
24 hours later, Apple fixes the bug in macOS High Sierra that allowed Root access with no password
1.12.2017 securityaffairs Apple
Just 24 hours later, Apple issued a security update for macOS High Sierra that addresses the bug that allowed Root access with no password
Yesterday I published a post on an embarrassing flaw affecting the macOS High Sierra, tracked as CVE-2017-13872, that that can be exploited to gain root access to a machine with no password.
The vulnerability is exploitable via the authentication dialog box in the Apple macOS High Sierra that asks for an administrator’s username and password when the user needs to do specific actions like configure privacy and network settings.
From the user login screen, if the user provides “root” as the username, leave the password box blank, hit “enter” and then click on unlock a few times, the prompt disappears and he gains admin rights.

D̒͂̕ă̋n̕ Ť̨̖̾̾̓͐͒͜͠ͅe̘͗̑́̋̂́͡ͅn̅̀̀͞t̾l̀̓̐͘e̓̒̂̚r
✔
@Viss
2:28 AM - Nov 29, 2017
41 41 Replies 361 361 Retweets 756 756 likes
Twitter Ads info and privacy
Initial reports suggested that the exploit works by entering the username “root” with a blank password, but the expert Tom Ervin discovered that it works with any password.
Tom Ervin
@techbytom
Everyone. Please, the MacOS “blank root password” vulnerability has nothing to do with a blank password. The first time someone tries to log in as root, whatever password they try becomes the password for root. DO NOT test with a blank password. SET A STRONG ROOT PASSWORD NOW.
10:32 AM - Nov 29, 2017
Replies 3 3 Retweets 5 5 likes
Twitter Ads info and privacy
The attack scenario needs physical access to the machine to log in, once inside the attacker can perform several malicious activities such as install a malware.
Even if the flaw was first reported on Apple developer forums on November 13 by a user, Apple only learned of it on Tuesday when the web developed Lemi Orhan Ergin tweeted about it.
Lemi Orhan Ergin
@lemiorhan
Dear @AppleSupport, we noticed a *HUGE* security issue at MacOS High Sierra. Anyone can login as "root" with empty password after clicking on login button several times. Are you aware of it @Apple?
7:38 PM - Nov 28, 2017
1,166 1,166 Replies 12,927 12,927 Retweets 15,519 15,519 likes
Twitter Ads info and privacy
The flaw affects macOS High Sierra 10.13 and macOS High Sierra 10.13.1, it doesn’t impact macOS Sierra 10.12.6 and earlier.

Just 24 hours later, Apple announced the availability of a security update for macOS High Sierra that addresses the issue.
“An attacker may be able to bypass administrator authentication without supplying the administrator’s password,” the company said in its advisory.
“A logic error existed in the validation of credentials. This was addressed with improved credential validation.”
Experts noticed that If they have a root account enabled and a password for it set, the trick will not work, for this reason Apple has deactivated the root account by default.
Police vs Privacy: US Supreme Court Looks at Cell Phone Tracking
1.12.2017 securityweek Mobil
Where do we go? Who do we talk to? What do we read about?
Our mobile phones are troves of personal, private information, and the US Supreme Court weighed Wednesday how easily police should be able to get it.
In a case seen as a landmark for privacy protection in the digital age, the court heard arguments over whether, police have the right to obtain the location data of a person's phone from providers without a search warrant.
During the hearing, most of the high court's nine justices appeared deeply concerned about how phone companies can track a person's movements via their device and hand that information, sometimes going back years, to police when asked.
Civil libertarians say that information is protected by the US Constitution.
But law enforcement officials say the location data transmitted from a phone to a cell tower has been essentially made public and handed over to a third party, giving up any claim the owner might have to privacy.
The specific case involves Timothy Carpenter, who was tracked down and convicted of theft in 2011 after the police obtained some 12,898 cell tower location points for Carpenter's device over four months from phone companies.
Justice Sonia Sotomayor appeared to agree with the pro-privacy advocates.
The cell phone "is an appendage now for some people," she noted.
"Right now we're only talking about the cell site records, but as I understand it, a cell phone can be pinged in your bedroom. It can be pinged at your doctor's office. It can ping you in the most intimate details of your life -- presumably at some point even in a dressing room as you're undressing."
- Constitutional test case -
The US Constitution's Fourth Amendment guarantees the privacy of citizens from "unreasonable searches and seizures," and says police must obtain warrants based on "probable cause" if they want to search a suspect's "persons, houses, papers, and effects."
Parties on both sides of the case agree that the law did not anticipate an era in which everyone relies on a cell phone and technology providers can amass data on a person via those phones.
Nathan Wessler, an attorney with the American Civil Liberties Union representing Carpenter, said the police collection of the phone location data constituted a "search" that required a warrant.
"The concern here is with the privacy invasion, which is quite severe over the long term, over these more than four months of data," he told the court.
But the government argues that the location data is not like tapping a phone conversation, which is illegal without a warrant.
"We're dealing here with routing information. We're not dealing with the contents of communications," argued Michael Dreeben, deputy solicitor general for the Department of Justice.
He argued that giving up the information is a voluntary act by the cell phone user, and so it is not protected.
"There is an element here of voluntariness in deciding to contract with a cell company, just like there's an element of voluntariness in getting a landline phone and making a call," Dreeben told the court.
- Implications for private data -
The case has much broader implications than cell phone location data, experts say.
Today, a huge amount of information from people's lives is held by "third parties": personal files stored in the internet cloud, information from home electronics collected by the makers of those appliances, and communications sent via cell phones and the internet.
"The advance of technology means that information you used to store in your desk drawer is now stored somewhere with third parties," said Greg Nojeim of the Center for Democracy & Technology.
To get information in a drawer, he noted, police would have to ask the court for a warrant.
The Supreme Court will likely make a decision on the case before the end of its current term in June 2018.
Patch of Dirty COW Vulnerability Incomplete, Researchers Claim
1.12.2017 securityweek Vulnerebility
The “Dirty COW” vulnerability (CVE-2016–5195) discovered last year in Linux was incompletely patched, Bindecy researchers say.
The vulnerability was found to be caused by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings. Discovered by Phil Oester, the bug could allow an unprivileged local attacker to escalate their privileges on a targeted system.
The vulnerability was found to impact Android as well, and could even escape containers. Soon after Google released a patch for the vulnerability, however, new attacks exploiting Dirty COW on Android were devised.
The most recent malware family to exploit the issue was observed in September of this year.
Although Dirty COW was one of the most hyped and branded vulnerabilities published, with every Linux version from the last decade affected, including Android, being vulnerable, the patch released for it stirred far little interest, Bindecy says. Because of that, over a year has passed since the patch was released, and no one noticed it was incomplete.
The original vulnerability impacted the get_user_pages function, which is used to get the physical pages behind virtual addresses in user processes. Basically, the bug would allow writing to the read-only privileged version of a page.
The fix for the vulnerability doesn’t reduce the requested permissions. Instead, “get_user_pages now remembers the fact the we went through a COW cycle,” the researchers explain.
Thus, on the next iteration, a read-only page is provided for a write operation only if FOLL_FORCE and FOLL_COW flags are specified, and the PTE is marked as dirty.
The problem, the security researchers say, is that the patch “assumes that the read-only privileged copy of a page will never have a PTE pointing to it with the dirty bit on.”
Bindecy discovered that the vulnerability can still be reproduced when Transparent Huge Pages (THP) and Page Medium Directory (PMD – one level above the PTE level), are involved.
While Linux usually uses 4096-bytes long pages, THPs can be even 2MB long, although they can be split into normal pages. Usually, the default THP support is for anonymous mapping only, but can be turned on or off while the system is running.
THP is implemented by turning on the _PAGE_PSE bit of the PMD, which results in PMD pointing to a 2MB physical page instead of a directory of PTEs.
What the researchers discovered was that Dirty COW patch code that deals with THP contains a function called can_follow_write_pmd that basically applies the same logic of can_follow_write_pte to huge PMDs.
According to the researchers, however, the issue is that, when it comes to huge PMD, “a page can be marked dirty without going through a COW cycle, using the touch_pmd function.” Each time get_user_pages tries to get a huge page, a called function results in the page being marked dirty without going through a COW cycle. Thus, can_follow_write_pmd’s logic is broken, the researchers say.
“At this point, exploiting the bug is straightforward — we can use a similar pattern of the original Dirty COW race. This time, after we get rid of the copied version of the page, we have to fault the original page twice — first to make it present, and then to turn on the dirty bit,” Bindecy notes.
The security researchers revealed information on a couple of exploit scenarios and also published a proof-of-concept to demonstrate the exploit. They reported the vulnerability (which was assigned CVE-2017–1000405) to the kernel and distros mailing lists last week and a patch was already committed to mainline kernel.
“This bug demonstrates the importance of patch auditing in the security development life-cycle. As the Dirty COW case and other past cases show, even hyped vulnerabilities may get incomplete patches. The situation is not reserved for closed source software only; open source software suffers just as much,” the researchers conclude.
Trust Your Security Vendor, 'They Have Access to Everything You Do,' Says F-Secure Research Chief
30.11.2017 securityweek IT
The DHS ban on government agencies using Kaspersky Lab's security products has reverberated around the security industry. The concern is not simply whether the Moscow-based security firm has colluded with Russian intelligence, but how many other security firms could, through their own products, potentially collude with their own national intelligence agencies.
This is bad news for security since security is built on trust; and without trust there is no security. Kaspersky Lab has denied any collusion and has offered to do anything possible, from testifying before Congress to third-party code reviews, to prove its innocence. At the same time, there is no actual proof of collusion; just a statement that the possibility is a cause for concern.
On Tuesday, at a media briefing in London, Eugene Kaspersky said he had never been asked by Russia to spy on its behalf. "If the Russian government comes to me and asks me to (do) anything wrong, or my employees, I will move the business out of Russia. We never helped the espionage agencies, the Russians or any other nation."
The DHS statement bans government agencies from using Kaspersky Lab products, saying, "The risk that the Russian government, whether acting on its own or in collaboration with Kaspersky, could capitalize on access provided by Kaspersky products to compromise federal information and information systems directly implicates U.S. national security."
Herein lies the problem. Before developing anti-virus software and forming Kaspersky Lab, Eugene Kaspersky studied cryptology at a KGB and defense-funded school, and later worked at Russia's Ministry of Defense as a cryptologist. So the link -- and therefore the risk -- exists. At the same time, however, any glance through LinkedIn's staff profiles for U.S. security firms will return a large number of senior employees with an NSA, CIA, FBI or State Department background, with many U.S. security firms boasting about their former government and military hires. Connections alone do not necessarily imply collusion.
The Wall Street Journal (WSJ) separately published an unsubstantiated claim that an NSA employee had been breached by Russian state-backed hackers via a vulnerability in a Kaspersky Lab product; and that they targeted the employee "after identifying the files through the contractor's use of" Kaspersky Lab AV. No proof of this is provided, but the implication is that Kaspersky Lab did not pass confidential files directly to Russian intelligence, but merely informed them of their presence on the employee's computer.
However, if the Kaspersky-Russian intelligence link is a concern, then by implication users should consider the potential for a McAfee and Symantec link with the NSA, and a Sophos link with GCHQ. In an attempt to counter any potentially growing lack of trust in security products in general, F-Secure's Chief Research Officer, Mikko Hypponen, has talked today about how his own company handles confidential user information.
There are two riders to his comments. First of all, F-Secure is a competitor to Kaspersky Lab; and secondly, F-Secure is not Kaspersky Lab. Nevertheless, insights into how one major anti-virus firm operates will inevitably provide some insights into how any other major AV firm operates.
Hypponen avoids or obfuscates his response to any direct question of possible Kaspersky Lab collusion with Russia. For example, he says, "Let's just state for the record that it's a great company and a great security product. These are world class researchers."
Asked later if he thought Kaspersky Lab "colluded with Russian intelligence, do you think they were breached, hacked, infiltrated?", he replied, "I don't know. It's all speculation, as are all the stories on this. So far everything's been speculation." He notes, however, that links with law enforcement are commonplace. Law enforcement agencies (LEAs) frequently ask security firms for assistance in the fight against cybercrime, and researchers commonly pass back data on discovered C&C servers.
He does, however, explain how F-Secure treats information about user files. First of all, almost all security firms collect this data -- it's simply how they work. The amount of data that needs to be analyzed to keep users safe simply cannot bedone on a local machine without reducing its operation to a crawl. Anti-virus and network anomaly products tend to collect data and send it to cloud servers for analysis by powerful machine-learning algorithms.
But F-Secure, and most likely all other security vendors, go to great lengths to anonymize and protect the information they collect. First of all, this is good practice; but secondly, privacy regulations in many jurisdictions could cause serious complications. GDPR, for example, requires that only necessary data be collected; and personal data is not necessary for the analysis of executable files.
The files that are collected are analyzed for any indication of malware. If they are found to be benevolent, they are deleted. This resonates with Kaspersky Lab's comments following the WSJ report. Its software found the NSA files on the employee's computer, did not recognize them as good files and uploaded them for further analysis. Here they were analyzed and determined to be 'sensitive' -- at which point they were deleted.
Unfortunately, this cannot disprove the possibility that someone in Kaspersky Lab then sent a quiet word to Russian intelligence saying, 'Hey guys, you might want to take a close look at this guy's computer.' But for that to have happened, Kaspersky Lab will have had to collect personal data as well as anonymized files.
Hypponen cannot say that Kaspersky Lab didn't do it; but he makes his opinion clear. He does, however, agree with the DHS. "Would I recommend using a foreign security product in US agencies, especially a Russian product? Probably I wouldn't. But for home users and users like that, it is a great product."
In the end, it's a question of who do you trust the most: your own government or a security firm that can only exist through trust?
"Choose your vendors carefully, because, in theory, they have access to everything you do," Hypponen said, adding that "when you are running low level software, like security software, you do have to trust your vendor."
But he clearly does not personally believe that Kaspersky Lab is guilty of any malicious behavior. "Why? Because that would be so short-sighted. If you do that and you get caught, your company is toast, and it should be toast. That's a bad business decision. If it's the Russian government using a local security company as their way of gaining access to information, that's short-sighted too. Because Kaspersky Lab is the biggest software success story out of Russia since Tetris."
Should Social Media be Considered Part of Critical Infrastructure?
30.11.2017 securityweek BigBrothers
Social Media Networks
Is Social Media a Critical Industry?
Russia interfered in the U.S. 2016 election, but did not materially affect it. That is the public belief of the U.S. intelligence community. It is a serious accusation and has prompted calls for additions to the official 16 critical infrastructure categories. One idea is that 'national elections' should be included. A second, less obviously, is that social media should be categorized as a critical industry.
The reason for the latter is relatively simple: social media as a communications platform is being widely used by adversary organizations and nations to disseminate their own propaganda. This ranges from ISIS using it as a recruitment platform, to armies of Russian state-sponsored trolls manipulating public opinion via Twitter.
Russian interference, or opinion manipulation, has not been limited to the U.S. Both France and Germany worried about it prior to their own national elections. On Nov. 3, this year, Damian Collins, Chair of the Digital Culture and Sport Select Committee in the UK wrote to Twitter's Jack Dorsey asking for information on the so-called Russian Internet Research Agency. He asked for a list of Russian accounts and posts linked to politics in the UK. Brexit is not mentioned, but interference in the UK Brexit referendum is clearly the concern.
One week later, CNN Money reported, "A network of Twitter accounts with ties to the Russian government-linked troll army that meddled in U.S. politics posted dozens of pro-Brexit messages on the day of the referendum on the United Kingdom's membership of the European Union in June 2016."
The assumed purpose of Russian interference in politics has been to promote extreme right-wing national populist movements that would weaken centrist governments. This is clearly an 'attack' against western nations, delivered primarily via social networks. It is noticeable that in both the US election and the Brexit referendum there was a late and in many ways unexpected shift to the right.
Nevertheless, the idea of social media as a critical industry is a difficult concept. Malcolm Harkins, chief security and trust officer at Cylance, doesn't think it is a great stretch. He points to the origins of the existing 16 industry sectors and notes that the primary motivation is to maintain their availability following the 9/11 attack.
The DHS introduces its definition of the critical infrastructure with, "There are 16 critical infrastructure sectors whose assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof." These include 'energy', 'finance', 'transport', 'communications' and 'IT'. Maintaining the availability and continued operation of all of these sectors is clearly critical to the well-being of the nation. Maintaining the availability of social media does not seem so critical.
Harkins' argument, however, is that the world has changed since the origins of the critical infrastructure classification.
Business and society have gone through, and are still going through, a dramatic 'digitization' of their operations. The internet and all things cyber have become fundamental to the operation of the economy and society.
"Where cyber is concerned," Harkins told SecurityWeek, "the 'A' of 'CIA' is not enough. The Availability of the critical infrastructure must now be bolstered by the Integrity of the critical infrastructure."
This should not be considered a trivial concern. The manipulation of information has always been a part of warfare, usually as a precursor to a kinetic attack.
"There has always been the notion of information manipulation in warfare -- such as deception," says Harkins. "If you can manipulate your enemy prior to a kinetic event, then you would have advantage over them."
Alexander's victory over Porus in 326 BC through the Allied landings in Normandy in 1944, to Stormin Norman's Desert Storm in 1991 have all relied heavily on feeding the enemy misinformation.
"The world today," he continued, "is based on information with headlong digitization of both business and society. With everything now based on our reaction to and use of information, the integrity of that information has never been more vital."
The availability of the Communications and IT sectors is already considered critical, and social media is the most important and widespread platform that unites the communications and IT sectors. If the concept of the critical infrastructure is widened from availability to include integrity, then social media is already, de facto, part of the critical infrastructure. "At what point," asks Harkins, "does the integrity of the information flowing through the IT sector or the communications sector hit a significant and material risk that will force us to consider it critical?"
How this could work in practice is a different matter, for it couldn't be limited to integrity in social media platforms. Facebook is not the only advertising medium that could run propagandist advertising (some 3,000 Russia-linked advertisements were placed on Facebook in 2016 apparently designed to influence the presidential election). "My guess is that even well beyond social media, mainstream physical advertising has been bought and used for the purpose of manipulating national sentiment." If social media can be considered 'critical', then the whole concept of Fake News must be treated in the same way.
That would be a major task. Social media is perhaps the most pressing aspect of this, and could even prove a testbed for wider communications controls. ìI think the case increasingly can, and will be made that social media is a part of critical infrastructure in that Twitter, Facebook and other media channels have become the 'go-to' resources for a large percentage of Americans," comments Dan Lohrmann, CSO at Security Mentor. "Yes - social media is slowly becoming a critical part of critical infrastructure for our nation and other developed countries."
But Nathan Wenzler, chief security strategist at AsTech, is not sure we are ready for this. He takes the 'availability' view of critical infrastructure. "Even with the potential influence of the last U.S. presidential election, I do not believe we should be looking at these social media services in the same way we view power, water, and other utility services which are required for people's daily lives," he told SecurityWeek. "If social media services were disrupted... there would be some outrage by the users, but by and large, their lives would not be dramatically impacted from a health or well-being standpoint. For this reason alone, I don't see that we're quite at the point of considering social media to be the same as these other critical services."
He believes things may change in the future, but raises two of the many practical problems that will arise: accountability for users and attribution for attackers. Chris Roberts, chief security architect at Acalvio, takes a similar view. "We have little ability or success in being able to protect that which is already classified as critical infrastructure. The red tape is worn thin with excuses: the technology is not in place to deal with both 20 year old systems and modern insecure devices interconnected through a cloud-like pea-soup fog," he said.
"If you want to consider the core systems as critical infrastructure, then you have to be able to manage, control and understand the access permissions, uniquely identify individuals and put some controls into access and other areas. That both seems like a tall challenge (getting 300M Americans to agree to security controls for their social media) and also something that might eventually break the constitutional rights of those folks to actually speak freely. If you put controls in place, where does that end?"
But if Harkins is right and the concept of integrity will need to be added to the concept of availability for the critical infrastructure, then something will have to change. There are signs that governments are beginning to feel threatened and therefore concerned. The UK government has been particularly vociferous over the last year, telling the social tech giants that if they don't get their house in order, government will do it for them.
Indeed, the current government's manifesto (a pre-election statement of intent) contains a strong purpose to control social media. "Some people say that it is not for government to regulate when it comes to technology and the internet," it says. "We disagree... it is for government, not private companies, to protect the security of people and ensure the fairness of the rules by which people and businesses abide."
The clear implication is that the tech giants' protestations of: 'don't limit freedom of speech', 'legislation will stifle innovation', and 'it's not technologically possible' will not be accepted. Even U.S. lawmakers seem to be moving in a similar direction. On Tuesday, Nov. 21, counsels for Google, Facebook and Twitter were in Washington answering questions put at the Senate hearing on social media's role in the 2016 election.
At one point, Senator John Kennedy (R-LA) said, "I don't believe you have the ability to identify all your advertisers." The tech companies effectively admitted this -- although the reality is probably they cannot control advertising without losing some of it. But if government wishes to prevent foreign entities interfering in future elections, this quality of knowledge is essential. Social media should take note that there is precedent; government has enforced advertising control on new technology in the past. In the 1930s, new radio services carried misinformation and propaganda in the form of advertisements. The government cracked down on this with the 1934 Communications Act, placing greater responsibility on the medium to choose which advertisements it accepted. It could do similar with social media.
The likelihood of some legislative control over social media is growing. In the U.S. the primary concern seems to be its potential for foreign propaganda aimed at controlling national sentiment.
In the UK the primary concern is its use by terrorist groups and organized crime -- although there is now some concern that Russia may have attempted to influence the Brexit referendum.
If Harkins is right, then this is really the visible effect of an underlying need to add integrity to the availability of the critical infrastructure. And if that is correct, then the legislation will need to apply to the whole communications sector and not just the social media aspect. But it goes further. If the need to apply integrity has grown through the digitization of industry, then the implication is that it will require confidentiality as well as integrity and availability if its security is to be assured. Confidentiality is best applied through encryption; and we are seeing increasing interest by government in controlling encryption. That, however, is a different battle; and both would benefit from a national debate.
AWS Launches New Cybersecurity Services
30.11.2017 securityweek Cyber
Amazon Web Services (AWS) announced this week at its AWS re:Invent conference the launch of several new cybersecurity services, including for threat detection, IoT security, and secure communications for Virtual Private Cloud.
Amazon GuardDuty
One of the new products is Amazon GuardDuty, an intelligent threat detection service that helps customers protect their AWS accounts and workloads by continuously looking for unauthorized and malicious activity.
Amazon GuardDuty, which can be enabled from the AWS Management Console, creates a baseline for normal account activity, and uses machine learning to identify any irregular behavior. If suspicious activity is detected, the AWS account owner is immediately notified.
The new service obtains threat intelligence from both AWS itself and third-party sources such as CrowdStrike and Proofpoint, it does not require any new hardware or software, and it can be integrated with products from Alert Logic, Evident.io, Palo Alto Networks, RedLock, Rapid7, Sumo Logic, Splunk and Trend Micro.
The list of organizations already using GuardDuty includes Autodesk, Netflix, Mapbox, GE, and the Financial Industry Regulatory Authority (FINRA).
AWS PrivateLink
Another new product launched this week is AWS PrivateLink, a managed service that allows developers to securely access third-party SaaS applications from their Virtual Private Cloud (VPC).AWS launches new security services
A majority of Amazon EC2 cloud instances run in VPCs these days, but using third-party SaaS applications can introduce security risks. With AWS PrivateLink, AWS allows users to initiate connections to third parties without exposing their VPC to the Internet, or connect their internal services across different VPCs and accounts.
The list of SaaS applications that support AWS PrivateLink can be found on the AWS Marketplace. Companies such as CA Technologies, Aqua Security, Dynatrace, Cisco and SigOpt have announced that they support PrivateLink.

AWS also announced the launch of several new services designed for managing, protecting and monitoring Internet of Things (IoT) devices. These are AWS IoT 1-Click, IoT Device Management, IoT Device Defender, IoT Analytics, Amazon FreeRTOS, and Greengrass ML Inference.
Three of the new IoT services help improve security. AWS IoT Device Management, which is available immediately, allows organizations to securely onboard, manage and monitor IoT devices, including to apply patches and software updates.
AWS IoT Device Defender, expected to become available in the first half of 2018, monitors devices for any suspicious activity, such as traffic going to an unknown IP, and ensures that IoT systems are compliant with security policies.
Amazon FreeRTOS allows users to securely connect small, low-power devices that use the FreeRTOS operating system (e.g. light bulbs, motion sensors) to AWS cloud services. The list of microcontroller manufacturers that support Amazon FreeRTOS includes Microchip, NXP Semiconductors, STMicroelectronics, Texas Instruments, Arm, IAR, Percepio, and WITTENSTEIN.
Cisco Patches Critical WebEx Vulnerabilities
30.11.2017 securityweek Vulnerebility
Updates released by Cisco for components of its online meetings and video conferencing platform WebEx patch nearly a dozen vulnerabilities, including critical flaws that can be exploited for remote code execution.
A total of six vulnerabilities affecting the WebEx Network Recording Player for Advanced Recording Format (ARF) and WebEx Recording Format (WRF) files have been classified as critical.
The impacted player is used to play back recorded WebEx meetings and it can be installed automatically when a recording file hosted on a WebEx server is opened.
The security holes affecting the Network Recording Player can be exploited by a remote attacker to cause a denial-of-service (DoS) condition in the software and possibly execute arbitrary code by getting the targeted user to open specially crafted ARF or WRF files. Cisco noted that the attacker can send the malicious files to victims via email or get them to open a web page hosting the files.
The vulnerabilities have been patched by Cisco in WebEx Business Suite meeting sites, WebEx Meetings sites, WebEx Meetings Server, and WebEx ARF and WRF Players. Cisco’s advisory provides detailed information on affected versions and the availability of fixes. The following CVE identifiers have been assigned: CVE-2017-12367, CVE-2017-12368, CVE-2017-12369, CVE-2017-12370, CVE-2017-12371 and CVE-2017-12372.
The flaws were reported to Cisco by Andrea Micalizzi (rgod) and Steven Seeley of Offensive Security via Trend Micro’s Zero Day Initiative (ZDI), Fortinet’s Kushal Arvind Shah, and Qihoo 360 researcher Yihan Lian. ZDI has yet to make the advisories for the flaws found by Seeley and Micalizzi public.
Cisco found no evidence that the vulnerabilities had been exploited in malicious attacks.
Lian also discovered a medium severity DoS vulnerability in the WebEx Network Recording Player. A remote attacker can cause the player to crash by getting the targeted user to open a malicious WRF file.
The networking giant published four other advisories detailing WebEx vulnerabilities on Wednesday. These weaknesses have also been rated “medium severity” and they include cross-site scripting (XSS) and URL redirection vulnerabilities in WebEx Meeting Center, an information disclosure bug in Event Center, and a flaw that can be exploited to modify the welcome message in Meeting Server.
Cryptocurrency Mining Scripts Now Run Even After You Close Your Browser
30.11.2017 thehackernews Security 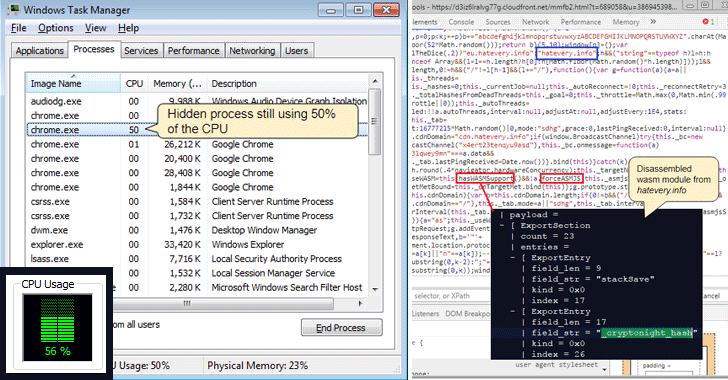
Some websites have found using a simple yet effective technique to keep their cryptocurrency mining javascript secretly running in the background even when you close your web browser.
Due to the recent surge in cryptocurrency prices, hackers and even legitimate website administrators are increasingly using JavaScript-based cryptocurrency miners to monetize by levying the CPU power of their visitor's PC to mine Bitcoin or other cryptocurrencies.
After the world's most popular torrent download website, The Pirate Bay, caught secretly using Coinhive, a browser-based cryptocurrency miner service, on its site last month, thousands of other websites also started using the service as an alternative monetization model to banner ads.
However, websites using such crypto-miner services can mine cryptocurrencies as long as you're on their site. Once you close the browser window, they lost access to your processor and associated resources, which eventually stops mining.
Unfortunately, this is not the case anymore.
Security researchers from anti-malware provider Malwarebytes have found that some websites have discovered a clever trick to keep their cryptocurrency mining software running in the background even when you have closed the offending browser window.
How Does This Browser Technique Work?
According to a blog post published Wednesday morning by Malwarebytes, the new technique works by opening a hidden pop-under browser window that fits behind the taskbar and hides behind the clock on your Microsoft's Windows computer.
From there (hidden from your view), the website runs the crypto-miner code that indefinitely generates cryptocurrency for the person controlling the site while eating up CPU cycles and power from your computer until and unless you notice the window and close it.
Researchers say this technique is a lot harder to identify and able to bypass most ad-blockers because of how cleverly it hides itself. The crypto-miner runs from a crypto-mining engine hosted by Amazon Web Servers.
"This type of pop-under is designed to bypass adblockers and is a lot harder to identify because of how cleverly it hides itself," Jérôme Segura, Malwarebytes' Lead Malware Intelligence Analyst, says in the post. "Closing the browser using the "X" is no longer sufficient."
To keep itself unidentified, the code running in the hidden browser always takes care of the maximum CPU usage and maintains threshold to a medium level.
You can also have a look at the animated GIF image that shows how this clever trick works.
This technique works on the latest version of Google's Chrome web browser running on the most recent versions of Microsoft's Windows 7 and Windows 10.
How to Block Hidden Cryptocurrency Miners
If you suspect your computer CPU is running a little harder than usual, just look for any browser windows in the taskbar. If you find any browser icon there, your computer is running a crypto-miner. Now simply, kill it.
More technical users can run Task Manager on their computer to ensure there is no remnant running browser processes and terminate them.
Since web browsers themselves currently are not blocking cryptocurrency miners neither does the integrated Windows Defender antivirus software, you can use antivirus programs that automatically block cryptocurrency miners on web pages you visit.
For this, you can contact your antivirus provider to check if they do.
Alternatively, you can make use of web browser extensions, like No Coin, that automatically block in-browser cryptocurrency miners for you, and regularly update themselves with new mining scripts that come out.
Created by developer Rafael Keramidas, No Coin is an open source extension that blocks Coin Hive and other similar cryptocurrency miners and is available for Google Chrome, Mozilla Firefox, and Opera.
No Coin currently does not support Microsoft Edge, Apple Safari, and Internet Explorer. So, those using one of these browsers can use an antimalware program that blocks cryptocurrency miners.
Hackers Exploit Recently Disclosed Microsoft Office Bug to Backdoor PCs
30.11.2017 thehackernews Exploit
A recently disclosed severe 17-year-old vulnerability in Microsoft Office that lets hackers install malware on targeted computers without user interaction is now being exploited in the wild to distribute a backdoor malware.
First spotted by researchers at security firm Fortinet, the malware has been dubbed Cobalt because it uses a component from a powerful and legitimate penetration testing tool, called Cobalt Strike.
Cobalt Strike is a form of software developed for Red Team Operations and Adversary Simulations for accessing covert channels of a system.
The vulnerability (CVE-2017-11882) that Cobalt malware utilizes to deliver the backdoor is a memory-corruption issue that allows unauthenticated, remote attackers to execute malicious code on the targeted system when opened a malicious file and potentially take full control over it.
This vulnerability impacts all versions of Microsoft Office and Windows operating system, though Microsoft has already released a patch update to address the issue. You can read more details and impact of the vulnerability in our previous article.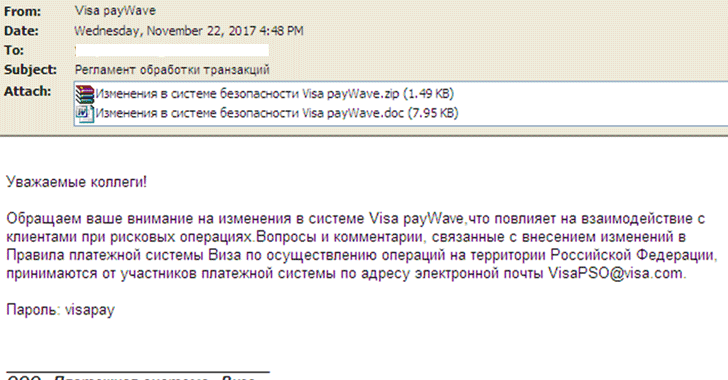
Since cybercriminals are quite quick in taking advantage of newly disclosed vulnerabilities, the threat actors started delivering Cobalt malware using the CVE-2017-11882 exploit via spam just a few days after its disclosure.
According to Fortinet researchers, the Cobalt malware is delivered through spam emails, which disguised as a notification from Visa regarding rule changes in Russia, with an attachment that includes a malicious RTF document, as shown.
The email also contains a password-protected archive with login credentials provided in the email to unlock it in order to trick victims into believing that the email came from the legitimate financial service.
"This is [also] to prevent auto-analysis systems from extracting the malicious files for sandboxing and detection," Fortinet researchers Jasper Manual and Joie Salvio wrote.
"Since a copy of the malicious document is out in the open... so it's possible that this is only to trick the user into thinking that securities are in place, which is something one would expect in an email from a widely used financial service."
Once the document is opened, the user has displayed a plain document with the words "Enable Editing." However, a PowerShell script silently executes in the background, which eventually downloads a Cobalt Strike client to take control of the victim's machine.
With control of the victim's system, hackers can "initiate lateral movement procedures in the network by executing a wide array of commands," the researchers said.
According to the researchers, cybercriminals are always in look for such vulnerabilities to exploit them for their malware campaigns, and due to ignoring software updates, a significant number of users out there left their systems unpatched, making them vulnerable to such attacks.
The best way to protect your computer against the Cobalt malware attack is to download the patch for the CVE-2017-11882 vulnerability and update your systems immediately.
The Shipping Giant Clarkson has suffered a security breach
30.11.2017 securityaffairs Incindent
Clarkson, one of the world’s largest providers of shipping services publicly disclosed a security breach.
Clarkson confirmed the hackers may release some of the stolen data, it hasn’t provided further details due to the ongoing law enforcement investigation.
The information disclosed by the company suggests cyber criminals blackmailed the company requesting the payment of a ransom in order to avoid having its data leaked online.
According to Clarkson, the hackers compromised a single user account to access the systems of the shipping giant.
“Clarkson PLC confirms that it was subject to a cybersecurity incident which involved unauthorised access to the Company’s computer systems.” Clarkson said in a statement.
“Our initial investigations have shown the unauthorised access was gained via a single and isolated user account which has now been disabled.”
The company has disabled the account after the incident and has started notifying affected customers and individuals.
The company had been expecting the cyber criminals to publish part of the stolen data on Tuesday, but nothing is still happening.

The company said it has been conducting a review of the security of its architecture and announced new IT security measures.
“As you would rightly expect, we’re working closely with specialist police teams and data security experts to do all we can to best understand the incident and what we can do to protect our clients now and in the future,” said Andi Case, CEO of Clarkson. “We hope that, in time, we can share the lessons learned with our clients to help stop them from becoming victims themselves. In the meantime, I hope our clients understand that we would not be held to ransom by criminals, and I would like to sincerely apologise for any concern this incident may have understandably raised.”
New variants of the UBoatRAT RAT hits targets in East Asia
30.11.2017 securityaffairs Apple
Palo Alto Networks discovered a custom RAT dubbed UBoatRAT that has been used in targeted attacks on personnel or organizations related to South Korea.
Security experts from Palo Alto Networks discovered custom remote access Trojan (RAT) dubbed UBoatRAT that has been used in targeted attacks on personnel or organizations related to South Korea and the video gaming industry.
The UBoatRAT has been distributed through Google Drive links, the malware obtains the address of the command and control (C&C) server from GitHub and uses Microsoft Windows Background Intelligent Transfer Service (BITS) to maintain persistence.

The address of the C&C and the destination port are hidden in a file hosted on GitHub, and the malware accesses the file using a specific URL. UBoatRAT communicates with the C&C served using a custom protocol.
Attackers used the GitHub account ‘elsa999’, according to the researchers the author has been frequently updating repositories since July.
UBoatRAT was first spotted on May 2017, at the time it was a simple HTTP backdoor leveraging a public blog service in Hong Kong and a compromised web server in Japan for C&C.
Across the months the authors added several new features to the RAT, the last variant was released during summer.
“Palo Alto Networks Unit 42 has identified attacks with a new custom Remote Access Trojan (RAT) called UBoatRAT.” reads the analysis published by Palo Alto Networks.
“The attacks with the latest variants we found in September have following characteristics.
Targets personnel or organizations related to South Korea or video games industry
Distributes malware through Google Drive
Obtains C2 address from GitHub
Uses Microsoft Windows Background Intelligent Transfer Service(BITS) to maintain persistence.”
The exact targets aren’t still clear at the moment, the experts speculate the hackers aimed to Korea or the video games industry, because Korean-language game titles, Korea-based game company names, and some words used in the video games business were used for delivery.
The UBoatRAT performs malicious activities on the infected machine only when joining an Active Directory Domain, this means that user systems that are not part of a domain would not be impacted.
Threat actors delivered the RAT through a ZIP archive hosted on Google Drive and containing a malicious executable file disguised as a folder or a Microsoft Excel spreadsheet. The latest variants of the UBoatRAT masquerade as Microsoft Word document files.
The RAT halts its execution when detects a virtualization software such as VMWare, VirtualBox, QEmu, when executed it attempts to obtain the Domain Name from network parameters. If it fails to get the domain name, it displays a fake error message and quits.
Otherwise, UBoatRAT copies itself as C:\programdata\svchost.exe, and creates and executes C:\programdata\init.bat, then it displays a specific message and quits.
Experts observed that the malware relies the Microsoft Windows Background Intelligent Transfer Service (BITS), a service for transferring files between machines, to maintain the persistence.
“Bitsadmin.exe is a command-line tool user can create and monitor BITS jobs. The tool provides the option, /SetNotifyCmdLine which executes a program when the job finishes transferring data or is in error. UBoatRAT takes advantage of the option to ensure it stays running on a system, even after a reboot.” continue the analysis.
Once established a covert channel with C&C, the malware waits following backdoor commands from the attacker.
Command Description
alive Checks if whether the RAT is alive
online Keeps the RAT online by sending the packets to C2 periodically
upfile Uploads file to compromised machine
downfile Downloads file from compromised machine
exec Executes process with UAC Bypass using Eventvwr.exe and Registry Hijacking
start Starts CMD shell
curl Downloads file from specified URL
pslist Lists running processes
pskill Terminates specified process
The researchers have identified fourteen samples of UBoatRAT, as well as one downloader associated with the attacks.
“Though the latest version of UBoatRAT was released in September, we have seen multiple updates in elsa999 accounts on GitHub in October. The author seems to be vigorously developing or testing the threat.” concluded Palo Alto Networks.