
New ThreadKit exploit builder used to spread banking Trojan and RATs
29.3.2018 securityaffairs Virus
A recently discovered Microsoft Office document exploit builder kit dubbed ThreadKit has been used to spread a variety of malware, including RATs and banking Trojans.
Security experts at Proofpoint recently discovered a Microsoft Office document exploit builder kit dubbed ThreadKit that has been used to spread a variety of malware, including banking Trojans and RATs (i.e. Trickbot, Chthonic, FormBook and Loki Bot).
The exploit kit was first discovered in October 2017, but according to the experts, crooks are using it at least since June 2017.
The ThreadKit builder kit shows similarities to Microsoft Word Intruder (MWI), it was initially being advertised in a forum post as a builder for weaponized decoy documents.
“In October 2017, Proofpoint researchers discovered a new Microsoft Office document exploit builder kit that featured a variety of recent exploits as well as a mechanism to report infection statistics.” reads the analysis published by ProofPoint. “While the documents produced by this kit exhibited some minor similarities to Microsoft Word Intruder (MWI), we determined that they were likely produced by a new exploit builder kit, which we started tracking as ThreadKit.”
Just after its appearance, documents created with the ThreadKit builder kit have been observed in several campaigns.
The decoy documents used in past campaigns performed an initial check-in to the command and control (C&C) server, a tactic also used by MWI.
The documents were triggering the CVE-2017-0199 vulnerability in Office to download and execute an HTA file that would then download the decoy and a malicious VB script to extract and run the embedded executable.

The last step of the infection sees the execution of the Smoke Loader, a small application used to download other malicious codes, in these specific attacks a banking malware.
Starting from October 2017, researchers observed the ThreadKit triggering the CVE 2017-8759 vulnerability.
“In October 2017, we started observing corresponding campaigns utilizing CVE-2017-8759. This version of ThreadKit employed a similar infection statistic initial C&C check-in and HTA to execute the embedded executable. Other changes were made to the way the exploit documents operate, in addition to integrating the new vulnerabilities.” continues the analysis.
Since November, ThreadKit integrated the code for the exploitation of the CVE 2017-11882, a 17-Year-Old flaw in MS Officeexploited by remote attackers to install a malware without user interaction.
In the last weeks, the exploit kit included new exploits targeting vulnerabilities such as the CVE-2018-4878 Adobe Flash zero-day and several Microsoft office vulnerabilities (i.e. CVE-2018-0802 and CVE-2017-8570).
Proofpoint researchers observed numerous campaigns featuring ThreadKit-generated Office attachments packing exploits that were likely copied from PoC code available on a researcher’s GitHub repo.
“ThreadKit is a relatively new and popular document exploit builder kit that has been used in the wild since at least June, 2017, by a variety of actors carrying out both targeted and broad-based crimeware campaigns. This new document exploit builder kit makes the use of the latest Microsoft Office exploits accessible to even low-skilled malicious actors.” concluded Proofpoint.
Meltdown security patches issued by Microsoft exposed to severe attacks
29.3.2018 securityaffairs Attack
A security researcher discovered that some of the Windows updates released by Microsoft to mitigate the Meltdown flaw introduce a severe bug.
Meltdown and Spectre security updates made the headlines again, according to the security researcher Ulf Frisk some of them issued for Windows introduce a severe flaw.
The Meltdown and Spectre security updates released by Microsoft in January and February for Windows 7 and Windows Server 2008 R2 patch Meltdown are affected by a vulnerability that could be exploited by attackers to easily read from and write to memory.
According to the expert, an attacker can exploit gigabytes of data per second by exploiting the vulnerability.
“Meet the Windows 7 Meltdown patch from January. It stopped Meltdown but opened up a vulnerability way worse … It allowed any process to read the complete memory contents at gigabytes per second, oh – it was possible to write to arbitrary memory as well.” wrote the expert.
“No fancy exploits were needed. Windows 7 already did the hard work of mapping in the required memory into every running process. Exploitation was just a matter of read and write to already mapped in-process virtual memory. No fancy APIs or syscalls required – just standard read and write! ”
In a test conducted by the experts, he successfully accessed the memory at speeds of over 4 Gbps.
The researcher pointed out that attacker doesn’t need sophisticated exploits because Windows 7 has already mapped the memory for each active process. The page tables are available to user mode code for each process, instead
“In short – the User/Supervisor permission bit was set to User in the PML4 self-referencing entry. This made the page tables available to user mode code in every process. The page tables should normally only be accessible by the kernel itself,” the researcher added. “
The PML4 is the base of the 4-level in-memory page table hierarchy that the CPU Memory Management Unit (MMU) uses to translate the virtual addresses of a process into physical memory addresses in RAM.”
Once the attacker obtained the access to the page tables it will gain full control over the memory and its content.
“Once read/write access has been gained to the page tables it will be trivially easy to gain access to the complete physical memory, unless it is additionally protected by Extended Page Tables (EPTs) used for Virtualization. All one have to do is to write their own Page Table Entries (PTEs) into the page tables to access arbitrary physical memory,” he added. 
Frisk developed an attack tool dubbed PCILeech to trigger the flaw.
“PCILeech uses PCIe hardware devices to read and write from the target system memory. This is achieved by using DMA over PCIe. No drivers are needed on the target system.” reads the description of the tool.
“PCILeech supports multiple memory acquisition devices. Primarily hardware based, but also dump files and software based techniques based on select security issues are supported. USB3380 based hardware is only able to read 4GB of memory natively, but is able to read all memory if a kernel module (KMD) is first inserted into the target system kernel. FPGA based hardware is able to read all memory.”
“PCILeech is capable of inserting a wide range of kernel implants into the targeted kernels – allowing for easy access to live ram and the file system via a “mounted drive”.
The experts successfully tested the attack against systems running Windows 7 x64 or Windows Server 2008 R2 with the Microsoft patches from January or February installed. Windows 10 and Windows 8.1 are not affected by the issue.
Hackers took down Baltimore 911 system during the weekend
29.3.2018 securityaffairs Incindent
Another US city hit by hackers, over the weekend, a cyber attack took down part of Baltimore 911 system for seventeen hours.
Part of its 911 service at the US city of Baltimore was taken down during the weekend by a cyber attack. The attackers targeted a specific server and took down the CAD system from 8.30am Saturday until around 2 am Sunday.
“Baltimore’s 911 dispatch system was hacked by an unknown actor or actors over the weekend, prompting a temporary shutdown of automated dispatching and an investigation into the breach, Mayor Catherine Pugh’s office confirmed Tuesday.” reported the Baltimore Sun.
“James Bentley, a spokesman for Pugh, confirmed that the Sunday morning hack affected messaging functions within the computer-aided dispatch, or CAD, system, but said the mayor would not otherwise comment on the matter Tuesday.”

The cyber attack shut down the emergency service’s Computer Aided Dispatch (CAD) that is used by 911 operators. No systems beyond the one CAD server were hit in the cyber attack, according to the media no data was exposed.
The function of the 911 service is essential to respond to any emergency and to direct police, fire, and ambulance to the place of an emergency.
During the attack, the 911 operators were forced to manually dispatch responders. 911 and 311 “were temporarily transitioned to manual mode.”
The attack was launched while thousands of protesters were participating in the nationwide march against gun violence.
City personnel were able to “isolate and take offline the affected server, thus mitigating the threat” of the hack, said Frank Johnson, chief information officer in the Mayor’s Office of Information Technology.
No systems beyond the one CAD server were hit by the cyber attack, and no data was exposed or stolen.
A few days ago, the networks of another major US city, Atlanta, were infected with a variant of the SamSam ransomware.
QR Code Bug in Apple iOS 11 Could Lead You to Malicious Sites
29.3.2018 thehackernews iOS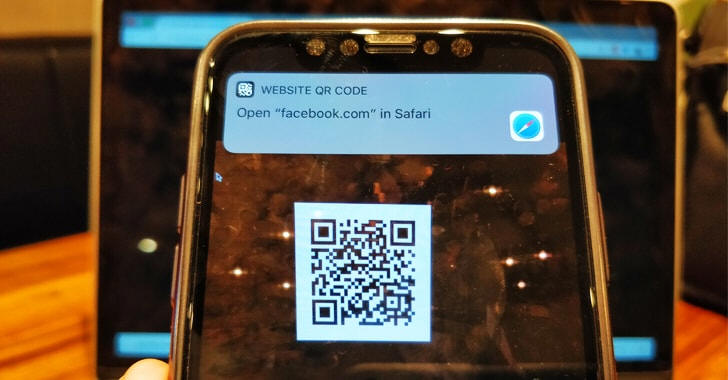
A new vulnerability has been disclosed in iOS Camera App that could be exploited to redirect users to a malicious website without their knowledge.
The vulnerability affects Apple's latest iOS 11 mobile operating system for iPhone, iPad, and iPod touch devices and resides in the built-in QR code reader.
With iOS 11, Apple introduced a new feature that gives users ability to automatically read QR codes using their iPhone's native camera app without requiring any third-party QR code reader app.
You need to open the Camera app on your iPhone or iPad and point the device at a QR code. If the code contains any URL, it will give you a notification with the link address, asking you to tap to visit it in Safari browser.
However, be careful — you may not be visiting the URL displayed to you, security researcher Roman Mueller discovered.
According to Mueller, the URL parser of built-in QR code reader for iOS camera app fails to detect the hostname in the URL, which allows attackers to manipulate the displayed URL in the notification, tricking users to visit malicious websites instead.
For the demo, the researcher created a QR code (shown above) with the following URL:
https://xxx\@facebook.com:443@infosec.rm-it.de/
If you scan it with the iOS camera app, it will show following notification:
Open "facebook.com" in Safari
When you tap it to open the site, it will instead open:
https://infosec.rm-it.de/
I have tested the vulnerability, as shown in the screenshot above, on my iPhone X running iOS 11.2.6 and it worked.
QR (Quick Response) code is a quick and convenient way to share information, but the issue becomes particularly more dangerous when users rely on QR codes for making quick payments or opening banking websites, where they might end up giving their login credentials away to phishing websites.
The researcher had already reported this flaw to Apple in December last year, but Apple hasn’t yet fixed the bug to the date.
U.S. Charges 9 Iranians With Hacking Universities to Steal Research Data
29.3.2018 thehackernews BigBrothers
The United States Department of Justice has announced criminal charges and sanctions against 9 Iranians involved in hacking universities, tech companies, and government organisations worldwide to steal scientific research resources and academic papers.
According to the FBI officials, the individuals are connected to the Mabna Institute, an Iran-based company created in 2013 whose members were allegedly hired by the Iranian government for gathering intelligence.
Though the content of the papers is not yet known, investigators believe it might have helped Iranian scientists to develop nuclear weapons.
In past four years, the state-sponsored hacking group has allegedly infiltrated more than 320 universities in 22 countries—144 of which were in the United States—and stolen over 30 terabytes of academic data and intellectual property.
The group used spear-phishing attacks to target more than 100,000 e-mail accounts and computer systems of the professors around the world, and successfully compromised 7,998 of those accounts till last December—3,768 of them at US universities.
"Their primary goal was to obtain usernames and passwords for the accounts of professors so they could gain unauthorized access and steal whatever kind of proprietary academic information they could get their hands on," said the FBI agent who investigated the case.
According to the indictment unsealed today in a Manhattan federal court, Mabna Institute also shared stolen credentials with the Islamic Revolutionary Guard Corps (IRGC)—a branch of Iran's Armed Forces responsible for gathering intelligence.
The group then exfiltrated the academic data and sold the content via Megapaper.ir and Gigapaper.ir, Iranian websites "where customers could access the online library systems of the hacked universities."
Following are the names and roles of the nine Iranians who were charged by the U.S. federal court:
Gholamreza Rafatnejad — one of the founding members of the Mabna Institute.
Ehsan Mohammadi — another founding member of the Mabna Institute and responsible for organising hacking campaign along with Rafatnejad.
Seyed Ali Mirkarimi — a hacker and Mabna Institute contractor, who was engaged in crafting and sending malicious spear phishing emails to steal credentials belonging to university professors.
Mostafa Sadeghi — another hacker working with the Mabna Institute, who allegedly compromised more than 1,000 university professors’ accounts and exchanged their credentials with Iranian partners.
Sajjad Tahmasebi — a Mabna Institute contractor who was maintaining the list of stolen credentials and helped other hackers in reconnaissance process in order to prepare the list of targeted universities and professors to facilitate the spear phishing campaign.
Abdollah Karima — a businessman who owned and operated a website to sell stolen academic materials online.
Abuzar Gohari Moqadam — an Iranian professor who exchanged stolen credentials for compromised accounts with Mabna Institute founders.
Roozbeh Sabahi — another contractor for the Mabna Institute.
Mohammed Reza Sabahi — another Mabna Institute contractor, who assisted in making the lists of targeted university professors and academic databases.
"Although it is difficult to calculate a dollar loss amount, through the course of the conspiracy, U.S.-based universities spent approximately $3.4 billion to procure and access data that the Iranians accessed for free because of their criminal activity," FBI said.
Targeted countries include Japan, China, Australia, Canada, Denmark, Finland, Germany, Ireland, Israel, Italy, Malaysia, the Netherlands, Norway, Poland, Singapore, South Korea, Spain, Sweden, Switzerland, Turkey, and the United Kingdom.
The US also imposes sanctions on "Game of Thrones" hacker
Besides these 9 Iranian hackers, the U.S. Department of Treasury has also charged a 10th Iranian hacker, named Behzad Mesri, in connection with cyber attacks against HBO and with leaking "Game of Thrones" episodes last summer.
According to the authorities, Mesri compromised multiple user accounts belonging to HBO in order to "repeatedly gain unauthorized access to the company’s computer servers and steal valuable stolen data including confidential and proprietary information, financial documents, and employee contact information."
Mesri then attempted to extort HBO for $6 million to delete the stolen data.
Facebook Collected Your Android Call History and SMS Data For Years
29.3.2018 thehackernews Social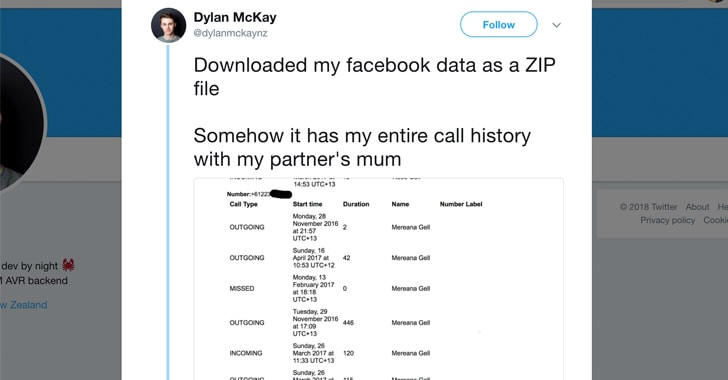
Facebook knows a lot about you, your likes and dislikes—it's no surprise.
But do you know, if you have installed Facebook Messenger app on your Android device, there are chances that the company had been collecting your contacts, SMS, and call history data at least until late last year.
A tweet from Dylan McKay, a New Zealand-based programmer, which received more than 38,000 retweets (at the time of writing), showed how he found his year-old data—including complete logs of incoming and outgoing calls and SMS messages—in an archive he downloaded (as a ZIP file) from Facebook.
Facebook was collecting this data on its users from last few years, which was even reported earlier in media, but the story did not get much attention at that time.
Since Facebook had been embroiled into controversies over its data sharing practices after the Cambridge Analytica scandal last week, tweets from McKay went viral and has now fueled the never-ending privacy debate.
A Facebook spokesperson explained, since almost all social networking sites have been designed to make it easier for users to connect with their friends and family members, Facebook also uploads its users’ contacts to offer same.
As Ars reported, in older versions of Android when permissions were a lot less strict, the Facebook app took away contact permission at the time of installation that allowed the company access to call and message data automatically.
Eventually, Google changed the way Android permissions worked in version 16 of its API, making them more clear and granular by informing users whenever any app tries to execute permissions.
However, developers were able to bypass this change, and Facebook continued accessing call and SMS data until Google deprecated version 4.0 of the Android API in October last year.
Even you can check what data the social network has collected on you so far by going to your Facebook's Settings→Download a copy of your Facebook data→Start My Archive.
If you don't want Facebook to store or continuously upload your contacts to its server, you can turn off the continuous uploading setting in the Messenger app. This change will also delete all your previously uploaded contacts.
Facebook users on Apple devices are on the safer side, as iOS has never allowed silent access to call data.
Leader of Hacking Group Who Stole $1 Billion From Banks Arrested In Spain
29.3.2018 thehackernews CyberCrime
Spanish Police has arrested the alleged leader of an organised Russian cybercrime gang behind the Carbanak and Cobalt malware attacks, which stole over a billion euros from banks worldwide since 2013.
In a coordinated operation with law enforcement agencies across the globe, including the FBI and Europol, Police detained the suspected leader of Carbanak hacking group in Alicante, Spain.
Carbanak hacking group started its activities almost five years ago by launching a series of malware attack campaigns such as Anunak and Carbanak to compromise banks and ATM networks, from which they swiped millions of credit card details from US-based retailers.
According to the Europol, the group later developed a sophisticated heist-ready banking malware known as Cobalt, based on the Cobalt Strike penetration testing software, which was in use until 2016.
"The magnitude of the losses is significant: the Cobalt malware alone allowed criminals to steal up to EUR 10 million per heist," Europol said.
In order to compromise bank networks, the group sent malicious spear-phishing emails to hundreds of employees at different banks, which if opened, infected computers with Carbanak malware, allowing hackers to transfer money from the banks to fake accounts or ATMs monitored by criminals.
According to the authorities, the criminal profits were also laundered via cryptocurrencies, through prepaid cards linked to the cryptocurrency wallets, which were used to buy goods such as luxury cars and houses.
In early 2017, the gang of financially-motivated cybercriminals was found abusing various Google services to issue command and control (C&C) communications for monitoring and controlling the machines of its victims.
In separate news, Ukraine Police announced today the arrest of another member of Cobalt group in Kiev, for developing malware and selling personal data from citizens worldwide.
The suspect was working with Cobalt group since 2016 and also involved in cyber-espionage activities. He allegedly sold a variety of malicious software in underground markets that allows anyone to access and control victims' computers remotely.
"This global operation is a significant success for international police cooperation against a top-level cybercriminal organisation. The arrest of the key figure in this crime group illustrates that cybercriminals can no longer hide behind perceived international anonymity," said Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3).
"This is another example where the close cooperation between law enforcement agencies on a worldwide scale and trusted private sector partners is having a major impact on top-level cyber criminality."
Intel CPUs Vulnerable to New 'BranchScope' Attack
28.3.2018 securityweek Attack
Researchers have discovered a new side-channel attack method that can be launched against devices with Intel processors, and the patches released in response to the Spectre and Meltdown vulnerabilities might not prevent these types of attacks.
The new attack, dubbed BranchScope, has been identified and demonstrated by a team of researchers from the College of William & Mary, University of California Riverside, Carnegie Mellon University in Qatar, and Binghamton University.
Similar to Meltdown and Spectre, BranchScope can be exploited by an attacker to obtain potentially sensitive information they normally would not be able to access directly. The attacker needs to have access to the targeted system and they must be able to execute arbitrary code.
Researchers believe the requirements for such an attack are realistic, making it a serious threat to modern computers, “on par with other side-channel attacks.” The BranchScope attack has been demonstrated on devices with three types of Intel i5 and i7 CPUs based on Skylake, Haswell and Sandy Bridge microarchitectures.
Experts showed that the attack works even if the targeted application is running inside of an Intel SGX enclave. Intel SGX, or Software Guard Extensions, is a hardware-based isolated execution system designed to prevent code and data from getting leaked or modified.
BranchScope is similar to Spectre as they both target the directional branch predictors. Branch prediction units (BPUs) are used to improve the performance of pipelined processors by guessing the execution path of branch instructions. The problem is that when two processes are executed on the same physical CPU core, they share a BPU, potentially allowing a malicious process to manipulate the direction of a branch instruction executed by the targeted application.
The BPU has two main components – a branch target buffer (BTB) and a directional predictor – and manipulating either one of them can be used to obtain potentially sensitive data from the memory. Intel recently published a video providing a high level explanation of how these attacks work.
Researchers showed on several occasions in the past how BTB manipulation can be used for attacks, but BranchScope involves manipulation of branch predictors.
“BranchScope is the first fine-grained attack on the directional branch predictor, expanding our understanding of the side channel vulnerability of the branch prediction unit,” the researchers explained in their paper.
The researchers who identified the BranchScope attack method have proposed a series of countermeasures that include both software- and hardware-based solutions.
Dmitry Evtyushkin, one of the people involved in this research, told SecurityWeek that while they have not been tested, the microcode updates released by Intel in response to Meltdown and Spectre might only fix the BTB vector, which means BranchScope attacks could still be possible. However, Intel told the researchers that software guidance for mitigating Spectre Variant 1 could be effective against BranchScope attacks as well.
“We have been working with these researchers and we have determined the method they describe is similar to previously known side channel exploits,” Intel said in an emailed statement. “We anticipate that existing software mitigations for previously known side channel exploits, such as the use of side channel resistant cryptography, will be similarly effective against the method described in this paper. We believe close partnership with the research community is one of the best ways to protect customers and their data, and we are appreciative of the work from these researchers.”
BranchScope is not the only CPU side-channel attack method uncovered following the disclosure of Meltdown and Spectre. One of them, dubbed SgxPectre, shows how Spectre can be leveraged to defeat SGX.
Researchers have also demonstrated new variants of the Meltdown and Spectre attacks, which they have named MeltdownPrime and SpectrePrime.
*Updated with statement from Intel