
Hackers Can Stealthily Exfiltrate Data via Power Lines
14.4.2018 securityweek Hacking
Researchers have created proof-of-concept (PoC) malware that can stealthily exfiltrate data from air-gapped computers using power lines.
The malware, dubbed PowerHammer, is the work of researchers at the Ben-Gurion University of the Negev in Israel. The university has previously published research on jumping air gaps via magnetic fields, infrared cameras, router LEDs, scanners, HDD activity LEDs, USB devices, the noise emitted by hard drives and fans, and heat emissions.
PowerHammer exfiltrates data from a compromised machine by regulating its power consumption, which can be controlled through the workload of the device’s CPU. Sensitive pieces of information, such as passwords and encryption keys, can be stolen one bit at a time by modulating changes in the current flow.
Researchers have devised two versions of the PowerHammer attack: line level power-hammering and phase level power-hammering.
In the line level variant, the attacker intercepts the bits of data exfiltrated by the malware by tapping the compromised computer’s power cable. In the phase level attack, the attacker collects the data from the main electrical service panel. The data can be harvested using a non-invasive tap that measures the emissions on power cables, and converting them to a binary form via demodulation and decoding.
A computer’s CPU is a significant power consumer and its workload has a direct impact on power consumption and implicitly the flow of current in the device’s power cable. By overloading the CPU with calculations and stopping and starting the workload, it’s possible to generate a signal over the power lines at a specified frequency.
In the case of PowerHammer, the attacker establishes two different frequencies – one representing a “0” bit and another frequency representing a “1” bit.
During their experiments, researchers saw transfer rates of up to 1000 bits/sec for the line level power-hammering attack and 10 bits/sec for the phase level attack. The best transfer rates were achieved on a PC, followed by a server (which had lower bit rates and more errors), and IoT devices (bit rates of up to 20 bits/sec and error rates of up to 18%).
While these can be significant transfer rates for exfiltrating small pieces of information such as passwords – obtaining one character from a string requires 8 bits to be transferred – reliable exfiltration requires more than just sending the raw data. Researchers created 44-bit data frames that, in addition to the actual data being exfiltrated, include a preamble that signals the start of the transmission and 8 bits of CRC code at the end of the frame for error detection.
As for countermeasures, researchers say PowerHammer attacks can be prevented by monitoring power lines for the presence of covert communication channels, by using power line filters to limit the leakage of conduction and radiation noise, and by installing software-level jammers that execute random workloads on the system in order to cause interference in the data transmission process.
25 Million U.S. Individuals Impacted by 2016 Uber Hack
14.4.2018 securityweek Incindent
The 2016 data breach that Uber made public in November 2017 impacted over 25 million riders and drivers in the United States, the Federal Trade Commission (FTC) reveals.
The hack, which the ride-sharing company kept silent about for a year, impacted more than 57 million users globally. Hackers managed to access data stored on an Amazon Web Services (AWS) account and steal names, email addresses and mobile phone numbers of customers around the world.
In February this year, Uber chief information security officer said that two individuals living in Canada and Florida were responsible for the massive data breach.
In an attempt to cover up the hack, Uber paid the attackers $100,000 through its third-party “bug bounty” program, which was designed to reward those who responsibly disclose vulnerabilities, rather than those who maliciously exploit them.
The company came under scrutiny after the hack was made public in November 2017, and even became the target of a US criminal investigation. The data breach was revealed only three months after Uber agreed to implement new data protection measures in a settlement with the FTC over a 2014 incident.
Now, the Commission says the ride-sharing company has agreed to expand the proposed settlement and that it will be subject to additional requirements. Under the new settlement, Uber could be subject to civil penalties if it doesn’t notify the FTC of future breaches in due time.
In a revised complaint (PDF) issued this week, the FTC claims hackers used an access key an Uber engineer had posted on a code-sharing website to access consumer data on a third-party cloud provider’s servers in November 2016.
The complaint alleges that attackers downloaded unencrypted files that provided them with access to over 25 million names and email addresses, 22 million names and mobile phone numbers, and 600,000 names and driver’s license numbers of U.S. individuals.
The revised order (PDF) not only compels Uber to disclose certain future incidents involving consumer data, but also requires the company to submit to the Commission “all the reports from the required third-party audits of Uber’s privacy program rather than only the initial such report.”
Uber is also required to retain records related to bug bounty reports on security bugs that could result in unauthorized access to consumer data.
“After misleading consumers about its privacy and security practices, Uber compounded its misconduct by failing to inform the Commission that it suffered another data breach in 2016 while the Commission was investigating the company’s strikingly similar 2014 breach,” Acting FTC Chairman Maureen K. Ohlhausen said.
“The strengthened provisions of the expanded settlement are designed to ensure that Uber does not engage in similar misconduct in the future,” Ohlhausen continued.
Britain Says Russia Spied on Skripals Before Poisoning
14.4.2018 securityweek BigBrothers
Russia was spying on former double agent Sergei Skripal and his daughter Yulia for at least five years before they were poisoned with a nerve agent, Britain's National Security Adviser Mark Sedwill said in a letter to NATO released on Friday.
Sedwill also said that Russia has tested means of delivering chemical agents "including by application to door handles", pointing out that the highest concentration of the chemical found after the attack was on Skripal's front door handle.
"We have information indicating Russian intelligence service interest in the Skripals, dating back at least as far as 2013, when email accounts belonging to Yulia Skripal were targeted by GRU cyber specialists," Sedwill wrote in the letter, referring to Russia's foreign military intelligence agency.
The Skripals were found slumped on a bench in the English city of Salisbury on March 4. Britain has blamed Russia for the attempted murder -- a charge that Moscow has strongly denied.
After testing samples from Salisbury, the Organisation for the Prohibition of Chemical Weapons (OPCW) on Thursday confirmed Britain's findings about the nerve agent used in the attack.
Skripal had moved to Britain in 2010 as part of a spy exchange after being imprisoned in Russia for selling secrets to British intelligence while he was working for the GRU.
His daughter, who lives in Moscow, was visiting him when the two were poisoned in an attack that has triggered an international diplomatic crisis between Russia and the West.
Sedwill's letter to NATO Secretary General Jens Stoltenberg alleged that Russia had "the technical means, operational experience and motive for the attack on the Skripals and that it is highly likely that the Russian state was responsible".
But Russia's embassy to London on Friday accused the British government of failing to produce evidence to support its claims.
Ambassador Alexander Yakovenko said the embassy would be publishing its own 33-page report about the incident.
Yakovenko also questioned the authenticity of a statement in which Yulia Skripal, who was discharged from hospital earlier this week, turned down Russian consular assistance.
"We are not allowed to see our citizens, talk to doctors, have no idea about the treatment the Russian nationals receive."
"We cannot be sure that Yulia's refusal to see us is genuine. We have every reason to see such actions as the abduction of two Russian nationals," Yakovenko said.
Covert chemical weapons programme
Sedwill said "credible open-source reporting and intelligence" showed that in the 1980s the Soviet Union developed a family of nerve agents known as Novichoks at a base in Shikhany near Volgograd.
"The codeword for the offensive chemical weapons programme (of which Novichoks were one part) was FOLIANT," he said.
"It is highly likely that Novichoks were developed to prevent detection by the West and to circumvent international chemical weapons controls," he said.
By 1993, when Russia signed the Chemical Weapons Convention, Sedwill said it was "likely" that some Novichoks had passed testing to allow their use by the Russian military.
He said Russia developed some Novichoks even after ratifying the convention.
In the 2000s, Sedwill said Russia had trained military personnel in using these weapons, including on door handles, and Russia "has a proven record of conducting state-sponsored assassination".
"Within the last decade, Russia has produced and stockpiled small quantities of Novichoks under the same programme," he said.
Russia has denied having any chemical weapons.
Hackers Start Exploiting Drupalgeddon2 Vulnerability
14.4.2018 securityweek Vulnerebility
Attempts to exploit a recently patched vulnerability in the Drupal content management system (CMS) were spotted by researchers shortly after someone published a proof-of-concept (PoC) exploit.
In late March, Drupal developers rolled out an update to address CVE-2018-7600, a highly critical remote code execution flaw that can be exploited to take full control of a site. The security hole affects Drupal 6, 7 and 8, and patches have been released for each of the impacted versions – Drupal 6 is no longer supported since February 2016, but a patch has still been created.
Drupalgeddon2
Experts warned at the time that exploitation of the vulnerability, dubbed Drupalgeddon2, was imminent. However, it took roughly two weeks for a proof-of-concept (PoC) exploit to become publicly available.
Researchers at Check Point and Drupal experts at Dofinity worked together to uncover the vulnerability and on Thursday they published a detailed technical analysis.
“In brief, Drupal had insufficient input sanitation on Form API (FAPI) AJAX requests,” they explained in a post on the Check Point blog. “As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication. By exploiting this vulnerability an attacker would have been able to carry out a full site takeover of any Drupal customer.”
Shortly after Check Point and Dofinity published their analysis, Vitalii Rudnykh published a PoC on GitHub for “educational or information purposes,” which others confirmed to be functional. Once the PoC was made public, Sucuri and the SANS Internet Storm Center started seeing attempts to exploit Drupalgeddon2.
At the time of writing, there are no reports of websites being hacked via CVE-2018-7600. Attackers are apparently scanning the web in search for vulnerable servers. The payloads spotted by SANS researchers use simple commands such as echo, phpinfo, whoami and touch.
Web security services, including Cloudflare's Web Application Firewall (WAF), should be able to block attacks exploiting the vulnerability.
“The exploit attempts are currently arriving at a pretty brisk pace,” said ISC handler Kevin Liston. Sucuri founder and CTO Daniel Cid also warned that the number of exploit attempts is expected to grow.
The original Drupalgeddon vulnerability, disclosed in October 2014, was first exploited just 7 hours after a patch was released and it was leveraged by cybercriminals for at least another two years.
'Spectrum' Service Extends Cloudflare Protection Beyond Web Servers
14.4.2018 securityweek Vulnerebility
Cloudflare on Thursday announced the availability of a new service that extends the company’s protection capabilities to gaming, remote access, email, IoT and other types of systems.
The new product, named Spectrum, allows enterprises to leverage Cloudflare not only to protect their websites, but also any other system that is exposed to the Internet through an open TCP port, including SSH, SFTP, SMTP and custom protocols.
Spectrum includes protection against distributed denial-of-service (DDoS) attacks, which will likely attract the interest of gaming companies. Hypixel, which runs the largest Minecraft server and one of the first victims of the massive Mirai botnet attacks, has already started using Spectrum.Cloudflare launches Spectrum
Banking services provider Montecito Bank & Trust has also started using Spectrum to protect its email and SSH servers.
The new service also integrates with Cloudflare’s IP Firewall, allowing users to choose which connections can pass through to their servers and which should be blocked.

Spectrum also allows organizations to terminate TLS at the edge of the Cloudflare infrastructure, which can speed up performance.
“We think the most interesting outcome is that just by adding support for TLS in the client, Cloudflare can now add encryption to legacy protocols and services that don’t traditionally support encrypted transit,” explained Cloudflare’s Dani Grant.
Spectrum is currently only available to enterprises due to the fact that TCP relies on each service having its own IP address for identification purposes. IPv4 addresses are hard to come by and expensive, but the company says it’s actively thinking about how it can offer Spectrum to everyone, including by offering only IPv6 addresses to non-enterprise customers, or asking users to pay for IPv4 addresses.
The company has released a video showing how easy it is to add TCP applications to Spectrum in the Cloudflare dashboard, and a blog post explaining exactly how Spectrum works and the challenges of implementing such a service.
Cloudflare also announced this year the launch of a remote access service designed to replace corporate VPNs, and a free DNS service.
Illumio, Qualys Partner on Vulnerability-based Micro-Segmentation
14.4.2018 securityweek Vulnerebility
Vulnerability management has two major components: discovering vulnerabilities, and mitigating those vulnerabilities. The first component is pointless without the second component. So, for example, Equifax, WannaCry, NotPetya, and many other breaches -- if not most breaches -- are down to a failure to patch, which is really a failure in vulnerability management.
In these examples the vulnerabilities were known, but not mitigated. Patches were available, but not implemented. It's a hugely complicated problem, because although there are vulnerability management platforms, immediate patching is not always possible (for fear of breaking essential applications); and the ramifications of not patching are not easily understood.
"Everyone does vulnerability management," says Illumio's VP of product management, Matthew Glenn. "It's like motherhood and apple pie -- it's just something you have to do." So, companies have a vulnerability team that scans for and locates vulnerabilities, and then that team tries to persuade the app team to patch the vulnerable application.
"This creates a really interesting tension," he continued, "because app teams really just want to make sure that their apps are running without interruption, while patching can create an unknown outcome. It takes time to get a patch installed. So, if they can't install a patch, they look for some form of compensating control."
Micro-segmentation firm Illumio is now seeking to provide that compensating control to this problem via a relationship with the Qualys vulnerability platform. Illumio already has a dependency mapping capability, called Illumination, as part of its Adaptive Security Platform. This shows dependencies and connections between different applications, even when spread across multiple data centers or in the cloud. It highlights whether connections are within policy, allowing companies to micro-segment the infrastructure to increase security.
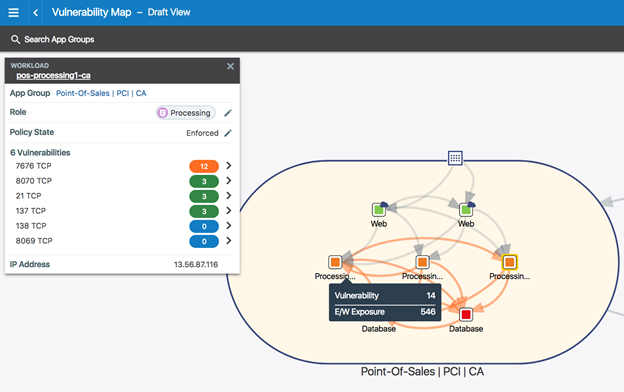
"What we've now added," explains Glenn, "is the ability to import vulnerability scans from Qualys. This creates a new capability we call vulnerability maps." The vulnerability map is color-coded from the Qualys data and overlaid on the app dependency map: green is low and informational; orange is medium risk; and red is critical.
But this doesn't just show the location of the vulnerabilities -- added to the app dependency map it shows the potential ramifications of that vulnerability across the network through open ports and connecting and communicating links, and with the internet. These are the paths that an intruder, having exploited a vulnerability, would seek out for lateral movement through the network.
"What we do," said Glenn, "is combine the Qualys vulnerability data with our application dependency map to let organizations do something they've never been able to do before -- which is just literally see the data paths within and between data centers in the way a bad actor does, and show the exposure of the vulnerabilities on the hosts. We think this is a transformational moment because traditionally the vulnerability management team and the application team are two different groups. This new approach allows them to collaborate together to do something they haven't been able to do before: to see how exposed those vulnerabilities actually are."
Patching individual vulnerabilities may not be immediately possible -- but micro-segmenting the network to isolate the vulnerability as far as possible, is possible. Operators can locate the vulnerability, can see the level of criticality, can see and measure paths open to an attacker (something Illumio calls the 'East-West' exposure score), and can automatically impose mitigating micro-segmentation controls that limit exposure without breaking any apps.
“Digital transformation leads to an explosion of connected environments where perimeter protection is no longer enough. The focus now needs to shift from securing network perimeters to safeguarding data spread across applications, systems, devices, and the cloud,” says Philippe Courtot, CEO and Chairman of Qualys. “The new Illumio integration with Qualys helps enterprises get visibility across hybrid environments and implement appropriate controls to protect assets from cyber threats, whether on premises or in the cloud.”
If a company has a high value application with a vulnerability that cannot be patched, but the vulnerability management team knows there is a 0-day exploit in the wild (all information courtesy of Qualys), the question becomes, what can be done? "You can use micro-segmentation," suggests Glenn, "as a way of creating compensating controls to reduce the exposure of the vulnerability. Arbitrarily blocking vulnerabilities is the pathway to breaking applications. So, we've created a very nuanced approach, where we look at the connectivity paths that allow us to reduce the exposure without breaking the applications.
"We use the connectivity paths to fine-tune a micro-segmentation policy. It can automatically block or constrain applications. Blocking only ever happens automatically if the ven [Illumio's virtual enforcement nodes, installed on each host] has never seen traffic on the pathway -- perhaps a developer left a port open months ago. Constraining, however, can use micro-segmentation to reduce the effect of a vulnerability without breaking the application. The visible map allows the operator to see the effect of any new policy rules that, once written, will be pushed out to effect the micro-segmentation."
“Vulnerability management is an invaluable tool in every security team’s arsenal. With our Qualys Cloud Platform integration, organizations can see a map of how active, exposed vulnerabilities can potentially be exploited by a bad actor,” adds Andrew Rubin, CEO and co-founder of Illumio. “By adding vulnerability maps to our Adaptive Security Platform, security teams can see potential attack paths in real time and immediately implement micro-segmentation to prevent the spread of breaches.”
Sunnyvale, Ca-based Illumio raised $100 million Series C financing in April 2015, followed by a further $125 million Series D funding in June 2017.
Researchers Sinkhole Deep-Rooted "EITest" Infection Chain
14.4.2018 securityweek Virus
Proofpoint on Thursday said that it has managed to sinkhole what could be the oldest “infection chain” out there, which redirected users to exploit kits (EKs), social engineering schemes, and other malicious or fraudulent operations.
Dubbed EITest and supposedly active since 2011, the infection chain has been associated with the distribution of ransomware, information stealers, and other malware. Performing around two million potential malicious redirects a day, the chain has been rendered ineffective after Proofpoint sinkholed it in collaboration with brillantit.com and abuse.ch.
In 2011, the infection chain was redirecting to a private EK known as Glazunov, but switched to Angler in July 2014, after being silent for about half a year. The actor behind EITest started rework on infrastructure around November 2013, the creation dates of command and control (C&C) domains reveal.
When the chain reappeared in July 2014, it was spreading multiple payloads, which suggested that it was either selling loads or traffic. The researchers confirmed the actor was selling traffic, “in blocks of 50-70,000 visitors for US$20 per thousand, generating between $1,000 and $1,400 per block of traffic.”
EITest began using social engineering schemes in January 2017, which over the past several months was primarily concentrated around social engineering and tech support scams leading to ransomware.
Last year, EITest was involved in a malicious campaign targeting Chrome users with fake font update notifications but serving malware instead. Also last year, the infection chain was observed redirecting to the RIG-V EK.
The security researchers managed to fully sinkhole the EITest operation on March 15, 2018.
“The C&C domains were generated from the resolution of a key domain ‘stat-dns[.]com’. Once seized, we pointed that domain to a new IP address to generate four new EITest C&C domains. These, in turn, were pointed to an abuse.ch sinkhole,” Proofpoint security researcher Kafeine explains.
By generating the new domains, the security researchers replaced the malicious server with a sinkhole, which allowed them to receive the traffic from the backdoors on the compromised websites. Thus, they could prevent the resulting malicious traffic and injects from reaching users, but the cleanup efforts are ongoing.
From March 15 to April 4, 2018, the sinkhole received nearly 44 million requests from roughly 52,000 servers, which revealed compromised domains and the IP addresses and user agents of the users who browsed to the compromised servers. The complete list of compromised websites was shared with national CERTs.
Most of the compromised websites were using the WordPress content management system, Kafeine reveals. The United States emerged as the top country accessing EITest-compromised websites, followed by Ukraine, Canada, France, and Ireland.
“EITest is one of the oldest and largest infection chains, which, early in its operation, primarily distributed malware via a private exploit kit. In more recent years, the operators of EITest became prolific sellers of traffic to EK operators and social engineering schemes through their large network of compromised web servers,” Kafeine notes.
Following the sinkhole operation, the EITest C&C proxies were shut down, and the actor behind the infection chain apparently went silent. The researchers did observe some encoded calls to the sinkhole that were associated with takeover attempts, but it’s unclear whether they were initiated by the operator or other researchers or threat actors.
When the Russian Malware coder Gatsoev is praised by the Russian head of Information Department of the Ministry of Education and Science of North Ossetia
14.4.2018 securityaffairs BigBrothers
When the Russian young Malware coder is praised by the Russian head of Information Department of the Ministry of Education and Science of North Ossetia. Under the spotlight: the story of Atsamaz Gatsoev (aka “1ms0rry”) who has set up his illegal business.
A new write-up made by a security researcher known as Benkow (@Benkow_) has been published, as ever on Sunday, and to be more precise on Sunday 8 April.
It’s about the story of a malware coder from Russia who is developing and selling two kinds of malware (a password stealer and a miner) with a lot of features and a variegated commercial offer: this malware actor is targeting also Russian people with his malware but Mr. Freud would absolve him (form the psychological point of view) analysing his nickname. The nickname, in fact, is “Im Sorry” (1ms0rry) which maybe talks about his interior drama: nevertheless, looking at what he does in his life the drama and the sorrow are for the thousands of victims he makes cry with his work.
The incredible side of this story is that the man has declared to not be worried to be recognized with his real name after Benkow crew has unmasked the real identity of this young criminal with a great page of investigative journalism.
But let’s go with order.
First of all we have to say that this time the post is written in cooperation with some Benkow’s (and this post author Odisseus) friends and the list of them is reported below in the same order can be found on the Benkow_ post: they are “.sS.!, coldshell, fumik0_, siri_urz, VxVault, Cybercrime-Tracker, MalwareMustDie, .sS.! (again)”.
Yes, at the beginning of the post there is this image showing there are no doubts that #MalwareMustDie team has also given a contribution in this post: interviewed by the author of this post, Odisseus, mr. @unixfreaxjp said that, of course, we have to expect more to come about malware and reversing from the #MMD team in the future.
Going back to the post published by Benkow, we have a very interesting work about the malware analysis referring the features spotted in the wild of a password Stealer malware made by “1ms0rry”: everything starts from a post published on a Russian hacker forum at the URL of the ifud.ws site the 7th of September 2017. There, a Russian hacker called “1ms0rry” – on Twitter (@ims0rry_off) – has published a post about a “Stealer N0F1L3 + admin panel ims0rry” with many different features. But let’s give a look at the malware capabilities.
First Malware: Starter Stealer N0F1L3 v1
Giving a closer look to his advertising page on the hack forum page as is possible to read in English – translated by Russian thanks to Google – the following detailed features of the malware are offered: the “Starter Stealer” is written in C# and is able to steal passwords from 7 internet browsers: the price is 20$ for the build version and 600$ for the source code.
But this is not all, the malware is able to do more:
Steal passwords and cookies from Chrome, Opera, Kometa, Orbitum, Comodo, Amigo, Torch and Yandex
Attack Crypto-Currencies wallets (btc, electrum, ltc, eth, bcn, DSH, XMR, ZEC)
Steal Filezilla Passwords
Get every file on the desktop with the extensions .txt .doc .docx .log
The password stealer malware has also the following features:
It is declared as FUD (maximum error from 0 to 5)
works without admin rights
build weight is 2 mb
supports all add-ons
The Benkow post reports that what is interesting how 1ms0rry stealer is able to attack also Russian browsers like Yandex.
As is possible to see in the C&C logs provided by the Benkow post, many IP addresses are related to the Russian Federation:
Regarding the C&C panels, they have some the vulnerabilities: it can be easy to change the password, Benkow reports how to, providing even detailed list of IOCs and Yara for the malware admin panel.
First Malware, the Advanced version N0F1L3 v2
The malware offer list includes an advanced version of the password stealer which is named N0F1L3 v2 and is injected by this malware called “Paradox Crypter” almost recognized by most of Antivirus and having a good detection ratio on Virustotal (46/67)
The advanced version is written in C – C++ and now is able to steal password also from Firefox.
Second Malware 1ms0rry Miner
The second malware is a made by a loader and a miner: the LoaderBot is developed in .NET and as Benkow says it reuses a lot of code by N0F1L3.
The LoaderBot it is a process that kills itself in the Task Manager then is not visible and install itself in the following PATH: C:\users\%userprofile%\AppData\Roaming\Windows\
The persistence of the LoaderBot is achieved by installing the adding an item in the Windows Registry hive called at the startup: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
As shown by Benkow the available feature are Update, Download and Execute, and the connection to the C&C is achieved using a Mozilla User-Agent defined like as “Mozilla/5.0 (Windows NT 10.0; WOW64; rv:53.0) Gecko/20100101 Firefox/53.0”
This means that first the infection is carried on by the Loader then the attacker installs the Miner.
The Miner is developed in C++, is able to hide itself, to detect a Wallet address in the clipboard and replace it: it runs RunPe using a known process hollowing procedure and the following System API CreateProcessA(Suspended)/SetThreadContext/WriteProcessMemoryResumeThread/ and the code is a copy paste from GitHub
For the details of C&C, vulnerabilities and attack vector they are widely provided in the Benkow research.
What is interesting now is how has been correlated with the “1ms0rry” nickname with a very promising Russian student named Ацамаз Гацоев or Atsamaz Gatsoev.
The core of the story: 1ms0rry identity has been unmasked
First of all the Russian guy has a Twitter account that is “Im Sorry” with the following URL: https://twitter.com/ims0rry_off. The account is still working at the moment, and the malware actor is answering till 17 hours ago at the moment we are writing.
“Im Sorry” answered to the tweet where Benkow launched his post about him telling to be happy to have people talking about his work, because he doesn’t hide his identity, on the contrary, he is happy that his crimes are associated to him.
That probably explains why as a malware actor he didn’t try to hide himself arriving to answer to another security researcher who was highlighting the IP address of one of his C&C panel:
At the beginning point, looking for “Im Sorry” have been found some accounts on different platforms: he has an account on Telegram, on GitHub and different mail addresses like:
gornostay322@mail.ru
lordatsa@mail.ru
your_email@whatever.com
with the following nicknames:
Gatsoev
hype
ims0rry
s0rry
Your Name
Then looking for lordatsa@mail.ru Benkow has found a mail.ru account at the following URL https://my.mail.ru/mail/lordatsa/photo that give us a first name and a second name: Аца Гацоев (Atsa Gatsoev) enabling to find something more, for instance the information contained in this Weblancer profile: https://www.weblancer.net/users/hypega/
Many interesting things are here, says Benkow:
the name Ацамаз Гацоев (Atsamaz Gatsoev) is the same as the mail.ru account,
The username used is hypega. hype was used to commit on github, hypega for “hypeGatsoev”
The personal website in the profile’s information is http://lordatsa.wix.com/gatsoevsummary and “lordatsa” is used as username for mail.ru http://lordatsa.wix.com/gatsoevsummary is also interesting to get other two profiles on VK and Google Plus.
From Google Plus the step to achieve the YouTube profile is easy: a good surprise is that in one of his videos Benkow and his crew found a special evidence related to a path raised during the password straealer reversing: a directory named [NEW] builder on the desktop of the user “gorno” is exactly what is raised in the pdb analysis of the LoaderBot: c:\Users\gorno\Desktop\[NEW] builder\Bot\Miner\obj\Release\LoaderBot.pdb
Then the user is “gorno” as is possible to see in the video at second 6 that there is Thermida and a local path, again “gorno” C:\Users\gorno\Desktop\winhost.exe
And again in another video it is possible to see “the viruscheckmate user” that is again “hypega”.
The name “hypega” give the opportunity to retrieve another 2 very interesting links:
a Portfolio website: at wix.com/e-consultant
a A GitHub account: com/Gatsoev/Nerve_MobileApp
This last one gives us the final proof that “1ms0rry” is Atsamaz Gatsoev.
How a criminal is working for the office of Russian “Information technologies and communications” of North Ossetia
What is probably confusing, looking at his photographs, is that he has the “face” of the good boy: and this is confirmed from a very recent and amazing post by Alan Salbiev in the 2013 known as “head of the Information Department of the Ministry of Education and Science of North Ossetia” and from 2017 is at “Management of North Ossetia-Alania in information technologies and communications Local business Vladikavkaz, Russia”
The 20th of March he writes the following Facebook post talking about “1ms0rry” as one who has done a great job in his office and more over he says that on “February 25, 2018 at competitions on sports hacking at the University ITMO our hero confidently walked rivals from Komsomolsk-on-Amur, Khanty-Mansiysk, Penza, Pyatigorsk, etc. As a result, a schoolboy from Vladikavkaz entered the top 15 in St. Petersburg.
At Atsamaz there is a dream – to enter the University of ITMO. Our Office will provide every possible assistance to a talented guy”.
Here the post:
We don’t know how much Mr. Alan Salbiev knows about his “dream” if he knows if he is a criminal or if he thinks that as a CTF hacker he has to get his Gym to become a perfect champion in Russia hacking and illegally stealing password or cryptocurrency to people in Russian and around the world.
For sure Europol or FBI now are hoping he is going to participate soon in competitions on sports hacking or some CTF competitions in Europe or USA.
Experts uncovered a proxy botnet composed of over 65,000 routers exposed via UPnP protocol
14.4.2018 securityaffairs BotNet
Security researchers at Akamai have discovered a proxy botnet composed of more than 65,000 routers exposed to the Internet via the Universal Plug and Play (UPnP) protocol.
Crooks have compromised the devices of this multi-purpose proxy botnet to conduct a wide range of malicious activities, including spamming and phishing, click fraud, account takeover and credit card fraud, distributed denial of service (DDoS) attacks, malware distribution, and also bypassing censorship,
While the researchers were investigating attacks against its customers they discovered that vulnerable devices have NAT injections that allow attackers to abuse them.
“While researching UPnP-enabled devices detected as participants in attacks against Akamai customers, we discovered that some devices appeared to be more susceptible to this vulnerability than others, and contained malicious NAT injections.” reads the analysis published by Akamai. “These injections were present on a handful of the devices found in the wild, and appeared to be part of an organized and widespread abuse campaign”

Akamai discovered over 4.8 million devices that were found to be vulnerable to simple UDP SSDP inquiries. Of these, roughly 765,000 (16% of total) were confirmed to also
expose their vulnerable TCP implementations while over 65,000 (1.3% of total) were discovered to have NAT injections.
“These injections appeared to point to multiple services and servers around the Internet. A majority of the injections appear to target TCP ports 53 (15.9M for DNS), 80 (9.5M for HTTP), and 443 (155K for HTTPS).” continues the analysis. “A wide range of devices are affected, most of them being consumer-grade networking hardware. “73 brands/manufacturers and close to 400 models [were affected].”
The UPnP communication protocol is widely adopted even if it is known to be vulnerable. In early 2013, researchers at Rapid7 published an interesting whitepaper entitled “Security Flaws in Universal Plug and Play” that evaluated the global exposure of UPnP-enabled network devices.
The report highlighted that over 23 million IPs related to Portable UPnP SDK were vulnerable to remote code execution just through a single UDP packet, over 6,900 product versions from over 1,500 vendors were vulnerable through UPnP due to the exposure of UPnP SOAP service to the internet.
Abusing the protocol attackers can control the traffic in and out the networks, UPnP allows the automated negotiation and configuration of port opening/forwarding within a NATed networking environment.
The malicious botnet uncovered by Akamai is composed of vulnerable devices including malicious NAT injections, it turns routers into proxies, for this reason, the experts called the injected devices UPnProxy.
“The injected NAT entries were designed to be working in sets across various devices. Thus, across the 65,000 infected devices, 17,599 unique endpoint IP addresses were discovered.” continues the report. “The most-identified IP was injected over 18.8 million times across 23,286 devices, while the second-most-injected IP appeared over 11 million times across 59,943 devices.”
According to Akamai, part of this proxy botnet was already discovered by researchers at Symantec while investigating into the “Inception Framework” used by an APT group, in that circumstance Symantec research confirmed that the UPnProxy instances were used obfuscate the operators’ true locations.
The APT associated with Inception Framework is still active and continuously evolved its arsenal and TTPs.
In order to check if your router has been compromised for UPnProxying is to scan the endpoint and audit your NAT table entries.
Many frameworks and libraries available online could be used for this purpose.
U.K. Launched Major Cyberattack on Islamic State: Spy Chief
13.4.2018 securityweek BigBrothers
The head of Britain’s Government Communications Headquarters (GCHQ) revealed this week that the U.K. has launched a major cyberattack on the Islamic State (IS) group, significantly disrupting its operations.
The attack was launched by the GCHQ in collaboration with the U.K. Ministry of Defence. The operation was the “first time the UK has systematically and persistently degraded an adversary’s online efforts as part of a wider military campaign,” GCHQ director Jeremy Fleming told an audience at the Cyber UK conference in Manchester.
“These operations have made a significant contribution to coalition efforts to suppress Daesh propaganda, hindered their ability to coordinate attacks, and protected coalition forces on the battlefield,” the spy chief said.
According to Fleming, these operations have been aimed at disrupting services or a specific online activity, deter an individual or group, or destroy equipment and networks used by the Islamic State, which is also known as ISIL, ISIS and Daesh.
“In 2017 there were times when Daesh found it almost impossible to spread their hate online, to use their normal channels to spread their rhetoric, or trust their publications. Of course, the job is never done – they will continue to evade and reinvent. But this campaign shows how targeted and effective offensive cyber can be,” Fleming said.
Ilia Kolochenko, CEO of web security firm High-Tech Bridge, says such attacks are not surprising.
“In the near future, we will see more offensive cyber operations backed by nations under attack. Unfortunately, cybercriminals, drug dealers and terrorists enjoy almost absolute impunity in the digital world, causing more damage there than on the streets, and it’s good to see the UK take a stand,” Kolochenko told SecurityWeek. “The efforts to suppress propaganda and hinder coordinated attacks will ultimately protect UK citizens.”
“From a legal point of view, it may be a tricky question, however,” Kolochenko added, “as some of their targets may be European or American citizens, raising complicated issues of the international law.”
The US military's secretive Cyber Command (CYBERCOM) and Europol have also been conducting operations aimed at the Islamic State’s online activities.
Pro-IS groups have continued launching hacker attacks and spreading propaganda, with some experts believing the terrorist organization has taken refuge in its “virtual caliphate.” However, even online, where its capabilities have for years already been described as relatively weak and poorly organized, IS has been in decline.
Uber agrees to new FTC settlement over 2016 data breach
13.4.2018 securityaffairs Incindent
Uber agrees to a new settlement with the Federal Trade Commission over the massive 2016 data breach, the authorities could assign civil penalties against the company if it will fail to share incident data with FTC.
Uber agrees to a new settlement with the Federal Trade Commission over the massive 2016 data breach.
“Uber Technologies, Inc. has agreed to expand the proposed settlement it reached with the Federal Trade Commission last year over charges that the ride-sharing company deceived consumers about its privacy and data security practices.” states the FTC.
“Due to Uber’s misconduct related to the 2016 breach, Uber will be subject to additional requirements. Among other things, the revised settlement could subject Uber to civil penalties if it fails to notify the FTC of certain future incidents involving unauthorized access of consumer information.”
In November 2017, the Uber CEO Dara Khosrowshahi announced that hackers broke into the company database and accessed the personal data of 57 million of its users, the disconcerting revelation was that the company covered up the hack for more than a year.
The attackers accessed also the names and driver’s license numbers of roughly 600,000 of its drivers in the United States.
The hack happened in 2016, it was easy for hackers that according to a report published by Bloomberg, obtained credentials from a private GitHub site used by the company development team. The hackers tried to blackmail Uber and demanded $100,000 from the company in exchange for avoiding publish the stolen data.
Rather than to notify the data breach to customers and law enforcement as is required by California’s data security breach notification law, the chief of information security Joe Sullivan ordered to pay the ransom and to cover the story destroying any evidence. The payout was disguised as a bug bounty prize complete with non-disclosure agreements signed

In 2017 the FTC charged the company for deceiving customers with its privacy and data security practices.
The first settlement dated back August 2017, according to the FTC, the company failed to apply security measures to protect customers and drivers data, later while investigating the settlement, the Commission discovered that the company did not disclose the 2016 data breach before 2017.
According to the new settlement with the Federal Trade Commission, Uber is obliged to disclose any future breach affecting consumer data and share reports from required third-party audits of its privacy program.
The company must maintain records related to bug bounty activities, the authorities could assign civil penalties against the company in case it will fail to implement the above actions.
“After misleading consumers about its privacy and security practices, Uber compounded its misconduct by failing to inform the Commission that it suffered another data breach in 2016 while the Commission was investigating the company’s strikingly similar 2014 breach,” said Acting FTC Chairman Maureen K. Ohlhausen. “The strengthened provisions of the expanded settlement are designed to ensure that Uber does not engage in similar misconduct in the future.”
$3.3 Million stolen from main Coinsecure Bitcoin wallet
13.4.2018 securityaffairs Cryptocurrency
Cryptocurrency exchange Coinsecure, India’s second exchange, announced that it has suffered a severe issue, 438 bitcoin, $3,3 million worth of bitcoin
Cryptocurrency exchange Coinsecure, India’s second exchange, announced that it has suffered a severe issue, 438 bitcoin, $3,3 million worth of bitcoin, have been transferred from the main wallet to an account that is not under their control.
CEO Mohit Kalra said that only he the Chief Strategist officer (CSO) Dr. Amitabh Saxena had private keys to the exchange’s main wallet.
“The current issue points towards losses caused during an exercise to extract BTG to distribute to our customers. Our Chief Strategist officer (CSO) Dr. Amitabh Saxena was extracting BTG and he claims that the funds have been lost in the process during the extraction of the private keys.” reads the statement published by Coinsecure.
According to the CEO of Coinsecure, the CSO is responsible for the transfer, the company posted two imaged on the websites containing company statement signed by the Coinsecure team and a scanned copy of a police complaint filed by Coinsecure CEO Mohit Kalra.


The Coinsecure CEO excluded the transfer was the result of a hack and accused the CSO, but Dr. Saxena denied any involvement in the case and informed Coinsecure that the funds “were stolen from company’s Bitcoin wallet due to some attack.”.
“Our system itself has never been compromised or hacked, and the current issue points towards losses caused during an exercise to extract BTG [Bitcoin Gold] to distribute to our customers, ” the Coinsecure team wrote in its statement
“Our CSO, Dr. Amitabh Saxena, was extracting BTG and he claims that funds have been lost in the process during the extraction of the private keys,” Coinsecure added.
“[he] making a false story to divert [his] attention and might have a role to play in this entire incident.”
The CEO is asking local police to seize the Saxena’s passport because he fears that the employee “might fly out of the country soon.”
Multi-Purpose Proxy Botnet Ensnares 65,000 Routers
13.4.2018 securityweek BotNet
More than 65,000 routers exposed to the Internet via the Universal Plug and Play (UPnP) protocol are being abused by cybercriminals as part of a large, multi-purpose proxy botnet, Akamai has discovered.
The vulnerable devices were found to have NAT injections that allow malicious actors to abuse them for various purposes, such as bypassing censorship, spamming and phishing, click fraud, account takeover and credit card fraud, distributed denial of service (DDoS) attacks, malware distribution, and more.
The 65,000 injected devices, Akamai reveals, are part of a larger set of over 4.8 million devices that were found to be vulnerable to simple UDP SSDP (the UDP portion of UPnP) inquiries. Around 765,000 of the devices were also found to expose their vulnerable TCP implementations, the security firm says.
Most of the impacted devices are consumer-grade networking hardware coming from 73 brands / manufacturers. Nearly 400 models were found vulnerable, but other manufacturers and devices are also believed to be affected by these vulnerable UPnP implementations, Akamai reveals in a report (PDF).
Designed to allow better communication between devices on a LAN, the UPnP protocol is widely used, but is also long-known to be vulnerable. In fact, flawed implementations have been exposed for over a decade, with a 2013 report revealing tens of millions of vulnerable devices on the Internet.
The protocol allows for automated negotiation and configuration of port opening/forwarding within a NATed networking environment, meaning that devices on the network can open ports to expedite routing of traffic in and out of the network. Some of the exposed services, however, are privileged and meant to only be used by trusted devices on a LAN.
Some of the vulnerable devices include malicious NAT injections that appear to be part of an organized and widespread abuse campaign. The purpose of these injections is to turn routers into proxies, which led researchers to call injected devices UPnProxy.
The injected NAT entries were designed to be working in sets across various devices. Thus, across the 65,000 infected devices, 17,599 unique endpoint IP addresses were discovered. The most-identified IP was injected over 18.8 million times across 23,286 devices, while the second-most-injected IP appeared over 11 million times across 59,943 devices.
The injections were designed to point to multiple services and servers around the Internet and most of them targeted TCP ports 53 (15.9M for DNS), 80 (9.5M for HTTP), and 443 (155K for HTTPS).
The multi-purpose proxy botnet, Akamai says, appears related to the Inception Framework threat actor that was first exposed in 2014. The group was previously observed targeting Energy and Defense sectors, along with organizations in the Consultancy/Security, Aerospace, Research, and Media sectors, in addition to embassies.
In a report earlier this year, Symantec revealed that the actor has continued to operate over the past years, despite an apparent silence. The group has changed its tools and techniques, uses modular malware in attacks, and has widened its use of cloud service providers for command and control purposes.
Symantec also said that the group was abusing Internet of Things devices to hide behind proxies, leveraging the UPnP protocol to hijack vulnerable routers.
Akamai used Symantec’s findings as a starting point for their research and discovered two clusters of highly chained proxies within the injected devices. One of them is more evenly distributed, supposedly using smaller nodes as final hop before exiting the chain to their final destinations. The other, however, routes to a much larger collection of outward medium and small nodes, making tracking more difficult.
“The UPnProxy vulnerability, like many of the problems we’ve seen recently, was caused by unauthenticated services being exposed to the public Internet in ways they were never meant to be. Attackers have taken several aspects of known issues with UPnP and combined them to create a powerful proxy network to hide their traffic. While this is neither a remote exploit that allows the attacker to take over a computer nor a new reflection vector for DDoS, it is still a significant concern because of how it allows the origin of traffic to be hidden,” Akamai notes.
OPAQ Networks Raises $22.5 Million in Series B Funding
13.4.2018 securityweek IT
Northern Virginia-based network security cloud company OPAQ Networks on Wednesday announced that it has secured $22.5 million in a Series B funding round, bringing the total raised by the firm to date to $43.5 million.
The funding round was led by venture capital firm Greenspring Associates, with participation from previous investors Columbia Capital and Harmony Partners. Hunter Somerville, partner at Greenspring Associates, will join OPAQ’s board of directors.OPAQ raises $22.5 million
The newly obtained funds will be used to accelerate growth and finance the company’s go-to-market initiatives for delivering its solutions to midsize enterprises.
“OPAQ Networks has redefined the security-as-a-service market. Its demonstrated progress to date and strategic acquisitions place the company in a position of real market leadership,” said Somerville. “OPAQ Networks joins an existing and prior portfolio of cyber security company investments like Proofpoint and Cloudflare. I look forward to working with the veteran security management team at OPAQ to continue to capitalize on this large and rapidly growing market opportunity.”
OPAQ’s cloud platform provides a fully encrypted private network backbone, along with continuous monitoring, firewall, compliance reporting, DDoS mitigation, microsegmentation, and automated security management capabilities. These capabilities, provided by third-parties and OPAQ’s own technology, are managed from a centralized dashboard.
Last year, OPAQ acquired Drawbridge Networks for $10 million and last month it bought business intelligence firm FourV Systems for an undisclosed sum.
LimeSurvey Flaws Expose Web Servers to Attacks
13.4.2018 securityweek Vulnerebility
A couple of vulnerabilities affecting the popular online survey tool LimeSurvey can be exploited by remote attackers to execute malicious code and take control of web servers with little or no user interaction, researchers warn.
LimeSurvey is a free and open source tool that allows users to create online surveys. The software is downloaded roughly 10,000 times every month and is used by individuals and organizations worldwide.
Researchers at RIPS Technologies discovered two potentially serious flaws in LimeSurvey version 2.72.3.
One of the security holes is a persistent cross-site scripting (XSS) issue that affects the “resume later” feature, which allows users to save partially completed surveys and reload them by providing an email address and password.
The email address field was not properly sanitized, allowing an attacker to inject malicious JavaScript code that would get executed when a user visited a specific web page – the attacker can lure a victim to this web page – or when an administrator viewed the partially saved data in the control panel.
The attacker can exploit the vulnerability to perform various actions on behalf of the authenticated user.
The second vulnerability is an arbitrary file write issue that allows an attacker to upload a malicious file by abusing LimeSurvey’s template editor. Exploiting this flaw requires authentication, but that can be achieved using the XSS bug.
According to RIPS researchers, the vulnerabilities can be chained into a single payload that gives the attacker control over the targeted web server.
“The vulnerability chaining [...] yields a single final exploit which would add malicious JavaScript code to the admin panel through the Continue Later functionality of a public survey,” explained RIPS researcher Robin Peraglie. “As soon as the JavaScript payload is executed in the administrator context it can exploit the arbitrary file write vulnerability to give the adversary persistent shell access to the operating system remotely to maximize impact.”
LimeSurvey developers patched the vulnerabilities in November 2017 with the release of version 2.72.4, just two days after the issues were reported. However, RIPS has advised users to update LimeSurvey to the latest release of version 3.
Mocana Launches Supply Chain Integrity Platform to Secure IoT, ICS Devices
13.4.2018 securityweek ICS
Mocana TrustCenter Manages Security Across IoT and ICS Device Lifecycles
Securing the supply chain, and securing industrial IoT devices and industrial control systems (ICS) are two of security's biggest challenges today -- but securing the supply chain of industrial IoT is particularly challenging.
Manufacturers are beginning to add security capabilities to the devices. Mocana's security software sits on around 100 million devices, and the company's customers include manufacturers such as Siemens, GE, Bosch and Panasonic. "Companies have begun to add security to IoT at the network level, and many have Mocana security onboard," Mocana's VP of marketing, Keao Caindec, told SecurityWeek; "but what is still missing is really a focus on protecting the supply chain."
Mocana Logo
A primary problem is a lack of essential security on the devices. Manufacturers still cut corners to keep costs down and speed of delivery up; while users tend to spend their security budget on threat detection and firewalls surrounding the devices rather than ensuring that the device has its own security. Mocana's device security can add security capabilities to the device. Now, with the launch of a new TrustCenter platform, it can also ensure that firmware updates and patches are genuine and not compromised by man-in-the-middle attacks.
Protecting the supply chain now completes the Mocana process of applying security to the complete IoT device security lifecycle.
Supply chain attacks are already happening. In one example, reported by Brian Krebs, the U.S. Secret Service issued an alert to banks in March 2018. Criminals are intercepting mail containing corporate debit payment cards. They swap the existing chip for an old or invalid chip and allow it to be delivered to the customer. The customer receives the apparently new card and activates it. Once this happens, the criminals can use the stolen chip for their own purposes.
The Secret Service warning does not indicate how the criminals intercept the card. However, an investigation by the BBC in 2017 describes postal workers in the UK being offered £1000 per week to intercept and steal mail, including bank cards. "In 2016," says the BBC, "there were 11,377 cases of fraud where a card is stolen in transit, costing card issuers £12.5m."
For embedded and installed devices, criminals are more likely to attack and compromise the software update process. "Securing devices during firmware updates is a big issue," said Caindec. "Automobile manufacturers have a big problem in front of them in scaling to support up to 100 ECUs (engine control units) in cars, controlling everything from infotainment to autonomous driving and obstacle avoidance -- and they need to update those in an almost constant stream of updates. How do you ensure that all of those updates are trusted and not being implemented on devices that are already compromised?"
Part of the larger issue of ensuring the integrity of the supply chain, he added, "is the sheer complexity, because it includes the component manufacturers, the software developer, and the operators and end users of the devices that need to be updated."
To ease this problem, his firm has announced the new Mocana TrustCenter. Its three primary purposes are to provide supply chain integrity, allow faster development and provisioning of devices containing TrustPoint security, and to reduce costs by automating secure enrollment and provisioning at a scale suitable for the billions of IoT devices being manufactured.
"It is a services platform that allows manufacturers and operators of devices to securely enroll and update their devices," he explained. "We automate the enrollment of the devices by using the enrollment over secure transport (EST -- RFC 7030) standard that automates certificate management. Customers can now implement a secure credential in these IoT devices automatically within seconds, reducing many of the manual processes that companies go through, from minutes down to seconds. This will help companies to really scale IoT and to secure their devices."
TrustCenter also provides a secure update service. "It is really a platform that we provide, that sits on the customer's own metal or in their public or private cloud infrastructure." It automates secure device onboarding, enrollment and over-the-air (OTA) updates for IoT and ICS. Mission-critical systems used in aerospace, defense, industrial manufacturing, transportation, medical, and automotive can now automate the IoT security software integration process.
It enables, continued Caindec, "a software developer to make a change to firmware, sign the code and pass it on to the manufacturer. The manufacturer can sign it, and provide it to the owner of the device -- who can then sign it and implement it securely knowing that the device is going to be able to verify through MFA software on the device that the software developer and manufacturer and owner have all approved this update. Only then will it decrypt the software and install the update."
The new Mocana TrustCenter secures the device firmware supply chain, while the Mocana TrustPoint secures the device itself. By integrating the two, Mocana seeks to secure the complete IoT security lifecycle.
“Traditional IT and OT security approaches are not enough to defend against the sophisticated threats from hackers and state actors,” comments William Diotte, Mocana's CEO. “With escalating cyber-attacks on critical infrastructure and IoT, it’s imperative that industrial companies implement stronger controls in their automation and control equipment. Mocana TrustCenter and TrustPoint make it easier to implement strong security into devices by automating the lifecycle of cybersecurity for a device."
San Francisco, CA-based Mocana was founded in 2004, originally to provide security for devices in military equipment, from aircraft to tanks. Since then it has diversified and raised a total of $80.7 million in a series of relatively small funding rounds including $25 million series D funding in 2012. The most recent Series F funding for $11 million was announced in May 2017.
'Operation Parliament' Imitates Another Actor to Stay Undetected
13.4.2018 securityweek CyberSpy
A series of geopolitically motivated attacks ongoing since early 2017 and targeting high profile organizations worldwide appear to be a symptom of escalating tensions in the Middle East region, Kaspersky Labs reveals.
Utilizing unknown malware, the actor remained under the radar by imitating another attack group in the region, which also made attribution difficult, especially given recent examples of false flags being planted to send investigators down the wrong tracks.
While the initial attacks look as the work of the unsophisticated Gaza Cybergang (decoys, file names), deeper analysis revealed a different picture, Kaspersky says.
The attacks, which Kaspersky refers to as Operation Parliament, were clearly centered on espionage, hitting top legislative, executive and judicial bodies. Since early 2017, the attackers targeted numerous organizations worldwide, but focused mainly on the Middle East and North Africa (MENA) region, especially Palestine.
Supposedly connected to incidents Cisco Talos detailed earlier this year, the assaults targeted high-profile entities such as parliaments, senates, top state offices and officials, political science scholars, military and intelligence agencies, ministries, media outlets, research centers, election commissions, Olympic organizations, large trading companies, and other unknown entities.
Kaspersky believes the attacks are the work of “a previously unknown geopolitically motivated threat actor” doing “just enough to achieve their goals.” The attackers supposedly have access to additional tools when needed and also use “an elaborate database of contacts in sensitive organizations and personnel worldwide, especially of vulnerable and non-trained staff.”
Compromised systems range from “personal desktop or laptop systems to large servers with domain controller roles or similar.” They belong to ministries responsible for telecommunications, health, energy, justice, finance, and other areas.
Victims were located in the Palestinian Territories, Egypt, Jordan, the UAE, Saudi Arabia, Djibouti, Qatar, Lebanon, Chile, Somalia, Iraq, Morocco, Syria, India, Iran, Canada, the USA, the UK, Germany, Israel, Afghanistan, Serbia, Russia, Oman, Kuwait, South Korea and Denmark.
The attackers have carefully verified victim devices before infecting them and also safeguarded their command and control (C&C) servers. The attacks slowed down since the beginning of this year, likely “winding down when the desired data or access was obtained,” Kaspersky notes.
“The targeting of specific victims is unlike previously seen behavior in regional campaigns by Gaza Cybergang or Desert Falcons and points to an elaborate information-gathering exercise that was carried out before the attacks (physical and/or digital),” the researchers point out.
Packed with VMProtect, the employed malware didn’t reveal similarities with previously known malicious programs. Encryption and obfuscation were applied to all strings and settings, while communication with the C&C server was achieved via HTTP.
Data sent to the C&C is encrypted and the malware uses different keys for local and network encryption. The malware initiates communications by sending basic information about the infected machine and the server responds with the encrypted serialized configuration.
The malware provides a remote CMD/PowerShell terminal for the attackers, which allows them to execute scripts and commands on the compromised machines, and to receive the results via HTTP requests.
Kaspersky would not provide full details on the attacks and the used malware, but points out that high-profile organizations should have advanced protections in place, given that attacks against them “are inevitable and are unlikely to ever cease.”
“These organizations need to pay particular attention to their security, implementing additional measures to ensure they are well protected. Anti-targeted attack solutions, threat intelligence capabilities and data flows, default-deny application lockdown, endpoint detection and response, data leak and insider threat prevention, and even isolated/air-gapped networks should form the basis of any strategy for protecting organizations in the current threat landscape,” Kaspersky concludes.
Key Points From Facebook-Zuckerberg Hearings
13.4.2018 securityweek Social
Facebook chief Mark Zuckerberg testified for nearly 10 hours over two days on Facebook's privacy and data protection issues before committees of the Senate and House on Tuesday and Wednesday. Here are key points:
Protecting the platform
"It's clear now we didn't do enough," Zuckerberg said on the protection of private user data and to prevent the hijacking of data on millions by Cambridge Analytica.
Zuckerberg said Facebook was built as "an idealistic and optimistic company" to help people connect but failed "to prevent these tools from being used for harm... that goes for fake news, for foreign interference in elections, and hate speech, as well as developers and data privacy."
He said that by the end of the year Facebook would have 20,000 people working on security and content review and would also step up use of artificial intelligence to weed out fake accounts and inappropriate content.
Regulation
Zuckerberg said regulation of social media companies is inevitable, but warned that rules could also hamper the industry's growth.
"The internet is growing in importance around the world in people's lives, and I think that it is inevitable that there will need to be some regulation," he told lawmakers.
"But I think you have to be careful about putting regulation in place. A lot of times regulations put in place rules that a company that is larger, that has resources like ours, can easily comply with, but that might be more difficult for a smaller startup company."
Zuckerberg said the EU's General Data Protection Regulation (GDPR) to come into effect on May 25 was more stringent than what was currently in place at Facebook and suggested it could serve as a rough model for US rules in the future.
Facebook is implementing the GDPR standards for European users next month, and some of its rules will be extended to US and other users later, he confirmed.
"The GDPR requires us to do a few more things and we are going to extend that to the world," he said.
Facebook model
Zuckerberg maintained that Facebook users deserve protection of private data but appeared to argue that its controls make it possible to determine how information is shared.
He claimed that "there's a very common misperception... that we sell data to advertisers," adding that "we do not sell data to advertisers. We don't sell data to anyone."
But he maintained that advertising enables Facebook to offer a free service and that targeted ads based on user categories were more acceptable to users, even if they could opt out.
Zuckerberg also said the company believed in an ad-supported business model, but appeared to leave open the possibility of a paid version.
"There will always be a version of Facebook that is free," Zuckerberg told the hearing.
Russian manipulation
The 33-year-old CEO said Facebook was in a constant struggle to guard against Russian manipulation of the Facebook platform to influence elections in the US and elsewhere.
"There are people in Russia whose job it is to try to exploit our systems and other internet systems and other systems as well," he said.
"So this is an arms race. They're going to keep getting better and we need to invest in getting better at this too."
Zuckerberg has previously acknowledged the social network failed to do enough to prevent the spread of disinformation during the last US presidential race.
"One of my greatest regrets in running the company is that we were slow in identifying the Russian information operations in 2016," he said.
"We expected them to do a number of more traditional cyber attacks, which we did identify and notify the campaigns that they were trying to hack into them. But we were slow at identifying the type of -- of new information operations."
He added that Facebook is cooperating with the special counsel investigation into Russian interference in the 2016 election.
"Our work with the special counsel is confidential. I want to make sure in an open session I don't reveal something that's confidential," he said.
APT33 devised a code injection technique dubbed Early Bird to evade detection by anti-malware tools
13.4.2018 securityaffairs APT
The Iran-linked APT33 group continues to be very active, security researchers at Cyberbit have discovered an Early Bird code injection technique used by the group.
The Early Bird method was used to inject the TurnedUp malware into the infected systems evading security solutions.
The technique allows injecting a malicious code into a legitimate process, it allows execution of malware before the entry point of the main thread of a process.
“We saw this technique used by various malware. Among them – the “TurnedUp” backdoor written by APT33 – An Iranian hackers group, A variant of the notorious “Carberp” banking malware and by the DorkBot malware.” reads the analysis published by the experts.
“The malware code injection flow works as follows:
Create a suspended process (most likely to be a legitimate windows process)
Allocate and write malicious code into that process
Queue an asynchronous procedure call (APC) to that process
Resume the main thread of the process to execute the APC”
Anti-malware tools insert hooks when a process starts running, the code sections placed on specific Windows API calls allows security solution to detect the threats while invoking the API.
APT33 Early Bird technique allows bypassing the anti-malware hooking mechanism.
The Early Bird technique “loads the malicious code in a very early stage of thread initialization, before many security products place their hooks – which allows the malware to perform its malicious actions without being detected,” continues the analysis published by Cyberbit.
Experts noticed that during the initialization phase of the main thread, immediately after the call to NtResumeThread, a function called NtTestAlert checks the APC queue to delay the code of the main threat until the APC code is finished.
“During the initialization phase of the main thread (Right after the call to NtResumeThread), a function called NtTestAlert checks the APC queue. If the APC queue is not empty – NtTestAlert will notify the kernel which in return jump to KiUserApcDispatcher which will execute the APC. The code of the main thread itself will not execute until the code of the APC is finished executing,” continues the analysis.
“Before returning to user-mode, the kernel prepares the user-mode thread to jump to KiUserApcDispatcher which will execute the malicious code in our case,”

Differently from other methods, the Early Bird technique aims to hide the malicious actions executed post-injection.
The APT33 group has been around since at least 2013, since mid-2016, the group targeted the aviation industry and energy companies with connections to petrochemical production.
CVE-2018-0950 flaw in Microsoft Outlook could be exploited to steal Windows Passwords
13.4.2018 securityaffairs Vulnerebility
An 18-month-old CVE-2018-0950 vulnerability in Microsoft Outlook could be exploited by hackers to steal the Windows Password.
Almost 18 months ago, the security researcher Will Dormann of the CERT Coordination Center (CERT/CC) has found a severe vulnerability in Microsoft Outlook (CVE-2018-0950), time is passed but Microsoft partially addressed it with the last Patch Tuesday updates.
The flaw in Microsoft Outlook ties the way Microsoft Outlook renders remotely-hosted OLE content when an RTF (Rich Text Format) an email is previewed and automatically initiates SMB connections.
The CVE-2018-0950 flaw could be exploited by attackers to steal sensitive data such as Windows login credentials by tricking victims into preview an email with Microsoft Outlook,
“Outlook blocks remote web content due to the privacy risk of web bugs. But with a rich text email, the OLE object is loaded with no user interaction. Let’s look at the traffic in Wireshark to see what exactly is being leaked as the result of this automatic remote object loading.” wrote Dormann.
The vulnerability, discovered by Will Dormann of the CERT Coordination Center (CERT/CC), resides in the way Microsoft Outlook renders remotely-hosted OLE content when an RTF (Rich Text Format) email message is previewed and automatically initiates SMB connections.
The attack scenario sees a remote attacker exploiting the vulnerability by sending an RTF email to the victim, the malicious message contains an image file (OLE object) that is loaded from a remote SMB server under the control of the attackers.
“Here we can see than an SMB connection is being automatically negotiated. The only action that triggers this negotiation is Outlook previewing an email that is sent to it.” The following screenshot shows that IP address, domain name, Username, hostname, SMB session key are being leaked.

“Microsoft Outlook will automatically retrieve remote OLE content when an RTF email is previewed. When remote OLE content is hosted on a SMB/CIFS server, the Windows client system will attempt to authenticate with the server using single sign-on (SSO).” states the CERT. “This may leak the user’s IP address, domain name, user name, host name, and password hash. If the user’s password is not complex enough, then an attacker may be able to crack the password in a short amount of time.”
Microsoft Outlook automatically renders OLE content, this means that it will initiate an automatic authentication with the attacker’s controlled remote server over SMB protocol using single sign-on (SSO). This will cause the leak of NTLMv2 hashed version of the password that could be cracked by the attacks with commercial tools and services.
Microsoft attempted to address the flaw in the last security updates, but it only successfully fixed automatically SMB connections when it previews RTF emails, any other SMB attack is still feasible.
“It is important to realize that even with this patch, a user is still a single click away from falling victim to the types of attacks described above,” Dormann added. “For example, if an email message has a UNC-style link that begins with “\\”, clicking the link initiates an SMB connection to the specified server.”

Summarizing, the installation of the Microsoft update for CVE-2018-0950 will not fully protect users from the exploitation of this issue.
Users are advised to apply the following mitigations:
Install the Microsoft update for CVE-2018-0950.
Block ports 445/tcp, 137/tcp, 139/tcp, along with 137/udp and 139/udp used for SMB sessions.
Block NT LAN Manager (NTLM) Single Sign-on (SSO) authentication.
Always strong passwords.
Never click on suspicious links embedded in emails.
Palo Alto Networks Acquires Incident Response Firm Secdo
12.4.2018 securityweek IT
Palo Alto Networks this week announced that it has entered a definitive agreement to acquire Israel-based incident response firm Secdo. Financial terms of the deal have not been disclosed, but some reports say Palo Alto is prepared to pay $100 million.
According to Palo Alto Networks, endpoint detection and response (EDR) capabilities obtained as a result of the Secdo acquisition will be used to improve the Palo Alto Networks Traps endpoint protection product and the Application Framework.
Secdo’s collection and visualization system will feed rich data to Palo Alto’s Logging Service in order to give applications running on the Application Framework greater precision, the companies said.
Secdo has raised a total of $11 million since it was founded in 2014 by security experts from Israel’s famous 8200 intelligence unit.
Israeli media claims to have learned from sources close to Secdo that Palo Alto Networks has agreed to pay $100 million, mostly in cash.
“We believe security operations teams need the most advanced and consistent approach to endpoint security. With Secdo’s EDR capabilities as part of our platform, we will accelerate our ability to detect and prevent successful cyberattacks across cloud, endpoint, and the network,” said Mark McLaughlin, chairman and CEO of Palo Alto Networks.
Palo Alto Networks expects to complete the acquisition in the third fiscal quarter.
Carbon Black Prepares for $100 Million IPO
12.4.2018 securityweek IT
Endpoint security solutions provider Carbon Black this week announced that it has filed an S-1 registration statement with the U.S. Securities and Exchange Commission (SEC) for a proposed initial public offering (IPO) of its common stock.
Waltham, Massachusetts-based Carbon Black says it’s looking to raise $100 million in the IPO. The company’s stock will be traded on NASDAQ under the ticker symbol CBLK.
Rumors of a Carbon Black IPO have been circulating for years, with some reports saying that the company filed confidentially for an IPO back in 2016.
Carbon Black files for IPO
Carbon Black has raised more than $191 million in over a dozen funding rounds since it was founded in 2002. The company was initially called Bit9, but in 2016, two years after a merger with Carbon Black, it became Carbon Black. The list of Carbon Black acquisitions includes Objective Logistics, VisiTrend, and Confer Technologies.
In its SEC filing, Carbon Black says it has more than 3,700 global customers, including some of the world’s largest security-focused government agencies and enterprises. These customers are served by more than 900 employees.
The company says it has experienced strong revenue growth in the past years, increasing from $70.6 million in 2015 to $116.2 million in 2016 and $162 million in 2017. However, losses have also increased, from $38.7 million in 2015 to $55.8 million in 2017, which the company has blamed on its continued investment in growth.
Carbon Black’s endpoint security solutions include application control, endpoint detection and response (EDR), and next-generation antivirus capabilities. Competitors named by the company in its SEC filing are McAfee, Symantec, Cisco, FireEye, Palo Alto Networks, Cylance, CrowdStrike, and Tanium.
The first cybersecurity firm to go public in 2018 was Zscaler, which started with an IPO price of $16 per share and closed the first day of trading at $33 per share. The company was hoping to raise $110 million, but ended up making nearly double that amount. The company’s stock currently trades at roughly $28.
Another cybersecurity company that went public recently is ForeScout Technologies, which raised $116 million in October in its IPO.
Financial experts have named several firms that could file for an IPO this year, including Illumio, Cloudflare, Tanium, AlienVault, Centrify and ForgeRock.
Czech Antivirus Targets London's Biggest Tech Float
12.4.2018 securityweek IT
Czech antivirus software maker Avast announced Thursday that it will float on the London stock market next month in the British capital's biggest ever technology IPO.
"Avast ... today announces that it intends to proceed with an initial public offering" in London, it said in a statement, adding that it was expected to occur in early May.
Prague-based Avast, one of the world's biggest online security software companies, will seek to float at least 25 percent of its share capital.
The IPO could value it at $4.0 billion (3.2 billion euros), according to the Financial Times.
"Over the past thirty years, Avast has grown from a visionary start-up to the number one consumer cybersecurity company," said Avast chief executive Vincent Steckler.
"This transformation of our company has happened because of the dramatic increase in the number and types of threats around the world which are a growing concern to people, and Avast's ability to stay ahead of the bad guys with new and evolving technologies and products."
The group is well positioned to take advantage of an expanding consumer cybersecurity market, which Steckler said was forecast to grow 10 percent annually and reach $21 billion by 2021.
Avast is 46-percent owned by its founders, while investment company CVC has a 29-percent stake.
The group, which has more than 435 million users around the world, has a workforce of 1,700 people and generated sales of $653 million in 2017. Avast purchased Dutch rival AVG Technologies in 2016.
Researchers discovered several flaws that expose electrical substations to hack
12.4.2018 securityaffairs ICS
The ICS-CERT and Siemens published are warning organizations of security flaws in Siemens devices (SIPROTEC 4, SIPROTEC Compact, and Reyrolle devices) that could be exploited by hackers to target electrical substations.
“Successful exploitation of these vulnerabilities could allow an attacker to upload a modified device configuration that could overwrite access authorization passwords, or allow an attacker to capture certain network traffic that could contain authorization passwords.” reads the advisory published by the ICS-CERT.
The Siemens devices provide integrated protection, control, measurement, and automation functions for several applications, including electrical substations.
Siemens has already issued security patches and mitigations for the flaws.

The vulnerabilities were discovered by security experts at Positive Technologies, let’s analyzed the flaws discovered by the experts.
“Positive Technologies experts Ilya Karpov, Dmitry Sklyarov, and Alexey Stennikov detected high-risk vulnerabilities in power-system protection from Siemens that is used to control and protect such power supply facilities equipment as electrical substations or hydroelectric power stations. Siemens has fixed the vulnerabilities and issued the corresponding advisories.” states the post published by Positive Technologies.
“By exploiting these vulnerabilities, an attacker is able to change the configuration of power-system protection relay which can lead to disruption of the power equipment protection function (and potentially to an accident) or customer curtailment.”
The most severe vulnerability (rated high severity), tracked as CVE-2018-4840 can be exploited by a remote and unauthenticated attacker to modify the device’s configuration and overwrite access passwords.
“The device engineering mechanism allows an unauthenticated remote user to upload a modified device configuration overwriting access authorization passwords. ” reads the security advisory published by Siemens.
The second flaw, tracked as CVE-2018-4839, is a medium severity issue that could be exploited by a local or network attacker to recover the access authorization password by intercepting network traffic or obtaining data from the targeted device. Once the attacker has obtained the password he can use it to gain complete access to a device.
Both CVE-2018-4840 and CVE-2018-4839 affects the EN100 Ethernet modules and the DIGSI 4 operation and configuration software used by SIPROTEC 4 and SIPROTEC Compact relay families.
Researchers at Positive Technologies also discovered a high severity vulnerability tracked as CVE-2018-4838 that resides in the web interface of the relays (SIPROTEC 4, SIPROTEC Compact, and Reyrolle relays that use EN100 modules.) that could be exploited by an unauthenticated attacker to downgrade the firmware on a device to a version that is known to be affected by vulnerabilities.
“CVE-2018-4838 allows an intruder to remotely upload an obsolete firmware version that contains known vulnerabilities and to execute code on the target system. Devices that use the EN100 communication module (SIPROTEC 4, SIPROTEC Compact, and Reyrolle) can be attacked.” states the advisory published by the company.
The above issued represent a serious threat to electrical substations that are a key component in the electric grids.
Microsoft Office 365 Gets Built-in Ransomware Protection and Enhanced Security Features
12.4.2018 thehachernews Safety 
Ransomware has been around for a few years, but it has become an albatross around everyone's neck, targeting big businesses, hospitals, financial institutions and individuals worldwide and extorting millions of dollars.
Last year, we saw some major ransomware outbreaks, including WannaCry and NotPetya, which wreaked havoc across the world, hitting hundreds of thousands of computers and business networks worldwide.
From small to mid-range businesses, Microsoft Office 365 remains the most widely used and fastest-growing work office suite, so it's no surprise that it has become a primary target for viruses, ransomware, and phishing scams.
In fact, most strains of ransomware target Microsoft productivity apps such as Word, Excel and encrypt sensitive data to hold the company hostage until the ransom is paid.
Now, to combat such cyber attacks, Microsoft has announced some new security features for Office 365 that can help users mitigate the damage done by ransomware and other malware infections.
The new features were initially introduced for OneDrive for Business, but that the company is now rolling them out to anyone who has signed up for an Office 365 Home or Personal subscription, Microsoft Office blog says.
Here below I have briefed the list of new features:
File Recovery and Anti-Ransomware
Files Restore—Microsoft Office 365 now allows users to restore entire OneDrive to a previous point in time within the last 30 days. This feature can be used to recover files from an accidental mass delete, file corruption, ransomware, or any catastrophic event.
Ransomware detection & recovery—Office 365 had also introduced a new security feature that detects ransomware attacks and alerts you through an email, mobile, or desktop notification while helping you restore your OneDrive to a point before the malware compromised files.
Security and Privacy Features
Office 365 has added three new features to help keep your confidential or personal data (such as tax documents, family budgets, or a new business proposal) secure and private when sharing them online.
Password protected sharing links—This feature allows you to set a password for your shared file and folders, preventing unauthorized access even if your recipient accidentally forwards protected documents to others.
Email encryption—This feature allows users to send/receive end-to-end encrypted emails in Outlook over a secure connection, providing additional protection to minimize the threat of being intercepted.
Prevent forwarding—Microsoft now enables you to restrict your email recipients from forwarding or copying emails you send to them from Outlook. Besides this, any MS Office document attached to your emails will remain encrypted even after downloading, so if the recipient shares your attachment with others, they will not be able to open it.
Advanced Protection from Viruses and Cybercrime
Advanced link checking in Word, Excel, and PowerPoint—Office 365 also offers built-in real-time web protection, which monitors every link you click in Word, Excel, and PowerPoint and notifies you if it is suspicious.
File Recovery and Anti-Ransomware features began rolling out starting today and will be available to all Office 365 users soon, while features to help keep your information secure and private (including password protected sharing links, email encryption, and prevent forwarding) will start rolling out in the coming weeks.
Advanced link checking and advanced attachment scanning are already available in MS Outlook that protects you from previously unseen viruses and phishing scams in real-time. However, advanced link checking in Word, Excel, and PowerPoint will roll out in the second half of 2018.
Here's how hackers are targeting Cisco Network Switches in Russia and Iran
12.4.2018 thehachernews Vulnerebility 
Since last week, a new hacking group, calling itself 'JHT,' hijacked a significant number of Cisco devices belonging to organizations in Russia and Iran, and left a message that reads—"Do not mess with our elections" with an American flag (in ASCII art).
MJ Azari Jahromi, Iranian Communication and Information Technology Minister, said the campaign impacted approximately 3,500 network switches in Iran, though a majority of them were already restored.
The hacking group is reportedly targeting vulnerable installations of Cisco Smart Install Client, a legacy plug-and-play utility designed to help administrators configure and deploy Cisco equipments remotely, which is enabled by default on Cisco IOS and IOS XE switches and runs over TCP port 4786.
Some researchers believe the attack involves a recently disclosed remote code execution vulnerability (CVE-2018-0171) in Cisco Smart Install Client that could allow attackers to take full control of the network equipment.
However, since the hack apparently resets the targeted devices, making them unavailable, Cisco believes hackers have been merely misusing the Smart Install protocol itself to overwrite the device configuration, instead of exploiting a vulnerability.
"The Cisco Smart Install protocol can be abused to modify the TFTP server setting, exfiltrate configuration files via TFTP, modify the configuration file, replace the IOS image, and set up accounts, allowing for the execution of IOS commands," the company explains.
Chinese security firm Qihoo 360's Netlab also confirms that that hacking campaign launched by JHT group doesn’t involve the recently disclosed code execution vulnerability; instead, the attack is caused due to the lack of any authentication in the Cisco smart install protocol, reported in March last year.
According to Internet scanning engine Shodan, more than 165,000 systems are still exposed on the Internet running Cisco Smart Install Client over TCP port 4786.
Since Smart Install Client has been designed to allow remote management on Cisco switches, system administrators need to enable it but should limit its access using Interface access control lists (ACLs).
Administrators who do not use the Cisco Smart Install feature at all should disable it entirely with the configuration command—"no vstack."
Although recent attacks have nothing to do with CVE-2018-0171, admins are still highly recommended to install patches to address the vulnerability, as with technical details and proof-of-concept (PoC) already available on the Internet, hackers could easily launch their next attack leveraging this flaw.
Finland's 3rd Largest Data Breach Exposes 130,000 Users' Plaintext Passwords
12.4.2018 thehachernews Incindent 
Over 130,000 Finnish citizens have had their credentials compromised in what appears to be third largest data breach ever faced by the country, local media reports.
Finnish Communications Regulatory Authority (FICORA) is warning users of a large-scale data breach in a website maintained by the New Business Center in Helsinki ("Helsingin Uusyrityskeskus"), a company that provides business advice to entrepreneurs and help them create right business plans.
Unknown attackers managed to hack the website (http://liiketoimintasuunnitelma.com) and stole over 130,000 users’ login usernames and passwords, which were stored on the site in plain-text without using any cryptographic hash. Right after knowing of the breach on 3rd April, the company took down the affected website, which is currently showing "under maintenance" notice with a press release about the incident on its homepage.
"We are very sorry for all the people who have been subjected to crime and who may be affected by mental or financial disadvantages. Unfortunately, we are not yet able to know exactly how many people are and what information this information breaks. We have filed an offense report, and the parties do not need to report to the police separately," says Jarmo Hyökyvaara, Chairman of the Board of the New Business Center of Helsinki.
"The maintenance and security of our service was the responsibility of our subcontractor, our long-term partner. Unfortunately, the security of the service has not been enough to prevent this kind of attack. This is, in part, our mistake, and as a subscriber and owner of the service we are responsible for this."
The company also ensures that the detailed information of its customers was stored on a different system, which was not affected by the data breach.
The incident has been reported to the Helsinki police, who is currently investigating the case as a gross fraud.
As soon as the website returns, users who have an account with the affected website are strongly recommended to change their passwords.
Since the plain-text passwords have been exposed to hackers, it would be a great idea for users to change their passwords for any other website, in case they are using identical to the one used on this website.
Critical Code Execution Flaw Found in CyberArk Enterprise Password Vault
12.4.2018 thehachernews Vulnerebility
A critical remote code execution vulnerability has been discovered in CyberArk Enterprise Password Vault application that could allow an attacker to gain unauthorized access to the system with the privileges of the web application.
Enterprise password manager (EPV) solutions help organizations securely manage their sensitive passwords, controlling privileged accounts passwords across a wide range of client/server and mainframe operating systems, switches, databases, and keep them safe from external attackers, as well as malicious insiders.
Discovered by German cybersecurity firm RedTeam Pentesting GmbH, the vulnerability affects one of such Enterprise Password Vault apps designed by CyberArk—a password management and security tool that manages sensitive passwords and controls privileged accounts.
The vulnerability (CVE-2018-9843) resides in CyberArk Password Vault Web Access, a .NET web application created by the company to help its customers access their accounts remotely.
The flaw is due to the way web server unsafely handle deserialization operations, which could allow attackers to execute code on the server processing the deserialized data.
According to the researchers, when a user logs in into his account, the application uses REST API to send an authentication request to the server, which includes an authorization header containing a serialized .NET object encoded in base64.
This serialized .NET object holds the information about a user's session, but researchers found that the "integrity of the serialized data is not protected."
Since the server does not verify the integrity of the serialized data and unsafely handles the deserialization operations, attackers can merely manipulate authentication tokens to inject their malicious code into the authorization header, gaining "unauthenticated, remote code execution on the web server."
Researchers have also released a full proof-of-concept code to demonstrate the vulnerability using ysoserial.net, an open source tool for generating payloads for .NET applications performing unsafe deserialization of objects.
The technical details of the vulnerability and exploit code came only after RedTeam responsibly reported the vulnerability to CyberArk and the company rolled out patched versions of the CyberArk Password Vault Web Access.
Enterprises using CyberArk Password Vault Web Access are highly recommended to upgrade their software to version 9.9.5, 9.10 or 10.2.
In case you cannot immediately upgrade your software, the possible workaround to mitigate this vulnerability is disabling any access to the API at the route / PasswordVault / WebServices.
Container Security Firm StackRox Raises $25 Million
12.4.2018 securityweek IT
Container security firm StackRox announced this week that it has secured $25 million in a Series B funding round, bringing the total raised to date by the company to more than $39 million.
The funding round was led by Redpoint Ventures with participation from previous investors Sequoia Capital and Amplify Partners. The new funds will be used to accelerate product development and support expanded go-to-market programs, which includes hiring new marketing and sales executives.
TJ Cooley, who served in senior positions at Tanium, VMware and Citrix, has joined StackRox as vice president of sales. Michelle McLean, who previously held senior marketing roles at ScaleArc, Silver Spring Networks, ConSentry Networks, Peribit Networks, and Trapeze Networks, has been named the company's first vice president of marketing.StackRox
Based in Mountain View, California, StackRox provides solutions that help enterprises secure cloud-native applications running on container technologies such as Docker and Kubernetes. The company’s flagship product, StackRox Detect and Respond, is designed to monitor activities at runtime, identify attack tactics, and neutralize threats. Improved performance and detection capabilities have now been added to the solution, the startup said.
Next week at the RSA Conference, the company will announce the general availability of its second product, Prevent, which helps minimize the attack surface, centralize governance, and prioritize risks.
StackRox says it works with a number of research and government organizations in an effort to understand threats to containers. The company claims its customers include government agencies and Global 2000 firms in the finance, tech and media sectors, including the DHS and City National Bank.
Companies specializing in securing containers have raised significant amounts of money in the past few years. Aqua Security has raised a total of $38 million, Twistlock secured $30 million, NeuVector raised $7 million, Capsule8 raised $8.5 million, and Tigera received $23 million.
Electrical Substations Exposed to Attacks by Flaws in Siemens Devices
12.4.2018 securityweek ICS
Electrical substations and other power supply facilities are exposed to hacker attacks due to several potentially serious vulnerabilities discovered by researchers in some Siemens protection relays.
On March 8, Siemens and ICS-CERT published advisories to warn organizations of the existence of three vulnerabilities in SIPROTEC 4, SIPROTEC Compact, and Reyrolle devices, which provide integrated protection, control, measurement, and automation functions for electrical substations and other applications. The vendor has released patches and mitigations for each of the flaws.
Positive Technologies, the company whose researchers discovered the flaws, has now provided information regarding the risk and impact.Siemens SIPROTEC relay flaws expose electrical substations to attacks
One of the vulnerabilities, tracked as CVE-2018-4840 and rated high severity, can be exploited by a remote and unauthenticated attacker to modify the device’s configuration and overwrite access passwords.
Another security hole, CVE-2018-4839, is a medium severity issue that allows a local or network attacker to recover the access authorization password by intercepting network traffic or obtaining data from the targeted device. The password can be used to gain complete access to a relay, Positive Technologies said.
CVE-2018-4840 and CVE-2018-4839 impact SIPROTEC 4 and SIPROTEC Compact protection relays, specifically the EN100 Ethernet modules and the DIGSI 4 operation and configuration software used by the devices.
Positive Technologies also informed Siemens of CVE-2018-4838, a high severity vulnerability in the web interface that allows an unauthenticated attacker to downgrade the firmware on a device to a version that contains known flaws. This security hole affects SIPROTEC 4, SIPROTEC Compact, and Reyrolle relays that use EN100 modules.

According to Positive Technologies, these vulnerabilities can pose a serious risk to electrical facilities and their exploitation could even result in power supply disruptions.
“By exploiting these vulnerabilities, an attacker is able to change the configuration of power-system protection relay which can lead to disruption of the power equipment protection function (and potentially to an accident) or customer curtailment,” the security firm warned.
Malicious actors targeting SIPROTEC relays is not unheard of. While analyzing the piece of malware known as Industroyer and Crashoverride, which is believed to have been used in the December 2016 attack aimed at an electrical substation in Ukraine, researchers discovered a denial-of-service (DoS) tool that exploits a SIPROTEC vulnerability patched in 2015 to cause relays to become unresponsive.
SAP Patches Critical Flaws in Business Client
12.4.2018 securityweek Vulnerebility
SAP this week released its April 2018 set of security patches, which include fixes for critical vulnerabilities in web browser controls delivered with SAP Business Client.
A total of 10 Security Notes were included in this month’s Security Patch Day, along with 2 updates to previously released security notes. One of the Notes was rated Hot News, 4 were High Priority, and 7 had a Medium Priority rating, SAP’s advisory reads.
The most important of the Security Notes addresses multiple vulnerabilities in the web browser controls used to display pages in SAP Business Client 6.5 PL5. The vulnerabilities impact browser controls for Microsoft's Internet Explorer (IE) and the open source Chromium.
“The latter has been determined to show multiple weaknesses like memory corruption, information disclosure and more. Although the SAP note does not explicitly mention it, similar security flaws can be expected for IE,” Onapsis, a firm that specializes in securing Oracle and SAP products, reveals.
Users who follow the Windows update process should be safe from the vulnerabilities in the IE browser control, given that the control “hooks into libraries that are patched alongside other Windows updates,” Onapsis explains.
Delivered with the SAP Business Client, the Chromium browser control requires the newly released security note to patch.
One of the High Priority Security Notes in SAP’s April 2018 patches addresses a denial of service (DoS) in SAP Business One (CVSS score of 7.5), but the bug actually exists in Apache (used as a HTTP server in the Business One service layer). By exploiting the bug, an attacker could terminate the vulnerable application’s process.
SAP also addressed an improper session management issue in SAP Business Objects (CVSS score of 7.3). Tracked as CVE-2018-2408, the vulnerability results in existing user sessions remaining active even after a password change.
This month, SAP also released an update to a Note addressing a code injection vulnerability in SAP Visual Composer (CVSS score of 7.4). The flaw allowed an attacker to inject code into the back-end application by sending a specially crafted HTTP GET request to the Visual Composer. SAP fixed that, but researchers discovered that the bug could be triggered using POST requests as well.
Additionally, SAP released Update 1 to Security Note 2376081. Also featuring a CVSS score of 7.4, the Note patches bugs in VCFRAMEWORK and VC70RUNTIME.
One other update included in this month’s Patch Day is Security Note 2201710. Rated Medium Priority and featuring a CVSS score of 5.4, it is an update to a note released with the September 2015 Patch Day: Fixing Logjam and Alternative chains certificate forgery vulnerabilities in multiple SAP products. 18 SAP products are impacted.
The remaining Security Notes released this month address bugs in SAP CP Connectivity Service and Cloud Connector, Disclosure Management, Solution Manager Incident Management Workcenter, Business One Browser Access, Crystal Reports Server OEM Edition, and Control Center and Cockpit Framework.
SAP also released 4 Security Notes after the second Tuesday of the previous month and before the second Tuesday of this month, for a total of 16 Security Notes, according to ERPscan, another firm specialized in securing Oracle and SAP products.
The resolved issues include 5 implementation flaws, 2 directory traversal, 2 cross-site scripting (XSS), 2 code injection, buffer overflow, missing authorization check, denial of service, XML external entity (XXE), and clickjacking.
New Authentication Standard Coming to Major Web Browsers
12.4.2018 securityweek Safety
Web browsers from Google, Microsoft, and Mozilla will soon provide users with a new, password-less authentication standard built by the FIDO Alliance and the World Wide Web Consortium (W3C) and currently in the final approval stages.
W3C has advanced a standard web API called Web Authentication (WebAuthn) to the Candidate Recommendation (CR) stage, the final step before the final approval of a web standard. Expected to deliver stronger web authentication to users worldwide, it is already being implemented for Windows, Mac, Linux, Chrome OS and Android platforms.
W3C’s WebAuthn API enables strong, unique, public key-based credentials for each site, thus eliminating the risk that passwords stolen on one site could be used on another. WebAuthn can be incorporated into browsers and web platform infrastructure, providing users with new methods to securely authenticate on the web, in the browser, and across sites and devices.
Along with FIDO’s Client to Authenticator Protocol (CTAP) specification, it is a core component of the FIDO2 Project, which enables “users to authenticate easily to online services with desktop or mobile devices with phishing-resistant security.”
CTAP enables an external authenticator to transmit strong authentication credentials over USB, Bluetooth, or NFC to a device that has Internet access (PC or mobile phone).
Both WebAuthn and CTAP are available today, so that developers and vendors can implement support for the new authentication methods into their products and services. Backed by leading browser vendors, the new specifications should provide ubiquitous, hardware-backed FIDO Authentication protection to all Internet users.
“After years of increasingly severe data breaches and password credential theft, now is the time for service providers to end their dependency on vulnerable passwords and one-time-passcodes and adopt phishing-resistant FIDO Authentication for all websites and applications,” Brett McDowell, executive director of the FIDO Alliance, said.
Enterprises and online service providers can soon deploy the new web authentication standards to protect themselves and their customers from the risks associated with passwords. The new FIDO2 specifications complement existing password-less FIDO UAF and second-factor FIDO U2F use cases. All FIDO2 web browsers and online services are backwards compatible with certified FIDO Security Keys.
The standards are currently being implemented in major web browsers, including Chrome, Firefox and Microsoft Edge. Android and Windows 10 will have built-in support for FIDO Authentication, FIDO says.
The Alliance says it would soon launch interoperability testing and that it also plans on issuing certifications for servers, clients, and authenticators adhering to FIDO2 specifications. Conformance test tools have already become available on FIDO’s website.
A new Universal Server certification for servers that interoperate with all FIDO authenticator types (FIDO UAF, FIDO U2F, WebAuthn, and CTAP) is also underway.
Web apps running in a browser on a device with a FIDO Authenticator can call to a public API to enable FIDO Authentication of users. Developers can learn more on FIDO’s new developer resources page.
With FIDO2, users would benefit from both simpler — they would log in with a single gesture, using internal / built-in authenticators (such as fingerprint or facial biometrics in PCs, laptops and/or mobile devices) or external authenticators (security keys and mobile devices) — and stronger authentication — credentials and biometric templates never leave the user’s device and accounts are protected from phishing, man-in-the-middle and replay attacks that use stolen passwords.
Industrial Internet Consortium Develops New IoT Security Maturity Model
12.4.2018 securityweek IoT
The Industrial Internet Consortium (IIC) has developed a new IoT Security Maturity Model (SMM), building on its own security framework and reference architecture. This week it has published the first of two papers: IoT Security Maturity Model: Description and Intended Use. This is primarily a high-level overview aimed at the less technical of IoT stakeholders.
"This is for the businessmen," Ron Zahavi, chief strategist for IoT standards at Microsoft, told SecurityWeek, "to help them understand what is needed of security, and to help them translate that into a required maturity level for their own business." The required maturity level becomes the target maturity level.
A second paper providing a more technical view for the security practitioners will be published in the summer. "The separation of the two," said Zahavi, "allows different groups and verticals to develop specific profiles that can be published with the second technical document."
The purpose of the model is to provide a single IoT SMM for all industry sectors, regardless of individual security requirements; and to be relevant to all IoT implementations, whether home, office or plant. The IIC's guiding principles were to develop a new model suitable for all industries, to cover both process and technology, to leverage existing frameworks such as NIST and ISA-62443 rather than seek to replace them, to be simple and extensible, and to be suitable for use by all existing security assessment firms.
It starts from the basis that maturity is built on three primary dimensions: governance, enablement, and hardening. Each dimension comprises different domains. "Governance covers strategy and the operation and management of practices and process such as threat modeling and risk assessment, and supply chain management," explained Zahavi. "Enablement includes the operation and management of traditional security technology, such as identity and access management, data protection, asset management, physical management, etcetera. Hardening," he added, "is about the operational aspects of vulnerability and patch management, incident response and auditing, and so on." In short, it is process, technology and operation.
Each of the domains and practices is then evaluated on two axes: 'comprehensiveness' and 'scope'. Comprehensiveness, said Zahavi, "is about the degree of depth and consistency that you apply security measures to the dimensions, domains and practices." There are four levels (five, if you include 'nothing'): minimal; ad hoc (where security tends to be reactive to a publicized incident or issue); consistent (using best practices and standards, and possibly centralized rather than spot solutions); and formalized (comprising a well-defined process for managing everything over time and with continuous improvement).
Scope is defined as the degree of fit to the industry or system needs. Here there are three levels: general (where there is no specific assessment of relevance to the specific IoT sector); industry specific (where security is implemented with regard to sector specific requirements – healthcare may be different to manufacturing); and system specific (where security implementation is aligned with the specific needs and risks of a particular system in a particular organization). For the system specific scope, Zahavi commented, "A retail organization might wish to delineate between its PoS sensors and its supply chain sensors."
Combining the comprehensiveness and scope across the different practices allows an organization to define its IoT security maturity at both actual and target levels, and at a very granular level of the security implementation.
The target level of maturity is almost a statement of risk appetite. It is a business function, not a security function. For many years, security teams have operated blindly, with little communication between business and security. This is changing. The digitalization of industry and the merging of operational technology (the primary home of IoT devices) with information technology, and the subsequent exposure of IoT devices to the internet is changing the bottom line of security failures.
While the loss of information can be costly and brand-damaging, the loss of manufacturing can be catastrophic. The growth in ICS attacks and the dramatic effects these can have on profitability has got the attention of the board – and the board is now asking security to explain whether their IoT implementations are secure. Using the IIC SMM can help better align security with business priorities, and can help business and security come together.
The recommended process is for business leaders to specify the maturity level targets, while the security team undertakes a current maturity assessment. The difference between the two levels can be assessed with a gap analysis from which a roadmap for closing any gaps can be developed. The roadmap should lead to any required security enhancements – which should then lead to a reassessment of the maturity level and a repeat of the process.
An aid to this process is a maturity profile template. The IIC hopes that different companies in different sectors will develop and publish high level IIC SMM maturity profiles that can be used by other organizations.
The intention of the IIC with this new IoT security maturity model is to augment, not replace, existing security frameworks. "There already exist accepted frameworks that get down to the control mechanisms for security," explained Zahavi. "But if you look, for example, at the table of controls and the mappings in NIST, they don't get into the level of 'what do I do for my industry and what levels do I need to be in?'.
"What we're doing," he continued, "is we're creating the higher-level maturity aspect of it, which is not met in all of those frameworks -- we're augmenting, we're not replacing. For example, we don't suggest specific required security controls. Instead, we're mapping the SMM – and we'll continue to do this (NIST, for example, is also an IIC member) – mapping practices and the appropriate maturity levels to existing frameworks and controls.
"So," he said, "the intent is, if you have a profile for retail or healthcare or manufacturing, you should be able to look at your industry sector, and go back to those existing frameworks with a much narrower view of which mechanisms and controls you need to then deploy to achieve your target maturity for your own company in your own sector."
The IIC IoT security maturity model is an aid to help companies employ existing favored security frameworks to reach their own defined target level of IoT security maturity.
Mobile Phishing Attacks Up 85 Percent Annually
12.4.2018 securityweek Phishing
The rate at which users are receiving and clicking on phishing URLs on their mobile devices has increased at an average rate of 85% per year since 2011, mobile security firm Lookout reports.
What’s more worrisome is the fact that 56% of users received and clicked on a phishing URL that bypasses existing layers of defense, the security firm says. On average, a user clicked on a mobile phishing URL six times per year.
In a new report (PDF) analyzing the present state of mobile phishing, the security company explains that attackers are successfully circumventing existing phishing protections to target the mobile devices. Thus, they manage to expose sensitive data and personal information at an alarming rate, the company claims.
With over 66% of emails first opened on a mobile device and email arguably the first point of attack for a phishing actor, unprotected emails on a mobile device can easily turn into a new avenue for attack.
“Most corporations are protected from email-based phishing attacks through traditional firewalls, secure email gateways, and endpoint protection. In addition, people today are getting better at identifying phishing attacks. Mobile, however, has made identifying and blocking phishing attacks considerably more difficult for both individuals and existing security technologies,” Lookout notes.
The security firm claims that existing phishing protections are not adequate for mobile devices, where the relatively small screen makes distinguishing a real login page from a fake one highly problematic. On mobile, email is only one of the possible attack vectors, with truncated malicious URLs and apps accessing potentially malicious links also being used for compromise.
SMS and MMS also provide attackers with new means of phishing, not to mention popular and highly used personal social media apps and messaging platforms such as WhatsApp, Facebook Messenger, and Instagram. According to Lookout, more than 25% of employees click on a link in an SMS message from a phone number spoofed.
One attacker known to have used a non-email means of phishing is the threat actor behind ViperRAT, who engaged into conversations with their victims after posing as women on social media platforms. Once they managed to establish their trust, the actor asked the victims to download an app for “easier communication.”
In another example, an attacker targeted iOS and Android users via Facebook Messenger, suggesting that they appeared in a YouTube video. When clicking on the provided link, the user was served a fake Facebook login page meant to steal their credentials.
Lookout also notes that users are three times more likely to click on a suspicious link on a phone than on a PC. On a mobile device, users can’t always see the entire link they click on, as they would on a desktop, and there isn’t always a firewall to keep the device protected, as would be the case with a PC in a corporate environment.
“Mobile phishing is increasingly the tip of the spear for sophisticated, large-scale attacks. Some of the most active attacks come from mobile advanced persistent threats, or mAPTs,” Lookout also notes.
While an APT is a group, usually a nation-state, which can persistently and effectively target other nation-states, businesses, or individuals to steal information, a mAPT brings such attacks to mobile. Dark Caracal and Pegasus are only a couple of the most recent examples of such attacks.
Furthermore, because some applications contain URLs in the codebase to communicate and fetch information in real-time, attackers can abuse the functionality for phishing. Thus, enterprises should worry about “benign apps” that access malicious URLs.
“For example, apps often use advertising to make money. In order to do so, they incorporate ad SDKs into their code. These SDKs connect to URLs behind the scenes in order to display ads to the end user. If a benign app uses an ad SDK run by an attacker, that attacker may use the SDK to access malicious URLs in order to display ads meant to trick the end user into giving over sensitive data,” Lookout explains.
AMD, Microsoft Release Spectre Patches
11.4.2018 securityweek Vulnerebility
AMD and Microsoft on Tuesday released microcode and operating system updates that should protect users against Spectre attacks.
When the existence of the Spectre and Meltdown vulnerabilities was brought to light, AMD downplayed their impact on its processors, but the company did promise to release microcode updates and add protections against these types of attacks to its future CPUs.
Meltdown attacks rely on a vulnerability identified as CVE-2017-5754, while Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). In the case of AMD, the company’s processors are not affected by Meltdown thanks to their design, and Spectre Variant 1 can be addressed with software patches – just like in the case of Intel processors.AMD releases microcode updates to patch Spectre
Mitigating Spectre Variant 2 attacks requires a combination of microcode and operating system updates, which AMD and Microsoft released on Tuesday.
“While we believe it is difficult to exploit Variant 2 on AMD processors, we actively worked with our customers and partners to deploy the above described combination of operating system patches and microcode updates for AMD processors to further mitigate the risk,” said Mark Papermaster, senior vice president and chief technology officer at AMD.
Microcode updates, which users can obtain from device manufacturers via BIOS updates, have been developed for AMD processors dating back to the first Bulldozer core products launched in 2011. The chip giant has published a document detailing the indirect branch control feature designed to mitigate indirect branch target injection attacks such as Spectre Variant 2.
Windows 10 updates released by Microsoft on Tuesday include Spectre Variant 2 mitigations for AMD devices. The patches are also expected to become available for Windows Server 2016 after they are validated and tested.
Microsoft started releasing Spectre patches for devices with AMD processors shortly after the CPU vulnerabilities were disclosed in early January. However, the company was forced to temporarily suspend the updates due to instability issues.
As for Linux devices, AMD said mitigations for Spectre Variant 2 were made available earlier this year.
While AMD processors appear to be less impacted compared to Intel products, lawsuits have still been filed against the company over the Spectre vulnerabilities.
SirenJack: Hackers Can Remotely Trigger Warning Sirens
11.4.2018 securityweek Hacking
Researchers at Bastille, a company that specializes in detecting threats through software-defined radio, have uncovered a new method that can be used to remotely hack emergency warning systems.
Sirens are used worldwide to alert the public of natural disasters, man-made disasters, and emergency situations, including tornadoes, hurricanes, floods, volcanic eruptions, nuclear accidents, chemical spills, and terrorist attacks. False alarms can cause widespread panic and annoyance.
Researchers say they have discovered a new attack method that allows hackers to remotely trigger sirens. This type of attack, dubbed SirenJack, is possible due to a vulnerability found in emergency alert systems made by ATI Systems, a company whose products are used by major cities, universities, military facilities, and industrial sites.
According to Bastille, the vulnerability, related to the use of insecure radio protocol controls, was initially found in the system used by the city of San Francisco and later confirmed at a second installation.
Bastille researcher Balint Seeber started analyzing the city’s outdoor public warning system in 2016 after noticing that it had been using RF communications. An analysis of the system showed that commands were sent without being encrypted, allowing a malicious actor to forge commands.
Attackers need to identify the radio frequency used by the targeted siren and send the system a specially crafted message that triggers an alarm.Sirenjack
“A single warning siren false alarm has the potential to cause widespread panic and endanger lives,” said Chris Risley, CEO of Bastille Networks. “Bastille informed ATI and San Francisco of the vulnerability 90 days ago, to give them time to put a patch in place. We’re now disclosing SirenJack publicly to allow ATI Systems’ users to determine if their system has the SirenJack vulnerability. We also hope that other siren vendors investigate their own systems to patch and fix this type of vulnerability.”
ATI Systems has been made aware of the vulnerability and it has created a patch that adds an additional layer of security to the packets sent over the radio. The company says the patch is being tested and will be made available shortly, but noted that installing it is not an easy task considering that many of its products are designed for each customer’s specific needs.
While Bastille has made it sound like an attack is easy to launch due to the unencrypted protocol, ATI Systems told customers not to panic, pointing out that the cybersecurity firm monitored its product for months before figuring out how to launch an attack.
ATI noted that its current products no longer use the old control protocols that often allowed malicious actors and pranksters to trigger false alarms. However, the company admitted that the system used in San Francisco was installed 14 years ago and acquiring a highly secure system, such as the ones used on military bases, can be too expensive for a city.
This is not the only interesting wireless attack method discovered by researchers at Bastille. The company has also targeted home networks (CableTap), wireless keyboards (KeySniffer), and mouse/keyboard dongles (MouseJack).
Karamba Security Raises $10 Million for Inorganic Growth
11.4.2018 securityweek IT
Karamba Security, a firm that specializes in cybersecurity solutions for autonomous and connected cars, on Tuesday announced that it has raised another $10 million, bringing the total raised to date to $27 million.
The latest funding round was led by Silicon Valley-based venture debt firm Western Technology Investment (WTI), which claims to have provided more than $5 billion of growth capital to companies in the past 38 years.
Karamba Security raises $10 million
Karamba plans on using the newly obtained funds for inorganic growth, specifically to acquire companies and technology that will help accelerate the progress of its portfolio. The money will also be used to address the growing demand for its products, the firm said.
“Our ongoing operations are well funded from the previous $17 million raised last year. This new funding provides a line of capital we can use as needed for inorganic growth to expand Karamba's solutions suite across the rapidly evolving automotive landscape,” said Karamba CEO Ami Dotan.
Since its launch in April 2016, Karamba Security says it has engaged with 17 automotive OEMs and tier-1 suppliers to help them secure their products. The company’s technology has been integrated with ARM, Intel, PowerPC, and Infineon chips, along with QNX, Linux and various RTOS and AUTOSAR platforms on the operating system level.
Top Music Videos Including 'Despacito' Defaced by Hackers
11.4.2018 securityweek Hacking
Some of the most popular music videos on YouTube including mega-hit "Despacito" momentarily disappeared Tuesday in an apparent hacking.
Fans looking for videos by top artists including Drake, Katy Perry and Taylor Swift found the footage removed and replaced by messages that included "Free Palestine."
Luis Fonsi's "Despacito" -- the most-watched video of all time at five billion views -- was briefly replaced by an image of a gun-toting gang in red hoods that appeared to come from the Spanish series "Money Heist."
Most videos were back up by early Tuesday US time but some still had defaced captions, which boasted of hacking by a duo calling themselves Prosox and Kuroi'SH.
YouTube, which is owned by search engine giant Google, said that the problem centered on Vevo -- a site backed by music labels that hosts videos -- and not YouTube itself.
"After seeing unusual upload activity on a handful of Vevo channels, we worked quickly with our partner to disable access while they investigate the issue," a YouTube spokesperson said.
Vevo confirmed a security breach on its end and said it had been contained.
"We are working to reinstate all videos affected and our catalog to be restored to full working order. We are continuing to investigate the source of the breach," it said in a statement.
A Twitter user identified as Kuroi'SH threatened more hacks including on the South Korean boy band BTS.
"This is not fake we are real!" he tweeted, adding, "Everything is hack-able."
Facebook to Offer 'Bounty' for Reporting Data Abuse
11.4.2018 securityweek Social
Facebook said Tuesday it would begin offering rewards to people who report misuse of private information from the social network, as part of an effort to step up data protection in the wake of a firestorm.
The new program "will reward people with first-hand knowledge and proof of cases where a Facebook platform app collects and transfers people's data to another party to be sold, stolen or used for scams or political influence," product security chief Collin Greene said in a statement.
Greene said the new offer was inspired by the "bug bounty" offered by Facebook and other online services to reward people who find security flaws.
The reward will be "based on the impact of each report," Greene said, with a minimum of $500 for verified cases of abuse affecting 10,000 people or more.
"While there is no maximum, high impact bug reports have garnered as much as $40,000 for people who bring them to our attention," he added.
The announcement comes with Facebook chief Mark Zuckerberg set to begin testimony at congressional hearings Tuesday and Wednesday on abuse of private data collected by the social network.
Facebook is under fire in the United States and around the world following disclosures of private data hijacked by the consultancy Cambridge Analytica, which was working for Donald Trump's 2016 campaign.
"We'll review all legitimate reports and respond as quickly as possible when we identify a credible threat to people's information," Greene said of the new program.
"If we confirm data abuse, we will shut down the offending app and take legal action against the company selling or buying the data, if necessary. We'll pay the person who reported the issue, and we'll also alert those we believe to be affected."
What Social Media Platforms And Search Engines Know About You
11.4.2018 securityweek Social
The Facebook scandal involving the harvesting of data from tens of millions of users has raised a lot of questions about social media and search engines.
As Facebook founder and CEO Mark Zuckerberg testifies before the US Congress this week on protecting user data, here is a primer on what they know about you:
Social media
Facebook, which has more than two billion users, has access to everything you do on the site: the photos and videos you post, your comments, your 'likes,' anything you share or consult, the identity of your friends and any other users you interact with, your location and other information.
Ditto for Instagram and WhatsApp, which are owned by Facebook, and for Snapchat and Twitter. A user can control some sharing of their Facebook data with privacy settings and the ad preferences page.
● What it sells: Facebook insists it does not sell advertisers personally identifiable information or even aggregate data. What it provides an advertiser with is the ability to reach a specific demographic, which enhances the effectiveness of an ad campaign. Twitter, for its part, provides access to an internal search engine that sweeps up all messages on the site.
● What it shares: Most social media platforms are open to outside developers who create apps fed in varying degrees by using data from users of these networks. In the case of Facebook, the public profile -- the whole page for some people, or just the first and last name and photo for others -- does not require authorization from the user, but accessing the rest may require a separate OK from the user.
Once data is mined by outside apps, it is no longer in the grasp of Facebook and trying to get hold of it again is difficult.
"Once people had access to that data, Facebook has no way of knowing for sure what they did with that data," said Ryan Matzner, co-founder of mobile app designer Fueled. "It's like sending an email to somebody and then saying: 'What did they do with that email?' You don't know."
Only bank and payment details held by Facebook are off-limits.
Search engines
● What they collect: Google, Yahoo and Bing gather all information involving searches including the websites that are accessed and the location of the user. This can be integrated with information from other services owned by the internet giants.
"You don't have to tell Google your age and your gender and all those things. They can determine all of that based on so many other factors," said Chirag Shah, a computer science professor at Rutgers University.
● What they sell: like social networks, their revenue comes largely from advertising. They do not sell data, but rather access to a consumer with very specific characteristics.
This comes from compiling search engine data but also, in the case of Google, from searches and content viewed on its YouTube platform. Google used to also mine the content of Gmail before ending this practice in June.
● What they share: Like social media networks, search engines share data with developers and third-party app makers.
Are there limits?
In the United States there are practically no laws against the use of data from social media or search engines.
But the Federal Trade Commission did sanction Facebook in 2011 for its handling of personal data.
In Canada and Europe, there are some limits on the use of data, mainly involving health.
Facebook was fined 110 million euros ($135.7 million) by the European Commission last year for sharing personal data with WhatsApp.
In an attempt to harmonize data privacy laws, the EU's General Data Protection Regulation is to go into force on May 25.
Adobe Patches Vulnerabilities in Six Products
11.4.2018 securityweek Vulnerebility
Adobe has patched a total of 19 vulnerabilities across six of its products, including Flash Player, Experience Manager, InDesign CC, Digital Editions, ColdFusion and the PhoneGap Push plugin.
A total of six flaws rated critical and important have been fixed in Flash Player with the release of version 29.0.0.140, including use-after-free, out-of-bounds read, out-of-bounds write and heap overflow bugs that can lead to remote code execution and information disclosure.
Four of the vulnerabilities have been reported to Adobe by researchers at Google Project Zero. While some of the issues have been rated critical, Adobe says there is no evidence of malicious exploitation and the company does not believe exploits are imminent.
The number of vulnerabilities fixed in Flash Player has dropped significantly since Adobe announced its intention to kill the application in 2020. However, malicious actors have not given up trying to find security holes they can exploit. In February, Adobe issued an emergency update to address a zero-day used by North Korean hackers.
The April Patch Tuesday updates from Adobe also cover Experience Manager, in which the company patched three moderate and important cross-site scripting (XSS) flaws.
An update has also been released for Adobe InDesign CC to fix a critical memory corruption that allows arbitrary code execution via specially crafted .inx files, and an untrusted search path issue in the installer that can lead to privilege escalation.
The latest version of Adobe Digital Editions resolves an out-of-bounds read vulnerability and a stack overflow, both of which can result in disclosure of information.
ColdFusion version 11 and the 2016 release have also received security updates. A total of five flaws have been patched, including local privilege escalation, remote code execution and information disclosure issues.
Finally, the Adobe PhoneGap Push plugin has been updated to address a same-origin method execution bug that exposes apps built with the affected plugin to JavaScript code execution.
Microsoft Patches Two Dozen Critical Flaws in Windows, Browsers
11.4.2018 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for April 2018 resolve a total of 66 vulnerabilities, including nearly two dozen critical issues affecting Windows and the company’s web browsers.
None of the flaws patched this month appear to have been exploited in the wild, but one privilege escalation vulnerability discovered by a Microsoft researcher in SharePoint has been disclosed to the public.
A majority of the critical flaws affecting Internet Explorer and Edge are related to scripting engines and they allow remote code execution.
A remote code execution flaw affecting the VBScript engine has also been rated critical. The security hole can be exploited via malicious websites or documents. Trend Micro’s Zero Day Initiative (ZDI) noted that while this is similar to browser bugs, the attack surface is broader due to the possibility of exploitation using Office documents.
Several critical vulnerabilities that allow remote code execution have also been found in graphics components, specifically font libraries and how they handle embedded fonts.
“Since there are many ways to view fonts – web browsing, documents, attachments – it’s a broad attack surface and attractive to attackers. Given the history of malicious fonts, these patches should be high on your test and deployment list. This is also a good time to remind you to not do day-to-day tasks as an administrator,” ZDI’s Dustin Childs explained in a blog post.
Microsoft also informed customers that its Wireless Keyboard 850 is affected by a security feature bypass vulnerability that can be exploited to simulate keystrokes and send malicious commands to the targeted computer. An attacker could also exploit this flaw to read keystrokes, which can include sensitive information, such as passwords.
“[The vulnerability] could allow an attacker to reuse an AES encryption key to send keystrokes to other keyboard devices or to read keystrokes sent by other keyboards for the affected devices. An attacker would first have to extract the AES encryption key from the affected keyboard device. The attacker would also need to maintain physical proximity – within wireless range – of the devices for the duration of the attack,” Microsoft said.
Adobe’s Patch Tuesday updates address a total of 19 vulnerabilities across six products. Six flaws have been fixed in Flash Player, which Microsoft also resolved in Windows.
Earlier this month, Microsoft announced the release of an update for its Malware Protection Engine to patch a critical vulnerability that could have been exploited to take control of a system by placing a malicious file in a location where it would be scanned.
Adobe April Security Bulletin Tuesday fixed 4 critical flaws in Flash
11.4.2018 securityaffairs Vulnerebility
Adobe April Security Bulletin Tuesday is out, the company has addressed four critical vulnerabilities in the Flash Player.
Adobe April Security Bulletin has addressed a total of 19 vulnerabilities in its products, including Flash Player, Experience Manager, InDesign CC, Digital Editions, ColdFusion and the PhoneGap Push plugin.
The company has released the Flash Player version 29.0.0.140 that fixed four critical flaws and two issues rated as important.
The flaws addressed with the Adobe April Security Bulletin Tuesday include a use-after-free, out-of-bounds read, out-of-bounds write and heap overflow bugs that could be exploited by remote attackers to execute arbitrary code on the target system and that could lead information disclosure.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities in Adobe Flash Player 29.0.0.113 and earlier versions. Successful exploitation could lead to arbitrary code execution in the context of the current user.” reads the security advisory published by Adobe.
Below the vulnerability details
Vulnerability Category Vulnerability Impact Severity CVE Number
Use-After-Free Remote Code Execution Critical CVE-2018-4932
Out-of-bounds read Information Disclosure Important CVE-2018-4933
Out-of-bounds read Information Disclosure Important CVE-2018-4934
Out-of-bounds write Remote Code Execution Critical CVE-2018-4935
Heap Overflow Information Disclosure Important CVE-2018-4936
Out-of-bounds write Remote Code Execution Critical CVE-2018-4937
Adobe acknowledged Google white hat hackers Mateusz Jurczyk and Natalie Silvanovich of Google Project Zero for reporting the CVE-2018-4936, CVE-2018-4935, CVE-2018-4934, CVE-2018-4937 flaw.
The CVE-2018-4933 vulnerability was reported by willJ of Tencent PC Manager, while the CVE-2018-4932 flaw was reported by Lin Wang of Beihang University.
The good news is that according to Adobe, there is no evidence of malicious exploitation in the wild.
Adobe also addressed three moderate and important cross-site scripting (XSS) flaws in the Experience Manager.
Adobe also fixed a critical memory corruption flaw (CVE-2018-4928) in Adobe InDesign CC that was reported by Honggang Ren of Fortinet’s FortiGuard Labs. Ren discovered a memory corruption flaw that could be exploited for arbitrary code execution.
Adobe also fixed an out-of-bounds read vulnerability and a stack overflow issue in Adobe Digital Editions and five flaws in ColdFusion.
The last issue covered by the company is a same-origin method execution bug in the Adobe PhoneGap Push plugin.
Public services at the Caribbean island Sint Maarten shut down by a cyber attack
11.4.2018 securityaffairs Cyber
A cyber attack shut down the entire government infrastructure of the Caribbean island Sint Maarten. public services were interrupted.
A massive cyber attack took offline the entire government infrastructure of the Caribbean island Sint Maarten. it is a constituent country of the Kingdom of the Netherlands.
Government building remained closed after the attack.
“The Ministry of General Affairs hereby informs the public that the recovery process of the Government of Sint Maarten ICT Network is progressing steadily and will continue throughout the upcoming weekend following the cyber-attack on Monday April 2nd” reported the media.
According to the local media, The Daily Herald a cyber attack hit the country on April 2nd, the good news is that yesterday the government services were resumed with the exception of the Civil Registry Department.

According to the authorities, this is the third attack in over a year, but at the time of writing, there are no public details on the assault.

“The system was hacked on Easter Monday, the third such attack in over a year. No further details about the hacking have been made public by government.
The Ministry “thanked the people of St. Maarten for their patience during this period.” continues the announcement.
Below the announcement made by the Government on Facebook.
The incident demonstrates the importance of a cyber strategy for any government, in this case, hacked shut down government networks but in other circumstances, they can hack into government systems to launch cyber attack against a third-party nation.
It is essential a mutual support among stated to prevent such kind of incident.
Top VEVO Music videos Including ‘Despacito’ defaced by hackers
11.4.2018 securityaffairs Hacking
Some of the most popular music VEVO videos on YouTube, including the world’s most popular video ‘Despacito’ has been hacked by a duo calling themselves Prosox and Kuroi’SH.
Some of the most popular music videos on YouTube, including the world’s most popular YouTube video ‘Despacito’ has been hacked.
Popular videos of pop stars like Shakira, Drake, Selena Gomez, Adele, Taylor Swift, and Calvin Harris were replaced by hackers that spread the message “Free Palestine.”
Despacito, the Luis Fonsi’s mega-hit that was watched five billion times was replaced by an image of a group of armed men dressed in hooded sweatshirts that appeared to come from the Spanish series “Money Heist.”

Source Welivesecurity.com
The videos were hacked by a duo calling themselves Prosox and Kuroi’SH.
All the hacked videos are on singers’ accounts belonging to the VEVO platform that is owned by a group of some of the biggest music corporations.
According to YouTube, the problem doesn’t affect its platform but Vevo.
“After seeing unusual upload activity on a handful of Vevo channels, we worked quickly with our partner to disable access while they investigate the issue,” a YouTube spokesperson said.
Vevo confirmed a security breach on systems.
“We are working to reinstate all videos affected and our catalog to be restored to full working order. We are continuing to investigate the source of the breach,” it said in a statement.
The alleged hacker @ProsoxW3b started posting severs Tweets first saying it has hacked for fun and not for profit.

Business-Critical Systems Increasingly Hit by Ransomware: Verizon 2018 DBIR
10.4.2018 securityweek ICS Ransomware
Ransomware has become the most prevalent type of malware and it has increasingly targeted business-critical systems, according to Verizon’s 2018 Data Breach Investigations Report (DBIR).
The 11th edition of the DBIR is based on data provided to Verizon by 67 organizations, and it covers more than 53,000 incidents and over 2,200 breaches across 65 countries.
According to Verizon, ransomware was found in 39% of cases involving malware. Experts believe ransomware has become so prevalent due to the fact that it’s easy to deploy — even for less skilled cybercriminals — and the risks and costs associated with conducting an operation are relatively small for the attacker.
Cybercriminals have increasingly started using ransomware to target mission-critical systems, such as file servers and databases, which causes more damage to the targeted organization compared to only desktop systems getting compromised.
By targeting a larger number of devices and more important systems within an organization, attackers can demand bigger ransoms.
“What is interesting to us is that businesses are still not investing in appropriate security strategies to combat ransomware, meaning they end up with no option but to pay the ransom – the cybercriminal is the only winner here!” explained Bryan Sartin, executive director of security professional services at Verizon. “As an industry, we have to help our customers take a more proactive approach to their security. Helping them to understand the threats they face is the first step to putting in place solutions to protect themselves.”
According to the latest DBIR, financially-motivated attacks remain the most common and accounted for 76% of breaches analyzed in 2017. Cyber espionage is the second most common type of attack, accounting for 13% of breaches.
Nearly three-quarters of attacks were conducted by outsiders, half of which were organized crime groups, and 12% were state-sponsored threat actors.
Almost half of the attacks analyzed by Verizon involved hacking and 30% relied on malware. One in five incidents involved mistakes made by employees, including misconfigured web servers, emails sent to the wrong person, and failure to shred confidential documents.
While 78% of employees did not click on any phishing links, 4% will fall for any given campaign. This is a small percentage, but one victim is enough for an attacker to gain access to an organization’s systems, Verizon warned.
The telecoms giant also revealed that the number of incidents involving pretexting has increased more than five times since the previous DBIR. Of the 170 incidents analyzed in 2017, 88 targeted HR staff with the goal of obtaining personal data that could be used to file fraudulent tax returns.
Both an executive summary and the full report are available directly from Verizon in PDF format — no registration is required.
Booby-trapped Office docs build with ThreadKit trigger CVE-2018-4878 flaw
10.4.2018 securityaffairs Vulnerebility
Microsoft Office documents created with the exploit builder kit dubbed ThreadKit now include the code for CVE-2018-4878 flaw exploitation.
At the end of March, security experts at Proofpoint discovered a Microsoft Office document exploit builder kit dubbed ThreadKit that has been used to spread a variety of malware, including banking Trojans and RATs (i.e. Trickbot, Chthonic, FormBook and Loki Bot).
The exploit kit was first discovered in October 2017, but according to the experts, crooks are using it at least since June 2017.
The ThreadKit builder kit shows similarities to Microsoft Word Intruder (MWI), it was initially being advertised in a forum post as a builder for weaponized decoy documents.
Just after its appearance, documents created with the ThreadKit builder kit have been observed in several campaigns.
Now threat actors are using the ThreadKit builder kit to target the recently patched CVE-2018-4878 Flash vulnerability, experts started observing exploit code samples in the wild a few days ago.

Adobe addressed the CVE-2018-4878 in February after North Korea’s APT group was spotted exploiting it in targeted attacks.
The vulnerability could be exploited by an attack by tricking victims into opening a document, web page or email containing a specially crafted Flash file.
According to the researcher Simon Choi the Flash Player flaw has been exploited by North Korea since mid-November 2017. The attackers exploited the zero-day vulnerability in attacks aimed at South Korean individuals involved in research activity on North Korea.
Now the exploit was included in the ThreadKit builder, based on Virus Total hashes posted to Pastebin.
The security expert Claes Splett has published a video that shows how to build a CVE-2018-478 exploit in ThreadKit.
Proofpoint experts reported that in the last weeks, the exploit kit included new exploits targeting vulnerabilities such as the CVE-2018-4878 Adobe Flash zero-day and several Microsoft office vulnerabilities (i.e. CVE-2018-0802 and CVE-2017-8570).
Linux open source utility Beep is affected by several vulnerabilitues
10.4.2018 securityaffairs Vulnerebility
Researchers have discovered several vulnerabilities in the Linux command line tool Beep, some experts suggest to remove the utility from distros.
An unnamed security researcher has found several vulnerabilities in the Linux command line tool Beep, including a severe flaw introduced by a patch for a privilege escalation vulnerability.
Beep is a small open source utility used in the past by Linux developers to produce a beep with a computer’s internal speaker, it allows users to control the pitch, duration, and repetitions of the sound.
The researcher discovered a race condition in the utility that could be exploited by an attacker to escalate privileges to root. Versions through 1.3.4 are affected by the flaw that was tracked as CVE-2018-0492.
Further info on the flaw is available on the website holeybeep.ninja

Is your system vulnerable? In order to discover if a system is vulnerable it is possible to run the following command:
curl https://holeybeep.ninja/am_i_vulnerable.sh | sudo bash
A vulnerable machine will beep.
The Holey Beep website also provides a patch, but experts noticed that it actually introduces a potentially more serious vulnerability that could be exploited to execute an arbitrary code on the patched system.
“The patch vulnerability seems more severe to me, as people apply patches all the time (they shouldn’t do it as root, but people are people),” reads a message published by Tony Hoyle on the Debian bug tracker. “It’s concerning that the holeybeep.ninja site exploited an unrelated fault for ‘fun’ without apparently telling anyone.”
Beep is also affected by other issues, including integer overflow vulnerabilities, and a flaw that can reveal information about the file on the system.
Waiting for a code review of the utility, probably it is time to remove the utility from distros because PC speaker doesn’t exist in most modern systems.
DMARC Not Implemented on Most White House Email Domains: Analysis
10.4.2018 securityweek Safety
Over 95% of the email domains managed by the Executive Office of the President (EOP) haven’t implemented the Domain Message Authentication Reporting & Conformance (DMARC) protocol, the Global Cyber Alliance (GCA) has discovered.
After analyzing 26 such domains, GCA discovered that 18 haven’t even started the deployment of DMARC, while 7 of them have implemented the protocol at the lowest level (“none”), which only monitors emails.
Because of that, none of these domains can prevent delivery of spoofed emails, GCA points out. Implementing DMARC ensures that fake emails (known as direct domain spoofing) that spammers and phishers send don’t end up in the users’ inboxes.
Some of the email domains under the control of the EOP include Budget.gov, OMB.gov, WhiteHouse.gov, USTR.gov, OSTP.gov and EOP.gov, all well-known email domains. Only the Max.gov domain has fully implemented the defence against email phishing and spoofing, the GCA report shows.
Without DMARC, these domains can be easily “hijacked” by phishers looking to trick government employees, government contractors, and U.S. citizens. This could lead to money theft, exfiltration of secrets, and could even putt national security at risk.
This widespread lack of DMARC implementation is surprising, given that half a year ago the U.S. Department of Homeland Security (DHS) issued a binding operational directive ordering all federal agencies to start using HTTPS, DMARC and STARTTLS.
As of October 2017, only a small percentage of federal agencies had fully implemented the system, but a January report revealed that half of the U.S. government domains had implemented the protocol, yet most had only implemented the lowest level.
Recently, 4 email domains managed by the EOP have deployed DMARC, with WhiteHouse.gov and EOP.gov, two of the most significant government domains, implementing it at its lowest setting.
“Email domains managed by the EOP are crown jewels that criminals and foreign adversaries covet. The lack of full DMARC deployment across nearly every EOP email address poses a national security risk that must be fixed. The good news is that four new domains have implemented DMARC at the lowest level, which I hope indicates that DMARC deployment is moving forward,” said Philip Reitinger, president and CEO of the Global Cyber Alliance.
Vulnerabilities Found in Linux 'Beep' Tool
9.4.2018 securityweek Vulnerebility
Several vulnerabilities have been found in the Linux command line tool Beep, including a potentially serious issue introduced by a patch for a privilege escalation flaw.
For well over a decade, Beep has been used by developers on Linux to get a computer’s internal speaker to produce a beep. What makes Beep useful for certain programs is the fact that it allows users to control the pitch, duration and repetitions of the sound. The open source application has not received any updates since 2013.
An unnamed researcher discovered recently that Beep versions through 1.3.4 are affected by a race condition that allows a local attacker to escalate privileges to root.
The security hole has been assigned CVE-2018-0492 and it has been sarcastically described as “the latest breakthrough in the field of acoustic cyber security research.” Someone created a dedicated website for it (holeybeep.ninja), a logo, and named it “Holey Beep.”
The individual or individuals who set up the Holey Beep website have also provided a patch, but someone noticed that this fix actually introduces a potentially more serious vulnerability that allows arbitrary command execution.
“The patch vulnerability seems more severe to me, as people apply patches all the time (they shouldn't do it as root, but people are people),” Tony Hoyle explained in a post on the Debian bug tracker. “It's concerning that the holeybeep.ninja site exploited an unrelated fault for 'fun' without apparently telling anyone.”
Furthermore, reports of other security issues affecting Beep emerged over the weekend, along with claims that the fix is incomplete. Beep is also said to be affected by some integer overflow bugs, and a vulnerability that can be exploited to obtain information about files on a system and conduct unauthorized activities.
“I question whether beep should be saved. It would require someone carefully reviewing the code and effectively become the new upstream. And all that for a tool talking to the PC speaker, which doesn't exist in most modern systems anyway,” said German researcher and journalist Hanno Böck. “Instead distros should consider not installing it as suid or just killing the package altogether. I heard some distros (suse) replace beep with a simple ‘printf '\a’ which seems also a safe solution. (although it obviously kills all frequency/length/etc features of original ‘beep’).”
Zuckerberg to Face Angry Lawmakers as Facebook Firestorm Rages
9.4.2018 securityweek Social
Mark Zuckerberg will appear before US lawmakers this week as a firestorm rocks Facebook over its data privacy scandal, with pressure mounting for new regulations on social media platforms.
The 33-year-old chief executive is expected to face a grilling before a Senate panel Tuesday, and follow up with an appearance in the House of Representatives the following day.
It comes amid a raft of inquiries on both sides of the Atlantic following disclosures that data on 87 million users was hijacked and improperly shared with Cambridge Analytica, a British political consultancy working for Donald Trump's presidential campaign.
On Sunday, Facebook said it had suspended another data analysis firm, US-based Cubeyou, after CNBC reported it used Facebook user information -- harvested from psychological testing apps, as in the case of Cambridge Analytica -- for commercial purposes.
"These are serious claims and we have suspended CubeYou from Facebook while we investigate them," a Facebook spokesperson told AFP in an email.
"If they refuse or fail our audit, their apps will be banned from Facebook."
Lawmakers, meanwhile, have signaled they intend to get tough on Facebook and other online services over privacy.
"A day of reckoning is coming for websites like @facebook," Democratic Senator Ed Markey wrote on Twitter Friday.
"We need a privacy bill of rights that all Americans can rely upon."
Representative Ro Khanna, a California Democrat, agreed that legislation is needed "to protect Americans' dignity and privacy from bad faith actors like Cambridge Analytica, who use social media data to manipulate people."
Khanna tweeted that "self-regulation will not work. Congress must act in the public interest to protect consumers and citizens."
Several lawmakers and activists believe the United States should follow the lead of Europe's data protection law set to be implemented in May, which has strict terms for notification and sharing of personal data online.
Zuckerberg told reporters Facebook would follow the European rules worldwide, although cautioned that its implementation may not be "exactly the same format" for various countries and regions.
- Shift on political ads -
Facebook meanwhile announced Friday it will require political ads on its platform to state who is paying for the message and would verify the identity of the payer, in a bid to curb outside election interference.
The change is meant to avoid a repeat of the manipulation efforts by Russian-sponsored entities which sought to foment discord in 2016, and also responds to criticism about anonymous messages based on Facebook profile data.
Zuckerberg said the change will mean "we will hire thousands of more people" to get the new system in place ahead of US midterm elections in November.
"We're starting this in the US and expanding to the rest of the world in the coming months," Zuckerberg said on his Facebook page.
"These steps by themselves won't stop all people trying to game the system. But they will make it a lot harder for anyone to do what the Russians did during the 2016 election and use fake accounts and pages to run ads."
Zuckerberg said Facebook is now endorsing the "Honest Ads Act," a bill that would require disclosure of the sources of online political ads.
"Election interference is a problem that's bigger than any one platform, and that's why we support the Honest Ads Act," he said. "This will help raise the bar for all political advertising online."
Some activists say Facebook needs to do more to guard against manipulation and deception on the platform.
Facebook "should really be turning their attention not only to election ads but to all ads," said Harlan Yu of the technology and social justice nonprofit group Upturn.
"They should disclose to the public a detailed accounting of all the bad ads they're taking down," Yu told a forum Thursday at the New America Foundation.
Facebook is also likely to face questions on whether it violated a 2011 agreement with the US Federal Trade Commission. Activists have alleged the social network failed to live up to promises to protect privacy.
- 'Serial offender' -
David Vladeck, a Georgetown University law professor who headed the FTC's enforcement division when the Facebook deal was negotiated, called the latest incident a "major breach" of the court-supervised settlement.
"Facebook is now a serial offender," Vladeck said in a Harvard Law Review blog post.
But Vladeck noted that a major problem with Facebook's privacy woes comes from its failure to get written contracts and guarantees with third parties such as app developers.
"It seems that Facebook made no effort to establish the (credential) of developers, much less verify or audit what user data app developers actually harvested and shared," Vladeck said.
Some analysts fear that Zuckerberg's appearance on Capitol Hill will be little more than a public relations exercise.
"Zuckerberg's dance before Congress will be delicate, and I'll bet that even a brainiac like him will have a damp shirt under his very nice suit coat not long into it," said Roger Kay, an analyst and consultant with Endpoint Technologies Associates.
"But in the end, he'll agree to some meaningless adjustments to how Facebook operates just to get out of there in one piece."
Schneider Electric Patches 16 Flaws in Building Automation Software
9.4.2018 securityweek ICS
Schneider Electric informed customers last week that the latest version of its U.motion Builder software patches a total of 16 vulnerabilities, including ones rated critical and high severity.
U.motion is a building automation solution used around the world in the commercial facilities, critical manufacturing and energy sectors. U.motion Builder is a tool that allows users to create projects for their U.motion devices.
Researchers discovered that the Builder software is affected by 16 vulnerabilities, including path traversals and other bugs that can lead to information disclosure, and remote code execution flaws via SQL injection.
A majority of the security holes have been classified as medium severity, but some of them are more serious based on their CVSS score.
The most severe, with a CVSS score of 10, actually impacts the Samba software suite. The flaw allows remote code execution and it has been dubbed “SambaCry” by some members of the industry due to similarities to the WannaCry attack. The vulnerability, tracked as CVE-2017-7494, has been found to impact devices from several major vendors, including Cisco, Netgear, QNAP, Synology, Veritas, Sophos and F5 Networks.
Another serious vulnerability in U.motion Builder, identified as CVE-2018-7777, allows an authenticated attacker to remotely execute arbitrary code by sending specially crafted requests to the targeted server. One of the SQL injection flaws, CVE-2018-7765, has also been classified as high severity.
Most of these weaknesses were reported to Schneider by researcher Andrea Micalizzi, also known as “rgod,” and one was disclosed to the company by Constantin-Cosmin Craciun.
The issues affect U.motion Builder versions prior to 1.3.4, which Schneider released in early February. In addition to providing patches, the company has shared some recommendations for mitigating potential attacks.
This is not the first time Micalizzi has been credited for finding vulnerabilities in U.motion Builder. Last year, ICS-CERT reported that the researcher had found half a dozen types of flaws in this software. Those issues were disclosed in late June 2017 before patches were made available by Schneider as they were reported to the vendor via Trend Micro’s Zero Day Initiative (ZDI) more than one year earlier.
Malware Activity Slows, But Attacks More Sophisticated: Report
9.4.2018 securityweek Virus
Malicious Cryptomining Spikes, While Virtually All Other Malware Declines
Malware activity declined in the first quarter of 2018, with both detections for ransomware and cryptominers lower than the last quarter of 2018, according to anti-malware vendor Malwarebytes. However, major reductions in consumer instances mask an increase in both activities against businesses, the company says.
Consumer cryptominers dropped from a peak of 25 million detections in October 2017 to 16 million detections in March 2018. Business detections spiked in February 2017 to around 550,000 detections dropping down to nearly 400,000 in March -- a downturn that may prove temporary due to "a shift in attack strategy".
Ransomware detections have continued the downward trend that started in the middle of last year. Again, however, the large 34% decrease in consumer detections hides a 27% increase in business detections from the last quarter of 2107 to the first quarter of 2018.
Figures come from Malwarebytes' Cybercrime Tactics and Techniques report (PDF) for Q1 2018. Details are gathered from the firm's consumer and business telemetry, and enhanced with intelligence from the company's research and data science teams. It confirms the findings of other malware researchers: that is, increasing criminal interest in cryptomining, where the proceeds of the criminal activity require less effort -- and are more certain -- than the collection of ransoms from ransomware victims.
They also show a shift (albeit only relative) away from consumers towards businesses. Businesses can afford to pay higher ransoms, and may be forced to pay for reasons outside of their own control (to ensure that service level and other contracts are met, or, for healthcare, to ensure continuous service to patients). At the same time, business computers will likely have greater processing capacity for illicit mining.
The one-time kings of ransomware, Locky and Cerber, have largely disappeared; "the most interesting examples of active ransomware in Q1 came in the form of GandCrab, Scarabey, and Hermes," reports Malwarebytes. GandCrab was first spotted in January 2018, being distributed by a diversified RIG EK and the returning GrandSoft EK. It is also distributed via Necurs email spam and ElTest malware campaigns via compromised websites.
While bitcoin remains the most frequently demanded payment mechanism for ransomware, there has been some recent diversification into other cryptocurrencies. GandCrab, for example, demands payment in Dash, "likely," says Malwarebytes, "a sign that threat actors are opting for currencies with lower transaction fees than BTC, and a touch more anonymity in the bargain."
Scarabey, a variant of the Scarab ransomware, seeks to frighten victims into rapid payment by threatening to permanently delete files every day that the ransom remains unpaid. Malwarebytes' analysis, however, concludes, "there's nothing in the ransomware's code that would allow this. It's just a pressure-filled ruse designed to panic victims into paying faster." The firm recommends that future claims of Scarabey's capabilities should be treated with 'a healthy dose of skepticism'.
Hermes was originally distributed via malicious Office documents. By March, it was using a sophisticated exploit kit called GreenFlash Sundown. "After analyzing Hermes," notes the report, "we found it to be a fully functional ransomware. However, we cannot be sure what the real motivations of the distributors were. Looking at the full context, we may suspect that it was politically motivated rather than a profit-driven attack."
The primary methods for illicit cryptomining are by delivered malware, or via the user's browser (through drive-by mining or malicious extensions). In both cases, attackers seek to compromise or make use of as many computers as possible in order to maximize the mining process. The malware itself is fairly unsophisticated, but the delivery mechanisms are not. Two separate groups, for example, made use of the same exploits used in WannaCry to infect hundreds of thousands of Windows servers and generate millions of dollars in revenue.
Drive-by browser-based cryptomining really started with CoinHive in mid-September 2017. Weaknesses in the API soon led to its abuse. Visitors to compromised websites found their computers being silently used, via their browser, for cryptomining -- a process that continues for as long as the visited page remains open. Some miners have developed pop-under capabilities to ensure that the mining continues in a hidden tab even after the user has 'left' the affected website.
As ad-blockers and security firms have got better at detecting and blocking CoinHive, criminals have gone to greater lengths to mask their activity. "The lowest number of drive-by cryptomining detections recorded in a single day," notes Malwarebytes, "was still over 1 million."
Cryptomining is now the second most detected malware for both businesses and consumers. Top for business is spyware, and top for consumers is adware. Ransomware is sixth for both business and consumer. Malwarebytes predicts that cryptomining will continue to grow -- not least, it suggests, because both spyware and adware have the ability to drive victims to cryptomining landing pages. Indeed, this has already happened with the Trickbot spyware. The future of ransomware is not clear. While it is unlikely to go away, "whether we will see a return to the levels of distribution we observed in previous years is anyone's guess."
Malwarebytes has timed the announcement of a new product with the publication of this report: Malwarebytes Endpoint Protection and Response. This is in keeping with the expansion of anti-malware capabilities into full endpoint protection and response (EDR) products (Barkly did similar last week). The intention is to provide greater visibility into the context of a malware incident in order to improve the security team's ability to respond to it.
"Many businesses don't have the resources to bring on dedicated, highly-specialized EDR technology and talent, leaving them with a tool that simply adds to a long queue of alerts, without fixing the underlying problems," explains Marcin Kleczynski, CEO at Malwarebytes. "Endpoint Protection and Response provides proven endpoint protection with integrated detection and response capabilities via a single agent, so organizations of all sizes can easily protect their endpoints from targeted attacks, thoroughly remediate systems and rollback ransomware."
Sodexo Filmology data breach – Users need cancel their credit cards
9.4.2018 securityaffairs Incindent
Sodexo food services and facilities management company notified a number of customers that it was the victim of a targeted attack on its cinema vouchers platform Sodexo Filmology.
Sodexo food services and facilities management company notified a number of customers that it was the victim of a targeted attack on its cinema vouchers platform, Filmology and it is urging them to cancel their credit cards.
The service rewards UK employee via discounted cinema tickets, the website was taken down in response to the incident “to eliminate any further potential risk” to consumers and to protect their data.

Sodexo Filmology reported the incident to the Information Commissioner’s Office and hired a specialist forensic investigation team.
“We would advise all employees who have used the site between 19th March-3rd April to cancel their payment cards and check their payment card statements,” reads the data breach notification issued by Sodexo Filmology.
“These incidents have been caused by a targeted attack on the system we use to host our Cinema Benefits platform, despite having put in place a number of preventative measures with CREST-approved security specialists.”
“We sincerely apologise for any inconvenience this has caused you and are doing all that we can to provide access to your benefits via alternative means. We will share more information on this with you, or your provider, in the coming days.”
Making a rapid search online, we can verify that the attack has been going on for several months, several employees reported fraudulent activities on the Money Saving Expert forum in February.
“After speaking to Filmology to ask exactly what had happened, I was informed that my bank details were stolen from the payment page and that the incident has been reported to the ICO. The hack on the payment page was carried out over 2 months and involved many accounts.” wrote the user Chris.
Crooks distribute malware masquerade as fake software updates and use NetSupport RAT
9.4.2018 securityaffairs Virus
Researchers at FireEye have spotted a hacking campaign leveraging compromised websites to spread fake updates for popular software that were also used to deliver the NetSupport Manager RAT.
NetSupport is an off-the-shelf RAT that could be used by system admins for remote administration of computers. In the past, crooks abuse this legitimate application to deploy malware on victim’s machines.
Researchers at FireEye have spotted a hacking campaign that has been active for the past few months and that has been leveraging compromised websites to spread fake updates for popular software (i.e. Adobe Flash, Chrome, and FireFox) that were also used to deliver the NetSupport Manager remote access tool (RAT).
Once the victims have executed the updates, a malicious JavaScript file is downloaded, in most cases from a Dropbox link.
“Over the last few months, FireEye has tracked an in-the-wild campaign that leverages compromised sites to spread fake updates. In some cases, the payload was the NetSupport Manager remote access tool (RAT).” reads the analysis published by FireEye.
“The operator behind these campaigns uses compromised sites to spread fake updates masquerading as Adobe Flash, Chrome, and FireFox updates.”
The JavaScript file gathers info on the target machine and sends it to the server that in turn sends additional commands, then it executes a JavaScript to deliver the final payload. The JavaScript that delivers the final payload is dubbed Update.js, it is executed from %AppData% with the help of wscript.exe.

According to FireEye, vxers used multiple layers of obfuscation to the initial JavaScript, while the second layer of the JavaScript contains the dec function that allows to decrypt and execute more JavaScript code.
“since the malware uses the caller and callee function code to derive the key, if the analyst adds or removes anything from the first or second layer script, the script will not be able to retrieve the key and will terminate with an exception.” continue the analysis.
Once executed, the JavaScript contacts the command and control (C&C) server and sends a value named ‘tid’ and the current date of the system in an encoded format, the server, in turn, provides a response that the script then decodes and executes it as a function named step2.
The step2 function collects and encodes various system information, then sends it to the server: architecture, computer name, user name, processors, OS, domain, manufacturer, model, BIOS version, anti-spyware product, anti-virus product, MAC address, keyboard, pointing device, display controller configuration, and process list.
The server then responds with a function named step3 and Update.js, which it the script to downloads and executes the final payload.
The Javascript uses PowerShell commands to download multiple files from the server, including:
7za.exe: 7zip standalone executable
LogList.rtf: Password-protected archive file
Upd.cmd: Batch script to install the NetSupport Client
Downloads.txt: List of IPs (possibly the infected systems)
Get.php: Downloads LogList.rtf
The script performs the following tasks:
Extract the archive using the 7zip executable with the password mentioned in the script.
After extraction, delete the downloaded archive file (loglist.rtf).
Disable Windows Error Reporting and App Compatibility.
Add the remote control client executable to the firewall’s allowed program list.
Run remote control tool (client32.exe).
Add Run registry entry with the name “ManifestStore” or downloads shortcut file to Startup folder.
Hide the files using attributes.
Delete all the artifacts (7zip executable, script, archive file).
Attackers use the NetSupport Manager to gain remote access to the compromised systems and control it.
The final JavaScript also downloaded a list of IP addresses that could be compromised systems, most of them in the U.S., Germany, and the Netherlands.
Further details, including the IOCs are reported in the analysis.
Verge Cryptocurrency suffered a cyber attack, dev team responded with an Hard Fork
9.4.2018 securityaffairs Cryptocurrency
The verge (XVG) currency schema was attacked last week, the hacker reportedly making off with $1 million-worth of tokens. The dev team responded with an Hard Fork.
Ripple (XRP) and Verge (XVG) are two cryptocurrencies that attracted many investors in the last months.
Last week attackers hackers the Verge cryptocurrency system by exploiting a vulnerability in its software and forced its developers to hard-fork the currency.
The bug in the cryptocurrency scheme allowed the attacker to mine blocks with bogus timestamps, it seems that attackers were able to generate new blocks at a rate of roughly one per second.
The hacker reportedly making off with $1 million-worth of tokens, the news was later confirmed on Bitcoin Talk forum by the user with the handle “ocminer” of the Suprnova Mining Pools.
“There’s currently a >51% attack going on on XVG which exploits a bug in retargeting in the XVG code. Usually to successfully mine XVG blocks, every “next” block must be of a different algo.. so for example scrypt, then x17, then lyra etc.” wrote ocminer.
“Due to several bugs in the XVG code, you can exploit this feature by mining blocks with a spoofed timestamp. When you submit a mined block (as a malicious miner or pool) you simply set a false timestamp to this block one hour ago and XVG will then “think” the last block mined on that algo was one hour ago. Your next block, the subsequent block will then have the correct time..
And since it’s already an hour ago (at least that is what the network thinks) it will allow this block to be added to the main chain as well.”
OCminer speculated it was a 51 per attack(aka majority attack), this means that hackers in somehow were able to control the majority of the network mining power (hashrate).
The Verge development team finally confirmed on Wednesday the attack that caused the XVG value to drop from $0.07 to $0.05.
vergecurrency
@vergecurrency
We had a small hash attack that lasted about 3 hours earlier this morning, it's been cleared up now. We will be implementing even more redundancy checks for things of this nature in the future! $XVG #vergefam
7:06 PM - Apr 4, 2018
1,366
691 people are talking about this
Twitter Ads info and privacy
In response to the incident, the Verge team hard forked XVG that resulted in the creation of a new blockchain.
“The XVG team erroneously forked their entire network to ‘undo’ the exploited blocks, but this resulted in the entire network being unable to sync,” noted cryptocurrency news site The Merkle.
“When the team was made aware of their mistake, they were able to re-sync the network, but still have not completely defeated the issue.”
At the time of writing the Verge currency has recovered all its value.

Cisco Switches in Iran, Russia Hacked in Apparent Pro-US Attack
9.4.2018 securityweek Attack Vulnerebility
A significant number of Cisco switches located in Iran and Russia have been hijacked in what appears to be a hacktivist campaign conducted in protest of election-related hacking. However, it’s uncertain if the attacks involve a recently disclosed vulnerability or simply abuse a method that has been known for more than a year.
Cisco devices belonging to organizations in Russia and Iran have been hijacked via their Smart Install feature. The compromised switches had their IOS image rewritten and their configuration changed to display a U.S. flag using ASCII art and the message “Don’t mess with our elections…”
The hackers, calling themselves “JHT,” told Motherboard that they wanted to send a message to government-backed hackers targeting “the United States and other countries.” They claim to have only caused damage to devices in Iran and Russia, while allegedly patching most devices found in countries such as the U.S. and U.K.
Iran’s Communication and Information Technology Ministry stated that the attack had impacted roughly 3,500 switches in the country, but said a vast majority were quickly restored.
Kaspersky Lab reported that the attack appeared to mostly target the “Russian-speaking segment of the Internet.”
While there are some reports that the attack involves a recently patched remote code execution vulnerability in Cisco’s IOS operating system (CVE-2018-0171), that might not necessarily be the case.
The Cisco Smart Install Client is a legacy utility that allows no-touch installation of new Cisco switches. Roughly one year ago, the company warned customers about misuse of the Smart Install protocol following a spike in Internet scans attempting to detect unprotected devices that had this feature enabled.
Attacks, including ones launched by nation-state threat actors such as the Russia-linked Dragonfly, abused the fact that many organizations had failed to securely configure their switches, rather than an actual vulnerability.
Cisco issued a new warning last week as the disclosure of CVE-2018-0171 increases the risk of attacks, but the networking giant said it had not actually seen any attempts to exploit this vulnerability in the wild. Cisco’s advisory for this flaw still says there is no evidence of malicious exploitation.
There are hundreds of thousands of Cisco switches that can be hijacked by abusing the Smart Install protocol, and Cisco Talos experts believe attackers are unlikely to bother using CVE-2018-0171.
The Network Security Research Lab at Chinese security firm Qihoo 360 says the data from its honeypot shows that the attacks have “nothing to do with CVE-2018-0171” and instead rely on a publicly available Smart Install exploitation tool released several months ago.
While none of the major players in the infosec industry have confirmed that the attacks on Iran and Russia rely on CVE-2018-0171, technical details and proof-of-concept (PoC) code have been made available by researchers, making it easier for hackers to exploit.
Hamed Khoramyar, founder of Sweden-based ICT firm Aivivid, said the attacks exploited CVE-2018-0171. Kudelski Security also reported seeing attacks involving both CVE-2018-0171 and another recently disclosed IOS vulnerability tracked as CVE-2018-0156. However, Kudelski’s blog post also lists Khoramyar as one of its sources.
NetSupport Manager RAT Spread via Fake Updates
9.4.2018 securityweek Virus
A campaign that has been active for the past few months has been leveraging compromised websites to spread fake software updates that in some cases delivered the NetSupport Manager remote access tool (RAT), FireEye reports.
A commercially available RAT, NetSupport Manager is employed by administrators for remote access to client computers. However, the legitimate application can also be abused by malicious actors who install it on victim computers without the owners’ knowledge, to gain unauthorized access to their machines.
For distribution, the actors abuse compromised websites and masquerade the RAT as fake updates for popular applications, including Adobe Flash, Chrome, and FireFox. Should the user accept the update, a malicious JavaScript file is downloaded, mostly from a Dropbox link.
The file collects basic system information and sends it to the server, receives additional commands from the server, and then executes a JavaScript to deliver the final payload. Named Update.js, the JavaScript that delivers the payload is executed from %AppData% with the help of wscript.exe, FireEye says.
The malware authors applied multiple layers of obfuscation to the initial JavaScript and attempted to make analysis harder for the second JavaScript file. By using the caller and callee function code to get the key for decryption, the attackers ensured that, once an analyst adds or removes anything from it, the script won’t retrieve the key and will terminate with an exception.
After initial execution, the JavaScript initiates the connection to the command and control (C&C) server and sends a value named tid and the current date of the system in encoded format. The script then decodes the server response and executes it as a function named step2.
This function collects various system information, encodes it and sends it to the server: architecture, computer name, user name, processors, OS, domain, manufacturer, model, BIOS version, anti-spyware product, anti-virus product, MAC address, keyboard, pointing device, display controller configuration, and process list.
The server then responds with encoded content: a function named step3 and Update.js, which downloads and executes the final payload.
The code leverages PowerShell commands to download multiple files from the server, including a 7zip standalone executable, a password-protected archive file containing the RAT, and a batch script to install the NetSupport client on the system.
The batch script was also designed to disable Windows Error Reporting and App Compatibility, add the remote control client executable to the firewall’s allowed program list, add a Run registry entry or download a shortcut file to Startup folder for persistence, hide files, delete artefacts, and execute the RAT. During analysis, the researchers noticed that the script was regularly updated by the malware.
With the help of NetSupport Manager, attackers could gain remote access to the compromised systems, transfer files, launch applications, get the system’s location, and remotely retrieve inventory and system information.
The final JavaScript also downloaded a txt file containing a list of IP addresses that the researchers say could be compromised systems. These IPs belong mostly to the U.S., Germany, and the Netherlands, but to other regions as well.
ATMJackpot, a new strain of ATM Malware discovered by experts
9.4.2018 securityaffairs Virus
A new strain of ATM jackpotting malware dubbed ATMJackpot has been discovered by experts at Netskope Threat Research Labs.
The malware is still under development and appears to have originated in Hong Kong, it has a smaller system footprint compared with similar threats.
“Netskope Threat Research Labs has discovered a new ATM malware, “ATMJackpot.” The malware seems to have originated from Hong Kong and has a time stamp on the binary as 28th March 2018.” reads the analysis published by the experts at Netskope.
“It is likely that this malware is still under development. Compared with previously-discovered malware, this malware has a smaller system footprint,”
The malware has a smaller system footprint, it has a simple graphical user interface that displays a limited number of information, including the hostname, the service provider information such as cash dispenser, PIN pad, and card reader information.

At the time, it is not clear that attack vector for the ATMJackpot malware, usually this kind of malware are manually installed via USB on ATMs, or downloaded from a compromised network.
“ATM Malware propagates via physical access to the ATM using USB, and also via the network by downloading the malware on to already-compromised ATM machines using sophisticated techniques.” continues the analysis.
ATMJackpot malware first registers the windows class name ‘Win’ with a procedure for the malware activity, then the malicious code creates the window, populates the options on the window, and initiates the connection with the XFS manager.
The XFS manager implements API to access that allow controlling the ATM devices from different vendors. The malware opens a session with the service providers and registers to monitor events, then it opens a session with the cash dispenser, the card reader, and the PIN pad service providers.
Once the session with service providers are opened, the malware is able to monitor events and issue commands.
Experts believe authors of the malware will continue to improve it and they expect it will be soon detected in attacks in the wild.
The number of ATM jackpot attacks is increasing in recent years, in January US Secret Service warned of cybercriminals are targeting ATM machines in the US forcing them to spit out hundreds of dollars with ‘jackpotting‘ attacks.
In May 2017, Europol arrested 27 for jackpotting attacks on ATM across Europe, in September 2017 Europol warned that ATM attacks were increasing.
Criminal organizations are targeting ATM machines through the banks’ networks, the operations involve squads of money mules for the cashout.
“The malware being used has evolved significantly and the scope and scale of the attacks have grown proportionately,” said Steven Wilson, head of Europol’s EC3 cyber crime centre.
A few weeks ago, the alleged head of the Carbanak group was arrested in Spain by the police, the gang is suspected of stealing about £870m (€1bn) in a bank cyberheist.
Further information on ATM Malware and jackpotting are available here.
Auth0 authentication bypass issue exposed enterprises to hack
9.4.2018 securityaffairs Vulnerebility
Auth0, one of the biggest identity-as-a-service platform is affected by a critical authentication bypass vulnerability that exposed enterprises to hack.
Auth0, one of the biggest identity-as-a-service platform is affected by a critical authentication bypass vulnerability that could be exploited by attackers to access any portal or application which are using it for authentication.
Auth0 implements a token-based authentication model for a large number of platforms, it managed 42 million logins every day and billions of login per month for over 2000 enterprise customers.

In September 2017, researchers from security firm Cinta Infinita discovered a flaw in Auth0’s Legacy Lock API while they were pentesting an unnamed application that used service for the authentication.
The vulnerability tracked as CVE-2018-6873 it related to improper validation of the JSON Web Tokens (JWT) audience parameter.
The experts exploited this issue to bypass login authentication using a cross-site request forgery (CSRF/XSRF) attack triggering the CVE-2018-6874 flaw against applications implementing Auth0 authentication.
The experts exploited the CSRF vulnerability to reuse a valid signed JWT generated for a separate account to access the targeted victim’s account.
The unique information needed by attackers is the victim’s user ID or email address, that could be easily obtained with social engineering attacks.
“So, now we had the ability to forge a valid signed JWT with the “email” and “user_id” of the victim.” reads the analysis of the experts.
“It worked!! Why? The audience claim was not being checked and JWTs generated from our test application were accepted by the Management Console app (same signing key / private certificate).”
Below a video PoC of the attack to demonstrate how to obtain the victim’s user id and bypass password authentication when logging into Auth0’s Management Dashboard by forging an authentication token.
The researchers explained that it is possible to use this attack against many organizations.
“Could we use this attack to access arbitrary applications? Yes, as long as we know the expected fields and values for the JWT. There is no need of social engineering in most of the cases we saw. Authentication for applications that use an email address or an incremental integer for user identification would be trivially bypassed.” continues the analysis.
Security firm Cinta Infinita reported the vulnerability to the company in October 2017 and Auth0 solved the issue in a few hours but it spent several months to reach each customers using the vulnerable SDK and supported libraries of Auth0.
“We waited for six months before publicly disclosing this issue so that Auth0could update all their Private SaaS Appliances (on-premise) as well.” continues the analysis.
“Auth0 published a blog post about their internal vulnerability management and remediation process where they mention our finding and the assistance we provided: https://auth0.com/blog/managing-and-mitigating-security-vulnerabilities-at-auth0/“
Experts spotted a campaign spreading a new Agent Tesla Spyware variant
9.4.2018 securityaffairs Virus
A new variant of the infamous Agent Tesla spyware was spotted by experts at Fortinet, the malware has been spreading via weaponize Microsoft Word documents.
Agent Tesla is a spyware that is used to spy on the victims by collecting keystrokes, system clipboard, screenshots, and credentials from the infected system. To do this, the spyware creates different threads and timer functions in the main function.
The experts first discovered the malware in June, when they observed threat actors spreading it via a Microsoft Word document containing an auto-executable malicious VBA Macro.
Once the users have enables the macro, the spyware will be installed on the victim’s machine
The mail used in the last campaign contains text that appears not clear and it asks users to double click to enable the clear view.

“As you can see, it asks the victim to double click the blue icon to enable a “clear view.” Once clicked, it extracts an exe file from the embedded object into the system’s temporary folder and runs it. In this case, the exe file is called “POM.exe”.” continues the blog post.
When the users click on the blue icon, a POM.exe file written in Visual Basic being extracted from the embedded object, then it is saved to the system’s temporary folder and executed.
According to Fortinet, the POM.exe is a sort of installer for the final malware.
“Based on my analysis, it’s a kind of installer program. When it runs, it drops two files: “filename.exe” and “filename.vbs” into the “%temp%\subfolder”. It then exits the process after executing the file “filename.vbs”. Below, in figure 4, is the content of “filename.vbs”.” continues the analysis.
The variant used in the last campaign is similar to the older one except for the usage of the SMTPS to send the collected data to the attacker’s email box, instead of HTTP POST requests.
“However, the way of submitting data to the C&C server has changed. It used to use HTTP POST to send the collected data. In this variant, it uses SMTPS to send the collected data to the attacker’s email box.” continues the analysis.
“Based on my analysis, the commands used in the SMTP method include “Passwords Recovered”, “Screen Capture”, and “Keystrokes”, etc. The commands are identified within the email’s “Subject” field. For example:
“System user name/computer name Screen Capture From: victim’s IP”
The attackers used a free Zoho email account for this campaign.