
BASHLITE Botnets peaked 1 Million Internet of Thing Devices
1.9.2016 securityaffeirs BotNet
A joint research conducted by Level 3 Communications and Flashpoint allowed the identification of a million devices infected by the BASHLITE malware.
Do you remember the BASHLITE malware? It was a strain of malware (also known as Lizkebab, Torlus and Gafgyt) detected by experts at Trend Micro shortly after the public disclosure of the ShellShock bug.
The BASHLITE malware includes the code of the ShellShock exploit and it had been used by threat actors in the wild to run distributed denial-of-service (DDoS) attacks.
It could infect multiple Linux architectures, for this reason, crooks used it to target Internet of Things devices.
In June, experts from the security firm Sucuri spotted a botnet composed of tens of thousands of CCTV devices that had been used by crooks to launch DDoS attacks against websites.
The BASHLITE source code was leaked online in early 2015, malware developers used it to create their own variant.
Now experts from Level 3 and Flashpoint confirmed the overall number of devices infected by the BASHLITE malware is more than 1 million.
The number includes compromised devices belonging to several botnets, according to the experts, almost every infected device are digital video recorders (DVRs) or cameras (95%), the remaining is composed of routers (4%), and Linux servers (1%).
“Of the identifiable devices participating in these botnets, almost 96 percent were IoT devices (of which 95 percent were cameras and DVRs), roughly 4 percent were home routers and less than 1 percent were compromised Linux servers. This represents a drastic shift in the composition of botnets compared to the compromised server- and home router-based DDoS botnets we’ve seen in the past.” states a blog post published by Level 3 firm.
The researchers have been tracking more than 200 C&C worldwide used by the BASHLITE botnets. Fortunately, the IP addresses of the C&C servers was found hardcoded in the instance of malware detected in the wild making easy for experts to shut down them.
The researchers provided interesting details about the Global Distribution of the gafgyt Bots, the vast majority of infected devices are located in Brazil, Taiwan and Colombia.
“Of the bots we’ve observed participating in attacks, peaking at more than 1 million devices, a large percentage are located in Taiwan, Brazil and Colombia. A large majority of these bots were using white-labeled DVRs generically described as “H.264 DVRs” and DVRs manufactured by the company Dahua Technology.” continues the post. “We have contacted Dahua Technology to make them aware of this issue. Our investigation shows more than one million of these two types of devices are accessible on the internet, providing a large pool of potential bots.”

It is quite easy for hackers to compromise DVRs that are affected by multiple critical vulnerabilities. In many cases, the same flawed software is used by multiple vendors for their devices.
“Most of these devices run some flavor of embedded Linux. When combined with the bandwidth required to stream video, they provide a potent class of DDoS bots,” continues the post.
According to the experts, crooks behind the botnets have used some of the C&C servers to launch more than 100 attacks per day.
“Most attacks are short-lived, with the median duration just over 2 minutes, and 75 percent of attacks shorter than 5 minutes.”
“The use of IoT devices in botnets is not new, but as they become more common, we expect these types of botnets to increase in number and power,” Level 3 said in a blog post. “The security of IoT devices poses a significant threat. Vendors of these devices must work to improve their security to combat this growing threat. ”
USBee exfiltrates data from air-Gapped networks via electromagnetic emission from USB
1.9.2016 securityaffeirs Virus
A group of Israeli researchers has devised a new technique dubbed USBee to hack air-gapped networks and exfiltrate information.
Mordechai Guri, head of R&D at Ben-Gurion’s Cyber Security Center and the chief scientist officer at Morphisec Endpoint Security, and his team have devised a new technique dubbed USBee to hack air-gapped networks and exfiltrate information.
This time, the Israel researchers exploited covert-channel via electromagnetic emission from USB. The USBee technique leverages USB connectors implanted with RF transmitters to steal sensitive data.
In this scenario, the USBee application is installed on a compromised computer. The attacker exploits a USB thumb drive already connected to the computer and establish a short-range RF transmission modulated with data. On the other end of the communication, the data transmitted are received by a nearby receiver and decoded.

“In recent years researchers have demonstrated how attackers could use USB connectors implanted with RF transmitters to exfiltrate data from secure, and even air-gapped, computers (e.g., COTTONMOUTH in the leaked NSA ANT catalog). Such methods require a hardware modification of the USB plug or device, in which a dedicated RF transmitter is embedded.” reads the introduction to the paper published by the experts. “In this paper we present USBee, a software that can utilize an unmodified USB device connected to a computer as a RF transmitter. We demonstrate how a software can intentionally generate controlled electromagnetic emissions from the data bus of a USB connector. We also show that the emitted RF signals can be controlled and modulated with arbitrary binary data. We implement a prototype of USBee, and discuss its design and implementation details including signal generation and modulation. We evaluate the transmitter by building a receiver and demodulator using GNU Radio. Our evaluation shows that USBee can be used for transmitting binary data to a nearby receiver at a bandwidth of 20 to 80 BPS (bytes per second).”
The researchers discovered that the transmission of a sequence of ‘0’ bits to a USB port generates a detectable emission between 240ℎ and 480ℎ. The researchers exploited this mechanism by sending data from the compromised computer to a USB device in order to generate controllable EMR that can carry modulated data. The researcher used a nearby RF receiver to receive the EMR and decode the information.
Guri and his team were able to exfiltrate 80 bytes per second using this technique, a transmission speed that could an attacker to send out a 4,096-bit crypto key in less than 10 seconds, very interesting when hacking air-gapped networks if compared with other hacking techniques.
The experts explained that it is possible to create a basic carrier wave using this algorithm:
inline static void fill_buffer_freq
(u32 *buf, int size, double freq)
{
int i = 0;
u32 x = 0;
double t = freq / 4800 * 2;
for (i = 0, x = 0x00000000; i<size*8; i++)
{
x = x<<1;
if ((int)(i*t)%2==0)
x++;
if((i%32)==31)
{
*(buf++) = x;
x=0x00000000;
}
}
}
The transmission starts when the application writes the fill_buffer_freq to an arbitrary data block in the USB device, the application just requires the permission to create a file on the device.
“The actual data transmission is done by writing the byte pattern generated by fill_buffer_freq to an arbitrary data block or stream in the USB device. For our purposes, we used a temporary file within the USB thumb drive’s file system. The transmission process doesn’t require special privileges (e.g., root or admin). It only requires permission to create a file on the removable device.” reads the paper.
The researchers also published a video PoC of the attack that shows how the data is exfiltrated by a laptop with a $30 radio antenna from around 15 feet away.
Spotify resets users’ passwords due to data breaches suffered by other firms
1.9.2016 securityaffeirs Hacking
In response to the numerous data breaches suffered by other services, the music streaming service Spotify forced a password reset for a number of users.
In the last months, numerous IT companies suffered a major data breach, including Dropbox, LinkedIn, MySpace, VK.com, and Tumblr. The criminal underground is flooded by login credentials from the above services that offered for sales by hackers.
These credentials could be used by hackers to target other services online and take over users’accounts, this is possible because users’ bad habit to share same usernames and passwords among different web services.
spotify
In response to the amazing string of data breaches, the music streaming service Spotify decided to force a password reset for a number of users. The company clarified that the measure was taken in response to the incident occurred to other firms and are not related to any problem occurred in its systems.

To protect your Spotify account, we’ve reset your password. This is because we believe it may have been compromised during a leak on another service with which you use the same password.” states a message sent via email to its users on Wednesday reads.
“Don’t worry! This is purely a preventative security measure. Nobody has accessed your Spotify account, and your data is secure,”
Spotify allows users to easily create a new password by simply clicking on a link.
In April, hundreds of Spotify account credentials appeared online on the website Pastebin, the information includes emails, usernames, passwords, account type and other details.
The popular Swedish streaming service denied any data breach and confirmed that its systems weren’t compromised by hackers. The company confirmed that it “has not been hacked” and its “user records are secure.”
“Spotify has not been hacked and our user records are secure. We monitor Pastebin and other sites regularly. When we find Spotify credentials, we first verify that they are authentic, and if they are, we immediately notify affected users to change their passwords.” states Spotify.
According to the Techcrunch media agency, the company security team proactively resets hacked passwords, meanwhile, a number of users are also reported problems with their accounts.
FBI flash alert says foreign hackers compromised state election systems
31.8.2016 securityaffeairs Hacking
The FBI issued a “flash” alert to election officials across the country confirming that foreign hackers have compromised state election systems in two states.
The FBI confirmed that foreign hackers have penetrated state election systems, federal experts have uncovered evidence of the intrusion. The hackers penetrated the databases of two state election systems in the last weeks, in response, the FBI issued a “flash” alert to election officials across the country inviting them to adopt security measured to protect their computer systems.
“The FBI warning, contained in a “flash” alert from the FBI’s Cyber Division, a copy of which was obtained by Yahoo News, comes amid heightened concerns among U.S. intelligence officials about the possibility of cyberintrusions, potentially by Russian state-sponsored hackers, aimed at disrupting the November elections.” reported Yahoo News that obtained a copy of the “flash” alert.
The alert does not provide details about the states that suffered the attacks, but according to Yahoo News, sources familiar with the document say it refers voter registration databases in Arizona and Illinois.
US authorities fear possible cyber attacks launched by nation-state actors like Russians that could have serious consequences on the result of the next Presidential Election.
The Homeland Security Secretary Jeh Johnson had a conference call with state election officials on Aug. 15 to offer all the necessary support to secure state election systems.
The DHS will provide cybersecurity experts to scan the voting systems searching for vulnerabilities that could be exploited by hackers.
“The government is offering to help states protect the Nov. 8 U.S. election from hacking or other tampering, in the face of allegations by Republican Party presidential candidate Donald Trump that the system is open to fraud.” reported the Reuters.
“Homeland Security Secretary Jeh Johnson told state officials in a phone call on Monday that federal cyber security experts could scan for vulnerabilities in voting systems and provide other resources to help protect against infiltration, his office said in a statement.”
Back to the FBI flash alert, titled “Targeting Activity Against State Board of Election Systems,” it was labeled as restricted for “NEED TO KNOW recipients.”

The warning confirms that the bureau was investigating cyber intrusions against two state election websites that occurred recently that lead to the exfiltration of voter registration data.
The FBI alert contains technical details about the attacks, including IP addresses involved in the both attacks.
“The FBI is requesting that states contact their Board of Elections and determine if any similar activity to their logs, both inbound and outbound, has been detected,” the alert reads. “Attempts should not be made to touch or ping the IP addresses directly.”
The TTPs adopted by attackers suggest the involvement of Russian hackers, one of the IP addresses included in the alert has surfaced before in Russian criminal underground hacker forums.
Menzel, the Illinois election official, confirmed that FBI is investigating a possible link to the Democratic National Committee hack and the attacks against the two state election systems.
The RIPPER malware linked to the recent ATM attacks in Thailand
31.8.2016 securityaffeairs Virus
Experts from FireEye who analyzed the RIPPER malware believe it was used by crooks in the recent wave of cyber attacks against ATM in Thailand.
Earlier this month a malware was used by a criminal organization to steal 12 million baht from ATMs in Thailand.
According to FireEye, the malware was uploaded for the first time to the online scanning service VirusTotal on Aug. 23, 2016. The malicious code was uploaded from an IP address in Thailand a few minutes the cyber heist was reported by media.
Experts from FireEye who analyzed the malware, dubbed RIPPER because researchers found the “ATMRIPPER” name in the sample, revealed that it implemented techniques not seen before.
Hackers belonging to a cybercrime gang from Eastern Europe have stolen over 12 Million Baht (approximately US$346,000) from a 21 ATMs in Thailand.
The Central Bank of Thailand (BoT) has issued a warning to all the banks operating in the country about security vulnerabilities that plague roughly 10,000 ATMs. It seems that hackers exploited such flaws to steal cash from the ATMs. The same gang was involved in similar attacks against top eight banks in Taiwan. In Taiwan, the thieves have stolen NT$70 Million ($2.2 Million) in cash forcing the banks to shut down hundreds of their cash machines.
The warning issued by the Central Bank of Thailand follows the decision of the Government Savings Bank (GSB) to shut down roughly 3,000 ATMs of its 7,000 machines in response to a recent wave of attacks that targeted its machines.
According to FireEye, the RIPPER malware borrows multiple features from other ATM malware:
Targets the same ATM brand.
The technique used to expel currency follows the same strategy (already documented) performed by the Padpin (Tyupkin),SUCEFUL and GreenDispenser.
Similar to SUCEFUL, it is able to control the Card Reader device to Read or Eject the card on demand.
Can disable the local network interface, similar to capabilities of the Padpin family.
Uses the “sdelete” secure deletion tool, similar to GreenDispenser, to remove forensic evidence.
Enforces a limit of 40 bank notes per withdrawal consistently, which is the maximum allowed by the ATM vendor.
The RIPPER malware also implements new features, for example, it was designed to target three of the main ATM Vendors worldwide, which is a first.
The RIPPER malware interacts with the ATM by inserting a specially manufactured ATM card with an EMV chip, with this mechanism crooks authenticate themselves to the cash machine. This mechanism is uncommon, the Skimmer use this method too.
In order to gain persistence, the RIPPER malware uses either a standalone service or masquerade itself as a legitimate ATM process.
When the RIPPER is installed as a service, it first killk the process “dbackup.exe”, then replaces it with its binary, then it installs the persistent service “DBackup Service.”
“RIPPER can stop or start the “DBackup Service” with the following arguments:
“service start” or “service stop”
RIPPER also supports the following command line switches:
/autorun: Will Sleep for 10 minutes and then run in the background, waiting for interaction.
/install: RIPPER will replace the ATM software running on the ATM as follows:
Upon execution, RIPPER will kill the processes running in memory for the three targeted ATM Vendors via the native Windows “taskkill” tool.
RIPPER will examine the contents of directories associated with the targeted ATM vendors and will replace legitimate executables with itself. This technique allows the malware to maintain the legitimate program name to avoid suspicion.” continues FireEye.
When RIPPER malware is executed without any parameters, it performs a series of actions, such as connecting with the local peripherals (i.e. Cash Dispenser, Card Reader, and the Pinpad).
Then the threat detects a card with a malicious EMV chip it starts a timer to allow a crook to control the ATM via the Pinpad.
The crooks can perform multiple malicious actions, including clear logs and shut down the ATM local network interface.
Back to the Thailand attacks, below are reported similarities between the RIPPER malware and the malicious code used by the gang.

Minecraft World Map data breach, 71,000 accounts leaked online
31.8.2016 securityaffeairs Hacking
The popular security expert Troy Hunt reported some 71,000 user accounts and IP addresses have been leaked from the website Minecraft World Map.
Another data breach affects the gaming industry, this time, 71,000 Minecraft World Map accounts has been leaked online after the ‘hack.’
Some 71,000 user accounts and IP addresses have been leaked from Minecraft fan website Minecraft World Map.
The Minecraft World Map site is very popular withing the Minecraft gaming community, gamers can use the web property to share the worlds they have built.
The popular security expert reported Troy Hunt reported the data dumps that include 71,000 user accounts and IP addresses.
Segui
Have I been pwned? @haveibeenpwned
New breach: Minecraft World Map had 71k user accounts hacked in Jan. 55% were already in @haveibeenpwned https://haveibeenpwned.com
03:30 - 29 Ago 2016
35 35 Retweet 13 13 Mi piace
Exposed records include email addresses, IP address data, login credentials for the popular site Minecraft World Map, Troy Hunt clarified that passwords included in the dumps were salted and hashed.

A rapid check allowed the Australian expert to verify that more than half of the compromised accounts were already listed in its online service haveibeenpwned.com that allows users to discover if they have an account that has been compromised in a data breach.
According to the experts, the website Minecraft World Map was breached in January 2016, but the incident was not publicly reported.
“In approximately January 2016, the Minecraft World Map site designed for sharing maps created for the game was hacked and over 71k user accounts were exposed. The data included usernames, email and IP addresses along with salted and hashed passwords.
Compromised data: Email addresses, IP addresses, Passwords, Usernames” Hunt wrote on his website.
Users have to reset their passwords on the Minecraft World Map and on any other website that shares the same login credentials.
This is the last incident occurred in the gaming industry disclosed online, recently security vulnerabilities in the vBulletin platform have exposed more than 27 million accounts, many of them belonging to gamers on mail.ru.
Giving a close look to the compromised mail.ru accounts they belong from CFire, parapa.mail.ru (ParaPa Dance City game), and tanks.mail.ru (Ground War: Tank game).
Lurk cybercrime Gang developed, maintained and rent the Angler EK
31.8.2016 securityaffeairs Crime
Experts from Kaspersky Lab confirmed that the Lurk cybercrime Gang developed, maintained and rent the infamous Angler Exploit Kit.
Security experts from Kaspersky Lab have confirmed that the Lurk cybercrime group are the author of the infamous Angler exploit kit. The members of the Lurk cybercrime crew were arrested by Russian law enforcement this summer, according to the experts they also offered for rent the Angler exploit kit that after the arrest disappeared from the exploit landscape.
Law enforcement arrested suspects in June, authorities accused them of stealing around $45 million USD from Russian financial institutions by using the Lurk banking trojan.
According to the Cisco Talos researchers, after the arrests of the individuals behind the Lurk banking trojan, it has been observed a rapid disappearance of the Angler EK in the wild.
Malware researchers confirmed that the overall traffic related to other EKs shows a drastic fall, around 96% since early April.
The Angler and Nuclear exploit kits rapidly disappeared, likely due to the operations conducted by the law enforcement in the malware industry.
A joint investigation conducted by the Russian Police and the Kaspersky Lab allowed the identification of the individuals behind the Lurk malware. The experts now confirmed that the Lurk group was also responsible for developing and maintaining the Angler exploit kit, that they called “XXX.”
Experts from Kaspersky published a blog post that details how the security firm helped law enforcement in catching the Lurk cybercrime group.
The experts explained that the Lurk gang started renting the Angler Exploit Kit after their fraudulent activities became less profitable.
“In addition to increasing the number of “minor” attacks, the cybercriminals were trying to solve their cash flow problem by “diversifying” the business and expanding their field of activity. This included developing, maintaining and renting the Angler exploit pack (also known as XXX). Initially, this was used mainly to deliver Lurk to victims’ computers. But as the number of successful attacks started to decline, the owners began to offer smaller groups paid access to the tools.”
“Judging by what we saw on Russian underground forums for cybercriminals, the Lurk gang had an almost legendary status,” reads the post. “So when Lurk provided other cybercriminals with access to Angler, the exploit pack became especially popular – a ‘product’ from the top underground authority did not need advertising.”
Lurk first appeared on the scene in 2011 when its activities were first spotted by Kaspersky experts. Kaspersky initially determined the Lurk cybercrime group was composed of roughly 15 people. Across the years the number of members of the criminal gang increased to 40.

Kaspersky also provided an estimation of the cost for the Lurk infrastructure that reached tens of thousands of dollars per month.
“The criminal group had an extensive and extremely costly network infrastructure, so, in addition to employees’ salaries, it was necessary to pay for renting servers, VPN and other technical tools. Our estimates suggest that the network infrastructure alone cost the Lurk managers tens of thousands of dollars per month.” continues the post.
Saudi government facilities hit by cyber attacks, Saudi cyber experts convened
31.8.2016 securityaffeairs Hacking
Saudi government facilities have been hit cyber attacks, the Government is investigating with the support of Saudi cyber experts.
Saudi government facilities have been targeted by major cyber attacks, in response, the Government has convened a group of cyber experts to examine the events.
According to the Saudi Press Agency, Saudi cyber experts held urgent talks on Tuesday after the cyber attack “in recent weeks targeted government institutions and vital installations in the kingdom.”
At the time I was writing there is no information about targeted agencies neither the alleged threat actor behind the cyber attacks against Saudi infrastructure.
FILE- In this Monday, Oct. 6, 2003 file photo, Saudi Arabian capital Riyadh with the 'Kingdom Tower' photographed through a window of the 'Al-Faislia Tower' in the Saudi Arabian capital Riyadh. Saudi Arabia�s stock exchange has opened up to direct foreign investment for the first time. The decision to open up the Tadawul stock exchange on Monday comes at a crucial time for Saudi Arabia, whose revenue has taken a hit from the plunge in oil prices over the past year. The kingdom is the world�s largest exporter of crude. (AP Photo/Markus Schreiber, File)
(AP Photo/Markus Schreiber, File)
The Saudi cyber security experts were involved in the investigation and according to the Saudi Press Agency, the kingdom’s Cybersecurity Centre “held an urgent workshop with a number of parties” to discuss the results of its investigations.
The attacks were launched from abroad, attackers targeted Saudi websites with a spyware to steal sensitive information from the targets.
This isn’t the first time that Saudi websites were hit by cyber attacks, in June hackers attacked a major Saudi newspaper and gained its control to publish fake news.
The Saudi cyber experts analyzed the attacks and proposed the necessary countermeasures to defeat the threat and protect the information targeted by the hackers.
Experts exposed the “necessary procedures to fix and to protect those sites”, reported the Saudi Press Agency.
The most clamorous attack against Saudi government facilities occurred in 2012 when a virus infected 30,000 workstations of one of the world’s largest energy companies, the Saudi Aramco.
iOS 9.3.4 and minor versions are vulnerable to the Trident Exploit
31.8.2016 securityaffeairs iOS
Its name is the Trident: a chain of zero-day exploits that aim to infect iPhone with commercial spyware. Researchers linked it to the NSO group.
Its name is the Trident: a chain of zero-day exploits that aim to infect iPhone with commercial spyware.
Researchers say it’s belonging to an exploit infrastructure connected to the NSO group.

Thanks to the great work made by the researchers from the Citizenlab organization and the Lookout firm that responsibly disclosed the exploits and their related vulnerabilities to Apple.
Given the severity of the Trident, Apple worked extremely quickly to patch these vulnerabilities and it has released iOS 9.3.5 to address them.
In this post, we want to give you a description and some technical information about the inner logic of the Trident exploit instead of the attack received by Ahmed Mansoor.
With the episode of Ahmed Mansoor we can quickly understand the infection vector of that exploit: SMS, email, social media, or any other message.
The most scaring part of that attack is that the single action the user have to do to trigger this dangerous attack is just a click on an external link.
The exploit seems to contain the logic to remote jailbreak an iPhone to install arbitrary applications and then deliver a commercial spyware called Pegasus as an espionage software to track the victim.
What is Pegasus and who is behind it?
Pegasus is a spy software installable on iOS devices that allow reading messages, emails, passwords and address lists as well as eavesdropping on phone calls, making and transmitting audio recordings and tracking the location on a compromised device (but we will look better in the following section).
It seems that this spyware is attributed to NSO Group, an Israeli firm based in Herzliya in the country’s “Silicon Valley”.
This spyware was attributed to the NSO Group because in the Mansoor’s attack the domain used for the phishing message (webdav.co) belongs to a network of domains that is a part of an exploit infrastructure provided by the company NSO Group.
NSO Group, now owned by US private equity firm Francisco Partners Management, has flown far under the radar, without even a website.
The Citizenlab reported that just opening the link included in the message sent to the victims with an iPhone version 9.3.3 it is possible to observe an active unknown software that was remotely implanted into the system through the delivery of unknown exploits from that link.
The complex exploit takes the name as Trident.
ATTACK SCENARIO
After the user get baited the exploit start his work to infect the phone, following the 3 main stages of that attack, better detailed here:
Delivery and WebKit vulnerability
This stage comes down over the initial URL in the form of an HTML file that exploits a vulnerability (CVE-2016-4655) in WebKit (used in Safari and other browsers).
CVE-2016-4655: Memory Corruption in Safari WebKit
A memory corruption vulnerability exists in Safari WebKit that allows an attacker to execute arbitrary code. Pegasus exploits this vulnerability to obtain initial code execution privileges within the context of the Safari web browser.
Jailbreak
This stage is downloaded from the first stage code based on the device type (32-bit vs 64- bit). Stage 2 is downloaded as an obfuscated and encrypted package. Each package is encrypted with unique keys at each download, making traditional network-based controls ineffective. It contains the code that is needed to exploit the iOS Kernel (CVE-2016-4656 and CVE-2016-4657) and a loader that downloads and decrypts a package for stage 3.
CVE-2016-4656: Kernel Information Leak Circumvents KASLR
Before Pegasus can execute its jailbreak, it must determine where the kernel is located in memory. Kernel Address Space Layout Randomization (KASLR) makes this task difficult by mapping the kernel into different and unpredictable locations in memory. In short, before attacking the kernel, Pegasus has to find it. The attacker has found a way to locate the kernel by using a function call that leaks a non-obfuscated kernel memory address in the return value, allowing the kernel’s actual memory location to be mapped.
CVE-2016-4657: Memory Corruption in Kernel leads to Jailbreak
The third vulnerability in Pegasus’ Trident is the one that is used to jailbreak the phone. A memory corruption vulnerability in the kernel is used to corrupt memory in both the 32- and 64-bit versions. The exploits are performed differently on each version.
Espionage software:
This stage is downloaded by stage 2 and is also based on the device type (32-bit vs 64-bit). Stage 3 contains the espionage software, daemons, and other processes that are used after the device has been jailbroken in stage 2. Stage 3 installs the hooks into the applications the attacker wishes to spy on. Additionally, stage 3 detects if the device was previously jailbroken through another method and, if so, removes any access to the device that the jailbreak provides, such as via SSH. The software also contains a failsafe to remove itself if certain conditions are present.
Jailbreak Persistence
Once the kernel has been exploited, both exploits perform similar tasks to prepare the system to be jailbroken:
• Disable kernel security protections including code signing
• Remount the system partition
• Clear the Safari caches (to help cover their tracks)
• Write the jailbreak files (including the main loader as /sbin/mount_nfs)
As a final step of stage 2, the exploit removes /etc/nfs.conf which triggers the file to load /sbin/mount_nfs (which is the stage 3 jailbreakloader). Because /sbin/mount_nfs is run as root, the code is run with full privileges. After stage 3 will be unpacked, Pegasus need to gain persistence on device reboot. So exploit replaces the system daemon rtbuddyd with a copy of the jsc binary and creates a link to a script that is similar to the exploit for CVE-2016-4655 .
THE ESPIONAGE SOFTWARE
“Pegasus is one of the most sophisticated pieces of surveillance and espionage software” stated Lookout company. It has a novel mechanism to install and hide itself and obtain persistence on the system. Once it is resident, it uses a number of ways to hide its communications and protect itself from discovery, and it hooks into a large number of the phone’s functions in order to gather data and intercept messages and calls.
Following we will list all the features Pegasus have to spy on the victim a fully detailed list with references of source code):
Persistence: JSC Privilege Escalation
Disabling Updates
Jailbreak Detection
Device Monitoring (Current Reachability, Sim and cell network information, Call info, SIM/Network change notification)
Stealth Update to Command & Control Infrastructure
Self Destruction
Steal Calendar
Steal Contacts
Steal GPS location
Capturing User Passwords
WiFi and Router Passwords
Interception of Calls and Messages
Following an image of an infected phone by Pegasus compared to a normal one:

Image from lookup.com
CONCLUSION
NSO Group reportedly has hundreds of employees and makes millions of dollars in annual revenue, effectively as a cyber arms dealer, from the sale of its sophisticated mobile attack software.
We strongly recommend to all iPhone owners to update to the latest version of iOS (9.3.5) immediately.
Dropbox Hacked — More Than 68 Million Account Details Leaked Online
31.8.2016 thehackernews Hacking
Hackers have obtained credentials for more than 68 Million accounts for online cloud storage platform Dropbox from a known 2012 data breach.
Dropbox has confirmed the breach and already notified its customers of a potential forced password resets, though the initial announcement failed to specify the exact number of affected users.
However, in a selection of files obtained through sources in the database trading community and breach notification service Leakbase, Motherboard found around 5GB of files containing details on 68,680,741 accounts, which includes email addresses and hashed (and salted) passwords for Dropbox users.
An unnamed Dropbox employee verified the legitimacy of the data.
Out of 68 Million, almost 32 Million passwords are secured using the strong hashing function "BCrypt," making difficult for hackers to obtain users' actual passwords, while the rest of the passwords are hashed with the SHA-1 hashing algorithm.
These password hashes also believed to have used a Salt – a random string added to the hashing process to further strengthen passwords in order to make it more difficult for hackers to crack them.
"We've confirmed that the proactive password reset we completed last week covered all potentially impacted users," said Patrick Heim, Head of Trust and Security for Dropbox.
"We initiated this reset as a precautionary measure so that the old passwords from prior to mid-2012 can’t be used to improperly access Dropbox accounts. We still encourage users to reset passwords on other services if they suspect they may have reused their Dropbox password."
Dropbox initially disclosed the data breach in 2012, notifying users that one of its employee passwords was acquired and used to access a file with users’ email addresses, but the company didn't disclose that the hackers were able to pilfer passwords too.
But earlier this week, Dropbox sent out emails alerting its users that a large chunk of its users’ credentials was obtained in 2012 data breach that may soon be seen on the Dark Web marketplace, prompting them to change their password if they hadn't changed since mid-2012.
"Our security teams are always watching out for new threats to our users. As part of these ongoing efforts, we learned about an old set of Dropbox user credentials (email addresses plus hashed and salted passwords) that we believe were obtained in 2012," the company wrote. "Our analysis suggests that the credentials relate to an incident we disclosed around that time."
Dropbox is the latest to join the list of "Mega-Breaches," that revealed this summer, when hundreds of Millions of online credentials from years-old data breaches on popular social network sites, including LinkedIn, MySpace, VK.com and Tumblr, were sold on Dark Web.
The takeaway:
Change your passwords for Dropbox as well as other online accounts immediately, especially if you use the same password for multiple websites.
Also use a good password manager to create complex passwords for different sites as well as remember them. We have listed some best password managers that could help you understand the importance of password manager and choose one according to your requirement.
Linux servers hit with FairWare ransomware – or is it just a scam?
30.8.2016 nethelpsecurity
Users posting on Bleeping Computer’s forums have alerted the world to a new threat targeting Linux server admins: the FairWare ransomware.
Whether the ransomware actually exists or not is still up for debate, as we only have the attackers’ claim that they are using it. It’s perfectly possible that they managed to compromise servers – apparently, through a brute-force SSH attack – and simply deleted the data they claim to have stolen.
Victims of the attack find their web folder deleted, and in its place a ransom note pointing them to an online paste.
There, they find the ransom note, saying that their server has been infected with “a ransomware variant called FAIRWARE,” that they have two weeks to send 2 Bitcoin to a specified address, and that they can contact the attackers via email, but should not expect to see proof that the attackers have the stolen files:

This definitely adds to the suspicion that they might have simply deleted the files in question and, even if the victims pay, they might not get them back.
“Most ransomware developers dont just delete files as it would quickly be found out and noone would pay the ransom,” Bleeping Computer’s Lawrance Abrams noted.
“Its possible they gzipped the www folders, uploaded it, and then deleted it. Unfortunately, wont know unless you email them.”
So far, the attackers’ Bitcoin address has yet to show evidence of a ransom payment. This threat is very recent, and the two week payment deadline is still far off, so victims are likely still trying to discover whether paying the ransom will bring their files back and are looking for answers online.
The son of a Russian lawmaker could face up to 40 years in the jail for hacking
30.8.2016 securityaffeairs Hacking
Roman Seleznev (32), the son of the Russian lawmaker and Russian Parliament member Valery Seleznev was convicted of stealing 2.9 Million credit card numbers
Roman Seleznev (32), the son of one of the most notorious Russian lawmaker and Russian Parliament member Valery Seleznev has been convicted in the US of hacking businesses and stealing 2.9 million US credit card numbers using Point-of-Sale (POS) malware
“A federal jury today convicted a Vladivostok, Russia, man of 38 counts related to his scheme to hack into point-of-sale computers to steal and sell credit card numbers to the criminal underworld, announced Assistant Attorney General Leslie R. Caldwell of the Justice Department’s Criminal Division and U.S. Attorney Annette L. Hayes of the Western District of Washington. ” reads the announcement published by the DoJ.
According to the Department of Justice, the hacking scheme defrauded banks of more than $169 Million. The stolen credit card data were offered for sale on multiple “carding” websites.
“Testimony at trial revealed that Seleznev’s scheme caused 3,700 financial institutions more than $169 million in losses.” continues the note published by the DoJ.
Attacks-as-a-Service-cybercrime
Seleznev, who was using the online moniker ‘Track2‘ was convicted in a Washington court on Thursday of 38 charges related to stolen credit card details, which includes:
Ten counts of Wire Fraud
Nine counts of obtaining information from a Protected Computer
Nine counts of possession of 15 Unauthorized Devices
Eight counts of Intentional Damage to a Protected Computer
Two counts of Aggravated Identity Theft
“Roman Valerevich Seleznev, aka Track2, 32, was convicted after an eight-day trial of 10 counts of wire fraud, eight counts of intentional damage to a protected computer, nine counts of obtaining information from a protected computer, nine counts of possession of 15 or more unauthorized access devices and two counts of aggravated identity theft. U.S. District Judge Richard A. Jones of the Western District of Washington scheduled sentencing for Dec. 2, 2016.”
Roman Seleznev, 32, the son of Russian Parliament member Valery Seleznev, was arrested in 2014 while attempting to board a flight in the Maldives, the arrest raised diplomatic tensions between American and Russian authorities.
The prosecution was built starting from data found on his laptop that was seized at the time of the arrest. The PC contained more than 1.7 million stolen credit card numbers, some of which were stolen from businesses in Western Washington.
The analysis of the laptop allowed the prosecutors to find additional evidence linking Seleznev to the servers, email accounts and financial transactions involved in the hacking scheme.
The prosecution was criticized by the Seleznev’s lawyer, John Henry Browne.
“I don’t know of any case that has allowed such outrageous behavior,” said Browne.
The US DoJ replied that Seleznev “was prosecuted for his conduct not his nationality.”
If convicted, Seleznev could face up to 40 years in the jail, his victims were small businesses and retailers hacked from 2008 to 2014.
Seleznev will be sentenced on December 2.
Shad0wS3C group hacked the Paraguay Secretary of National Emergency
30.8.2016 securityaffeairs Hacking
Shad0wS3C hacker group has hacked the Paraguay’s Secretary of National Emergency (SNE) and leaked online a dump from a PostgreSQL database.
Not so long ago I interviewed Gh0s7, the leader of the Shad0wS3C hacker crew, now he contacted me to announce the hack of the Paraguay’s Secretary of National Emergency (SNE).
“The reason for this data leak. The government of Paraguay has violated so many human rights, and either the UN (Don’t rely on them) or anyone has done anything. just to name a few:
Impunity and justice system
Torture and other ill-treatment
Violation of Women’s and girls’ rights
Violation against Human rights defenders”
this is the Shad0wS3C message.

The group has shared as proof of the hack a data dump from a PostgreSQL database, just after the announced security breach the Government website sen.gov.py was up.
The leaked data dump includes information about material stocks and also PII belonging to Paraguay’s Secretary of National Emergency employees. Users’ records include names, emails, phone numbers, addresses, salary information, and other data related to their activity within the Government organization (i.e Roles in the case of national emergencies).

The leaked data also includes details on hundreds website login credentials, with hashed passwords.
Shad0wS3c is a hacker group recently formed, in July it claimed responsibility for the data breach of the EJBCA that resulted in the exposure of credentials and certificates.
Spam and phishing in Q2 2016
30.8.2016 Kaspersky Spam
Spam: quarterly highlights
The year of ransomware in spam
Although the second quarter of 2016 has only just finished, it’s safe to say that this is already the year of ransomware Trojans. By the end of Q2 there was still a large number of emails with malicious attachments, most of which download ransomware in one way or other to a victim’s computer. However, in the period between 1 June and 21 June the proportion of these emails decreased dramatically.
The majority of malicious attachments were distributed in ZIP archives. The decline can therefore be clearly seen in the following graph showing spam with ZIP attachments that arrived in our traps:
Number of emails with ZIP archives, Q2 2016
In addition to the decline, June saw another interesting feature: this sort of spam was not sent out on Saturdays or Sundays.
The same situation could be observed in KSN: the number of email antivirus detections dropped sharply on 1 June and grew on 22 June.
Number of email antivirus detections by day, Q2 2016
This decline was caused by a temporary lull in activity by the Necurs botnet, which is mostly used to distribute this type of malicious spam. After the botnet resumed its activity, the spam email template changed, and the malicious attachments became even more sophisticated.
As in the previous quarter, the spam messages were mainly notifications about bills, invoices or price lists that were supposedly attached to the email. The attachments actually contained a Trojan downloader written in Javascript, and in most cases the malware loaded the Locky encryptor.
For example, some emails (see the screenshot above) contained an attachment with a Trojan downloader. When run, it downloaded Trojan-Ransom.Win32.Locky.agn, which encrypts the data on a victim’s computer and demands a ransom, to be paid in bitcoin.
Obfuscation
The second quarter saw spammers continue to mask links using various Unicode ranges designed for specific purposes. This tactic became especially popular in 2015, and is still widely used by spammers.
The link in this example looks like this:
If you transfer the domain from UTF-8 into the more familiar HTML, it becomes . The characters, which look quite ordinary, in fact belong to the Mathematical Alphanumeric Symbols UTF range used in highly specific mathematical formulas, and are not intended for use in plain text or hyperlinks. The dot in the domain is also unusual: it is the fullwidth full stop used in hieroglyphic languages. The rest of the hyperlink, as well as the rest of the text in these spam messages, is written using the Latin alphabet.
Spam in APT attacks
In Q2, we came across a number of APT attacks in the corporate sector. Emails were made to look as if they came from representatives of the targeted company, and contained a request to immediately transfer money to a specific account. The text was fairly plausible and hinted at a personal acquaintance and previous communication. In some cases, the emails included the logo of the attacked company. All the messages conveyed a sense of urgency (“ASAP”, “urgent”, “must be completed today”) – scammers often use this trick in an attempt to catch people off guard, so that they act rather than think.
Below is an example:
Hello NNNNN,
How are you doing! Are you available at the office? I need you to process an overdue payment that needs to be paid today.
Thanks,
XXXXX
The emails were sent selectively – to individual employees, usually connected to the finance department. The knowledge shown by the scammers suggests the attack was carefully prepared.
The most suspicious aspect of the attack was the domain used in the ‘From’ field – myfirm.moby – that differed from the corporate one. Perhaps the attackers hope that some email clients only show the sender’s name by default, while concealing the address.
It is not that difficult to write any domain in the ‘From’ field, and in the future we can expect more well-prepared attacks.
Sporting events in spam
Spam mailings exploiting real-life events have long become an integral part of junk email. Sporting events are not as popular among spammers as political events, although their use is increasing with every year. There is a continuous stream of emails mentioning various political figures, while sport-related spam messages usually only appear in the run-up to an event. However, we have noticed that mass mailings can now be launched long before an event starts. For instance, emails exploiting the Olympic Games in Brazil were discovered over a year ago, in the second quarter of 2015. The majority of them were fraudulent emails designed to trick recipients and steal their personal information and money.
The classic scenario involves false notifications about lottery wins related to 2016 Olympics. The messages claim that the lottery was held by the official organizers of the games and the recipient was selected at random from millions of addresses. In order to claim the cash, the recipient has to reply to the email and provide some personal information.
The text of the message was often contained in an attached file (.pdf, .doc, .jpg), while the body of the message only displayed a short text prompting the recipient to open the attachment.
There were also more traditional messages where the spammer text was included directly in the body of the message.
In addition to fraudulent messages, advertising spam was also sent out.
Unlike the Olympics, football tournaments have long been used by scammers to grab people’s attention to their spam. Q2 2016 saw the long-awaited UEFA European Championship, and in the run-up to the tournament spam traffic included fake notifications of lottery wins. The content was no different from that dedicated to the Olympic Games, and the emails also contained attachments explaining why the message was sent.
The football theme was also exploited by ‘Nigerian’ scammers. They sent out emails supposedly on behalf of the former FIFA president, and used the infamous corruption scandal associated with his name to make their messages look more realistic. They believed that a fabricated story about how Sepp Blatter had supposedly received money and secretly transferred it to an account in a European bank would not arouse suspicion. In return for keeping the money in their bank accounts, the recipients were promised a 40% cut of the total sum.
In order to convince recipients that the message was genuine, the authors even went to the trouble of using the correct name and domain in the ‘From’ field.
US politicians in spam
The presidential election campaign is now in full swing in the United States and the nominees and their entourages are under close media scrutiny. Of course, spammers couldn’t resist using the names of high-profile politicians in their advertising and fraudulent emails. For example, numerous ‘Nigerian’ letters were sent in the name of current president Barack Obama and his wife Michelle. In their ‘official’ emails, the ‘President’ and the ‘First lady’ assured the recipient that a bank card or a check for a very large sum of money had already been issued in their name. The only thing the recipient had to do was complete some formalities, and the money would be delivered shortly afterwards. In order to get the instructions from the White House the recipient had to send some personal information, including their email address and the password for their email account, as well as detailed passport information to spoofed email addresses.
Another politician whose name regularly cropped up in spam was Donald Trump, one of the contenders for the US presidency. Spammers offered a unique Trump technique for earning money online: anyone who wanted to know how to get rich, had to click a link in the emails which were designed to look like news reports from CNN and Fox News.
The links led to fake news sites also in the style of major media outlets and news networks. The sites contained a story about a simple method for earning money – the publication of links, which is basically another kind of spam distribution. In order to participate in the program, a user had to register by providing their phone number and email address.
Statistics
Proportion of spam in email traffic
Percentage of spam in global email traffic, Q2 2016
The largest percentage of spam in the second quarter – 59.46% – was registered in May and was 3 p.p. more than in April. The average percentage of spam in global email traffic for Q2 amounted to 57.25%.
Sources of spam by country
Sources of spam by country, Q2 2016
In Q2 2016, the biggest three sources of spam remained the same as in the previous quarter – the US (10.79%), Vietnam (10.10%) and India (10.01%). However, the figures for each country changed: the gap between them narrowed to within a single percentage point.
China (6.52%) moved up to fourth with an increase of 1.43 p. p. compared to Q1. Mexico (4.55%) came fifth, followed by Russia (4.07%) and France (3.60%). Brazil (3.28%), which was fourth in the previous quarter, lost 2.2 p.p. and dropped to eighth place. Germany (2.97%) and Turkey (2.30%) completed the TOP 10.
Spam email size
Breakdown of spam emails by size, Q1 and Q2 2016
Traditionally, the most commonly distributed emails are very small – up to 2 KB (72.26%), although the proportion of these emails dropped by 9.6 p.p. compared to the previous quarter. Meanwhile, the share of emails sized 10-20 KB increased by 6.76 p.p. The other categories saw minimal changes.
Malicious email attachments
Currently, the majority of malicious programs are detected proactively by automatic means, which makes it very difficult to gather statistics on specific malware modifications. So we have decided to turn to the more informative statistics of the TOP 10 malware families.
TOP 10 malware families
The three most popular malware families remained unchanged from the previous quarter – Trojan-Downloader.JS.Agent (10.45%), Trojan-Downloader.VBS.Agent (2.16%) and Trojan-Downloader.MSWord.Agent (1.82%).
The Trojan.Win32.Bayrob family moved up to fourth place (1.68%), while the Backdoor.Win32.Androm family fell from fourth to ninth place with 0.6%.
TOP 10 malware families in Q2 2016
A newcomer to this ranking was the Trojan.Win32.Inject family (0.61%). The malicious programs from this family embed their code in the address space of other processes.
The Trojan-Spy.HTML.Fraud family (0.55%) rounded off the TOP 10 in Q2 2016.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, Q2 2016
Germany (14.69%) topped the ranking of countries targeted by malicious mailshots, although its share decreased 4.24 p.p. It was followed by China (13.61%) whose contribution grew 4.18 p.p. Japan (6.42%) came third after ending the previous quarter in seventh with a share of 4.29%.
Fourth place was occupied by Brazil (5.57%). Italy claimed fifth with a share of 4.9% and Russia remained in sixth (4.36%).
The US (4.06%) was the seventh most popular target of malicious mailshots. Austria (2.29%) rounded off this TOP 10.
Phishing
In Q2 2016, the Anti-Phishing system was triggered 32,363,492 times on the computers of Kaspersky Lab users, which is 2.6 million less than the previous quarter. Overall, 8.7% of unique users of Kaspersky Lab products were attacked by phishers in Q2 of 2016.
Geography of attacks
The country where the largest percentage of users is affected by phishing attacks was China (20.22%). In Q2 2016, the proportion of those attacked increased by 3.52 p.p.
Geography of phishing attacks*, Q2 2015
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in the country
The percentage of attacked users in Brazil decreased by 2.87 p.p. and accounted for 18.63%, placing the country second in this ranking. Algeria (14.3%) came third following a 2.92 p.p. increase in its share compared to the previous quarter.
TOP 10 countries by percentage of users attacked:
China 20.22%
Brazil 18.63%
Algeria 14.3%
United Kingdom 12.95%
Australia 12.77%
Vietnam 11.46%
Ecuador 11.14%
Chile 11.08%
Qatar 10.97%
Maldives 10.94%
Organizations under attack
The statistics on phishing targets are based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
In Q2 of 2016, the share of the ‘Global Internet portals’ category (20.85%), which topped the rating in the first quarter, decreased considerably – by 7.84 p.p. The share of the ‘Financial organizations’ category grew 2.07 p.p. and accounted for 46.23%. This category covers ‘Banks’ (25.43%, +1.51 p.p.), ‘Payment systems’ (11.42%, -0.42 p.p.) and ‘Online stores’ (9.39%, +0.99 p.p.).
Distribution of organizations affected by phishing attacks by category, Q2 2016
The share of attacks on the ‘Social networking sites’ category increased by 2.65 p.p. and reached 12.4%. The ‘Online games’ category was also attacked more often (5.65%, + 1.96 p.p.). Meanwhile, the ‘Telephone and Internet service providers’ (4.33%) and the ‘IMS’ (1.28%) categories lost 1.17 p.p. and 2.15 p.p. respectively.
Hot topics this quarter
The Olympics in Brazil
For a number of years now Brazil has been among the countries with the highest proportion of users targeted by phishing. In 2015 and 2016 phishers have focused on the Rio Olympic Games in Brazil. Last quarter showed that as well as ordinary users, the potential victims of phishing included the organizers of the Olympic Games.
The Olympic theme remained popular in Q2, with phishers working overtime to send out fake notifications about big cash wins in a lottery that was supposedly organized by the Brazilian government and the Olympic Committee.
‘Porn virus’ for Facebook users
Facebook users are often subjected to phishing attacks. During one attack in the second quarter, a provocative video was used as bait. To view it, the user was directed to a fake page imitating the popular YouTube video portal, and told to install a browser extension.
This extension requested rights to read all the data in the browser, potentially giving the cybercriminals access to passwords, logins, credit card details and other confidential user information. The extension also distributed more links on Facebook that directed to itself, but which were sent using the victim’s name.
Phisher tricks
Compromising domains with good reputation
To bypass security software filters, fraudsters try to place phishing pages on domains with good reputations. This significantly reduces the probability of them being blocked and means potential victims are more trusting. The phishers can strike it big if they can use a bank or a government agency domain for their purposes. In Q2, we came across a phishing attack targeting the visitors of a popular Brazilian e-commerce site: the fake page was located on the domain of a major Indian bank. This is not the first time fraudsters have compromised the domain of a large bank and placed their content on it.
Phishing pages targeting the users of the Brazilian store americanas.com
When trying to purchase goods on the fake pages of the store, the victim is asked to enter lots of personal information. When it’s time to pay, the victim is prompted to print out a receipt that now shows the logo of a Brazilian bank.
The domains of state structures are hacked much more frequently by phishers. In Q2 2016, we registered numerous cases where phishing pages were located on the domains belonging to the governments of various countries. Here are just a few of them:
Phishing pages located on the domains of government authorities
The probability of these links being placed on blacklists is negligible thanks to the reputation of the domain.
TOP 3 organizations attacked
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections of Kaspersky Lab’s heuristic anti-phishing component fall on phishing pages hiding behind the names of fewer than 15 companies.
The TOP 3 organizations attacked most frequently by phishers accounted for 23% of all phishing links detected in Q2 2016.
Organization % of detected phishing links
1 Microsoft 8.1
2 Facebook 8.03
3 Yahoo! 6.87
In Q2 2016, this TOP 3 ranking saw a few changes. Microsoft was the new leader with 8.1% (+0.61 p.p.), while Facebook (8.03%, +2.32 p.p.) came second. The share of attacks targeting Yahoo! (6.87%) fell 1.46 p.p., leaving last quarter’s leader in third.
Q2 leader Microsoft is included in the ‘Global Internet portals’ category because the user can access a variety of the company’s services from a single account. This is what attracts the fraudsters: in the event of a successful attack, they gain access to a number of services used by the victim.
Example of phishing on Live.com, a Microsoft service
Conclusion
In the second quarter of 2016, the proportion of spam in email traffic increased insignificantly – by 0.33 p.p. – compared to the previous quarter and accounted for 57.25%. The US remained the biggest source of spam. As in the previous quarter, the top three sources also included Vietnam and India.
Germany was once again the country targeted most by malicious mailshots, followed closely by China. Japan, which was seventh in the previous quarter’s ranking, completed the TOP 3 in Q2.
Trojan-Downloader.JS.Agent remained the most popular malware family distributed via email. Next came Trojan-Downloader.VBS.Agent and Trojan-Downloader.MSWord.Agent. A significant amount of malicious spam was used to spread ransomware Trojans such as Locky. For almost a month, however, cybercriminals did not distribute their malicious spam, but then the Necurs botnet began working again. We don’t expect to see any significant reduction in the volume of malicious spam in the near future, although there may be changes in email patterns, the complexity of the malware, as well as the social engineering methods used by attackers to encourage a user to launch a malicious attachment.
The focus of phishing attacks shifted slightly from the ‘Global Internet portals’ to the ‘Financial organizations’ category.
The theme of the Olympic Games was exploited by both phishers and spammers to make users visit fake pages with the aim of acquiring their confidential information or simply to get their money.
Events in the political arena, such as the presidential election in the US, also attracted spammers, while the sites of government agencies were compromised in phishing attacks.
As we can see, the overriding trend of the quarter is that of fraud and making quick money from victims using direct methods such as Trojan cryptors that force unprotected users to pay a ransom, or phishing attacks that target financial organizations, rather than long drawn-out scams. All of this once again highlights the need for both comprehensive protection on computers and increased vigilance by Internet users.
Chinese Certificate Authority 'mistakenly' gave out SSL Certs for GitHub Domains
30.8.2016 thehackernews Safety
github-ssl-certificate
A Chinese certificate authority (CA) appeared to be making a significant security blunder by handing out duplicate SSL certificates for a base domain if someone just has control over its any subdomain.
The certificate authority, named WoSign, issued a base certificate for the Github domains to an unnamed GitHub user.
But How? First of all, do you know, the traditional Digital Certificate Management System is the weakest link on the Internet today and has already been broken?
Billions of Internet users blindly rely on hundreds of Certificate Authorities (CA) around the globe to ensure the confidentiality and integrity of their personal data.
But, these CAs have powers to issue valid SSL cert for any domain you own, despite the fact you already have one purchased from another CA.
...and that's the biggest loophole in the CA system.
In the latest case as well, WoSign issued a duplicate SSL certificate for GitHub domains without verifying ownership of the base domain.
The incident was first publicly disclosed by British Mozilla programmer Gervase Markham on Mozilla's security policy mailing list saying the issue occurred over a year ago in July 2015 but went unreported.
"In June 2015, an applicant found a problem with WoSign's free certificate service, which allowed them to get a certificate for the base domain if they were able to prove control of a subdomain," Markham wrote in the mailing list.
According to Markham, an unnamed security researcher accidentally discovered this security blunder when trying to get a certificate for 'med.ucf.edu' but mistakenly also applied for 'www.ucf.edu' and WoSign approved it, handing over the certificate for the university's primary domain.
For testing purpose, the researcher also used this trick against Github base domains i.e. github.com and github.io, by proving his control over a user-based subdomain.
...And guess what? WoSign handed over the certificate for GitHub main domains, too.
The researcher reported this issue to WoSign by giving only the Github certificate as an example. Thus, the Chinese CA only revoked the GitHub certificate, despite revoking both the certificates.
Why Just One? It is quite possible that the CA company doesn't have any tracking ability to discover and revoke all mistakenly issued base certificates for other domains by self-investigation even after getting informed of the problem.
The researcher recently got in touch with Google and reported that the ucf.edu cert had still not been revoked almost a year later.
How to check whether a rogue cert for your domain has been issued to someone else, probably a malicious attacker?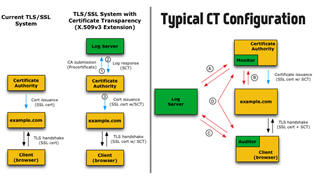
Solution: Certificate Transparency or CT, a public service that allows individuals and companies to monitor how many digital security certs have secretly been issued for their domains.
Certificate Transparency requires CAs to declare publicly (to Certificate Log) every digital cert they have generated. Even WoSign has participated in CT.
Certificate Log offers you a way to look up all of the digital certificates that have been issued for your domain name.
Also read: Learn How Certificate Transparency Monitoring Tool Helped Facebook Early Detect Duplicate SSL Certs?
Although Certificate Transparency doesn't prevent CA from issuing forged certificates, it makes the process of detecting rogue certificates much easier.
Currently, Google, Symantec, DigiCert, and a few other CAs are hosting public CT logs.
You can try Google's Certificate Transparency Lookup Tool or Comodo's Certificate Transparency Search tool to check all certificates present in public Certificate Transparency logs that have been issued for your domain.
If you find a fraud certificate issued for your domain, report respective CA and address it immediately.
Russian Lawmaker's Son Convicted of Stealing 2.9 Million Credit Card Numbers
29.8.2016 thehackernews Crime
Russian Lawmaker's Son Convicted of Stealing 2.9 Million Credit Card Numbers
The son of a prominent Russian lawmaker has been found guilty in the United States of running a hacking scheme that stole and sold 2.9 million US credit card numbers using Point-of-Sale (POS) malware, costing financial institutions more than $169 Million.
Roman Seleznev, 32, the son of Russian Parliament member Valery Seleznev, was arrested in 2014 while attempting to board a flight in the Maldives, which sparked an international dispute between American and Russian authorities, who characterized the extradition as a "kidnapping."
Prosecutors introduced evidence from a corrupted laptop seized by the authorities at the time of his arrest. "I don't know of any case that has allowed such outrageous behavior," said his lawyer, John Henry Browne.
Also Read: How to Freeze Credit Report To Protect Yourself Against Identity Theft.
According to the Department of Justice, Seleznev, who also went by the moniker 'Track2' online, was convicted in a Washington court on Thursday of 38 charges related to stolen credit card details, which includes:
Ten counts of Wire Fraud
Nine counts of obtaining information from a Protected Computer
Nine counts of possession of 15 Unauthorized Devices
Eight counts of Intentional Damage to a Protected Computer
Two counts of Aggravated Identity Theft
Seleznev and potentially other criminals who are unknown to the authorities developed a hacking scheme that used automated techniques to hack into POS machines in retailers and then installed malware to steal copies of credit card numbers.
The lists of stolen credit card numbers were then sold on various online "carding" websites. According to prosecutors, more than 3,700 businesses were hit by the hacking attacks.
If convicted, Seleznev could face up to 40 years in prison for hacking into Seattle pizza shops, retailers and U.S. businesses around the globe from 2008 to 2014 and stealing millions of credit card details.
Seleznev faces a mandatory jail term of 4 years, and will be sentenced on 2 December.
The US Justice Department said Seleznev "was prosecuted for his conduct not his nationality."