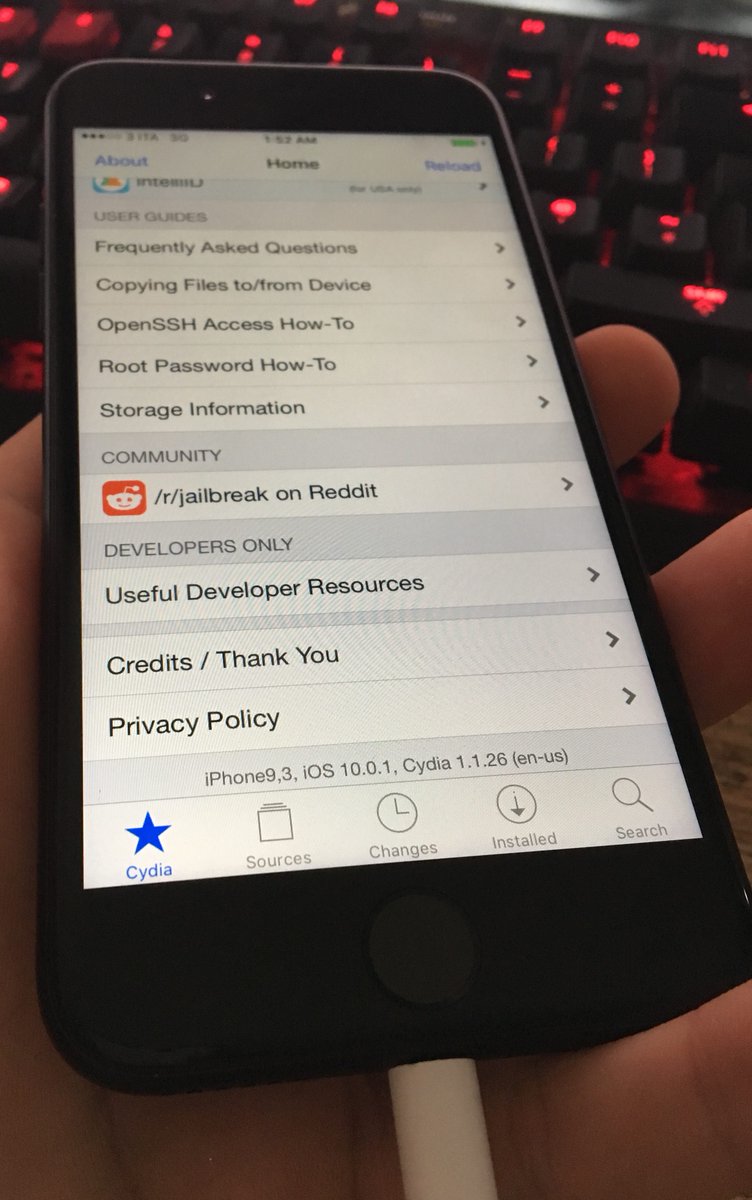
The image shows an iPhone 7 running both iOS 10.0.1 as well as the Cydia repository, used by owners of jailbroken device to install apps and other software that Apple does not officially support.
Young hacker Luca Todesco announced the iPhone 7 jailbreak
23.9.2016 thehackernews Apple
The popular hacker Luca Todesco (aka @qwertyoruiopz) has announced the existence of the iPhone 7 jailbreak for devices running iOS 10.
Only a few hours, this is the time spent by the popular hacker Luca Todesco (aka @qwertyoruiopz) to jailbreak the new and secure iPhone 7. The iPhone 7 was launched by Apple a few days ago and of course, hackers worldwide started their race to jailbreak the new device.
The 19-year-old hacker Luca Todesco shared via Twitter an image of his jailbroken iPhone 7, not so bad! The expert exploited a series of bugs to hack the device in just 24 hours and demonstrating that also the iPhone 7 is “not 100 percent secure-like nothing else is“
Visualizza l'immagine su Twitter
Visualizza l'immagine su Twitter
Segui
qwertyoruiop @qwertyoruiopz
obligatory cydia screenshot
11:00 - 21 Set 2016
333 333 Retweet 619 619 Mi piace

The image shows an iPhone 7 running both iOS 10.0.1 as well as the Cydia repository, used by owners of jailbroken device to install apps and other software that Apple does not officially support.

Cydia is an application very popular within the community of iOS Apple users, it is the jailbreaker’s App Store alternative for iOS. The unofficial store contains thousands of apps, themes, and many other downloads. Using Cydia iOs users can find and install applications on their jailbroken iOS Apple devices, the majority of the software in the store are available for free.
At the time I was writing it is not clear if Todesco will release the iPhone 7 jailbreak to the public, he hasn’t provided much information about the hack, for example he doesn’t explain if the exploit is an untethered jailbreak.
An untethered jailbreak is a procedure that doesn’t require the iPhone any reboot every time it connects to an external device capable of executing commands on the device.
The untethered jailbreak is more complicated, it makes the jailbroken device totally independent of the computer and allows users turning off and on the device without problems.
While the tethered jailbreak code is seen from iBoot, the untethered jailbreak totally resides on the device.
iPhone 7 jailbreak
The hacking community is celebrating the news, although Todesco has not released the exploit, he showed that it is possible to hack the iPhone 7.
Only you do now is sit and wait for a team that will release an untethered jailbreak for the new iPhone 7.Since it is not good news for Apple, the company would likely block the vulnerability used to develop jailbreak in its next iOS update, of course.
As of October 5, automatic OAuth 2.0 token revocation upon password reset
23.9.2016 securityaffairs Security
Google announced a change to its security policy to increase the account security that includes the OAuth 2.0 token revocation upon password reset.
Google has finally announced a new OAuth 2.0 token revocation according to its security policy, the company will roll out the change starting on Oct. 5.
The change to the Google security policy was announced last year by Google, the company explained that OAuth 2.0 tokens would be revoked when a user’s password was changed.
Google decided not to move forward with this change for Apps customers and began working on a more admin-friendly approach.
The company has implemented the OAuth 2.0 authentication protocol in 2012 with the intent of boosting the security of its services like Gmail and Google Talk.
Google aims to improve users’ security limiting the impact on the usability of its application, at least in this first phase so although initially planned for a wider set of applications, the OAuth 2.0 token revocation rule will be limited to the email mail service.
Google confirmed that the App Script tokens and apps installed via the Google Apps Marketplace are not subject to the token revocation.
“To achieve the security benefits of this policy change with minimal admin confusion and end-user disruption, we’ve decided to initially limit the change to mail scopes only, and to exclude Apps Script tokens. Apps installed via the Google Apps Marketplace are also not subject to the token revocation.” reads the Google announcement. “Once this change is in effect, third-party mail apps like Apple Mail and Thunderbird―as well as other applications that use multiple scopes that include at least one mail scope―will stop syncing data upon password reset until a new OAuth 2.0 token has been granted. A new token will be granted when the user re-authorizes with their Google account username and password.”
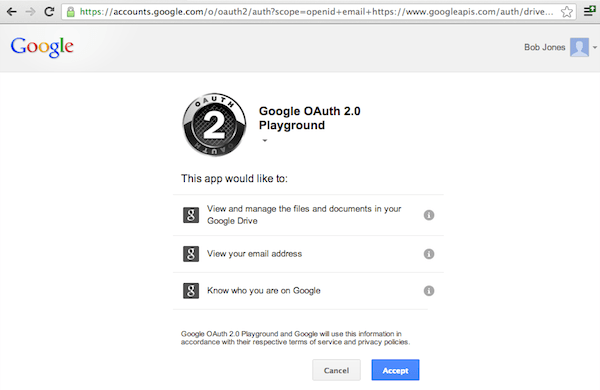
After the change will be effective, third-party mail applications that include at least one mail scope will no longer sync data when the user password is reset. The data syncing will start again after a new OAuth 2.0 token has been granted.
The change will impact also mobile users, it will affect for example mail applications. The Apple iOS users who use the mail application included in the mobile OS will have to re-authorize it with their Google account credentials when they change their password.
This is nothing new for Gmail apps on both iOS and Android the already require to grant a new OAuth 2.0 token upon password reset, but Google will enforce the change also to third-party apps.
For further information on the new OAuth 2.0 token revocation rule give a look at the post published by Google that includes also a list of FAQ
BT Wi-Fi extender, extends to XSS and password changing vulnerabilities
23.9.2016 securityaffairs Vulnerebility
Following an investigation by Pen Test Partners, British Telecom (BT) has released a firmware upgrade for their popular range of Wi-Fi extenders.
The investigation uncovered vulnerabilities within the firmware when left the device exposed to possible XSS (Cross Site Scripting) Exploits as well as the ability to change the user’s password without notification.
By combining these flaws it was proved possible to grab the victim’s WPA passphrase following tricking them into visiting a maliciously crafted website from their home network.
BT was quick to offer an upgrade, available here, which resolves the issues. The telecommunications giant were also quick to credit Pen Test Partners, thanking them for the discovery:
“We are grateful to Pen Test Partners for alerting us to this issue. We have been working to address this potential weakness and issued an update which corrected the problem in August 2016. We are not aware of any cases where customers have suffered any issues. Customers should ensure they download the firmware update from the BT website.”
The report detailed that a malformed JavaScript could be created and spammed over the local network (if the IP of the extender was unknown), which could be crafted to change the password without ever seeking verification of the previous password, as is standard in many applications.
The var:errorpage parameter within the configuration was also found to be vulnerable, this time to XSS. The device also didn’t validate input or its HTML encoding when it rewrites changes back out to the web page.
Altering cookie parameters also allowed unauthenticated users to glean username and passwords directly.
“The var:errorpage parameter seems to be vulnerable to reflected cross-site scripting because it is not correctly validated on input, nor HTML-encoded when it is written out to the web page again.
Example:

Also, if we try it with document[.]cookie instead of ‘1’, we get to see the username and password.” states the report from Pen Test Partners.
Pen Test Partners combined these vulnerabilities, grabbed the cookies and ended up with the victim’s NAT IP, admin password, SSID as well as their Pre-Shared Key.
The popularity of BT Wi-Fi extenders, as well as, the extent of the vulnerabilities and relative ease of performing this exploit means that all home users without version 1.1.8, if they haven’t done so, should stop what they’re doing, especially if it’s online, and upgrade immediately.
Yahoo Data Breach, the company confirms the incident that exposed 500M accounts
23.9.2016 securityaffairs Incindent
The announcement about the Yahoo data breach is online, the company confirmed that hackers managed to access data from at least 500 million user accounts.
Today I wrote about the imminent announce of the Yahoo data breach related to an incident that resulted in the leakage of 200 million Yahoo account credentials this summer.
The company has finally made the announce, the news related the Yahoo data breach is in the headlines. The IT giant confirmed that hackers have stolen at least 500 million user accounts in a data breach dating back to 2014.
Yahoo also added that its security experts suspect the involvement of nation-state actors.
“We have confirmed that a copy of certain user account information was stolen from the company’s network in late 2014 by what it believes is a state-sponsored actor. The account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (the vast majority with bcrypt) and, in some cases, encrypted or unencrypted security questions and answers.” reads the security notice issued by Yahoo.
“The ongoing investigation suggests that stolen information did not include unprotected passwords, payment card data, or bank account information; payment card data and bank account information are not stored in the system that the investigation has found to be affected. Based on the ongoing investigation, Yahoo believes that information associated with at least 500 million user accounts was stolen and the investigation has found no evidence that the state-sponsored actor is currently in Yahoo’s network. Yahoo is working closely with law enforcement on this matter.”
This summer the notorious hacker Peace advertised 200 Million Yahoo accounts on Dark Web, and the company was aware of the sale.
Peace offered for sale the 200 million of Yahoo account credentials (from “2012 most likely,”) on The Real Deal black marketplace. Yahoo was informed of the events and launched an internal investigation avoiding public comment on the case. The hacker was offering the data leak for 3 bitcoins (roughly $1,800 at the time of the disclosure).

The security notice informs users that the company is taking the necessary action to protect them. Below the list published by Yahoo:
We are notifying potentially affected users. The content of the email Yahoo is sending to those users will be available at https://yahoo.com/security-notice-content beginning at 11:30 am (PDT).
We are asking potentially affected users to promptly change their passwords and adopt alternate means of account verification.
We invalidated unencrypted security questions and answers so they cannot be used to access an account.
We are recommending that all users who haven’t changed their passwords since 2014 do so.
We continue to enhance our systems that detect and prevent unauthorized access to user accounts.
We are working closely with law enforcement on this matter.
We encourage our users to follow these security recommendations:
Change your password and security questions and answers for any other accounts on which you used the same or similar information used for your Yahoo account.
Review your accounts for suspicious activity.
Be cautious of any unsolicited communications that ask for your personal information or refer you to a web page asking for personal information.
Avoid clicking on links or downloading attachments from suspicious emails.
Yahoo is encouraging users to use the Yahoo Account Key in order to definitively eliminates the need to use a password.
iPhone 7 Jailbreak Has Already Been Achieved In Just 24 Hours!
22.9.2016 thehackernews Apple
It has only been a few days since the launch of Apple's brand new iPhone 7 and iPhone 7 Plus, but it appears that the new iPhone has already been jailbroken.
That didn't take long. Right?
Security researcher and well-known hacker Luca Tedesco shared an image of his jailbroken smartphone on his Twitter account to show off the world that the new iPhone 7 has been jailbroken.
The image posted by Tedesco on Wednesday clearly shows an iPhone 7 running both iOS 10.0.1 as well as the Cydia app store, which allows jailbreakers to install apps and other software that Apple does not officially support.
Unfortunately, Tedesco has not publically released the exploit, nor he has provided much information about it. So, right now, it is hard to say if and when he will release the iPhone 7 jailbreak to the public.
It is also not clear whether the exploit is an untethered jailbreak.
The untethered jailbreak is a jailbreak where your device doesn't require any reboot every time it connects to an external device capable of executing commands on the device.
Eventually, there is no tool available yet that you can use to jailbreak your device, but the good news is that a jailbreak has already been developed, which suggests that it's indeed possible to jailbreak iPhone 7.
So, early buyers looking to jailbreak their iPhone 7 or iPhone 7 Plus and install unauthorized Cydia tweaks have to wait until firms like Pangu or someone else come up with the same exploit.
Pangu is the same Chinese jailbreak team that released the first untethered jailbreak for iOS 9.
Since it is not good news for Apple, the company would likely block the vulnerability used to develop iPhone 7 jailbreak in its next iOS update, of course.
Beware — Someone is dropping Malware-infected USB Sticks into People's Letterbox
22.9.2016 thehackernews Virus
Don't plug in that USB stick into your laptop. It could infect your computer with malware and viruses.
Australia's Victoria Police Force has issued a warning regarding unmarked USB flash drives containing harmful malware being dropped inside random people's letterboxes in the Melbourne suburb of Pakenham.
It seems to one of the latest tactics of cyber criminals to target people by dropping malware-laden USB sticks into their mailboxes, in the hope unsuspecting users will plug the infected devices into their personal or home computers.
The warning, published on the official website of the Victoria Police, one of Australia's state police departments, reads:
"Members of the public are allegedly finding unmarked USB drives in their letterboxes.
Upon inserting the USB drives into their computers victims have experienced fraudulent media streaming service offers, as well as other serious issues [malware].
The USB drives are believed to be extremely harmful and members of the public are urged to avoid plugging them into their computers or other devices."
The warning comes after a recent flood of reports from residents in the suburb of Pakenham who found compromised unmarked drives in their mailboxes and inserted them into their computers.
Although the police did not provide any further detail on the type of malware on the drives or whether the victims were served ransomware demands on running the malicious code on the drives, this is no surprise to us that some people plugged in the drives into their PCs.
Cyber Criminals are Leveraging Human Psychology
A study conducted by a group of researchers from the University of Illinois, the University of Michigan and Google revealed that nearly half of people would not only plug a USB drive they've found on the ground into their PCs, but would also open files and click on unfamiliar links.
The worst part is that people don't make this blunder unknowingly because it has long been known that USB drives can carry and transfer destructive malware and viruses to your computers, perhaps the most infamous example of it was the Stuxnet worm.
The Stuxnet sabotage malware was allegedly designed by the U.S. and Israel to disrupt Iran's nuclear facility and destroyed its uranium enrichment centrifuges in 2010. The infection is believed to have been carried through an infected USB stick.
Keeping this human psychology in mind, just last month a Hong Kong-based company started selling a USB stick, dubbed USB Kill v2, that can fry any computer it's plugged into.
So, next time when you find any USB drive or receive it in the post, show more caution and make sure you don't plug it into your laptop or computer.
Yahoo is going to confirm the data breach that exposed 200 Million Yahoo accounts
22.9.2016 securityaffairs Hacking
It’s a question of hours, security experts believe Yahoo will confirm the massive data breach that exposed at least 200 Million Yahoo accounts.
Yahoo is ready to confirm a massive data breach that affected its service that has exposed several hundred million user accounts.
“Yahoo is poised to confirm a massive data breach of its service, according to several sources close to the situation, hacking that has exposed several hundred million user accounts.” reported the website recode.net.
“While sources were unspecific about the extent of the incursion, since there is the likelihood of government investigations and legal action related to the breach, they noted that it is widespread and serious.”
In August, the notorious hacker Peace advertised 200 Million Yahoo accounts on Dark Web, and the company is aware of the sale.
Peace offered for sale the 200 million of Yahoo account credentials (from “2012 most likely,”) on The Real Deal black marketplace. Yahoo was informed of the events and launched an internal investigation avoiding public comment on the case. The hacker was offering the data leak for 3 bitcoins (roughly $1,800 at the time of the disclosure).

While the Yahoo security team was investigating the incident, the company suggested its customers to use strong passwords, one for each web service they use, and enable two-factor authentication when it is available.
Security experts believe its question of hours before the Yahoo will publicly confirm the data breach that caused at least the exposure of 200 million of Yahoo account credentials.
Of course, the news will have a significant impact on the company because the hackers attacked the core service of the IT giant. Analysts speculate a possible interference with the announced $4.8 billion sale of the company to Verizon.
CVE-2016-6374 – Don’t waste time, patch your CISCO Cloud Services Platform
22.9.2016 securityaffairs Vulnerebility
Cisco has issued a security patch to address a remote hijacking vulnerability, tracked as CVE-2016-6374, in the Cloud Services Platform (CSP).
This patch is very important, CISCO urges all customers who run CSP 2100 software to install the 2.1.0 update that addresses a “high” risk remote code execution flaw.
The CISCO Cloud Services Platform (CSP) is a product designed to manage virtualized network services and components, it runs as a Linux x86 virtual machine built into a Cisco network appliance.

The Cisco Cloud Services Platform 2100 allows to quickly deploy any Cisco or third-party network virtual service through a simple, built-in, native web user interface (WebUI), command-line interface (CLI), or representational state transfer (REST) API.
“A vulnerability in the web interface of Cisco Cloud Services Platform (CSP) 2100 could allow an unauthenticated, remote attacker to execute arbitrary code on a targeted system.” reads the security advisory published by CISCO.
According to CISCO, the exploitation of the CVE-2016-6374 flaw is simple, attackers just need to send malformed HTTP requests to achieve remote code execution. An unauthenticated attacker has to use a malicious DNS-lookup request through the CSP web interface in order to execute commands on the server.
“The vulnerability is due to insufficient sanitization of specific values received as part of a user-supplied HTTP request. An attacker could exploit this vulnerability by sending a malicious dnslookuprequest to the affected system. An exploit could allow the attacker to execute arbitrary code with the privileges of the user.”
The Cisco Product Security Incident Response Team (PSIRT) confirmed that its experts are not aware of any public announcements or malicious use of the CVE-2016-6374 vulnerability in the wild.
Cisco customers have no choice due to the absence of mitigations for the CVE-2016-6374 flaw, they need urgently to apply the patch.
A few days ago CISCO issued another patch for a high-severity vulnerability in the IOS platform that was discovered while analyzing the exploits included in the Equation Group data leak.
Inteligentní virus pro Android zneužíval popularity Pokémon Go
22.9.2016 Žive.cz Viry
Více než pět set tisíc obětí si na sklonku léta nainstalovalo aplikaci pro Android jménem Guide For Pokémon Go New. Na tom by nebyl nic zvláštního, kdyby se ovšem nejednalo o sofistikovaný malware, který poté telefon oběti zapojil do botnetu.
Specialisté z Kaspersky Lab nyní virus analyzovali a je to docela nepříjemné čtení – především z pohledu toho, jak se malware chová.
Návod na pokémony měl na Play Storu poměrně důvěryhodné hodnocení, přesto obsahoval zákeřný malware
Program totiž po instalaci nezačal okamžitě útočit, ale vyčkával i několik hodin, během kterých analyzoval, jestli skutečně běží na telefonu a nikoliv třeba ve virtuálním prostředí. Tím se snažil vyvarovat odhalení ze strany Googlu a antivirových společností.
Teprve když si byl program jistý, že je na reálném telefonu (sledoval například, jestli uživatel instaluje i další aplikace), spojil se se serverem operátora a zaslal mu informaci o typu telefonu, poloze a tak dále.
Operátor se poté rozhodl, jestli mu daný telefon vyhovuje a dal mu zelenou k samotné instalaci viru, který se pokusil zneužit zranitelností z posledních let k tomu, aby získal práva root a plnou kontrolou nad systémem.
Inteligentní virus tedy útočil pouze tam, kde se mu to vyplatilo a na ostatních telefonech byl potichu, což ještě více znesnadnilo jeho odhalení. Právě tento způsob chování a šifrování části kódu s virem, kterou obslužná aplikace rozbalí a spustí, jen když se ji to hodí, může obalamutit mnohé automatické systémy na její včasné odhalení. A takový malware pak může přežívat i na oficiálním Play Storu dostatečně dlouho k tomu, aby nakazil tisíce zařízení jako v tomto případě.
iSpy, a new sophisticated commercial keylogger in the criminal underground
22.9.2016 securityaffairs Virus
The new variant of the popular iSpy keylogger (version 3.x) was available in the criminal underground with sophisticated features.
Security researchers at Zscaler warn of a new sophisticated commercial keylogger dubbed iSpy. The malware is a perfect surveillance tool, it was developed to capture victim’s keystroke and screenshots, access webcam, steal user data and license keys to popular applications.
“Zscaler ThreatLabZ recently came across a signed keylogger campaign in our cloud sandbox. In this blog, we will provide an analysis of this malicious commercial keylogger, known as iSpy. Written in .Net 2.0, iSpy is configured for keylogging, stealing passwords and screenshots, and monitoring webcams and clipboards. It is being sold on underground forums via multiple subscription packages” states the alert issued by Zscaler.
iSpy has a modular structure, buyer can choose the features it has to include, it implements also multiple features that are designed to make it hard to detect.
The keylogger sends stolen data to C&C server via FTP, SMTP, or HTTP protocols, it gains persistence on the infected host by creating an entry in “SOFTWARE\Microsoft\Windows\CurrentVersion\Run” key under HKLM or HKCU.
The attack chain starts with spam email that has malicious JavaScript or Document as an attachment. When victims open the document iSpy is downloaded to the infected machine.
“iSpy is delivered via spam email that has malicious JavaScript or Document as an attachment, which then downloads the keylogger payload.” continues the analysis. “The main iSpy payload is usually compressed using a custom packer. So far, we have seen packers written in Visual Basic 6.0, AutoIt, and .Net. We have also seen a campaign of signed .NET crypter where iSpy was served. This crypter uses different digital certificates (mostly invalid certificates) and drops different malware samples”
The iSpy keylogger implements advanced keylogger functionalities to spy on its victims avoid detection, some of the packers analyzed by Zscaler are digitally signed with invalid certificates.
The malware researchers highlighted the presence of a license stealing feature implemented by iSpy that could be used by crooks to monetize their efforts by reselling the license keys of popular applications (i.e. Microsoft Office, Adobe Photoshop) in the cyber criminal underground.
” It also contains code to steal the license keys of application software, such as Adobe Photoshop, Microsoft Office, and others. It also collects saved passwords from web browsers, email clients (such as Outlook), FTP clients (like FileZilla and CoreFTP), and games like Minecraft.” states the analysis published by Zscaler.
ISpy is currently available for sale in several crime forums, sellers are offering multiple subscription packages including scalable technical features.
A Bronze Package which offers a one-month access to the malware, instant activation, free support and free updates goes for $25. iSpy is also offered with a “small business” package that goes for $35 and includes six-month access to the malware and six months of free support and updates.
The most popular option is the Diamond Package that costs $45 for one-year access, support, and upgrades.

The version of iSpy analyzed by Zscaler has a web panel that allows attackers to monitor all the activities on the infected system.

I suggest you give a look at the report that also includes Indicators of Compromise.
RAUM tool allows to spread malware through torrent files
22.9.2016 securityaffairs Virus
InfoArmor has discovered the RAUM tool in criminal forums, it is a special tool to distribute malware by packaging it with popular torrent files.
It is not a novelty, torrent files are a privileged channel for malware diffusion, according to a study conducted by researchers at Digital Citizens Alliance and RiskIQ, almost one-third of the 800 torrent sites served malware on the users’ machine between June and August 2015.
Now a new tool appeared on the cyber crime underground allows cyber criminals to distribute malware through torrent files in exchange for a fee.
Experts from InfoArmor discovered the tool, so-called RAUM tool, in invite-only underground forums.
According to InfoArmor, the creators of RAUM tool belong to an Eastern European organized crime group known as Black Team.
It leverages torrent files, especially games, to spread malware. The RAUM tool allows to package torrent files with malware and then uploaded for victims to download.
The experts at InfoArmor pointed out the innovative “Pay-Per-Install” model implemented by the crooks behind the RAUM tool.
“The so-called “RAUM” tool has been actively used on uncovered underground affiliate networks based on a “Pay-Per-Install” model (PPI). This model leverages paying cybercriminals to distribute malware through modified torrent files that are joined with malware. Members of these networks are invited by special invitation only, with strict verification of each new member.” reads the blog post published by InfoArmor.
The RAUM tool allows crooks to monitor the status of their malicious campaigns, through its interface, it is possible to control malware diffusion over popular sites such as The Pirate Bay and ExtraTorrent.
“Threat actors were systematically monitoring the status of the created malicious seeds on famous torrent trackers such as The Pirate Bay, ExtraTorrent and many others. In some cases, they were specifically looking for compromised accounts of other users on these online communities that were extracted from botnet logs in order to use them for new seeds on behalf of the affected victims without their knowledge, thus increasing the reputation of the uploaded files.” continues the post.

“In some cases, the lifespan of these seeded malicious files exceeded 1.5 months and resulted in thousands of successful downloads,” InfoArmor said.
In some cases, the creators of the RAUM tool have attempted to hijack the accounts of known uploaders of torrent files in order to use them to spread trojanized torrent files.
Security experts associated identified RAUM tool instances with popular ransomware such as CryptXXX, CTB-Locker and Cerber, Dridex banking Trojan, and Pony data stealer.
The report published by InfoArmor also includes the IoC for the RAUM tool.
Warning — You Can't Install Linux On Microsoft Signature Edition PCs from Lenovo
21.9.2016 thehackernews Hacking
In past few months, Microsoft opened the source code of a lot of its projects, convincing people that the company loves Linux.
But a new report shows that Microsoft is not really a big supporter of Linux.
Microsoft has banned Linux on some Windows 10 powered Signature Edition PCs, which provides the cleanest Windows experience on the market.
Signature Edition PCs are different from other systems because it is carefully and meticulously configured by Microsoft to run Windows 10 with no bloatware, paid promotional web shortcuts, or other pre-installed apps, for providing better performance.
But besides bloatware and other pre-installed apps, Microsoft won't allow you to install Linux (or any operating system) on it.
This news is not a rumor as a Reddit user BaronHK reported that he found it impossible to install Linux on the Signature Edition Lenovo Yoga 900 ISK2 UltraBook because Microsoft has locked the SSD in a proprietary RAID mode that can only be read by Windows.
When contacted Lenovo, the company confirmed that it had signed an agreement with Microsoft to make this happen.
"This system has a Signature Edition of Windows 10 Home installed. It is locked per our agreement with Microsoft," a Lenovo employee responded to a comment made by BaronHK about the issue.
Lenovo laptops that are not allowing its users to install Linux include the aforementioned Yoga 900 ISK2, the Yoga 900S, as well as the Yoga 710S.
Some have suggested that the issue that prevents Linux from being installed could be Microsoft decision, while others believe that the issue could be related to how the systems have been configured by Lenovo.
For now, all which is clear is that, if you own a Lenovo Signature Edition laptop, you can not install Linux on it.
Microsoft and Lenovo still have to officially comment on this possible restriction configured for Signature Edition PCs.
Over 840,000 Cisco systems affected by the Equation Group’s flaw CVE-2016-6415
21.9.2016 securityaffairs Vulnerebility
The Shadowserver Foundation has conducted a scan of the Internet for CISCO devices running IOS software affected by the CVE-2016-6415 vulnerability.
Recently experts from CISCO discovered a vulnerability, tracked as CVE-2016-6415, in IOS system,while investigating the Equation Group‘s exploits leaked by the Shadow Broker hacker group. In particular, experts from CISCO were evaluating the impact of the BENIGNCERTAIN exploit. The experts also discovered another zero-day exploit dubbed EXTRABACON that could be used to hack CISCO ASA software.
The CVE-2016-6415 resides in the IKEv1 packet processing code. A remote, unauthenticated attacker could exploit it retrieve memory contents.
“The vulnerability is due to insufficient condition checks in the part of the code that handles IKEv1 security negotiation requests. An attacker could exploit this vulnerability by sending a crafted IKEv1 packet to an affected device configured to accept IKEv1 security negotiation requests,” reads the security advisory published by Cisco.
The flaw affects Cisco IOS XR versions 4.3.x, 5.0.x, 5.1.x and 5.2.x – versions 5.3.0 and later are not impacted. All IOS XE releases and various versions of IOS are affected.
Which is the real impact of the CVE-2016-6415 vulnerability?
The Shadowserver Foundation tried to provide further information to estimate the impact of the vulnerability in the wild, it has conducted an Internet scan for the Internet Security Association and Key Management Protocol (ISAKMP), which is a part of IKE.
“This scan is looking for devices that contain a vulnerability in their IKEv1 packet processing code that could allow an unauthenticated, remote attacker to retrieve memory contents, which could lead to the disclosure of confidential information. More information on this issue can be found on Cisco’s site at: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160916-ikev1” reads the page related to the Vulnerable ISAKMP Scanning Project.
“The goal of this project is to identify the vulnerable systems and report them back to the network owners for remediation. Information on these vulnerable devices has been incorporated into our reports and is being reported on a daily basis.”
With the support of CISCO experts, the organization queried all computers with routable IPv4 addresses that are exposed on the Internet without firewall protection. They used a specifically crafted 64 byte ISAKMP packet collecting the response from the scanned appliance.
“We normally tune our scans as tightly as possible to limit the impact on the end users as well as trying to be nice to the general network traffic. In this case we are not as tuned as we would like to be since we are having to do a full IKE negotiation making our packets almost 2600 bytes in size, at least in the first sets of tests. With a huge amount of assistance from Cisco we were able to reduce the packet size down to 64 bytes. ” reads the page on the “ISAKMP Scanning and Potential Vulnerabilities.”
cve-2016-6415-scan
The scan results are disconcerting, the experts discovered more than 840,000 unique IP addresses related to appliances vulnerable to the CVE-2016-6415 exploit.
Below the Top 20 countries with vulnerable ISAKMP
COUNTRY TOTAL
UNITED STATES 255,606
RUSSIAN FEDERATION 42,281
UNITED KINGDOM 42,138
CANADA 41,115
GERMANY 35,132
JAPAN 33,092
MEXICO 26,970
FRANCE 26,818
AUSTRALIA 22,827
CHINA 22,767
ITALY 21,308
NETHERLANDS 17,812
POLAND 14,630
SPAIN 11,811
TURKEY 10,355
BRAZIL 9,298
CZECH REPUBLIC 8,943
UKRAINE 8,514
INDIA 8,282
KOREA, REPUBLIC OF 8,058
The highest percentage of vulnerable devices were in the United States (255,000), six times more than Russia (42,000), United Kingdom (42,000) and Canada (41,000). The experts also analyzed the autonomous system numbers (ASNs),discovering a predominance of Comcast and AT&T’s network IPs.
Below the top 20 ASNs With Vulnerable ISAKMP
ASN AS NAME COUNTRY TOTAL
AS7922 COMCAST-7922 US 35,429
AS7018 ATT-INTERNET4 US 23,660
AS8151 Uninet MX 21,014
AS3215 AS3215 FR 16,427
AS209 CENTURYLINK-US-LEGAC US 14,445
AS3320 DTAG DE 13,991
AS4713 OCN JP 11,460
AS3269 ASN IT 10,265
AS5089 NTL GB 9,389
AS4134 CHINANET CN 9,203
AS701 UUNET US 8,766
AS22773 ASN-CXA-ALL-CCI-2277 US 8,722
AS1221 ASN AU 8,194
AS20115 CHARTER-NET-HKY-NC US 8,028
AS7029 WINDSTREAM US 8,015
AS2856 BT-UK GB 7,265
AS9121 TTNET TR 7,159
AS6167 CELLCO-PART US 6,758
AS10796 SCRR-10796 US 6,733
AS2514 INFOSPHERE JP 6,688
According to Shadowserver, there is no evidence that the products of vendors other than Cisco are affected by the vulnerability, but the organization noted that it is not a conclusive test.
Cisco has released an online tool that allows its customers to determine if their products are affected by the CVE-2016-6415 flaw.
To naštve. Lidé instalovali antivirus, a přitom to byl ransomware, který jim zašifroval data
21.9.2016 Zive.cz Viry
Ransomware je jedním z nejnebezpečnějších typů malwaru, se kterým se může surfař setkat. Zatímco zapojení do spamovacího botnetu oběť fakticky nebolí, protože útočník zneužívá jen její výpočetní výkon a konektivitu, ransomware je vyděračský vir, který vám zašifruje data a klíč získáte až po zaslání určitého obnosu na anonymní bitcoinový účet.
Klepněte pro větší obrázek
Virus se vydával za antivirus, zašifroval data a požadoval výkupné
A tak lidé instalují antiviry, aby je před ransomwarem ochránily. Autoři virů si toho jsou samozřejmě vědomi, proto se pokoušejí situace využít. Před pár dny prolétla internetem zpráva, že jeden z takových virů, DetoxCrypto, se vydával přímo za zbraň, která s ním měla zatočit – za antivirový software Malwarebytes.
Oběti si tedy v dobré víře instalovali antivirový program, ve skutečnosti to však byl ransomware, který jim poté zašifroval data a požadoval výkupné 2 BTC, což po přepočtu činí skoro 30 tisíc Kč.
Klepněte pro větší obrázek
Dokud nezadáte správný klíč, data nezískáte
Podobné platby jsou přitom vždy určitou sázkou do loterie, není totiž vůbec jisté, jestli má ransomware ještě nějakého aktivního operátora, který na platbu opravdu zareaguje. Obrana před tímto typem malwaru je přitom snadná – zálohovat opravdu klíčová data, o která nechceme přijít.
Nový ransomware šifruje autonomně, bez komunikace se zločinci
21.9.2016 ComputerWorld Viry
Novou verzi ransomwaru RAA objevili experti společnosti Kaspersky Lab. Aktualizovaná verze je schopná zašifrovat data off-line, aniž by potřebovala heslo příkazového serveru.
Nový trojan se ke svým obětem dostává e-mailem, ke kterému se připojuje nebezpečný soubor s příponou .js. Experti se domnívají, že díky této verzi malwaru budou podvodníci častěji útočit na podniky.
Ransomware RAA se objevil v červnu 2016 a je prvním ransomwarem, který je kompletně napsaný v JScriptu. Nová verze je ze srpna. Tentokrát je ale škodlivý kód ukrytý v heslem chráněné příloze, kterou je zazipovaný soubor. Kybernetičtí zločinci zavedli toto opatření především proto, aby oklamali AV řešení, pro které je těžší prozkoumat obsah zaheslovaného archivu.
Experti analyzovali e-maily a došli k závěru, že podvodníci raději cílí na společnosti než na běžné uživatele, a to pomocí nebezpečných e-mailů, které informují o nezaplacených platbách dodavatelům.
Podvodníci dodávají komunikaci důvěryhodnost zmínkou, že z bezpečnostních důvodů je přiložený soubor zaheslovaný (heslo je poskytnuté na konci e-mailu) a navíc je chráněný asymetrickým šifrováním. Toto prohlášení může znít uživatelům, kteří se zajímají o bezpečnost, směšně, důvěřivé oběti se ale nechají přesvědčit.
Další postup útoku je podobný tomu u předchozí verze RAA ransomwaru. Oběť otevře soubor .js, který spustí celý škodlivý proces. Trojan ukazuje podvodný textový dokument, který obsahuje náhodnou kombinaci písmen.
Tím se mu podaří zmást svou oběť. Zatímco se napadený uživatel snaží přijít na to, o co jde, RAA na pozadí kóduje soubory uložené v počítači. Nakonec ransomware na ploše vytvoří poznámku o výkupném a všem zašifrovaným souborům dá novou příponu .locked.
V případě šifrovaní dat v počítači oběti nyní RAA vůbec nepotřebuje komunikovat s C&C serverem. To je hlavní rozdíl od předchozí verze. Místo, aby trojan požadoval „master key“ od serveru, generuje, šifruje a ukládá jej přímo v napadeném počítači.
Kybernetičtí zločinci mají k dispozici soukromý klíč, který dokáže rozšifrovat unikátní „master key“. Jakmile oběť zaplatí výkupné, podvodníci ji požádají o zaslání „master key“, který jí vrátí rozšifrovaný společně s částí dešifrovacího softwaru.
Tento postup byl zavedený z důvodu, aby malware mohl počítač zašifrovat nehledě na to, zda je připojený k internetu.
Horší je, že oběti společně s ransomwarem RAA obdrží i trojan Pony. Ten je schopný ukrást hesla všech e-mailových klientů včetně těch korporátních a poslat je útočníkovi. Podvodníci pak mohou díky těmto heslům šířit malware jménem napadeného uživatele. Oběti je pak snadnější přesvědčit, že je e-mail legální.
Z korporátního e-mailu oběti tak může být malware rozšířený celé řadě firemních kontaktů. Podvodníci z nich mohou vybrat určité kontakty, které je zajímají, a provést na ně cílený útok.
It seems that Internet Explorer and Edge users were in danger for so long
21.9.2016 securityaffairs Vulnerebility
Microsoft recently issued the patches to fix set of flaws in Internet Explorer, years after their discovery by black-hats in the hacking underground.
Microsoft finally fixed a set of vulnerabilities in Internet Explorer years after they were discovered by black-hats in the hacking underground. I have contacted a black hat in the underground that who made a catastrophic prediction:
“And millions of people affected by it, but most of them still unaware of that they got hacked nearly a year ago” [4]
On September 13, 2016, Microsoft released two major security updates (MS16-105, MS16-104 for Edge and Internet Explorer browsers. [1][2]
The updates address various vulnerabilities rated with a severity level included from “Critical” to “Moderate.” According to ZDI some of these vulnerabilities have been reported to Microsoft on May 2016. Unfortunately evidence suggests that -hopefully- “some of them” has been known since 2014 and has been used in major attacks in the wild, such as the CVE-2016-3351 (creation date is 2016-03-15).
The CVE-2016-3351 flaw allows malicious script to just step back -or filter out- on configurations that are suspected to be on security analysis by checking various file type integrations such as .pcap files which are used to get network packet dumps by various traffic analysis software.
On December 15, Proofpoint has mentioned this vulnerability in its threat-insight blog mentioning Angler EK. [4]

The expert that I have been in touch was claiming that both CVE-2016-3351 and CVE-2016-3295 have been discovered long before their recent disclosure by actors in the underground, but only the CVE-2016-3351 was resolved in public. He also added that actively used CVE-2016-3295 exploit was always confused as CVE-2015-0046 and will be understood shortly. [4]

Hopefully we will get more details as POCs will be provided us.
References
[1] https://technet.microsoft.com/library/security/MS16-105
[2] https://technet.microsoft.com/library/security/MS16-104
[3] https://www.proofpoint.com/uk/threat-insight/post/The-Shadow-Knows
[4] “An underground hacker”
Italian security firm spotted BadEpilogue: The Perfect Evasion
21.9.2016 securityaffairs Spam
Security firm Certego has been detecting multiple viral spam campaigns leveraging a new malware evasion technique it called BadEpilogue.
Starting from May 2016, Certego Threat Intelligence platform has been detecting multiple viral spam campaigns using a new evasion technique. These attacks are able to hide malicious attachments inside a specific area of the MIME/Multipart structure and to avoid Content Filtering controls.
Certego has verified that some of the most common email clients and web mail services, using a different way of rendering the MIME/Multipart structure, are able to identify and extract the attachment, resulting in a Malware Evasion technique that we called BadEpilogue.

The picture shows a snippet of the source of a malicious email message using BadEpilogue evasion technique.
badepilogue-campaign-malware-1
Rows from 53 to 57 contain the end of the HTML message, while the attachment is located within an area that RFC2046 defines as Epilogue of a MIME/Multipart message, right after the final boundary of the Multipart message located at line 59 ending with the double “-” character.
According to RFC 2046, the message epilogue should not contain any useful text and, in particular, it should be ignored by MIME-compliant software:
“NOTE: These “preamble” and “epilogue” areas are generally not used because of the lack of proper typing of these parts and the lack of clear semantics for handling these areas at gateways, particularly X.400 gateways. However, rather than leaving the preamble area blank, many MIME implementations have found this to be a convenient place to insert an explanatory note for recipients who read the message with pre-MIME software, since such notes will be ignored by MIME-compliant software.
In the attack, right after the closing boundary of the MIME/Multipart message and at the beginning of the Epilogue area, there is a new boundary (see line 61) that starts another Multipart section containing the malicious attachment.”
Certego verified that many libraries used in Antispam and Antivirus systems to extract and analyze email attachments are unable to detect files hidden in the Epilogue area. On the other hand, popular email clients such as Outlook, Thunderbird, Evolution and Web Mail services are able to detect the attachment and to show it to the user resulting in a new malware evasion technique.
Responsible Disclosure Policy
Certego has described this evasion technique to the developers of email clients impacted by BadEpilogue. At the same time, we have informed the vendors of major Antispam systems that some of their Content Filters are ignoring attachments hidden in the Epilogue area.
We reported the technique to Microsoft and Mozilla. Microsoft has just released a patch for their email client in their last Security Bulletin MS16-107 (CVE-2016-3366) fixing the anomaly.
Certego also contacted Google and TrendMicro and both vendors confirmed the problem. TrendMicro has released a hotfix for their products, while Google informed us that a solution will be released shortly.
Is my email infrastructure affected by BadEpilogue?
In order to be effective, BadEpilogue must fulfill two conditions.
The first is that the Antispam filter, being compliant to RFC 2046, is unable to detect the attachment hidden in the Epilogue area. The second condition is that the email client or the web mail application is able to detect the attachment and to show it to the user.
If you want to check if your antispam system is vulnerable to BadEpilogue, you can download the following EML file which contains an EICAR test file hidden in the Epilogue area. The EICAR file is a harmless test file for signature based virus detection software. Using any email client (better if installed on a virtual machine with no antivirus software or the antivirus will detect and block the EICAR file), you can send the file to the destination address you want to test. If the recipient receives the message, then your antispam system is probably vulnerable to the BadEpilogue evasion technique.
If you want to check if your email client can detect and open attachments hidden with BadEpilogue, you can download a sample message from this link. The message contains a simple text attachment inserted in the Mime/Multipart’s epilogue. You can double click the file to open it with your favorite email client or use the “File -> Open” menu to manually open it. If the program lets you see the attachment, then your email client is vulnerable to BadEpilogue evasion technique.
Detecting BadEpilogue using a SNORT signature
Certego has created the following Snort signature to detect all incoming SMTP messages exploiting the BadEpilogue evasion technique.
alert tcp any any -> $HOME_NET [25,587] (msg:"CERTEGO CURRENT_EVENTS Incoming SMTP Message with Possibly Malicious MIME Epilogue 2016-05-13 (BadEpilogue)"; flow:to_server,established; content:"|0d 0a|Content-Type|3a 20|multipart|2f|mixed|3b|"; pcre:"/\x0d\x0a--(?P<boundary>[\x20\x27-\x29\x2b-\x2f0-9\x3a\x3d\x3fA-Z\x5fa-z]{1,70})--(?:\x0d\x0a(?!--|\x2e|RSET).*)*\x0d\x0a--(?P=boundary)\x0d\x0a/"; reference:url,www.certego.local/en/news/badepilogue-the-perfect-evasion/; classtype:bad-unknown; sid:9000501; rev:3;)
The campaigns
As mentioned, this evasion technique has been detected in the wild since May 2016, in at least eleven different campaigns targeting Italian users. These campaigns use messages written in a fluent Italian asking the user to open an attachment labeled as invoice or payment receipt. The attachment is in ZIP format and it contains a malware in PE EXE format. This attack pattern is typical of the so-called Viral Spam campaigns that were prevalent until a few months ago, but it has now been deemed ineffective by antispam filters blocking ZIP files containing PE EXE. In this case, the BadEpilogue evasion technique allows the attacker to generate extremely effective campaigns that can reach a very high number of targets.
While the first campaigns were spreading a malicious attachment containing a Trojan Downloader of the Fareit family which downloaded a variant of the Andromeda Infostealer, the latest campaigns have started working mainly with ransomware and in the last few days we have observed a massive amount of emails containing Zlader.
The following picture shows the various campaigns using the BadEpilogue evasion technique as reported by our systems.

The following picture shows the geolocation of IP addresses used to spread the malicious emails. Spreading patterns seem to be related to a single botnet that is expanding and contracting over time. This seems to be confirmed also by the fact that so far only Italian users have been targeted by these attacks.

Experts found apps in Google Play serving the Overseer malware to overseas travelers
21.9.2016 securityaffairs Virus
Google has removed from the Google Play store four apps trojanized with the Overseer malware to target overseas travelers seeking embassy information.
Google has removed from the official Google Play store four trojanized apps that targeted overseas travelers seeking embassy information and news for specific European countries.
Three apps were named “Embassy”, “European News”, “Russian News,” a fourth one was using Cyrillic. I personally consider the threat as severe because who is behind the Overseer malware is targeting foreign travelers, especially enterprise executives that had downloaded the Embassy app during their business travels.

The malicious apps were spotted in late July by security experts from the Lookout’s Security Research and Response Team, which called the threat Overseer. The mobile apps were developed to gather user information from their Android devices, including contacts, email, GPS data, device data (i.e. Model, device ID, device rooted or not).
Lookout malware experts reported the presence of the Overseer malware in the apps of the Google Play on Aug. 4, Bit G promptly removed them from the store.
The Overseer apps were downloaded 10,000 times via Google Play.
“Through close collaboration with an enterprise customer, Lookout identified Overseer, a piece of spyware we found in four apps live on the Google Play store. One of the apps was an Embassy search tool intended to help travelers find embassies abroad. The malware was also injected as a trojan in Russian and European News applications for Android.” reported a blog post published by Lookout.
The threat actors behind the app used command-and-control servers located on Facebook’s Parse Server, hosted on Amazon Web Services. This technical choice allows Vxers to avoid malicious traffic detection.
“By using the Facebook and Amazon services, the spyware makes use of HTTPS and a C&C residing in the United States on a popular cloud service. This allows it to remain hidden because it doesn’t cause Overseer’s network traffic to stand out and could potentially present a challenge for traditional network-based IDS solutions to detect,” continues the post.
Once the Overseer malware has infected the Android mobile device it would contact the C&C server to receive instructions or malicious payloads and exploits to download and execute.
“Devices infected with Overseer periodically beacon to the api.parse.com domain, checking whether there are any outstanding commands the attacker wants to run. Depending on the response, the malware is capable of exfiltrating a significant amount of information from an infected device. These communications are all encrypted over the wire, which hides the traffic from network security solutions.” reads the analysis published by Lookout.
The researchers from Lookout discovered more apps in the Play Store also infected with the Overseer malware, a circumstance that led them to believe that these apps were created for the purpose of distributing the Overseer malware.
A mistake allowed us a peek into North Korea Internet infrastructure
21.9.2016 securityaffairs Security
A mistake allowed us a peek into the North Korea Internet infrastructure, a security researcher discovered that Pyongyang has just 28 websites.
The North Korea is one of the countries that most of all is investing to improve its cyber capabilities and that has one of the largest cyber armies.
But North Korea is also known for its limited exposure on the Internet, it fears cyber attacks from foreign Governments against its infrastructure.
Until today no one had any idea of the number of websites registered by the country for its top-level domain, .kp.
This week something is changed, likely due to an error in the configuration of a North Korean nameserver. The apparent mistake has revealed a list of all the domains for the top-level domain .kp and related info.
Segui
Nicolas Krassas @Dinosn
North Korea accidentally leaks DNS for .kp: only 28 domains https://github.com/mandatoryprogrammer/NorthKoreaDNSLeak …
12:31 - 20 Set 2016
Photo published for mandatoryprogrammer/NorthKoreaDNSLeak
mandatoryprogrammer/NorthKoreaDNSLeak
NorthKoreaDNSLeak - Snapshot of North Korea's DNS data taken from zone transfers.
github.com
30 30 Retweet 36 36 Mi piace
According to leaked zone files, the North Korea has only 28 registered domains
“Now we have a complete list of domain names for the country and it’s surprisingly (or perhaps unsurprisingly) very small,” Matt Bryant, the expert who has found the mistake, said to Motherboard
After Bryant discovered the mistake, he downloaded the data from the domain name servers.
Some of the sites in the list are not reachable, experts speculated that they were flooded with the traffic of curious netizens and went down.

The list of domains includes commercial and educational websites like the one of the state Air Koryo airline or the Kim Il Sung University.
The leaked info also revealed the site of the official newspaper of North Korea’s communist party which is considered the core of the Government propaganda machine.

The leaked list also includes a social network website, the state version of Facebook, friend.com.kp.

and portal.net.kp that is the equivalent of the Yahoo.
Below the complete list:
airkoryo.com.kp
cooks.org.kp
friend.com.kp
gnu.rep.kp
kass.org.kp
kcna.kp
kiyctc.com.kp
knic.com.kp
koredufund.org.kp
korelcfund.org.kp
korfilm.com.kp
ma.gov.kp
masikryong.com.kp
naenara.com.kp
nta.gov.kp
portal.net.kp
rcc.net.kp
rep.kp
rodong.rep.kp
ryongnamsan.edu.kp
sdprk.org.kp
silibank.net.kp
star-co.net.kp
star-di.net.kp
star.co.kp
star.edu.kp
star.net.kp
vok.rep.kp
Now just for a second try to think if the North Korean Government will host an exploit kit leveraging on a zero-day exploit on one of the above domains 🙂
The banker that can steal anything
20.9.2016 Kaspersky Crime
In the past, we’ve seen superuser rights exploit advertising applications such as Leech, Guerrilla, Ztorg. This use of root privileges is not typical, however, for banking malware attacks, because money can be stolen in numerous other ways that don’t require exclusive rights. However, in early February 2016, Kaspersky Lab discovered Trojan-Banker.AndroidOS.Tordow.a, whose creators decided that root privileges would come in handy. We had been watching the development of this malicious program closely and found that Tordow’s capabilities had significantly exceeded the functionality of most other banking malware, and this allowed cybercriminals to carry out new types of attacks.
Penetration
A Tordow Infection begins with the installation of a popular app, such as VKontakte, DrugVokrug, Pokemon Go, Telegram, Odnoklassniki or Subway Surf. In this particular case, we’re not talking about the original apps but copies that are distributed outside the official Google Play store. Malware writers download legitimate applications, disassemble them and add new code and new files.
Code added to a legitimate application
Anyone who possesses even a little knowledge of Android development can do it. The result is a new app that is very similar to the original, performs all the stated legitimate functions, but that also has the malicious functionality that the attackers need.
How it works
In the case in question, the code embedded in the legitimate app decrypts the file added by the cybercriminals in the app’s resources and launches it.
The launched file calls the attacker’s server and downloads the main part of Tordow, which contains links to download several more files – an exploit to gain root privileges, new versions of malware, and so on. The number of links may vary depending on the criminals’ intentions; moreover, each downloaded file can also download from the server, decrypt and run new components. As a result, the infected device is loaded with several malicious modules; their number and functionality also depend on what the Tordow owners want to do. Either way, the attackers get the chance to remotely control the device by sending commands from the C&C.
As a result, cybercriminals get a full set of functions for stealing money from users by applying the methods that have already become traditional for mobile bankers and ransomware. The functionality of the malicious app includes:
Sending, stealing, deleting SMS.
Recording, redirecting, blocking calls.
Checking the balance.
Stealing contacts.
Making calls.
Changing the C&C.
Downloading and running files.
Installing and removing applications.
Blocking the device and displaying a web page specified by a malicious server.
Generating and sending a list of files contained on the device; sending and renaming of files.
Rebooting a phone.
Superuser rights
In addition to downloading modules belonging to the banking Trojan, Tordow (within the prescribed load chain of modules) also downloads a popular exploit pack to gain root privileges, which provides the malware with a new attack vector and unique features.
Firstly, the Trojan installs one of the downloaded modules in the system folder, which makes it difficult to remove.
Secondly, using superuser rights the attackers steal the database of the default Android browser and the Google Chrome browser if it’s installed.
Code for sending data from browsers to the server
These databases contain all the logins and passwords stored by the user in the browser, browsing history, cookies, and sometimes even saved bank card details.
Login and password from a specific site in the browser database
As a result, the attackers can gain access to several of the victim’s accounts on different sites.
And thirdly, the superuser rights make it possible to steal almost any file in the system – from photos and documents to files containing mobile app account data.
These attacks can result in the theft of huge amounts of critical user data. We recommend that users do not install apps from unofficial sources and use antivirus solutions to protect Android-based devices.
Car Hacking – Chinese hacker team remotely hacked Tesla Model S
20.9.2016 securityaffairs Hacking
A group of security researchers from the Chinese firm Tencent have found a series of flaws that can be exploited to remotely hack a Tesla Model S.
Security experts at the Keen Lab at Chinese firm Tencent have found a series of vulnerabilities that can be exploited by a remote attacker to hack an unmodified Tesla Model S.
The researchers demonstrated that it is possible to hack the Tesla Model S while it is parked or if it is on the move.

The team published a Video PoC of the hack that shows how to take the control of the sunroof, of the position of the seats, of the turn signals, and the door locking system.
The most scaring part of the hack is when the car is on the move, the hackers were able to activate the brakes from 12 miles, activate the windshield wipers, fold the side view mirrors, and open the trunk.
“With several months of in-depth research on Tesla Cars, we have discovered multiple security vulnerabilities and successfully implemented remote, aka none physical contact, control on Tesla Model S in both Parking and Driving Mode. It is worth to note that we used an unmodified car with latest firmware to demonstrate the attack.” the researchers explained in a blog post.
The researchers are the first team of hackers that is able to compromise CAN Bus to remote control Tesla cars by exploiting a series of flaws.
“As far as we know, this is the first case of remote attack which compromises CAN Bus to achieve remote controls on Tesla cars,” the researchers said. “We have verified the attack vector on multiple varieties of Tesla Model S. It is reasonable to assume that other Tesla models are affected.” continues the post.
“As far as we know, this is the first case of remote attack which compromises CAN Bus to achieve remote controls on Tesla cars. We have verified the attack vector on multiple varieties of Tesla Model S. It is reasonable to assume that other Tesla models are affected. Keen Security Lab would like to send out this reminder to all Tesla car owners:”
The experts were able to identify a specific Tesla Model S and hack it while the owner is searching for nearby charging stations.
The team reported the issues to Tesla Motors that in turn awarded $10,000 them under the Bugcrowd-hosted bug bounty program.
Tesla has verified the presence of the vulnerabilities and is currently working to fix them. The company will not recall any Tesla Model S because it is able to push out firmware updates over-the-air.
Car hacking is a scaring reality, when deal with this specific kind of attacks we cannot avoid mentioning the hack demonstrated by the popular hackers Charlie Miller and Chris Valasek, who have managed to control remotely a Fiat Chrysler connected car.
Almost every car maker is currently working to make its connected car secure by adding specific countermeasures.