled either before or during the first few months of the Trump administration, it is interesting to see the extent of UK concern -- even to the extent that it could upset Five Eyes relationships.
"Any significant change in US policies relating to detainee treatment," states the Committee, "would pose very serious questions for the UK-USA intelligence relationship. The US agencies are well aware of the implications for cooperation with the UK and other allies, and the UK Agencies are monitoring the situation closely." In fairness, neither the Committee nor the intelligence community expected this to happen.
Brexit is also a concern for international intelligence relations. While Brexit cannot affect the Five Eyes (none of which, after Brexit, will be part of the European Union), nevertheless is will affect the UK. The Director General of MI5 told the Committee that there were two sides to the problem. National security falls outside of the Lisbon Treaty (the basis of the European Union), and the UK expects to continue working with European intelligence agencies.
What's driving this, he said, is that "Half of Europe is scared of terrorism and the other half is scared of Russia and both halves want us to help them... So that will not change with Brexit because Article 4.2 [of the Lisbon Treaty] had all of that outside scope anyway." But he added that other parts of cyber relations do fall within Lisbon scope, "in areas like data sharing, what happens with borders... what happens with law enforcement cooperation..." All of this is far from decided yet.
GCHQ is more relaxed. Its European partnerships are bilateral, and not connected with any European institutions; "So there is no reason why it would be affected by Brexit." GCHQ is, however, concerned about data sharing and trade with Europe. "The big companies, will need to be able to share data in a way that is legally compliant on... both sides, the UK and the EU. That's a policy issue way beyond intelligence, actually, but it will have big implications for us, so getting that right is important."
Asked for a formal assessment of the effect of Brexit on their operations, both GCHQ and MI5 referred the Committee to the Cabinet Office, saying it was a political matter. The Cabinet Office then declined to respond; and the report registers the Committee's disapproval. "The decision to leave the EU clearly has direct and indirect implications for the work of the Agencies -- and these are well within this Committee's remit."
Much of the report is necessarily concerned with budgets (usually redacted), staffing and premises. However, wherever cyber security, both offensive and defensive, is discussed, the report provides a bullish picture of improving UK capabilities.