Intel CPUs Vulnerable to New 'BranchScope' Attack
27.3.2018 securityweek Attack
Researchers have discovered a new side-channel attack method that can be launched against devices with Intel processors, and the patches released in response to the Spectre and Meltdown vulnerabilities might not prevent these types of attacks.
The new attack, dubbed BranchScope, has been identified and demonstrated by a team of researchers from the College of William & Mary, University of California Riverside, Carnegie Mellon University in Qatar, and Binghamton University.
Similar to Meltdown and Spectre, BranchScope can be exploited by an attacker to obtain potentially sensitive information they normally would not be able to access directly. The attacker needs to have access to the targeted system and they must be able to execute arbitrary code.
Researchers believe the requirements for such an attack are realistic, making it a serious threat to modern computers, “on par with other side-channel attacks.” The BranchScope attack has been demonstrated on devices with three types of Intel i5 and i7 CPUs based on Skylake, Haswell and Sandy Bridge microarchitectures.
Experts showed that the attack works even if the targeted application is running inside of an Intel SGX enclave. Intel SGX, or Software Guard Extensions, is a hardware-based isolated execution system designed to prevent code and data from getting leaked or modified.
BranchScope is similar to Spectre as they both target the directional branch predictors. Branch prediction units (BPUs) are used to improve the performance of pipelined processors by guessing the execution path of branch instructions. The problem is that when two processes are executed on the same physical CPU core, they share a BPU, potentially allowing a malicious process to manipulate the direction of a branch instruction executed by the targeted application.
The BPU has two main components – a branch target buffer (BTB) and a directional predictor – and manipulating either one of them can be used to obtain potentially sensitive data from the memory. Intel recently published a video providing a high level explanation of how these attacks work.
Researchers showed on several occasions in the past how BTB manipulation can be used for attacks, but BranchScope involves manipulation of branch predictors.
“BranchScope is the first fine-grained attack on the directional branch predictor, expanding our understanding of the side channel vulnerability of the branch prediction unit,” the researchers explained in their paper.
The researchers who identified the BranchScope attack method have proposed a series of countermeasures that include both software- and hardware-based solutions.
Dmitry Evtyushkin, one of the people involved in this research, told SecurityWeek that while they have not been tested, the microcode updates released by Intel in response to Meltdown and Spectre might only fix the BTB vector, which means BranchScope attacks could still be possible. However, Intel told the researchers that software guidance for mitigating Spectre Variant 1 could be effective against BranchScope attacks as well.
BranchScope is not the only CPU side-channel attack method uncovered following the disclosure of Meltdown and Spectre. One of them, dubbed SgxPectre, shows how Spectre can be leveraged to defeat SGX.
Researchers have also demonstrated new variants of the Meltdown and Spectre attacks, which they have named MeltdownPrime and SpectrePrime.
McAfee Enhances Product Portfolio, Unveils New Security Operations Centers
27.3.2018 securityweek Safety
Since emerging from Intel as a standalone cybersecurity company in April 2017, McAfee has consistently made multiple new product announcements simultaneously. It has continued that model this week with a new version of the Enterprise Security Manager (ESM 11), and enhancements to Behavioral Analytics, Investigator, Advanced Threat Defense, and Active Response.
Significantly, it has also unveiled two new security operation centers (SOCs) that combine physical and cybersecurity into the McAfee Security Fusion Centers, located in Plano, Texas and Cork, Ireland. This is McAfee using its own products for its own organization: McAfee 'eating its own dog food' as its own Customer Zero.
McAfee LogoThe SOCs have a triple purpose -- to protect McAfee; to use McAfee products in a live scenario to provide practical feedback to the developers; and to provide an educational environment for customers to see McAfee SOC products in live action rather than choreographed simulation. The 'practical feedback' also provides an illustration of a key principle in McAfee's product philosophy: man and machine integration, each learning from and benefiting the other.
"The big deal for the McAfee Security Fusion Centers," writes McAfee CISO Grant Bourzikas in an associated blog, "is that they have a dual mission: 1) to protect McAfee, and; 2) help us build better products. And for myself, I would add a third objective: help our customers to learn from our experiences protecting McAfee. We want to help them build better reference architectures, learn how to communicate with boards of directors and become more innovative in solving cybersecurity problems." The Fusion Centers also, of course, demonstrate McAfee's faith in its own products.
The new ESM 11 architecture shares large volumes of raw, parsed and correlated security events to allow threat hunters to quickly search recent events, while storing the data for future forensic and compliance requirements. The architecture is horizontally scalable with active/active availability through the addition of extra ESM appliances or virtual machines.
Behavioral Analytics provides machine learning technology to discover high risk events that might otherwise be missed by human hunters. It distills billions of events down to hundreds of anomalies and then to 'a handful of prioritized threat leads' -- highlighting the signal in the noise -- and integrating with the McAfee product portfolio and other third-party SIEMs.
Investigator shares data with open source and third-party tools to streamline workflows and improve collaboration.
Active Response has been enhanced by integration with Investigator to help analysts scope the impact of a threat across endpoints in real-time. Integration with Advanced Threat Protection also allows analysts to view sandbox reports and IoCs from a single workspace; while allowing the detection of PowerShell exploits and their remediation by isolating any affected host.
"Existing tools and approaches are too reliant on human expertise" says Jason Rolleston, VP of security analytics, commenting on the product announcements. "The answer is human-machine teaming, where analytics- and machine learning-powered solutions augment the security team to detect more threats, faster and with fewer people."
ESM 11 and Behavioral Analytics are available now. Investigator will be available in April, and the enhancements to Advanced Threat Defense and Active Response will be available in May.
Grey Heron, the new Co in the surveillance industry that promises to spy on Signal and Telegram
27.3.2018 securityaffairs Hacker techniques
Who is behind the newborn Grey Heron surveillance company? According to an investigation conducted by Motherboard, the firm is linked to the Italian surveillance firm Hacking Team.
The development and sale of surveillance software is a profitable business, many government agencies use spyware for different purposes, in some their involvement is very questionable.
Early this month, the journalist Joseph Cox from Motherboard wrote an interesting post on a mysterious surveillance firm called Grey Heron.
The company was advertising a spyware that is able to spy on Signal and Telegram communications.
The name Grey Heron was unknown also among the security community, but the investigation conducted by Motherboard linked the company to the controversial Italian surveillance firm Hacking Team,
Motherboard obtained a brochure of the company that uses the following statement to describe its mission:
“Grey Heron’s mission is to provide to law enforcement the strong tools to balance the capabilities of those who wish to do harm,”

Source Motherboard
According to a source familiar with the company, Grey Heron was formed from several players surveillance industry.
In 2015, the company suffered a major data breach, the hacker known as Phineas Fisher exfiltrated more than 400 gigabytes of internal data from company servers.
The hackers stole company’s emails, customer records, and the source code for hacking tools and exploits.
In 2017, the company was bought by an entity linked to the Saudi Government bought.
A new post written by Joseph Cox along with the colleague Lorenzo Franceschi-Bicchierai, cited a former Hacking Team employee, who speaking on condition of anonymity, confirmed the link between Hacking Team and Grey Heron.
“[it would] make sense to use a different name to continue to sell to those clients who weren’t happy after the hack.” said the former employee.
“Except those customers who don’t care because they buy spyware without thinking twice,” “I imagine that there’s a lot of them who don’t see Hacking Team favorably anymore, including the reselling partners, perhaps even more so than the final customers.”
The interesting news is that Grey Heron has confirmed privately that the Italian Government has given it the permission to export its products throughout the European Union.
Grey Heron is looking with great interest at both the European and North American markets.
Experts uncovered a watering hole attack on leading Hong Kong Telecom Site exploiting CVE-2018-4878 flaw
27.3.2018 securityaffairs Vulnerebility
Researchers at Morphisec have uncovered a watering hole attack on leading Hong Kong Telecom website exploiting the CVE-2018-4878 flash vulnerability.
Security experts at Morphisec have discovered a watering hole attack on leading Hong Kong Telecom website exploiting the CVE-2018-4878 flash vulnerability.
In a watering hole attack, hackers infect the websites likely to be visited by their targeted victims, this technique requires more effort than common spear-phishing attack and it is usually associated with APT groups.

Early February, Adobe rolled out an emergency patch that fixed two critical remote execution vulnerabilities, including the CVE-2018-4878, after North Korea’s APT group was spotted exploiting it in targeted attacks.
At the time, South Korea’s Internet & Security Agency (KISA) warned of a Flash zero-day vulnerability (CVE-2018-4878) that has reportedly been exploited in attacks by North Korea’s hackers.
By the end of February, the researchers at Morphisec reported that threat actors were exploiting the use-after-free flaw to deliver malware.
“On March 21,2018, Morphisec Labs began investigating the compromised website of a leading Hong Kong Telecommunications company after being alerted to it by malware hunter @PhysicalDrive0.” reads the analysis published by Morphisec.
“The investigation, conducted by Morphisec researchers Michael Gorelik and Assaf Kachlon, determined that the Telecom group’s corporate site had indeed been hacked. Attackers added an embedded Adobe Flash file that exploits the Flash vulnerability CVE-2018-4878 on the main home.php page. The attack is a textbook case of a watering hole attack.”
Threat actors behind the attack uncovered by the experts adopted advanced evasive techniques, they used a purely fileless malicious code, without persistence or any trace on the disk. It is interesting to note also the usage of a custom protocol over the 443 port.
The Flash exploit used in this attack was similar to the one involved in the attacks involving the CVE-2018-4878 vulnerability, but it employs a different shellcode executed post exploitation.
“Generally, this advanced type of watering hole attack is highly targeted in nature and suggests that a very advanced group is behind it,” continues the post.
“The Flash exploit that was delivered has a high degree of similarity to the previously published analysis of the CVE-2018-4878. The major difference in this exploit is in the shellcode that is executed post exploitation”
The shellcode executes rundll32.exe and overwrites the content of the memory with a malicious code that was designed to download additional code directly into the memory of the rundll32 process.
The additional code downloaded directly into the memory of the rundll32 process includes Metasploit Meterpreter and Mimikatz modules.
The analysis of the modules revealed that were compiled on February 15, a few days before the attack.
“As our analysis shows, this watering hole attack is of advanced evasive nature. Being purely fileless, without persistence or any trace on the disk, and the use of custom protocol on a non-filtered port, makes it a perfect stepping stone for a highly targeted attack chain. This clearly suggests that very advanced threat actors are responsible for it,” Morphisec says.
The experts noticed that despite the advanced evasive features, the attack used basic Metasploit framework components that were compiled just before the attack and did not show any sophistication, obfuscation or evasion.
At this time, the company hasn’t attributed the attack to a specific threat actor, it is still investigating the incident.
Canadian Firm Linked to Cambridge Analytica Exposed Source Code
27.3.2018 securityweek Social
Source code belonging to Canada-based digital advertising and software development company AggregateIQ has been found by researchers on an unprotected domain. The exposed files appear to confirm reports of a connection between AggregateIQ and Cambridge Analytica, the controversial firm caught in the recent Facebook data scandal.
On March 20, Chris Vickery of cyber risk company UpGuard stumbled upon an AggregateIQ subdomain hosting source code for the company’s tools. The files, stored using a custom version of the code repository GitLab, were accessible simply by providing an email address.
The exposed information included the source code of tools designed for organizing information on a large number of individuals, including how they are influenced by ads, and tracking their online activities. The files also contained credentials that may have allowed malicious actors to launch damaging attacks, UpGuard said.
The nature of the exposed code is not surprising considering that the firm is said to have developed tools used in political campaigns around the world, including in the United States and United Kingdom.
AggregateIQ has been linked by the press and a whistleblower to Cambridge Analytica, a British political consulting and communications firm said to be involved in the presidential campaigns of Donald Trump and Ted Cruz, and the Brexit “Vote Leave” campaign.
Cambridge Analytica recently came under fire after it was discovered that it had collected information from 50 million Facebook users' profiles and used it to create software designed to predict and influence voters. Facebook has suspended the company’s account after news broke, but the social media giant has drawn a lot of criticism, both from customers and authorities.
According to some reports, AggregateIQ was originally launched with the goal of helping Cambridge Analytica and its parent company SCL Group. In a statement published on its website over the weekend, AggregateIQ denied reports that it’s part of Cambridge Analytica or SCL. It has also denied signing any contracts with the British firm and being involved in any illegal activity.
However, there appears to be some evidence that Cambridge Analytica owns AggregateIQ’s intellectual property, and the files discovered by UpGuard also seem to show a connection.
For example, two of the AggregateIQ projects whose source code was exposed contained the string “Ripon,” which is the name of Cambridge Analytica’s platform. The code also included a piece of text that may have been used in phone calls made by Ted Cruz supporters during his presidential campaign.
Researchers also noticed that one of the user accounts mentioned in the exposed files was named “SCL,” which could be a reference to Cambridge Analytica’s parent company.
“Taken in full, it remains unclear why what resembles a version of the app Cambridge Analytica promised would be ‘revolutionary’ for the Cruz campaign would be found in the development repository of AggregateIQ,” said UpGuard, which plans on publishing follow-up reports on this story.
FTC to Probe Facebook Over Privacy Practices
27.3.2018 securityweek Social
A US consumer protection agency said Monday it has opened an investigation into Facebook's privacy practices, another blow to the social network, which is struggling to deal with a growing crisis on misuse of private data.
The Federal Trade Commission (FTC) confirmed news reports from last week that it had opened an inquiry over the harvesting of data on tens of millions of Facebook users by the British consulting group Cambridge Analytica.
While the FTC normally refuses to comment on its probes, it took the unusual step of confirming a "non-public investigation" into Facebook over whether it mishandled private data or violated a 2011 agreement which settled an earlier probe.
Acting FTC consumer protection chief Tom Pahl said the agency will look into whether Facebook violated its privacy promises or failed to comply with the US-EU agreement on data protection known as the Privacy Shield.
The agency also will also determine if Facebook engaged "in unfair acts that cause substantial injury to consumers in violation of the FTC Act."
The FTC suggested that Facebook could face new legal problems if it violated the consent decree with the consumer agency in 2011 settling charges that it deceived consumers on how it handled private data.
"Companies who have settled previous FTC actions must also comply with FTC order provisions imposing privacy and data security requirements," Pahl said in the statement.
"Accordingly, the FTC takes very seriously recent press reports raising substantial concerns about the privacy practices of Facebook."
Facebook shares reversed early losses and closed up 0.42 percent on Monday, after having lost some 14 percent last week.
Separately, Senate Judiciary Committee chairman Charles Grassley said he had asked Facebook CEO Mark Zuckerberg to appear at a hearing on April 10 "to discuss Facebook's past and future policies regarding the protection and monitoring of consumer data."
Grassley said he also invited Google CEO Sundar Pichai and Twitter CEO Jack Dorsey "to discuss the future of data privacy in the social media industry."
- Germany to boost oversight -
Germany's justice minister meanwhile said Monday that Facebook should face "stricter" oversight and be more transparent with its users.
Speaking after a meeting with European Facebook executives in Berlin, Justice Minister Katarina Barley said the firm's assurances that it had already cracked down on the misuse of personal data were "not enough."
"In future we will clearly have to monitor companies like Facebook more strictly and punish data protection violations severely and quickly," she told reporters.
The world's biggest social network is facing calls on both sides of the Atlantic for more information on how its user data was leaked. Several US states have opened investigations.
A public apology by Zuckerberg has failed to quell outrage over the hijacking of personal data.
Separately, Facebook disputed reports that it had been logging call and text data surreptitiously from its users.
A Facebook statement said call and text history logging "is part of an opt-in feature" for those using Messenger or Facebook Lite on Android.
"This helps you find and stay connected with the people you care about, and provides you with a better experience across Facebook," the statement said, while pointing to ways users can turn off the feature.
In London, authorities said they were assessing data seized in a raid on the offices of Cambridge Analytica as part of their investigation.
About 18 enforcement agents from the Information Commissioner's Office participated in the raid late Friday after getting a court order.
"This is one part of a larger investigation by the ICO into the use of personal data and analytics by political campaigns, parties, social media companies and other commercial actors," the UK agency said.
Cambridge Analytica, which worked on US President Donald Trump's election campaign, has been accused of illegally mining tens of millions of users' Facebook data and using it to target potential voters.
Facebook took out full-page ads in nine major British and US newspapers on Sunday to apologize to users.
"We have a responsibility to protect your information. If we can't we don't deserve it," Zuckerberg said in the ads.
GoScanSSH Malware spread avoiding Government and Military networks
27.3.2018 securityaffairs BigBrothers
Security experts at Cisco Talos discovered a new piece of malware dubbed GoScanSSH that was being used to compromise SSH servers exposed online.
Security researchers at Cisco Talos have discovered a new piece of malware dubbed GoScanSSH that was being used to compromise SSH servers exposed online.
The malicious code was written in Go programming language, uncommon for malware development, and implements several interesting features, for example, it tries to avoid infecting devices on government and military networks.
“Talos identified a new malware family that was being used to compromise SSH servers exposed to the internet. This malware, which we have named GoScanSSH, was written using the Go programming language, and exhibited several interesting characteristics.” reads the analysis published by Talos.
The attacker created unique malware binaries for each infected system, researchers also reported that the GoScanSSH command and control (C2) infrastructure was leveraging the Tor2Web proxy service making hard the tracking of the C&C infrastructure and resilient to takedowns.
GoScanSSH conducted brute-force attack against publicly accessible SSH servers that allowed password-based SSH authentication. The hackers are leveraging a word list containing more than 7,000 username/password combinations. When GoScanSSH discovered a valid credential set, a unique GoScanSSH malware binary is then created and uploaded to the compromised SSH server and executed.
While scanning for vulnerable SSH servers, GoScanSSH randomly generates IP addresses, avoiding special-use addresses. the malware then compares each IP address to a list of CIDR blocks that the malicious code will not attempt to scan because they are network ranges primarily controlled by various government and military entities.
The malware specifically avoids ranges assigned to the U.S. Department of Defense, experts also noticed that one of the network ranges in the list is assigned to an organization in South Korea.
The researchers detected more than 70 unique malware samples associated with the GoScanSSH malware family, the experts observed samples that were compiled to support multiple system architectures including x86, x86_64, ARM and MIPS64.
The experts also observed multiple versions (e.g, versions 1.2.2, 1.2.4, 1.3.0, etc.) of the malware in the wild, a circumstance that suggests the threat actors behind the malicious code is continuing to improve the malware.

According to the researchers, threat actors are likely trying to compromise larger networks, experts believe attackers are well resourced and with significant skills.
They are being active since June 2017 and already deployed 70 different versions of the GoScanSSH malware using over 250 distinct C&C servers.
The analysis of passive DNS data related to all of the C2 domains collected from all of the samples Talos analyzed confirmed that the number of infected systems is low.
“In analyzing passive DNS data related to all of the C2 domains collected from all of the samples Talos analyzed, resolution attempts were seen dating back to June 19, 2017, indicating that this attack campaign has been ongoing for at least nine months. Additionally, the C2 domain with the largest number of resolution requests had been seen 8,579 times.” states the analysis published by Talos.
Further details on the GoScanSSH malware, including IoCs, are reported in the analysis published by Talos.
Statistics Say Don't Pay the Ransom; but Cleanup and Recovery Remains Costly
27.3.2018 securityweek Ransomware
Businesses have lost faith in the ability of traditional anti-virus products to detect and prevent ransomware. Fifty-three percent of U.S companies infected by ransomware in 2017 blamed legacy AV for failing to detect the ransomware. Ninety six percent of those are now confident that they can prevent future attacks, and 68% say this is because they have replaced legacy AV with next-gen endpoint protection.
Thes details come from a February 2018 survey undertaken by Vanson Bourne for SentinelOne, a next-gen provider, allowing SentinelOne to claim, "This distrust in legacy AV further confirms the required shift to next-gen endpoint protection in defending against today's most prominent information security threats." This is a fair statement, but care should be taken to not automatically confuse 'legacy AV' with all traditional suppliers -- many can also now be called next-gen providers with their own flavors of AI-assisted malware detection.
SentinelOne's Global Ransomware Report 2018 (PDF) questioned 500 security and risk professionals (200 in the U.S., and 100 in each of France, Germany and the UK) employed in a range of verticals and different company sizes.
The result provides evidence that paying a ransom is not necessarily a solution to ransomware. Forty-five percent of U.S. companies infected with ransomware paid at least one ransom, but only 26% had their files unlocked. Furthermore, 73% of those firms that paid the ransom were targeted at least once again. Noticeably, while defending against ransomware is a security function, responding to it is a business function: 44% of companies that paid up did so without the involvement or sanction of the IT/security teams.
The attackers appear to have concluded that U.S. firms are the more likely to pay a ransom, and more likely to pay a higher ransom. While the global average ransom is $49,060, the average paid by U.S. companies was $57,088. "If the cost of paying the ransomware is less than the lost productivity caused by downtime from the attack, they tend to pay," SentinelOne's director of product management, Migo Kedem, told SecurityWeek. "This is not good news, as it means the economics behind ransomware campaigns still make sense, so attacks will continue."
This is in stark contrast to the UK, where the average payment is almost $20,000 lower at $38,500. It is tempting to wonder if this is because UK companies just don't pay ransoms. In 2016, 17% of infected UK firms paid up; now it is just 3%. This may reflect the slightly different approaches in law enforcement advice. While LEAs always say it is best not to pay, the UK's NCSC says flatly, 'do not pay', while the FBI admits that it is ultimately the decision of each company.
Paying or not paying, is, however, only a small part of the cost equation; and the UK's Office for National Statistics (ONS) provides useful figures. According the SentinelOne, these figures show that in a 12-month period, the average cost of a ransomware infection to a UK business was £329,976 ($466,727). With 40% of businesses with more than 1000 employees being infected, and 2,625 such organizations in the UK, the total cost of ransomware to UK business in 12 months was £346.4 million ($490.3 million).
Clearly, although the number of UK companies actually paying the ransom is low, the cost of cleanup and recovery remains very high; making prevention a more important consideration than whether to pay or not.
"Attackers are continually refining ransomware attacks to bypass legacy AV and to trick unwitting employees into infecting their organization. Paying the ransom isn't a solution either -- attackers are treating paying companies like an ATM, repeating attacks once payment is made," said Raj Rajamani, SentinelOne VP of products. "The organizations with the most confidence in stopping ransomware attacks have taken a proactive approach and replaced legacy AV systems with next-gen endpoint protection. By autonomously monitoring for attack behaviors in real-time, organizations can detect and automatically stop attacks before they take hold."
In 2016, SentinelOne began to offer a ransomware guarantee . "We're proud to have been the first," said chief security consultant Tony Rowan (now lead security architect at Cyberbit), "and still only, next generation endpoint protection company to launch a cyber security guarantee with our $1,000 per endpoint, or $1 million per company pay out in the event they experience a ransomware attack after installing our product."
"We offered that program for the last two years and I am glad to share we were never required to pay," Kedem told SecurityWeek. "SentinelOne products successfully protected our customers against even the WannaCry campaign that hit the UK pretty hard."
Mountain View, Calif-based SentinelOne raised $70 million in a Series C funding round announced in January 2017, bringing the total amount of funding to $109.5 million.
Axonius Uses Existing Tools to Find, Secure Devices
27.3.2018 securityweek Safety
Axonius emerged from stealth mode on Tuesday with a platform designed to help organizations identify and secure all the devices on their network by leveraging existing security and management tools.
The company aims to bridge the gap between device discovery and vulnerability assessment products with a solution that combines data from existing tools in an effort to provide a centralized view of all devices and help enterprises ensure that all their systems are patched.
Vulnerability assessment tools may be efficient in identifying and prioritizing systems that need patching, but they often don’t have access to all devices due to the fragmented nature of corporate environments.
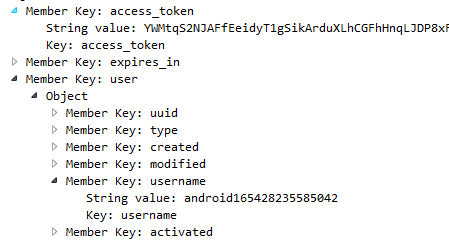
Axonius says its Cybersecurity Asset Management Platform can leverage combinations of nearly 30 tools from various vendors in order to discover all the devices on a network, obtain information about those systems, and ensure that they are not neglected by vulnerability scanners.Axonius emerges from stealth mode
The company has created what it calls “adapters” to integrate tools from Microsoft, Amazon, Cisco, enSilo, ESET, Forcepoint, Fortinet, IBM, Juniper, McAfee, ManageEngine, Qualys, Rapid7, Splunk, Symantec, VMware and others into its platform.
New adapters will be added in the future based on customers’ needs – the company is currently working on integrating tools from Carbon Black, Cylance, ObserveIT, CrowdStrike and others. Adding new adapters is in most cases an easy task given that most vendors provide APIs.
The company told SecurityWeek that it’s unlikely for an organization that has a problem with fragmentation and visibility not to have at least some of the supported tools – for example, Microsoft’s Active Directory can be found in most companies.
Security teams can manually query devices to ensure that they adhere to their organization’s policies, but they can also configure the platform to automatically alert them via email or syslog whenever a device that fits specified criteria is detected.
In addition to helping organizations gain full visibility into the devices on their network, Axonius says its platform can also be used to enforce policies. Employees can manually choose to either block a device, scan it, or deploy an agent, but they can also automate various tasks using plugins.
Since it does not require the deployment of an agent, Axonius says its platform can be deployed quickly and easily once it has access to all the credentials and third-party tools. The company claims it has deployed its solution in an afternoon at an organization with roughly 10,000 endpoints, and the job has never taken more than a couple of days.
“Since we do connect to the security and management systems a customer already has, there's no custom work to do, no professional services, and we're able to start showing value immediately,” Nathan Burke, CMO of Axonius, told SecurityWeek. “At most organizations, security teams are swamped and time is their scarcest resource. The last thing they want to do is spend time on a lengthy and complicated deployment.”
Deploying the solution only requires a VMware ESXi machine that has inbound and outbound access to all managed adapters. Pricing for the product is based on an annual subscription and it depends on the number of devices.
Axonius’ headquarters is in New York and its research and development department is located in Israel. The company received $4 million in seed funding in September 2017 and it has now announced the general availability of its product, which it claims is already used by very large companies around the world to manage more than 100,000 endpoints.
The Top Vulnerabilities Exploited by Cybercriminals
27.3.2018 securityweek Vulnerebility
Cybercriminals are shifting their focus from Adobe to Microsoft consumer products, and are now concentrating more on targeted attacks than on web-based exploit kits.
Each year, Recorded Future provides an analysis of criminal chatter on the dark web in its Top Ten Vulnerabilities Report. It does this because it perceives a weakness in traditional vulnerability databases and scanning tools -- they do not indicate which vulnerabilities are currently being exploited, nor to what extent. Reliance on vulnerability lists alone cannot say where patching and remediation efforts should be prioritized.
"We do this analysis because the sale and use of exploits is a for-profit industry," Recorded Future's VP of technical solutions, Scott Donnelly told SecurityWeek. This means that exploit developers have to sell their products, while other criminals have to buy them -- and this leads to the chatter that Recorded Future analyzes.
"If you're a cybercriminal trying to make money, you have to discuss it. If you hold back too much you're not going to make any money; so, there's a necessity for the criminals to stick their heads up a little bit -- and we can take advantage of that and call out some of the big conversations." It assumes a correlation between chatter about a vulnerability with active exploitation of that vulnerability -- an assumption that common sense rather than science suggests is reasonable.
Donnelly is confident that his firm's knowledge of and access to the dark web is statistically valid. Nation-state activity is specifically excluded from this analysis, because, he says, "If you're a nation-state with an exploit, or if you're a third-party supplier of exploits to a nation state, you're less likely to talk about it in a general criminal forum."
At the macro level, this year's analysis highlights a move away from Adobe vulnerabilities towards Microsoft consumer product vulnerabilities. While Flash exploits have dominated earlier annual reports, seven of the top ten (including the top five) most discussed vulnerabilities are now Microsoft vulnerabilities. "As Adobe Flash Player has begun to see its usage significantly drop, this year we find that it's a lot of Microsoft consumer products that are seeing heavy exploitation," says Donnelly.
The three most used vulnerabilities are CVE-2017-0199 (which allows attackers to download and execute a Visual Basic script containing PowerShell commands from a malicious document), CVE-2016-0189 (which is an old Internet Explorer vulnerability that allows attackers to use an exploit kit to drop malware, such as ransomware), and CVE-2017-0022 (which enables data theft).
A second major takeaway from the analysis is that 2017 has seen a significant drop in the development of new exploit kits. "This has been noticed before," Donnelly told SecurityWeek, "but mainly because researchers simply haven't seen them in action. This is now evidence that the criminals themselves aren't talking about or trying to sell that many new kits."
In raw numbers, Recorded Future's analysis noted 26 new kits in 2016, but only 10 new kits in 2017 (from a total list of 158 EKs). "The observed drop in exploit kit activity," suggests Donnelly, "overlaps with the rapid decline of Flash Player usage. Users have shifted to more secure browsers, and attackers have shifted as well. Spikes in cryptocurrency mining malware and more targeted victim attacks have filled the void."
At the micro level, the big takeaway from this report is the anomalous position of CVE-2017-0022. It is the third most discussed vulnerability on the dark web forums, yet in relation to just two pieces of malware: exploit kits Astrum (aka Stegano) and Neutrino. This is the lowest number of associated malware in the top ten vulnerabilities -- both of the two more popular vulnerabilities are associated with ten different peices of malware. CVE-2017-0199 is associated with malware including Hancitor, Dridex and FinFisher, while CVE-2016-0189 is associated with nine different exploit kits and the Magniber ransomware.
But it's not just in malware associations that CVE-2017-0022 is anomalous. It has a Common Vulnerability Scoring System (CVSS) rating of just 4.3. The next lowest rating in the top ten vulnerabilities is 7.6, while the top two are rated at 9.3 and 7.6. CVSS defines a 4.3 score as medium risk; and yet Recorded Future's research shows it to be the third most exploited vulnerability, commenting, "'In the wild' severity does not always correlate with the Common Vulnerability Scoring System (CVSS) score."
This is a prime example of the reason for the analysis. Security teams could check the CVSS score and conclude on this evidence alone that the vulnerability does not require expedited remediation or patching. As the third most exploited vulnerability, Recorded Future's latest threat analysis suggests otherwise.
Boston, Mass.-based Recorded Future raised $25 million in a Series E funding round led by Insight Venture Partners in October 2017 -- bringing the total funding raised to $57.9 million.
New "ThreadKit" Office Exploit Builder Emerges
27.3.2018 securityweek Vulnerebility
A newly discovered Microsoft Office document exploit builder kit has been used for the distribution of a variety of malicious payloads, including banking Trojans and backdoors, Proofpoint reports.
The exploit builder kit was initially discovered in October 2017, but Proofpoint's researchers have linked it to activity dating back to June 2017. The builder kit shows similarities to Microsoft Word Intruder (MWI), but is a new tool called ThreadKit.
In June 2017, the kit was being advertised in a forum post as being able to create documents with embedded executables and embedded decoy documents, and several campaigns featuring such documents were observed that month. The documents would perform an initial check-in to the command and control (C&C) server, a tactic also used by MWI.
The documents were targeting CVE-2017-0199 and were focused on downloading and executing a HTA file that would then download the decoy and a malicious VB script to extract and run the embedded executable. The payload was Smoke Loader, which in turn downloaded banking malware.
In October, ThreadKit started targeting CVE 2017-8759 as well, but continued to use the initial C&C check-in and the HTA file to execute the embedded executable, Proofpoint says. However, changes were made to the manner in which the exploit documents operate and new exploits were integrated as well.
In November, ThreadKit was quick to incorporate exploits for new Microsoft Office vulnerabilities, and started being advertised as capable of targeting CVE 2017-11882 too. Soon after, campaigns that featured the previously observed check-in already started to emerge.
In February and March 2018, the kit was embedding new exploits, targeting vulnerabilities such as an Adobe Flash zero-day (CVE-2018-4878) and several new Microsoft office vulnerabilities, including CVE-2018-0802 and CVE-2017-8570.
At the same time, the researchers noticed a large spike in email campaigns featuring ThreadKit-generated Office attachments packing these exploits. The exploits appear copied from proofs of concept available on a researcher’s GitHub repo.
As part of these attacks, the attachments would drop the contained packager objects into the temp folder, then the exploits would execute the dropped scriptlet file, thus leading to the execution of the dropped batch files, which in turn run the executable.
Proofpoint found that not all ThreadKit documents contain a valid URL for the statistics check-in (some contain placeholder URLs). Furthermore, not all documents followed the same execution chain, with some scripts modified to perform other actions, a customization that may be provided as a service by the kit author.
“In 2017, several new vulnerabilities entered regular use by threat actors and the first months of 2018 have added to that repertoire. Document exploit builder kits like ThreadKit enable even low-skilled threat actors to take advantage of the latest vulnerabilities to distribute malware. Organizations and individuals can mitigate the risk from ThreadKit and other document exploit-based attacks by ensuring that clients are patched for the latest vulnerabilities in Microsoft office and other applications,” Proofpoint concludes.
First OpenSSL Updates in 2018 Patch Three Flaws
27.3.2018 securityweek Vulnerebility
The first round of security updates released in 2018 for OpenSSL patch a total of three vulnerabilities, but none of them appears to be serious.
OpenSSL versions 1.1.0h and 1.0.2o patch CVE-2018-0739, a denial-of-service (DoS) vulnerability discovered using Google’s OSS-Fuzz service, which has helped find several flaws in OpenSSL in the past period.
The security hole, rated “moderate,” is related to constructed ASN.1 types with a recursive definition.
“Constructed ASN.1 types with a recursive definition (such as can be found in PKCS7) could eventually exceed the stack given malicious input with excessive recursion,” the OpenSSL Project said in its advisory.
Another moderate severity flaw, which only affects the 1.1.0 branch, is CVE-2018-0733. This is an implementation bug in the PA-RISC CRYPTO_memcmp function, and it allows an attacker to forge authenticated messages easier than it should be.
The OpenSSL Project learned about this vulnerability in early March from IBM. Only HP-UX PA-RISC systems are impacted.
Finally, OpenSSL 1.1.0h fixes an overflow bug that could allow an attacker to access TLS-protected communications. The vulnerability, CVE-2017-3738, was first disclosed in December 2017, but since an attack is not easy to carry out the issue has been assigned a low severity rating and it has only been patched now.
Four rounds of security updates were released for OpenSSL last year, and only one of the eight fixed vulnerabilities was classified as high severity.
Threat Landscape for Industrial Automation Systems in H2 2017
27.3.2018 Kaspersky Analysis ICS
For many years, Kaspersky Lab experts have been uncovering and researching cyberthreats that target a variety of information systems – those of commercial and government organizations, banks, telecoms operators, industrial enterprises, and individual users. In this report, Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) publishes the findings of its research on the threat landscape for industrial automation systems conducted during the second half of 2017.
The main objective of these publications is to provide information support to global and local incident response teams, enterprise information security staff and researchers in the area of industrial facility security.
Overview of ICS vulnerabilities identified in 2017
The analysis of vulnerabilities was performed based on vendor advisories, publicly available information from open vulnerability databases (ICS-CERT, CVE, Siemens Product CERT), as well as the results of Kaspersky Lab ICS CERT’s own research. Vulnerability data published on the ICS-CERT website in 2017 was used to create statistical diagrams.
Vulnerabilities in various ICS components
Number of vulnerabilities identified
In 2017, the total number of vulnerabilities identified in different ICS components and published on the ICS-CERT website was 322. This includes vulnerabilities identified in general-purpose software and in network protocols that are also relevant to industrial software and equipment. These vulnerabilities are discussed in this report separately.
Analysis by Industry
The largest number of vulnerabilities affect industrial control systems in the energy sector (178), manufacturing processes at various enterprises (164), water supply (97) and transportation (74).
Number of vulnerable products used in different industries
(according to ICS-CERT classification)
vulnerabilities published in 2017
Severity levels of the vulnerabilities identified
More than half (194) of the vulnerabilities identified in ICS systems were assigned CVSS v.3.0 base scores of 7 or higher, corresponding to a high or critical level of risk.
Table 1 – Distribution of published vulnerabilities by risk level
Severity score
9 to 10 (critical) 7 to 8.9 (high) 4 to 6.9 (medium) 0 to 3.9 (low)
Number of vulnerabilities 60 134 127 1
The highest severity score of 10 was assigned to vulnerabilities identified in the following products:
iniNet Solutions GmbH SCADA Webserver,
Westermo MRD-305-DIN, MRD-315, MRD-355, and MRD-455,
Hikvision Cameras,
Sierra Wireless AirLink Raven XE and XT,
Schneider Electric Modicon M221 PLCs and SoMachine Basic,
BINOM3 Electric Power Quality Meter,
Carlo Gavazzi VMU-C EM and VMU-C PV.
All vulnerabilities that were assigned the severity rating of 10 have much in common: they have to do with authentication issues, can be exploited remotely and are easy to exploit.
In addition, the highest severity rating was assigned to a vulnerability in the Modicon Modbus Protocol, which is discussed below.
It should be noted that the CVSS base score does not account for the aspects of security that are specific to industrial automation systems or for the distinctive characteristics of each organization’s industrial processes. This is why, when assessing the severity of a vulnerability, we recommend keeping in mind, in addition to the CVSS score, the possible consequences of its exploitation, such as the non-availability or limited availability of ICS functionality that affects the continuity of the industrial process.
Types of vulnerabilities identified
The most common types of vulnerabilities include buffer overflow (Stack-Based Buffer Overflow, Heap-Based Buffer Overflow) and improper authentication (Improper Authentication).
At the same time, 23% of all vulnerabilities identified are web-related (Injection, Path Traversal, Cross-Site Request Forgery (CSRF), Cross-Site Scripting) and 21% are associated with authentication issues (Improper Authentication, Authentication Bypass, Missing Authentication for Critical Function) and with access control problems (Access Control, Incorrect Default Permissions, Improper Privilege Management, Credentials Management).
Most common vulnerability types
Exploitation of vulnerabilities in various ICS components by attackers can lead to arbitrary code execution, unauthorized control of industrial equipment and that equipment’s denial of service (DoS). Importantly, most vulnerabilities (265) can be exploited remotely without authentication and exploiting them does not require the attacker to have any specialized knowledge or superior skills.
Exploits have been published for 17 vulnerabilities, increasing the risk of their exploitation for malicious purposes.
Vulnerable ICS components
The largest number of vulnerabilities were identified in:
SCADA/HMI components (88),
networking devices designed for industrial environments (66),
PLCs (52),
and engineering software (52).
Vulnerable components also include protection relays, emergency shutdown systems, environmental monitoring systems and industrial video surveillance systems.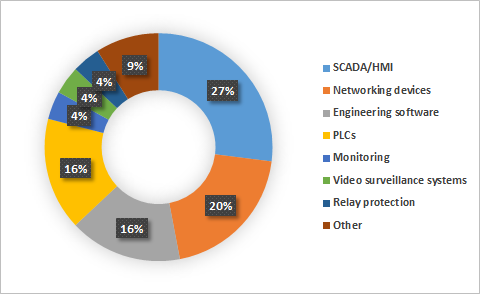
Distribution of vulnerabilities identified by ICS components
Vulnerabilities in industrial protocols
An important part of ICS software security research in 2017 was identifying serious vulnerabilities in implementations of industrial protocols. Specifically, vulnerabilities were identified in the implementation of the Modbus Protocol in Modicon series controllers (that vulnerability was assigned a CVSS v. 3 base score of 10), as well as in implementations of the OPC UA protocol stack and in an implementation of the PROFINET Discovery and Configuration Protocol. The security issues identified affect entire product families.
Impact of vulnerabilities in ‘traditional’ technologies on industrial systems
In addition to ICS-specific vulnerabilities, a number of serious flaws were identified in H2 2017 in software platforms and network protocols that can be exploited to attack industrial systems.
The vulnerabilities in the WPA2 protocol unexpectedly turned out to be relevant to industrial solutions. They were found to affect equipment from several vendors, including Cisco, Rockwell Automation, Sierra Wireless, ABB and Siemens. Industrial control systems were also affected by multiple vulnerabilities in the Dnsmasq DNS server, Java Runtime Environment, Oracle Java SE, and Cisco IOS and IOS XE.
Vulnerabilities in Intel products can also affect the security of industrial equipment. In the second half of 2017, information on several vulnerabilities in Intel products (ME, SPS and TXE) was published. These vulnerabilities affect mainly SCADA server hardware and industrial computers that use vulnerable CPUs. These include, for example, Automation PC 910 by B&R, Nuvo-5000 by Neousys and the GE Automation RXi2-XP product line. As a rule, vendors do not consider it necessary to release public advisories on vulnerabilities of this type (derived from using third-party technologies). Of course, there are some positive exceptions. For example, Siemens AG has released an advisory stating that these vulnerabilities affect a range of the company’s products. Earlier, the company published information about similar vulnerabilities in Intel technologies affecting its products.
IoT device vulnerabilities
2017 was marked by a growing number of vulnerabilities being identified in internet of things (IoT) devices. As a consequence, such vulnerabilities were increasingly often exploited to create botnets. The activity of three new botnets was uncovered in the last two months of 2017 only. These included the Reaper botnet and new Mirai variants, including the Satori botnet.
Multiple vulnerabilities were identified in Dlink 850L routers, WIFICAM wireless IP cameras, Vacron network video recorders and other devices.
On top of the new IoT device flaws, some old vulnerabilities are still not closed, such as CVE-2014-8361 in Realtek devices and the vulnerability dating back to 2012 that can be exploited to get the configuration of Serial-to-Ethernet converters, including the Telnet password, by sending a request on port 30718. The vulnerability in Serial-to-Ethernet converters directly affects the industrial internet of things (IIoT), since many systems that enable the operators of industrial equipment to remotely control its status, modify its settings and control its operation are based on serial interface converters.
The security of IoT devices is also affected by issues relating to the security of traditional information technology. Specifically, vulnerabilities in implementations of the Bluetooth protocol led to the emergence of the new attack vector, BlueBorne, which poses a threat to mobile, desktop and IoT operating systems.
Vulnerabilities identified by Kaspersky Lab ICS CERT
In 2017, Kaspersky Lab ICS CERT experts not only analyzed the security issues associated with different vendors’ ICS components, but also focused on the common ICS components, platforms and technologies used in different vendors’ solutions. This type of research is important because vulnerabilities in such components significantly increase the number of potential attack victims. Research in this area continues in 2018.
Number of vulnerabilities identified
Based on its research, Kaspersky Lab ICS CERT identified 63 vulnerabilities in industrial and IIoT/IoT systems in 2017.
Distribution of vulnerabilities identified by Kaspersky Lab ICS CERT in 2017
by types of components analyzed
Every time we identified a vulnerability, we promptly notified the respective product’s vendor.
Number of CVE entries published
During 2017, 11 CVE entries were published based on information about vulnerabilities identified by Kaspersky Lab ICS CERT. It should be noted that some of these CVE entries were published after vendors closed vulnerabilities information on which had been provided to them in 2016.
Information on other vulnerabilities identified by Kaspersky Lab ICS CERT experts will be published after these vulnerabilities are closed by the respective vendors.
Capabilities provided by the vulnerabilities identified
The largest number of vulnerabilities identified (29) could allow an attacker to cause denial of service (DoS) remotely. 8% of the vulnerabilities identified could allow an attacker to execute arbitrary code remotely on the target system.
Distribution of vulnerabilities identified by Kaspersky Lab ICS CERT in 2017
by capabilities provided
Vulnerabilities in ICS components
In 2017, Kaspersky Lab ICS CERT experts identified 30 vulnerabilities in ICS products from different vendors. These are mainly large automation system vendors, such as Schneider Electric, Siemens, Rockwell Automation, Emerson, and others.
Severity ratings of the vulnerabilities identified
To assess the severity of vulnerabilities identified in ICS components, Kaspersky Lab ICS CERT used its own vulnerability rating system based on the metrics defined in CVSS v3.0 (Common Vulnerability Scoring System) standard, with the following vulnerability severity levels identified:
least severe: CVSS v3.0 base score of 5.0 or less,
medium severity: CVSS v3.0 base score of 5.1 to 6.9 (inclusive),
most severe: CVSS v3.0 base score of 7.0 or more.
The absolute majority of vulnerabilities identified are in the most severe group. These include the XXE vulnerability in industrial solutions that use the Discovery Service of the OPC UA protocol stack.
Vulnerabilities in OPC UA implementations
One of the research areas involved searching for vulnerabilities in different implementations of the OPC UA technology. This type of research is needed to improve the overall security level of products from different vendors that use the technology in their solutions. Vulnerabilities in such technologies are a Swiss army knife of sorts for attackers, enabling them to hack industrial systems from different vendors.
A total of 17 critical denial-of-service vulnerabilities were identified during the period.
Some of the vulnerabilities were identified in sample software implementations of various OPC UA functions available in the official Github repository. In the process of communicating to several vendors of industrial automation systems, we found out that many of them had used code from such samples in their product code. This means that the vulnerabilities identified may affect complete product lines from different vendors.
Vulnerabilities in third-party hardware-based and software solutions
Kaspersky Lab ICS CERT experts have also analyzed third-party hardware-based solutions that are widely used in industrial automation systems.
Specifically, experts analyzed the SafeNet Sentinel hardware-based solution by Gemalto. As a result of the research, 15 vulnerabilities were identified in the software part of the solution (11 in December 2016 and 4 in 2017). These flaws affect a large number of products that use the vulnerable software, including solutions by ABB, General Electric, HP, Cadac Group, Zemax and other software developers, the number of which may reach 40 thousand, according to some estimates.
Vulnerabilities in internet of things (IoT and IIoT) components
Another area of research was the assessment of the information security status of internet of things (IoT), components, including industrial internet of things (IIoT) components.
Kaspersky Lab experts are working with vendors to improve the security of their solutions with respect to 11 vulnerabilities identified. Vulnerabilities were found in the following components and solutions:
smart cameras,
hardware-based IIoT solutions.
It should be noted that vulnerabilities in implementations of OPC UA standards, which are discussed above, also directly affect IIoT security.
Vulnerabilities in industrial routers
In the past year, 18 vulnerabilities were identified in industrial networking equipment from different vendors. Typical vulnerabilities: information disclosure, privilege escalation, arbitrary code execution, denial of service.
Working with software vendors
With respect to information on the vulnerabilities identified, Kaspersky Lab follows the principle of responsible information disclosure, promptly reporting vulnerabilities to the respective software vendors.
In 2017, Kaspersky Lab ICS CERT researchers actively collaborated with various companies to ensure that the vulnerabilities identified would be closed.
Of the 63 vulnerabilities identified by Kaspersky Lab ICS CERT in 2017, vendors closed 26. Vulnerabilities were closed by Siemens, General Electric, Rockwell Automation, Gemalto and the OPC Foundation industrial consortium.
It should be noted that most vendors of software for industrial automation systems that we have worked with have lately been devoting much more care and resources to the task of closing the vulnerabilities identified and fixing information security issues in their products, including their earlier versions.
At the same time, the issue of closing vulnerabilities in industrial automation systems remains relevant. In many cases, it takes large vendors a long time to close vulnerabilities in their products. Sometimes software vendors decide to patch only new versions of a vulnerable product, which they are planning to release in the future.
In addition, some vendors still need to improve the organizational and technical aspects of the procedures they use to inform customers about the vulnerabilities patched. Even after an update has been released, many users are unaware of the relevant security issue and use vulnerable versions of the product. This is particularly important for embedded software, as well as the technologies and specific program modules used by numerous third-party vendors (one example can be found here).
Positive examples include Siemens and the OPC Foundation, which have quickly closed the vulnerabilities identified and released public advisories on existing vulnerabilities.
Malware in industrial automation systems
As we have mentioned before, many industrial companies use modern networking technologies that improve the transparency and efficiency of enterprise management processes, as well as providing flexibility and fault tolerance for all tiers of industrial automation. As a result, industrial networks are increasingly similar to corporate networks – both in terms of use case scenarios and in terms of the technologies used. The unfortunate flip side of this is that internet threats, as well as other traditional IT threats, increasingly affect the industrial networks of modern organizations.
In the second half of 2017, Kaspersky Lab security solutions installed on industrial automation systems detected over 17.9 thousand different malware modifications from about 2.4 thousand different malware families.
Accidental infections
In the vast majority of cases, attempts to infect ICS computers are accidental and are not part of targeted attacks. Consequently, the functionality implemented in malware is not specific to attacks on industrial automation systems. However, even without ICS-specific functionality, a malware infection can have dire consequences for an industrial automation system, including an emergency shutdown of the industrial process. This was demonstrated by the WannaCry outbreak in May 2017, when several enterprises in different industries had to suspend their industrial processes after being infected with the encryption malware. We wrote about encryption malware-related threats in our previous report and several articles (see here and here).
Unexpected consequences of the WannaCry outrbreak
It is important to note that some IT threats can do much more significant harm in an industrial network than in an office network. To demonstrate this, we look at two incidents investigated by the Kaspersky Lab ICS-CERT team.
In H2 2017, we were approached by several industrial enterprises at once, where mass infections of industrial networks with WannaCry encryption malware had been detected. It was later determined that the initial infections of office networks at the victim companies had in all the cases taken place back in the first half of 2017, at the height of the WannaCry outbreak. However, the infections were not noticed until the malware propagated to the enterprises’ industrial networks. As it turned out during investigation, encryption functionality in the malware samples was damaged and the infected systems on corporate networks continued to operate normally, without any failures. However, the infection of industrial networks in these cases had unexpected negative consequences.
At one of the enterprises infected by WannaCry, the workstations used by operators started to bring up the Blue Screen of Death all the time, leading to emergency reboots. The reason for this unexpected consequence of infection was that the machines ran Windows XP. It is a well-known fact that the DoublePulsar exploit used by WannaCry to propagate causes WindowsXP to crash, resulting in a Blue Screen of Death and a reboot. In cases when numerous machines in the industrial segment of an organization’s network are infected, WindowsXP machines are often attacked and go into emergency reboots. As a result, operators are rendered incapable of monitoring and controlling the industrial process. This makes WannaCry a denial-of-service attack tool of sorts.
In another incident, the propagation of WannaCry caused some of the devices on an enterprise’s industrial network to become temporarily unavailable during periods when the network activity of the malware coincided with certain stages in the industrial process. This resulted in emergency interruptions of an industrial process that was critical for the enterprise for an average of 15 minutes.
Cryptocurrency miners in industrial network infrastructure
According to Kaspersky Lab ICS CERT data, cryptocurrency mining programs attacked 3.3% of industrial automation system computers during the period from February 2017 to January 2018.
Up to August 2017, the percentage of ICS computers attacked by cryptocurrency miners did not exceed 1%. This figure grew in September and did not go back to less than 1% for the rest of 2017. In October, cryptocurrency miner attacks against ICS computers peaked, with 2.07% of ICS computers being attacked.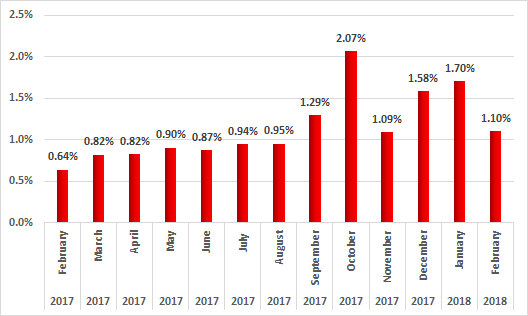
Percentage of ICS computers attacked by cryptocurrency mining malware
Like other malware infecting systems at industrial enterprises, cryptocurrency miners can pose a threat to industrial process monitoring and control. In the process of its operation, malware of this type creates a significant load on the computer’s computational resources. An increased load on processors can negatively affect the operation of the enterprise’s ICS components and threaten their stability.
According to our assessments, in most cases cryptocurrency miners infect ICS computers accidentally. There is no reliable information on machines that are part of the industrial network infrastructure being infected as a result of targeted attacks the goal of which is to mine cryptocurrencies, with the exception of cases when miners are installed by unscrupulous employees of victim enterprises. The cryptocurrency mining malware typically enters the industrial network infrastructure from the internet or, less commonly, from removable media or network shares.
Sources of ICS computer infections with cryptocurrency miners
Percentage of systems attacked, February 2017 – January 2018
Cryptocurrency miners have infected numerous websites, including those of industrial companies. In such cases, cryptocurrencies are mined on the systems of users who visit infected web resources. This technique is called cryptojacking.
Screenshot showing a fragment of code found on a web resource infected with mining malware
Botnet agents in the industrial network infrastructure
In most cases, the functionality of botnet agents includes searching for and stealing financial information, stealing authentication data, brute forcing passwords, sending spam, as well as conducting attacks on specified remote internet resources, including denial-of-service (DDoS) attacks. In addition, in cases where a botnet agent attacks third-party resources (such cases have been detected), the companies that own the IP addresses from which the attacks are launched may face certain reputational risks.
Although the destructive activity of botnet agents is not specifically designed to disrupt the operation of any industrial system, an infection with this type of malware may pose a significant threat to a facility that is part of the industrial infrastructure. Malware of this type can cause network failures, denial of service (DoS) of the infected system and other devices on the network. It is also common for malware to contain errors in its code and/or be incompatible with software used to control the industrial infrastructure, potentially resulting in the disruption of industrial process monitoring and control.
Another danger associated with botnet agents is that malware of this type often includes data collection functionality and, like backdoor malware, enables the attackers to control the infected machine surreptitiously. System data collected by bots by default is sufficient for accurately identifying the company that owns the system and the type of the infected system. What’s more, access to machines infected with botnet agents is often put up for sale at specialized exchanges on the Darknet. Consequently, threat actors interested in infected industrial control systems can gain access to a victim company’s sensitive data and/or systems used to control the industrial infrastructure.
In 2017, 10.8% of all ICS systems were attacked by botnet agents. Moreover, botnet agent attack statistics show that 2% of ICS systems were attacked by several malicious programs of this type at once.
Percentage of ICS computers attacked by botnet agents in 2017
The main sources of botnet agent attacks on ICS systems in 2017 were the internet, removable media and email messages.
Sources of ICS infection with botnet agents, percentage of ICS computers attacked, 2017
This once again demonstrates the need for access control to ensure that information is exchanged securely between an enterprise’s industrial network and other networks, as well as the need to block unauthorized removable media from connecting to ICS systems and to install tools designed to detect and filter malicious objects from email messages.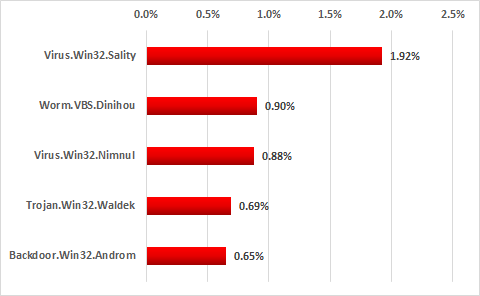
Top 5 botnet agent most commonly found on ICS systems in 2017,
percentage of ICS computers attacked
Nearly two percent of all systems analyzed were attacked with Virus.Win32.Sality malware. In addition to infecting other executable files, this malware includes the functionality of resisting antivirus solutions and downloading additional malicious modules from the command-and-control server. The most widespread Sality modules are components for sending spam, stealing authentication data stored on the system and downloading and installing other malware.
The Dinihou botnet agent, which attacked 0.9% of ICS systems analyzed, is in second position. The malware includes functionality that enables the attackers to upload an arbitrary file from an infected system, creating the threat of sensitive data leaks for victim organizations. In addition, both Worm.VBS.Dinihou and Virus.Win32.Nimnul, which is in third place with 0.88%, can be used to download and install other malware on infected systems.
Most modifications of Trojan.Win32.Waldek are distributed via removable media and include functionality to collect information on infected systems and send it to the attackers. Based on the system data collected, the attackers create packages of additional malware to be installed on the infected system using the relevant Waldek functionality.
The fifth position is taken up by Backdoor.Win32.Androm, which ranked highest based on the number of attacks on ICS systems in H2 2016. The malware provides the attackers with a variety of information on the infected system and enables them to download and install modules for performing destructive activities, such as stealing sensitive data.
Targeted attacks
2017 saw the publication of information on two targeted attacks on systems that are part of the industrial infrastructure – Industroyer and Trisis/Triton. In these attacks, for the first time since Stuxnet, threat actors created their own implementations of industrial network protocols, gaining the ability to communicate with devices directly.
Trisis/Triton
In December 2017, researchers reported discovering previously unknown malware that targeted critical infrastructure systems. The discovery was made as a result of investigating an incident at an unnamed industrial enterprise. The malicious program was dubbed Triton or Trisis.
The malware is a modular framework that can automatically find Triconex Safety Controllers on the enterprise network, get information on their operating modes and plant malicious code on these devices. Trisis/Triton embeds a backdoor in the device’s firmware, enabling the attackers to remotely read and modify not only the code of the legitimate control program, but also the code of the compromised Triconex device’s firmware. With such capabilities, attackers can do serious damage to the enterprise’s industrial process. The least harmful of possible negative consequences is the system’s emergency shutdown and interruption of the industrial process. It was this type of event that caused a victim organization to launch an investigation, which resulted in the attack being detected.
It remains unknown how the attackers penetrated the enterprise’s infrastructure. What is known is that they must have been inside the compromised organization’s network for a sufficiently long time (several months) and used legitimate software and ‘dual-use’ utilities for lateral movement and privilege escalation.
Although the attack was designed to modify code on Triconex devices, the code that the attackers were apparently trying to inject in the last stage of the attack has never been found, so it is currently impossible to determine the final objective of the attack.
Spear phishing — Formbook spyware
Spear phishing attacks on industrial organizations continued in the second half of 2017. We have already written about spear phishing used by threat actors in Business Email Compromise (BEC) attacks. Compared to attacks described earlier, the attackers’ tactics have not changed significantly. However, in addition to known Trojan-Spy malware sent in phishing emails to global industrial and energy companies (FareIT, HawkEye, ISRStealer, etc.), a new representative of this malware class – Formbook – gained popularity in the second half of 2017.
Formbook attacks involve sending phishing emails with malicious Microsoft Office documents attached. To download and install malware on target systems, these documents exploit the CVE-2017-8759 vulnerability or use macros. Some phishing emails include attached archives of different formats containing the malicious program’s executable file. Examples of attached file names:
RFQ for Material Equipment for Aweer Power Station H Phase IV.exe
Scanned DOCUMENTS & Bank Details For Confirmation.jpeg (Pages 1- 4) -16012018. jpeg.ace
PO & PI Scan.png.gz
zip
QUOTATION LISTS.CAB
shipping receipts.ace
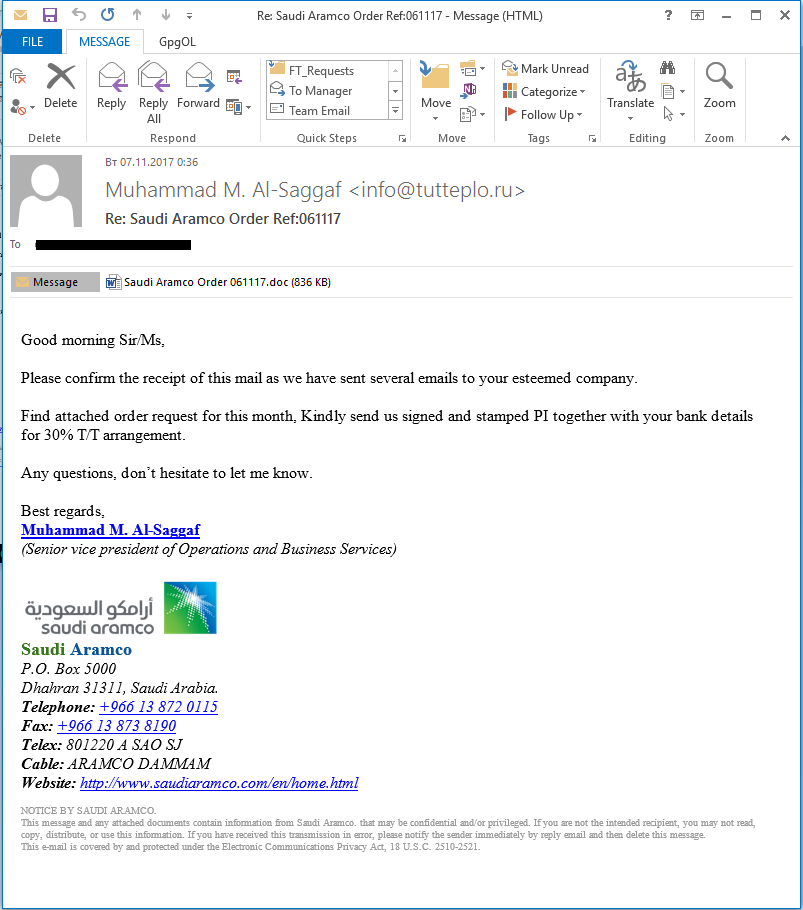
Sample phishing email used to distribute Formbook
In terms of implementation and the techniques used to obfuscate the code and encrypt the payload, Formbook differs from its ‘peers’ in that its functionality is more extensive. In addition to standard spyware features, such as making screenshots, capturing keypresses and stealing passwords stored in browsers, Formbook can steal sensitive data from HTTP/HTTPS/SPDY/HTTP2 traffic and web forms. Additionally, the malware implements remote system control functionality and uses an unusual technique to resist the analysis of network traffic. The Trojan generates a set of URLs to which it is going to connect, using a list of legitimate domains stored in its body. It then adds one URL for its command-and-control server. In this way, the malware attempts to mask its connections to the malicious domain by sending numerous requests to legitimate resources, making its detection and analysis more difficult.
Threat statistics
All statistical data used in this report was collected using the Kaspersky Security Network (KSN), a distributed antivirus network. The data was received from those KSN users who gave their consent to have data anonymously transferred from their computers. We do not identify the specific companies/organizations sending statistics to KSN, due to the product limitations and regulatory restrictions.
Methodology
The data was received from ICS computers protected by Kaspersky Lab products that Kaspersky Lab ICS CERT categorizes as part of the industrial infrastructure at organizations. This group includes Windows computers that perform one or several of the following functions:
supervisory control and data acquisition (SCADA) servers,
data storage servers (Historian),
data gateways (OPC),
stationary workstations of engineers and operators,
mobile workstations of engineers and operators,
Human Machine Interface (HMI).
The statistics analyzed also include data received from computers of industrial control network administrators and software developers who develop software for industrial automation systems.
For the purposes of this report, attacked computers are those on which our security solutions have been triggered at least once during the reporting period. When determining percentages of machines attacked, we use the ratio of unique computers attacked to all computers in our sample from which we received anonymized information during the reporting period.
ICS servers and stationary workstations of engineers and operators often do not have full-time direct internet access due to restrictions specific to industrial networks. Internet access may be provided to such computers, for example, during maintenance periods.
Workstations of system/network administrators, engineers, developers and integrators of industrial automation systems may have frequent or even full-time internet connections.
As a result, in our sample of computers categorized by Kaspersky Lab ICS CERT as part of the industrial infrastructure of organizations, about 40% of all machines have regular or full-time internet connections. The remaining machines connect to the Internet no more than once a month, many less frequently than that.
Percentage of computers attacked
In the second half of 2017, Kaspersky Lab products blocked attempted infections on 37.8% of ICS computers protected by them, which is 0.2 percentage points more than in the first half of 2017 and 1.4 percentage points less than in the second half of 2016.
June – August 2017 saw a decline in the number of attacked computers. However, in September there was a notable increase in cybercriminal activity, with the proportion of attacked machines rising to 20% and not falling below that level again for the rest of the year.
Percentage of ICS computers attacked globally by month, 2017
When comparing these values with the same period in 2016, we see that the July numbers are practically identical. However, for all other months the percentage of attacked machines in 2016 was higher than in 2017.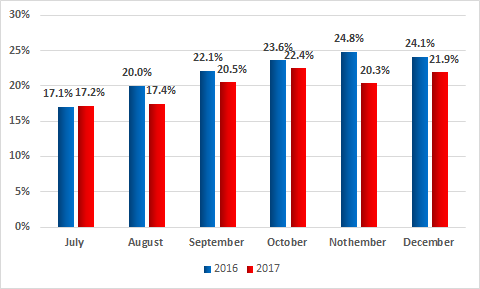
Percentage of ICS computers attacked globally by month, H2 2017 vs H2 2016
A certain decrease in the percentage of computers attacked can be attributed to several factors. It is likely that one has to do with industrial enterprises paying more attention to the security of industrial segments on their networks. According to our experts’ assessments, changes for the better may be largely due to simple measures: enterprises have begun to conduct audits of the industrial segments of their networks, train employees in the principles of cyber-hygiene, more properly differentiate access rights between the corporate and the industrial segments of their network, etc.
Percentage of ICS computers attacked in different industries
According to our assessment, medium-size and large companies with mature IT security processes tend to use Kaspersky Lab corporate solutions (mainly Kaspersky Industrial CyberSecurity and Kaspersky Endpoint Security) to safeguard their ICS infrastructure. Many smaller organizations and individual engineers, along with companies whose IT and OT cybersecurity still leaves much to be desired, may rely on Kaspersky Lab consumer solutions to protect their ICS computers. The percentage of such computers attacked by malware during the reporting period is significantly higher compared to the corresponding figures for computers protected by corporate products.
We intentionally excluded statistics coming from our consumer solutions when analyzing attacks on industrial facilities in different industries, using only telemetry data coming from Kaspersky Lab products for corporate users. This resulted in lower average attacked computers percentage values than for the rest of the analysis results presented in this report, where both Kaspersky Lab corporate and consumer product statistics were used.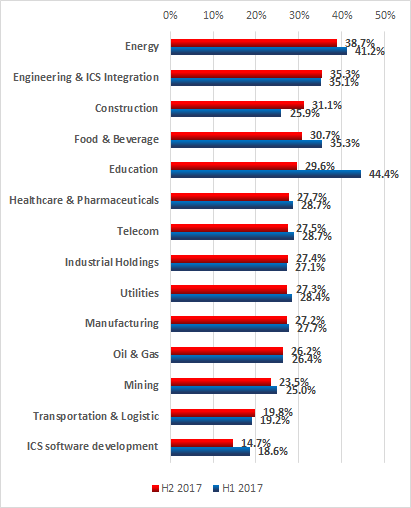
Percentage of ICS computers attacked in different industries*, H2 2017 vs H1 2017
*In this report, unlike our previous reports, we calculated the percentage of attacked ICS computers for each industry (the percentage of ICS computers attacked in an industry to all ICS computers in that industry).
In previous reports, we included the distribution of attacked ICS computers by industry (the percentage of computers attacked in a given industry to all attacked computers in our sample).
According to statistics on attacks against facilities in different industries, nearly all industries demonstrate similar percentages of attacked ICS computers, which are in the range from 26 to 30 percent. We believe this may be due to the similarity of ICS architectures used to automate industrial processes at enterprises in various industries and, possibly, similarities in the processes used by enterprises to exchange information with external entities and inside the enterprises themselves.
Two industries were attacked more than others during the reporting period: the figures for Energy (38.7%) and Engineering & ICS Integrators (35.3%) are above 35%.
We believe that the high percentage of attacked ICS systems in the energy sector may be explained, on the one hand, by the greater network connectivity of electric power sector facilities (compared to facilities in other industries) and, on the other hand, perhaps by the fact that, on average, more people have access to the industrial control systems of energy sector facilities that to those at enterprises in other industries.
The supply chain attack vector has infamously been used in some devastating attacks in recent years, which is why the high percentage of attacked ICS computers in Engineering and ICS Integration businesses is a problem that is serious enough to be noticed.
The only industry whose figures showed a significant growth in the six months (+ 5.2 p.p.) is Construction (31.1%). The reason for the high percentage of ICS computers attacked in construction organizations could be that, for enterprises in the industry, industrial control systems often perform auxiliary functions, were introduced a relatively short time ago and are consequently at the periphery of company owners’ and managers’ attention. The upshot of this may be that objectives associated with protecting these systems from cyberthreats are regarded as having a relatively low priority. Whatever the reason for the high percentage of attacks reaching industrial control systems in construction and engineering, the fact seems sufficiently alarming. Construction is known to be a highly competitive business and cyberattacks on industrial organizations in this industry can be used as a means of unfair competition. So far, cyberattacks have been used in the construction industry mainly for purposes associated with the theft of commercial secrets. Infecting industrial control systems may provide threat actors with a new weapon in their fight against competitors.
The three least attacked industries are Mining (23.5%), Logistic & Transportation (19.8%) and ICS Software Development (14.7%).
ICS vendor infections might be very dangerous, because the consequences of an attack, spread over the infected vendor’s partner ecosystem and customer base, could be dramatic, as we saw in the recent wide-scale incidents, such as the exPetr malware epidemic.
This report includes information on ICS computers at educational facilities. These figures include not only ICS systems used in demonstration stands and labs performing instructional and research functions, but also in industrial automation systems of various facilities that are part of the infrastructure of educational establishments, such as power supply systems (including power generation and distribution), utilities, etc., as well as ICS used in pilot production facilities.
The figure for educational establishments can be regarded as representing the “background level” of accidental threats affecting ICS systems, considering systems at educational establishments to be as insecure as such systems can get. This is because ICS systems at educational establishments are usually connected to the respective organizations’ general-purpose networks and are less isolated from the outside world than the systems of industrial facilities.
At the same time, we believe that attacks on ICS systems at educational establishments can also pose a significant threat to enterprises in different real-sector industries – primarily because universities/colleges maintain working contacts and engage in collaboration with industrial enterprises. This includes joint research labs, engineering and development centers, personnel training and career development centers, etc.
In addition, such ICS systems can be used by attackers to test and debug malicious code and refine attacks against real-sector enterprises.
Education demonstrates the greatest difference between the H1 and H2 percentages of ICS systems attacked. The high figure for H1 was due to the large number of internet-borne attacks, as well as attacks by malware belonging to the Trojan.Multi.Powercod family. That malware uses techniques that are similar to those described by our colleagues here. In H1 2017, 9.8% of ICS computers in educational establishments from our sample were attacked by Powercod Trojans. In H2, the corresponding figure was 0.7%.
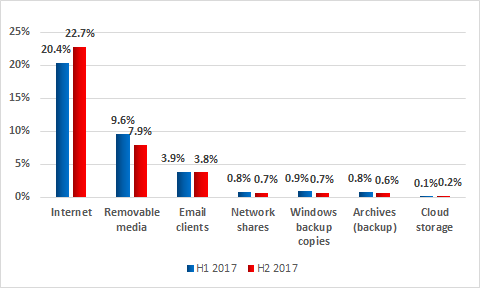
Main sources of threats blocked on ICS computers,
percentage of ICS computers attacked, H2 2017 vs H1 2017
In the second half of 2017, most of the numbers for the main infection sources remained at H1 2017 levels.
For computers that are part of the industrial infrastructure, the internet remains the main source of infection. Contributing factors include interfaces between corporate and industrial networks, availability of limited internet access from industrial networks, and connection of computers on industrial networks to the internet via mobile phone operator networks (using mobile phones, USB modems and/or Wi-Fi routers with 3G/LTE support). Contractors, developers, integrators and system/network administrators that connect to the control network externally (directly or remotely) often have unrestricted internet access. Their computers are in the highest-risk group and can be used by malware as a channel for penetrating the industrial networks of the enterprises they serve. As we mentioned above, about 40% of computers in our sample connect to the internet on a regular basis. It should be noted that, in addition to malicious and infected websites, the “Internet” category includes phishing emails and malicious attachments opened in web-based email services (in browsers).
Experts from Kaspersky Lab ICS-CERT note that malicious programs and scripts built into email message bodies are often used in targeted attacks on industrial enterprises. In most cases, the attackers distribute emails with malicious attachments in office document formats, such as Microsoft Office and PDF, as well as archives containing malicious executable files.
There has also been a 1.7 p.p. decrease in the proportion of threats detected while scanning removable media. This is an important indicator, because such devices are often used to transfer information in industrial networks.
The other figures did not change appreciably.
Classes of malware
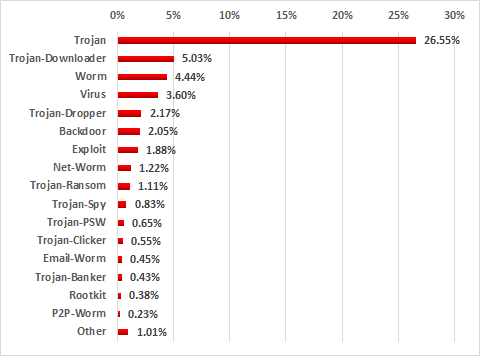
Trojan malware, which is designed to penetrate the systems being attacked, deliver and launch other malware modules, remains relevant to ICS computers. The malicious code of o these programs was most commonly written in scripting languages (Javascript, Visual Basic Script, Powershell, AutoIt in the AutoCAD format) or took the form of Windows shortcuts (.lnk) that pointed to the next malicious modules.
These Trojans most often tried to download and execute the following malware as main modules:
spyware Trojans (Trojan-Spy and Trojan-PSW)
ransomware (Trojan-Ransom)
backdoors (Backdoor)
remote administration tools installed without authorization (RAT)
Wiper type programs (KillDisk) designed to delete (wipe) data on the hard drive and render the computer unusable
Malware infections of computers on an industrial network can result in the loss of control or the disruption of industrial processes.
Platforms used by malware
In the second half of 2017, we saw a significant increase in the percentage of ICS computers affected by malware written for the JavaScript platform.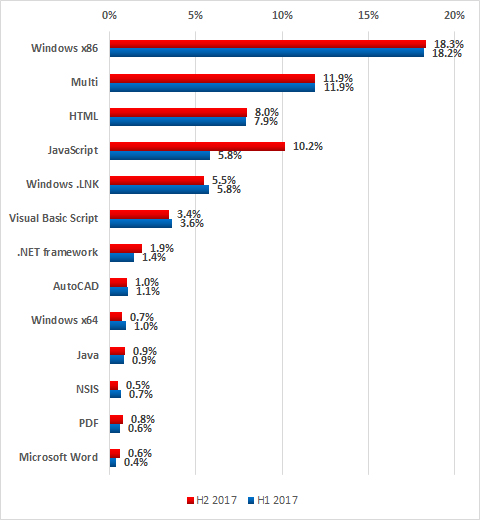
Platforms used by malware, percentage of ICS computers attacked, H2 2017 vs H1 2017
The main reason for growing figures for the JavaScript platform is the increase in the number of phishing emails that include a loader for Trojan-Ransom.Win32.Locky.
In the latest versions of such emails, the attackers used a fax-received notification template.
The phishing emails include an attachment – an obfuscated loader written in JavaScript and designed to download and execute the main malicious module from servers controlled by the attackers.
It is important to note that threat actors often attack legitimate websites in order to host malware components on these sites. Threat actors do this to hide malicious traffic behind legitimate domains to mask the traces of an attack.
Cryptocurrency miners also made a small contribution to the increase in the share of the JavaScript platform – both the versions for browsers and the script-based loaders of miners for the Windows platform.
Geographical distribution of attacks on industrial automation systems
The map below shows the percentages of industrial automation systems attacked to the total number of such systems in each country.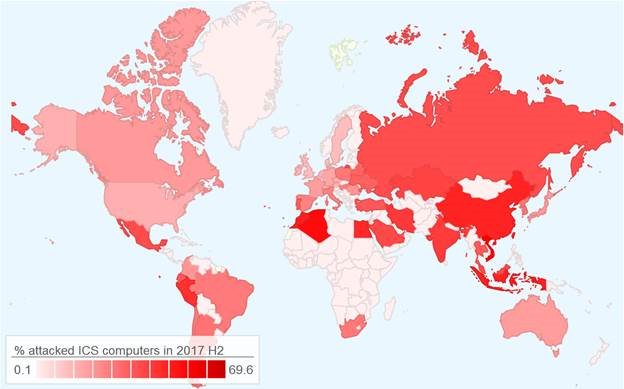
Geographical distribution of attacks on industrial automation systems, H2 2017
Percentage of attacked ICS computers in each country
TOP 15 countries by percentage of ICS computers attacked:
Country* % of systems attacked
1 Vietnam 69.6
2 Algeria 66.2
3 Morocco 60.4
4 Indonesia 60.1
5 China 59.5
6 Egypt 57.6
7 Peru 55.2
8 Iran 53.0
9 India 52.4
10 Kazakhstan 50.1
11 Saudi Arabia 48.4
12 Mexico 47.5
13 Russia 46.8
14 Malaysia 46.7
15 Turkey 44.1
*Countries in which the number of ICS computers monitored by Kaspersky Lab ICS CERT was insufficient to obtain representative data sets were excluded from the ranking.
The Top 5 has remained unchanged since H1 2017.
The least affected countries in this ranking are Israel (8.6%), Denmark (13.6%), the UK (14.5%), the Netherlands (14.5%), Sweden (14.8%) and Kuwait (15.3%).
Egypt has moved from ninth place to sixth – the percentage of attacked ICS machines in that country grew by 6.1 p.p. This is the most significant growth among all countries of the world. Internet threats accounted for most of the growth in the percentage of attacked ICS computers in Egypt. Among the internet threats detected, the most common were sites infected with script-based cryptocurrency miners and attempts to download malware by following URL links.
Main sources of threats blocked on ICS computers in Egypt
percentage of ICS computers attacked, H2 2017 vs H1 2017
Malware distributed via removable media is also a real problem for many ICS in Egypt. Malware loaders distributed on removable media are disguised as existing user files on the removable drive, increasing the chances of a successful attack.
Examples of names used for loaders of malware distributed via removable media that were blocked on ICS computers in Egypt in H2 2017
In most cases, the loaders that we detected were designed to launch the malware module responsible for infecting the system, including downloading the main module, infecting removable media and network shares and propagating via email/instant messengers to an existing list of contacts.
Malicious code for the AutoIt platform, launched by a malicious .lnk loader
blocked on an ICS computer in Egypt in H2 2017
In Russia during H2 2017, 46.8% of ICS computers were attacked at least once – a 3.8 p.p. rise on H1 2017. This saw Russia move up from 21st to 13th.
The proportions of attacked ICS machines vary greatly between different regions of the world.
Percentage of ICS systems attacked in regions of the world, H2 2017 vs H1 2017
All regions can be assigned to one of three groups according to the percentage of attacked ICS machines:
Proportion of attacked ICS systems below 30%. This group includes North America and Europe, where the situation looks the most peaceful. Kaspersky Lab ICS CERT specialists say this does not necessarily mean that industrial enterprises in these regions are less frequently attacked by cybercriminals; rather, it could be that more attention is paid to ensuring information security at industrial enterprises in these regions, which results in fewer attacks reaching their targets.
Proportion of attacked ICS systems between 30% and 50%. This group includes Latin America, Russia and the Middle East.
Proportion of attacked ICS systems above 50%. The situation is most acute in Africa and the Asia-Pacific region.
It should be noted that values may differ significantly between countries within the same region. This may be due to different practices and approaches to ICS information security in those countries.
In particular, the Asia-Pacific region includes Vietnam with the highest global proportion of attacked ICS systems (69.6%) alongside countries such as Japan (25%), Australia (24.1%) and Singapore (23.2%), where figures did not exceed 25%.
Percentage of attacked ICS computers in Asia-Pacific countries, H2 2017 vs H1 2017
In Europe, Denmark’s score (13.6%) was not only the lowest in the region but also one of the lowest globally, while the proportions of attacked ICS systems in Belarus (41%), Portugal (42.5%) and Ukraine (41.4%) were all above 40%.
Percentage of attacked ICS computers in Europe, H2 2017 vs H1 2017
Let’s now look at the sources of attacks that affected ICS systems in different regions.

Main sources of threats blocked on ICS computers in different regions, H2 2017
In all regions of the world, the internet remains the main source of attacks. However, in Europe and North America, the percentage of blocked web-borne attacks is substantially lower than elsewhere. This may be because most enterprises operating in those regions adhere to information security standards. In particular, internet access is restricted on systems that are part of industrial networks. The situation is similar for infected removable devices: the highest numbers are seen in Africa and the Asia-Pacific region, while the lowest are in Europe and North America. These figures also reflect the level of compliance with information security standards and, in particular, whether restrictions are in place to prevent the connection of unauthorized removable media to industrial infrastructure systems.
Curiously, in spite of the sufficiently high overall percentage of attacks that reached ICS systems, the percentages of ICS computers attacked via removable media and email clients in Russia were relatively small – 4.4% and 1.4% respectively. One possible explanation is that risks associated with these attack vectors are largely mitigated through organizational measures, as well as removable media and email handling practices established at industrial enterprises. This interpretation is reassuring, since removable media and email are often used as penetration vectors in sophisticated targeted and APT attacks.
For countries of the Middle East, email was a significant (5%) source of infection, with the region leading the ranking based on this parameter.
Our recommendations
To prevent accidental infections in industrial networks, we recommend taking a set of measures designed to secure the internal and external perimeters of these networks.
This includes, first and foremost, measures required to provide secure remote access to automation systems and secure transfer of data between the industrial network and other networks that have different trust levels:
Systems that have full-time or regular connections to external networks (mobile devices, VPN concentrators, terminal servers, etc.) should be isolated into a separate segment of the industrial network – the demilitarized zone (DMZ);
Systems in the demilitarized zone should be divided into subnets or virtual subnets (VLAN), with restricted access between subnets (only the communications that are required should be allowed);
All the necessary communication between the industrial network and the outside world (including the enterprise’s office network) should be performed via the DMZ;
If necessary, terminal servers that support reverse connection methods (from the industrial network to the DMZ) can be deployed in the DMZ;
Thin clients should be used whenever possible to access the industrial network from the outside (using reverse connection methods);
Access from the demilitarized zone to the industrial network should be blocked;
If the enterprise’s business processes are compatible with one-way communication, we recommend that you consider using data diodes.
The threat landscape for industrial automation systems is continually changing, with new vulnerabilities regularly found both in application software and in industrial software. Based on the threat evolution trends identified in H2 2017, we recommend placing special emphasis on the following security measures:
Regularly updating the operating systems, application software and security solutions on systems that are part of the enterprise’s industrial network;
Installing firmware updates on control devices used in industrial automation systems in a timely manner;
Restricting network traffic on ports and protocols used on the edge routers between the organization’s network and those of other companies (if information is transferred from one company’s industrial network to another company);
An emphasis on account control and password policies is recommended. Users should have only those privileges that are required for them to perform their responsibilities. The number of user accounts with administrative privileges should be as limited as possible. Strong passwords (at least 9 characters, both upper and lower case, combined with digits and special characters) should be used, with regular password changing enforced by the domain policy, for example, every 90 days.
To provide protection from accidental infections with new, previously unknown malware and targeted attacks, we recommend doing the following on a regular basis:
Taking an inventory of running network services on all hosts of the industrial network; where possible, stopping vulnerable network services (unless this will jeopardize the continuity of industrial processes) and other services that are not directly required for the operation of the automation system; special emphasis should be made on services that provide remote access to file system objects, such as SMB/CIFS and/or NFS (which is relevant in the case of attacks on systems running Linux).
Auditing ICS component access control; trying to achieve maximum access granularity.
Auditing the network activity in the enterprise’s industrial network and at its boundaries. Eliminate any network connections with external and other adjacent information networks that are not required by industrial processes.
Verifying the security of remote access to the industrial network; placing a special emphasis on whether demilitarized zones are set up in compliance with IT security requirements. To the fullest extent possible, minimizing or completely eliminating the use of remote administration tools (such as RDP or TeamViewer). More details on this are provided above.
Ensuring that signature databases, heuristics and decision algorithms of endpoint security solutions are up-to-date. Checking that all the main protection components are enabled and running and that ICS software folders, OS system folders or user profiles are not excluded from the scope of protection. Application startup control technologies configured in whitelisting mode and application behavior analysis technologies are particularly effective for industrial enterprises. Application startup control will prevent cryptomalware from running even if it finds its way on to the computer, while application behavior analysis technologies are helpful for detecting and blocking attempts to exploit vulnerabilities (including unknown) in legitimate software.
Auditing policies and practices related to using removable media and portable devices. Blocking devices that provide illegitimate access to external networks and the Internet from being connected to industrial network hosts. Wherever possible, disabling the relevant ports or controlling access to these ports using properly configured dedicated tools.
In addition, to provide protection from targeted attacks directed at the enterprise’s industrial network and its main industrial assets, we recommend deploying tools that provide network traffic monitoring and detection of cyberattacks on industrial networks. In most cases, such measures do not require any changes to ICS components or their configuration and can be carried out without suspending their operation.
Of course, completely isolating the industrial network from adjacent networks is virtually impossible, since transferring data between networks is required to perform a variety of important functions – controlling and maintaining remote facilities, coordinating sophisticated industrial processes, parts of which are distributed between numerous workshops, lines, plants and support systems. We hope, however, that our recommendations will help you provide maximum protection for your industrial networks and automation systems against existing and future threats.
Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) is a global project of Kaspersky Lab aimed at coordinating the work of industrial automation system vendors, owners and operators of industrial facilities and IT security researchers in addressing issues associated with protecting industrial enterprises and critical infrastructure facilities.
Ukrainian Suspected of Leading Carbanak Gang Arrested in Spain
26.3.2018 securityweek CyberCrime
A Ukrainian national suspected of being the leader of a gang that used Carbanak malware to steal a significant amount of money from banks worldwide has been arrested in Spain, Europol and the Spanish government announced on Monday.
According to authorities, the man is believed to be the mastermind of an operation that resulted in losses totaling over €1 billion ($1.24 billion). The hackers targeted over 100 financial organizations in more than 40 countries around the world, stealing up to €10 million ($12.4 million) in a single heist.
The suspect was arrested in Alicante, Spain, following an investigation conducted by the Spanish National Police and supported by Europol, private cybersecurity firms, and law enforcement agencies in the United States, Romania, Belarus and Taiwan.
Spain’s interior ministry identified the suspect as Ukrainian national “Denis K” and noted that he ran the operation with help from three Russian and Ukrainian nationals. The mastermind of the operation had been working from Spain, and he found his accomplices online, but they never met in person.
The gang targeted ATMs in Spain’s capital city of Madrid in the first quarter of 2017, stealing half a million euros.
Police seized computers, jewelry worth €500,000 ($620,000), documents, and two luxury vehicles following Denis K’s arrest. Bank accounts and two houses valued at roughly €1 million ($1.24 million) were also blocked.
The cybercrime group, tracked as Carbanak, Anunak and Cobalt, has been around since at least 2013 and its activities were first detailed in 2014. According to Spain’s interior ministry, investigations into the group started in 2015.
According to Europol, the cybercriminals started out by using a piece of malware they had dubbed Anunak. They later improved their malware, a version that the cybersecurity industry has dubbed Carbanak. Starting with 2016, they launched more sophisticated attacks using a custom version of the penetration testing tool Cobalt Strike. It’s worth noting that this is not the only cybercrime group known to use the Carbanak malware.
The hackers delivered their malware to bank employees using spear-phishing emails. Once the malware was deployed, it gave attackers access to the compromised organization’s internal network, including servers controlling ATMs.
The cybercriminals used their access to these servers to remotely instruct ATMs to dispense cash at a predetermined time, when the group’s mules would be nearby to collect the money. They also transferred funds from the targeted bank to their own accounts, and modified balances to allow members of the gang to withdraw large amounts of money at cash machines.
Authorities said the group worked with the Russian and Moldovan mafia, which were responsible for the money mules involved in the operation. The criminal proceeds were often laundered using bitcoins – the gang is said to have acquired 15,000 bitcoins, currently worth more than $118 million.
“It appears that the ultimate downfall was spurred on by what ends up bringing down most organized crime groups: accounting. This reinforces the need for law enforcement organizations to continue focusing on traditional 'follow the money angles' as much as cyber forensic capabilities. As long as you cannot make major purchases with cryptocurrencies, the Achilles heel of any organized crime activity will be laundering money and taxes,” commented Ross Rustici, senior director of intelligence services at Cybereason.
“Pinching these types of actors from both a prevention of movement in cyberspace and a reduced ability to enjoy their illicit gains often results in the largest successes for law enforcement,” Rustici added. “What remains to be seen is whether this arrest will result in a serious degradation of Carbanak’s capabilities or merely a short-term hindrance while the group refocuses its activity.”
Drupal to Patch Highly Critical Vulnerability This Week
26.3.2018 securityweek Vulnerebility
Drupal announced plans to release a security update for Drupal 7.x, 8.3.x, 8.4.x, and 8.5.x on March 28, 2018, aimed at addressing a highly critical vulnerability.
The Drupal security team hasn’t provided information on the vulnerability and says it won’t release any details on it until the patch arrives. An advisory containing all the necessary information will be published on March 28.
Before that, however, the team advises customers to be prepared for the update’s release and to apply it immediately after it is published, given its high exploitation potential.
“The Drupal Security Team urges you to reserve time for core updates at that time because exploits might be developed within hours or days,” Drupal announced.
The highly popular content management system (CMS) powers over one million sites and is used by a large number of e-commerce businesses.
Due to the widespread use of Drupal, currently the second most used CMS after WordPress, the security update will be released for Drupal versions 8.3.x and 8.4.x as well, although they are no longer supported.
“While […] we don't normally provide security releases for unsupported minor releases, given the potential severity of this issue, we are providing 8.3.x and 8.4.x releases that include the fix for sites which have not yet had a chance to update to 8.5.0,” Drupal says.
The Drupal security team urges customers to update to the appropriate release for their CMS version as soon as it is made available on March 28.
Thus, sites on 8.3.x should be updated to the upcoming 8.3.x iteration and then to the latest 8.5.x security release in the next month, while sites on 8.4.x should apply the next 8.4.x release and then upgrade to 8.5.x as well.
All sites on Drupal versions 7.x or 8.5.x should immediately apply the update when the advisory is released, using the normal update methods.
All of the appropriate version numbers for the impacted Drupal 8 branches will be listed in the upcoming advisory.
“Your site's update report page will recommend the 8.5.x release even if you are on 8.3.x or 8.4.x, but temporarily updating to the provided backport for your site's current version will ensure you can update quickly without the possible side effects of a minor version update,” Drupal also notes.
Energy Sector Most Impacted by ICS Flaws, Attacks: Study
26.3.2018 securityweek ICS
The energy sector was targeted by cyberattacks more than any other industry, and many of the vulnerabilities disclosed last year impacted products used in this sector, according to a report published on Monday by Kaspersky Lab.
The security firm has analyzed a total of 322 flaws disclosed in 2017 by ICS-CERT, vendors and its own researchers, including issues related to industrial control systems (ICS) and general-purpose software and protocols used by industrial organizations.
Of the total number of security holes, 178 impact control systems used in the energy sector. Critical manufacturing organizations – this includes manufacturers of primary metals, machinery, electrical equipment, and transportation equipment – were affected by 164 of these vulnerabilities.
Other industries hit by a significant number of vulnerabilities are water and wastewater (97), transportation (74), commercial facilities (65), and food and agriculture (61).
Many of the vulnerabilities disclosed last year impacted SCADA or HMI components (88), industrial networking devices (66), PLCs (52), and engineering software (52). However, vulnerabilities in general purpose software and protocols have also had an impact on industrial organizations, including the WPA flaws known as KRACK and bugs affecting Intel technology.
As for the types of vulnerabilities, nearly a quarter are web-related and 21 percent are authentication issues.
A majority of the flaws have been assigned severity ratings of medium or high, but 60 weaknesses are considered critical based on their CVSS score. Kaspersky pointed out that all vulnerabilities with a CVSS score of 10 are related to authentication and they are all easy to exploit remotely.
Kaspersky said 265 of the vulnerabilities can be exploited remotely without authentication and without any special knowledge or skills. It also noted that exploits are publicly available for 17 of the security holes.
The company has also shared data on malware infections and other security incidents. In the second half of 2017, Kaspersky security products installed on industrial automation systems detected nearly 18,000 malware variants from roughly 2,400 families. Malware attacks were blocked on almost 38 percent of ICS computers protected by the company, which was slightly less than in the second half of the previous year.
Again, the energy sector was the most impacted. According to the security firm, roughly 40 percent of the devices housed by energy organizations were targeted.
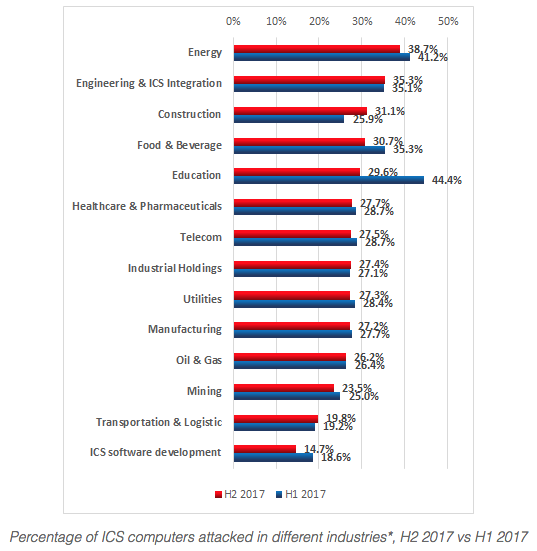
“In the vast majority of cases, attempts to infect ICS computers are accidental and are not part of targeted attacks,” Kaspersky said. “Consequently, the functionality implemented in malware is not specific to attacks on industrial automation systems. However, even without ICS-specific functionality, a malware infection can have dire consequences for an industrial automation system, including an emergency shutdown of the industrial process.”
One example was the WannaCry attack, which, according to Kaspersky, in some cases resulted in temporary disruptions to industrial processes.
Researchers noted that botnet agents can also pose a significant threat, including by stealing sensitive data and by causing disruptions to industrial processes as a side effect of coding errors and incompatibility. Kaspersky reported that last year more than 10 percent of the systems it monitored were targeted by botnet agents.
Pentagon Looks to Counter Ever-stealthier Warfare
26.3.2018 securityweek BigBrothers
The US military has for years enjoyed a broad technological edge over its adversaries, dominating foes with superior communications and cyber capabilities.
Now, thanks to rapid advances by Russia and China, the gap has shrunk, and the Pentagon is looking at how a future conflict with a "near-peer" competitor might play out.
Air Force Secretary Heather Wilson recently warned that both Russia and China are experimenting with ways to take out the US military's satellites, which form the backbone of America's warfighting machine.
"They know that we are dominant in space, that every mission the military does depends on space, and in a crisis or war they are demonstrating capabilities and developing capabilities to seek to deny us our space assets," Wilson said.
"We're not going to let that happen."
The Pentagon is investing in a new generation of satellites that will provide the military with better accuracy and have better anti-jamming capabilities.
Such technology would help counter the type of "asymmetric" warfare practised by Russia, which combines old-school propaganda with social media offensives and cyber hacks.
Washington has blamed Moscow for numerous cyber attacks, including last year's massive ransomware attack, known as NotPetya, which paralyzed thousands of computers around the world.
US cyber security investigators have also accused the Russian government of a sustained effort to take control of critical US infrastructure systems, including the energy grid.
Russia denies involvement and so far, such attacks have been met with a muted US military response.
- Public relations shutdown -
General John Hyten, who leads US Strategic Command (STRATCOM), told lawmakers the US has "not gone nearly far enough" in the cyber domain.
He also warned that the military still does not have clear authorities and rules of engagement for when and how it can conduct offensive cyber ops.
"Cyberspace needs to be looked at as a warfighting domain, and if somebody threatens us in cyberspace, we need to have the authorities to respond," Hyten told lawmakers this week.
Hyten's testimony comes after Admiral Michael Rogers, who heads both the NSA -- the leading US electronic eavesdropping agency -- and the new US Cyber Command, last month said President Donald Trump had not yet ordered his spy chiefs to retaliate against Russian interference in the 2016 US election.
Russia has also been blamed for the March 4 poisoning of former spy Sergei Skripal and his daughter Yulia, who were found unconscious on a bench outside a shopping center in England.
NATO countries are working to determine when a cyber attack might trigger the alliance's Article 5 collective defense provision, General Curtis Scaparrotti, the commander of NATO forces in Europe, said this month.
NATO "recognizes the difficulty in indirect or asymmetric activity that Russia is practising, activities below the level of conflict," Scaparrotti said.
In 2015, the Air Force opened the highly secretive National Space Defense Center in Colorado, where airmen work to identify potential threats to America's satellite network.
After officials told a local newspaper, The Gazette, that the center had started running on a 24-hour basis, Air Force higher ups grew alarmed that too much information had been revealed.
In an example of how sensitive the issue of cybersecurity now is, the Air Force reacted by putting its entire public operations department on a "stand down" while it reviews how it interacts with journalists.
One Year Later, Hackers Still Target Apache Struts Flaw
26.3.2018 securityweek Vulnerebility
One year after researchers saw the first attempts to exploit a critical remote code execution flaw affecting the Apache Struts 2 framework, hackers continue to scan the Web for vulnerable servers.
The vulnerability in question, tracked as CVE-2017-5638, affects Struts 2.3.5 through 2.3.31 and Struts 2.5 through 2.5.10. The security hole was addressed on March 6, 2017 with the release of versions 2.3.32 and 2.5.10.1.
The bug, caused due to improper handling of the Content-Type header, can be triggered when performing file uploads with the Jakarta Multipart parser, and it allows a remote and unauthenticated attacker to execute arbitrary OS commands on the targeted system.
The first exploitation attempts were spotted one day after the patch was released, shortly after someone made available a proof-of-concept (PoC) exploit. Some of the attacks scanned servers in search of vulnerable Struts installations, while others were set up to deliver malware.
Guy Bruneau, researcher and handler at the SANS Internet Storm Center, reported over the weekend that his honeypot had caught a significant number of attempts to exploit CVE-2017-5638 over the past two weeks.
The expert said his honeypot recorded 57 exploitation attempts on Sunday, on ports 80, 8080 and 443. The attacks, which appear to rely on a publicly available PoC exploit, involved one of two requests designed to check if a system is vulnerable.
Bruneau told SecurityWeek that he has yet to see any payloads. The researcher noticed scans a few times a week starting on March 13, coming from IP addresses in Asia.
“The actors are either looking for unpatched servers or new installations that have not been secured properly,” Bruneau said.
The CVE-2017-5638 vulnerability is significant as it was exploited by cybercriminals last year to hack into the systems of U.S. credit reporting agency Equifax. Attackers had access to Equifax systems for more than two months and they managed to obtain information on over 145 million of the company’s customers.
The same vulnerability was also leveraged late last year in a campaign that involved NSA-linked exploits and cryptocurrency miners.
This is not the only Apache Struts 2 vulnerability exploited by malicious actors since last year. In September, security firms warned that a remote code execution flaw tracked as CVE-2017-9805 had been exploited to deliver malware.
Watering Hole Attack Exploits North Korea's Flash Flaw
26.3.2018 securityweek Exploit
An attack leveraging the compromised website of a Hong Kong telecommunications company is using a recently patched Flash vulnerability that has been exploited by North Korea since mid-November 2017, Morphisec warns.
The targeted vulnerability, CVE-2018-4878, first became public in early February, after South Korea’s Internet & Security Agency (KISA) issued an alert on it being abused by a North Korean hacker group. Adobe patched the flaw within a week.
By the end of February, cybercriminals were already abusing the vulnerability. The newly observed incident, Morphisec notes, is a textbook case of a watering hole assault. As part of such attacks, which are mainly focused on cyber-espionage, actors plant malware on websites their victims are likely to visit.
The newly observed incident revealed advanced evasive characteristics, as it was purely fileless, without persistence or any trace on the disk. Furthermore, it used a custom protocol on a non-filtered port.
“Generally, this advanced type of watering hole attack is highly targeted in nature and suggests that a very advanced group is behind it,” the security researchers note.
The Flash exploit used in this assault was highly similar to the one detailed in the previous analysis of the CVE-2018-4878 vulnerability, albeit it employs a different shellcode executed post exploitation.
The shellcode executes rundll32.exe and overwrites its memory with malicious code. This malicious code was designed to download additional code directly into the memory of the rundll32 process.
The security researchers also discovered that the command and control (C&C) server uses a custom protocol over the 443 port to communicate with the victim.
The additional code downloaded into the memory of rundll32 includes Metasploit Meterpreter and Mimikatz modules. Most of the modules were compiled on February 15, less than a week before the attack.
“As our analysis shows, this watering hole attack is of advanced evasive nature. Being purely fileless, without persistence or any trace on the disk, and the use of custom protocol on a non-filtered port, makes it a perfect stepping stone for a highly targeted attack chain. This clearly suggests that very advanced threat actors are responsible for it,” Morphisec says.
Despite these advanced evasive features, the attack used basic Metasploit framework components that were compiled just before the attack and lacked any sophistication, obfuscation or evasion, which creates confusion and makes it difficult to pinpoint the attack to an actor.
According to Morphisec, this attack, the exploit kits that were updated to target CVE-2018-4878, the campaign observed a few weeks ago, the vulnerability’s abuse by nation-based groups, all creates a certain sense of déjà vu.
“It is like the anarchy of 2-3 years ago when we had new exploits targeting a particular vulnerability discovered every week. Each one different enough to evade detection for those crucial first moments and security solutions always racing to catch up,” the security firm concludes.
Former Barclays CISO to Head WEF's Global Center for Cybersecurity
26.3.2018 securityweek Cyber
Troels Oerting to Head the Global Centre for Cybersecurity
The 48th annual meeting of the World Economic Forum (WEF) at Davos, Switzerland, in January announced the formation of a new Global Centre for Cybersecurity. Today it announced that Troels Oerting will be its first Head, assuming the role on April 2, 2018.
Oerting has been the group chief information security officer (CISO) at Barclays since February 2015. Before that he was head of the European Cybercrime Centre (EC3) -- part of Europol formed in 2013 to strengthen LEA response to cross-border cybercrime in the EU -- and head of the Europol Counter Terrorist and Financial Intelligence Center (since 2012). He also held several other law enforcement positions (such as Head of the Serious Organised Crime Agency with the Danish National Police), and also chaired the EU Financial Cybercrime Coalition.
Oerting brings to WEF's Global Center for Cybersecurity a unique combination of hands-on cybersecurity expertise as Barclay's CISO, together with experience of and contacts within European-wide cyber intelligence organizations, and a deep knowledge of the financial crimes that will be of particular significance to WEF's members. It is a clear statement from the WEF that the new center should be taken seriously.
“The Global Centre for Cybersecurity is the first global platform to tackle today’s cyber-risks across industries, sectors and in close collaboration with the public sector. I’m glad that we have found a proven leader in the field who is keen and capable to help us address this dark side of the Fourth Industrial Revolution,” said Klaus Schwab, founder and executive chairman of the World Economic Forum.
WEF's unique position at the heart of trans-national business, with the ear of governments, provides the opportunity to develop a truly global approach to cybersecurity. Most current cybersecurity regulations and standards are based on national priorities aimed against an adversary that knows no national boundaries. The aims of the new center are to consolidate existing WEF initiatives; to establish an independent library of best practices; to work towards an appropriate and agile regulatory framework on cybersecurity; and to provide a laboratory and early-warning think tank on cybersecurity issues.
Law enforcement arrested the head of the Carbanak gang that stole 1 billion from banks
26.3.2018 securityaffairs Virus
The head of the crime ring behind the Carbanak gang that since 2013 targeted banks worldwide has been arrested in Spain.
The mastermind suspected of stealing about £870m (€1bn) in a bank cyber heist has been arrested in Spain.
The man is suspected to be the kingpin of the crime ring behind the Carbanak gang that since 2013 targeted banks worldwide with the homonym malware and the Cobalt malicious code.
“The leader of the crime gang behind the Carbanak and Cobalt malware attacks targeting over a 100 financial institutions worldwide has been arrested in Alicante, Spain, after a complex investigation conducted by the Spanish National Police, with the support of Europol, the US FBI, the Romanian, Belarussian and Taiwanese authorities and private cyber security companies.” reads the official announcement from the Europol. “Since 2013, the cybercrime gang have attempted to attack banks, e-payment systems and financial institutions using pieces of malware they designed, known as Carbanak and Cobalt. The criminal operation has struck banks in more than 40 countries and has resulted in cumulative losses of over EUR 1 billion for the financial industry. The magnitude of the losses is significant: the Cobalt malware alone allowed criminals to steal up to EUR 10 million per heist.”
The operation that allowed to arrest the head of the gang was conducted by the Europol, the FBI, along with cyber-security firms and law enforcement agencies in Spain, Romania, Belorussia and Taiwan.
In early 2016, the Carbanak gang target banks and financial institutions, mainly in the US and the Middle East.The Carbanak gang was first discovered by Kaspersky Lab in 2015. the group has stolen arounbd 1 billionn from 100 financial institutions.
In November 2016, experts at Trustwave uncovered a new campaign launched by the group targeting organizations in the hospitality sector.
In January 2017, the Carbanak gang started using Google services for command and control (C&C) communication.
The arrest was the result of one of the most important investigations conducted by the European authorities.
“This global operation is a significant success for international police cooperation against a top level cybercriminal organisation. The arrest of the key figure in this crime group illustrates that cybercriminals can no longer hide behind perceived international anonymity.” said Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3). “This is another example where the close cooperation between law enforcement agencies on a worldwide scale and trusted private sector partners is having a major impact on top level cybercriminality.”
Which is the Carbanak modus operandi?
The infection started with a classic spear phishing attack that allowed Carbanak cybergang to compromise banks’ computer systems. The malicious emails included a link that once clicked triggered the download of the malware.
The malicious code was used by the hackers of the Carbanak cybergang to gather information on the targeted bank, for example, to find employees who were in charge of cash transfer systems or ATMs. In a second phase of the attacks, the hackers installed a remote access tool (RAT) to control the machines of those employees. With this tactic the Carbanak cybergang collected imagines of victims’ screens and study what their daily activity in the bank. At this point, the hackers were able to remotely control the ATMs to dispense money or transfer money to fake accounts.

“The bank’s internal computers, used by employees who process daily transfers and conduct bookkeeping, had been penetrated by malware that allowed cybercriminals to record their every move. The malicious software lurked for months, sending back video feeds and images that told a criminal group — including Russians, Chinese and Europeans — how the bank conducted its daily routines, according to the investigators.
Then the group impersonated bank officers, not only turning on various cash machines, but also transferring millions of dollars from banks in Russia, Japan, Switzerland, the United States and the Netherlands into dummy accounts set up in other countries.” reported the New York Times
Facebook collected call and SMS data from Android users if not explicitly forbidden
26.3.2018 securityaffairs Social
After the Cambridge Analytica scandal, Facebook made the headlines again, the company collected users’ Android call and SMS metadata for years.
The Cambridge Analytica case it raised the discussion about the power of social networks and the possibility of their abuse for the conditioning of political activities.
The non-professionals have discovered how important their digital experience is and how companies specialized in data analysis operate without their knowledge.
Social network platforms have an impressive quantity of information about and are able not only to profile us but also to influence our choice.
Six years ago I was banned by the “democratic” Wikipedia because I coined a term that described how it is possible to manipulate social network, the voice “Social network poisoning,” was deleted by Wikipedia English but it is still present in Wikipedia Italian version.
Give a look at the translated version … and if you have friends at Wikipedia tell them that was an error to ban me
https://translate.google.it/translate?sl=it&tl=en&js=y&prev=_t&hl=it&ie=UTF-8&u=https%3A%2F%2Fit.wikipedia.org%2Fwiki%2FSocial_Network_Poisoning&edit-text=
Back to the present, many of you probably still don’t know that if you have installed Facebook Messenger app on your Android device, there are chances that the social network giant had been collecting your data (the start time for each call, the duration, and the contact’s name), including contacts, SMS data but not the text, and call history data at least until late last year.
The Facebook Messenger app logged phone call data only related to numbers saved in the phone’s address book. Facebook was collecting such kind of data, this is not a surprise for tech-savvy people because we have discussed it in the past.
In January, the popular Italian expert Simone Margaritelli wrote a blog post (Italian) on Medium inviting users to uninstall Facebook and Whatsapp.
The programmer Dylan McKay was able to find data, including logs of calls and SMS messages, in an archive he downloaded (as a ZIP file) from Facebook.
Mat Johnson, a Professor at the University of Houston Creative Writing Program, also made the same disturbing discovery.
Mat Johnson
✔
@mat_johnson
Oh wow my deleted Facebook Zip file contains info on every single phone cellphone call and text I made for about a year- cool totally not creepy.
12:54 AM - Mar 24, 2018
3,066
2,072 people are talking about this
Twitter Ads info and privacy
The Cambridge Analytica case has is giving users another point of view regarding the collection of such kind of data made by Facebook and the real way they are using for.
A Facebook spokesperson explained that the platform collects this data to improve the users’ experience.

“This [above] screen in the Messenger application offers to conveniently track all your calls and messages. But Facebook was already doing this surreptitiously on some Android devices until October 2017, exploiting the way an older Android API handled permissions.” wrote Sean Gallagher, Ars Technica’s IT and National Security Editor.
“Facebook began explicitly asking permission from users of Messenger and Facebook Lite to access SMS and call data to “help friends find each other” after being publicly shamed in 2016 over the way it handled the “opt-in” for SMS services. That message mentioned nothing about retaining SMS and call data, but instead it offered an “OK” button to approve “keeping all of your SMS messages in one place.””
Facebook denied to collect call data surreptitiously with an official blog post, the social network giant highlighted that it never commercialized the data and that users are in total control of the data uploaded to the platform.
“When you sign up for Messenger or Facebook Lite on Android, or log into Messenger on an Android device, you are given the option to continuously upload your contacts as well as your call and text history.” reads the blog post published by Facebook. “For Messenger, you can either turn it on, choose ‘learn more’ or ‘not now’. On Facebook Lite, the options are to turn it on or ‘skip’. If you chose to turn this feature on, we will begin to continuously log this information, which can be downloaded at any time using the Download Your Information tool.”
Users can check data collected by Facebook going to your Facebook Settings→Download a copy of your Facebook data→Start My Archive.
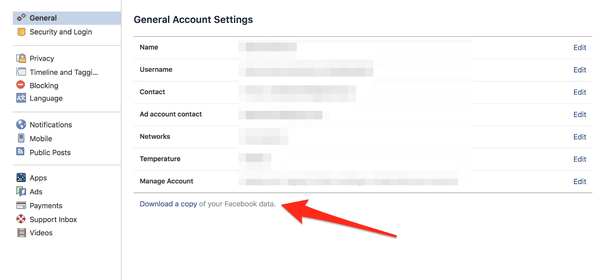
“Call and text history logging is part of an opt-in feature for people using Messenger or Facebook Lite on Android. This helps you find and stay connected with the people you care about, and provide you with a better experience across Facebook. People have to expressly agree to use this feature. If, at any time, they no longer wish to use this feature they can turn it off in settings, or here for Facebook Lite users, and all previously shared call and text history shared via that app is deleted. While we receive certain permissions from Android, uploading this information has always been opt-in only.” continues Facebook.
If you want to stop Facebook from continuously upload your contacts to its server, you can turn off the uploading feature in the Messenger app. In this way, all previously uploaded contacts will be deleted.
iOS users are not affected by this issue.
Lesson leaned … every time we use an app it is essential to carefully read the documentation that details its work.
The Internet Engineering Task Force has finally announced the approval of TLS 1.3
26.3.2018 securityaffairs Safety
The Internet Engineering Task Force (IETF) has finally announced the approval of TLS 1.3, the new version of the Transport Layer Security traffic encryption protocol.
It was a long journey, the IETF has been analyzing proposals for TLS 1.3 since April 2014, the final release is the result of the work on 28 drafts.
The TLS protocol was designed to allow client/server applications to communicate over the Internet in a secure way preventing message forgery, eavesdropping, and tampering.
TLS 1.2 and TLS 1.3 are quite different, the new version introduces many major features to improve performance and to make the protocol more resilient to certain attacks such as the ROBOT technique.
Below the description of one of the most important changes introduced with TLS 1.3:
The list of supported symmetric algorithms has been pruned of all algorithms that are considered legacy. Those that remain all use Authenticated Encryption with Associated Data (AEAD) algorithms. The ciphersuite concept has been changed to separate the authentication and key exchange mechanisms from the record protection algorithm (including secret key length) and a hash to be used with the key derivation function and HMAC.
A 0-RTT mode was added, saving a round-trip at connection setup for some application data, at the cost of certain security properties.
Static RSA and Diffie-Hellman cipher suites have been removed; all public-key based key exchange mechanisms now provide forward secrecy.
All handshake messages after the ServerHello are now encrypted. The newly introduced EncryptedExtension message allows various extensions previously sent in clear in the ServerHello to also enjoy confidentiality protection from active attackers.
The key derivation functions have been re-designed. The new design allows easier analysis by cryptographers due to their improved key separation properties. The HMAC-based Extract-and-Expand Key Derivation Function (HKDF) is used as an underlying primitive.
The handshake state machine has been significantly restructured to be more consistent and to remove superfluous messages such as ChangeCipherSpec (except when needed for middlebox compatibility).
Elliptic curve algorithms are now in the base spec and new signature algorithms, such as ed25519 and ed448, are included. TLS 1.3 removed point format negotiation in favor of a single point format for each curve.
Other cryptographic improvements including the removal of compression and custom DHE groups, changing the RSA padding to use RSASSA-PSS, and the removal of DSA.
The TLS 1.2 version negotiation mechanism has been deprecated in favor of a version list in an extension. This increases compatibility with existing servers that incorrectly implemented version negotiation.
Session resumption with and without server-side state as well as the PSK-based ciphersuites of earlier TLS versions have been replaced by a single new PSK exchange.
TLS 1.3
TLS 1.3 deprecates old cryptographic algorithms entirely, this is the best way to prevent the exploiting of vulnerabilities that affect the protocol and that can be mitigated only when users implement a correct configuration.
In the last few years, researchers discovered several critical issues in the protocol that have been exploited in attacks.
In February, the OpenSSL Project announced support for TLS 1.3 when it unveiled OpenSSL 1.1.1, which is currently in alpha.
One of the most debated problems when dealing with TLS is the role of so-called middleboxes, many companies need to inspect the traffic for security purposes and TLS 1.3 makes it very hard.
“The reductive answer to why TLS 1.3 hasn’t been deployed yet is middleboxes: network appliances designed to monitor and sometimes intercept HTTPS traffic inside corporate environments and mobile networks. Some of these middleboxes implemented TLS 1.2 incorrectly and now that’s blocking browsers from releasing TLS 1.3. However, simply blaming network appliance vendors would be disingenuous.” reads a blog post published by Cloudflare in December that explained the difficulties of mass deploying for the TLS 1.3.
According to the tests conducted by the IETF working group in December 2017, there was around a 3.25 percent failure rate of TLS 1.3 client connections.
IETF Approves TLS 1.3
26.3.2018 securityweek Safety
The Internet Engineering Task Force (IETF) last week announced the approval of version 1.3 of the Transport Layer Security (TLS) traffic encryption protocol. The Internet standards organization has been analyzing proposals for TLS 1.3 since April 2014 and it took 28 drafts to get it to its current form.
TLS is designed to allow client and server applications to communicate over the Internet securely. It provides authentication, confidentiality, and integrity mechanisms that should prevent eavesdropping and tampering, even by an attacker who has complete control over the network.IETF approves TLS 1.3
There are nearly a dozen major functional differences between TLS 1.2 and TLS 1.3, including ones that should improve performance and eliminate the possibility of certain types of attacks, such as the recently disclosed ROBOT method. The most important changes have been described by the IETF as follows:
The list of supported symmetric algorithms has been pruned of all algorithms that are considered legacy. Those that remain all use Authenticated Encryption with Associated Data (AEAD) algorithms. The ciphersuite concept has been changed to separate the authentication and key exchange mechanisms from the record protection algorithm (including secret key length) and a hash to be used with the key derivation function and HMAC.
A 0-RTT mode was added, saving a round-trip at connection setup for some application data, at the cost of certain security properties.
Static RSA and Diffie-Hellman cipher suites have been removed; all public-key based key exchange mechanisms now provide forward secrecy.
All handshake messages after the ServerHello are now encrypted. The newly introduced EncryptedExtension message allows various extensions previously sent in clear in the ServerHello to also enjoy confidentiality protection from active attackers.
The key derivation functions have been re-designed. The new design allows easier analysis by cryptographers due to their improved key separation properties. The HMAC-based Extract-and-Expand Key Derivation Function (HKDF) is used as an underlying primitive.
The handshake state machine has been significantly restructured to be more consistent and to remove superfluous messages such as ChangeCipherSpec (except when needed for middlebox compatibility).
Elliptic curve algorithms are now in the base spec and new signature algorithms, such as ed25519 and ed448, are included. TLS 1.3 removed point format negotiation in favor of a single point format for each curve.
Other cryptographic improvements including the removal of compression and custom DHE groups, changing the RSA padding to use RSASSA-PSS, and the removal of DSA.
The TLS 1.2 version negotiation mechanism has been deprecated in favor of a version list in an extension. This increases compatibility with existing servers that incorrectly implemented version negotiation.
Session resumption with and without server-side state as well as the PSK-based ciphersuites of earlier TLS versions have been replaced by a single new PSK exchange.
The most controversial of these changes is related to the introduction of the 0-RTT (zero round trip time resumption) mode. This feature brings significant improvements in terms of speed, particularly in the case of resumed connections, but it makes the connection slightly less secure.
The main concern are replay attacks, but experts believe the risk is manageable and website administrators should not have anything to worry about. However, some members of the IETF believe there are bound to be successful attacks against existing mitigations in the future. Cloudflare published a blog post last year detailing 0-RTT benefits and risks.
Cloudflare announced support for TLS 1.3 in September 2016, but the company reported in late December 2017 that major web browsers had yet to enable the new version of the protocol by default, with only 0.06% of the traffic passing through its network leveraging TLS 1.3.
Cloudflare has blamed this delay on network appliances that need to intercept HTTPS traffic on corporate networks, and the original design of TLS 1.3. Poor implementation of TLS 1.3 has been known to cause serious problems.
The OpenSSL Project announced support for TLS 1.3 in February when it unveiled OpenSSL 1.1.1, which is currently in alpha.
Reddit banned the biggest Darknet markets subreddit /R/DarkNetmarkets
26.3.2018 securityaffairs CyberCrime
Recently Reddit decided to ban the biggest darknet subreddit, /r/darknetmarkets, used by crime communities to discuss producta and services in the most popular darknet markets.
Darknet markets have a crucial role in the cybercrime underground, they are excellent places of aggregation for the demand and the offer of illegal products and services.
Communities around principal Darknet markets use to exchange information about products and services also on the clear web, for example using the Reddit social media platform.
Now Reddit decided to ban the biggest darknet subreddit, /r/darknetmarkets, used for darknet-related conversation.
Officially, Reddit maintainers banned the subreddit because the community violated Reddit’s illegal transaction rules.
“this subreddit was banned due to a violation of Reddit’s policy against transactions involving prohibited goods or services.” states Reddit,

Reddit forbids direct deals related to illegal products and services, in the specific case, subreddit violated rules about the sourcing of illegal drugs.
The moderators initially deleted posts containing drug sourcing. but the subreddit was considered a source of darknet drug market addresses.
This isn’t the first ban related to darknet markets, Reddit banned in 2015 the subreddit Evolution and the recent ban of the DNM UK and DNM OZ subreddits.
“In addition to the main subreddit, Reddit banned two subreddits for sourcing research chemicals (r/EU_RCSources and RCSources); a second UK darknet market subreddit (r/DarknetUK); and subreddits specific to individual darknet markets (r/RaptureMarket, r/dreammarket2, and r/dream_dnm).” states a blog post published on deepdotweb.com
“The era of discussing darknet markets on the clearnet has likely ended.”
Even if Reddit has banned the subreddit, operators of the black markets will simply migrate to other platforms to share their content.
If you are searching for more info on Darknet markets and cyber criminal communities in the dark web give a look at my new book, titled ‘Digging the Deep Web: Exploring the dark side of the web“.