Ransomware? Bad Rabbit spíše pouze maskoval phishingový útok na Ukrajině
7.11.2017 CNEWS.cz Viry
Co když sledujete útok a nevšimnete si, že mezitím za vašimi zády probíhá útok jiný? Na Ukrajině během výskytu Bad Rabbitu probíhal útok phishingový.
Koncem října postihl část světa další velký útok ransomwaru, jenž vzbudil pozornost médií. Vypadá to, že v tomto roce je vůbec nejvíce postižena Ukrajina, nebo aspoň patří k nejvíce postiženým. Zatímco ransomware WannaCry postihl mnoho organizací po celém světě, koncem června dorazila hrozba jménem Petya. Tentokrát byla nejvíce postižena právě Ukrajina.
Zajímavé je, že ačkoli se zdánlivě jednalo o útok ransomwaru, ve skutečnosti to byl spíše zákeřný malware, jehož cílem byl způsobit rozsáhlé škody. Dodávám, že cílem ransomwaru je naproti tomu vydělat peníze – zašifruje data na počítači a pak za ně vyžaduje výkupné. Malware byl tedy založen na ransomwaru Petya, nicméně s ohledem na jeho chování a účel byl tento škodlivý kód bezpečnostními experty a expertkami nazván i jako NotPetya.
Ransomware pro odvedení pozornosti
NotPetya není mrtvý. Jak ukazují nedávná zkoumání, na jeho základech staví nedávno řádící ransomware Bad Rabbit. Malwarebytes Labs uvádí, že za oběma škodlivými kódy stojí pravděpodobně stejní lidé. Se zajímavým tvrzením pak exkluzívně přišla agentura Reuters, jež před pár dny získala vyjádření šéfa kybernetické policie Serhiye Demedyuka.
Zatímco byl svět zaneprázdněn Bad Rabbitem, probíhal na Ukrajině paralelně jiný útok. Jednalo se o phishingový útok s cílem ukrást informace finanční a tajné informace. Ačkoli se v Rusku Bad Rabbit rozšířil více, nová informace říká, že hlavním cílem byla pravděpodobně Ukrajina. Demedyuk řekl, že se hybridní útoky stávají běžnými. Samotná taktika, kdy je vyvolána událost, která odpoutá pozornost od skutečného problému, není vůbec nová.

Ransomware Petya (foto: Avast)
Phishingový útok byl zacílen na uživatelky a uživatele softwaru od ruské firmy 1C, jež produkuje mj. nástroje pro účetnictví. Útok ransomwaru Petya/NotPetya byl přitom zahájen rovněž prostřednictvím softwaru pro účetnictví, jenž se nazývá M.E.Doc. Podvodné e-maily rozeslané během nedávného útoku se tvářily, jako by přicházely od vývojářského studia 1C. Ukrajinská policie získala oznámení od patnácti firem, které phishingovému útoku podlehly.
Celkový rozsah útoku prý zatím odhadnout nelze. Zato je zajímavé, že ukrajinské orgány dokázaly od června zastavit pětici velkých útoků na finanční instituce a strategickou infrastrukturu, jak zjistili v Reuters.
V USA chystají obvinění členů ruské vlády z hackerských útoků
7.11.2017 Novinky/Bezpečnost BigBrother
Americké ministerstvo spravedlnosti má dostatek důkazů, aby obvinilo šest členů ruské vlády z podílu na loňském hackerském útoku proti serverům Demokratické strany. Oznámil to list The Wall Street Journal. Prokuratura by prý mohla přivést kauzu k soudu příští rok, podle amerického listu je ale zadržení obviněných nepravděpodobné.
Z Ruska byl údajně před loňskými prezidentskými volbami v USA veden hackerský útok, při němž bylo ze serverů americké Demokratické strany ukradeno velké množství elektronické pošty, která vrhala nepříznivé světlo na prezidentskou kandidátku Hillary Clintonovou. Později se e-maily objevily na kontroverzním serveru WikiLeaks.
Americká kontrarozvědka už v lednu údajně zjistila, že útok zorganizovaly ruské tajné služby na přímý příkaz prezidenta Vladimira Putina, který chtěl Clintonovou znevýhodnit v souboji s republikánským kandidátem a pozdějším volebním vítězem Donaldem Trumpem. Kreml jakékoli vměšování do amerických voleb popírá.
U soudu příští rok
Na vyšetřování v USA se podle listu The Wall Street Journal podíleli agenti FBI a prokurátoři z Washingtonu, Filadelfie, Pittsburghu a San Franciska. Kauza by se mohla dostat před soud příští rok. Obvinění by ruským činitelům znepříjemnilo cesty do zahraničí, zatýkání či věznění se ale nepředpokládá, píše americký list.
Spojené státy obvinily Rusy z hackerských útoků už letos v březnu. Ministerstvo spravedlnosti vzneslo obvinění proti dvěma ruským zpravodajským důstojníkům a dvěma hackerům, kteří údajně v roce 2014 organizovali útok na půl miliónu účtů internetové společnosti Yahoo.
Ruská oficiální místa na informaci amerického listu zatím nereagovala. Ruská agentura RBK napsala, že jména údajných ruských viníků by mohla být zveřejněna počátkem příštího roku.
Hack of Global Law Firm Appleby Exposes Rich and Famous
7.11.2017 securityweek Incindent
'Paradise Papers' Expose Financial Moves by Global Elite
Following the huge 2016 leak of documents stolen from Panamanian firm Mossack Fonseca (aka, the Panama Papers), the expected analyses of documents stolen more recently from the Appleby law firm (aka, the Paradise Papers) has begun. The route is the same in both cases -- the German newspaper Suddeutsche Zeitung obtained the stolen documents from an anonymous source (possibly the hacker, or via a third party), and passed them to the International Consortium of Investigative Journalists (ICIJ).
The ICIJ then worked with 95 media partners to explore a total of 13.4 million documents comprising those stolen from Appleby together with other documents from the smaller family-owned trust company, Asiaciti, and from company registries in 19 secrecy jurisdictions.
Very little is known about the actual hack of Appleby. The firm released a statement over the weekend in response to a BBC Panorama program broadcast on Sunday, and other media coverage beginning to appear via ICIJ's media partners. The ICIJ says it "and its media partners will be publishing multiple stories in the coming days and weeks." These stories will disclose the efforts taken by the rich and famous to use offshore tax regulations to their best advantage -- ranging from the Queen of England and Apple (BBC report) to the rock star Bono and many, many more.
Appleby says, "We wish to reiterate that our firm was not the subject of a leak but of a serious criminal act. This was an illegal computer hack. Our systems were accessed by an intruder who deployed the tactics of a professional hacker and covered his/her tracks to the extent that a forensic investigation by a leading international Cyber & Threats team concluded that there was no definitive evidence that any data had left our systems."
The greater part of the Appleby statement is an attempt at brand damage limitation. "The journalists do not allege, nor could they, that Appleby has done anything unlawful. There is no wrongdoing. It is a patchwork quilt of unrelated allegations with a clear political agenda and movement against offshore."
That the hack and leak of documents is politically motivated is clear and obvious. This is pure hacktivism with a motivation similar to that of the Occupy Movement -- and the reality is that hacktivism is difficult to defend against.
"While the mechanics of the breach itself have yet to be revealed, this was clearly a targeted attack," comments Mark Sangster, VP and industry security strategist at eSentire. "Appleby took appropriate response steps in notifying their clients; but you can't insure [against] this. This class of events demonstrates why law firms must protect their clients' confidential information. No amount of cyber insurance, data back strategies, nor business continuity planning can ever put this genie back in the bottle."
Incident response is relatively meaningless if no incident is detected -- or not, as in this case, detected until too late.
"Financial information, particularly tax arrangements," says Andy Waterhouse, EMEA director at RSA Security, "can be as sensitive as medical information and if exposed can be the source of embarrassment and reputational damage for Appleby's clients. Even if they are not breaking any laws, it's the public perception that can be damaging. When selecting partners, these individuals expect that their data will be highly guarded to prevent such exposure. The fact that they have been exposed in this way creates a huge break in trust with Appleby and could have serious ramifications in the long term on its own reputation as a vault of secrecy."
The whole incident demonstrates why data protection regulators are increasingly specifying the need to use encryption to protect sensitive information. Since no organization can guarantee that it will never be breached, and since business continuity and cyber insurance are meaningless against the loss of this type of data, encryption is the most effective defense.
The ICIJ tells us, "The Paradise Papers documents include nearly 7 million loan agreements, financial statements, emails, trust deeds and other paperwork over nearly 50 years from inside Appleby, a prestigious offshore law firm with offices in Bermuda and beyond." There are clearly many documents that are now historical documents. These, at the very least, should have been encrypted.
Many Brother Printers Vulnerable to Remote DoS Attacks
7.11.2017 securityweek Vulnerebility Attack
Remote attackers can cause thousands of Brother printers to temporarily stop working by exploiting an unpatched vulnerability discovered recently by researchers at Trustwave.
According to an advisory published by the security firm, the flaw is related to an embedded httpd server named Debut that some Brother products use to host their web interfaces. The security hole is tracked as CVE-2017-16249 and it affects version 1.20 and earlier of the Debut software.
A remote attacker can exploit the security hole by sending a specially crafted HTTP request to the targeted device. The request causes the server to hang until it eventually responds with an HTTP 500 error. During the time the server is hung, users cannot perform print jobs over the network and the web interface becomes inaccessible.
Trustwave noted that an attacker can generate a DoS condition for an extended period of time by continuously sending malicious requests to a device. The security firm has identified more than 16,000 vulnerable printers that can be attacked remotely over the Internet.
“Some people dismiss Denial of Service attacks as a mere nuisance, but they can tie up resources and reduce productivity at any organization,” a Trustwave researcher explained in a blog post. “They can also be used as a part of an in-person attack on a organization. For instance, an attacker can launch a Denial of Service like this one and then show up at the organization as the ‘technician’ called to fix the problem. Impersonating a technician would allow the attacker direct physical access to IT resources that they might never have been able to access remotely.”
Trustwave has been trying to inform Brother about the vulnerability since September, but it decided to make its findings public, along with proof-of-concept (PoC) code, after all attempts to contact the vendor failed. The flaw remains unpatched, the company said.
Brother is not the only company whose printers are affected by vulnerabilities. A report published early this year showed that several devices from HP, Brother, Lexmark, Dell, Samsung, Konica, OKI and Kyocera had at least one flaw, including ones that could be exploited for DoS attacks or to obtain sensitive information.
Last year, a researcher demonstrated the risks associated with unprotected printers by getting thousands of devices around the world to print anti-Semitic flyers.
Container Security Firm NeuVector Raises $7 Million
7.11.2017 securityweek IT
NeuVector, a San Jose, Calif.-based developer of container security technology, today announced that it has raised $7 million in Series A funding led by Hummer Winblad Venture Partners.
Launched in January 2017 by tech industry veterans from Fortinet, VMware, and Trend Micro, NeuVector, offers a ‘container firewall’ that provides application-layer segmentation to isolate container traffic, to help detect and block suspicious connections within the container environment.
“As more enterprises turn to containers for deploying business-critical applications, the need to inspect and secure all internal traffic within these container environments has become increasingly clear,” the company explained. “Data breaches and zero-day attacks are becoming more common and dangerous – and containers are not immune.”
NeuVector LogoThe NeuVector solution is a container itself and provides runtime vulnerability scanning across all running containers and hosts, and provides threat detection designed to mitigate DDoS, DNS, and other types of attacks. NeuVector also says that its offering leverages behavioral learning to automatically recognize and whitelist normal behavior, applying zero-configuration security policies that safeguard container traffic.
“Enterprises are increasingly tapping into the power of containers for application deployment – and the bad guys have taken notice,” said Fei Huang, CEO, NeuVector.
NeuVector joins several other startups looking to tap the container security market.
In September, Tel Aviv, Israel-based container security startup Aqua Security announced that it had raised $25 million in Series B funding, bringing the total amount raised by the company to $38.5 million.
In July, StackRox emerged from stealth mode armed with $14 million in funding to take its adaptive security platform for containers to market.
Container-focused security firm Twistlock has raised more than $30 million in funding over multiple rounds.
In June, cloud-based security and compliance solutions provider Qualys launched a product designed for securing containers across cloud and on-premises deployments.
According to a 2015 survey of 272 IT decision makers in North America conducted by Twistlock, 91 percent of the respondents said they were concerned about the security of containers.
Twitter-Happy Trump to Enter China's Great Firewall
7.11.2017 securityweek BigBrothers
US President Donald Trump has tweeted energetically throughout his Asian tour so far, but in China he will likely be one of a select few to skirt the country's ban on his cherished website.
The Twitter-happy president has fired off a slew of posts -- on both domestic and international issues -- since he started his trip in Japan and moved on to South Korea on Tuesday.
But when he lands in China on Wednesday, Trump will enter the so-called "Great Firewall" of online censorship that monitors people's internet habits and blocks websites such as Twitter, Facebook and Google.
Chinese can face fines or even jail time for unfavourable social media posts. Authorities have further tightened internet controls in recent months, shutting down celebrity gossip blogs and probing platforms for "obscenity".
Asked whether Trump –- who will get red-carpet treatment during his state visit –- would be able to tweet, Chinese vice foreign minister Zheng Zeguang told reporters: "How President Trump communicates with the outside is not something you need to worry about."
Trump, who has used an iPhone for Twitter posts, could use some options available to people in China to evade the Great Firewall -- though US presidents in any case travel with their own sophisticated communications systems.
- 'Trump can't live without Twitter' -
Web users can circumvent the firewall if they download a virtual private network (VPN) -- software that allows people to surf the internet as if they were using a server in another country.
But Beijing mandated in January that all developers must obtain government licences to offer VPN software, raising concern it might ban them outright.
Foreign visitors can also access banned websites with their phones if they are in roaming mode -- but only because the authorities currently allow it, according to experts.
Trump should be able to use roaming "but it depends on the policy of the (Chinese) government. If they chose not to allow you to (use roaming) then they can do it," James Gong, a Chinese cyber law expert at Herbert Smith Freehills law firm, told AFP.
"But if you're the president you should be able to do it. Donald Trump cannot live without Twitter," Gong said.
Mobile devices on roaming in China still use the local telecom service infrastructure, which raises privacy and security questions.
Charlie Smith, co-founder of the anti-censorship group Greatfire.org, said phones using data or virtual private networks (VPNs) are "generally" safe from hacking but it depends on the phone, user settings and other factors.
"As you know, every day in China, almost all mobile phone use is monitored and tens of thousands of people are under close watch," he told AFP.
"US officials should be well trained and prepared for travelling overseas and for maintaining secure communications, as the Chinese leadership are when they travel overseas."
Trump could also use an alternative temporary phone as another way to avoid the risk of compromising his smartphone in a country which is often accused of hacking.
- Jail time -
While Trump will likely find ways around the firewall, Chinese people face increasingly stringent controls over what they can do, say and see on the internet.
Chinese internet users face three years in prison for writing defamatory messages that are re-posted 500 times under a law passed in 2013. Web users can be jailed if offending posts are viewed more than 5,000 times.
New rules policing content were imposed this year and several of the country's biggest tech firms were fined for failing to remove illegal online content such as pornography and violence.
China has its own version of Twitter, Weibo, which boasts more than 300 million monthly active users.
Weibo users mostly sounded lukewarm about Trump's upcoming visit: One posted a chart showing heavy pollution levels in Beijing and asked if Trump would regret leaving the Paris climate pact.
But people must be wary of what they write.
Last year, a man who wrote a Weibo post critical of China's decades-old land reform policies on a local traffic police account was sentenced to a year in prison, reports said.
Another man, Qiao Mu, a former professor of international political communications in Beijing, recently moved to the United States after being targeted for his social media commentary.
He said authorities closed over 100 of his Weibo accounts and 17 of his accounts on the WeChat messaging service.
"There is no place for me to publish inside China's firewall," Qiao told AFP, explaining that he had tried to start new accounts after each was shut down.
Vietnamese Spies Rival Notorious Russian Group in Sophistication
7.11.2017 securityweek APT
The campaigns of a cyber espionage group believed to be operating out of Vietnam have become increasingly sophisticated, up to the point where they rival operations launched by the notorious Russia-linked advanced persistent threat (APT) actor known as Turla, incident response firm Volexity said on Monday.
The group, tracked as OceanLotus and APT32, has been around since at least 2012, targeting various types of organizations in Southeast Asian countries such as Vietnam, Philippines and China, with some campaigns extending to Europe and the United States. The list of targeted entities includes governments, journalists, activists, tech firms, consumer product manufacturers, banks, and organizations in the hospitality sector.
OceanLotus has used both Windows and Mac malware in its operations, along with some clever techniques that have allowed the group to evade detection.
Volexity has been tracking the threat actor since May 2017, specifically attacks aimed at the Association of Southeast Asian Nations (ASEAN), and media, human rights, and civil society organizations. The security firm agrees with FireEye’s previous assessment that OceanLotus is likely based in Vietnam.
“Volexity believes the size and scale of this attack campaign have only previously been rivaled by a Russian APT group commonly referred to as Turla,” the security firm said in a blog post.
Volexity’s analysis showed that OceanLotus’s watering hole attacks involved more than 100 compromised websites belonging to government, military, media, civil society, human rights and oil exploitation entities.
Researchers determined that the group’s attacks are highly targeted; the compromised sites served malicious code only to visitors who were on a whitelist. Targeted users are shown a fake screen designed to trick them into authorizing a malicious Google app that could access the victim’s emails and contacts. Some of the compromised websites were also set up to deliver backdoors and other types of tools, including legitimate software (e.g. Cobalt Strike) and custom malware.
Researchers also noticed that the attackers created many fake domains designed to mimic legitimate services such as AddThis, Akamai, Baidu, Cloudflare, Disqus, Facebook and Google. Many of these websites leveraged SSL certificates provided by Let’s Encrypt, whose services have been increasingly abused by cybercriminals.
“Volexity believes the OceanLotus threat group has rapidly advanced its capabilities and is now one of the more sophisticated APT actors currently in operation,” the company concluded.
OceanLotus’ sophistication was also described recently in a report from Cybereason, which detailed the group’s cat-and-mouse games within the systems of a global company operating in Asia.
One Third of The Internet Has Seen a DDoS Attack In The Past Two Years
7.11.2017 securityaffairs Attack
A group of researchers has conducted a rigorous comprehensive characterization of this DDoS attacks and of countermeasures to mitigate the associated risks.
Denial of Service (DoS) attacks have been around about as long as computers have been network connected. A website’s purpose is to accept connections from the Internet and return information. A bad actor can take advantage of this setup to overwhelm the web server with so many connection requests that valid connections are denied. If your business relies on eCommerce to sell products, a DoS attack directly affects your revenue. For this reason, a lot of people work to find methods to guard against such attacks. And bad actors work to find new ways of overcoming such protections.
One method deployed by the bad actors is the Distributed Denial of Service (DDoS) attack. Many computers work together to attack a single target. Defenders put in new defences and attackers combine ever-larger collections of devices in a cyber arms race of sorts. This arms race took a new turn in 2016 when the Mirai botnet was unleashed against DNS servers showing how potent a DDoS attack can be. Leveraging consumer devices like home routers and webcams, Mirai was able to maintain a sustained attack of 640Gbps. This overwhelmed DNS servers in the United States making large portions of the Internet unavailable. There followed several equally high profile attacks and people woke up to the new reality.
In 2017, researchers uncovered a new botnet which is expanding on the tricks used by Mirai. In addition to scanning for default passwords, Reaper uses exploits to compromise more devices and grow the attack potential. There are disagreements about the specific size of the Reaper botnet, but everyone agrees it is a significant threat.
These major botnets are capable of impacting large portions of the Internet and getting into the headlines doing it. But there is another DoS story that is arguably more impactful and less well known. Over 28,00 DoS attacks occur on the Internet every day!
A group of researchers unveiled their findings at the recent AMC Internet Measurement Conference in London. They gathered data from DDoS Protection Services (DPS) , amplification honeypots, and a DNS measurement platform. The data showed that one-third of all /24 networks recently estimated to be active on the Internet have suffered at least one DoS attack over the last two years.
“Our results reveal the massive scale of the DoS problem, including an eye-opening statistic that one-third of all /24 networks recently estimated to be active on the Internet have suffered at least one DoS attack over the last two years. We also discovered that often targets are simultaneously hit by different types of attacks” reads the research paper published by the experts.
While large-scale attacks like Mirai and Reaper may get the headlines, this amount of DDoS attacking will have real impacts for the victims.

The researchers noted that victims are likely to engage DPS providers following an attack.
“One of the things we show is if a website is attacked, this creates an urgency for people to start outsourcing to protection services,” said Mattjis Jonker, one of the researchers from the University of Twente.
This early research sheds light on the breadth and scale of the problem beyond the headline-grabbing attacks.
“During this recent two-year period under study, the internet was targeted by nearly 30,000 attacks per day,” said Alberto Dainotti, one of the researchers from CAIDA (Center for Applied Internet Data Analysis)
“These absolute numbers are staggering, a thousand times bigger than other reports have shown.”
The researchers have also validated some assumptions about potential targets. The United States hosts around 25% of web addresses and received around 25% of DDoS attacks. Following a similar pattern, Google, GoDaddy, and Wix services host the most websites and also see the most attacks.
Following this early success, researchers are next planning to include more data including DoS attacks on email servers with the ultimate goal being DDoS protection solutions.
The researchers plan to investigate the impact of DoS attacks on mail infrastructure in future projects, they already instrumented a measurement infrastructure to query for more DNS RRs on the names found in MX records.
New GIBON Ransomware Emerges
7.11.2017 securityweek Ransomware
A newly discovered ransomware family called "GIBON" is targeting all files on machines that it has managed to infect, except those located in the Windows folder.
The ransomware is being sold on underground criminal forums for $500 and has been available there since at least May 2017. Despite that, however, security researchers got a glimpse of it only recently, and a decrypter for it was released last week.
The observed attack involving this threat was using malicious spam emails for distribution, but the exact delivery mechanism isn’t known at the moment.
Once it has infected a machine, GIBON connects to its command and control (C&C) server and registers the new victim by sending a base64 encoded string containing the timestamp, Windows version, and the "register" string (which tells the C&C that this is a new victim).
The server’s response contains a base64 encoded string that the ransomware uses as the ransom note. As BleepingComputer’s Lawrence Abrams notes, this setup allows the malware author to update the ransom note on the fly, without having to compile a new executable.
Once the victim has been registered, the ransomware generates an encryption key locally and then sends it to the C&C server as a base64 encoded string. The key is used to encrypt all of the files on the computer and appends the .encrypt extension to every encrypted file's name.
The threat continues to ping the server during the encryption process to inform it that the operation is still ongoing. When the process has been completed, it sends a final message to the server, containing the string "finish", a timestamp, Windows version, and the number of files encrypted.
GIBON drops a ransom note on each folder where a file has been encrypted, providing users with information on what happened and instructing them to contact the malware author via email at bomboms123@mail.ru or subsidiary:yourfood20@mail.ru for payment instructions.
While analyzing the advertisement for the malware, the researchers discovered that the author falsely claims that a RSA-2048 key is used for encryption. In fact, an addition cipher is used, and the ransomware then encrypts this cipher with a RSA-2048 key.
GIBON’s author also claims that files encrypted with the ransomware are impossible to decrypt, which is false as well, given that a decryptor has been already released.
Qakbot, Emotet Increasingly Targeting Business Users: Microsoft
7.11.2017 securityweek Virus
The Quackbot and Emotet information stealing Trojans have been showing renewed activity over the past several months and are increasingly targeting enterprises, small and medium businesses, and other organizations, Microsoft says.
Featuring similar behavior, the two malware families have typically focused on individual online banking users, but their operators seem interested in new revenue streams. They also have expanded the Trojans’ capabilities with spreading functionality to increase the chances of multiple infections in corporate networks.
Over the years, the authors of Qakbot and Emotet focused on improving their code to evade detection, stay under the radar longer, and increase the chances of spreading to other potential victims. A look at the behavior of both malware families shows many similarities, Microsoft notes in a blog post.
Both Trojans use a dropper for infection (some recent Quakbot variants are spread via exploit kits), with the dropper being responsible for injecting code into explorer.exe, dropping the payload into random folders, and ensuring persistence. The two malware families can send encrypted information to the command and control (C&C) server.
Both Qakbot and Emotet have been designed to steal victim’s information and can do so by logging keystrokes, by hooking browser and network-related APIs, and stealing cookies and certificates.
The two Trojans also have the ability to spread to accessible network shares and drives, including removable drives such as USB sticks. They can also spread via default admin shares and shared folders and can attempt to brute-force attacks using enumerated Active Directory accounts and can use Server Message Block (SMB) to infect other machines.
According to Microsoft, while Windows 10 already includes a variety of features to keep users safe from malware families such as Qakbot and Emotet, enterprises can apply a series of steps to mitigate possible infections and remove the threats from their networks.
The first step would be to cut the infected machines from the network until they have been cleaned (an operation that can be easily performed with the help of Windows Defender Advanced Threat Protection, the company says) and to stop sharing folders that show sign of infection. Good credential hygiene should help as well.
As a second step, locking down the Scheduled Tasks folder and disabling autorun should prevent the malware from automatically running on the compromised machines. The next step would be to remove the Qakbot and Emotet from the infected systems, as well as any other related malware accompanying them.
Finally, enterprises are advised to determine the initial infection vector and take steps to address it, as well as to enable real-time protections on all machines in the network to prevent future infections. Setting email policies to block messages that might be carrying malware, protecting domain credentials and educating employees on such threats should also help prevent future infections.
Cisco patches a DoS vulnerability in IOE XE operating system
7.11.2017 securityaffairs Vulnerebility
Cisco fixed a vulnerability in IOE XE software that was introduced due to changes to its implementation of the BGP over an Ethernet VPN.
Cisco patches a DoS vulnerability in IOE XE software that was introduced due to changes to its implementation of the Border Gateway Protocol (BGP) over an Ethernet VPN.
The Cisco IOS XE operating system automates network operations and manages wired and wireless networks.
The vulnerability in the IOS XE, tracked as CVE-2017-12319, could be exploited remotely by an unauthenticated attacker to cause a DoS condition by crashing or corrupting the BGP routing table.
The flaw is linked is to a change in the implementation of the BGP MPLS-based Ethernet VPN(RFC 7432).
“A vulnerability in the Border Gateway Protocol (BGP) over an Ethernet Virtual Private Network (EVPN) for Cisco IOS XE Software could allow an unauthenticated, remote attacker to cause the device to reload, resulting in a denial of service (DoS) condition, or potentially corrupt the BGP routing table, which could result in network instability.” reads the Cisco security advisory.
The implementation change happened between IOS XE releases, releases prior to 16.3 that support BGP over Ethernet VPN configurations are vulnerable.
Cisco warned that only devices configured for an Ethernet VPN are vulnerable.
“When the BGP Inclusive Multicast Ethernet Tag Route or BGP EVPN MAC/IP Advertisement Route update packet is received, it could be possible that the IP address length field is miscalculated,” continues the Cisco advisory. “An attacker could exploit this vulnerability by sending a crafted BGP packet to an affected device after the BGP session was established. An exploit could allow the attacker to cause the affected device to reload or corrupt the BGP routing table; either outcome would result in a DoS.”
CISCO IOE XE
CISCO BGP implementation accepts packets only from defined peers, attackers must send malicious TCP packets spoofing the identity of a trusted BGP peer. An attacker could also inject malicious messages into the target BGP network.
“This would require obtaining information about the BGP peers in the affected system’s trusted network,” Cisco added. “The vulnerability may be triggered when the router receives a crafted BGP message from a peer on an existing BGP session. At least one BGP neighbor session must be established for a router to be vulnerable.”
Paradise Papers were the result of the hack of external attackers
7.11.2017 securityaffairs CyberSpy
Most of the Paradise Papers came from offshore legal firm Appleby, which confirms the leak came from a hack on its network and no insiders were involved.
The Paradise Papers is a collection of more than 13.4 million financial documents leaked online that has shed light on how major figures in the world of business, politics, entertainment, and sport move their funds through offshore tax havens.
Many stories emerged from the huge trove of documents, such as the allegations that Russia funded Facebook and Twitter investments through a business associate of Jared Kushner, President Donald Trump’s son-in-law and senior White House adviser.
“The investments were made through a Russian technology magnate, Yuri Milner, who also holds a stake in a company co-owned by Kushner, Donald Trump’s son-in-law and senior White House adviser.” reported The Guardian.
“The discovery is likely to stir concerns over Russian influence in US politics and the role played by social media in last year’s presidential election.”
Other documents analyzed by the BBC linked the Donald Trump’s commerce secretary, Wilbur Ross, to a shipping company firm transporting oil and gas for a firm whose shareholders include Vladimir Putin’s son-in-law and two men subject to US sanctions.

The Paradise Papers also revealed the £10m investment made by the UK Queen into funds in the Cayman Islands and Bermuda.
Most of the leaked documents came from the hack of the offshore legal firm Appleby.
The documents were first obtained by the German newspaper Süddeutsche Zeitung, the same that analyzed for first the Panama Papers last year.
The German newspaper did not reveal the source of the leak, however, Appleby blamed external hackers for the intrusion in its systems.
In a statement, Appleby said the leaked information came from a criminal hack on its computer systems, a subsequent forensic investigation excluded the incident was caused by insiders.
“We wish to reiterate that our firm was not the subject of a leak but of a serious criminal act. This was an illegal computer hack. Our systems were accessed by an intruder who deployed the tactics of a professional hacker and covered his/her tracks to the extent that a forensic investigation by a leading international Cyber & Threats team concluded that there was no definitive evidence that any data had left our systems. This was not the work of anybody who works at Appleby.” reported Appleby.
Appleby highlighted that it has done anything unlawful, anyway the incident could trigger serious legal repercussions against the company.
The Rise of Super-Stealthy Digitally Signed Malware—Thanks to the Dark Web
6.11.2017 thehackernews Virus
Guess what's more expensive than counterfeit United States passports, stolen credit cards and even guns on the dark web?
It's digital code signing certificates.
A recent study conducted by the Cyber Security Research Institute (CSRI) this week revealed that stolen digital code-signing certificates are readily available for anyone to purchase on the dark web for up to $1,200.
As you may know, digital certificates issued by a trusted certificate authority (CA) are used to cryptographically sign computer applications and software, and are trusted by your computer for execution of those programs without any warning messages.
However, malware author and hackers who are always in search of advanced techniques to bypass security solutions have been abusing trusted digital certificates during recent years.
Hackers use compromised code signing certificates associated with trusted software vendors in order to sign their malicious code, reducing the possibility of their malware being detected on targeted enterprise networks and consumer devices.
The infamous Stuxnet worm that targeted Iranian nuclear processing facilities in 2003 also used legitimate digital certificates. Also, the recent CCleaner-tainted downloads infection was made possible due to digitally-signed software update.
Stealthy Digitally-Signed Malware Is Increasingly Prevalent
However, separate research conducted by a team of security researchers have found that digitally signed malware has become much more common than previously thought.
The trio researchers—Doowon Kim, BumJun Kwon and Tudor Dumitras from the University of Maryland, College Park—said they found a total of 325 signed malware samples, of which 189 (58.2%) carried valid digital signatures while 136 carry malformed digital signatures.
"Such malformed signatures are useful for an adversary: we find that simply copying an Authenticode signature from a legitimate sample to an unsigned malware sample may help the malware bypass AV detection," the researchers said.
Those 189 malware samples signed correctly were generated using 111 compromised unique certificates issued by recognized CAs and used to sign legitimate software.
malware-digital-certificate
At the time of writing, 27 of these compromised certificates had been revoked, although malware signed by one of the remaining 84 certificates that were not revoked would still be trusted as long as carry a trusted timestamp.
"A large fraction (88.8%) of malware families rely on a single certificate, which suggests that the abusive certificates are mostly controlled by the malware authors rather than by third parties," the trio said.
The researchers have released a list of the abusive certificates at signedmalware.org.
Revoking Stolen Certificate Doesn't Stop Malware Immediately
Even when a signature is not valid, the researchers found that at least 34 anti-virus products failed to check the certificate's validity, eventually allowing malicious code to run on the targeted system.
The researchers also conducted an experiment to determine if malformed signatures can affect the anti-virus detections. To demonstrate this, they downloaded 5 random unsigned ransomware samples that almost all anti-virus programs detected as malicious.
The trio then took two expired certificates that previously had been used to sign both legitimate software and in-the-wild malware and used them to sign each of the five ransomware samples.
Top Antivirus Fail to Detect Malware Signed With Stolen Certificates
When analysing the resulting ten new samples, the researchers found that many anti-virus products failed to detect the malware as malicious.
The top three anti-virus products—nProtect, Tencent, and Paloalto—detected unsigned ransomware samples as malware, but considered eight of out ten crafted samples as benign.
Even popular anti-virus engines from Kaspersky Labs, Microsoft, TrendMicro, Symantec, and Commodo, failed to detect some of the known malicious samples.
Other affected anti-virus packages included CrowdStrike, Fortinet, Avira, Malwarebytes, SentinelOne, Sophos, TrendMicro and Qihoo, among others.
"We believe that this [inability in detecting malware samples] is due to the fact that AVs take digital signatures into account when filter and prioritize the list of files to scan, in order to reduce the overhead imposed on the user’s host," the researchers said.
"However, the incorrect implementation of Authenticode signature checks in many AVs gives malware authors the opportunity to evade detection with a simple and inexpensive method."
The researchers said they reported this issue to the affected antivirus companies, and one of them had confirmed that their product fails to check the signatures correctly and they had planned to fix the issue.
The researchers presented their findings at the Computer and Communications Security (CCS) conference in Dallas on Wednesday.
For more detailed information on the research, you can head on to their research paper [PDF] titled "Certified Malware: Measuring Breaches of Trust in the Windows Code-Signing PKI."
Learn Ethereum Development – Build Decentralized Blockchain Apps
6.11.2017 thehackernews IT

As of today — 1 Bitcoin = $7300 USD (Approx 471,000 INR)
At the beginning of this year, 1 Bitcoin was approximately equal to $1000, and now it has surged to a new height, marking its market capitalization at over $124 billion.
Is it really too late to invest in Bitcoin or other cryptocurrencies like Ethereum?
For those wondering if they have missed the money-making boat, the answer is—NO, it's never too late to invest.
In case you are new to cryptocurrency trading, we have a simple step-by-step guide on our deal store that explains how to invest in cryptocurrencies.
However, the blockchain, the revolutionary technology behind Bitcoin and other digital currencies, is not always about cryptocurrencies.
Though it is a decentralized public database which ensures that all transactions are properly conducted and recorded, Blockchains can be used for a wide variety of applications, such as for digital identity management, smart assets, digital voting, distributed cloud storage, and so on.
While Bitcoin has long been dominant in the cryptocurrency market, the second largest cryptocurrency—Ethereum—offers much faster data processing than Bitcoin.
Moreover, Bitcoin was designed to be used as a currency only, whereas the Ethereum blockchain facilitates the development of all sorts of next-generation decentralized applications.
Organisations are recognizing Ethereum potential to make processes more efficient and secure, and programmers are opting for Ethereum development.
Also, since Ethereum technology is still in the early adopter stage, you can get in at ground level and become proficient before it blows up.
How to Become An Ethereum Developer?

So are you considering to learn blockchain technology and Ethereum development?
The Hacker News is making things easier for you by providing you an amazing deal on "The Complete Ethereum Blockchain Mastery Bundle," at a discount of 95 percent.
The Complete Ethereum Blockchain Mastery Bundle includes four online courses:
1. Ethereum Blockchain Developer: Build Projects Using Solidity—This course will help you get your hands on development practice with solidity and successfully build a complex, real-world, Ethereum-based distributed app using core development tools such as Mist, Geth & Ethereum Studio.
2. Blockchain Technology: A Guide To The Blockchain Ecosystem—This course will help you understand the blockchain ecosystem and the technology that surrounds it.
3. Ethereum Developer: Build A Decentralized Blockchain App—This course will help you build your own decentralized blockchain application.
4. Ethereum Developer Masterclass: Build Real-World Projects—This is the last course in The Complete Ethereum Blockchain Mastery Bundle that will help you launch an initial coin offering (ICO) and at the same time will help you build a decentralized exchange on the blockchain.
The Internet Sees Nearly 30,000 Distinct DoS Attacks Each Day: Study
6.11.2017 securityweek Attack
The incidence of denial-of-service (DoS) attacks has consistently grown over the last few years, "steadily becoming one of the biggest threats to Internet stability and reliability." Over the last year or so, the emergence of IoT-based botnets -- such as Mirai and more recently Reaper, with as yet unknown total capacity -- has left security researchers wondering whether a distributed denial-of-service (DDoS) attack could soon take down the entire internet.
The problem is there is no macroscopic view of the DoS ecosphere. Analyses tend to be by individual research teams examining individual botnets or attacks. Now academics from the University of Twente (Netherlands); UC San Diego (USA); and Saarland University (Germany) have addressed this problem "by introducing and applying a new framework to enable a macroscopic characterization of attacks, attack targets, and DDoS Protection Services (DPSs)."
The initial results, published in a paper (PDF) presented at IMC 2017 in London this week, took the researchers by surprise. In devising a methodology to assess the entire DoS ecosphere, they discovered "the massive scale of the DoS problem, including an eye-opening statistic that one-third of all /24 networks recently estimated to be active on the Internet have suffered at least one DoS attack over the last two years."
In developing their framework for a macroscopic evaluation of Dos, the researchers aggregated and analyzed data over the last two years from the the UCSD Network Telescope -- which captures evidence of DoS attacks that involve randomly and uniformly spoofed addresses -- and the AmpPot DDoS honeypots -- which witness reflection and amplification of DoS attacks.
The results are staggering. "Together," say the researchers, "our data sets of attack events account for 20.90 M attacks, targeting 6.34 M unique IP addresses, over a two-year period." The daily figures are no less surprising. By combining the direct attacks with the reflection attacks, the researchers discovered that the internet suffers an average of 28,700 distinct DoS attacks every day. This is claimed to be 1000 times greater than other reports have indicated.
"A takeaway from these results," say the researchers, "is that each day we see attacks on tens of thousands of unique target IP addresses, spread over thousands of autonomous systems."
The geolocation of the targets closely reflects internet address space utilization -- for example, the USA has 25.56% of all unique IP addresses, and is the target for about 25% of all randomly spoofed attacks. Chinese IP addresses are the second most common target for random spoofing attacks. However, there are some exceptions. Russia and France both rank higher in the percentage of attacks than their overall percentage of internet address space -- making these locations statistically more likely to receive DoS attacks. Japan is the opposite with almost 7% of address space (the third largest region), but ranking 14th in the honeypot dataset and 25th in the telescope data set of attacks -- making Japan statistically one of the safer regions.
The purpose of the study as to understand the overall scope and extent of DoS attacks together with the market reaction to them so that more efficient responses might be developed. In terms of current market reaction, it concludes that low-level, even if repeated, attacks are largely ignored by the site owners. By correlating attacks with the time web sites migrated their DoS defense to third-party DPS companies, the researchers were able to determine what triggers the use of a DPS. They found, in general, that attack duration does not strongly correlate with DPS migration; but early migration follows attacks of high intensity.
For now, this is a work in progress, and the researchers hope to expand its extent and coverage. For example, the current study concentrates on web attacks. The researchers note, however, that GoDaddyís e-mail servers, which are used by tens of millions of domain names, are frequently targeted by DoS attacks. "In future work," they say, "we plan to investigate the impact of DoS attacks on mail infrastructure and for this purpose we recently instrumented our measurement infrastructure to query for more DNS RRs on the names found in MX records."
The biggest single takeaway from this study, which aimed to provide a macroscopic view of the worldwide DoS problem, is that it has simultaneously discovered that the DoS problem is already many times greater than previously thought.
Malware signed with stolen Digital code-signing certificates continues to bypass security software
6.11.2017 securityaffairs Virus
A group of researchers demonstrated that malware signed with stolen Digital code-signing certificates continues to bypass security software.
A recent study conducted by the Cyber Security Research Institute (CSRI) revealed that stolen digital code-signing certificates are available for sale for anyone to purchase on the dark web for up to $1,200.
Digital code-signing certificates are a precious commodity in the criminal underground, digital certificates issued by a trusted certification authority (CA) are used to cryptographically sign software that is trusted by security solutions for execution on your machine.
Digitally signing malicious code could allow its execution on a machine, bypassing security measures in place.
One of the first malicious codes abusing digital code-signing certificates was the Stuxnet worm that was used to compromise Iranian nuclear enrichment process in 2005. Back to the present, the recent attack against the supply chain of the CCleaner software also leveraged a signed tainted version of the popular application to avoid the detection.
The security researchers Doowon Kim, BumJun Kwon and Tudor Dumitras from the University of Maryland, College Park have investigated the phenomena. The research team has found a total of 325 signed malware samples, of which 189 (58.2%) carried valid digital signatures while 136 carry malformed digital signatures.
The team published a research paper titled “Certified Malware: Measuring Breaches of Trust in the Windows Code-Signing PKI.”
“Digitally signed malware can bypass system protection mechanisms that install or launch only programs with valid signatures.” reads the paper.
“It can also evade anti-virus programs, which often forego scanning signed binaries. Known from advanced threats such as Stuxnet and Flame, this type of abuse has not been measured systematically in the
broader malware landscape”
The researchers reported that 189 malware samples signed correctly were generated using 111 compromised unique certificates issued by trusted CAs and used to sign legitimate software.
The experts have published the list of certificates abused by attackers at signedmalware.org.
“We identify 325 signed malware samples in our data set. Of these, 189 (58.2%) samples are properly signed while 136 carry malformed digital signatures, which do not match the binary’s digest” states the paper.
“Such malformed signatures are useful for an adversary: we find that simply copying an Authenticode signature from a legitimate sample to an unsigned malware sample may help the malware bypass AV detection,” explained the researchers.

At the time of writing, 27 of these compromised certificates had been revoked, the experts highlighted that executable files signed with one of the 84 certificates that were not revoked may still be valid.
“At the time of writing, 27 of these certificates had been revoked. While all the abusive certificates in our data set had expired, executable files signed with one of the 84 certificates that were not revoked may still be valid, as long as they carry a trusted timestamp obtained during the validity of the certificate” continues the paper
“A large fraction (88.8%) of malware families rely on a single certificate, which suggests that the abusive certificates are mostly controlled by the malware authors rather than by third parties,”
The experts explained that even after a stolen certificate is revoked it will not stop crooks from abusing them immediately.
The researchers found that at least 34 antivirus software failed to check the validity of digital certificates, allowing malicious code to run on the infected system.
The experts also conducted an experiment to determine if malformed signatures can affect the anti-virus detections, they downloaded 5 random unsigned ransomware samples that almost all anti-virus programs detected as malicious, then they signed their code using two expired certificates.
According to the experts, many anti-virus software failed to detect the malware.
“However, the impact of this attack varies with the AV products. The top three AVs affected are nProtect, Tencent, and Paloalto. They detected unsigned ransomware samples as malware, but considered eight of out our ten crafted samples as benign. Even well-known AV engines, e.g. Kaspersky, Microsoft, Symantec, and Commodo,
allow some of these samples to bypass detection.” explained the researchers.
“We believe that this [inability in detecting malware samples] is due to the fact that AVs take digital signatures into account when filter and prioritize the list of files to scan, in order to reduce the overhead imposed on the user’s host,”
“However, the incorrect implementation of Authenticode signature checks in many AVs gives malware authors the opportunity to evade detection with a simple and inexpensive method.”
The researchers reported this issue to the affected antivirus companies, in one case the company confirmed that their product fails to check the signatures correctly.
Bug in Tor Browser Exposed IP Addresses of macOS and Linux Users
6.11.2017 securityweek Vulnerebility
A critical vulnerability that could reveal a Tor user’s IP address was addressed over the weekend in the privacy-focused web browser.
Tracked as CVE-2017-16541, the vulnerability only impacted macOS and Linux users and was caused by a Firefox bug in handling file:// URLs. By exploiting the vulnerability, a malicious site could leak a user’s IP address.
“Once an affected user navigates to a specially crafted URL the operating system may directly connect to the remote host, bypassing Tor Browser,” a post on the Tor Project’s blog reveals.
The organization also notes that they are not aware of the vulnerability being exploited in the wild.
The vulnerability didn’t affect Windows users and was addressed in Tor Browser 7.0.9 and Tor Browser 7.5a7 in the alpha channel. Tails users and people using the sandboxed-tor-browser weren’t affected either, the browser’s developers explained.
Dubbed TorMoil, the security flaw was reported on October 26 by Filippo Cavallarin of wearesegment.com. Working together with Mozilla engineers, the Tor developers released a workaround the next day, but only resolved the issue partially. An additional fix was issued to patch all known bugs.
“The fix we deployed is just a workaround stopping the leak. As a result of that navigating file:// URLs in the browser might not work as expected anymore. In particular entering file:// URLs in the URL bar and clicking on resulting links is broken. Opening those in a new tab or new window does not work either. A workaround for those issues is dragging the link into the URL bar or on a tab instead,” the blog post continues.
Last week, the Tor Project also announced plans for a series of new features, including “offline service keys, advanced client authorization, a control port interface, improved guard algorithms, secure naming systems, statistics, mixed-latency routing, blockchain support, AI logic and a VR interface.”
These features build on the first alpha release of next generation of onion services, which was announced several weeks ago, following four years of development. Replacing the legacy onion system, which has been around for over 10 years, the new services include new crypto algorithms, improved authentication schemes, better defenses against info leaks, and reduced overall attack surface.
The legacy system will remain the default option for some more time, to provide users with enough time to migrate to the next generation. After bugs are addressed and features introduced, the next gen system will become default, and then the legacy system will be phased out entirely.
AWS S3 Buckets at Risk of "GhostWriter" MiTM Attack
6.11.2017 securityweek Attack
GhostWriter: Writable AWS S3 Buckets Could Be Exploited to Overwrite Existing Data and Files, or Upload Malware
The exposure of sensitive data via misconfigured AWS S3 buckets has been regular over the last few years. In two months this summer, researchers discovered thousands of potentially sensitive files belonging to the U.S. National Geospatial-Intelligence Agency (NGA); information on millions of Verizon customers; and a database containing details of 198 million American voters.
In each case a misconfiguration of the S3 buckets left the data freely accessible to anyone via the internet. Amazon's 'shared responsibility' model clearly states that Amazon is responsible for security of the cloud (that is, the cloud infrastructure) while the customer is responsible for security in the cloud (that is, protecting data through AWS configuration and/or other means). In leaving the data open to public reads, S3 data exposure is clearly the fault of the customers and not Amazon.
Now, however, Skyhigh Networks research has discovered that some AWS customers are also leaving their data open to public writes. Skyhigh calls this vulnerability, 'GhostWriter'. In a blog post Friday, chief scientist & VP Eng., Sekhar Sarukkai, warned, "In such cases a 3rd party, unbeknownst to either the data owner or the data consumer, can launch a surreptitious man-in-the-middle (MITM) attack."
Vulnerable buckets found by Skyhigh -- which has reported its findings to AWS -- are owned by leading national news/media sites, large retail stores, popular cloud services, and leading advertisement networks. An adversary merely has to locate writable buckets to be able to overwrite existing data and files, or upload malware into the bucket.
"Bucket owners who store JavaScript or other code should pay particular attention to this issue," warns Sarukkai, "to ensure that 3rd parties don't silently overwrite their code for drive-by attacks, bitcoin mining or other exploits. Even benign image or document content left open for overwriting can be exploited for steganography attacks or malware distribution."
Ironically, this vulnerability could affect researchers who find a readable bucket and download the data for analysis, not knowing that a third-party has already altered the data. However, the biggest danger will be to the data owners and authorized users who access the stored data. They could download and use incorrect data, or even download malware from their own or a partner's data.
It is not known whether this vulnerability has ever been exploited -- but it certainly exists. "We've informed our customers about misconfigured S3 Buckets and the possible opportunity for GhostWriter attacks and there has been some alarm," Skyhigh's chief European spokesperson Nigel Hawthorn told SecurityWeek. "Some have been experiencing issues of differing severity recently which GhostWriter may have been the cause of. Considering how widely used S3 is, it's hard to see how it hasn't been exploited. We have worked with those customers and AWS to rectify configurations."
Sarukkai believes that there are two aspects to staying safe from GhostWriter: 'trust but verify' (by ensuring that staff can only download from own or third-party buckets that are not susceptible to GhostWriter); and 'trust but audit' (by making sure that an organization's own S3 buckets are not publicly writable).
Skyhigh Networks has the facility to audit S3 buckets used by its own CASB customers, while "AWS provides many native best-practices and tools to manage and validate policies for configuring S3," notes Sarukkai. In August, Amazon announced a new service called Macie. Macie uses machine learning to help its customers discover, classify and protect sensitive data.
KRACK Detector is a tool to detect and prevent KRACK attacks in your network
6.11.2017 securityaffairs Attack
How to discover if your network is vulnerable to KRACK attack?
KRACK Detector is a script that can detect attacks against client devices on your network.
Last week I published a post warning of many industrial networking devices from various vendors are still vulnerable to the recently disclosed KRACK attack (Key Reinstallation Attack).
The Belgian researcher Mathy Vanhoef of imec-DistriNet, KU Leuven and his team of researchers discovered in the middle-October several key management flaws in the core of Wi-Fi Protected Access II (WPA2) protocol that could be exploited by an attacker to hack into Wi-Fi network and eavesdrop on the Internet communications stealing sensitive information (i.e. credit card numbers, passwords, chat messages, emails, and pictures).
The researchers devised an attack method dubbed KRACK attack (Key Reinstallation Attack) that works against almost any WPA2 Wi-Fi network.
The KRACK attack allows attackers to decrypt WiFi users’ data without cracking or knowing the password.
According to the researchers, the KRACK attack works against:
Both WPA1 and WPA2,
Personal and enterprise networks,
Ciphers WPA-TKIP, AES-CCMP, and GCMP
The KRACK attack works by exploiting a 4-way handshake of the WPA2 protocol that’s used to establish a key for encrypting traffic.
“When the victim reinstalls the key, associated parameters such as the incremental transmit packet number (i.e. nonce) and receive packet number (i.e. replay counter) are reset to their initial value,” explained Vanhoef. “Essentially, to guarantee security, a key should only be installed and used once. Unfortunately, we found this is not guaranteed by the WPA2 protocol. By manipulating cryptographic handshakes, we can abuse this weakness in practice.”

The attacker just needs to trick a victim into re-installing an already-in-use key, which is achieved by manipulating and replaying cryptographic handshake messages.
How to discover if your network is vulnerable to KRACK attack?
KRACK Detector is a script written in Python Language that can detect possible KRACK attacks against client devices on your network. It uses Python 2 for backward compatibility with older operating systems.
“KRACK Detector is a Python script to detect possible KRACK attacks against client devices on your network. The script is meant to be run on the Access Point rather than the client devices. It listens on the Wi-Fi interface and waits for duplicate message 3 of the 4-way handshake. It then disconnects the suspected device, preventing it from sending any further sensitive data to the Access Point.” states the description of the tool.
Network administrators have to run the script on the Access Point rather than the client devices, it listens on the Wi-Fi interface and waits for duplicate message 3 of the 4-way handshake. Once it detects a device sending the handshake message it then disconnects it in order to prevent it from sending any further sensitive data to the Access Point.
The presence of message 3 of the 4-way handshake is a necessary condition for the Krack attack, however, it might be retransmitted even if no attack is ongoing.
“In such a case the client device will be disconnected from the Wi-Fi network. Some client devices will take some time to re-authenticate themselves, losing the Wi-Fi connection for a few seconds.” reported the Kitploit.com.
No external Python packages are required, network administrators have to run the script as root and pass the Wi-Fi interface as a single argument.
Administrators need to use the actual Wi-Fi interface and not any bridge interface it connects to.
python krack_detect.py wlan0
The tool also allows avoiding suspending suspected devices by using the “-n” flag
python krack_detect.py -n wlan0
The tool is available on Github at the following link:
Download KRACK Detector
The GIBON Ransomware appears in the threat landscape
6.11.2017 securityaffairs Ransomware
A new strain of ransomware dubbed GIBON ransomware was spotted by the ProofPoint researcher Matthew Mesa that observed it being distributed via malspam.
The spam messages use a malicious document as attachment containing macros that once enabled will download and install the ransomware on a victim’s machine.
The researcher dubbed the ransomware GIBON because of the presence of the string “GIBON” in two places. The experts first noticed this name in the user agent string of the malware using in the communications with the Command & Control server.

The second place where it is possible to find the string “GIBON” is the Admin panel for the ransomware, the logo is from the Russian television company VID.

When the GIBON ransomware is first executed, it will connect to the C&C and register a new victim by sending a base64 encoded string that contains the timestamp, the version of Windows, and the “register” string.
The C&C, in turn, will send back a response that contains a base64 encoded string that will be used by GIBON ransomware as the ransom note.
Once the infected machine is registered with the C&C, it will locally generate an encryption key and send it to the server as a base64 encoded string. The malware will use the key to encrypt all files on the target computer, it appends the .encrypt extension to the encrypted file’s name.
“Now that the victim has been registered and key transmitted to the C2, the ransomware will begin to encrypt the computer. While encrypting the computer, it will target all files regardless of the extension as long as they are not in the Windows folder.” reads the blog post published by Lawrence Abrams.
“During the encryption process, GIBON will routinely connect to the C2 server and send it a “PING” to indicate that it is still encrypting the computer.”
The malware drops a ransom note in each folder containing the encrypted files, it also generates a ransom note named READ_ME_NOW.txt.
“Attention! All the files are encrypted!
To restore the files, write to the mail:bomboms123@mail.ru
If you do not receive a response from this mail within 24 hours,
then write to the subsidiary:yourfood20@mail.ru”
Once the GIBON ransomware completed the file encryption a computer, it will send a message to the C&C server with the string “finish”, a timestamp, the Windows version, and the number of files that were encrypted.
The good news is that files encrypted by this ransomware can be decrypted using the GibonDecrypter.
Hackers leak WhatsApp screenshots and intimate photos of WWE Diva Paige
6.11.2017 securityaffairs Hacking
A new batch of WhatsApp screenshots and intimate photos of the WWE celebrity Diva Paige was published on a popular celebrity leak website.
In March, hackers leaked online nude photos and videos of WWE Diva Paige (real name is Saraya Jade-Bevis), and now a new batch of x-rated images of the celebrity appeared on the Internet.
PAIGE ✔@RealPaigeWWE
Personal and private photos of mine were stolen and unfortunately they were shared publicly without my consent.
12:16 AM - Mar 18, 2017
4,464 4,464 Replies 7,100 7,100 Retweets 19,597 19,597 likes
Twitter Ads info and privacy
The photos are authentic and were published on the celebrity gossip site called CelebJihad.

Other WWE celebrities are listed on the popular websites, other athletes, in fact, were targeted by the same hackers.
The same website proposes personal and private photos of WWE’s Diva and ring announcer JoJo.
Hackers published WhatsApp screenshots of explicit photos and selfies along with chat conversations with WWE wrestler Xavier Woods.
The WWE star is planning to return to fight after the convalescence of successful neck surgery.
The same content was also shared by Twitter account.
The hacker who leaked the pictures online announced to release more content in coming days.
Unfortunately, these events are becoming even more frequent, in 2017 personal and private photos of other WWE celebrities were leaked online.
The colleagues at the Hackread.com reported the data leaks belonging Maria, Melina, Kaitlyn, Charlotte Flair, and Victoria.
On August, intimate images of Miley Cyrus, Stella Maxwell, Kristen Stewart, Tiger Woods and Lindsey Vonn have been posted online by the same celebrity leak website.
Below the list of recommendations to keep your iCloud account secure.
Do not click on any suspicious links or attachments in unsolicited emails you received, even if they appear to have been sent by Google, Apple or Microsoft.
Enable two-factor authentication on your accounts.
Never provide sensitive and personal information via email.
Use strong passwords and change them regularly. Use different passwords for all your accounts.
The TorMoil Bug – Tor Browser Critical Security Vulnerability
6.11.2017 Vulnerebility
Recently, our CEO, Filippo Cavallarin, discovered a critical security vulnerability in Tor Browser affecting Mac and Linux users that can lead to the leakage of users real IP address. We named it TorMoil.
We are Segment respects the Responsible Disclosure principles so further details are not disclosed right now as not all users have updated yet. We’ll disclose the exploit and all the details once a proper fix for the underlying issue is available to all users.
Due to a Firefox bug in handling file:// URLs it is possible on both systems that users leak their IP address. Once an affected user navigates to a specially crafted web page, the operating system may directly connect to the remote host, bypassing Tor Browser
If you are one of those people that rely on Tor Browser to safely browse the Internet, the message is just one: keep your Tor Browser updated!
For those of you who don’t know what Tor Browser is, it is a free application to browse the internet with a high degree of privacy. Using Tor Browser is advantageous to people around the world facing a variety of threats, from advertisers collecting and selling personal data, to oppressive censorship and surveillance. More information about the Tor Project is available at: https://torproject.org.
Populární stránka ke streamování anime Crunchyroll infikovala návštěvníky malwarem
6.11.2017 Živě.cz Viry

Je celkem obvyklé, že na velké weby čas od času zaútočí podlí útočníci, ale Crunchyroll, největší streamovací služba s japonskými seriály anime, se stala o víkendu terčem mimořádné závažného útoku.Neznámí pachatelé nahradili domovskou stránku Crunchyroll falešnou a návštěvníky zkoušeli infikovat malwarem.K útoku došlo během soboty. Útočníci se snažili docílit toho, aby si návštěvníci s Windows PC stáhli infikovaný program „CrunchyViewer“. Když to člověk udělal a soubor spustil, na pozadí systému se mu aktivoval nechtěný proces. Mobilní uživatelé ohroženi nebyli. Stalo se to, že útočníkům se podařilo napadnou Cloudflare konfiguraci mateřské společnosti služby Ellation, která běžně přesměrovává provoz do Crunchyroll a nasměrovali ji na falešný server obsahující malware. Dobrá správa pro uživatele tak je, že vlastní stránka zasažena nebyla a všechny uživatelské účty jsou v bezpečí.V tuto chvíli je již vše v pořádku a návštěvníci se nemusí ničeho obávat. Bude ale chvíli trvat, než se internet dozví, kdo za útokem stál.
Je celkem obvyklé, že na velké weby čas od času zaútočí podlí útočníci, ale Crunchyroll, největší streamovací služba s japonskými seriály anime, se stala o víkendu terčem mimořádně závažného útoku. Neznámí pachatelé nahradili hlavní stránku falešnou a návštěvníky zkoušeli infikovat malwarem.
K útoku došlo během soboty. Útočníci se snažili docílit toho, aby si návštěvníci s Windows PC stáhli infikovaný program „CrunchyViewer“. Když to člověk udělal a soubor spustil, na pozadí systému se mu aktivoval nechtěný proces. Mobilní uživatelé ohroženi nebyli.
Kdo za útokem stojí a co bylo jeho účelem, je předmětem vyšetřování. Stalo se nicméně to, že útočníkům se podařilo napadnou konfiguraci uložiště Cloudflare mateřské společnosti služby Ellation, která běžně přesměrovává provoz do Crunchyroll, a nasměrovali ji na falešný server obsahující malware. Vlastní stránka zasažena nebyla a všechny uživatelské účty jsou v bezpečí.
Nic tragického se nestalo, ani pokud člověk infikovaný soubor stáhnul a nespustil. Pokud tak však udělal, je možné manuálně odstranit problematické soubory a registry. Jak na to, Ellation popisuje na své stránce.
The NIC Asia Bank is the last victim of the SWIFT hackers
6.11.2017 securityaffairs Hacking
The NIC Asia Bank requested the support of the Central Investigation Bureau of Nepal Police to track down the crooks who hacked the SWIFT server.
Once again hackers targeted SWIFT systems to steal money from a financial institution. The victim is the NIC Asia Bank that once discovered illegal fund transfer with its SWIFT server requested support from the Central Investigation Bureau of Nepal Police to track down the crooks.

NIC Asia Bank had carried out a forensic investigation with the support of experts from KPMG India and submitted its findings to Nepal Rastra Bank. NIC Asia Bank also sent the report of the initial investigation to the Central Investigation Bureau.
Pushkar Karki, deputy inspector general of Nepal Police and chief of CIB, confirmed that the payment order was placed by hackers who compromised the bank’s SWIFT server.
“CIB has started investigating how the server was hacked,” said Karki. “Our investigation will reveal whether or not the bank had adopted proper safeguards and which party was involved in the hacking.”
The official said NIC Asia Bank recently sought CIB support after the initial investigation carried out by KPMG and NRB.
“NIC Asia’s reluctance to report the case to CIB and the ‘inconclusive’ investigation carried out by KPMG had raised doubts whether a foreign party was involved in the illegal transfer of fund or it was an insider job.” reported The Himalayan Times.
CIB is investigating the incident with the support of both the central bank and NIC Asia Bank. NIC Asia Bank immediately reported the security breach to NRB after it discovered the suspicious transactions through its SWIFT server.
The SWIFT server of NIC Asia Bank was hacked during Tihar and the hacker tried to transfer the money to various parties in six countries, including Japan, UK, the US, and Singapore, through Standard Chartered New York and Mashreq Bank New York, through which the bank operates its foreign currency accounts.
The collaboration with the central bank and the other banks, NIC Asia was able to block the fraudulent transactions except for around Rs 60 million that was reportedly released to the concerned parties.
The overall amount of money retrieved by the bank was around Rs 460 million, Rs 400 million has been retrieved.
“A separate investigation carried out by the central bank immediately after NIC Asia Bank notified the regulator revealed that staffers assigned to operate the SWIFT system of the bank had used a computer dedicated for SWIFT operation for other purposes also.” added The Himalayan Times
The NIC Asia Bank has transferred all of the six staffers who handled the SWIFT operation to other departments.
Popular Anime crunchyroll.com hijacked to distribute a keylogger
5.11.2017 securityaffairs Hacking
The popular Anime site Crunchyroll.com was hijacked to distribute malware, according to the operators the site was not hacked.
The popular Anime site Crunchyroll.com was hijacked to distribute malware, once discovered the hack, the operators have issued alerts informing visitors to don’t visit the site and later they took it offline.
4 Nov
Crunchyroll.de ✔ @Crunchyroll_de
ACHTUNG! BITTE TEILEN!
Bitte gegenwärtig NICHT unsere Webseite ansteuern, da wir aktuell ein Problem mit Schadsoftware haben.
Crunchyroll.de ✔@Crunchyroll_de
And for our English-speaking audience
Please DO NOT access our website at the current time. We are aware of the issues and are working on it
1:06 PM - Nov 4, 2017
39 39 Replies 1,247 1,247 Retweets 895 895 likes
Twitter Ads info and privacy
The visitors were prompted to download and try a new desktop version of Crunchyroll software that was tainted with a malware.
“Their main page auto downloads a suspicious .exe file. So far I havent seen more info on their twitter about what happened.” reported a Reddit user.

It was a fake desktop application that was not offered by the Crunchyroll site.
According to Crunchyroll, attackers did not breach the website, it appears as a DNS hijack that redirected users to a bogus copy of the website used by the attackers to deliver the malware.
4 Nov
Crunchyroll.de ✔ @Crunchyroll_de
ACHTUNG! BITTE TEILEN!
Bitte gegenwärtig NICHT unsere Webseite ansteuern, da wir aktuell ein Problem mit Schadsoftware haben.
Crunchyroll.de ✔@Crunchyroll_de
And for our English-speaking audience
Please DO NOT access our website at the current time. We are aware of the issues and are working on it
1:06 PM - Nov 4, 2017
39 39 Replies 1,247 1,247 Retweets 895 895 likes
Twitter Ads info and privacy
At the time, the situation has been solved.
Crunchyroll ✔@Crunchyroll
We've just gotten the all-clear to say that http://www.crunchyroll.com/ is back online!! Thank you SO MUCH for your patience ~ ❤️
5:31 PM - Nov 4, 2017
278 278 Replies 3,141 3,141 Retweets 8,227 8,227 likes
Twitter Ads info and privacy
Lawrence Abrams from Bleepingcomputer.com has analyzed the malicious code delivered by the website, once executed it would extract an embedded base64 encoded file to %AppData%\svchost.exe and execute it.
When the malware starts, it will create an autostart called Java that executes the %AppData%\svchost.exe program when the victim logs into the computer.
According to the security researcher Bart Blaze who followed the hack, the malware was a keylogger.
“There are claims the malware will additionally install ransomware – I have not observed this behaviour, but it is definitely possible once the C2 sends back (any) commands. More likely, it is a form of keylogger – malware that can record anything you type, and send it back to the attacker.” wrote Blaze.
The good news for users infected by the malware is that it is easy to remove even if it is detected only by 25 out of 67 antivirus software.
Below the instructions published by Lawrence Abrams from Bleepingcomputerfrom;
Open the Windows Registry Editor by typing regedit in the Start Menu search bar. When you see regedit.exe or Registry Editor in the search results, click on it to launch the program.
When the Registry Editor is open, navigate to HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run and single-left click on the Run key. You should now see in the right pane a value called Java.
Now right-click on the Java entry and select Delete as shown in the image below.
When it asks you to confirm that you wish to delete the value, click on the Yes button.
Now reboot your computer and when you log back in, the malware executable will no longer be started.
Now navigate to the %AppData% (Typically C:\users\[user_name]\appdata\roaming) folder and you should see a program called svchost.exe.
Right-click on this file and select Delete to delete it from the computer.
Now perform a scan using your installed security software. If you do not have a security software, now may be a good time to install one.
If this malware was indeed a keylogger, you may also want to consider changing the password to any sites that you logged into after installing this fake Crunchyroll program.
Flaws in IEEE P1735 electronics standard expose intellectual property
5.11.2017 securityaffairs Vulnerebility
Experts discovered flaws in IEEE P1735 electronics standard, which describes methods for encrypting electronic-design intellectual property (IP).
Crypto flaws in the IEEE P1735 electronics standard expose highly-valuable intellectual property in plaintext.
The IEEE P1735 electronics standard provides recommendations on methods and techniques for encrypting electronic-design intellectual property about the hardware and software in electronic equipment.
The standard describes how to protect intellectual property (IP) for commercial electronic design, as well as the management of access rights for such IP. It defines interoperability models to allow hardware and software from different to interact and at the same time protecting them from reverse-engineering and IP theft.
“This standard specifies embeddable and encapsulating markup syntaxes for design intellectual property encryption and rights management, together with recommendations for integration with design specification formats described in other standards.” states IEEE.
“It also recommends use models for interoperable tool and hardware flows, which will include selecting encryption and encoding algorithms and encryption key management.”

According to the IEEE P1735 electronics standard allow code from different manufacturers to run in hardware components and interact securely, this means that it is not possible to decrypt them.
The IEEE P1735 is implemented by almost all vendors to protect their intellectual property.
Now a group of researchers from the University of Florida has recently reviewed the IEEE P1735 electronics standard and discovered that some vulnerabilities expose it to cyber attacks.
The team composed of five experts published a paper titled “Standardizing Bad Cryptographic Practice,” at the end of September.
“The P1735 IEEE standard describes methods for encrypting electronic-design intellectual property (IP), as well as the management of access rights for such IP. The methods are flawed and, in the most egregious cases, enable attack vectors that allow recovery of the entire underlying plaintext IP.” reported the US-CERT.
“Some of these attack vectors are well-known, such as padding-oracle attacks. Others are new, and are made possible by the need to support the typical uses of the underlying IP.”
The experts discovered several crypto weaknesses, one of them could be exploited by an attacker to bypass encryption safety guards and access intellectual property in cleartext.
The access to such information represents a serious problem for hardware and software vendors, they can suffer intellectual property theft and they can potentially go out of business.
Another vulnerability discovered by the researchers could be exploited by hackers to hide hardware malware inside products. The exploitation of the flaw could allow a competitor to sabotage a vendor.
Below the list of CVE IDs assigned to the major vulnerabilities discovered by the experts:
CVE-2017-13091: improperly specified padding in CBC mode allows use of an EDA tool as a decryption oracle.
CVE-2017-13092: improperly specified HDL syntax allows use of an EDA tool as a decryption oracle
CVE-2017-13093: modification of encrypted IP cyphertext to insert hardware trojans.
CVE-2017-13094: modification of the encryption key and insertion of hardware trojans in any IP.
CVE-2017-13095: modification of a license-deny response to a license grant.
CVE-2017-13096: modification of Rights Block to get rid of or relax access control.
CVE-2017-13097: modification of Rights Block to get rid of or relax license requirement.
Warning: Critical Tor Browser Vulnerability Leaks Users’ Real IP Address—Update Now
5.11.2017 thahackernews Safety
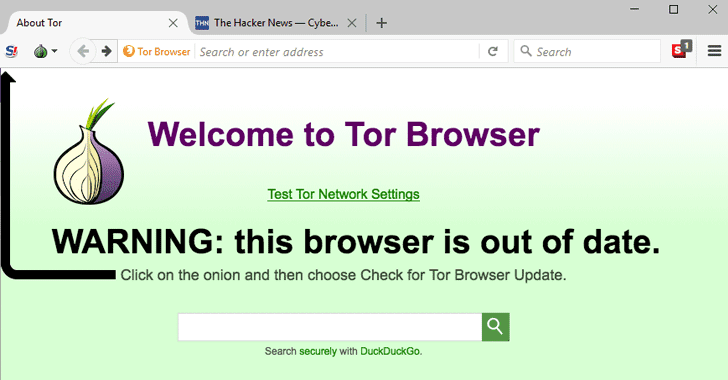
If you follow us on Twitter, you must be aware that since yesterday we have been warning Mac and Linux users of the Tor anonymity browser about a critical vulnerability that could leak their real IP addresses to potential attackers when they visit certain types of web pages.
Discovered by Italian security researcher Filippo Cavallarin, the vulnerability resides in FireFox that eventually also affects Tor Browser, since the privacy-aware service that allows users to surf the web anonymously uses FireFox at its core.
Dubbed by the researcher as TorMoil, the vulnerability affects Tor browser for macOS and Linux and not for Windows, but keeping in mind the security and privacy of Tor users, details about this flaw has not been yet publicly revealed.
Cavallarin, CEO of the security firm We Are Segment, privately reported the security vulnerability to Tor developers on Thursday (October 26), and the Tor developers have rolled out an emergency update Tor version 7.0.8.
According to a short blog post published Tuesday by We Are Segment, the TorMoil vulnerability is due to a Firefox issue in "handling file:// URLs."
Important: Tor Browser 7.0.9 is released (Linux/MacOS users) - Fixes a critical security flaw that leaks IP address https://t.co/gITj8F7DnW
— The Hacker News (@TheHackersNews) November 3, 2017
TorMoil is triggered when users click on links that begin with file:// addresses, instead of the more common https:// and http:// addresses.
"Due to a Firefox bug in handling file:// URLs it is possible on both systems that users leak their IP address," the blog post reads.
"Once an affected user [running macOS or Linux system] navigates to a specially crafted web page, the operating system may directly connect to the remote host, bypassing Tor Browser."
The Tor Project has currently issued a temporary workaround to prevent the real IP leakage.
So, macOS and Linux users may found the updated versions of the Tor anonymity browser not behaving properly while navigating to file:// addresses, until a permanent patch becomes available.
"The fix we deployed is just a workaround stopping the leak. As a result of that navigating file:// URLs in the browser might not work as expected anymore. In particular entering file:// URLs in the URL bar and clicking on resulting links is broken," the Tor Project said in a blog post published Friday.
"Opening those in a new tab or new window does not work either. A workaround for those issues is dragging the link into the URL bar or on a tab instead. We track this follow-up regression in bug 24136."
According to the Tor Project, users of both the Windows versions of Tor, Tails and the sandboxed-tor-browser that's in alpha testing are not affected.
The Tor Project also said there's no evidence the TorMoil vulnerability has been actively exploited by hackers to obtain the IP addresses of Tor users.
However, lack of evidence does not prove the bug was not exploited by nation-state attackers and skilled hackers, given the high-demand of Tor zero-day exploit in the market, where Zerodium is ready to pay anyone $1 Million for its exploit.
In an attempt to keep its users' privacy protected, the Tor Project has recently announced the release of Tor 0.3.2.1-alpha that includes support for the next generation onion services, with the integration of new cutting-edge encryption and improvement of overall authentication into its web service.
The Tor Project to Beef Up Privacy with Next-Generation of Onion Services
5.11.2017 thahackernews Safety

The Tor Project has made some significant changes to its infrastructure by improving the way the 'onion' network protects its users' privacy and security.
Since the beginning, the largest free online anonymity network has been helping users browse the web anonymously, and its onion service provides a network within which encrypted websites can be run anonymously.
However, the infrastructure design and encryption behind the service has become little outdated, eventually leaving it vulnerable to potential and resourceful attackers.
Tor network has become such a potential target that even Zerodium, a company that acquires and resells zero-day exploits, is ready to pay $1 million for Tor zero-day exploits.
Keeping these concerns in mind, the Tor Project has been working to upgrade its infrastructure over the past four years, and the good news is…
A few weeks ago, the Tor Project announced the release of Tor 0.3.2.1-alpha that includes support for the next generation onion services, with the integration of new cutting-edge encryption algorithms and improvement of overall authentication into its web service.
The directory system has also been designed entirely to "defend against info leaks and reduce the overall attack surface," George Kadianakis from the Tor Project said while discussing the cryptography used in the new implementation.
The alpha release also addresses recently discovered security issues in the protocol including the potential for rogue nodes to learn about the network, eventually reducing anonymity.
The Tor Project has announced a few more security features for the upcoming update, which will make it much harder for attackers to unmask the real identity of the Tor users.
"As the current code stabilizes further, we plan to add features like offline service keys, advanced client authorization, a control port interface, improved guard algorithms, secure naming systems, statistics, mixed-latency routing, blockchain support, AI logic and a VR interface (j/k about some of these)," The Tor Project's blog post reads.
This new implementation of the onion service for now also supports the current onion network, but it will soon replace the whole network and become the default implementation.
The updates are available for the alpha release, which can be found here.
Fake WhatsApp On Google Play Store Downloaded By Over 1 Million Android Users
5.11.2017 thahackernews Social

Cybercriminals are known to take advantage of everything that's popular among people in order to spread malware, and Google's official Play Store has always proved no less than an excellent place for hackers to get their job done.
Yesterday some users spotted a fake version of the most popular WhatsApp messaging app for Android on the official Google Play Store that has already tricked more than one million users into downloading it.
Dubbed Update WhatsApp Messenger, came from an app developer who pretended to be the actual WhatsApp service with the developer title "WhatsApp Inc."—the same title the actual WhatsApp messenger uses on Google Play.
You might be wondering how the sneaky app developer was able to use the same title as the legitimate Facebook-owned maker of the messaging client—thanks to a Unicode character space.
The app maker added a Unicode character space after the actual WhatsApp Inc. name, which in computer code reads WhatsApp+Inc%C2%A0.
However, this hidden character space at the end of the WhatsApp Inc. would be easily invisible to an average Android user browsing Google Play Store, allowing this dodgy version of the app to masquerade as a product of WhatsApp Inc.
In other words, the titles used by the fake app maker and real WhatsApp service are different but appeared same to a user.
According to Redditors, who first spotted this fake app on Friday, the app was not a chat app; instead, it served Android users with advertisements to download other apps.
"I've also installed the app and decompiled it," one Redditor said. "The app itself has minimal permissions (internet access) but it's basically an ad-loaded wrapper which has some code to download a second apk, also called 'whatsapp.apk.' The app also tries to hide by not having a title and having a blank icon."
Google has now removed the fake WhatsApp Android app from its official Play Store, but this incident once again marked the tech giant's failure to spot the scam on its app platform—even for the program that had more than a million downloads.
It is an unfortunate truth that even after so many efforts by Google (even recently launched Bug Bounty Program), malicious apps continuously somehow managed to fool its Play Store's security mechanism and infect millions of Android users.
Google Play Store is still surrounded by hundreds of other fake and malicious apps that trick users into downloading and installing them and potentially infect their smartphones to carry out malicious things without their knowledge.
So, users are advised to be more vigilant while downloading apps not only from the third-party app store but also from official Play Store in order to protect themselves.
Hacker threatens Canadian University to dump student info unless the university pay a ransom
5.11.2017 securityaffairs Ransomware
A hacker is attempting to extort the Canadian University of Fraser Valley (UFV), threatening to dump student information unless the university pays a ransom.
Extortion is a winning criminal model for crooks, a hacker is attempting to extort the Canadian University of Fraser Valley (UFV), threatening to dump student information unless the university pay 30,000 CAD (23,000 USD).
The University of Fraser Valley (UFV), is located in the Canadian town of Abbotsford, south-east of Vancouver.

The hackers breached the network at the university and gathered student information, including names, email addresses, phone numbers, physical addresses, grades information, some in some case financial data.
At the time it is not clear the time of the attack or the way hackers breached the university’s network, the Canadian University is still investigating the breach along with the local police.
Over last weekend, the hacker sent an email to UFV students with the personal information of 29 UVF students and a ransom demand of 30,000 CAD (23,000 USD). The hacker is threatening to release further details if the university will not pay the ransom in 48 hours.
The deadline has passed, but it’s unclear if the University paid the ransom.
The University admitted the security breach and issued four security alerts during the week.
“The students directly affected have been contacted and UFV is working with them to take steps to secure their privacy and personal information,” said a UFV spokesperson.
In response to the data breach, on Wednesday, the UFV shut down its email system announcing that it will be restored on November 6. The measure aims to prevent the spreading of emails containing data of other students.
















