
You need to patch your Samba installation as soon as possible
23.11.2017 securityaffairs Vulnerebility
The major Linux distributions rolled out security fixes for a use-after-free error, tracked as CVE-2017-14746, affecting all versions of SAMBA since 4.0.
The major Linux distributions (Red Hat, Ubuntu, Debian and others) rolled out security patches for a use-after-free error, tracked as CVE-2017-14746, affecting all versions of SAMBA since 4.0.
Administrations have to apply the fixes to their distributions, another possibility consists in turning off SAMBA 1, and operation that could hide some difficulties.
According to the project’s advisory, an attacker can use a malicious SMB1 request to control the contents of heap memory via a deallocated heap pointer.
“All versions of Samba from 4.0.0 onwards are vulnerable to a use after free vulnerability, where a malicious SMB1 request can be used to control the contents of heap memory via a deallocated heap pointer. It is possible this may be used to compromise the server.” reads the advisory.
The patch to fix the issue is available at the following URL:
http://www.samba.org/samba/security/
The versions 4.7.3, 4.6.11 and 4.5.15 have been issued to address the vulnerability.
The maintainers of the project have also issued patches for older versions at:
http://samba.org/samba/patches/.
The advisory includes also a workaround, it consists in preventing SMB1 access to the server by setting the parameter:
server min protocol = SMB2
to the [global] section of your smb.conf and restart smbd.
Unfortunately, the advisory warns of problems, older clients to be unable to connect to the server.
Administrators running vulnerable versions are advised to apply the patch as soon as possible.

There is also another flaw, tracked as CVE-2017-15275, that affects all the versions from 3.6.0 onwards that has been fixed by Samba.
According to the advisory, the server may return the contents of heap allocated memory to the client revealing “password hashes or other high-value data”.
“There is no known vulnerability associated with this error, but uncleared heap memory may contain previously used data that may help an attacker compromise the server via other methods. Uncleared heap memory may potentially contain password hashes or other high-value data.” reads the advisory.
Patched versions have been made available here.
Intel potvrzuje: v Management Engine jsou vážné bezpečnostní díry
23.11.2017 Root.cz Zranitelnosti
Intel potvrdil, že bezpečnostní audit provedený na jeho procesorech odhalil vážné bezpečnostní hrozby. Ty mohou vést až ke spuštění cizího nepodepsaného kódu hluboko v procesoru, kde na něj operační systém nevidí.
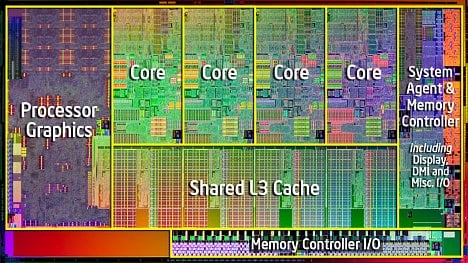
Když pánové Maxim Goryachy a Mark Ermolov ze společnosti Positive Technologies oznámili, že na prosincové konferenci Black Hat odhalí bezpečnostní slabiny v procesorech Intel, nechal jejich výrobce udělat velký audit technologií Intel Management Engine (ME), Intel Trusted Execution Engine (TXE) a Intel Server Platform Services (SPS).
Výsledkem je objevení většího množství bezpečnostních chyb uvnitř firmware, který běží na novějších procesorech. V těch je hluboko (ring –3) ukrytý operační systém MINIX, který provádí spoustu činností a dovoluje počítač spravovat na dálku. Goryachy a Ermolov tvrdí, že jimi objevené chyby dokáží ovládnout počítač i ve vypnutém stavu.
Problém přitom postihuje poměrně širokou škálu procesorů, konkrétně těch s firmwarem ME verzí 11.0, 11.5, 11.6, 11.7, 11.10 a 11.20, firmware SPS verze 4.0 a TXE verze 3.0. Verze jednotlivých komponent je obvykle možné najít v BIOS/UEFI, kde pravděpodobně najdete jen jednu z těchto technologií.
ME je možné najít na klientských stanicích a levných serverech bez samostatného řídicího rozhraní (IPMI). SPS je pak přítomno ve velkých serverech s tímto rozhraním a TXE je určeno především pro tablety a zařízení s nízkým příkonem.
Nebezpečné rozhraní je možné najít na následujících procesorech:
6th, 7th & 8th Generation Intel® Core™ Processor Family
Intel® Xeon® Processor E3–1200 v5 & v6 Product Family
Intel® Xeon® Processor Scalable Family
Intel® Xeon® Processor W Family
Intel® Atom® C3000 Processor Family
Apollo Lake Intel® Atom Processor E3900 series
Apollo Lake Intel® Pentium™
Celeron™ N and J series Processors
Podle Intelu je možné chyby zneužít k lokálnímu napadení počítače a spuštění libovolného kódu mimo dosah uživatele a operačního systému. Je také možné zhoršit stabilitu počítače nebo způsobit pád operačního systému.
Intel vydal testovací utilitu pro Linux a Windows, která prozkoumá váš hardware a software a pomůže vám odhalit bezpečnostní problémy v konkrétním počítači.
Výrobci už začali vydávat aktualizace firmware : Dell Client, Dell Server, Intel® NUC, Intel® Compute Stick a Intel® Compute (stránka podpory Intel), Lenovo. Oprava spočívá v aktualizaci BIOS/UEFI, který se při startu postará o nahrání opraveného firmware do procesoru.
Více informací zatím k dispozici není, podle Intelu jde o proaktivní řešení, které má za cíl významně zlepšit bezpečnost. Detaily budeme pravděpodobně znát až po konferenci Black Hat, zatím jen víme, že je ohroženo poměrně velké množství počítačů nejrůznějších typů a určení, protože v nich běží proecsory Intel.
Matthew Garrett
@mjg59
Thoughts on the latest Intel ME vulnerabilities: based on public information, we have no real idea how serious this is yet. It could be fairly harmless, it could be a giant deal.
11:01 PM - Nov 20, 2017
7 7 Replies 158 158 Retweets 201 201 likes
Twitter Ads info and privacy
Dobrou zprávou je, že podle dostupných informací je ke zneužití chyb potřeba mít fyzický přístup k počítači. Intel ale poznamenává, že teoreticky může přijít nový vektor útoku, který dovolí zaútočit s administrátorskými právy v operačním systému. Vzhledem k tomu, že některé zde zmíněné problémy dovolují si práva navýšit, je možné, že bude stačit běžný uživatelský účet, ze kterého pak povede cesta dál.
Remotely Exploitable Flaw Found In HP Enterprise Printers—Patch Now
23.11.2017 thehackernews Vulnerebility
Security researchers have discovered a potentially dangerous vulnerability in the firmware of various Hewlett Packard (HP) enterprise printer models that could be abused by attackers to run arbitrary code on affected printer models remotely.
The vulnerability (CVE-2017-2750), rated as high in severity with 8.1 CVSS scale, is due to insufficiently validating parts of Dynamic Link Libraries (DLL) that allows for the potential execution of arbitrary code remotely on affected 54 printer models.
The security flaw affects 54 printer models ranging from HP LaserJet Enterprise, LaserJet Managed, PageWide Enterprise and OfficeJet Enterprise printers.
This remote code execution (RCE) vulnerability was discovered by researchers at FoxGlove Security when they were analyzing the security of HP's MFP-586 printer (currently sold for $2,000) and HP LaserJet Enterprise M553 printers (sold for $500).
According to a technical write-up posted by FoxGlove on Monday, researchers were able to execute code on affected printers by reverse engineering files with the ".BDL" extension used in both HP Solutions and firmware updates.
"This (.BDL) is a proprietary binary format with no publicly available documentation," researchers said. "We decided that reverse engineering this file format would be beneficial, as it would allow us to gain insight into exactly what firmware updates and software solutions are composed of."
Since HP has implemented the signature validation mechanism to prevent tampering with the system, the researchers failed to upload a malicious firmware to the affected printer.
However, after some testing researchers said that "it may be possible to manipulate the numbers read into int32_2 and int32_3 in such a way that the portion of the DLL file having its signature verified could be separated from the actual executable code that would run on the printer."
The researchers were able to bypass digital signature validation mechanism for HP software "Solution" package and managed to add a malicious DLL payload and execute arbitrary code.
FoxGlove Security has made the source code of the tools used during its research available on GitHub, along with the proof-of-concept (PoC) malware payload that could be remotely installed on the printers.
The actions performed by their proof of concept malware are as follows:
It downloads a file from http[://]nationalinsuranceprograms[.]com/blar
Executes the command specified in the file on the printer
Waits for 5 seconds
Repeat
FoxGlove Security reported this remote code execution vulnerability to HP in August this year, and the vendor fixed the issue with the release of new firmware updates for its business and enterprise printers.
To download the new firmware update, visit the HP website in your web browser, and select Support from the top of the page and select Software & drivers. Now, enter the product name or model number in the search box, then scroll down in the search results to firmware and download the necessary files.
Google gathers Android users’ location data even when location services are disabled
23.11.2017 securityaffairs Android
Google is secretly gathering location data from billions of Android users, the news is disconcerting and once again raise the debate about user’s privacy.
The disconcerting discovery was made by researchers from Quartz.
Big G has been caught collecting location data on every Android device owner in the past 11 months. The worse news is that the Google is gathering location data even when location services are completely disabled.
“Since the beginning of 2017, Android phones have been collecting the addresses of nearby cellular towers—even when location services are disabled—and sending that data back to Google. The result is that Google, the unit of Alphabet behind Android, has access to data about individuals’ locations and their movements that go far beyond a reasonable consumer expectation of privacy.” states Quartz.
The experts discovered that Android smartphones have been collecting the addresses of nearby cellular towers, an information that could be used to track the location of mobile devices with the “Cell Tower Triangulation” technique.
When an Android device is within the range of a new cell tower, it gathers the cell tower address and sends this data back to Google when the device is connected via a WiFi network or cellular data network.
A source familiar with the matter said Quartz that the cell tower addresses were being sent to Google after a change in early 2017 to the Firebase Cloud Messaging service.
The Firebase Cloud Messaging service is the component responsible for collecting location data that manages push notifications and messages on the operating system, unfortunately it cannot be disabled.
“Even devices that had been reset to factory default settings and apps, with location services disabled, were observed by Quartz sending nearby cell-tower addresses to Google.” continues Quartz media.
“Devices with a cellular data or WiFi connection appear to send the data to Google each time they come within range of a new cell tower. When Android devices are connected to a WiFi network, they will send the tower addresses to Google even if they don’t have SIM cards installed.”
Quartz contacted Google for a comment and a spokesman for the company replied that the location-sharing practice was implemented to improve its service.
“We began looking into using Cell ID codes as an additional signal to further improve the speed and performance of message delivery.” said Google spokesperson.

“It has pretty concerning implications,” explained Bill Budington, a software engineer at the Electronic Frontier Foundation. “You can kind of envision any number of circumstances where that could be extremely sensitive information that puts a person at risk.”
According to the experts there is no doubt, the fact that the Google Android system is collecting location data is a complete violation of user’s privacy.
Why Google collects data from Android devices when all location services are disabled?
Reading the Google privacy policy about location sharing, it is possible to note that the company will collect location information from devices that use its services, but there is no reference to data gathering from Android devices when all location services are disabled.
“When you use Google services, we may collect and process information about your actual location,” Google’s privacy policy reads.
“We use various technologies to determine location, including IP address, GPS, and other sensors that may, for example, provide Google with information on nearby devices, Wi-Fi access points, and cell towers.”
Google declared that never used or stored this location data it collected and that it is now taking steps to end this practice.
According to Google, Android phones will no longer collect location data by the end of this month.
Many vendors will release fixes for flaws in the Intel Management Engine
23.11.2017 securityaffairs Vulnerebility
Almost any PC vendor announced the imminent release of fixes for the flaws in Intel Management Engine, but many of them will be available only in 2018.
Intel has started to issue security updated to fix multiple flaws in Intel’s CPUs, unfortunately many of them will not be available to the end-users until 2018.
The tech giant has fixed multiple vulnerabilities in Intel’s Management Engine, Server Platform Services, and Trusted Execution Engine.
An attacker can exploit the vulnerabilities to remotely access the vulnerable machine and perform in a stealth way malicious activities, including to deliver a malware.
This type of flaws is very insidious because any countermeasure implemented at the operating system level is not able to detect malicious operation because Active Management Technology (AMT) has direct access to the computer’s network hardware. Malicious traffic is routed directly to the Management Engine and passed on to AMT, but the local OS never sees it.
The flaws were first found by the experts at the security firm Positive Technologies that published a detailed analysis of the attack scenarios.
Almost any PC vendor announced the imminent release of security fixes, but many of them still haven’t distributed them.
Acer announced the future availability of the security updates for 240 models, far more than ten models listed in the Lenovo’s advisory.
Panasonic announced the availability of the fixes for six models by the end of January 2018, while Dell will release the updates between Christmas and February 2nd, 2018, on February 2, in fact, the vendor plans to address the problems for four models.
Fujitsu distributed the patches for Japanese and EMEA customers, there no info related to the release date for clients in the rest of the world.
Good news for HPE customers, the company has already made the fixes available.
The time necessary to release the fixes is not surprising, patch management is a complex and time consuming activity, especially when the updates must be distributed to a large number of machines.
Intel, for example, will not able to fix its NUC, ComputeStick and ComputeCard products, before December 2017.
Other PC makers have not published advice related to the Intel flaws and the availability of security patches.
Consider also the many flawed CPUs were currently used in other appliances, including network attached storage.
Crooks set up a fake Symantec Blog to spread the macOS Proton malware
23.11.2017 securityaffairs Apple
A new strain of the notorious macOS Proton malware is spreading through a blog spoofing the legitimate blog of the security firm Symantec.
The attackers used the same domain registration information of the original site, except for the email address.
The SSL digital certificate for the site is a legitimate certificate issued by Comodo instead of the Symantec’s certificate authority.
The attackers created a the fake blog symantecblog[dot]com that mirrored content from the original website. The experts from Malwarebytes discovered that a post about a new version of CoinThief malware was promoting the application called “Symantec Malware Detector,” that was used to distribute the OSX.Proton.
“The malware is being promoted via a fake Symantec blog site at symantecblog[dot]com. The site is a good imitation of the real Symantec blog, even mirroring the same content. The registration information for the domain appears, on first glance, to be legitimate, using the same name and address as the legitimate Symantec site. The email address used to register the domain is a dead giveaway,” reads the analysis published by Malwarebytes.
Threat actors spread links to the fake blog on Twitter using both fake and legitimate compromised accounts. The Symantec Malware Detector application acts like a dropper.
The malicious Symantec Malware Detector application displays a simple window with the Symantec logo requiring the authorization to perform a system check.If the victim agrees to run the check, the admin password is requested, allowing the malware stealing the password. Next, the app displays a progress bar to trick victims into believing that it is scanning the computer, instead it is installing the Proton malware in the background.

Once installed, the Proton malware gathers user information, such as the admin password and other personally-identifying information (PII). The malicious code saves all data to a hidden file.
“The malware also captures and exfiltrates things like keychain files, browser auto-fill data, 1Password vaults, and GPG passwords. Since the malware has phished the user’s password, the hackers will be able to decrypt the keychain files at a minimum.” continues the analysis.
Once this “dropper” app has been run, the following paths are created on the target system:
/Library/LaunchAgents/com.apple.xpcd.plist
/Library/.cachedir/
/Library/.random/
The Proton executable is dropped in the .random directory and is kept running by the com.apple.xpcd.plist launch agent. The stolen data is stored in the. cachedir folder.
In order to prevent future infections, Apple has revoked the certificate used to sign the malware.
“Fortunately, Apple is aware of this malware and has revoked the certificate used to sign the malware. This will prevent future infections by the Symantec Malware Detector. Revoking the certificate will not, by itself, do anything to protect a machine that is already infected,” states the report.
Experts believe that the Proton malware will continue to circulate, Macs will continue to be the targets of an increasing amount of malware.
Over 400 Popular Sites Record Your Every Keystroke and Mouse Movement
23.11.2017 thehackernews Hacking
How many times it has happened to you when you look for something online and the next moment you find its advertisement on almost every other web page or social media site you visit?
Web-tracking is not new.
Most of the websites log its users' online activities, but a recent study from Princeton University has suggested that hundreds of sites record your every move online, including your searches, scrolling behavior, keystrokes and every movement.
Researchers from Princeton University's Centre for Information Technology Policy (CITP) analyzed the Alexa top 50,000 websites in the world and found that 482 sites, many of which are high profile, are using a new web-tracking technique to track every move of their users.
Dubbed "Session Replay," the technique is used even by most popular websites, including The Guardian, Reuters, Samsung, Al-Jazeera, VK, Adobe, Microsoft, and WordPress, to record every single movement a visitor does while navigating a web page, and this incredibly extensive data is then sent off to a third party for analysis.
"Session replay scripts" are usually designed to gather data regarding user engagement that can be used by website developers to improve the end-user experience.
However, what's particularly concerning is that these scripts record beyond the information you purposely give to a website—which also includes the text you type out while filing a form and then delete before hitting 'Submit.'
"More and more sites use "session replay" scripts. These scripts record your keystrokes, mouse movements, and scrolling behaviour, along with the entire contents of the pages you visit, and send them to third-party servers," Princeton researcher Steven Englehardt wrote in a blog post under the No Boundaries banner.
"Collection of page content by third-party replay scripts may cause sensitive information such as medical conditions, credit card details and other personal information displayed on a page to leak to the third party as part of the recording. This may expose users to identity theft, online scams, and other unwanted behaviour."
Most troubling part is that the information collected by session replay scripts cannot "reasonably be expected to be kept anonymous." Some of the companies that provide session replay software even allow website owners to explicitly link recordings to a user's real identity.
Services Offering Session Replay Could Capture Your Passwords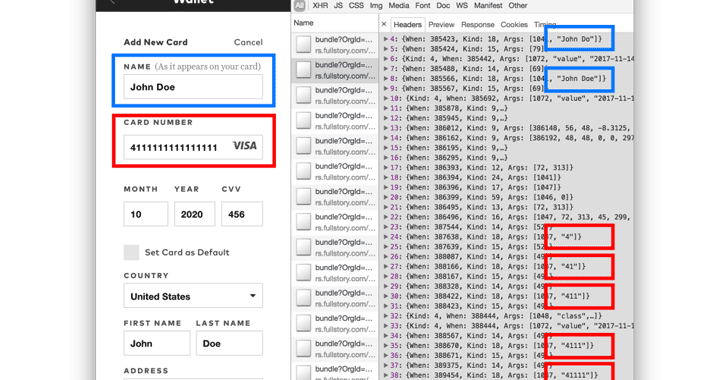
The researchers looked at some of the leading companies, including FullStory, SessionCam, Clicktale, Smartlook, UserReplay, Hotjar, and Yandex, which offer session replay software services, and found that most of these services directly exclude password input fields from recording.
However, most of the times mobile-friendly login forms that use text inputs to store unmasked passwords are not redacted on the recordings, which ends up revealing your sensitive data, including passwords, credit card numbers, and even credit card security codes.
This data is then shared with a third party for analysis, along with other gathered information.
"We found at least one website where the password entered into a registration form leaked to SessionCam, even if the form is never submitted," the researcher said.
The researchers also shared a video which shows how much detail these session recording scripts can collect on a website's visitor.
World's Top Websites Record Your Every Keystroke
There are a lot of significant firms using session replay scripts even with the best of intentions, but since this data is being collected without the user's knowledge or visual indication to the user, these websites are just downplaying users' privacy.
Also, there is always potential for such data to fall into the wrong hands.
Besides the fact that this practice is happening without people's knowledge, the people in charge of some of the websites also did not even know that the script was implemented, which makes the matter a little scary.
Companies using such software included The Guardian, Reuters, Samsung, Al-Jazeera, VK, Adobe, Microsoft, WordPress, Samsung, CBS News, the Telegraph, Reuters, and US retail giant Home Depot, among many others.
So, if you are logging in one of these websites, you should expect that everything you write, type, or move is being recorded.
Uber in Legal Crosshairs Over Hack Cover-up
23.11.2017 securityweek Hacking
Two US states on Wednesday confirmed they are investigating Uber's cover-up of a hack at the ride-sharing giant that compromised the personal information of 57 million users and drivers.
Uber purportedly paid data thieves $100,000 to destroy the swiped information -- and remained quiet about the breach for a year.
That decision evidently came despite a promise by the firm to "adopt leading data security protection practices" in a settlement with New York attorney general Eric Schneiderman.
Schneiderman and his counterpart in Connecticut, George Jepsen, on Wednesday told AFP that Uber is the target of probes in their states over the hidden hack.
"None of this should have happened, and I will not make excuses for it," Uber chief executive Dara Khosrowshahi, who took over at the company in August, said Tuesday.
Two members of the Uber information security team who "led the response" that included not alerting users about the data breach were let go from the San Francisco-based company effective Tuesday, according to Khosrowshahi.
The Uber chief said he only recently learned that outsiders had broken into a cloud-based server used by the company for data and downloaded a "significant" amount of information.
Stolen files included names, email addresses, and mobile phone numbers for riders, and the names and driver license information of some 600,000 drivers, according to Uber.
Uber paid the hackers $100,000 to destroy the data, not telling riders or drivers whose information was at risk, according to a source familiar with the situation.
Co-founder and ousted chief Travis Kalanick was advised of the breach shortly after it was discovered, but it was not made public until Khosrowshahi learned of the incident, the source confirmed.
In early 2016, Schneiderman announced a settlement with Uber stemming from an investigation into the company's handling and protection of riders' personal information.
The probe was prompted by word of a hack, and by reports that Uber executives were able to track the locations of riders in real-time using a tool known internally as "God View."
The settlement required Uber to better protect rider data, and pay $20,000 for failing to tell drivers about the 2014 data breach in a timely manner.
Experts found a way to exploit HP Enterprise printers to hack into company networks
23.11.2017 securityaffairs Hacking
Researchers at FoxGlove Security have found a potentially serious remote code execution vulnerability in some of HP’s enterprise printers.
HP dedicates significant efforts in designing secure printing systems, a recent marketing campaign launched by the firm shows the dangers of vulnerable printers for corporate networks.
HP launched new enterprise LaserJet printers back in 2015 and introduced several security improvements across the time.
Experts from FoxGlove Security tested an HP PageWide Enterprise 586dn multi-functional printer (MFP) and an HP LaserJet Enterprise M553n printer.
HP printers hacking
The team used a hacking tool dubbed PRET (PRinter Exploitation Toolkit) developed by researchers from Ruhr-Universität Bochum in Germany.
At the time, the tool was used by the author to find security vulnerabilities in 20 printer models manufactured by Dell, Brother, Konica, Samsung, HP, OKI, and Lexmark.

The printers were affected by flaws related to common printing languages, PostScript and PJL, used in most laser printers. The flaws are not a novelty, according to the experts, they have existed for decades.
Now experts from FoxGlove used the PRET tool to find a path traversal flaw that allowed them to access the content of any print job, including those jobs protected by a PIN code. The same team found vulnerabilities that can be exploited by attackers to manipulate the content of print jobs and reset devices to factory settings.
In order to find a remote code execution (RCE) the researchers reverse engineered the firmware extracted from the HP printer, bypassing anti-tampering mechanisms implemented by the vendor.
The team analyzed firmware updates and HP Software Solutions discovering they leverages the OXP platform and SDK to extend a printer’s functionality. Both Solutions and firmware updates are delivered as a single bundle (.BDL) file that must be digitally signed.
“PJL is a language that computers will speak with the printer when submitting print jobs. This language has also been extended to have the ability of performing some administrative tasks.” stated the analysis published by the experts.
“One of the capabilities of PJL is very limited management of files on the printer. For example, it is possible to store and delete files, but only in a very specific location, a small “jail” on the filesystem that it should not be possible for a user speaking PJL to escape from:”
The experts failed to upload a malicious firmware to the device due to the signature validation checks, but they devised possible attack vectors.
“A BDL file modified in this way was uploaded to the printer and confirmed working, however no malicious changes to code could be implemented just yet. When we tried to replace any of the DLL files in the ZIP we began getting DLL signature validation errors.” continues the analysis.
The researchers succeeded in cracking signature validation for Solutions files and uploading a malicious DLL and execute arbitrary code.
The experts shared the source code of the tools used during the tests, including the proof-of-concept (PoC) malware the exploited.
The team reported the discovery to HP on August 21 and the tech giant is committed to release a security update this week.
ERPScan Launches AI-Driven SAP Security Platform
22.11.2017 securityweek Cyber
ERPScan, a company that specializes in security solutions for SAP and Oracle enterprise resource planning (ERP) products, announced this week the launch of a new AI-driven cybersecurity platform for SAP systems.
The new product, ERPScan SMART Cybersecurity Platform for SAP, is designed to help organizations prevent, detect, and respond to threats targeting their SAP systems.
The platform’s assessment module allows security teams to identify vulnerabilities, custom code issues, misconfigurations, and segregation of duties (SoD) violations that could introduce risks. The prevention component enables employees to address issues and apply virtual patches.
The SMART Cybersecurity Platform for SAP includes modules for detecting malware and other malicious activity, and helps incident response teams quickly obtain information needed to contain a breach. The product also provides C-level executives and managers a comprehensive view of their organization’s security posture.
According to ERPScan, the platform leverages machine learning, specifically deep learning, to create a baseline for normal user behavior, which it then uses to detect potentially malicious activity carried out by both insiders and external entities.
The new platform combines the functionality of existing ERPScan SAP tools with machine learning and new modules for detection, response and monitoring.
“This solution is a real breakthrough for us,” said Alexander Polyakov, founder and CTO of ERPScan. “We spent the last two years on developing a solution that would be able to not only cover all areas of SAP cybersecurity, but also be intuitive by adding machine learning and adaptive interfaces. Our secret team of data scientists and machine learning experts battled with the experienced Research team and taught the system to detect advanced attacks and anomalous user behavior. Now we are ready to present the new generation of SAP cybersecurity products, and it's so exciting.”
Polyakov told SecurityWeek that the product is currently being tested by some early adopters, and expects it to become generally available in the second half of January 2018.
ERPScan has made significant contributions to improving SAP security, not only through its products, but also by informing the vendor of many vulnerabilities discovered by its researchers.
Apple Patches USB Code Execution Flaw in macOS
22.11.2017 securityweek Apple
One of the vulnerabilities addressed by Apple in its latest set of security patches for macOS is an arbitrary code execution flaw, which could be exploited via malicious USB devices.
Discovered by Trend Micro security researchers and reported to Apple in April this year, the issue resides in fsck_msdos, a system tool designed to check for and fix errors in devices formatted with the FAT filesystem.
The security researchers discovered that because the tool is automatically invoked by macOS when a device using the FAT filesystem (such as a USB disk or an SD card) is inserted, a security bug could allow malicious devices to execute arbitrary code when they are connected to a Mac.
The vulnerability is created by a memory corruption issue and its exploitation could lead to an attacker taking full control of a vulnerable system, Trend Micro says.
“We do not believe that this attack has been used in the wild. We strongly recommend that users update their software to address this flaw, as well as the others that were part of this update cycle,” the security researchers note.
Trend Micro found that malicious code could modify a byte containing the high bits of a memory address with an arbitrary value and set it to point to another address.
“If the target address is sprayed with a malformed dosDirEntry structure, arbitrary code execution is now possible. This can potentially allow an attacker to take over the vulnerable device,” the security researchers note.
Tracked as CVE-2017-13811, the vulnerability was addressed by Apple with the release of macOS High Sierra 10.13.1 (and Security Update 2017-001 Sierra, and Security Update 2017-004 El Capitan), which resolved nearly 150 vulnerabilities, including three KRACK-related flaws.
Trend Micro explains that fsck_msdos is used in other BSD-based operating systems, as well as in Android. Because of that, other vendors were also informed of the vulnerability, including Google.
However, it appears that the issue won’t be resolved in Android, because “fsck_msdos runs under a very restricted SELinux domain.” Nevertheless, Google is apparently looking into addressing the bug in a future release of the operating system, the researchers note.
To mitigate the impact of this vulnerability, IT administrators are advised to restrict USB access to devices, especially considering that this is a method frequently used by malware to enter targeted systems. They should also consider physical controls for especially sensitive devices.
'Advanced' Cyber Attack Targets Saudi Arabia
22.11.2017 securityweek BigBrothers
Saudi authorities said Monday they had detected an "advanced" cyber attack targeting the kingdom, in a fresh attempt by hackers to disrupt government computers.
The government's National Cyber Security Centre said the attack involved the use of "Powershell", but it did not comment on the source of the attack or which government bodies were targeted.
"The NCSC has detected a new Advanced Persistent Threat (APT) that is targeting Saudi Arabia," the agency said in a statement, adding the attack sought to infiltrate computers using email phishing techniques.
Saudi Arabia has come under frequent cyber attacks, including "Shamoon", the aggressive disc-wiping malware employed in attacks against the Saudi energy sector in 2012.
Saudi Aramco, the world's biggest oil company, was among the firms hit by Shamoon, in what is believed to be the country's worst cyber attack yet.
US intelligence officials at the time said they suspected a link to the kingdom's regional rival Iran.