
31 Million of client records belonging to the virtual keyboard app AI.type leaked online
6.12.2017 securityaffairs Hacking
Another day, another clamorous data breach, this time let’s discuss a data breach that exposes personal data collected by the Keyboard App AI.type.
This story reminds us that every time we download an app we are enlarging our surface of attack, in the majority of cases we are not aware of exact amount of data they collect and how they use them
A group of researchers at the Kromtech Security Center has discovered online a huge trove of personal data belonging to more than 31 million users of the popular virtual keyboard app, AI.type.
The data was included in a MongoDB database that has been accidentally exposed online without any mechanism of protection.
“The Kromtech Security Center has discovered a massive amount of customer files leaked online and publically available. Researchers were able to access the data and details of 31,293,959 users.” states the post published by Kromtech Security.
“The misconfigured MongoDB database appears to belong to Ai.Type a Tel Aviv-based startup that designs and develops a personalized keyboard for mobile phones and tablets for both Android and iOS devices.”
Ai.Type was founded in 2010, its customizable and personalizable on-screen keyboard for Android was downloaded about 40 million times from the Google Play store.
The misconfigured MongoDB database exposed 577 GB of data online, the records include sensitive details on the users, and the worst thing is that such data was not even necessary for the app to work. Researchers highlighted the fact that the Ai.Type request “Full Access” to all data stored on the mobile devices.
“When researchers installed Ai.Type they were shocked to discover that users must allow “Full Access” to all of their data stored on the testng iPhone, including all keyboard data past and present. It raises the question of why would a keyboard and emoji application need to gather the entire data of the user’s phone or tablet?” continues the post.
“Based on the leaked database they appear to collect everything from contacts to keystrokes. This is a shocking amount of information on their users who assume they are getting a simple keyboard application.”

The leaked data includes:
Full name, phone number, and email address
Device name, screen resolution and model details
Android version, IMSI number, and IMEI number
Mobile network name, country of residence and even user enabled languages
IP address (if available), along with GPS location (longitude/latitude).
Links and the information associated with the social media profiles, including birth date, emails, photos.
The researcher made another shocking discovery, the 6,435,813 records contained data collected by the app from users’ contact books. The leaked database included more than 373 million records scraped from registered users’ phones, which include all their contacts saved/synced on linked Google account.
The archive also includes a range of statistics.
“There was a range of other statistics like the most popular users’ Google queries for different regions. Data like average messages per day, words per message, the age of users, words_per_day’: 0.0, ‘word_per_session and a detailed look at their customers,” the researchers say.
The real question is, “why would like a keyboard, and emoji application need to gather the entire data of the user’s phone or tablet?”
Android Security Bulletin—December 2017
5.12.2017 Google Android
2017-12-01 security patch level—Vulnerability details
In the sections below, we provide details for each of the security vulnerabilities that apply to the 2017-12-01 patch level. Vulnerabilities are grouped under the component that they affect. There is a description of the issue and a table with the CVE, associated references, type of vulnerability, severity, and updated AOSP versions (where applicable). When available, we link the public change that addressed the issue to the bug ID, like the AOSP change list. When multiple changes relate to a single bug, additional references are linked to numbers following the bug ID.
Framework
The most severe vulnerability in this section could enable a local malicious application to bypass user interaction requirements in order to gain access to additional permissions.
CVE References Type Severity Updated AOSP versions
CVE-2017-0807 A-35056974 EoP High 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2
CVE-2017-0870 A-62134807 EoP High 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0871 A-65281159 EoP High 8.0
Media framework
The most severe vulnerability in this section could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process.
CVE References Type Severity Updated AOSP versions
CVE-2017-0872 A-65290323 RCE Critical 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0876 A-64964675 RCE Critical 6.0
CVE-2017-0877 A-66372937 RCE Critical 6.0
CVE-2017-0878 A-65186291 RCE Critical 8.0
CVE-2017-13151 A-63874456 RCE Critical 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-13153 A-65280854 EoP High 8.0
CVE-2017-0837 A-64340921 EoP High 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0873 A-63316255 DoS High 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0874 A-63315932 DoS High 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0880 A-65646012 DoS High 7.0, 7.1.1, 7.1.2
CVE-2017-13148 A-65717533 DoS High 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
System
The most severe vulnerability in this section could enable a proximate attacker to execute arbitrary code within the context of a privileged process.
CVE References Type Severity Updated AOSP versions
CVE-2017-13160 A-37160362 RCE Critical 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-13156 A-64211847 EoP High 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-13157 A-32990341 ID High 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-13158 A-32879915 ID High 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-13159 A-32879772 ID High 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
2017-12-05 security patch level—Vulnerability details
In the sections below, we provide details for each of the security vulnerabilities that apply to the 2017-12-05 patch level. Vulnerabilities are grouped under the component that they affect and include details such as the CVE, associated references, type of vulnerability, severity, component (where applicable), and updated AOSP versions (where applicable). When available, we link the public change that addressed the issue to the bug ID, like the AOSP change list. When multiple changes relate to a single bug, additional references are linked to numbers following the bug ID.
Kernel components
The most severe vulnerability in this section could enable a local malicious application to execute arbitrary code within the context of a privileged process.
CVE References Type Severity Component
CVE-2017-13162 A-64216036* EoP High Binder
CVE-2017-0564 A-34276203* EoP High ION
CVE-2017-7533 A-63689921
Upstream kernel EoP High File handling
CVE-2017-13174 A-63100473* EoP High EDL
MediaTek components
The most severe vulnerability in this section could enable a local malicious application to execute arbitrary code within the context of a privileged process.
CVE References Type Severity Component
CVE-2017-13170 A-36102397*
M-ALPS03359280 EoP High Display driver
CVE-2017-13171 A-64316572*
M-ALPS03479086 EoP High Performance service
CVE-2017-13173 A-28067350*
M-ALPS02672361 EoP High System server
NVIDIA components
The most severe vulnerability in this section could enable a local malicious application to execute arbitrary code within the context of a privileged process.
CVE References Type Severity Component
CVE-2017-6262 A-38045794*
N-CVE-2017-6262 EoP High NVIDIA driver
CVE-2017-6263 A-38046353*
N-CVE-2017-6263 EoP High NVIDIA driver
CVE-2017-6276 A-63802421*
N-CVE-2017-6276 EoP High Mediaserver
Qualcomm components
The most severe vulnerability in this section could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process.
CVE References Type Severity Component
CVE-2017-11043 A-64728953
QC-CR#2067820 RCE Critical WLAN
CVE-2016-3706 A-34499281
QC-CR#1058691 [2] RCE Critical UDP RPC
CVE-2016-4429 A-68946906
QC-CR#1058691 [2] RCE Critical UDP RPC
CVE-2017-11007 A-66913719
QC-CR#2068824 EoP High Fastboot
CVE-2017-14904 A-63662821*
QC-CR#2109325 EoP High Gralloc
CVE-2017-9716 A-63868627
QC-CR#2006695 EoP High Qbt1000 driver
CVE-2017-14897 A-65468973
QC-CR#2054091 EoP High RPMB driver
CVE-2017-14902 A-65468970
QC-CR#2061287 EoP High MProc
CVE-2017-14895 A-65468977
QC-CR#2009308 EoP High WLAN
Qualcomm closed-source components
These vulnerabilities affect Qualcomm components and are described in further detail in the appropriate Qualcomm AMSS security bulletin or security alert. The severity assessment of these issues is provided directly by Qualcomm.
CVE References Type Severity Component
CVE-2017-6211 A-36217326* N/A Critical Closed-source component
CVE-2017-14908 A-62212840* N/A High Closed-source component
CVE-2017-14909 A-62212839* N/A High Closed-source component
CVE-2017-14914 A-62212297* N/A High Closed-source component
CVE-2017-14916 A-62212841* N/A High Closed-source component
CVE-2017-14917 A-62212740* N/A High Closed-source component
CVE-2017-14918 A-65946406* N/A High Closed-source component
CVE-2017-11005 A-66913715* N/A High Closed-source component
CVE-2017-11006 A-66913717* N/A High Closed-source component
Anti-Phishing Firm IRONSCALES Raises $6.5 Million
5.12.2017 securityweek IT
IRONSCALES, an Israel-based startup that specializes in automated phishing prevention, detection and response, announced on Tuesday that it has raised $6.5 million in a Series A funding round.
This brings the total raised by IRONSCALES since 2015 to more than $8 million. The company says this has been its third consecutive year of triple-digit revenue growth.
The investment round was led by K1 Investment Management, with participation from existing investor RDC. The company says the newly raised funds will be used to accelerate its channel partner program, expand its global sales team, and expedite research and development for its threat detection, intelligence sharing, and incident response technologies.Ironscales raises $6.5 million
“IRONSCALES’ unique approach to phishing detection and remediation particularly resonated with the K1 team, and we looking forward to leveraging our previous experience in partnering with growing security companies as the company strengthens its position within a rapidly evolving market,” commented Hasan Askari, managing partner at K1.
IRONSCALES also announced on Tuesday that its North American headquarters will be launched in the first quarter of 2018. The company’s VP of sales will be based in Atlanta, Georgia, while R&D will remain in Israel.
IRONSCALES products provide protection for every stage of an email-based phishing attack. IronSchool provides simulations and training for an organization’s employees, while IronSights is designed to detect phishing attacks in users’ inboxes. IronTraps is a solution for automated incident response, and Federation provides real-time intelligence sharing.
Android's December 2017 Patches Resolve Critical Flaws
5.12.2017 securityweek Android
The December 2017 Android security patches that Google released this week resolve 47 vulnerabilities, including 10 rated Critical severity.
The patches affect a variety of platform components and were split in two packages, or security patch levels, as Google calls them. The first addresses 19 vulnerabilities while the second resolves 28 issues.
The 2017-12-01 security patch level resolves 6 Critical severity vulnerabilities and 13 High risk flaws, Google notes in a security bulletin.
The issues affect the framework (3 High risk elevation of privilege bugs), Media framework (5 Critical remote code execution, 2 High elevation of privilege, and 4 High denial-of-service bugs), and System components (1 Critical remote code execution, 1 High elevation of privilege, and 3 High information disclosure issues).
The 2017-12-05 security patch level addresses 4 Critical risk vulnerabilities and 24 High severity issues.
The vulnerabilities were found in Kernel components (4 High elevation of privilege bugs), MediaTek components (3 High elevation of privilege flaws), NVIDIA components (3 High elevation of privilege issues), Qualcomm components (3 Critical remote code execution and 6 High elevation of privilege flaws), and Qualcomm closed-source components (1 Critical and 8 High flaws of undisclosed type).
Devices updated with the 2017-12-01 or later patch level are safe from all issues associated with the 2017-12-01 security patch level. The security patch levels of 2017-12-05 or later, on the other hand, resolve the issues associated with all previous patch levels as well.
Along with the Android security bulletin for December 2017, Google announced a separate set of security updates for Nexus and Pixels devices, meant to address vulnerabilities and bring functional improvements to supported Google devices.
As part of this month’s set of patches, Google resolved a total of 48 issues in Media framework, Broadcom, Kernel, MediaTek, NVIDIA, and Qualcomm components, as well as in Qualcomm closed-source components.
Most of the resolved vulnerabilities were elevation of privilege bugs, but Google also addressed DoS and information disclosure bugs. The vast majority of the issues were Moderate severity, except for a Critical bug in Qualcomm closed-source components and a High severity issue in Kernel components.
All supported Nexus and Pixel devices will receive these patches as part of the 2017-12-05 security patch level.
MailSploit — Email Spoofing Flaw Affects Over 30 Popular Email Clients
5.12.2017 thehackernews Hacking

If you receive an email that looks like it's from one of your friends, just beware! It's possible that the email has been sent by someone else in an attempt to compromise your system.
A security researcher has discovered a collection of vulnerabilities in more than 30 popular email client applications that could allow anyone to send spoofed emails bypassing anti-spoofing mechanisms.
Discovered by security researcher Sabri Haddouche, the set of vulnerabilities, dubbed MailSploit, affects Apple Mail (macOS, iOS, and watchOS), Mozilla Thunderbird, several Microsoft email clients, Yahoo Mail, ProtonMail, and others.
Although most of these affected email client applications have implemented anti-spoofing mechanisms, such as DKIM and DMARC, MailSploit takes advantage of the way email clients and web interfaces parse "From" header.
Email spoofing is an old-school technique, but it works well, allowing someone to modify email headers and send an email with the forged sender address to trick recipients into believing they are receiving that email from a specific person.
In a dedicated website went up today, Haddouche explained how the lack of input sanitization implemented by vulnerable email clients could lead to email spoofing attack—without actually exploiting any flaw in DMARC.
To demonstrate this attack, Haddouche created a payload by encoding non-ASCII characters inside the email headers, successfully sending a spoofed email from an official address belonging to President of the United States.
"Using a combination of control characters such as new lines or null-byte, it can result in hiding or removing the domain part of the original email," Haddouche says in his blog post.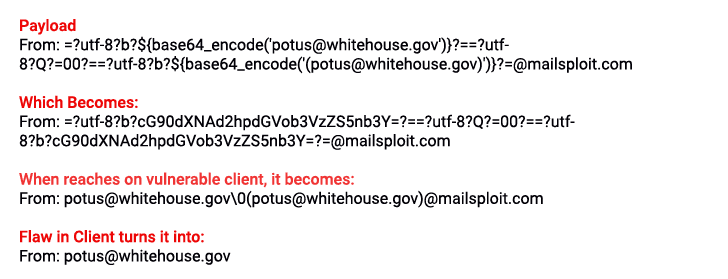
"We've seen a lot of malware spreading via emails, relying on social engineering techniques to convince users to open unsafe attachments, or click on phishing links. The rise of ransomware distributed over email clearly demonstrates the effectivity of those mechanisms."
Besides spoofing, the researcher found some of the email clients, including Hushmail, Open Mailbox, Spark, and Airmail, are also vulnerable to cross-site scripting (XSS) vulnerabilities, which stems from the email spoofing issue.
Haddouche reported this spoofing bug to 33 different client applications, 8 of which have already patched this issue in their products before the public disclosure and 12 are on their way to fix it.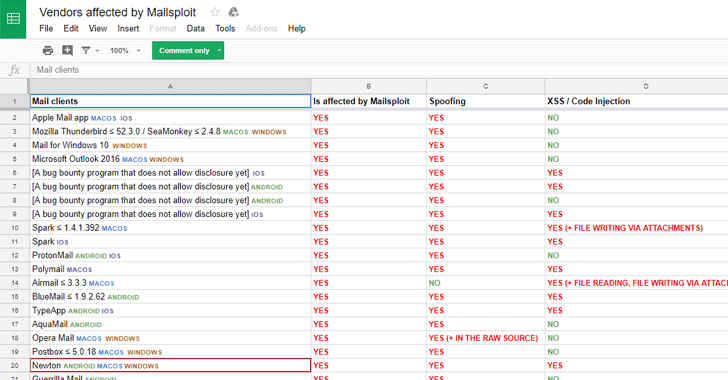
Here you can find the list of all email and web clients (both patched and unpatched) that are vulnerable to MailSploit attack.
However, Mozilla and Opera consider this bug to be a server-side issue and will not be releasing any patch. Mailbird closed the ticket without responding to the issue, while remaining 12 vendors did not yet comment on the researcher's report.
Young Hacker, Who Took Over Jail Network to Get Friend Released Early, Faces Prison
5.12.2017 thehackernews Hacking
Well, "a friend in need is a friend indeed" goes a long way, but in this case, this phrase hardly makes any sense.
A 27-year-old Michigan man who hacked into the government computer system of Washtenaw County Jail to alter inmate records and gain early release for his friend is now himself facing federal charges after getting caught.
Konrads Voits from Ann Arbor, Michigan, pleaded guilty in federal court last week for hacking into the Washtenaw County government computer system earlier this year using malware, phishing, and social engineering tricks in an attempt to get his friend released early from jail.
Prosecutors say Voits also used phone calls to prison staff claiming to be a manager at the County Jail's IT department and tricking them into downloading and running malware on their computers by visiting a phony website at "ewashtenavv.org," which mimics the Washtenaw official URL, "ewashtenaw.org."
Voit then obtained the remote login information of one of the Jail employees and used that information to install malware on the County's network and gain access to sensitive County's XJail system in March this year.
Gaining access to this system eventually allowed Voits to steal jail records of several inmates, search warrant affidavits and personal details, including passwords, usernames, and email addresses, of over 1,600 employees, along with altering electronic records of at least one inmate for early release.
However, things did not work as Voits wanted them to, and instead, they all backfired on him when jail employees detected changes in their records and alerted the FBI.
No prisoners were then released early.
This incident took place between January 24th, 2017 and March 10th, 2017 and cost Washtenaw County more than $235,000 to fix the whole mess before authorities busted Voits.
"Cyber intrusions affect individuals, businesses and governments. Computer hackers should realize that unlawfully entering another's computer will result in a felony conviction and a prison sentence," said the United States Attorney Daniel Lemisch.
"We applaud the dedication of so many hard-working law enforcement officers to take away this man's [Voits] ability to intrude into the computer systems of others."
Voits was arrested by the authorities a month later and pleaded guilty last week. He is now facing a fine of up to $250,000 and a maximum sentence of ten years prison, though he is unlikely to receive the maximum sentence.
Voits has agreed to surrender his belongings used during the attack, including his laptop, four cellphones and an undisclosed amount of Bitcoin.
Voits is currently in federal custody and is set to face a sentencing hearing on 5 April 2018.
PayPal Subsidiary Data Breach Hits Up to 1.6 Million Customers
5.12.2017 thehackernews Incindent
Global e-commerce business PayPal has disclosed a data breach that may have compromised personally identifiable information for roughly 1.6 million customers at a payment processing company PayPal acquired earlier this year.
PayPal Holdings Inc. said Friday that a review of its recently acquired company TIO Networks showed evidence of unauthorized access to the company's network, including some confidential parts where the personal information of TIO's customers and customers of TIO billers stored.
Acquired by PayPal for US$233 Million in July 2017, TIO Network is a cloud-based multi-channel bill payment processor and receivables management provider that serves the largest telecom, wireless, cable and utility bill issuers in North America.
PayPal did not clear when or how the data breach incident took place, neither it revealed details about the types of information being stolen by the hackers, but the company did confirm that its platform and systems were not affected by the incident.
"The PayPal platform is not impacted in any way, as the TIO systems are completely separate from the PayPal network, and PayPal's customers' data remains secure," The data breach in TIO Networks was discovered as part of an ongoing investigation for identifying security vulnerabilities in the payment processing platform.
As soon as PayPal identified an unauthorized access to the TIO's network, PayPal took action by "initiating an internal investigation of TIO and bringing in additional third-party cybersecurity expertise to review TIO's bill payment platform," PayPal press release [PDF] reads.
The company has begun working with companies it services to notify potentially affected customers.
Besides notifying, the company is also working with a consumer credit reporting agency, Experian, to provide free credit monitoring memberships for fraud and identity theft to those who are affected by the breach.
To protect its customers, TIO has also suspended its services until a full-scale investigation into the incident is completed.
"At this point, TIO cannot provide a timeline for restoring bill pay services, and continues to recommend that you contact your biller to identify alternative ways to pay your bills," TIO's Consumer FAQ reads.
"We sincerely apologize for any inconvenience caused to you by the disruption of TIO's service."
Since the investigation is ongoing, PayPal will communicate with TIO customers and merchant partners directly as soon as the company has more details on the incident. Also, the affected customers will be directly contacted by the company.
Is Your DJI Drone a Chinese Spy? Leaked DHS Memo Suggests
5.12.2017 thehackernews BigBrothers
The United States Department of Homeland Security (DHS) has recently accused Da-Jiang Innovations (DJI), one of the largest drone manufacturers, of sending sensitive information about U.S. infrastructure to China through its commercial drones and software.
A copy memo from the Los Angeles office of the Immigration and Customs Enforcement bureau (ICE) has begun circulating online more recently, alleging "with moderate confidence" that DJI drones may be sending US critical infrastructure and law enforcement data back to China.
However, the bureau accessed "with high confidence" that this critical data collected by the DJI systems could then be used by the Chinese government to conduct physical or cyber attacks against the U.S. critical infrastructure and its population.
The memo goes on to specify the targets the Chinese Government has been attempting to spy on, which includes rail systems, water systems, hazardous material storage facilities, and construction of highways, bridges, and rails.
The memo, marked as "unclassified/law enforcement sensitive," was dated back to August this year, but was recently published by the Public Intelligence project.
In its memo, ICE cited what it called a reliable source in the drone industry "with first and secondhand access," but did not identify it, specifying that the concern is over DJI drones used by companies and institutions, not the ones flown by hobbyists in the U.S. and elsewhere.
According to ICE, the DJI drones operate on two Android smartphone apps—DJI GO and Sky Pixels—that automatically tag GPS imagery and locations, access users' phone data, and register facial recognition data even when the system is off.
Beside this, ICE says the apps also capture users identification and personal information, like their full names, email addresses, phone numbers, computer credentials, images, and videos.
"Much of the information collected includes proprietary and sensitive critical infrastructure data, such as detailed imagery of power control panels, security measures for critical infrastructure sites, or materials used in bridge construction," the ICE memo reads.
Citing an unnamed source, ICE alleged that DJI then automatically uploads this collected information to its cloud storage systems located in China, Taiwan, and Hong Kong, which the Chinese government most likely has access to.
Drone Maker Denies Sending Data to Chinese Government
Of course, the drone-maker has denied the allegations, saying that the memo from the US government office was based on "clearly false and misleading claims."
"The allegations in the bulletin are so profoundly wrong as a factual matter that ICE should consider withdrawing it, or at least correcting its unsupportable assertions," DJI said in a statement, cited by The New York Times.
According to a DJI spokesman, users have complete control over how much data they can share with the Chinese drone maker, and the automatic function offered by the DJI apps to store user flight logs can also be turned off.
Moreover, the DJI has recently added a new feature that allows pilots to cut off all outside internet connections while the drone is flying.
According to drone research firm Skylogic Research, DJI dominates the overall drone market with an almost two-thirds share in the United States and Canada. Not just hobbyists, but DJI drones are also used by commercial customers like contractors, police and realtors.
The accusation that DJI is facing is similar to the one faced by Kaspersky Labs for spying on its users and sending the stolen data back to the Russian government.
The DHS has also banned Kaspersky antivirus products in US government agencies over Russian spying fears without actually having any substantial evidence. The company has always denied any direct involvement with the Russian spies in the alleged incident.
Feds Shut Down 'Longest-Running' Andromeda Botnet
5.12.2017 thehackernews BotNet
In a coordinated International cyber operation, Europol with the help of international law enforcement agencies has taken down what it called "one of the longest-running malware families in existence" known as Andromeda.
Andromeda, also known as Win32/Gamarue, is an infamous HTTP-based modular botnet that has been around for several years now, and infecting computers with it's malicious intentions ever since.
The primary goal of Andromeda bot is to distribute other malware families for mass global malware attacks.
The botnet has been associated with at least 80 malware families, and in the last six months, it was detected (or blocked) on an average of more than 1 million machines per month.
Last year, law enforcement agencies took down the criminal infrastructure of the infamous Avalanche botnet in a similar massive international cyber operation. Avalanche botnet was used as a delivery platform to spread other malware families, including Andromeda.
While investigating into the Avalanche botnet, information obtained by the German authorities was shared with the Federal Investigation of Bureau (FBI) via Europol, which eventually helped the international agencies to tear down Andromeda just last week.
In a joint operation, the international partners took down servers and more than 1,500 web domains which were being used to distribute and control Andromeda malware.
"This is another example of international law enforcement working together with industry partners to tackle the most significant cybercriminals and the dedicated infrastructure they use to distribute malware on a global scale," Steven Wilson, the Head of Europol's European Cybercrime Centre (EC3), said.
"The clear message is that public-private partnerships can impact these criminals and make the internet safer for all of us."
Using sinkholing the now-seized domains, tactic researchers use to redirect traffic from the infected machines to a self-controlled system; authorities found over 2 million unique IP addresses from at least 223 countries associated with Andromeda victims with just 48 hours.
Further investigation also helped law enforcement authorities arrest a suspect in Belarus, who was allegedly involved in the Andromeda cybercrime gang.
Just last week, Europol seized more than 20,000 web domains for illegally selling counterfeit products, including luxury products, sportswear, electronics, pharmaceuticals and online piracy on e-commerce platforms and social networks in its fight against the online trade of counterfeit goods.
German Government prepares Law for backdoors and hacking back
5.12.2017 securityaffairs BigBrothers
The German Government is preparing a law that will force hardware vendors to include a backdoor in their products and to allow its unit to hack back.
The German Government is preparing a law that will force hardware vendors to include a backdoor in their products. The law aims to allow law enforcement agencies to use backdoors to gather information during their investigations.
The law would target devices in any industry, including telecommunications, automotive and IoT products.
According to local news outlet RedaktionsNetzwerk Deutschland (RND), German Officials are expected to submit their proposal for debate this week.
“The acting Federal Minister of the Interior Thomas de Maizière (CDU) wants to oblige the industry, German security authorities to open digital gateway for the spying on private cars, computers and smart TVs.” states the news outlet.
“The application is overwritten with “Need for action on the legal obligation of third parties for measures of covert information gathering according to §§ 100c and 100f StPO”. De Maizière wants to drastically expand the so-called eavesdropping attack by “using technical means against individuals”. Above all, large corporations and producers of digital security systems should be required to provide information and notification.”
The proposal is strongly supported by the Federal Minister of the Interior Thomas de Maizière who cites the difficulty investigations have had in the past especially when fighting against terrorist organizations.

The Interior Minister explained that modern technology is able to alert suspects for every suspicious activity conducted by law enforcement agencies.
The Minister cited the cases of smart cars that alert an owner as soon as the car is shaken or any other anomalous activity is conducted by police officers.
Well the presence of a backdoor could allow investigators to operate stopping any warning is sent to the suspect.
De Maizière stressed out that companies have a “legal obligation” to introduce backdoors for the use of law enforcement agencies.
The Minister aims to oblige hardware manufacturer to disclose their “programming protocols” for analysis of Government experts and consequently to force companies to disclose details about their encrypted communication practices.
“Accordingly, eavesdropping would in future be possible wherever devices are connected to the Internet. The industry should give the state exclusive access rights, such as private tablets and computers, smart TVs or digitized kitchen appliances. A precondition for all measures of the extended wiretapping attack, however, would remain a judicial decision.” continues the news outlet.
One of the most disturbing aspects of the new law is that it would give German officials powers to hack back any remote computer that is suspected to be involved in attacks against the country infrastructure.
Something similar was discussed by the French Defense Minister Le Drian comments in January 2017 and by the US authorities, in both cases, the Government officials were referencing the cyber attacks conducted by the Russian intelligence.
The Minister says this is important to “shut down private computers in the event of a crisis,” such as is the case with botnet takedowns.
“De Maizière also wants an authorization for the security authorities to shut down private computers in the event of a crisis. An “Botnet takedown specialist concept” will allow security authorities to use private data to alert end users in good time if hackers want to misuse their computers for criminal purposes. In the event that online providers refuse to cooperate, far-reaching penalties are provided for.” continues the RedaktionsNetzwerk Deutschland.
Privacy advocates believe the German law could open the door to a mass surveillance programs, Government officials will have full powers of snooping everyone’s online communications.
The German authorities refused such kind of accusations and highlighted that any access to data gathered under these surveillance programs would be allowed only after law enforcement have obtained a court order.
The reality is that the presence of backdoor dramatically reduces the overall security of any system, the backdoors could be discovered and used by malicious actors such as a foreign government and a criminal syndicate with unpredictable consequences.
Global operation allowed law enforcement agencies to take down the Andromeda Botnet
5.12.2017 securityaffairs BotNet
A joint international operation conducted by the FBI, law enforcement agencies in Europe and private partners managed to dismantle the Andromeda botnet.
A joint international operation conducted by the FBI and law enforcement agencies in Europe managed to dismantle the dreaded Andromeda botnet (aka Gamarue and Wauchos) last week.
The Andromeda botnet has been around since 2011, it was used across the years to distribute several malware families, including the Dridex banking Trojan or the GamaPoS point-of-sale (PoS) malware.
Law enforcement authorities worldwide dismantled several long-running botnets powered by the malware family dubbed as Gamarue, mostly detected by the security firm ESET as Win32/TrojanDownloader.Wauchos.
ESET worked with Microsoft to disruption the botnets, the experts tracked the malicious infrastructure, identified their C&C servers and the threat delivered by each of them.
“Microsoft then contacted law enforcement with information that included: 464 distinct botnets, 80 associated malware families, and 1,214 domains and IP addresses of the botnet’s C&C servers.” states the analysis published by ESET.

The joint operation was performed on November 29 and involved experts from the FBI, the Luneburg Central Criminal Investigation Inspectorate in Germany, Europol’s European Cybercrime Centre (EC3), the Joint Cybercrime Action Task Force (J-CAT), Eurojust, and private-sector partners,
The takeover of the Andromeda botnet was also possible thanks to the last year’s shut down of a large criminal network known as Avalanche, an infrastructure used to power mass global malware attacks and money mule recruiting.
“One year ago, on 30 November 2016, after more than four years of investigation, the Public Prosecutor’s Office Verden and the Luneburg Police in Germany, the United States Attorney’s Office for the Western District of Pennsylvania, the Department of Justice, the FBI, Europol, Eurojust and global partners, had dismantled the international criminal infrastructure Avalanche. This was used as a delivery platform to launch and manage mass global malware attacks such as Andromeda, and money mule recruitment campaigns.” states the report published by the Europol.
“Insights gained during the Avalanche case by the investigating German law enforcement entities were shared, via Europol, with the FBI and supported this year’s investigations to dismantle the Andromeda malware last week.”
According to the Europol, the experts were able to identify 1500 domains used by the Avalanche platform and used the sinkholing technique to analyzed its traffic and track the infected systems. Microsoft revealed that during 48 hours of sinkholing, the experts observed approximately 2 million unique Andromeda victim IP addresses from 223 countries.
The operation also included the search and arrest of a suspect in Belarus.
The investigators then extended the sinkholing of the Avalanche infrastructure for another year, as globally 55% of the computers originally infected in Avalanche continue to be infected.
The activity against Andromeda and Avalanche involved the following countries: Austria, Belgium, Finland, France, Italy, the Netherlands, Poland, Spain, the United Kingdom, Australia, Belarus, Canada, Montenegro, Singapore, and Taiwan.
“This is another example of international law enforcement working together with industry partners to tackle the most significant cyber criminals and the dedicated infrastructure they use to distribute malware on a global scale. The clear message is that public-private partnerships can impact these criminals and make the internet safer for all of us,” Steven Wilson, the Head of Europol’s European Cybercrime Centre, said.
Technical details about the global operations are included in a report published by ESET.
DJI drones may be sending data about U.S. critical infrastructure and law enforcement to China
5.12.2017 securityaffairs BigBrothers
The US DHS has accused the Chinese Da-Jiang Innovations (DJI) of cyber espionage on U.S. critical infrastructure and law enforcement.
The US Department of Homeland Security (DHS) has recently accused the Chinese Da-Jiang Innovations (DJI), one of the largest drone manufacturers, of sending sensitive information about U.S. critical infrastructure and law enforcement to China.
A copy memo from the Los Angeles office of the Immigration and Customs Enforcement bureau (ICE) was published recently by the Public Intelligence project. The copy was marked as “unclassified / law enforcement sensitive, it alleges “with moderate confidence” that DJI drones were used by the Chinese Government as spying tools.
The authors of the memo provide several examples of law enforcement and critical infrastructure organizations using the DJI drones.
The situation is worrisome because data gathered by the DJI could be used by the Chinese government to conduct physical or cyber attacks against the US critical infrastructure (i.e. rail systems, water systems, hazardous material storage facilities, and construction of highways, bridges, and rails).

The concern is related only to DJI drones used by companies and government organizations, not the unmanned vehicles used by hobbyists.
“It is based on information derived from open source reporting and a reliable source within the unmanned aerial systems (UAS) industry with first and secondhand access. The date of information is 9 August 2017.” reads the intelligence bulletin.
“(U//LES) SIP Los Angeles assesses with moderate confidence that Chinese-based company DJI Science and Technology is providing U.S. critical infrastructure and law enforcement data to the Chinese government. SIP Los Angeles further assesses with high confidence the company is selectively targeting government and privately owned entities within these sectors to expand its ability to collect and exploit sensitive U.S. data.”
According to the ICE, the DJI drones operate on two Android smartphone applications called DJI GO and Sky Pixels that automatically tag GPS imagery and locations, register facial recognition data even when the system is off, and access smartphone data.
The ICE revealed the mobile apps also gather user’s identification and personal information, including full names, email addresses, phone numbers, computer credentials, images, and videos.
“Additionally, the applications capture user identification, e-mail addresses, full names, phone numbers, images, videos, and computer credentials. Much of the information collected includes proprietary and sensitive critical infrastructure data, such as detailed imagery of power control panels, security measures for critical infrastructure sites, or materials used in bridge construction.” the ICE memo reads.
“According to the source of information (SOI), DJI automatically uploads this information into cloud storage systems located in Taiwan, China, and Hong Kong, to which the Chinese government most likely has access. SIP Los Angeles assesses with high confidence a foreign government with access to this information could easily coordinate physical or cyber attacks against critical sites.”
The Chinese drone manufacturer denied the allegations, in a statement, the company said the report was “based on clearly false and misleading claims.”
“The allegations in the bulletin are so profoundly wrong as a factual matter that ICE should consider withdrawing it, or at least correcting its unsupportable assertions,” DJI said in a statement, cited by The New York Times.
According to a DJI spokesman, users can properly configure their drones to control over how much data they can share with the Chinese drone manufactures.
“DJI does strive to comply with local laws and regulations in each country where its drones operate and to facilitate compliance by our customers. To the extent that there are location-specific rules and policies within China, we ensure that our systems comply with these rules, including the need to register or include no-fly zones on board,” DJI stated.
“In compliance with the Chinese regulation, DJI utilizes the user’s IP address, GPS location, and MCC ID to determine if a drone is being operated in China. If so, DJI provides the customer with the features necessary to comply with Chinese regulations and policies. Otherwise, DJI provides no information about or data collected by the drone to the Chinese government,”
Moreover, the DJI has recently implemented a new feature that allows pilots to cut off all outside internet connections while the drone is flying.
Hacked password service Leakbase shuts down, someone suspects it was associated to the Hansa seizure
5.12.2017 securityaffairs Hacking
LeakBase, an online service that provided paid access to leaked credentials, was shut down over the weekend, what has happened?
LeakBase, an online service that provided paid access to leaked credentials, was shut down over the weekend and started redirecting to the data breach notification website HaveIBeenPwned.
2 Dec
LeakBase
@LeakbasePW
This project has been discontinued, thank you for your support over the past year and a half.
LeakBase
@LeakbasePW
We understand many of you may have lost some time, so in an effort to offer compensation please email, refund@leakbase.pw
Send your LeakBase username and how much time you had left.
We will have a high influx of emails so be patient, this could take a while
3:38 AM - Dec 3, 2017
2 2 Replies 1 1 Retweet 2 2 likes
Twitter Ads info and privacy
The service started selling membership access in September 2016, claiming to provide access to two billion credentials resulting from major data leaks.
In January 2017, after launching the paid breach notification service, the LeakedSource went dark, apparently because it was raided by feds.

The popular investigator Brian Krebs associated the shutdown of the LeakBase service with the seizure of the Hansa black marketplace occurred in July, Krebs cited a source close to the matter.
“A source close to the matter says the service was taken down in a law enforcement sting that may be tied to the Dutch police raid of the Hansa dark web market earlier this year.” wrote Krebs.
Leakbase reportedly came under new ownership in April 2017, after it was hacked. According to the anonymous source cited by Krebs, the new owners of Leakbase dabbled in dealing illicit drugs at Hansa dark web marketplace.
“The Dutch police had secretly seized Hansa and operated it for a time in order to gather more information about and ultimately arrest many of Hansa’s top drug sellers and buyers. ” continues Krebs.
“According to my source, information the Dutch cops gleaned from their Hansa takeover led authorities to identify and apprehend one of the owners of Leakbase. This information could not be confirmed, and the Dutch police have not yet responded to requests for comment.”
Leakbase denied the accusation in this tweet:
LeakBase
@LeakbasePW
The fact that we need to tweet this is disappointing in its self, non of the LeakBase operators have any connections to Hansa.
The fact that this can be portrayed as near fact is astonishing as it is only a claim.
4:10 PM - Dec 4, 2017
2 2 Replies 4 4 Retweets 3 3 likes
Twitter Ads info and privacy
Regardless of whether a connection to Hansa exists, the ownership of these services could prove that their commercial activity aimed to help potential victims of data breaches and not to facilitating further crimes.