admin/QwestM0dem : 1175 (69.4%) out of 1694″

A new Mirai variant is rapidly spreading, around 100,000 IPs running the scans in the past 60 hours
26.11.2017 securityaffairs BotNet
A new Mirai variant is rapidly spreading, experts observed around 100K IPs running the scans in the past 60 hours searching for flawed ZyXEL PK5001Z routers.
According to Li Fengpei, a security researcher with Qihoo 360 Netlab, the publication of the proof-of-concept (PoC) exploit code in a public vulnerabilities database is the root cause of the increase of activity associated with the Mirai botnet.
After the publication of the PoC exploit code on October 31, the experts observed scans using it starting on Wednesday, November 22.
“About 60 hours ago, since 2017-11-22 11:00, we noticed big upticks on port 2323 and 23 scan traffic, with almost 100k unique scanner IP came from Argentina. After investigation, we are quite confident to tell this is a new mirai variant.” reads the analysis published by Fengpei.
The PoC triggers the flaw CVE-2016-10401 in old ZyXEL PK5001Z routers that was publicly disclosed in January 2016. ZyXEL PK5001Z routers have a hardcoded super-user password (zyad5001) that could be used to elevate a user’s access to root level. The su password cannot be used to log into the device.
Anyway, attackers have discovered that there’s a large amount of ZyXEL devices are using admin/CentryL1nk and admin/QwestM0dem as default Telnet credentials.
The PoC code recently published first logs into a remote ZyXEL device using one of the two Telnet passwords, and then uses the hardcoded su password to gain root privileges.
Starting on Wednesday, Netlab has detected a spike of scans on ports 23 and 2323 for Telnet authentication the evidence that attackers are using the above PoC to infect exposed device with Mirai.
“The abuse of these two credentials began at around 2017-11-22 11:00, and reached its peak during 2017-11-23 daytime. This is a good time span match with this 2323/23 port scanning on Scanmon.” continues the analysis.
“Quite a lot of IP abusing these two credential also appear in ScanMon radar.
admin/CentryL1nk : 748 (66.5%) out of 1125
admin/QwestM0dem : 1175 (69.4%) out of 1694″
Experts from Netlab detected around 100,000 IPs running the scans in the past 60 hours, this means that the new Mirai botnet is already composed of roughly 100,000 devices looking for vulnerable ZyXEL devices.
65,700 of these bots were located in Argentina because the ISP has shipped devices with the default credentials included in the public PoC.
There are no reports that Telefonica users are suffering from Internet connectivity outages, a circumstance that suggests that the owners of infected routers are not aware of the infection.
The security researcher Troy Mursch confirmed that that most of the scanner IP came from Argentina, precisely from the network of local ISP Telefonica de Argentina.
23 Nov
Bad Packets Report
@bad_packets
Replying to @bad_packets
DAILY TOP 4 ASN
New unique IPs seen in Mirai-like #botnet by ASN
🇦🇷 AS22927: 493
🇯🇵 AS4713: 25
🇨🇳 AS4837: 21
🇨🇳 AS4134: 20 pic.twitter.com/TQ24Zmm8bY
Bad Packets Report
@bad_packets
879 new unique IP addresses were found in the #Mirai-like #botnet on 2017-11-22
This is an all-time record for the most new unique IP address that I've seen added to the botnet in one day.
A massive increase of volume from Argentina (@Telefonica) is largely the cause. pic.twitter.com/c8GBUpKNgW

10:13 AM - Nov 23, 2017
View image on Twitter
2 2 Replies 2 2 Retweets 1 1 like
Twitter Ads info and privacy
The good news is that the Mirai bots do not have a persistence mechanism, this means that it could be eradicated when the infected device is rebooted.
This isn’t the first time that the Mirai bornet was used to target the devices belonging to a particular ISP’s network, late 2016 it was used to compromise more than 900,000 routers of the Deutsche Telekom in Germany.
GOLDEN SAML attack technique forges authentication to cloud apps
25.11.2017 securityaffairs Attack
Golden SAML could be exploited by an attacker to create fake enterprise identities and access to valuable cloud resources.
Security experts at CyberArk Labs have devised a post-intrusion attack technique dubbed Golden SAML that could be exploited by an attacker to create fake enterprise identities and forge authentication to gain access to valuable cloud resources in a federated environment.
The attackers can impersonate any users gaining the highest privileges by forging SAML “authentication object.”
SAML is an open standard for exchanging authentication and authorization data between an identity provider and a service provider.
“The vector enables an attacker to create a golden SAML, which is basically a forged SAML “authentication object,” and authenticate across every service that uses SAML 2.0 protocol as an SSO mechanism.” states the analysis published by CyberArk.
“In a golden SAML attack, attackers can gain access to any application that supports SAML authentication (e.g. Azure, AWS, vSphere, etc.) with any privileges they desire and be any user on the targeted application (even one that is non-existent in the application in some cases).”
The Golden SAML name reminds us of another notorious attack known as golden ticket, devised by Benjamin Delpy who developed the popular hacking tool Mimikatz.
“The name resemblance is intended, since the attack nature is rather similar. Golden SAML introduces to a federation the advantages that golden ticket offers in a Kerberos environment – from gaining any type of access to stealthily maintaining persistency.” continues the analysis.
The Golden Ticket attack could be launched by attackers to gain full control of an IT infrastructure by manipulating the Windows Server Kerberos authentication framework.
In a similar way, the Golden SAML attack leverages the Security Assertion Markup Language 2.0 (SAML) protocol. Each SAML assertion is trusted and signed via a specific RSA key stored with an identity provider environment.
To carry on the such attack, the attackers will need the private key that signs the SAML objects along with an Active Directory Federation Services user account, token-signing private key, an identity provider (IdP) public certificate and an IdP name.
“Here’s a list of the requirements for performing a golden SAML attack. The mandatory requirements are highlighted in purple. For the other non-mandatory fields, you can enter whatever you like.”
Token-signing private key
IdP public certificate
IdP name
Role name (role to assume)
Domain\username
Role session name in AWS
Amazon account ID
The prerequisites of such attacks are important and make this technique not easy to be used in a real attack scenario.
The experts explained that mitigate the Golden SAMLattack is not simple.
“This attack doesn’t rely on a vulnerability in SAML 2.0. It’s not a vulnerability in AWS/ADFS, nor in any other service or identity provider.
Golden ticket is not treated as a vulnerability because an attacker has to have domain admin access in order to perform it. That’s why it’s not being addressed by the appropriate vendors. The fact of the matter is, attackers are still able to gain this type of access (domain admin), and they are still using golden tickets to maintain stealthily persistent for even years in their target’s domain.” concluded the researchers.
“As for the defenders, we know that if this attack is performed correctly, it will be extremely difficult to detect in your network. “
CyberArk released a new tool dubbed shimit that implements Golden SAML attack.

A new version of the Scarab ransomware is now being distributed via the Necurs botnet
25.11.2017 securityaffairs Ransomware
The Scarab ransomware is now being distributed to millions of users via a massive spam campaign powered with the dreaded Necurs botnet.
Scarab is a strain of ransomware, first spotted in June by the security researcher Michael Gillespie, that is now being distributed to millions of users via a massive spam campaign powered with the dreaded Necurs botnet.
Security researchers believe that Necurs botnet was rented by a threat actor to spread the Scarab ransomware.
The Necurs botnet was used in the past months to push many other malware, including Locky, Jaff, GlobeImposter, Dridex and the Trickbot.
The ongoing spam campaign started on concurrently the Thanksgiving, most of the experts in the security community reporting the ongoing spam campaign, including security firms F-Secure and Forcepoint,
Forcepoint experts highlighted huge volume of spam emails sent in a few hours, 12.5 million emails.
“Forcepoint Security Labs have observed another piece of ransomware called “Scarab” being pushed by the infamous Necurs botnet. The massive email campaign started at approximately 07:30 UTC and is active as of 13:30 today, totalling over 12.5 million emails captured so far.” reads the analysis published by Forcepoint.

MalwareHunterTeam
@malwrhunterteam
Necurs now spreading Scarab (https://twitter.com/dvk01uk/status/933611940173066240 …).
Interesting...
🤔
Let's see if it will be more successful than Locky in past months...@BleepinComputer @demonslay335
cc @MalwareTechBlog
11:27 AM - Nov 23, 2017
1 1 Reply 13 13 Retweets 19 19 likes
Twitter Ads info and privacy
“Necurs’ spam botnet business is doing well as it is seemingly acquiring new customers. The Necurs botnet is the biggest deliverer of spam with 5 to 6 million infected hosts online monthly, and is responsible for the biggest single malware spam campaigns. Its service model provides the whole infection chain: from spam emails with malicious malware downloader attachments, to hosting the payloads on compromised websites.” reported F-Secure.
“The final payload (to our surprise) was Scarab ransomware, which we haven’t seen previously delivered in massive spam campaigns. Scarab ransomware is a relatively new ransomware variant first observed last June, and its code is based on the open source “ransomware proof-of-concept” called HiddenTear.”

The Necurs botnet pushed tens of millions of spam emails of the Scarab ransomware.
According to Forcepoint, by noon, Necurs had already sent out 12.5 million emails carrying what appeared to be a new version of the Scarab ransomware.

Necurs spam volume pushing Scarab ransomware
The massive Scarab ransomware campaign is evident also from data from the ID-Ransomware service that allows users to detect the type of ransomware that infected their system. The following graph shows the number of submissions for the Scarab ransomware per day.
Scarab emails disguised as archives carrying scanned images, email subjects are chose to trick victims into opening the archive, some of the most popular subject lines used in the campaign were:
Scanned from Lexmark
Scanned from HP
Scanned from Canon
Scanned from Epson
These emails carried a 7Zip archive that contained a Visual Basic script that act as a dropper of the Scarab ransomware.
Researchers observed that this Visual Basic script contained the same Game of Thrones references that were observed in other Necurs campaigns that delivered the Locky ransomware in September.
A first variant of the Scarab ransomware was discovered in June, in July the Malwarebytes researcher Marcelo Rivera spotted a second version that used the “.scorpio” extension.
18 Jun
Marcelo Rivero
@MarceloRivero
Replying to @demonslay335
#Scarab #Ransomware sample: ext ".[resque@plague.desi].scarab"https://www.virustotal.com/en/file/53f73dc2e8af9c059136029b3b535e885d4452d3375586eb9a0336d7a389aad5/analysis/1497737613/ … cc//@BleepinComputer @malwrhunterteam @Amigo_A_ pic.twitter.com/yuv3pF4Mfx
Marcelo Rivero
@MarceloRivero
#Scorpio #Ransomware (aka #Scarab) new sample, same rescue note, new ext: [Help-Mails@Ya.Ru].Scorpiohttps://www.virustotal.com/en/file/89258854adce5f5fd4d99ece5aad39b306f40585810ced9b0f79dad43fd8e036/analysis/ … pic.twitter.com/rZ9lyYDfdd
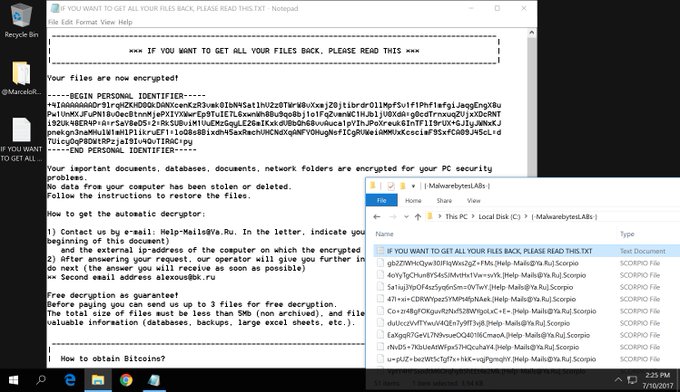
The variant currently used by crooks appends the “.[suupport@protonmail.com].scarab” extension to the original filenames of encrypted files.
The Scarab ransomware deletes shadow volume copies to make impossible to recovery the files, the malware drops a ransom note named “IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT” on victims’ PCs.
The ransom does refer the ransom sum to pay, but urges victims to contact the Scarab authors via email or BitMessage as soon as possible to pay the smaller the ransom sum.
Imgur was hacked in 2014, 1.7 million user accounts were compromised
25.11.2017 securityaffairs Incindent
Imgur, the popular image sharing service, confirms email addresses and passwords were stolen in a security breach occurred in 2014.
Are you an Imgur user?
News of the day it that the popular image sharing service Imgur was hacked in 2014, the incident was confirmed by the company a few days after Uber admitted to have concealed a data breach that exposed 57 Million records in 2016 and paid hackers to delete stolen records.
Imgur admitted that it had suffered a data breach back in 2014 that, email addresses and passwords of 1.7 million user accounts were accessed by hackers, a small portion of the 150 million user base.
The company said the breach didn’t include personal information because its service has “never asked” for real names, addresses, or phone numbers.
“On November 23, Imgur was notified of a potential security breach that occurred in 2014 that affected the email addresses and passwords of 1.7 million user accounts. While we are still actively investigating the intrusion, we wanted to inform you as quickly as possible as to what we know and what we are doing in response.” reads a data breach notification published by Imgur on its website.
The company had been notified on Thanksgiving of a data breach on November 23 by a the popular expert Troy Hunt, who runs the data breach notification service Have I Been Pwned.
Have I been pwned?
✔
@haveibeenpwned
New breach: imgur was hacked in 2013. 4 years later, 1.7M records with email addresses and cracked passwords surfaced. 60% were already in @haveibeenpwned. Read more: http://www.zdnet.com/article/imgur-reveals-hackers-stole-login-data/ …
1:02 AM - Nov 25, 2017
Imgur confirms it was hacked
The hackers stole email addresses and passwords.
zdnet.com
4 4 Replies 232 232 Retweets 188 188 likes
Twitter Ads info and privacy
Hunt informed the company on Thursday, a US national holiday observing Thanksgiving, when most businesses are closed.
One day later, the company started resetting the passwords of affected accounts and published a data breach notice.
The company said that the stolen passwords were protected with the SHA-256 hashing algorithm that can be easily cracked using brute force attacks.
“We have always encrypted your password in our database, but it may have been cracked with brute force due to an older hashing algorithm (SHA-256) that was used at the time. We updated our algorithm to the new bcrypt algorithm last year.” continues the data breach notice.
Imgur is investigating the incident, but it is still unclear how it is possible that the incident was revealed only three years later.
Below the Troy Hunt’s comment about the incident handling procedure implemented by the company.
“I want to recognise @imgur’s exemplary handling of this: that’s 25 hours and 10 mins from my initial email to a press address to them mobilising people over Thanksgiving, assessing the data, beginning password resets and making a public disclosure. Kudos!” Hunt tweeted.
“This is really where we’re at now: people recognise that data breaches are the new normal and they’re judging organizations not on the fact that they’ve had one, but on how they’ve handled it when it happened.”
Troy Hunt
✔
@troyhunt
I want to recognise @imgur's exemplary handling of this: that's 25 hours and 10 mins from my initial email to a press address to them mobilising people over Thanksgiving, assessing the data, beginning password resets and making a public disclosure. Kudos! https://twitter.com/haveibeenpwned/status/934210666335891456 …
1:03 AM - Nov 25, 2017
8 8 Replies 145 145 Retweets 360 360 likes
Twitter Ads info and privacy
According to Hunt, 60 percent of email addresses were already in Have I Been Pwned‘s database of more than 4.8 billion records.
Imgur users that want to check if their accounts have been exposed in the security breach can do it on the data breach notification service Have I Been Pwned that according to Hunt already includes 60 percent of email exposed in the hack.
Imgur is just the last notorious victim of a data breach, other companies revealed major security breaches they had suffered many years ago, including Uber, Yahoo, LinkedIn, and MySpace.