Philippine Bank Accuses Bangladesh of Heist 'Cover-Up'
13.12.2017 securityweek CyberCrime
A Philippine bank on Tuesday accused Bangladesh's central bank of a "massive cover-up" over an $81-million cyber-heist last year, as it rejected allegations it was mostly to blame.
Unidentified hackers shifted $81 million in February last year from the Bangladesh central bank's account with the US Federal Reserve in New York to a Manila branch of the Rizal Commercial Banking Corp (RCBC).
The money was quickly withdrawn and laundered through Manila casinos.
With only a small amount of the stolen money recovered and frustration building in Dhaka, Bangladesh's Finance Minister A.M.A Muhith said over the weekend he wanted to "wipe out" RCBC.
RCBC on Tuesday said Muhith's remarks were "extremely irresponsible".
"Last year's theft of $81 million of Bangladesh's Central Bank's (BB) funds was an inside job and BB is engaging in a massive cover-up by maligning RCBC and refusing to divulge its findings," the bank said in a statement on Tuesday.
Related: US Suspects North Korea in $81 Million Bangladesh Theft
"BB should stop making RCBC its scapegoat."
The Philippines last year imposed a record $21-million fine on RCBC after a "special examination" of the bank and its role in the audacious cyber heist.
Philippine authorities have filed money laundering charges against the RCBC branch manager.
On Tuesday RCBC said an "inside job" at Bangladesh Bank made the heist possible.
"If it was stolen by your own people, why ask us? We are actually a victim of BB's negligence," RCBC said.
Asked about the allegation of an inside job, Bangladesh Bank deputy governor Razee Hassan insisted RCBC was at fault for releasing the stolen money.
"(RCBC) did not do due diligence. Their central bank did not fine them without any reason," he told AFP.
Singapore Ministry of Defence Announces Bug Bounty Program
13.12.2017 securityweek BigBrothers
Singapore’s Ministry of Defence (MINDEF) has invited roughly 300 white hat hackers from around the world to take part in a two-week bug bounty program targeting eight of its Internet-facing systems.
The MINDEF Bug Bounty Programme, scheduled to run between January 15 and February 4, 2018 is powered by the HackerOne platform.
The initiative covers the Defence Ministry’s public website, its I-Net and email services, the Central Manpower Base site, the Defence Science and Technology Agency site, and the NS, eHealth, LearNet 2 and myOASIS portals. Some of the targeted systems belong to the Singapore Armed Forces (SAF).
Rewards will range between S$150 (USD110) and roughly S$20,000 (USD15,000), and the total amount paid out will depend on the number and quality of bug reports. However, the cost of running the bug bounty program is expected to be less than what a commercial cybersecurity company would charge for an assessment, the Ministry said.
“Singapore is constantly exposed to the increasing risk of cyberattacks, and MINDEF is an attractive target for malicious cyber activity,” MINDEF said. “It is not possible to fully secure modern day computer software systems, and new vulnerabilities are discovered every day. As hackers with malicious intent find new methods to breach networks, MINDEF must constantly evolve and improve its defences against cyber threats.”
The announcement comes just months after the Ministry admitted that hackers had managed to breach a military system that stored non-classified data and personal information on servicemen and employees.
Singapore announced last year its intention to block Internet access on government computers for security reasons, but officials later clarified that the goal was to segregate sensitive systems from other online activities.
Singapore is the home city for SecurityWeek’s 2018 Singapore ICS Cyber Security Conference, an event dedicated to serving critical infrastructure and industrial internet stakeholders in the APAC region. The conference will take place April 24-26, 2018 at the Fairmont Singapore.
Greek Court Orders Extradition of Russian Bitcoin Suspect to US
13.12.2017 securityweek Crime
Greece's Supreme Court on Wednesday ordered that a Russian accused of laundering $4 billion using bitcoin digital currency be extradited to the United States, a court source said.
Greece's justice minister will now have the final say on whether to extradite Alexander Vinnik, who headed BTC-e, an exchange for the cyber currency.
He was indicted by a US court in July on 21 charges ranging from identity theft and facilitating drug trafficking to money laundering.
Vinnik has been held in a Greek jail since his arrest on July 25 in the northern Greek tourist resort of Halkidiki. He denies the accusation.
Russia has also filed a demand to extradite Vinnik so he can stand trial on separate fraud charges.
Two Greek courts separately approved both extradition requests in October.
BTC-e, founded in 2011, became one of the world's largest and most widely used digital currency exchanges.
According to the US indictment, it was "heavily reliant on criminals".
In addition, BTC-e "was noted for its role in numerous ransomware and other cyber-criminal activity".
It allegedly received more than $4 billion (3.4 billion euros) worth of Bitcoin over the course of its operation.
Vinnik was also charged with receiving funds from the infamous hack of Mt. Gox -- an earlier digital currency exchange that eventually failed, in part due to losses attributable to hacking.
The US Treasury Department has slapped BTC-e with a $110 million fine for "wilfully violating" US anti-money laundering laws. Vinnik himself has been ordered to pay $12 million.
In Russia, Vinnik is wanted on separate fraud charges totalling 9,500 euros.
He has said he would accept extradition to his home country.
New Spider Ransomware Emerges
13.12.2017 securityweek Ransomware
A new ransomware family discovered when analyzing a mid-scale campaign that started over the weekend uses decoy documents auto-synced to enterprise cloud storage and collaborations apps, security researchers have say.
Dubbed Spider, the new threat was observed being distributed via an Office document supposedly targeting users in Bosnia and Herzegovina, Serbia, and Croatia. The spam emails suggest the sender is looking to collect some debt from the recipient in attempt to trick the user into opening the attached file.
Obfuscated macro code embedded in the Office document, however, launches a Base64 encrypted PowerShell script to download the malicious payload, Netskope’s Amit Malik says.
If the malware is able to successfully infect a system, it starts encrypting user’s files and adds the ‘.spider’ extension the affected files.
A decrypter was designed to display the user interface and allow users decrypt the files using a decryption key. It is executed alongside the encrypter but runs in the background until the encryption process has been completed, BleepingComputer’s Lawrence Abrams explains.
According to Malik, the Spider decrypter monitors system processes and prevents the launch of tools such as taskmgr, procexp, msconfig, regedit, cmd, outlook, winword, excel, and msaccess.
During encryption, the malware skips files in the following folders: tmp, Videos, winnt, Application Data, Spider, PrefLogs, Program Files (x86), Program Files, ProgramData, Temp, Recycle, System Volume Information, Boot, and Windows.
After completing the encryption process, the decrypter displays a warning (available in English and Croatian) informing users on how they can decrypt their files. A help section is also included, with links and references to the resources needed to make the payment.
The ransom payment demanded is roughly $120.
“As ransomware continues to evolve, administrators should educate employees about the impact of ransomware and ensure the protection of the organization’s data by making a regular backup of critical data. In addition to disabling macros by default, users must also be cautious of documents that only contain a message to enable macros to view the contents and also not to execute unsigned macros and macros from untrusted sources,” Netskope says.
ISIS & Al Qaeda: What’s Coming Down the Line for the U.S. in 2018
13.12.2017 securityaffairs Cyber
ISIS & Al Qaeda: What’s Coming Down the Line for the U.S. in 2018. From drones to chemical attacks, which are the major risks?
Last month, the Department of Homeland Security (DHS) warned that, “our enemies remain focused on attacking the United States, and they are constantly adapting. DHS and its partners are stepping up efforts to keep terrorists out of America and to prevent terrorist recruitment and radicalization here at home, and we urge the public to remain vigilant and report suspicious activity.”
The DHS also indicated the U.S. is facing a significant, ongoing terror threat and the agency’s website displayed an “Elevated” alert level (second from the most severe), which means a credible threat of terrorism against the U.S. exists.
Guess Who’s Back
Al Qaeda never really went away, of course. The 30-year-old terrorist organization had just, for the most part, receded to the background while the Islamic State took center stage. While ISIS has been driven out of Iraq and Syria, they are alive and well in Africa and Europe. ISIS supporters can be found in the U.S. as well, as evidenced by recent activity by the group’s devotees.
Al Qaeda has reemerged as stronger now than they were when Bin Laden was killed. While the world was focused on ISIS, al Qaeda was quietly amassing power, planning, strengthening alliances and fundraising.
Earlier in the year, Stratfor reported that some are concerned that al Qaeda and ISIS may reunite:
“The idea of the global jihadist movement’s two major poles joining forces is certainly a troubling one. The combined capabilities of the Islamic State and al Qaeda could pose a significant threat to the rest of the world, making them a much more dangerous enemy together than divided.”
Though both groups follow Salafist ideology, it might be difficult to merge the two groups’ divergent goals. The Islamic State seeks global conquest in the establishment of Caliphate, while Al Qaeda is focused on the demise of the United States. Al Qaeda boasts a sophistication gained from years of experience, selectivity in recruiting and an assortment of well-educated scholars, including scientists and engineers.
Viewed as crude, by al Qaeda, ISIS also lacks the restraint exercised by al Qaeda.
Some collaboration, between these two terrorist groups, has already occurred in Syria, where fighters with Hayat Tahrir al-Sham (HTS), also known as al Qaeda in Syria, and ISIS were found to have a somewhat cooperative relationship. Additionally, al Qaeda emir Ayman al Zawahiri has been attempting to build bridges among groups with similar enemies. And, al Zawahiri reiterated the fact that the U.S. is al Qaeda’s number one priority.
In comparing the two groups, Critical Threats points out that, “while ISIS had used conquest and bombastic proclamations to capture popular support and gain momentum, al Qaeda worked quietly with a softer approach to securing support.”
Moreover:
“The strengthening of al Qaeda is more dangerous than the success of ISIS. Al Qaeda’s softer approach to building popular support at the grassroots level evoked little, if any, reaction from the West. The West bought al Qaeda’s line that its local focus is a local issue. Al Qaeda further managed the reactions of the communities into which it was insinuating itself by permitting outbursts of local resistance and adjusting its time line to avoid generating backlash. ISIS’s conquest, by contrast, resulted in the West mobilizing a military effort against the group and harsh reaction from its conquered communities over time. ISIS’s coerced popular support in the Muslim world will collapse. Al Qaeda is positioned to absorb the remnants of ISIS, benefit from ISIS’s global mobilization, and sustain its own momentum within Sunni communities to strengthen the Salafi-jihadi movement.”
Al Qaeda does have sleeper cells, within the U.S., who are responsible for planning and launching attacks. But, there are also “lone wolf” supporters of Al Qaeda, in addition to ISIS proponents, in the U.S., who are preparing to launch attacks on their own.
There has also been found to be increasing collaboration among various terror groups in the Maghreb- particularly in Libya. They have been exchanging ideas for training, military tactics, PR, recruitment, and financing.
AEI reports:
“Libya is a key node for the global Salafi-jihadi movement.7 The Libyan base provides the global movement with a destination for jihad, a transit and training zone, and a key node for global foreign fighter flows. It is already an important enabler for the global Salafi-jihadi threat against the United States, Europe, and American interests.
Al Qaeda and ISIS are consolidating a safe haven in Libya from which they will directly threaten the West over the long term.”
Add to that the fact that al Qaeda in the Maghreb (AQIM) has managed to turn a profit of around $100 million through ransom, drug trading, taxing locals and donations from around the world, according to a study by the Foundation for Defense of Democracies.
The global Salafi-jihadi movement was and remains more than just al Qaeda—or ISIS, however. The American Enterprise Institute cautions that, “the need is urgent. Al Qaeda, the Islamic State, and the global Salafi-jihadi movement together are stronger today than they have ever been.”
Holiday season threats have been issued primarily to Europe, but to New York City, also:
The Hill reports: “An ominous poster of Santa Claus standing next to a box of dynamite in Times Square appeared in a pro-ISIS forum earlier this week with the headline ‘we meet at Christmas in New York soon.’ A picture of a masked jihadi, with a rifle in the front seat of a car driving toward the Vatican marked with the banner ‘Christmas Blood so wait’ appeared a few days before that.”
A new series of threatening images posted on social media and messaging apps, with ISIS imagery, is being shared. These graphics call for terror attacks on New York City, Paris and London.
Other posters include images of London’s Regent Street and the Eiffel Tower in Paris, with images of jihadists and blood superimposed on them. A chilling message in English, German and French is included: ‘Soon on your holidays.’
According to Metro.co.uk, “a propaganda poster emerged showing a terrorist in the Vatican with a rocket launcher. The message warned that ‘the crusaders feast is approaching’, suggesting they are planning to attack the Catholic church’s holy city. Another was shared online showing a masked figure driving towards St Peter’s Basilica with a gun and a backpack inside his car, with the message ‘Christmas blood’ written in red underneath.”
Potential Terror Threats to the U.S. in 2018
Hezbollah – “While I’m not here today to speak publicly about any specific, or credible, or imminent threat to the homeland, we in the intelligence community do in fact see continued activity on behalf of Hezbollah here inside the homeland,” National Counterterrorism Center Director Nicholas Rasmussen said. Rasmussen went on to say that it is the center’s, “assessment that Hezbollah is determined to give itself a potential homeland option as a critical component of its terrorism playbook.” He pointed out the recent arrests of alleged Hezbollah operatives in Michigan and New York.
The two alleged operatives that were arrested are Ali Kourani and Samer el Debek. Charged with providing material support to Hezbollah’s Islamic Jihad Organization, Kourani described his role as a “sleeper.” And, according to the complaint, El Debek was trained in making landmines and other explosives.
Dirty Bombs – Terrorist could use drones to drop dirty bombs or poison on U.S. cities. Security officials have said that it may just be a matter of time before such schemes could come to fruition in America. In August, Australian federal police disrupted an ISIS plot to construct an “improvised chemical dispersion device,” which they planned to deploy in urban areas. Hydrogen sulfide, a poisonous gas, would have been spread over the urban areas had the plot not been foiled.
Possible Backlash – Some Muslim leaders have said they view the plan to move the U.S. Embassy to from Tel Aviv to Jerusalem as “a declaration of war.”
Also, Jihadists across the ideological spectrum have beseeched Muslims to take physical action instead of merely protesting the planned move of the U.S. Embassy to Jerusalem.
For its part, al-Qaeda has urged followers all around the world to target U.S. interests, its allies and Israel in response to the U.S. Embassy plan. “A statement posted Friday on al-Qaeda’s media arm as-Sahab, in both Arabic and English, urged holy war or jihad and described America as a modern-era ‘pharaoh’ oppressing Muslims. Branches of the global terror network, including the North Africa branch known as Al-Qaeda in the Islamic Maghreb and also al-Qaeda in the Arabian Peninsula, issued similar statements.”
Then too, Sheikh Hamza bin Laden, son of Osama bin Laden, has called for the group’s supporters to “embrace the kinds of ‘lone wolf attacks’ used by Islamic State, its bitter rival, in which jihadists execute terror operations acting largely on their own and without direction.”
Attacks on the US Government & Critical Infrastructure – Some experts anticipate that in 2018 a major attack on U.S. critical infrastructure will occur. “Additionally, tension between the U.S. and other countries could escalate to online cyberattacks. In October, the FBI and DHS warned of advanced persistent threat activity targeting energy, nuclear, water, aviation, construction, and critical manufacturing sectors. Critical infrastructure companies are behind in preparing their operational facilities to confront cyberattacks – making them an easy target for politically-motivated attackers – Adi Dar, CEO, Cyberbit”
On social media and encrypted messenger apps, training materials are being produced and shared at an alarming rate and volume. This includes an astonishing assortment of bomb-making instructions and recipes for a whole host of gases and volatile compounds.
Of late, in these online forums, a lot of emphasis is placed on bioterrorism, with detailed training materials being provided on how to execute attacks on “kuffars” using substances such as anthrax, ricin and botulism.
Regarding bioterrorism, former White House biodefense aide Robert Kadlec said that, “the trends indicate more terrorist groups are interested in conducting such attacks.”
In 2016, ISIS operatives planned to contaminate water sources in Turkey with bacteria causing tularemia, which is a potentially fatal human illness. In another ISIS-linked ploy, an anthrax attack in Kenya was thwarted by the police. And, in yet another instance in Nigeria, the army intercepted poisoned fish believed to have been brought into the country by Boko Haram operatives.
Both al Qaeda and ISIS have threatened public transportation in the U.S., but online, al Qaeda has been heavily promoting its train derailment tool, providing detailed instructions on how to use it and the best routes across the country to use it on.
On the Telegram app, there are channels in which collaboration among the supporters of ISIS, al Qaeda and other Salafist terrorist groups, such as Ansar al Sharia, is taking place. Shared on these channels is a seemingly endless array of tools for lone wolves, including remote control detonators, a device that explodes when one opens a door, car bombs, hidden bombs and much more. Very detailed instructions are given for all of these explosive devices. The channels generally have hundreds of participants and the channels get reported and shut down frequently, but are back up again shortly afterwards. Channel administrators simply continue distributing materials to those who desire to be a well-equipped, adequately trained lone wolf.

The massive cache of Islamic State propaganda videos found on the cellphone of Sayfullo Saipov, the man accused of using a truck to mow down pedestrians and cyclists recently in New York City, provided a glimpse of the vast amount of jihadist content on the internet.
Along with 90 videos and 3,800 images found,were depictions of beheadings and bomb-making instructions.
The amount of jihadist content on the internet is staggering. The efforts of law enforcement, intelligence agents and private intel agencies around the world are not sufficient to thwart every planned attack, though many have been thwarted.
One way individuals can help is by always being aware of their surroundings. People should report any suspicious behavior potentially related to terrorism to law enforcement.
And, since many terror attacks are closely linked to online activity such as planning attacks, garnering materials and instructions on how to carry out attacks, warnings about attacks and gloating immediately following an attack, be sure to also report suspicious behavior you see online.
Adobe Patch Tuesday only addressed a moderate severity regression issue affecting Flash Player
13.12.2017 securityaffairs Vulnerebility
Adobe released the Patch Tuesday, this month it only addressed a moderate severity regression issue affecting Flash Player tracked as CVE-2017-11305.
It was a poor Patch Tuesday this month for Adobe that only addressed a moderate severity regression issue affecting Flash Player tracked as CVE-2017-11305.
The vulnerability was described as a “business logic error,” that can cause the unintended reset of the global settings preference file.
“Adobe has released a security update for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. This update addresses a regression that could lead to the unintended reset of the global settings preference file.” reads the Adobe Security Bulletin.
According to the company, there is no evidence of exploitation in the wild.
The regression issue affects version 27.0.0.187 and earlier of Flash Player on Windows, Mac, Linux and Chrome OS. Adobe patched the flaw with the release of version 28.0.0.126. Microsoft has also updated the Flash Player components used by its software in order to address this issue.
In November, Adobe addressed a total of 80 vulnerabilities across 9 products, most of which for Acrobat and Reader, including dozens of RCE issues.
A banking Trojan targeting the Polish banks was found in Google Play
13.12.2017 securityaffairs Android
It has happened again, several banking Trojan samples have been found on Google Play, this time the malicious code targeted a number of Polish banks.
The malware was disguised as seemingly legitimate apps “Crypto Monitor”, a cryptocurrency price tracking app, and “StorySaver”, a third-party tool for downloading stories from Instagram.
The malicious code is able to display fake notifications and login forms on the infected device to harvest login credentials used to access legitimate banking applications. The code is also able to intercept SMS messages to bypass two-factor authentication used by the financial institutions.
The same malware was discovered by experts at security firm RiskIQ in November.
According to researchers from ESET, the “Crypto Monitor” app was uploaded to the Play store on November 25 by the developer walltestudio, while the “StorySaver” app was uploaded by the developer kirillsamsonov45 on November 29.
“Together, the apps had reached between 1000 and 5000 downloads at the time we reported them to Google on December 4. Both apps have since been removed from the store.” states the analysis published by ESET.

When the user launches the malicious apps, they compare the apps installed on the infected device against a list of fourteen apps used by Polish banks and once found one of them, the malicious code can display fake login forms imitating those of the targeted legitimate apps.
App name Package name
Alior Mobile com.comarch.mobile
BZWBK24 mobile pl.bzwbk.bzwbk24
Getin Mobile com.getingroup.mobilebanking
IKO pl.pkobp.iko
Moje ING mobile pl.ing.mojeing
Bank Millennium wit.android.bcpBankingApp.millenniumPL
mBank PL pl.mbank
BusinessPro pl.bph
Nest Bank pl.fmbank.smart
Bank Pekao eu.eleader.mobilebanking.pekao
PekaoBiznes24 eu.eleader.mobilebanking.pekao.firm
plusbank24 eu.eleader.mobilebanking.invest
Mobile Bank eu.eleader.mobilebanking.raiffeisen
Citi Handlowy com.konylabs.cbplpat
In some cases the fake login form is displayed to the user only after he clicks on a fake notification presented by the malware imitated the ones used by the targeted bank app.
“ESET’s security systems detect the threat as Android/Spy.Banker.QL and prevent it from getting installed.” states ESET.
“ESET telemetry shows that 96% of the detections come from Poland (the remaining 4% from Austria), apparently due to local social engineering campaigns propagating the malicious apps.”
The experts noticed that it is very easy to remove the malicious apps by going to Settings > (General) > Application manager/Apps, searching for the malicious apps and uninstalling them.
“To avoid falling prey to mobile malware in the future, make sure to always check app ratings and reviews, pay attention to what permissions you grant to apps, and use a reputable mobile security solution to detect and block latest threats.” concluded ESET.
ESET, who credited Witold Precikowski for the discovery, included the IoCs for this specific threat in its report.
December Microsoft Patch Tuesday addresses 19 Critical browser issues
13.12.2017 securityaffairs Vulnerebility
Microsoft released Patch Tuesday updates for December 2017 that address more than 30 vulnerabilities, including 19 Critical browser issues.
Microsoft has released its Patch Tuesday updates for December 2017 that address more than 30 vulnerabilities, including 19 critical flaws affecting the Internet Explorer and Edge web browsers.
Microsoft addressed several memory corruption flaws that can be exploited for remote code execution. Most of the vulnerabilities reside in the browser’s scripting engine, an attack can trigger them by tricking the victim into visiting a specially crafted website or a site that serves malicious ads.
Microsoft acknowledged researchers from Google, Palo Alto Networks, McAfee and Qihoo 360 for finding the issues.
The list of vulnerabilities fixed this month includes “important” information disclosure flaw tracked as CVE-2017-11927. The vulnerability affects the Windows its:// protocol handler, where the InfoTech Storage Format (ITS) is the storage format used in CHM files.
“An information disclosure vulnerability exists when the Windows its:// protocol handler unnecessarily sends traffic to a remote site in order to determine the zone of a provided URL. This could potentially result in the disclosure of sensitive information to a malicious site.” read the security advisory published by Microsoft.
“To exploit the vulnerability an attacker would have to trick a user into browsing to a malicious website or to an SMB or UNC path destination. An attacker who successfully tricked a user into disclosing the user’s NTLM hash could attempt a brute-force attack to disclose the corresponding hash password.”
The list of flaws addressed by Microsoft also includes a collection of information disclosure issues in Office, a privilege escalation vulnerability affecting SharePoint, a spoofing issue in Exchange, and a remote code execution vulnerability in Excel.
The good news is that according to Microsoft, none of the vulnerabilities addressed with the December Patch Tuesday has been exploited in attacks or disclosed publicly before fixes were released.
Adobe has also published its December Patch Tuesday, this month the company only patched one moderate severity vulnerability in Flash Player.
ROBOT Attack: RSA TLS crypto attack worked against Facebook, PayPal, and tens of 100 top domains
13.12.2017 securityaffairs Krypto
ROBOT ATTACK – Security experts have discovered a 19-year-old flaw in the TLS network security protocol that affects many software worldwide.
The security researchers Hanno Böck and Juraj Somorovsky of Ruhr-Universität Bochum/Hackmanit, and Craig Young of Tripwire VERT, have discovered a 19-year-old vulnerability in the TLS network security protocol in the software several tech giants and open-source projects.
The flaw in RSA PKCS #1 v1.5 encryption affects the servers of 27 of the top 100 web domains, including Facebook and PayPal, it could be exploited by an attacker to decrypt encrypted communications.
The researchers dubbed the flaw ROBOT, which stands for Return Of Bleichenbacher’s Oracle Threat.
“ROBOT is the return of a 19-year-old vulnerability that allows performing RSA decryption and signing operations with the private key of a TLS server.” the researchers explained.
“In 1998, Daniel Bleichenbacher discovered that the error messages given by SSL servers for errors in the PKCS #1 1.5 padding allowed an adaptive-chosen ciphertext attack; this attack fully breaks the confidentiality of TLS when used with RSA encryption.
We discovered that by using some slight variations this vulnerability can still be used against many HTTPS hosts in today’s Internet.”
Today we are still discussing the ROBOT attack because the mitigations drawn up at the time were not enough and many software vendors did not properly implement these protections.
“The real underlying problem here is that the protocol designers decided (in 1999) to make workarounds for using an insecure technology rather than replace it with a secure one as recommended by Bleichenbacher in 1998.” said Young.

This ROBOT attack could allow attackers to decrypt RSA ciphertexts without recovering the server’s private key as explained in a security advisory published by CISCO.
“An attacker could iteratively query a server running a vulnerable TLS stack implementation to perform cryptanalytic operations that may allow decryption of previously captured TLS sessions.” states the advisory published by Cisco.
“To exploit this vulnerability, an attacker must be able to perform both of the following actions:
Capture traffic between clients and the affected TLS server.
Actively establish a considerable number of TLS connections to the vulnerable server. The actual number of connections required varies with the implementation-specific vulnerabilities, and could range from hundreds of thousands to millions of connections.”
Fortunately, the vulnerability affects only 2.8% of the top million websites, this small value is due to the fact that the affected library is mainly used for expensive commercial products that are often used to enforce security controls on popular websites.
Similar issues exist in XML Encryption, PKCS#11 interfaces, Javascript Object Signing and Encryption (JOSE), and Cryptographic Message Syntax / S/MIME.
As a proof-of-concept for the ROBOT attack, the experts have demonstrated practical exploitation by signing a message with the private key of facebook.com’s HTTPS certificate.
Facebook was using a patched version of OpenSSL for its vulnerable servers, according to the tech giant the issue was caused by custom patches applied by the company.
Facebook has patched its servers before the disclosure of the paper on the ROBOT attack.
Several vendors have fixes pending, the following list includes patches that are already available.
F5 BIG-IP SSL vulnerability CVE-2017-6168
Citrix TLS Padding Oracle Vulnerability in Citrix NetScaler Application Delivery Controller (ADC) and NetScaler Gateway CVE-2017-17382
Radware Security Advisory: Adaptive chosen-ciphertext attack vulnerability CVE-2017-17427
Cisco ACE End-of-Sale and End-of-Life CVE-2017-17428
Bouncy Castle Fix in 1.59 beta 9, Patch / Commit CVE-2017-13098
Erlang OTP 18.3.4.7, OTP 19.3.6.4, OTP 20.1.7 CVE-2017-1000385
WolfSSL Github PR / patch CVE-2017-13099
MatrixSSL Changes in 3.8.3 CVE-2016-6883
Java / JSSE Oracle Critical Patch Update Advisory – October 2012 CVE-2012-5081
According to Young, the most interesting attack scenarios see hackers having access to the target’s network traffic, a position that could be obtained by an attacker exploiting the KRACK attack to target a Wi-Fi connection.
The impact of ROBOT attacks is severe, an attacker can steal sensitive and confidential data, including passwords, credit card data, and other sensitive details.
The experts released a python tool to scan for vulnerable hosts so everyone can check his HTTPS server against ROBOT attack.
Researchers also included countermeasures in their paper, they recommend to deprecate the RSA encryption key exchange in TLS and the PKCS #1 v1.5 standard.
“We can therefore conclude that there is insufficient testing of modern TLS implementations for old vulnerabilities. The countermeasures in the TLS standard to Bleichenbacher’s attack are incredibly complicated and grew more complex over time. It should be clear that this was not a viable strategy to avoid these vulnerabilities.
The designers of TLS 1.3 have already decided to deprecate the RSA encryption
key exchange. However, as long as compatibility with RSA encryption
cipher suites is kept on older TLS versions these attacks remain a problem.” concludes the research paper.
“To make sure Bleichenbacher attacks are finally resolved we recommend to fully
deprecate RSA encryption based key exchanges in TLS. For HTTPS we believe
this can be done today”
ROBOT Attack: 19-Year-Old Bleichenbacher Attack Leaves Encrypted Web Vulnerable
12.12.2017 thehackernews Attack

A 19-year-old vulnerability has been re-discovered in the RSA implementation from at least 8 different vendors—including F5, Citrix, and Cisco—that can give man-in-the-middle attackers access to encrypted messages.
Dubbed ROBOT (Return of Bleichenbacher's Oracle Attack), the attack allows an attacker to perform RSA decryption and cryptographic operations using the private key configured on the vulnerable TLS servers.
ROBOT attack is nothing but a couple of minor variations to the old Bleichenbacher attack on the RSA encryption protocol.
First discovered in 1998 and named after Swiss cryptographer Daniel Bleichenbacher, the Bleichenbacher attack is a padding oracle attack on RSA-based PKCS#1 v1.5 encryption scheme used in SSLv2.
Leveraging an adaptive chosen-ciphertext attack which occurred due to error messages by SSL servers for errors in the PKCS #1 1.5 padding, Bleichenbacher attack allows attackers to determine whether a decrypted message is correctly padded.
This information eventually helps attackers decrypt RSA ciphertexts without recovering the server's private key, completely breaking the confidentiality of TLS when used with RSA encryption.
"An attacker could iteratively query a server running a vulnerable TLS stack implementation to perform cryptanalytic operations that may allow decryption of previously captured TLS sessions." Cisco explains in an advisory.
In 1998, Bleichenbacher proposed to upgrade encryption scheme, but instead, TLS designers kept the vulnerable encryption modes and added a series of complicated countermeasures to prevent the leakage of error details.
Now, a team of security researchers has discovered that these countermeasures were incomplete and just by using some slight variations, this attack can still be used against many HTTPS websites.
"We changed it to allow various different signals to distinguish between error types like timeouts, connection resets, duplicate TLS alerts," the researchers said.
"We also discovered that by using a shortened message flow where we send the ClientKeyExchange message without a ChangeCipherSpec and Finished message allows us to find more vulnerable hosts."
According to the researchers, some of the most popular websites on the Internet, including Facebook and Paypal, are affected by the vulnerability. The researchers found "vulnerable subdomains on 27 of the top 100 domains as ranked by Alexa."
ROBOT attack stems from the above-mentioned implementation flaw that only affects TLS cipher modes using RSA encryption, allowing an attacker to passively record traffic and later decrypt it.
"For hosts that usually use forward secrecy, but still support a vulnerable RSA encryption key exchange the risk depends on how fast an attacker is able to perform the attack," the researchers said.
"We believe that a server impersonation or man in the middle attack is possible, but it is more challenging."
The ROBOT attack has been discovered by Hanno Böck, Juraj Somorovsky of Ruhr-Universitat Bochum/Hackmanit GmbH, and Craig Young of Tripwire VERT, who also created a dedicated website explaining the whole attack, its implications, mitigations and more.
The attack affects implementations from several different vendors, some of which have already released patches and most have support notes acknowledging the issue.
You will find the list of affected vendors on the ROBOT website.
The researchers have also released a python tool to scan for vulnerable hosts. You can also check your HTTPS server against ROBOT attack on their website.
Still Stealing
12.12.2017 Kaspersky Android
Two years ago in October 2015 we published a blogpost about a popular malware that was being distributed from the Google Play Store. Over the next two years we detected several similar apps on Google Play, but in October and November 2017 we found 85 new malicious apps on Google Play that are stealing credentials for VK.com. All of them have been detected by Kaspersky Lab products as Trojan-PSW.AndroidOS.MyVk.o. We reported 72 of them to Google and they deleted these malicious apps from Google Play Store, 13 other apps were already deleted. Furthermore, we reported these apps with technical details to VK.com. One of these apps was masquerading as a game and was installed more than a million times according to Google Play Store.
One of the apps detected as Trojan-PSW.AndroidOS.MyVk.o was distributed as a game.
There were some other popular apps among them too – seven apps had 10,000-100,000 installations from Google Play and nine apps had 1,000-10,000 installation. All other apps had fewer than 1,000 installations.
App detected as Trojan-PSW.AndroidOS.MyVk.o on Google Play Store
Most of these apps were uploaded to Google Play in October 2017, but several of them were uploaded in July 2017, so they were being distributed for as long as 3 months. Moreover, the most popular app was initially uploaded to the Google Play Store on March 2017, but without any malicious code—it was just a game. Cybercriminals updated this app with a malicious version only in October 2017, having waited more than 7 months to do so!
Most of these apps looked like apps for VK.com – for listening to music or for monitoring user page visits.
App detected as Trojan-PSW.AndroidOS.MyVk.o on Google Play Store
Sure, such apps need a user to login into an account – that’s why they didn’t look suspicious. The only apps whose functionality was not VK-related were game apps. Because VK is popular mostly in CIS countries, cybercriminals checked the device language and asked for VK credentials only from users with certain languages – Russian, Ukrainian, Kazakh, Armenian, Azerbaijani, Belarusian, Kyrgyz, Romanian, Tajik, and Uzbek.
Code where a Trojan checks the device language.
These cybercriminals were publishing their malicious apps on Google Play Store for more than two years, so they had to modify their code to bypass detection. In these apps they used a modified VK SDK with tricky code–users logged on to the standard page, but the cybercriminals used malicious JS code to get the credentials from the login page and pass them back to the app.
Malicious code where a Trojan executes JS code to get VK credentials.
Then the credentials are encrypted and uploaded to the malicious website.
Code where a Trojan decrypts a malicious URL, encrypts stolen credentials and uploads them.
The interesting thing is that although most of these malicious apps had a described functionality, a few of them were slightly different—they also used malicious JS code from the OnPageFinished method, but not only for extracting credentials but for uploading them too.
Malicious code where a Trojan executes JS code to get and upload VK credentials
We think that cybercriminals use stolen credentials mostly for promoting groups in VK.com. They silently add users to promote various groups and increase their popularity by doing so. We have reason to think so because there were complaints from some infected users that their accounts had been silently added to such groups.
Another reason to think so is that we were able to find several other apps on Google Play that were published by the same cybercriminals responsible for Trojan-PSW.AndroidOS.MyVk.o. They were published as unofficial clients for Telegram, a popular messaging app. All of them were detected by Kaspersky Lab products as not-a-virus:HEUR:RiskTool.AndroidOS.Hcatam.a. We notified Google about these apps too and they deleted them from Google Play Store.
App infected with not-a-virus:HEUR:RiskTool.AndroidOS.Hcatam.a on Google Play Store
These apps were not only masquerading as Telegram apps, they were actually built using an open source Telegram SDK and work almost like every other such app. Except one thing – they added users to promoted groups/chats. These apps receive a list with groups/chats from their server. What’s more, they can add users to groups anytime – to do so they steal a GCM token which allows cybercriminals to send commands 24/7.
We also discovered an interesting thing about the malicious website extensionsapiversion.space. According to KSN statistics, in some cases it was used for mining cryptocurrencies by using an API from http://coinhive.com.
CNC
space
guest-stat.com
APPS
Package name MD5
com.parmrp.rump F5F8DF1F35A942F9092BDE9F277B7120
com.weeclient.clientold 6B55AF8C4FB6968082CA2C88745043A1
com.anocat.stelth C70DCF9F0441E3230F2F338467CD9CB7
com.xclient.old 6D6B0B97FACAA2E6D4E985FA5E3332A1
com.junglebeat.musicplayer.offmus 238B6B7069815D0187C7F39E1114C38
com.yourmusicoff.yourmusickoff 1A623B3784256105333962DDCA50785F
com.sharp.playerru 1A7B22616C3B8223116B542D5AFD5C05
com.musicould.close 053E2CF49A5D818663D9010344AA3329
com.prostie.dvijenija 2B39B22EF2384F0AA529705AF68B1192
com.appoffline.musicplayer 6974770565C5F0FFDD52FC74F1BCA732
com.planeplane.paperplane 6CBC63CBE753B2E4CB6B9A8505775389
Cloud Security Startup ShieldX Networks Raises $25 Million
12.12.2017 securityweek IT
ShieldX Networks, a San Jose, Calif.-based cloud security company, announced that it has closed a $25 million Series B round of funding with participation from new investors including FireEye founder Ashar Aziz, Dimension Data and Symantec Ventures.
The company describes its flagship “APEIRO” platform as a solution that delivers Software-Defined Security through a containerized, microservices architecture that helps secure complex, multi-cloud environments.
The scalable cloud-based solution supports real-time threat prevention and helps detect and stop suspicious activities in cloud environments that see high-volume, lateral traffic.
“This funding will allow us to expand our marketing and sales efforts to meet increasing market demands while also keeping a strong focus on product development, including increased automation and intelligence across popular cloud environments that will meet customer demand,” said Dr. Ratinder Paul Singh Ahuja, CEO of ShieldX.
According to the company, its customer list includes organizations such as Alaska Airlines, Iowa State University and Park Holidays.
“Alaska Airlines is actively moving processes to next generation private and public cloud environments in an effort to support the rapid application development and innovation that really delights our guests. We were looking for a security and micro-segmentation solution that could scale and adapt with our new multi-cloud strategy with a comprehensive and consistent security policy across all environments,” said Brian Talbert, Director of Network and Connectivity Solutions at Alaska Airlines. “ShieldX has been an ideal partner throughout the development process by meeting our on premise and cloud needs, rapidly responding to our input, and by supporting our new Microsoft Azure requirements.”
Existing investors, Bain Capital Ventures, Aspect Ventures and FireEye also participated in the Series B round.
Did Major Cyberattacks of 2017 Impact Security Budgets?
12.12.2017 securityweek Cyber
The Effect of WannaCry and NotPetya Outbreaks on Corporate Security Budgets is...Complicated
Despite common perception, the WannaCry and NotPetya outbreaks of 2017 have not -- at least, not yet -- had any marked effect on security budgets.
AlienVault surveyed 233 IT professionals globally to see how roles have changed following the high profile attacks of 2017 that many commentators assumed would act as a wake-up call for senior management. The results disprove this. Just 14% of the respondents have had their budgets for cyber security increased, and only a fifth (20%) have been able to implement changes or projects that were previously put on hold.
"WannaCry and NotPetya are generally believed to have marked a turning point in cyber awareness, but the reality on the ground paints a different picture," comments AlienVault security advocate, Javvad Malik.
The questions posed by AlienVault can loosely be described as three categories: did you get more quantifiable support from senior management; have attitudes towards security changed since the outbreaks; and how has your company reacted to the outbreaks? For the first, 70% of the respondents replied that the outbreaks have made no difference financially to their role; that is, WannaCry and NotPetya have not resulted in the expected security budget increase.
Similarly, there has been little change in attitude towards the security function, either internally to the organization, or externally in the wider marketplace. For example, less than 10% of boards have shown any greater interest in the security role, while more than 60% of respondents replied that the outbreaks have made no difference to the way they are viewed within their organizations. And while 7% of respondents have noticed an increase in new job offers since the outbreaks, 90% say they have made no difference.
Of the questions posed in this survey, two, however, show the practical effect of WannaCry and NotPetya on patching and posture. Two-thirds of the respondents say they are now more up-to-date with patching than they were before the outbreaks, while just one-third say it has made no difference. Further, 58% of respondents carried out a review of their organizations' security posture following the outbreaks (41% did not).
What isn't clear, however, is whether these actions were the result of board pressure or support, or simply the respondents taking their own action from within their existing budgets. The latter is implied by the apparent lack of reaction by boards shown in the other questions -- and this is further supported by a recent PwC survey.
PwC's annual Global State of Information Security Surveys question around 10,000 security professionals in more than 100 different countries. The 2017 survey found that UK security budgets (where firms and especially the NHS were badly hit by WannaCry) stood at around £6.2 million (double the previous year's £3 million average). The latest 2018 survey, announced after the WannaCry and NotPetya outbreaks in October 2017, shows the UK slashing average budgets back down to £3.9 million.
Surprisingly, however, both of these surveys seem to be in contrast to Gartner published only last week. Gartner's Ruggero Contu commented, "Overall, a large portion of security spending is driven by an organization's reaction toward security breaches as more high profile cyberattacks and data breaches affect organizations worldwide. Cyberattacks such as WannaCry and NotPetya, and most recently the Equifax breach, have a direct effect on security spend, because these types of attacks last up to three years."
Noticeably, Gartner increased its global security spend prediction for 2018 by $3 billion over an earlier prediction in August 2017; apparently on the expected effect of WannaCry, NotPetya and the Equifax breach.
Three major firms have now commented on security budgets in the last two months; all of them after the WannaCry and NotPetya outbreaks (with two of them specifically referencing those outbreaks). One (Gartner) says that budgets will increase because of the outbreaks; another (AlienVault) implies 'no change' despite the outbreaks; while the third (PwC) indicates slashed budgets in a country that was severely hit by WannaCry.
This discrepancy highlights the problem with all surveys and predictions. Each one is accurate, but only within the context of its delivery. Gartner based its forecast on the results of a 2016 survey where the highest percentage of respondents said that a security breach is the main security risk influencing their security spending. On this basis, security spend will undoubtedly increase.
The PwC figures covering the UK show a decrease in budget, but only after the previous year's rather dramatic increase; which, according to PwC, took the UK to "over one and a half times more than their global counterparts."
The AlienVault survey questioned a relatively low number of "233 IT professionals." We don't know where they are located, what size company they work for, nor their specific cybersecurity role. AlienVault decided to press-headline the survey results with "Cyber Threats Are Still Being Brushed Aside, Even After WannaCry and NotPetya". (The associated blog title is less dramatic: "The Impact of NotPetya and WannaCry".)
When challenged by SecurityWeek, Malik suggested that the AlienVault and Gartner results may not be so very different. Despite the headline, he told SecurityWeek, "Our results are not based on our opinion, but are the aggregated results of a survey from the Spiceworks community -- which may or may not be representative of the wider market. So, while only 14% have claimed that their budgets for cybersecurity have increased, the broader survey does show that over half of organizations carried out a review of their cyber security posture, two thirds are more up-to-date with patching, and half are using threat intelligence more."
One thing is clear from these differences: if you want to get an accurate picture of what is really going on, you need to look beyond the individual headlines.
Millions Impacted by Credential-Stealers in Google Play
12.12.2017 securityweek Android
During October and November 2017, Kaspersky Lab researchers discovered 85 applications in Google Play that were designed to steal credentials for Russian social network VK.com. One of the malicious applications had more than a million downloads.
While most of the applications were listed in the marketplace in October and gathered fewer than 1,000 installations, some were uploaded in July and proved to be highly popular among users. Seven of the apps had between 10,000 and 100,000 downloads, while nine had between 1,000 and 10,000 installations.
The most popular of the apps masqueraded as a game. It was submitted to Google Play in April 2017 without malicious code in it, but an update in October 2017 added the information stealing capabilities. The game gathered more than 1 million downloads in the seven months it was active on Google Play.
Most of the offending applications were designed to look like apps for the VK.com social platform, supposedly allowing users to listen to music or monitor user page visits. Because apps of this type normally ask for the user to log into their account, they didn’t raise suspicion. Some of the programs were game apps.
The campaign was targeted at VK users only. The platform is highly popular in CIS countries, and the malicious apps first checked the device language and only asked for login credentials if Russian, Ukrainian, Kazakh, Armenian, Azerbaijani, Belarusian, Kyrgyz, Romanian, Tajik, and Uzbek were in use, Kaspersky has discovered.
The actors behind these apps had been publishing their malicious applications in Google Play for over two years, so they had to modify their code to bypass detection, Kaspersky's researchers say.
The recently observed apps used a modified VK SDK with tricky code, which served the standard login page to the user, relied on malicious JS code to steal credentials from the login page and pass them back to the app. The stolen credentials were encrypted and then uploaded to a remote server.
Most of the malicious apps had the described functionality, but some were slightly different: they also used malicious JS code from the OnPageFinished method for extracting credentials and for uploading them.
“We think that cybercriminals use stolen credentials mostly for promoting groups in VK.com. They silently add users to promote various groups and increase their popularity by doing so. We have reason to think so because there were complaints from some infected users that their accounts had been silently added to such groups,” Kaspersky says.
The researchers also note that other Google Play apps submitted by these miscreants were published as unofficial clients for popular messaging app Telegram. Built using an open source Telegram SDK, these apps would work just as any other such software, but they would also add users to promoted groups/chats (based on a list received from the server).
The credential-stealing apps are detected as Trojan-PSW.AndroidOS.MyVk.o. Kaspersky reported 72 of the apps to Google, all of which were removed (13 apps had been removed before). The malicious Telegram clients are detected as not-a-virus:HEUR:RiskTool.AndroidOS.Hcatam.a. They too were removed from Google Play.
Patchwork Cyberspies Adopt New Exploit Techniques
12.12.2017 securityweek CyberSpy
Malware campaigns attributed to the Patchwork cyberespionage group have been using a new delivery mechanism and exploiting recently patched vulnerabilities, Trend Micro warns.
Also known as Dropping Elephant or Chinastrats and believed to be operating out of the Indian subcontinent, the group is said to have been active since 2014. Initially focused on government-associated organizations that have connections to Southeast Asia and the South China Sea, the actor has expanded its target list to include entities in a broad range of industries.
In a new report (PDF) on Patchwork’s latest operations, Trend Micro says that the group has added businesses to its list of targets and that its use of numerous infection vectors and payloads makes it a credible threat.
Campaigns that security researchers have associated with the group over the course of 2017 revealed diverse methods (social engineering hooks, attack chains, and backdoors), along with the adoption of Dynamic Data Exchange (DDE), Windows Script Component (SCT), and exploits for recently reported vulnerabilities.
“These imply they’re at least keeping an eye on other threats and security flaws that they can repurpose for their own ends. Also of note are its attempts to be more cautious and efficient in their operations,” Trend Micro notes.
Targets and attack vectors
The observed campaigns focused on multiple sectors in China and South Asia, but also hit organizations in the U.K., Turkey, and Israel. Using spear-phishing emails, the cyberespionage group targeted high-profile personalities, business-to-consumer (B2C) online retailers, telecommunications and media companies, aerospace researchers, and financial institutions. The United Nations Development Programme was targeted as well.
The spear-phishing emails contained website redirects, direct links, or malicious attachments. Some emails contained direct links to malicious documents hosted on the attacker-owned servers. The group spoofed a news site and used it to divert visitors to socially engineered, malware-ridden documents and was also observed misusing email and newsletter distribution services.
A fake Youku Tudou website (a social video platform popular in China) was used for drive-by downloads. The victim was tricked into downloading and executing a fake Adobe Flash Player update that was, in fact, a variant of the xRAT Trojan.
Patchwork was also observed phishing for credentials to take over a target’s emails and other online accounts. One attack copied a webpage from a legitimate web development company and displayed the fake page to victims alone.
Using Rich Text Format (RTF) documents, the group exploited vulnerabilities such as CVE-2012-1856 – a remote code execution (RCE) in the Windows common control MSCOMCTL, or CVE-2015-1641 – a memory corruption in Microsoft Office. They also exploited the CVE-2014-4114 Sandworm RCE vulnerability in Windows’ Object Linking and Embedding (OLE) via PowerPoint (PPSX) files.
More recent vulnerabilities the actor has been abusing include CVE-2017-0199 – an RCE in Microsoft Office’s Windows OLE, patched in April 2017, and CVE-2017-8570 – an RCE in Microsoft Office patched in July 2017. They were exploited via PowerPoint (PPT) and PPSX files.
The malicious PPSX files exploiting CVE-2017-8570 downloaded a Windows Script Component (SCT) file from a Patchwork-owned server to eventually deliver the xRAT malware.
“Apart from exploit-laden documents, Patchwork also misused DDE to retrieve and execute xRAT in the infected machine. They also sent a document embedded with an executable, which downloads a decoy document and a backdoor, then executes the latter,” Trend Micro explains.
Malware and infrastructure
In addition to using a variety of malicious documents for their nefarious purposes, the Patchwork hackers also deployed a miscellany of backdoors and information stealers onto their victims’ machines. Some of these tools appear to be used solely by this group, the security researchers say.
The threat actor was observed dropping malware such as the NDiskMonitor custom backdoor (believed to be Patchwork’s own, it can list files and logical drives and download and execute files from specified URLs); and Socksbot, which can start Socket Secure (SOCKS) proxy, take screenshots, and run executables and PowerShell scripts.
Malware such as the xRAT remote access tool (its source code is available online) and the Badnews backdoor (potent information-stealing and file-executing malware) were also associated with the group’s activities, as well as a series of file stealers (Taskhost Stealer and Wintel Stealer targeting .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pdf, and RTF files, along with .eml and .msg email messages; as well as versions of file stealers written in AutoIt).
Trend Micro has discovered 30 to 40 IP addresses and domain names used by the group in 2017 and says that each of the servers has had a different purpose. While some were only meant as command and control (C&C) servers that would collect data from the used stealers, others were used only to host phishing websites.
In some cases, the same server was being used for both C&C communication and to host distributing malware (or malicious documents) through hosting content copied from legitimate websites.
The group has been using publicly available PHP scripts for retrieving files from the server without disclosing their real paths, likely to prevent security researchers from finding open directories. Trend Micro also observed the group temporarily removing a file so it could not be retrieved or replacing it with a legitimate one. Sometimes they would display “a fake 302 redirection page to trick researchers into thinking the files are gone.”
“Patchwork is in a vicious cycle, given the group’s habit of rehashing tools and malware. The more those are used, the likelier that they’d be incorporated in the group’s arsenal. The takeaway for enterprises? The gamut of tools and techniques at Patchwork’s disposal highlights the significance of defense in depth: arraying proactive defense to thwart threats at each level—from the gateways, endpoints, and networks to servers,” Trend Micro notes.
Golduck Malware Infects Classic Android Games
12.12.2017 securityweek Android
Several classic game applications in Google Play have been silently downloading and installing a malicious APK file onto Android devices, Appthority reports.
The malicious code was downloaded from a "Golduck" server and installed on devices using a technique called Java reflection. The offending applications, the security company says, were also observed running shell commands and sending SMS messages.
Appthority describes the malicious applications as high quality classic games, including Tank and Bomber. Rated high on Google Play, the games had up to 10.5 million downloads when their nefarious behavior was exposed.
The extra APK was being fetched from hxxp://golduck.info/pluginapk/gp.apk, after which the original game app would load the downloaded code via the /system/bin/dex2oat command.
Appthority's security researchers discovered three folders inside the loaded gp.apk file, each featuring seemly benign names, such as “google.android”, “startapp.android.unity.ads,” and “unity.ads.” The malicious code was hidden inside the google.android folder.
By analyzing the content of the folders, Appthority found code (PackageUtils.class) designed to silently install applications using system permissions.
“These malicious apps seem to be at their initial stage and the code is not obfuscated,” the company notes.
The downloaded payload also contains code for sending SMS messages to users’ contacts. These messages contained game information, thus potentially increasing the chances that the malware would spread to other users.
The Golduck malware, the security company says, could allow attackers to completely compromise the infected device, especially if root is available. The threat also sets the stage for adware-related attacks.
Appthority found two Golduck-infected applications in Google Play and informed Google on the matter on Nov. 20, 2017. All of the offending applications have been taken down by the Android Security team.
To stay protected from the Golduck malware, users are advised to keep an eye on unusual activity on their mobile devices, such as the availability of root access without their intent. SMS charges from unknown sources would also indicate possible infection.
Users are also advised to avoid installing applications from unknown developers and from unofficial app stores.
The applications Appthority has found infected with Golduck include Classic Block Puzzle, Classic Bomber, and Classic Tank vs Super Bomber. Users are advised to uninstall these as soon as possible.
Adobe Patches 'Business Logic Error' in Flash Player
12.12.2017 securityweek Vulnerebility
The only security update released by Adobe this Patch Tuesday addresses a moderate severity regression issue affecting Flash Player.
The vulnerability, tracked as CVE-2017-11305 and described as a “business logic error,” can lead to the unintended reset of the global settings preference file.
There is no evidence of exploitation in the wild and Adobe appears to have discovered the bug on its own.
The flaw affects version 27.0.0.187 and earlier of Flash Player on Windows, Mac, Linux and Chrome OS, and it has been patched with the release of version 28.0.0.126. Microsoft has also updated the Flash Player components used by its software in order to address this issue.
Last month, Adobe addressed a total of 80 vulnerabilities across Flash Player, Photoshop, Connect, Acrobat and Reader, DNG Converter, InDesign, Digital Editions, Shockwave Player, and Experience Manager. Five of the security holes affected Flash.
In October, the company initially announced that it had no Patch Tuesday updates, but a few days later it was forced to release an out-of-band update for Flash Player after Kaspersky Lab researchers noticed that a Middle Eastern threat actor named BlackOasis had been exploiting a zero-day vulnerability to deliver spyware.
The number of flaws found in Flash Player in the past months has decreased considerably, which may be a result of the decision to kill Flash Player by 2020. Nevertheless, as long as the software is still widely utilized, zero-day exploits are highly valuable to malicious actors.
Collection of 1.4 Billion Plain-Text Leaked Passwords Found Circulating Online
12.12.2017 thehackernews Incindent

Hackers always first go for the weakest link to quickly gain access to your online accounts.
Online users habit of reusing the same password across multiple services gives hackers opportunity to use the credentials gathered from a data breach to break into their other online accounts.
Researchers from security firm 4iQ have now discovered a new collective database on the dark web (released on Torrent as well) that contains a whopping 1.4 billion usernames and passwords in clear text.
The aggregate database, found on 5 December in an underground community forum, has been said to be the largest ever aggregation of various leaks found in the dark web to date, 4iQ founder and chief technology officer Julio Casal noted in a blog post.
Though links to download the collection were already circulating online over dark-web sites from last few weeks, it took more exposure when someone posted it on Reddit a few days ago, from where we also downloaded a copy and can now verify its authenticity.
Researchers said the 41GB massive archive, as shown below, contains 1.4 billion usernames, email, and password combinations—properly fragmented and sorted into two and three level directories.
The archive had been last updated at the end of November and didn't come from a new breach—but from a collection of 252 previous data breaches and credential lists.
The collective database contains plain text credentials leaked from Bitcoin, Pastebin, LinkedIn, MySpace, Netflix, YouPorn, Last.FM, Zoosk, Badoo, RedBox, games like Minecraft and Runescape, and credential lists like Anti Public, Exploit.in.
"None of the passwords are encrypted, and what's scary is that we've tested a subset of these passwords and most of the have been verified to be true," Casal said. "The breach is almost two times larger than the previous largest credential exposure, the Exploit.in combo list that exposed 797 million records."
"This new breach adds 385 million new credential pairs, 318 million unique users, and 147 million passwords pertaining to those previous dumps."
The database has been neatly organized and indexed alphabetically, too, so that would-be hackers with basic knowledge can quickly search for passwords.
For example, a simple search for "admin," "administrator" and "root," returned 226,631 passwords used by administrators in a few seconds.
Although some of the breach incidents are quite old with stolen credentials circulating online for some time, the success ratio is still high for criminals, due to users lousy habit of re-using their passwords across different platforms and choosing easy-to-use passwords.
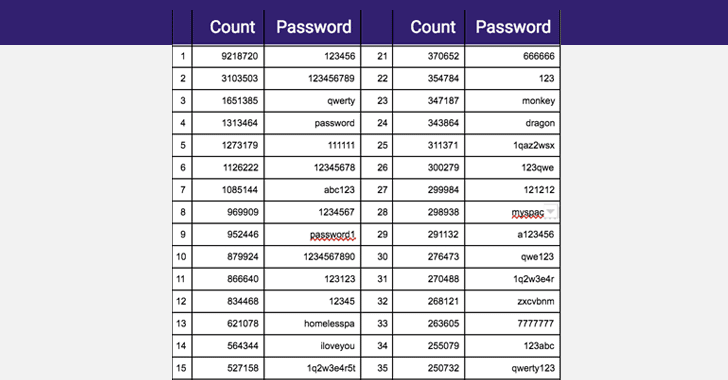
The most common yet worst passwords found in the database are "123456", "123456789", "qwerty," "password" and "111111."
It is still unclear who is responsible for uploading the database on the dark web, but whoever it is has included Bitcoin and Dogecoin wallets for any user who wants to donate.
To protect yourself, you are strongly advised to stop reusing passwords across multiple sites and always keep strong and complex passwords for your various online accounts.
If it's difficult for you to remember and create complex passwords for different services, you can make use of the best password manager. We have listed some good password managers that could help you understand the importance of such tool and choose one according to your requirement.






