
Probably you ignore that Facebook also tracks non-users across the web
18.4.2018 securityaffairs Social
Facebook explained how it is tracking Non-Users across the Internet and for which purposes it is using their metadata.
Facebook is still in the middle of a storm for its conduct and the way it approached the privacy of its users after the Cambridge Analytica case.
Now Facebook is under scrutiny after Zuckerberg testified in front of the US Congress, the social network giant disclosed more information on data collection activity that aimed to gather info related to non-Facebook users.
Yes, it is true! Facebook can track you even if you are not using it, this is possible if you visit a website or an application that uses the services of the tech giant.
The services include Social plugins (i.e. Like and Share buttons), Facebook Login, Facebook Analytics, and ads and measurement tools.
“When you visit a site or app that uses our services, we receive information even if you’re logged out or don’t have a Facebook account. This is because other apps and sites don’t know who is using Facebook.” explained product management director David Baser.
“Many companies offer these types of services and, like Facebook, they also get information from the apps and sites that use them. Twitter, Pinterest and LinkedIn all have similar Like and Share buttons to help people share things on their services. Google has a popular analytics service. And Amazon, Google and Twitter all offer login features.”
As you can imagine, all these companies also offer targeted advertising services by leveraging the information gathered through their services.
Everytime a user visits a website, his browser shares the IP address to the website along with info about the machine (i.e. browser, operating system) and cookies. Facebook also collects data related to website or app accessed by the user.
According to Baser, the social network platform uses the information received from websites and apps, to implements its services, to target the advertising and to improve the safety and security on Facebook.
Data collected by the company also allows it to measure the success of its advertising campaigns.
Facebook also uses this information to prevent abuses and identify threat actors targeting its users.
“We also use the information we receive from websites and apps to help protect the security of Facebook. For example, receiving data about the sites a particular browser has visited can help us identify bad actors.” added Baser.
“If someone tries to log into your account using an IP address from a different country, we might ask some questions to verify it’s you. Or if a browser has visited hundreds of sites in the last five minutes, that’s a sign the device might be a bot.”
Websites and apps who use the services of the social network have to inform users that they are collecting and sharing said information with the social network. They need an explicit consent and are requested to explain the purpose data are collected.
Drupal Sites Targeted With Backdoors, Miners in Drupalgeddon2 Attacks
18.4.2018 securityweek Attack
The recently patched Drupal vulnerability tracked as CVE-2018-7600 and dubbed Drupalgeddon2 has been exploited in the wild to deliver backdoors, cryptocurrency miners and other types of malware.
While much of the online activity targeting CVE-2018-7600 still appears to represent scanning (i.e. attempts to find vulnerable systems), attackers have also started exploiting the flaw to install malware.
The SANS Internet Storm Center has spotted attempts to deliver a cryptocurrency miner, a simple PHP backdoor that allows attackers to upload more files to the targeted server, and an IRC bot written in Perl.
One of the attacks observed by SANS delivers the XMRig Monero miner. In the same attack, the hackers have also downloaded a script that kills competing miners on the compromised system.
Drupalgeddon2
Data from Imperva shows that 90% of activity is associated with scanning, 3% with backdoors, and 2% with miners. A vast majority of the attacks seen by the company originated from the United States (53%) and China (45%).
Researchers at Volexity have also been monitoring Drupalgeddon2 attacks and they have linked one of the Monero miner campaigns to a cybercrime group that last year exploited a vulnerability in Oracle WebLogic Server (CVE-2017-10271) to infect systems with cryptocurrency malware. Volexity identified some of the wallets that had stored the group’s cryptocurrency and found more than $100,000 in Monero.
The Drupalgeddon 2 vulnerability can be exploited for remote code execution and it allows malicious actors to take complete control of websites. The flaw affects Drupal 6, 7 and 8, and it was patched with updates released in late March.
Experts expected to see exploits almost immediately, but the first attacks were spotted only two weeks later, after a technical analysis and a proof-of-concept (PoC) exploit were made public.
“It appeared every one of the black hats was waiting for someone else to do the research and share the exploit. Perhaps most hackers don’t care for the actual work of finding ways to exploit a vulnerability. They just wait until something is public and then use it to attack. Before that, we saw almost no traffic whatsoever!” Imperva said.
Now, based on the volume of attempts to exploit CVE-2018-7600, researchers at both Sucuri and SANS warn that users should assume their Drupal websites have been compromised if the patches have not been installed.
CrowdStrike Unveils New Endpoint Protection, Threat Analysis Solutions
18.4.2018 securityweek Safety
CrowdStrike this week unveiled its new Falcon Endpoint Protection Complete solution and announced the addition of an automated threat analysis module to its Falcon platform.
Falcon Endpoint Protection Complete is a turnkey solution that combines Falcon Endpoint Protection technology with the experience and skills of the Falcon Endpoint Protection team.
CrowdStrike says the new solution, which can be used by organizations of all sizes, unifies people, technology and processes to address every aspect of endpoint security, from deployment, configuration and maintenance to monitoring, alert handling and remediation.CrowdStrike unveils new solutions
The new threat analysis subscription module added by CrowdStrike to its Falcon platform is called Falcon X and it’s designed to help analysts conduct comprehensive investigations in just seconds instead of hours or days, the endpoint security firm says.
Falcon X combines malware search, malware sandboxing and intelligence to provide indicators of compromise (IOCs) for the threat being analyzed and all its known variants. The results are shared with other security products via an API, including firewalls, gateways and orchestration tools.
Threat intelligence data associated with the analyzed attack is displayed alongside alerts to help analysts understand the risks and quickly take action.
CrowdStrike also announced that its Falcon Insight endpoint detection and response (EDR) solution now includes two new features designed to provide incident responders immediate access to all systems across the distributed enterprise.
The company says the new features, Real Time Response and Real Time Query, leverage the existing Falcon sensors, cloud and console without any impact on performance or infrastructure.
“The Real Time Response feature adds powerful interactive capabilities, delivering instant visibility into the local file system, registry, network, and more. It also allows responders to close the door on threats by killing malicious processes and removing remaining traces left behind by the attacker,” CrowdStrike explained. “Real Time Query delivers the ultimate visibility and control to responders, empowering them through custom-tailored information collection and response actions.”
Facebook Admits to Tracking Non-Users Across the Internet
18.4.2018 securityweek Social
Facebook this week confirmed that it indeed knows when users access websites and apps that use Facebook services, even if they don’t have an account on the social network.
The social media platform has been under heavy scrutiny over user privacy for the past month, after it became public knowledge that at least one firm gathered information on millions of Facebook users without their knowledge or consent.
Over the past weeks, Facebook took various steps towards improving users’ privacy, by limiting apps’ access to user data, introducing bug bounties for data abuse, and updating its terms on privacy and data sharing.
After Facebook CEO Mark Zuckerberg testified in front of the United States Congress last week, the company on Monday shared more information on data collection practices that impact non-Facebook users.
Indeed, the social platform can track people who don't use it, as long as they access websites and applications that do use Facebook services. In other words, when anyone browses to a page that uses such a service, Facebook knows about it, product management director David Baser explains.
These Facebook services include social plugins such as the Like and Share buttons, Facebook Login (allows users to sign into websites and apps with their Facebook account), Facebook Analytics (offers usage data to websites and apps), and Facebook ads and measurement tools (websites and apps can show ads from Facebook advertisers and can run their own ads on Facebook or elsewhere).
“When you visit a site or app that uses our services, we receive information even if you’re logged out or don’t have a Facebook account. This is because other apps and sites don’t know who is using Facebook,” Baser says.
He also points out that other companies offer similar services too, including Twitter, Pinterest, LinkedIn, Google, and Amazon.
“In fact, most websites and apps send the same information to multiple companies each time you visit them,” he notes.
The data sent to Facebook is supposedly meant to make content and ads better. Some of the information a browser sends to the visited website includes user’s IP address, browser and operating system information, and cookies, and Facebook receives the same information. Additionally, the social platform knows which website or app the user accessed.
The information received from websites and apps, Facebook says, is used to provide services to those apps and sites, to improving the safety and security on Facebook, and to improve the social platform’s products and services.
According to Baser, Facebook uses data such as the IP address, browser/operating system, and visited website or app to make features such as the Like button or Facebook Login work. Other information allows the platform better understand how websites, apps, and services are used, and to determine what kind of ads to show to a person. Such data also tells advertisers how many people are responding to their ads.
The information, Baser adds, is also used for security purposes, to better protect users by identifying bad actors and determining whether an account has been compromised. This, of course, only applies to users who already have a Facebook account.
“If someone tries to log into your account using an IP address from a different country, we might ask some questions to verify it’s you. Or if a browser has visited hundreds of sites in the last five minutes, that’s a sign the device might be a bot. We’ll ask them to prove they’re a real person by completing additional security checks,” Baser notes.
Based on the received information, Facebook can also deliver better targeted ads, depending on the websites a user has visited.
Baser underlines that websites and apps who use Facebook services are required to inform users that they are collecting and sharing said information with the platform, and to request permissions to do so. He also notes that users have control over “how the data is used to provide more relevant content and ads,” and that users can completely opt out of being targeted with said ads.
Intel announced the new Threat Detection Technology and Security Essentials
18.4.2018 securityaffairs Safety
Intel announced a new Threat Detection Technology and a framework of critical root-of-trust hardware security capabilities in its chips.
Intel continues to innovate its products, the tech giant announced two new technologies, the Threat Detection Technology (TDT) and Security Essentials.
The Threat Detection Technology leverages the silicon-level telemetry and functionality to allow security products detect sophisticated threats.
The new Intel Threat Detection Technology (TDT) includes two main capabilities, the Accelerated Memory Scanning and Advanced Platform Telemetry.
The Accelerated Memory Scanning feature allows anti-malware solutions to use Intel’s integrated GPU to scan and detect fileless malware attacks without having any impact on performance and power consumption.
Microsoft will integrate the Accelerated Memory Scanning feature into Windows Defender Advanced Threat Protection (ATP) within a couple of weeks.
According to Intel researchers, using the GPU instead of the CPU to scan the memory will allow frequent scanning reducing the impact on performance, Intel tests revealed that the CPU usage dropped from 20 percent to as little as 2 percent.
“The first new capability is Accelerated Memory Scanning. Current scanning technologies can detect system memory-based cyberattacks, but at the cost of CPU performance.” reads the announcement published by Intel
“With Accelerated Memory Scanning, the scanning is handled by Intel’s integrated graphics processor, enabling more scanning, while reducing the impact on performance and power consumption. Early benchmarking on Intel test systems show CPU utilization dropped from 20 percent to as little as 2 percent”
The second Intel Threat Detection Technology is Intel Advanced Platform Telemetry that was designed to include cloud-based machine learning and endpoint data collection to improve threat detection.
“Intel Advanced Platform Telemetry combines platform telemetry with machine learning algorithms to improve the detection of advanced threats, while reducing false positives and minimizing performance impact.” continues Intel.
The New Intel Advanced Platform Telemetry technology will first be integrated into Cisco Tetration, a solution designed to provide data center security and cloud workload protection.
Intel has announced Security Essentials, a set of critical root-of-trust hardware security capabilities in Intel chips, including Core, Xeon and Atom processors.
“These capabilities are platform integrity technologies for secure boot, hardware protections (for data, keys and other digital assets), accelerated cryptography and trusted execution enclaves to protect applications at runtime.” continues Intel“This standard set of capabilities will accelerate trusted computing as customers build solutions rooted in hardware-based protections.”

UK NCSC, DHS and the FBI Warn of Russian hacking campaign on Western networks
18.4.2018 securityaffairs BigBrothers
UK NCSC, DHS, and the FBI warn of Russian hacking campaign on Western networks, state-sponsored hackers are targeting network infrastructure key components.
US and Britain government agencies warn of Russian state-sponsored cyber attacks to compromise government and business networking equipment. Russian hackers aim to control the data flaw “to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations,”
The operation was “to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations,” Washington and London said in a joint statement.
“Russian state-sponsored actors are using compromised routers to conduct spoofing ‘man-in-the-middle’ attacks to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations,” reads a joint statement issued by UK and US Goverments.
“Whoever controls the routing infrastructure of a network essentially controls the data flowing through the network.”
According to the US DHS, the campaign is part of well known Grizzly Steppe.
In December 2016, the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) published a Joint Analysis Report(JAR) that provided information about the tools, infrastructure and TTPs used by the Russian civilian and military intelligence Services (RIS) against United States election.
U.S. Government linked the cyber activity to a Russian threat actor designated as GRIZZLY STEPPE. It was the first time that the JAR attributed a malicious cyber activity to specific countries or threat actors.
The JAR reports the activity of two different RIS actors, the APT28 and the APT29, that participated in the cyber attacks on a US political party. The APT29 known as (Cozy Bear, Office Monkeys, CozyCar, The Dukes and CozyDuke) broke into the party’s systems in summer 2015. The APT28 known as (Fancy Bear, Pawn Storm, Sofacy Group, Sednit and STRONTIUM) entered in spring 2016.
Back to the present, the new alert was issued by Britain’s National Cyber Security Centre, DHS and the US Federal Bureau of Investigation.
Russian hacking espionage
The alert came from the UK National Cyber Security Centre, DHS and the US Federal Bureau of Investigation, the government agencies believe hackers could compromise Western critical infrastructures like power grids and water utilities.
Hackers specifically target routers, switches and firewalls with the intent to compromise the target networks to control traffic and manipulate it for espionage and to deliver malware.
“Targets are primarily government and private-sector organizations, critical infrastructure providers, and the Internet service providers (ISPs) supporting these sectors. This report contains technical details on the tactics, techniques, and procedures (TTPs) used by Russian state-sponsored cyber actors to compromise victims. Victims were identified through a coordinated series of actions between U.S. and international partners.” states the report.
“This report builds on previous DHS reporting and advisories from the United Kingdom, Australia, and the European Union. [1-5] This report contains indicators of compromise (IOCs) and contextual information regarding observed behaviors on the networks of compromised victims.
According to the report, Russian threat actors attempt to exploit flaws in legacy systems or weak protocols and service ports associated with network administration activities. Cyber actors use these weaknesses to
identify vulnerable devices;
extract device configurations;
map internal network architectures;
harvest login credentials;
masquerade as privileged users;
modify
device firmware,
operating systems,
configurations; and
copy or redirect victim traffic through Russian cyber-actor-controlled infrastructure.
The experts explained that threat actors behind the Russian hacking campaign do not need to leverage zero-day vulnerabilities or install malware to compromise networking devices. In most cases, Russian hackers exploited the following issues:
devices with legacy unencrypted protocols or unauthenticated services,
devices insufficiently hardened before installation, and
devices no longer supported with security patches by manufacturers or vendors (end-of-life devices).
“FBI has high confidence that Russian state-sponsored cyber actors are using compromised routers to conduct man-in-the-middle attacks to support espionage, extract intellectual property, maintain persistent access to victim networks, and potentially lay a foundation for future offensive operations.” states the alert.
The Government experts warn hackers are specifically targeting devices utilizing Generic Routing Encapsulation (GRE), Cisco Smart Install (SMI), and Simple Network Management Protocol (SNMP).
The main problem is that device administrators often fail to apply a robust configuration, in many cases, they leave default settings and fail to protect theri systems by for example by applying necessary patches.
In this scenario it is quite easy for threat actors to target networking infrastructure.
Trend Micro Analyzes Writing Style to Detect Email Fraud
17.4.2018 securityweek Safety
Trend Micro on Monday unveiled a new capability that allows its products to identify email fraud attempts by using a writing style analysis system powered by artificial intelligence (AI).
The new Writing Style DNA, which Trend Micro has integrated into multiple products, uses AI to create a blueprint of a user’s style of writing based on more than 7,000 characteristics.
The text of every incoming email is compared to the trained AI model. If it doesn’t match the known writing style, a warning is sent out to the intended recipient, the apparent sender – in business email compromise (BEC) attacks the fake email comes from a spoofed address or a hacked account – and the company’s IT department.
Writing Style DNA also allows executives to provide feedback on flagged emails to help improve detection rates and reduce false positives.
The new capability is expected to become generally available in June 2018 as part of Trend Micro’s Cloud App Security product for Microsoft Office 365 and the ScanMail Suite for Microsoft Exchange. It will also be included at no extra charge in other existing BEC protection systems. Beta versions are already available.
BEC scams involve fake emails typically referencing payments and transfers. They can be designed to impersonate a foreign supplier requesting a fund transfer to a new account, CEOs and other executives making transfer requests to employees in finance, or an employee/executive asking vendors to make payments to a specified bank account.
Last year, the FBI reported that BEC attacks caused losses of roughly $5.3 billion between 2013 and 2016 to more than 40,000 victims, and Trend Micro predicts that the total will increase to $9 billion this year.
Trend Micro also announced this week the general availability of Phish Insight, a free phishing simulation platform designed to help IT teams train employees to spot attacks.
“All it takes is one administrator, four steps and five minutes to run a real-world exercise designed to mimic what employees might see at their desks,” Trend Micro said. “With the detailed reporting results, displayed in a handy graphical interface, IT teams can then tailor their education programs to make lasting behavioral changes.”
Phish Insight has been available in Asia for a year and Trend Micro has now announced that the service can be used for free by organizations all around the world.
US, UK Detail Networking Protocols Abused by Russian Cyberspies
17.4.2018 securityweek BigBrothers
A joint technical alert issued on Monday by the United States and the United Kingdom details how cyberspies believed to be working for the Russian government have abused various networking protocols to breach organizations.
According to the Department of Homeland Security (DHS), the Federal Bureau of Investigation (FBI), and the United Kingdom’s National Cyber Security Centre (NCSC), the hackers targeted routers, switches, firewalls, and network-based intrusion detection systems (NIDS). Their main targets have been government and private-sector organizations, critical infrastructure operators, and their Internet service providers (ISPs).
“FBI has high confidence that Russian state-sponsored cyber actors are using compromised routers to conduct man-in-the-middle attacks to support espionage, extract intellectual property, maintain persistent access to victim networks, and potentially lay a foundation for future offensive operations,” the report reads.
The first technical report from the DHS and FBI accusing Russia of cyberattacks was the GRIZZLY STEPPE report published in December 2016. Another technical report blaming Russia for cyber operations was published in March, when the U.S. accused Moscow of campaigns targeting the energy and other critical infrastructure sectors. The alert on critical infrastructure attacks was first released in October 2017, but the attacks had not been openly attributed to Russia at the time.
The latest technical alert focuses on the tactics, techniques, and procedures (TTPs) used by Russian threat actors, specifically the networking protocols they have abused in their attacks. According to authorities, the attackers identify vulnerable devices, extract their configuration, map internal network architectures, harvest login credentials, and use them to gain access to the system as privileged users. The hackers then modify the targeted device’s firmware, operating system and configuration so that the victim’s traffic is redirected through their own infrastructure.
In the reconnaissance phase of their campaign, the attackers scan the Web for devices that have Internet-facing ports and services. The targeted protocols include Telnet, HTTP, the Simple Network Management Protocol (SNMP) and Cisco’s Smart Install (SMI).
Data collected during these initial scans can help the cyberspies obtain information about the devices and the organizations using them.
In the weaponization and delivery phases of the attack, hackers send specially crafted SNMP and SMI messages that cause the targeted device to send its configuration file to an attacker-controlled server via Trivial File Transfer Protocol (TFTP). The configuration file can contain password hashes and other information that can be useful to the threat actor.
Legitimate credentials can also be obtained through brute-force attacks and other methods, and they ultimately allow the hackers to access the device via Telnet, SSH, or its web management interface.
The Cisco Smart Install Client is a legacy utility that allows no-touch installation of new Cisco switches. Attackers can abuse the SMI protocol to modify the configuration file on switches running IOS and IOS XE software, force the device to reload, load a new OS image, and execute high-privilege commands.
Hackers have been abusing insecurely configured SMI installations since 2016 when an exploitation tool was made public. Researchers also discovered recently that Smart Install is affected by a critical vulnerability (CVE-2018-0171) that can be exploited for remote code execution, but there is no indication that this flaw has been used in attacks.
Cisco has warned organizations about the risks associated with Smart Install since 2016 and it recently issued a new warning following the discovery of CVE-2018-0171. The networking giant says the protocol has been abused in critical infrastructure attacks by the Russia-linked threat group known as Dragonfly (aka Crouching Yeti and Energetic Bear).
Once they access a device with compromised credentials or via a backdoor planted by uploading a malicious OS image, attackers can mirror or redirect the victim’s traffic through their own network, the agencies said in their report. One other protocol cyberspies have abused while in a man-in-the-middle (MitM) position is Generic Routing Encapsulation (GRE), a tunneling protocol developed by Cisco.
“Cyber actors are not restricted from modifying or denying traffic to and from the victim,” the technical alert reads. “Although there are no reports of this activity, it is technically possible.”
The report from the FBI, DHS and NCSC also includes recommendations on how organizations can defend themselves against these types of attacks.
IBM Releases Open Source AI Security Tool
17.4.2018 securityweek Security
IBM today announced the release of an open source software library designed to help developers and researchers protect artificial intelligence (AI) systems against adversarial attacks.
The software, named Adversarial Robustness Toolbox (ART), helps experts create and test novel defense techniques, and deploy them on real-world AI systems.
There have been significant developments in the field of artificial intelligence in the past years, up to the point where some of the world’s tech leaders issued a warning about how technological advances could lead to the creation of lethal autonomous weapons.
Some of the biggest advances in AI are a result of deep neural networks (DNN), sophisticated machine learning models inspired by the human brain and designed to recognize patterns in order to help classify and cluster data. DNN can be used for tasks such as identifying objects in an image, translations, converting speech to text, and even for finding vulnerabilities in software.
While DNN can be highly useful, one problem with the model is that it’s vulnerable to adversarial attacks. These types of attacks are launched by giving the system a specially crafted input that will cause it to make mistakes.
For example, an attacker can trick an image recognition software to misclassify an object in an image by adding subtle perturbations that are not picked up by the human eye but are clearly visible to the AI. Other examples include tricking facial recognition systems with specially designed glasses, and confusing autonomous vehicles by sticking patches onto traffic signs.
IBM’s Python-based Adversarial Robustness Toolbox aims to help protect AI systems against these types of threats, which can pose a serious problem to security-critical applications.
According to IBM, the platform-agnostic library provides state-of-the-art algorithms for creating adversarial examples and methods for defending DNN against them. The software is capable of measuring the robustness of the DNN, harden it by augmenting the training data with adversarial examples or by modifying its architecture to prevent malicious signals from propagating through its internal representation layers, and runtime detection for identifying potentially malicious input.
“With the Adversarial Robustness Toolbox, multiple attacks can be launched against an AI system, and security teams can select the most effective defenses as building blocks for maximum robustness. With each proposed change to the defense of the system, the ART will provide benchmarks for the increase or decrease in efficiency,” explained IBM’s Sridhar Muppidi.
IBM also announced this week that it has added intelligence capabilities to its incident response and threat management products.
Android Trojan Spreads via DNS Hijacking
17.4.2018 securityweek Android
An Android Trojan masquerading as popular mobile applications is propagating via smartphones roaming between Wi-Fi networks, Kaspersky Lab warns.
Over the span of two months, the Moscow-based security firm observed the malware mainly targeting users in Asia. As part of the attack, DNS settings of routers are hijacked to redirect users to malicious IP addresses, where they serve fake versions of popular applications.
Dubbed Roaming Mantis, the Trojan appears to be the work of a financially motivated actor familiar with both Simplified Chinese and Korean. The attackers were observed using Trojanized applications named facebook.apk and chrome.apk to trick users into installing the malware.
After being redirected to a malicious website, users are prompted, for example, to install an update for Chrome: “To better experience the browsing, update to the latest chrome version,” the popup message displayed by the rogue server reads, Kaspersky says.
During installation, Roaming Mantis requests permission to be notified when the device is booted, to use the Internet, collect account information, manage SMS/MMS and make calls, record audio, control external storage, check packages, work with file systems, draw overlay windows, and more.
After installation, the malware overlays a message over all other windows, after which it starts its own webserver on the device, and renders a page spoofing Google’s authentication on 127.0.0.1. Using the Google account name collected from the infected device, the threat asks the user to provide a name and date of birth, claiming that this would facilitate access to the account.
The Trojan also attempts to get a verification code for two-factor authentication, but a bug in the code resulted in the Korean text to be displayed for Japanese and English users as well. The malware developers could also attempt to steal verification codes using the receive/read/write/send SMS/MMS and record audio permissions.
The malware’s code also contains references to Android applications popular in South Korea, linked to mobile banking and games: wooribank.pib.smart, kbstar.kbbank, ibk.neobanking, sc.danb.scbankapp, shinhan.sbanking, hanabank.ebk.channel.android.hananbank, smart, epost.psf.sdsi, kftc.kjbsmb, smg.spbs, webzen.muorigin.google, ncsoft.lineagem19, ncsoft.lineagem, co.neople.neopleotp, co.happymoney.android.happymoney, nexon.axe, nexon.nxplay, atsolution.android.uotp2.
The malware also verifies the presence of the su binary (superuser), which is usually an indication that the device is rooted (the su binary is not present on regular Android devices). This could allow attackers to gain elevated privileges on the system.
The malware appears to be receiving code updates on a regular basis, and the security researchers note that it also includes a new feature to communicate with the C&C via email protocols. The Trojan sends data such as language, phone number, access information, and the result of a PING test to the C&C.
Between February 9 and April 9, 2018, Kaspersky observed more than 6,000 occurrences of the malware, but only around 150 unique users appeard to be impacted.
Most detections came from South Korea, Bangladesh, and Japan, which isn’t surprising, as the malware’s capabilities suggest it was designed to be spread mainly in Asian countries. The researchers noticed around 3,000 connections to the C&C infrastructure per day, which reveals a much larger infection campaign.
Based on the system locale information the malware sends to the C&C, the researchers discovered that 98% of affected devices appear to have the Korean locale set. The remaining devices use English (both U.K. and U.S.), Simplified Chinese, Japanese, and others.
Roaming Mantis can not only steal information from the infected devices, but also provide attackers with full control over them. Likely the work of cybercriminal hackers, the Trojan is being updated each day, showing that the malicious actor is highly active.
Roaming Mantis Malware Campaign Leverages Hacked Routers to Infect Android Users With Banking Trojan
17.4.2018 securityaffairs Android
According to experts at Kaspersky, the Roaming Mantis malware is designed for distribution through a simple, but very efficient trick based on DNS hijacking.
Imagine a nefarious person swapped out your phone book with one they created, where all of the important phone numbers have been changed to call the bad actors’ friends instead of the bank you were trying to call.
Then imagine whomever answered the phone was able to convince you they actually are the bank you thought you were calling. You answer your security questions over the phone and when you hang up, the bad actor then calls your bank and successfully masquerades as you since they now have answers to your security questions. It is a flawed analogy since none of us use phone books anymore. But if you replace “phone books” with “DNS”, it is not just an analogy — it is a real cyberattack targeting mobile phone users in Asia right now — and it appears to be after users’ banking details.
In March 2018, reports began to surface about hacked routers in Japan redirecting users to compromised websites. Investigation by Kaspersky Lab indicates that the ongoing attack is targeting users in Asia with fake websites customized for English, Korean, Simplified Chinese and Japanese. Infection statistics show that users in Bangladesh, Japan and South Korea are the most impacted.
“Our research revealed that the malware (sic) contains Android application IDs for popular mobile banking and game applications in South Korea. The malware is most prevalent in South Korea, and Korean is the first language targeted in HTML and test.dex. Based on our findings, it appears the malicious app was originally distributed to South Korean targets. Support was then added for Traditional Chinese, English, and Japanese, broadening its target base in the Asian region.”
The attack begins when a user attempts to access a legitimate website through a compromised router. Instead of reaching the intended website, the user is redirected to a convincing copy of the website and will be presented with a popup dialog box which says, “To better experience the browsing, update to the latest Chrome version.” When the user clicks on the OK button, a file called chrome.apk is downloaded, but instead of containing an updated Chrome browser, the file contains the Roaming Mantis malware. During installation of the malware, the user will be prompted to authorize a number of permissions including the ability to appear on top of other applications, access the contact list, collecting account information, sending/receiving SMS messages, making phone calls, recording audio.
Once these permissions have been confirmed by the user, the next stage of the compromise begins.
Using the ability to appear on top of other applications, the malware displays a warning message that says, “Account No. exists risks, use after certification.” When the user presses the Enter button, a fake version of a Google website hosted on a temporary web server on the phone is displayed. The fake pages show the user’s Gmail ID and ask for the user’s Name and Date of Birth. This will provide the bad actors with users’ Google IDs, full names and dates of birth which is enough to start compromising banking information.
Most banks require a second authentication factor (2FA) before allowing a user to make changes, but the malware is authorized to intercept SMS messages which should subvert many 2FA processes.

Bad actors implement upgrade processes for malware to ensure they can adapt and improve over time. Roaming Mantis makes use of popular Chinese social media site my.tv.sohu.com for its command & control (C2) needs. Simply making changes to a specific user profile on the social media network can trigger updates on all infected systems. It will be very difficult for technical systems to identify malicious account updates from benign ones.
What is a user to do? It starts with securing the router. Up-to-date firmware, strong passwords for admin access and disabling remote access to the administration interfaces on the router will make it difficult to compromise. This attack targets DNS services running on routers. A DNS service running on a server inside your network is not at risk to this attack (but is not impervious to all attacks.) Only install software from trusted app stores (e.g. Google Play.) Even when installing from a legitimate app store, pay attention to the permissions that are being requested. You are being prompted to approve the permissions so you can make an informed choice. And finally, bad actors are getting much better at language translations. When you see something in your language that doesn’t sound “right” be extra suspicious.
Intel Unveils New Threat Detection Technology
17.4.2018 securityweek Safety
Intel late on Monday announced two new security-related technologies, including a threat detection system and a framework for building protection into processors, and a strategic collaboration with Purdue University whose goal is to address the shortage of cybersecurity talent.
Following the discovery of the Meltdown and Spectre vulnerabilities, Intel has promised to take steps to avoid these types of situations through protections built into CPUs, a dedicated bug bounty program, and industry collaboration.
Intel recently detailed the protection mechanisms it plans on adding to its chips, and the company has now unveiled its Threat Detection Technology. This system uses silicon-level telemetry and functionality to help security products detect sophisticated cyber threats.Intel announces new silicon-level security technologies
One component of the Threat Detection Technology is called Accelerated Memory Scanning, which Microsoft will integrate into Windows Defender Advanced Threat Protection (ATP) later this month.
The Accelerated Memory Scanning capability will allow Windows Defender and other security products to more efficiently scan the system memory for threats by using Intel’s integrated graphics processor.
Using the GPU instead of the CPU will enable more frequent scanning, and will result in reduced impact on performance and power consumption, Intel said. Tests made by the company showed a drop in CPU usage from 20 percent to as little as 2 percent.
On the other hand, using the GPU to conduct scans can have a negative performance impact on processes that require the graphics processor, Intel admitted during a call with reporters. However, the company says it’s working on figuring out how to optimize performance based on the CPU and GPU workloads.
The second component of Intel Threat Detection Technology is called Advanced Platform Telemetry and it combines telemetry with machine learning algorithms to improve threat detection, reduce false positives, and minimize impact on performance.
The Advanced Platform Telemetry capability will first be integrated into Cisco Tetration, a product that provides holistic workload protection for multicloud data centers.
Intel has also unveiled Security Essentials, a framework that standardizes built-in security features in Intel chips, including Core, Xeon and Atom processors.
“These capabilities are platform integrity technologies for secure boot, hardware protections (for data, keys and other digital assets), accelerated cryptography and trusted execution enclaves to protect applications at runtime,” explained Rick Echevarria, vice president and general manager of Intel Platforms Security Division.
“This standard set of capabilities will accelerate trusted computing as customers build solutions rooted in hardware-based protections. Further, these capabilities, directly integrated into Intel silicon, are designed to improve the security posture of computing, lower the cost of deploying security solutions and minimize the impact of security on performance,” Echevarria added.
As for the strategic collaboration with Purdue University, Intel announced a Design for Security Badge Program whose goal is to accelerate the development and availability of cybersecurity professionals.
US, Britain Warn of Russian Campaign to Hack Networks
17.4.2018 securityweek BigBrothers
Russian government-sponsored hackers are compromising the key hardware of government and business computer networks like routers and firewalls, giving them virtual control of data flows, Britain and the United States warned Monday.
The operation was "to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations," Washington and London said in a joint statement.
"Russian state-sponsored actors are using compromised routers to conduct spoofing 'man-in-the-middle' attacks to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations," they said.
"Whoever controls the routing infrastructure of a network essentially controls the data flowing through the network."
The US Department of Homeland Security said the hacking was part of a broad operation dubbed Grizzly Steppe, which DHS says comprises concerting cyberattacks by Moscow's civilian and military intelligence agencies.
The router hacking operation has targeted both government and private sector groups, and the key providers of network infrastructure and internet services serving them.
The announcement came in an unprecedented joint alert that underscored closer cooperation between Western governments fighting what they say is an ongoing, multifaceted hacking and online disinformation campaign by Moscow.
The alert came from the Britain's National Cyber Security Centre, DHS and the US Federal Bureau of Investigation.
In came after more than one year of separate warnings over the attempted hacking of key infrastructure like power and water utilities in Western countries.
The two sides did not give any examples of systems that had been broken into, but said those compromised risked losing data, identities, passwords and even control of their own systems.
- Critical network components targeted -
The hacking effort goes to the critical components of a computer network: the routers, switches and firewalls designed to safely and accurate deliver data from one computer to another.
Taking over a router virtually would give a hacker the ability to manipulate, divert or stop any data from going through it.
In an operation like an electric power plant, the hacker could shut down the service or physically damage a plant.
A hacker could also "potentially lay a foundation for future offensive operations," the joint alert said.
"The current state of US and UK network devices, coupled with a Russian government campaign to exploit these devices, threatens our respective safety, security, and economic well-being," it said.
Both countries have accused Moscow of concerted efforts to use social media to interfere with public affairs, particularly with the British Brexit referendum and US presidential election in 2016.
UK GCHQ spy agency warns telcos of the risks of using ZTE equipment and services
17.4.2018 securityweek BigBrothers
The UK GCHQ intelligence agency warns UK telcos firms of the risks of using ZTE equipment and services for their infrastructure.
The alert was issued by the National Cyber Security Centre that said the Chinese firm “would present risk to UK national security that could not be mitigated effectively or practicably”.
Let’s remind that the ZTE is a state-owned enterprise and many experts highlighted the risks of using its products.
The Agency did not provide further details about the threat to UK telco infrastructure, it only explained that at the time it is not possible to mitigate the risks of adopting the Chinese equipment.
“NCSC assess[es] that the national security risks arising from the use of ZTE equipment or services within the context of the existing UK telecommunications infrastructure cannot be mitigated,” reads the statement issued by the GCHQ.
The problems for ZTE are not ended, the U.S. Department of Commerce’s Bureau of Industry and Security (BIS) announced that Chinese firm has been banned from purchasing goods from US companies. This root cause is that ZTE was discovered violating Iran and North Korean sanctions.
ZTE, such as Huawei, are considered as potential threats by the US Government too, but differently from ZTE has worked with UK intelligence to demonstrate that its products don’t represent a threat. Huawei created a Cyber Security Evaluation Centre, also known as “the Cell,” in Banbury to allow intelligence the review of its products and software.
“HCSEC fulfilled its obligations in respect of the provision of assurance that any risks to UK national security from Huawei’s involvement in the UK’s critical networks have been sufficiently mitigated,” reads the Huawei Cyber Security Evaluation Centre (HCSEC) Oversight Board: annual report 2017.

In March, UK suspended ZTE from the immigration scheme used by foreign companies to allow foreign nationals to work locally.
The news was reported in exclusive by El Reg that wrote: “The Home Office has suspended the Tier 2 visa sponsor license for the Chinese state-owned telecomms giant, the fourth largest supplier of telecommunications equipment in the world.”
“The Register understands that ZTE had not fulfilled its duties under the Tier 2 scheme, which includes a “robust compliance system”.”
While experts have never discovered a backdoor in Huawei devices, in 2012 researchers spotted a critical security hole in ZTE phones.
“ZTE Corp, the world’s No.4 handset vendor and one of two Chinese companies under U.S. scrutiny over security concerns, said one of its mobile phone models sold in the United States contains a vulnerability that researchers say could allow others to control the device.” reported the Reuters at the time.
Cisco Launches New Email Security Services
16.4.2018 securityweek Safety
Cisco today announced new security products and services aimed at protecting email users from malware and phishing and spoofing attacks.
With malicious emails and spam continuing to be popular tools for cybercriminals looking to distribute malware, organizations should focus on protecting their domains from becoming the delivery mechanism of malicious emails, as well as defending users from phishing and spoofing attacks, Cisco says.
Through an OEM agreement with Agari, Cisco is now better positioned to market and sell new services that enhance its Email Security and is offering new email security services to its customers, namely Cisco Domain Protection and Cisco Advanced Phishing Protection.
Domain Protection prevents phishing through automated use of email authentication, and can also protect from fraud and maintain email governance through the analysis, updating, and auctioning against the misuse of domains to send malicious email.
It employs the Domain-Based Message Authentication, Reporting, and Conformance (DMARC) email authentication standard and delivers real-time reporting about noncompliant emails sent from a domain.
Advanced Phishing Protection, on the other hand, leverages machine learning to block “advanced identity deception attacks for inbound email by assessing its threat posture.” The new service validates the reputation and authenticity of senders to help organizations discover emails carrying targeted phishing and business email compromise (BEC) attacks.
To prevent malware attacks before they can hurt individuals or organizations, Cisco has added new capabilities to its Advanced Malware Protection (AMP) for Endpoints. The cloud-managed endpoint security solution now includes the necessary mechanisms to prevent fileless attacks, ransomware execution, and crypto-mining malware from infecting a system, the company says.
AMP also offers threat investigation features, courtesy of Cisco Visibility, a new cloud application built into the endpoint console. The solution combines threat intelligence from Talos and third parties with internal data (security events and alerts) from an organization’s infrastructure.
Cisco also promises fast access to data from Talos, Cisco Umbrella Investigate, Threat Grid, AMP, and other sources, all in a single place.
Through an expanded relationship with ConnectWise, Cisco Security is available for managed service providers (MSP) to include in their portfolio, thus making the new capabilities available to customers of all sizes.
A new ConnectWise Advanced Security Dashboard cloud management platform is available as part of the expanded relationship, complementing ConnectWise Unite with Cisco, the existing portal for MSPs.
The new Dashboard, which launches on April 19, offers the ability to deliver managed security services with Cisco’s AMP for Endpoints, Umbrella, Stealthwatch Cloud, Adaptive Security Appliances, Next-Generation Firewall, and Meraki MX appliances.
IBM Adds Intelligence to Incident Response, Threat Management
16.4.2018 securityweek Safety
IBM has added intelligent orchestration capabilities to its Resilient incident response platform, and launched new threat and vulnerability management services as part of its X-Force offering.
The latest announcements are what IBM has described as efforts to combine human and machine intelligence for more efficiently managing cybersecurity incidents.
The company says it has spent nearly 200,000 hours on the research and development of its new Resilient Incident Response Platform with Intelligent Orchestration, which is a result of IBM’s acquisition of Resilient Systems back in 2016.
The new orchestration capabilities allow security analysts to manage and automate hundreds of repetitive, time-consuming, and complicated response actions that until now required significant manual intervention.
IBM says the new platform provides out-of-the-box integrations and a drag-and-drop business process management notation (BPMN) workflow engine that makes it easier for security teams to investigate incidents. Integrations cover products from several major firms, including Cisco, Carbon Black, McAfee, Splunk and Symantec.
“The Resilient IRP automatically initiates activities across these partner technologies spanning monitoring and escalation, identification and enrichment, communication and coordination, and containment, response, and recovery,” IBM said.
As for the new X-Force Threat Management Services, they rely on a patented artificial intelligence engine that, according to IBM, will change the way analysts and technologies interact.
The goal is to allow analysts to more easily and efficiently investigate potential threats. Threat Management Services is powered by the new IBM X-Force Protection Platform, which combines tools from IBM and its partners with machine learning and AI algorithms to guide analysts through the threat management process and automate simple functions that previously required human intervention.
The new platform uses AI to compare an incident with real-time and historical data in order to help triage events. This includes eliminating false positives and duplicates, setting up quarantines, and escalating an incident to a higher-level analyst.
The new threat management product can be combined with the Resilient platform for more complex incident response activities.
Android Vendors Regularly Omit Patches in Security Updates
16.4.2018 securityweek Android
There is a good chance that your Android phone doesn’t have all of the security patches that it should, as vendors regularly omit some vulnerability fixes, security researchers have discovered.
After looking at the firmware of devices from tens of device makers, Germany-based Security Research Labs researchers discovered that not all relevant patches are included in the monthly updates that Android phones receive.
After the Stagefright vulnerabilities were found to impact nearly one billion devices three years ago, Google started releasing monthly security updates for the Android platform, to improve its overall security stance. Many vendors followed suit, announcing plans to keep up with Google and regularly deliver patches to their users.
However, only 17% of Android devices were found to run the most recent patch level in June 2016, and fixes were arriving slow in October that year. While many vendors have improved their patching frequency and phones started receiving monthly security updates, not all issues are addressed accordingly, the security researchers have discovered.
“Installing patches every month is an important first step, but is still insufficient unless all relevant patches are included in those updates. Our large study of Android phones finds that most Android vendors regularly forget to include some patches, leaving parts of the ecosystem exposed to the underlying risks,” Security Research Labs says.
The security researchers analyzed the firmware of devices from over twenty vendors, looking for Critical and High severity patches they might be missing. They analyzed some phones multiple times, with different firmware releases and only considered phones patched from October 2017 or later.
The analysis revealed that most vendors forgot to deliver at least one patch to their users, while a handful of them didn’t deliver 4 or more patches. Given that not all patches were included in the tests, the actual number of missing patches could be much higher, the researchers say.
Missing patches don’t necessary imply that the phones are vulnerable, considering the security improvements in modern operating systems, such as ASLR and sandboxing, which typically prevent hacking, the security researchers argue.
This means that a few missing patches don’t usually render a device prone to remote compromise. A hacker would need to chain together multiple bugs for a successful attack, the researchers note, adding that cybercriminals do understand these challenges.
“Instead criminals focus on social engineering users into installing malicious apps, often from insecure sources, and then granting excessive permissions to these apps. In fact, hardly any criminal hacking activity has been observed around Android over the past year,” Security Research Labs says.
Those willing to invest into hacking Android devices are state-sponsored and other persistent threats. Operating stealthily and well-funded, these hackers normally leverage zero-day vulnerabilities in attacks, though they may also use known bugs to build exploit chains.
With monthly security updates arriving on many Android devices, it is important that these updates include all relevant patches. Users should start verifying their vendor’s claims about the security of their devices, and can measure their patch levels using free apps.
“As Android is ever increasing in popularity, the hacking incentives will only keep growing, as does the ecosystem’s responsibility for keeping its users secure. No single defense layer can withstand large hacking incentives for very long, prompting “defense in depth” approaches with multiple security layers. Patching is critically important to uphold the effectiveness of the different security layers already found in Android,” Security Research Labs concludes.
Symantec Releases Targeted Attack Analytics Tool
16.4.2018 securityweek Security
Symantec is releasing its own targeted attack analytics (TAA) tool to existing Symantec Advanced Threat Protection (ATP) customers free of additional charge. It is the same tool that Symantec's researchers use, and was used to uncover Dragonfly 2.0. Its primary purpose is to uncover stealthy and targeted attacks.
Symantec's data scientists developed TAA by applying artificial intelligence machine learning to the process, knowledge and capabilities of the firm's own security experts and researchers. These researchers have a long and successful history of detecting and analyzing global cyber threats. The reasoning behind TAA was to automate the task of analyzing the vast pool of telemetry gathered from the Symantec global customer base with the expertise of its human researchers; that is, to automate those tasks previously performed by human analysts -- finding more things, faster, with the help of advanced analytics.
Now made available to customers, TAA analyzes incidents within the network against incidents discovered within one of the largest threat data lakes in the world. Since its inception, TAA has been used by Symantec to detect security incidents at more than 1,400 organizations, and to help track around 140 organized hacking groups.
It functions by uncovering suspicious activity in individual endpoints and collating that information to determine whether individual actions indicate stealthy malicious activity. "Security has changed a lot over the last couple of decades," commented Eric Chien, distinguished engineer at Symantec, in a blog post. "It used to be a question of defending a single machine and making sure that it was protected. That's no longer the case."
This is particularly relevant to today's stealthy, targeted attacks. With criminals increasingly making use of built-in OS tools in fileless attacks, individual actions on one endpoint need to be analyzed in the context of actions on other systems. Kevin Haley, director of Symantec's Security Technology and Response Group comments, "You have to bring your security data together because if something is happening in one place and something else is happening in another, by themselves that may not have meaning."
"Symantec's team of cyber analysts has a long history of uncovering the world's most high-profile cyber-attacks and now their deep understanding of how these attacks unfold can be put to use by our customers without the need to employ a team of researchers," said Greg Clark, Symantec CEO. "Targeted Attack Analytics uses advanced analytics and machine learning to help shorten the time to discovery on the most targeted and dangerous attacks and to help keep customers and their data safe."
TAA continuously learns from and adapts to the evolving attack methods used by increasingly sophisticated criminals and nation-state actors, and the cloud-based approach enables the frequent re-training and updating of analytics to adapt to the new attack methods without the need for product updates.
"Up until now, we've had the telemetry and data necessary to uncover the warning signs of dangerous targeted attacks, but the industry has lacked the technology to analyze and code the data quickly," said Chien. "With TAA, we're taking the intelligence generated from our leading research teams and uniting it with the power of advanced machine learning to help customers automatically identify these dangerous threats and take action."
TAA, says the blog, "merges the best threat hunting talent in the business with machine learning and AI and productizes it, putting in our customers hands, the most sophisticated advance threat detection possible." It is available now as part of Symantec's Integrated Cyber Defense Platform for Symantec Advanced Threat Protection (ATP) customers.
U.S. Energy Department Offers $25 Million for Cybersecurity Tech
16.4.2018 securityweek IT
The United States Department of Energy (DOE) on Monday announced that it’s prepared to award up to $25 million for the research and development of technologies designed to protect the country’s energy infrastructure against cyber threats.
The funding opportunity announcement (FOA) comes from the Office of Electricity Delivery and Energy Reliability’s Cybersecurity for Energy Delivery Systems (CEDS) program and it seeks applications for researching, developing and demonstrating novel approaches to improving cyber resilient energy delivery systems.Energy Department offers $25 million for cybersecurity
Specifically, the offer is for projects focusing on designing a cyber-resilient architecture for the electric and oil and natural gas (ONG) subsectors, security for the ONG environment, secure communications, secure cloud-based technologies in operational technology (OT) networks, and enhancing security in the energy sector.
Applicants must not only conduct research and develop the products, but also demonstrate them in an actual facility. Proposals, which need to be submitted until June 18, must also include a strategy for transitioning from existing systems either by commercializing the new solution or by making it open source.
“This FOA builds on DOE’s efforts with the private sector toward improving the security of the Nation's critical energy infrastructure, and reducing the risk of a cyber incident that could disrupt energy delivery,” the DOE said. “It will expand the development and adoption of energy technologies that will help ensure a more secure, resilient, and reliable electricity system.”
As of last year, the DOE said it had invested more than $270 million since 2010 in cybersecurity research, development and demonstration projects led by members of the industry, universities and the agency’s own National Laboratories.
In September 2017, the Energy Department announced its intention to invest $50 million in the research and development of tools and technologies that would make the country’s energy infrastructure more resilient and secure, including more than $20 million in cybersecurity.
Earlier this year, the DOE announced the creation of the Office of Cybersecurity, Energy Security, and Emergency Response (CESER) to help the organization efficiently coordinate preparedness and response to both manmade and natural threats.
Energy facilities in the United States and the Energy Department itself have often been targeted by malicious hackers in the past years, although the attacks have not been as damaging as the ones that hit Iran, Saudi Arabia and Ukraine
McAfee Expands Cloud Security Program
16.4.2018 securityweek IT
At RSA Conference 2018 at San Francisco, CA, McAfee has announced two additions to its cloud security program, and published a new analysis of the corporate adoption of cloud services. The new services are centered on securing containers in the cloud, and adding consistent security to third-party cloud services. The analysis, Navigating a Cloudy Sky, surveyed 1,400 IT decision makers around the world, and interviewed several C-level executives.
Key findings from the survey (PDF) are that cloud adoption is continuing to grow, but the cloud-first strategy has slowed. Ninety-seven percent of organizations now use cloud services (either public, private, or both; up from 93% one year ago); but the adoption of a cloud first strategy has dropped from 82% last year to 65% this year.
It isn't immediately clear why the cloud first strategy has slowed, but it could partly be down to uncertainty about the EU's General Data Protection Regulation (GDPR) coming into effect in May 2018. While fewer than 10% of organizations expect to decrease their cloud investments because of GDPR, there are marked differences in the expected increases. Forty-nine percent of firms expect to increase their investment in private and hybrid cloud; but only 37% expect to increase investment in the public cloud (where they are likely to have less control of and visibility into their data).
A disparity between the growing use of containers and serverless computing in the cloud, and the secure use of those technologies is also apparent from the survey. Eighty percent of those surveyed are using or experimenting with these technologies, while only 66% have a security strategy for containers, and 65% have a security strategy for serverless computing.
This issue is now addressed with McAfee's announcement that support will be included in its Cloud Workload Security (CWS) v5.1, which will be available before the end of Q2 2018.
"As enterprises turn to the cloud to transform themselves into a digital business and develop compelling experiences for their customers, they often overlook the security challenges involved in adopting a multi-cloud or hybrid-cloud environment," said Rajiv Gupta, SVP of the cloud security business unit. "McAfee Cloud Workload Security enables organizations to secure cloud workloads and containers across AWS, Azure, VMware, and their private cloud, addressing key security, compliance and governance requirements so that they can accelerate their business in the cloud."
This version will discover new Docker containers within five minutes of their deployment. It allows administrators to quarantine concerning workloads or containers using micro- and nano-segmentation with a single click, isolating threats and inhibiting their spread. It also offers enhanced threat monitoring and detection with AWS GuardDuty alerts available within the CWS dashboard; and includes policy compliance assessments to PCI, SOX, HIPAA and more to enable simple remediation.
McAfee has also, and separately, announced the McAfee CASB Connect Program. This is designed to allow customers to apply the same set of security policies across all their cloud applications. It is, says McAfee, the industry's first self-serve framework and accompanying program that enables any cloud service provider or partner to rapidly build lightweight API connectors to McAfee® Skyhigh Security Cloud within days, without writing a single line of code.
But only if the cloud service is incorporated within the 'McAfee CASB Connect Catalog'. Right now, there are just 12 entries in this catalog (out of some 20,000 different cloud services); but they include heavyweights such as O365, Box, Salesforce, Slack and Dropbox.
Gopi Krishna Boyinapalli, a senior product manager with McAfee's CASB, explains the problem being addressed in an associated blog: "Organizations not only need to enforce appropriate security controls for different cloud services, they also require a central control point to enforce the same set of security policies across their SaaS, PaaS, and IaaS deployments. In fact, Gartner predicts that, through 2020, 95% of cloud security failures will be the customer's fault. This has caused enterprises to look for ways to enforce additional security controls on their cloud solutions beyond what a cloud service provider offers natively."
Clearly, the Connect Catalog will need to expand before it is of serious value to the McAfee customer; but we can expect the company to react to customer requests for the inclusion of new cloud services, just as we can expect new and small, perhaps niche, cloud providers to seek inclusion to become more attractive to the existing McAfee cloud customer base.
In time, it should benefit both cloud service providers and cloud service consumers. The providers can minimize the cost and complexity of customizing their security controls to meet the data and security requirements of different customers; while consumers can more easily and rapidly adopt new cloud services without having to extend their security and compliance policies to every new service.
"One of the core tenets of our vision," explains Rajiv Gupta, SVP of the McAfee cloud security business unit, "is to make cloud the most secure environment for businesses. The McAfee CASB Connect Program framework enables every cloud service in the catalog to easily conform to the security needs of enterprises, thus minimizing the security barriers that hinder cloud adoption and allowing enterprises to confidently adopt cloud services to accelerate their business."
McAfee's cloud security business unit combines McAfee with the Skyhigh cloud access security broker that it acquired in January 2018. McAfee itself was spun out of Intel in April 2017. Intel had acquired McAfee for $7.68 billion in 2010.
Massive Ransomware attack cost City of Atlanta $2.7 million
16.4.2018 securityaffairs Ransomware
According to Channel 2 Action News that investigated the incident, the ransomware attack on the City of Atlanta cost it at least $2.7 million.
In the last weeks, I wrote about a massive ransomware attack against computer systems in the City of Atlanta.
The ransomware infection has caused the interruption of several city’s online services, including “various internal and customer-facing applications” used to pay bills or access court-related information.
Investigators believe that hackers initially compromised a vulnerable server, then the ransomware began spreading to desktop computers throughout the City network. Crooks demanded a payment of 6 Bitcoin, around $51,000 at the current rate,
New Atlanta Chief Operating Officer Richard Cox said that several departments have been affected.
No critical infrastructure and services seem to be affected, the departments responsible for public safety, water, and airport services are operating as normal, however.

How much cost this attack on the City of Atlanta?
According to Channel 2 Action News that investigated the incident, the ransomware attack cost the city at least $2.7 million.
“They were probably not as protected as we probably thought they were,” Georgia State University cybersecurity researcher Don Hunt said.
Channel 2 investigative reporter Aaron Diamant obtained new records that allowed the media outlet to estimate the overall cost of the attack.
Aaron Diamant
✔
@AaronDiamantWSB
Coming up at 5...with few specifics from City of Atlanta leaders, the clues we found of the growing cost to taxpayers from last months crippling cyberattack on city networks. @wsbtvstorm
11:03 PM - Apr 11, 2018
1
See Aaron Diamant's other Tweets
Twitter Ads info and privacy
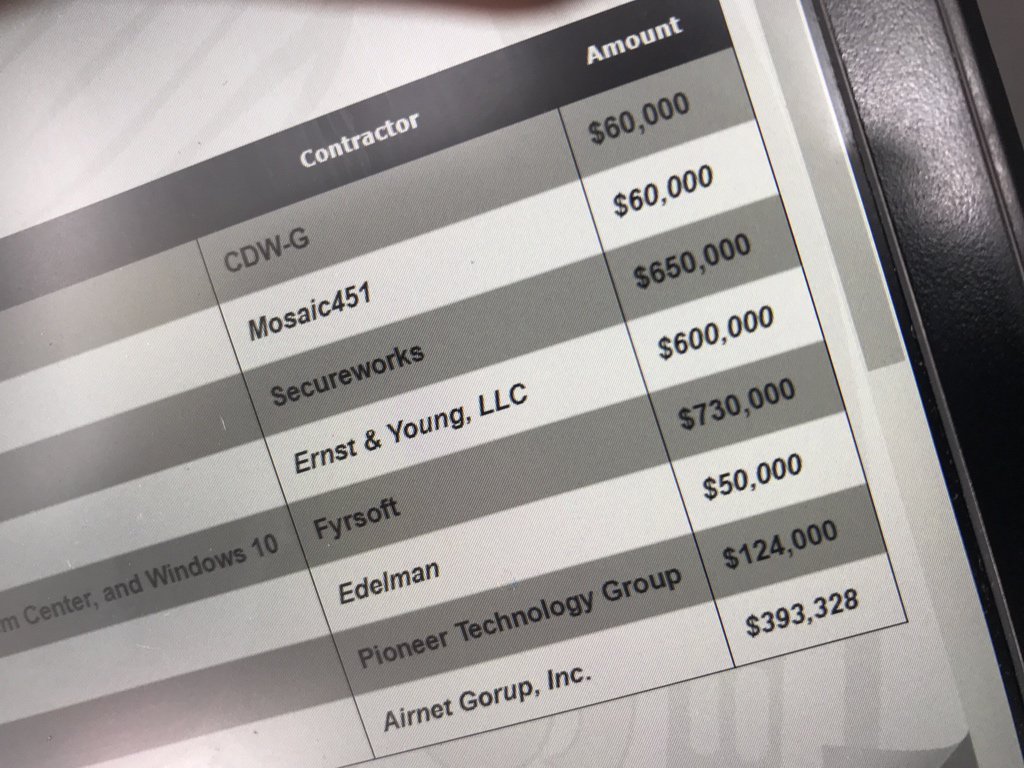
The $2.7 million cost includes eight emergency contracts that were signed just after the malware compromised the city networks.
“They’ve got some really big players on the team there, and they’re spending a lot of money, so the depth of the problems that they had are probably enormous,” Hunt said.
The leaders of the City of Atlanta signed a $650,000 contract with cybersecurity firm SecureWorks that was involved in the incident response.
Accessing the records the journalist discovered that the leaders signed other contracts as reported in the above image, a $600,000 contract with management consultant Ernst and Young for advisory services and another $730,000 to Firsoft.
“That’s absolutely construction work. What they’re looking to do is not revamping the system, they’re starting from scratch and going from the ground up again,” Hunt added.
“You’re talking about the possibility of privacy being violated. It could be an indicator that you’ve got a deeper problem inside or potentially a deeper problem that you want to get ahead of right away,”
Bitcoin web wallet addresses generated with a flawed library are exposed to brute-force attacks
16.4.2018 securityaffairs Cryptocurrency
Multiple vulnerabilities in the SecureRandom() function expose Bitcoin web wallet addresses generated by the flawed library to brute-force attacks.
Old Bitcoin web wallet addresses generated in the browser or through JavaScript-based wallet apps might be affected by a cryptographic vulnerability that could be exploited b attackers to steal funds.
According to the experts, the popular JavaScript SecureRandom() library isn’t securely random, this means that an attacker can launch brute-force attacks on private keys.
The flaw affects the JavaScript SecureRandom() function that is used for generating a random Bitcoin address and its adjacent private key, currently, it doesn’t actually.
“It will generate cryptographic keys that, despite their length, have less than 48 bits of entropy, […] so its output will have no more than 48 bits of entropy even if its seed has more than that,” said the system administrator David Gerard.
“SecureRandom() then runs the number it gets through the obsolete RC4 algorithm, which is known to be more predictable than it should be, i.e. less bits of entropy,” Gerard added. “Thus, your key is more predictable.”
Gerard concluded that all Bitcoin addresses generated using the SecureRandom() function are vulnerable to brute-force attacks.
“The conclusion seems to be that at least all wallets generated by js tools inside browsers since bitcoin exists until 2011 are impacted by the Math.random weakness if applicable to the related implementations, the Math.random or RC4 (Chrome) weakness between 2011 and 2013, and RC4 weakness for Chrome users until end of 2015” continues Gerard.
Gerard explained that several web-based or client-side wallet apps used the SecureRandom() function, the expert said that all Bitcoin addresses possibly affected are:
BitAddress pre-2013;
bitcoinjs before 2014;
current software that uses old repos they found on Github.
A user has thrown the same alert on the Linux Foundation mailing list:
“A significant number of past and current cryptocurrency products contain a JavaScript class named SecureRandom(), containing both entropy collection and a PRNG. The entropy collection and the RNG itself are both deficient to the degree that key material can be recovered by a third party with medium complexity.” reads the alert.
The researcher Mustafa Al-Bassam added that several old implementations for web and client-side Bitcoin wallets apps leveraged the jsbn.js cryptographic library for generating Bitcoin addresses. Unfortunately, the jsbn.js cryptographic library used the SecureRandom() function, this means that Bitcoin address private keys were exposed to attack.
“The original disclosure didn’t contain any information about the library in question, so I did some digging.” added Mustafa.
“I think that the vulnerability disclosure is referring to a pre-2013 version of jsbn, a JavaScript crypto library. Before it used the CSRNG in the Web Crypto API, it tried to use nsIDOMCrypto, but incorrectly did a string comparison when checking the browser version.”
If you are using a Bitcoin wallet address generated with tools using the flawed functions you need to generate new Bitcoin address and transfer the funds to the new one.
Talos experts found many high severity flaws in Moxa EDR-810 industrial routers
16.4.2018 securityaffairs ICS
Security experts at Cisco’s Talos group have discovered a total of 17 vulnerabilities in Moxa EDR-810 industrial routers manufactured by Moxa.
The Moxa EDR-810 is an integrated industrial multiport router that implements firewall, NAT, VPN and managed Layer 2 switch capabilities.
These devices are used in industrial environments to protect systems such as PLC and SCADA systems in factory automation and DCS in oil and gas organizations.
“Today, Talos is disclosing several vulnerabilities that have been identified in Moxa EDR-810 industrial secure router.” reads the security advisory published by Talos.
“Moxa EDR-810 is an industrial secure router with firewall/NAT/VPN and managed Layer 2 switch functions. It is designed for Ethernet-based security applications in remote control or monitoring networks. Moxa EDR-810 provides an electronic security perimeter for the protection of critical assets such as pumping/ treatment systems in water stations, DCS systems in oil and gas applications, and PLC/SCADA systems in factory automation.”
Researchers have discovered many high severity command injection vulnerabilities (CVE-2017-12120, CVE-2017-12121, CVE-2017-12125, CVE-2017-14432 to 14434) affecting the web server functionality.
Some of the issues discovered by Cisco Talos team could allow an attacker to escalate privileges and obtain a root shell on the target Moxa EDR-810 devices by simply sending specially crafted HTTP POST requests.
“TALOS-2017-0472 is an exploitable command injection vulnerability that exists in the web server functionality of Moxa EDR-810. A specially crafted HTTP POST can cause a privilege escalation resulting in attacker having access to a root shell.” reads the description for the CVE-2017-12120 flaw.
“An attacker may be able to inject OS commands into the ifs= parm in the “/goform/net_WebPingGetValue” uri to trigger this vulnerability and take control over the targeted device.”
Similar is the CVE-2017-12121 that resides in the web server functionality of Moxa EDR-810.
“A specially crafted HTTP POST can cause a privilege escalation resulting in attacker having access to a root shell. An attacker can inject OS commands into the rsakey\_name= parm in the “/goform/WebRSAKEYGen” uri to trigger this vulnerability and take control over the targeted device.” continues the analysis published by Talos.

The experts also discovered several high severity DoS vulnerabilities (CVE-2017-14435 to 14437, CVE-2017-12124, CVE-2017-14438 and 14439) that can be exploited by sending specially crafted requests to the device.
“TALOS-2017-0476 is an exploitable denial of service vulnerability that exists in the web server functionality of Moxa EDR-810. Access to a specially crafted HTTP URI can cause a null pointer dereference resulting in the web server crashing. An attacker can send a crafted URI to trigger this vulnerability.” reads the description for the CVE-2017-12124.
The experts also reported four medium severity issues related to the storage in plaintext of the passwords, information disclosure affecting the Server Agent functionality, and the use of weakly encrypted or clear text passwords.
Moxa has released an updated version of the firmware to address the above issues.
Severe Flaws Expose Moxa Industrial Routers to Attacks
16.4.2018 securityweek ICS
Cisco’s Talos intelligence and research group has reported identifying a total of 17 vulnerabilities in an industrial router from Moxa, including many high severity command injection and denial-of-service (DoS) flaws.
The security holes have been identified in Moxa EDR-810, an integrated industrial multiport secure router that provides firewall, NAT, VPN and managed Layer 2 switch capabilities. According to the vendor, the device is designed for controlling, monitoring and protecting critical assets, such as pumping and treatment systems in water stations, PLC and SCADA systems in factory automation applications, and DCS in oil and gas organizations.Moxa industrial router vulnerabilities
Several of the problems found by Cisco have been described as high severity command injection vulnerabilities affecting the web server functionality of this Moxa router. The flaws allow an attacker to escalate privileges and obtain a root shell on the system by sending specially crafted HTTP POST requests to the targeted device.
The industrial router is also impacted by several high severity DoS flaws that can be exploited by sending specially crafted requests to the device.
There are also four medium severity issues related to the transmission of passwords in clear text, information disclosure involving the Server Agent functionality, and the use of weakly encrypted or clear text passwords. Cisco has made available technical details and proof-of-concept (PoC) code for each of the vulnerabilities.

The vulnerabilities have been reproduced on Moxa EDR-810 v4.1 devices, and they have been patched by the vendor with the release of version 4.2 on April 12. The issues were reported to Moxa in mid and late November 2017, which means it took the company roughly 150 days to release a fix – this is the average patching time for SCADA systems, according to a report published last year by ZDI.
This was not the first time Talos researchers found vulnerabilities in Moxa products. Last year, Talos published advisories describing more than a dozen security holes uncovered in Moxa access points.
This is also not the first time security experts find weaknesses in Moxa’s EDR routers. Back in 2016, researcher Maxim Rupp identified multiple high severity vulnerabilities that could have been exploited for DoS attacks, privilege escalation, and arbitrary code execution.
Attackers exfiltrated a casino’s high-roller list through a connected fish tank
16.4.2018 securityaffairs Hacking
Nicole Eagan, the CEO of cybersecurity company Darktrace, revealed that is company investigated that hack of an unnamed casino that was breached via a thermometer in a lobby fish tank.
Internet of things devices are enlarging our attack surface, smart devices are increasingly targeted by hackers in the wild.
The case we are going to discuss demonstrate it, Nicole Eagan, the CEO of cybersecurity company Darktrace, revealed that is company investigated that hack of an unnamed casino that was breached via a thermometer in a lobby aquarium.
“There’s a lot of internet of things devices, everything from thermostats, refrigeration systems, HVAC [air conditioning] systems, to people who bring in their Alexa devices into the offices. There’s just a lot of IoT. It expands the attack surface and most of this isn’t covered by traditional defenses.” Nicole Eagan, the CEO of cybersecurity company Darktrace, told the WSJ CEO Council in London on Thursday.
“The attackers used that to get a foothold in the network. They then found the high-roller database and then pulled that back across the network, out the thermostat, and up to the cloud,”
The hackers stole the casino’s high-roller database through a thermometer in the lobby fish tank.

This isn’t the first a thermometer hack reported by experts at Darktrace, in July 2017 hackers attempted to exfiltrate data from a US casino by hacking into an Internet-connected fish tank.
A connected fish tank included sensors used to control the temperature, food distribution, and cleanliness of the tank.
“Somebody got into the fish tank and used it to move around into other areas (of the network) and sent out data,” said Justin Fier, Darktrace’s director of cyber intelligence.
At the time, hackers exfiltrated 10 GB of data that were sent out to a device in Finland.
TrueMove H, the biggest 4G mobile operator in Thailand suffered a data leak
16.4.2018 securityaffairs Mobil
TrueMove H, the biggest 4G mobile operator in Thailand suffered a data leak, 46000 people’s data store on an AWS bucked were left on accessible online, including driving licenses and passports.
Let’s speak about a new data breach, this time the victim is TrueMove H, the biggest 4G mobile operator in Thailand.
The operator exposed online customers personal data that were stored in an Amazon AWS S3 bucket.
The leaked data also includes scans of identity documents, the data were left accessible until April 12, when the company restricted the access.
The huge trove of data was discovered by security researcher Niall Merrigan that attempted to notify the issue to TrueMove H, but the operator did not respond.
Merrigan told El Reg that the AWS bucked contained 46,000 records for a total of 32GB.
The experts published a blog post on the case, he explained that tools like bucket stream and bucket-finder allow scanning the internet for open S3 AWS buckers.
Merrigan used the bucket-finder tool to find open S3 Buckets when noticed the one belonging to the TrueMove H.
“The output from bucket-finder showed several issues such as config files, source code and other potential information disclosures. Bucket finder only gets the top 1000 files via the AWS S3 API. To simplify things, I loaded the results into a small SQL database for analysis. I found all the sites that had 1000 files and did a quick visual scan to see what they contained and if there was a way to identify the owner if the need arose.” wrote the expert.
“One such owner was True Move H, the second largest mobile operator in Thailand,”

“Representatives of the telco initially told him to ring its head office when he asked for the contact details of a security response staffer before telling him his concerns had been passed on some two weeks later, after El Reg began asking questions on the back of Merrigan’s findings.” reported El Reg.
TrueMove H has issued a statement to clarify that the data leak affected their subsidiary I True Mart.
Microsoft engineer charged with money laundering linked to Reveton ransomware
16.4.2018 securityaffairs Ransomware
The Microsoft network engineer Raymond Uadiale (41) is facing federal charges in Florida for the alleged involvement in Reveton Ransomware case.
The man is suspected to have had a role in helping launder money obtained from victims of the Reventon ransomware.
Uadiale currently works at Microsoft site in Seattle since 2014, according to Florida police between October 2012 and March 2013 he operated online with a UK citizen that used the moniker K!NG.
K!NG was responsible for Reveton ransomware distribution meanwhile Uadiale is accused to have managed the victims’ payments and shared them with K!NG.
“The judge did a double take when he heard that Uadiale has been working for Microsoft in the Seattle area since 2014.” reported the SunSentinel.
“Cybersecurity, don’t tell me?” U.S. Magistrate Judge Barry Seltzer quipped. “Are they aware of the charges?”
Assistant U.S. Attorney Jared Strauss confirmed in court that Uadiale involvement in Reveton campaign occurred before he was hired by Microsoft and prosecutors don’t have any evidence that he had any involvement in actually spreading the malware.
“Reveton is described as drive-by malware because unlike many viruses—which activate when users open a file or attachment—this one can install itself when users simply click on a compromised website. Once infected, the victim’s computer immediately locks, and the monitor displays a screen stating there has been a violation of federal law.” reads an alert published by the FBI in 2012.

The Reveton ransomware locks the screen on the infected devices and requests victims to buy GreenDot MoneyPak vouchers and insert their code into the Reveton screen locker to unlock them.
The locked screen would display a fake message purportedly from the FBI or other law enforcement agency would claim the user had violated federal law.
While K!NG was accumulating victims’ payments on GreenDot MoneyPak prepaid cards, Uadiale was transferring them to the man in the UK via the Liberty Reserve virtual currency. The Liberty Reserve was shut down in 2013 and its founder Arthur Budovsky was sentenced to 20 years in jail for committing money laundering.
Court documents confirmed that Uadiale transferred more than $130,000 to K!NG.
Uadiale, is currently free on $100,000 bond and must wear an electronic monitor, he risks a maximum sentence of up to 20 years in prison, a fine of up to $500,000, and up to three years of supervised release.
UK GCHQ director confirmed major cyberattack on Islamic State
16.4.2018 securityaffairs BigBrothers
GCHQ director Jeremy Fleming announced this week that the U.K. has launched a major cyberattack on the Islamic State (IS) terrorist organization.
According to the spy chief, the GCHQ the attack was launched in collaboration with the U.K. Ministry of Defence and has distributed operations of the Islamic State.
The UK intelligence believes this is the first time it “systematically and persistently degraded an adversary’s online efforts as part of a wider military campaign,”

Source BBC
Fleming explained that UK cyber experts have operated to disrupt online activities and networks of the Islamic State, and deter an individual or group.
“These operations have made a significant contribution to coalition efforts to suppress Daesh propaganda, hindered their ability to coordinate attacks, and protected coalition forces on the battlefield,” GCHQ chief told an audience at the Cyber UK conference in Manchester.
“In 2017 there were times when Daesh found it almost impossible to spread their hate online, to use their normal channels to spread their rhetoric, or trust their publications. Of course, the job is never done – they will continue to evade and reinvent. But this campaign shows how targeted and effective offensive cyber can be,”
Mr. Fleming did not reveal details of the cyber attacks because it was “too sensitive to talk about,” he praised the success of such kind of operations against a threat that is abusing technology to spread propaganda.
“Much of this is too sensitive to talk about, but I can tell you that GCHQ, in partnership with the Ministry of Defence, has conducted a major offensive cyber campaign against Daesh.” added Mr. Fleming.
“These operations have made a significant contribution to coalition efforts to suppress Daesh propaganda, hindered their ability to coordinate attacks, and protected coalition forces on the battlefield. But cyber is only one part of the wider international response. This is the first time the UK has systematically and persistently degraded an adversary’s online efforts as part of a wider military campaign.”
The US CYBERCOM and Europol have also been conducting cyber operations against online activities of the Islamic State.
Mr. Fleming has also spoken about Russia defining its cyber activity as an “unacceptable cyber-behaviour” that was a “growing threat” to the West.
“We’ll continue to expose Russia’s unacceptable cyber behaviour, so they’re held accountable for what they do, and to help Government and industry protect themselves. The UK will continue to respond to malicious cyber activity in conjunction with international partners such as the United States. We will attribute where we can.” added Flaming.
“And whilst we face an emboldened Russia, we also see the tectonic plates in the Middle East moving. We see Iran and its proxies meddling throughout the region. The use of Chemical Weapons in Syria. We’re watching the dispersal of Daesh fighters. Serious Crime Gangs smuggling people from Eastern Europe and Northern Africa.”
Flaming also cited the NotPetya ransomware attack on Ukraine that both UK and US attributed to Russia.
“They’re not playing to the same rules,” Mr Fleming concluded. “They’re blurring the boundaries between criminal and state activity.”
Hackers Have Started Exploiting Drupal RCE Exploit Released Yesterday
15.4.2018 thehackernews Exploit
Hackers have started exploiting a recently disclosed critical vulnerability in Drupal shortly after the public release of working exploit code.
Two weeks ago, Drupal security team discovered a highly critical remote code execution vulnerability, dubbed Drupalgeddon2, in its content management system software that could allow attackers to completely take over vulnerable websites.
To address this vulnerability the company immediately released updated versions of Drupal CMS without releasing any technical details of the vulnerability, giving more than a million sites enough time to patch the issue.
Two days ago, security researchers at Check Point and Dofinity published complete technical details about this vulnerability (CVE-2018-7600), using which, a Russian security researcher published a proof-of-concept (PoC) exploit code for Drupalgeddon2 on GitHub.
The Drupalgeddon2 vulnerability that affects all versions of Drupal from 6 to 8 allows an unauthenticated, remote attacker to execute malicious code on default or common Drupal installations.
According to checkpoint's disclosure, the vulnerability exists due to the insufficient sanitation of inputs passed via Form API (FAPI) AJAX requests.
"As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication," Check Point researchers said.
"By exploiting this vulnerability, an attacker would have been able to carry out a full site takeover of any Drupal customer."
However, shortly after the public release of the PoC exploit, which many confirmed to be functional, researchers at Sucuri, Imperva, and the SANS Internet Storm Center started seeing attempts to exploit Drupalgeddon2, though none have yet to see any reports of websites being hacked.
Sites administrators still running vulnerable versions of Drupal are highly recommended to patch the vulnerability by updating their CMS to Drupal 7.58 or Drupal 8.5.1 as soon as possible to avoid exploits.
The vulnerability also affects Drupal 6, which is no longer supported by the company since February 2016, but a patch for the version has still been created.
Hacker Can Steal Data from Air-Gapped Computers through Power Lines
15.4.2018 thehackernews Attack
Do you think it is possible to extract data from a computer using its power cables?
If no, then you should definitely read about this technique.
Researchers from Israel's Ben Gurion University of the Negev—who majorly focus on finding clever ways to exfiltrate data from an isolated or air-gapped computer—have now shown how fluctuations in the current flow "propagated through the power lines" could be used to covertly steal highly sensitive data.
Sound something like a James Bond movie? Well, the same group of researchers has previously demonstrated various out-of-band communication methods to steal data from a compromised air-gapped computer via light, sound, heat, electromagnetic, magnetic and ultrasonic waves.
Air-gapped computers are those that are isolated from the Internet and local networks and therefore, are believed to be the most secure devices that are difficult to infiltrate or exfiltrate data.
"As a part of the targeted attack, the adversary may infiltrate the air-gapped networks using social engineering, supply chain attacks, or malicious insiders. Note that several APTs discovered in the last decade are capable of infecting air-gapped networks, e.g., Turla, RedOctober, and Fanny," researchers said.
"However, despite the fact that breaching air-gapped systems has been shown feasible, the exfiltration of data from an air-gapped system remains a challenge."
Dubbed PowerHammer, the latest technique involves controlling the CPU utilization of an air-gapped computer using a specially designed malware and creating fluctuations in the current flow in morse-code-like pattern to transfer data hints in binary form (i.e., 0 and 1).
In order to retrieve modulated binary information, an attacker needs to implant hardware to monitor the current flow being transmitted through the power lines (to measure the emission conducted) and then decodes the exfiltrated data.
"We show that a malware running on a computer can regulate the power consumption of the system by controlling the workload of the CPU. Binary data can be modulated on the changes of the current flow, propagated through the power lines, and intercepted by an attacker," researchers said.
According to the researchers, attackers can exfiltrate data from the computer at a speed of 10 to 1,000 bits-per-second, depending upon their approach.
The higher speed would be achieved if attackers are able to compromise the power lines inside the target building that connects the computer. This attack has been called "line-level powerhammering."
The slower speed is achieved in "phase-level powerhammering" that that can be exploited from the outside electrical service panel of a building.
In both variants of the attack, the attacker measures and encodes the emission conducted and then decodes the exfiltrated data.
With the line-level PowerHammering attack, researchers were able to exfiltrate data from a PC running an Intel Haswell-era quad-core processor at the rate of 1000 bits/second and an Intel Xeon E5-2620-powered server at 100 bits/second, both with a zero percent error rate.
The phase-level variant attack suffers performance degradation. Due to the background noise in the phase level, (since power is shared with everything else connected, such as appliances and lights), the researchers could achieve speeds up to 3 bits/second at a zero percent error rate, though this increased to 4.2% at speeds of 10 bits/second.
"The results indicate that in the phase level power-hammering attack, desktop computers could only be used to exfiltrate small amount of data such as passwords, credential tokens, encryption keys, and so on," the researchers said.
For more details on the PowerHammer attack, you can head onto the paper [PDF] titled, 'PowerHammer: Exfiltrating Data from Air-Gapped Computers through Power Lines.'
Popular Android Phone Manufacturers Caught Lying About Security Updates
15.4.2018 thehackernews Android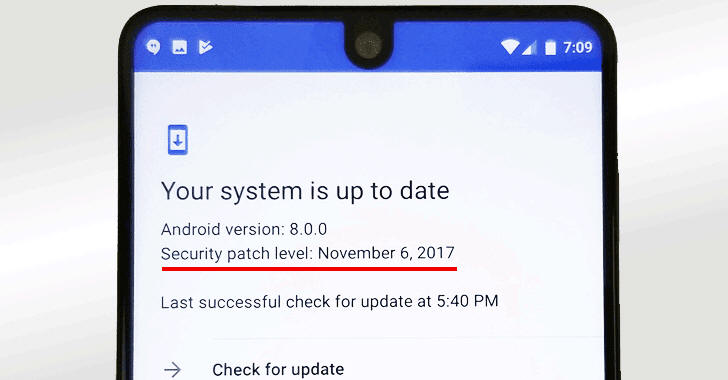
Android ecosystem is highly broken when it comes to security, and device manufacturers (better known as OEMs) make it even worse by not providing critical patches in time.
According to a new study, most Android vendors have been lying to users about security updates and telling customers that their smartphones are running the latest updates.
In other words, most smartphone manufacturers including big players like Samsung, Xiaomi, OnePlus, Sony, HTC, LG, and Huawei are not delivering you every critical security patch they're supposed to, a study by Karsten Nohl and Jakob Lell of German security firm Security Research Labs (SRL) revealed.
Nohl and Lell examined the firmware of 1,200 smartphones from over a dozen vendors, for every Android patch released last year, and found that many devices have a "patch gap," leaving parts of the Android ecosystem exposed to hackers.
"Sometimes these guys just change the date without installing any patches. Probably for marketing reasons, they just set the patch level to almost an arbitrary date, whatever looks best," Nohl says in an interview with Wired.
Google releases security patches every month to keep its Android ecosystem safe and secure from the underlying risks, but since every manufacturer and mobile carrier modify the operating system to make their smartphone unique, they often fail to apply all those patches in time.
SRL researchers investigated smartphones that had supposedly received and installed the latest Android updates and released the following breakdown of their findings:
0-1 missed patches—Google, Sony, Samsung, Wiko Mobile
1-3 missed patches—Xiaomi, OnePlus, Nokia
3-4 missed patches—HTC, Huawei, LG, Motorola
4+ missed patches—TCL, ZTE
Specifically, the above result focused on security patches for Critical and High severity vulnerabilities that were released in 2017.
As shown above, Google, Samsung, Wiko Mobile and Sony are still doing great in installing patches, but others, specifically Chinese vendors like Xiaomi and OnePlus are worse in protecting their customers against latest security flaws.
In order to address the patch gap issue, Google has already launched a project, dubbed Treble, under which the company brought some significant changes to the Android system architecture last year to gain more control over the update process.
Project Treble was included as part of Android 8.0 Oreo and has been designed to separate core hardware code from the OS code, eliminating OEMs’ dependencies over to deliver Android updates faster.
However, even if your Android device runs Oreo 8.0 operating system, it's not necessary that it supports Treble project, as it's still up to the device manufacturer to include it. For example, Oreo firmware update for OnePlus devices don't support Treble yet.
But new devices will be required to support Treble moving forward.
Check Your Device For ‘Patch Level’
Meanwhile, SRL has developed an app called SnoopSnitch, which you can download for free, to measure the patch level of your own Android smartphone, helping you verify vendor claims about the security of your devices.
Malware researcher have dismantled the EITest Network composed of 52,000
15.4.2018 securityaffairs Virus
Malware researchers from Abuse.ch, BrillantIT, and Proofpoint have sinkholed the control infrastructure behind EITest campaign and shut down it.
Malware researchers from Abuse.ch, BrillantIT, and Proofpoint have sinkholed the control infrastructure behind EITest campaign that leveraged on a network of hacked servers exploited by crooks to distribute traffic (TDS).
The network was used to redirect users to compromised domains hosting exploit kits, delivering malware or used for other fraudulent activities such as tech scams.
EITest infrastructure was first discovered back in 2011, from middle 2014 crooks started using it as a TDS botnet.
“researchers traced the chain via server side artifacts and some historical analysis of server side compromises to infections as early as 2011 when it was redirecting to a private EK known as Glazunov.” wrote Proofpoint researcher Kafeine.
“The infection chain appears to have paused between the end of 2013 and the beginning of July 2014, when it began directing into Angler“
Hackers installed a backdoor on the compromised machines and used it to redirect legitimate traffic to malicious websites, for this reason, experts defined EITest as the “king of traffic distribution.”
“EITest is one of the longest malicious delivery campaigns that has continued to evolve. In the spring of 2017, it started redirecting Internet Explorer users to tech support scams in addition to the existing redirections with the fake Chrome fonts.” reads the analysis published “Malware don’t need coffee.” website.
“Actors behind this campaign are generating hundreds of domains per day.The only purpose of those domains names is to redirect users to tech support scams or malicious websites.”
According to researcher Kafeine, crooks behind the EITest campaign started selling hijacked traffic from hacked sites for $20 per 1,000 users, selling traffic blocks of 50-70,000 visitors, generating between $1,000 and $1,400 per block of traffic.
“in the past month the activity behind this infection chain has primarily consisted of social engineering [1] and tech support scams [3] leading to ransomware.” added Kafeine.
Early 2018, a malware a researcher at BrillantIT was able to sinkhole the botnet after discovered how to crack the way the bots contact the C&C servers.

The experts were able to hijack the entire EITest network by seizing just one domain (stat-dns.com) Traffic analysis allowed the researchers to discover that the botnet handled about two million users per day coming from over 52,000 compromised websites, most of which were WordPress sites.
Kafeine added that following the successful sinkhole operation, the operators behind the botnet have shut down their C&C proxies. Kafeine added the experts noticed some encoded calls to the sinkhole that embedded commands they would associate with takeover attempts. At the time it is not clear who sent them, likely the operators or other researchers attempting to interact control infrastructure.
“Following the successful sinkhole operation, the actor shut down their C&C proxies, but we have not observed further overt reactions by the operators of EITest,” concluded Kafeine.
“However, we will continue to monitor EITest activity as the EITest actor may attempt to regain control of a portion of the compromised websites involved in the infection chain.”
Are your Android devices updated? Researchers say maybe no
15.4.2018 securityaffairs Android
Probably you don’t know that many Android smartphone vendors fail to roll out Google’s security patches and updates exposing the users to severe risks.
Researchers at Security Research Labs (SRL) that the problem also involves major vendors, including HTC, Huawei, and Motorola.
In some cases, manufacturers roll out incomplete security patches leaving the devices vulnerable to cyber attacks.
“Phones now receive monthly security updates. Installing patches every month is an important first step, but is still insufficient unless all relevant patches are included in those updates. Our large study of Android phones finds that most Android vendors regularly forget to include some patches, leaving parts of the ecosystem exposed to the underlying risks.” reads the blog post published by the SRL team.
The popular SRL experts Karsten Nohl and Jakob Lell presented the findings of the research at the Hack In The Box security conference in Amsterdam, the Netherlands.
The experts pointed out that that, even if Google is able to install some security patched over-the-air without vendor interaction, in some cases the fixes affect low-level faulty software components, such as drivers and system libraries, and this process needs the involvement of manufacturers.
The experts explained that some Android devices receive only half of the monthly updates, in some cases only from Google and none from the manufacturer.
The following table shows the average number of missing Critical and High severity patches before the claimed patch date (Samples – Few: 5-9; Many: 10-49; Lots: 50)
Experts clarified that some phones are included multiple times with different firmware releases.

Researchers at SRL explained that the only way to discover what is installed on your device is to take a look at what is included in the monthly fixes from Google verify that most important updates are present on the device.
The good news for users is that the failure in patch management is some cases is not enough for an attacker to remotely compromise an Android device and bypass defense mechanisms like Android’s sandbox and ASLR.
“Modern operating systems include several security barriers, for example, ASLR and sandboxing, all of which typically need to be breached to remotely hack a phone.” continues the researchers.
“Owing to this complexity, a few missing patches are usually not enough for a hacker to remotely compromise an Android device. Instead, multiple bugs need to be chained together for a successful hack.”
I suggest you read the research paper for more details.
Enterprise App Security Firm Onapsis Raises $31 Million
14.4.2018 securityweek IT
Application security firm Onapsis has raised $31 million through a Series C funding round led by new investor LLR Partners, the company announced Friday, bringing the total amount raised to $62 million.
Onapsis, which helps companies protect ERP systems and applications such as SAP and Oracle, says the funding will help support sales and marketing efforts as it expands in the application security market, and also support product development, threat research and scaling its channel and partner programs.
With more than 180 employees globally, the company says it currently has more than 200 Fortune 2000 companies as customers, and has achieved record year-over-year growth for five consecutive years.
Existing institutional investors .406 Ventures, Evolution Equity Partners and Arsenal Venture Partners. David Stienes, Partner at LLR Partners, also participated in the funding round.
“Onapsis is helping to solve a multi-billion-dollar security and compliance problem, which is now becoming even more widespread with complex digital transformation and ERP cloud migration projects on almost all board room agendas. We are excited to partner with the Onapsis team and leverage our experience and expertise in cybersecurity to help them execute their vision,” said David Stienes, Partner at LLR Partners.
Great Western Railway asks users to reset passwords due to a security breach
14.4.2018 securityaffairs Incindent
The British train company Great Western Rail announced it has suffered a security breach that affected at least 1,000 accounts out of more than a million.
The company owned by the FirstGroup transport business runs trains between London, Penzance, and Worcester
Great Western Rail is urging affected customers to change the password used to access the GWR.com portal, it also informed the UK Information Commissioner’s Office.
Attackers used credential stuffing to access the accounts, this means that hackers attempted to access the accounts by using credentials leaked from other data breaches.
The company is now extending the incident response measure to other account holders.
“We have identified unauthorised automated attempts to access a small number of GWR.com accounts over the past week,” a spokesman told the BBC.
“While we were able to shut this activity down quickly and contact those affected, a small proportion of accounts were successfully accessed.”
“The success rate of the automated logins was extremely low, suggesting any passwords used were likely harvested elsewhere,”
In the following image is reported a data breach notification received by a customer.

The messages inform users that Great Western Rail has reset all GWR.com passwords as a precaution.
“To ensure the security of your personal information you will need to do this when you next log in to the GWR.com website.” reads the message.
“You should use a unique password for each of your accounts for security, and we recommend you review all of your accounts for maximum security, and we recommend you review all your online passwords and change any that are the same.”
If you are a Great Western Rail user change your password and change the password for each website where you used the same credentials.
As usual, let me suggest using a strong password and enable two-factor authentication when available.
Experts warn threat actors are scanning the web for Drupal installs vulnerable to Drupalgeddon2
14.4.2018 securityaffairs Vulnerebility
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes,” experts started observing bad actors attempting to exploit the flaw.
At the end of March, the Drupal Security Team confirmed that a “highly critical” vulnerability (dubbed Drupalgeddon2), tracked as CVE-2018-7600, was affecting Drupal 7 and 8 core and announced the availability of security updates on March 28th.
The vulnerability was discovered by the Drupal developers Jasper Mattsson.
Both Drupal 8.3.x and 8.4.x are no more supported, but due to the severity of the flaw, the Drupal Security Team decided to address it with specific security updates and experts called it Drupalgeddon2.
Drupal development team released the security update in time to address CVE-2018-7600.

A week after the release of the security update, a proof-of-concept (PoC) exploit was publicly disclosed.
The experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
“In brief, Drupal had insufficient input sanitation on Form API (FAPI) AJAX requests. As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication.” reads the analysis.
“By exploiting this vulnerability an attacker would have been able to carry out a full site takeover of any Drupal customer.”
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw.
The experts at the Sucuri firm confirmed that they are seeing attempts for the Drupal RCE (CVE-2018-7600) in the wild, below the Tweet published by Sucuri founder and CTO Daniel Cid.
Daniel Cid
✔
@danielcid
We are seeing attempts for the Drupal RCE (CVE-2018-7600) in the wild now: https://www.drupal.org/sa-core-2018-002 …
Expect that to grow with the new exploits being shared publicly:https://github.com/a2u/CVE-2018-7600/blob/master/exploit.py …
Also, good read from from CheckPoint explaining it:https://research.checkpoint.com/uncovering-drupalgeddon-2/ …
Patch now!
12:15 AM - Apr 13, 2018
Uncovering Drupalgeddon 2 - Check Point Research
By Eyal Shalev, Rotem Reiss and Eran Vaknin Abstract Two weeks ago, a highly critical (21/25 NIST rank) vulnerability, nicknamed Drupalgeddon 2 (SA-CORE-2018-002 / CVE-2018-7600), was disclosed by...
research.checkpoint.com
39
40 people are talking about this
Twitter Ads info and privacy
According to the researchers at the SANS Institute, threat actors are currently scanning the web for vulnerable servers using simple commands such as echo, phpinfo, whoami, and touch.
“The payload pings a host where the hostname of the target is prefixed to the hostname to be pinged. This is sort of interesting as mu6fea[.]ceye[.]io is a wildcard DNS entry, and *.mu6fea[.]ceye[.]io appears to resolve to 118.192.48.48 right now. So the detection of who is “pinging” is made most likely via DNS.” states the SANS.
Experts have no doubts, hackers will start soon exploiting the flaw to hack vulnerable websites in the wild.
APT Trends report Q1 2018
14.4.2018 Kaspersky Analysis APT
In the second quarter of 2017, Kaspersky’s Global Research and Analysis Team (GReAT) began publishing summaries of the quarter’s private threat intelligence reports in an effort to make the public aware of the research we have been conducting. This report serves as the next installment, focusing on the relevant activities that we observed during Q1 2018.
These summaries serve as a representative snapshot of what has been discussed in greater detail in our private reports, in order to highlight the significant events and findings that we feel people should be aware of. For brevity’s sake, we are choosing not to publish indicators associated with the reports highlighted. However, if you would like to learn more about our intelligence reports or request more information on a specific report, readers are encouraged to contact: intelreports@kaspersky.com.
Remarkable new findings
We are always very interested in analyzing new techniques used by existing groups, or in finding new clusters of activity that might lead us to discover new actors. In Q1 2018 we observed a bit of both, which are briefly summarized in this section.
We would like to start by highlighting all the new exploitation techniques applicable for the Meltdown/Spectre vulnerabilities that affect different CPU architectures and vendors. Even though we haven’t seen any of them exploited in the wild so far (only several PoCs) and although vendors have provided various patches to mitigate them, there is still no real solution. The problem relies on the optimization methods used at the processor’s architecture level. Given that a massive hardware replacement is not a realistic solution, Meltdown and Spectre might very well open the door to new infection vectors and persistence methods that we will see in the future.
A similar case was the announcement of several flaws for AMD processors. Even when the full technical details were not yet available, AMD confirmed that these flaws could be exploited for privilege escalation and persistence once a target has been compromised.
We also observed an increasing interest from attackers, including sophisticated actors, in targeting routers and networking hardware. Some early examples of such attacks driven by advanced groups include Regin and CloudAtlas. Additionally, the US Government published an advisory on unusual reboots in a prominent router brand, which might indicate that these specific devices are being actively targeted.
In our Slingshot analysis, we described how the campaign was using Mikrotik routers as an infection vector, compromising the routers to later infect the final victim through the very peculiar mechanism that Mikrotik used for the remote management of devices. In actual fact, we recognised the interest of some actors in this particular brand when the Chimay-red exploit for Mikrotek was mentioned in Wikileak´s Vault7. This same exploit was later reused by the Hajime botnet in 2018, showing once again how dangerous leaked exploits can be. Even when the vulnerability was fixed by Mikrotik, networking hardware is rarely managed properly from a security perspective. Additionally, Mikrotik reported a zero day vulnerability (CVE-2018-7445) in March 2018.
We believe routers are still an excellent target for attackers, as demonstrated by the examples above, and will continue to be abused in order to get a foothold in the victim´s infrastructure.
One of the most relevant attacks during this first quarter of 2018 was the Olympic Destroyer malware, affecting several companies related to the Pyeongchang Olympic Games’ organization and some Olympic facilities. There are different aspects of this attack to highlight, including the fact that attackers compromised companies that were providing services to the games´ organization in order to gain access, continuing the dangerous supply chain trend.
Besides the technical considerations, one of the more open questions is related to the general perception that attackers could have done much more harm than they actually did, which opened some speculation as to what the real purpose of the attack was.
MZ DOS and Rich headers of both files (3c0d740347b0362331c882c2dee96dbf – OlympicDestroyer, 5d0ffbc8389f27b0649696f0ef5b3cfe – Bluenoroff) are exactly the same.
In addition, a very relevant aspect is the effort attackers put in to planting several elaborative false flags, making this attack one of the most difficult we have analyzed in terms of attribution.
In February, we published a report about a previously unknown advanced Android backdoor that we call Skygofree. It seems that the author could be an Italian company selling the product in a similar way to how Hacking Team did in the past, however we don’t yet have any proof of this. Interestingly, shortly after we detected the Android samples of this malware, we also found an early iOS version of the backdoor. In this case, attackers had abused a rogue MDM (Mobile Device Management) server in order to install their malware in victims’ devices, probably using social engineering techniques to trick them into connecting with the rogue MDM.
Finally, we would like to highlight three new actors that we have found, all of them focused in the Asia region:
Shaggypanther – A Chinese-speaking cluster of activity targeting government entities, mainly in Taiwan and Malaysia, active since 2008 and using hidden encrypted payloads in registry keys. We couldn’t relate this to any known actor.
Sidewinder – An actor mainly targeting Pakistan military targets, active since at least 2012. We have low confidence that this malware might be authored by an Indian company. To spread the malware, they use unique implementations to leverage the exploits of known vulnerabilities (such as CVE-2017-11882) and later deploy a Powershell payload in the final stages.
CardinalLizard – We are moderately confident that this is a new collection of Chinese-speaking activity targeting businesses, active since 2014. Over the last few years, the group has shown an interest in the Philippines, Russia, Mongolia and Malaysia, the latter especially prevalent during 2018. The hackers use a custom malware featuring some interesting anti-detection and anti-emulation techniques. The infrastructure used also shows some overlaps with RomaingTiger and previous PlugX campaigns, but this could just be due to infrastructure reuse under the Chinese-speaking umbrella.
Activity of well-known groups
Some of the most heavily tracked groups, especially those that are Russian-speaking, didn´t show any remarkable activity during the last three months, as far as we know.
We observed limited activity from Sofacy in distributing Gamefish, updating its Zebrocy toolset and potentially registering new domains that might be used for future campaigns. We also saw the group slowly shift its targeting to Asia during the last months.
In the case of Turla (Snake, Uroburos), the group was suspected of breaching the German Governmental networks, according to some reports. The breach was originally reported as Sofacy, but since then no additional technical details or official confirmation have been provided.
The apparent low activity of these groups – and some others such as The Dukes – could be related to some kind of internal reorganization, however this is purely speculative.
Asia – high activity
The ever-growing APT activity in this part of the World shouldn´t be a surprise, especially seeing as the Winter Olympic Games was hosted in South Korea in January 2018. More than 30% of our 27 reports during Q1 were focused on the region.
Probably one of the most interesting activities relates to Kimsuky, an actor with a North-Korean nexus interested in South Korean think tanks and political activities. The actor renewed its arsenal with a completely new framework designed for cyberespionage, which was used in a spear-phishing campaign against South Korean targets, similar to the one targeting KHNP in 2014. According to McAfee, this activity was related to attacks against companies involved in the organization of the Pyeongchang Olympic Games, however we cannot confirm this.
The Korean focus continues with our analysis of the Flash Player 0-day vulnerability (CVE-2018-4878), deployed by Scarcruft at the end of January and triggered by Microsoft Word documents distributed through at least one website. This vulnerability was quickly reported by the Korean CERT (KN-CERT), which we believe helped to quickly mitigate any aggressive spreading. At the time of our analysis, we could only detect one victim in South Africa.
Forgotten PDB path inside the malware used by Scarcruft with CVE-2018-4876
Furthermore, IronHusky is a Chinese-speaking actor that we first detected in summer 2017. It is very focused on tracking the geopolitical agenda of targets in central Asia with a special focus in Mongolia, which seems to be an unusual target. This actor crafts campaigns for upcoming events of interest. In this case, they prepared and launched one right before a meeting with the International Monetary Fund and the Mongolian government at the end of January 2018. At the same time, they stopped their previous operations targeting Russian military contractors, which speaks volumes about the group’s limitations. In this new campaign, they exploited CVE-2017-11882 to spread common RATs typically used by Chinese-speaking groups, such as PlugX and PoisonIvy.
The final remark for this section covers the apparently never-ending greed of BlueNoroff, which has been moving to new targets among cryptocurrencies companies and expanding its operations to target PoS’s. However, we haven´t observed any new remarkable changes in the modus operandi of the group.
Middle East – always under pressure
There was a remarkable peak in StrongPity’s activity at the beginning of the year, both in January and March. For this new wave of attacks, the group used a new version of its malware that we simply call StrongPity2. However, the most remarkable aspect is the use of MiTM techniques at the ISP level to spread the malware, redirecting legitimate downloads to their artifacts. The group combines this method with registering domains that are similar to the ones used for downloading legitimate software.
StrongPity also distributed FinFisher using the same MiTM method at the ISP level, more details of which were provided by CitizenLab.
Desert Falcons showed a peak of activity at the end of 2017 and the beginning of 2018. Their toolset for this new campaign included Android implants that they had previously used back in 2014. The group continues to heavily rely on social engineering methods for malware distribution, and use rudimentary artifacts for infecting their victims. In this new wave we observed high-profile victims based mostly in Palestine, Egypt, Jordan, Israel, Lebanon and Turkey.
A particularly interesting case we analyzed was the evolution of what we believe to be the Gaza Team actor. What makes us question whether this is the same actor that we have tracked in the past, is the fact that we observed a remarkable boost in the artifacts used by the group. We actually can´t be sure whether the group suddenly developed these new technical capabilities, or if they had some internal reorganization or acquired improved tools. Another possibility is that the group itself was somehow hacked and a third actor is now distributing their artifacts through them.
Final Thoughts
As a summary of what happened during the last 3 months, we have the impression that some well-known actors are rethinking their strategies and reorganizing their teams for future attacks. In addition, a whole new wave of attackers are becoming much more active. For all these new attackers we observe different levels of sophistication, but let´s admit that the entry barrier for cyberespionage is much lower than it used to be in terms of the availability of different tools that can be used for malicious activities. Powershell, for instance, is one of the most common resources used by any of them. In other cases, there seems to be a flourishing industry of malware development behind the authorship of the tools that have been used in several campaigns.
Some of the big stories like Olympic Destroyer teach us what kind of difficulties we will likely find in the future in terms of attribution, while also illustrating how effective supply chain attacks still are. Speaking of new infection vectors, some of the CPU vulnerabilities discovered in the last few months will open new possibilities for attackers; unfortunately there is not an easy, universal protection mechanism for all of them. Routing hardware is already an infection vector for some actors, which should make us think whether we are following all the best practices in protecting such devices.
Operation Parliament, who is doing what?
14.4.2018 Kaspersky CyberSpy
Summary
Kaspersky Lab has been tracking a series of attacks utilizing unknown malware since early 2017. The attacks appear to be geopolitically motivated and target high profile organizations. The objective of the attacks is clearly espionage – they involve gaining access to top legislative, executive and judicial bodies around the world.
The attackers have targeted a large number of organizations globally since early 2017, with the main focus on the Middle East and North Africa (MENA), especially Palestine. High-profile organizations have also been targeted in other regions. The number of attacks has decreased since the beginning of 2018.
The attacks were initially discovered while investigating a phishing attack that targeted political figures in the MENA region. At first the attacks looked to be the work of the low-sophistication Gaza Cybergang (decoys, file names), but further analysis painted a very different picture.
Targets include high-profile entities such as parliaments, senates, top state offices and officials, political science scholars, military and intelligence agencies, ministries, media outlets, research centers, election commissions, Olympic organizations, large trading companies, and other unknown entities.
The malware basically provides a remote CMD/PowerShell terminal for the attackers, enabling them to execute any scripts/commands and receive the result via HTTP requests.
Kaspersky Lab users and Threat Management and Defense clients are protected from the attacks.
Cisco Talos recently published a blogpost describing targeted attacks in the Middle East region which we believe may be connected.
Victimology and Statistics
Based on our findings, we believe the attackers represent a previously unknown geopolitically motivated threat actor. The campaign started in 2017, with the attackers doing just enough to achieve their goals. They most likely have access to additional tools when needed and appear to have access to an elaborate database of contacts in sensitive organizations and personnel worldwide, especially of vulnerable and non-trained staff. The victim systems range from personal desktop or laptop systems to large servers with domain controller roles or similar. The nature of the targeted ministries varied, including those responsible for telecommunications, health, energy, justice, finance and so on.
Victims have been spotted in the Palestinian Territories, Egypt, Jordan, the UAE, Saudi Arabia, Djibouti, Qatar, Lebanon, Chile, Somalia, Iraq, Morocco, Syria, India, Iran, Canada, the USA, the UK, Germany, Israel, Afghanistan, Serbia, Russia, Oman, Kuwait, South Korea and Denmark.
Victim organization type Number of victim organizations
Unknown 91
Senates/Parliaments 7
Prime Ministerial Offices 3
Military/Intelligence Agencies 5
Other Gov./Ministerial/Diplomatic Offices 20
Financial/Banking Institutions 5
Media Outlets 2
Olympic/Sports Bodies 2
Research Centers/Scholars 2
Election Commissions 1
Distribution/Logistics 1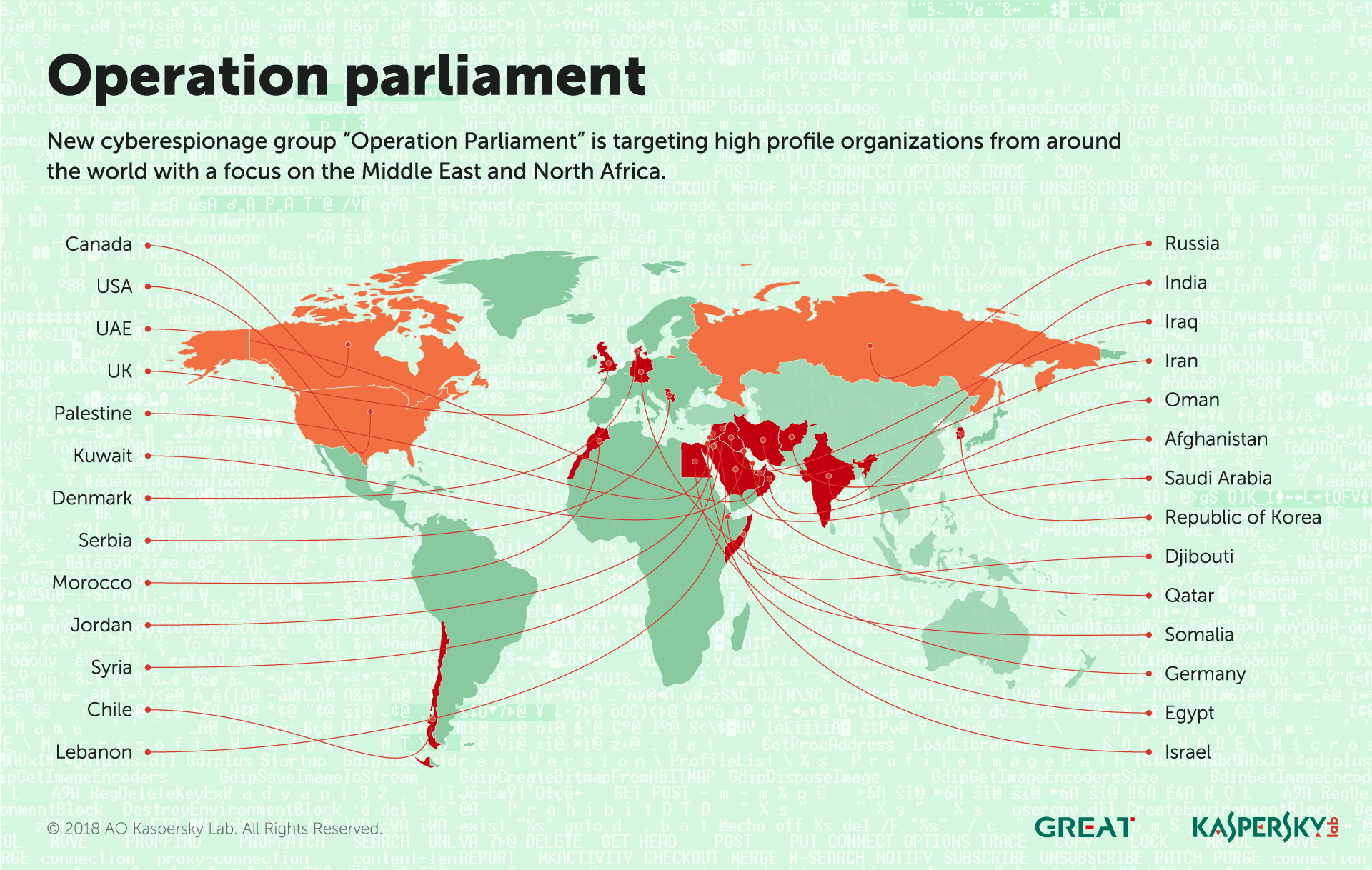
The number of victims/victim organizations probably doesn’t represent the full scope of the attacks – only a portion.
Attack description and attribution
Operation Parliament appears to be another symptom of escalating tensions in the Middle East region. The attackers have taken great care to stay under the radar, imitating another attack group in the region. They have been particularly careful to verify victim devices before proceeding with the infection, safeguarding their command and control servers. The targeting seems to have slowed down since the beginning of 2018, probably winding down when the desired data or access was obtained. The targeting of specific victims is unlike previously seen behavior in regional campaigns by Gaza Cybergang or Desert Falcons and points to an elaborate information-gathering exercise that was carried out before the attacks (physical and/or digital).
With deception and false flags increasingly being employed by threat actors, attribution is a hard and complicated task that requires solid evidence, especially in complex regions such as the Middle East.
See the following for more information and examples of false flags being used in cyberattacks:
Wave your false flags! …or the Nightmares and Nuances of a Self-Aware Attribution Space
OlympicDestroyer is here to trick the industry
Malware description
The malware was first seen packed with VMProtect; when unpacked the sample didn’t show any similarities with previously known malware. All the strings and settings were encrypted and obfuscated. Functionality was identified that enables HTTP communication with the C&C server and invokes “processcreate” based on parameters received as a response.
The configuration and strings are encrypted using 3DES and Base64 encoding. Data sent to the C&C server is also encrypted using 3DES and Base64. Different keys are used for local and network encryption.
The malware starts communicating with the C&C server by sending basic information about the infected machine. The C&C server then replies with the encrypted serialized configuration.
The malware basically provides a remote CMD/PowerShell terminal for the attackers, enabling them to execute scripts/commands and receive the results via HTTP requests.
Sample of the C&C response with encrypted commands and configurations
Examples of attack decoys
Translation: Contacts list of media personnel
Translation: Relations between UAE and Jordan, and the impact caused by the non-boycott of Qatar
Translation: Military retirement statement 2017 June
Translation: The new Hamas structure for Gaza strip 2017
Translation: Clarification report (on Gaza employee salaries)
What should high-profile organizations do?
High-profile organizations should have elevated levels of cybersecurity. Attacks against them are inevitable and are unlikely to ever cease. These organizations need to pay particular attention to their security, implementing additional measures to ensure they are well protected. Anti-targeted attack solutions, threat intelligence capabilities and data flows, default-deny application lockdown, endpoint detection and response, data leak and insider threat prevention, and even isolated/air-gapped networks should form the basis of any strategy for protecting organizations in the current threat landscape.
The victims of Operation Parliament need to re-evaluate their approach to cybersecurity.
Google Turns TLS on By Default on Android P
14.4.2018 securityweek Android
Applications targeting the next version of Android (Android P) are required to use encrypted connections by default, Google said on Thursday.
To keep user data and devices safe, the company is protecting all inbound and outbound data on Android devices with Transport Layer Security (TLS) in transit. Thus, applications on Android P are no longer allowed to use unencrypted connections by default.
This is the latest step the Internet giant has taken to keep Android users better protected, after preventing accidental unencrypted connections on Android (6.0) Marshmallow.
The search company also added the Network Security Config feature to Android (7.0) Nougat, allowing apps to indicate that they do not intend to send network traffic without encryption.
However, Android Nougat and Oreo still allowed cleartext connections, necessary for legacy purposes, such as establishing a connection to an old server.
In Android P, currently available as Developer Preview, TLS is turned on by default, Google says. Applications that already use the protocol for all of their connections won’t be affected by the change, but those that don’t should be updated to use TLS to encrypt communications.
“Android considers all networks potentially hostile and so encrypting traffic should be used at all times, for all connections,” Chad Brubaker, Senior Software Engineer Android Security, notes in a blog post.
He also points out that mobile devices are at risk because they connect to different networks, including public Wi-Fi hotspots.
“All traffic should be encrypted, regardless of content, as any unencrypted connections can be used to inject content, increase attack surface for potentially vulnerable client code, or track the user,” Brubaker says.
To update their applications to use TLS, developers only need to implement the protocol to their servers, and then change all URLs in the app and server responses to HTTPS. When making a socket, devs should use an SSLSocketFactory instead of a SocketFactory, Brubaker points out.
For applications that still require cleartext connections for legacy purposes, changes should be made to the app’s network security configuration to allow such connections.
If the application supports opening arbitrary content from links over insecure connections, the cleartext connections to the developer’s servers should be disabled while they are enabled for arbitrary hosts, Brubaker advises.
Google has been long advocating for the adoption of HTTPS over HTTP and started pushing encrypted pages to the top of search results lists several years ago. Other companies have been pushing for an encrypted Internet as well, including Apple, GitHub, WordPress, and others.