
Tor Project fixed TorMoil, a critical Tor Browser flaw that can leak users IP Address
5.11.2017 securityaffairs Safety
The Tor Project fixed a critical vulnerability dubbed TorMoil that could leak users real IP addresses to potential attackers.
Tor users must update their Tor browser to fix a critical vulnerability, dubbed TorMoil, that could leak their real IP addresses to potential attackers when they visit websites with certain content.
The Tor Project released the Tor Browser 7.0.9 version for both Linux and MacOS, users of both the Windows versions of Tor, Tails and the sandboxed-tor-browser that’s in alpha testing are not affected.
“This release features an important security update to Tor Browser for macOS and Linux users. Due to a Firefox bug in handling file:// URLs it is possible on both systems that users leak their IP address.” reported the security advisory published by the Tor Project.
“Once an affected user navigates to a specially crafted URL the operating system may directly connect to the remote host, bypassing Tor Browser. Tails users and users of our sandboxed-tor-browser are unaffected, though.”

The vulnerability was discovered by the Italian security expert Filippo Cavallarin, CEO at security firm We Are Segment.
The TorMoil flaw resides in FireFox browser for macOS and Linux on which the Tor Browser is based, it could be triggered when users click on links that begin with file:// addresses, instead of the more common https:// and http:// addresses.
“Due to a Firefox bug in handling file:// URLs it is possible on both systems that users leak their IP address. Once an affected user navigates to a specially crafted web page, the operating system may directly connect to the remote host, bypassing Tor Browser” reads the blog post published by We Are Segment.
“If you are one of those people that rely on Tor Browser to safely browse the Internet, the message is just one: keep your Tor Browser updated!”
Cavallarin privately reported the security flaw to Tor development team on October 26, and the developers at the Tor project have rolled out an emergency update Tor version 7.0.8. The new version implements a temporary workaround to prevent the real IP leakage.
macOS and Linux users may found the updated versions of the Tor anonymity browser might not work as expected while navigating to file:// addresses, until the permanent patch becomes available.
“We are currently preparing updated macOS and Linux bundles for our alpha series which will be tentatively available on Monday, November 6. Meanwhile macOS and Linux users on that series are strongly encouraged to use the stable bundles or one of the above mentioned tools that are not affected by the underlying problem.” continues the Tor Project.
“Known issues: The fix we deployed is just a workaround stopping the leak. As a result of that navigating file:// URLs in the browser might not work as expected anymore. In particular entering file:// URLs in the URL bar and clicking on resulting links is broken. Opening those in a new tab or new window does not work either. A workaround for those issues is dragging the link into the URL bar or on a tab instead. We track this follow-up regression in bug 24136.”
The Tor Project also said there’s no evidence the TorMoil flaw has been actively exploited by threat actors in the wild to de-anonymize Tor users.
It is important to highlight that flaws in the Tor browsers are precious commodities, recently the zero-day broker Zerodium offered $1 Million reward for working exploits.
On the other side, the Tor Project continues to improve its software, it has recently announced the release of Tor 0.3.2.1-alpha that includes support for the next generation onion services.
Spam and phishing in Q3 2017
4.11.2017 Kaspersky Spam Analysis
Blockchain and spam
Cryptocurrencies have been a regular theme in the media for several years now. Financial analysts predict a great future for them, various governments are thinking about launching their own currencies, and graphics cards are swept off the shelves as soon as they go on sale. Of course, spammers could not resist the topics of cryptocurrency, mining and blockchain technology.
Last quarter we wrote that many Trojans were downloading ‘miners’ as a payload on victims’ computers, and in third quarter of 2017 this practice became even more widespread.
Fraud, cryptocurrencies and binary options
Financial fraud makes very active use of the cryptocurrency topic: users receive messages that vividly describe the use of special software for trading on the cryptocurrency market and how it can secure their financial future.
Examples of emails with offers “to secure your financial future”
After clicking on a link, users end up on a site where they are once again persuaded to join the ranks of the rich who only have one problem in life – how to spend their money. In reality, such sites are partners for shady brokerage houses, and purveyors of new, inexperienced customers. It is there that new users are redirected.
The plan is to get the victim to deposit a certain amount to their account, usually several hundred dollars, for the opportunity to start trading. We should note here that we’re no longer talking about cryptocurrencies – in most cases, trading involves binary options.
The problem is not even in the questionable legality of the actual trading, but that no one guarantees the honesty of the brokerage offices and, consequently, there are no guarantees that the invested funds will be returned. The fraudsters start by motivating people to invest more and more money, and then simply disappear, leaving the victim to read angry reviews on the Internet from other cheated depositors.
There are also more primitive types of fraud, where the email directly asks the recipient to transfer bitcoins to a specific wallet, with a promise to return the investment with interest five days later. But only the most naïve recipients are likely to fall for such an offer.
Naive users are invited to “invest” bitcoins for a short time at a high high rate of interest
Webcasts
Another example of the cryptocurrency theme being used in spam is that of webcasts. In most cases, scammers suggest taking a study course that will help the user understand more about cryptocurrencies and how to invest in them. Of course, the sums invested in “training” will result in huge profits in the near future, according to the organizers.
Natural disasters and the ‘White House administration’
In August and September, the world’s attention was focused on hurricanes Irma and Harvey, and the earthquake in Mexico. There were dozens of victims of these disasters, and the damage caused was estimated to be billions of dollars. These tragic events inevitably attracted the attention of so-called Nigerian scammers trying to cash in on people’s grief. They sent messages on behalf of family members whose relatives died during the hurricanes and asked for help obtaining an inheritance left by them. Natural disasters were also mentioned in emails promoting job offers and loans.
In the third quarter, ‘Nigerian’ letters also mentioned the name of Donald Trump, the current US president. The authors pretended to be representatives of state or banking organizations, and to make their message sound more important they claimed they were appointed by the US president or were acting on his behalf. The spammers spun the standard tales in their fraudulent letters, promising millions of dollars to users, with the scammers asking for personal information so that they could supposedly track the money transfer. The letters contained identical text but with different layouts and contact details.
Letters ‘from the US president’s office’
B2B fakes in malicious emails
There is still a tendency to create emails with malicious attachments for fake commercial offers. At times their quality is so good that you suspect they could be a man-in-the-middle attack.
The file in the attachment is detected as HEUR: Trojan.Java.Agent.gen. This malware is written to startup and tries to close programs such as Process Hacker, system explorer and security software processes. It then communicates with the remote server and waits for the command to install other malicious programs
The attachment is detected as HEUR: Exploit.MSOffice.Generic, exploiting the vulnerability CVE-2017-0199 in MS Word. As a result, other malicious programs are downloaded to the victim’s computer
Both archives contain the same malicious object, detected as Trojan.Win32.VBKrypt.xtgt. It collects information from the victim’s computer and transfers it to the remote server
Release of new iPhone
In September, Apple unveiled the new models of its smartphone – iPhone 8 and iPhone X. This event was widely covered in the media, and spammers, weren’t going to miss out.
Even before the official presentation, we began to record spam mailings with offers to test the updated phone for free and participate in a prize draw to win one. Some mailings even reported the recipient had won a device before it was publicly unveiled. In most cases, the links in these emails could end up downloading Reimage Repair ‘advertising software’. Immediately after the release of the smartphone, Chinese factories got in on the act, sending out emails advertising various accessories for the new model. Our traps also recorded a large volume of phishing associated with the purchase and delivery of the popular gadget.
Statistics
Proportion of spam in email traffic
Percentage of spam in global email traffic, Q2 and Q3 2017
In the third quarter of 2017, the largest share of spam was recorded in September – 59.56%. The average share of spam in global email traffic was 58.02%, which was almost 1.05 p.p. more than the average for the previous quarter.
Sources of spam by country
Sources of spam by country, Q3 2017
According to the results for the third quarter of 2017, China (12.24%) became the biggest source of spam, after finishing third the previous quarter. Last quarter’s leader Vietnam (11.17%) was second after a decrease of 1.2 p.p. The US fell one place to third (9.62%), while India (8.49%) remained fourth in this rating. Iran rounded off the top 10, accounting for 2.07% of all spam.
Spam email size
Breakdown of spam emails by size, Q2 and Q3 2017
The share of very small emails (up to 2 KB) in spam increased by 9.46 p.p. to 46.87% in the third quarter. The proportion of emails between 5 and 10 KB in size also increased by 6.66 p.p. compared with the previous quarter and amounted to 12.6%.
The number of emails between 10 and 20 KB decreased, however, with their share falling by 7 p.p. There was also a decrease in emails sized 20 to 50 KB. Their share this quarter amounted to 19%, which was a fall of 8.16 p.p. compared to the previous reporting period.
Overall, the number of very small emails continues to grow.
Malicious attachments in email
Top 10 malware families
TOP 10 malware families in Q3 2017
Backdoor.Java.QRat (3.11%) became the most widespread malicious program family in email traffic. Next came the Trojan-Downloader.VBS.Agent family (2.95%), followed by Trojan-Downloader.JS.SLoad (2.94%). The newcomers in this rating – Trojan.Win32.VBKrypt and Trojan-Downloader.VBS.SLoad (a VBS script that downloads and launches other malicious programs on the victim machine, usually cryptographers) occupy fifth and eighth places with 2.64% and 2.02% respectively. The Trojan.PDF.Badur family (1.79%) rounds off the top 10.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, Q3 2017
Germany remained the country targeted most by malicious mailshots in the third quarter of 2017. Its share increased by 6.67 p.p. and amounted to 19.38%.
China came second, with 10.62% of mail antivirus verdicts recorded there – a drop of 1.47 p.p. compared to Q2. Russia, which came fifth the previous quarter, completed the top three (9.97%) after its share increased by 4.3 p.p. Fourth and fifth were occupied by Japan (5.44%) and Italy (3.90%) respectively.
Phishing
In the third quarter of 2017, the anti-phishing system prevented 59,569,508 attempted visits to phishing pages on the computers of Kaspersky Lab users. Overall, 9.49% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q3 2017.
Geography of attacks
The country with the largest percentage of users affected by phishing attacks was once again Brazil (19.95%, +1.86p.p.).
Geography of phishing attacks*, Q3 2017
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in that country
Australia (16.51%) came second after its share increased by 3.81 p.p. In third place was New Zealand (15.61%, + 3.55pp). China (12.66%) fell from second place to fourth, with its share losing 0.19 p.p. Next came France (12.42%), Peru (11.73%), Argentina (11.43%), Canada (11.14%), Qatar (10.51%,) and Georgia (10.34%).
Brazil 19.95%
Australia 16.51%
New Zealand 15.61%
China 12.66%
France 12.42%
Peru 11.73%
Argentina 11.43%
Canada 11.14%
Qatar 10.51%
Georgia 10.34%
TOP 10 countries by percentage of users attacked
Organizations under attack
Rating the categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
In the third quarter of 2017, almost half (47.54%) of the heuristic components of the anti-phishing system were recorded on pages with references to brands from financial categories such as Banks (24.1%, + 0.61 p.p.), Payment systems (13.94%, -4.46 p.p.) and Online stores (9.49%, -0.08 p.p.).
Distribution of organizations affected by phishing attacks by category, Q3 2017
Hot topics this quarter
Airline tickets
Last quarter we described a scam involving a free giveaway of airline tickets supposedly by popular airlines, with information being spread via reposts from victims on a social network. In the third quarter, scammers continued to spread the ‘giveaway’ using WhatsApp instead. Judging by the decrease in the number of anti-phishing verdicts in the Airlines category, however, we can assume that this approach wasn’t as effective.
The downturn may also be due to the fact that scammers switched to ‘prize draws’ not only for air tickets but also other prizes, for example, sports shoes, cinema tickets, gift cards for Starbucks, etc.
Before you could claim your prize you had to share information about the prize draw with eight contacts on WhatsApp.
After clicking the button, users are redirected to WhatsApp.
The redirect function in the instant messenger and the message that has to be sent to contacts
This is what the message looks like in the app
The message needs to be sent a minimum of eight times
After sending the message to their contacts the victim, instead of winning a prize, is redirected to some dubious resource, for example, a page where malicious extensions are installed, a new survey, etc.
WhatsApp
WhatsApp users are also subjected to phishing attacks that hide behind the app brand.
More often than not the scammers try to steal money on the pretext of updating the application or paying for a subscription. At one time WhatsApp really did request a subscription payment, although now it’s free.
Scammers offer a choice of subscription – for one year, three years or five. However, victims will lose much more than the stated amount if they enter their bank card details on such a site.
Netflix
Netflix users are another popular target of phishers. The number of attacks on them increased in the third quarter. The criminals usually coax bank card details from users on the pretext of a failed payment or other problems linked to subscription renewal.
Green Card
On the eve of the Green Card lottery conducted by the US government in October-November of each year, we are seeing a surge in activity by scammers offering help to apply.
After completing the form on the fraudulent site, the user is asked to pay for their application. If the victim enters their bank card details, much more money than the amount indicated on the site can end up being withdrawn from their account.
Rap battle
Even niche events can be good cover for phishing activity. On 15 October, a rap battle was held between Russian artist Oxxxymiron and Dizaster, one of the best battle MCs in the US. This followed another battle that took place just a few months earlier between Oxxxymiron and Slava KPSS. Less than 12 hours later a video of the event had gained around 5 million views – and it wasn’t just thematic sites writing about the battle but also a lot of the mainstream Russian media.
Shortly before the publication of the official video, phishing web pages dedicated to the event began to appear online:
If a user tried to view the video, they were prompted to first sign in to the popular Russian social network VKontakte.
After entering the login and password, the victim was redirected to the official page of the Versus site on the social network, and their personal data went to the scammers.
TOP 3 attacked organizations
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections by Kaspersky Lab’s heuristic anti-phishing component are for phishing pages hiding behind the names of fewer than 15 companies. At the same time, the composition of the top three has remained unchanged for several quarters:
Organization % of detected phishing links
Facebook 7.96
Microsoft Corporation 7.79
Yahoo! 4.79
Conclusion
In terms of the average share of spam in global email traffic (58.02%), the third quarter of 2017 was almost identical to the previous reporting period: once again growth was slightly more than one percentage point – 1.05 (and 1.07 p.p. in Q2 2017). As in previous quarters, spammers were quick to react to high-profile events and adapted their fraudulent emails to the news agenda. This quarter they were quickly to use the theme of natural disasters following hurricanes Irma and Harvey, and the earthquake in Mexico. The popular theme of cryptocurrency was also used: trusting victims were offered seminars and ‘help’ with trading that came with profits guaranteed.
Scammers continued to use all available communication channels to spread phishing content, including social networks and instant messengers: in the current quarter, the anti-phishing component prevented more than 59 million attempts to redirect to phishing pages, which is 13 million more than in Q2.
The most common malware family in the third quarter of 2017 was Backdoor.Java.QRat (3.11%), followed by Trojan-Downloader.VBS.Agent (2.95%), and Trojan-Downloader.JS.SLoad (2.94%).
Hackers poisoned Google Search results to spread Zeus Panda banking Trojan
4.1.2017 securityaffairs Virus
Experts at Cisco Talos observed crooks exploiting black Search Engine Optimization (SEO) to spread the Zeus Panda banking Trojan.
Threat actors behind the Zeus Panda banking Trojan leveraged black Search Engine Optimization (SEO) to propose malicious links in the search results. Crooks were focused on financial-related keyword queries.
The campaign was first spotted by experts at Cisco Talos, attackers used to spread a new version of the Zeus Panda banking Trojan that can steal user’s financial credentials and other sensitive data.
“The initial vector used to initiate this infection process does not appear to be email based. In this particular campaign, the attacker(s) targeted specific sets of search keywords that are likely to be queried by potential targets using search engines such as Google.” reads the analysis published by Cisco. “By leveraging compromised web servers, the attacker was able to ensure that their malicious results would be ranked highly within search engines, thus increasing the likelihood that they would be clicked on by potential victims.”
The researchers reported a specific case in which the crooks’ poisoned results were displayed several times on Page 1 of the Search Engine Results Page (SERP) for the set of keyword targeted by hackers. The attackers used keyword groups specific to financial institutions in India and the Middle East.
Experts from Cisco discovered hundreds of malicious pages specifically designed to redirect victims to the malicious payload, in order to improve the infection process the hackers implemented a multiple stage attack.
Cisco Talos reported that the same redirection system and associated infrastructure has been used in tech support and fake AV scams aimed at the distribution of Zeus Trojan.
The query results point malicious webpages including JavaScript used by crooks to redirect users to an intermediary site where more JavaScript is executed, which results in an HTTP GET request to another page. Following server’s response, the victim is redirected to another compromised site hosting a malicious Word document.

The Word document includes malicious macros that once enabled download and execute a PE32 executable that infects the victim’s machine with the Zeus Panda banking Trojan.
“The payload that Talos analyzed was a multi-stage payload, with the initial stage featuring several anti-analysis techniques designed to make analysis more difficult and prolonged execution to avoid detection. It also featured several evasion techniques designed to ensure that the malware would not execute properly in automated analysis environments, or sandboxes.” continues Cisco Talos.
The malware checks the system language and halts if it detects Russian, Belarusian, Kazak, or Ukrainian keyboard layouts. It also checks if its code is executed in sandbox environments.
The experts observed that the malware makes a large number of exception calls to cause sandboxes to crash preventing automated analysis.
“Attackers are constantly trying to find new ways to entice users to run malware that can be used to infect the victim’s computer with various payloads. Talos uncovered an entire framework that is using ‘SERP poisoning’ to target unsuspecting users and distribute the Zeus Panda banking Trojan. In this case, the attackers are taking specific keyword searches and ensuring that their malicious results are displayed high in the results returned by search engines,” Cisco concluded.
US DoJ Identifies at least 6 Russian Government officials Involved in DNC hack
4.1.2017 securityaffairs BigBrothers
The United States Department of Justice has gathered evidence to charge at least six Russian government officials involved in the 2016 DNC hack.
The United States Department of Justice has gathered evidence to charge at least six Russian government officials involved in the DNC hack during the 2016 Presidential election.
In the past months, US intelligence blamed Russia for cyberattacks aimed at influencing the 2016 Presidential Election in Donald Trump’s favour.
An FBI-DHS JAR report released in December 2016 implicated Russian hacking group APT28 and APT29 in attacks against 2016 Presidential Election.
Security experts from Mandiant who analyzed the cyber attacks also linked the hack to a cyber espionage campaign associated with the APT28 group.
Now, the Wall Street Journal reported that United States federal prosecutors could bring charges against the alleged unnamed Russian officials early next year.
“The Justice Department has identified more than six members of the Russian government involved in hacking the Democratic National Committee’s computers and swiping sensitive information that became public during the 2016 presidential election, according to people familiar with the investigation.” wrote the Wall Street Journal.
The identities of the six suspects are yet to be revealed.
The US federal intelligence investigators believe that Russian Government conducted a larger campaign that involved “dozens” of other Russian officials in the DNC hack and subsequent data leak.
The acted obeying a direct order of the Russian President Vladimir Putin, that always denied allegations.
The hackers who breached the DNC computer system in 2016 leaked thousands of stolen DNC emails, including personal and sensitive emails from Hillary Clinton campaign manager John Podesta.
The sensitive information was published by the WikiLeaks website.
This is the second time in 2017 when the US Government has charged Russian officials with hacking crimes, in March 2017, the US authorities charged two former Russian FSB agents and two hackers for 2014 Yahoo data breach that caused the exposure of 500 Million Yahoo Accounts.
Advantech Patches Code Execution Flaws in SCADA Product
4.11.2017 securityweek Vulnerebility
An update released by Taiwan-based industrial automation company Advantech for its WebAccess product patches two remote code execution vulnerabilities, ICS-CERT reported on Thursday.
Advantech WebAccess is a browser-based software package for human-machine interfaces (HMI) and supervisory control and data acquisition (SCADA) systems.
According to ICS-CERT, WebAccess versions prior to 8.2_20170817 are affected by a stack-based buffer overflow (CVE-2017-14016) and an untrusted pointer dereference issue (CVE-2017-12719).
“The application lacks proper validation of the length of user-supplied data prior to copying it to a stack-based buffer, which could allow an attacker to execute arbitrary code under the context of the process,” ICS-CERT described the buffer overflow, which has been classified as medium severity.
As for the second flaw, which has been rated high severity, the organization warned that “a remote attacker is able to execute code to dereference a pointer within the program causing the application to become unavailable.”
The vulnerabilities were reported to the vendor by Steven Seeley of Offensive Security through Trend Micro’s Zero Day Initiative (ZDI).
ZDI has yet to make public the advisories describing these vulnerabilities. However, these are not the only Advantech flaws that the company will disclose in the upcoming period – its “Upcoming Advisories” section lists more than 70 vulnerabilities, including ones rated critical. A majority of them were reported by Seeley.
ZDI plans on disclosing many of the security holes in late November and early December. A report published by the company in May showed that it takes Advantech, on average, 131 days to patch vulnerabilities, which exceeds ZDI’s 4-month disclosure deadline.
Researchers have discovered a significant number of flaws in the company’s WebAccess product in the past years. Just a few months ago, ICS-CERT revealed that a total of ten weaknesses, including ones that allowed remote code execution and unauthorized access, had been resolved by the vendor.
While Advantech has addressed many of the vulnerabilities found by researchers, there have been cases where the company failed to release fixes before public disclosure, the patches were not complete, and even issued patches that introduced new flaws.
New York State Proposes Stricter Data Protection Laws Post Equifax
4.11.2017 securityweek Cyber
New York State Attorney General Eric T. Schneiderman introduced new legislation Thursday, designed to protect New Yorkers from corporate data breaches like the recent Equifax breach that affected more than 145 million Americans, including 8 million New York residents. Its purpose is to increase the security of private information in a business-friendly manner.
Called the Stop Hacks and Improve Electronic Data Security Act (SHIELD Act), it was introduced by Schneiderman as a program bill, and is sponsored by Senator David Carlucci and Assemblymember Brian Kavanagh. "It's clear that New York's data security laws are weak and outdated. The SHIELD Act would help ensure these hacks never happen in the first place. It's time for Albany to act, so that no more New Yorkers are needlessly victimized by weak data security measures and criminal hackers who are constantly on the prowl," said Schneiderman.
It is worth noting that Schneiderman's SHIELD Act is not the same as Senator Markey's proposed Cyber Shield Act. A draft (PDF) of Markey's bill coincidentally became available last week. While Markey's proposal is to bake security into IoT devices, Schneiderman's proposal is to bring security to businesses by through reasonable security safeguards with new controls over breach disclosure backed by financial sanctions.
Under current New York law, companies can compile personally identifiable information (PII), but are not required to meet any data security requirements if that PII does not include a social security number -- for example, the current law does not require companies to report data breaches of username-and-password combinations, or biometric data like the fingerprint used to unlock an iPhone. The changes will be achieved through amendments to the existing General Business Law and the State Technology Law.
The SHIELD Act requires businesses to adopt "reasonable" administrative, technical, and physical safeguards for sensitive data. Its scope covers any business that holds New Yorkers' sensitive data rather than simply conducts business within New York. It expands the types of data that trigger reporting requirements, to include username-and-password combinations, biometric data, and HIPAA-covered health data.
Penalties for violation are increased. It allows the attorney general to seek civil penalties and injunctions if businesses do not provide adequate security for PII. This could be $5,000 for each violation, or up to $20 for each instance of failed notification (up to a total of $250,000).
The attempt by Schneiderman is to protect New Yorkers' personal data just as the European General Data Protection Regulation (GDPR) seeks to protect European's personal information. Schneiderman, however, tries to be more business-friendly. Firstly, the penalties are much lower. Secondly, the required breach disclosure timeline is more flexible. "The disclosure shall be made in the most expedient time possible and without unreasonable delay, consistent with the legitimate needs of law enforcement..."
Thirdly, there is an explicit encryption exemption. PII is only classified as PII "when either the personal information or the data element is not encrypted or encrypted with an encryption key that has also been ACCESSED OR acquired."
Fourthly, it provides a safe harbor against attorney general enforcement for companies already compliant with the NYS DFS, Gramm-Leach-Bliley, and HIPAA regulations; and those with independent certification of compliance with ISO and NIST standards. And fifthly, it provides a flexible approach for small businesses provided they "implement and maintain reasonable safeguards that are appropriate to the size and complexity of the small business."
David Zetoony, the leader of Bryan Cave's consumer protection practice, commented, "Providing a safe harbor for companies that go above-and-beyond to certify good data security is innovative, unique, and friendly to business. It rewards businesses that go the extra mile to audit and verify compliance with an industry data security practice, removing the costs and unpredictability of government litigation. It also does not penalize smaller businesses that have good security practices, but cannot afford the significant cost of annual data security audits and certifications. This is the type of thought leadership needed to improve data security legislation across the country."
Despite these exemptions and flexibility, the Shield Act will enforce stronger personal data protection than has so far been required outside of the regulated New York financial institutions. The definition of a data breach is broadened to include an unauthorized person gaining access to information, while the reach of the law has been widened from companies that do business in New York to companies that hold personal information of New Yorkers.
"While the federal government drags their feet we must act to protect New Yorkers. The SHIELD Act will serve as a blueprint for NY and the rest of the nation to follow to keep Americans safe," said co-sponsor Senator David Carlucci.
Poisoned Google Search Results Lead to Banking Trojan
4.11.2017 securityweek Virus
A recently observed Zeus Panda banking Trojan attack used poisoned Google search results for specific banking related keywords to infect users, Cisco Talos researchers warn.
As part of this attack, the actor behind Zeus Panda used Search Engine Optimization (SEO) to make their malicious links more prevalent in the search results. By targeting financial-related keyword searches, the actor attempted to increase the efficiency of the attack through ensuring that the infected users are regularly using financial platforms.
“By leveraging compromised web servers, the attacker was able to ensure that their malicious results would be ranked highly within search engines, thus increasing the likelihood that they would be clicked on by potential victims,” Cisco reveals.
In one specific case, the actor’s poisoned results were displayed several times on Page 1 of the Search Engine Results Page (SERP) for the targeted keyword, the researchers discovered. The attack was mainly aimed at keyword groups specific to financial institutions in India and the Middle East.
Cisco was able to identify hundreds of malicious pages that redirected victims to the malicious payload and says that the infection process included multiple stages. Moreover, the researchers observed the same redirection system and associated infrastructure being used in tech support and fake AV scams that attempted to trick victims into believing they have been infected with Zeus.
The malicious webpages use JavaScript to redirect users to an intermediary site where more JavaScript is executed, which results in an HTTP GET request to another page. Following server’s response, the victim is sent to another compromised site where a malicious Word document is hosted.
The victim is prompted to download the document, which includes malicious macros the user is lured to run. The malicious macro code is basic, but obfuscated. It was designed to download and execute a PE32 executable that results in the system being infected.
The payload is a new version of the Zeus Panda banking Trojan that can steal user’s financial credentials and other sensitive data. The payload used in this attack was multi-stage, featuring a variety of anti-analysis and evasion techniques ensuring the malware won’t execute properly in automated analysis environments, or sandboxes.
The threat first queries the system's keyboard mapping to determine the system language and terminates itself if it detects Russian, Belarusian, Kazak, or Ukrainian keyboard layouts. It also checks if it runs in a series of sandbox environments, including VMware, VirtualPC, VirtualBox, Parallels, Sandboxie, Wine, and SoftIce. Next, it checks for tools and utilities typically used for analysis purposes.
“In an attempt to hinder analysis, the initial stage of the malicious payload features hundreds of valid API calls that are invoked with invalid parameters. It also leverages Structured Exception Handling (SEH) to patch its own code. It queries and stores the current cursor position several times to detect activity and identify if it is being executed in a sandbox or automated analysis environment,” Cisco reveals.
The malware performs a variety of other operations as well, in an attempt to make analysis significantly more difficult. For example, they create hundreds of case comparisons, thus hindering code tracing. The researchers also noticed the use of a high number of exception calls to cause sandboxes to crash, thus preventing automated analysis.
“Attackers are constantly trying to find new ways to entice users to run malware that can be used to infect the victim's computer with various payloads. Talos uncovered an entire framework that is using ‘SERP poisoning’ to target unsuspecting users and distribute the Zeus Panda banking Trojan. In this case, the attackers are taking specific keyword searches and ensuring that their malicious results are displayed high in the results returned by search engines,” Cisco notes.
Equifax Says Execs Unaware of Hack When They Sold Stock
4.11.2017 securityweek Hacking
Equifax said Friday an internal review found that four executives who sold shares ahead of disclosure of a massive data breach at the credit agency were unaware of the incident ahead of the sale.
The company released the findings of its review of the stock sales worth some $1.8 million just prior to public disclosure of the hack affecting sensitive data of some 145 million as well as some British and Canadian nationals.
The "special committee" investigating for the company concluded that "none of the four executives had knowledge of the incident" and that none engaged in insider trading.
The committee reviewed more than 55,000 documents including emails, text messages, phone logs and other records, according to a company statement.
"I'm grateful for the timely and thorough review," non-executive chairman Mark Feidler said in the statement.
"It is critically important for the public, our shareholders, our customers and our employees to know that we will not tolerate any violation of company policy or the law regarding the trading of securities."
The data breach -- potentially one of the worst in history because of the sensitivity of the data that was leaked -- remains the subject of investigations by US authorities and congressional committees.
Equifax, which gathers data on consumers for credit inquiries, has blamed a combination of human and technical error for the massive breach.
The breach led to the retirement of Equifax chief executive Richard Smith, who has remained as a consultant to the company during the investigation.
New York State Proposes Stricter Data Protection Laws Post Equifax
3.11.2017 securityweek BigBrothers
New York State Attorney General Eric T. Schneiderman introduced new legislation Thursday, designed to protect New Yorkers from corporate data breaches like the recent Equifax breach that affected more than 145 million Americans, including 8 million New York residents. Its purpose is to increase the security of private information in a business-friendly manner.
Called the Stop Hacks and Improve Electronic Data Security Act (SHIELD Act), it was introduced by Schneiderman as a program bill, and is sponsored by Senator David Carlucci and Assemblymember Brian Kavanagh. "It's clear that New York's data security laws are weak and outdated. The SHIELD Act would help ensure these hacks never happen in the first place. It's time for Albany to act, so that no more New Yorkers are needlessly victimized by weak data security measures and criminal hackers who are constantly on the prowl," said Schneiderman.
It is worth noting that Schneiderman's SHIELD Act is not the same as Senator Markey's proposed Cyber Shield Act. A draft (PDF) of Markey's bill coincidentally became available last week. While Markey's proposal is to bake security into IoT devices, Schneiderman's proposal is to bring security to businesses by through reasonable security safeguards with new controls over breach disclosure backed by financial sanctions.
Under current New York law, companies can compile personally identifiable information (PII), but are not required to meet any data security requirements if that PII does not include a social security number -- for example, the current law does not require companies to report data breaches of username-and-password combinations, or biometric data like the fingerprint used to unlock an iPhone. The changes will be achieved through amendments to the existing General Business Law and the State Technology Law.
The SHIELD Act requires businesses to adopt "reasonable" administrative, technical, and physical safeguards for sensitive data. Its scope covers any business that holds New Yorkers' sensitive data rather than simply conducts business within New York. It expands the types of data that trigger reporting requirements, to include username-and-password combinations, biometric data, and HIPAA-covered health data.
Penalties for violation are increased. It allows the attorney general to seek civil penalties and injunctions if businesses do not provide adequate security for PII. This could be $5,000 for each violation, or up to $20 for each instance of failed notification (up to a total of $250,000).
The attempt by Schneiderman is to protect New Yorkers' personal data just as the European General Data Protection Regulation (GDPR) seeks to protect European's personal information. Schneiderman, however, tries to be more business-friendly. Firstly, the penalties are much lower. Secondly, the required breach disclosure timeline is more flexible. "The disclosure shall be made in the most expedient time possible and without unreasonable delay, consistent with the legitimate needs of law enforcement..."
Thirdly, there is an explicit encryption exemption. PII is only classified as PII "when either the personal information or the data element is not encrypted or encrypted with an encryption key that has also been ACCESSED OR acquired."
Fourthly, it provides a safe harbor against attorney general enforcement for companies already compliant with the NYS DFS, Gramm-Leach-Bliley, and HIPAA regulations; and those with independent certification of compliance with ISO and NIST standards. And fifthly, it provides a flexible approach for small businesses provided they "implement and maintain reasonable safeguards that are appropriate to the size and complexity of the small business."
David Zetoony, the leader of Bryan Cave's consumer protection practice, commented, "Providing a safe harbor for companies that go above-and-beyond to certify good data security is innovative, unique, and friendly to business. It rewards businesses that go the extra mile to audit and verify compliance with an industry data security practice, removing the costs and unpredictability of government litigation. It also does not penalize smaller businesses that have good security practices, but cannot afford the significant cost of annual data security audits and certifications. This is the type of thought leadership needed to improve data security legislation across the country."
Despite these exemptions and flexibility, the Shield Act will enforce stronger personal data protection than has so far been required outside of the regulated New York financial institutions. The definition of a data breach is broadened to include an unauthorized person gaining access to information, while the reach of the law has been widened from companies that do business in New York to companies that hold personal information of New Yorkers.
"While the federal government drags their feet we must act to protect New Yorkers. The SHIELD Act will serve as a blueprint for NY and the rest of the nation to follow to keep Americans safe," said co-sponsor Senator David Carlucci.
US Identifies 6 Russian Government Officials Involved In DNC Hack
3.11.2017 thehackernews BigBrothers
The United States Department of Justice has reportedly gathered enough evidence to charge at least six Russian government officials for allegedly playing a role in hacking DNC systems and leaking information during the 2016 presidential race.
Earlier this year, US intelligence agencies concluded that the Russian government was behind the hack and expose of the Democratic National Committee (DNC) emails in order to influence the 2016 presidential election in Donald Trump's favour.
Now, citing people familiar with the investigation, the Wall Street Journal reported on Thursday that United States federal prosecutors could bring charges against the alleged unnamed Russian officials early next year.
The US federal intelligence investigators also believe that "dozens" of other Russian officials may have also participated in the DNC hack, which was allegedly ordered by Russian President Vladimir Putin himself.
However, both Putin and Russian government officials have denied allegations.
The DNC computer system hack last year led to thousands of stolen DNC emails, including personal and sensitive emails from Hillary Clinton campaign manager John Podesta, appeared on whistleblowing website WikiLeaks.
In a separate forensic investigation conducted by FireEye incident response firm Mandiant identified hacking tools and techniques used in the DNC hack associated with Fancy Bear—also known as APT28, Sofacy, Sednit, and Pawn Storm—a state-sponsored hacking group believed to be a unit of Russian Military Intelligence (the GRU).
U.S. federal agents and prosecutors in Washington, Pittsburgh, Philadelphia and San Francisco have been cooperating with the DNC investigation. However, none of them has revealed the actual identity of the six suspects.
However, even after getting charged, the Russian officials or hackers will hardly be prosecuted in the United States until they enter the US soil because the country has no extradition agreement with Russia.
This is the second time in this year when the United States has charged Russian officials with cyber crimes.
In March 2017, the DoJ charged two Russian intelligence officers—Dmitry Aleksandrovich Dokuchaev and Igor Anatolyevich Sushchin—and two criminal hackers—Alexsey Alexseyevich Belan and Karim Baratov—in connection with the 2014 Yahoo hack that exposed about 500 million Yahoo user accounts.
However, no one has ever seen the insides of a United States courtroom.
Estonia suspends security digital certificates for up to 760,000 state-issued electronic ID-cards over Identity-Theft risk
3.11.2017 securityaffairs BigBrothers
It has happened, one of the most cyber-savvy states, Estonia decided to block Electronic ID Cards over identity theft risk.
On Thursday, Estonia announced that it would suspend security digital certificates for up to 760,000 state-issued electronic ID-cards that are using the buggy chips to mitigate the risk of identity theft.
The decision comes after IT security researchers recently discovered a vulnerability in the chips used in the cards manufactured by the Swiss company Trub AG that open the doors to malware-based attacks.
The Prime Minister Juri Ratas announced the decision to suspend security certificates for cards until their owners download an update to patch the flaw.
“The functioning of an e-state is based on trust and the state cannot afford identity theft happening to the owner of an Estonian ID card,” explained Prime Minister Juri Ratas on Thursday.
“By blocking the certificates of the ID cards at risk, the state is ensuring the safety of the ID card,”
“As far as we currently know, there has been no instances of e-identity theft, but the threat assessment of the Police and Border Guard Board and the Information System Authority indicates that this threat has become real,”
In September, the Gemalto-owned announced they were helping the Estonian government on solving the problem.
Since October 31, all users having faulty ID cards can update their security certificates remotely and at Estonian police and border guard service points.
As of Thursday night, around 40,000 users had already updated their certificates.

Estonia is considered the most technological European Country, it tested e-voting since 2005, for this reason, it is called E-stonia
Estonia has already issued 1.3 million electronic ID cards offering citizens online access to a huge number of services through the “e-government” state portal. The Estonian electronic ID cards have been manufactured by the Swiss company Trub AG and its successor Gemalto AG since 2001.
According to the Government experts, other cards based on the same faulty chips are exposed to the same cyber risk.
Russia-Linked Hackers Target Turkish Critical Infrastructure
3.11.2017 securityweek BigBrothers
A Russia-linked threat group has been targeting people associated with Turkish critical infrastructure through compromised Turkish sites, according to threat management firm RiskIQ.
Called Energetic Bear, but also known as Dragonfly and Crouching Yeti, the group has been active since at least 2010. First detailed in 2014, the threat group has been focused mainly on the energy sector in the United States and Europe.
In July, Cisco revealed that the group has used template injection in attacks aimed at energy facilities and other critical infrastructure organizations in the United States. At least a dozen power firms in the country were hit in these attacks, including the Wolf Creek nuclear facility in Kansas.
In late October, the Department of Homeland Security and Federal Bureau of Investigation issued a joint alert to warn of an attack campaign associated with the group that has been ongoing since at least May 2017. The attacks target entities and organizations in the energy, nuclear, water, aviation, and critical manufacturing sectors.
RiskIQ now reveals that the group leveraged a supply chain attack to compromise a website belonging to a Turkish energy company and later used the site as a watering hole attack targeting people associated with Turkish critical infrastructure.
The group injected the site with SMB credential-harvesting malware and the security researchers managed to link the infrastructure to related Turkish sites that were compromised for the same purpose.
To set up their attacks, Energetic Bear compromises websites that give them exposure to specific targets, RiskIQ explains. They used the same technique for the website of Turcas Petrol, a Turkish energy company, located at turcas.com.tr.
The URL of an image the group included on the website “redirects to a link using the file:// scheme, which forces the connection through the file protocol, which then allows the group to harvest Microsoft SMB credentials,” the RiskIQ's researchers explained. The compromise appears targeted at Turcas Petrol and those close with the business, which is a tactic typically employed by Energetic Bear.
According to RiskIQ, the SMB credential harvesting host is not always directly included on the websites, but an intermediary host is typically used to redirect visitors to SMB harvesting (possibly after some filtering is done).
“Additionally, the URL format of the file requested, which in this case was turcas_icon.png, is not related to the referring website. Instead, Energetic Bear seems to use a form of tagging to correlate any possible victims and their source website. The format we observed is <tag>_icon.png and <tag>.png,” the RiskIQ team says.
RiskIQ discovered that the threat group has compromised ‘general purpose’ websites too, such as plantengineering.com, which serves as an information and news hub for the critical infrastructure sector and which is owned by CFE Media LLC. Two other sites registered with the same email address were also compromised, namely controleng.com and csemag.com.
The security researchers believe that CFE Media’s other websites were affected as well, “because they’re geared toward engineers working in the critical infrastructure sector and thus prime targets for this watering hole attack.” They also note that the compromise campaign likely started between beginning of February and the end of March.
Savitech Audio Drivers Caught Installing Root Certificate
3.11.2017 securityweek Vulnerebility
Savitech drivers used by several companies that provide specialized audio products expose computers to hacker attacks by installing a new root certificate into the Trusted Root Certification Authorities store in Windows.
The USB audio drivers from Savitech, a company that offers application-specific integrated circuits for audio and video solutions, are used by several vendors. The CERT Coordination Center lists products from Accuphase, AsusTek, Audio-Technica, Creek Audio, EMC, FiiO Electronics, HiFime, Intos, JDS Labs, McIntosh Laboratory, ShenZhen YuLong Audio, Stoner Acoustics, Sybasonic, and TeraDak Audio as possibly being affected.
Savitech used the “SaviAudio” root certificate as part of its effort to support the outdated Windows XP operating system, but the certificate is no longer installed by the latest version of the drivers released by the company.
According to RSA’s Kent Backman, the researcher who discovered the flaw, self-signed root certificates were silently installed by the packages provided by Savitech between 2013 and 2017.
Installing such a certificate allows hackers who are in possession of the Savitech private key to impersonate online services, sign malicious software, and decrypt network traffic via man-in-the-middle (MitM) attacks.
While this worst case scenario sounds serious, in reality, the risk of an attack is low as, hopefully, Savitech has taken steps to ensure that the private key cannot be obtained easily by malicious actors. CERT/CC noted that there is no evidence of the key being compromised.
The vulnerability, tracked as CVE-2017-9758 and dubbed by RSA “Inaudible Subversion,” was introduced by Savitech in an attempt to seamlessly support Windows XP, which Microsoft abandoned several years ago.
While users still running Windows XP are exposed to attacks due to much more serious vulnerabilities left unpatched in the operating system, the audio drivers install the root certificate on newer versions of Windows as well, despite not being needed.
“In the big picture of things, we think that Inaudible Subversion may be a vulnerability of low--if any--consequence, but illustrates the influence of market forces behind hardware vendor sustainment of a still-popular operating system that is no longer supported by Microsoft,” Backman said in a blog post.
Version 2.8.0.3 or later of the Savitech drivers no longer install the root certificate, but they do not remove the existing certificate. Users have been advised to manually remove previously installed certificates.
The root certificate installed by the audio drivers was configured to trust any certificate issued by the SaviAudio CA for “All” purposes. This is typical of certificates issued by Microsoft itself or certificates used by security products for SSL traffic inspection. While the use of root certificates for traffic inspection by security products is considered acceptable, tests have shown that some implementations actually weaken HTTPS security. On the other hand, root certificates installed by any other software pose serious security and privacy risks.
Russian 'Fancy Bear' Hackers Abuse Blogspot for Phishing
3.11.2017 securityweek BigBrothers
The cyber espionage group known as Fancy Bear, which is widely believed to be backed by the Russian government, has been abusing Google’s Blogspot service in recent phishing attacks.
Threat intelligence firm ThreatConnect spotted the use of the blogging service while analyzing attacks aimed at Bellingcat, a group of investigative journalists that uses open source information to report on various events taking place around the world.
Fancy Bear, also known as Pawn Storm, APT28, Sofacy, Sednit, Strontium and Tsar Team, was first seen targeting Bellingcat in 2015 as part of a campaign aimed at entities investigating Russia’s involvement in the downing of Malaysia Airlines flight MH17 in July 2014 as it was crossing a conflict zone in Ukraine.
The latest attacks aimed at Bellingcat involved fake emails instructing users to change their Gmail passwords as a result of unauthorized activity on their account, and Dropbox invitations to view shared folders.
The buttons included in these emails pointed to a randomly generated Blogspot subdomain set up to redirect visitors to a phishing page. The phishing sites used HTTPS and they were hosted on subdomains that may have tricked many individuals into thinking they were legitimate. Experts believe the attackers likely used Blogspot in an effort to get past spam filters.
“A URL hosted on Google's own systems, in this case Blogspot, may be more likely to get past spam filters than URLs hosted on a third party IP address or hostname,” ThreatConnect researchers said in a blog post.
Fancy Bear is believed to be behind many high profile attacks, including a campaign that may have attempted to interfere in last year’s presidential election in the United States.
Researchers at SecureWorks reported last year that they had identified thousands of Gmail accounts targeted by the hackers. The security firm recently provided the entire list of accounts to The Associated Press, whose reporters have analyzed them in an effort to find who they belong to.
They identified the email addresses of entities in 116 countries, including former U.S. Secretaries of State John Kerry and Colin Powell, NATO Supreme Commanders Air Force Gen. Philip Breedlove and Army Gen. Wesley Clark, defense contractors such as Raytheon and Lockheed Martin, U.S. politicians and intelligence officials, Ukrainian officials and the pope’s representative in Kiev, and Russian opponents of the Kremlin.
FireEye announced the arrest of LeakTheAnalyst, the hacker who claimed to have breached its systems
3.11.2017 securityaffairs CyberCrime
FireEye CEO Kevin Mandia announced the arrest of LeakTheAnalyst, the hacker who claimed to have breached its systems back in July.
Late July a hacker who goes online with the moniker LeakTheAnalyst claimed to have breached FireEye systems. The hacker leaked details alleged stolen from a compromised system maintained by Adi Peretz, a Senior Analyst at Mandiant.
The hacker leaked a 337MB PST file containing the expert’s emails and also images of its accounts, including One Drive, Live, LinkedIn, geo-tracking of personal devices for at least a year, billing records and PayPal receipts.
At that time, the hacker claimed to have launched the #LeakTheAnalyst operation that aimed at doxing the security analysts who hunt hackers.
“Let’s trash their reputation in the field,” the hacker said. “It was fun to be inside a giant company named “Mandiant” we enjoyed watching how they try to protect their clients and how their dumb analysts are trying to reverse engineer malware and stuff.”
“This leak was just a glimpse of how deep we breached into Mandiant, we might publish more critical data in the future.”

FireEye denied any intrusion in its systems, according to the security firm, the hackers did not hack the company network or the Adi Peretz’s personal or corporate computers.
The login credentials used by Peretz were exposed in the past in numerous data breaches, including LinkedIn.
The experts discovered that the attackers started using the stolen credentials to access several of the Victim’s personal online accounts (LinkedIn, Hotmail and OneDrive accounts) in September 2016.
The documents publicly released were obtained from the victim’s personal online accounts and many of them were already available online.
On Thursday, the alleged hacker has been arrested and taken into custody by international police. The news was confirmed by FireEye CEO Kevin Mandia at the company’s Q3 Earnings Results Conference Call on Wednesday.
The name of the hacker arrested by law enforcement has not yet been disclosed or the place of the arrest.
“These attackers rarely, if ever get caught…Over my career, I have found it frustrating how little risk or repercussions exist for the attackers, who hide behind the anonymity of the internet to cause harm to good, well-intentioned people,” Mandia said.
“Therefore, I am pleased that, in this case, we were able to impose repercussions for the attacker and achieve a small victory for the good guys.”
Mandia explained that his company had to sink a “tremendous amount of its time and effort into investigating the hacker’s claims.”
Threat actors using default SSH credentials to hijack Ethereum miners
3.11.2017 securityaffairs CyberCrime
Attackers scanned for the entire IPv4 range and look for Ethereum miners with open SSH connections.
Hackers target Ethereum-mining farms in the attempt to hijack the funds by replacing the user’s wallet with their one.
The attacks were first spotted on Monday, threat actors attempted to change the default configuration of Ethereum miners.
“Illicit digital currency mining, either directly in the browser or via maliciously-delivered miners, is nothing new, but our honeypot systems have started flagging a different type of attack against Ethereum-mining farms.” wrote Bitdefender threat analyst Bogdan Botezatu.
“We detected the first attacks on Monday, when our SSH honeypots prompted us about a bot attempting to change the system configuration to hijack funds from Ethereum-mining operations.”
The attackers are specifically targeting EthOS, the operating system optimized for mining cryptocurrencies, including Ethereum, Zcash, and Monero. The operating system currently runs on more than 38,000 mining rigs across the world. It comes pre-loaded with the necessary tools, and a default username and password, the only effort requested to the user during the installation is the set up of a wallet address used as a recipient for mining fees and the change of default credentials.

The attacks were detected by a honeypot set up by Bitdefender, attackers scanned for the entire IPv4 range and look for Ethereum miners with open SSH connections.
“The bot scans for the entire IPv4 range and looks for open SSH connections. If found, it attempts to log in using the default username and password to the EthOS operating system: ethos:live and root:live,” explained Botezatu.
If the login succeeds, the attackers try to change the Ethereum wallet to hijack the mining process to the attacker’s Ethereum address. In the attacks observed by the researchers, threat actors used the wallet “0xb4ada014279d9049707e9A51F022313290Ca1276” that received 10 transactions over the past days worth a total of $611 in Ether.
“So, if you are running an Ether Miner based on Ethereum OS, make sure you have changed the default login credentials. If you haven’t done so, now would be a good time to check whether the miner is sending money to you, not hackers,” concluded Botezatu.
Estonia Blocks Electronic ID Cards Over Identity-Theft Risk
3.11.2017 securityweek BigBrothers
Cyber-savvy Estonia said on Thursday it would suspend security certificates for up to 760,000 state-issued electronic ID-cards with faulty chips as of Friday midnight to mitigate the risk of identity theft.
Dubbed E-stonia for being one of the world's most wired nations, the Baltic eurozone state of 1.3 million people issues electronic ID cards giving citizens online access to virtually all public services at a special "e-government" state portal.
IT security experts recently discovered a flaw in the Swiss-made chips used in the cards that makes them vulnerable to malware.
"The functioning of an e-state is based on trust and the state cannot afford identity theft happening to the owner of an Estonian ID card," Prime Minister Juri Ratas said Thursday as he announced the decision to suspend security certificates for cards until their owners download an update to patch the flaw.
"By blocking the certificates of the ID cards at risk, the state is ensuring the safety of the ID card," Ratas said.
"As far as we currently know, there has been no instances of e-identity theft, but the threat assessment of the Police and Border Guard Board and the Information System Authority indicates that this threat has become real," he added.
Estonia has made a name for itself for being a trailblazer in technology, notably pioneered e-voting in 2005 and playing host to NATO's cyber defence centre.
Estonian authorities also warned that other cards and computer systems using the chips produced by the same manufacturer were also at risk.
Since 2001 Estonian electronic ID cards have been manufactured by the Swiss company Trub AG and its successor Gemalto AG.
In September, Trub Baltic AS that belongs to the Gemalto group, announced they were cooperating with the Estonian government on solving the problem.
As of October 31, all users of faulty ID cards can update their security certificates remotely and at Estonian police and border guard service points.
As of Thursday night around 40,000 users had already done so.
'LeakTheAnalyst' Hacker Who Claimed to Have Hacked FireEye Arrested
2.11.2017 thehackernews CyberCrime
Remember the hacker who claimed to have breached FireEye late July this year?
That alleged hacker has been arrested and taken into custody Thursday by international law enforcement, FireEye CEO Kevin Mandia informed the media.
Late July, the hacker, whose name has not yet been disclosed, managed to hack the personal online accounts of a Senior Threat Intelligence Analyst at Mandiant—a Virginia-based cybersecurity firm owned by the FireEye—and leaked nearly 32 megabytes of data belonging to Peretz.
At that time, the hacker claimed that he had started #LeakTheAnalyst operation that aimed at doxing the security analysts who hunt hackers. The hacker also claimed to have had complete access to the company's internal networks since 2016.
"Let's trash their reputation in the field," the hacker said. "It was fun to be inside a giant company named “Mandiant” we enjoyed watching how they try to protect their clients and how their dumb analysts are trying to reverse engineer malware and stuff."
"This leak was just a glimpse of how deep we breached into Mandiant, we might publish more critical data in the future."
Later in August, FireEye announced that it found no evidence the company's corporate network were compromised, saying the attacker merely managed to compromise social media accounts of just one of its employees.
The attacker did so by re-using credentials for the employee's social media and email accounts that were previously exposed in publicly-disclosed third-party data breach.
FireEye CEO announced the hacker's arrest at the company's Q3 Earnings Results Conference Call on Wednesday.
"These attackers rarely, if ever get caught...Over my career, I have found it frustrating how little risk or repercussions exist for the attackers, who hide behind the anonymity of the internet to cause harm to good, well-intentioned people," Mandia said.
"Therefore, I am pleased that, in this case, we were able to impose repercussions for the attacker and achieve a small victory for the good guys."
Mandia also told CRN that FireEye had to spend a "tremendous" amount of its time and effort into investigating the hacker's July claims, which costs the company a lot, both in efforts and money.
So far, neither the law enforcement officials nor FireEye have reveal the real name of the hacker and the location from where he was arrested.
SSH-based Hijacker Targeting Ethereum Miners
2.11.2017 securityweek Hacking
Crypto-currency miners represent an easy solution when it comes to taking advantage of a system’s computing power to earn some money, but can result in no gain if the mined coins are going to someone else’s wallet.
In a recent example of how users could end up with no cash despite putting their computers to work, Ethereum-mining farms are at the receiving end of an attack involving a hijacker that simply attempts to replace the user’s wallet with an unknown actor’s.
The attack takes advantage of the increased popularity emerging crypto-currencies such as Monero and Ethereum have seen lately. First spotted on Monday, the attack relies on changing the default configuration of Ethereum-miners to hijack the funds, Bitdefender’s threat analyst Bogdan Botezatu reveals.
The attackers are specifically targeting EthOS, an operating system optimized for Ethereum mining, but also capable of mining Zcash, Monero, and other crypto-currencies that rely on GPU power. The platform is said to run on more than 38,000 mining rigs across the world at the moment and to arrive pre-loaded with all the necessary tools, as well as with a default username and password.
After deployment, the user simply needs to add their own wallet for mining fees and to change the default username and password. Systems where the default credentials haven’t been changed are those targeted in the newly discovered attack.
“The bot scans for the entire IPv4 range and looks for open SSH connections. If found, it attempts to log in using the default username and password to the EthOS operating system: ethos:live and root:live,” Botezatu explains.
Should the login be successful, the bot then attempts to change the existing configuration for Ethereum and hijack the mining process so that the funds are sent to the attacker’s Ethereum address. The security researchers discovered that the attackers’ wallet had already received 10 transactions over a couple of days, worth a total of $611 in Ether.
“So, if you are running an Ether Miner based on Ethereum OS, make sure you have changed the default login credentials. If you haven’t done so, now would be a good time to check whether the miner is sending money to you, not hackers,” Botezatu concludes.
New Vera Product Lets Firms Protect, Recall Emails
2.11.2017 securityweek Safety
Data protection startup Vera announced this week the launch of a new product designed to provide organizations full control over the messages and files sent out via email by their employees.
Vera’s platform aims to address the challenges associated with protecting data once it leaves an organization’s network. The company’s solutions allow companies to encrypt, track and maintain control of their data whether it’s shared directly or via cloud storage services such as Dropbox, Box and Google Drive.
The new product, Vera for Mail, extends the functionality to emails and the files attached to them. It provides seamless integration with popular email clients from Microsoft, Google and Apple, and it’s designed to have minimal workflow impact.Vera for Mail
When users want to secure an email, they type it as they normally would and before sending it they use Vera for Mail, which introduces a drop-down list into the new email window, to select the desired policy. They can allow the recipient to make any modifications, prevent them from taking screenshots, track the email (i.e. who opens it, from where and for how long), allow just “view only” permissions, or dynamically watermark the email.
Recipients see the email as being sent via the Vera service and they are either provided a “View Email” button (if the email is opened in the browser) or a policy badge (if the message is opened in an email client) that tells them what they can and cannot do with the content. Users can view the emails without installing any application, but they are also given the option to download the Vera app for “an enhanced experience.”
Emails and attachments sent via Vera for Mail are encrypted and opened on the recipient’s system inside a secure container that prevents the user from taking screenshots, downloading the content, forwarding it, or modifying it – depending on the policy set by the sender. This also allows the sender to change the policies at any time or simply revoke access to the content. Furthermore, if a message or attachment can be forwarded or downloaded, the restrictions set via Vera remain in place.
Microsoft’s Outlook email client also provides recall functionality, but it only works for messages sent within the same organization and if the recipient has an Exchange account. On the other hand, Vera for Mail allows users to protect and recall emails without the recipient installing any software or having a specific configuration.
“By applying our data-centric security platform to email, not only are you protecting the confidentiality of your communications, you’re also getting better visibility into what information is leaving your organization,” explained Vera’s Grant Shirk. “And you’re doing so without interrupting the way people work. Track who’s accessing mail, from which devices, get notifications, change permissions, and revoke access at any time.”
Analysis of 3,200 Phishing Kits Sheds Light on Attacker Tools and Techniques
2.11.2017 securityweek Phishing
Phishing kits are used extensively by cybercriminals to increase the efficiency of stealing user credentials. The basic kit comprises an accurate clone of the target medium's login-in page (Gmail, Facebook, Office 365, targeted banks, etc), and a pre-written php script to steal the credentials -- both bundled and distributed as a zip file. Successfully phished credentials are mailed by the script to the phisher, or gathered in a text file for later collection. This is commodity phishing; not spear-phishing.
A legitimate website, often a Wordpress site with old and vulnerable add-ons, is compromised. An orphaned page with no internal links is created, and the kit uploaded and unzipped. It is largely unknown to the site's administrator and invisible to external search engines; and is ready to use. The criminal merely has to send out his phishing emails pointing to the spoofed login on the compromised website.
Duo Security R&D engineer Jordan Wright found and analyzed a single phishing kit; and decided to investigate the extent of their use. The results were published this week in a new report (PDF).
Wright used two different community-driven phishing URL feeds to locate them: PhishTank run by OpenDNS, and OpenPhish.
"We polled these feeds repeatedly over a month to get new suspect phishing URLs to analyze," Wright told SecurityWeek. "We collected about 66,000."
The purpose was to try to grab any related phishing kit by visiting the URL and accessing the folder's index page. Where this was possible, it would expose any original phishing kit zip file that could be downloaded. This gave the Duo researchers access to any complete bundle left behind by lazy attackers, including the php script file used to steal and forward the credentials. Over the course of the month, Duo gathered 3,200 unique phishing kits for analysis.
One of the first things discovered was widespread use of persistence techniques. A common method on compromised WordPress sites is the inclusion of an htaccess directory configuration file within the phishing kit, that blocked access to the phishing folder from threat intelligence services. One example blocks more than 220 specified domains (including major endpoint protection firms, law enforcement agencies, and individual IP addresses). "Comparison of the different htaccess files," said Wright, "showed that there is definite information sharing between the kit developers."
The same functionality was sometimes provided by php scripts included in the kit -- but Duo detected more than 200 instances of the kit developers' own backdoors buried within the code. It is a simple call to the system function. "It takes whatever you give it as a parameter and executes it as a system command," explained Wright. "This lets anyone gain access to the host, leaving it wide open for future attack." It gives the original kit developer future access to the host without having to go through the process of compromising it himself. In a similar vein, some of the scripts contained obfuscated code to quietly send the stolen credentials to the developer as well as the phisher.
By hashing the collected phishing kits, Duo was able to examine the extent of kit reuse. In the month-long investigation, it found that the majority of kits were only used once -- but 27% (more than 900 kits) were seen on more than one host. Two were found on more than thirty hosts, indicating very active attackers. "We expect," said Wright, "that as we continue this study, we shall see more instances of reuse."
The email addresses of the individual kit users were extracted and correlated to show which phishers were connected with which campaigns and which phishing kits. Duo found that the kit developer would often use the 'From' header as a 'brand' signing card, tying multiple different kits to the same author. One in particular called himself 'wirez[@]googledocs[.]org'. This branding was found in more than 115 unique phishing kits spoofing multiple service providers.
While information sharing in the cybercriminal world is well-known, this is the first evidence of the extent to which phishing kits and phishing information are also shared.
"A next step from this study, and something we are trying to establish," Wright told SecurityWeek, "is a funnel to send the discovered email addresses of the phishers to the relevant authorities -- both email providers and law enforcement. If we can get that email address shut down as soon as we find it, any credentials harvested by the phishing kit will not be sent to the phisher -- and that's a net gain for the defenders." It neutralizes the phishing kit without having to go through the process of shutting down the compromised website -- which may otherwise be perfectly legitimate.
But that's not the only practical value from this study. "Kits can be used all day," explained Wright, "but if we can't find them, that knowledge doesn't give us much value. We're trying to shine a light on what is happening in the phishing world: here's how it works, here's what it looks like. Another part of that is, here's what you can do about it. We're open-sourcing all the code we wrote to do this research, and we're putting it up on GitHub. Organizations can download it and try to replicate the results for their own organization. They can adapt this code to say, I only want to look at these phishing URLs that I know are hitting my organization and are hitting my users. Then I can try to go out and find the phishing kit -- because whenever I'm doing incident response, knowledge is everything.
"I'll be able to say, I know this information was collected," he continued, "and from there it was emailed to that attacker. I've already been in touch with Gmail or Yahoo to get that address taken down -- well, that's huge. If I have that kind of knowledge and I have that kind of insight into what happened, I can take effective action in my incident response cleanup activities."
The reality, however, is that this level of information could also lead to some organizations taking matters into their own hands with 'active defense'. If a particular phishing kit attacking a particular organization is discovered, and found to include the system call backdoor in the php script code, then that organization could enter the host and remove the danger. "A risk with any kind of hacking back is it's so easy to cause collateral damage," warned Wright; "and that's what you have to be so careful about. This study is about how you can help protect your organization -- it's not about hacking back." Which is, of course. illegal -- for now at least.
Duo Security raised $70 million in a Series D funding round led by Meritech Capital Partners and Lead Edge Capital in October 2017.
Tech Investor VT Partners Aims to Fuel Cybersecurity Firms in Europe
2.11.2017 securityweek Cyber
Newly Formed VT Partners Seeks to Combine International Finance, American Adventure, and European Innovation
A recently formed venture capital investment firm aims to feed European technology companies and seed a new entrepreneurial approach to cybersecurity businesses in Europe. Formed earlier this year and now partnered by cybersecurity investment specialist Paladin Capital Group, VT Partners came out of the shadows last week.
VT Partners is a European B2B growth capital firm, founded by ex-Carlyle Group director, Nazo Moosa and former GMT Partners senior partner, Natalie Tydeman. The collaboration with Paladin is designed to provide high potential technology companies -- whether they are early stage companies or more established technology SMEs -- with a one-stop platform for their funding needs. Moosa becomes Paladin's new Senior Strategic Partner Europe.
Venture capital in cybersecurity is not without its critics. It has been claimed, for example, that it can promote products beyond their actual worth. While accepting that "venture capital gave birth to many great security companies that would otherwise unavoidably fail," High-Tech Bridge CEO Ilia Kolochenko believes that the relative stability of the cybersecurity market during a period of great economic instability has attracted investors with little or no knowledge of security.
"Genuine venture capital," he says, "is not just about cash, but about the tangible help and practical support it can provide to skyrocket the business. Very few VCs really do this -- many just create an active semblance of coaching and support that rather hinders the business. Cybersecurity startups should be very careful when they select a VC, and keep in mind that this step is quintessential for their success or failure."
VT Partners would probably agree with this assessment. It focuses on cybersecurity, artificial intelligence, and critical industries. Paladin is also cybersecurity-centric, with existing successful investments in PhishMe, Digital Shadows, Anomali, Endgame and Panaseer.
"We think that being a generalist in technology is a mug's game," Moosa told SecurityWeek. "It's difficult to invest in the more dynamic sections of technology when you are pursuing a generalist strategy. Cybersecurity is a very good example of that -- it's complex and frequently changing, there's a lot of vendor churn -- and the only way to get smart about the industry is to narrow your focus and spend a lot of time and resources getting to know that industry. Paladin has been doing just that for the last 16 years."
The reality, however, is that despite similar populations, the U.S. has five-times the venture funding of Europe -- and there are reasons for this. "Europe is not short of ideas," said Moosa. Think of the God Particle, graphene, public key encryption and the world wide web itself. "But the U.S. has more than just capital, it also has a well-established entrepreneurial infrastructure." This is what is lacking in Europe. "There's not just a dearth of capital, there's a dearth of certain skills in Europe."
Moosa sees the biggest problem for European companies in turning a differentiated product into a market success is a lack of entrepreneurial expertise in product management and marketing. Reflecting Kolochenko's view of what makes good venture capital, she sees her role as not just providing capital, but in helping clients find the right people to ensure success. "We've seen a real excitement around emerging technologies," she said, "particularly in artificial intelligence, machine learning and data analytics where Europe is leading. But many European businesses do not have access to the appropriate levels of capital and mentorship required to place their business onto a global stage."
To provide the mentorship, she is turning to the entrepreneurial market pool in the U.S., and especially in Silicon Valley. "I try to bring back certain ex-pats who have successfully moved to the US -- sometimes I'm successful, sometimes I'm not. Our collaboration with Paladin in this area is valuable because they have a very strong US cybersecurity market and we tap into that -- but ultimately its really about knowing the individuals who are strong in these areas -- some are coming out of the companies we invested in ten or 15 years ago -- and bringing those into the organizations we invest in. But I do believe that there is a real gap in Europe that needs to be filled if you want to take a product beyond the early stage. The only way to really be able to do that is to work very closely with management teams -- management still runs the business, but we try to complement them and fill in the gaps with both temporary and long term solutions."
The time is ripe for European venture capital. Moosa acknowledges some of the criticism of VC in the U.S. "We are possibly at the peak of the current market -- you could argue that markets peak every seven or 8 years; and we're in year 8 or 9 in the current sequence. Such criticism is often made at this stage, and sometimes legitimately: that there is more money going in, and that there's more venture capital than intellectual capital in some of the new companies. But I've seen two great peaks in 2000 and now in 2007, so criticism might simply reflect where we are in the market right now; but the point that I would bring us back to is that Europe is very, very different."
If Moosa succeeds, she will bring a combination of international finance and Silicon Valley energy to an underdeveloped but innovative European cybersecurity space. She acknowledges that some of these companies might achieve some success and up-sticks to move to America -- if only because many of the early adopters of new technology are American. In her heart, however, she wants to be a part of developing a new and vibrant European cybersecurity industry that will remain very much European.
OpenSSL Patches Flaws Found With Google Fuzzer
2.11.2017 securityweek Vulnerebility
OpenSSL updates released on Thursday patch two low and medium severity vulnerabilities discovered using Google’s open source OSS-Fuzz fuzzing service.
The medium severity flaw patched with the release of OpenSSL 1.1.0g and 1.0.2m is CVE-2017-3736. Described as a carry propagating bug in the x86_64 Montgomery squaring procedure, the security hole affects processors that support BMI1, BMI2 and ADX extensions (e.g. Intel Broadwell 5th generation and later, or AMD Ryzen).
These types of flaws could allow an attacker to recover encryption keys and access protected communications, but OpenSSL developers believe an attack is difficult to carry out.
“Analysis suggests that attacks against RSA and DSA as a result of this defect would be very difficult to perform and are not believed likely. Attacks against DH are considered just feasible (although very difficult) because most of the work necessary to deduce information about a private key may be performed offline,” OpenSSL said in an advisory.
“The amount of resources required for such an attack would be very significant and likely only accessible to a limited number of attackers. An attacker would additionally need online access to an unpatched system using the target private key in a scenario with persistent DH parameters and a private key that is shared between multiple clients,” it added.
Developers pointed out that the vulnerability is very similar to CVE-2015-3193, which was patched in December 2015, and CVE-2017-3732, one of the four security holes fixed this January. However, they believe CVE-2017-3736 needs to be treated separately.
The second vulnerability patched with the release of OpenSSL 1.1.0g and 1.0.2m is a low severity issue that could lead to an out-of-bounds (OOB) read. The flaw, tracked as CVE-2017-3735, has existed since 2006 and it was disclosed in August. While a source code fix was made available in August, developers believed it did not deserve an update due to its low severity.
The flaws resolved in the latest versions of OpenSSL were discovered using OSS-Fuzz, an open source fuzzing service launched by Google in December 2016. In the first months, the fuzzer helped find 264 potential security issues in 47 open source projects.
This is the fourth round of OpenSSL updates released this year, but only two of the previous updates, from January and February, included security patches.
Shadow IT Growth Introducing Huge Compliance Risks: Report
2.11.2017 securityweek Safety
Organizations Not Working to Defend Shadow IT Are in Danger of Data Loss and Regulatory Violations
Shadow IT continues to grow, while senior management remains in denial. The average enterprise now uses 1,232 cloud apps (up 33% from the second half of last year), while CIOs still believe their organizations use between just 30 and 40 cloud apps and services. Within this cloud, 20% of all stored data is at risk from being 'broadly shared'.
The figures come from 1H 2017 Shadow Data Report (PDF), based on aggregated and anonymized data from 22,000 cloud apps and services, 465 million documents, and 2.3 billion emails used by Symantec's CloudSOC (CASB) customers.
CloudSOC was acquired by Symantec when it bought Blue Coat Systems for $4.65 billion in June 2016. Symantec defines 'broadly shared' as "documents that are widely shared with employees within the organization, documents that have been shared externally with specific individuals such as contractors and partners, and documents shared to the public." Put briefly, they have a high risk of exposure.
Of that 20% of broadly shared data, 2% specifically contain compliance-related data such as personally identifiable information (PII), payment card industry information (PCI) and protected health information (PHI). This means that CloudSOC customers over-shared 93 million documents. Of these, 2% (1.86 million) contained PCI; 19% (17.67 million) contained PII; and 79% (73.47 million) contained PHI; all of which potentially put the organization in breach of a range of regulatory requirements.
The figures are even worse for emails. Twenty-nine percent of the 2.3 billion emails analyzed are broadly shared and at risk of leakage. Nine percent of these contain compliance-related data: 64% contain PII, 9% contain PHI, and 27% contain PCI. To put these figures in context, Symantec found 207 million at risk emails. Within these, it found 132.48 million emails containing PII data.
Cloud apps are a popular target for hackers, and Symantec's research evaluated the incidence of users' high risk actions in the cloud. The biggest threat is the loss of data, and the researchers found that 71% of the detected high risk behaviors indicated attempts to exfiltrate data. Seventeen percent indicated attempted brute force attacks; 6% indicated attempts to destroy data; and 6% indicated attempts to hack into user cloud accounts.
The researchers mapped the high risk behaviors to the users' organizations. It found that an astonishing 14% of companies have 50% or more of their employees demonstrating high risk behavior within the cloud apps and services. On the plus side, 53% of their customers have zero high risk employees -- indicating that some organizations are doing a good job with their user awareness training, while others have a distance to go.
It is important to remember that these figures come from customers of Symantec's CloudSOC CASB. They are already making efforts to protect their cloud-based data. We don't know if similar figures would be replicated by other CASB users -- but one thing is clear. Any organization that is not specifically trying to defend its Shadow IT is in serious danger of data loss and regulatory violations.
Gangs, States and 'Geeks' Behind Canada Cyberattacks: Minister
2.11.2017 securityweek CyberCrime
Cyberattacks on Canadian government computers by what a minister described Tuesday as gangsters, rogue states and "geeks in basements" are on the rise, but are also failing more, according to a report.
The nation's ultra-secretive eavesdropping agency or Communications Security Establishment (CSE) however concluded that Canada is not doing enough to fend off intruders.
"Some of it is just nuisance," Public Safety Minister Ralph Goodale told reporters. "Some of it is criminal in intent."
"It comes from organized crime. It comes from rogue states. It comes from foreign militaries. It comes from geeks in the basement," he said.
In the report, the CSE found that the government blocks more than 600 million attempts each day to identify or exploit system vulnerabilities.
Between 2013 and 2015, this included more than 2,500 state-sponsored cyber attacks. The culprits were not identified, but Ottawa previously said that China was responsible for a major cyberattack on its National Research Council in 2014.
"Although more than six percent of these attempts breached the government of Canada's systems in 2013, this number had fallen to less than two percent in 2015," it noted.
Still, Ottawa's investment in security systems remains "inadequate," the CSE said.
The government's outreach to the private sector has also largely failed because, according to the agency, "private sector companies seem to lack trust in the public sector's ability to safeguard their information."
According to a senate committee studying cybersecurity and cyberfraud, eight million Canadians fell victim to a cybercrime last year.
Goodale said cyber crimes cost businesses around the world an estimated Can$400 billion each year, and that figure is predicted to rise to Can$2 trillion annually by 2020.
Given allegations of Russian meddling in last year's US presidential vote, Ottawa is also taking measures to safeguard its elections.
The CSE warned in a separate report earlier this year that "almost certainly multiple hacktivist groups will deploy cyber capabilities in an attempt to influence the democratic process in 2019," when the next federal elections are scheduled.
OpenSSL patches vulnerabilities discovered with Google OSS-Fuzz fuzzing service
2.11.2017 securityaffairs Vulnerebility
OpenSSL patches two low and medium severity vulnerabilities that were discovered by using Google’s open source OSS-Fuzz fuzzing service.
The medium severity vulnerability tracked as CVE-2017-3736 was addressed with the release of OpenSSL 1.1.0g and 1.0.2m.
The flaw is a carry propagating bug in the x86_64 Montgomery squaring procedure, it affects processors that support BMI1, BMI2 and ADX extensions, such as Intel Broadwell 5th generation and later and the AMD Ryzen.
An attacker can exploit this kind of vulnerability to recover encryption keys and access protected communications.
“There is a carry propagating bug in the x86_64 Montgomery squaring procedure. No
EC algorithms are affected.” read the OpenSSL advisory.
“Analysis suggests that attacks against RSA and DSA as a result of this defect would be very difficult to perform and are not believed likely. Attacks against DH are considered just feasible (although very difficult) because most of the work necessary to deduce information about a private key may be performed offline,”
The OpenSSL development team believe that trigger the issue in a real scenario attack is difficult due to the significant effort needed.
“The amount of resources required for such an attack would be very significant and likely only accessible to a limited number of attackers. An attacker would additionally need online access to an unpatched system using the target private key in a scenario with persistent DH parameters and a private key that is shared between multiple clients,” continues the advisory.
The CVE-2017-3736 vulnerability is very similar to CVE-2015-3193 that was patched in December 2015, and CVE-2017-3732 fixed in January, however, OpenSSL developers highlight it needs to be treated separately.
The second flaw, tracked as CVE-2017-3735, was patched with the release of OpenSSL 1.1.0g and 1.0.2m, it is a low severity issue that could lead to an out-of-bounds (OOB) read.
The vulnerability disclosed in August 2016 has existed since 2006, the source code patch was available since August.
“If an X.509 certificate has a malformed IPAddressFamily extension, OpenSSL could do a one-byte buffer overread. The most likely result would be an erroneous display of the certificate in text format. As this is a low severity fix, no release is being made. The fix can be found in the source repository (1.0.2, 1.1.0, and master branches); see
https://github.com/openssl/openssl/pull/4276. This bug has been present
since 2006.” reads the advisory.
“This issue was found by Google’s OSS-Fuzz project on August 22. The fix was developed by Rich Salz of the OpenSSL development team.”
Both vulnerabilities were discovered using OSS-Fuzz, an open source fuzzing service launched by Google in December.
“OSS-Fuzz’s goal is to make common software infrastructure more secure and stable by combining modern fuzzing techniques with scalable distributed execution. OSS-Fuzz combines various fuzzing engines (initially, libFuzzer) with Sanitizers (initially, AddressSanitizer) and provides a massive distributed execution environment powered by ClusterFuzz.” wrote Google when announced the service.
Five months after the launch of OSS-Fuzz, Google revealed that its robot army has been working hard at fuzzing, processing 10 trillion test inputs a day.
The fuzzer helped find 264 potential security vulnerabilities in 47 open source projects.

Hacker Falsely Claiming to Breach FireEye Arrested, CEO Says
2.11.2017 securityweek Crime
The hacker who falsely claimed to have breached FireEye -- it was just the personal online accounts of one employee -- was arrested by international law enforcement and taken into custody on October 26, FireEye CEO Kevin Mandia said Wednesday.
"These attackers rarely, if ever get caught and therefore I'm pleased, that in this case we're able to impose repercussions for the attacker and achieve a small victory for the good guys," Mandia said during a conference call.
He did not provide the name for the hacker, nor the location for the arrest. In July 2017, the hacker made grandiose claims that he was part of a new LeakTheAnalyst operation aimed at doxing the security professionals who hunt hackers. "Let's trash their reputation in the field," he posted to Pastebin. In reality, he had little of any value, taken from the online accounts of one FireEye employee.
According to FireEye's CFO Frank Verdecanna, the incident is not thought to have had any significant negative effect on FireEye's financial performance over the last three months, beyond the internal cost and time required to investigate the hacker's claims. "I don't want to underestimate the unfairness of the situation of an anonymous person making false claims," Mandia told CRN. "You have to prove the negative, which is really annoying."
The hacker's arrest was announced at FireEye's Q3 Earnings Results Conference Call on Wednesday. While Q3 performance was a little better than expected, FireEye is still yet to report a profit since it went public in 2013. During Q3, the net loss attributable to shareholders narrowed to $72.9 million (41 cents per share) from $123.4 million (75 cents per share) a year earlier.
This would indicate that FireEye is moving in the right direction. However, investors were disappointed in the forecasts made for Q4. "For Q4, we're now expecting billings in the range of $210 million to $230 million, and revenue in the range of $190 million to $196 million," announced Verdecanna. He believes that the firm is on track to deliver non-GAAP operating profitability in Q4.
Investors evidently hoped for better. Analysts, on average, were expecting total revenue of about $195.6 million, at the top end of FireEye's forecast, according to Thomson Reuters I/B/E/S. The effect was an immediate tumble in share price on NASDAQ in aftermarket trading (at the time of publishing, it is down 12%).
In publicity terms, it has been a challenging period for FireEye. Apart from the alleged hack and the new tumble in share price, it has been employed to investigate the massive Equifax breach. While this is positive, the firm reportedly removed a case study from its website where Equifax endorsed FireEye for protecting it from zero-day attacks. However, FireEye's technology is typically used to protect against advanced malware attacks that leverage zero-day vulnerabilities in popular operating systems and business applications such as Microsoft Office and Adobe Flash. The Equifax hack was pulled off by leveraging a vulnerability in Apache Struts, which was used by a web application and allowed the attack to happen assumingly without requiring malware to be used.
One positive area for FireEye is strong growth in sales of its new Helix product announced in November 2016. Helix helps accelerate incident response with automation and orchestration by leveraging detection capabilities from FireEye's Endpoint Security (HX) and Network Security (NX) engines, along with FireEye iSIGHT Intelligence.
"Both FireEye as a service and iSIGHT threat intelligence had strong quarters, and we added 57 new Helix customers bringing the total to 71," announced Verdecanna. It remains slow progress for FireEye, but it still expects to report profits in 2018.
FireEye went public in September 2013, with the share price immediately soaring by more than 90% before settling at around $38.74. At the time of writing this, it is $14.45. FireEye purchased Mandiant for $1 billion in January 2014. Mandiant's Kevin Mandia took over as CEO at FireEye in June 2016.
Smartphone Exploits Earn Hackers Over $500,000
2.11.2017 securityweek Congress
White hat hackers earned more than half a million dollars at this year’s Mobile Pwn2Own competition after successfully demonstrating exploits against Samsung’s Galaxy S8, Apple’s iPhone 7 and Huawei’s Mate 9 Pro.
The hacking contest, organized by Trend Micro’s Zero Day Initiative (ZDI) at the PacSec conference in Tokyo, Japan, offered more than $500,000 for exploit chains targeting browsers, short distance communications (Wi-Fi, Bluetooth and NFC), messaging, and baseband components in the Google Pixel, Galaxy S8, iPhone 7 and Mate 9 Pro.
All devices had been running the latest versions of the software and operating systems – Apple, Google and Huawei released patches the night before the event started.
On the first day, participants earned a total of $350,000 for disclosing vulnerabilities that allow attacks against Internet Browser on the Galaxy S8, Safari on the iPhone 7, Wi-Fi on the iPhone 7, and the baseband on the Mate 9 Pro.
On the second day, MWR Labs earned $25,000 for hacking Google Chrome of the Mate 9 Pro via 5 logic bugs in Huawei apps that allowed a browser sandbox escape and data exfiltration.
The same team took home an additional $25,000 after exploiting 11 flaws across six different apps to hack Internet Browser on the Galaxy S8. The exploit resulted in arbitrary code execution and sensitive data leakage.
A researcher from China-based Qihoo 360 earned $20,000 for a partially successful exploit targeting the iPhone 7’s Wi-Fi component. The exploit worked properly, but one of the three vulnerabilities it leveraged had been previously disclosed at Pwn2Own by a different contestant. The same Chinese expert was awarded another $25,000 for hacking Safari on the iPhone 7.
The last entry came from the researcher Amat Cama (aka Acez), who earned $50,000 for a baseband exploit targeting the Galaxy S8. The exploit relied on a stack-based buffer overflow that allowed arbitrary code execution.
The total amount of money paid to researchers over the course of two days at Mobile Pwn2Own 2017 was $495,000. The Tencent Keen Security Lab team got the highest number of Master of Pwn points, which also earned them 65,000 ZDI reward points, worth roughly $25,000.
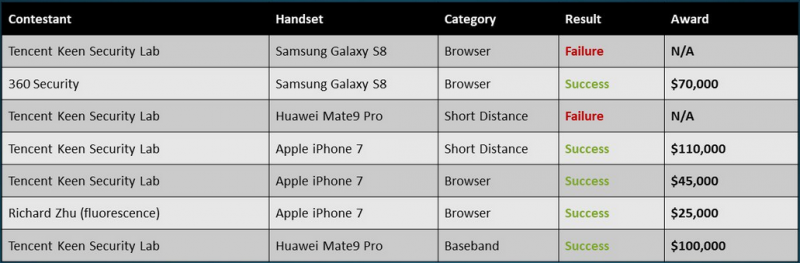
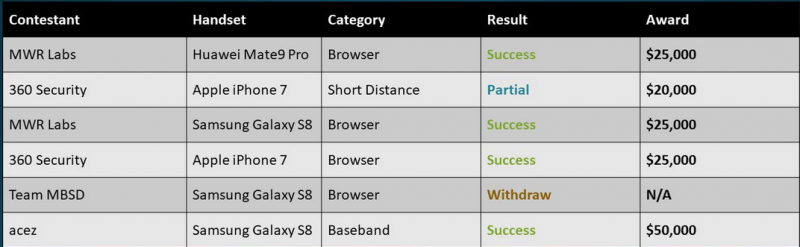
While one successful entry did target the Chrome browser, no one has attempted to demonstrate an exploit on Google’s Pixel phone.
Affected vendors have been provided the details of the vulnerabilities used at the event and ZDI will give them 90 days to release fixes before a limited advisory describing the flaws will be made public.
Automated System Defeats reCAPTCHA With High Accuracy
2.11.2017 securityweek Security
A newly devised system that targets the audio version of Google’s reCAPTCHA challenges can break them with very high accuracy.
Dubbed unCAPTCHA, the automated system designed by computer science experts from the University of Maryland (UM) is said to be able to defeat the audio reCaptcha system with 85% accuracy.
The system uses browser automation software to interact with the target site and engage with the captcha. The tool, which has been published on GitHub, can properly identify spoken numbers to pass the reCaptcha programmatically and trick the site into thinking their bot is a human, the authors claim.
“Specifically, unCaptcha targets the popular site Reddit by going through the motions of creating a new user, although unCaptcha stops before creating the user to mitigate the impact on Reddit,” the experts say.
To correctly bypass the captcha, which includes numbers that are read aloud at varied speeds, pitches, and accents through background noise, the attack identifies the audio message on the page, downloads it, and then automatically splits it by locations of speech.
Next, each number audio bit is uploaded to 6 different online audio transcription services that are free to use, namely IBM, Google Cloud, Google Speech Recognition, Sphinx, Wit-AI, and Bing Speech Recognition, and the results are collected.
“We ensemble the results from each of these to probabilistically enumerate the most likely string of numbers with a predetermined heuristic. These numbers are then organically typed into the captcha, and the captcha is completed. From testing, we have seen 92%+ accuracy in individual number identification, and 85%+ accuracy in defeating the audio captcha in its entirety,” the system’s authors reveal.
Another recently revealed tool for defeating CAPTCHA systems is targeting text-based systems and was designed to mimic the human eye. Called the Recursive Cortical Network (RCN), it incorporates neuroscience insights into a structured probabilistic generative model framework.
In a paper (PDF), the team of researchers behind RCN explain that the tool is capable of solving Google reCAPTCHA with a 66.6% accuracy, but that it is also highly efficient against other systems: 64.4% for BotDetect, 57.4% for Yahoo, and 57.1% for PayPal image challenges. The findings were published in the Science magazine.
“By drawing inspiration from systems neuroscience, we introduce a probabilistic generative model for vision in which message-passing based inference handles recognition, segmentation and reasoning in a unified way. The model demonstrates excellent generalization and occlusion-reasoning capabilities, and outperforms deep neural networks on a challenging scene text recognition benchmark while being 300-fold more data efficient,” the researchers say.
Cisco Patches Serious DoS, Injection Flaws in Several Products
2.11.2017 securityweek Vulnerebility
Cisco has released updates for several of its security, networking and cloud products to address over a dozen vulnerabilities, including high severity issues that can be used for command injections and denial-of-service (DoS) attacks.
The list of severe weaknesses includes two DoS vulnerabilities in Cisco’s Wireless LAN Controllers. The security holes, tracked as CVE-2017-12275 and CVE-2017-12278, allow attackers to cause affected devices to reload and enter a DoS condition.
Cisco has also fixed high severity flaws in some of its Aironet access points. The bugs, identified as CVE-2017-12273 and CVE-2017-12274, can be exploited by unauthenticated attackers that have access to devices via Layer 2 radio frequency to cause the system to enter a DoS condition by sending specially crafted requests.
As for security products, Cisco patched a severe vulnerability in some of its Firepower appliances. The flaw (CVE-2017-12277) allows an authenticated attacker to remotely inject commands that could get executed with root privileges.
Another security product patched this week is the Cisco Identity Services Engine (ISE), which has a privilege escalation bug (CVE-2017-12261) that could allow an authenticated local attacker to run arbitrary command-line interface (CLI) commands with elevated privileges.
The cloud products impacted by high severity flaws are the Prime Collaboration Provisioning application, which is affected by a SQL injection weakness that can be exploited remotely with authentication (CVE-2017-12276), and Cisco Application Policy Infrastructure Controller, which allows an unauthenticated attacker to gain privileged access to services only available on the internal network (CVE-2017-12262).
A majority of these flaws were discovered internally by Cisco and there is no evidence of exploitation for malicious purposes.
White hat hackers earn over $500,000 for mobile exploits at Mobile Pwn2Own 2017 competition
2.11.2017 securityaffairs Congress
Let’s see what has happened at Mobile Pwn2Own 2017 competition organized by Trend Micro’s Zero Day Initiative (ZDI) at the PacSec conference in Tokyo.
Here we are discussing once again of the Mobile Pwn2Own competition organized by Trend Micro’s Zero Day Initiative (ZDI) at the PacSec conference in Tokyo.
White hat hackers earned more than half a million dollars at Mobile Pwn2Own 2017 competition devising successfully exploits against popular smartphones running the latest versions of OSs.
Major vendors, including Apple, Google and Huawei released patches the night before the event started.
The exploits target browsers, short distance communications (Wi-Fi, Bluetooth, and NFC), messaging, and baseband components in the mobile devices, including Samsung’s Galaxy S8, Apple’s iPhone 7 and Huawei’s Mate 9 Pro.
Participants earned a total of $350,000 for triggering vulnerabilities in Internet Browser on the Galaxy S8, Safari on the iPhone 7, Wi-Fi on the iPhone 7, and the baseband on the Mate 9 Pro.
“The first day of Mobile Pwn2Own 2017 has come to a close, and we’ve awarded a total of $350,000 and 55 Master of Pwn points. Today saw five successful attempts and two failed attempts as the ZDI program acquired 11 bugs for the Samsung Galaxy S8, Apple iPhone 7, and the Huawei Mate9 Pro.” states ZDI blog post.
There were also failures, for example the Tencent Keen Security Lab (@keen_lab) targeting the Samsung Internet Browser on the Samsung Galaxy S8 failed as they could not get their exploit chain to work within the allotted time.
Fortunately, the same team demonstrated a successful WiFi exploit on the Apple iPhone 7.
“They used a total of four bugs to gain code execution and escalate privileges to allow their rogue application to persist through a reboot. They earned $60,000 for the WiFi exploit and added $50,000 for the persistence bonus – a total of $110,000 and 11 Master of Pwn points. This screenshot may not look like much, but all it took was connecting to a WiFi network to get the “KeenLab” app to appear.” continues ZDI.
Day Two
On the second day, experts with the MWR Labs earned $25,000 for hacking Google Chrome of the Mate 9 Pro via 5 logic flaws in Huawei apps that them to escape the browser sandbox and exfiltrate data.
MWR Labs hackers also earned $25,000 after exploiting 11 vulnerabilities across six different apps to hack Internet Browser on the Galaxy S8, they triggered the flaws to remotely execute arbitrary code and force sensitive data leakage.
A researcher from China-based Qihoo 360 (@mj0011sec) earned $20,000 for a partially successful exploit targeting the iPhone 7’s Wi-Fi component, later he was awarded another $25,000 for hacking Safari on the iPhone 7.
The total amount of money paid to participants at Mobile Pwn2Own 2017 was $495,000, The Tencent Keen Security Lab team obtained the highest number of Master of Pwn points.
What’s next?
The ZDI already reported to the vendor the details of the vulnerabilities exploited during the contest. Vendors have 90 days to release fixes before a limited advisory describing the flaws will be made public.
Undetectable ATM shimmers used to steal Chip Based Card worldwide
2.11.2017 securityaffairs CyberCrime
Crooks continue using skimmers in card frauds, these devices are becoming even more sophisticated, last wave of attacks leverages on so-called Shimmers.
Crooks continue to skimmers in payment card frauds, these devices are becoming even more sophisticated.
The number of cyber attacks against ATM involving so-called ‘insert skimmers’ is increasing. Insert Skimmers are wafer-thin fraud devices designed to fit invisibly inside the ATM card slot.
Insert Skimmers are able to capture card data and store it on an embedded flash memory.
In July, the popular investigator Brian Krebs reported in some cases the use of insert skimmers that were able to transmit stolen card data wirelessly via infrared.
The infrared is a short-range communication technology, every day we use it when we change TV program with a television remote control.
Krebs cited a case that has happened a few weeks before in the Oklahoma City metropolitan area where at least four banks were victims of ATM attacks involving insert skimmers.
Latest warning is arriving from Canada where experts observed a new wave of attacks using sophisticated ATM skimming devices called ‘Shimmers.’ The Shimmers are skimming devices that could be used to steal data from chip-based credit and Debit cards while cardholders use them in POS (Point-of-sale) terminal.
Shimmers, and more in general insert skimmers are substituting bulkier skimmers, as explained by Const. Alex Bojic of the Coquitlam RCMP economic crime unit.

“A major Coquitlam business now includes daily testing of its computerized point-of-sale terminals as part of its security routine. On January 11, 2017, one of those routine daily checks found that a test card was sticking inside the terminals. When the terminals were opened, they contained four very slim, plastic card ‘shimmers’ that contained microchips meant to illegally capture the banking data on your credit or debit cards. If the data had been successfully stolen it could have been used to create fake credit or debit cards.” reads the blog post published by the Coquitlam RCMP economic crime unit.
“The Coquitlam RCMP Economic Crime Unit (ECU) says these new, tiny card shimmers make the once-bulky, overlay systems called ‘skimmers’ virtually obsolete. You can’t see a shimmer from the outside like the old ‘skimmer’ versions says Cst. Alex Bojic of Coquitlam RCMP ECU, businesses and consumers should immediately report anything abnormal about the way their card is acting. That’s especially true if the card is sticking inside the machine.

The shimmers have been used in attacks against POS Machine located in retailed stores and other public areas.
“Most skimming devices made to steal credit card data do so by recording the data stored in plain text on the magnetic stripe on the backs of cards. A shimmer, on the other hand, is so named because it acts a shim that sits between the chip on the card and the chip reader in the ATM or point-of-sale device — recording the data on the chip as it is read by the underlying machine.” wrote Krebs.
The crimes were initially reported in in Canada, but law enforcement is warning financial institutions worldwide.
The shimmers work by fitting inside a card reader, then they are able to record information from chip cards.
The ATM shimmers attacks exploit the fact that some financial institutions apparently don’t correctly implement the EMV chip card standard.
According to gbhackers.com, ATM giant NCR Corp wrote in a 2016 alert that an essential condition for the success of this attack is if a bank card “issuer neglects to check the CVV when authorizing a transaction”.
“All issuers MUST make these basic checks to prevent this category of fraud. Card Shimming is not a vulnerability with a chip card, nor with an ATM, and therefore it is not necessary to add protection mechanisms against this form of attack to the ATM.”
Silence – a new Trojan attacking financial organizations
2.11.2017 Kaspersky Virus
In September 2017, we discovered a new targeted attack on financial institutions. Victims are mostly Russian banks but we also found infected organizations in Malaysia and Armenia. The attackers were using a known but still very effective technique for cybercriminals looking to make money: gaining persistent access to an internal banking network for a long period of time, making video recordings of the day to day activity on bank employees’ PCs, learning how things works in their target banks, what software is being used, and then using that knowledge to steal as much money as possible when ready.
We saw that technique before in Carbanak, and other similar cases worldwide. The infection vector is a spear-phishing email with a malicious attachment. An interesting point in the Silence attack is that the cybercriminals had already compromised banking infrastructure in order to send their spear-phishing emails from the addresses of real bank employees and look as unsuspicious as possible to future victims.
The attacks are currently still ongoing.
Technical details
The cybercriminals using Silence send spear-phishing emails as initial infection vectors, often using the addresses of employees of an already infected financial institution, with a request to open an account in the attacked bank. The message looks like a routine request. Using this social engineering trick, it looks unsuspicious to the receiver:
Spear-phishing email in Russian.
Malicious .chm attachment
md5 dde658eb388512ee9f4f31f0f027a7df
Type Windows help .chm file
The attachment we detected in this new wave is a “Microsoft Compiled HTML Help” file. This is a Microsoft proprietary online help format that consists of a collection of HTML pages, indexing and other navigation tools. These files are compressed and deployed in a binary format with the .CHM (compiled HTML) extension. These files are highly interactive and can run a series of technologies including JavaScript, which can redirect a victim towards an external URL after simply opening the CHM. Attackers began exploiting CHM files to automatically run malicious payloads once the file is accessed. Once the attachment is opened by the victim, the embedded .htm content file (“start.htm”) is executed. This file contains JavaScript, and its goal is to download and execute another stage from a hardcoded URL:
Part of start.htm embedded file
The goal of the script is to download and execute an obfuscated .VBS script which again downloads and executes the final dropper
Obfuscated VBS script that downloads binary dropper
Dropper
md5 404D69C8B74D375522B9AFE90072A1F4
Compilation Thu Oct 12 02:53:12 2017
Type Win32 executable
The dropper is a win32 executable binary file, and its main goal is to communicate with the command and control (C&C) server, send the ID of the infected machine and download and execute malicious payloads.
After executing, the dropper connects to the C&C using a GET request, sends the generated victim ID, downloads the payloads and executes them using the CreateProcess function.
C&C connect request string with ID
C&C connect procedure
Payloads
The payloads are a number of modules executed on the infected system for various tasks like screen recording, data uploading etc.
All the payload modules we were able to identify are registered as Windows services.
Monitoring and control module
md5 242b471bae5ef9b4de8019781e553b85
Compilation Tue Jul 19 15:35:17 2016
Type Windows service executable
The main task for this module is to monitor the activity of the victim. In order to do so it takes multiple screenshots of the victim´s active screen, providing a real-time pseudo-video stream with all the victim´s activity. A very similar technique was used in the Carbanak case, where this monitoring was used to understand the victim´s day to day activity.
The module is registered and started by a Windows service named “Default monitor”.
Malicious service module name
After the initial startup, it creates a Windows named pipe with a hardcoded value – “\\.\pipe\{73F7975A-A4A2-4AB6-9121-AECAE68AABBB}”. This pipe is used for sharing data in malicious inter-process communications between modules.
Named pipe creation
The malware decrypts a block of data and saves it as a binary file with the hardcoded name “mss.exe” in a Windows temporary location, and later executes it using the CreateProcessAsUserA function. This dropped binary is the module responsible for the real-time screen activity recording.
Then, the monitoring module waits for a new dropped module to start in order to share the recorded data with other modules using the named pipe.
Screen activity gathering module
md5 242b471bae5ef9b4de8019781e553b85
Compilation Tue Jul 19 15:35:17 2016
Type Windows 32 executable
This module uses both the Windows Graphics Device Interface (GDI) and the Windows API to record victim screen activity. This is done using the CreateCompatibleBitmap and GdipCreateBitmapFromHBITMAP functions. Then the module connects to the named pipe created by the previously described module and writes the data in there. This technique allows for the creation of a pseudo-video stream of the victim’s activity by putting together all the collected bitmaps.
Writing bitmaps to pipe
C&C communication module with console backconnect
md5 6A246FA30BC8CD092DE3806AE3D7FC49
Compilation Thu Jun 08 03:28:44 2017
Type Windows service executable
The C&C communication module is a Windows service, as are all the other modules. Its main functionality is to provide backconnect access to the victim machine using console command execution. After the service initialization, it decrypts the needed Windows API function names, loads them with LoadLibrary and resolves with GetProcAddress functions.
WinAPI resolving
After successful loading of the WinAPI functions, the malware tries to connect to the C&C server using a hardcoded IP address (185.161.209[.]81).
C&C IP
The malware sends a special request to the command server with its ID and then waits for a response, which consists of a string providing the code of what operation to execute. The options are:
“htrjyytrn” which is the transliteration of “reconnect” (“реконнект” in russian layout).
“htcnfhn” which is the transliteration of “restart” (“рестарт” in russian layout).
“ytnpflfybq” which is the transliteration of “нет заданий” meaning “no tasks”
Finally the malware receives instructions on what console commands to execute, which it does using a new cmd.exe process with a parameter command.
Instruction check
The described procedure allows attackers to install any other malicious modules. That can be easily done using the “sc create” console command.
Winexecsvc tool
md5 0B67E662D2FD348B5360ECAC6943D69C
Compilation Wed May 18 03:58:26
Type Windows 64 executable
Also, on some infected computers we found a tool called the Winexesvc tool. This tool basically provides the same functionality as the well-known “psexec” tool. The main difference is that the Winexesvc tool enables the execution of remote commands from Linux-based operating system. When the Linux binary “winexe” is run against a Windows server, the winexesvc.exe executable is created and installed as a service.
Conclusion
Attacks on financial organization remain a very effective way for cybercriminals to make money. The analysis of this case provides us with a new Trojan, apparently being used in multiple international locations, which suggests it is an expanding activity of the group. The Trojan provides monitoring capabilities similar to the ones used by the Carbanak group.
The group uses legitimate administration tools to fly under the radar in their post-exploitation phase, which makes detection of malicious activity, as well as attribution more complicated. This kind of attack has become widespread in recent years, which is a very worrisome trend as it demonstrates that criminals are successful in their attacks. We will continue monitoring the activity for this new campaign.
The spear-phishing infection vector is still the most popular way to initiate targeted campaigns. When used with already compromised infrastructure, and combined with .chm attachments, it seems to be a really effective way of spreading, at least among financial organizations.
Recommendations
The effective way of protection from targeted attacks focused on financial organizations are preventive advanced detection capabilities such as a solution that can detect all types of anomalies and scrutinize suspicious files at a deeper level, be present on users’ systems. The Kaspersky Anti Targeted Attack solution (KATA) matches events coming from different infrastructure levels, discerns anomalies and aggregates them into incidents, while also studying related artifacts in a safe environment of a sandbox. As with most Kaspersky products, KATA is powered by HuMachine Intelligence, which is backed by on premise and in lab-running machine learning processes coupled with real-time analyst expertise and our understanding of threat intelligence big data.
The best way to prevent attackers from finding and leveraging security holes, is to eliminate the holes altogether, including those involving improper system configurations or errors in proprietary applications. For this, Kaspersky Penetration Testing and Application Security Assessment services can become a convenient and highly effective solution, providing not only data on found vulnerabilities, but also advising on how to fix it, further strengthening corporate security.
IOC’s
Kaspersky lab products detects the Silence trojan with the following verdicts:
Backdoor.Win32.Agent.dpke
Backdoor.Win32.Agent.dpiz
Trojan.Win32.Agentb.bwnk
Trojan.Win32.Agentb.bwni
Trojan-Downloader.JS.Agent.ocr
HEUR:Trojan.Win32.Generic
Full IOC’s and YARA rules delivered with private report subscription.
MD5
Dde658eb388512ee9f4f31f0f027a7df
404d69c8b74d375522b9afe90072a1f4
15e1f3ce379c620df129b572e76e273f
D2c7589d9f9ec7a01c10e79362dd400c
1b17531e00cfc7851d9d1400b9db7323
242b471bae5ef9b4de8019781e553b85
324D52A4175722A7850D8D44B559F98D
6a246fa30bc8cd092de3806ae3d7fc49
B43f65492f2f374c86998bd8ed39bfdd
cfffc5a0e5bdc87ab11b75ec8a6715a4
Gaza Cybergang – updated activity in 2017:
2.11.2017 Kaspersky CyberCrime
New targets, use of MS Access Macros and CVE 2017-0199, and possible mobile espionage
1. Summary information
The Gaza cybergang is an Arabic-language, politically-motivated cybercriminal group, operating since 2012 and actively targeting the MENA (Middle East North Africa) region. The Gaza cybergang’s attacks have never slowed down and its typical targets include government entities/embassies, oil and gas, media/press, activists, politicians, and diplomats.
One of the interesting new facts, uncovered in mid-2017, is its discovery inside an oil and gas organization in the MENA region, infiltrating systems and pilfering data, apparently for more than a year.
Another interesting finding is the use of the recently discovered CVE 2017-0199 vulnerability, and Microsoft Access files into which the download scripts were embedded to reduce the likelihood of their detection. Traces of mobile malware that started to appear from late April 2017, are also being investigated.
Recent targets for the group seem to be varied in nature; the attackers do not appear to be choosing targets selectively, but rather seeking different kinds of MENA intelligence.
Some of the interesting new updates about the Gaza cybergang:
Gaza cybergang attackers have continued their interest in government entities in MENA
New targets identified include oil and gas in MENA
New tools and techniques include
Abuse of the CVE 2017-0199 vulnerability
Usage of macros inside Microsoft Access files, enabling lower detection rates
Possible Android mobile malware being used by attackers
Previous published research:
https://securelist.com/gaza-cybergang-wheres-your-ir-team/72283/
Kaspersky Lab products and services successfully detect and block Gaza cybergang attacks, detection names below:
HEUR:Exploit.MSOffice.Generic
HEUR:Trojan.Win32.Cometer.gen
HEUR:Trojan.Win32.Generic
Trojan-Downloader.Win32.Downeks
Trojan-Spy.MSIL.Downeks
Win32.Bublik
Win32.Agentb
More information about Gaza cybergang is available to customers of the Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
2. Technical details
Previously, Gaza cybergang attacks were surprisingly successful in using simple and common tools to achieve their goals. They relied on a variety of Remote Access Trojans (RATs) to perform their activities, including Downeks, Qasar, Cobaltstrike…
As recently as June 2017, however, the attackers started using the CVE 2017-0199 vulnerability which enables direct code execution from a Microsoft office document on non-patched victim systems (Cobaltstrike payload in this case). Another finding is a possible Android Trojan that the attackers positioned on one of their command servers in April 2017.
In most cases, malware is sent by email as a compressed attachment or download links. Starting from March 2017, we have observed downloaders or Microsoft office documents with embedded macros being sent to victims. When opened, the downloader would contact a URL or IP address to retrieve the actual payload. Once successfully executed, the malware grants full access to the attackers, providing them with the ability to collect files, keystrokes and screenshots from victims’ devices. If the initial downloaded malware was detected by the victim, the downloader would attempt to retrieve other malware files to the victim’s device, in the hope that one of those files would work.
The full list of indicators of compromise (IOCs) can be found in Appendix I. The list of the most interesting lure content, malware files and related droppers, and command servers can be found in Appendix II.
3. Summary of recent campaigns
Below can be found the list of recent findings related to Gaza cybergang operations:
Command and control server Hash First seen File name/Social engineering lure
upgrade.newshelpyou[.]com 552796e71f7ff304f91b39f5da46499b 25-07-2017 nvStView.exe
6fba58b9f9496cc52e78379de9f7f24e 23-03-2017 صور خاصة.exe
(Translation: Special photos)
eb521caebcf03df561443194c37911a5 03-04-2017 صور خاصة.exe
(Translation: Special photos)
moreoffer[.]life 66f144be4d4ef9c83bea528a4cd3baf3 27-05-2017 تصريح لأمير قطر واتهام الإمارات في اختراق وكالة الأنباء.exe
(Translation: A statement by the Emir of Qatar accusing the UAE of breaking the news agency)
3ff60c100b67697163291690e0c2c2b7 11-05-2017 MOM.InstallProxy.exe
b7390bc8c8a9a71a69ce4cc0c928153b 05-04-2017 تعرف على المنقبة التي أساءت للسعودية
(Translation: Learn about the woman wearing niqab which offended Saudi)
f43188accfb6923d62fe265d6d9c0940 21-03-2017 Gcc-Ksa-uae.exe
056d83c1c1b5f905d18b3c5d58ff5342 16-03-2017 مراسلة بخصوص اجتماع رؤساء البعثات.exe
(Translation: Correspondence regarding the meeting of Heads of Missions)
138.68.242[.]68 87a67371770fda4c2650564cbb00934d 20-06-2017 hamas.doc
نقاط اتفاق حماس وتيار فتح الاصلاحي.doc (Translation: the points of agreement between Hamas and the reformist Fateh movement)
محضر اجتماع مركزية فتح الليلة.doc (Translation: minutes of the tonight meeting)
سلفة أم راتب للموظفين يوم الثلاثاء المقبل؟.doc (Translation: An advance on salary or full salary for employees next Tuesday?)
lol.mynetav[.]org 4f3b1a2088e473c7d2373849deb4536f 20-06-2017 Notepad.exe
attachment.scr
https://drive.google.com/uc?export=download&id=0B1NUTMCAOKBTdVQzTXlUNHBmZUU
signup.updatesforme[.]club 7d3426d8eb70e4486e803afb3eeac14f 04-05-2017 Palestinian Retirement Authority Ramallah.exe
0ee4757ab9040a95e035a667457e4bc6 27-04-2017 27-4-2017 Fateh Gaza plo.exe
ping.topsite[.]life b68fcf8feb35a00362758fc0f92f7c2e 19-03-2017 Downloaded by Macro in MDB files:
http://download.data-server.cloudns[.]club/indexer.exe
7bef124131ffc2ef3db349b980e52847 13-03-2017 الأخ اسماعيل هنية -نائب رئيس المكتب السياسي .exe
(Translation: Brother Ismail Haniyeh – Deputy Head of the Political Bureau)
d87c872869023911494305ef4acbd966 19-03-2017 Downloaded by Macro in MDB files: http://download.data-server.cloudns[.]club/wordindexer.exe
a3de096598e3c9c8f3ab194edc4caa76 12-04-2017 viewimages.exe
c078743eac33df15af2d9a4f24159500 28-03-2017 viewimages.exe
70d03e34cadb0f1e1bc6f4bf8486e4e8 30-03-2017 download-file.duckdns[.]org/send/Egyptian_agreement_with_President_Mahmoud_Abbas.exe
67f48fd24bae3e63b29edccc524f4096 17-04-2017 http://alasra-paper.duckdns[.]org/send/رسالة_وفد_الرئيس ابومازن_لحماس_في قطاع_غزة.rar
(Message from President Abu Mazen to Hamas in Gaza Strip)
7b536c348a21c309605fa2cd2860a41d 17-04-2017 http://alasra-paper.duckdns[.]org/send/ورقة_الاسرى_المقدمة_لفك_الاضراب .rar
(Translation: captives paper submitted to stop the strike)
alasra-paper.duckdns[.]org Mobile malware N/A 23-04-2017 Possible Android malware. http://alasra-paper.duckdns[.]org/send/%D9%88%ket-Edition-1.04_ApkHouse.com/Dont-Starve-Pocket-Edition-1.04_ApkHouse.com.apk
hamas-wathaq.duckdns[.]org cf9d89061917e9f48481db80e674f0e9 16-04-2017 وثائق تنشر لأول مره عن حكم حماس لقطاع غزه .exe
(Translation: Documents published for the first time on Hamas ruling of Gaza Strip)
manual.newphoneapp[.]com 86a89693a273d6962825cf1846c3b6ce 02-02-2017 SQLiteDatabaseBrowserPortable.exe
3f67231f30fa742138e713085e1279a6 02-02-2017 SQLiteDatabaseBrowserPortable.exe
The above listed files are further described in Appendix 1.
4. New findings
Gaza Cybergang attackers have been continuously evolving their skills on different levels, using new methods and techniques to deliver malware, in addition to adapting social engineering decoys to regional political and humanitarian incidents.
In mid-2017, the attackers were discovered inside an oil and gas organization in the MENA region, infiltrating systems and pilfering data, apparently for more than a year. The malware files that were found had been reported previously: https://securelist.com/gaza-cybergang-wheres-your-ir-team/72283/
While traces of Android mobile malware have been spotted, attackers have continuously used the Downeks downloader and the Quasar or Cobaltstrike RATs to target Windows devices, enabling them to obtain remote access spying and data exfiltration abilities. This is now achieved more efficiently using the CVE 2017-0199 vulnerability which enables direct code execution abilities from a Microsoft office document on non-patched victim Windows systems. The use of Microsoft Access database files has also enabled the attackers to maintain low levels of detection, as it’s not an uncommon method to deliver malware.
These developments have helped the attackers continue their operations, targeting a variety of victims and organizations, sometimes even bypassing defences and persisting for prolonged periods.
4.1. The extended use of humanitarian and political causes in social engineering attacks
Attackers have continuously targeted victims and organizations in government entities/embassies, oil and gas, media/press, activists, politicians, and diplomats.
The Gaza cybergang relies increasingly on advanced and up-to-date social engineering techniques with political and humanitarian aspects that directly reflect regional incidents. Here is a short list of incidents that were each used multiple times:
Palestinian Government not paying salaries to Gaza employees
Palestinian prisoners’ hunger strike in Israeli jails
The political crisis in Qatar
Recent targets for the group seem to be varied in nature, the attackers do not appear to be choosing targets selectively, but rather seeking any type of intelligence.
4.1.1. Example lure
MD5: 66f144be4d4ef9c83bea528a4cd3baf3
تصريح لأمير قطر واتهام الإمارات في اختراق وكالة الأنباء.exe
(Translation: A statement by the Emir of Qatar accusing the UAE of breaking the news agency)
Attackers have recently used political events related to the Qatar political crisis in the Middle East in targeting their victims.
Original filename: Qatar-27-5-2017.rar
Extracts to 66f144be4d4ef9c83bea528a4cd3baf3
تصريح لأمير قطر واتهام الإمارات في اختراق وكالة الأنباء.exe
Sha256 7fcac2f18a8844e4af9f923891cfb6f637a99195a457b6cdb916926d709c6a04
C2: moreoffer[.]life
First seen: 27 May 2017
Translation: new details on the hack of the Qatar News Agency
4.2. The use of Microsoft Access files with macros
Microsoft Access files with macro is another new development by the attacker group. MS Access database-embedded macros are proving to have very low detection rates.
MD5: 6d6f34f7cfcb64e44d67638a2f33d619
Filename: GAZA2017.mdb
C1: http://download.data-server.cloudns[.]club/GAZA2017.mdb
Downloads and executes:
data-server.cloudns[.]club/wordindexer.exe
data-server.cloudns[.]club/indexer.exe
Translation: database of employees not receiving salaries, click “enable content” to see data
Decrypted code
4.3. Exploitation of the CVE 2017-0199 vulnerability
MD5: 87a67371770fda4c2650564cbb00934d
First seen: 20-06-2017
Filenames:
doc
نقاط اتفاق حماس وتيار فتح الاصلاحي.doc (Translation: the points of agreement between Hamas and the reforment Fateh movement)
محضر اجتماع مركزية فتح الليلة.doc (Translation: minutes of the tonight Fateh meeting)
سلفة أم راتب للموظفين يوم الثلاثاء المقبل؟.doc (Translation: An advance on salary or full salary for employees next Tuesday?)
The attacks are a typical exploitation of CVE-2017-0199, starting with an email that distributes a malicious RTF document. The vulnerability is in the code that handles Ole2Link embedded objects, which allows Microsoft Office Word to run remote files, downloaded in this case from 138.68.242[.]68. The downloaded payload is Cobaltstrike, which then connects to lol.mynetav[.]org to receive commands from the attackers. Additional details on the Gaza cybergang’s use of CVE 2017-0199 with Cobaltstrike, can be found here: http://bobao.360.cn/learning/detail/4193.html
4.4. Possible Android mobile malware
Traces of APK files have been seen on one of the attackers’ command centers, starting from 23-04-2017.
URL: http://alasra-paper.duckdns[.]org/send/%D9%88%ket-Edition-1.04_ApkHouse[.]com/Dont-Starve-Pocket-Edition-1.04_ApkHouse[.]com.apk
The file name (Dont-Starve-Pocket-Edition-1.04_ApkHouse[.]com.apk), is an Android application file hiding as a popular game. We believe the android Trojan could be related to a previously investigated Android Trojan around the Gaza strip: https://securelist.com/breaking-the-weakest-link-of-the-strongest-chain/77562/
5. Conclusion
The Gaza Cybergang has demonstrated a large number of attacks and advanced social engineering, in addition to active development of attacks, infrastructure and the utilization of new methods and techniques. Attackers are actively improving their toolkit in an effort to minimize their exposure to security products and services. Kaspersky Lab expects these types of attacks to intensify in the near term, both in terms of quality and quantity.
In order to protect your company from malware, Kaspersky Lab researchers recommend implementing the following measures:
Educate staff to be able to distinguish spear-phishing emails or a phishing link from legitimate emails and links
Use proven corporate grade security solution in combination with anti-targeted attacks solutions capable of catching attacks by analyzing network anomalies
Provide security staff with access to the latest threat intelligence data, which will arm them with helpful tools for targeted attacks prevention and discovery, such as indicators of compromise and YARA rules
Make sure enterprise grade patch management processes are well established and executed.
More information about Gaza cybergang is available to customers of Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
6. Appendix 1: malware files description and decoys
In the following, we list the description of malware files found from March 2017, including decoys used, first dates files seen, parent files…
6.1. b7390bc8c8a9a71a69ce4cc0c928153b
Parent file: 970e6188561d6c5811a8f99075888d5f 5-4-2017.zip
C2: moreoffer[.]life
First seen: 5 April 2017
Translation: Get to know the women wearing niqab and talking bad about the kingdom
6.2. f43188accfb6923d62fe265d6d9c0940
Filename: Gcc-Ksa-uae.exe
C2: moreoffer[.]life (185.11.146[.]68)
First Seen: 21 March 2017
Translation: the permanent delegation of the cooperation council for the Arab states of the Gulf (GCC) to the United Nation and other international organizations, Geneva
6.3. 056d83c1c1b5f905d18b3c5d58ff5342
مراسلة بخصوص اجتماع رؤساء البعثات.Filename: exe
Translation: Correspondence regarding the meeting of Heads of Missions (Saudi related)
Parent file: fb549e0c2fffd390ee7c4538ff30ac3e
C2: moreoffer[.]life
First Seen: 16 March 2017
Translation: The fourth foreign meeting of the Kingdom’s head of missions under the title “message of the embassador”.
6.4. 0ee4757ab9040a95e035a667457e4bc6
Filename: 27-4-2017 Fateh Gaza plo.exe
C2: signup.updatesforme[.]club
First seen 27 April 2017
Translation: Clarification report
6.5. 7bef124131ffc2ef3db349b980e52847
الأخ اسماعيل هنية -نائب رئيس المكتب السياسي .exe
(Translation: Brother Ismail Haniyah – Deputy Head of the Political Bureau)
C2: ping.topsite[.]life
First seen: 14 March 2017
Translation: Brother Ismail Haniyah – Deputy Head of the Political Bureau
6.6. 70d03e34cadb0f1e1bc6f4bf8486e4e8
download-file.duckdns[.]org/send/Egyptian_agreement_with_President_Mahmoud_Abbas.exe
C1: download-file.duckdns[.]org
C2: ping.topsite[.]life
First seen: 30 March 2017
Translation: methods to apply the palestinian national agreement pact.
6.7. 67f48fd24bae3e63b29edccc524f4096
C1: http://alasra-paper.duckdns[.]org/send/رسالة_وفد_الرئيس ابومازن_لحماس_في قطاع_غزة.rar
C2: ping.topsite[.]life
RAR extracts to: 5d74487ea96301a933209de3d145105d
رسالة_وفد_الرئيس ابومازن_لحماس_في قطاع_غزة.exe
First seen: 17 April 2017
Translation: a severely threatening message from Abbas’s delegation to Hamas
6.8. 7b536c348a21c309605fa2cd2860a41d
C1: http://alasra-paper.duckdns[.]org/send/ورقة_الاسرى_المقدمة_لفك_الاضراب .rar
Extracts to: d973135041fd26afea926e51ce141198, named (RTLO technique):
ورقة الاسرى المقدمة لفك الاضراب .exe
Translation: captives paper submitted to stop the strike
C2:ping.topsite[.]life
First seen: 17 April 2017
Translation: The primary demands of the captives in the strike of freedom and dignity
6.9. cf9d89061917e9f48481db80e674f0e9
وثائق تنشر لأول مره عن حكم حماس لقطاع غزه .exe c11516cd8c797f0182d63cdf343d08ed
Translation: Documents published for the first time on Hamas ruling of Gaza Strip
C1: http://hamas-wathaq.duckdns[.]org/send/وثائق_تنشر_لأول_مره_عن_حكم_حماس_لقطاع_غزه.rar
C2:ping.topsite[.]life
First seen: 16 April 2017
Translation: Scandals and facts published for the first time on Hamas’s ruling of Gaza Strip
7. Appendix 2: List of IOCs
7.1. Malicious domain names
moreoffer[.]life
signup.updatesforme[.]club
ping.topsite[.]life
alasra-paper.duckdns[.]org
hamas-wathaq.duckdns[.]org
download.data-server.cloudns[.]club
upgrade.newshelpyou[.]com
manual.newphoneapp[.]com
hnoor.newphoneapp[.]com
lol.mynetav[.]org
7.2. IP addresses
138.68.242[.]68
185.86.149[.]168
185.11.146[.]68
45.32.84[.]66
45.32.71[.]95
107.161.27[.]158
46.246.87[.]74
7.3. Hashes
MD5
87a67371770fda4c2650564cbb00934d
4f3b1a2088e473c7d2373849deb4536f
c078743eac33df15af2d9a4f24159500
3ff60c100b67697163291690e0c2c2b7
a3de096598e3c9c8f3ab194edc4caa76
7d3426d8eb70e4486e803afb3eeac14f
3f67231f30fa742138e713085e1279a6
552796e71f7ff304f91b39f5da46499b
6fba58b9f9496cc52e78379de9f7f24e
eb521caebcf03df561443194c37911a5
b68fcf8feb35a00362758fc0f92f7c2e
d87c872869023911494305ef4acbd966
66f144be4d4ef9c83bea528a4cd3baf3
B7390bc8c8a9a71a69ce4cc0c928153b
F43188accfb6923d62fe265d6d9c0940
056d83c1c1b5f905d18b3c5d58ff5342
0ee4757ab9040a95e035a667457e4bc6
7bef124131ffc2ef3db349b980e52847
70d03e34cadb0f1e1bc6f4bf8486e4e8
67f48fd24bae3e63b29edccc524f4096
7b536c348a21c309605fa2cd2860a41d
cf9d89061917e9f48481db80e674f0e9
6d6f34f7cfcb64e44d67638a2f33d619
86a89693a273d6962825cf1846c3b6ce
5472d0554a0188c0ecebd065eddb9485
SHA256
0b6fe466a3ba36895208e754b155a193780c79ba8b5c1c9f02c4f7e479116e5f
0c4aa50c95c990d5c5c55345626155b87625986881a2c066ce032af6871c426a
0d235478ae9cc87b7b907181ccd151b618d74955716ba2dbc40a74dc1cdfc4aa
1f2b128d26a58a572ea1faee2c4d9dc759eb8add16d9ad0547b3f0305fea212a
205f32cc717c2d82baeff9ff5aa9fc31967b6ae5cde22fafe14aec9c9ec62acc
284af7a2fafdbff3bbc28b9075f469d2352758b62d182b0e056d29ee74688126
344dc6ece5a6dacce9050a65305d4b34865756051a6f414477b6fa381e1c1b63
42e4298f5162aba825309673187e27121e3f918238e81f3a6e021c03f3455154
44a8d0561a9cc6e24d6935ff4c35b7b7db50c4001eb01c48ea1cfd13253bc694
57a12f20c6bbd69b93e76d6d5a31d720046b498aa880b95b85a4f3fda28aac4f
72b039550d31afaeee11dedf7d80333aeda5c504272d426ae0d91bc0cd82c5b0
72d2ad8f38e60c23c96698149507fc627664a5706a4431b96014fbf25495b529
788f7fd06030f87d411c61efbc52a3efca03359570353da209b2ce4ccf5b4b70
7fcac2f18a8844e4af9f923891cfb6f637a99195a457b6cdb916926d709c6a04
84adba3c81ad1c2a8285c31d1171f6f671492d9f3ed5ee2c7af326a9a8dc5278
852ccc491204f227c3da58a00f53846296454d124b23021bdb168798c8eee2fb
86bd78b4c8c94c046d927fb29ae0b944bf2a8513a378b51b3977b77e59a52806
9347a47d63b29c96a4f39b201537d844e249ac50ded388d66f47adc4e0880c7e
b597d7b5b9c2f1962257f912e911961ad0da4c28fc6a90a0b7db4e242aa007d8
bfb88878a22c23138a67cc25872e82d77e54036b846067ddc43e988c50379915
c23f715c8588c8d8725352ed515749389d898996107132b2d25749a4efc82a90
c47bc2c15f08655d158bb8c9d5254c804c9b6faded526be6879fa94ea4a64f72
db53b35c80e8ec3f8782c4d34c83389e8e9b837a6b3cc700c1b566e4e4450ec2
dd9debe517717552d7422b08a477faa01badbcc4074830c080a1a1c763e1a544
b800d29d6e1f2f85c5bc036e927c1dae745a3c646389599b0754592d76b5564b