
Google launched Google Play Security Reward bug bounty program to protect apps in Play Store
20.10.2017 securityaffairs Android
Google has launched Google Play Security Reward, the bug bounty program that will pay $1,000 rewards for flaws in popular apps.
Google has officially launched a bug bounty program for Android apps on Google Play Store, a measure that aims to improve the security of Android apps. The initiative, called Google Play Security Reward, will involve the security community in finding and reporting vulnerabilities in some of the most popular Android apps available in the official store.
The Google Play Security Reward offers security researchers to work directly with Android app developers to find and fix security issues in their applications, the experts will receive $1000 in rewards.
“The Google Play Security Reward Program recognizes the contributions of security researchers who invest their time and effort in helping us make apps on Google Play more secure. ” read a blog post published by Google.
“All Google’s apps are included and developers of popular Android apps are invited to opt-in to the program. Interested developers who aren’t currently in the program should discuss it with their Google Play partner manager. Through the program, we will further improve app security which will benefit developers, Android users, and the entire Google Play ecosyste“
The Google Play Security Reward Program is operated in collaboration with the bug bounty platform HackerOne.
Everyone that wants to participate the bug bounty program can submit his/her findings directly to the app development team. Once the vulnerability has been fixed, the expert only needs to submit his/her bug report through the HackerOne platform.

According to the Google Vulnerability Criteria, the experts will receive their $1,000 rewards. Currently, the program is focused on finding RCE (remote-code-execution) vulnerabilities and related exploit codes that work on Android 4.4 devices and higher. An attacker must to able to run arbitrary code on a user’s device without user knowledge or interaction.
“All vulnerabilities must be reported directly to the app developer first. Only submit issues to the Play Security Rewards Program that have already been resolved by the developer.” reads the announcement published on the HackerOne.
“For now, the scope of this program is limited to RCE (remote-code-execution) vulnerabilities and corresponding POCs (Proof-of-concepts) that work on Android 4.4 devices and higher.”
Recently, security experts reported numerous cases of malicious apps deployed on the Google Play store that infected millions of Android users.
The Google Play Security Reward program does not include reporting fake or bogus apps available on Google play store, this means that it will not allow limiting the number of malicious applications in the official store.
At the time, only a few Android apps have been added to Google Play Security Reward Program, including Alibaba, Snapchat, Duolingo, Line, Dropbox, Headspace, Mail.ru and Tinder.
URSNIF spam campaign expose new macro evasion tactics
20.10.2017 securityaffairs Spam
Trend Micro recently observed a new campaign leveraging the Ursnif banking Trojan using new malicious macro tactics payload delivery and evade detection.
Researchers at Trend Micro have recently spotted a new campaign leveraging the Ursnif banking Trojan featuring new malicious macro tactics for payload delivery.
Malicious macros are widely adopted by crooks for malware distribution, usually, they are embedded in documents and attackers trick victims into enabling them. Then the malicious code (i.e. PowerShell) is executed to drop and run the final malware.

Unfortunately, cybercriminals continue to improve the effectiveness of macros tactics in the attempt to evade detection.
Recently, in spam email distributing URSNIF, the researchers observed the malware was using simple checks to evade sandbox detections.
One the tactic used by threat actors is the use of AutoClose, which can run the PowerShell script after the document was closed, evading sandbox detections focused on the analysis of the macro itself.
“This method is becoming a common feature in many malicious macros because it is easy to implement.” reads the analysis from Trend Micro.
“After coercing the victim to enable macros, the macro waits for the would-be victim to close the document and only then will PowerShell execute. Sandbox detections might miss the malicious behavior since the malicious routines will only run after the document is closed.”
Another tactic relies on enumeration variables which allow attackers to determine the Office version by comparing them to certain values.
Microsoft Office provides users several enumeration variables for its macros containing predefined values, but some enumerations are only present in later versions making possible the check of the office version.
The tactic allows the attacker to avoid using the macro for certain Office versions, like Office 2007.
Another sandbox evasion tactic is based on the filename check in the macro. When automating the analysis of a file in a sandbox, the file is sometimes renamed to its MD5, SHA-1 or SHA-256 equivalent. The attackers check the filename length in the VBScript before triggering the malicious action. In presence of long filename that could reveal the use of a sandbox, the macro will not execute the malicious routines to evade detection.
All the techniques observed by the experts use PowerShell scripts to download and execute the final payload. In all cases analyzed by the researchers, the final payload was a variant of the Ursnif Trojan.
“Most of the samples analyzed have one thing in common—they run PowerShell script that downloads and executes another malware. For the samples we analyzed, the malware downloaded is a variant of the URSNIF malware (detected by Trend Micro as TSPY_URSNIF).” concluded Trend Micro
“However, these are not unique to one malware; it is possible that others may be downloaded. As malware and their delivery methods continue to evolve, security must be updated as well.”
Google Play Store Launches Bug Bounty Program to Protect Popular Android Apps
20.10.2017 thehackernews Android
Better late than never.
Google has finally launched a bug bounty program for Android apps on Google Play Store, inviting security researchers to find and report vulnerabilities in some of the most popular Android apps.
Dubbed "Google Play Security Reward," the bug bounty program offers security researchers to work directly with Android app developers to find and fix vulnerabilities in their apps, for which Google will pay $1000 in rewards.
"The goal of the program is to further improve app security which will benefit developers, Android users, and the entire Google Play ecosystem," the technology giant says in a blog post published today.
Google has collaborated with bug bounty platform, HackerOne, to manage backend for this program, like submitting reports and inviting white-hat hackers and researchers.
White-hat hackers who wish to participate can submit their findings directly to the app developers. Once the security vulnerability has been resolved, the hacker needs to submit his/her bug report to HackerOne.
Google will then pay out a reward of $1,000 based on its Vulnerability Criteria, wherein, according to the company, more criteria may be added in the future, creating more scope for rewards.
"All vulnerabilities must be reported directly to the app developer first. Only submit issues to the Play Security Rewards Program that have already been resolved by the developer." HackerOne said.
"For now, the scope of this program is limited to RCE (remote-code-execution) vulnerabilities and corresponding POCs (Proof-of-concepts) that work on Android 4.4 devices and higher."
It is an unfortunate truth that even after so many efforts by Google, malicious apps continuously somehow managed to fool its Play Store's security mechanism and infect millions of Android users.
It's notable that Google Play Security Reward program does not include finding and reporting fake, adware or malware apps available on Google play store, so the program will not affect the increase in malicious apps on Google's app platform.
For now, a limited number of Android apps have been added to Google Play Security Reward Program, including Alibaba, Snapchat, Duolingo, Line, Dropbox, Headspace, Mail.ru and Tinder.
So what you are waiting for?
Roll up your sleeves and start hunting for vulnerabilities. For more details about Google Play Security Reward Program, visit HackerOne.
Enable Google's New "Advanced Protection" If You Don't Want to Get Hacked
20.10.2017 thehackernews Security
It is good to be paranoid when it comes to cybersecurity.
Google already provides various advanced features such as login alerts and two-factor authentication to keep your Google account secure.
However, if you are extra paranoid, Google has just introduced its strongest ever security feature, called "Advanced Protection," which makes it easier for users, who are usually at high risk of targeted online attacks, to lock down their Google accounts like never before.
"We took this unusual step because there is an overlooked minority of our users that are at particularly high risk of targeted online attacks," the company said in a blog post announcing the program on Tuesday.
"For example, these might be campaign staffers preparing for an upcoming election, journalists who need to protect the confidentiality of their sources, or people in abusive relationships seeking safety."
Even if a hacker somehow gets your password—using advanced phishing attacks, zero-day exploits or spyware—and tries to access your Google account, they will not be able to get in.
To enable Google's Advanced Protection feature, you will need two physical security keys that work with FIDO Universal 2nd Factor (U2F)—which offers a hardware-based two-factor authentication that does not require secret codes via SMS or emails.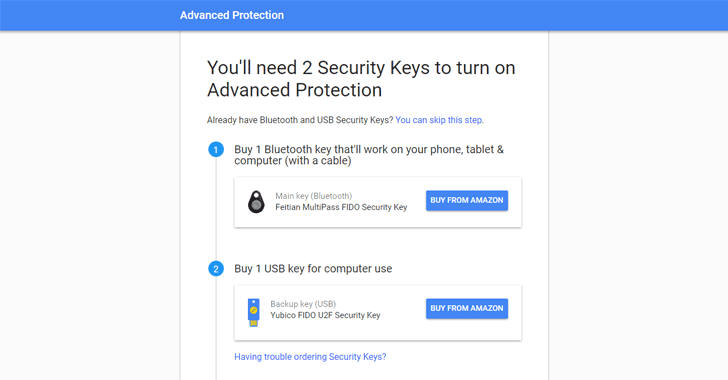
To log into your Google account from a computer or laptop will require a special USB stick while accessing from a smartphone or tablet will similarly require a Bluetooth-enabled dongle, paired with your phone.
"They [security devices] use public-key cryptography and digital signatures to prove to Google that it's really you," the post reads. "An attacker who does not have your Security Key is automatically blocked, even if they have your password."
Google's Advanced Protection offer three features to keep your account safe:
Physical Security Key: Signing into your account requires a U2F security key, preventing other people (even with access to your password) from logging into your account.
Limit data access and sharing: Enabling this feature allows only Google apps to get access to your account for now, though other trusted apps will be added over time.
Blocking fraudulent account access: If you lose your U2F security key, the account recovery process will involve additional steps, "including additional reviews and requests for more details about why you've lost access to your account" to prevent fraudulent account access.
Advanced Protection feature is not designed for everyone, but only for people, like journalists, government officials and activists, who are at a higher risk of being targeted by government or sophisticated hackers and ready to sacrifice some convenience for substantially increased e-mail protection.
Currently, if you want to enrol in the Advanced Protection Program, you will need Google Chrome, since only Chrome supports the U2F standard for Security Keys. However, the technology expects other browsers to incorporate this feature soon.
Google Adds ESET Malware Detection to Chrome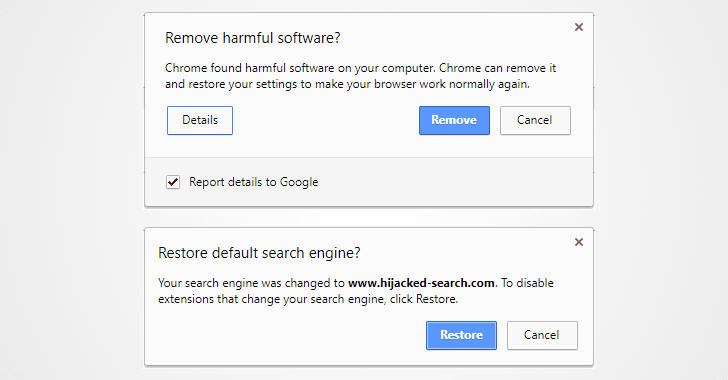
Google has also made a notable change by partnering with anti-virus software firm ESET to expand the scope of malware detection and protection in its browser through the Chrome Cleanup feature.
Chrome Cleanup now has a malware detection engine from ESET, which works in tandem with Chrome's sandbox technology.
"We can now detect and remove more unwanted software than ever before, meaning more people can benefit from Chrome Cleanup," Google said in a blog post published Monday.
"Note this new sandboxed engine is not a general-purpose antivirus—it only removes software that doesn’t comply with our unwanted software policy."
You can sign-up for Google's Advanced Protection here.
G7 to Put Squeeze on Internet Giants at Terror Talks
20.10.2017 securityweek BigBrothers
Tech giants including Google, Facebook and Twitter will come under pressure in Italy this week to go further and faster in helping G7 powers tackle the ever-greater threat of extremists online.
A two-day meeting of Group of Seven interior ministers, which kicks off on the Italian island of Ischia on Thursday, comes just days after US-backed forces took full control of Raqa in Syria, which had become a byword for atrocities carried out by the Islamic State group.
Despite the breakthrough in the battle against IS, the head of Britain's domestic intelligence service said Tuesday that the UK was facing its most severe terrorist threat ever, particularly due to the spread of jihadist material online.
MI5 head Andrew Parker said attacks could now accelerate rapidly from inception to action, and "this pace, together with the way extremists can exploit safe spaces online, can make threats harder to detect".
In a first for a G7 meeting, representatives from Google, Microsoft, Facebook and Twitter will take part in the talks between the seven ministers from Britain, Canada, France, Germany, Italy, Japan and the United States.
"The internet plays a decisive role in radicalization. Over 80 percent of conversations and radicalisation happen online," said Italy's Marco Minniti, who is hosting the summit on the volcanic island off Naples.
- 'Wake up' -
"We need to study a system for automatically blocking specific content. IS contaminated the web with a 'terror malware'. The providers need to help us block this malware with an automatic antivirus," Minniti said.
"We don't want to impose anything, success will rely on us having a collaborative spirit," he added.
In June, Facebook, Microsoft, Twitter and YouTube announced the launch of an anti-terror partnership, the "Global Internet Forum to Counter Terrorism", aimed at thwarting the spread of extremist content online.
Facebook has launched campaigns in Belgium, Britain, France and Germany to develop "best practices".
And in September, Twitter touted victories in the battle against tweets promoting extremist violence, saying it has been vanquishing those kinds of accounts before governments even ask.
But last month top Western counter-terror chiefs said they need more support from social media companies to detect potential threats, particularly with jihadist attacks increasingly being carried out by home-grown "lone wolves".
Tough privacy laws and protections enjoyed by the largely US-based web giants are impeding authorities, they said.
Some firms are using software aimed at helping them quickly find and eliminate extremist content, developed by Dartmouth College computer science professor Hany Farid, a senior advisor to the US Counter Extremism Project.
But Farid told AFP it was unclear how broadly it was being deployed and urged the G7 to "give serious consideration to legislative relief" if the tech giants fail to "wake up and respond more aggressively" to abuses of their systems.
- Dark web vs 'likes' -
While some warn terror online will be difficult to conquer, with extremists simply moving onto the dark web, Italian expert Marco Lombardi said jihadists would not readily give up the mass-audience potential of social media.
Opportunities for "conversion, propaganda and dissemination" lie "on sites capable of influencing thousands of youngsters with a few 'likes'," said Lombardi, director of the research centre ITSTIME (Italian Team for Security, Terrorist Issues & Managing Emergencies).
The British government has outlined an internet safety strategy with proposals it will likely share with fellow G7 members, including an attempt to persuade leading web players to pay for measures to combat dangers.
While Germany has focused particularly on defending itself from cyber attacks, it launched the ZITis surveillance agency last month, which will specialise in "digital forensics" as part of its strategy to fight terrorism.
For its part, despite being labelled an enemy by IS, Japan has escaped attacks to date. Nevertheless, in June its lawmakers passed a controversial bill allowing authorities to target terror conspiracies.
BoundHook Hooking Is Invisible to Windows 10's PatchGuard
20.10.2017 securityweek Security
A newly discovered hooking technique can go completely undetected by the current implementation of PatchGuard, CyberArk security researchers warn.
Called BoundHook, the method relies on causing an exception in a very specific location in a user-mode context, as well as on catching that exception to gain control over the thread execution. It can bypass PatchGuard, or Kernel Patch Protection, which was designed by Microsoft to prevent malicious code from running at kernel level on 64-bit versions of Windows.
Hooking is known to provide control over the operating system or applications, and both legitimate and malicious programs can leverage it. The newly discovered method can be used in post-exploitation scenarios where the attacker has already established control over the system.
BoundHook uses the BOUND instruction, which is part of Intel MPX (Memory Protection Extensions) and which was designed to increase software security by checking pointer references susceptible to malicious exploitation at runtime due to memory corruption vulnerabilities.
Because Intel designed it to generate a fault to allow examination of the bound check failure, the BOUND instruction “checks an array index against bounds and raises software interrupt 5 if the test fails,” CyberArk explains. When a bound fault occurs, registered bounds-exception callback routines are executed.
Kernel-mode drivers and shellcode payloads running in kernel-mode are able to register callback routines for bound faults. With no parameters, such a callback routine should return a BOUND_CALLBACK_STATUS.
The researchers also explain that, after the bound fault registration, the kernel-mode code gets a pointer to the user-mode DLL base address. Then it obtains the address of the function to hook, after which it attempts to start writing to that address.
To perform this operation as stealthily as possible and avoid triggering the COW (copy-on-write) protection, one could either manipulate the CR0 register or allocate their “own memory descriptor list (MDL) to describe the memory pages and adjust permissions on the MDL”. The latter method, CyberArk says, is stealthier and “completely invisible by design to the current PatchGuard implementation.”
The security researchers also explain that, writing directly to a DLL’s COW page allows them to hook every process on the system that uses the specific DLL. By setting the kernel-mode code performing the hooking to write the code to a function’s prologue, the researchers’ kernel-mode callback function could take control of the thread when user-mode thread called that function.
Because the hooked page will still be COW, the performed modifications won’t be visible to anti-malware solutions, especially with most anti-virus makers unaware of the new method. Furthermore, user-mode debuggers can’t catch the hook, because “BoundHook’s method traps the execution flow by the kernel bound faults handler.”
“This method is invisible to most PatchGuard (PG) protection mechanisms. The MDL approach to bypass the COW mechanism is not detectable by PG today by design. As for the CR0 modification approach, although the CR0 is protected by PG, since it is modified for a very short period of time, the chance of being caught by PG is minimal,” the security researchers argue.
CyberArk says that BoundHook does not meet Microsoft’s requirements to be considered a security vulnerability, given that machine administrator rights need to be obtained for this method to work.
The researchers were in a similar situation earlier this year, when they disclosed GhostHook, an attack targeting Windows 10’s PatchGuard and able to bypass it and hook a malicious kernel code (rootkit). At the time, Microsoft revealed that the issue, although not a security vulnerability, may be addressed in a future version of Windows.
Ursnif Trojan Uses New Malicious Macro Tactics
20.10.2017 securityweek Virus
Recently observed distribution campaigns featuring the Ursnif banking Trojan were using new malicious macro tactics for payload delivery, Trend Micro has discovered.
Malicious macros have been used for over a decade for malware distribution, and have become highly popular among cybercriminals over the past several years, despite Microsoft’s efforts to block them. They are used to drop all types of malware, including banking malware, ransomware, spyware, and backdoors.
The normal infection chain when malicious macros are used involves tricking the victim into enabling the macro in the document received via spam email. Next, malicious code (usually PowerShell) is executed to download and run the final payload.
The effectiveness of macros as a delivery method inspires miscreants to continue to use the technique and improve it, in an attempt to evade detection and hinder analysis. Ursnif’s operators have already shown a focus on evading sandbox detection, and recently adopted checks that allow them to do so.
One employed tactic is the use of AutoClose, which can run the PowerShell script after the document was closed, thus preventing detection that focuses on analyzing the macro itself. The method is easy to implement and Trend Micro says it is becoming a common feature in many malicious macros.
“After coercing the victim to enable macros, the macro waits for the would-be victim to close the document and only then will PowerShell execute. Sandbox detections might miss the malicious behavior since the malicious routines will only run after the document is closed,” the researchers say.
Another detection evasion technique involves enumeration variables, which allow attackers to check the Office version by comparing them to certain values, given that some of these variables are only present in later versions of Microsoft Office. One specific enumeration variable allows attackers to detect Office 2007, which is commonly used in sandboxes for automated analysis. Thus, if Office 2007 is detected, the macro won’t deploy.
Another sandbox evasion tactic involves the use of a filename check in the macro. This method is meant to counter sandboxes where the file is renamed to its MD5, SHA-1, or SHA-256 equivalent. Thus, if the script detects a long filename, the macro won’t execute the malicious routines.
The one thing that these samples had in common was the use of PowerShell scripts to download and execute the final payload. In all cases, that was a variant of the Ursnif Trojan, but other malware could also use them, the researchers admit.
“However, these are not unique to one malware; it is possible that others may be downloaded. As malware and their delivery methods continue to evolve, security must be updated as well. Users need to be protected with the latest solutions that can combat new and evolving threats,” Trend Micro concludes.
Cisco addresses a critical vulnerability in Cloud Services Platform (CSP)
20.10.2017 securityaffairs Vulnerebility
Cisco patched critical and high severity vulnerabilities in several products, including the Cloud Services Platform (CSP).
Cisco patched critical and high severity vulnerabilities in several products, including the Cloud Services Platform (CSP), the Firepower Extensible Operating System (FXOS) and NX-OS software, and some Small Business IP phones.
The most severe vulnerability patched in this round it the CVE-2017-12251, a critical unauthorized access flaw affecting the Cloud Services Platform 2100.
The Cloud Services Platform is used by many organizations to deploy Cisco and third-party network virtual services.
The vulnerability resides in the web console of the Cisco Cloud Services Platform (CSP) 2100 and could be exploited by a remote an authenticated attacker to interact maliciously with the services or virtual machines (VMs) on an affected CSP device.
“The vulnerability is due to weaknesses in the generation of certain authentication mechanisms in the URL of the web console. An attacker could exploit this vulnerability by browsing to one of the hosted VMs’ URLs in Cisco CSP and viewing specific patterns that control the web application’s mechanisms for authentication control.” reads the security advisory. “An exploit could allow the attacker to access a specific VM on the CSP, which causes a complete loss of the system’s confidentiality, integrity, and availability.”
The vulnerability affects the Cloud Services Platform 2100 versions 2.1.0, 2.1.1, 2.1.2, 2.2.0, 2.2.1 and 2.2.2. Cisco has addressed the vulnerability with the release of version 2.2.3.
According to Cisco, threat actors haven’t exploited the flaw in attacks in the wild.
“The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability that is described in this advisory.” continues the security advisory.

Cisco also notified customers of a high severity denial-of-service (DoS) vulnerability, tracked as CVE-2017-3883, that affects the authentication, authorization, and accounting (AAA) implementation of the FXOS and NX-OS software.
An attacker could exploit the vulnerability by powering a brute-force login attack against a device that is configured with AAA security services.
“A vulnerability in the authentication, authorization, and accounting (AAA) implementation of Cisco Firepower Extensible Operating System (FXOS) and NX-OS System Software could allow an unauthenticated, remote attacker to cause an affected device to reload.” reads the security advisory.
The vulnerability affects Firepower appliances, Nexus and Multilayer Director switches, and some Unified Computing System products.
Cisco also addressed two DoS vulnerabilities affecting the Small Business IP phones.
The first flaw, tracked as CVE-2017-12260 affects the Session Initiation Protocol (SIP) functionality in Cisco Small Business SPA50x, SPA51x and SPA52x series IP phones, while the second one tracked as CVE-2017-12259, affects the same feature in only SPA51x series phones.
Both flaws could be exploited by an unauthenticated attacker to trigger a DoS condition by sending specially crafted SIP requests to the targeted device.
Let’s close with a mention to the recently disclosed KRACK vulnerability that affects many Cisco products, the tech giant is already rolling out security patches for vulnerable devices, many others are under investigation.
Sockbot Ensnares Android Devices into Botnet
19.10.2017 securityweek BotNet
A newly discovered Android malware has the ability to add the compromised devices to a botnet that could potentially launch distributed denial-of-service (DDoS) attacks, Symantec warns.
Dubbed Sockbot, the highly prevalent threat was found masquerading as legitimate apps in Google Play. Symantec has discovered eight such applications and says that they have been downloaded between 600,000 and 2.6 million times.
The malware is mainly targeting users in the United States, but some of the infected devices are located in Russia, Ukraine, Brazil, and Germany, the security researchers say.
The applications hiding the malware were designed to modify the look of the characters in Minecraft: Pocket Edition (PE). In the background, however, they enable sophisticated and well-disguised attacking functionality.
The malicious app connects to a command and control (C&C) server on port 9001. The server requests the app to open a socket using SOCKS and wait for a connection, which arrives along with a command to connect to a target server.
After connecting to the target server, the application receives a list of ads and associated metadata. Through the SOCKS proxy mechanism, the app is also pointed to an ad server and commanded to launch ad requests. However, the security researchers discovered that the decoy app doesn’t include functionality to display ads.
“This highly flexible proxy topology could easily be extended to take advantage of a number of network-based vulnerabilities, and could potentially span security boundaries. In addition to enabling arbitrary network attacks, the large footprint of this infection could also be leveraged to mount a distributed denial of service (DDoS) attack,” Symantec reveals.
The infection campaign was tracked to a single developer account named FunBaster and each app was signed with a different developer key, likely in an attempt to avoid static analysis-based heuristics. The malicious code is also obfuscated and features encrypted key strings, thus thwarting base-level forms of detection.
Symantec informed Google on the presence of these malicious apps in the application store and the Internet giant has already removed them.
In August this year, security companies worked together to take down a large Android botnet. Called WireX, it was designed to launch DDoS attacks, and one variant was capable of launching high-volume UDP flood attacks, the researchers discovered.
DMARC Not Implemented by Most Federal Agencies: Report
19.10.2017 securityweek Security
The U.S. Department of Homeland Security (DHS) recently ordered all federal agencies to start using DMARC, but currently only a small percentage have fully implemented the system, according to a report from security firm Agari.
The DHS’s Binding Operational Directive (BOD) 18-01 orders all federal agencies to implement web and email security technologies such as HTTPS, DMARC, SPF/DKIM and STARTTLS in the coming months.
DMARC, which stands for “Domain-based Message Authentication, Reporting and Conformance”, is an authentication, policy, and reporting protocol designed to detect and prevent email spoofing. Organizations using DMARC can specify what happens to unauthenticated messages: they can be monitored but still delivered to the recipient’s inbox (“none” setting), they can be moved to the spam folder (“quarantine” setting), or their delivery can be blocked completely (“reject” setting).DMARC
Federal agencies have been given 90 days to roll out DMARC with at least a “none” setting. Within one year, they will have to fully implement the protocol to ensure that malicious emails are blocked.
Agari has used its DMARC Lookup Tool to check 1,300 domains owned by federal agencies and determined that nearly 82 percent lack DMARC entirely. Roughly nine percent have fully implemented the system (i.e. quarantine or reject), while the other nine percent only monitor emails (i.e. none).
Agari monitors 400 government domains and noticed that nearly 90 percent of them were targeted with fraudulent or unauthorized emails between April and October 2017. Of the more than 336 million emails apparently sent from these domains during that timeframe, more than 85 million, representing roughly a quarter of the total, failed authentication due to being fraudulent or for some other reason.
“DMARC has proven incredibly effective at combating phishing across billions of emails daily,” said Patrick Peterson, founder and executive chairman of Agari. “This DHS directive is an important step to protect our government, businesses and citizenry from cybercrime.”
“We would like to recognize Agari’s customers that pioneered DMARC in the federal government including the U.S. Senate, Health and Human Services, Customs and Border Protection, U.S. Census Bureau, Veterans Affairs and the U.S. Postal Service. We hope their leadership and experience serves as a resource for best practices among their government peers who are beginning this journey,” Peterson added.
Agari also recently analyzed the use of DMARC in Fortune 500, FTSE 100 and ASX 100 companies and found that many had failed to fully implement the standard.
New Magniber Ransomware Emerges
19.10.2017 securityweek Ransomware
A brand new ransomware family currently being distributed through the Magnitude exploit kit appears to be targeting South Korean users exclusively, security researchers have discovered.
Dubbed Magniber, the threat checks the language of the compromised systems and only fully executes on machines featuring the locale identifier string 0x0412, which is the identifier for Korean, Trend Micro reports.
The new malware family was first observed this week, when Magnitude returned to activity after nearly a month of silence. The EK was usually distributing the Cerber ransomware, but it appears that its operators have moved to other payloads.
While most of the Magnitude attacks over the past two months and a half focused on Taiwan (81%), the security researchers noticed a shift toward South Korea on October 15. Magnitude campaigns use malvertising to infect users and deliver malicious payloads by exploiting the Internet Explorer vulnerability CVE-2016-0189, which Microsoft patched in May 2016.
Magnitude was the last exploit kit to have delivered Cerber, which appears to have disappeared from the threat landscape last month. Now, the toolkit is pushing a ransomware family that apparently uses the same payment system as Cerber.
This is why the security researchers who discovered the threat called it Magniber (Magnitude+Cerber), although there doesn’t seem to be code base resemblance between the two, Bleeping Computer’s Lawrence Abrams notes.
Specific to the new malware is the fact that it uses the victim’s unique ID as a subdomain to the payment portal on Tor. This subdomain is then displayed in the ransom note deployed on the infected system.
Once on the infected system, the malware starts searching for files to encrypt. At the moment, it is targeting over 700 file types, Malwarebytes says. The ransomware avoids encrypting files located in folders such as Windows, Program Files, Boot, Recycle Bin, Local Settings, and several Documents and Settings subfolders, among others.
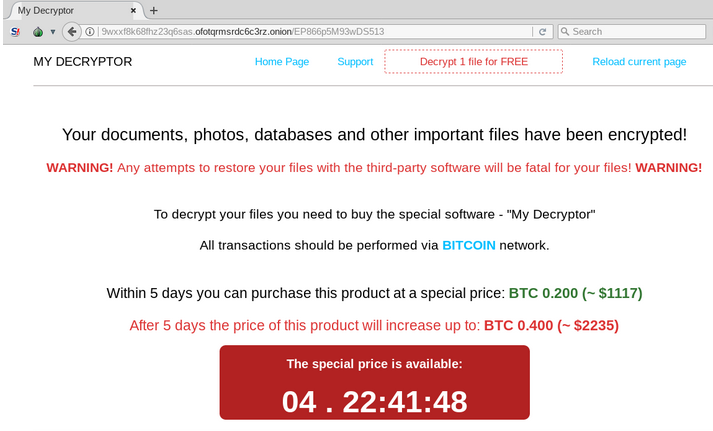
According to Trend Micro, Magniber’s code shows that the ransomware might still be under development. According to them, the threat could be still in experimental stages, supposedly built by Magnitude’s developers.
“Indeed, we’re bound to see more developments in both Magnitude and Magniber as their capabilities and tactics are fine-tuned. While Magnitude’s distribution of Magniber is still relatively muted, their ability to exploit security gaps in the system and encrypt its files makes their combination a credible threat,” the security researchers note.
According to Abrams, files encrypted by Magniber can be decrypted for free, so victims should refrain from paying the ransom. All users, however, are advised to keep their applications and operating systems updated at all times, and to install and maintain an anti-virus solution to avoid being infected in the first place. Users should also back up their data at all times, for easy recovery in the event of an infection.
Threat actors started scanning for SSH Keys on websites
19.10.2017 securityaffairs Hacking
Threat actors in the wild are mass-scanning websites for directories containing SSH private keys to hack them.
The SSH allows a secure way to connect to servers hosting the websites, it allows administrators to get a terminal on them and enter commands.
The SSH authentication could rely on login credentials (username and password), or on a “key-based” approach.
When using key-based authentication, users generate an encryption key pair, a public and private key. The public key is placed on the server users want to sign in to. The private key is saved by the users in a local SSH configuration directory.
“Wordfence is seeing a significant spike in SSH private key scanning activity.” warned the WordPress security firm. “If your private SSH key ever gets out, anyone can use it to sign in to a server where you have set up key-based authentication. It is very important to keep your private key safe.”
Threat actors are mass-scanning the web searching for web directories containing the terms, or combinations of terms, such as “root,” “ssh,” or “id_rsa.”
Researchers observed a spike in SSH Private Key scans in the past 48 hours.
“The graph shows a massive spike in scanning activity in the past 48 hours,” said Wordfence CEO Mark Maunder. “We think this increase of activity may indicate that an attacker is having some success scanning for private keys and has decided to increase their efforts. This may indicate a common bug or operational mistake that is being made by WordPress site owners, by which private keys are being accidentally made public.”

Recently the provider of identity protection services Venafi published a report that revealed that 61% of organizations have minimal control of SSH privileged access.
The company conducted a study among 410 IT security professionals and found “a widespread lack of SSH security controls.”
“Cybercriminals can abuse SSH keys to secure and automate administrator-to-machine and machine-to-machine access to critical business functions. According to Venafi’s research, even though SSH keys provide the highest levels of administrative access they are routinely untracked, unmanaged and poorly secured.” states the report.
Website administrators are advised to check if they haven’t accidentally uploaded their SSH private key on servers, or committed the SSH private key to Git or SVN repositories.
“Your SSH keys are usually kept in a private directory on your workstation. On Apple workstations, the keys are kept in the following directory:
/Users/<yourname>/.ssh/<key-filename>
On Windows workstations, the location where SSH keys are stored depends on which software you are using, so check your vendor documentation.” concluded Wordfence.
No Patches for Vulnerabilities in Linksys Wireless Routers
19.10.2017 securityweek Vulnerebility
IT security services and consulting company SEC Consult has disclosed the details of several apparently unpatched vulnerabilities affecting Linksys E-Series wireless home routers.
The flaws were reported to Linksys in July and while the vendor was initially responsive, it stopped answering SEC Consult’s emails in early September, when it said that patches for some of the vulnerable devices had been on their way to QA.
SecurityWeek has reached out to Belkin, the company that owns the Linksys brand, regarding the availability of patches, and will update this article if the company provides any information.Linksys router
According to an advisory published by SEC Consult, Linksys E900, E1200 and E8400 AC2400 routers have been confirmed to be vulnerable by the vendor. The security firm conducted its tests on an E2500 device, but it believes E900-ME, E1500, E3200, E4300 and WRT54G2 routers are affected as well.

Researchers have discovered a total of five types of vulnerabilities and proof-of-concept (PoC) examples have been made available for each of them. The flaws include denial-of-service (DoS), HTTP header injection, improper session protection, cross-site request forgery (CSRF), and cross-site scripting (XSS) issues.
SEC Consult’s analysis revealed that various combinations of these vulnerabilities can be exploited to cause a permanent DoS condition, redirect users to malicious websites, change a device’s configuration, and execute malicious code in the context of the victim’s browsing session.
The security firm has advised users to keep an eye out for the patches from Linksys and apply them as soon as they become available. In the meantime, users can prevent potential attacks by restricting network access to the device.
This is not the first time researchers have disclosed vulnerabilities in Linksys routers before patches were made available. Back in April, IOActive said it had found a total of 10 flaws in devices that support the Smart Wi-Fi feature. While patches had not been released, Linksys did provide some mitigation advice.
Cisco Patches Critical Flaw in Cloud Services Platform
19.10.2017 securityweek Vulnerebility
Cisco informed customers on Wednesday that it has patched critical and high severity vulnerabilities in several of its products, including the Cloud Services Platform (CSP), the Firepower Extensible Operating System (FXOS) and NX-OS software, and some Small Business IP phones.
The most serious of the patched flaws is CVE-2017-12251, a critical unauthorized access issue affecting CSP 2100, a platform that helps organizations deploy Cisco and third-party network virtual services.
Chris Day, senior security consultant at MWR InfoSecurity, discovered that the platform’s web console is affected by a flaw that allows an authenticated attacker to remotely interact with the services and virtual machines on a CSP device.
“The vulnerability is due to weaknesses in the generation of certain authentication mechanisms in the URL of the web console. An attacker could exploit this vulnerability by browsing to one of the hosted VMs' URLs in Cisco CSP and viewing specific patterns that control the web application's mechanisms for authentication control,” Cisco said in its advisory.
The vulnerability affects CSP 2100 versions 2.1.0, 2.1.1, 2.1.2, 2.2.0, 2.2.1 and 2.2.2. The issue has been resolved with the release of version 2.2.3, and Cisco says it’s not aware of any attacks exploiting the flaw.
Cisco also informed customers of a high severity denial-of-service (DoS) flaw affecting the authentication, authorization and accounting (AAA) implementation of the FXOS and NX-OS software.
A remote, unauthenticated hacker can cause affected devices to reload by launching a brute-force attack on their login system.
The security hole (CVE-2017-3883) affects Firepower appliances, Nexus and Multilayer Director switches, and some Unified Computing System products. Both patches and workarounds have been made available by Cisco.
As for Small Business IP phones, two different DoS vulnerabilities have been found by Cisco during internal testing. One of the security holes, CVE-2017-12260, affects the Session Initiation Protocol (SIP) functionality in Cisco Small Business SPA50x, SPA51x and SPA52x series IP phones, while the other, CVE-2017-12259, impacts the same functionality in only SPA51x series phones.
Both vulnerabilities allow an unauthenticated attacker to cause a DoS condition by sending specially crafted SIP requests to the targeted device.
Cisco has also warned customers that many of its products are vulnerable to the recently disclosed Wi-Fi attack method known as KRACK. Similar to other affected vendors, the networking giant has already started releasing patches for vulnerable devices.
Microsoft provides details of a code execution vulnerability in Chrome
19.10.2017 securityaffairs Vulnerebility
Microsoft’s Offensive Security Research (OSR) team disclosed a remote code execution vulnerability in the Chrome web browser.
Microsoft’s Offensive Security Research (OSR) team has disclosed a remote code execution vulnerability in the Chrome web browser that was discovered by its experts.
The flaw, tracked as CVE-2017-5121, was addressed by Google last month with the release of Chrome 61, but the company has yet disclosed the details of the flaw .
Microsoft researchers have used the ExprGen fuzzer developed by themselves for testing their own Chakra javascript engine.
The analysis of the Chrome V8 open-source JavaScript engine revealed initially an information leak, but further analysis confirmed it was arbitrary code execution in the Chrome renderer process.
As you know, Google Chrome browser use a sandbox to restrict the execution environment of the web applications, this means that in order to escape the sandbox and take over the machine it is necessary to chain the flaw with a second vulnerability.
Microsoft operated without knowing the second vulnerability and discovered that executing arbitrary code within a renderer process can allow an attacker to bypass the Single Origin Policy (SOP), which is the mechanism in place to prevents a malicious script on one page from obtaining access to sensitive data on another web page.
“Each renderer is meant to be the brains behind one or more tabs—it takes care of parsing and interpreting HTML, JavaScript, and the like. The sandboxing model makes it so that these processes only have access to as little as they need to function. As such, a full persistent compromise of the victim’s system is not possible from the renderer without finding a secondary bug to escape that sandbox.” Microsoft wrote in a blog post.
“With that in mind, we thought it would be interesting to examine what might be possible for an attacker to achieve without a secondary bug.”
Bypassing the SOP mechanism, an attacker can steal the saved password from any website by hijacking the PasswordAutofillAgent interface, inject arbitrary JavaScript into web pages via universal cross-site scripting (UXSS), and also silently navigate to any website, including the ones that embed crypto mining codes or host exploit kit.
“A better implementation of this kind of attack would be to look into how the renderer and browser processes communicate with each other and to directly simulate the relevant messages, but this shows that this kind of attack can be implemented with limited effort,” continues the blog post. “While the democratization of two-factor authentication mitigates the dangers of password theft, the ability to stealthily navigate anywhere as that user is much more troubling because it can allow an attacker to spoof the user’s identity on websites they’re already logged into.”
Microsoft criticized the way Google releases patches for Chrome through the open-source browser project Chromium. The source code changes that address the flaw are often available on GitHub before the actual patch is released to customers allowing threat actors to develop their own exploit codes.
Cyber espionage – China-Linked group leverages recently patched .NET Flaw
19.10.2017 securityaffairs CyberSpy
Security researchers at Proofpoint spotted a cyber espionage campaign conducted by a group previously linked to China.
The hackers have been using a recently patched .NET vulnerability, tracked as CVE-2017-8759, in attacks aimed at organizations in the United States.
“Proofpoint researchers are tracking an espionage actor targeting organizations and high-value targets in defense and government. Active since at least 2014, this actor has long-standing interest in maritime industries, naval defense contractors, and associated research institutions in the United States and Western Europe.” reads the report published by Proofpoint.
The attackers have been active since at least 2014, they are known for the use of a remote access trojan (RAT) named NanHaiShu. The threat actors targeted various U.S. and Western European organizations with ties to the maritime sector, including naval defense contractors and research institutions.
“NanHaiShu – We have observed variants of this JavaScript backdoor used in various campaigns, including those publically reported. The actor continues to improve and refine the malware by, for example, wrapping it inside an HTA wrapper” continues the report.
Last year, experts at security firm F-Secure analyzed the attacks conducted by the group against the participants of a Permanent Court of Arbitration case focusing on a dispute between China and the Philippines over the South China Sea.
According to the report published by F-Secure, the NanHaiShu malware had Chinese origins.
In the last campaign spotted in mid-September, attackers targeted various US entities, including a shipbuilding company and a university research center with ties to the military.
According to researchers at Proofpoint, threat actors attacker sent spear-phishing emails to the victims, the messages use documents crafted to exploit the CVE-2017-8759. The CVE-2017-8759 flaw is a .NET vulnerability patched by Microsoft just a few days before the hacker crew launched the attacks.

The CVE-2017-8759 flaw is a .NET vulnerability patched by Microsoft just a few days before the hacker crew launched the attacks.
According to FireEye, the CVE-2017-8759 has actively been exploited by an APT group to deliver the surveillance malware FinFisher Spyware (FinSpy) to a Russian-speaking “entity” via malicious Microsoft Office RTF files in July.
Proofpoint discovered other attacks launched by the cyber espionage group in early August when hackers exploited the CVE-2017-0199 flaw, an Office vulnerability that had also been exploited in attacks since April.
The hackers targeted several defense contractors, they leveraged malicious Microsoft Publisher files, PowerPoint docs, and domains set up to mimic ones belonging to an important provider of military ships and submarines.
The arsenal of the group also includes a backdoor dubbed “Orz,” which was used in past attacks and in the August 2017 campaigns, the SeDLL and MockDLL loaders, and a publicly available commercial software for “Adversary Simulations and Red Team Operations.” Cobalt Strike.
The actor sometimes leverages the access at one compromised organization for lateral movements and target another organization in the same industry.
“Similarly the actor attempts to compromise servers within victim organizations and use them for command and control (C&C) for their malware.” continues the analysis.
“The tools, techniques, and targets consistently connect their work, particular given their attention to naval and maritime defense interests and use of custom backdoors,” concluded the researchers. “While defense contractors and academic research centers with military ties should always be cognizant of the potential for cyberattacks, organizations fitting their targeting profiles should be especially wary of legitimate-looking but unsolicited emails from outside entities.”
Australia Spy Chief Warns of Growing Foreign Meddling
19.10.2017 securityweek BigBrothers
Foreign powers are waging an "extensive, unrelenting" campaign of espionage and meddling in Australia, notably targeting ethnic and religious minorities, the country's spy chief warned Thursday.
The Australian Security Intelligence Organisation (ASIO) said it was struggling to cope with the threat, with its resources stretched from fighting terrorism.
Spy chief Duncan Lewis said in a forward to ASIO's annual report that over the past year there had been a "steadily worsening overall security and operational environment".
He pinpointed heightened terror fears, but also growing foreign interference which was "extensive, unrelenting and increasingly sophisticated".
Overseas powers had sought classified information on Australia's alliances and partnerships, its position on diplomatic, economic and military issues, energy and mineral resources, and innovations in science and technology, he said.
"Espionage and foreign interference is an insidious threat -- activities that may appear relatively harmless today can have significant future consequences," he warned.
Officials last week revealed sensitive data about Australia's F-35 stealth fighter and P-8 surveillance aircraft programmes was stolen when a defence subcontractor was hacked using a tool widely used by Chinese cyber criminals.
Without naming any countries, Lewis pointed to "a number of states and other actors".
"Our investigations revealed countries undertaking intelligence operations to access sensitive Australian government and industry information," he said.
"We identified foreign powers clandestinely seeking to shape the opinions of members of the Australian public, media organisations and government officials in order to advance their country's own political objectives.
"Ethnic and religious communities in Australia were also the subject of covert influence operations designed to diminish their criticism of foreign governments," Lewis added.
He said the activities represented "a threat to our sovereignty, the integrity of our national institutions and the exercise of our citizens' rights".
The report comes after recent public warnings from Australian officials about the level of Chinese government interference on university campuses.
There are mounting concerns about the way Beijing uses nationalist student groups to monitor Chinese students, and challenge academics whose views do not align with Communist Party doctrine, particularly over issues such as Taiwan and border disputes.
Foreign Minister Julie Bishop stressed this week international students were welcome but Australia was a democracy and "we don't want to see freedom of speech curbed in any way involving foreign students or foreign academics".
According to state broadcaster ABC, Beijing's intrusion into Western universities has sparked a push by Australia's closest allies, including the US, Britain, Canada and New Zealand, for a more coordinated response to the tactics.
While foreign meddling was a major concern for ASIO, so was the heightened terror threat which was placing "considerable pressure" on the domestic spy agency.
Its report said three planned attacks in Australia were disrupted over the past 12 months, while highlighting concern about the growing influence of Islamic State in Southeast Asia.
Many Equifax Hack Victims Had Info Stolen Prior to Breach: IRS
19.10.2017 securityweek Hacking
The U.S. Internal Revenue Service (IRS) believes the recent Equifax breach will not make a significant difference in terms of tax fraud considering that many victims already had their personal information stolen prior to the incident.
IRS Commissioner John Koskinen told the press on Tuesday that 100 million Americans have had their personally identifiable information (PII) stolen by hackers, according to The Hill. He also advised consumers to assume that their data has already been compromised and act accordingly.
The Equifax breach, which affected more than 145 million individuals, allowed cybercriminals to access social security numbers, dates of birth and other information. Despite this being one of the largest data breaches in history, Koskinen said it likely “won’t make any significantly or noticeable difference.”
In prepared remarks, Koskinen said the IRS stopped 883,000 attempts to file tax returns using stolen information in 2016, which represents a 37% drop compared to the previous year. Another 30% decrease in fraud attempts was observed this year, when 443,000 instances were discovered throughout August.
Koskinen also pointed out that the number of identity theft victims, based on reports received by the IRS, dropped by 46% in 2016 to 376,000. Another significant decrease in the number of identity theft reports was recorded this year.
“We know cybercriminals are planning for the 2018 tax season just as we are. They are stockpiling the names and SSNs they have collected. They try to leverage that data to gather even more personal information. This coming filing season, more than ever, we all need to work more diligently and work together to combat this common enemy,” the commissioner said.
The IRS has been working on strengthening the security of its systems. In the past year, the agency was forced to suspend several of its online services due to security concerns, including the Identity Protection PIN tool, the Get Transcript service, and the Data Retrieval Tool for Federal Student Aid applications. The Get Transcript service was abused by fraudsters to access the online accounts of more than 700,000 taxpayers.
Recently Patched .NET Flaw Exploited by China-Linked Cyberspies
19.10.2017 securityweek Exploit
A cyber espionage group previously linked to China has been using a recently patched .NET vulnerability in attacks aimed at organizations in the United States, including a shipbuilding company and a university research center with ties to the military.
The threat actor, known for its use of a remote access trojan (RAT) named NanHaiShu, has been active since at least 2014. In the past years, it has targeted various U.S. and Western European organizations with ties to the maritime sector, including naval defense contractors and research institutions.
A report published last year by F-Secure detailed attacks launched by the group against the participants of a Permanent Court of Arbitration case focusing on a dispute between China and the Philippines over the South China Sea.
F-Secure did not directly attribute the attacks to the Chinese government, but researchers found several pieces of evidence suggesting that the NanHaiShu malware had Chinese origins.
The latest round of attacks attributed to this group were observed by researchers at Proofpoint in mid-September. Experts noticed that the attacker sent spear-phishing emails to a U.S. shipbuilding company and a U.S. university research center with ties to the military.
The emails carried documents designed to exploit CVE-2017-8759, a .NET vulnerability patched by Microsoft just days before the attacks were launched. At the time when Microsoft released fixes, the flaw had already been exploited by a Middle Eastern threat actor to deliver spyware.
Proofpoint has also seen attacks launched by the cyber espionage group in early August. These attacks exploited CVE-2017-0199, an Office vulnerability that had also been exploited in attacks when Microsoft released a patch for it back in April.
The attacks targeted several defense contractors and they involved malicious Microsoft Publisher files, PowerPoint presentations, and domains set up to mimic ones belonging to an important provider of military ships and submarines. Researchers from other companies also analyzed these attacks and some pointed out that many of the targets were in South Korea.
In addition to NanHaiShu, the attackers have used a backdoor dubbed “Orz,” which has been spotted in both old attacks and ones launched in August 2017, loaders such as SeDLL and MockDLL, and the Cobalt Strike penetration testing tool.
In some cases, researchers noticed that the attackers used one organization’s compromised email accounts to send malicious attachments to others in the same industry. The hackers also used hijacked servers for command and control (C&C).
“The tools, techniques, and targets consistently connect their work, particular given their attention to naval and maritime defense interests and use of custom backdoors,” Proofpoint researchers said in a blog post. “While defense contractors and academic research centers with military ties should always be cognizant of the potential for cyberattacks, organizations fitting their targeting profiles should be especially wary of legitimate-looking but unsolicited emails from outside entities.”
Duo Security Raises $70 Million at More Than $1 Billion Valuation
19.10.2017 securityweek IT
Duo Security, a cloud-based provider of identity and access management solutions, today announced that it has raised an additional $70 million in funding led by Meritech Capital Partners and Lead Edge Capital.
The Series D funding round brings the total amount raised by the Ann Arbor, Michigan-based software-as-a-service (SaaS) company to $119 million, with a post-money valuation pegged at $1.17 billion.
According to the company, the additional cash will be used to expand global operations and fund product development.
Duo says that it currently serves more than 10,000 customers and protects more than 300 million logins worldwide every month. Customers include Facebook, Etsy, Facebook, K-Swiss, Paramount Pictures, Toyota, Random House, Yelp, Zillow and more.
Duo Security LogoThrough its flagship two-factor authentication (2FA) app, Duo's "Trusted Access" product suite helps verify the identity of users, and the health of their devices, before granting them access to applications. The platform supports Macs, PCs and mobile devices, and gives administrators visibility into end user devices accessing the corporate network.
In term of company performance, Duo says it has doubled its annual recurring revenue for the past four years, and currently has more than 500 employees globally, after doubling its headcount in 2016.
In late September, Duo issued a research report showing discrepancy between the frequency and thoroughness of Apple's Mac Operating System (OS X) and app security updates, and updates for the underlying firmware (EFI) on Mac computers. Duo’s research found that on a sample of 73,324 Macs deployed in production settings, 4.2% were running outdated EFI -- leaving them potentially vulnerable to new exploits.
In addition to its Ann Arbor, Michigan headquarters, Duo currently maintains offices in Austin, Texas; San Mateo, California; and London, England.
The Series D round included new investors, Geodesic Capital and Index Ventures, as well as existing investors Redpoint Ventures and True Ventures. Workday, a new strategic partner, also participated in the round. Other investors in the company include, Benchmark, Google Ventures, Lead Edge Capital, Meritech Capital Partners, Radar Partners.
Oracle Fixes 252 Vulnerabilities in October 2017 Patch Update
19.10.2017 securityweek Vulnerebility
Oracle on Tuesday released its Critical Patch Update (CPU) for October 2017 to address a total of 252 security vulnerabilities across multiple product families. More than half of the bugs may be remotely exploitable without authentication.
The most affected Oracle products this month include Fusion Middleware (40 vulnerabilities, 26 remotely exploitable without authentication), Hospitality Applications (37 flaws, 13 remotely exploitable), E-Business Suite (26 - 25), MySQL (25 - 6), PeopleSoft Products (23 - 13), Communications Applications (23 - 18), and Java SE (22 - 20).
Oracle this year resolved 1119 vulnerabilities in its products, or 22% more than in 2016. That’s not surprising, given that both the April 2017 CPU and July 2017 CPU passed the 300 patches mark.
Of the 252 vulnerabilities addressed in this CPU, 182, or 72% of the total, directly affect business-critical applications. Impacted products also include Sun Systems Products Suite (10 vulnerabilities), Retail Applications (9), Siebel CRM (8), Supply Chain Products Suite (7), Virtualization (6), Database Server (6), Hyperion (4), JD Edwards Products (2), Financial Services Applications (2), Health Sciences Applications (1), Construction and Engineering Suite (1), and Enterprise Manager Grid Control (1).
The most critical vulnerabilities addressed this month affect Hospitality Reporting and Analytics, Siebel Apps, and Hospitality Cruise AffairWhere and feature CVSS Base Scores of 10.0 or 9.9. By exploiting these issues, an attacker could either take over the application or hang or frequently crash (complete denial of service) the application.
Of the 26 issues patched in Oracle E-Business Suite, 21 were assessed as High risk, 2 as Low, and three received no severity rating. 15 of the vulnerabilities were found by Onapsis, a company that specializes in security Oracle and SAP products, and three of them were unauthenticated SQL injection bugs.
Affecting Oracle EBS versions 12.1 and 12.2, the flaws could be abused over a network without any username and password credentials. By exploiting the vulnerabilities, an attacker could potentially gain access to and modify critical documents and information, including credit card data, customer information, HR documents, and financial records, Onapsis notes.
9 other flaws were discovered by ERPscan, a company also focused on Oracle and SAP applications, all of them Cross Site Scripting (XSS) bugs and all of them with a CVSS base score of 8.2. By exploiting these vulnerabilities, an attacker could steal cookies or perform “session riding” attacks.
“The message from Oracle to their customers was loud and clear: you need to make cybersecurity a top priority. Organizations still need to remain focused on applying patches at the business-critical application layer. This is a complex process and sometimes falls through cracks between IT, application and security teams,” said Mariano Nunez, CEO, Onapsis.
Oracle EBS is one of the most critical applications used by large organizations in enterprise resource planning (ERP), customer relationship management (CRM), supply chain management (SCM), finance management, human capital management, procurement and many others.
Last month, Oracle released patches to address vulnerabilities in the Apache Struts 2 framework, including CVE-2017-9805, a flaw actively exploited by attackers. Some of the affected Oracle products included MySQL Enterprise Monitor, Communications Policy Management, FLEXCUBE Private Banking, Retail XBRi, Siebel, WebLogic Server, and various Financial Services and Insurance products.
Europol Looks to Solve IP-Based Attribution Challenges
19.10.2017 securityweek Security
Europol Calls for a Solution to the IP Address Attribution Problems Caused by CGNs
Europol has called for the end of carrier grade NAT (CGN) to increase accountability online. This is not a new campaign from Europol, but it now seeks to gain public support: "Are you sharing the same IP address as a criminal?" it asks.
"Law enforcement is using the 'distinguish yourself from a criminal' tactic in order to provoke the 'nothing to hide' scare tactic," Tom Van de Wiele, principal security consultant at F-Secure told SecurityWeek, "which is unfortunate, because as far as our privacy is concerned it's about protection. Privacy is the right to select which people to share what information with. But when it comes to the push of Europol in this case, there is more to it than that."
Van de Wiele sees the call as symptomatic of law enforcement's desire to remove anonymity from the internet, which is effectively an attack against privacy.
Everybody with home computers uses network address translation (NAT) within their routers. The ISP allocates an IP address for the router (usually on a temporary basis), and the NAT ensures incoming traffic to that IP goes to the right computer. It allows one IP address to be used for multiple home computers.
NATs are not a problem for law enforcement -- the problem comes with the carrier grade NATs (CGNs) used by the ISPs. These allow dozens, hundreds and perhaps even thousands of routers or computers or mobile devices to share a single IP address simultaneously. The problem for law enforcement is that the ISP is currently unable to say which computer is being used by a particular IP address at a particular time.
For law enforcement, it means that it is virtually impossible to trace the physical location of an IP address under investigation. "This is relevant as in criminal investigations an IP address is often the only information that can link a crime to an individual," said Europol in an announcement https://www.europol.europa.eu/newsroom/news/are-you-sharing-same-ip-addr... yesterday. "It might mean that individuals cannot be distinguished by their IP addresses anymore, which may lead to innocent individuals being wrongly investigated by law enforcement because they share their IP address with several thousand others – potentially including criminals."
There is some irony in this since in October 2016, the Court of Justice of the European Union (CJEU) ruled that IP addresses can in some circumstances qualify as personal data under European law. Europol is now implying, however, that an innocent user could be investigated by law enforcement solely by the accident of sharing the same IP address as a criminal.
Van de Wiele sees something verging on sinister from this latest push by Europol. "This is another attempt by law enforcement to try and single out individuals and to reduce the possibilities of anonymity to get closer to their active targets while increasing their success of traffic analysis for all traffic they are vacuuming up." He points out that it was law enforcement that forced Facebook into the policy of all users using their own identity, and getting 'friends' to confirm whether profiles are accurate. "These are cold war tactics and they are troubling," he says.
Europol's concern over the growing use of CGNs is not new. It raised the issues in its Internet Organised Crime Threat Assessment (IOCTA) in both 2014 http://www.securityweek.com/europol-analyzes-cybercrime-services-industry and 2016. A study it conducted in summer 2016 showed that 80% of surveyed European cybercrime investigators had encountered problems in their investigations relating to the use of CGN, causing them to be either delayed or stopped. These cases concerned investigations of offenses including online child sexual exploitation, arms trafficking and terrorist propaganda.
Europol's Executive Director Rob Wainwright said yesterday, "CGN technology has created a serious online capability gap in law enforcement efforts to investigate and attribute crime. It is particularly alarming that individuals who are using mobile phones to connect to the internet to facilitate criminal activities cannot be identified because 90% of mobile internet access providers have adopted a technology which prevents them from complying with their legal obligations to identify individual subscribers."
Steven Wilson, Head of Europol's European Cybercrime Center, added: "The issues relating to CGN, specifically the non-attribution of malicious groups and individuals, should be resolved."
This will be difficult. ISPs introduced CGNs, ostensibly as a temporary technical measure, to bridge the gap between the depletion of IPv4 addresses and the uptake of effectively limitless IPv6 addresses. But IPv6 uptake has been far slower than expected. "This was supposed to be a temporary solution until the transition to IPv6 was completed," says Europol, "but for some operators it has become a substitute for the IPv6 transition. Despite IPv6 being available for more than 5 years the internet access industry increasingly uses CGN technologies (90% for mobile internet and 50% for fixed line) instead of adopting the new standard."
Indeed, it could be said that the use of CGNs is actually delaying the transition to IPv6. The 2016 study, 'A Multi-perspective Analysis of Carrier-Grade NAT Deployment', concluded, "CGNs actively extend the lifetime of IPv4 and hence also fuel the demand of the growing market for IPv4 address space, which in turn affects market prices and possibly hampers the adoption IPv6."
"Most peering companies and ISPs are nowhere near being ready when it comes to IPv6," says Van de Wiele; "and with it, we will also see a whole slew of security issues when the SOHO and home users get IPv6 in the process. Having a unique IP address for every user or device without NAT offers tremendous possibilities technically, but that also means you can be tracked more easily by ad companies and other entities such as law enforcement."
In the meantime, what was introduced as a temporary fix has become entrenched. In most cases the use of CGNs is unnoticed and unknown by the user -- and hence, perhaps, this new appeal to public opinion by Europol. However, even if Europol solves the CGN issue, it is not at all clear that it will solve the problem of attribution.
"Unfortunately, CGN is not the only challenge when enforcing enacted laws and prosecuting cybercrime," commented Ilia Kolochenko, CEO of High-Tech Bridge. "A great wealth of currently available VPN service providers that you can purchase for bitcoins open up new opportunities to all kinds of digital offenders and predators." Without backdoor access to the VPN concerned, law enforcement will not have access to the IP address at all.
Furthermore, Kolochenko points out that the ability to tie a particular IP address to a particular physical computer will still not solve the problem. "The new trend in cybercrime," he said, "is to compromise a third-party with a motive to commit crime (e.g. a competitor) and conduct the attack from its infrastructure. On the Dark Web, you can buy compromised machines of law enforcement and judicial officers to be used as proxies for attacks. Most cybercrimes become technically uninvestigable or the price of their investigation outweighs any public interest."
Trump Team 'Dispels' EU Doubts on Data Protection Deal
19.10.2017 securityweek BigBrothers
US President Donald Trump's administration has "dispelled" doubts over whether it will stand by a hard-won personal data protection accord with Europe struck during Barack Obama's presidency, the EU said Wednesday.
But Brussels said it still wanted Washington to improve on a deal to protect European personal data transferred to the US by internet giants like Google and Facebook.
Last year's deal replaced a previous arrangement struck down by the bloc's top court, leaving the big companies unsure whether they could transfer data without facing a legal challenge.
However, Trump's "America first" policy, which has caused him to back out of agreements sealed by Obama, had raised European Union concerns.
"I can say that my second visit dispelled my doubts whether 'America First' does not mean 'America only'," EU Justice Commissioner Vera Jourova said at a press conference in Brussels.
Jourova said US Commerce Secretary Wilbur Ross and his team, whom she met last month in Washington, "have been very clear about their commitment to the privacy shield."
"And I got the feeling they understood the concerns Europeans have about the transfer of their personal data."
But she acknowledged there was "still some differences" between the two sides over the balance to strike between protecting privacy and ensuring security.
The European Commission, the executive of the 28-nation EU, said the deal "continues to ensure an adequate level of protection" for personal data transferred to firms in the US.
Jourova said the US, for example, has put in place ways in which EU individuals and firms can seek and obtain redress for complaints they may have with data transfers.
She added that more than 2,400 companies had already been certified by the US Commerce Department to participate in the scheme.
The commission said relevant US safeguards remained in place over access to personal data by US public authorities for national security reasons.
"But we also found space for improvement," Jourova added.
The commission recommended that US authorities do more to monitor whether companies were complying with their obligations under the deal as well as regularly search participating companies that make false claims.
It called for closer cooperation between relevant US authorities and their EU data protection counterparts.
Jourova urged Washington to name "as soon as possible" an ombudsman to tackle complaints from EU citizens, though there was "no concrete deadline".
Microsoft Discloses Code Execution Flaw in Chrome
19.10.2017 securityweek Vulnerebility
Microsoft has disclosed the details of a remote code execution vulnerability found by its employees in the Chrome web browser. Google patched the flaw last month with the release of Chrome 61.
Microsoft’s Offensive Security Research (OSR) team analyzed Chrome’s V8 open-source JavaScript engine using ExprGen, a fuzzer developed by Microsoft for testing its own JavaScript engine, Chakra. Microsoft hoped that using ExprGen could help find some new bugs, given that publicly available fuzzers had likely already been used to test V8.
Microsoft’s tests initially led to the discovery of an information leak, which ultimately resulted in arbitrary code execution in the Chrome renderer process.
However, Chrome relies on sandboxing to ensure that web applications are executed in a restricted environment. This means that a second vulnerability, one that allows a sandbox escape, needs to be identified in order to take full and persistent control of a system.
Microsoft researchers wanted to determine how far they can go without finding a second vulnerability. They discovered that executing arbitrary code within a renderer process can be used to bypass the Single Origin Policy (SOP), which prevents a malicious script on one page from obtaining access to sensitive data on another web page.
Once the SOP is bypassed, an attacker can steal saved password from any website, inject arbitrary JavaScript into webpages via universal cross-site scripting (UXSS), and silently navigate to any website.
“A better implementation of this kind of attack would be to look into how the renderer and browser processes communicate with each other and to directly simulate the relevant messages, but this shows that this kind of attack can be implemented with limited effort,” Microsoft said in a blog post. “While the democratization of two-factor authentication mitigates the dangers of password theft, the ability to stealthily navigate anywhere as that user is much more troubling, because it can allow an attacker to spoof the user’s identity on websites they’re already logged into.”
The vulnerability is tracked as CVE-2017-5121 and it was patched by Google last month with the release of Chrome 61. Google has yet to make the details of the flaw public on its own bug tracker.
Microsoft researchers earned a total of $15,837 via Google’s bug bounty program for this and other vulnerabilities, an amount that they plan on donating to charity.
Microsoft also pointed out an issue with how Google releases patches for Chrome, which is based on the open-source browser project Chromium. The problem, according to Microsoft, is that source code changes that fix vulnerabilities often make it to GitHub before the actual patch is released to customers, which could give malicious actors the opportunity to exploit flaws against unprotected users.
On the other hand, Google also recently criticized Microsoft’s patch process, noting that attackers can compare patched Windows 10 builds to vulnerable builds in order to find flaws that they may be able to exploit against users of earlier versions of Windows.
Google researchers have found numerous vulnerabilities in Microsoft products in the past years, although the search giant has not always given Microsoft the opportunity to release a patch before making details public.
October 2017 Oracle Critical Patch Update addresses 252 Vulnerabilities
19.10.2017 securityaffairs Vulnerebility
Oracle released the October 2017 Critical Patch Update (CPU) that addresses a total of 252 security vulnerabilities that affect multiple products.
Most of the vulnerabilities fixed by Oracle could be remotely exploitable without authentication.
This is the last Oracle Critical Patch Update of 2017, this year the tech giant already resolved 1119 vulnerabilities, or 22% more than in 2016.

The largest number of fixed vulnerabilities was affecting Fusion Middleware (40 vulnerabilities, 26 remotely exploitable without authentication), Hospitality Applications (37), E-Business Suite (26), MySQL (25), PeopleSoft Products (23), Communications Applications (23), and Java SE (22).
182 of the 252 vulnerabilities addressed by this October 2017 Critical Patch Update affect business-critical applications, including Sun Systems Products Suite (10 vulnerabilities), Retail Applications (9), Siebel CRM (8), Supply Chain Products Suite (7), Virtualization (6), Database Server (6), Hyperion (4), JD Edwards Products (2), Financial Services Applications (2), Health Sciences Applications (1), Construction and Engineering Suite (1), and Enterprise Manager Grid Control (1).
The most critical vulnerabilities affect Hospitality Reporting and Analytics, Siebel Apps, and Hospitality Cruise AffairWhere, they were received a CVSS Base Scores of 10.0 or 9.9. An attacker can exploit these flaws to take over vulnerable applications or to trigger a DoS condition.
Two vulnerabilities in Oracle Hospitality Reporting and Analytics were assessed with the maximum CVSS score of 10.0. Both flaws were exploitable by an unauthentic attacker over HTTP to access all of the reporting and analytics data running on the vulnerable system.
The October 2017 Critical Patch Update also addressed a critical vulnerability in PeopleSoft core engine tracked as CVE-2017-10366. Attackers can trigger the flaw to gain remote code execution on a server running PeopleSoft software.
“This vulnerability can be exploited by sending a HTTP request to the PeopleSoft service with a serialized JAVA object,” said Alexander Polyakov, CTO at ERPScan. “After unserialization, it can run any command on the server.
“Because this vulnerability was found in HTTP service it can be easily available via the internet if company exposes their PeopleSoft system to the Internet,”
The experts at ERPscan who queried Shodan search engine for vulnerable PeopleSoft systems discovered more than 1,000 installations exposed on the internet, including more than 200 belonging to government agencies and universities in the U.S.
9 Cross Site Scripting (XSS) vulnerabilities were discovered by security firm ERPscan, all of them with a CVSS base score of 8.2. The researchers explained that attacker could exploit these flaws to steal cookies or perform “session riding” attacks.
For further details on the October 2017 Oracle Critical Patch Update let me suggest reading the excellent report published by ERPscan.
The Necurs botnet is back spreading a downloader with new interesting features
19.10.2017 securityaffairs BotNet
The Necurs botnet is spreading a new downloader that takes screenshots of the victims’ desktops and Runtime Errors back to the operators.
The Necurs botnet is back once again, the dreaded botnet was spreading a downloader that takes screenshots of the victims’ desktops and Runtime Errors back to the attackers.
“Recently we have seen a resurgence of emails sent by the Necurs botnet. The latest blast of emails is spreading a new variant of the Locky ransomware (Ransom.Locky) or Trickybot (Trojan.Trickybot).” reads the analysis published by Symantec. “What’s interesting about this new wave is that the downloader now contains new functionality to gather telemetry from victims. It can take screen grabs and send them back to a remote server. There’s also an error-reporting capability that will send back details of any errors that the downloader encounters when it tries to carry out its activities.”
The Necurs malware spread via spam campaigns or through compromised web servers, last time we read about it in January when it was being used by crooks to deliver the Locky ransomware.
Now the Necurs Botnet, one of the world’s largest malicious architecture, is spreading a downloader with two interesting new features.
The first feature consists in the addition of a Powershell script that takes a screengrab of the infected user’s screen, that is uploaded to a remote server after waiting a few seconds.
The second addition is a built-in error reporting feature that monitors the Necurs downloader for errors and sends collected info back to Necurs botmaster.
This is the first time that a downloader implements such kind of feature. experts believe Necurs operators gather intelligence about their campaigns.
“When you consider the screen grab functionality together with the new error-reporting capability, it suggests that the Necurs attackers are actively trying to gather operational intelligence (OPINTEL) about the performance of their campaigns. ” continues Symantec.
Collected data could allow the attackers to measure the efficiency of their campaign and detect when the malicious code has infected valuable environments, such as corporate networks.
The error reporting feature allows coders to fix bugs in their software improving their success rates.
The following graph reports the spam waves observed in the last months, after a period of silence from end of 2016 and into early 2017 it appeared again in March.
The evidence collected by the researchers suggest an intensification of the activities related to the Necurs botnet.
“Necurs went through a long spell of silence from end of 2016 and into early 2017. It burst back onto the scene around March and since then, it has been cranking up its activity levels, with recent months seeing the most action so far in 2017″ concludes Symantec.
“With our data showing a resurgence in activity, and the apparent efforts to collect operational intelligence, we can expect to see continued evolution of the capabilities and a steady increase in Necurs activity levels in the coming months.”

South Africa – About 30-million identity numbers and other personal and financial information leaked online
19.10.2017 securityaffairs Incindent
South Africa – About 30-million identity numbers and other personal and financial information leaked online, it is the largest data leak in the country.
About 30-million identity numbers and other personal and financial information had been hacked and leaked online, it could be the biggest data breach suffered by the South Africa.
The data breach was discovered by the popular cyber security expert Troy Hunt, he discovered an about 27 gigabytes dump that contained a wide range of sensitive information belonging to South Africans, including citizens ID numbers, personal income, age, employment history, company directorships, race group, marital status, occupation, employer and previous addresses.
Follow
Troy Hunt ✔@troyhunt
South African followers: I have a very large breach titled "masterdeeds". Names, genders, ethnicities, home ownership; looks gov, ideas?
8:40 AM - Oct 17, 2017 · Melbourne, Victoria
45 45 Replies 128 128 Retweets 69 69 likes
Twitter Ads info and privacy
Fortunately, the huge trove of data wasn’t offered for sale yet, but it is a matter of time.
The dump includes information from at least as far back as the early 1990s, the analysis of date of file suggest the security breach took place in April 2015.
The source of the database is still unknown, Hunt shared some information on it to speed up its identification.
Data headers suggest the source may be Government, but we cannot exclude in this phase that data could be related to a financial organization or credit bureau.
South Africa data leak
According to the editorial staff at the iafrikan.com website, the source of data is the GoVault platform of the Dracore Data Sciences.which counts among its customers TransUnion, one the largest credit bureaux in South Africa.
“I first checked their GoVault platform as it is advertised as “the goldmine of information offers easy access to the contact details of South African consumers and homeowners.” states the website iafrikan.com.
“They’ve [Dracore] fucked up in a seriously large scale here. They’ve collected an enormous volume of data and I’m not sure the owners of that data ever gave their consent. That may still be legal, but the backlash will be severe. They then published that data to a web server with absolutely zero protection and, of course, unauthorized parties found it. You yourself [iAfrikan] found it very quickly just by searching for it. There is now going to be a very serious spotlight shone on them for the sheer incompetence of their actions and they’re in no position the threaten those who’ve reported this to them responsibly,” said Hunt when speaking to iAfrikan.
At this stage we can conclusively stop calling it a data hack or data breach, it is more like a leak, and I’m being kind calling it a leak as the DATA IS STILL UP ON THE WEBSITE AS I TYPE THESE WORDS!!!” concluded iAfrikan.”
Google introduces new Advanced Protection feature to protect its users
19.10.2017 securityaffairs Safety
Google continues working to improve the security of its users, the last measure introduced by the company it the ‘Advanced Protection’ feature.
The Advanced Protection feature was designed to improve the security of users, who are at high risk of targeted attacks.
“We took this unusual step because there is an overlooked minority of our users that are at particularly high risk of targeted online attacks. For example, these might be campaign staffers preparing for an upcoming election, journalists who need to protect the confidentiality of their sources, or people in abusive relationships seeking safety.” reads the blog post published by Google.
“Sometimes even the most careful and security-minded users are successfully attacked through phishing scams, especially if those phishing scams were individually targeted at the user in question.”
Even if the threat actor obtains the victim’s credentials via spear phishing messages, advanced or using a malware he will not be able to access the Google account.
Users that want to enable the Google’s Advanced Protection feature need two physical security keys that work with FIDO Universal 2nd Factor (U2F).
U2F is an open authentication standard that allows users to securely access many online services, with one single device with no drivers, or client software needed.
This hardware-based two-factor authentication does not require secret codes via SMS, apps or emails.

Log into a Google account is very simple, just plug the USB stick, in the port, while accessing from a smartphone or tablet will require a Bluetooth-enabled dongle, paired with the device.
According to Google, the new feature implements the best protection against:
Phishing.
Accidental sharing.
Fraudulent account access.
“They [security devices] use public-key cryptography and digital signatures to prove to Google that it’s really you,” the post reads. “An attacker who does not have your Security Key is automatically blocked, even if they have your password.” continues Google.Advanced Protection offer three features to keep your account safe:
The Google Advanced Protection program implements the following features:
Physical Security Key: The access to the account is allowed only if the user is in possession of a U2F security key.
Limit data access and sharing: Enabling this feature only Google apps to get access to your account, for now, other trusted apps will be added in the future.
Blocking fraudulent account access: If the user loses the U2F security key, the account recovery process will involve additional steps, “including additional reviews and requests for more details about why you’ve lost access to your account” to prevent fraudulent account access.
Advanced Protection feature is not designed for everyone, but only for people, like journalists, government officials and activists, who are at a higher risk of being targeted by government or sophisticated hackers and ready to sacrifice some convenience for substantially increased e-mail protection.
Currently, Google users can enroll in the Advanced Protection Program using Google Chrome that already supports the U2F standard for Security Keys, other browsers are expected to support the same technology.
Users that want to use the Advanced Protection have to sign up at the following address:
https://landing.google.com/advancedprotection/
Google also announced the partnership with security firm ESET for malware detection in the Chrome browser through the Chrome Cleanup feature.
Chrome Cleanup now leverages the malware detection engine from ESET.
“Under the hood, we upgraded the technology we use in Chrome Cleanup to detect and remove unwanted software. We worked with IT security company ESET to combine their detection engine with Chrome’s sandbox technology.” Google announced in a blog post. “We can now detect and remove more unwanted software than ever before, meaning more people can benefit from Chrome Cleanup. Note this new sandboxed engine is not a general-purpose antivirus—it only removes software that doesn’t comply with our unwanted software policy.”
Unpatched Flaws Possibly Stolen From Microsoft in 2013 Hack: Report
18.10.2017 securityweek Vulnerebility
Hackers may have stolen information on unpatched vulnerabilities after breaching Microsoft’s systems and gaining access to a bug tracker back in 2013, Reuters reported on Monday.
At the time of the breach, Microsoft informed customers that it had been targeted in an attack similar to the ones aimed at Facebook and Apple.
“During our investigation, we found a small number of computers, including some in our Mac business unit, that were infected by malicious software using techniques similar to those documented by other organizations. We have no evidence of customer data being affected and our investigation is ongoing,” Microsoft said at the time.
Reuters learned from five former Microsoft employees that the attackers also breached a database that stored information on unpatched flaws affecting Windows and other products. The database had been protected only with a password.
While Microsoft fixed all the vulnerabilities within months of the intrusion and found no evidence of the flaws being exploited in other attacks, it’s still possible that the malicious actor created exploits that it used in other campaigns.
The former employees said Microsoft analyzed breaches suffered by other organizations at the time, but found no clear evidence that the stolen vulnerability information had been abused.
However, three of the former employees claim the study had too little data and noted that Microsoft relied on automated reports generated by software crashes to find exploits. However, experts argued that sophisticated attacks may have not generated crashes that would tip off Microsoft. In fact, the company did observe attacks exploiting the vulnerabilities, but concluded that they could have been obtained elsewhere.
SecurityWeek has reached out to Microsoft for comment and will update this article if the company responds.
The hacker group that targeted Microsoft, Apple, Twitter and Facebook back in 2013 is known as Butterfly, Morpho and Wild Neuton. The threat actor, described as a financially motivated espionage group, is believed to have been active since at least 2011.
The hackers leveraged watering holes, Java zero-day exploits, and Windows and Mac backdoors to target the tech giants. The attackers went silent for nearly a year after these campaigns and reemerged in late 2013, when they started targeting organizations in the legal, real estate, investment, IT and healthcare sectors around the world. They also launched attacks on individual users and Bitcoin companies.
Microsoft is not the only company whose bug-tracking database has been breached. Back in 2015, Mozilla informed users that an attacker breached its Bugzilla bug tracker using stolen credentials and accessed information on 185 non-public vulnerabilities affecting Firefox and other products.
Google to Offer Stepped-up Security For 'High Risk' Users
18.10.2017 securityweek Attack
Google said Tuesday it would offer stronger online security for "high risk" users who may be frequent targets of online attacks.
The US technology titan said anyone with a personal Google account can enroll in the new "advanced protection," while noting that it will require users to "trade off a bit of convenience" for extra security.
"We took this unusual step because there is an overlooked minority of our users that are at particularly high risk of targeted online attacks," said a Google security blog post.
"For example, these might be campaign staffers preparing for an upcoming election, journalists who need to protect the confidentiality of their sources, or people in abusive relationships seeking safety."
Google will require these users to log into their accounts with a physical USB key which will be part of two-factor authentication, to guard against fraudulent access.
"An attacker who doesn't have your security key is automatically blocked, even if they have your password," the statement said.
Google will provide additional monitoring for these accounts and limit access to sensitive applications, aiming to protect against impersonation and "phishing" to gain access to an account.
"Sometimes even the most careful and security-minded users are successfully attacked through phishing scams, especially if those phishing scams were individually targeted at the user in question," the company said.
Phishing is the use of deception to gain confidential information such as usernames, passwords, bank account details and credit card numbers.
In one of the most highly publicized phishing attacks, Hillary Clinton's campaign chairman John Podesta gave up his password to a hacker, resulting in a series of embarrassing leaks during the 2016 presidential race.
RSA Unveils New GDPR Compliance Offerings
18.10.2017 securityweek Krypto
RSA Says GDPR is More About Evidence-based Process Than Technology
Europe's General Data Protection Regulation (GDPR) is, by name, just another information security compliance regulation requiring that organizations protect personal data from being stolen by hackers. As such, there should be little for organizations to do since most companies already do all they can to defend against breaches (albeit not always successfully). That, however, would be a total misunderstanding of this new regulation.
The emphasis on data protection has changed: it is traditionally designed to protect data from criminals; but this regulation is designed to protect data for the user. It is a subtle change with huge ramifications, because now users are in charge of their own personal information. They must explicitly agree to the collection of data for a specific purpose; and they can withdraw consent and require companies to delete that data.
RSA LogoThis simple change means that data governance is now front and center, side-by-side with data security. Organizations will need to be able to prove user agreement to the collection of personal data; and must be able to demonstrate deletion of that data after demand. This also means that organizations must be aware of the location of all personal data at all times.
"GDPR is not just about technology," Rashmi Knowles, RSA Field CTO EMEA told SecurityWeek. "I think the bigger part of GDPR is to do with process, and the process burden is going to be huge. One of the big new things is the whole personal data lifecycle -- from getting consent and proving user consent, to processing user data and then deleting that data after processing it solely for the purpose for which it was collected; and being able to delete it at any time on the users' request. Although some organizations already do that, a lot of companies don't do it very well, and don't have the evidence to prove they are doing it. GDPR is very much evidence based."
There is another major change. Sanctions for non-compliance have been dramatically increased. While large corporations could simply accept the minimal fines from the existing Directive-based European laws as part of acceptable risk tolerance; under the Regulation fines are now geared, potentially, to seriously affect the bottom-line of non-compliant companies for many years. The regulators are taking GDPR very seriously, and they expect organizations to do the same. There is the implication that these regulators will not back away from imposing very heavy fines for the worst cases of non-compliance.
It is against the background of GDPR being as much about data governance as it is about information security that RSA has today beefed up its Archer governance suite specifically to aid compliance with the governance side -- and more -- of GDPR. "Ultimately," it says in a statement released today, "GDPR is not just a Governance, Risk and Compliance (GRC) issue. GDPR spans the full enterprise and forces companies to adopt a healthier privacy and security risk posture in four critical areas: Risk Assessment, Breach Readiness, Data Governance, and Compliance Management."
It is in these four areas that Archer, combined with RSA NetWitness and the RSA Data Risk and Security Practice can aid GDPR compliance. On risk assessment, RSA suggests that Archer's components will help accelerate the identification of the linkage between risks and internal controls, potentially reduce the GDPR compliance gaps and improve risk mitigation strategies.
On breach response, GDPR requires that regulators are notified of a breach generally within 72 hours of the company becoming aware of the breach. Here, RSA says its NetWitness product will scan the entire network infrastructure looking for indications of a compromise. It uses, explains RSA, "behavioral analysis and machine learning to help better understand the scope and nature of a breach with improved visibility into the attack sequence, enabling faster notification."
RSA offers its SecurID suite and Data Risk and Security Practice service to cover the mainstream governance side of GDPR. Compliance is no longer a destination, but a continuing state, it suggests. While under earlier European laws, companies needed only worry about compliance if they were breached, with GDPR they can be found non-compliant in data governance areas at any time. This suite of services helps an organization optimize a GRC program; put in place the processes to enable a prompt response to cyber incidents; prepare to meet the new 72-hour notification requirements; and plan and implement GDPR-compliant data access programs.
"Organizations will "see quicker reaction to emerging issues, create a more proactive and resilient environment, and reduce the churn in driving accountability towards GDPR compliance," says RSA.
But while GDPR may be more about process and evidence, the technology side cannot be ignored. The term 'breach' is given a wider than usual scope under GDPR. "A breach in GDPR could be lack of availability," Knowles told SecurityWeek; "so a successful DDoS -- which may not usually be classed as a breach -- could be classed as a breach in GDPR terms if users lose access to their data."
In this sense, being struck by something like ransomware would prove a double-whammy. Firstly the victim gets all the disruption and cost of the ransomware, but secondly it is potentially and automatically in breach of GDPR. "If you can show that you are doing the right things, that you have the right controls in place," says Knowles, "then the regulators are more likely to be lenient from the GDPR perspective. But on the other hand, if the ransomware could have been stopped had you applied the correct patches, the regulator might not be so lenient."
GDPR compliance is a complex mix of security technology to protect the data, tied together with governance processes to manage the personal data lifecycle, backed up by the availability of continuous evidence to prove that you are doing the right things at all times.
Elevation of Privilege Flaw Impacts Linux Kernel
18.10.2017 securityweek Vulnerebility
The Linux kernel is susceptible to a local escalation of privilege impacting the Advanced Linux Sound Architecture (ALSA), Cisco warns.
Tracked as CVE-2017-15265, the vulnerability can be exploited by an attacker to gain elevated privileges on the targeted system. However, because the issue requires local access to the targeted system, the likelihood of a successful exploit is reduced.
“The vulnerability is due to a use-after-free memory error in the ALSA sequencer interface of the affected application. An attacker could exploit this vulnerability by running a crafted application on a targeted system. A successful exploit could allow the attacker to gain elevated privileges on the targeted system,” Cisco explains in an advisory published on Friday, October 13.
Discovered by Michael23 Yu and already confirmed by Kernel.org, the bug starts with a potential race window that opens when creating and deleting a port via ioctl.
The issue is that snd_seq_create_port() creates the port object and returns its pointer, but can be deleted immediately by another thread because it doesn't take the refcount. snd_seq_ioctl_create_port() still calls for snd_seq_system_client_ev_port_start() with the created port object being deleted, thus triggering the use-after-free.
A patch has been already published on the ALSA project’s website: “it's fixed simply by taking the refcount properly at snd_seq_create_port() and letting the caller unref the object after use. Also, there is another potential use-after-free by sprintf() call in snd_seq_create_port(), and this is moved inside the lock.”
Security Pros Admit Snooping on Corporate Network: Survey
18.10.2017 securityweek IT
IT security professionals, particularly executives, often access information that is not relevant to their day-to-day work, according to a new One Identity study focusing on “snooping” on the corporate network.
Dimensional Research polled more than 900 IT security professionals on behalf of One Identity. The respondents were from various types of companies in the United States, the United Kingdom, Germany, France, Australia, Singapore and Hong Kong, with at least 500 employees.
When asked if their company’s employees ever attempt to access information that is not necessary for their day-to-day work, 92% admitted it happens and 23% said it happens frequently. There are no major differences based on region or the size of the company.
Roughly two-thirds of the IT security pros that took part in the survey admitted snooping themselves, although 51% claim they do it rarely. Professionals from the U.S. seem to snoop the least (50%) while ones in Germany snoop the most (80%).
Interestingly, executives appear to be the guiltiest (71% said they snoop), followed by managers (68%) and other members of the IT security team (56%).
Globally, one in three IT security professionals who took part in the survey said they had accessed sensitive information about their company’s performance, despite not being required to do so as part of their job. This behavior can be seen more in Europe and Asia, and less in the U.S. and Australia, the report shows.
Again, executives and managers are more likely to look at company performance data compared to non-managers.
The survey also found that cybersecurity professionals working in the technology sector are most likely to look for data on their organization’s performance.
“While insider threats tend to be non-malicious in intent, our research depicts a widespread, intrusive meddling from employees when it comes to information that falls outside their responsibility -- and it could be that meddling that ends up putting their employers in hot water,” explained John Milburn, president and general manager of One Identity.
“Without proper governance of access permissions and rights, organizations give employees free reign to move about the enterprise and access sensitive information like financial performance data, confidential customer documentation, or a CEO's personal files. If that information winds up in the wrong hands, corporate data loss, customer data exposure or compliance violations are possible risks that could result in irreversible damage to the business's reputation or financial standing,” Milburn added.
Supreme Court Will Hear U.S. Vs Microsoft Privacy Case
18.10.2017 securityweek BigBrothers
World Will Watch the U.S. Government Vs Microsoft Played Out in the Supreme Court
The continuing battle between the U.S. government and Microsoft over access to private emails stored in Ireland is going to the Supreme Court. The case was accepted by the Supreme Court on Monday.
It began in 2013 when the government served a search warrant on Microsoft, seeking emails it believed would help in the prosecution of a drugs-trafficking case. Microsoft handed over relevant information stored in America, but declined to deliver emails stored in Ireland. It argued overreach, claiming that a search warrant could only apply within U.S. borders.
The government went to court to force Microsoft to comply. At first its warrant was upheld, but Microsoft appealed and the U.S. Court of Appeals for the 2nd Circuit subsequently overturned the ruling.
The basic arguments are relatively simple. The government contends that an inability to access evidence pertaining to U.S. means that "hundreds if not thousands of investigations of crimes -- ranging from terrorism, to child pornography, to fraud -- are being or will be hampered by the government's inability to obtain electronic evidence." It holds that the warrant is valid because the actual search would be conducted in the U.S.
Microsoft contends that the relevant law, the Stored Communications Act of 1986, was written in an age that had no concept of private emails being stored in different locations across the globe. But it also claims there are wider issues to consider. "If U.S. law enforcement can obtain the emails of foreigners stored outside the United States," wrote Microsoft's president and chief legal officer Brad Smith in a blog post yesterday, "what's to stop the government of another country from getting your emails even though they are located in the United States?"
The current laws were written for the era of the floppy disk, he added, "not the world of the cloud. We believe that rather than arguing over an old law in court, it is time for Congress to act by passing new legislation, such as the International Communications Privacy Act (ICPA) of 2017."
Writing in the Volokh Conspiracy blog yesterday, George Washington University law professor Orin Kerr points out that it is unusual for the Supreme Court to hear a case without lower court split. "It's typical for the justices to wait for lower courts to divide on an issue before they will step in," he wrote. "Relying on splits uses lower-court disagreement as a signal for the kind of difficult and important issues that the justices need to resolve." It is, he suggests, "a recognition among the justices of the tremendous importance of digital evidence collection. Whatever the right answers are, the justices need to provide them."
While the drama is being played out on the U.S. legal stage, it is being watched closely around the world -- and no more so than in Europe. Europe has a different attitude towards privacy than the U.S., typified first in the European Data Privacy Directive, and now in the European General Data Protection Regulation (GDPR). Both require that European personal data should not be exported to a location with lower privacy protections than in Europe. The U.S. is considered one such location.
To get round this potential impasse, Europe and the U.S. developed a Safe Harbor arrangement to allow American companies to export European data to servers in America; but this was thrown out by the European Court of Justice (the EU's equivalent to the Supreme Court) in September 2015. The primary reason was unfettered access to personal data by the U.S. government.
Since then the two governments have developed Privacy Shield as a stronger replacement for Safe Harbor -- but Privacy Shield has not yet been tested in the courts. Europe's reaction to the US government's potential ability to unilaterally extract European data from within Europe will test Privacy Shield to the limits.
"In a keenly watched case," summarizes Robert Cattanach, a partner at the international law firm Dorsey & Whitney, "the US Supreme Court has agreed to review a decision by the Second Circuit Court of Appeals that Microsoft did not have to turn over user data stored overseas in response to a search warrant issued under the Stored Communication Act. The case pits the interests of law enforcement access to information against concerns over government overreach, and could have ramifications globally as other nations likely will adapt their policies regarding access to information stored in other countries based on what the US Supreme Court decides. Privacy advocates have decried the prospect of borderless search authority by governments across the world, while law enforcement have painted the specter of criminal activities being shielded by convenient placement of data. All of this is being played out as the European Union continues its review of the Privacy Shield measure that allows the transfer of personal data of EU residents to the US under the presumption that it can be adequately protected."
ATM Malware Sold on Underground Markets for $5K
18.10.2017 securityweek Virus
A recently discovered piece of malware targeting automated teller machines (ATM) is being sold on underground markets for $5,000, Kaspersky Lab reports.
Dubbed CUTLET MAKER, the malware is being sold as part of a kit that also consists of a password generator and a Stimulator, which is an application that can grab information on the status of cash cassettes in a target ATM (such as currency, value, and the amount of notes).
Kaspersky's security researchers discovered the forum post advertising the malware in May 2017 and say that the offer was initially published on AlphaBay, a darknet marketplace that was taken down over the summer. The post provides information on the required equipment and targeted ATM models, along with tips and tricks for the malware’s operation and part of a detailed manual for the toolkit.
The manual “Wall ATM Read Me.txt” was observed being distributed as a plain text file, but the researchers say that it was written in poor English and with bad text formatting. The text contained slang and grammatical mistakes that pointed to a Russian author, and the malware’s name suggests the same (Russian slang term “Cutlet” means “a bundle of money”), the researchers reveal.
According to Kaspersky, the crimeware kit is a collection of programs possibly written by different authors, but the same protection was used for both CUTLET MAKER and Stimulator. There is also a simple terminal-based application called c0decalc that hasn’t been protected at all.
The researchers also say that the malware’s functionality suggests that two people should be involved in the theft, namely a “drop” and a “drop master”.
“Access to the dispense mechanism of CUTLET MAKER is password protected. Though there could be just one person with the c0decalc application needed to generate a password. Either network or physical access to an ATM is required to enter the code in the application text area and also to interact with the user interface,” the researchers say.
Kaspersky found different versions of the main component, with the first known version apparently submitted to a public multiscanner service on June 22, 2016.
“This type of malware does not affect bank customers directly, it is intended for the theft of cash from specific vendor ATMs. CUTLET MAKER and Stimulator show how criminals are using legitimate proprietary libraries and a small piece of code to dispense money from an ATM,” Kaspersky notes.
Countermeasures against such malware attacks include default-deny policies and device control, the first of which prevents criminals from running their own code on the ATM’s internal PC. According to Kaspersky, the attackers using this malware might have had physical access to the PC, possibly through USB drives used to install the malware onto the machine. Device control software should prevent the connection of new devices, such as USB sticks.
BAE Systems report links Taiwan heist to North Korean LAZARUS APT
18.10.2017 securityaffairs APT
Researchers at BAE Systems investigated the recent cyber-heist that targeted a bank in Taiwan and linked the action to the notorious Lazarus APT group.
The activity of the Lazarus APT Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. Security researchers discovered that North Korean Lazarus APT group was behind recent attacks on banks, including the Bangladesh cyber heist.
According to security experts, the group was behind, other large-scale cyber espionage campaigns against targets worldwide, including the Troy Operation, the DarkSeoul Operation, and the Sony Picture hack.
The Lazarus group, tracked by the U.S. government as Hidden Cobra, seems to be behind recent attacks against U.S. defense contractors, likely in cooperation with other hacker groups.
Back to the recent attack, hackers exploited the SWIFT global financial network to steal roughly $60 million from Taiwan’s Far Eastern International Bank.
Reports of $60M being stolen are not correct, the overall amount actually stolen by the hackers were considerably lower.
The hackers transferred the money outside the island, but the bank claimed it had managed to recover most of it.
The Sri Lanka police have recently arrested two men allegedly involved in the cyberheist, the suspects are accused to have hacked into computers at a Taiwan bank and stole millions of dollars
Researchers at BAE Systems have identified some of the tools used in the cyber heist and linked them to the Lazarus‘s arsenal.
Researchers believe attackers used a piece of ransomware known as Hermes as a distraction tactic. According to researchers at McAfee, the Hermes variant used in the attack on the Taiwanese bank did not display a ransom note, a circumstance that suggests it wasn’t used for a different purpose, distraction.
“Was the ransomware used to distract the real purpose of this attack? We strongly believe so,” McAfee researchers said. “Based on our sources, the ransomware attack started in the network when the unauthorized payments were being sent.”
Lazarus operators likely used the Hermes ransomware on the bank’s network to interfere with the investigations and destroy evidence of their attack.
“The Hermes strain used on FEIB’s network did not change the infected computer’s wallpaper and didn’t leave a flashy ransom note behind, like the original Hermes note, portrayed below.” reported Bleeping computer.
“Instead, the Hermes version used in the FEIB attacks only showed a popup with the text “finish work” and left a file named “UNIQUE_ID_DO_NOT_REMOVE” in every directory.”
The Hermes samples analyzed by researchers at BAE Systems drop a ransom note in each encrypted folder.
The experts also analyzed another strain of malware used in the attack dubbed Bitsran, it is a loader used to spreads a malicious payload on the targeted network. The analysis of its code revealed the presence of hardcoded credentials for the network of the Far Eastern International Bank. The malware was likely used in a reconnaissance phase.
“Sample #2 [Bitsran] is designed to run and spread a malicious payload on the victim’s network.” states the report.
“The malware then enumerates all processes, searching for specific anti-virus processes and attempts to kill these using the command line tool taskkill.”
Other malware used by the attackers are the same used by the Lazarus group, including in attacks aimed at financial organizations in Poland and Mexico.

The malicious code contains string written in the Russian Language, but researchers believe is a false flag to deceive them.
The sample of Hermes ransomware analyzed by the experts checks the infected machine’s language settings and stopped running if use Russian, Ukrainian or Belarusian languages. This feature widely adopted by Russian and Ukrainian vxers who often avoid targeting machines in their country. However, experts speculate this could also be a false flag.
“The ransomware calls GetSystemDefaultLangID() to obtain language identifier for the system locale. It contains a list of three system language codes: 0x0419 (Russian), 0x0422 (Ukrainian), and 0x0423 (Belarusian). However, it only checks against the last two, and, if matching, the malware quits. Whether this is a false-flag or not is unknown.” states the analysis.
Below the hallmarks of the Lazarus group that were recognized by BAE experts in the attack on the Taiwanese Far Eastern International Bank:
Destination beneficiary accounts in Sri Lanka and Cambodia – both countries have been used previously as destinations for Lazarus’ bank heist activity;
Use of malware previously seen in Lazarus’ Poland and Mexico bank attacks. Where these files were found and the context of their use needs to be confirmed, but could provide a crucial attributive link;
Use of unusual ransomware, potentially as a distraction.
“Despite their continued success in getting onto payment systems in banks, the Lazarus group still struggle getting the cash in the end, with payments being reversed soon after the attacks are uncovered,” concluded BAE Systems.
“The group may be trying new tricks to disrupt victims and delay their ability to respond – such as different message formats, and the deployment of ransomware across the victim’s network as a smokescreen for their other activity. It’s likely they’ll continue their heist attempts against banks in the coming months and we expect they will evolve their modus operandi to incorporate new ways of disrupting victims (and possibly the wider community) from responding,”
CUTLET MAKER ATM malware offered for 5000 USD on darknet forum
18.10.2017 securityaffairs Virus
Hacking ATM could be very easy thanks to the availability of the CUTLET MAKER ATM malware on an underground hacking forum.
Wannabe crooks can buy an ATM malware on a Darknet market for around $5000, the discovery was made by researchers at Kaspersky Lab that noticed a forum post advertising the malicious code dubbed Cutlet Maker.
“In May 2017, Kaspersky Lab researchers discovered a forum post advertising ATM malware that was targeting specific vendor ATMs. The forum contained a short description of a crimeware kit designed to empty ATMs with the help of a vendor specific API, without interacting with ATM users and their data.” states the blog post published by Kaspersky Lab. “The post links to an offer that was initially published on the AlphaBay Darknet marketplace, which was recently taken down by the FBI.”

The post was initially proposed on the AlphaBay black marketplace that was recently shut down by law enforcement.

The forum post includes a description of the malware and a detailed manual for the malware toolkit. The crimeware kit was designed to target various Wincor Nixdorf ATM models using a vendor API, without interacting with ATM users and their data.
The manual “Wall ATM Read Me.txt” was likely written by a native Russian-speaker with a poor English, it also mentions the Tyupkin ATM malware used to conduct Jackpotting attacks worldwide.
The manual provides a detailed description of all parts composing the toolset and how to use them. The list of crimeware from the kit consists of CUTLET MAKER ATM malware, the core element, with a password generator included and the Stimulator that is an application used to gather cash cassette statuses of a target ATM.
Another component is the ‘c0decalc‘ that is a simple terminal-based application without any protection at all.
Experts noticed that the crimeware kit is composed of programs likely developed by different authors.
The functionality of the Cutlet Maker malware suggests that two distinct roles are supposed to be involved in the cyber heist, the “drop” and “drop master.”
The ATMjackpot crew posted four videos that show how someone can gain access to an ATM’s USB port, connect the needed hardware, run the malware, and make the ATM spit out cash. Bleeping Computer has uploaded two of the four videos on YouTube, embedded below. We removed the sound from one video as it contained a copyrighted song.
“Access to the dispense mechanism of CUTLET MAKER is password protected. Though there could be just one person with the c0decalc application needed to generate a password,” the researchers say.
“Either network or physical access to an ATM is required to enter the code in the application text area and also to interact with the user interface.”
The experts concluded cyber “criminals are using legitimate proprietary libraries and a small piece of code to dispense money from an ATM.”
According to Bleepingcomputer, crooks launched a new website named ATMjackpot and started offering the same ATM malware including some modifications on demand.
The ATMjackpot hackers also published four videos that show how someone can gain access to an ATM’s USB port, connect the hardware, and execute the malware to control the machine.
The Cutlet Maker is currently offered on the ATMjackpot website for $1,500 worth of Bitcoin.
“Cutlet Maker is currently sold on the ATMjackpot portal for $1,500 worth of Bitcoin, a price that will double starting with the buyer’s second month.” reported Bleepingcomputer.com
“The price of this fee represents one credit, and one credit is valid for cashing out one ATM.”
Serious Crypto-Flaw Lets Hackers Recover Private RSA Keys Used in Billions of Devices
17.10.2017 thehackernews Vulnerebility
If you think KRACK attack for WiFi is the worst vulnerability of this year, then hold on…
...we have got another one for you which is even worse.
Microsoft, Google, Lenovo, HP and Fujitsu are warning their customers of a potentially serious vulnerability in widely used RSA cryptographic library produced by German semiconductor manufacturer Infineon Technologies.
It's noteworthy that this crypto-related vulnerability (CVE-2017-15361) doesn't affect elliptic-curve cryptography and the encryption standard itself, rather it resides in the implementation of RSA key pair generation by Infineon's Trusted Platform Module (TPM).
Infineon's Trusted Platform Module (TPM) is a widely-used, dedicated microcontroller designed to secure hardware by integrating cryptographic keys into devices and is used for secured crypto processes.
This 5-year-old algorithmic vulnerability was discovered by security researchers at Masaryk University in the Czech Republic, who have released a blog post with more details about the weakness as well as an online tool to test if RSA keys are vulnerable to this dangerous flaw.
ROCA: Factorization Attack to Recover Private RSA Keys
Dubbed ROCA (Return of Coppersmith's Attack), the factorization attack introduced by the researchers could potentially allow a remote attacker to reverse-calculate a private encryption key just by having a target's public key—thanks to this bug.
"Only the knowledge of a public key is necessary and no physical access to the vulnerable device is required," the researchers said. "The vulnerability does NOT depend on a weak or a faulty random number generator—all RSA keys generated by a vulnerable chip are impacted."
This could eventually allow the attacker to impersonate key owner, decrypt victim's sensitive data, inject malicious code into digitally signed software, and bypass protections that prevent accessing or tampering with the targeted computer.
ROCA Attack Exposes Billions of Devices to Attack
The ROCA attack affects chips manufactured by Infineon as early as 2012 and is feasible for key lengths, including 1024 and 2048 bits, which is most commonly used in the national identity cards, on PC motherboards to securely store passwords, in authentication tokens, during secure browsing, during software and application signing, and with message protection like PGP.
The flaw also weakens the security of government and corporate computers protected using Infineon's cryptographic library and chips.
Majority of Windows and Google Chromebook devices developed by HP, Lenovo and Fujitsu are amongst those affected by the ROCA attack.
"We found and analyzed vulnerable keys in various domains including electronic citizen documents, authentication tokens, trusted boot devices, software package signing, TLS/HTTPS keys and PGP," the researchers said.
"The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable."
More Details, Testing Tool, and Patches
The security researchers have released a brief blog post about the flaw, which includes a number of tools for detection, mitigation and workarounds.
The vulnerability was discovered and reported to Infineon Technologies in February this year and the researchers will present their full findings, including the factorization method, on November 2nd at the ACM Conference on Computer and Communications Security.
Their research paper, titled "The Return of Coppersmith's Attack: Practical Factorization of Widely Used RSA Moduli" (ROCA), will also be released after their presentation.
So, companies and organisations have enough time to change affected encryption keys before the details of how this vulnerability works and could be exploited are released.
Major vendors including Infineon, Microsoft, Google, HP, Lenovo, and Fujitsu have already released the software updates for their relevant hardware and software as well as guidelines for a mitigation of this vulnerability.
"Some Windows security features and potentially third-party software rely on keys generated by the TPM (if available on the system)," according to a Microsoft advisory. "Microsoft is releasing Windows security updates to help work around the vulnerability by logging events and by allowing the generation of software based keys."
Therefore, users are strongly recommended to patch their devices as soon as possible—AGAIN!
Microsoft Kept Secret That Its Bug-Tracking Database Was Hacked In 2013
17.10.2017 thehackernews Vulnerebility
It was not just Yahoo among "Fortune 500" companies who tried to keep a major data breach incident secret.
Reportedly, Microsoft had also suffered a data breach four and a half years ago (in 2013), when a "highly sophisticated hacking group" breached its bug-reporting and patch-tracking database, but the hack was never made public until today.
According to five former employees of the company, interviewed separately by Reuters, revealed that the breached database had been "poorly protected with access possible via little more than a password."
This incident is believed to be the second known breach of such a corporate database after a critical zero-day vulnerability was discovered in Mozilla's Bugzilla bug-tracking software in 2014.
As its name suggests, the bug-reporting and patch-tracking database for Windows contained information on critical and unpatched vulnerabilities in some of the most widely used software in the world, including Microsoft's own Windows operating system.
The hack was believed to be carried out by a highly-skilled corporate espionage hacking group known by various names, including Morpho, Butterfly and Wild Neutron, who exploited a JAVA zero-day vulnerability to hack into Apple Mac computers of the Microsoft employees, "and then move to company networks."
With such a database in hands, the so-called highly sophisticated hacking group could have developed zero-day exploits and other hacking tools to target systems worldwide.
There's no better example than WannaCry ransomware attack to explain what a single zero-day vulnerability can do.
"Bad guys with inside access to that information would literally have a ‘skeleton key’ for hundreds of millions of computers around the world," said Eric Rosenbach, who was American deputy assistant secretary of defence for cyber at the time of the breach.
When Microsoft discovered the compromised database in earlier 2013, an alarm spread inside the company.
Following the concerns that hackers were using stolen vulnerabilities to conduct new attacks, the tech giant conducted a study to compare the timing of breaches with when the bugs had entered the database and when they were patched.
Although the study found that the flaws in the stolen database were used in cyber attacks, Microsoft argued the hackers could have obtained the information elsewhere, and that there's "no evidence that the stolen information had been used in those breaches."
Former employees also confirmed that the tech giant tightened up its security after the 2013 hacking incident and added multiple authentication layers to protect its bug-reporting system.
However, three of the employees believes the study conducted by Microsoft did not rule out stolen vulnerabilities being used in future cyber attacks, and neither the tech giant conducted a thorough investigation into the incident.
On being contacted, Microsoft declined to speak about the incident, beyond saying: "Our security teams actively monitor cyber threats to help us prioritise and take appropriate action to keep customers protected."
Dangerous Malware Allows Anyone to Empty ATMs—And It’s On Sale!
17.10.2017 thehackernews Virus
Hacking ATM is now easier than ever before.
Usually, hackers exploit hardware and software vulnerabilities to hack ATMs and force them to spit out cash, but now anyone can simply buy a malware to steal millions in cash from ATMs.
Hackers are selling ready-made ATM malware on an underground hacking forum that anybody can simply buy for around $5000, researchers at Kaspersky Lab discovered after spotting a forum post advertising the malware, dubbed Cutlet Maker.
The forum post provides a brief description and a detailed manual for the malware toolkit designed to target various ATMs models with the help of a vendor API, without interacting with ATM users and their data.
Therefore, this malware does not affect bank customers directly; instead, it is intended to trick the bank ATMs from a specific vendor to release cash without authorisation.
The manual also mentions an infamous piece of ATM malware, dubbed Tyupkin, which was first analysed in 2014 by Kaspersky Lab and used by an international cybercrime gang to conduct Jackpotting attack and make Millions by infecting ATMs across Europe and beyond.
The list of crimeware contains in the toolkit includes:
Cutlet Maker—ATM malware which is the primary element of the toolkit
Stimulator—an application to gather cash cassette statuses of a targeted ATM
c0decalc—a simple terminal-based application to generate a password for the malware.
According to Kaspersky researchers, the functionality of the Cutlet Maker malware suggests that two people are supposed to be involved in the ATM money theft—the roles are called "drop" and "drop master."
"Access to the dispense mechanism of CUTLET MAKER is password protected. Though there could be just one person with the c0decalc application needed to generate a password," the researchers say.
"Either network or physical access to an ATM is required to enter the code in the application text area and also to interact with the user interface."
In order to operate, the application needs a special library, which is part of a proprietary ATM API and controls the cash dispenser unit—this shows how cyber "criminals are using legitimate proprietary libraries and a small piece of code to dispense money from an ATM."
The price of this ATM malware toolkit was $5000 at the time of Kaspersky's research.
The advertisement of this Cutlet Maker ATM malware was initially published on the AlphaBay Darknet marketplace, which was recently taken down by the FBI.
Vendors Race to Fight KRACK Wi-Fi Attacks
17.10.2017 securityweeek Attack
Technology companies worldwide have released or are working on releasing patches to address the dangerous Wi-Fi vulnerabilities publicly disclosed this week.
Setting the stage for a new attack method called Key Reinstallation Attack, or KRACK, these vulnerabilities affect the Wi-Fi standard itself and potentially expose all Wi-Fi Protected Access II (WPA2) protocol implementations.
An attacker capable of exploiting the issues could steal sensitive information transmitted over Wi-Fi, including credit card numbers, passwords, chat messages, emails, photos, and more. All major operating systems, including Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others, are affected.
The good news, however, is that the attacker needs to be in within range of an affected wireless access point, and that only data encrypted using the WPA2 protocol is exposed. Data encrypted using other standards, including HTTPS, TLS, and the like, should be safe from this attack.
What’s more, the Wi-Fi Alliance says that there is no evidence that the vulnerabilities have been exploited maliciously and confirmed that a straightforward software update should resolve them. However, the industry organization has already released a vulnerability detection tool for use by any Wi-Fi Alliance member.
As the US-CERT noted in its advisory, the issues affect the Wi-Fi standard itself, meaning that all correct implementations are exposed. Thus, there’s a general consensus of urgency among top vendors to address the bug through software updates, and some of them have already released patches.
Microsoft has already addressed the issue its October 2017 patches and published an advisory on the matter. Apple is reportedly taking steps in this direction by including patches in the latest beta releases of macOS, iOS, tvOS, and watchOS.
Android 6.0 and above and Linux were said to be affected the most, with the attack being “exceptionally devastating” against them. While security updates have been released for Linux, Google seems determined to address the issue in the coming weeks, most likely with the November 2017 monthly Android patches.
The issue is being addressed in Debian, Fedora, Red Hat, and Ubuntu. Patches are available for OpenBSD as well, and are being prepared for the FreeBSD Project.
Intel has released an advisory listing all affected products, while Netgear has released fixes for some products and is working on updates for others. Cisco too has released patches for affected products, the same as Fortinet, MikroTik, Ubiquiti Networks, WatchGuard, and Aruba. Zyxel also confirmed that some of its products are affected.
The list of affected and potentially affected vendors is much more extensive than that, as US-CERT has revealed. Most of the vendors were notified on the vulnerabilities in late August, but it’s yet unclear how many of them are affected.
DHS Orders Federal Agencies to Use DMARC, HTTPS
17.10.2017 securityweeek Safety
The U.S. Department of Homeland Security (DHS) has issued a binding operational directive requiring all federal agencies to start using web and email security technologies such as HTTPS, DMARC and STARTTLS within the next few months.
Within the next 30 days, agencies will have to develop a plan of action for implementing the requirements of Binding Operational Directive (BOD) 18-01.
Agencies have been given 90 days to configure all Internet-facing email servers to use STARTTLS, a protocol command that allows clients to indicate that they want unprotected connections upgraded to a secure connection using SSL or TLS.
The DHS also wants them to gradually roll out DMARC (Domain-based Message Authentication, Reporting and Conformance), an email authentication, policy, and reporting protocol designed to detect and prevent email spoofing. Organizations using DMARC can specify what happens to unauthenticated messages: they can be monitored but still delivered to the recipient’s inbox (none), they can be moved to the spam or junk folder (quarantine), or their delivery can be blocked completely (reject).
DHS wants federal agencies to use HTTPS, DMARC
Within 90 days, agencies must roll out a DMARC policy that is set at least to “none,” and at least one address needs to be configured to receive aggregate and/or failure reports. Within one year, the DMARC policy must be set to “reject.”
In the same timeframe, the DHS wants all second-level agency domains to have valid SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) records, which allow organizations to specify which servers are allowed to send emails using their domain.
Federal agencies must also improve email security by ensuring that SSLv2 and SSLv3, known to have protocol weaknesses, are disabled on mail servers. The 3DES and RC4 ciphers, which are also considered weak, must also be disabled. Agencies have been given 120 days to complete this task.
As for web security, SSLv2, SSLv3, 3DES and RC4 must be disabled on web servers, and all public websites need to be served via an HTTPS connection with HTTPS Strict Transport Security (HSTS).
“It is critical that U.S. citizens can trust their online engagements with all levels of the federal government,” said Jeanette Manfra, Assistant Secretary for the Office of Cybersecurity and Communications at the DHS, at a cybersecurity roundtable hosted by the Global Cyber Alliance. “Today, we are calling on all federal agencies to deploy a toolkit of advanced cybersecurity technologies that will enable them to better fulfill our ultimate mission – serving and protecting the American public.”
The decision to order the use of these security technologies comes just months after Senator Ron Wyden urged the DHS to get federal agencies to deploy DMARC for .gov domains.
A study conducted recently by email security firm Agari showed that many Fortune 500, FTSE 100 and ASX 100 companies still haven’t properly implemented DMARC.
BlackBerry Patches Vulnerabilities in Workspaces Server
17.10.2017 securityweeek Vulnerebility
Updates released by BlackBerry for some Workspaces Server components address two vulnerabilities, including a high severity flaw that can be exploited for arbitrary code execution.
BlackBerry Workspaces, formerly known as WatchDox, is a platform that allows organizations to securely access, share and manage important files.
Eric Rafaloff, a researcher at Gotham Digital Science (GDS), discovered that some BlackBerry Workspaces Server components are affected by a couple of flaws.
One of the security holes, CVE-2017-9368, is related to a file server API that is designed for uploading and downloading files. Sending specially crafted HTTP GET requests to this API allows an unauthenticated attacker to view the file server’s source code.
After exploiting this vulnerability and looking at the source code, Rafaloff found an even more serious issue – a directory traversal that allows an unauthenticated attacker to upload a web shell to the server’s webroot and leverage it for code execution. This flaw is tracked as CVE-2017-9367.
“For example, upon exploitation of this vulnerability, GDS was able to read the contents of the Workspace Server’s database and compromise highly sensitive information,” GDS said in its advisory.
The vulnerabilities were reported to BlackBerry in May and they were patched this week. The company pointed out that exploitation of the flaws requires the attacker to know the structure of the Workspaces Server directory and have access to the targeted organization’s network. BlackBerry also noted that the exposed source code is not unique to each customer, and encrypted information obtained by exploiting CVE-2017-9367 remains protected by strong encryption technology.
BlackBerry has determined that the impacted components are Appliance-X versions 1.11.2 and earlier, vApp versions 5.6.0 to 5.6.6, and vApp versions 5.5.9 and earlier. The issues have been addressed with the release of Appliance-X version 1.12.0 and vApp version 5.7.2. Workspaces Server users and administrators who deploy on-premises versions of BlackBerry Workspaces in their organization have been advised to install the updates.
Taiwan Bank Heist Linked to North Korean Hackers
17.10.2017 securityweeek CyberCrime
A recent cyber-heist that targeted a bank in Taiwan has been linked by security researchers to an infamous threat group believed to be operating out of North Korea.
Hackers exploited the SWIFT global financial network to steal roughly $60 million from Taiwan’s Far Eastern International Bank. The money was transferred to several countries, but bank officials claimed they had managed to recover most of it. Two individuals were arrested earlier this month in Sri Lanka for their role in the operation.
Researchers at BAE Systems have identified some of the tools used in the attack and found connections to the North Korean threat actor known as Lazarus. This group is also believed to be behind the 2014 attack on Sony Pictures and campaigns targeting several banks, including Bangladesh’s central bank.
The attack on the Bangladesh bank, which resulted in the theft of $81 million, also involved the SWIFT system. Similar methods were also used to target several other banks, but SWIFT said some of the operations failed due to the new security measures implemented by the company.
While it’s still unclear how attackers gained access to the systems of Far Eastern International Bank, an analysis of various malware samples apparently involved in the attack suggests that the hackers may have used a piece of ransomware as a distraction.
The ransomware involved in the attack is known as Hermes. According to Bleeping Computer, the threat surfaced in February and its latest version has an encryption mechanism that makes it impossible to recover files without paying the ransom.
However, researchers at McAfee discovered that the Hermes variant used in the attack on the Taiwanese bank did not display a ransom note, which led them to believe it may have been only a distraction.
“Was the ransomware used to distract the real purpose of this attack? We strongly believe so,” McAfee researchers said. “Based on our sources, the ransomware attack started in the network when the unauthorized payments were being sent.”
BAE Systems has seen samples that drop a ransom note in each encrypted folder, but even they believe Hermes may have been used to distract the bank’s security team.
Another malware sample linked by BAE Systems to this attack is a loader named Bitsran, which spreads a malicious payload on the targeted network. This threat contained what appeared to be hardcoded credentials for Far Eastern International’s network, which suggests the threat group may have conducted previous reconnaissance.
Some pieces of malware discovered by BAE Systems are known to have been used by the Lazarus group, including in attacks aimed at financial organizations in Poland and Mexico. The malware includes commands and other messages written in Russia, which experts believe is likely a false flag designed to throw off investigators.
It’s worth noting that the Hermes ransomware samples checked the infected machine’s language settings and stopped running if Russian, Ukrainian or Belarusian was detected. This is common for malware created by Russian and Ukrainian hackers who often avoid targeting their own country’s citizens. However, this could also be a false flag.
Another piece of evidence linking the Taiwan bank attacks to Lazarus is the fact that money was transferred to accounts in Sri Lanka and Cambodia, similar to other operations attributed to the group.
Some experts believe that these bank heists and the WannaCry attack, which has also been linked by some to Lazarus, are campaigns launched by North Korea for financial gain. However, many of these operations don’t appear to have been very successful on this front.
“Despite their continued success in getting onto payment systems in banks, the Lazarus group still struggle getting the cash in the end, with payments being reversed soon after the attacks are uncovered,” BAE Systems researchers explained.
“The group may be trying new tricks to disrupt victims and delay their ability to respond – such as different message formats, and the deployment of ransomware across the victim’s network as a smokescreen for their other activity. It’s likely they’ll continue their heist attempts against banks in the coming months and we expect they will evolve their modus operandi to incorporate new ways of disrupting victims (and possibly the wider community) from responding,” they added.
ROCA vulnerability (CVE-2017-15361) allows attackers to recover users Private RSA Keys
17.10.2017 securityaffairs Vulnerebility
ROCA vulnerability (CVE-2017-15361) allows attackers to recover users Private RSA Keys, billion devices potentially impacted.
While security experts are discussing the dreaded KRACK attack against WiFi networks IT giants, including Fujitsu, Google, HP, Lenovo, and Microsoft are warning their customers of a severe flaw in widely used RSA cryptographic library produced by German semiconductor manufacturer Infineon Technologies.
The vulnerability, tracked as CVE-2017-15361, affects the implementation of RSA key pair generation by Infineon’s Trusted Platform Module (TPM).
Infineon TPM is a dedicated microcontroller designed to secure hardware by integrating cryptographic keys into devices and helps to shield against unauthorized access to the data stored by improving the system integrity.
The vulnerability in Infineon’s Trusted Platform Module (TPM), dubbed ROCA (Return of Coppersmith’s Attack), was discovered by security researchers at Masaryk University in the Czech Republic.
The researchers published the details of the ROCA vulnerability in a blog post and also published a tool online that could be used to test if RSA keys are vulnerable to this dangerous flaw.

According to the experts, the ROCA factorization attack could potentially allow a remote attacker to reverse-calculate a private encryption key just by having a target’s public key.
“A newly discovered vulnerability in generation of RSA keys used by a software library adopted in cryptographic smartcards, security tokens and other secure hardware chips manufactured by Infineon Technologies AG allows for a practical factorization attack, in which the attacker computes the private part of an RSA key. The attack is feasible for commonly used key lengths, including 1024 and 2048 bits, and affects chips manufactured as early as 2012, that are now commonplace.” reads the blog post.
“Only the knowledge of a public key is necessary and no physical access to the vulnerable device is required, The vulnerability does NOT depend on a weak or a faulty random number generator—all RSA keys generated by a vulnerable chip are impacted.”
Exploiting the ROCA vulnerability, an attacker can impersonate key owner, and abuse the private key for different purposes, including decryption of sensitive messages and forgery of signatures.
The ROCA attack works against differed key lengths, including 1024 and 2048 bits, which is widely used for differed applications, including the national identity cards and message protection like PGP.
“The actual impact of the vulnerability depends on the usage scenario, availability of the public keys and the lengths of keys used. We found and analyzed vulnerable keys in various domains including electronic citizen documents, authentication tokens, trusted boot devices, software package signing, TLS/HTTPS keys and PGP.” said the researchers. “The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable. The details will be presented in two weeks at the ACM CCS conference.”
The ROCA vulnerability was reported to Infineon Technologies in February, details about the flaw are included in the research paper titled “The Return of Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli” (ROCA).
The experts will present their findings, including the factorization method, on November 2nd at the ACM Conference on Computer and Communications Security.
Hurry up, change the affected keys before the experts will publicly reveal the findings of their research.
Major vendors, including Infineon, Microsoft, Google, HP, Lenovo, and Fujitsu have already addressed the ROCA vulnerability with software updates.
Let me close with an important reminder, vulnerable chips are pervasive and are sold also by other vendors that include in their architectures Infineon chips.
Even With The Best Email Spoofing Defences in The World, HMRC is Spoofed
17.10.2017 securityaffairs Spam
Even with the most advanced email protections in place and an entire government organization to support them, the bad actors were able to spoof Her Majesty’s Revenue and Customs (HMRC) emails to spread a Java-based remote administration tool to unsuspecting UK recipients.
In September 2017, Trustwave identified a scam campaign that pretended to come from HMRC. The bad actors registered the cousin domain ‘hmirc-gov.co.uk‘ and sent emails to unsuspecting UK citizens with the subject “VAT Return Query.” The message body warns the recipient that there was an error with their online VAT return as detailed in the attachment. The extra tricky part is that there was no attachment included with the message. What appeared to be an attachment was actually an embedded HTML image with a link to a Microsoft OneDrive location. A user clicking on the “attachment” would download a file named “VAT RETURN QUERY.ZIP” from OneDrive which in turn contains a file called “VAT Return Query.pdf.jar” This Jar file contains the Java RAT malware jRAT which is a popular remote administration tool widely used by bad actors. But HMRC claims to have the most advanced email spoofing protection. How did this happen?
The best email defenses are the ones that prevent the malicious emails from ever reaching the intended recipients. Big data algorithms are successful at limiting traditional attacks where the same email is sent to millions of people. This type of SPAM is pretty obvious when viewed in aggregate and it is rare to find it in your inbox these days. But there are a lot of phishers out there spending a lot of time finding ways around these big data driven defences. Sending emails to smaller groups of people is one way that might work since it starts to look like legitimate email traffic between trusted sender and recipient. The automated tools will likely catch the email if it comes from a suspicious domain (e.g. @J8eZY5FzPJ.net) so the bad actors want to impersonate a legitimate domain. They are able to make the email look however they want, it is simple to make it appear to come from a legitimate domain like your bank, or the tax office. If you can’t trust the email what can you do?
HRMC famously implemented Domain-based Message Authentication, Reporting and Conformance (DMARC) in 2016 after several years of preparation and experimentation. In the first year, they reduced the number of spoofed emails by 300 million! At this point, it is almost impossible for the criminals to send an email from the official HRMC domain. And yet in 2017, the bad actors were distributing jRAT malware under the guise of VAT refund issues at the HRMC. How did they accomplish this? DMARC is very effective at validating emails from legitimate domains, but it cannot defend against cousin domains which look similar enough to the legitimate domain to fool people. To understand this limitation, one must first understand how DMARC works. And to understand DMARC, one must understand SPF and DKIM.
Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) were implemented to provide a way for email recipients to distinguish between legitimate and spoofed emails. The SPF record is defined by the authorized owner of a domain and identifies email servers that are authorized to send email on behalf of that domain. Phishers shouldn’t have access to these authorized email servers so if the recipient’s email system checks the SPF record and compares it against the IP address noted in the message it can identify spoofed messages. Unfortunately, there are situations where SPF might also block legitimate emails messages. For example, if you forward an email message, the IP address of the email server is changed and it would fail the SPF record check — although it is not a malicious message. Similarly, if the authorized sender hasn’t implemented SPF protection, the recipient has no SPF record to validate against. For this reason, few recipients will automatically block ALL messages that fail the SPF validation. So it is an incomplete solution.
In addition to SPF, authorized senders can leverage DomainKeys Identified Mail (DKIM) to mark their email as legitimate. With DKIM, the sender digitally signs the message which allows the recipient to verify that the message came from an authorized sender — slightly different than SPF which is validating the specific, authorized email server. As with SPF, DKIM implementations are not complete, so recipients cannot rely solely on DKIM certificates to distinguish legitimate from unwanted email. They become one more piece of information for the automated tools to make decisions with but not a comprehensive tool.
Due to inconsistent implementations of SPF and DKIM, authorized senders and recipients have been slow to completely rely on these tools. Authorized senders do not know how well the configurations are working to protect their brand from spoofing, and recipients don’t know how many legitimate emails are being dropped by their filtering tools. Domain-based Message Authentication, Reporting and Conformance (DMARC) is intended to address these shortcomings. With DMARC enabled, the authorized sender is able to provide direction to recipients on how to deal with the message when it is received. For example, if the sender has implemented SPF, the DMARC record can instruct recipients’ email filters to drop any message that doesn’t pass SPF validation. In addition, the DMARC framework provides feedback to authorized senders identifying attempts to spoof their email domain.
From the HMRC example, we see that DMARC is very effective for protecting legitimate email domains, but it still doesn’t address the threat of cousin domains that can fool unsuspecting recipients.
“People will never leave HMRC alone because we have 50 million customers. But, we can make those criminals’ jobs as difficult as possible, and force them into using more spurious domains for this purpose, giving our customers a better chance to spot the phish. Sadly you’ll never end phishing as it’s too lucrative a business for the criminals. We just have to make things difficult and affect their ROI.”, says Ed Tucker, head of cyber-security at HMRC and recipient of the 2016 UK Security Professional of the Year award.
Even with the latest DMARC protections in place to validate emails from HMRC’s legitimate domain, the criminals were able to fool people with emails from a domain that looks very similar to the legitimate one — to a human. It is impractical to pre-authorize all email senders since email is the most common way of introduction for new companies so we need to receive an initial email to determine we wish to trust the recipient. We expect our automated tools to allow the trustworthy emails to get through and block the unwanted emails — but we don’t always know the difference ourselves until we receive the message. As good as the tools are, they will never be 100% so we will always have to rely on the human recipient for that last line of defence.
Cyberespionage group stolen Microsoft vulnerabilities DB back in 2013
17.10.2017 securityaffairs CyberSpy
Another day, another news about a clamorous data breach, this time the Reuters agency revealed that Microsoft suffered a major security breach back in 2013.
According to five former employees, hackers broke into the company vulnerabilities and bug reports database, but the news was never disclosed.
The former employees explained that Microsoft addressed all the vulnerabilities listed in the compromised database within months so that the vulnerabilities would have limited exploitation against Microsoft systems in the wild.
“Microsoft Corp’s secret internal database for tracking bugs in its own software was broken into by a highly sophisticated hacking group more than four years ago, according to five former employees, in only the second known breach of such a corporate database.” reported the Reuters.
You can imagine the importance of the archive for intelligence agencies and hackers, the database contained details of unfixed vulnerabilities in some of the most popular software and operating systems in the world.Spies for governments around the globe and other hackers covet such information because it shows them how to create tools for electronic break-ins.
The knowledge of such zero-day vulnerabilities would have been exploited in targeted attacks in the wild.
The employees attributed the attack to a “highly sophisticated hacking group,” likely they were referring a nation-state actor.
After the incident, Microsoft investigated every breach suffered by third-party companies in the following period to check if any of the vulnerabilities contained within the breached database were exploited in the attacks. The company declared that did not find any evidence of cyber attacks in the wild exploiting the information included in the hacked vulnerability database.
“Sometime after learning of the attack, Microsoft went back and looked at breaches of other organizations around then, the five ex-employees said. It found no evidence that the stolen information had been used in those breaches.” continued the Reuters.
The Reuters claims the threat actor behind the data breach is an APT group known Wild Neutron. (i.e. Morpho, Jripbot, Butterfly, ZeroWing, or Sphinx Moth). Wild Neutron is a financially motivated espionage group that targeted large enterprises, including Microsoft, Apple, Twitter, and Facebook.

According to the analysis published by Kaspersky Lab in 2015, the Morpho APT group is specialized in corporate espionage and has been active since at least 2011.
The researchers speculate that the group is responsible for the attacks in 2013 on the IT giants Apple, Facebook, Microsoft, and Twitter.
The above attacks were discovered in February 2013, a few weeks after, Microsoft admitted an attack, but it specified the attackers had limited access to its network.
“As reported by Facebook and Apple, Microsoft can confirm that we also recently experienced a similar security intrusion,” the company said on Feb. 22, 2013.
“We found a small number of computers, including some in our Mac business unit, that were infected by malicious software using techniques similar to those documented by other organizations. We have no evidence of customer data being affected, and our investigation is ongoing.”
Three of the five former employees declared that the vulnerability have been used in attacks in the wild.
“They absolutely discovered that bugs had been taken,” said one. “Whether or not those bugs were in use, I don’t think they did a very thorough job of discovering.”
The Morpho team exploited a Flash Player and Java zero-day in its attacks and digitally signed its malicious code by using stolen Acer Incorporated digital certificates.
The hackers exploited a Java zero-day, tracked as CVE-2013-0422, in the attacks against Twitter and Facebook. Hackers tricked Twitter and Facebook employees into visiting hacked forums hosting the Java zero-day exploit.
Wi-Fi WPA2 má kritickou chybu, všem hrozí krádeže citlivých dat
17.10.2017 SecurityWorld Zranitelnosti
Kritická zranitelnost protokolu WPA2, označovaná jako Krack (Key Reinstallation Attacks), má podle expertů potenciál degradovat zabezpečení Wi-Fi připojení prakticky pro všechna bezdrátová zařízení nebo sítě, což umožňuje útočníkům, aby špehovali internetovou komunikaci nebo dokonce injektovali škodlivý kód.
Dobrou zprávou je, že pokud používáte počítač se systémem Windows, jste již v bezpečí – tedy přinejmenším pokud použijete nové aktualizace, které Microsoft v průběhu minulého týdně potichu na Windows aplikoval.
Microsoft podle svých slov totiž vydal bezpečnostní aktualizaci 10. října a zákazníci, kteří mají povolenou službu Windows Update a používají aktualizace zabezpečení, jsou tak prý automaticky chránění.
Zranitelnost zabezpečovacího mechanizmu WPA2 včera uveřejnil Mathy Vanhoef, výzkumný pracovník Katholieke Universiteit Leuven v Belgii. Podle Vanhoefa slabiny v WPA2 umožnily zločincům číst informace přenášené po síti Wi-Fi, o které se podle protokolu myslí, že jsou zašifrovány.
"Útočníci mohou tuto techniku napadnout a následně číst informace, které byly dříve považované za bezpečně šifrované," tvrdí Vanhoef. To se podle něj může zneužít ke krádežím citlivých informací, jako jsou čísla kreditních karet, hesla, zprávy z chatu, e-maily, fotky a tak dále.
Krack se zaměřil na třetí krok ve čtyřkrokovém procesu "handshake" při ověřování. Ten se vykonává, když se klientské zařízení Wi-Fi pokouší připojit k chráněné síti Wi-Fi.
Šifrovací klíč se může během třetího kroku opakovaně přeposílat a pokud útočníci shromažďují a opakovaně opakují přenosy určitým způsobem, může být šifrování Wi-Fi kompromitované.
Macy, iPhony, telefony s Androidem, počítače se systémem Linux, směrovače a další zařízení potřebují záplaty, které je chrání před zranitelností. Naštěstí existují způsoby, jak se v mezidobí chránit – třeba formou využití VPN sítí.
„Spojení probíhající přes HTTPS jsou dodatečně šifrována a jejich obsah tedy zůstává zabezpečen. Záleží tedy na uživateli, jestli kontroluje přítomnost ´zeleného zámečku´ v adresním řádku (nicméně ne všechny webové stránky podporují HTTPS),“ tvrdí zpráva českého centra CSIRT.
Sám Vanhoef doporučuje dočasný zákaz funkce klientů na směrovačích a přístupových bodech a odpojení služby 802.11r. Pokud chcete více informací, problému se týkají následující CVE: CVE-2017-13077, 13078, 13079, 13080, 13081, 13082, 13084, 13086, 13087 a 13088.
Také podle Esetu jde o vážnou situaci, neboť zde není žádný jiný standard, kterým by bylo možné WPA2 okamžitě nahradit. Někteří výrobci hardwaru již nicméně bezpečnostní záplaty na své produkty vydali, ostatní by tak měli teprve učinit.
„Bude ještě zajímavé sledovat, kolik zařízení zůstane nakonec bez záplat,“ říká Miroslav Dvořák, technický ředitel Esetu. Podle něj uživatel může využít tzv. VPN, která vytvoří bezpečný šifrovaný tunel mezi ním a jeho či cílovou sítí. Tento ‚tunel‘ nemůže útočník napadnout, respektive nemá možnost číst probíhající komunikaci v čitelné formě.
Dalším doporučením je zkontrolovat si, zda je či bude v brzké době k dispozici bezpečnostní záplata pro jejich zařízení, která by tuto zranitelnost řešila.
„Ale pozor, některé z variant zranitelnosti se zdaleka netýkají pouze hardwaru, ale i například operačních systémů Android, Linux, Apple, Windows nebo OpenBSD,“ dodává Dvořák.
Nedejte šanci, aby vás obrali hackeři
17.10.2017 SecurityWorld APT
S útoky typu APT (Advanced Persistent Threat, pokročilá perzistentní hrozba) se firmy mohou setkat stále častěji – a roste také jejich závažnost. Stejně tak ale stoupají i náklady spojené s ochranou před touto hrozbou. Je vaše organizace připravená na boj proti útokům APT? Měla by.
Útoky APT odpovídají svému názvu – je to typ síťového útoku, při kterém útočník vybere konkrétní cíl, používá sociální inženýrství a pokročilé technologie k průniku do sítě a poté se zaměřuje na vybraný cíl po dobu týdnů, měsíců nebo let až do okamžiku, kdy se mu podaří dosáhnout plánovaného výsledku nebo kdy dojde ke zmaření útoku.
Jakmile se dostane do sítě, je cílem útočníka zůstat neodhalený, zatímco přitom používá některé typy malwaru k zachytávání důvěrných informací, jež nakonec odesílá do jiné lokality k analýze a následnému prodeji na černém trhu.
Útoky APT jsou vysoce organizované, někdy se jich účastní celý tým útočníků a mívají dostatek finančních a technologických zdrojů.
Přestože APT mohou používat běžné hackerské nástroje, častěji využívají sofistikovaný, na zakázku vytvořený software, u kterého je nižší pravděpodobnost odhalení systémem ochrany zabezpečení. Typy útoků APT a jejich mechanismy zahrnují útoky nultého dne, phishing, pokročilý malware a rovněž celou řadu forem zneužití webů.
Tento příspěvek se zaměřuje na pět způsobů ochrany majetku organizace před útoky APT. Důležité jsou přitom úplně všechny.
1. Implementace hloubkové obrany
Bezpečnostní experti zdůrazňují potřebu zabezpečení, které využívá vrstvy (neboli hloubkovou obranu) jako součást běžné strategie zabezpečení sítí. Hloubková obrana je také jedním z nejlepších způsobů, jak zastavit útok APT ještě předtím, než infiltruje síť.
Znamená to kontrolovat vstupy a výstupy sítě, používat firewally nové generace, nasadit systémy detekce a prevence vniknutí (IDS/IPS), systémy SIEM (správa informací a událostí zabezpečení), implementovat systém správy zranitelností, využívat silnou autentizaci a správu identit, udržovat aktuálnost oprav zabezpečení a používat ochranu koncových bodů.
Protože je malware často zdrojem útoků APT, potřebujete také vysoce spolehlivé řešení pro omezování rizika malwaru. Vzhledem k tomu, že útoky APT mohou využívat špičkové technologie, musí být vaše bezpečnostní vybavení také na špičce. Znamená to volit pokročilá řešení pro detekci na základě chování, kdykoli je to možné.
Vaším cílem je zvýšení obtížnosti počátečního průniku do sítě, ale i pokud by došlo k překonání této vrstvy, musí každá další vrstva zabezpečení představovat další významnou překážku, která zastaví šíření útoku nebo ho dostatečně zpomalí, aby ho bylo možné zjistit a eliminovat.
Protože útočníci neustále aktualizují své nástroje a hledají nové zranitelnosti (mezery v pancíři), musejí být vaše nástroje také aktuální.
Poznámka: V loňském roce tvořil obrat v segmentu řešení ochrany před útoky APT více než 1,9 miliardy dolarů. Společnost The Radicati Group v roce 2015 uvedla, že očekává do roku 2019 nárůst na více než 6,7 miliardy dolarů ročně.
Ne každé bezpečnostní řešení však musí udělat díru do rozpočtu. Například sada Emet (Enhanced Mitigation Experience Toolkit) od Microsoftu je bezplatným bezpečnostním nástrojem založeným na systému Windows, který doplňuje existující obranu zabezpečení a pomáhá detekovat a blokovat metody zneužívající zranitelnosti.
SecurityIQ je zase služba institutu InfoSec, která vám umožní zasílat personálu fiktivní phishingové e-maily k otestování povědomí o zabezpečení. Silné interní zásady zabezpečení a pravidelné hodnocení rizik a zabezpečení jsou také nezbytné. Umožňují zaměřit bezpečnostní kontrolu tam, kde na tom nejvíce záleží.
2. Využití metod sledování a detekce
Důkladné sledování bezpečnostních kontrol vám pomůže rozpoznat první varovné známky útoku APT, které se často objevují v podobě anomálií v protokolech, přenosech a ve formě dalších aktivit neodpovídajících profilům.
Je kriticky důležité sledovat veškeré příchozí a odchozí síťové přenosy, interní přenosy a všechna zařízení, která přistupují k vaší síti.
Nepřetržitý monitoring vám nejen pomůže odhalit podezřelou aktivitu co nejdříve, ale také omezuje možnosti eskalace oprávnění a dlouhodobé průniky. Výstupy z monitoringu mohou navíc sloužit jako forenzní důkazy, pokud se útok dostane až do takového bodu.
3. Využívání služby threat intelligence
Několik dodavatelů zabezpečení nabízí služby threat intelligence, v rámci kterých se z několika zdrojů sbírají surová data o nově vznikajících hrozbách a poté dochází k jejich analýze a filtrování za účelem vytvoření užitečných a k akci použitelných informací.
Tyto informace jsou často ve formě datových kanálů pro systémy řízení zabezpečení a také reportů pro manažery IT a ředitele, aby jim pomohly pochopit hrozby existující v jejich oboru.
Pro threat intelligence je klíčová souvislost globálních zpráv s hrozbami pro vlastní síť organizace. Bezpečnostní personál tak může v reálném čase rychle identifikovat a vyřešit hrozby s vysokým rizikem.
Útoky APT se mohou šířit různými metodami a mohou se zaměřovat na zranitelnosti, které ještě nejsou bezpečnostním společnostem známé, takže je nezbytné rozpoznávat příznaky útoku APT, co nejdříve to je možné.
Threat intelligence například často poskytne chybějící článek, který propojí anomálie zaznamenané v protokolu (log) sítě se zranitelností nultého dne.
4. Školení pro zvyšování povědomí o zabezpečení
Existuje dobrý důvod, proč se téměř v každé diskuzi o bezpečnosti IT zmiňuje nutnost školení pro zvyšování povědomí o zabezpečení.
Když zaměstnanci skutečně rozumějí tomu, jak je nebezpečné klikat na ošemetné odkazy v e-mailech, a dokážou rozpoznat metody sociálního inženýrství, stanou se z nich partneři v boji proti bezpečnostním hrozbám a nakonec to pomáhá chránit sítě a v nich uložená data.
Školení tohoto druhu musejí zahrnovat rychlý přehled bezpečnostních zásad organizace a také následků pro všechny zaměstnance, pokud by došlo k bezpečnostnímu incidentu v důsledku jejich činnosti.
V závislosti na okolnostech to může znamenat další školení, kritiku na personálním oddělení, nebo dokonce okamžité propuštění. Mějte však na paměti, že zaměstnanec obvykle chce dělat svou práci dobře a nechce být příčinou firemních ztrát plynoucích z útoku.
Nejlepším přístupem tedy je zdůrazňování pozitivních aspektů během školení pro zvyšování povědomí a různé formy motivace pro zvyšování znalostí o zabezpečení.
5. Plán reakce na incidenty
Dokonce i s největším úsilím a s využíváním drahých technologií se může stát, že v určitý okamžik dojde k narušení zabezpečení firmy: většina expertů se shoduje, že otázkou není „jestli“, ale „kdy“.
Použití solidního plánu reakcí na incidenty dokáže eliminovat útok, minimalizovat škody a zastavit další úniky dat – výsledkem je minimalizace následných škod na pověsti a značce.
Kromě popisu odpovědnosti jednotlivých pracovních rolí za konkrétní akce od identifikace po řešení by měl váš plán reakcí na incidenty obsahovat kroky k ochraně forenzních důkazů o narušení. Vaše organizace může tyto důkazy potřebovat k usvědčení útočníků, pokud dojde k jejich dopadení, což bohužel není příliš pravděpodobné.
Forenzní důkazy také pomohou vašemu týmu zabezpečení najít bezpečnostní díry, zesílit kontrolu a zabránit opakování v budoucnu. Jedním z dobrých nápadů také je seznámit se s frameworkem Cyber Kill Chain společnosti Lockheed Martin, který pracuje s modelem útoku a řeší každou posloupnost bezpečnostní události.
Znalost způsobů, jak útočník identifikuje cíl a prochází fázemi útoku, může pomoci personálu zabezpečení rozpoznat útok v rané fázi procesu.
Terčem útoků APT může být každá organizace bez ohledu na její velikost. Pochopení toho, jak útok APT funguje, vybudování nejlepší možné obrany v rámci vašich možností a vzdělávání vašeho personálu, tak aby dokázal rozpoznat vše podezřelé, může omezit škody a v některých případech i v první linii zabránit útoku.