
Exclusive, CSE CybSec ZLAB Malware Analysis Report: The Italian Job – Android malware masqueraded as Fake Tre Updater
4.12.2017 securityaffairs Android
The CSE CybSec Z-Lab Malware Lab analyzed a new strain of malware apparently developed to target the customers of the Italian telco operator “Tre”.
The malware researchers from ZLab analyzed a new strain of Android malware that appears as a fake 3MobileUpdater. The malware looks like a legitimate app used to retrieve the mobile system update, but it hides a powerful spyware which gathers user info from the smartphone.
In order to trick users, the malicious app pretends to be a software distributed by the Italian Telco company Tre H3G (see the app logo) to check and download smartphone updates.

Figure 1 – Fake Tre Updater – App logo and alert
When the user clicks on the “3 Mobile Updater”, the app shows the screen in the above picture, inviting the user to wait while the system configuration is updated.
In this way, the user will not remove the application waiting form the installation of the legitimate update, but in the background the malware is able to launch a service which periodically sends information and retrieves commands from a Command and Control available at the link “url[.]plus”.
The capabilities of this malicious app are enormous and include the information gathering from various sources, including the most popular social apps, including Whatsapp, Telegram, Skype, Instagram, Snapchat. It is able to steal picture from the gallery, SMS and calls registry apps. All this data is first stored in a local database, created by the malicious app, and later it is sent to the C2C.
Despite its capabilities, the app doesn’t appear well written. The DEBUG flag of the application is enabled, so many activities are logged on the Android logcat and are visible in a simple way.
The presence of the string “TEST” in many strings and some evident coding errors, along the absence of obfuscation mechanism, suggest the malicious app is not written by skilled developers.
The fake Tre updater is probably a “beta” release or in a test phase, this means that the application is not yet widespread.
Finally, it is interesting to highlight the fact that the malware authors used the Italian language, both in the logcat messages and in the code. This circumstance along with the fact that attackers masqueraded the malware as a a fake Tre updater suggest the vxers are Italian.
According to our analysis the fake Tre updater was developed by an Italian firm, targets and motivations are still not clear.
This report could be the starting point for an investigation of Italian law enforcement, it also includes Yara rules that could be used to detect the threat.
You can download the full ZLAB Malware Analysis Report at the following URL:
Malware Analysis Report: Fake 3MobileUpdater
RSA Authentication SDK affected by two critical vulnerabilities, patch it now!
4.12.2017 securityaffairs Vulnerebility
Two different critical vulnerabilities were found in the RSA Authentication SDK (software development kit), patch them asap.
The first bug, tracked as CVE-2017-14377, is authentication bypass that affects the RSA Authentication Agent for Web for Apache Web Server. The flaw could be exploited by a remote unauthenticated user by sending a crafted packet that triggers a validation error, in this way it can gain access to resources on the target.
“Due to an improper input validation flaw in RSA Authentication Agent for Web for Apache Web Server, a remote malicious user can potentially bypass user authentication and gain unauthorized access to resources protected by the agent. The privilege level of an unauthorized user who gains access depends on the authorization policy set by the underlying application that is using the agent.” reads the security advisory.
This vulnerability is only present when the RSA Authentication Agent for Web for Apache Web Server is configured to use the TCP protocol to communicate with the RSA Authentication Manager server. UDP implementation, which is the default configuration, is not vulnerable. Please refer to the RSA Authentication Agent 8.x for Web for Apache Web Server Installation and Configuration Guide for configuration details.”

It is possible to mitigate the issue by configuring the authentication agent to use UDP, RSA has already released a patch at the following address:
https://community.rsa.com/community/products/securid/authentication-agent-web-apache
The second critical vulnerability tracked as CVE-2017-14378 affects the RSA Auth Agent SDK for C, this means that any other systems developed with the SDK would inherit it. The vulnerability doesn’t affect the Java version of the SDK.
The versions 8.5 and 8.7 of the RSA Authentication Agent SDK had an error handling flaw affecting TCP asynchronous mode implementations that could be exploited by an attacker to bypass the authentication in certain limited implementations.
“A security vulnerability in RSA Authentication Agent API/SDK for C versions 8.5 and 8.6 could potentially lead to authentication bypass in certain limited implementations.”
“RSA Authentication Agent API/SDK 8.5/8.6 for C has an error handling flaw that could lead to authentication bypass in certain limited implementations. This issue will occur when the API/SDK is used in TCP asynchronous mode and return codes from the API/SDK are not handled properly by the application.” reads the security advisory.
“Implementations handling the API/SDK return codes appropriately (per coding guidelines documented in the RSA Authentication Agent API for C Developer’s Guide) are not vulnerable.”
The patch for the C version of the SDK is available at the following URL:
https://community.rsa.com/docs/DOC-40601#agents
Experts discovered a new variant of Shadow BTCware Ransomware Variant
4.12.2017 securityaffairs Ransomware
The security expert Michael Gillespie discovered a new variant of the Shadow BTCware Ransomware which is manually installed on unsecured systems.
The security expert Michael Gillespie discovered a new variant of the BTCWare ransomware, the malicious code was spread by hacking into poorly protected remote desktop services and manually installed by crooks.
The new Shadow BTCware Ransomware variant appends the .[email]-id-id.shadow extension to the encrypted files, compared to previous versions it uses new email addresses a victim should contact to receive the instructions to pay the ransomware.
In the last version analyzed by the expert and reported by Bleeping Computer, the contact email address used by crooks is paydayz@cock.li.

The extension appended to encrypted files is also changed, the Shadow BTCware Ransomware variant appends the .[email]-id-[id].shadow extension to encrypted file’s name. (i.e. The file test.jpg is renamed to test.jpg.[paydayz@cock.li]-id-C0C.shadow).
“All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail paydayz@cock.li
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 3 files for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins.” reads an excerpt of the ransom note
As usual, to protect your system you need a proper cybersecurity posture. You should have a reliable and tested backup of data and of course, you have to use behavioral detections security solutions.
As usual, let me suggest to do not open attachments coming with unsolicited email messages, malware scan attachments with security tools (i.e. VirusTotal), make sure the OS and all the software are up to date.
Use strong passwords to protect your web services and never reuse the same password at multiple sites.
Further details, including the IoCs, have been published by Bleeping Computer.
UK Warns Against Gov Use of Russia-based AV Companies
4.12.2017 securityweek BigBrothers
UK NCSC Chief Warns of Supply Chain Risk from Anti-Virus (AV) Software Products
The UK's National Cyber Security Center (NCSC) has warned against the use of UK government and government agencies using Kaspersky Lab products. The ban is not as forthright or as explicit as September's DHS ban on U.S. government agencies using Kaspersky; but it will, for the time being at least, have a similar effect in the UK.
On Friday, NCSC chief Ciaran Martin wrote to permanent secretaries (the most senior civil servants in a UK government ministry) warning about the issue of supply chain risk in cloud-based products. In this sense it is a general warning that all security officers would do well to heed. The NCSC is not a regulator and cannot insist -- but its guidance will undoubtedly be observed.
The warning focuses on Russia and explicitly calls out Kaspersky Lab.
"The NCSC advises that Russia is a highly capable cyber threat actor which uses cyber as a tool of statecraft. This includes espionage, disruption and influence operations. Russia has the intent to target UK central Government and the UK's critical national infrastructure," Martin wrote. "However," adds the letter, "the overwhelming majority of UK individuals and organisations are not being actively targeted by the Russian state, and are far more likely to be targeted by cyber criminals."
The unstated implication is that consumers can carry on using Kaspersky Lab, but that government -- or indeed any organization that processes information classified SECRET and above -- should never use a Russia-based AV provider. This idea is expanded in an associated blog post from Ian Levy, the NCSC technical director. He comments, "We see no compelling case at present to extend that advice to wider public sector, more general enterprises, or individuals." In fact, he goes further: "We really don't want people doing things like ripping out Kaspersky software at large, as it makes little sense."
However, there is also a silver lining for Kaspersky Lab in this warning. Kaspersky is specifically named only twice towards the end of the letter to the permanent secretaries. Firstly, the letter states that the NCSC is in discussion with the Russian firm "about whether we can develop a framework that we and others can independently verify, which would give the Government assurance about the security of their involvement in the wider UK market." Secondly, the letter adds that the NCSC will be transparent about the outcome of these discussions, and "will adjust our guidance if necessary in the light of any conclusions."
This is an approach that Kaspersky Lab has already offered to the U.S. government. In July 2017 Kaspersky Lab offered to give its source code to the U.S. government for analysis. "Anything I can do to prove that we don't behave maliciously I will do it," said CEO Eugene Kaspersky. There is precedent for such code review in the UK. In October, Kaspersky launched a Global Transparency Initiative whose goal is to help the company clear its name following the reports about its inappropriate ties to the Russian government.
Chinese firm Huawei's network products are effectively banned in the U.S. over fears that they could contain backdoors capable of leaking sensitive information back to China. These products are not banned in the UK -- largely down to the operations of a building, commonly known as The Cell, in the market town of Banbury. Here the NCSC has oversight of Huawei source code, and engineers reverse engineer the code looking for flaws and backdoors. Huawei has been given a green light in the UK.
If Kaspersky Lab and the NCSC can come to a similar arrangement with the anti-virus code, then a UK accommodation with Kaspersky Lab might be possible. Eugene Kaspersky is optimistic, tweeting on Saturday, "Let me stress: there is *no* ban for KL products in the UK. We are in touch with @NCSC regarding our Transparency Initiative and I am sure we will find the way to work together."
It will not be easy. Analyzing firmware in a hardware product is easier than analyzing the flow of traffic into and through the cloud; and it is noticeable that the NCSC's primary concern is "the issue of supply chain risk in cloud-based products."
"By definition," explains cyber security researcher and consultant Stewart Twyneham, "anti-virus software needs to have total access to a computer in order to prevent infection -- and modern quarantine mechanisms will often upload suspect viruses to the cloud so that researchers can learn more. This is alleged to have happened in the case of Nghia Hoang Pho back in 2015 -- who copied secret NSA security exploits onto his home computer, which was running Kaspersky's anti-virus."
Pho was charged and pleaded guilty late last week to removing and retaining top-secret documents from his employer, the NSA. The suggestion is that Russian intelligence learned of the presence of this data through automatic uploads of suspect malicious files to Kaspersky's cloud, and then hacked into Pho's computer. How Russian intelligence learned of the NSA files is what is unknown and is the cause for concern. But since this sort of knowledge cannot come from a code review, the possibility even if not the probability of a clandestine relationship between Kaspersky Lab and Russian intelligence can never be proven one way or the other.
If a Kaspersky Lab code review by NCSC finds no back doors or flaws in the software, it is still unlikely to change NCSC guidance over top secret documents. However, since there will be little interest from Russian intelligence in standard consumer computers, it could lead to a tacit acceptance guide for any user outside of government. Further, since the NCSC has promised to be transparent in any findings, that tacit acceptance could be interpreted as explicit acceptance for all users outside of government.
In March of this year, the NCSC warned about "the potential for hostile action against the UK political system." Without confirming that the main threat is from Russia, the letter makes it clear that the primary threat is considered to be that country.
Breach at PayPal Subsidiary Affects 1.6 Million Customers
4.12.2017 securityweek Incindent
PayPal informed customers on Friday that personal information for 1.6 million individuals may have been obtained by hackers who breached the systems of its subsidiary TIO Networks.
TIO is a publicly traded bill payment processor that PayPal acquired in July 2017 for roughly $230 million. The company is based in Canada and it serves some of the largest telecom and utility network operators in North America. TIO has more than 10,000 supported billers and it serves 16 million consumer bill pay accounts.
On November 10, PayPal announced that TIO had suspended operations in an effort to protect customers following the discovery of security vulnerabilities on the subsidiary's platform. PayPal said it had found issues with TIO’s data security program that did not adhere to its own standards.
An investigation conducted in collaboration with third-party cybersecurity experts revealed that TIO’s network had been breached, including servers that stored the information of TIO clients and customers of TIO billers. PayPal said the attackers may have obtained personally identifiable information (PII) for roughly 1.6 million customers.
Affected companies and individuals will be contacted via mail and email, and offered free credit monitoring services via Experian.
While it’s unclear exactly what type of data the hackers have gained access to, the information shared by PayPal and TIO suggests that payment card data and in some cases even social security numbers (SSNs) may have been compromised.
PayPal has highlighted that TIO’s systems have not been integrated into its own platform. “The PayPal platform is not impacted in any way, as the TIO systems are completely separate from the PayPal network, and PayPal’s customers’ data remains secure,” the company said.
The New York State Department of Financial Services (DFS), an agency responsible for regulating financial services and products, has also issued a statement on the incident.
“DFS is working with our regulated entity, PayPal, to investigate and address issues related to cybersecurity vulnerabilities identified at PayPal’s subsidiary, TIO Networks,” the DFS said. “We applaud PayPal’s rapid response to the matter, which put consumers and business clients first, and we appreciate their efforts to inform DFS, as required, in a timely manner. Events like these illustrate the necessity of DFS’s landmark cybersecurity regulation and underscore the strength and effectiveness of our strong state-based financial services regulatory framework, including for the fintech industry.”
TIO said services will not be fully restored until it’s confident that its systems and network are secure.
DHS Says Drone Maker DJI Helping China Spy on U.S.
4.12.2017 securityweek BigBrothers
A memo from the U.S. Department of Homeland Security (DHS) warns that China-based Da-Jiang Innovations (DJI), one of the world’s largest drone manufacturers, has been providing information on critical infrastructure and law enforcement to the Chinese government.
The Los Angeles office of Immigrations and Customs Enforcement (ICE), specifically its Special Agent in Charge Intelligence Program (SIP), issued an intelligence bulletin back in August claiming that DJI is helping China spy on the United States.
A copy of the memo, marked “unclassified / law enforcement sensitive,” was published recently by the Public Intelligence project. The document, based on information from open source reporting and a “reliable source” in the unmanned aerial systems industry, assesses with moderate confidence that DJI is providing data on U.S. critical infrastructure and law enforcement to the Chinese government. The authors of the memo provide several examples of law enforcement and critical infrastructure organizations using DJI drones.
The agency also assesses with high confidence that the company is targeting government and private entities in these sectors in an effort to “expand its ability to collect and exploit sensitive U.S. data.”DJI using drones to help China spy on US
ICE claims two of the Android applications provided by DJI for some of its drones automatically tag GPS imagery and location, register facial recognition data even when turned off, and access data in the user’s phone. The data, which the agency claims to include personal information and other sensitive data, such as power control panels and security measures for critical infrastructure sites, is allegedly stored on cloud servers to which the Chinese government “likely has access.”
“SIP Los Angeles assesses with high confidence the critical infrastructure and law enforcement entities using DJI systems are collecting sensitive intelligence that the Chinese government could use to conduct physical or cyber attacks against the United States and its population,” the memo reads. “Alternatively, China could provide DJI information to terrorist organizations, hostile non-state entities, or state-sponsored groups to coordinate attacks against U.S. critical infrastructure.”
The intelligence bulletin also points to a recent memo of the U.S. Army, which instructs units to stop using DJI drones due to cybersecurity vulnerabilities, and a U.S. Navy memo on the operational risks associated with the use of the Chinese firm’s products. DJI has taken some measures to improve privacy following the Army ban.
The ICE document also claims that DJI aggressively dropped drone prices in 2015 to force its main competitors out of the market.
“The bulletin is based on clearly false and misleading claims from an unidentified source,” DJI said in response to the ICE memo. “Several of the key claims made by this unnamed source show a fundamental lack of understanding of DJI, its technology and the drone market.”
The company claims its products are not capable of recognizing a person’s face for identification purposes – a feature exists for tracking the movement of the shape of a person or the shape of their face in order to control the drone, but DJI claims it only works when the system is powered on and the Active Track mode is enabled.
DJI also refutes claims that its pricing strategy has caused competitors to stop production, and denies selling its products cheaper in the U.S. than in China.
“DJI does strive to comply with local laws and regulations in each country where its drones operate and to facilitate compliance by our customers. To the extent that there are location-specific rules and policies within China, we ensure that our systems comply with these rules, including the need to register or include no-fly zones on board,” DJI stated.
“In compliance with the Chinese regulation, DJI utilizes the user’s IP address, GPS location, and MCC ID to determine if a drone is being operated in China. If so, DJI provides the customer with the features necessary to comply with Chinese regulations and policies. Otherwise, DJI provides no information about or data collected by the drone to the Chinese government,” the company added.
DJI has also shared some more information regarding a recent incident involving a researcher who took part in the company’s bug bounty program. The expert had been offered $30,000 after finding some serious vulnerabilities, but he walked away from the deal due to an agreement DJI had asked him to sign.
The accusations brought against DJI are similar to the allegations that Kaspersky Lab is spying for the Russian government. Kaspersky’s products have been banned in U.S. government agencies by the DHS after several media reports on the topic. However, no evidence has been provided to back the claims.
Here's the NSA Employee Who Kept Top Secret Documents at Home
3.12.2017 thehackernews BigBrothers
A former employee—who worked for an elite hacking group operated by the U.S. National Security Agency—pleaded guilty on Friday to illegally taking classified documents home, which were later stolen by Russian hackers.
In a press release published Friday, the US Justice Department announced that Nghia Hoang Pho, a 67-year-old of Ellicott City, Maryland, took documents that contained top-secret national information from the agency between 2010 and 2015.
Pho, who worked as a developer for the Tailored Access Operations (TAO) hacking group at the NSA, reportedly moved the stolen classified documents and tools to his personal Windows computer at home, which was running Kaspersky Lab software.
According to authorities, the Kaspersky Labs' antivirus software was allegedly used, one way or another, by Russian hackers to steal top-secret NSA documents and hacking exploits from Pho's home PC in 2015.
"Beginning in 2010 and continuing through March 2015, Pho removed and retained U.S. government documents and writings that contained national defense information, including information classified as Top Secret and Sensitive Compartmented Information," the DoJ said in disclosing Pho's guilty plea.
"This material was in both hard-copy and digital form, and was retained in Pho’s residence in Maryland."
For those unaware, the U.S. Department of Homeland Security (DHS) has even banned Kaspersky Labs' antivirus software from all of its government computers over suspicion of the company's involvement with the Russian intelligence agency and spying fears.
Kaspersky CEO Says He Would Leave If Russia Asked Him To Spy
Though there's no substantial evidence yet available, an article published by US news agency WSJ in October claimed that Kaspersky software helped Russian spies steal highly classified documents and hacking tools belonging to the NSA in 2015 from a staffer's home PC.
However, Kaspersky Labs has denied any direct involvement with the Russian spies in the alleged incident.
Just last month, Kaspersky claimed that its antivirus package running on the Pho's home PC detected the copies of the NSA exploits as malicious software, and uploaded them to its cloud for further analysis by its team of researchers.
According to the company, as soon as its analysts realized that its antivirus had collected more than malicious binaries, the company immediately deleted the copy of the classified documents, and also created a special software tweak, preventing those files from being downloaded again.
Even, when asked if Russian intel agency had ever asked him to help it spy on the West at a media briefing at the Kaspersky's offices in London on Tuesday, CEO Eugene Kaspersky said "They have never asked us to spy on people. Never."
Kaspersky further added that "If the Russian government comes to me and asks me to anything wrong, or my employees, I will move the business out of Russia."
NSA Hacker Faces A Prison Sentence Of Up To 10 Years
In Pho's plea deal with prosecutors, the NSA hacker admitted that he copied information from NSA computers multiple times between 2010 and 2015 and took it all home with him.
Taking classified documents at home is a clear violation of known security procedures—and in this process, Pho eventually exposed the top secret information to Russian spies.
Pho has pleaded guilty in a United States district court in Baltimore to one count of willful removal and retention of national defense information, with no other charges filed against him and there's no mention of Pho selling or passing off that confidential data.
The retention of national defense information offense carries a possible 10-year prison sentence.
Federal prosecutors said they would seek an eight-year sentence for Mr. Pho. However, his attorney can ask for a more lenient sentence.
Pho remains free while awaiting sentencing on 6th April next year.
Google to Block Third-Party Software from Injecting Code into Chrome Browser
3.12.2017 thehackernews Safety
To improve performance and reduce crashes caused by third-party software on Windows, Google Chrome, by mid-2018, will no longer allow outside applications to run code within its web browser.
If you are unaware, many third-party applications, like accessibility or antivirus software, inject code into your web browser for gaining more control over your online activities in order to offer some additional features and function properly.
However, Google notes that over 15 percent of Chrome users running third-party applications on their Windows machines that inject code into their web browsers experience crashes—and trust me it's really annoying.
But don't you worry. Google now has a solution to this issue.
In a blog post published Thursday on Chromium Blog, Google announced its plan to block third-party software from injecting code into Chrome—and these changes will take place in three steps:
April 2018 — With the release of Chrome 66, Google will begin informing users if code injection causes their browsers to crash, alerting them with the name of the responsible application and a guide to update or remove it.
July 2018 — Chrome 68 will start blocking third-party software from injecting code into Chrome processes. But if this blocking prevents Chrome from starting, the browser will restart and allow the injection. But it will also display a warning for guiding users to remove that particular software.
January 2019 — With no exception, starting with Chrome 72, Google will completely block code injection by any third-party software.
However, there will be some exceptions. Google Chrome will continue to allow Microsoft-signed code, accessibility software, and IME software to inject code into your browsers.
Today's blog post is an advance notification for all developers out there, whose applications rely on code injection to function properly, forcing them to use either Native Messaging API calls or Chrome extensions to add functionality to the web browser.
"With Chrome extensions and Native Messaging, there are now modern alternatives to running code inside of Chrome processes," Google said.
According to Google, both methods can be used by developers to retain their app features without having to risk browser crashes.
"Fewer crashes mean more happy users, and we look forward to continuing to make Chrome better for everyone," Google said while summing up its blog post.
So, companies have almost 13 months to remove the code injecting bits from their software. Google is encouraging developers to use Chrome Beta channel and test their code, though these changes will more likely take effect in the Dev or Canary channels even sooner.
Now, what you are waiting for? Get ready to start rewriting your code.
After 27-Year Sentence, Russian Hacker Faces Another 14 Years in Prison
3.12.2017 thehackernews Crime
Roman Valerevich Seleznev, the son of a prominent Russian lawmaker who's already facing a 27-year prison sentence in the United States, has been handed another 14-year prison sentence for his role in an "organized cybercrime ring" that caused $59 Million in damages across the US.
In April this year, Seleznev, the 33-year-old son of a Russian Parliament member of the nationalist Liberal Democratic Party (LDPR), was sentenced to 27 years in prison for payment card fraud, causing nearly $170 million in damages to small business and financial institutions in the US.
The sentence was so far the longest sentence ever imposed in the United States for a hacking-related case.
Now, after pleading guilty in two criminal cases stemming from a hacking probe in September, Seleznev Thursday received another 14-year prison sentence for racketeering in Nevada and another 14 years for conspiracy to commit bank fraud charges in Georgia.
The sentences will run concurrently to one another as well as to the previous 27-year prison sentence for 38 counts of payment card fraud, wire fraud, hacking, and identity theft.
Besides the prison sentence, Seleznev has also been ordered to pay almost $51 million in the Nevada case and more than $2.1 million in the Georgia case.
The Justice Department said that Seleznev admitted to helping run an identity theft and credit card fraud ring through the Carder.su website.
According to his plea agreement in the Nevada case, Seleznev admitted developing a website that allowed fraudsters and cybercriminals to easily purchase stolen credit card account data for roughly $20 per account number and advertised his site on Carder.su.
"The defendant's website had a simple interface that allowed members to search for the particular type of credit card information they wanted to buy, add the number of accounts they wished to purchase to their 'shopping cart' and upon check out, download the purchased credit card information," US prosecutors said on Thursday.
"Payment of funds was automatically deducted from an established account funded through L.R., an online digital currency payment system. The Carder.su organization's criminal activities resulted in loss to its victims of at least $50,893,166.35."
According to his guilty plea agreement in the Georgia case, Seleznev admitted that he acted as a "casher" who worked with other criminal hackers to withdraw cash using stolen bank account information.
This scheme defrauded an Atlanta-based company that processed credit and debit card transactions on behalf of banks and financial institutions.
Seleznev admitted that in pursuit of this scheme, hackers breached the company's systems in November 2008 and stole 45.5 million debit card numbers, which they used to fraudulently withdraw more than $9.4 million from 2,100 ATMs in 280 cities worldwide in less than 12 hours.
According to the Department of Justice, law enforcement authorities charged a total of 55 individuals in four separate indictments in their massive operation targeting the Carder.su organization, which they called Operation Open Market.
To date, 33 individuals of the charged individuals have been convicted, while the rest are either pending trials or on the run.
Seleznev, aka Track2, Bulba and Ncux, was arrested in 2014 while attempting to board a flight in the Maldives and then extradited to America. His arrest sparked an international dispute between the US and Russia, who characterized the extradition as a "kidnapping."
Seleznev, along with other cybercriminals, also developed a hacking scheme that leveraged automated techniques to hack into Point-of-Sale (POS) machines in retailers and install malware to steal copies of credit card numbers.
While his sentencing in April, Seleznev's father and Russian MP Valery Seleznev said that the sentence was "passed by man-eaters" and that his son was "abducted."
Russian MP also said that his "son was tortured because being in jail in a foreign country after abduction is torture in itself. He is innocent," and that he viewed the prison sentence as a life sentence as his son would never survive these much years in prison.
Cryptocurrency Mining Scripts Now Run Even After You Close Your Browser
3.12.2017 thehackernews Safety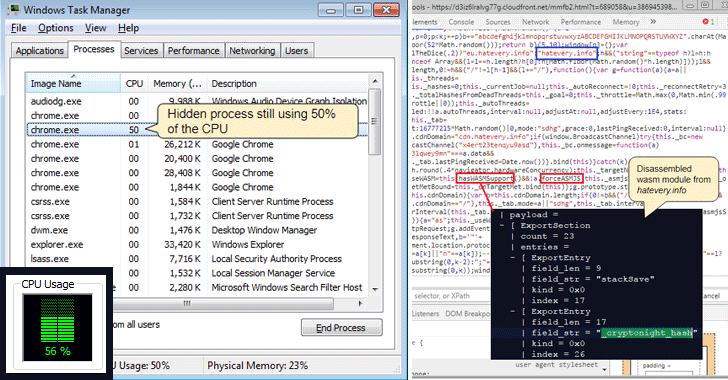
Some websites have found using a simple yet effective technique to keep their cryptocurrency mining javascript secretly running in the background even when you close your web browser.
Due to the recent surge in cryptocurrency prices, hackers and even legitimate website administrators are increasingly using JavaScript-based cryptocurrency miners to monetize by levying the CPU power of their visitor's PC to mine Bitcoin or other cryptocurrencies.
After the world's most popular torrent download website, The Pirate Bay, caught secretly using Coinhive, a browser-based cryptocurrency miner service, on its site last month, thousands of other websites also started using the service as an alternative monetization model to banner ads.
However, websites using such crypto-miner services can mine cryptocurrencies as long as you're on their site. Once you close the browser window, they lost access to your processor and associated resources, which eventually stops mining.
Unfortunately, this is not the case anymore.
Security researchers from anti-malware provider Malwarebytes have found that some websites have discovered a clever trick to keep their cryptocurrency mining software running in the background even when you have closed the offending browser window.
How Does This Browser Technique Work?
According to a blog post published Wednesday morning by Malwarebytes, the new technique works by opening a hidden pop-under browser window that fits behind the taskbar and hides behind the clock on your Microsoft's Windows computer.
From there (hidden from your view), the website runs the crypto-miner code that indefinitely generates cryptocurrency for the person controlling the site while eating up CPU cycles and power from your computer until and unless you notice the window and close it.
Researchers say this technique is a lot harder to identify and able to bypass most ad-blockers because of how cleverly it hides itself. The crypto-miner runs from a crypto-mining engine hosted by Amazon Web Servers.
"This type of pop-under is designed to bypass adblockers and is a lot harder to identify because of how cleverly it hides itself," Jérôme Segura, Malwarebytes' Lead Malware Intelligence Analyst, says in the post. "Closing the browser using the "X" is no longer sufficient."
To keep itself unidentified, the code running in the hidden browser always takes care of the maximum CPU usage and maintains threshold to a medium level.
You can also have a look at the animated GIF image that shows how this clever trick works.
This technique works on the latest version of Google's Chrome web browser running on the most recent versions of Microsoft's Windows 7 and Windows 10.
How to Block Hidden Cryptocurrency Miners
If you suspect your computer CPU is running a little harder than usual, just look for any browser windows in the taskbar. If you find any browser icon there, your computer is running a crypto-miner. Now simply, kill it.
More technical users can run Task Manager on their computer to ensure there is no remnant running browser processes and terminate them.
Since web browsers themselves currently are not blocking cryptocurrency miners neither does the integrated Windows Defender antivirus software, you can use antivirus programs that automatically block cryptocurrency miners on web pages you visit.
For this, you can contact your antivirus provider to check if they do.
Alternatively, you can make use of web browser extensions, like No Coin, that automatically block in-browser cryptocurrency miners for you, and regularly update themselves with new mining scripts that come out.
Created by developer Rafael Keramidas, No Coin is an open source extension that blocks Coin Hive and other similar cryptocurrency miners and is available for Google Chrome, Mozilla Firefox, and Opera.
No Coin currently does not support Microsoft Edge, Apple Safari, and Internet Explorer. So, those using one of these browsers can use an antimalware program that blocks cryptocurrency miners.
HP Silently Installs Telemetry Bloatware On Your PC—Here's How to Remove It
3.12.2017 thehackernews Safety
Do you own a Hewlett-Packard (HP) Windows PC or laptop?
Multiple HP customers from around the world are reporting that HP has started deploying a "spyware" onto their laptops—without informing them or asking their permission.
The application being branded as spyware is actually a Windows Telemetry service deployed by HP, called "HP Touchpoint Analytics Client," which was first identified on November 15.
According to reports on several online forums, the telemetry software—which the HP customers said they never opted to have installed and had no idea was continually running in the background—was pushed out in a recent update.
However, it's not yet clear whether the software has come with the latest Microsoft's Windows updates, or via HP's support assistant processes.
An official description of the software says that the program "harvests telemetry information that is used by HP Touchpoint's analytical services."
HP Touchpoint Makes Your Computer Slow
HP customers also complained that the installation slowed down their system significantly.
On HP's customer forum, one user even reported that due to more than 95 percent CPU usage by the analytics service, his system anti-malware software started checking for suspicious activity.
Another user owning an HP laptop head on to Reddit and said:
"So today all of a sudden, I'm experiencing a considerable slowdown in my laptop (Pavilion P3V59PA). Once I look for the problem in Task Manager, I found out that the program called HP Touchpoint Analytics Client (and it's subsequent follow up) constantly jumping the memory usage (~300Mb at a minimum, ~nearly 2Mb at maximum)."
"I don't remember ever installing this program whatsoever, and in control panel, I found that for some reason this program was silently installed today, without my consent."
German blog reader Detlef Krentz contacted borncity this weekend and wrote:
"I noticed that HP secretly installed the program 'HP Touchpoint Analytics Client' on all my HP devices on November 20, 2017. The program connects every day to HP. The files sent can be found under 'Program Data/HP/HP Touchpoint Analytics Client/Transfer Interface.'"
The program seems to send data to the company's server once per day. If you own an HP PC or laptop, you can find this data under ProgramData\HP\HP Touchpoint Analytics Client\Transfer Interface on the Windows drive.
While responding to the allegations, HP said that the company has been shipping the same software on HP laptops since 2014 as part of its Support Assistant software and that it only collects anonymous information about the computer's hardware performance.
However, the only thing that the company has changed is the name.
"HP Touchpoint Analytics is a service we have offered since 2014 as part of HP Support Assistant. It anonymously collects diagnostic information about hardware performance. No data is shared with HP unless access is expressly granted. Customers can opt-out or uninstall the service at any time," HP said in a statement.
"HP Touchpoint Analytics was recently updated, and there were no changes to privacy settings as part of this update. We take customer privacy very seriously and act in accordance with a strict policy, available here."
Here’s How to Remove HP Touchpoint Analytics Client
If you don't want this application to send data from your computer to HP's servers, you can disable the service or uninstall the program completely, which is relatively quickly and easily.
To uninstall this service, go to Control Panel and right-click on the program name, and select Uninstall to remove it.
Alternatively, you can just press Windows+R, type "appwiz.cpl," and press Enter to load the Programs and Features control panel applet. Now, select "HP Touchpoint Analytics Client" from the list and click the "Uninstall/Change" to remove the service from your PC.
A few months ago, HP was caught using a built-in keylogger that silently spied on your all keystrokes, and stored every single key-press in a human-readable file located at the public folder, making it accessible to any user or 3rd party app installed on the PC.
Recently, Lenovo has also settled a massive $3.5 million fine from the Federal Trade Commission (FTC) for preinstalling spyware onto laptops without users' consent.
Halloware Ransomware, a new malware offered for sale on the Dark Web for Only $40
3.12.2017 securityaffairs Ransomware
The Halloware ransomware is a new malware offered for sale in the dark web, the author that goes online with the moniker Luc1F3R is selling it for just $40.
According to the experts at Bleeping Computer, Luc1F3R started selling the Halloware this week through a dedicated portal on the Dark web. Luc1F3R claims to be a 17-year-old college student from Northeast India.
“Currently, the malware dev is selling and/or advertising his ransomware on a dedicated Dark Web portal, on Dark Web forums, two sites hosted on the public Internet, and via videos hosted on YouTube.” reported Bleeping Computer.
“The sites are offering a lifetime license for the Halloware ransomware for only $40.”
The low price has made the researchers suspicious, so they decided to investigate the case suspecting a scam.
Operational mistakes in the websites used by to Luc1F3R to sell the ransomware allowed the expert from Bleeping Computer to track down a web page where Luc1F3R was hosting the index of Halloware files, The page included weaponized documents used to deliver the malware.

One of the files in the list, hmavpncreck.exe, had the same SHA256 hash for which Luc1F3R included NoDistribute scan results in Halloware’s ad, confirming that it was the malware binary the experts were looking for.
Another file named ran.py seems to be Halloware’s source code.
“While the file was protected, Bleeping Computer managed to extract its source code, which will end up in the hands of other security researchers to create decrypters, in case someone buys this ransomware and uses it to infect real users.” continues the analysis from Bleeping Computer.
The researchers highlighted that Halloware is a working ransomware that encrypts files using a hardcoded AES-256 key and prepends the “(Lucifer)” string to encrypted file names. For example, once encrypted a file named image.png, it will appear as (Lucifer)image.png.
Once the Halloware ransomware has completed the encryption process it pops up a window showing a creepy clown with a ransom message containing the instruction to pay the ransom and decrypt the data. The victim’s desktop wallpaper, also displays a similar message, but experts noticed that Halloware ransomware does not drop text files with ransom notes on the infected PCs.

Wannabe criminals that buy the ransomware can generate their own install by changing two images and adding their customized payment site URL.
Anyway the experts noticed that the ransomware uses a hardcoded AES key and does not save any information on a remote server, this characteristic makes the malware not useful for the criminal underground.
According to Bleeping Computer Luc1F3R is a novice without particular skills. His tutorials published on YouTube describe basic hacking techniques or promote unsophisticated malware.
Some of the video tutorials include a Luc1F3R’s GitHub account that hosts four malware strains:
A Batch-based ransomware.
A Windows keylogger.
A Linux keylogger.
A bulk spoofed email sender.
Further details, including IoCs are available on the Bleeping Computer website.
Europol and law enforcement agencies dismantled a criminal ring specialized in ATM attacks and payment Card Fraud
3.12.2017 securityaffairs CyberCrime
Law enforcement agencies dismantled a criminal ring and arrested four key members responsible for ATM attacks and performing illegal transactions.
European law enforcement agencies announced the success of an operation called “Neptune” that allowed to dismantle a criminal ring and arrest of four key members responsible for stealing payment card data and performing illegal transactions.
The investigation supported by the Europol, involved law enforcement agencies in Italy, Bulgaria, and the Czech Republic.
“The operation run by the Italian Carabinieri, in cooperation with the Bulgarian General Directorate of Combating Organised Crime, and the National Police of Czech Republic, supported by Europol’s European Cybercrime Centre (EC3) culminated today with the arrest of four Bulgarian citizens.” states the press release published by the Europol
“The leaders of the transnational criminal group actively supervised all stages of criminal activities, including placing technical equipment on ATMs in the central areas of European cities, producing counterfeit credit cards and subsequently cashing out money from ATMs in non-European countries, for example Belize, Indonesia and Jamaica.”
The four criminals were arrested on November 30, 2017, they are all Bulgarian citizens.
Crooks targeted ATMs in central areas of European cities to steal credit card data by placing skimmers and hidden cameras. The stolen data were used to clone the cards and use the fake cards to cash out money from ATMs in non-European countries, including as Belize, Indonesia and Jamaica.

Investigators identified dozens of ATMs that have been compromised by the crooks.
Law enforcement seized more than 1,000 counterfeit credit cards and collected of evidence of many fraudulent international transactions worth more than EUR 50,000.
“The coordination and exchange of intelligence has been supported by the Joint Cybercrime Action Taskforce (J-CAT) set up at Europol. Since most of the illegal transactions with counterfeit cards took place overseas, the cooperation through dedicated investigative networks set up by Europol has been instrumental.” continues the press release.
In September, a report published by the Europol warned of a rise of cyber attacks against ATM machines. Criminal organizations are targeting ATM machines through the banks’ networks, the operations involve squads of money mules for the cashout.
Earlier this week, Europol shared the results of the European Money Mule Action ‘EMMA3’, a global law enforcement operation against money mulling. The operation resulted in 159 arrested, 409 suspects interviewed, and 766 money mules and 59 money mule organizers identified.
Kaspersky case – Now we know who is the NSA hacker who kept Agency’s cyber weapons at home
3.12.2017 securityaffairs BigBrothers
A former NSA hacker pleaded guilty on Friday to illegally taking classified documents home, which were later stolen by Russian cyber spies.
A member of the US National Security Agency Tailored Access Operations hacking team, Nghia Hoang Pho (67) pleaded guilty in a US district court in Baltimore on Friday to one count of willful retention of national defense information.
The Vietnam-born American citizen, who lives in Ellicott City, Maryland, has been charged with illegally removing top secret materials.
The NSA hacker admitted taking home copies of classified NSA hacking tools and exploits with the knowledge that they were cyber weapons.
The tools were detected by the Kaspersky Lab software installed on the NSA hacker’s personal computer and were sent back to Kaspersky’s server for further analysis.
Kaspersky Lab, published recently a detailed report on how cyber spies could have easily stolen the software exploits from the NSA employee’s Windows PC.
According to the telemetry logs collected by the Russian firm, the staffer temporary switched off the antivirus protection on the PC, and infected his personal computer with a spyware from a product key generator while trying to use a pirated copy of Office.
On September 11, 2014, Kaspersky antivirus detected the Win32.GrayFish.gen trojan on the NSA employee’s PC, sometime later the employee disabled the Kaspersky software to execute the activation-key generator.
Then the antivirus was reactivated on October 4, it removed the backdoored key-gen tool from the NSA employee’s PC and uploaded it to Kaspersky’s cloud for further analysis.
Kaspersky published a second report that sheds the light on the investigation conducted by the firm on the NSA-linked Equation Group APT.
Kaspersky has begun running searches in its databases since June 2014, 6 months prior to the year the alleged hack of its antivirus, for all alerts triggered containing wildcards such as “HEUR:Trojan.Win32.Equestre.*”. The experts found a few test signatures in place that produced a LARGE number of false positives.
The analysis revealed the presence of a specific signature that fired a large number of times in a short time span on just one system, specifically the signature “HEUR:Trojan.Win32.Equestre.m” and a 7zip archive (referred below as “[undisclosed].7z”). This is the beginning of the analysis of the system that was found containing not only this archive, but many files both common and unknown that indicated this was probably a person related to the malware development.
The analysis of the computer where the archive was found revealed that it was already infected with malware. In October of that year the user downloaded a pirated copy of the Microsoft Office 2013, but the .ISO was containing the Mokes backdoor.
Kaspersky was able to detect and halt Mokes, but the user turned off the Russian software to execute the keygen.
Once the antivirus was turned on again, it detected the malware. Kaspersky added that over a two month its security software found 128 separate malware samples on the machine that weren’t related to the Equation Group.
Kaspersky found that the Mokes’ command and control servers were apparently being operated by a Chinese entity going by the name “Zhou Lou”, from Hunan, using the e-mail address “zhoulu823@gmail.com.”
The security firm explained that it’s also possible that the NSA contractor’s PC may have been infected with a sophisticated strain of malware developed by an APT that was not detected at the time.

The NSA hacker Pho now faces roughly six to eight years in prison, with sentencing set for April 2017.
According to the plea deal, Pho broke federal law because he took the codes at home multiple times, he admitted that, over a five-year period starting in 2010, he copied the information from NSA machines and took it all home with him.
“Beginning in 2010 and continuing through March 2015, Pho removed and retained U.S. Government documents and writings that contained national defense information, including information classified as Top Secret and Sensitive Compartmented Information,” the US Department of Justice said in disclosing the guilty plea.
“This material was in both hard-copy and digital form, and was retained in Pho’s residence in Maryland.”
The positive aspect of the story is that Pho did act with cyber espionage purposes, he wasn’t charged to sell or pass off any of the data.
The fact that Pho was the third NSA employee charged in the past two years for taking home top-secret information is embarrassing and highlights the risk of insiders.
Anonymous launch Brazilian Corrupt Public Sector Entities Data Leak
3.12.2017 securityaffairs Cyber
In an astonishing move, Anonymous leak public sector entities infrastructure topology data for the people of Brazil in the midst of Lava Jato scandal.
The compromised data includes IP addresses from the public sector, ranging law enforcement agencies and local municipality. This data leak comes at a moment where a strong fight against corruption is taking place.
The data leak represents a lack of maturity in adopting a framework, like NIST, for maintaining the secret of information in today’s country information technology marketplace.
Nowadays, it may seem quite usual see these events take place in the evolving, and changing, the threat landscape of digital menaces, but it was expected to take place as hackers usually comes with new attacks as the year approaches its end.
The data reveal in high details, how is structured the network topology of critical services infrastructure including routers, firewalls and other open services.

It is important to notice that all IP ranges from São Paulo military and civil police was leaked, including servers related to public identification and public safety. The compromised data also describes the police servers entirely exposing not only the identity of every police officer, but also the entire public security office.
As it is presented with a message, the intent of the hackers were in the fight against corruption in Brazil, where it took a new ground: the 5th domain. The cyber domain has reached the public opinion where the scrutinity of the society claiming for justice can be reached on the click of a mouse. These corrupt law enforcement agencies are globally known to be involved in extortion, drug traffic dealing, murdering, oppression, violation of the United Nations Human Rights and violence against minorities like black people and homosexuals alike.
The fight against corruption, abuse of power and authority can be a new front line to Lava Jato operation, including the police of the state of São Paulo, where the population lives as hostages to the public service colluding with the organized crime. As shown in the media outlets this week, a strong instance must be taken to reach out the public demands of justice and morality in the tax paid from every citizen.
This single event brings forth an important question: The importance of developing and implementing a security framework like NIST to address the cyber security on ICS/SCADA industrial control system. It is important to notice that the framework is structured in such way that it can be adapted to the existing current model in use. The critical infrastructure, in the face of today’s challenge of information security, must address rogue nation’s threat like North Korea and China.
The data leak is available at the following URL
https://pastebin.com/PfGnk1a7
At least six thousand Lantronix Serial-To-Ethernet devices are leaking Telnet passwords
3.12.2017 securityaffairs Safety
Security researcher discovered thousands of Lantronix Serial-to-Ethernet devices connected online that leak Telnet passwords.
The security researcher Ankit Anubhav, principal researcher at NewSky Security, has discovered thousands of Serial-to-Ethernet devices connected online that leak Telnet passwords.
Hackers can use the leaked passwords to launch cyber attacks against the equipment that is connected to them.
Serial-to-Ethernet “device servers” are used by companies to connect to remote equipment that only exposed a serial interfaces.
The flawed Serial-to-Ethernet “device servers” are manufactured by the US vendor Lantronix.
The products UDS and xDirect easily allow to manage the devices via a LAN or WAN connection, such type of devices allows to easily implement Ethernet connectivity to virtually any device or machine with a serial interface.
Users just need to connect the device RS-XXX serial connector to the product that exposes an RJ-45 Ethernet connector that can be used to control the device.
The “device servers” are widely adopted in to give connectivity to ICS (Industrial Control Systems), most of them are very old equipment that only comes with serial ports.
According to Ankit Anubhav, a half of Lantronix device servers are exposed online leaking their Telnet passwords. An attacker can take over the device via Telnet and use the privileged access to send serial commands to the connected devices.
“6,464 Lantronix device servers that may be connected to critical ICS-grade equipment are proudly exposing their passwords,” Anubhav told Bleeping Computer. “This accounts for 48% of the devices on Shodan.”
Imagine the potential dangers of a cyber attack against an ICS equipment exposed online through the vulnerable Lantronix device.
Anubhav explained that data exposure is an old flaw that could be exploited by attackers to retrieve the setup config of Lantronix devices by sending a malformed request on port 30718.
The Metaploit hacking platform includes a Lantronix “Telnet Password Recovery” module that could be exploited to retrieve the setup record from Lantronix serial-to-ethernet devices via the config port (30718/udp, enabled by default on old versions of Lantronix devices) and extracts the Telnet password in plain text.
Once again patch management is the root cause of the problem, vulnerable devices have not installed security updates to fix the issue.
Microsoft Office obsahuje 17 let starou chybu. Zneužívají ji hackeři
3.12.2017 Novinky/Bezpečnost Zranitelnosti
Populární kancelářský balík Office od společnosti Microsoft má kritickou bezpečnostní chybu. Americký softwarový gigant sice již vydal pro tuto trhlinu opravu, ale je takřka jisté, že ji nezanedbatelná část uživatelů ještě nenainstalovala. A právě na ně se nyní zaměřují počítačoví piráti, uvedl server The Hacker News.
Problém se týká kancelářských balíků Office 2007, 2010, 2013 a 2016.
Trhlina se týká editoru rovnic, který je nedílnou součástí balíku Office. Jde však o velmi starý program, který si odbyl premiéru už v roce 2000.
A po 17 letech v tomto modulu, který využívají velmi často studenti, byla nalezena kritická bezpečnostní chyba. Tu mohou počítačoví piráti zneužít k tomu, aby do PC nainstalovali prakticky jakýkoliv škodlivý kód, klidně mohou i počítač ovládnout na dálku.
Útočníci podstrčí speciálně upravený dokument
Stačí přitom, aby oběť otevřela speciálně upravený dokument, čímž kyberzločincům otevře zadní vrátka do operačního systému.
Bezpečnostní experti ze společnosti Fortinet nyní zachytili již několik škodlivých kódů, které se snaží tuto trhlinu zneužít. Útočníci sází na to, že celá řada uživatelů podceňuje zabezpečení svých PC a nestahuje pravidelně aktualizace. A to ani ty důležité – bezpečnostní.
Tito uživatelé tak dávají svůj počítač všanc počítačovým pirátům.
Nainstalovat aktualizace. Neprodleně
Trhlina se týká kancelářských balíků Office 2007, 2010, 2013 a 2016. Editor rovnic je v nich začleněn jako základní funkce. Teoreticky mohou být postiženi také majitelé balíků Office 2000 a 2003, v těchto verzích se však modul instaloval volitelně.
Uživatelé dotčených kancelářských balíků by měli neprodleně nainstalovat všechny bezpečnostní aktualizace, které jsou aktuálně k dispozici. Stahovat se dají přímo z prostředí Office, případně prostřednictvím služby Windows Update.
Researchers discover a vulnerability in the DIRTY COW original patch
2.12.2017 securityaffairs Vulnerebility
Researchers discovered that the original patch for the Dirty COW vulnerability (CVE-2016-5195) is affected by a security flaw.
The original patch for the Dirty COW vulnerability (CVE-2016-5195) is affected by a security flaw that could be exploited by an attacker to run local code on affected systems and exploit a race condition to perform a privilege escalation attack.
The vulnerability was rated as “Important” and it received a score 6.1 on the CVSS scale, it was patched in October 2016.
The name ‘Dirty COW‘ is due to the fact that it’s triggered by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings.
According to the security advisory published by Red Had, the vulnerability, tracked as CVE-2016-5195, allows local attackers to modify existing setuid files.

Now the flaw in the original patch, tracked as CVE-2017-1000405, was identified by researchers at the security firm Bindecy.
” In the “Dirty COW” vulnerability patch (CVE-2016-5195), can_follow_write_pmd() was changed to take into account the new FOLL_COW flag (8310d48b125d “mm/huge_memory.c: respect FOLL_FORCE/FOLL_COW for thp“). We noticed a problematic use of pmd_mkdirty() in the touch_pmd() function. touch_pmd() can be reached by get_user_pages().” reads the advisory published by Bindecy.
“In such case, the pmd will become dirty. This scenario breaks the new can_follow_write_pmd()’s logic – pmd can become dirty without going through a COW cycle – which makes writing on read-only transparent huge pages possible.”
The new bug is not as severe as the original ‘Dirty cow’ vulnerability that affected many more Linux distributions and the Android operating system.
The current bug doesn’t affect Android and Red Hat Enterprise Linux, anyway millions of machines are vulnerable.
According to Red Hat, the vulnerability does not affect the Linux kernel packages shipped with Red Hat Enterprise Linux 5, 6, 7 and Red Hat Enterprise MRG 2.
The patch released in October 2016 patch addressed the Dirty COW vulnerability for both regular pages and transparent huge pages.
Eylon Ben Yaakov published a technical report on the flaw in the DIRTY COW patch.
The researchers reported the flaw to the Linux Kernel Organization on November 22, the patch was committed to the mainline kernel on November 27, the flaw was officially released on December 1.
Bindecy experts published a PoC code that overwrites the zero-page of the system.
The advisory published by Red Hat includes a mitigation suggestion that consists in disabling the use of “zero page”.
“It is possible to prevent the zero page from being mapped as a huge page, by modifying a configuration tunable in the /sys directory… This prevents the flaw from being exercised in this method. # echo 0 > /sys/kernel/mm/transparent_hugepage/use_zero_page Disabling huge pages: It is possible to mitigate this flaw by disabling hugepages on a system,” according to Red Hat.
Google Chrome will block code injection from third-party software within 14 months
2.12.2017 securityaffairs Safety
Google announced the block of code injection from third-party applications into the Chrome browser. Developers have 14 months to update their code.
Google continues to improve security of its product and services, the IT giant announced the for blocking third-party applications from injecting code into the Chrome browser.
The decision of the company will have a significant impact on many applications from third-party, including antivirus and security software that use to inject code into the browser processed to intercept cyber threats.
“Roughly two-thirds of Windows Chrome users have other applications on their machines that interact with Chrome, such as accessibility or antivirus software.” states the blog post published on Google Chromium.
“In the past, this software needed to inject code in Chrome in order to function properly; unfortunately, users with software that injects code into Windows Chrome are 15% more likely to experience crashes”
The tech giant will introduce the security improvements in three main phases over a 14-months plan.
Below the plan
Phase 1:
In April 2018, starting with Chrome 66 will begin showing users a warning after a crash, alerting them that third-party software attempted to inject code into the browser and providing suggestions on possible fixes or instructions to remove that software.

Phase 2:
Starting from July 2018, Chrome 68 will begin blocking third-party software from injecting into Chrome processes.
If this blocking prevents the Chrome browser from starting, it will restart and allow the injection. Google experts decided that in this scenario, the browser will show a warning that guides the user to remove the software.
Phase 3:
In January 2019, Chrome 72 will remove the warning and will block code injection by default.
Google will allow some exceptions for Microsoft-signed code, accessibility software, and IME (Input Method Editor) type-assist software.
“While most software that injects code into Chrome will be affected by these changes, there are some exceptions. Microsoft-signed code, accessibility software, and IME software will not be affected. As with all Chrome changes, developers are encouraged to use Chrome Beta for early testing.” continues Google.
According to the search giant, fewer crashes means more happy users and the company is committed in giving the users a better experience.
Developers of Windows software that works with Chrome are encouraged to switch Chrome channels and test their code through the Beta channel that allow to test it on next versions of the browser.
Developers can start using new modern Chrome features such as browser extensions or the Native Messaging API, instead of the code injection.
Russian cybercriminal Roman Seleznev gets another prison sentence
2.12.2017 securityaffairs CyberCrime
Seleznev gets another prison sentence. He received 14-year prison sentence for charge in Nevada and another 14 years for the second charge in Georgia.
In April, the Russian hacker Roman Seleznev, aka Track2, Bulba and Ncux, was sentenced to 27 years in prison, he was convicted of causing $170 million in damage by hacking into point-of-sale systems.
The 33-year-old was previously sentenced by a U.S. court to 27 years in prison for 38 counts of wire fraud, hacking, identity theft, and payment card fraud.
Seleznev was pleading guilty to racketeering and conspiracy to commit bank fraud charges on September 7, now he received further 14-year prison sentence for the first charge in Nevada and another 14 years for the second charge in Georgia.
Seleznev must pay roughly $51 million in the Nevada case and more than $2.1 million in the Georgia case.
The overall sentence is added to the previous 27-year sentence.
Seleznev was one of the members of the criminal ring known as Carder.su focused on identity theft and credit card fraud. The hackers advertised his website on Carder.su offering stolen payment card data.
According to the US prosecutors, activities conducted by members of Carder.su caused $50,893,166.35 losses, roughly the same amount that Seleznev has been ordered to pay.

Authorities conducted a massive operation against members of the Carder.su community, they charged 55 individuals and 33 of them have already been convicted.
Seleznev admitted being a “casher” in the Georgia case, he withdrew cash using stolen bank account information. He was involved in a fraudulent activity against an Atlanta-based firm that processed credit and debit card transactions for financial institutions.
Crooks stole more than 45 million payment cards from the financial firm, then they used them to withdraw over $9.4 million from 2,100 ATMs in 280 cities worldwide in less than 12 hours.
Elite U.S. Government Hacker Charged With Taking Secret Information
2.12.2017 securityweek BigBrothers
A member of the US National Security Agency's elite hacking team has been charged with illegally removing top secret materials, in an embarrassing breach for the crucial electronic espionage body.
The Justice Department said Friday that Nghia Hoang Pho, 67, a 10-year veteran of the NSA's Tailored Access Operations unit, which broke into computer systems, agreed to plead guilty to a single charge of removing and retaining top-secret documents from the agency.
He kept the material at his Ellicott City, Maryland home.
According to The New York Times, it was Vietnam-born Pho's computer that apparent Russian hackers accessed via his use of Kaspersky software to steal files and programs the NSA developed for its own hacking operations.
The Justice Department said Pho had taken printed and digital copies of documents and writings labelled "secret," and containing sensitive "national defense information," and stored them in his home from 2010 until he was caught in 2015.
It gave no detail on why he did that, and did not say whether Pho had revealed or lost any of the information.
Pho faces up to 10 years in prison, though could negotiate a lighter punishment.
He was the third NSA employee charged in the past two years for taking home top-secret information.
The NSA declined to respond to questions on the case.
In October The Wall Street Journal reported that Russian hackers exploited anti-virus software made by Kaspersky Lab to steal top secret materials from an unnamed NSA employee.
The Journal said the 2015 hack led to the Russians obtaining information on how the NSA itself penetrates foreign computer networks and protects itself from cyberattacks.
The incident was a key reason why the US government earlier this year announced a ban on use of Kaspersky anti-virus software on government computers, warning that the Moscow-based company has suspect links to Russian intelligence.
Kaspersky denies any ties to the Russian government, but said its own forensic investigation did show that hackers made use of its software to break into the NSA worker's home computer.
Kaspersky said what was stolen included essential source code for so-called Equation Group hacking software from the NSA.