
Počítačoví piráti se zaměřili na uživatele oblíbené směnárny s kybernetickými měnami Poloniex.
Necurs Returns With New Scarab Ransomware Campaign
25.11.2017 securityweek Ransomware
The world's largest spam botnet, Necurs, is delivering a new version of the Scarab ransomware. The campaign started at 07:30 UTC on Thanksgiving Day. By 13:30 UTC, security firm Forcepoint had already blocked more than 12.5 million Necurs emails.
The new campaign was also noted by F-Secure. "This morning at 9AM (Helsinki time, UTC +2) we observed the start of a campaign with malicious .vbs script downloaders compressed with 7zip," blogged researcher Paivi Tynninen on Thursday.
"Based on our telemetry," noted Forcepoint researchers, "the majority of the traffic is being sent to the .com top level domain (TLD). However, this was followed by region-specific TLDs for the United Kingdom, Australia, France and Germany."
Necurs, weaponizing between 5 and 6 million hosts per month, was originally best known for distributing the Dridex banking trojan, the Locky ransomware, and 'pump-and-dump' schemes. This year it has also spammed out Jaff and GlobeImposter ransomware. Scarab is new.
Scarab was first spotted in June 2017 by Michael Gillespie, creator of ID Ransomware (a service that allows users to submit a ransom note to discover which ransomware has infected them). According to F-Secure, Scarab's code "is based on the open source ìransomware proof-of-concept called HiddenTear."
Necurs is delivering a malicious VBS script downloader compressed with 7zip. As in previous campaigns, the script contains a number of Games of Thrones references, such as the strings 'Samwell' and 'JohnSnow'. The final payload is Scarab.
The email itself is typical Necurs: minimal text body with business-related subjects; in this case suggesting the attachment contains images of scanned documents. Popular subjects are 'Scanned from...' with either Lexmark, HP, Cannon or Epson added.
"The download domains used as part of this campaign were compromised sites which have previously been used by Necurs-based campaigns," notes Forcepoint. It is probable that many organizations will have these domains blacklisted, but the sheer size of the campaign will likely lead to many new Scarab infections.
If the downloader runs and Scarab is installed, it encrypts files and appends a new extension ending in '[suupport@protonmail.com].scarab'. The email address part of the extension is the same contact email provided in the ransom note.
The ransom note, with the filename ìIF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXTî, is dropped into each affected folder. This note does not specify the amount of ransom required, saying instead that the amount will depend upon the speed of response from the victim. It does, however, offer to decrypt three files free of charge to prove the decryption will work: "Before paying you can send us up to 3 files for free decryption."
Počítačové piráty lákají virtuální měny
24.11.2017 Novinky/Bezpečnost Podvod
Počítačové piráty stále častěji lákají nejrůznější virtuální měny, jako jsou například velmi populární bitcoiny. Na rozdíl od klasických bankovních účtů totiž transakce s virtuálními mincemi na internetu nejsou nijak monitorovány, ukradené peníze je tak prakticky nemožné vystopovat.
V minulých měsících se například kyberzločinci zaměřili na uživatele oblíbené směnárny s kybernetickými měnami Poloniex. Snažili se jim podstrčit falešnou aplikaci, díky které získají přístup k jejich účtům. Jejich virtuální mince, které je možné směnit za skutečné peníze, by pak mohli snadno odcizit. Upozornili na to bezpečnostní experti z antivirové společnosti Eset.
Šířily dvě podvodné aplikace
Právě Eset odhalil dvě podvodné aplikace v internetovém obchodě Google play, které byly určeny pro zařízení s operačním systémem Android. Obě se přitom snažily vypadat jako legitimní programy internetové směnárny Poloniex.

Počítačoví piráti se zaměřili na uživatele oblíbené směnárny s kybernetickými měnami Poloniex.
FOTO: repro poloniex.com
Útočníci se tak snažili vylákat od svých obětí přihlašovací údaje, aby získali přístup nejen k účtům na Poloniexu, ale také k e-mailovým schránkám na Gmailu. „Okolo kryptoměn je v současné době hodně rozruchu a počítačoví zločinci se pokoušejí chopit jakékoli nové příležitosti, která se jim naskytne,“ uvedl Miroslav Dvořák, technický ředitel společnosti Eset.
„Ať již v uvozovkách krádeží výpočetního výkonu zařízení uživatelů za účelem těžení kryptoměn přes prohlížeče internetu nebo tím, že infi kují nedostatečně aktualizované počítače. Také se snaží využívat falešné webové stránky a aplikace zaměřené na získávání osobních dat,“ doplnil Dvořák.
Napálily se tisíce lidí
První škodlivá aplikace byla umístěna do Google Play pod jménem „POLONIEX“ a nabízel ji vývojář „Poloniex“. Vtip byl právě v tom, že název falešné aplikace byl napsán velkými písmeny. Od konce srpna do poloviny září si ji nainstalovalo navzdory varovným hodnocením od dalších uživatelů a negativním recenzím na 5000 lidí.
Druhá aplikace „POLONIEX EXCHANGE“ od vývojáře „POLONIEX COMPANY“ se na Google Play objevila 15. října 2017 a zaznamenala 500 stažení, než ji Google na základě oznámení od společnosti Eset odstranil. Také zde byl název falešné aplikace psán velkými písmeny.
Kolik uživatelů nakonec své přihlašovací údaje dalo všanc kyberzločincům a kolik si počítačoví piráti na úkor podvedených lidí vydělali, není v tuto chvíli jasné. Tak velké množství uživatelů se nicméně napálilo patrně kvůli tomu, že Poloniex je jednou z nejvyužívanějších směnáren kryptoměn na světě. Obchodovat je zde možné s více než 100 různými typy virtuálních mincí.
Těžba láká i piráty
Popularitě kybernetických mincí nahrávají stále rostoucí kurzy, ale také fakt, že za pořízení virtuálních mincí nemusí zaplatit ani korunu. Pokud totiž uživatelé mají dostatečně výkonný počítač, mohou si nainstalovat speciální software a s jeho pomocí kryptoměny doslova těžit – tento program totiž používá předem nastavené výpočty, jejich výsledkem je zisk virtuálních mincí. Za ty je pak možné klidně nakupovat prakticky cokoliv.
Jenže právě toho jsou si vědomi také počítačoví piráti. Ti stále častěji instalují podobný software do cizích počítačů místo klasických virů. Podobně zotročené stroje pak kyberzločincům vydělávají peníze, aniž by o tom majitelé počítačů měli ponětí.
A rozhodně nejde o nějaký zanedbatelný počet počítačů. Podle analýzy společnosti AdGuard totiž podvodníci takovýmto způsobem infikovali více než 500 miliónů PC.
Vydělávají velké peníze
Tyto stroje generují útočníkům nemalé peníze. I když přesné odhady nejsou k dispozici, pravděpodobně si ale touto cestou vydělají počítačoví podvodníci podle nejstřízlivějších odhadů několik stovek tisíc korun každý den.
Jak je z řádků výše patrné, virtuálních měn existuje mnoho. Jednou z nejstarších a aktuálně nejpopulárnějších jsou bitcoiny. Ty vznikly už v roce 2009, větší popularitě se ale těší v posledních letech.
Tato měna byla vytvořena tak, aby se nedala ovlivňovat žádnou vládou ani centrální bankou. Kybernetické mince „razí“ síť počítačů se specializovaným softwarem naprogramovaným tak, aby uvolňoval nové mince stabilním, ale stále klesajícím tempem. Počet mincí v oběhu má dosáhnout nakonec 21 miliónů, což má být kolem roku 2140.
Děravý Intel Management Engine lze nahradit minimalistickým Linuxem a Go
24.11.2017 Root.cz Zranitelnosti
Uvnitř procesorů Intel běží skrytě plnohodnotný operační systém včetně síťového stacku a web serveru. Zbavit se ho zcela není možné, ale můžeme ho nahradit něčím minimalistickým a méně děravým.
Už víme, že uvnitř procesorů Intel běží velmi mocný firmware založený na operačním systému MINIX. Už v něm byly nalezeny první vážné bezpečnostní chyby, které mohou vést až k ovládnutí celého počítače na dálku. Není se čemu divit, MINIX není maličký firmware nutný k běhu procesoru, ale plnohodnotný operační systém, který obsahuje například podporu pro IPv4 a IPv6, ovladače, souborový systém nebo třeba web server.
Běží navíc ve velmi privilegovaném režimu, ke kterému nemá běžný operační systém přístup, takže běží zcela skrytě a může provádět prakticky cokoliv za zády uživatele. Není divu, že se uživatelé takové věci ve svém počítači bojí a velké firmy v čele s Googlem se jí snaží zbavit. Protože není snadné takovou věc vypnout, přichází ke slovu jiné řešení: otevřené, minimalistické a postavené na Linuxu.
Proprietární software ve vašem CPU
Detaily celého projektu popsal Ronald Minnich z Google na pražské Embedded Linux Conference Europe. To je člověk, který stojí za vývojem nástroje Coreboot, který byl dříve znám pod názvem LinuxBIOS. Jeho cílem je nahradit uzavřený BIOS v základních deskách něčím otevřeným. Principiálně jde tedy o podobný problém, ale na zcela jiné softwarové vrstvě.
Hlavní problém podle Minnicha je v tom, že Linux ztratil kontrolu nad hardwarem. V 90. letech byl operační systém pánem celého stroje a mohl provádět cokoliv. Dnes jsou mezi ním a hardwarem minimálně další dvě a půl jádra. Mají vyšší práva než operační systém a mohou manipulovat s ním i s hardware. Navíc jsou uzavřená a samozřejmě také úspěšně exploitovatelná.
Co víc, exploity je možné zapsat přímo do paměti v desce, takže zůstávají persistentní a není možné je odstranit. V takovém stavu zbývá jen desku zahodit. Pokud svému počítači věříte, jste šílenci, řekl na své přednášce Minnich. Na vašem procesoru totiž běží ohromné množství proprietárního software, o kterém nevíte téměř nic a nemůžete ho nahradit. Naštěstí existují lidé, kteří pracují na tom, abychom přestali být šílení a získali trochu příčetnosti.
Co mi to tu běží?
Pokud chceme pochopit rozvrstvení operačních systémů ve svém procesoru, musíme se zabývat takzvanými Ringy (kruhy). Ty tvoří jednotlivé vrstvy a dovolují řídit procesy ve vyšších kruzích. Tradičně nejnižším, a tedy hlavním, kruhem býval ten s číslem nula. V něm běží jádro operačního systému, které řídí činnost uživatelského software ve vyšších kruzích – dnes typicky v tom s číslem tři.
Aby bylo možné provozovat jednoduše hardwarovou virtualizaci, přišel do nových procesorů (společně s Intel VT-x a AMD AMD-V) kruh s číslem –1. V něm běží hypervizor, tedy virtualizační hostitel, který si pak založí kruhy nula a v nich spouští běžné operační systémy. Má tedy vyšší privilegia a je pro ně neviditelný.
Ještě nad touto vrstvou pak existuje Ring –2, který se stará o samotný hardware a ke kterému nemají vyšší kruhy vůbec přístup. V něm běží 16bitové mikrojádro SMM starající se o zdroje v CPU a 64bitové UEFI jádro. Tyhle věci se starají o to, aby fungovaly například různé „hardwarové“ funkce počítačů – když třeba zaklapnete displej u notebooku, probudí se právě tyhle kusy software a zajistí třeba uspání.
Tady jsme si dlouho mysleli, že to končí. Ukázalo se ale, že existuje ještě privilegovanější režim označený analogicky jako Ring –3. To je ta věc, které se lidé bojí, říká Minnich. V něm totiž běží další plnohodnotný operační systém postavený na MINIX 3. Jednoduše to shrnuje následující schéma: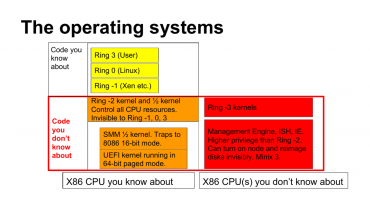
Operační systémy ve vašem procesoru
V kruzích –2 a –3 běží různý software, oba ale mají společné to, že se jedná o plnohodnotné operační systémy se spoustou vlastností: IPv4 a IPv6 stack, souborové systémy, ovladače pro různá zařízení (USB, disky, síťové karty a další) a také třeba web servery. Intel Management Engine (dále jen ME) totiž potřebuje znát souborový systém, protože může být použit k dálkovému přepsání operačního systému na disku. Jak Ronald Minnich připomíná, je možné to udělat i s vypnutým počítačem – pokud je zapojen v zásuvce a v síti.
Všude samá díra
Uvnitř navíc běží spousta komponent, jejichž smyslu nerozumíme. Mají rozličné názvy jako „full network manageability“, „regular network manageability“, „manageability“ a „outbreak containment heuristic“. Už v roce 2010 bylo ukázáno, že většina těchto komponent má bezpečnostní mezery [PDF] a část chyb stále ještě není opravená.
Že je to realita ukázal Intel na začátku roku, kdy opravil sedm let starou díru. Ta umožňovala na dálku do webového serveru v ME poslat heslo o nulové délce a získat plný přístup k dálkové správě počítače. Intel sice tvrdí, že nezaznamenal žádné pokusy o zneužití, ale v praxi je těžké uhlídat miliardu procesorů a není možné sledovat provoz všude. Navíc při takovém množství nikdy nebudou záplatovány všechny systémy.
O úroveň výše běží už zmíněný SMM, který původně sloužil ke správě napájení u starých systému s DOS. Přebírá od operačního systému řízení v případě, že přijde některá ze zajímavých událostí (SMI). Zajímavé je, že jakmile je SMM aktivován, už není možné jej vypnout. Ukousne si 8 MB systémové paměti, do které přestane vidět operační systém. Navíc pro něj existuje celá řada exploitů.
Ve stejném kruhu běží ještě zmíněné UEFI, což je prý extrémně komplexní kernel, pro nějž dopisují funkce jednotliví dodavatelé počítačů. Podle Minnicha ovšem jejich programátoři úplně dobře nerozumí všem pravidlům takového kódu, proto dělají chyby. Výsledkem je, že jsou tam obrovské gigantické díry, kterými je dovnitř možné dostat exploit. Těch existuje velké množství, navíc UEFI aktualizuje sám sebe, takže je možné vytvořit perzistentní malware, který se usídlí uvnitř UEFI a bude se při dalších pokusech o aktualizace tvářit, že všechno funguje správně.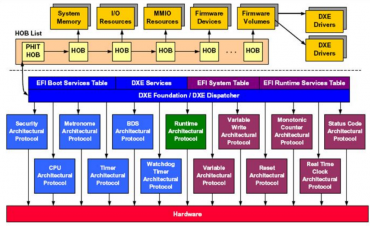
Komponenty UEFI
Jak to celé opravíme?
Co s takovou bezpečnostní noční můrou můžeme dělat? Přejít na AMD není řešením, protože i tam existují uzavřené části, do kterých nevidíme. Vznikl proto projekt, který se snaží minimalizovat privilegovaný software uvnitř procesoru, aby ubylo kódu, snížilo se riziko bezpečnostních děr a omezily se schopnosti těchto potenciálně děravých firmwarů.
Výsledkem je projekt s názvem Non-Extensible Reduced Firmware, neboli nerozšiřitelný zmenšený firmware, zkráceně NERF. Nerozšiřitelný je, protože se vývojáři domnívají, že právě rozšiřitelnost je hlavním problémem originálního software.
Hlavním cílem je udělat minimální firmware, se kterým by počítač správně bootoval a fungoval. Zároveň s tím přichází podstatně větší otevřenost a možnost kdykoliv velmi rychle opravit případné chyby. Prakticky je to realizováno tak, že z původního firmware jsou odstraněny téměř všechny komponenty – zrušit ME úplně není možné, počítač by bez něj nenabootoval a pokud už ano, za 30 minut by se sám vypnul. Dobrou zprávou ale je, že většinu komponent ME je možné odstranit.
Vznikla proto velmi okleštěná náhrada, která nebude obsahovat web server, síťové stacky a ovladače hardware. Standardní ME zabírá 5 MB z integrované 8MB flash paměti, ale tuto velikost se podařilo redukovat na pouhých 300 KB. Kromě toho jsou z ME a UEFI odstraněny také schopnosti vlastní aktualizace, takže o případné flashování se postará sám NERF.
Nad vším sedí Linux
NERF se skládá z několika částí: osekanou ME ROM, minimalizovanou UEFI ROM a vypnutým SMM. Nad tím vším sedí linuxové jádro s uživatelským prostředím napsaným v Go (u-root). Neexistuje příliš mnoho důvodů proč mít SMM zapnuté, pokud by však některá z jeho funkcí byla v budoucnu potřeba, dokáže ji zastat Linux.
Během bootu počítače nejprve proběhnou dvě fáze (security neboli SEC a pre-EFI initialization čili PEI), které jsou kompletně proprietární a jejich funkce nebudou nikdy zveřejněny. Poté ale už nastupuje driver execution environment (DXE), což je naopak dobře dokumentovaná funkce starající se například o výběr operačního systému a jeho zavedení. O tuto část už se může postarat integrované linuxové jádro.
Některé části svázané přímo s hardwarem pravděpodobně nebudeme schopni nikdy nahradit, ale cílem je hlavně vyměnit ty velké komplexní komponenty, které ukrývají nejvíce bezpečnostních děr a jsou proto největším problémem. V tuto chvíli už je možné NERF sestavit a nabootovat, zatím je nejlepších výsledků dosahováno na serverech od firem Dell, MinowMax a OCP nodech.
Použití tohoto alternativního firmware také dovoluje výrazně zjednodušit správu. Zatímco v případě UEFI je nutné mít pro každý hardware jiné sestavení, použití univerzálního linuxového jádra většinu těchto problému ruší. Samozřejmě se předpokládá, že budou prováděny různá jádra pro různé systémy, ale už teď se daří startovat stejný firmware na malých deskách MinnowMax i na velkých OCP systémech.
Uživatelská část celého firmware je napsána v jazyce Go, který je bezpečnější než čisté C, takže lze předpokládat menší množství bezpečnostních děr. Výsledkem je 5,9MB initramfs, který obsahuje kompletní kód, kompilátor i toolchain. Jednotlivé funkce se kompilují až při použití, což zabere asi 200 ms. Podle Minnicha je to dobré proto, že je kód stále k dispozici v otevřené podobě vhodné k auditu.
Pro případy, kdyby ve flash paměti nebylo dost místa nebo by procesor byl na kompilaci příliš pomalý, je možné použít režim u-root, který je podobný BusyBoxu. Jde také o jednu velkou binárku, na kterou jsou nalinkovány jednotlivé názvy příkazů. V tomto formátu má pak celý userspace jen 2 MB a jeho provoz je velmi rychlý i na pomalých strojích. Protože je celý software velmi malý a jednoúčelový, zkracuje také dobu bootu celého počítače.
Ronald Minnich předpokládá, že se první počítače s NERF a u-root objeví už v roce 2018. Firmy chtějí používat firmware, kterému rozumí. Chtějí také bootovat rychle a bezpečně, říká Minnich.
Firefox will notify users who visit sites that suffered a data breach
24.11.2017 securityaffairs Security
Mozilla developer revealed the Firefox browser will soon include a new feature to notify users who visit sites that suffered a data breach
Firefox browser is going to introduce a new security feature to make the users’ experience online more secure, it will warn users if they visit websites that have experienced data breaches.
The news was revealed by the Mozilla developer Nihanth Subramany and it was confirmed by the presence of a recently-released GitHub repo titled “Breach Alerts Prototype.”
“This is an extension that I’m going to be using as a vehicle for prototyping basic UI and interaction flow for an upcoming feature in Firefox that notifies users when their credentials have possibly been leaked or stolen in a data breach.” states the description published on GitHub.
The developer has teamed with haveibeenpwned.com as data source related for data breaches.
The new feature is still not complete, the developer explained that in its current state it is in no way meant to represent actual production code, or how the feature will work or look like when it ships.
He also listed the following basic goals for the new security feature:
Inform users about data breaches through the Firefox UI – for example, a notification when they visit a site (or maybe when they focus a form on a login page) known to have recently been breached.
Expose documentation/educational information about data breaches in the Firefox UI – for example, a “Learn more” link in the notification mentioned above leading to a support page.
Offer a way for interested users to learn about and opt into a service that notifies them (e.g. via email) when they may be affected by breaches in the future.
FireFox data breach notification service
The developer also approached privacy concerns since the users would need to supply an email address to receive security notifications.
“The third goal brings up some privacy concerns, since users would need to supply an email address to receive notifications. Who is the custodian of this data? Can we avoid sending user data to haveibeenpwned.com? Can we still offer useful functionality to users who opt out of subscribing their email address? While the project is still in infancy, the idea is to offer as much utility as possible while respecting the user’s privacy.” added the developer.
The notifications will also include old data breaches such as the ones suffered by Adobe.com or LinkedIn.com several years ago.
Android commercial spyware
24.11.2017 Kaspersky Android
There’s certainly no shortage of commercial spying apps for Android, with most positioned as parental control tools. In reality, however, these apps barely differ from spyware, with the exception perhaps of the installation method. There’s no need to even resort to Tor Browser or other darknet activity either – all you need to do is type something like “android spy app” into Google.
They are called ‘commercial’ because anyone can buy an app like this for just a few dollars.
Kaspersky Lab mobile products detect this sort of commercial Android spyware as not-a-virus:Monitor.AndroidOS.*. According to our telemetry, the popularity of these apps has been growing in recent years:
Unique users attacked by not-a-virus:Monitor.AndroidOS.*, 2016-2017
That’s why we decided to take a closer look at this controversial type of mobile software.
Features
Almost all commercial spyware apps are installed by manually accessing the target’s phone, and this is the only big difference between these apps and classic malicious spyware like DroidJack or Adwind. Customers have to download the app, install it and enter credentials that are received after purchasing. After that, the spying app becomes invisible on the phone. Installation usually only takes a couple of minutes.
Regular installation process (https://tispy.net/install-guide.html)
Some of these tools use device admin features to gain persistence and self-protection on the target’s phone.
So what does the customer get? Features may vary, but some of them are present in almost all these kinds of apps:
Stealing SMSs
Stealing calls (logs/recordings)
GPS tracking
Stealing browser data (history/bookmarks)
Stealing stored photos/videos
Stealing address books (with emails and even photos sometimes)
And if you’re still not impressed, then check out the actual feature lists (in addition to the above) of some popular commercial spyware for Android. We have added the infamous Pegasus APT and Droidjack spyware to our comparison table below to show the difference in features between them and monitoring apps. Pegasus is an advanced persistent threat, created by NSO Group. Droidjack is an RAT that was sold some time ago for a $210 lifetime license. This tool is more akin to TrojWare, because of features such as remote installation and customization of your own C&C server. However, even after several users in European countries were arrested, malware author Sanjeevi claimed that Droidjack is “very useful for users who use it legally”. He stated that “Droidjack is a parental tool for remote Android administration. It is strictly meant for that and no other reasons”. Anyone who breaks these rules, adds Sanjeevi, will have their license revoked.
Stealing emails Stealing surrounding voice Stealing scheduled tasks/ calendar/ notes Stealing social media/IM data Backdoor behavior (e.g., remote control) Photo/ video/ screenshot capture Keylogging Stealing clipboard
Pegasus + + + + + + + –
DroidJack – + – + + + – –
TiSpy + + + + – + + +
Exaspy + + + + + + – –
iKeyMonitor + + – + – + + +
Mobistealth + + + + – + + –
mSpy + – + + + – + –
iSpyoo + + + + + – – –
SpyHuman – + – + + + – –
TheftSpy – + – + + + – –
TheTruthSpy – + – + + – + –
OneSpy + + – + – + – –
Highster Mobile + – – + – – – –
Spymaster Pro – – – + – + – –
DroidWatcher – – – + – + – –
This comparison table shows that the difference between known sophisticated spyware and some commercial monitor apps is not that great and, in some cases, monitor applications can even grab more private user information.
Exaspy is an especially interesting case. This is a classic monitor application with a regular manual-access installation method (you have to enter license credentials after installation to start spying):
However, after news about a high-profile victim – a senior executive at a company – this monitor app is considered illegal for now. Note that there are a lot of similar apps that can result in cases like this.
Some special features (spying on social media apps, for example) only work on a rooted device, but the list is still impressive. The ‘Stealing social media/IM data’ feature is particularly important. It means that the spyware is able to attack other social media or messenger apps (depending on the specific product), for example, Facebook, Viber, Skype, WhatsApp, etc. As a result, an attacker can observe messenger conversations, feeds and other personal data from the victim’s social media profile.
These products use the same techniques as standard malicious spyware to steal data, and sometimes on a bigger scale. For example, here is a fragment of code from a commercial application called OneSpy with a list of external attacked applications:
As you can see, the commercial app is interested in all popular social media apps and messengers.
It’s ‘legal’
Above we mentioned that some commercial Android spyware apps like Exaspy were recognized as illegal after investigations. But many commercial spyware applications are still considered legitimate because, according to their sites, they were created “for everyone who needs a helping hand in protection of their loved-ones, their children, family and employees”.
Some of them claim that their products are ‘100% undetectable’. This may be true for the naked eye, but definitely not for our products.
But why do we think commercial spyware poses a danger and why do we detect it? There are several reasons:
Almost all commercial spyware is distributed from its own site and landing pages. This results in vendors prompting users to enable the “Allow install of non-market applications” setting. This setting is very important for device safety because enabling it makes an Android device vulnerable to malware installation. For security reasons this method of distribution is contrary to Google policy.
Source: http://ispyoo.com/ispyoo-spy-android-installation-guide/
Because some spying features only work on a rooted device, many vendors recommend rooting the targeted device. This opens the door for potential malware infection, and moreover, device rooting is contrary to Google policy.
Source: https://ikeymonitor.com/rooted-vs-non-rooted-features-for-android
Not every vendor can guarantee the safety of personal data, and that applies not only to hacker attacks but also to simple methods of product security.
The last point is very important and our concerns aren’t baseless. I analyzed one commercial spyware app, investigating the vendor’s main site and C&C server. I soon found lots of files that had been uploaded to the server and that turned out to be users’ personal data collected by the app. Private files were stored on the server without any protection and could be accessed by anyone.
uh… security?
Many users of spyware apps who want to monitor the private lives of their relatives simply don’t understand that they may not be the only ones who will have access to such information.
To sum up, installing such apps, even on your child’s device, is a risky step that could lead to malware infection, data leaks or other unpleasant consequences. In our products we use a special technology for Android OS that helps detect dangerous apps capable of violating a customer’s data privacy. There is one simple and very important tip for everyone – always protect your phone with a password, PIN or fingerprint, so an attacker won’t be able to manually access your device.
Self-Replicating Malware exploits MS Office Built-In feature
24.11.2017 securityaffairs Virus
An Italian researcher from the security firm InTheCyber devised an attack technique to create self-replicating malware hidden in MS Word documents.
A few weeks ago, a security researcher reported a flaw that affects all versions of Microsoft Office that could be exploited by attackers to spread macro-based self-replicating malware.
Microsoft promptly implemented a security mechanism in MS Office that prevents such kind of attacks.
Now the researcher from the security firm InTheCyber Lino Antonio Buono has found has devised an attack technique to bypass the security control implemented by Microsoft and create self-replicating malware hidden in MS Word documents.
Buono reported the flaw to Microsoft in October, but unfortunately, the tech giant doesn’t consider the issue a security vulnerability. Microsoft explained that the feature exploited by the Italian researcher was implemented to work exactly in this way.
The worst news is that crooks are already exploiting the same attack vector devised by Buono.
A couple of days ago, malware researchers from Trend Micro detailed a recently discovered macro-based self-replicating ransomware dubbed ‘qkG‘ that exploits the same MS office feature used by Buono in his attack technique.
“Further scrutiny into qkG also shows it to be more of an experimental project or a proof of concept (PoC) rather than a malware actively used in the wild. This, however, doesn’t make qkG less of a threat. As the qkG samples demonstrated, its behaviors and techniques can be fine-tuned by its developer or other threat actors.” states the analysis published by Trend Micro.
“When we first saw samples of it in VirusTotal last November 12, for instance, it didn’t have a Bitcoin address yet. It had one only two days later, along with a routine that encrypts a document on a specific day and time. The next day, we saw a qkG sample with a different behavior (viz., not encrypting documents with a specific file name format).”
The qkG ransomware relies on the Auto Close VBA macro technique to execute malicious macro when victim closes the document.
Although the first variant of the qkG ransomware did include a Bitcoin address, the latest sample analyzed by Trend Micro includes it and demands $300 in BTC.
Experts observed that the Bitcoin address hasn’t received any payment yet, a circumstance that suggest crooks still haven’t spread it in the wild.
Experts also discovered the qkG ransomware is currently using the hardcoded password “I’m QkG@PTM17! by TNA@MHT-TT2” that allows to decrypt the files.
Buono shared a video PoC of the attack technique with colleagues at The Hacker News. The video shows how an MS Word document embedding malicious VBA code could be used to deliver a self-replicating multi-stage malware.
Microsoft has untrusted external macros by default and to restrict default programmatic access to Office VBA project object model. Users can manually enable “Trust access to the VBA project object model,” if required.
Once the “Trust access to the VBA project object model” setting is enabled, MS Office trusts all macros and automatically runs any code without showing any security warning or requiring user’s permission.

Buono discovered that it is possible to enabled/disabled the “Trust access to the VBA project object model” setting by editing a Windows registry, eventually enabling the macros to write more macros without the user’s consent and knowledge.
The malicious MS Doc file crafted by Buono that is used in the video PoC first edits the Windows registry and then injects the same macro payload (VBA code) into every doc file that the victim manipulates.
The Buono’s attack technique just sees attackers tricking victims into run macros included in a bait document.
“In order to (partially) mitigate the vulnerability it is possible to move the AccessVBOM registry key from the HKCU hive to the HKLM, making it editable only by the system administrator.” Buono suggests as mitigation strategy.
Artificial Intelligence is Important for Cybersecurity, But It’s Not Enough
24.11.2017 securityaffairs Cyber
The advent of Artificial Intelligence has brought with it a new scope for cybersecurity. Why the artificial intelligence is important for cybersecurity?
In my last blog, I discussed AI and Big Data. Now, I am going to explain about AI and Cybersecurity.
The advent of Artificial Intelligence has brought with it a new scope for cybersecurity. After all, an intelligent security system is expected to overcome any sophisticated threats. However, many security experts believe that AI is a double-edged sword and hence it could become dangerous at an epic level if it gets into the wrong hands. Let us make a quick analysis on the unison between cybersecurity and AI.
Cybersecurity is the need of the day. As if we didn’t have enough to worry about with terrorists running wild – always looking to inflict damage – we now have to worry about Cybercriminals as well. And in many cases, they can be a lot more dangerous than your average terrorist.
The significance of having a perfect cybersecurity strategy or solution has grown over the years. All the credit goes to the proliferation of smart devices on the Internet. Also, because of the growing endpoints that are always connected to the cyberspace, cybercriminals now have a plethora of opportunities to infiltrate devices.

Not only do hackers have more entry points to breach, but they also have more sophisticated tools to penetrate even into highly-secured devices or networks. How are they doing it? By mass producing sophisticated malware.
According to the 22nd threat report by Symantec, it is found that over 300 million malware were detected in 2016 alone. Not only this! John – the contributor at thebestvpn, shared the shocking statistic that one in every 131 emails contains a malware. The massive figure presents quite a shocking blow to businesses who then rush to come up with a more potent cybersecurity solution.
Moreover, we can’t ignore the fact that with the passage of time, cybercriminals have become smarter and more adept at countering traditional security practices. A survey conducted in 2017 of 70 professional hackers and pen testers found that 60% of hackers claim they can compromise a system within just 6 hours. Plus, over 80% of the hackers and testers said they could remain hidden from the network for 100 days after stealing sensitive data.
To combat such threats, we need to come up with a disruptive security technology that is not only efficient, but also proactive, faster and more intelligent. One such disruption that can prove itself an ideal security solution is Artificial Intelligence (AI).
Artificial Intelligence & Cybersecurity: A Perfect Unison or a Calamity
When we talk about Artificial Intelligence, the first thing that pops into our mind are technologies like Tesla’s self-driving cars or the Amazon Echo. This is because we take AI only as a “Buzzword” and nothing else.
Regardless, AI can offer more firepower when it comes to cybersecurity. It can cover the lack of manpower that we see in this highly complex field. Likewise, it can run things faster and hence detect threats before they could compromise a system and inflict damage.
Although there is a lot of potential in Artificial Intelligence for tackling complex cyber threats for good, there are some aspects that make it a double-edged sword. Before we move on to the other aspects of AI, let’s take a look at why it seems to be a great cybersecurity tool.
The Significance of AI as a Security Solution
IT experts at a company have a lot on their hands to monitor and analyze. They are always challenged with sifting through loads of security logs and activities, finding security threats that could pose a serious threat and coming up with mitigation strategies to contain it.
Moreover, there are weeks and months of logs that need to be scrutinized and vetted for security purposes. Identifying any abnormality in such vast amount of data and then formulating the right solution require not only more manpower but also more tools and resources.
However, an AI-powered machine can greatly assist IT personnel in monitoring, tracking and detecting anomalies efficiently.
Ryan Permeh, Cylance Chief Scientist, said in an online interview conducted by CSOOnline, “Historically, an AV researcher might see 10,000 viruses in a career. Today there are over 700,000 per day.” He further states that his security firm uses AI to tackle such attacks.
Apart from that, AI as a security tool can help with the lack of manpower that the cybersecurity industry is currently facing. Over 40% of organizations claim that they suffer from a “problematic shortage” of talent in cybersecurity.
Shahid Shah, the CEO of Netspective Communications, claims that there is a lot of skill shortage in different cybersecurity areas such as advanced malware prevention, compliance, IDS/IPS, identity and access management, etc.
Shah further states that by implementing AI, security firms can depend on “computers to do the grunt work and leave humans to the decision-making.”
Why AI Currently Isn’t a ‘Perfect’ Cybersecurity Solution
If AI can be used to shield our systems or networks from cyber-attacks, it is rational to expect the technology being used for more attacks. Shortly, when AI becomes more automated and developed, we might see more sophisticated cyber-attacks carried out by intelligent malware or viruses.
In fact, Endgame’s security expert, Hyrum Anderson has proved just that at the DEF CON 2017. The team demonstrated an intelligent application that can re-engineer a malware and make it undetectable to even a smart antivirus. A group of researchers was successful in circumventing the protective layers of the AI-powered antivirus with its AI-powered malware 16% of the time.
The research was conducted to show that even AI can have blind spots that could be used to compromise systems.
The demonstration Hyrum Anderson presented isn’t the only research that indicates the negative implications of relying solely on AI. In fact, another research conducted by a security firm, Cylance, predicts AI “weaponization” soon.
According to the research, 62% of security experts believe that AI-powered cyber-attacks will increase in the near future, and hence the technology will be used as an intelligent cyber weapon.
“While AI may be the best hope for slowing the tide of cyberattacks and breaches, it may also create more advanced attacker tactics in the short-term,” says Cylance.
Final Say
AI-powered systems may reinforce our cybersecurity infrastructure, enabling our workforce to detect, contain, mitigate or stop cyber threats. However, relying solely on an intelligent technology that could be molded at our will can be dangerous. Plus, an AI-enabled attack may prove to be detrimental at an epidemic level.
Advanced cyber attack hits Saudi Arabia to disrupt government computers
24.11.2017 securityaffairs Cyber
Saudi Arabia announced to have detected an “advanced” cyber attack targeting the kingdom with the intent to disrupt government computers.
On Monday, Saudi authorities announced to have detected an “advanced” cyber attack targeting the kingdom. According to the experts at the Saudi National Cyber Security Centre, the attackers aimed to disrupt government computers.
The attackers leveraged the Powershell, but at the time of writing Government experts it did not comment on the source of the attack.
PowerShell is extremely powerful and that attackers are increasingly using it in their attack methods. PowerShell is a default package that comes with Microsoft Windows OS and hence it is readily available on the victim machines to exploit.
“Powershell is Predominantly used as a downloader”
The most prominent use of PowerShell, that is observed in the attacks in-the-wild, is to download the malicious file from the remote locations to the victim machine and execute it using commands like Start-Process, Invoke-Item OR Invoke-Expression (-IEX) file OR downloading the content of the remote file directly into the memory of the victim machine and execute it from there.
Back to the attacks that hit Saudi computers, the NCSC speculates the involvement of an APT that used spear phishing attacks to infiltrate computers in the Kingdom.
“The NCSC has detected a new Advanced Persistent Threat (APT) that is targeting Saudi Arabia,” the agency said in a statement.
Saudi Arabia was targeted several times by APT, the most clamorous attack was conducted with the Shamoon wiper in 2012 against computers in the Saudi energy sector in 2012.
Computers at Saudi Aramco, one of the world’s biggest oil companies, was disrupted by Shamoon in what is believed to be the country’s worst cyber attack yet.
In the attack against Saudi Aramco Shamoon wipe data on over 30,000 computers and rewrite the hard drive MBR (Master Boot Record) with an image of a burning US flag.
The first team that discovered the malware was Kaspersky Lab that had analyzed some instances of the threat linked to the “wiper agent” due to the presence of a module of a string with a name that includes “wiper” as part of it.
Early this year, Saudi authorities warned of a new wave of attacks that leveraged the Shamoon 2 malware targeting the country.
In January, the Saudi Arabian labor ministry had been attacked and also a chemical firm reported a network disruption.

According to security experts, the threat actor behind the Shamoon attacks was likely working on behalf of the Iranian government in 2012.
Device Manufacturers Working on Patches for Intel Chip Flaws
24.11.2017 securityweek Vulnerebility
Acer, Dell, Fujitsu, HPE, Lenovo, Intel and Panasonic are working on releasing patches for the recently disclosed vulnerabilities affecting Intel CPUs, but it could take a while until firmware updates become available to all customers.
After external researchers identified several potentially serious vulnerabilities affecting its Management Engine (ME) and Active Management Technology (AMT), which allow users to remotely manage computers, Intel has decided to conduct a comprehensive review of the products.
The analysis revealed the existence of several vulnerabilities in ME, Trusted Execution Engine (TXE) and Server Platform Services (SPS). The security holes can be leveraged to impersonate the ME, SPS and TXE services and impact the validity of local security feature attestation, execute arbitrary code without being detected by the user or the operating system, and crash the system or make it unstable.
Exploitation is currently not trivial and an attack often requires local access to the vulnerable device. However, remote hacking over the network may be possible as well in certain circumstances, and researchers warned that attacks may become easier to conduct once repeatable exploits are developed.
Intel has made available firmware patches for device manufacturers using its affected processors, which include some Core, Xeon, Atom, Pentium and Celeron CPUs present in millions of systems.
However, it will take some time until all users will receive the necessary patches. Intel itself only expects to release BIOS updates for its affected NUC, Compute Stick, and Compute Card mini PCs and development kits in December. More than 30 device models are impacted by the vulnerabilities.
Acer has published a list of roughly 240 affected notebooks and desktop PCs, including Packard Bell, Gateway, Aspire, Veriton, TravelMate, Predator, and Extensa models. The company has yet to determine when firmware updates will become available.
Dell has published an advisory for laptops and desktop PCs, and a separate advisory for PowerEdge servers. Over 180 laptops and desktop PCs are affected by the security holes, including many Alienware, Inspiron, Latitude, OptiPlex, Precision, Vostro, and XPS models.
Dell expects to release firmware updates for some of the impacted products next month or in January 2018, but for most systems the target date has yet to be determined. In the meantime, the company has advised users to “ensure that systems are physically secured where possible, and follow good security practices to ensure that only authorized personnel have hands-on access to devices.”
Fujitsu has also published an advisory, informing users that more than 30 of its mainboards, 43 Esprimo desktop PCs, 11 Celsius workstations, 10 Primergy servers, and 67 LifeBook, Stylistic and Celsius laptops and tablets are affected. The vendor’s investigation is ongoing so new models could be added to the list at any time.
Updates are already available for some of the impacted Fujitsu products, but a release date has yet to be confirmed for many of them.
HPE has advised users to install the available firmware updates for affected ProLiant and Synergy servers. The company also pointed out that attacks requiring physical access to the motherboard can be detected using the optional hood latch. In addition, attacks should be blocked by the vendor’s Silicon Root of Trust feature, which ensures that unauthorized firmware cannot be run on a machine.
Lenovo has already released patches for many of its products and more updates are expected to become available this week.
Panasonic has also published an advisory to inform customers that its rugged laptops and tablets are affected by the vulnerabilities in Intel chips. Some of the impacted devices will receive updates in January 2018.
Intel has released a tool that can be used to check if a system is affected by the vulnerabilities.
MS Office Built-In Feature Could be Exploited to Create Self-Replicating Malware
23.11.2017 thehackernews Virus
Earlier this month a cybersecurity researcher shared details of a security loophole with The Hacker News that affects all versions of Microsoft Office, allowing malicious actors to create and spread macro-based self-replicating malware.
Macro-based self-replicating malware, which basically allows a macro to write more macros, is not new among hackers, but to prevent such threats, Microsoft has already introduced a security mechanism in MS Office that by default limits this functionality.
Lino Antonio Buono, an Italian security researcher who works at InTheCyber, reported a simple technique (detailed below) that could allow anyone to bypass the security control put in place by Microsoft and create self-replicating malware hidden behind innocent-looking MS Word documents.
What's Worse? Microsoft refused to consider this issue a security loophole when contacted by the researcher in October this year, saying it's a feature intended to work this way only—just like MS Office DDE feature, which is now actively being used by hackers.
New 'qkG Ransomware' Found Using Same Self-Spreading Technique
Interestingly, one such malware is on its way to affect you. I know, that was fast—even before its public disclosure.
Just yesterday, Trend Micro published a report on a new piece of macro-based self-replicating ransomware, dubbed "qkG," which exploits exactly the same MS office feature that Buono described to our team.
Trend Micro researchers spotted qkG ransomware samples on VirusTotal uploaded by someone from Vietnam, and they said this ransomware looks "more of an experimental project or a proof of concept (PoC) rather than a malware actively used in the wild."
The qkG ransomware employs Auto Close VBA macro—a technique that allows executing malicious macro when victim closes the document.
The latest sample of qkG ransomware now includes a Bitcoin address with a small ransom note demanding $300 in BTC as shown.
It should be noted that the above-mentioned Bitcoin address hasn't received any payment yet, which apparently means that this ransomware has not yet been used to target people.
Moreover, this ransomware is currently using the same hard-coded password: "I’m QkG@PTM17! by TNA@MHT-TT2" that unlocks affected files.
Here's How this New Attack Technique Works
In order to make us understand the complete attack technique, Buono shared a video with The Hacker News that demonstrates how an MS Word document equipped with malicious VBA code could be used to deliver a self-replicating multi-stage malware.
If you are unaware, Microsoft has disabled external (or untrusted) macros by default and to restrict default programmatic access to Office VBA project object model, it also offers users to manually enable "Trust access to the VBA project object model," whenever required.
With "Trust access to the VBA project object model" setting enabled, MS Office trusts all macros and automatically runs any code without showing security warning or requiring user's permission.
Buono found that this setting can be enabled/disabled just by editing a Windows registry, eventually enabling the macros to write more macros without user's consent and knowledge.
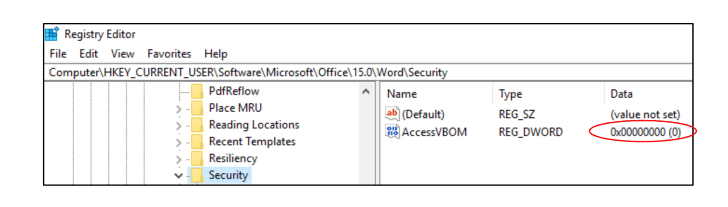
windows-registry-enable-macro
As shown in the video, a malicious MS Doc file created by Buono does the same—it first edits the Windows registry and then injects same macro payload (VBA code) into every doc file that the victim creates, edits or just opens on his/her system.
Victims Will be Unknowingly Responsible for Spreading Malware Further
In other words, if the victim mistakenly allows the malicious doc file to run macros once, his/her system would remain open to macro-based attacks.
Moreover, the victim will also be unknowingly responsible for spreading the same malicious code to other users by sharing any infected office files from his/her system.
This attack technique could be more worrisome when you receive a malicious doc file from a trusted contact who have already been infected with such malware, eventually turning you into its next attack vector for others.
Although this technique is not being exploited in the wild, the researcher believes it could be exploited to spread dangerous self-replicating malware that could be difficult to deal with and put an end.
Since this is a legitimate feature, most antivirus solutions do not flag any warning or block MS Office documents with VBA code, neither the tech company has any plans of issuing a patch that would restrict this functionality.
Buono suggests "In order to (partially) mitigate the vulnerability it is possible to move the AccessVBOM registry key from the HKCU hive to the HKLM, making it editable only by the system administrator."
The best way to protect yourself from such malware is always to be suspicious of any uninvited documents sent via an email and never click on links inside those documents unless adequately verifying the source.