OPC UA security analysis
11.5.2018 Kaspersky Analysis ICS
This paper discusses our project that involved searching for vulnerabilities in implementations of the OPC UA protocol. In publishing this material, we hope to draw the attention of vendors that develop software for industrial automation systems and the industrial internet of things to problems associated with using such widely available technologies, which turned out to be quite common. We hope that this article will help software vendors achieve a higher level of protection from modern cyberattacks. We also discuss some of our techniques and findings that may help software vendors control the quality of their products and could prove useful for other software security researchers.
Why we chose the OPC UA protocol for our research
The IEC 62541 OPC UA (Object Linking and Embedding for Process Control Unified Automation) standard was developed in 2006 by the OPC Foundation consortium for reliable and, which is important, secure transfer of data between various systems on an industrial network. The standard is an improved version of its predecessor – the OPC protocol, which is ubiquitous in modern industrial environments.
It is common for monitoring and control systems based on different vendors’ products to use mutually incompatible, often proprietary network communication protocols. OPC gateways/servers serve as interfaces between different industrial control systems and telemetry, monitoring and telecontrol systems, unifying control processes at industrial enterprises.
The previous version of the protocol was based on the Microsoft DCOM technology and had some significant limitations inherent to that technology. To get away from the limitations of the DCOM technology and address some other issues identified while using OPC, the OPC Foundation developed and released a new version of the protocol.
Thanks to its new properties and well-designed architecture, the OPC UA protocol is rapidly gaining popularity among automation system vendors. OPC UA gateways are installed by a growing number of industrial enterprises across the globe. The protocol is increasingly used to set up communication between components of industrial internet of things and smart city systems.
The security of technologies that are used by many automation system developers and have the potential to become ubiquitous among industrial facilities across the globe is one the highest-priority areas of research for Kaspersky Lab ICS CERT. This was our main reason to do an analysis of OPC UA.
Another reason was that Kaspersky Lab is a member of the OPC Foundation consortium and we feel responsible for the security of technologies developed by the consortium. Getting ahead of the story, we can say that, following the results of our research, we received an invitation to join the OPC Foundation Security Working Group and gratefully accepted it.
OPC UA protocol
Originally, OPC UA was designed to support data transport for two data types: the traditional binary format (used in previous versions of the standard) and SOAP/XML. Today, data transfer in the SOAP/XML format is considered obsolete in the IT world and is almost never used in modern products and services. The prospects of it being widely used in industrial automation systems are obscure, so we decided to focus our research on the binary format.
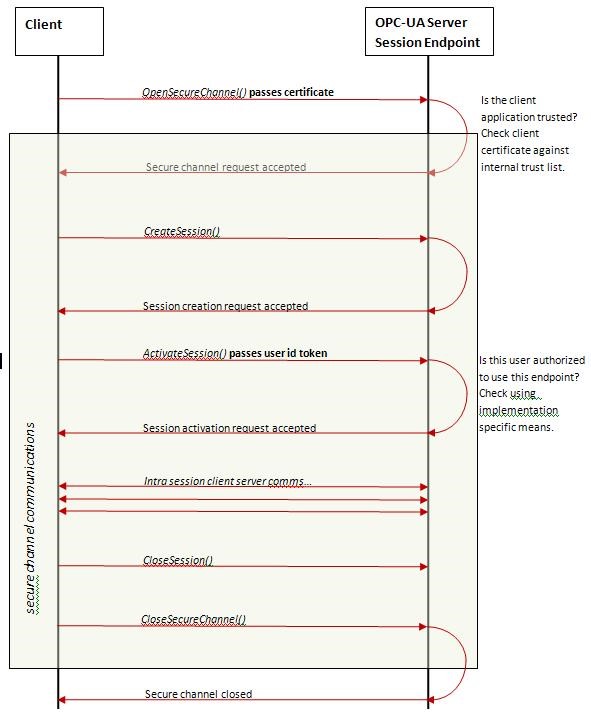
If packets exchanged by services running on the host are intercepted, their structure can easily be understood. There are four types of messages transmitted over the OPC UA protocol:
HELLO
OPEN
MESSAGE
CLOSE
The first message is always HELLO (HEL). It serves as a marker for the start of data transfer between the client and the server. The server responds by sending the ACKNOWLEDGE (ACK) message to the client. After the initial exchange of messages, the client usually sends the message OPEN, which means that the data transmission channel using the encryption method proposed by the client is now open. The server responds by sending the message OPEN (OPN), which includes the unique ID of the data channel and shows that the server agrees to the proposed encryption method (or no encryption).
Now the client and the server can start exchanging messages –MESSAGE (MSG). Each message includes the data channel ID, the request or response type, a timestamp, data arrays being sent, etc. At the end of the session, the message CLOSE (CLO) is sent, after which the connection is terminated.
Source: https://readthedocs.web.cern.ch/download/attachments/21178021/OPC-UA-Secure-Channel.JPG?version=1&modificationDate=1286181543000&api=v2
OPC UA is a standard that has numerous implementations. In our research, we only looked at the specific implementation of the protocol developed by the OPC Foundation.
The initial stage
We first became interested in analyzing the OPC UA protocol when the Kaspersky Lab ICS CERT team was conducting security audits and penetration tests at several industrial enterprises. All of these enterprises used the same industrial control system (ICS) software. With the approval of the customers, we analyzed the software for vulnerabilities as part of the testing.
It turned out that part of the network services in the system we analyzed communicated over the OPC UA protocol and most executable files used a library named “uastack.dll”.
The first thing we decided to do as part of analyzing the security of the protocol’s implementation was to develop a basic “dumb” mutation-based fuzzer.
“Dumb” fuzzing, in spite of being called “dumb”, can be very useful and can in some cases significantly improve the chances of finding vulnerabilities. Developing a “smart” fuzzer for a specific program based on its logic and algorithms is time-consuming. At the same time, a “dumb” fuzzer helps quickly identify trivial vulnerabilities that can be hard to get at in the process of manual analysis, particularly when the amount of code to be analyzed is large, as was the case in our project.
The architecture of the OPC UA Stack makes in-memory fuzzing difficult. For the functions that we want to check for vulnerabilities to work correctly, the fuzzing process must involve passing properly formed arguments to the function and initializing global variables, which are structures with a large number of fields. We decided not to fuzz-test functions directly in memory. The fuzzer that we wrote communicated with the application being analyzed over the network.
The fuzzer’s algorithm had the following structure:
read input data sequences
perform a pseudorandom transformation on them
send the resulting sequences to the program over the network as inputs
receive the server’s response
repeat
After developing a basic set of mutations (bitflip, byteflip, arithmetic mutations, inserting a magic number, resetting the data sequence, using a long data sequence), we managed to identify the first vulnerability in uastack.dll. It was a heap corruption vulnerability, successful exploitation of which could enable an attacker to perform remote code execution (RCE), in this case, with NT AUTHORITY/SYSTEM privileges. The vulnerability we identified was caused by the function that handled the data which had just been read from a socket incorrectly calculating the size of the data, which was subsequently copied to a buffer created on a heap.
Upon close inspection, it was determined that the vulnerable version of the uastack.dll library had been compiled by the product’s developers. Apparently, the vulnerability was introduced into the code in the process of modifying it. We were not able to find that vulnerability in the OPC Foundation’s version of the library.
The second vulnerability was found in a .NET application that used the UA .NET Stack. While analyzing the application’s traffic in wireshark, we noticed in the dissector that some packets had an is_xml bit field, the value of which was 0. In the process of analyzing the application, we found that it used the XmlDocument function, which was vulnerable to XXE attacks for .NET versions 4.5 and earlier. This means that if we changed the is_xml bit field’s value from 0 to 1 and added a specially crafted XML packet to the request body (XXE attack), we would be able to read any file on the remote machine (out-of-bound file read) with NT AUTHORITY/SYSTEM privileges and, under certain conditions, to perform remote code execution (RCE), as well.
Judging by the metadata, although the application was part of the software package on the ICS that we were analyzing, it was developed by the OPC Foundation consortium, not the vendor, and was an ordinary discovery server. This means that other products that use the OPC UA technology by the OPC Foundation may include that server, making them vulnerable to the XXE attack. This makes this vulnerability much more valuable from an attacker’s viewpoint.
This was the first step in our research. Based on the results of that step, we decided to continue analyzing the OPC UA implementation by the OPC Foundation consortium, as well as products that use it.
OPC UA analysis
To identify vulnerabilities in the implementation of the OPC UA protocol by the OPC Foundation consortium, research must cover:
The OPC UA Stack (ANSI C, .NET, JAVA);
OPC Foundation applications that use the OPC UA Stack (such as the OPC UA .NET Discovery Server mentioned above);
Applications by other software developers that use the OPC UA Stack.
As part of our research, we set ourselves the task to find optimal methods of searching for vulnerabilities in all three categories.
Fuzzing the UA ANSI C Stack
Here, it should be mentioned that there is a problem with searching for vulnerabilities in the OPC UA Stack. OPC Foundation developers provide libraries that are essentially a set of exported functions based on a specification, similar to an API. In such cases, it is often hard to determine whether a potential security problem that has been discovered is in fact a vulnerability. To give a conclusive answer to that question, one must understand how the potentially vulnerable function is used and for what purpose – i.e., a sample program that uses the library is necessary. In our case, it was hard to make conclusions on vulnerabilities in the OPC UA Stack without looking at applications in which it was implemented.
What helped us resolve this problem associated with searching for vulnerabilities was open-source code hosted in the OPC Foundation’s repository on GitHub, which includes a sample server that uses the UA ANSI C Stack. We don’t often get access to product source code in the course of analyzing ICS components. Most ICS applications are commercial products, developed mostly for Windows and released with a licensing agreement the terms of which do not include access to the source code. In our case, the availability of the source code helped find errors both in the server itself and in the library. The UA ANSI C Stack source code was helpful for doing manual analysis of the code and for fuzzing. It also helped us find out whether new functionality had been added to a specific implementation of the UA ANSI C Stack.
The UA ANSI C Stack (like virtually all other products by the OPC Foundation consortium) is positioned as a solution that is not only secure, but is also cross-platform. This helped us our during fuzzing, because we were able to build a UA ANSI С Stack together with the sample server code published by the developers in their GitHub account, on a Linux system with binary source code instrumentation and to fuzz-test that code using AFL.
To accelerate fuzzing, we overloaded the networking functions –socket/sendto/recvfrom/accept/bind/select/… – to read input data from a local file instead of connecting to the network. We also compiled our program with AddressSanitizer.
To put together an initial set of examples, we used the same technique as for our first “dumb” fuzzer, i.e., capturing traffic from an arbitrary client to the application using tcpdump. We also added some improvements to our fuzzer – a dictionary created specifically for OPC UA and special mutations.
It follows from the specification of the binary data transmission format in OPC UA that it is sufficiently difficult for AFL to mutate from, say, the binary representation of an empty string in OPC UA (“\xff\xff\xff\xff”) to a string that contains 4 random bytes (for example, “\x04\x00\x00\x00AAAA”). Because of this, we implemented our own mutation mechanism, which worked with OPC UA internal structures, changing them based on their types.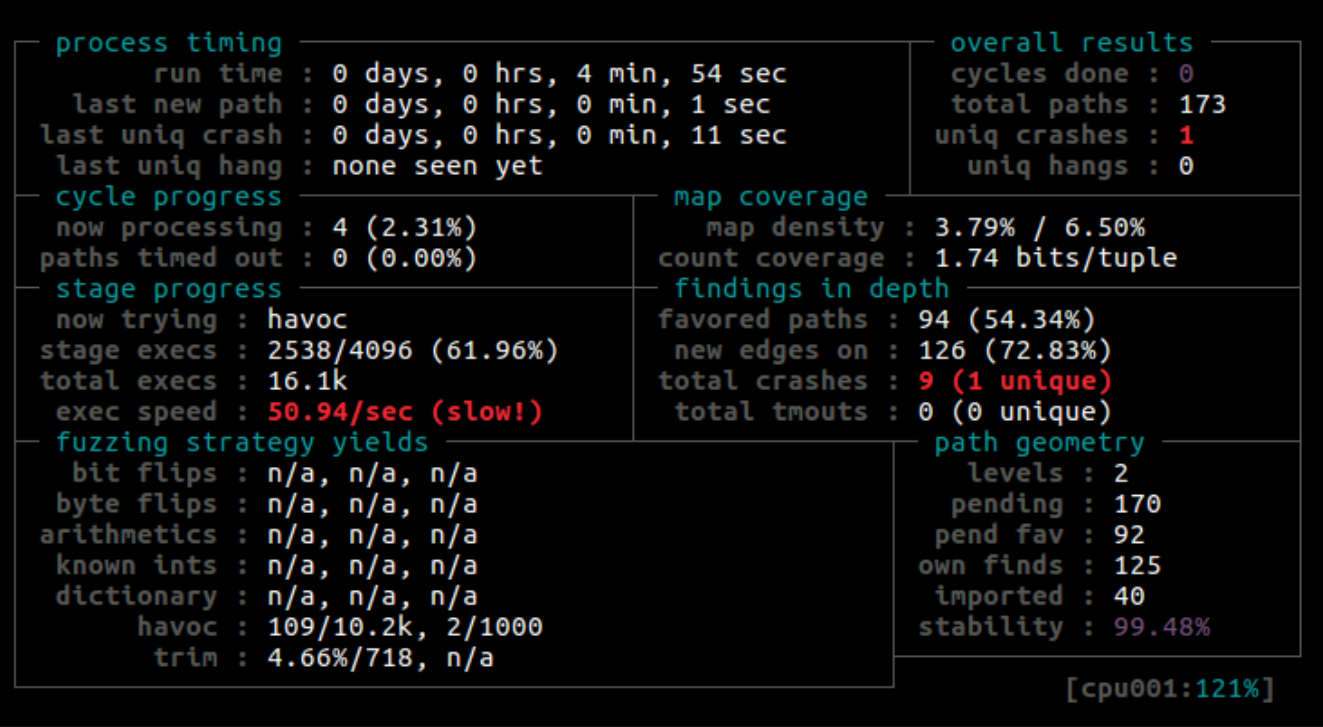
After building our fuzzer with all the improvements included, we got the first crash of the program within a few minutes.
An analysis of memory dumps created at the time of the crash enabled us to identify a vulnerability in the UA ANSI C Stack which, if exploited, could result at least in a DoS condition.
Fuzzing OPC Foundation applications
Since, in the previous stage, we had performed fuzzing of the UA ANSI C Stack and a sample application by the OPC Foundation, we wanted to avoid retesting the OPC UA Stack in the process of analyzing the consortium’s existing products, focusing instead on fuzzing specific components written on top of the stack. This required knowledge of the OPC UA architecture and the differences between applications that use the OPC UA Stack.
The two main functions in any application that uses the OPC UA Stack are OpcUa_Endpoint_Create and OpcUa_Endpoint_Open. The former provides the application with information on available channels of data communication between the server and the client and a list of available services. The OpcUa_Endpoint_Open function defines from which network the service will be available and which encryption modes it will provide.
A list of available services is defined using a service table, which lists data structures and provides information about each individual service. Each of these structures includes data on the request type supported, the response type, as well as two callback functions that will be called during request preprocessing and post-processing (preprocessing functions are, in most cases, “stubs”). We included converter code into the request preprocessing function. It uses mutated data as an input, outputting a correctly formed structure that matches the request type. This enabled us to skip the application startup stage, starting an event loop to create a separate thread to read from our pseudo socket, etc. This enabled us to accelerate our fuzzing from 50 exec/s to 2000 exec/s.
As a result of using our “dumb” fuzzer improved in this way, we identified 8 more vulnerabilities in OPC Foundation applications.
Analyzing third-party applications that use the OPC UA Stack
Having completed the OPC Foundation product analysis stage, we moved on to analyzing commercial products that use the OPC UA Stack. From the ICS systems we worked with during penetration testing and analyzing the security status of facilities for some of our customers, we selected several products by different vendors, including solutions by global leaders of the industry. After getting our customers’ approval, we began to analyze implementations of the OPC UA protocol in these products.
When searching for binary vulnerabilities, fuzzing is one of the most effective techniques. In previous cases, when analyzing products on a Linux system, we used source code binary instrumentation techniques and the AFL fuzzer. However, the commercial products using the OPC UA Stack that we analyzed are designed to run on Windows, for which there is an equivalent of the AFL fuzzer called WinAFL. Essentially, WinAFL is the AFL fuzzer ported to Windows. However, due to differences between the operating systems, the two fuzzers are different in some significant ways. Instead of system calls from the Linux kernel, WinAFL uses WinAPI functions and instead of static source code instrumentation, it uses the DynamoRIO dynamic instrumentation of binary files. Overall, these differences mean that the performance of WinAFL is significantly lower than that of AFL.
To work with WinAFL in the standard way, one has to write a program that will read data from a specially created file and call a function from an executable file or library. Then WinAFL will put the process into a loop using binary instrumentation and will call the function many times, getting feedback from the running program and relaunching the function with mutated data as arguments. That way, the program will not have to be relaunched every time with new input data, which is good, because creating a new process in Windows consumes significant processor time.
Unfortunately, this method of fuzzing couldn’t be used in our situation. Owing to the asynchronous architecture of the OPC UA Stack, the processing of data received and sent over the network is implemented as call-back functions. Consequently, it is impossible to identify a data-processing function for each type of request that would accept a pointer to the buffer containing the data and the size of the data as arguments, as required by the WinAFL fuzzer.
In the source code of the WinAFL fuzzer, we found comments on fuzzing networking applications left by the developer. We followed the developer’s recommendations on implementing network fuzzing with some modifications. Specifically, we included the functionality of communication with the local networking application in the code of the fuzzer. As a result of this, instead of executing a program, the fuzzer sends payload over the network to an application that is already running under DynamoRIO.
However, with all our efforts, we were only able to achieve the fuzzing rate of 5 exec/s. This is so slow that it would take too long to find a vulnerability even with a smart fuzzer like AFL.
Consequently, we decided to go back to our “dumb” fuzzer and improve it.
We improved the mutation mechanism, modifying the data generation algorithm based on our knowledge of the types of data transferred to the OPC UA Stack.
We created a set of examples for each service supported (the python-opcua library, which includes functions for interacting with virtually all possible OPC UA services, proved very helpful in this respect).
When using a fuzzer with dynamic binary instrumentation to test multithreaded applications such as ours, searching for new branches in the application’s code is a sufficiently complicated task, because it is difficult to determine which input data resulted in a certain behavior of the application. Since our fuzzer communicated to the application over the network and we could establish a clear connection between the server’s response and the data sent to it (because communication took place within the limits of one session), there was no need for us to address this issue. We implemented an algorithm which determined that a new execution path has been identified simply when a new response that had not been observed before was received from the server.
As a result of the improvements described above, our “dumb” fuzzer was no longer all that “dumb”, and the number of executions per second grew from 1 or 2 to 70, which is a good figure for network fuzzing. With its help, we identified two more new vulnerabilities that we had been unable to identify using “smart” fuzzing.
Results
As of the end of March 2018, the results of our research included 17 zero-day vulnerabilities in the OPC Foundation’s products that had been identified and closed, as well as several vulnerabilities in the commercial applications that use these products.
We immediately reported all the vulnerabilities identified to developers of the vulnerable software products.
Throughout our research, experts from the OPC Foundation and representatives of the development teams that had developed the commercial products promptly responded to the vulnerability information we sent to them and closed the vulnerabilities without delays.
In most cases, flaws in third-party software that uses the OPC UA Stack were caused by the developers not using functions from the API implemented in the OPC Foundation’s uastack.dll library properly – for example, field values in the data structures transferred were interpreted incorrectly.
We also determined that, in some cases, product vulnerabilities were caused by modifications made to the uastack.dll library by developers of commercial software. One example is an insecure implementation of functions designed to read data from a socket, which was found in a commercial product. Notably, the original implementation of the function by the OPC Foundation did not include this error. We do not know why the commercial software developer had to modify the data reading logic. However, it is obvious that the developer did not realize that the additional checks included in the OPC Foundation’s implementation are important because the security function is built on them.
In the process of analyzing commercial software, we also found out that developers had borrowed code from OPC UA Stack implementation examples, copying that code to their applications verbatim. Apparently, they assumed that the ОРС Foundation has made sure that these code fragments were secure in the same way that it had ensured the security of code used in the library. Unfortunately, that assumption turned out to be wrong.
Exploitation of some of the vulnerabilities that we identified results in DoS conditions and the ability to execute code remotely. It is important to remember that, in industrial systems, denial-of-service vulnerabilities pose a more serious threat than in any other software. Denial-of-service conditions in telemetry and telecontrol systems can cause enterprises to suffer financial losses and, in some cases, even lead to the disruption and shutdown of the industrial process. In theory, this could cause harm to expensive equipment and other physical damage.
Conclusion
The fact that the OPC Foundation is opening the source code of its projects certainly indicates that it is open and committed to making its products more secure.
At the same time, our analysis has demonstrated that the current implementation of the OPC UA Stack is not only vulnerable but also has a range of significant fundamental problems.
First, flaws introduced by developers of commercial software that uses the OPC UA Stack indicate that the OPC UA Stack was not designed for clarity. Unfortunately, an analysis of the source code confirms this. The current implementation of the protocol has plenty of pointer calculations, insecure data structures, magic constants, parameter validation code copied between functions and other archaic features scattered throughout the code. These are features that developers of modern software tend to eliminate from their code, largely to make their products more secure. At the same time, the code is not very well documented, which makes errors more likely to be introduced in the process of using or modifying it.
Second, OPC UA developers clearly underestimate the trust software vendors have for all code provided by the OPC Foundation consortium. In our view, leaving vulnerabilities in the code of API usage examples is completely wrong, even though API usage examples are not included in the list of products certified by the OPC Foundation.
Third, we believe that there are quality assurance issues even with products certified by the OPC Foundation.
It is likely that use fuzz testing techniques similar to those described in this paper are not part of the quality assurance procedures used by OPC UA developers – this is demonstrated by the statistics on the vulnerabilities that we have identified.
The open source code does not include code for unit tests or any other automatic tests, making it more difficult to test products that use the OPC UA Stack in cases when developers of these products modify their code.
All of the above leads us to the rather disappointing conclusion that, although OPC UA developers try to make their product secure, they nevertheless neglect to use modern secure coding practices and technologies.
Based on our assessment, the current OPC UA Stack implementation not only fails to protect developers from trivial errors but also tends to provoke errors –we have seen this in real-world examples. Given today’s threat landscape, this is unacceptable for products as widely used as OPC UA. And this is even less acceptable for products designed for industrial automation systems.
Tech giant Telstra warns cloud customers they’re at risk of hack due to a SNAFU
11.5.2018 securityaffairs Hacking
On May 4th Tech giant Telstra discovered a vulnerability in its service that could potentially expose customers of its cloud who run self-managed resources.
Telstra is a leading provider of mobile phones, mobile devices, home phones and broadband internet. On May 4th, the company has discovered a vulnerability in its service that could potentially expose users of its cloud who run self-managed resources.
Telstra told its users that their “internet facing servers are potentially vulnerable to malware or other malicious activity,” the experts from the company urge to “delete or disable” the “TOPS or TIRC account (privileged administrator accounts) on self-managed servers”.

The company sent to users of self-managed servers a letter and advised customers of Telstra-managed servers that they’re in the clear.
“We’ve also taken steps to access your account and remove the TOPS or TIRC accounts to minimise the risk on your behalf,” reads the advisory issued by the company.
“We’re still encouraging you to check your account settings and remove/disable any unused accounts as we can’t confirm at this stage if we’ll be successful updating the accounts from our end.”
Experts speculate that TOPS and TIRC Telstra accounts are using default passwords, attackers can easily use them to access them.
“Our customers’ security is our number one priority. We identified a weakness, moved quickly to address it and worked closely with our customers to ensure the necessary steps were taken to fully secure their systems.” a Telstra spokesperson told El Reg.
At the time of writing, there are no info on the origin of the security issue.
Symantec Stock Plunges After Firm Announces Internal Probe
10.5.2018 securityweek IT
Symantec announced its fourth quarter and full year financial results on Thursday and while its revenue has increased, the cybersecurity firm’s stock dropped roughly 20% after it revealed that an internal investigation will likely delay its annual report to the U.S. Securities and Exchange Commission (SEC).
Symantec reported a Q4 GAAP revenue of $1.22 billion, which represents a 10% year-over-year increase, and $1.23 billion in non-GAAP revenue, an increase of 5% year-over-year.
As for the full fiscal year ended on March 30, GAAP revenue increased by 21% year-over-year to $4.84 billion, while non-GAAP revenue went up 19% to nearly $5 billion. The company said it had a cash flow of $950 million from operating activities for the fiscal year 2018.
Despite strong financial results, Symantec stock dropped from over $29 to less than $24 in after-hours trading after the company announced the launch of an internal investigation by the Audit Committee of the Board of Directors.
Few details have been made public by the company, but the probe was apparently triggered by concerns raised by a former employee.
“The Audit Committee has retained independent counsel and other advisors to assist it in its investigation. The Company has voluntarily contacted the Securities and Exchange Commission to advise it that an internal investigation is underway, and the Audit Committee intends to provide additional information to the SEC as the investigation proceeds. The investigation is in its early stages and the Company cannot predict the duration or outcome of the investigation,” Symantec said.
The security firm believes it’s unlikely that it will be able to file its annual 10-K report with the SEC in a timely manner due to the investigation.
In response to news of the internal probe, investor rights law firm Rosen Law Firm announced the preparation of a class action to recover losses suffered by Symantec investors. Rosen says it’s investigating allegations that Symantec “may have issued materially misleading business information to the investing public.”
Many Vulnerabilities Found in OPC UA Industrial Protocol
10.5.2018 securityweek Vulnerebility
Researchers at Kaspersky Lab have identified a significant number of vulnerabilities in the OPC UA protocol, including flaws that could, in theory, be exploited to cause physical damage in industrial environments.
Developed and maintained by the OPC Foundation, OPC UA stands for Open Platform Communications Unified Automation. The protocol is widely used in industrial automation, including for control systems (ICS) and communications between Industrial Internet-of-Things (IIoT) and smart city systems.
Researchers at Kaspersky Lab, which is a member of the OPC Foundation consortium, have conducted a detailed analysis of OPC UA and discovered many vulnerabilities, including ones that can be exploited for remote code execution and denial-of-service (DoS) attacks.OPC Foundation patches 17 vulnerabilities in OPC UA protocol
There are several implementations of OPC UA, but experts focused on the OPC Foundation’s implementation – for which source code is publicly available – and third-party applications using the OPC UA Stack.
A total of 17 vulnerabilities have been identified in the OPC Foundation’s products and several flaws in commercial applications that use these products. Most of the issues were discovered through fuzzing.
Exploitation of the vulnerabilities depends on how the targeted network is configured, but in most cases, it will require access to the local network, Kaspersky researchers Pavel Cheremushkin and Sergey Temnikov told SecurityWeek in an interview at the company’s Security Analyst Summit in March. The experts said they had never seen a configuration that would allow attacks directly from the Internet.
An attacker first has to identify a service that uses OPC UA, and then send it a payload that triggers a DoS condition or remote code execution. Remote code execution vulnerabilities can be leveraged by attackers to move laterally within the network, control industrial processes, and to hide their presence. However, DoS attacks can have an even more significant impact in the case of industrial systems.
“In industrial systems, denial-of-service vulnerabilities pose a more serious threat than in any other software,” Cheremushkin and Temnikov wrote in a report published on Thursday. “Denial-of-service conditions in telemetry and telecontrol systems can cause enterprises to suffer financial losses and, in some cases, even lead to the disruption and shutdown of the industrial process. In theory, this could cause harm to expensive equipment and other physical damage.”
All the security holes were reported to the OPC Foundation and their respective developers and patches were released. Applying the patches is not difficult considering that the OPC Stack is a DLL file and updates are performed simply by replacing the old file with the new one.
The OPC Foundation has released advisories for the security holes discovered by Kaspersky researchers, but grouped all the issues under two CVE identifiers: CVE-2017-17433 and CVE-2017-12069. The latter also impacts automation and power distribution products from Siemens, which has also published an advisory.
“Based on our assessment, the current OPC UA Stack implementation not only fails to protect developers from trivial errors but also tends to provoke errors – we have seen this in real-world examples. Given today’s threat landscape, this is unacceptable for products as widely used as OPC UA. And this is even less acceptable for products designed for industrial automation systems,” researchers said.
Industry Reactions to Iran Cyber Retaliation Over U.S. Nuclear Deal Exit
10.5.2018 securityweek Cyber
President Donald Trump announced this week that the U.S. is withdrawing from the Iran nuclear deal and reimposing sanctions on the Middle Eastern country. Many experts fear that Iran will retaliate by launching cyberattacks on Western organizations.
Industry professionals contacted by SecurityWeek all say that there is a strong possibility of attacks, but they mostly agree that Iran will likely not try to cause too much damage as that could lead to massive response from the United States and its allies.
And the feedback begins...
Ross Rustici, senior director, intelligence services, Cybereason:
“Iran is currently in a precarious position, any disproportionate retaliation risks alienating the European community that is currently aligned with continued sanctions relief in exchange for IAEA inspections. Compounding that with the fact the Iran's domestic situation has degraded over the last several years a result of its intervention in the broader Middle East and its proxy war with Saudi Arabia, leaves Iran's leadership needing to be very careful with how directly it confronts the United States on this issue.
In the near term Iran is most likely going to take a wait and see approach to the decertification of the deal by Trump. If sanctions are imposed on Iran and it serves to cause significant economic harm though rigorous enforcement, then Iran will probably seek to retaliate in a fashion similar to what the US experienced in 2013 with the DDoS attacks against the financial sector. Despite the Iranian cyber program maturing significantly in the past five years, they will focus on a proportional response to whatever sanctions regime is levied against them. Disruptions that cause financial loss rather that destruction is where the regime is likely to go first. Iran is only likely to use significant destructive capabilities if the situation escalates or the US expands its role in supporting Saudi Arabia.
Given Iran's growth over the last five years in the cyber domain, I would expect them to at least be initially successful against civilian targets in the US should they decide to go that route. From a technical perspective they have more than enough capability to carry out successful attacks, as we have seen in the Middle East and the United States. If private sector networks are left to their own defences, Iran will have a high success rate. The thing that will reduce their operational capacity is if the US government takes a proactive and aggressive counter cyber posture and actively disrupts Iran's program before an attack is launched. While this would greatly hamper Iran's efforts it would not eliminate them completely and it would also be an escalation that could result in Iran taking more destructive measures because they have less options and control.”
Priscilla Moriuchi, Director of Strategic Threat Development, Recorded Future:
“President Trump’s actions have placed American businesses at increased risk for retaliatory and destructive cyber attacks by the Islamic Republic. We assess that within months, if not sooner, American companies in the financial, critical infrastructure, oil, and energy sectors will likely face aggressive and destructive cyber attacks by Iranian state-sponsored actors.
Further, our research indicates that because of the need for a quick response, the Islamic Republic may utilise contractors that are less politically and ideologically reliable (and trusted) and as a result, could be more difficult to control. It is possible that this dynamic could limit the ability of the government to control the scope and scale of these destructive attacks once they are unleashed.”
Phil Neray, VP of Industrial Cybersecurity, CyberX:
“Cyber is an ideal mechanism for weaker adversaries like Iran because it allows them to demonstrate strength on the global stage without resorting to armed conflict. I expect that Iran will continue to escalate its cyberattacks on US targets but will keep them below the threshold that would require a kinetic response from the US.
TRITON shows that Iran has the skills to launch damaging attacks on critical infrastructure. However, for now they confine these attacks to Middle Eastern targets in the same way that Russia has so far only shut down the power grid in the Ukraine. We should expect Iran to conduct phishing and cyber espionage attacks against US-based industrial and critical infrastructure firms -- as we've seen with Russian threat actors -- with the goal of establishing footholds in OT networks that could later be used for more destructive attacks.”
Gen. Earl Matthews, senior vice president and chief strategy officer, Verodin:
“The Iranians continue to improve and have become more sophisticated with their cyber capabilities. In my opinion, they are in the top 5 of countries with significant capabilities. We will definitely see increased cyber activity as a result of the US backing out of the nuclear agreement. Attacks not only against the US but many of our allies, especially Israel.
Iran has previously attacked our financial institutions with Denial of Service and most recently penetrated a number of universities. The latest attacks represented the continued loss of intellectual property of our nation. It wouldn’t surprise me if many of these universities were specifically targeted because they are doing research and development on behalf of the US Government.
Iran most certainly has the capability of launching significant attacks but I would view that probability to be low. They will continue to pursue softer targets where common means of access will be through social engineering and penetrate organizations with weak cyber hygiene. These attacks can be mitigated if organizations continuously automated and measured the validity, value, and effectiveness of their cybersecurity controls. We are well beyond the checklist compliance and thinking we are safe.”
John Hultquist, Director of Intelligence Analysis, FireEye:
“Iranian actors remain among the most aggressive we track, carrying out destructive and disruptive attacks in addition to stealthier acts of cyber espionage. Prior to the nuclear agreement, Iranian actors carried out several attacks against the West. There were also clear signs these actors were probing Western critical infrastructure in multiple industries for future attack. These efforts did not entirely disappear with the agreement, but they did refocus on Iran’s neighbors in the Middle East. With the dissolution of the agreement, we anticipate that Iranian cyberattacks will once again threaten Western critical infrastructure.”
Sherban Naum, senior vice president for corporate strategy and technology, Bromium:
“The premise that Iran can or will increase their attacks is predicated on both their existing computer network attack practices and risk tolerance to potential retaliation. The regime may see a need to show strength internally and take action. They will have to balance the time and resources dedicated to increase offensive efforts with the need to shore up defensive efforts due to the increased conflicts in the region from regional actors as well a potential retaliation by those that they attack.
[...]
There are three possible areas they could focus: Critical infrastructure, a doxxon like attack looking to shame those involved with the reversal decision and the third being in region actors and their weapons systems.
[...]
The questions to ask are what would motivate their taking action and their acceptable outcomes. Taking action, putting lives at risk could result in a kinetic response from the US and/or its allies as well as put into question Europe’s current support of the agreement. If they were to take out a power station and a hospital loses power, they lose the PR war and retaliation from the US is quite plausible. At this point, they want to show the world they are going to continue down the path of adhering to the nuclear agreement, that they are the ones targeted and have so much to lose. They would be better off influencing Europe to play into their hands as it could suit their economic needs and try to influence their own social media movement.”
Robert Lee, CEO, Dragos:
“ICS cyber attacks and espionage can be highly geopolitical in nature. Every time we see increased tension between states we expect to see a rise in ICS targeting, this does not mean we expect to see attacks. In this case, activity moves beyond conducting early reconnaissance to gaining access to infrastructure companies and stealing information that could be used at a later date. However simply having access to the information does not mean an attack is easy or imminent. Avoiding such tension while also defending against such aggressive efforts is the goal.”
Sanjay Beri, CEO & Founder of Netskope:
“While the repercussions of the United States pulling out of the Iran nuclear deal will be wide reaching, one of the first places you can expect to see a response is cyberspace. Nation-states, including Iran, have historically used cyberattacks as a low-risk, high-reward tactic for retaliating to political opposition. We saw this with North Korea in the form of the Sony hack, and Iran’s attack against US banks following Stuxnet.
The U.S. needs cybersecurity leadership today more than ever if we are to stand a chance at defending the country from nation-state sponsored cyber attacks. Forming a cohesive cyber defense strategy has become nearly impossible as hundreds of departments report into a siloed set of decision makers. There’s no silver bullet, but appointing a federal CISO to oversee all of our nation’s cybersecurity initiatives and promote inter-agency collaboration would be a big step in the right direction.”
Willy Leichter, Vice President of Marketing, Virsec:
“It seems likely that a deteriorating relationship between the US and Iran will lead to more cyberattacks. There have been numerous reports about state-sponsored hacking groups in Iran including APT33 that have already targeted critical infrastructure in Saudi Arabia, South Korea, and the US. These hacking groups have access to advanced tools (many leaked from the NSA through the Shadow Brokers) to launch attacks that corrupt legitimate processes and memory, and have proved adept at creating multiple variants of these exploits. We need to expect ongoing cyber warfare to be the new normal, and it’s critical that all organizations take security much more seriously, improve their detection and protection capabilities, and train all employees to protect their credentials against theft.”
Andrew Lloyd, President, Corero Network Security:
“Given multiple reports implicating the Iranian government in the cyber-attack on the Saudi petrochemical plant, the prospect of cyber-retribution for the US withdrawal certainly exists. Also, it’s well worth remembering that even if a nation doesn't have well developed cyberwarfare resources, there’s plenty of bad actors on the global stage who are more than happy to launch attacks against the foes of anyone who’s willing to pay. Moreover, the irony is that such bad actors are able to leverage the exploits that major forces such as the US government have themselves developed and which subsequently leaked across the Dark Web’s darker commercial corners. For example, it’s well reported that groups such as the Shadow Brokers have released and brokered tools from the NSA.
Also, basic and advanced DDoS-for-hire services abound, as we’ve seen in recent weeks and months. This all underscores the fact that all operators of essential services (and especially, critical national infrastructure) must up their game when it comes to DDoS defences. Ironically, today is the day that the EU NIS Directive becomes law in all 28 EU Member States.”
Cyber Insurance Startup At-Bay Raises $13 Million
10.5.2018 securityweek IT
Cyber insurance firm At-Bay announced this week that it has raised $13 million in Series A funding, which brings the company’s total funding to $19 million.
The Mountain View, Calif-based company emerged from stealth in November 2017 with a mission to shake up the status quo in cyber insurance.
At-Bay brings a new model of security cooperation between insured and insurer to reduce risk and exposure to both parties.
"We will be collecting data and using researchers to push the limits of our understanding of risk," Rotem Iram, CEO and founder of At-Bay, previously told SecurityWeek. "As we do that, we will be improving the quality of our product. Product quality is depressed today because insurance companies do not really understand the cybersecurity risk.”
The Series A funding round was co-led by Keith Rabois of Khosla Ventures, Yoni Cheifetz of Lightspeed, and Shlomo Kramer.
"Cyber insurance is one of the fastest growing and complex markets, yet the incumbents are still currently relying on standardized checklists and irrelevant actuarial data to model risk. At-Bay is focusing on customized and real-time risk modeling and risk reduction for its customers which unlocks superior pricing and coverage options for them," said Keith Rabois, general investment partner at Khosla Ventures.
The company said the new round of financing will help accelerate development of its proactive cyber security monitoring service and roll out its insurance products.
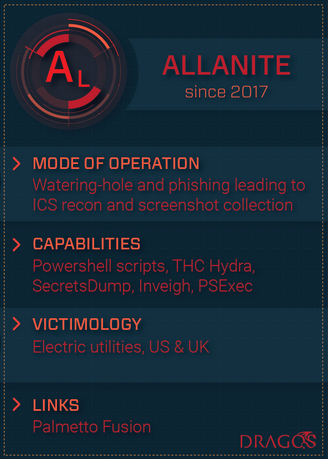
Allanite threat actor focused on critical infrastructure is targeting electric utilities and ICS networks
10.5.2018 securityaffairs ICS
Security experts from the industrial cybersecurity firm Dragos warn of a threat actor tracked as Allanite has been targeting business and industrial control networks at electric utilities in the United States and the United Kingdom.
Dragos experts linked the campaigns conducted by the Dragonfly APT group and Dymalloy APT, aka Energetic Bear and Crouching Yeti, to a threat actors they tracked as ‘Allanite.’
Allanite APTAllanite has been active at least since May 2017 and it is still targeting both business and ICS networks at electric utilities in the US and UK.
Experts believe the APT group is conducting reconnaissance and gathering intelligence for later attacks.
Dragos, Inc.
@DragosInc
Today, we're unveiling a public dashboard of ICS-focused activity groups that aim to exploit, disrupt, and potentially destroy industrial systems. Each week this month, we'll release new content discussing these adversary details that you can read here: https://dragos.com/adversaries.html …
4:53 PM - May 3, 2018
121
83 people are talking about this
Twitter Ads info and privacy
For those that are unaware of Dymalloy APT, the threat actor was discovered by Dragos researchers while investigating the Dragonfly’s operations. The Dragonfly APT group is allegedly linked to Russian intelligence and it is believed to be responsible for the Havex malware.
According to the researchers, the TA17-293A alert published by the DHS in October 2017 suggests a link between Dragonfly attacks with Allanite operations
Dragos experts highlighted that Allanite operations present similarities with the Palmetto Fusion campaign associated with Dragonfly by the DHS in July 2017.
At the same time, the experts believe the threat actor is different from Dragonfly and Dymalloy.
Like Dragonfly and Dymalloy, Allanite hackers leverage spear phishing and watering hole attacks, but differently from them, they don’t use any malware.
Is Allanite a Russia-linked threat actor?
Many security experts linked the APT group to Russia, but Dragos researchers did not corroborate the same thesis.
According to the Dragos, the hackers harvest information directly from ICS networks in campaigns conducted in 2017.
At the time the group has never hacked into a system to cause any disruption or damage.
The report published by Dragos on the Allanite APT is the first analysis of a collection of related to threat groups targeting critical infrastructure.
Summary info on threat actors will be made available through an Activity Groups dashboard, but users interested in the full technical report need to pay it.
The source code of the TreasureHunter PoS Malware leaked online
10.5.2018 securityaffairs Virus
Security experts at Flashpoint confirmed the availability online for the source code of the TreasureHunter PoS malware since March.
The researchers found evidence that the threat has been around since at least late 2014. TreasureHunt was first discovered by researchers at the SANS Institute who noticed the malware generating mutex names to evade detection.
TreasureHunt enumerates the processes running on the infected systems and implement memory scraping functions to extract credit and debit card information. Stolen payment card data are sent to C&C servers through HTTP POST requests.
The experts at FireEye believe who analyzed the malware back in 2016, discovered that cyber criminals compromised the PoS systems by using stolen or weak credentials. Once the TreasureHunt malware infects the systems, it installs itself in the “%APPDATA%” directory and maintains persistence by creating the registry entry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\jucheck
Flashpoint experts discovered the source code of TreasureHunter on a top-tier Russian-speaking forum, the guy who posted the code also leaked the source code for the graphical user interface builder and administrator panel.
The original developer of the PoS malware appears to be a Russian speaker who is proficient in English.
“The source code for a longstanding point-of-sale (PoS) malware family called TreasureHunter has been leaked on a top-tier Russian-speaking forum. Compounding the issue is the coinciding leak by the same actor of the source code for the malware’s graphical user interface builder and administrator panel.” reads the analysis published by Flashpoint.
“The availability of both code bases lowers the barrier for entry for cybercriminals wishing to capitalize on the leaks to build their own variants of the PoS malware.”
Cybercriminals could take advantage of the availability of the above code bases to create their own version of the TreasureHunter PoS malware, according to the experts, the number of attacks leveraging this threat could rapidly increase.
The actor behind the TreasureHunter leak said: “Besides alina, vskimmer and other sniffers, Treasure Hunter still sniffs ( not at a very high rate, but it still does ) and besides that , since now you have the source code, it can be update anytime for your own needs.”
The good news is that that availability of the source code could allow security firms to analyze the threat and take the necessary countermeasures.
Flashpoint proactively collaborated with researchers at Cisco Talos to prevent the diffusion of the malicious code.
“In the meantime, Russian-speaking cybercriminals have been observed on the vetted underground discussing improvements and weaponization of the leaked TreasureHunter source code,” continues the analysis.
“Originally, this malware appears to have been developed for the notorious underground shop dump seller “BearsInc,” who maintained presence on various low-tier and mid-tier hacking and carding communities (below is a graphical representation of such an operation on the Deep & Dark Web). It’s unknown why the source code was leaked at this time.”

The malicious code is written in pure C, it doesn’t include C++ features, and was originally compiled in Visual Studio 2013 on Windows XP.
The code project appears to be called internally trhutt34C, according to the researchers the author was working to improve it by redesign several features, including anti-debugging, code structure, and gate communication logic.
“The source code is consistent with the various samples that have been seen in the wild over the last few years. TreasureHunter\config.h shows definite signs of modification over the lifespan of the malware.” concluded the analysis.
“Early samples filled all of the configurable fields with FIELDNAME_PLACEHOLDER to be overwritten by the builder. More recent samples, and the source code, instead writes useful config values directly into the fields. This makes the samples slightly smaller and uses fresh compiles to create reconfigured files.”
TreasureHunter PoS Malware Source Code Leaked Online
10.5.2018 securityweek Virus
New variants of the TreasureHunter point-of-sale (PoS) malware are expected to emerge after its source code was leaked online in March, Flashpoint warns.
Capable of extracting credit and debit card information from processes running on infected systems, the PoS malware family has been around since at least 2014. To perform its nefarious activities, it scans all processes on the machine to search for payment card data, and then sends the information to the command and control (C&C) servers.
The malware’s source code was posted on a top-tier Russian-speaking forum by an actor who also leaked the source code for the malware’s graphical user interface builder and administrator panel.
The availability of both code bases is expected to allow more cybercriminals to build their own PoS malware variants and start using them in attacks. However, the availability of the code also provides security researchers with the possibility to better analyze the threat. In fact, Flashpoint, which discovered the leak in March, has been working together with Cisco Talos to improve protections and disrupt potential copycats who may have obtained the leaked source code.
“In the meantime, Russian-speaking cybercriminals have been observed on the vetted underground discussing improvements and weaponization of the leaked TreasureHunter source code,” the security researchers explain in a report shared with SecurityWeek.
The original malware developer is likely a Russian speaker who is proficient in English. According to Flashpoint, the threat might have been originally developed for the notorious underground shop dump seller BearsInc, but the reason why the code was leaked is unknown.
TreasureHunter likely installed using weak credentials. The attacker accesses a Windows-based server and the point-of-sale terminal, installs the threat, and then establishes persistence through creating a registry key to execute the malware at startup.
The threat then enumerates running processes and starts scanning the device memory for track data such as primary account numbers (PANs), separators, service codes, and more. Next, it establishes a connection with the C&C and sends the stolen data to the attacker.
“Besides alina, vskimmer and other sniffers, Treasure Hunter still sniffs (not at a very high rate, but it still does) and besides that, since now you have the source code, it can be update anytime for your own needs,” the actor behind the TreasureHunter leak apparently said.
Internally, the code project was supposedly called trhutt34C. The malware is written in pure C with no C++ features and was originally compiled in Visual Studio 2013 on Windows XP. The researchers believe the malware author was also looking to improve and redesign various features including anti-debugging, code structure, and gate communication logic.
The source code is consistent with the previously analyzed TreasureHunter samples and a config.h file shows “definite signs of modification over the lifespan of the malware.” More recent samples write useful config values directly into the fields, which makes them smaller.
LG Patches Serious Vulnerabilities in Smartphone Keyboard
10.5.2018 securityweek Vulnerebility
Updates released this week by LG for its Android smartphones patch two high severity keyboard vulnerabilities that can be exploited for remote code execution.
The vulnerabilities were reported to LG late last year by Slava Makkaveev of Check Point Research. The electronics giant patched them with its May 2018 updates, which also include the latest security fixes released by Google for the Android operating system (security patch level 2018-05-01).
According to Check Point, the flaws affect the default keyboard (LG IME) shipped with all mainstream LG smartphones. Researchers successfully reproduced and exploited the security holes on LG G4, G5 and G6 devices.
An attacker could exploit the flaws to remotely execute arbitrary code with elevated privileges by manipulating the keyboard update process, specifically for the MyScript handwriting feature. Hackers can leverage the weaknesses to log keystrokes and capture credentials and other potentially sensitive data.
The first vulnerability is related to installing new languages or updating existing ones. The device obtains the necessary files from a hardcoded server over an HTTP connection, which allows a man-in-the-middle (MitM) attacker to deliver a malicious file instead of the legitimate update.
The second flaw can be exploited by an MitM attacker to control the location where a file is downloaded. A path traversal issue allows hackers to place a malicious file in the LG keyboard package sandbox by including the targeted location in the name of the file.
If the file is assigned a .so extension, it will be granted executable permissions. In order to get the keyboard app to load the malicious file, the attacker can appoint it as an “input method extension library” in the keyboard configuration file. The malware will be loaded as soon as the keyboard application is restarted.
LG noted in its advisory that the vulnerabilities only impact the MyScript handwriting feature.
Reports published last year showed that LG had a 20 percent market share in the U.S. and 4 percent globally. This means there are plenty of devices that hackers could target using the vulnerabilities discovered by Check Point. On the other hand, there are also many critical and high severity flaws in Android itself that hackers could try to exploit and those can pose a bigger risk considering that they could be weaponized against multiple Android smartphone brands.
Firefox 60 Brings Support for Enterprise Deployments
10.5.2018 securityweek Security
Released on Wednesday, Firefox 60 allows IT administrators to customize the browser for employees, and is also the first browser to feature support for the Web Authentication (WebAuthn) standard.
The new application release also comes with various security patches, on-by-default support for the latest draft TLS 1.3, redesigned Cookies and Site Storage section in Preferences, and other enhancements.
To configure Firefox Quantum for their organization, IT professionals can either use Group Policy on Windows, or a JSON file that works across Mac, Linux, and Windows operating systems, Mozilla says. What’s more, enterprise deployments are supported for both the standard Rapid Release (RR) of Firefox or the Extended Support Release (ESR), which is now version 60.
While the standard Rapid Release automatically receives performance improvements and new features on a six-week basis, the Extended Support Release usually receives the features in a single update per year. Critical security updates are delivered to both releases as soon as possible.
Mozilla has published the necessary information for IT professionals to get started with using Firefox Quantum in their organization on this site.
The WebAuthn standard allows end users to use a single device to log into their accounts without typing a password. The feature is available only on websites that have adopted the standard and can also be used as a secondary authentication after entering a password.
“Essentially, WebAuthn is a set of anti-phishing rules that uses a sophisticated level of authenticators and cryptography to protect user accounts. It supports various authenticators, such as physical security keys today, and in the future mobile phones, or biometric mechanisms such as face recognition or fingerprints,” Mozilla explains.
One of the first major web services to have adopted the standard is Dropbox, which announced on Wednesday that WebAuthn is now supported as a two-step verification.
Firefox 60 also brings along patches for over two dozen security vulnerabilities, including two memory safety bugs rated Critical severity.
The latest version of the browser patches 6 High severity flaws, namely use-after-free with SVG animations and clip paths, use-after-free with SVG animations and text paths, same-origin bypass of PDF Viewer to view protected PDF files, insufficient sanitation of PostScript calculator functions in PDF viewer, integer overflow and out-of-bounds write in Skia, and uninitialized memory use by WebRTC encoder.
A total of 14 Medium severity flaws were addressed in the new release (including one that only affects Windows 10 users running the April 2018 update or later), alongside 4 Low risk issues.
Protego Labs Raises $2 Million in Seed Funding
10.5.2018 securityweek IT
Serverless application security firm Protego Labs announced Wednesday that it has raised $2 million seed funding from a group of investors led by Ron Gula of Gula Tech Adventures, Glilot Capital Partners, and the MetroSITE Group of security industry pioneers, including former RSA CTO, Tim Belcher.
The serverless approach -- where the server being used is managed by a cloud provider rather than the application owner -- offers great advantages in speed, simplicity and cost-savings. Gula believes it is a transformative step in leveraging the full potential of the public cloud.
Protego"But," he adds, "but it also presents a host of new threats and security challenges that traditional application security cannot handle. Protego offers a security solution designed specifically with serverless in mind, putting it at the forefront of this major technology shift."
Protego summarizes the security problem in a blog published in March 2018. "Not owning the platform means not being able to leverage the platform for security in ways you might have in the past. You’re at the mercy of whatever security mechanisms the cloud provider puts in place for you, and those rarely provide the level and granularity of protection you’d like."
The Protego platform operates by continuously scanning the serverless infrastructure, including functions, logs, and databases. It uses machine-based analysis and deep learning algorithms to build a model of normal behavior to find threats by anomaly detection as they initiate and begin to propagate. It does this in real time allowing the minimal effective protection dose in the right place -- maximizing security while minimizing costs.
Protego has offices in Baltimore, MD, and Israel. It was founded by Tsion (TJ) Gonen, Hillel Solow, Shali Mor, Itay Harush and Benny Zemmour. In January 2018 it won the Startup Competition for the most innovative cyber initiative at the Cybertech Tel Aviv 2018 Conference.
'Allanite' Group Targets ICS Networks at Electric Utilities in US, UK
10.5.2018 securityweek ICS
A threat actor has been targeting business and industrial control networks at electric utilities in the United States and United Kingdom, according to industrial cybersecurity firm Dragos.
The group, tracked as “Allanite,” has been linked to campaigns conducted by Dragonfly (aka Energetic Bear and Crouching Yeti) and Dymalloy, which Dragos discovered while analyzing Dragonfly attacks.
According to Dragos, a report published by the DHS in October 2017 combined Dragonfly attacks with Allanite activity. The company also noted that Allanite’s operations closely resemble the Dragonfly-linked Palmetto Fusion campaign described by the DHS in July 2017. However, while their targets and techniques are similar, Dragos believes Allanite is different from Dragonfly and Dymalloy.
Allanite leverages phishing and watering hole attacks to gain access to targeted networks. The group does not use any malware and instead relies on legitimate tools often available in Windows, Dragos says.
While the U.S. government and private sector companies have linked Allanite activity to Russia, Dragos says it “does not corroborate the attribution of others.”
In July 2017, US officials told the press that the hackers had not gained access to operational networks, but Dragos confirmed third-party reports that Allanite did in fact harvest information directly from ICS networks.
Allanite has been active since at least May 2017 and continues to conduct campaigns. Its operations target both business and ICS networks at electric utilities in the US and UK in an effort to conduct reconnaissance and collect intelligence.
Dragos believes with moderate confidence that the threat actor gains access to industrial systems in an effort to obtain information needed to develop disruptive capabilities and be ready in case it decides to cause damage. However, the security firm says the group has yet to actually cause any disruption or damage.
Dragos’ report on Allanite is the first in a series focusing on threat groups targeting critical infrastructure. Information on each actor will be made available through an Activity Groups dashboard, with full technical details made available to paying customers.
Is The Education System Keeping Women Out of Cybersecurity?
10.5.2018 securityweek Cyber
While the Gender Bias in Professions Remains Strong, There Are Indications That Factors Beyond Genuine Aptitude Are at Play
Despite the increasing cybersecurity skills shortage, projected by Frost & Sullivan to reach 1.8 million unfilled roles by 2020, we are yet to engage with the obvious solution. There is currently more interest in reducing vacancies using artificial intelligence (AI) and automation than in training youngsters to adopt the profession.
The problem with AI as a solution, according to a report published Tuesday by ProtectWise, is, "The impact of artificial intelligence on the man-hours required to staff a security operations center is basically nil today -- and will be for a significant amount of time."
This is confirmed by a separate survey (PDF) published Wednesday by Exabeam. Exabeam queried 481 cybersecurity professionals around the world. It found nearly 68% of respondents reported they do not currently use AI or ML in their jobs or don’t have plans to use in the future, even though 75% agreed AI/ML can make their job better or easier and improve security.
The short-term solution to the skills gap must necessarily be to increase skills rather than the long-term reduction of demand.
Together with the skills gap is an awareness of the paucity of women in security. This is also confirmed by Exabeam's study, which found that 90% of security professionals are male.
ProtectWise returned to the data it gathered in an ESG survey last year, but specifically looked for any indication that the two problems may be linked: in short, could increasing the number of young women entering the security profession reduce the skills gap?
What it found is somewhat counterintuitive. Although the well-known gender bias in professions remains strong, there are indications that factors other than genuine aptitude are at play. In high school, twice as many men as women plan to study engineering, computer science or mathematics at college. Similarly, twice as many men as women consider IT as a future career.
At the same time, women are less confident in their aptitude for a career in cybersecurity. Forty-two percent of women profess to not knowing enough about the subject, compared to 35% of men; while 34% of women (compared to 25% of men) consider they do not have the aptitude.
What is surprising, however, is that the early exposure to technology that is believed to be the springboard to first studies and then careers in IT is stronger in young women than it is in young men. As many women as men game online, and the numbers that consider themselves to be early adopters of technology are also similar.
In some cases, however, young women are actually the early adopters -- 52% of women had tried VR compared to 42% of men; and more women than men have advanced technology in their household.
One conclusion that can be drawn is that the education system is the block. Young men and women enter the system with an equal aptitude for technology in general; but fewer women than men leave it to pursue technology careers. More concerning for cybersecurity is that very few of either gender consider security as a potential career.
A primary reason is that they simply do not have the option. Sixty-nine percent of the respondents said they had never taken a cybersecurity class in school, and 65% said that their school never offered a cybersecurity course.
This lack of interest from the schools does their pupils no favors. The Exabeam study shows a median salary range of $75,000 - $100,000 per year, with 34% earning more than $100,000 per year (chief security officers can expect around $200,000 and above); while 86% of existing professionals would recommend a career as a security analyst to new graduates. Good money and job satisfaction should be strong incentives.
ProtectWise co-founder and CTO Gene Stevens believes the problem is a latency between society's needs and society's understanding of those needs. “Our society has not yet embraced cybersecurity as a civilization-defining competency, yet it is exactly central to our capacity to function in this massively technological age," he told SecurityWeek. "In foundational terms, it's an education and awareness problem."
The solution is a sustained effort to get cybersecurity into the educational syllabus. "In education," he continued, "one of the best roads is to have cybersecurity technology standards baked into state standards of expectation for all students. State boards review these on a regular basis, usually every three to five years. We should reach out to departments of education state by state to engage on this topic. As digital citizenship is currently being developed locally, we need to reach out to school counselors and partner with teachers -- reaching out to education associations to offer resource and support is easy and could be highly beneficial."
While educational restraints may be playing a part in a lacking cybersecurity workforce, Ashley Arbuckle, Cisco’s VP of Security Services, believes that inclusion will help put a stop the perpetual scrambling for cybersecurity workers.
“No matter how you measure it, the number of unfilled cybersecurity positions is big and it’s a problem we’ve been lamenting for years,” Arbuckle wrote in a recent SecurityWeek column. “The traditional approach to address the shortage has been to encourage more individuals to pursue technical and engineering degrees. But which individuals? And if you aren’t “technical” does that mean there’s no room for you in cybersecurity? If we think more broadly about the type of talent we need and how to build even better security teams, we’ll see that the solution to the workforce gap is through inclusion.”
Arbuckle also believes there is no one definition of a cybersecurity professional and no one path to get there. “By increasing awareness of the varied skills needed and providing support to cultivate such talent, we have an opportunity to expand the pool of workers and improve security and financial performance in the process, with teams that are based on inclusion and diversity. We need to marshal all our resources to strengthen our defenses,” Arbuckle said.
Lenovo releases updates to fix Secure Boot flaw in servers and other issues
10.5.2018 securityaffairs Vulnerebility
Lenovo has released security patches that address the High severity vulnerability CVE-2017-3775 in the Secure Boot function on some System x servers.
The standard operator configurations disable signature checking, this means that some Server x BIOS/UEFI versions do not properly authenticate signed code before booting it.
“Lenovo internal testing discovered some System x server BIOS/UEFI versions that, when Secure Boot mode is enabled by a system administrator, do not properly authenticate signed code before booting it. As a result, an attacker with physical access to the system could boot unsigned code.” reads the security advisory.
“Lenovo ships these systems with Secure Boot disabled by default, because signed code is relatively new in the data center environment, and standard operator configurations disable signature checking.”
An attacker can exploit the vulnerability to execute unauthenticated code at the bootstrap of the affected system. The CVE-2017-3775 vulnerability impacts a dozen models, including Flex System x240 M5, x280 X6, x480 X6, x880, x3xxx series, and NeXtScale nx360 M5 devices.
Lenovo disclosed the complete list of impacted products and provided the related BIOS/UEFI update, it also explained that they ship with Secure Boot disabled by default.

Lenovo also issued a patch to address the CVE-2018-9063 buffer overflow in Lenovo System Update Drive Mapping Utility. -The flaw could be exploited by attackers for different kind of attacks, include the execution of arbitrary code on the target machine.
“MapDrv (C:\Program Files\Lenovo\System Update\mapdrv.exe) contains a local vulnerability where an attacker entering very large user ID or password can overrun the program’s buffer, causing undefined behaviors, such as execution of arbitrary code.” reads the security advisory.
“No additional privilege is granted to the attacker beyond what is already possessed to run MapDrv.”
The flaw could be easily exploited by an attacker entering very large user ID or password in order to overrun the program’s buffer. The attacker could potentially execute code with the MapDrv’s privileges.
Users need to update the application to Lenovo System Update version 5.07.0072 or later.
Users can launch Lenovo System Update to automatically checks for newer versions and accept the update if present, otherwise it is possible to manually update the application downloading the latest app version from the company website.
Analysis of CVE-2018-8174 VBScript 0day and APT actor related to Office targeted attack
10.5.2018 securityaffairs Vulnerebility
Recently, the Advanced Threat Response Team of 360 Core Security Division detected an APT attack exploiting a 0-day vulnerability tracked as CVE-2018-8174. Now the experts published a detailed analysis of the flaw.
I Overview
Recently, the Advanced Threat Response Team of 360 Core Security Division detected an APT attack exploiting a 0-day vulnerability and captured the world’s first malicious sample that uses a browser 0-day vulnerability. We codenamed the vulnerability as “double kill” exploit. This vulnerability affects the latest version of Internet Explorer and applications that use the IE kernel. When users browse the web or open Office documents, they are likely to be potential targets. Eventually the hackers will implant backdoor Trojan to completely control the computer. In response, we shared with Microsoft the relevant details of the 0day vulnerability in a timely manner. This APT attack was analyzed and attributed upon the detection and we now confirmed its association with the APT-C-06 Group.
On April 18, 2018, as soon as 360 Core Security detected the malicious activity, we contacted Microsoft without any delay and submitted relevant details to Microsoft. Microsoft confirmed this vulnerability on the morning of April 20th and released an official security patch on May 8th. Microsoft has fixed the vulnerability and named it CVE-2018-8174. After the vulnerability was properly resolved, we published this report on May 9th, along with further technical disclosure of the attack and the 0day.
II Affection in China
According to the sample data analysis, the attack affected regions in China are mainly distributed in provinces that actively involved in foreign trade activities.Victims include trade agencies and related organizations.
III Attack Procedure Analysis
The lure documents captured in this attack are in Yiddish. The attackers exploit office with OLE autolink objects (CVE-2017-0199) to embed the documents onto malicious websites. All the exploits and malicious payload were uploaded through remote servers.

Once victims opened the lure document, Word will firstly visit a remote website of IE vbscript 0day (CVE-2018-8174) to trigger the exploit. Afterward, Shellcode will be running to send several requests to get payload from remote servers. The payload will then be decrypted for further attack.

While the payload is running, Word will release three DLL backdoors locally. The backdoors will be installed and executed through PowerShell and rundll32. UAC bypass was used in this process, as well as file steganography and memory reflection uploading, in order to bypass traffic detection and to complete loading without any files.

IV IE VBScript 0day (CVE-2018-8174)
1. Timeline
On April 18, 2018, Advanced Threat Response Team of 360 Core Security Division detected a high-risk 0day vulnerabilities. The vulnerability affects the latest version of Internet Explorer and applications that use the IE kernel and has been found to be used for targeted APT attacks. On the same day, 360 immediately communicated with Microsoft and submitted details of the vulnerability to Microsoft. Microsoft confirmed this vulnerability on the morning of April 20th and released an official security patch on May 8th. The 0day vulnerability was fixed and it was named CVE-2018-8174.
CVE-2018-8174 is a remote code execution vulnerability of Windows VBScript engine. Attackers can embed malicious VBScript to Office document or website and then obtain the credential of the current user, whenever the user clicks, to execute arbitrary code.
2. Vulnerability Principles
Through the statistical analysis of the vulnerability samples, we found out that obfuscation was used massively. Therefore, we filtered out all the duplicated obfuscation and renamed all the identifiers.
Seeing from the POC created by using the exploit samples we captured, the principles of the exploit is obvious. The POC samples are as below:
Detailed procedures:

1) First create a cla1 instance assigned to b, and then assign value 0 to b, because at this point b’s referenced count is 1, causing cla1’s Class_Terminate function to be called.
2) In the Class_Terminate function, again assign b to c and assign 0 to b to balance the reference count.
3) After the Class_Terminate return, the memory pointed to by the b object will be released, so that a pointer to the memory data of the released object b is obtained.
4) If you use another object to occupy the freed memory, it will lead to the typical UAF or Type Confusion problem
3. Exploitation
The 0-day exploit exploits UAF multiple times to accomplish type confusion. It fakes and overrides the array object to perform arbitrary address reading and writing. In the end, it releases code to execute after constructing an object. Code execution does not use the traditional ROP or GodMod, but through the script layout Shellcode to stabilize the use.
Fake array to perform arbitrary address reading and writing
Mem members of 2 classes created by UAF are offset by 0x0c bytes, and an array of 0x7fffffff size is forged by reading and writing operation to the two mem members.

typedef struct tagSAFEARRAY {
USHORT cDims; // cDims = 0001
USHORT fFeatures; fFeatures =0x0880
ULONG cbElements; // the byte occupied by one element (1 byte)
ULONG cLocks;
PVOID pvData; // Buffer of data starts from 0x0
SAFEARRAYBOUND rgsabound[1];
} SAFEARRAY, *LPSAFEARRAY;
typedef struct tagSAFEARRAYBOUND {
ULONG cElements; // the number of elements (0x7fffffff, user space)
LONG lLbound; // the initial value of the index (starting from 0)
} SAFEARRAYBOUND, *LPSAFEARRAYBOUND;
A forged array composes of a one-dimensional array, the number of elements is 7fffffff, each element occupies 1 byte, and the element memory address is 0. So the accessible memory space for the array is from 0x00000000 to 0x7ffffffff*1. Therefore, the array can be read and written at any address. But the storage type of lIlIIl is string, so only by modifying the data type to 0x200C, i.e. VT_VARIANT|VT_ARRAY( array type), attackers can achieve their purpose.
Read the storage data of the specified parameter

In the malicious code, the above function is mainly used to read the data of the memory address specified by the parameter. The idea is to obtain the specified memory read capability via the characteristics of the first 4 bytes of the string address (namely, the content of the bstr, type, size field) returned by the lenb (bstr xx) in the vb (the data type in the VBS is bstr).
This is shown in the above code. If the input argument is addr(0x11223344), first add 4 to the value to get 0x11223348, and then set the variant type to 8 (string type). Next, call len function: if found to be BSTR type, vbscript will assume that the forward 4 bytes (0x11223344) is the address memory to store the length. So the len function will be executed and the value of the specified memory address will be returned.
Obtain Key DLL Base Address
The attacker leaks the virtual function table address of the CScriptEntryPoint object in the following way, which belongs to Vbscript.dll.
Obtain the vbscript.dll base address in the following way.
Because vbscript.dll imported msvcrt.dll, the msvcrt.dll base address was obtained by traversing the vbscript.dll import table, msvcrt.dll introduces kernelbase.dll, ntdll.dll, and finally the NtContinue, VirtualProtect function address was obtained.

Bypass DEP to execute shellcode
Use arbitrary reading and writing technique to modify the VAR type type to 0x4d, and then assign it with a value of 0 to make the virtual machine perform VAR:: Clear function.
Control with caution and let the code Execute function ntdll!ZwContinue. The first parameter CONTEXT structure was also constructed by the attacker.

Control the code with caution to execute ntdll! ZwContinue function. The first parameter CONTEXT structure is also carefully constructed by the attacker.
The first parameter of ZwContinue is a pointer to the CONTEXT structure. The CONTEXT structure is shown in the following figure, and the offset of EIP and ESP in CONTEXT can be calculated.

5. The values of the Eip and Esp in the actual runtime CONTEXT and the attacker’s intention are shown in the figure below.

V Powershell Payload
After the bait DOC file is executed, it will start to execute the Powershell command to the next step payload.

First of all, Powershell will fuzzy match incoming parameter names, and it is case-insensitive.

Second step, decrypt the obfuscated command.

Next, the script uses a special User-Agent access URL page to request the next load and execute.

The size of the requested payload file is approximately 199K. The code fragment is as follows.

We found that this code was modified from invoke-ReflectivePEInjection.ps1. buffer_x86 and buffer_x64 in the code are the same function but from different versions of dll files. File export module name: ReverseMet.dll.
DLL file decrypts ip address, port and sleep time from the configuration. After the decryption algorithm xor 0xA4, and subtracted 0x34, the code is as follows.

Decryption configuration file from the ip address 185.183.97.28 port 1021 to obtain the next load and execute.

After it connects to the tcp port, it will get 4 bytes to apply for a memory.
Subsequent acquired writes into the new thread, and execute the acquired shellcode payload, Since the port of the sample CC server is closed, we cannot get the next load for analysis.
VI UAC Bypass Payload
In addition to use PowerShell to load the payload, the bait DOC file also runs rundll32.exe to execute another backdoor locally. There are several notable features of the backdoor program it uses: the program uses COM port to copy files, realize UAC bypass and two system DLL hijacks; it also uses the default DLLs of cliconfg.exe and SearchProtocolHost.exe to take advantage of whitelist; finally in the process of component delivery, use file steganography and memory reflection loading method to avoid traffic monitoring and achieve no file landing load.

1. Retro backdoor execution
The backdoor program used in this attack is actually the Retro series backdoor known to be used by the APT-C-06 organization. The following is a detailed analysis of the implementation process of the backdoor program.
First execute the DLL disguised as a zlib library function with rundll32 and execute the backdoor installation functions uncompress2 and uncompress3.
It uses a COM port for UAC bypass, copying its own DLL to the System32 path for DLL hijacking, and the hijacked targets are cliconfg.exe and SearchProtocolHost.exe

Copy the DLL file in the AppData directory to the System32 directory through the COM interface and name it msfte.dll and NTWDBLIB.dll.
Then copy the file NTWDBLIB.dll to the System directory and execute the system’s own cliconfig to achieve DLL hijacking and load NTWDBLIB.dll.
The role of NTWDBLIB.dll is to restart the system service WSearch, and then start msfte.dll.

The script will then generate and execute the MO4TH2H0.bat file in the TEMP directory, which will delete the NTWDBLIB.DLL and its own BAT from the system directory.
Msfte.dll is the final backdoor program whose export is disguised as zlib. The core export functions are AccessDebugTracer and AccessRetailTracer. Its main function is to communicate with CC and further download and execute subsequent DLL programs.
Similar to the previously analyzed sample, it is also using image steganography and memory reflection loading. The decrypted CC communication information is as follows:

The format of the request is:
Hxxp://CC_Address /s7/config.php ?p=M&inst=7917&name=
Among them, the parameter p is the current process authority, there are two types of M and H, inst parameter is the current installation id, name is the CC_name obtained by decryption, this time is pphp.
After decryption after downloading, the process is exactly the same as the format of the previous image steganography transmission.
For the CC URL corresponding to the test request, because we did not obtain the corresponding image during the analysis, the CC is suspected to have failed.
In the implementation process, Retro disguised fake SSH and fake zlib, intended to obfuscate and interfere with users and analysts. Retro’s attack method has been used since 2016.
2. Retro backdoor evolvement
The back door program used in the APT-C-06 organization’s early APT operation was Lucker. It is a set of self-developed and customized modular Trojans. The set of Trojans is powerful, with keyboard recording, voice recording, screen capture, file capture and U disk operation functions, etc. The Lucker ‘s name comes from the PDB path of this type of Trojan, because most of the backdoor’s function use the LK abbreviation.


In the middle to late period we have discovered its evolution and two different types of backdoor programs. We have named them Retro and Collector by the PDB path extracted from the program. The Retro backdoor is an evolution of the Lucker backdoor and it actives in a series of attacks from 2016 till now. The name comes from the pdb path of this type of Trojan with the label Retro, and also has the word Retro in the initial installer.

C:\workspace\Retro\DLL-injected-explorer\zlib1.pdb
C:\workspace\Retro\RetroDLL\zlib1.pdb
The evolution of the reflective DLL injection technique can be found from the relevant PDB paths, and there are a lot of variants of this series of backdoors.

VII Attribution
1. Decryption Algorithm
During the analysis, we found the decryption algorithm that malware used is identical to APT-C-06’s decryption algorithm.
In the further analysis, we found the same decryption algorithm was used in the 64-bit version of the relevant malware.
2. PDB Path
The PDB path of the malware used in this attack has a string of “Retro”. It is one specific feature of Retro Trojan family.

3. Victims
In the process of tracing victims, we found one special compromised machine. It has a large amount of malware related to APT-C-06. By looking at these samples in chronological order, the evolution of the malicious program can be clearly seen. The victim has been under constant attack acted by APT-C-06 since 2015. The early samples on the compromised machine could be associated with DarkHotel. Then it was attacked by Lurker Trojan. Recently it was under the attack exploiting 0-day vulnerabilities CVE-2018-8174.
VIII Conclusion
APT-C-06 is an overseas APT organization which has been active for a long time. Its main targets are China and some other countries. Its main purpose is to steal sensitive data and conduct cyber-espionage. DarkHotel can be regarded as one of its series of attack activities.
The attacks against China specifically targeted government, scientific research institutions and some particular field. The attacks can be dated back to 2007 and are still very active. Based on the evidence we have, the organization may be a hacker group or intelligence agency supported by a foreign government.
The attacks against China have never stopped over the past 10 years. The Techniques the group uses keep evolving through time. Based on the data we captured in 2017, targets in China are trade related institutions and concentrated in provinces that have frequent trading activities. The group has been conducting long-term monitoring on the targets to stole confidential data.
During the decades of cyber attacks, APT-C-06 exploits several 0-day vulnerabilities and used complicated malware. It has dozens of function modules and over 200 malicious codes.
In April, 2018, the Advanced Threat Response Team of 360 Core Security Division takes the lead in capturing the group’s new APT attack using 0-day vulnerabilities (CVE-2018-8174) in the wild, and then discovers the new type attack – Office related attack exploiting 0-day VBScript vulnerabilities.
After the capture of the new activity, we contacted Microsoft immediately and shared detailed information with them. Microsoft’s official security patch was released on 8th May. Now, we published this detailed report to disclose and analyze the attack.
Further technical details including IoCs are reported in the analysis published by 360 Core Security Team at the following URL:
http://blogs.360.cn/blog/cve-2018-8174-en/
Misinterpretation of Intel docs is the root cause for the CVE-2018-8897 flaw in Hypervisors and OSs
10.5.2018 securityaffairs Vulnerebility
Developers of major operating systems and hypervisors misread documentation from Intel and introduced a the CVE-2018-8897 vulnerability into to their products.
The development communities of major operating systems and hypervisors misread documentation from Intel and introduced a potentially serious vulnerability to their products.
The CERT/CC speculates the root cause of the flaw is the developers misinterpretation of existing documentation provided by chip manufacturers.
“The MOV SS and POP SS instructions inhibit interrupts (including NMIs), data breakpoints, and single step trap exceptions until the instruction boundary following the next instruction” states the advisory published by CERT/CC.
The flaw, tracked as CVE-2018-8897, relates the way the operating systems and hypervisors handle MOV/POP to SS instructions.
“In some circumstances, some operating systems or hypervisors may not expect or properly handle an Intel architecture hardware debug exception. The error appears to be due to developer interpretation of existing documentation for certain Intel architecture interrupt/exception instructions, namely MOV to SS and POP to SS.” continues the security advisory published by CERT/CC.
The CVE-2018-8897 flaw was discovered by the security experts Nick Peterson of Everdox Tech and Nemanja Mulasmajic of triplefault.io.
The CERT/CC published a security advisory to warn of the CVE-2018-8897 flaw that impact the Linux kernel and software developed by major tech firms including Apple, the DragonFly BSD Project, Red Hat, the FreeBSD Project, Microsoft, SUSE Linux, Canonical, VMware, and the Xen Project (CERT/CC published the complete list of companies whose products may be impacted)
An attacker needs local access to exploit the vulnerability and the impact depends on the specific vulnerable software. In the worst scenario, attackers can, potentially, gain access to sensitive memory information or control low-level operating system functions.
“Therefore, in certain circumstances after the use of certain Intel x86-64 architecture instructions, a debug exception pointing to data in a lower ring (for most operating systems, the kernel Ring 0 level) is made available to operating system components running in Ring 3.” continues the advisory.
“This may allow an attacker to utilize operating system APIs to gain access to sensitive memory information or control low-level operating system functions.”

Experts explained that in the case of Linux, the flaw can trigger a denial-of-service (DoS) condition or cause the crash of the kernel.
According to Microsoft, an attacker can exploit the security flaw on Windows for privilege escalation.
“An elevation of privilege vulnerability exists when the Windows kernel fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” reads the Microsoft’s kernel advisory
“To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application to take control of an affected system.”
Security patches for CVE-2018-8897 flaw have been released for many OS, including the Linux kernel, Windows, Xen, and Red Hat.”
Proof-of-concept (PoC) exploits have been released for Windows and Linux operating systems.
The King is dead. Long live the King!
10.5.2018 Kaspersky Vulnerebility
Root cause analysis of the latest Internet Explorer zero day – CVE-2018-8174
In late April 2018, a new zero-day vulnerability for Internet Explorer (IE) was found using our sandbox; more than two years since the last in the wild example (CVE-2016-0189). This particular vulnerability and subsequent exploit are interesting for many reasons. The following article will examine the core reasons behind the latest vulnerability, CVE-2018-8174.
Searching for the zero day
Our story begins on VirusTotal (VT), where someone uploaded an interesting exploit on April 18, 2018. This exploit was detected by several AV vendors including Kaspersky, specifically by our generic heuristic logic for some older Microsoft Word exploits.
Virustotal scan results for CVE-2018-8174
After the malicious sample was processed in our sandbox system, we noticed that a fully patched version of Microsoft Word was successfully exploited. From this point we began a deeper analysis of the exploit. Let’s take a look at the full infection chain:
Infection chain
The infection chain consists of the following steps:
A victim receives a malicious Microsoft Word document.
After opening the malicious document, a second stage of the exploit is downloaded; an HTML page containing VBScript code.
The VBScript code triggers a Use After Free (UAF) vulnerability and executes shellcode.
Initial analysis
We’ll start our analysis with the initial Rich Text Format (RTF) document, that was used to deliver the actual exploit for IE. It only contains one object, and its contents are obfuscated using a known obfuscation technique we call “nibble drop“.
Obfuscated object data in RTF document
After deobfuscation and hex-decoding of the object data, we can see that this is an OLE object that contains a URL Moniker CLSID. Because of this, the exploit initially resembles an older vulnerability leveraging the Microsoft HTA handler (CVE-2017-0199).
URL Moniker is used to load an IE exploit
With the CVE-2017-0199 vulnerability, Word tries to execute the file with the default file handler based on its attributes; the Content-Type HTTP header in the server’s response being one of them. Because the default handler for the “application/hta” Content-Type is mshta.exe,it is chosen as the OLE server to run the script unrestricted. This allows an attacker to directly call ShellExecute and launch a payload of their choice.
However, if we follow the embedded URL in the latest exploit, we can see that the content type in the server’s response is not “application/hta”, which was a requirement for CVE-2017-0199 exploitation, but rather “text/html”. The default OLE server for “text/html” is mshtml.dll, which is a library that contains the engine, behind Internet Explorer.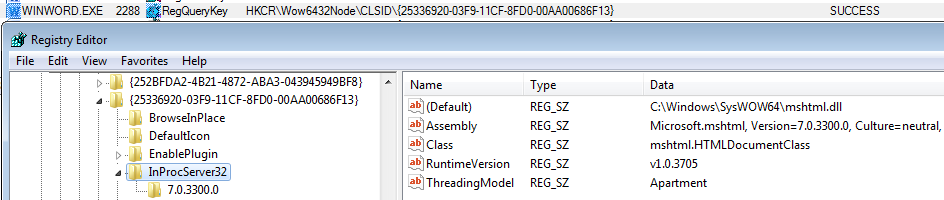
WINWORD.exe querying registry for correct OLE server
Furthermore, the page contains VBScript, which is loaded with a safemode flag set to its default value, ‘0xE’. Because this disallows an attacker from directly executing a payload, as was the case with the HTA handler, an Internet Explorer exploit is needed to overcome that.
Using a URL moniker like that to load a remote web page is possible, because Microsoft’s patch for Moniker-related vulnerabilities (CVE-2017-0199, CVE-2017-8570 and CVE-2017-8759) introduced an activation filter, which allows applications to specify which COM objects are restricted from instantiating at runtime.
Some of the filtered COM objects, restricted from creating by IActivationFilter in MSO.dll
At the time of this analysis, the list of filtered CLSIDs consisted of 16 entries. TheMSHTML CLSID ({{25336920-03F9-11CF-8FD0-00AA00686F13}}) is not in the list, which is why the MSHTML COM server is successfully created in Word context.
This is where it becomes interesting. Despite a Word document being the initial attack vector, thevulnerability is actually in VBScript, not in Microsoft Word. This is the first time we’ve seen a URL Moniker used to load an IE exploit, and we believe this technique will be used heavily by malware authors in the future. This technique allows one to load and render a web page using the IE engine, even if default browser on a victim’s machine is set to something different.
The VBScript in the downloaded HTML page contains both function names and integer values that are obfuscated.
Obfuscated IE exploit
Vulnerability root cause analysis
For the root cause analysis we only need to look at the first function (‘TriggerVuln’) in the deobfuscated version which is called right after ‘RandomizeValues’ and ‘CookieCheck’.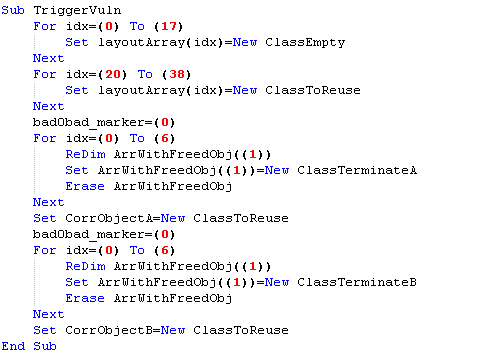
Vulnerability Trigger procedure after deobfuscation
To achieve the desired heap layout and to guarantee that the freed class object memory will be reused with the ‘ClassToReuse’ object, the exploit allocates some class objects. To trigger the vulnerability this code could be minimized to the following proof-of-concept (PoC):
CVE-2018-8174 Proof Of Concept
When we then launch this PoC in Internet Explorer with page heap enabled we can observe a crash at the OLEAUT32!VariantClear function.
Access Violation on a call to freed memory
Freed memory pointer is reused when the second array (ArrB) is destroyed
With this PoC we were able to trigger a Use-after-free vulnerability; both ArrA(1) and ArrB(1) were referencing the same ‘ClassVuln’ object in memory. This is possible because when “Erase ArrA” is called, the vbscript!VbsErase function determines that the type of the object to delete is a SafeArray, and then calls OLEAUT32!SafeArrayDestroy.
It checks that the pointer to a tagSafeArray structure is not NULL and that its reference count, stored in the cLocks field is zero, and then continues to call ReleaseResources.
VARTYPE of ArrA(1) is VT_DISPATCH, so VBScriptClass::Release is called to destruct the object
ReleaseResources, in turn will check the fFeatures flags variable, and since we have an array of VARIANTs, it will subsequently call VariantClear; a function that iterates each member of an array and performs the necessary deinitialization and calls the relevant class destructor if necessary. In this case, VBScriptClass::Release is called to destroy the object correctly and handle destructors like Class_Terminate, since the VARTYPE of ArrA(1) is VT_DISPATCH.
Root cause of CVE-2018-8174 – ‘refCount’ being checked only once, before TerminateClass function
This ends up being the root cause of the vulnerability. Inside the VBScriptClass::Release function, the reference count is checked only once, at the beginning of the function. Even though it can be (and actually is, in the PoC) incremented in an overloaded TerminateClass function, no checks will be made before finally freeing the class object.
Class_Terminate is a deprecated method, now replaced by the ‘Finalize’ procedure. It is used to free acquired resources during object destruction and is executed as soon as object is set to nothing and there are no more references to that object. In our case, the Class_Terminate method is overloaded, and when a call to VBScriptClass::TerminateClass is made, it is dispatched to the overloaded method instead. Inside of that overloaded method, another reference is created to the ArrA(1) member. At this point ArrB(1) references ArrA(1), which holds a soon to be freed ClassVuln object.

Crash, due to calling an invalid virtual method when freeing second object
After the Class_Terminate sub is finished, the object at Arr(1) is freed, but ArrB(1) still maintains a reference to that freed class object. When the execution continues, and ArrB is erased, the whole cycle repeats, except that this time, ArrB(1) is referencing a freed ClassVuln object, and so we observe a crash when one of the virtual methods in the ClassVuln vtable is called.
Conclusion
In this write up we analyzed the core reasons behind CVE-2018-8174, a particularly interesting Use-After-Free vulnerability that was possible due to incorrect object lifetime handling in the Class_Terminate VBScript method. The exploitation process is different from what we’ve seen in exploits for older vulnerabilities (CVE-2016-0189 and CVE-2014-6332) as the Godmode technique is no longer used. The full exploitation chain is as interesting as the vulnerability itself, but is out of scope of this article.
With CVE-2018-8174 being the first public exploit to use a URL moniker to load an IE exploit in Word, we believe that this technique, unless fixed, will be heavily abused by attackers in the future, as It allows you force IE to load ignoring the default browser settings on a victim’s system.
We expect this vulnerability to become one of the most exploited in the near future, as it won’t be long until exploit kit authors start abusing it in both drive-by (via browser) and spear-phishing (via document) campaigns. To stay protected, we recommend applying latest security updates, and using a security solution with behavior detection capabilities.
In our opinion this is the same exploit which Qihoo360 Core Security Team called “Double Kill” in their recent publication. While this exploit is not limited to browser exploitation, it was reported as an IE zero day, which caused certain confusion in the security community.
After finding this exploit we immediately shared the relevant information with Microsoft and they confirmed that it is in fact CVE-2018-8174.
This exploit was found in the wild and was used by an APT actor. More information about that APT actor and usage of the exploit is available to customers of Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
Detection
Kaspersky Lab products successfully detect and block all stages of the exploitation chain and payload with the following verdicts:
HEUR:Exploit.MSOffice.Generic – RTF document
PDM:Exploit.Win32.Generic – IE exploit – detection with Automatic Exploit Prevention technology
HEUR:Exploit.Script.Generic – IE exploit
HEUR:Trojan.Win32.Generic – Payload
IOCs
b48ddad351dd16e4b24f3909c53c8901 – RTF document
15eafc24416cbf4cfe323e9c271e71e7 – Internet Explorer exploit (CVE-2018-8174)
1ce4a38b6ea440a6734f7c049f5c47e2 – Payload
autosoundcheckers[.]com
Signal disappearing messages can be recovered by the macOS client
10.5.2018 securityaffairs Apple
The macOS client for the Signal fails to properly delete disappearing messages from the recipient’s system, potentially exposing sensitive messages.
Signal is considered the most secure instant messaging app, searching for it on the Internet it is possible to read the Edward Snowden’ testimony:
“Use anything by Open Whisper Systems” Snowden says.
The Cryptographer and Professor at Johns Hopkins University Matt Green and the popular security expert Bruce Schneier are other two admirers of the Signal app
Signal was also approved by the U.S. Senate for official communications among staff members.
But even most complex and efficient software could be affected by severe bugs.
The macOS client for the Signal fails to properly delete disappearing messages from the recipient’s system, potentially exposing sensitive messages.
The disappearing messages in Signal are automatically deleted after a specific interval of time set up by the sender. The peculiarity of the feature is that there is no trace of the destroyed message on the receiver’s device or Signal servers, at least this is the expected behavior.
The security expert Alec Muffett discovered that the messages once disappeared can still be recovered from the recipient’s device.

Alec Muffett
@AlecMuffett
#HEADSUP: #Security Issue in #Signal. If you are using the @signalapp desktop app for Mac, check your notifications bar; messages get copied there and they seem to persist — even if they are "disappearing" messages which have been deleted/expunged from the app.
8:14 PM - May 8, 2018
42
55 people are talking about this
Twitter Ads info and privacy
Former NSA hacker and security expert Patrick Wardle analyzed the issue and discovered that macOS client makes a copy (partial for long messages) of disappearing messages in a user-readable database of macOS’s Notification Center. This copy could be recovered anytime by researchers and hackers.
“While the application deletes the messages (once the ‘disappear’ time is hit) from the app’s UI – the message may still remain in macOS’s Notification Center.” wrote Wardle.
“This apparently occurs because:
Signal displays (posts) a message notification (with the content of the message) to the Notification Center (if the app is not in the foreground).
The OS automatically dismisses the notification ‘banner’ … but the notification (which contains the message contents) remain in the Notification Center.”
Signal, does not explicitly delete this notification when it deletes messages from the app UI.”
To discover where the disappearing messages are stored Wardle used the macOS’s built-in file monitoring utilty ‘fs_usage.’
“Looks like the ‘user notification daemon’ (usernoted) is accessing a file related to a database (specifically a SQLite write-ahead log).” added the expert.
“Running the ‘file’ command on the ‘db2/db’ file reveals (rather unsurprisingly) it’s an SQLite database, that is readable with user (i.e. non-root) permissions”
Wardle noticed the ‘record’ table that contains the notifications, including their contents.

Data is stored in ‘binary’ format so Wardle converted it from hex to ASCII, obtaining “bplist00”. It is a binary plist that can be easily decoded/parsed using the biplist module.
The decoded text included the text of all Signal messages, including the disappearing messages.
“Well Alec, hope this explains exactly why those ‘disappearing’ Signal messages still are hanging around. In short, anything that gets displayed as a notification (yes, including ‘disappearing’ Signal messages) in the macOS Notification Center, is recorded by the OS.” concluded Wardle.
“If the application wants the item to be removed from the Notification Center, it must ensure that the alert is dismissed by the user or programmatically! However, it is not clear that this also ‘expunges’ the notifications (and the their contents) from the notification database… i’m guessing not! If this is the case, Signal may have to avoid generating notifications (containing the message body) for disappearing messages…”
The good news is that the Signal’s iOS application is not affected at least the messages are removed from the iOS Notification Center once the user has viewed them.
SAP Patches Internet Graphics Server Flaws
9.5.2018 securityweek Vulnerebility
SAP this week released its May 2018 set of security patches to address more than a dozen vulnerabilities across its product portfolio, including four bugs in Internet Graphics Server.
The company released 9 new Security Notes as part of the SAP Security Patch Day, to which Support Package Notes and updates to previously released notes are added, for a total of 16 notes released since the previous Patch Day (the second Tuesday of the previous month).
Most of the security bugs addressed this month were rated Medium severity, with just one assessed with a Low severity rating.
Missing authorization checks and Denial of service issues were the most commonly encountered vulnerabilities, but SAP also addressed Cross-Site Scripting, code injection, information disclosure, open redirect, XML external entity, implementation flaw, and spoofing bugs.
SAP Internet Graphics Server (IGS), the engine used by SAP for generating visual components like graphics or charts, was the most affected product this month, accounting for four of the Security Notes.
The vulnerabilities addressed in it include CVE-2018-2420 – Unrestricted File Upload (allowing an attacker to upload any file (including script files) without proper file format validation), CVE-2018-2421 and CVE-2018-2422 – Denial of Service, and CVE-2018-2423 – Denial of Service in IGS HTTP and RFC listener.
By exploiting CVE-2018-2420, an attacker could “gain access to user’s session and learn business-critical information, in some cases it is possible to get control over this information. In addition, XSS can be used for unauthorized modifying of displayed site content,” ERPScan reveals.
CVE-2018-2420 and CVE-2018-2421 are addressed in security notes #2615635 and #2616599, both expected to be discussed at an upcoming security conference in June.
SAP has addressed numerous vulnerabilities in IGS over the past months, including Denial of Service, Cross-Site Scripting (XSS), and Log Injection attacks, amongst others, Onapsis points out.
Two notes released in February (#2525222) and March (#2538829) addressed together more than 15 vulnerabilities, some very severe.
Another important vulnerability addressed this month is CVE-2018-2418, a Code Injection in SAP MaxDB ODBC Driver. The flaw allows an attacker to inject and run their own code, obtain additional sensitive information, modify or delete data, change the output of the system, create new users, control the behavior of the system, or escalate privileges and perform a DoS attack.
This month, SAP also re-released security note #2190621 (initially published two and a half years ago) with updated CVSS, prerequisite and solution information related to incorrect logging of IP addresses in the Security Audit Logging (SAL) function.
In some environments where the SAP system is behind a proxy or a NAT, the original client IP address is logged instead of the NAT-translated IP address. Not only can client IP addresses be easily manipulated, but the upcoming General Data Protection Regulation (GDPR) could consider client IP addresses as personal data, Onapsis notes.
A couple of weeks ago, Onapsis revealed that 9 out of 10 SAP systems were found to be vulnerable to a SAP Netweaver bug that was first identified in 2005. The vulnerability provides an attacker with unrestricted access to the system, allowing them to read information, extract data, or shut the system down.
“The threat still exists within the default security settings of every Netweaver based SAP product such as SAP ERP, SAP CRM, S/4 HANA, SAP GRC Process and Access Control, SAP Process Integration/Exchange Infrastructure (PI/XI), SAP Solution Manager, SAP SCM, SAP SRM and others,” the firm explains.
Google Releases Additional Meltdown Mitigations for Android
9.5.2018 securityweek Android
As part of its May 2018 Android Security Bulletin, Google this week released additional mitigations for the Meltdown attack that impacts microprocessors from Intel, AMD, and other vendors.
The attack leverages CVE-2017-5754, a security vulnerability that allows applications to bypass memory isolation and read arbitrary kernel memory locations. Meltdown was made public in January 2018 alongside Spectre, an attack residing in speculative execution (leveraging CVE-2017-5753 and CVE-2017-5715).
In January, Google released protections for both Meltdown and Spectre attacks, and this month delivered additional mitigations as part of the 2018-05-05 security patch level. Impacting Kernel components, the issue was addressed along with CVE-2017-16643, an information disclosure in USB driver.
“The most severe vulnerability in this section could enable a local malicious application to bypass operating system protections that isolate application data from other applications,” Google notes in an advisory.
The May 2018 Android Security Bulletin is split into two parts, the first being the 2018-05-01 security patch level, which addresses 7 High severity vulnerabilities in Android runtime, Framework, Media framework, and System.
The bugs include Information Disclosure, Elevation of Privilege, and Denial of Service and impact Android 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0, and 8.1 releases.
In addition to the Meltdown mitigations, the 2018-05-05 security patch level also includes patches for security flaws in NVIDIA and Qualcomm components.
Three vulnerabilities were addressed in NVIDIA components: an elevation of privilege rated Critical, along with an information disclosure and an elevation of privilege assessed as High risk. The most severe of the vulnerabilities could allow a malicious application to execute code within the context of the trusted execution environment (TEE).
A total of 11 vulnerabilities were addressed in Qualcomm components, including a Critical remote code execution bug that could be exploited by an attacker over WLAN. Rated High severity, the remaining bugs included 9 elevation of privilege flaws and one denial of service issue.
Also this week, Google released a new set of patches for the Pixel and Nexus devices to address a total of 34 security bugs. Impacting Framework, Media framework, System, and Kernel, NVIDIA and Qualcomm components, the vulnerabilities feature a Moderate severity rating (two are considered High risk on Android 6.0 and 6.0.1).
In addition to security patches, the Pixel / Nexus Security Bulletin—May 2018 includes a couple of functional updates to address issues not related to the security of these devices.
Misinterpretation of Intel Docs Leads to Flaw in Hypervisors, OSs
9.5.2018 securityweek Vulnerebility
The developers of several major operating systems and hypervisors misinterpreted documentation from Intel and introduced a potentially serious vulnerability to their products.
According to an advisory published on Tuesday by CERT/CC, the flaw impacts the Linux kernel and software made by Apple, the DragonFly BSD Project, Red Hat, the FreeBSD Project, Microsoft, SUSE Linux, Canonical, VMware, and the Xen Project. CERT/CC also provides a long list of other companies whose products may be affected.
The vulnerability, tracked as CVE-2018-8897, exists due to the way operating systems and hypervisors handle MOV/POP to SS instructions. Exploitation requires local access to the targeted system.
Impact varies depending on the affected software. In the case of Linux, it can lead to a crash of the kernel and a denial-of-service (DoS) condition. Microsoft says an attacker can exploit the security hole on Windows for privilege escalation. The Xen Project says a malicious PV guest can escalate privileges to the ones of the hypervisor, while CERT/CC warns that an attacker can “read sensitive data in memory or control low-level operating system functions.”
Patches have been released for the Linux kernel, Windows, Xen and various Linux distributions, but in most cases the issue has been classified only as “moderate” or “important.” Proof-of-concept (PoC) exploits have been created for both Windows and Linux.
The researchers who discovered the vulnerability, Nick Peterson of Everdox Tech and Nemanja Mulasmajic of triplefault.io, say it impacts both Intel and AMD hardware. A paper published by the experts provides technical details.
According to CERT/CC, the problem appears to exist due to developers misinterpreting existing documentation.
“The MOV SS and POP SS instructions inhibit interrupts (including NMIs), data breakpoints, and single step trap exceptions until the instruction boundary following the next instruction,” CERT/CC wrote in its advisory.
“If the instruction following the MOV to SS or POP to SS instruction is an instruction like SYSCALL, SYSENTER, INT 3, etc. that transfers control to the operating system at Current Privilege Level (CPL) < 3, a debug exception is delivered after the transfer to CPL < 3 is complete. Such deferred #DB exceptions by MOV SS and POP SS may result in unexpected behavior.
“Therefore, in certain circumstances after the use of certain Intel x86-64 architecture instructions, a debug exception pointing to data in a lower ring (for most operating systems, the kernel Ring 0 level) is made available to operating system components running in Ring 3. This may allow an attacker to utilize operating system APIs to gain access to sensitive memory information or control low-level operating system functions,” CERT/CC added.
Siemens Patches DoS Flaws in Medium Voltage Converters
9.5.2018 securityweek ICS
Siemens has released updates for many of its SINAMICS medium voltage converters to address two remotely exploitable denial-of-service (DoS) vulnerabilities.
According to advisories published by ICS-CERT and Siemens, the flaws impact SINAMICS GH150, GL150, GM150, SL150, SM120 and SM150 converters, which are used worldwide in the energy, chemical, critical manufacturing, water and wastewater, and food and agriculture sectors.Siemens patches two DoS vulnerabilities in SINAMICS medium voltage converters
The more serious of the flaws, identified as CVE-2017-12741 and classified “high severity,” can be exploited to cause a DoS condition by sending specially crafted packets to the device on UDP port 161.
The second weakness, tracked as CVE-2017-2680 and rated “medium,” can be exploited by sending specially crafted PROFINET DCP broadcast packets to the targeted device. This issue is less serious due to the fact that exploitation requires direct Layer 2 access to the impacted product. Siemens noted that PROFIBUS interfaces are not affected.
In both cases, manual intervention is required to restore the device after it has entered a DoS condition.

The vulnerabilities can be patched by updating the firmware to versions 4.7 SP5 HF7, 4.7 HF30 or 4.8 SP2. Siemens says attacks involving CVE-2017-12741 can also be mitigated by blocking network access to port 161.
While in general DoS vulnerabilities may not pose a major risk, these types of weaknesses can have a significant impact in industrial environments, where availability is often crucial.
Google Brings Android to Internet of Things
9.5.2018 securityweek IoT
Less than a month after Microsoft announced an operating system built for Internet of Things (IoT) security, Google is releasing its own platform for IoT: Android Things.
The managed operating system was designed to provide manufacturers with all the ingredients for a winning IoT recipe: certified hardware, rich developer APIs, and secure managed software updates via Google’s infrastructure.
The platform has been in developer preview until this week, and has already registered over 100,000 SDK downloads, Google says. More than 10,000 developers have provided feedback on Android Things, ultimately leading to the platform’s initial release.
Android Things 1.0 was released with support for new System-on-Modules (SoMs) based on the NXP i.MX8M, Qualcomm SDA212, Qualcomm SDA624, and MediaTek MT8516 hardware platforms. Raspberry Pi 3 Model B and NXP i.MX7D devices (but not NXP i.MX6UL) will continue to be supported for development purposes.
“These modules are certified for production use with guaranteed long-term support for three years, making it easier to bring prototypes to market. Development hardware and reference designs for these SoMs will be available in the coming months,” Google says.
More important, however, is Google’s aim to provide devices running Android Things with timely software updates over-the-air (OTA). All devices will have automatic updates on by default, and stability fixes and security patches will arrive on production hardware platforms.
Currently, Google is releasing patches for Android devices on a monthly basis, in an attempt to improve the overall security stance of the platform. The company started delivering these monthly updates in 2015, after the Stagefright flaw was said to impact nearly one billion devices.
Android Things developers looking to ship commercial products running the new platform are required to sign a distribution agreement with Google to be able to deliver software updates to all devices (currently only 100 active devices are supported in the Android Things Console).
“For each long-term support version, Google will offer free stability fixes and security patches for three years, with additional options for extended support. Even after the official support window ends, you will still be able to continue to push app updates to your devices,” the Internet giant explains.
The Android Things Console also provides developers with the possibility to configure hardware peripherals.
Google has already partnered with leading manufacturers for the release of Android Things devices. Thus, Smart Speakers from LG and iHome and Smart Displays from Lenovo, LG, and JBL are expected to arrive on shelves this summer.
Developers interested in building products running Android Things can apply for a special limited program to partner with the Android Things team for technical guidance and support.
May 2018 Android Security Bulletin includes additional Meltdown fix
9.5.2018 securityaffairs Android
Google releases additional Meltdown mitigations for Android as part of the May 2018 Android Security Bulletin. The tech giant also addresses flaws in NVIDIA and Qualcomm components.
Both Meltdown and Spectre attacks could be exploited by attackers to bypass memory isolation mechanisms and access target sensitive data.
The Meltdown attack (CVE-2017-5754 vulnerability) could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The good news is that Meltdown attacks are not easy to conduct and the risk of exploitation is considered low.
Early this year, Google released mitigations for both Meltdown and Spectre attacks, and not delivered additional mitigations. The Meltdown mitigation was addressed along with the information disclosure flaw in USB driver tracked as CVE-2017-16643.
“The most severe vulnerability in this section [Kernel components] could enable a local malicious application to bypass operating system protections that isolate application data from other applications,” reads the security advisory published by Google.
The May 2018 Android Security Bulletin is composed of two parts, the first one being the 2018-05-01 security patch level, that addresses seven High severity issues (CVE-2017-13309, CVE-2017-13310, CVE-2017-13311, CVE-2017-13312, CVE-2017-13313, CVE-2017-13314, CVE-2017-13315) in Android runtime, Framework, Media framework, and System.
The flaws addressed in the 2018-05-01 security patch level include Information Disclosure, Elevation of Privilege, and Denial of Service that affects Android 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0, and 8.1 releases.
The second section is the “2018-05-05 security patch level vulnerability details” that includes details for each of the security vulnerabilities that apply to the 2018-05-05 patch level.
The 2018-05-05 security patch level includes patches for security vulnerabilities affecting NVIDIA and Qualcomm components.
Three vulnerabilities that were fixed in the NVIDIA components are CVE-2017-6289, CVE-2017-5715, CVE-2017-6293, respectively a critical elevation of privilege, an information disclosure and an elevation of privilege ranked as High risk.
“The most severe vulnerability in this section could enable a local malicious application to execute arbitrary code within the context of the TEE.” continues the advisory.
Google addressed 11 vulnerabilities in Qualcomm components, including a Critical remote code execution flaw that could be exploited by an attacker over WLAN. The remaining issued are 9 elevation of privilege vulnerabilities and one denial of service issue.
Are you using Python module ‘SSH Decorator’? Newer versions include a backdoor
9.5.2018 securityaffairs Hacking
A backdoor was discovered in the Python module named SSH Decorator (ssh-decorate), that was developed by Israeli developer Uri Goren.
Are you using the Python module ‘SSH Decorator’? You need to check the version number, because newer versions include a backdoor.
The library was developed to handle SSH connections from Python code.
Early this week, a developer noticed that multiple backdoored versions of the SSH Decorate module, the malicious code included in the library allowed to collect users’ SSH credentials and sent the data to a remote server controlled by the attackers.
The remote server that received stolen data is accessible at the following address:


The following images were shared bleepingcomputer.com that first reported the news.
SSH Decorator Python SSH Backdoor 1 SSH Decorator Python SSH Backdoor 2
The Israeli developer Uri Goren, once notified to the problem, confirmed that backdoor was added by attackers.
Initially, the developer has updated the password for the PyPI Python central repo hub and published a sanitized version of the package.
“I have updated my PyPI password, and reposted the package under a new name ssh-decorator,” he said.
“I have also updated the readme of the repository, to make sure my users are also aware of this incident.”
“It has been brought to our attention, that previous versions of this module had been hijacked and uploaded to PyPi unlawfully. Make sure you look at the code of this package (or any other package that asks for your credentials) prior to using it.” reads the README file.
The presence of the backdoor in the SSH Decorator module alerted many users on Reddit, many of them accused Goren that for this reason decided to take down the package from both GitHub and PyPI — the Python central repo hub.
Developers that use the SH Decorator (ssh-decorate) module need to use the last safe version was 0.27, later version 0.28 through 0.31 were compromised.
WhatsApp Group Video Call and Instagram Video Chat Are Coming Soon
9.5.2018 thehackernews Social

Facebook announced a whole lot of new features at its 2018 Facebook F8 developers conference, including Dating on Facebook, letting users clear their web browsing history, real-time language translation within Messenger, and many more.
Besides announcing exciting features for its social media platform, Facebook CEO Mark Zuckerberg also gave us a quick look at the features Facebook introduced for companies that it owns, like WhatsApp and Instagram.
During Facebook's F8 conference on Tuesday, Zuckerberg announced a long-awaited feature for WhatsApp—Group Video Calling. Yes, you heard that right. WhatsApp would soon be adding a group video calling feature to the popular end-to-end messaging app, making it possible for its over billion users to have face-to-face conversations with multiple people at once.
Although there are not many details about the WhatsApp group video calling feature at this moment, it is clear that WhatsApp will now allow four people to have one-on-one video chat in groups. The feature will only work with smartphones (not for WhatsApp Web).
Previously, video calling feature was only available for personal chats (involving two parties).
According to Zuckerberg, video calling is one of the most popular features on WhatsApp, and people have already spent about 2 billion minutes for video calling on WhatsApp alone.
Therefore, with the launch of WhatsApp group video calling, the company hopes that the messaging app will become more popular.
Besides group video calling, WhatsApp will also bring support for stickers in the months ahead, just like Messenger, Facebook revealed later.
This year's F8 has also brought a major update to Instagram. Facebook is also bringing the video chat feature to Instagram, giving Instagrammers a new way to spend time together, even when they can not be together.
To start a video chat one-on-one with someone or with a group of people, you simply need to tap the new camera icon at the top of a Direct message thread. You can even minimize the video window and continue the chat while doing other stuff on Instagram.
Besides video chat, Instagram will also be having a redesigned Explore feature to make it easier for Instagrammers to discover things they are interested in.
Both the new Explore and video chat features are currently in the testing phase and will roll out globally soon.
Facebook also introduced a new way for people to share from their favorite apps, like Spotify and GoPro, to Instagram Stories as well as Facebook Stories.
To know everything Facebook announced at 2018 F8 developer conference on Tuesday, you can simply head on the blog post published by the company.
Nintendo Switches Hacked to Run Linux—Unpatchable Exploit Released
9.5.2018 thehackernews Hacking
Two separate teams of security researchers have published working proof-of-concept exploits for an unpatchable vulnerability in Nvidia's Tegra line of embedded processors that comes on all currently available Nintendo Switch consoles.
Dubbed Fusée Gelée and ShofEL2, the exploits lead to a coldboot execution hack that can be leveraged by device owners to install Linux, run unofficial games, custom firmware, and other unsigned code on Nintendo Switch consoles, which is typically not possible.
Both exploits take advantage of a buffer overflow vulnerability in the USB software stack of read-only boot instruction ROM (IROM/bootROM), allowing unauthenticated arbitrary code execution on the game console before any lock-out operations (that protect the chip's bootROM) take effect.
The buffer overflow vulnerability occurs when a device owner sends an "excessive length" argument to an incorrectly coded USB control procedure, which overflows a crucial direct memory access (DMA) buffer in the bootROM, eventually allowing data to be copied into the protected application stack and giving attackers the ability to execute code of their choice.
In other words, a user can overload a Direct Memory Access (DMA) buffer within the bootROM and then execute it to gain high-level access on the device before the security part of the boot process comes into play.
"This execution can then be used to exfiltrate secrets and to load arbitrary code onto the main CPU Complex (CCPLEX) application processors at the highest possible level of privilege (typically as the TrustZone Secure Monitor at PL3/EL3)," hardware hacker Katherine Temkin of ReSwitched, who released Fusée Gelée, said.
However, the exploitation requires users to have physical access to the hardware console to force the Switch into USB recovery mode (RCM), which can simply be done by pressing and shorting out certain pins on the right Joy-Con connector, without actually opening the system.
By the way, fail0verflow said a simple piece of wire from the hardware store could be used to bridge Pin 10 and Pin 7 on the console's right Joy-Con connector, while Temkin suggested that simply exposing and bending the pins in question would also work.
Once done, you can connect the Switch to your computer using a cable (USB A → USB C) and then run any of the available exploits.
Fusée Gelée, released by Temkin, allows device owners only to display device data on the screen, while she promised to release more scripts and full technical details about exploiting Fusée Gelée on June 15, 2018, unless someone else made them public.
She is also working on customized Nintendo Switch firmware called Atmosphère, which can be installed via Fusée Gelée.
On the other hand, ShofEL2 exploit released by famous fail0verflow team allows users to install Linux on Nintendo Switches.
"We already caused temporary damage to one LCD panel with bad power sequencing code. Seriously, do not complain if something goes wrong," fail0verflow team warns.
Meanwhile, another team of hardware hackers Team Xecutor is also preparing to sell an easy-to-use consumer version of the exploit, which the team claims, will "work on any Nintendo Switch console regardless of the currently installed firmware, and will be completely future proof."
Nintendo Can't Fix the Vulnerability Using Firmware Update
The vulnerability is not just limited to the Nintendo Switch and affects Nvidia's entire line of Tegra X1 processors, according to Temkin.
"Fusée Gelée was responsibly disclosed to NVIDIA earlier, and forwarded to several vendors (including Nintendo) as a courtesy," Temkin says.
Since the bootROM component comes integrated into Tegra devices to control the device boot-up routine and all happens in Read-Only memory, the vulnerability cannot be patched by Nintendo with a simple software or firmware update.
"Since this bug is in the Boot ROM, it cannot be patched without a hardware revision, meaning all Switch units in existence today are vulnerable, forever," fail0verflow says. "Nintendo can only patch Boot ROM bugs during the manufacturing process."
So, it is possible for the company to address this issue in the future using some hardware modifications, but do not expect any fix for the Switches that you already own.
Police Shut Down World's Biggest 'DDoS-for-Hire' Service–Admins Arrested
9.5.2018 thehackernews Attack
In a major hit against international cybercriminals, the Dutch police have taken down the world's biggest DDoS-for-hire service that helped cyber criminals launch over 4 million attacks and arrested its administrators.
An operation led by the UK's National Crime Agency (NCA) and the Dutch Police, dubbed "Power Off," with the support of Europol and a dozen other law enforcement agencies, resulted in the arrest of 6 members of the group behind the "webstresser.org" website in Scotland, Croatia, Canada and Serbia on Tuesday.
With over 136,000 registered users, Webstresser website lets its customers rent the service for about £10 to launch Distributed Denial of Service (DDoS) attacks against their targets with little or no technical knowledge.
"With webstresser.org, any registered user could pay a nominal fee using online payment systems or cryptocurrencies to rent out the use of stressers and booters," Europol said.
The service was also responsible for cyber attacks against seven of the UK's biggest banks in November last year, as well as government institutions and gaming industry.
"It's a growing problem, and one we take very seriously. Criminals are very good at collaborating, victimizing millions of users in a moment from anywhere in the world," said Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3).
The Webstresser site has now been shut down, and its infrastructure has been seized in the Netherlands, Germany, and the United States. The site has been replaced with a page announcing that law enforcement authorities had taken the service offline.
"As part of the operational activity, an address was identified and searched in Bradford and a number of items seized," NCA said.
Moreover, the authorities have also taken against the top users of this marketplace in the Netherlands, Italy, Spain, Croatia, the United Kingdom, Australia, Canada and Hong Kong, Europol announced.
The Dutch police said the Operation Power Off should send a clear warning to users of sites like webstresser.
"Don't do it," Gert Ras, head of the Dutch police's High Tech Crime unit, said. "By tracking down the DDoS service you use, we strip you of your anonymity, hand you a criminal record and put your victims in a position to claim back damages from you."
The police also reminded people that DDoSing is a crime, for which the "penalties can be severe." If you conduct a DDoS attack, or make, supply or obtain stresser or booter services, you could end up in prison, and fine or both.
Third Critical Drupal Flaw Discovered—Patch Your Sites Immediately
9.5.2018 thehackernews Vulnerebility
Damn! You have to update your Drupal websites.
Yes, of course once again—literally it’s the third time in last 30 days.
As notified in advance two days back, Drupal has now released new versions of its software to patch yet another critical remote code execution (RCE) vulnerability, affecting its Drupal 7 and 8 core.
Drupal is a popular open-source content management system software that powers millions of websites, and unfortunately, the CMS has been under active attacks since after the disclosure of a highly critical remote code execution vulnerability.
The new vulnerability was discovered while exploring the previously disclosed RCE vulnerability, dubbed Drupalgeddon2 (CVE-2018-7600) that was patched on March 28, forcing the Drupal team to release this follow-up patch update.
According to a new advisory released by the team, the new remote code execution vulnerability (CVE-2018-7602) could also allow attackers to take over vulnerable websites completely.
How to Patch Drupal Vulnerability
Since the previously disclosed flaw derived much attention and motivated attackers to target websites running over Drupal, the company has urged all website administrators to install new security patches as soon as possible.
If you are running 7.x, upgrade to Drupal 7.59.
If you are running 8.5.x, upgrade to Drupal 8.5.3.
If you are running 8.4.x, which is no longer supported, you need first to update your site to 8.4.8 release and then install the latest 8.5.3 release as soon as possible.
It should also be noted that the new patches will only work if your site has already applied patches for Drupalgeddon2 flaw.
"We are not aware of any active exploits in the wild for the new vulnerability," a drupal spokesperson told The Hacker News. "Moreover, the new flaw is more complex to string together into an exploit."
Technical details of the flaw, can be named Drupalgeddon3, have not been released in the advisory, but that does not mean you can wait until next morning to update your website, believing it won't be attacked.
We have seen how attackers developed automated exploits leveraging Drupalgeddon2 vulnerability to inject cryptocurrency miners, backdoors, and other malware into websites, within few hours after it's detailed went public.
Besides these two flaws, the team also patched a moderately critical cross-site scripting (XSS) vulnerability last week, which could have allowed remote attackers to pull off advanced attacks including cookie theft, keylogging, phishing and identity theft.
Therefore, Drupal website admins are highly recommended to update their websites as soon as possible.
Release of PoC Exploit for New Drupal Flaw Once Again Puts Sites Under Attack
9.5.2018 thehackernews Vulnerebility

Only a few hours after the Drupal team releases latest updates to fix a new remote code execution flaw in its content management system software, hackers have already started exploiting the vulnerability in the wild.
Announced yesterday, the newly discovered vulnerability (CVE-2018-7602) affects Drupal 7 and 8 core and allows remote attackers to achieve exactly same what previously discovered Drupalgeddon2 (CVE-2018-7600) flaw allowed—complete take over of affected websites.
Although Drupal team has not released any technical details of the vulnerability to prevent immediate exploitation, two individual hackers have revealed some details, along with a proof-of-concept exploit just a few hours after the patch release.
If you have been actively reading every latest story on The Hacker News, you must be aware of how the release of Drupalgeddon2 PoC exploit derived much attention, which eventually allowed attackers actively hijack websites and spread cryptocurrency miners, backdoors, and other malware.
As expected, the Drupal team has warned that the new remote code execution flaw, let's refer it Drupalgeddon3, is now actively being exploited in the wild, again leaving millions of websites vulnerable to hackers.
In this article, I have briefed what this new flaw is all about and how attackers have been exploiting it to hack websites running unpatched versions of Drupal.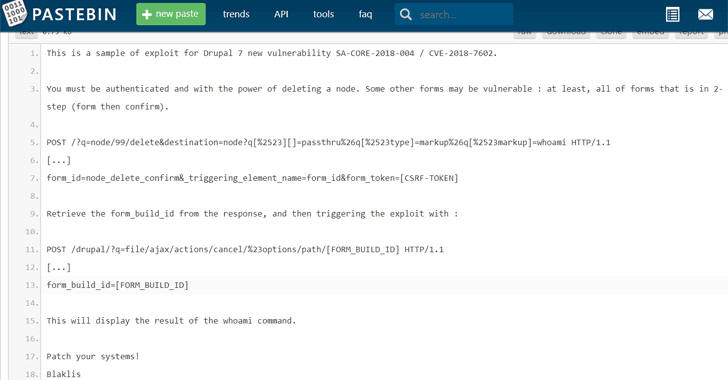
The exploitation process of Drupalgeddon3 flaw is somewhat similar to Drupalgeddon2, except it requires a slightly different payload to trick vulnerable websites into executing the malicious payload on the victim's server.
Drupalgeddon3 resides due to the improper input validation in Form API, also known as "renderable arrays," which renders metadata to output the structure of most of the UI (user interface) elements in Drupal. These renderable arrays are a key-value structure in which the property keys start with a hash sign (#).
A Twitter user with handle @_dreadlocked explains that the flaw in Form API can be triggered through the "destination" GET parameter of a URL that loads when a registered user initiates a request to delete a node; where, a "node" is any piece of individual content, such as a page, article, forum topic, or a post.
Since this "destination" GET query parameter also accepts another URL (as a value) with its own GET parameters, whose values were not sanitized, it allowed an authenticated attacker to trick websites into executing the code.
What I have understood from the PoC exploit released by another Twitter user, using handle @Blaklis_, is that the unsanitized values pass though stripDangerousValues() function that filters "#" character and can be abused by encoding the "#" character in the form of "%2523".
The function decodes "%2523" into "%23," which is the Unicode version for "#" and will be processed to run arbitrary code on the system, such as a whoami utility.
At first, Drupal developers were skeptical about the possibility of real attacks using the Drupalgeddon3 vulnerability, but after the reports of in-the-wild attacks emerged, Drupal raised the level of danger of the problem to "Highly critical."
Therefore, all Drupal website administrators are highly recommended to update their websites to the latest versions of the software as soon as possible.
Amazon Alexa Has Got Some Serious Skills—Spying On Users!
9.5.2018 thehackernews CyberSpy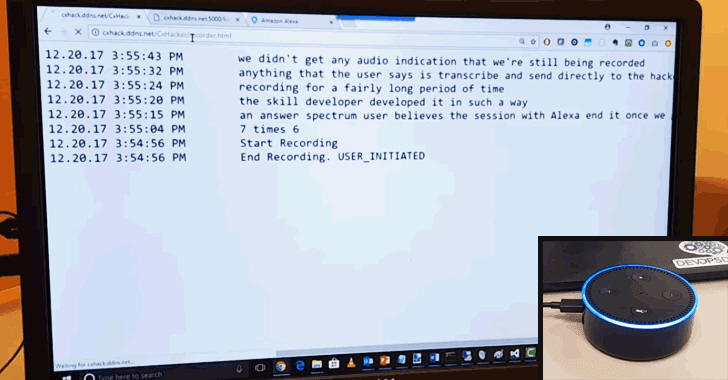
"Alexa, are you spying on me?" — aaaa.....mmmm.....hmmm.....maybe!!!
Security researchers have developed a new malicious 'skill' for Amazon's popular voice assistant Alexa that can turn your Amazon Echo into a full-fledged spying device.
Amazon Echo is an always-listening voice-activated smart home speaker that allows you to get things done by using your voice, like playing music, setting alarms, and answering questions.
However, the device doesn’t remain activated all the time; instead, it sleeps until the user says, "Alexa," and by default, it ends a session after some duration.
Amazon also allows developers to build custom 'skills,' applications for Alexa, which is the brain behind millions of voice-activated smart devices including Amazon Echo Show, Echo Dot, and Amazon Tap.
However, security researchers at cybersecurity firm Checkmarx created a proof-of-concept voice-driven 'skill' for Alexa that forces device to indefinitely record surround voice to secretly eavesdrop on users’ conversations and then also sends the complete transcripts to a third-party website.
Disguised as a simple calculator for solving maths problems, the malicious skill, if installed, immediately gets activated in the background after a user says "Alexa, open calculator."
"The calculator skill is initialized, and the API\Lambda-function that's associated with the skill receives a launch request as an input," researchers said in its report.
In a video demonstration, researchers show that when a user opens up a session with the calculator app (in the background), it also creates a second session without verbally indicating the user that the microphone is still active.
By design, Alexa should either end a session or ask the user for another command to keep the session open. However, the hack could allow attackers to keep the second session active for spying on users while ending the first when user interaction get overs.
Luckily, you can still spot the spy red handed if you notice the blue light on your Echo device activated for a longer period, especially when you are not chit-chatting with it.
Checkmarx reported the issue to Amazon, and the company has already addressed the problem by regularly scanning for malicious skills that "silent prompts or that listen for unusual lengths of time" and kicking them out of their official store.
It's not the first Alexa hack demonstrated by the researchers. Last year, a separate group of researchers at MWR InfoSecurity showed how hackers could turn some models of Amazon Echo into the covert listening device.
Faulty Patch for Oracle WebLogic Flaw Opens Updated Servers to Hackers Again
9.5.2018 thehackernews Vulnerebility
Earlier this month, Oracle patched a highly critical Java deserialization remote code execution vulnerability in its WebLogic Server component of Fusion Middleware that could allow attackers to easily gain complete control of a vulnerable server.
However, a security researcher, who operates through the Twitter handle @pyn3rd and claims to be part of the Alibaba security team, has now found a way using which attackers can bypass the security patch and exploit the WebLogic vulnerability once again.
WebLogic Server acts as a middle layer between the front end user interface and the backend database of a multi-tier enterprise application. It provides a complete set of services for all components and handles details of the application behavior automatically.
Initially discovered in November last year by Liao Xinxi of NSFOCUS security team, the Oracle WebLogic Server flaw (CVE-2018-2628) can be exploited with network access over TCP port 7001.
If exploited successfully, the flaw could allow a remote attacker to completely take over a vulnerable Oracle WebLogic Server. The vulnerability affects versions 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3.
Since a proof-of-concept (PoC) exploit for the original Oracle WebLogic Server vulnerability has already been made public on Github and someone has just bypassed the patch as well, your up-to-date services are again at risk of being hacked.
Although @pyn3rd has only released a short GIF (video) as a proof-of-concept (PoC) instead of releasing full bypass code or any technical details, it would hardly take a few hours or days for skilled hackers to figure out a way to achieve same.
Currently, it is unclear when Oracle would release a new security update to address this issue that has re-opened CVE-2018-2628 flaw.
In order to be at least one-step safer, it is still advisable to install April patch update released by Oracle, if you haven't yet because attackers have already started scanning the Internet for vulnerable WebLogic servers
A New Cryptocurrency Mining Virus is Spreading Through Facebook
9.5.2018 thehackernews Cryptocurrency
If you receive a link for a video, even if it looks exciting, sent by someone (or your friend) on Facebook messenger—just don't click on it without taking a second thought.
Cybersecurity researchers from Trend Micro are warning users of a malicious Chrome extension which is spreading through Facebook Messenger and targeting users of cryptocurrency trading platforms to steal their accounts’ credentials.
Dubbed FacexWorm, the attack technique used by the malicious extension first emerged in August last year, but researchers noticed the malware re-packed a few new malicious capabilities earlier this month.
New capabilities include stealing account credentials from websites, like Google and cryptocurrency sites, redirecting victims to cryptocurrency scams, injecting miners on the web page for mining cryptocurrency, and redirecting victims to the attacker's referral link for cryptocurrency-related referral programs.
It is not the first malware to abuse Facebook Messenger to spread itself like a worm.
Late last year, Trend Micro researchers discovered a Monero-cryptocurrency mining bot, dubbed Digmine, that spreads through Facebook messenger and targets Windows computers, as well as Google Chrome for cryptocurrency mining.
Just like Digmine, FacexWorm also works by sending socially engineered links over Facebook Messenger to the friends of an affected Facebook account to redirect victims to fake versions of popular video streaming websites, like, YouTube.
It should be noted that FacexWorm extension has only been designed to target Chrome users. If the malware detects any other web browser on the victim's computer, it redirects the user to an innocuous-looking advertisement.
How Does the FacexWorm Malware Work
If the malicious video link is opened using Chrome browser, FacexWorm redirects the victim to a fake YouTube page, where the user is encouraged to download a malicious Chrome extension as a codec extension to continue playing the video.
Once installed, FacexWorm Chrome extension downloads more modules from its command and control server to perform various malicious tasks.
"FacexWorm is a clone of a normal Chrome extension but injected with short code containing its main routine. It downloads additional JavaScript code from the C&C server when the browser is opened," the researchers said.
"Every time a victim opens a new webpage, FacexWorm will query its C&C server to find and retrieve another JavaScript code (hosted on a Github repository) and execute its behaviors on that webpage."
Since the extension takes all the extended permissions at the time of installation, the malware can access or modify data for any websites the user opens.
Here below I have listed a brief outline of what FacexWorm malware can perform:
To spread itself further like a worm, the malware requests OAuth access token for the Facebook account of the victim, using which it then automatically obtains the victim's friend list and sends that malicious, fake YouTube video link to them as well.
Steal the user's account credentials for Google, MyMonero, and Coinhive, when the malware detects that the victim has opened the target website’s login page.
FacexWorm also injects cryptocurrency miner to web pages opened by the victim, which utilizes the victim computer's CPU power to mine Cryptocurrency for attackers.
FacexWorm even hijacks the user's cryptocurrency-related transactions by locating the address keyed in by the victim and replacing it with the one provided by the attacker.
When the malware detects the user has accessed one of the 52 cryptocurrency trading platforms or typed keywords like "blockchain," "eth-," or "ethereum" in the URL, FacexWorm will redirect the victim to a cryptocurrency scam webpage to steal user's digital coins. The targeted platforms include Poloniex, HitBTC, Bitfinex, Ethfinex, and Binance, and the wallet Blockchain.info.
To avoid detection or removal, the FacexWorm extension immediately closes the opened tab when it detects that the user is opening the Chrome extension management page.
The attacker also gets a referral incentive every time a victim registers an account on Binance, DigitalOcean, FreeBitco.in, FreeDoge.co.in, or HashFlare.
So far, researchers at Trend Micro have found that FacexWorm has compromised at least one Bitcoin transaction (valued at $2.49) until April 19, but they do not know how much the attackers have earned from the malicious web mining.
Cryptocurrencies targeted by FacexWorm include Bitcoin (BTC), Bitcoin Gold (BTG), Bitcoin Cash (BCH), Dash (DASH), ETH, Ethereum Classic (ETC), Ripple (XRP), Litecoin (LTC), Zcash (ZEC), and Monero (XMR).
The FacexWorm malware has been found surfacing in Germany, Tunisia, Japan, Taiwan, South Korea, and Spain. But since Facebook Messenger is used worldwide, there are more chances of the malware being spread globally.
Chrome Web Store had removed many of the malicious extensions before being notified by Trend Micro researchers, but the attackers keep uploading it back to the store.
Facebook Messenger can also detect the malicious, socially engineered links and regularly block the propagation behavior of the affected Facebook accounts, researchers said.
Since Facebook Spam campaigns are quite common, users are advised to be vigilant when clicking on links and files provided via the social media site platform.
Along with Dating, Here’s a List of New Features Coming to Facebook
9.5.2018 thehackernews Social

Facebook announced a whole lot of new features at its 2018 Facebook F8 developers conference, along with the keynote by its CEO Mark Zuckerberg addressing concerns from app developers after Facebook paused 3rd-party app review in the wake of the Cambridge Analytica scandal.
Here are some big takeaways from Zuckerberg's keynote on Day 1 of Facebook F8, held for two days, May 1 and 2, at the McEnery Convention Center in San Jose, California:
FaceDate—Facebook's New Tinder-Like 'Dating' Feature
Still Single? Don't worry because Facebook doesn't want you to remain single for long.
The social network giant is introducing a new dating feature that will allow you to build your profile that will only be visible to other Facebook users (non-friends) who have also opted into looking for love.
Dubbed FaceDate, the new feature will match your profile based on all its data with others to find potential suitors and messaging will happen in a dedicated inbox rather than its default Messenger application.
And worry not. Neither FaceDate will match your profile with your friends, nor your friends will not be able to see your dating profile.
FaceDate is "not just for hookups," said Zuckerberg said. Rather, the feature has been designed for "real long-term relationships."
Shortly after the announcement of FaceDate, the share price of Match Group, the parent company of Match.com, fell 22%, and IAC, the parent of both popular hookup app Tinder and Match Group, fell more than 16%.
Facebook Adds 'Clear History' Tool
Facebook had been embroiled in controversies over its data sharing practices after the Cambridge Analytica scandal, forcing people to think about how the social media handles user privacy, collects data and uses it.
Now to help users protect their privacy, Facebook introduced a new feature, dubbed "Clear History," that will let users clear their browsing history on Facebook.
Clear History will enable users to see the websites and apps that send Facebook information when users use them, delete this information from users' account, and turn off Facebook's ability to store the data "associated with your account" going forward.
Once you clear your history, Facebook will remove identifying information so a history of the sites and apps you have used will not be associated with your account.
It is unclear how Facebook defines 'associated with your account.'
However, Facebook will take a few months to build the Clear History feature, and work with "privacy advocates, academics, policymakers, and regulators to get their input on our approach," Facebook VP and chief privacy officer Erin Egan said in a blog post.
"After going through our systems, this is an example of the kind of control we think you should have," Zuckerberg said. "It's something privacy advocates have been asking for."
Facebook also warned users that by using the Clear History tool, they might be required to sign back in everytime they want to log into their account.
Facebook is also committed to preventing "fake news" and fake accounts from spreading on its platform, though Zuckerberg did not tell much about how Facebook plans to do it.
Facebook Re-Opens App Reviews On Its Platform
In the wake of the Cambridge Analytica scandal, Facebook paused third-party app review, but now Zuckerberg announced that the company is re-opening app reviews for developers starting Tuesday.
The relationship between Facebook and app developers has gotten complicated since it was revealed how digital consultancy firm Cambridge Analytica improperly obtained and misused data on potentially 87 million Facebook users to reportedly help Donald Trump win the US presidency in 2016.
Facebook paused review of new apps after it was revealed that a third-party app developer named Aleksandr Kogan, who created personality quiz app and collected personal data on millions of users who took the quiz, handed over the data to Cambridge Analytica.
"I know it hasn’t been easy being a developer these past couple months, and that’s probably an understatement," Zuckerberg said.
Facebook has re-opened app review, but the process has changed a bit. The company will now "require business verification for apps that need access to specialized APIs or extended Login permissions."
"Apps that ask for basic public profile or additional permissions, such as a birthday or user friends, are not subject to business verification," a blog post published Tuesday reads.
Real Time Language Translations In Facebook Messenger
Facebook has introduced chat translation within Messenger through its M Suggestions assistant, which will translate conversations in real time, just like web browsers do.
However, the feature will be rolled out to users in the United States throughout this year and will only translate English-Spanish conversions.
In the coming weeks, all American Messenger users will get access to this feature, and over time the social media says it will "launch this functionality in additional languages and countries."
Launching in closed beta, businesses will now be able to integrate augmented reality (AR) camera effects for its customers to experience directly into Messenger.
Now when you interact with certain businesses on Messenger, you will be able to virtually try or customize merchandise by opening the app's camera and use a pre-populated brand-specific AR effect.
Facebook is also making simplifications to Messenger's interface. Since the app's quest to embrace businesses, bots, Stories and visual sharing have made it bloated, the company has re-designed Messenger by cutting out the games and camera tabs from the navigation bar.
Besides these features, Facebook has also introduced a new way for people to share from their favorite apps, like Spotify and GoPro, to both Facebook and Instagram Stories. The company has also made its first standalone VR headset Oculus Go available globally for anyone to purchase, starting at $199.
To know more about new launches and watch the full keynote, you can head on to this blog post.
No Evidence Russian Hackers Changed Votes in 2016 Election: Senators
9.5.2018 securityweek BigBrothers
Hackers backed by the Russian government attempted to undermine confidence in the voting process in the period leading up to the 2016 presidential election, but there is no evidence that they manipulated votes or modified voter registration data, according to a brief report published on Tuesday by the Senate Intelligence Committee.
According to the Senate panel, threat actors had attempted to access numerous state election systems and in some cases voter registration databases.
Authorities are confident that Russian threat actors targeted election systems in at least 18 states, and there is some evidence that three other states may have also been hit. These numbers only cover local or state government organizations – attacks on political parties and NGOs are not included.
Several other states reported seeing malicious activity, but investigators have not been able to confidently attribute the incidents to Russia.
Nearly all the targeted states observed attempts to find vulnerabilities in their systems. These scans were often aimed at the website of the Secretary of State and voter registration infrastructure, the Senate panel said in its report.
In at least six states, Russian hackers attempted to breach voting-related websites, and in a small number of cases they were able to gain unauthorized access to election infrastructure components, and even obtained the access necessary for altering or deleting voter registration data. However, it does not appear that they could have manipulated individual votes or aggregate vote totals.
The Russian government is believed to have launched this campaign at least as early as 2014 with the goal of gathering information and discrediting the integrity of the United States’ voting process and election results, senators said.
The Senate panel has admitted that its assessment, as well as the assessments of the DHS and FBI, are based on information provided by the targeted states, and there may be some attacks or breaches that have not been detected.
“While the full scope of Russian activity against the states remains unclear because of collection gaps, the Committee found ample evidence to conclude that the Russian government was developing capabilities to undermine confidence in our election infrastructure, including voter processes,” senators wrote in their report.
“The Committee does not know whether the Russian government-affiliated actors intended to exploit vulnerabilities during the 2016 elections and decided against taking action, or whether they were merely gathering information and testing capabilities for a future attack. Regardless, the Committee believes the activity indicates an intent to go beyond traditional intelligence collection,” they added.
The Trump administration recently imposed sanctions against several Russian spy agencies and 19 individuals for trying to influence the 2016 presidential election.
Adobe fixed a Critical Code Execution issue in Flash Player
9.5.2018 securityaffairs Vulnerebility
Adobe has released security updated to address several vulnerabilities in its products, including Flash Player, Creative Cloud and Connect products.
The security updates also address a Critical Code Execution vulnerability in Flash Player tracked as CVE-2018-4944. The flaw is a critical type confusion that could be exploited to execute arbitrary code, the good news is that Adobe has rated the flaw with a rating of “2” because the company considers not imminent the development of exploit code.
The vulnerability affects Flash Player 29.0.0.140 and earlier versions and was addressed with the release of version 29.0.0.171 for Windows, Mac, Linux and Chrome OS.
The flaw is a critical type confusion that allows arbitrary code execution (CVE-2018-4944), but Adobe has assigned it a severity rating of “2,” which indicates that exploits are not considered imminent and there is no rush to install the update.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities in Adobe Flash Player 29.0.0.140 and earlier versions. Successful exploitation could lead to arbitrary code execution in the context of the current user.” reads the advisory published by Adobe.
Adobe also addressed three security vulnerabilities in the Creative Cloud desktop applications for Windows and macOS, the issues affect version 4.4.1.298 and earlier of the apps.
“Adobe has released a security update for the Creative Cloud Desktop Application for Windows and MacOS.” reads the advisory.
“This update resolves a vulnerability in the validation of certificates used by Creative Cloud desktop applications (CVE-2018-4991), and an improper input validation vulnerability (CVE-2018-4992) that could lead to privilege escalation.”
The flaws affecting the Creative Cloud desktop applications are:
an improper input validation that can be exploited to escalate privilege (critical);
an improper certificate validation problem that can lead to a security bypass (important);
an unquoted search path that can be exploited for privilege escalation (important);
All of the vulnerabilities received a priority rating of “2.”
Adobe also addressed an authentication bypass vulnerability affecting Connect versions 9.7.5 and earlier. The flaw rated as “important” could lead the exposure of sensitive information.
“An important authentication bypass vulnerability (CVE-2018-4994) exists in Adobe Connect versions 9.7.5 and earlier. Successful exploitation of this vulnerability could result in sensitive information disclosure.” reads the advisory.
May 2018 Patch Tuesday: Microsoft fixes 2 zero-day flaws reportedly exploited by APT group
9.5.2018 securityaffairs Vulnerebility
Microsoft has released the May 2018 Patch Tuesday that addresses more than 60 vulnerabilities, including two Windows zero-day flaws that can be exploited for remote code execution and privilege escalation.
Microsoft May 2018 Patch Tuesday includes security patches for 67 vulnerabilities, including two zero-days that have already been exploited in the wild by threat actors.
The security updates address 21 vulnerabilities that are rated as critical, 42 rated important, and 4 rated as low severity. The flaws affect many products, including Microsoft Windows, Internet Explorer, Microsoft Edge, Outlook, Microsoft Office, Microsoft Office Exchange Server, .NET Framework, Microsoft Hyper-V, ChakraCore, Azure IoT SDK, and others.
The most severe issue is CVE-2018-8174 zero-day, dubbed Double Kill, a critical vulnerability that could be exploited by remote attackers to execute arbitrary code on all supported versions of Windows.
The vulnerability was first reported by experts at Qihoo 360, according to the experts is was exploited by a known advanced persistent threat (APT) group in targeted attacks that targeted Internet Explorer and leveraged specially crafted Office weaponized documents.
The Double Kill vulnerability is a use-after-free issue that resides in the way the VBScript Engine handles objects in computer memory. An attacker can exploit the flaw to execute code that runs with the same system privileges as of the logged-in user.
“A remote code execution vulnerability exists in the way that the VBScript engine handles objects in memory. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.” reads the advisory published by Microsoft. ” If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
Security experts from Kaspersky confirmed the CVE-2018-8174 flaw was exploited in targeted attacks by an APT group, the hackers delivered weaponized documents to allow the download of a second-stage payload. Hackers tricked victims into visiting a malicious HTML page that contained the code to trigger the UAF and a shellcode that downloads the malicious payload.
“In a web-based attack scenario, an attacker could host a specially crafted website that is designed to exploit the vulnerability through Internet Explorer and then convince a user to view the website. An attacker could also embed an ActiveX control marked ‘safe for initialization’ in an application or Microsoft Office document that hosts the IE rendering engine,” reads Microsoft’s explains in its advisory.
“The attacker could also take advantage of compromised websites and websites that accept or host user-provided content or advertisements. These websites could contain specially crafted content that could exploit the vulnerability.”
The Microsoft May 2018 Patch Tuesday also addresses another zero-day vulnerability tracked as CVE-2018-8120, a privilege escalation that is related the way the Win32k component handles objects in memory. The flaw could be exploited by an authenticated attacker to execute arbitrary code in kernel mode.
“An elevation of privilege vulnerability exists in Windows when the Win32k component fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” reads the advisory.
“To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application that could exploit the vulnerability and take control of an affected system.”
The CVE-2018-8120 flaw only affects Windows 7 and Windows Server 2008.
Microsoft May 2018 Patch Tuesday
The Microsoft May 2018 Patch Tuesday also fixed two Windows vulnerabilities rated as “important” whose details have been made public. The flaws are respectively a privilege escalation issue (CVE-2018-8170) and an information disclosure (CVE-2018-8141).
Lenovo Patches Secure Boot Vulnerability in Servers
9.5.2018 securityweek Vulnerebility
Lenovo has released patches for a High severity vulnerability impacting the Secure Boot function on some System x servers.
Exploitation of this security vulnerability could result in unauthenticated code being booted. Discovered by the computer maker’s internal testing team and tracked as CVE-2017-3775, the issue impacts a dozen models, including Flex System x240 M5, x280 X6, x480 X6, x880, x3xxx series, and NeXtScale nx360 M5 devices.
“Lenovo internal testing discovered some System x server BIOS/UEFI versions that, when Secure Boot mode is enabled by a system administrator, do not properly authenticate signed code before booting it. As a result, an attacker with physical access to the system could boot unsigned code,” the manufacturer notes.
These systems ship with Secure Boot disabled by default, because signed code is relatively new in the data center environment, the company says, adding that standard operator configurations disable signature checking.
In its advisory, the computer maker published not only the complete list of affected models, but also links to the appropriate BIOS/UEFI update for each model. The company advises admins relying on Secure Boot to control physical access to systems prior to applying the updates.
Lenovo also released a patch for a buffer overflow in Lenovo System Update Drive Mapping Utility. Tracked as CVE-2018-9063, the vulnerability could result in undefined behaviors, such as execution of arbitrary code, the company notes.
Discovered by SaifAllah benMassaoud and assessed with a Medium severity rating, the vulnerability can be exploited by an attacker entering very large user ID or password in order to overrun the program’s buffer. An attacker could potentially execute code with the MapDrv’s privileges.
Lenovo System Update version 5.07.0072 or later addresses the vulnerability and users are advised to update the application to remain protected. To determine the currently installed version of Lenovo System Update, users should launch the application, click the green question mark in the top right corner and then select “About.”
Lenovo System Update automatically checks for newer version when executed, and users should simply launch the application and accept the update when prompted. Manual updates are also possible, by downloading the latest app version from Lenovo’s site.
Telegram Rivaling Tor as Home to Criminal 'Forums'
9.5.2018 securityweek Social
Telegram Channels Offer Great Anonymity and Are Being Increasingly Used by Cybercriminals
Serious criminals are abandoning the upper levels of the dark web. The reasons appear to be the relative ease with which such criminal forums are penetrated by law enforcement agents and security researchers -- and the recent shut-downs of major criminal forums Hansa Market and AlphaBay.
Last month, Cybereason tested this idea, and concluded that serious criminals have migrated to the deeper, closed forums of the dark web. Published yesterday, researchers from Check Point now postulate an alternative destination for these criminals; that is, not to deep, dark, Tor-hidden forums, but to Telegram.
Telegram is an encrypted instant messaging system first released in 2013. Like WhatsApp, it offers individual conversations and group chats -- but what sets it apart is its security strength and end-to-end encryption. "As a result, some of its hosted chat groups have become a useful alternative to the secretive forums on the Dark Web," say the Check Point security team.
Telegram groups are known as channels. It is these channels that are increasingly used by criminals. "Any threat actor with a shady offer or conversation to start, can enjoy private and end-to-end encrypted chats instead of the exposed threads that are seen in online forums." The advantages are obvious. They are easier to operate, easier to join, and offer even greater anonymity.
Check Point gives three examples of how Telegram is used. Three channels were found in Russia known as Dark Job, Dark Work and Black Markets. Dark Jobs recruits staff for illegal jobs. The jobs are graded white (for little danger), grey (for greater illegality and difficulty), and black (for dangerous with legal risks). Anyone with the Telegram app can join this channel and can both post advertisements and apply for jobs with complete anonymity. The same principle applies to other channels, and some already have thousands of subscribers.
The simplicity of this criminal method is particularly worrying.
"This is especially worrying," say the researchers, "considering the accessibility of the channels and the promises of high salaries made to those who might otherwise refrain or have no way to reach these markets." In other words, the migration of criminals to Telegram might easily increase the general level of criminality in society.
One area that particularly worries Check Point is the promotion of insider deals. It is easy to imagine a channel called 'Insiders'. This could attract any authorized employee with a grudge or need for additional finances to sell inside access to corporate networks anonymously via Telegram.
"Threat actors might take advantage of these employees in order to obtain insider information and sensitive data that is unavailable to the public," warn the researchers. "This inside information could then be used for personal purposes or sold, or to conduct a cyber-attack from the inside of the company. This would thus eliminate the efficiency of some security solutions. After all, having someone "on the inside" is a very powerful tool. Just like in the real world, in the world of cybercrime it can often be not what you know but who you know."
This is already happening on the Dark Job channel. One advertisement is looking for employees of Western Union or MoneyGram that have access to certain systems -- and offering payment of $1000 per day.
The Dark Work channel seems to be more geared towards criminal projects than employments. One example reads, "Wanted for a dark project: Cryptor running on all systems from Windows XP to 10. Bypassing the top AV especially Avast and Defender." The concern here is that a criminal entrepreneur could outsource an entire project without needing to know anything about technology, nor even his suppliers.
The Dark Market is simply that -- a marketplace for shady goods. Novice users, say the researchers, can find "messages promoting stealthy crypto-miners that will run without the victims' knowledge in exchange for 600 rubles, or even infostealers that collect documents, screenshots and passwords in exchange for 1000 rubles." This makes the Telegram channels very similar to the dark web marketplaces (such as the old Silk Road), but easier and more secure to use.
Government recognition of the increasing criminal use of Telegram is likely behind both the recent national bans, and the western demands for law enforcement encryption backdoors. In March, Russia's Supreme Court ordered that Telegram must provide decryption keys to the country's security services -- which Telegram declined. In mid-April, Russia began blocking Telegram.
Iran also banned Telegram on April 30, 2018, but is so far having little success. As of May 7, Iran's state-owned Telecommunications Infrastructure Company (TIC), which operates under President Hassan Rouhani's Telecommunications Ministry, has yet to comply with a prosecutor's order to block the Telegram messaging app. Radio Farda, a Persian language broadcaster at Radio Free Europe/Radio Liberty, reported today that many Iranians will use filtering software to avoid the ban. Of 9,485 respondents to a question, 9,024 replied they would "stay on Telegram using filtering circumvention software". (This is not a scientific study and is biased towards Iranian citizens already listening to a foreign broadcaster.)
In western democracies, the growing use of Telegram amply illustrates law enforcement's concern that criminals are going dark; and that law enforcement requires encryption backdoors to counter the threat. "Through the use of such tools, access to malware has never been easier, personal documents and certificates can be spread to unknown destinations and companies can be threatened by their own employees," concludes Check Point.
Critical Code Execution Flaw Patched in Flash Player
9.5.2018 securityweek Vulnerebility
Adobe has patched several vulnerabilities in its Flash Player, Creative Cloud and Connect products, but the company believes it’s unlikely that the flaws will be exploited in the wild any time soon.
Only one vulnerability has been patched in Flash Player with the release of version 29.0.0.171 for Windows, Mac, Linux and Chrome OS. The issue, reported to Adobe by Jihui Lu of Tencent KeenLab, impacts Flash Player 29.0.0.140 and earlier versions.
The flaw is a critical type confusion that allows arbitrary code execution (CVE-2018-4944), but Adobe has assigned it a severity rating of “2,” which indicates that exploits are not considered imminent and there is no rush to install the update.
A total of three security holes have been patched by Adobe in the Creative Cloud desktop applications for Windows and macOS. Researchers discovered that version 4.4.1.298 and earlier of the apps are impacted by an improper input validation issue that can lead to privilege escalation, an improper certificate validation problem that can lead to a security bypass, and a flaw described as an “unquoted search path” that can be exploited for privilege escalation.
The certificate validation vulnerability has been classified “critical,” while the other two issues have been rated “important.” All of them have a priority rating of “2.”
Wei Wei of Tencent's Xuanwu Lab, Ryan Hileman of Talon Voice, Chi Chou, and Cyril Vallicari of HTTPCS – Ziwit have been credited for finding the flaws.
Finally, Adobe patched an “important” authentication bypass vulnerability affecting Connect versions 9.7.5 and earlier. Exploitation of the flaw can result in the exposure of sensitive information.