Russian financial cybercrime: how it works
19.11.2015 Zdroj: Kaspersky
The Russian-language cybercrime market is known all over the world. By ‘Russian-language market’ we mean cybercriminals who are citizens of the Russian Federation and some former USSR countries, predominantly Ukraine and the Baltic states. Why is this market known worldwide? There are two main factors: the first of these is frequent global media coverage of the activity of Russian-language cybercriminals. The second is the open accessibility of online platforms used by the cybercriminal community for communications, promoting a variety of “services” and “products” and discussing their quality and methods of application, if not for making actual deals.
Over time, the range of “products” and “services” available through this underground market has evolved, becoming more focused on financial attacks, and with an ever-increasing level of sophistication. One of the most common types of cybercrime was (and still is) the turnover of stolen payment card data. With the emergence of online stores and other services involving e-payment transactions, DDoS-attacks and financial cybercrime have become especially popular with the fraudsters whose main targets are users’ payment data or the theft of money directly from user accounts or companies.
Attacks on users’ and companies’ e-wallets were initiated by the Trojan ibank in 2006; then came ZeuS (2007) and SpyEye (2009) followed by the groups Carberp (2010) and Carbanak (2013). And this list is incomplete; there are more Trojans out there, used by criminals to steal users’ money and data.
With online financial transactions becoming more common, the organizations supporting such operations are becoming more attractive to cybercriminals. Over the last few years, cybercriminals have been increasingly attacking not just the customers of banks and online stores, but the enabling banks and payments systems directly. The story of the Carbanak cybergroup which specializes in attacking banks and was exposed earlier this year by Kaspersky Lab is a clear confirmation of this trend.
Kaspersky Lab experts have been monitoring the Russian hacker underground since it first emerged. Kaspersky Lab regularly issues reports on financial cyber-threats which track changes in the number of financial malware attacks carried out over time. Information on the number of attacks may indicate the extent of the problem but does not reveal anything about who creates them and how. We hope that our review will help to shed light on this aspect of financial cybercrime.
Between 2012-15, law enforcement agencies arrested over 160 Russian-speaking cybercriminals
Tweet
The data presented in this article is compiled from dozens of investigations that Kaspersky Lab experts have participated in over the last few years, as well as their many years’ experience observing the Russian cybercrime market.
Situation overview
According to Kaspersky Lab, between 2012 and 2015, law enforcement agencies from a number of different countries, including the United States, Russia, Belarus, Ukraine and the EU arrested over 160 Russian-speaking cybercriminals who were members of small, medium-sized and large criminal groups. They were all suspected of being engaged in stealing money using malware. The total damage resulting from their worldwide activity exceeded $790 million dollars. (This estimate is based both on the analysis of public information about the arrests of people suspected of committing financial cybercrime in the period between 2012 and 2015 and on Kaspersky Lab’s own data.) Of this sum, about $509 million dollars was stolen outside the borders of the former USSR. Of course, this figure only includes confirmed losses, the details of which were obtained by law enforcement authorities during the investigation. In reality, cybercriminals could have stolen a much larger amount.
The number of arrests of Russian-speaking cybercriminals as officially announced during the period 2012 to 2015
Since 2013, Kaspersky Lab’s Computer Incidents Investigation team has participated in the investigation of more than 330 cybersecurity incidents. More than 95% of these were connected with the theft of money or financial information.
Although the number of arrests of Russian-language criminals suspected of financial cybercrime increased significantly in 2015 compared with the previous year, the cybercriminal market is still “crowded.” According to Kaspersky Lab experts, over the last three years Russian-language cybercrime has recruited up to a thousand people. These include people involved in the creation of infrastructure, and writing and distributing malware code to steal money, as well as those who either stole or cashed the stolen money. Most of those arrested are still not in prison.
We can calculate fairly precisely the number of people who make up the core structure of an active criminal group: the organizers, the money flow managers involved in withdrawing money from compromised accounts and the professional hackers. Across the cybercriminal underground, there are only around 20 of these core professionals. They are regular visitors of underground forums, and Kaspersky Lab experts have collected a considerable amount of information that suggests that these 20 people play leading roles in criminal activities that involve the online theft of money and information.
The exact number of groups operating across Russia and its neighboring countries is unknown: many of those involved in criminal activities participate in several thefts and then, for various reasons cease their activity. Some participants of known but apparently disbanded groups continue their criminal activities as part of new groups.
Kaspersky Lab’s Computer Incidents Investigation Department can now confirm the activity of at least five major cybercriminal groups specializing in financial crimes. These are the groups whose activities have been monitored by the company’s experts over the last few years.
All five groups came to the attention of the company’s experts in 2012-2013, and are still active. They each number between ten and 40 people. At least two of them are actively attacking targets not only in Russia but also in the USA, the UK, Australia, France, Italy and Germany.
There are ~20 of people, who make up the core structure of an active criminal group
Tweet
Since the investigation into these groups has not been completed, it is not possible to publish more detailed information on the activities of these groups. Kaspersky Lab continues to investigate their activity and is cooperating with the law enforcement agencies of Russia and other countries in order to curb their cybercriminal business.
Investigation into the activities of these groups has allowed Kaspersky Lab experts to form an idea about their methods of operation and the structure of the cybercriminal market.
The structure of the Russian-language cybercriminal market
“A Range of products and services”
The cybercriminal market usually comprises a set of “services” and “products”, used for various illegal actions in cyberspace. These “products” and “services” are offered to users of dedicated online communities, most of which are closed to outsiders.
The “products” include:
Software designed to gain unauthorized access to a computer or a mobile device, in order to steal data from an infected device or money from a victim’s account (the Trojans);
Software designed to take advantage of vulnerabilities in the software installed on a victim’s computer (exploits);
Databases of stolen credit card data and other valuable information;
Internet traffic (a certain number of visits to a customer-selected site by users with a specific profile.)
The “services” include:
Spam distribution;
Organization of DDoS attacks (overloading sites with requests in order to make them unavailable to legitimate users);
Testing malware for antivirus detection;
“Packing” of malware (changing malicious software with the help of special software (packers) so that it is not detected by antivirus software);
Renting out exploit packs;
Renting out dedicated servers;
VPN (providing anonymous access to web resources, protection of the data exchange);
Renting out abuse-resistant hosting (hosting that does not respond to complaints about malicious content, and therefore does not disable the server);
Renting out botnets;
Evaluation of the stolen credit card data;
Services to validate the data (fake calls, fake document scans);
Promotion of malicious and advertising sites in search results (Black SEO);
Mediation of transactions for the acquisition of “products” and “services”;
Withdrawal of money and cashing.
Payments for such “products” and “services” on the cybercriminal market are generally made via an e-payment system such as WebMoney, Perfect Money, Bitcoin and others.
All of these “products” and “services” are bought and sold in various combinations in order to enable four main types of crime. These types can also be combined in various ways depending on the criminal group:
DDoS attacks (ordered or carried out for the purpose of extortion);
Theft of personal information and data to access e-money (for the purpose of resale or money theft);
Theft of money from the accounts of banks or other organizations;
Domestic or corporate espionage;
Blocking access to data on the infected computer for the purpose of extortion;
According to Kaspersky Lab experts, the theft of money is currently the most widespread type of crime. The rest of this report therefore focuses on this segment of the Russian-language cybercrime market.
The “labor market” of financial cybercrime
The variety of skills required for the creation of “products” and the provision of “services” has given rise to a unique labor market of professionals involved in financial cybercrime.
The list of key roles is almost exactly the same as that seen in any IT-related company:
Programmers / encoders / virus writers (for the creation of new malicious software and modification of existing malware);
Web designers (for the creation of phishing pages, emails, etc.);
System administrators (for the construction and support of the IT infrastructure);
Testers (to test the malicious software);
“Cryptors” (responsible for the packing of malicious code to bypass antivirus detection).
The list does not include the heads of the criminal groups, the money flow managers engaged in withdrawing money from compromised accounts, and the heads of money mules supervising the process of cashing the stolen money. This is because the relationship between these elements of the criminal groups is not an employer-employee one, but more of a partnership.
Depending on the type and extent of the criminal enterprise, the heads of the groups either employ “staff” and pay them a fixed salary or work with them on a freelance basis paying for a particular project.
An offer of employment posted on a semi-closed forum inviting a programmer to join a cybercriminal group. The job requirements include experience in writing complex bots.
“Employees” are recruited either via sites where those involved in criminal activity traditionally gather or via resources for those interested in non-standard ways of making money online. In some cases, the ads are placed on mainstream job search sites or on the labor exchanges for remote employees.
We can confirm the activity of at least 5 major cybercriminal groups specializing in financial crimes
Tweet
In general, employees involved in cybercrime can be divided into two types: those who are aware of the illegality of the project or the work they are offered, and those who (at least in the beginning) know nothing about it. In the latter case, these are usually people performing relatively simple operations such as copying the interface of banking systems and sites.
By advertising “real” job vacancies, cybercriminals often expect to find employees from the remote regions of Russia and neighboring countries (mostly Ukraine) where problems with employment opportunities and salaries for IT specialists are quite severe.
A fraudster has advertised a job vacancy for java / flash specialists on a popular Ukrainian website. The job requirements include a good level of programming skills in Java, Flash, knowledge of JVM / AVM specifications, and others. The organizer offers remote work and full employment with a salary of $2,500.
The idea of searching for “employees” in these regions is simple – they carry a saving because staff can be paid less than employees based in large cities. Criminals also often give preference to candidates who have not previously been involved in cybercrime activity.
Often, such job offers are presented as legitimate work, with the true purpose of the work only becoming clear once the task is received.
In this example, the organizer of the criminal group offers a job to a javascript programmer, masking it under a vacancy at a “Web-innovation studio specializing in the development of highly sophisticated Internet applications.”
In the case of illegal job search sites, less-experienced candidates are expected.
This vacancy invites a C ++ developer to develop “custom” software. In this context “custom” software means malicious software.
The second reason in favor of remote “personnel” is the organizer’s aim of making the activity of the group as anonymous as possible, and to ensure that no single contractor possesses complete information about the group.
Options for organizing a criminal group
Criminal groups involved in stealing money or financial information that will enable them to get access to money, differ in the number of participants and scope of activities. There are three main types of involvement:
Affiliate programs
Single dealers, small and middle-sized groups (up to ten members)
Large organized groups (ten or more participants)
This division is nominal. The scale of the group’s activity depends on the skillfulness of its participants, their ambition and the overall level of organizational abilities. In some cases, Kaspersky Lab experts came across relatively small criminal groups performing tasks that usually require a greater number of participants.
Affiliate programs
Affiliate programs are the easiest and least expensive method of getting involved in cybercrime activities. The idea behind an affiliate program is that the organizers provide their “affiliates” with almost all the tools they need to commit a crime. The task of the “affiliates” is to generate as many successful malware infections as possible. In return, the owner or owners of the affiliate program share the income received as a result of these infections with the affiliates. Depending on the type of fraudulent scheme this could be a share of:
The sums stolen from the accounts of Internet banking users;
The money paid by the user as a ransom when cybercriminals use ransomware Trojans;
The money stolen from the “prepaid” accounts of mobile device users by sending out SMS messages to premium mobile numbers with the help of a malicious program.
Creating and supporting an affiliate program for the purpose of stealing money is a cybercrime committed, as a rule, by a group of users. However, such projects are often carried out by large organized groups whose activity is analyzed later in this document.
This advertisement announces the launch of the beta testing of an affiliate program used to distribute encrypting ransomware. Judging by its characteristics, the group’s activity is focused on companies located in the US and the UK. This is indicated by the comment saying that the malware distributed via the partner network is able to encrypt files with 80 different extensions, many of which are files of applications used in companies. The text on requirements for candidates to participate in testing includes a demonstration of the presence of traffic or downloads from the United States and the United Kingdom.
According to Kaspersky Lab experts, affiliate programs are becoming less popular with Russian-language cybercriminals. The main driver of their popularity had been fraudulent schemes used to infect users’ mobile devices with malicious programs which then sent out SMS messages to premium numbers. However, in the spring of 2014, the Russian regulator introduced new requirements for the organization of such services, which included a need to secure additional confirmation of subscription to a particular paid mobile service. This change was instrumental in reducing the number of malicious mobile partner programs to practically zero. Nevertheless, this type of joint cybercriminal activity is still used by groups specializing in the distribution of encrypting ransomware.
Small Groups
What distinguishes this form of cybercriminal activity from an affiliate program is that in this instance the criminal or criminals organize their own fraudulent scheme. Most of the components needed for the attack, such as malware and its modifications (“re-packed” malware), the traffic, the servers, etc., are bought on the black market. Often, members of such groups are not experts in the field of computer and network technologies; they learn about the components and organization of financial attacks from public sources, usually forums. The abilities of such groups can be restricted by a number of factors. Specifically, the use of widely-available malware results in rapid detection by security solutions. This, in turn, makes cybercriminals invest more money in the distribution of malware and in its “re-packing” to bypass detection. The end result is a significant drop in profits for the attacker.
Mistakes made by this type of cybercriminal often result in their identification and arrest. However, as a relatively low cost entry into the world of cybercriminal activity (from $ 200), this “amateur” format continues to attract new dealers.
An example of such an “amateur” criminal organization is the group that in 2012 was convicted by the Russian court for stealing more than 13 million rubles (then worth about $422,000) from a Russian bank’s online customers. During a comprehensive investigation Kaspersky Lab experts were able to collect the information that allowed law enforcement authorities to identify those behind the theft.
The court sentenced two members of the criminal group, giving each a suspended sentence of four and a half years. However, this verdict did not stop the criminals, and they continued to commit crimes, stealing almost as much again over the next two and a half years. They were re-arrested in May 2015.
Large organized criminal groups
Large criminal groups differ from the other players, both through a larger scale of activity and through a more thorough approach to the organization and operation of criminal schemes. Such groups can comprise up to several dozen people (not including money mules used for cashing and “laundering” money.) The targets of their attacks are not limited to individual online banking customers: they also attack small and medium-sized companies, while the largest and most sophisticated of them, such as Carbanak focus mostly on banks and e-payment systems.
The operational structure of large groups differs significantly from smaller groups. To a certain extent, the structure reflects that of an ordinary, average-sized company engaged in software development.
In particular, large groups have some form of regular staff – a group of associates who perform organizational tasks in return for a regular, fixed payment. However, even in these large, professional groups some of the tasks are passed to third-party contractors. For example, the “re-packing” of malware can be performed by the staff or hired virus writers or via third-party services where the process is automated with the help of special software. The same is true for many other elements of the IT infrastructure required for committing crime.
Examples of large, organized criminal groups are Carberp, whose members were arrested in Russia and Ukraine in 2012 and 2013 respectively, and Carbanak, unmasked by Kaspersky Lab in early 2015.
Although the damage from the activity of partner programs and small groups can run into hundreds of thousands of dollars, the large criminal groups are the most dangerous and destructive. The estimated damage caused by Carberp reaches several hundred million dollars (up to a billion). In this regard, studying how these groups function and the tactics they use is extremely important, as it strengthens our ability to effectively investigate their activity and – ultimately – to suppress it.
Distribution of roles in a large cybercriminal group
A major financial cybercrime undertaken by criminal “experts” in security and the finance sector can result in multi-million dollar losses for attacked organizations. As a rule, such crimes are preceded by many months of preparation. This preparation includes constructing complex infrastructure, and selecting and developing malicious software, as well as a thorough study of the target organization in order to clarify the details of its internal operations and security vulnerabilities. Each member of the criminal group has their own responsibilities.
The following role distribution is typical for a criminal group involved in stealing money. The distribution of roles in groups that specialize in other types of cybercrime may be different.
Virus writer/Programmer
A virus writer or programmer is responsible for creating malicious programs, i.e. the programs that allow the attackers to gain a foothold in the corporate network of the target organization, download additional malware that will help to obtain the necessary information, and ultimately steal money.
The significance of this group member and the nature of their relationship with the organizers may vary from group to group. For example, if the group uses ready-made malware taken from open sources or bought from other virus writers, their functions may be limited to setting and modifying malicious programs to work in the infrastructure created specifically for a certain cybercrime, or to adapt it for attacks on specific institutions. The most advanced groups, however, tend to rely on their own “developments” since it makes a malicious program less visible to most security solutions and provides more opportunities for malware modification. Where this is the case, the virus writer’s role becomes more important as they are responsible for the architecture and feature set of a malicious program.
A virus writer can also take on responsibility for malware “re-packing”. But this happens only when the organizer wants to keep the maximum number of tasks within the group, and where original software is used for malware “re-packing”. In most cases, however, this procedure is shifted to third-party contractors or packing-services.
Testers
The function of testers in a criminal group is not that different from testers working in legal IT companies. In both cases, testers receive from their managers the specifications for testing programs in different environments (different versions of operating systems, different sets of installed applications, etc.) and execute them. If a fraudulent scheme involves fake interfaces of remote banking or e-payment systems, the task of testers also includes monitoring the correct operation of these fakes.
Web designers and Web programmers
Typically, web designers and web programmers are remote employees, whose tasks include creating phishing pages and websites, fake application interfaces and web injects, all of which are used to steal data to get access to e-payment and e-banking system.
Distributors
Distributors aim to ensure the download of malicious software on as many devices as possible. The result is achieved by using several tools. Generally, the group organizer determines the profile of the users to be infected and buys the required type of traffic from the so-called traffic providers (services to attract users with certain characteristics to a particular website).
An advert offering to buy traffic. Cybercriminals are willing to pay only for the successful installation of malicious software at $ 140 per 1000 “call-backs” (a message that is sent by the malware to the command server after a successful infection).
The organizer can choose and order a spam mailing that will contain either an infected attached file or a link taking a victim to a malicious website. The organizers can also choose the site with the necessary target audience; involve hackers in breaking into it and placing the exploit pack on it. Of course, all these tools can be used in combination with each other.
Hackers
Often, in the course of an attack, the exploits and other malicious software the organizer has to hand is not enough to infect all the computers necessary for the attack and to anchor in them. It may become necessary to hack into a specific computer or site. In such cases, the organizers involve hackers, people who have considerable skills in information security and are able to perform non-standard tasks. In many of the cases examined by Kaspersky Lab experts, hackers were occasionally involved and were paid on a fee-for-service basis. However, if hacking is required regularly (e.g., for targeted attacks on financial institutions), a hacker becomes a “team member” and is often one of the cybercriminal group’s key participants, along with the organizers and money flow managers.
System administrators
System administrators in cybercriminal groups perform near-identical tasks to their counterparts in legitimate businesses: they implement the IT infrastructure and maintain it in working condition. Cybercriminal system administrators configure management servers, buy abuse-resistant hostings for servers, ensure the availability of tools for anonymous connection to the servers (VPN) and resolve other technical challenges, including the interaction with remote system administrators hired to perform small tasks.
Call services
Social engineering is important for the success of the cybercriminal business. Especially when it comes to attacks on organizations that result in the theft of huge sums of money. In most cases, even if the attackers are able to establish control over the computer from which the transaction could be performed, confirmation of its legitimacy is required to successfully complete the operation. This is what the “call service” is for. At the specified time, its “employees” play the role of an employee of the attacked organization or a bank with which the organization works, and confirm the legitimacy of the transaction.
“Call services” can participate in a particular cybercrime both as a subdivision of the criminal group, or as a third-party organization, performing a specific task on a fee-for-service basis. The forums that users involved in cybercrime use to communicate with each carry plenty of ads offering such services.
This advertisement offers “call services” in English, German, Dutch and French. The group specializes in calls to Internet stores and banks, as well to duped mules. Also, the group offers the quick creation of local toll-free numbers used to imitate support services in fraudulent schemes, receiving SMS messages, and receiving and sending faxes. The criminals ask from $10 to $12 for one call, $ 10 for receiving SMS and from $ 15 for creating toll-free numbers.
According to Kaspersky Lab, large cybercriminal groups prefer to have their own “call services” so they hardly ever turn to third-party providers.
Money flow managers
Money flow managers are members of the cybercriminal group who come into play when all the technical tasks for organizing the attack (choosing and infecting the target and anchoring in its infrastructure) are fulfilled, and everything is ready to commit the theft. Money flow managers are the people who withdraw money from compromised accounts. However, their participation is not limited to pressing the keys; they play a key role in the whole process.
The list of key roles in financial cyber gangs almost mirrors IT-companies
Tweet
Money flow managers usually thoroughly understand the internal rules of the attacked organization (they even know the lunch hours of the employee from whose computer the fraudulent transaction will be made). They know how the automated anti-fraud systems operate and how to bypass them. In other words, in addition to their criminal role of thieves, money flow managers perform “expert” tasks that are difficult or impossible to automate. Perhaps because of this special status, money flow managers are one of the few members of the criminal group who receive a percentage of the stolen money rather than a fixed “salary”.
Money flow managers often perform as botnet operators. i.e. members of the criminal group who analyze and classify the information obtained from infected computers (the access to the remote banking services, availability of money on the accounts which could be accessed, the organization where the infected computer is located, etc.).
Besides money loaders, these “working conditions” are only shared by the leaders of mule projects.
Head of Mules (Mule “project” leader)
Head of mules is a representative of the criminal group working closely with the people involved in the process of stealing money. The function of the mules is to get the stolen money, cash it and transfer to the criminal group its due share. To do this, the head of mules builds their own infrastructure, which consists of legal entities and individuals with their own bank accounts, to which the stolen money is transferred and from which it is later withdrawn and moved into the pockets of the fraudsters. The mule project leader cooperates with the organizer of the criminal group, and provides them with the numbers of the accounts to which the money loader sends the stolen money. Both mule project leaders and money flow managers work on commission which, according to the information obtained by Kaspersky Lab during the course of investigation, can amount to half the sum stolen.
Mule “projects”
Mule projects are a vital component of any financial cybercrime. Such groups comprise one or more organizers and up to several dozen individual mules.
A mule (or drop) is a holder of a means of payment who, on command from the money mules manager, cashes the money received into their/an account, or transfers it to another account as specified by the money mules manager.
Mules can be divided into two types: duped and non-duped. Duped mules are people who, at least at the beginning of their cooperation with the money mules manager, do not realize they are involved in a criminal scheme. As a rule, the task of getting and transferring money is presented to them under some plausible pretext. For example, the money mules manager can establish a legal entity and appoint to an executive position (the general or financial director, for example) a person who will perform the functions of the duped mule: such as signing corporate documents which will, in fact serve as a legal screen for withdrawing stolen money.
Non-duped mules are well aware of the real purpose of the money mules manager’s tasks.
The options used by the mule projects to withdraw money are manifold. Depending on the amount of money stolen, they may include individual credit card holders ready to cash money and give it to the representative of the money mules manager for a small fee, or specially created legal entities, whose representatives open “salary projects” (credit cards for transferring the salaries of company employees) at their corporate bank.
Yet another common method for constructing a mule scheme is for non-duped mules to open dozens of accounts at different banks.
This advert offers sets of payment cards (the card, the documents based on which the card was authorized, the SIM card with which the bank account of the card is associated) that can be used for cashing stolen money. For sale is the card issued by Russian banks and banks from neighboring countries, as well as banks from the countries of Europe, Asia and the United States. The Momentum-type set is costs 3000 rubles (less than $50), the set with the Platinum card – eight thousand rubles (about $120).
When the theft occurs outside of Russia, the role of the non-duped mules is performed by a citizen or group of citizens of an Eastern Europe country, who within a short period of time visit several countries on the continent and in each of them open accounts in their names. Then the non-dupe mules provide the money mules manager with the data to access all these accounts. These accounts are used later to withdraw the stolen money.
An example of an ad offering for sale a list of companies registered in the Russian Federation and in the offshore zone. The services of cybercriminals cost from $560 to $750.
Stuffers
The word “stuffer” comes from the word “stuff” (a colloquial word for “goods”). One way to withdraw stolen money is by buying goods in e-stores with the stolen money, reselling them and returning to the fraudsters their due percent. This is done by the stuffers, members of the cybercriminal groups engaged in spending money from compromised accounts on purchasing goods in online stores.
In fact, a stuffer is a variation of the money flow manager. Withdrawing money by purchasing goods is generally practiced if the stolen sums are relatively small. As a rule, the stuffers work in a team with the fences. Working “in tandem” often involves purchasing a certain type of goods, sometimes from a specific manufacturer or a clearly-defined model.
Organizer
If we consider cybercrime as a project, the organizer of the criminal group is its general manager. Their duties usually include financing the preparatory phase of the attack, allocating tasks to executors, monitoring their performance and interacting with third-party agents such as mule projects and call services (if the group does not have its own). The organizer determines the targets for attacks, selects the necessary “specialists” and negotiates with them.
Stages of the attacks
It should be noted that the above classifications are not set in stone. In some cases, a single member of the criminal group can combine several roles. Nevertheless, regardless of how many people execute them, each of the roles described can be found when investigating almost every money-related cybercriminal incident. Here’s how they work in “real time.”
Exploration. When it comes to targeted attacks on a specific company, the organizer first instructs the contractors to collect information about the company, which will help to develop a plausible social engineering scheme for the first stage of attack. If we are talking about an attack on individual users, the preliminary exploration stage is skipped or limited to choosing a “target audience” for the attack (for example, the users of the online banking service of a specific bank) and creating phishing emails and phishing sites with relevant content.
Infection. Penetration of the corporate network is performed by spear-phishing or a phishing mass-mailing that contains an attachment with the special document or a malicious web-link. Opening the attachment or following the link leads to malware infection. Often, infection occurs automatically without the user’s awareness or participation – after clicking on the link, a malicious program is automatically downloaded on the user’s computer (drive-by download) and runs on it.
In other cases, infection is carried out via compromised popular sites on which a tool is placed that invisibly redirects users to a third-party site containing a set of exploits. Once on this site, the user will be infected with malware.
Once inside the system cybercriminals use a number of malicious tools to consolidate their presence. For example, to ensure that internal sites of compromised organizations have the malware reinstalled when the organization’s security software deletes the previous version. In addition, attackers are often set up within the infrastructure software of the attacked organization, enabling easy access to the internal corporate network from outside.
Exploration and implementation. The programs for remote, hidden administration and management are downloaded onto compromised computers. They are used by cybercriminals to gain system administrators’ credentials. Legal programs for remote management and administration whose functionality is known to many users are often used for this.
Money theft. In the final stage, cybercriminals access the financial systems of the targeted organization and transfer money from its accounts to the accounts of the mule projects or withdraw money directly at ATMs.
Conclusion
Financial cybercrime backed by Russian-speaking criminals has become widespread in recent years and this growth is due to a number of causes. The main ones are:
Not enough qualified staff in law enforcement agencies;
Inadequate legislation allowing criminals in many cases to avoid responsibility or to receive a lighter sentence;
A lack of established procedures for international cooperation between law enforcement agencies and expert organizations in different countries.
Unlike the real world, a robbery in cyberspace usually goes unnoticed and there is a very small window for collecting digital evidence after the crime. Further, criminals have no need to stay in the country where the crime is committed.
Unfortunately, for Russian-speaking cybercriminals current conditions are more than favorable: the risk of prosecution is low while the potential rewards are high. As a result, the number of crimes and the damage caused by them is growing, and the market for cybercriminal services is increasing momentum.
A relatively low cost of entry ($ 200) to cybercrime attracts new dealers
Tweet
The lack of established mechanisms for international cooperation also plays into the hands of criminals: for example, Kaspersky Lab experts know that the members of some criminal groups permanently reside and work in Russia’s neighbors, while the citizens of the neighboring states involved in criminal activity often live and operate in the territory of the Russian Federation.
Kaspersky Lab is doing everything possible to terminate the activity of cybercriminal groups and encourages other companies and law enforcement agencies in all countries to cooperate.
The international investigation of Carbanak’s activity, initiated by Kaspersky Lab, is the first example of successful international cooperation. If the world is to see a serious and positive change there should be more such cases.
Reference. What is Kaspersky Lab Computer Incidents Investigation?
Kaspersky Lab is a well-known developer of anti-malware security solutions. But the company provides comprehensive protection, and this also includes services for computer incidents investigation.
Evidence of an incident, mainly presented in the form of digital data, needs to be collected and recorded so that there are no grounds for doubt in the investigation and trial when a victim makes a court application.
Kaspersky Lab Computer Incidents Investigation is responsible for:
Responding to IT security incidents and providing a quick analysis of the situation;
Collecting digital evidence and determining the circumstances of IT security incidents in accordance with established procedures;
Analyzing the evidence collected, searching the information related to the circumstances of the incident on the Internet and fixing them;
Preparing materials for the victim’s application to law enforcement agencies;
Providing expert support to investigative operations.
A huge amount of data is processed when responding to IT security incidents and supporting investigative operations. The analysis of this data, in combination with statistics on malicious objects detected identifies the trends of criminal behavior in cyberspace.
The Kaspersky Lab Computer Incidents Investigation Department was established in 2011 and involves six forensic experts.
New Dyre variant in the wild supports Windows 10 and Microsoft Edge
19.11.2015
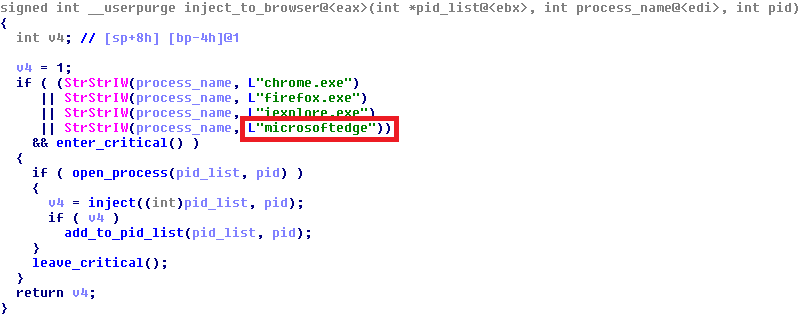
The developers of the Dyre banking Trojan have released a new version of the malware that includes support for Windows 10 and Microsoft Edge.
The security firms Heimdal Security and F5 Networks have uncovered a new version of the Dyre (Dyreza) banking Trojan that includes support for Windows 10 and Microsoft Edge.
The new variant of Dyre now also targets Chrome, Firefox and Internet Explorer, and it is able to hook its code into the process of Microsoft Edge.
According to the Heimdal Security more than 80.000 machines are already infected with Dyre Trojan across the world.
The experts at F5 who analyzed the new Dyre Trojan have discovered that the authors have renamed some of the existing commands and have implemented new functionalities.
Below the list of new commands added to the new variant of the malware:
0xF1”lli” – Get the botid name
srvv – Get the C&C IP
dpsr – Get the data POST server IP
grop – Get the botnet name
seli – Get the self-IP
gcrc – Get the fake pages configuration
gcrp – Get the server-side webinjects configuration
pngd – Get the account information stolen by the pony module
sexe – Among other jobs, it copies the droppee path and its content both to Dyre’s special structure and the configuration file on disk. It also tries to get the anti-antivirus module from the C&C.
gsxe – Get the droppee path
The new commands are used to get the IP of the command and control (C&C) server, the botnet name, configuration for fake pages, configuration for server-side webinjects, account information stolen by the Pony module, and an anti-antivirus module.
The Dyte include a module specifically designed to locate security products installed on the infected machine and disable them, this module is named “aa32” on Windows 32-bit versions and “aa64” on 64-bit versions. The module is injected into the “spoolsv.exe” process and it is able to neutralize the principal antivirus software, including solutions designed by Avira, AVG, Malwarebytes, Fortinet, Trend Micro and also the Windows Defender service.
To make the malware more difficult to analyze, the authors of the last version have encrypted hardcoded debug strings and only decrypt them during runtime.
Previous versions of Dyre gain persistence by using a Run key in the registry, but the last one used a scheduled task that is run every minute.
“We conclude from the addition of these features that the authors of the malware strive to improve their resilience against anti-viruses, even at the cost of being more conspicuous,” is reported in the blog post published by F5. “They also wish to keep the malware up-to-date with current OS releases in order to be ‘compatible’ with as many victims as possible. There is little doubt that the frequent updating will continue, as the wicked require very little rest.”
Experts believe that the new variant of Dyre is spreading in the wild to monetize the coming holiday season.
“The timing of this new strain is just right: the season for Thanksgiving, Black Friday and Christmas shopping is ready to start, so financial malware will be set to collect a huge amount of financial data. Users will be busy, prone to multitasking and likely to choose convenience over safety online,” Heimdal Security noted.
Telegram — Secret Messaging app — Shuts Down 78 ISIS Channels
19.11.2015
The terrorist groups affiliated with the Islamic State have an extensive presence not only on social media accounts but also on the popular end-to-end encrypted messaging app Telegram through which they communicate with their followers and spread terror propaganda materials.
Telegram has always been terrorist's favorite, but ISIS had been using the app since October, when Telegram introduced an end-to-end encrypted Secret Chat feature that lets users broadcast messages to an unlimited number of subscribers.
Moreover, Telegram also provides self-destructing message feature that allows users to set their messages to self-destruct itself after a certain period of time.
But, the Good News is:
The nonprofit organization that runs Telegram has blocked around 78 ISIS-affiliated channels that the terrorists used to:
Communicate with their members
Spread propaganda
Recruit foreign supporters
Plan operations
Radicalize young people
"We were disturbed to learn that Telegram's public channels were being used by ISIS to spread their propaganda," Telegram writes. "As a result, this week alone we blocked 78 ISIS-related channels across 12 languages."
In the wake of the horrific Paris terrorist attacks, the Telegram creators said they are carefully reviewing all user-submitted reports sent to them and are taking appropriate action to block such channels that are used to spread terror-related contents.
Telegram — Secret Messaging app
Islamic State (ISIS) — Terror Has gone Social
Just after Anonymous declared war against ISIS, the militants started encouraging its members and followers to use Telegram secure instant messaging app, so that they can effectively make their conversations invisible from Government spies.
We also reported that ISIS issued some basic Internet safety tips to its followers via one of its Channel on Telegram, teaching terrorists how to avoid being caught or hacked by Anonymous.
No doubt, ISIS is leveraging the power of Social media to spread its message around the globe and deleting just 78 ISIS-affiliated Telegram Channels and 5,500 Twitter accounts won't stop them.
According to our analyses, there are still more than 100 other ISIS Telegram channels and thousands of Twitter and Facebook accounts affiliated with ISIS and each followed by thousands of Jihadists.
How to Report ISIS-related Abusive and Illegal Activities
Telegram — Secret Messaging app
So, if you come across any terror-related messages and want to contribute to preventing the terrorists from spreading their roots via social media platform, you can file your reports to the respective social media.
Is Telegram Really Secure? — 4 Major Privacy Issues Raised by Researcher
19.11.2015
The terrorist groups are encouraging its followers to use Telegram to make their propaganda invisible from law enforcement, but some security experts believe that Telegram may not be as secure as jihadi advocates may like to believe.
Telegram is an end-to-end encrypted messaging service that has been adopted by a lot more people than ISIS — as of last year, the company claimed more than 50 Million Telegram users sending 1 Billion messages per day.
Terrorists love Telegram because it not only provides an encrypted Secret Chat feature that lets its users broadcast messages to unlimited subscribers but also offers self-destructing message allowing users to set their messages to self-destruct itself after a certain period.
Is Telegram Really Secure?
In a blog post published Wednesday, the security researcher known as "the Grugq" pointed out several issues with Telegram that might obstruct terrorists from using it.
Here's the list of issues with Telegram:
1. Error prone
Telegram's end-to-end encrypted chat feature is not enabled by default. One has to select Secret Chat before start chatting, and it is not possible to encrypt an existing conversation.
Also Read: Anonymous Hackers Release Hacking Guide to Help Defeat ISIS Online Propaganda
2. Contact Theft
Telegram requires you to register a working phone number and uploads the entire Contacts database to its servers, helping it create a trail of breadcrumbs for law enforcement and investigators to follow.
"This allows Telegram to build a huge social network map of all its users and how they know each other," the Grugq wrote in his blog post.
3. Leak Voluminous Metadata
The use of a mobile phone can expose a wide range of metadata. Even if secure chat is enabled, law enforcement can collect other Metadata for sure by compromising the servers.
This could help them track down who talked to whom, at what time, from which location, which will be an enough information for agencies seeking for possible suspects.
For Example: If A and B are communicating with each other on encrypted channel, and A is on the suspect list of agencies, then they can at least figure out the connection between both using this Metadata.
Also Read: ISIS Called Anonymous "IDIOTS" and Issued Lame Tips to Avoid Getting Hacked
4. Wonky Homebrew Encryption
Some security experts are also worried about the encryption that Telegram uses, although its encryption hasn't been publicly broken.
Telegram has announced a contest to crack the app's encryption with a prize money of $300,000, but nobody claimed it.
However, when it comes to nation-state adversary, one wouldn't trust encryption protection in Telegram, as the app might work for the average user, but is not secure enough for terrorists.
Whatever be the privacy concerns regarding Telegram, the good news is:
Telegram has blocked 78 ISIS-affiliated Channels that the terrorist used to communicate with their members, spread propaganda and plan operations.
Blackhole Exploit Kit Resurfaces in the wild
19.11.2015
The experts at Malwarebytes have noticed that threat actors in the wild are reusing the Blackhole Exploit Kit despite its limited effectiveness.
The Blackhole exploit kit has reappeared in the wild surprising the security industry after that in October 2013 its author, know as Paunch, was arrested. Paunch was the author of two of the most popular exploit kits, Blackhole and the Cool Exploit Kit, that dominated the underground scene in recent years.
The Blackhole exploit kit was widely used to hack into several Web browsers and exploit flaws in popular software such as Adobe Reader. The winning factors for the success of Blackhole exploit kit were its efficiency, the availability of various models for sale (e.g. I was available for sale and rent in the underground market), availability of frequent updates and an affordable price (Blackhole was offered for rent as little as $200 to $300 per week).
The experts at Malwarebytes have noticed that threat actors in the wild are reusing the exploits despite their limited effectiveness. Malwarebytes observed the new variant of the BlackHole Exploit kit includes old PDF and Java exploits.
“The new drive-by download attacks we caught over the weekend rely on the same structure as the original Blackhole, even reusing the old PDF and Java exploits. The only difference is the malware payload being dropped, which is current and had very low detection on VirusTotal.” reports MalwareBytes.
The source code of the Blackhole was leaked online four years ago allowing cybercriminals to reuse it and add new features to the core modules. The numerous hacking communities could offer their variant of the Blackhole exploit kit that implements fresh exploits for vulnerabilities recently discovered.
Fortunately, the researchers at Malwarebytes have discovered that threat actors behind the new Blackhole campaign left the server that hosted the control infrastructure open on the Internet, a circumstance that allowed the expert to access it.
“The server used to host the exploit infrastructure happens to be fully browsable (thanks @MeJz024 for the tip). The folder structure shows with no doubt this is taken straight from the Blackhole source code that had been leaked.” reads the blog post.
The intent of the attacker is to try to compromise the numerous computer still vulnerable on the Internet, but the experts highlight the infection rate would be quite low due to the aging exploits
“Although the exploits are old, there are probably still vulnerable computers out there who could get compromised,” Segura wrote. “We are not quite sure why this old exploit kit is being used in live attacks considering the infection rate would be quite low due to the aging exploits.” said Jerome Segura, a senior security researcher for Malwarebytes.
MalwareBytes also published the Indicators of compromise on its website.
Telegram messaging service tries to ban ISIS, but..
19.11.2015
Telegram messaging service announced its actions against the abuses made by members of the ISIS, but it still allows communications in private groups.
In the wake of recent Paris attacks the experts increased their investigation on the communication channels used by members of the ISIS organization.
A few hours after the Paris attacks, investigators speculated terrorists were using the voice over IP implemented by the Play Station, but the unique certainly in this moment is that the terrorist organization is using the popular Telegram messaging service for its communications and to spread propaganda.
The terrorists are using the “Channels” feature implemented in the Telegram messaging service that allow users to subscribe to broadcast content published through a permanent URL. The feature allows publishers to reach a wide audience, the publishers can share messages, files, and images in an anonymous way both using a mobile device or PC.
Now the nonprofit organization running the Telegram messaging service announced that it is operating to ban the activities of terrorists. The organization has already identified several channels used by the ISIS and blocked them in response of abuse reports filed by Telegram users.
“We were disturbed to learn that Telegram’s public channels were being used by ISIS to spread their propaganda,” a Telegram spokesperson posted in the service’s Telegram News channel. “We are carefully reviewing all reports sent to us at abuse@telegram.org and are taking appropriate action to block such channels. As a result, this week alone we blocked 78 ISIS-related channels across 12 languages.”
Telegram messaging service
Telegram can block channels and also “sticker set” images, another feature abused to spread images through automated “bot” message applications.
strikers Telegram messaging service
Telegram clarifies that every time an abuse complaint is filed against public content, it checks the content alleged violated the publishing policy, then it evaluates to remove it:
“Please note that this does not apply to local restrictions on freedom of speech. For example, if criticizing the government is illegal in a country, Telegram won‘t be a part of such politically motivated censorship. This goes against our founders’ principles.”
“While we do block terrorist (e.g. ISIS-related) bots and channels, we will not block anybody who peacefully expresses alternative opinions.” states Telegram.
Unfortunately, terrorists could still establish private connections, Telegram admitted that it is not able to block communications that happen in private groups, which can include up to 200 users.
“All Telegram chats and group chats are private amongst their participants,” Telegram’s spokesperson wrote. “We do not process any requests related to them.”
This is a bad news because it means that group of ISIS members can still use the Telegram messaging service to share propaganda materials, operational instructions, and other information, within private groups.
French activist accuses Anonymous #OpParis of hindering Law Enforcement
19.11.2015
The collective Anonymous launched the #OpParis to track terrorists online, but a French activist accuses them of hindering Law Enforcement.
Just days following the horrific Paris attacks carried out by the ISIS, Anonymous hackers wedged a full-fledged war against the Islamic radicals, knocking out several thousand pro-ISIS Twitter accounts. However, a French blogger has spoken out against the hacker collective’s recent actions under the #OpParis campaign, saying they are hindering law enforcement’s ability to monitor and keep up with ISIS.
In a recent video published by Anonymous, the collective waged war against ISIS, saying “You should know that we will find you and we will not let you go under #OpISIS.”
#OpParis
Olivier Laurelli, a French citizen and computer security blogger said Anonymous shutting down pro-ISIS accounts is a bad idea as it leaves authorities blind to tracking activities of pro-ISIS members.
“To close those accounts is to leave police deaf and blind around some matters. It is important to know that one account is in France, another in Syria or in Iraq and if you see that someone who is connected to the attacks has a link to someone else, it’s important for police. Twitter has been quick to close down a large number of accounts, but I don’t know if it’s a good idea,” Laurelli told to AFP.
According to the blogger, the collectives relentless work to unmask ISIS members is an embarrassment for the police as it’s their duty to monitor the accounts and see who is spreading pro-ISIS propaganda. It’s also their job to keep the accounts under control from rapid growth on social media, exactly what Anonymous is currently doing.
Laurelli claims that the information Anonymous is destroying as part the #OpParis would have allowed law enforcement to properly counter the Paris attacks, in which 129 people lost their lives and 415 got injured.
Anonymous has taken #OPISIS strongly to social media, trying to get everyone to work together and unmask ISIS members. However, Facebook wasn’t too fond of the idea and decided to block a few Anonymous groups on Facebook for revealing the identity of an alleged ISIS member.
Laurelli’s comments come just after Anonymous published a list of more than 9,000 pro-ISIS twitter accounts that were promptly removed by Twitter.
Disk image Microsoftu s Windows 10 umožní uživatelům přeskočit čekání na listopadový update
18.11.2015 Software
Microsoft zveřejnil odkazy disk image soubory ve formátu .iso, které obsahují první aktualizaci na Windows 10. Uživatelé tak již mají možnost nainstalovat si nejnovější verzi operačního systému, aniž by museli čekat, než společnost vydá oficiální kód přes Windows Update.
Díky disk image mohou uživatelé vytvářet instalační média jako flash disky nebo DVD pro jedno nebo hned několik zařízení současně. Díky nim pak mohou například přeinstalovat operační systém přes jeho narušenou kopii.
Soubory .iso, které mají v anglické verzi Windows velikosti 2,8 GB pro 32 bitovou verzi a 3,7 GB pro 64 bitovou verzi, se dají využít také k upgradu původní verze Windows 10 z července letošního roku.
Rady k upgradu systému prostřednictvím disk image dával Microsoft také nespokojeným uživatelům Windows 10 na svých diskuzních fórech. Některým se totiž nedařilo nainstalovat verzi Windows 10 1511 přes klasický Windows Update.
Nová verze Windows 10 nepůjde okamžitě na všechna zařízení fungující na letošním operačním systému. Microsoft bude verzi 1511 zveřejňovat postupně.
„Aktualizaci budeme vypouštět ve vlnách. Ta první začala již včera,“ potvrdil mluvčí Microsoftu.
Počkat si budou muset například ti, kteří na Windows 10 přešli v nedávné době z jeho předchozích generací.
„Pokud je to méně než 31 dní od vašeho upgradu na Windows 10, neobdržíte listopadovou aktualizaci okamžitě. Díky tomu budete mít možnost vrátit se na předchozí verzi Windows,“ píše Microsoft ve svém FAQ. „Po 31 dnech váš počítač stáhne a nainstaluje aktualizaci automaticky."
Upgrade, kterému Microsoftu vytrvale říká „Listopadový Update“, dostanou stálí uživatelé Windows 10 automaticky. Disk image s Windows 10 1511 se dají na stránkách Microsoftu stáhnout také ze zařízení se staršími generacemi Windows i z platforem využívajících Applovský OS X.
Analýza crypto-ransomware Linux.Encoder.1
18.11.2015 Viry
Šifrovaná data jako rukojmí? Obchodní model placení výkupného se už osvědčil i v elektronickém světě, a tak zřejmě budeme svědky jeho masivnějšího využívání – vzpomeňme na CryptoWall, CryptoLocker, CoinVault a řadu dalších. O premiéru pro OS Linux se postaral crypto-ransomware pojmenovaný Linux.Encoder.1.
Oběti crypto-ransomware Linux.Encoder.1 se našly i v České republice a některé z nich za dešifrování zaplatily – naše forenzní laboratoř dostala příležitost prozkoumat zakoupený dešifrovací balíček.
Linux.Encoder.1
Základní popis malware je uveden například na ArsTechnica nebo SecurityWeek. Po zneužití zranitelnosti v CMS Magento je spuštěn vlastní ransomware, který zašifruje soubory na disku a ve všech zašifrovaných adresářích zanechá textový soubor s instrukcemi.
Your personal files are encrypted! Encryption was produced using a unique
public key RSA-2048 generated for this computer.
To decrypt files you need to obtain the private key.
The single copy of the private key, which will allow to decrypt the files,
located on a secret server at the Internet. After that, nobody and never will
be able to restore files...
To obtain the private key and php script for this computer, which will
automatically decrypt files, you need to pay 1 bitcoin(s) (~420 USD).
Without this key, you will never be able to get your original files back.
______________________________________________
!!!!!!!!!!!!!!!!!!!!! PURSE FOR PAYMENT(ALSO AUTHORIZATION CODE):
XXXXXXXXXXfiSdX2h3EZFRDdCZOi27e6Tpp !!!!!!!!!!!!!!!!!!!!!
WEBSITE: https://XXXXXXXXXl6uze2.onion.to
INSTRUCTION FOR DECRYPT:
After you made payment, you should go to website
https://XXXXXXXXXl6uze2.onion.to
Use purse for payment as ur authorization code
(XXXXXXXXXXfiSdX2h3EZFRDdCZOi27e6Tpp).
If you already did the payment, you will see decryption pack available
for download, inside decryption pack - key and script for decryption,
so all what you need just upload and run that script ( for example:
http://http://magentodemo.AAAA.XXXX.cz/decrypt.php )
Also, at this website you can communicate with our supports and we can
help you if you have any troubles,
but hope you understand we will not answer at any messages if you not
able to pay.
!!!P.S. Our system is fully automatic, after payment you will receive
you're decrypt pack IMMEDIATELY!!!
...
Q: How to use decryption pack?
A: Put all files from archive to your server and just run decrpyt.php
(example: website.com/decrypt.php)
Aktuálně už je znám způsob,jak data dešifrovat bez zaplacení výkupného a existuje i nástroj pro dešifrování. V prvních dnech výskytu však tato možnost nebyla k dispozici a některé oběti raději zaplatily, aby se ke svým datům dostaly hned. V takovém případě, po zaplacení určené částky, autoři malware zašlou odkaz ke stažení dešifrovacího balíčku ze sítě Tor s instrukcemi, jak provést vlastní dešifrování.
Dešifrovací balíček
V doručeném archivu typu zip se nachází textový soubor s instrukcemi (readme.txt), dešifrovací klíč (key.pem) a dešifrovací skript (decrypt.php).
Decrypt.php
Při pohledu do skriptu decrypt.php je jeho činnost ihned zřejmá – detekuje použitou architekturu a podle toho vytvoří příslušný spustitelný soubor s názvem host. Vlastní kód pro tři podporované architektury je zakódován base64 a uložen uvnitř skriptu v proměnných $so32, $so64 a $so.
$so32 = {…}
$so64 = {...}
...
$arch = 64;
if (intval("9223372036854775807") == 2147483647)
{
$arch = 32;
echo "x64=0\n";
}
else echo "x64=1\n";
if ($freebsd == 0){
$so = $arch == 32 ? $so32 : $so64;
}
else {
$so = {…}
}
…
file_put_contents("./host", base64_decode($so))
…
Dále je vytvořen skript 1.sh a nastavena práva 777 pro soubory host a 1.sh. V dalším kroku je tento vytvořený skript spuštěn – jeho úkolem je spustit vytvořený soubor host s patřičnými parametry a poté smazat sám sebe:
./host decrypt key.pem /index.html
rm 1.sh
Soubor decrypt.php tedy poskytuje uživatelsky relativně přívětivý způsob spuštění dešifrovacího programu. Souvislosti výše zmiňovaných souborů jsou naznačeny na obrázku:
Host
Binární soubor host provádí vlastní dešifrování se zadaným dešifrovacím klíčem, a jak se při reverzní analýze ukázalo, stejný soubor je používán také k zašifrování souborů na disku. Zkrátka racionalizace – jeden soubor slouží pro dva účely. Pro nás jako analytiky je to ulehčení práce, protože je vidět, jak probíhá proces šifrování a co přesně je do zašifrovaného souboru ukládáno. Stejně potěšující je absence obfuskace a relativně smysluplné pojmenování používaných funkcí.
Reverzní analýzou bylo zjištěno, že jsou očekávány tři parametry příkazové řádky:
první parametr: řetězec „encrypt“ nebo „decrypt“ určující druh činnosti
druhý parametr: jméno souboru obsahující klíč (veřejný nebo soukromý) podle činnosti
třetí parametr: cesta k souboru „index.html“ v adresáři „www-document-root“
Validita parametrů není nijak kontrolována a program skončí ve chvíli, kdy se mu zadané parametry nepodaří správně použít.
Po spuštění proběhne inicializace generátoru náhodných čísel aktuálním časem (což se ve spojení se zahájením šifrování ve stejný okamžik ukázalo jako zásadní slabina, viz dále) a je funkcí LoadRSA() načten vhodný klíč asymetrické šifry – veřejný pro mód šifrování nebo soukromý pro mód dešifrování.
Poté se proces spustí v režimu daemon a veškerá další činnost tak probíhá na pozadí. Soubor host je v následném kroku smazán z pevného disku a je zahájeno vlastní (de)šifrování souborů na disku.
Veřejný i soukromý klíč pro RSA je programu host dodáván zvenčí. Z dostupných dat (dešifrovací balíček) nelze zjistit, jak jsou tyto klíče generovány, ale klíče jsou vygenerovány přímo na napadeném zařízení, přičemž veřejný klíč je používán během procesu šifrování, zatímco soukromý klíč je odeslán na CaC server. Oba klíče jsou následně ze zařízení odstraněny. Zpátky se pak soukromý klíč dostává až jako součást dešifrovacího balíčku, který si uživatel stáhne po zaplacení.
Průběh zašifrování dat
Nejprve je vhodné zmínit jak probíhá výběr vhodných adresářů a souborů k zašifrovaní. Klíčová funkce int encrypt_directory(char *directory) , která zajišťuje zašifrování zadaného adresáře je v pevném pořadí postupně spuštěna na adresáře
/home
/root
/var/lib/mysql
všechny domovské adresáře uvedené v /etc/passwd (získáváno pomocí standardní funkce getpwent())
/
V řadě případů k zašifrování nedojde kvůli absenci potřebných práv, protože zneužívaný CMS Magento zpravidla běží pod uživatelem www-data.
Součástí kódu je testování přítomnosti adresáře v „ignore listu“, který byl však v testovaném vzorku prázdný. Úplně vždy však budou šifrovány adresáře začínající řetezcem public_html, webapp nebo backup. Zřejmě jde o přípravu na další funkcionalitu nebo pozůstatek z jiného kódu. Zašifrovány by měly být také pouze soubory s následujícími příponami: php, html, tar, gz, sql, js, css, pdf, tgz, war, jar, java, class, ruby, rar, zip, db, 7z, doc, xls, properties, xml, jpg, jpeg, png, gif, mov, avi, wmv, mp3, mp4, wma, aac, wav, pem, pub, docx, apk, exe, dll, tpl, psd, asp, phtml, aspx, csv, public_html.
Vlastní zašifrování souboru je prováděno funkcí int encrypt_file(char *plain, char *encrypted) ,a to následujícím způsobem (viz obrázek):
Pro každý plain soubor je vytvořen nový soubor s příponou .encryptedpro uložení zašifrovaných dat.
Do tohoto souboru je nejprve uložena jeho vlastnostst_mod (přístupová práva nastavitelná příkazem chmod() ) (4 byty).
Poté je pro soubor vygenerován jedinečný AES-128 klíč a do nového souboru uložena jeho velikost v bytech (4 byty, prakticky vždy 0×00 01 00 00) a hned za ním samotný AES klíč zašifrovaný RSA klíčem (16 bytů).
Za zmínku stojí, že způsob generování AES klíče je velmi … nestandardní, protože je generován pouze jako 16 znakový řetězec sestávající z malých písmen a číslic a nevyužívá maximální možnou entropii.
Ukládání velikosti klíče, který je na mnoha místech hardcoded na 16B, ukazuje na využití jiného obecnějšího kódu.
Následně je vygenerován inicializační vektor pro AES a uložen do souboru (16B).
Pak už jsou z původního souboru postupně načítány 16B bloky, šifrovány pomocí AES a výsledky ukládány do výstupního souboru.
Za zmínku stojí opět ne příliš standardní implementace šifrování, kdy je používán stejný IV pro všechny bloky, místo aby byl použit výstup předchozího bloku.

Když už byly zmíněny slabiny v šifrovacím algoritmu, sluší se také doplnit, že inicializovat generátor pseudonáhodných čísel časem spuštění – což je fakticky i čas vytvoření prvního zašifrovaného souboru – opravdu nebyl dobrý nápad. Výzkumníci BitDefenderu tuto vlastnost využilia připravili nástroj pro dešifrování dat, který vygeneruje stejnou posloupnost pseudonáhodných čísel a tedy je schopen vytvořit stejné AES klíče. Pro dešifrování souborů je však potřeba mít úplně všechny zašifrované soubory s nezměněnými časovými značkami – jinak nástroj nebude moci zistit čas spuštění, správně incializovat generátor a zopakovat generování klíčů ve správném pořadí.
Pro zjištění všech přítomných souborů, které analyzovaný malware zašifroval, je potřeba hledat soubory s příponou .encrypted, které obsahují 00 01 00 00 na offsetu 4–7. Například příkazem
find / -name "*.encrypted" -exec sh -c "hexdump -n 8 {} | grep -qE '0100 0000\s*
Původní soubory jsou po dokončení jejich zašifrování smazány pomocí funce unwind(), takže existuje nenulová pravděpodobnost, že se smazané soubory dají obnovit forenzní analýzou napadeného disku. Volný prostor však mezitím mohl být přepsán, nebo – pokud se jedná o SSD disk a OS s podporou TRIM – mohla být data smazána garbage collectorem disku.
V každém adresáři, který byl zpracován šifrovacím algoritmem, je vytvořen soubor README_FOR_DECRYPT.txt, obsahující instrukce k dešifrování.
Průběh dešifrování
Spuštění programu s parametrem „decrypt“ provede dešifrování, přičemž jednotlivé kroky téměř přesně kopírují šifrovací postup. Opět jsou procházeny všechny výše zmíněné adresáře a volány funkce int decrypt_all(char *directory) a int decrypt_file(char *encrypted, char *plain).
Na všechny nalezené a dostupné soubory s příponou .encrypted je aplikováno dešifrování.
Je vytvořen nový soubor – jméno odpovídá zašifrovanému souboru s odstraněním přípony .encrypted.
Do nového souboru je dešifrován obsah zašifrovaného souboru.
Zašifrovaný soubor je smazán.
Nově vytvořenému souboru jsou nastavena práva skupin pomocí funkce chmod() .
Všechny nalezené soubory s názvem README_FOR_DECRYPT.txt jsou smazány. Prakticky je tak obnoven původní stav před spuštěním ransomware, s jedinou výjimkou – přiřazení vlastníka a skupiny.
Shrnutí
Analýzou „dešifrovacího balíčku“ zakoupeného obětí crypto-ransomware Linux.Encryptor.1 bylo zjištěno, jakým způsobem jsou soubory (de)šifrovány, které adresáře a soubory jsou v centru pozornosti a jak jednoduše identifikovat zašifrované soubory.
Každý soubor je zašifrován s použitím symetrické šifry AES-128, přičemž příslušný klíč je jedinečný pro každý soubor a je v tomto souboru uložen v zašifrované podobě (s použitím asymetrické šifry RSA2048) spolu s inicializačním vektorem a nastavením přístupových práv. Klíče asymetrické šifry jsou společné pro všechny soubory v daném zařízení.
V analyzovaném kódu je vidět řada přípravných prací na používání šifrovacích klíčů obecné délky, ale ve většině případů je velikost 16 bytů zadána napevno. Také jsou přítomny funkce pro whitelisting a blacklisting adresářů určených k zašifrování, ale v analyzovaném vzorku nejsou využívány.
Získání zašifrovaných souborů je možné i bez zaplacení výkupného, díky predikovatelnosti použitých náhodných čísel při generování AES klíčů a známých inicializačních vektorů. Predikovatelnost je umožněna použitím aktuálního času jako seed pro funci srand() , která inicializuje generátor pseudonáhodných čísel, přičemž hodnota použitého aktuálního času je známa – jde o čas vytvoření prvního zašifrovaného souboru. I bez této chyby by pravděpodobně část souborů bylo možné obnovit, protože původní soubory nebyly přepsány šifrovaným obsahem, ale smazány standardní cestou.
Po zaplacení výkupného se z oběti stává vážený zákazník a tvůrci ransomware myslí na jeho pohodlí – dešifrování probíhá způsobem zaplať-stáhni-spusť-enjoy. Také dešifrovací algoritmus se snaží zrušit všechny změny, které provedl, což se mu kromě přiřazení původního vlastníka a skupiny i daří. Zřejmě i ve vyděračském průmyslu je potřeba mít spokojené zákazníky, kteří se rádi vracejí…
Hey ISIS! Check Out How 'Idiot' Anonymous Hackers Can Disrupt your Online Propaganda
18.11.2015
The online Hacktivist group Anonymous declared War against the Islamic State militant group (ISIS) that claimed responsibility for the horrific terrorist attacks that rocked Paris last week.
In response to the Anonymous’ warning of launching their "biggest operation ever" against the terrorist group, ISIS militants called Anonymous – "IDIOTS".
It seems like Anonymous has taken ISIS response very seriously and the group has started carrying out their attacks against the terror organisation.
Anonymous First 'Cyber Attack' on ISIS
Soon after its war declaration, Anonymous claimed to have taken down more than 5,500 pro-ISIS Twitter accounts in #OpParis (Operation Paris).
In the past, hackers and organizations associated with Anonymous brought down websites allegedly connected with ISIS and claimed to have taken down thousands of ISIS accounts, disrupting their social media recruitment efforts.
Also Read: Would Encryption Backdoor Stop Paris-like Terror Attacks?
Anonymous' most famous targets include the white supremacist group Ku Klux Klan (KKK), the Vatican, the Westboro Baptist Church (known for its hate speech against the Jews, LGBT community, and liberal politicians), the governments, and even the CIA.
How Anonymous Can Disrupt ISIS's Online Propaganda
So, calling Anonymous idiots doesn’t make them idiots, because the hacktivist group has proved itself to be fully capable of launching successful attacks – and ISIS knows it.
That's why the terror organisation is spreading lame instructions through its affiliated official channels on Telegram on how to prevent getting hacked by Anonymous.
ISIS Online Propaganda: How They Manipulates Social Media
ISIS is a terrorist organisation whose most interesting aspect is how it leverages the huge power of Twitter and Facebook to radicalize young people, spread its message around the globe, recruit foreign supporters to its fight and shock people into taking notice of its actions.
Also Read: ISIS Issues 5 Lame Tips for its Members to Avoid Getting Hacked
Many ISIS militants maintain extremely active accounts on the popular social media platforms. They also have a strong presence on the most popular encrypted messaging app Telegram with more than 100,000 followers.
According to The Atlantic, there were more than 46,000 ISIS-affiliated Twitter accounts with an average of 1,000 followers each.
The group has also established a 24-hour Jihadi Help Desk to help its foot soldiers spread their message around the world, recruit followers and launch more terror attacks on foreign soil, NBC reports.
So How Anonymous can Defeat ISIS?
When taking into consideration ISIS's extensive presence on Twitter, taking down its social media presence is the actual key to defeating the terror group, and it does make an impact at worst.
So, taking down the group's 5,500 Twitter accounts could be the first step towards disrupting ISIS online propaganda.
No doubt, we doesn't have any silver bullet solution to this problem, neither cyber attacks can vanish ISIS from its roots, but at least hackers can disrupt their online propaganda that may disable them to plan or plot Paris-like terrorist attacks.
Also Read: We Can't Blame Edward Snowden and Encryption for Terror Attacks
Besides social media takeovers, the hacker collective is using "Distributed Denial of Service" (DDoS) attacks to shut down websites affiliated with ISIS, including its fundraising sites from where ISIS get fed.
Anonymous has previously used successful DDOS attacks to shut down services of companies or organizations the group deems fit for the attack, including the municipal computer system of Ferguson, Missouri in the wake of Michael Brown death.
Anonymous Releases Newbie "How-to" Hacking Guide
Now, this will really panic ISIS:
How Anonymous Can Disrupt ISIS's Online Propaganda
Anonymous group has also released a newbie How-to Hacking Guide for all wannabe hackers, in an effort to recruit more people in their Fight against Islamic State.
The Instruction set includes:
NoobGuide — Methods to hack websites associated with Islamic State
Reporter — How to set up a Twitter bot for uncovering IS accounts.
Searcher — How to identify and take down ISIS related websites and social media accounts
"Instead of sitting idle in the channel or lurking around and doing nothing, you can benefit greatly from the different tools and guides that have been provided to you. Your contribution means a lot and we encourage you to partake in all of the Op's activities if you can, the more the merrier," an anonymous member wrote.
It seems like, Anonymous is silently saying to ISIS… Just wait and watch what these idiots can do to you.
Kaspersky Security Bulletin. 2016 Predictions
18.11.2015 Zdroj: Kaspersky
It's the end of the world for APTs as we know it
As the year comes to an end, we have an opportunity to take stock of how the industry has evolved and to cast our predictions for the coming years. Taking advantage of a rare global meeting of our GReAT and Anti-Malware Research experts, we tossed ideas into the ring and I have the privilege of selecting some of the more noteworthy and plausible for both the coming year and the long-term future as we foresee it. The outlook for our rapidly evolving field of study is quite thought-provoking and will continue to present us with interesting challenges. By sticking to sober metrics, perhaps we can skip the usual science fiction fear mongering and come to some accurate predictions for both the short- and long-term.
No more APTs
Before you start celebrating, we should point out that we’re referring to the ‘Advanced’ and ‘Persistent’ elements – both of which the threat actors would gladly drop for overall stealth. We expect to see a decrease in the emphasis on persistence, placing a greater focus on memory-resident or fileless malware. The idea will be to reduce the traces left on an infected system and thus avoid detection altogether. Another approach will be to reduce the emphasis on advanced malware. Rather than investing in bootkits, rootkits, and custom malware that gets burned by research teams, we expect an increase in the repurposing of off-the-shelf malware. Not only does this mean that the malware platform isn’t burned upon discovery but it also has the added benefit of hiding the actor and his intentions in a larger crowd of mundane uses for a commercially available RAT. As the shine of cyber-capabilities wears off, return on investment will rule much of the decision-making of state-sponsored attackers – and nothing beats low initial investment for maximizing ROI.
APT: a decrease in the emphasis on persistence, a focus on memory-resident or fileless malware #KL2016Prediction
Tweet
The nightmare of ransomware continues
We expect to see the success of Ransomware spread to new frontiers. Ransomware has two advantages over traditional banking threats: direct monetization and relatively low cost per victim. This amounts to decreased interest from well-resourced third-parties such as banks, as well as low levels of reporting to law-enforcement agencies. Not only do we expect ransomware to gain ground on banking trojans but we also expect it to transition into other platforms. Weak attempts at bringing ransomware to mobile (Simplelocker) and Linux (Ransom.Linux.Cryptor, Trojan-Ransom.FreeBSD.Cryptor) have already been witnessed, but perhaps the more desirable target platform is OS X. We expect ransomware to cross the Rubicon to not only target Macs but also charge ‘Mac prices’. Then, in the longer term, there is the likelihood of IoT ransomware, begging the question, how much would you be willing to pay to regain access to your TV programming? Your fridge? Your car?
We expect ransomware to gain ground on banking trojans and to transition into other platforms #KL2016Prediction
Tweet
Betting against the house: financial crimes at the highest level
The merging of cybercrime and APT has emboldened financially motivated criminals who have gracefully transitioned from attacking end users to going after the financial institutions themselves. The past year has seen plenty of examples of attacks on point-of-sale systems and ATMs, not to mention the daring Carbanak heist that pilfered hundreds of millions of dollars. In the same vein, we expect cybercriminals to set their sights on novelties like alternate payment systems (ApplePay and AndroidPay) whose increasing rate of adoption should offer a new means of immediate monetization. Another inevitable point of interest is stock exchanges, the true mother lode. While frontal attacks may yield quick payoffs, we mustn’t overlook the possibility of more subtle means of interference, such as going after the black-box algorithms employed in high-frequency trading to ensure prolonged gains with a lower likelihood of getting caught.
Cybercriminals will set sights on novelties like alternate payment systems and stock exchanges #KL2016Prediction
Tweet
Attacks on security vendors
As attacks on security vendors rise, we foresee an interesting vector in compromising industry-standard reverse-engineering tools like IDA and Hiew, debugging tools like OllyDbg and WinDbg, or virtualization tools like the VMware suite and VirtualBox. CVE-2014-8485, a vulnerability in the Linux implementation of ‘strings’, presents an example of the vulnerable landscape of nontrivial security research tools that determined attackers may choose to exploit when targeting researchers themselves. In a similar vein, the sharing of freeware research tools through code repositories like Github is an area ripe for abuse, as users will more often than not pull code and execute it on their systems without so much as a glance. Perhaps we should also be casting a suspicious glance towards popular implementations of PGP so eagerly embraced by the infosec community.
We foresee a vector in compromising reverse-engineering, debugging & virtualization tools #KL2016Prediction
Tweet
Sabotage, extortion and shame
From dumps of celebrity nudes to the Sony and Ashley Madison hacks and the HackingTeam dump, there has been an undeniable increase in DOXing, public shaming, and extortion. Hacktivists, criminals, and state-sponsored attackers alike have embraced the strategic dumping of private pictures, information, customer lists, and code to shame their targets. While some of these attacks are strategically targeted, some are also the product of opportunism, taking advantage of poor cybersecurity to feign hacker prowess. Sadly, we can only expect this practice to continue to rise exponentially.
Whom do you trust?
Perhaps the scarcest commodity in the current internet age is trust. Abuse of trusted resources will further drive this scarcity. Attackers will continue to enlist open-source libraries and whitelisted resources for malicious purposes. We expect another form of trust to be abused, that of a company’s internal resources: as crafty attackers seek to expand their foothold on an infected network, they may target resources limited to the company intranet such as waterholing Sharepoint, file server, or ADP portals. Perhaps we’ll even witness the furthest extension of the already rampant abuse of trusted certificates as attackers establish an entirely fabricated certificate authority to issue certificates for their malware.
Attackers will enlist open-source libraries and whitelisted resources for malicious purposes #KL2016Prediction
Tweet
APT actors down the road
The profitability of cyberespionage has not escaped the attention of our foes and, as we expected, mercenaries have begun populating the scene. This trend will only increase to match the demand for cyber-capabilities by both companies as well as known APT actors looking to outsource less critical tasking without risking their tools and infrastructure. We could float the term ‘APT-as-a-Service’, but perhaps more interestingly we can expect the evolution of targeted attacks to yield ‘Access-as-a-Service’. The latter entails the sale of access to high-profile targets that have already fallen victim to mercenaries.
We'll see members of well-established APT teams potentially coming out of the shadows #KL2016Prediction
Tweet
Looking further into the future of cyberespionage, we see members of well-established APT teams (‘APT 1%ers’, if you will) potentially coming out of the shadows. This would happen in one of two forms: as part of the private sector with the proliferation of ‘hacking back’, or by sharing their insights with the larger infosec community, perhaps by joining us at conferences to share the other side of the story. In the meantime, we can expect the APT Tower of Babel to incorporate a few more languages.
The future of the Internet
The infrastructure of the internet itself has shown signs of tension and cracks in recent years. Concerns over massive router botnets, BGP hijacking and dampening, DNS attacks en masse, or server-powered DDoSes betray a lack of accountability and enforcement on a global scale. Looking further down the line to long-term predictions, we can consider what the internet might look like if that narrative of a globally connected village continues to wither. We may end up with a balkanized internet divided by national borders. At that point, concerns over availability may come down to attacks on the service junctures that provide access between different sections, or perhaps geopolitical tensions that target the cables that connect large swathes of the internet. Perhaps we’ll even see the rise of a black market for connectivity. Similarly, we can expect that as technologies that power the internet’s underbelly continue to gain mainstream attention and widespread adoption, developers with a stake in shadow markets, exchanges, and forums are likely to develop better technologies to keep the underground truly underground.
The internet's cracked: we may end up with a balkanized internet divided by national borders #KL2016Prediction
Tweet
The future of transportation
As investment and high-end research capabilities are dedicated to developing autonomous vehicles for both personal and commercial distribution, we will witness the rise of distributed systems to manage the routes and traffic of large volumes of these vehicles. The attacks may not focus on the distribution systems themselves, but perhaps on the interception and spoofing of the protocols they rely on (a proof of concept of the vulnerabilities of the widely adopted Global Star satcom system was presented by a Synack researcher at this year’s BlackHat conference). Foreseeable intentions behind these attacks include theft of high-value goods or kinetic damage resulting in loss of life.
Crypto: a breakdown in the reliability of standards and a need of 'post-quantum cryptography' #KL2016Prediction
Tweet
The cryptopocalypse is nigh
Finally, we cannot overemphasize the importance of cryptographic standards in maintaining the functional value of the internet as an information-sharing and transactional tool of unparalleled promise. These cryptographic standards rely on the expectation that the computational power required to break their encrypted output is simply above and beyond our combined means as a species. But what happens when we take a paradigmatic leap in computational capabilities as promised by future breakthroughs in quantum computing? Though quantum capabilities will not be initially available to the common cybercriminal, it signals a breakdown in the reliability of current crypto-standards and a need to design and implement ‘post-quantum cryptography’. Given the poor rate of adoption or proper implementation of high-quality cryptography as it is, we do not foresee a smooth transition to counterbalance cryptographic failures at scale.
Spam and phishing in Q3 2015
18.11.2015 Zdroj: Kaspersky
MALICIOUS SPAM MALWARE MALWARE DESCRIPTIONS PHISHING SPAM LETTERS SPAM REPORT SPAM STATISTICS SPAMMER TECHNIQUES TEMATIC SPAM
Download PDF version
Spam: features of the quarter
Online dating
The dating theme is typical for spam emails, but in the third quarter of 2015 we couldn’t help but notice the sheer variety appearing in these types of mailings. We came across some rather interesting attempts to deceive recipients and to bypass filters, as well as new types of spam mailings that were bordering on fraud.
The main aim of spammers exploiting the dating theme is usually to advertise recently created dating sites that are still relatively unknown. The owners of these sites resort to spamming to attract the largest possible audience to their resource. The messages often address different categories of recipients, for example, dating sites for older people, married people or the religious.
Yet another type of advert is for marriage agencies offering a selection of brides (mainly from Russia and Ukraine) to foreign suitors. This type of spam is usually distributed in the English-language segment of the Internet. The messages contain an invitation to register on a site, a short text promising to find the perfect life partner and a link leading to the advertised site.
Q3 2015, the percentage of spam in email traffic accounted for 54.2% #KLReport #infosec
Tweet
Similar emails can also be sent from a “bride”. This type of spam is closer to the fraudulent tactics used by ‘Nigerian letters’. The email is supposedly written by a girl who provides a few details about herself, about how hard her life is in the Russian hinterland, and her dreams of meeting Prince Charming. A photo is often attached, though not necessarily a photo of the “bride” – it could easily be taken from someone’s social networking page and attached to make the message look more convincing. That’s why emails from different girls may contain the same photos. However, the messages vary: a host of synonyms are used to bypass spam filters. The usual channel for receiving feedback is via email. The address is different for each email – they are obviously created in large quantities on free email services for each mass mailing. After replying, the user will, at best, receive a notification that the address is non-existent. The worst case scenarios will see his address targeted by further spam mailings and he may even get caught up in a scam where the girl asks for money to buy a ticket to come and see him. Once she gets the money, she disappears without a trace.
A similar method is used to advertise dating sites “for adults”. The emails contain either an invitation to register on the site and a promise of intimate dating, or a message from a girl who is looking for a partner for intimate relations plus a link to the resource with her alleged profile. This type of spam is often disguised as personal notifications on social networking sites, as well as image or audio files sent via instant messengers. As a result, the site is hidden, and the user cannot clearly identify what it is until he follows all the links. Of course, the contents of these messages aim to arouse the recipient’s interest and make him click the links, often due to the flirty content or heavy hints and intimate photos.
And finally, yet another type of spam we detected in Q3 was quite blatantly fraudulent. During the quarter we observed a mass mailing that prompted recipients to send a text message to a specific telephone number; in return a girl promised to send intimate photos of herself. The text of the emails varied, as did the mobile numbers specified in them. We sent messages to some of the numbers and found that they were not premium-rate numbers as might be expected, and users were not charged for sending a text message. We got a reply from a girl, but after a couple of answers it became clear we were dealing with a robot whose task was to make us download an application so we could continue chatting and receive the promised photos. As a result, we received several text messages containing short links that led to an article about useful mobile apps that appeared in a well-known American newspaper. During the redirect to the article an archive with mobile malware was downloaded to the user’s phone.
Seasonal malicious spam
The amount of seasonal spam traditionally increases in summer. This is true for both advertising and malicious spam. The holiday season saw spam with a travel theme: fake notifications from booking services, airlines and hotels were used to spread malicious programs.
Fake notifications from major international airlines and booking services were detected by Kaspersky Lab as Trojan-Downloader.JS.Agent.hhy and Trojan-Downloader.Win32.Upatre.
We came across similar emails supposedly sent by popular airlines that had messages in French. The text informed recipients that the attachment contained an e-ticket. In fact, the ZIP archive contained Trojan.Win32.Xtrat Trojan and the DDoS bot Nitol (the module used to organize DDoS attacks).
In July, fraudsters tried to trick users by sending fake notifications on behalf of hotels. The message thanked the recipients for staying in their hotel and asked them to view the attached bill. The attached archive actually contained Trojan-Downloader.Win32.Upatre.dhwi, which in turn downloaded and ran Trojan- Banker.Win32.Dyre (viewed as 98. ***. **. 39/cv17.rar) by clicking the links written in the body of the downloader.
In addition to fake emails sent on behalf of well-known companies we observed a message in English from an individual. The email contained a request to change a room booking because some friends had cancelled.
The text in the email could easily be seen as a legitimate request from a client; however, the ZIP attachment contained Trojan-Downloader.JS.Agent.hhi that downloaded Backdoor.Win32.Androm.
Spammer tricks
The text in a standard phishing email is usually in the body of the message, while personal information is entered on a web page that opens after clicking a fraudulent link in the text, or in the HTML fields of a page attached to the email, or is sent back in a reply email. The latter is most typical when asking recipients to confirm the address and the password for an email account.
Q3 2015, Top 3 biggest sources of spam globally were the #USA, #Vietnam & #China #KLReport
Tweet
In Q3 2015, cybercriminals came up with a new way of distributing phishing emails and bypassing spam filters. The text of the phishing email and the fake link were included in a PDF document attached to the email. After clicking the link, a standard phishing page opened and the user was asked to enter his personal information. The majority of emails utilizing the new technique imitated bank notifications. The body of these messages usually contained a short text describing the problem; sometimes there was no text at all.
It should be noted that the spammers used well-known phrases and tricks in the text of the emails: notifications about an account being blocked, the need to pass a verification procedure, security issues, an investigation into phishing incidents, etc. As usual, the fraudulent links were masked by legitimate links and text fragments.
However, there were emails with detailed text in the message body providing genuine links to official bank resources. The phishing notification was included in the PDF attachment.
Our colleagues also came across a different type of phishing message using Mediabox objects in attached PDF files.
A Mediabox object is a document opened by a mouse click and used to redirect the user to a phishing website.
Statistics
Proportion of spam in email traffic
Percentage of spam in email traffic, April-September 2015
After some relatively stable months in the second quarter the percentage of spam in global email traffic began to change again. A slight growth in July and August of 2015 was followed by a noticeable drop in September. As a result, the average percentage of spam in Q3 amounted to 54.19% – slightly higher than the average for the previous quarter.
Sources of spam by country, Q3 2015
The US (15.34%) remained the biggest source of spam in Q3. Vietnam was second with 8.42% of global spam, compared to 3.38% in the previous quarter. China rounded off the Top 3 (7.15%) – its share remained unchanged from the previous quarter.
Russia’s share (5.79%) dropped by 2.03 p.p., pushing it from second to fourth position. It was followed by Germany (4.39%) and France (3.32%) – their shares changed only slightly compared to Q2.
 Spam email size distribution, Q2 2015 and Q3 2015
Spam email size distribution, Q2 2015 and Q3 2015
The most commonly distributed emails were very small – up to 2 KB (79.05%). The proportion of these emails grew from the previous quarter (13.67 p.p.), while the share of emails sized 20-50 KB (3.32%) fell by approximately the same number of percentage points. The share of all other emails saw no significant change from Q2 of 2015.
Top 10 malicious programs sent by email, Q3 2015
Trojan-Spy.HTML.Fraud.gen remained the most popular malicious program sent by email. This program is a fake HTML page sent via email that imitates an important notification from a large commercial bank, online store, or software developer, etc.
Second and ninth places in the Top 10 are occupied by Trojan-Downloader.JS.Agent.hhi and Trojan-Downloader.JS.Agent.hfq, respectively. Both are an obfuscated Java-script. The downloaders use ADODB.Stream technology that allows them to download and run DLL, EXE and PDF files.
Trojan-Downloader.VBS.Small.lj and Trojan-Downloader.VBS.Agent.aqp came third and sixth, respectively. These VBS scripts, which also use the ADODB.Stream technology, download ZIP archives and run malware extracted from them.
Q3 2015, Upatre was the most common malware family sent by email #KLReport
Tweet
Trojan-Downloader.MSWord.Agent.oq came fourth. This malicious program is a DOC file with embedded VBS macros that run when the document is opened. The macros download another malicious VBS script from the cybercriminals’ site and run it on the victim’s computer.
Email-Worm.Win32.Mydoom.l rounds off the Top 5. This network worm is spread as an email attachment via file-sharing services and writable network resources. It harvests email addresses from infected computers so they can be used for further mass mailings. The worm also enables attackers to remotely control the infected computer.
Trojan-Downloader.HTML.Meta.ay, Trojan-Downloader.HTML.Agent.aax and Trojan-Downloader.HTML.Meta.aq were seventh, eighth and tenth in the rating, respectively. They all are HTML pages which, when opened, redirect users to a rigged site. Once there, a victim usually encounters a phishing page or is asked to download a program – Binbot, a binary option trading bot. The three malicious programs spread via email attachments and the only difference between them is the link which redirects users to the rigged sites.
Malware families
As in the previous two quarters, Upatre (9.46%) was the most common malware family. Malware from this family downloads the Trojan banker known as Dyre, Dyreza, Dyzap.
The MSWord.Agent family (5.55%) remained in second position. To recap, these malicious programs are DOC files with an embedded macro written in Visual Basic for Applications (VBA), which runs on opening the document. It downloads and runs other malware, such as malicious programs from the Andromeda family.
In third place was the VBS.Agent (5.44%) family. Unlike MSWord.Agent, the malicious programs of this family use the embedded VBS script. To download and run other malware on the user’s computer they use the ADODB.Stream technology.
Distribution of email antivirus verdicts by country, Q3 2015
There were some significant changes in the Top 3 countries targeted most often by mailshots in Q3 2015. Russia’s appearance in third place (7.56%) was the biggest surprise: its share grew by 2.82 p.p., pushing it up two places from fifth.
Germany (18.47%) remained on top, although its contribution dropped by 1.12 p.p. compared to Q2. Brazil ended the quarter in second place (11.7%) – the amount of malicious spam originating from there almost doubled compared to Q2.
The UK (4.56%), which was second in Q2, ended Q3 in sixth place.
Special features of malicious spam
In spam traffic at the beginning of September we came across a large-scale malicious mass mailing containing emails imitating a non-delivery auto-reply sent by an email server. The text and subject of the message looked very similar to an automatic notification; however, the sender address belonged to an individual, which raised doubts about the legitimacy of the email. The attached ZIP archive named Google_drive_1711 was also suspicious because notifications from email services do not normally contain attachments. Closer inspection revealed that the archive included Trojan Trojan-Downloader.JS.Agent.hhi, which in turn downloaded Backdoor.Win32.Androm.
At the beginning of the third quarter cybercriminals were actively sending out emails in French containing macro viruses. The macros that we detected belonged to a category of Trojan downloaders and were used to download and install the banking Trojan Dridex on victim computers. To deceive the recipient, the fraudsters imitated a notification about the receipt of an order or an invoice.
In July, spammers exploited the theme of loans to spread malicious files that are now traditional for advertising spam. Some scammer emails offered a loan attracting potential customers with very favorable terms, low interest rates, etc. Other messages notified the recipient that his loan application had been approved. Interestingly, this content can also be seen in ordinary advertising spam, but malicious spam usually contains an attachment masquerading as detailed information about the loan.
Interestingly, malicious emails with Trojan-Downloader.Win32.Upatre in the attachment were sent to employees at different companies.
Phishing
In Q3 2015, the Anti-Phishing system was triggered 36,300,537 times on computers of Kaspersky Lab users, which is 6 million times more than the previous quarter. Of them, 15,764,588 attempts were blocked by our heuristic detection components and 20,535,949 by signature detection components. 839,672 phishing wildcards were added to the Kaspersky Lab databases.
The country where the largest percentage of users is affected by phishing attacks was once again Brazil (21.7%). In Q3 2015, the share of those attacked increased by 11.33 p.p., meaning Brazil returned to the same sort of figures last seen in Q1.
Geography of phishing attacks*, Q3 2015
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in the country
The percentage of attacked users in Japan and China also grew considerably (+10.9 p.p. and +7.85 p.p., respectively), which saw these countries ranked second and third in the rating.
Top 10 countries by percentage of users attacked:
Country % of users
1 Brazil 21.07
2 Japan 16.86
3 China 15.08
4 Vietnam 14.5
5 Bangladesh 13.32
6 Nigeria 13.05
7 Russia 12.91
8 Kazakhstan 12.85
9 India 12.44
10 Columbia 12.25
Organizations under attack
The statistics on phishing targets is based on detections of Kaspersky Lab’s anti-phishing component. It is activated every time a user enters a phishing page while information about it is not included in Kaspersky Lab databases. It does not matter how the user enters this page – by clicking the link contained in a phishing email or in the message in a social network or, for example, as a result of malware activity. After the activation of the security system, the user sees a banner in the browser warning about a potential threat.
In the third quarter of 2015, the ‘Global Internet portals’ category (30.93%) topped the rating of organizations attacked by phishers although its share decreased by 11.42 p.p. from the previous quarter. The share of ‘Social networking sites’ (21.44%) increased by 6.69 p.p. In third place came ‘Banks’ with 18.07% (+4.65 p.p.). The ‘Online games’ category also increased by half and accounted for 4.02%.
Distribution of organizations affected by phishing attacks, by category, Q3 2015
The proportion of phishing attacks on organizations in the ‘Cloud data storage’ category increased by 0.26 p.p. and amounted to 1.06%. Users are increasingly using cloud storage technology, thus attracting the attention of cybercriminals. The stolen information is used for blackmail, sold to third parties or used in targeted attacks.
This type of phishing is often distributed via email or social networks in the form of a message inviting users to download a document allegedly uploaded to a popular cloud service. Messages can arrive from a compromised account from a user’s friend list or, in the case of email, on behalf of a cloud service administrator.
Q3 2015, Anti-Phishing system was triggered more than 36M times on computers of @Kaspersky Lab users #KLReport
Tweet
Phishing pages imitating well-known cloud storage sites are used to distribute various malicious programs. In such cases, a user automatically downloads a malicious program to his computer by clicking the link on the page.
Below is an example of an attack where the user is asked to download an important PDF document. The link in the email leads to a phishing page imitating the site of the popular cloud service Dropbox.
Example of a phishing attack targeting users of Dropbox
In addition to stealing data stored in the cloud and spreading malware, cybercriminals often use the Dropbox name to steal the victim’s email account data.
Example of a phishing page using the Dropbox brand
Here is yet another example of phishing, with the scammers trying to steal the user’s AppleID and password for iCloud.
Example of a phishing attack on iCloud users
Among other things, if successful, the attackers gain access to any content purchased by the user as well as his email account.
Top 3 organizations attacked
Fraudsters continue to focus the greatest part of their non-spear phishing attacks on the most popular brands. In this way they are trying to increase the chances of success for their latest phishing attack. In more than half of cases the heuristic component of Anti-Phishing is triggered when a user follows a link to phishing pages hiding behind the names of more than 30 well-known companies.
The Top 3 organizations most often attacked by phishers account for 26.39% of all phishing links detected in Q3 2015.
Organization % of all detected phishing links
1 Yahoo! 15.38
2 VKontakte 9.44
3 Facebook 8.95
In Q3 2015, the leading three organizations targeted by phishers saw a few changes. Yahoo! remained top with 15.38%, although its share almost halved (-13.65 p.p.). The Russian social networking site VKontakte (9.44%) came second. Facebook (8.95%) fell by 1.49 p.p. and moved from second to third place.
Conclusion
In Q3 of 2015, the percentage of spam in email traffic accounted for 54.2%, a 0.8 p.p. drop from the previous quarter. The Top 3 biggest sources of spam distributed worldwide were: the US (15.3%), Vietnam (8.4%) and China (7.2%).
The holiday season saw an increase in tourism-related malicious spam. Cybercriminals sent out fake notifications from well-known booking services, airlines and hotels, as well as emails from individuals. They typically included attached archives with different Trojan downloaders.
Trojan-Spy.HTML.Fraud.gen remained the most popular malicious program sent by email. As in the previous two quarters, the rating of the most popular malware families was topped by Upatre. Germany topped the ranking of countries whose users were most often targeted by mailshots – 18.5% of antivirus detections were registered there.
A particular feature of Q3 was a new trick used in phishing emails – in order to bypass spam filters they placed the text of the email and fraudulent link in an attached PDF document rather than in the message body.
In Q3, Kaspersky Lab solutions blocked more than 36 million attempts to follow links to phishing pages, which is 6 million more than in the previous quarter. The country where the largest percentage of users is affected by phishing attacks was once again Brazil (21.7%).
Anonymous has taken down 5,500 ISIS accounts
18.11.2015
The collective of hackers Anonymous claimed Tuesday to have taken out 5,500 Twitter accounts used by the Islamic State organization.
The hacking collective Anonymous launched the operation #OpParis against the ISIS in response to the dramatic Paris attacks. The hackers belonging to Anonymous are targeting social media accounts used by members of the terrorist organization. Anonymous released a video on the Internet announcing that his members will catch ISIS members online. In the video, an avatar of Anonymous with a strong French accent declared war to the terrorists
In a couple of days, more than five thousand Twitter account were brought down by Anonymous, as announced by the collective in Tweet.
“We report that more than 5500 Twitter account of #ISIS are now #down! #OpParis #Anonymous #ExpectUs,” states the tweet published by Anonymous on Tuesday.
It is not clear how Anonymous has taken down the Twitter accounts used by the ISIS. Anonymous said it posted the accounts to an online forum using the hashtag #daeshbags (Daesh is the Arabic acronym for the Islamic State group).

On the hacker side also the hackers belonging to the ISIS have released a statement in response to Anonymous’s #OpParis, the members of the ISIS called Anonymous – IDIOTS.
“The #Anonymous hackers threatened… that they will carry out a major hack operation on the Islamic state (idiots),” the message said.
The message was posted via the messaging service Telegram, the communication channel mostly used by the ISIS members in this period.

This is just the beginning, for sure in the next days the hackers will surprise us. Don’t forget that Anonymous is inviting its members to avoid to launch DDoS attacks against the ISIS websites, instead the collective is asking to hack them stealing sensitive data to disclose.
The ISIS is warning its members, on a separate Telegram Channel, Khilafah News, the ISIS spread a message to its followers that instructs them on how to prevent getting hacked by Anonymous.
Below the list of recommendations:
Don’t open any links unless sure of the source.
Change Internet Protocol addresses “constantly.”
Do not talk to people you do not know on Telegram.
Do not talk to people on Twitter direct messaging.
Do not make the same email as your username on Twitter.
Anonymous vs ISIS telegram darknet 3
The ISIS message was shared among various ISIS channels on Telegram.
JPMorgan hackers also hacked an anti-fraud corporation
18.11.2015
According to the Federal indictment about the JPMorgan case, the cyber gang also hacked an anti-fraud corporation labeled as “Victim #12” to remain hidden.
According to the Federal indictment about the JPMorgan case of 83 million stolen customer records, there is a firm labeled as “Victim #12,” that had been hacked to enable hackers to more easily push through payments for spam-advertised prescription drugs and fake antivirus schemes.
The US authorities have charged three individuals over the hack of the JPMorgan Chase and other financial institutions. The data breach suffered by the JPMorgan Chase is considered the largest ever hacking case in financial history.
According to Bloomberg, the cyber thieves have stolen details of “over 100 Million customers,” meanwhile the spokeswoman for JPMorgan Chase Patricia Wexler confirmed the number of affected customers was around 80 Million. The US Court of the Southern District of New York has charged three men, Gery Shalon, Ziv Orenstein, and Joshua Samuel Aaron, accusing them of hacking into a number of financial institutions, including JPMorgan Chase.
The Victim #12 is the G2 Web Services LLC based on many sources such as KrebsonSecurity and has the expertise in helping banks and financial institutions detect websites that are fraudulent or sell contraband.
“One of them, identified in the indictments only as “Victim #12,” is an entity that helps banks block transactions for dodgy goods advertised in spam. Turns out, the hackers targeted this company so that they could more easily push through payments for spam-advertised prescription drugs and fake antivirus schemes.” reported Brian Krebs.
Most probably, these hackers targeted the aforementioned victim to prevent blocking of the payments for the illegal transactions for fake anti-virus or pharmaceutical products. The gang that hacked also the JPMorgan has managed to monitor the detection processes of the victim and read staff emails that eventually enabled them arrange their steps to evade detection.
“Prosecutors say the ringleader of the cybercrime gang accused of breaking into JPMC,Scottrade, E-Trade and others is 31-year-old Gery Shalon, a resident of Tel Aviv and Moscow. Investigators allege Shalon and his co-conspirators monitored credit card transactions processed through their payment processing business to attempt to discern which, if any, were undercover transactions made on behalf of credit card companies attempting to identify unlawful merchants. The government also charges that beginning in or about 2012, Shalon and his co-conspirators hacked into the computer networks of Victim-12 (G2 Web Services).” continues Krebs.
In short, the hackers have blacklisted list of credit and debit cards belonging to employees of the Victim #12 used for detection of unlawful merchants and rejects all the transactions from the blacklist and as a consequence evade the detection.
“In particular, through their unlawful intrusion into Victim-12’s network, Shalon and his co-conspirators determined which credit and debit card numbers Victim-12 employees were using the make undercover purchases of illicit goods in the course of their effort to detect unlawful merchants,” reports the Shalon’s indictment. “Upon identifying those credit and debit card numbers, Shalon and his co-conspirators blacklisted the numbers from their payment processing business, automatically declining any transaction for which payment was offered through one of those credit or debit card numbers.”
jpmorgan
The moral of this story is the depth of organized cybercrimes and how cybercriminals are trying to keep their activities and business model in a covert manner.
“It’s a cat-and-mouse game. They go from one business into another.” said Alan Krumholz, principal data scientist at G2.
In conclusion, the above news helps us understand that all the companies co-operating are chained and lack of attention to security practices and standards of one of the parties may influence others even more traumatically.
Google’s $85 Chromebit Lets You Turn Any Monitor or TV into a Computer
18.11.2015
Asus and Google Chromebit Lets You Turn Any Monitor or TV into a Computer
Google and Asus are finally ready to release their new micro Chrome OS computer called the Chromebit — that retails at a great price, just $85.
That is quite cheap for what is essentially a portable computer that you can take anywhere in your pocket.
Also Read: CHIP — The World's First $9 Computer.
Announced back in March, the Chromebit is a fully featured Computer-on-a-Stick that plugs into TV or any screen and turns it into what Google calls a "full-fledged Chrome OS-based computer."
All you need to do is:
Plug the Chromebit into any HDMI port
Hook up the power cable, a Bluetooth keyboard and a mouse
Your instant computer is ready
It has a smarter clinch on the business end so that you can easily plug the Chromebit into practically any HDMI port without the need for any extension cable.
Also Read: Mouse Box — An Entire Computer inside a Mouse.
Despite its low price of just $85, the Chromebit offers you a complete Chrome OS experience, meaning you will be able to do everything you can do on your Chromebook or your Chromebox.
Asus and Google Chromebit Lets You Turn Any Monitor or TV into a Computer
Chromebit is currently available in United States, Australia, Canada, Denmark, Finland, Japan, New Zealand, Norway, Spain, Sweden, Taiwan and the UK. Users in the US can get the Chrombit from Amazon, Fry’s and Newegg.
ISIS Calls Anonymous "IDIOTS" and Issues 5 Lame Tips for its Members to Avoid Getting Hacked
18.11.2015
ISIS Calls Anonymous — IDIOTS — Issues Advice to Avoid Getting Hacked
The Anonymous Hacking group on Sunday declared Total War against the ISIS, the Islamic State terror organization that claimed responsibility for the Paris attacks on Friday that killed 129 people and hundreds more injured.
In a sinister video posted on YouTube, the Cyber Hacktivists said they will launch their "biggest operation ever" with the warning that "Anonymous from all over the world will hunt you down.”
Also Read: Would Encryption Backdoor Stop Paris-like Terror Attacks?
Now, The Islamic State militant group (ISIS) has released a statement, responding to Anonymous’s declaration of total war.
They (ISIS) called Anonymous – IDIOTS,
… and issued some anti-hacking tips to pro-ISIS supporters to protect against cyber attacks.
The message from ISIS to Anonymous came through one of the ISIS-affiliated official channels, dubbed ELITE SECTION of IS, on the messaging app Telegram.
The message read:
"The #Anonymous hackers threatened in a new video release that they will carry out a major hack operation on the Islamic state (idiots)."
ISIS issues 5 Lame Advice to Avoid Getting Hacked
isis-telegram-channels
On a separate Telegram Channel, Khilafah News, ISIS sent out a message to its supporters and followers that go on to provide instructions on how to prevent getting hacked by Anonymous.
These guidelines read:
Don't open any links unless sure of the source.
Change Internet Protocol addresses "constantly."
Do not talk to people you do not know on Telegram.
Do not talk to people on Twitter direct messaging.
Do not make the same email as your username on Twitter.
This ISIS message was then forwarded around to various other ISIS-affiliated Telegram channels to spread awareness among its members.
Also Read: ISIS Militants linked to Paris Attacks had a Bitcoin Wallet worth $3 Million
It seems like ISIS is taking Anonymous hackers seriously, as the hacktivist group has already taken down more than 5,500 Twitter accounts linked to ISIS supporters and members as a result of its #OpParis campaign.
Stop DDoS attacks in seconds
17.11.2015
An Israeli company named “L7 Defense” is trying to do the impossible – to stop application layer DDoS attacks in seconds instead of hours.
It wants to do so by using an automatic protection system based on an immune-biological model that combines with Real Time Big Data analysis.
“The body knows how to deal in real time with damage to critical systems. He is broadcasting warnings such as fever or other signs that activate the immune system. We found that combining biological model for analyzing the BIG DATA, identifies sophisticated DDoS attacks in real-time,” said Israel Gross, co-founder, and L7 Defense CMO.
Alongside Gross, the partners are Dr. Doron Chema (CEO) Bio-Information by Training, whom also developed the System model and Mr. Mark Ginsburg, a senior algorithmic developer who served in Elite Cyber Unit (IDF).
“DDoS attacks on the application layer are very challenging today. A major reason for this is the use of tools that successfully simulate human behavior and are tailor made for the specific target”, says Gross. “The trick in application layer DDoS is to attack a large number of vulnerabilities while exhausted the target servers’ resources in a short time period”.
DDOS Attack Concept.
Gross explains that today defense systems against DDoS attacks are mainly based on forwarding the traffic to human analysts for a test. “In reality, the average time to discovery and blockage of complex DDoS attacks is more than an hour,” says Gross. “We strive for detection and blocking in no more than a few seconds automatically, regardless of the number of attacking vectors. This protection model is patented”.
DDoS attacks began in the 90s when the original method is to “strangle” the network traffic. Over the years, this type of attack has become easier to identify and block. At the same time, a new trend was born in recent years – targeted attacks on system servers.
These attacks are called, “application layer DDoS” operate relatively modest volume of traffic, and very efficient due to their adaptation to the target. For example, in an e-commerce site, each search request could have a potential of serving as an attacking vector. One can carry out DDoS attack by using Bots, sending multiple search requests to products simultaneously. The result of the load focused on a search engine which usually supported by heavy mechanisms may bring down the entire site or at least a significant slowdown.
L7 Company’s system is software based, located within the boundaries of enterprise systems (DMZ) and can be installed in a public cloud (AMAZON, AZURE, etc.) and / or the customer’s server farm. The system is compact and can be installed as a single server, serving as a protective reverse proxy system.
The system operates at all times (ALWAYS ON), with no prior knowledge or accumulated memory (such as the use of a central signatures bank). From the moment of identifying an attack in real time, the system produces an unequivocal identification of each attack vector and stops them immediately.
“Demonstrations show that the system is dealing effectively with the detection and blocking of 4-5 vectors simultaneously without prior knowledge. It is not limited to blocking even more complex attacks,” says Gross.
“Recall that currently identifying and stopping more than one vector is a real challenge to the SOC personnel in various organizations and usually lasts a few hours by a team of dedicated experts.
“Our system is adapted to the current situation where organizations are attacked frequently and over days or even weeks. It does not require manual operation by teams of experts that the level their availability decrease and the level of cost increases accordingly”.
In July this year, the company raised 750 thousand dollars from Incubate (Elbit Systems Technology Venture) and Israeli office of the Chief Scientist (OCS). “Elbit is a strategic partner and it opens doors for us,” says Gross.
Defense L7 company began operating officially in last July and has been awarded first prize in start-up companies competition in Germany (Tech Ecosystems). “Winning the competition will expose us to the German market,” concludes Gros.
A flaw in D-Link Switches opens corporate networks to hack
17.11.2015
A flaw in certain D-Link switches can be exploited by remote attackers to access configuration data and hack corporate networks.
The independent security researcher Varang Amin and the chief architect at Elastica’s Cloud Threat Labs Aditya Sood have discovered a vulnerability in the D-Link Switches belonging to the DGS-1210 Series Gigabit Smart Switches.
The security experts revealed the existence of the flaw at the ToorCon security conference, but they avoided to disclose the details about the exploit to give the D-Link the necessary time to solve the issue.
D-Link Switches 2
This family of network devices allows the storage of backup files, including logs, firmware and configuration files, in the device’s flash memory or on a web server. Unfortunately, the system lacks of proper authorization and authentication mechanisms, allowing an attacker to access the stored backup files.
The experts discovered that file stored in the flash memory can be accessed remotely by simply knowing the IP address of the D-Link Switches. The exposition of information contained in the configuration files could give the attackers precious information on the targeted network, the attackers could also control internal traffic by compromising the D-Link Switches.
“Once the configuration file is accessed, all the details about the switch, including configuration, username, etc., can be obtained by the attacker. For example, the configuration can be uploaded on another switch (purchased from the market) to obtain the details. Log files reveal information about the clients that accessed the switch and other infrastructure-related information,” said Sood. “Compromising network switches can have disastrous consequences as the attacker can control the traffic flow.”
The duo of experts highlighted that also the root directory of the web server is easily accessible by hackers.
“Usually, when the backup option is selected, the log files and configuration file are stored on the flash drive. Logs are enabled by default in many versions, but a majority of administrators have backup configured so downloading these files is easy,” explained Sood.
Although the security vulnerability has been reported early October, D-Link hasn’t fixed it yet.
Nebezpečné softwarové knihovny
17.11.2015 Zranitelnosti
Chyby v knihovnách třetích stran si často najdou svou cestu do koncových produktů – a to je problém, kterým se budou vývojáři a správci systémů v následujících měsících zabývat.
V dnešním světě agilního vývoje softwaru a rychlých cyklů vydávání nových verzí vývojáři při práci stále více spoléhají na knihovny a komponenty třetích stran. Protože mnoho z těchto knihoven pochází z dlouhodobých open source projektů, vývojáři často předpokládají, že jde o dobře napsaný bezchybný kód. Ale mnohdy se mýlí.
Hlavní záplatovací úsilí vyvolané chybami, jako Heartbleed (krvácení srdce), Shellshock či Poodle z poslední doby, slouží jako ukázky důsledků kritických chyb zabezpečení v kódu třetí strany. Chybami postižený software běžící na serverech, ve stolních počítačích, mobilních zařízeních a hardwarových řešeních ovlivňuje miliony spotřebitelů a firem.
Tyto vysoce medializované chyby zabezpečení však nebyly ojedinělými incidenty. Podobné chyby byly zjištěné v knihovnách, jako OpenSSL, LibTIFF, libpng, OpenJPEG, FFmpeg, Libav a bezpočtu dalších, a našly si během let cestu do tisíců produktů.
Jedním z důvodů, proč tyto chyby skončí v hotových produktech, je víra vývojářů, že jimi použitý kód třetích stran je bezpečný, protože ho už použilo mnoho lidí.
Mýtus nevýznamných chyb
„Existuje mýtus, že je open source software bezpečnější, protože ho může každý zkontrolovat a více očí zajistí, že zůstanou jen nevýznamné chyby,“ připomíná Jake Kouns, ředitel zabezpečení informací ve společnosti Risk Based Security, která se specializuje na sledování chyb zabezpečení.
„Skutečností je, že zatímco všichni mohou zkoumat kód, nedělají to a odpovědnost za kvalitu je zpožděná. Vývojáři a firmy používající knihovny třetích stran nevyhradí vlastní prostředky na testování bezpečnosti kódu někoho jiného. Ať už je to dobře nebo špatně, všichni si myslí, že chyby v zabezpečení najde někdo jiný a že publikovaný kód je bezpečný,“ dodává Kouns.
Skutečností je, že mnoho open source projektů, a to i ty, které produkují kód rozhodující pro internetovou infrastrukturu, je často špatně financovaných, potýkají se s nedostatkem lidských zdrojů a nemají ani zdaleka dostatek prostředků na zaplacení profesionálních auditů kódu nebo pracovní lidské síly, která by se zapojila do masivního přepisování starého kódu.
OpenSSL je významným příkladem takového případu, ale není zdaleka jediný. Poté, co došlo k oznámení kritické chyby Heartbleed v dubnu loňského roku, vyšlo najevo, že projekt OpenSSL měl jen jednoho vývojáře pracujícího na plný úvazek a že projekt byl primárně financovaný jako zakázková práce, kterou dělali ostatní členové týmu ve svém volném čase pro společnosti s potřebou expertizy SSL/TLS.
Vývojáři OpenBSD kritizovali OpenSSL za používání starého kódu pro platformy, o které se zajímá málo lidí, a rozhodli se udělat „fork“ projektu a vytvořit čistší verzi knihovny s názvem LibreSSL.
Chyby v open source knihovnách jsou často důsledkem jednoho nebo více z následujících důvodů: starý kód nebo nízká zralost kódu, nedostatečný audit a nedostatečné „fuze“ testování (procesem hledání chyb zabezpečení automatickým zadáváním neočekávaného vstupu do aplikací) a příliš málo udržovatelů, uvádí Carsten Eiram, ředitel výzkumu společnosti Risk Based Security.
„Vidíme, že mnoho chyb zabezpečení v těchto knihovnách výzkumníci najdou jen spuštěním nejnovějších fuzzerů, takže je to často něco, co mohli udržovatelé či společnosti používající uvedené knihovny udělat sami. Dodavatelé softwaru rychle implementují knihovny do svých produktů, ale jen zřídka předtím udělají audit, nebo dokonce fuzz, ani nepomáhají v jejich údržbě,“ podotýká Eiram.
Je to všechno marketing
Chyby zabezpečení typu Heartbleed zvedly zájem mezi vývojáři softwaru a správci systémů částečně z důvodu velké pozornosti, jaké se chybám dostalo v médiích. Někteří dodavatelé stále nacházejí produkty ovlivněné těmito chybami a vydávají pro ně opravy – tedy řadu měsíců po jejich prvním oznámení...
Paris Attacks — NO! We Can't Blame Edward Snowden and Encryption for Terror Attacks
17.11.2015
Terrorist groups are increasingly using high-grade, advanced end-to-end encryption technologies so that no law enforcement can catch them.
The deadliest terror attacks in Paris that killed 129 people were the latest example of it.
How did the Terrorists Communicate and Organize the Plot?
The Paris terrorists almost certainly used difficult-to-crack encryption technologies to organize the plot – locking law enforcement out, FBI Director James B. Comey told Congress Wednesday.
The ISIS mastermind behind the Friday's Paris massacre is identified to be Abdelhamid Abaaoud, who is based in Syria. So to transmit his plans to the suicide bombers and gunmen, he would have made use of secure communication to keep law enforcement out.
FBI's Comey believes ISIS is making use of popular social media platforms to reach out to potential recruits and smartphone messaging applications that are end-to-end encrypted, meaning even the company cannot read the messages.
Blame Game: Ex-CIA Director Blames Edward Snowden For Paris Attack
Ex-CIA Director James Woolsey, who once said Snowden "should be hanged by his neck until he is dead," has blamed NSA whistleblower Edward Snowden for revealing the agency's efforts to break encryption and for teaching terrorists how to avoid being caught.
Also Read: Anonymous declares War on ISIS: We will Hunt you Down!
Woolsey said, Snowden, who leaked a vast trove of classified files detailing the extent and workings of the United States intelligence system, is responsible for the Paris terror attacks and now has 'blood on his hands.'
According to Woolsey, it was Snowden's leak of top-secret documents about how American and British spy agencies monitor and track people worldwide that led terrorist groups like...
...ISIS and Al-Qaeda to adopt new communication methods, including end-to-end encryption channels, to avoid surveillance.
But, Why Blaming Snowden? It's Intelligence Failure
The tougher and more important question here is – If terrorists used encryption to plan the strikes in Paris, did they circumvent our spying agencies' Bulk Interception tools and offensive cyber operations?
"I was a bit surprised just by how quickly and blatantly – how shamelessly – some of them jumped to exploit the emotions prompted by the carnage in France to blame Snowden: doing so literally as the bodies still lay on the streets of Paris," the journalist Glenn Greenwald said, who has worked with Snowden to expose NSA secrets.
Bulk interception is the collection of the vast quantity of internet data, sometimes from thick undersea cables and then storing it in databases for a limited time.
However, the government's claims about the NSA bulk surveillance of email and phone records that the operations are to keep the country safe from terrorism are overblown and even misleading.
Also Read: ISIS Militants linked to Paris Attacks had a Bitcoin Wallet worth $3 Million
Surveillance of phone metadata has had no visible impact on preventing terrorist attacks, so it is a total failure of our intelligence agencies, and not Snowden.
The fact that, long before Snowden's leaks, our so-called intelligence agencies around the world failed to prevent many terrorist attacks, including:
The Bali bombing in 2002
The Madrid train bombing in 2004
The 7/7 London attacks in 2005
The series of attacks in Mumbai in 2008
The Boston Marathon bombing in 2013 that took place in the intense security at the leading annual event in a major American city
However, after all these terrorist attacks, the government response has been uniform – Give the intelligence agencies more powers and greater abilities to track, surveil and monitor anyone they believe is suspicious.
"The Snowden revelations were not significant because they told The Terrorists their communications were being monitored; everyone – especially The Terrorists – has known that forever," Greenwald said.
Moreover, one of the leaked GCHQ documents contains what the agency calls a "Jihadist Handbook" of security measures, which was written in 2003, that instructs terrorists to learn and use sophisticated, strong encryption techniques to avoid government surveillance.
So, how could we blame Snowden, who exposed law enforcement’s mass surveillance operations in 2013; almost 10 years after the Jihadist Handbook was written.
After Paris Attack, Government's arguments about Encryption and Backdoor
Now in the wake of the recent Paris terrorist attacks, the US government has renewed their assault on encryption and revived their efforts to force tech companies to install backdoors in their products, like encrypted messaging apps.
Also Read: US Court Rules NSA Phone surveillance Program is illegal.
The intelligence agencies have gotten it all wrong. Due to the bulk collection and interception, the overall volume of encrypted internet traffic has gone up and up, that the intercepted data has become inaccessible even to intelligence agencies.
So, it's not Snowden who is responsible for the Paris attacks, it's the Failure of our government and intelligence agencies.
Would Encryption Backdoor Stop Paris-like Terror Attacks?
17.11.2015
With 129 people killed in Paris terror attacks and dozens critically wounded, the law enforcement and intelligence officials are reviving their efforts to force companies to put some backdoors in encryption so that they can access your information.
How did the Intelligence agencies fail to Intercept terrorist plans of these attacks?
In the wake of the Paris terror attacks, Former CIA Director Michael Morell argued on TV that encrypted communication services may have aided the planning and plotting of the Paris attacks, blaming Edward Snowden and US companies for the attacks.
Also Read: NO, We Can't Blame Edward Snowden and Encryption for Terror Attacks
With more Surveillance and Encryption backdoor, Is it possible that Friday's attacks could have been stopped before they began?
Morell suggested that recalcitrant US companies should be forced to install government backdoors in their software and hand over encryption keys to the government, thinking that Encryption Backdoor could stop Paris-like Terror attacks.
NO, Encryption Backdoors Can't Stop Paris-like Terror Attacks
US intelligence and Law enforcement agencies have been warning for years that due to their inability to decrypt communication between computers and phones, they are unable to know what terrorist groups are planning.
But in my opinion, no backdoors can help law enforcement, and intelligence agencies tackle terrorism.
Here's Why:
Forcing US companies to put Backdoors in their encryption software and hand over encryption keys to the law enforcement would not help them catch terrorist suspects who are using their:
Jihadist's Home-Brewed Encryption products, or,
Services and Products made in Countries not controlled by US Laws.
You can not stop a terrorist from installing an app made in Russia or Brazil, neither you can stop them creating and using their own encryption apps. In both cases, such backdoors will be useless.
Also Read: Anonymous declares War on ISIS: 'We will Hunt you Down!'
Let's talk about some real examples where terrorist groups and online jihadists have proved that they are already aware of intelligence and law enforcement agencies' ability to track them.
Jihadist's Home-Brewed Encryption Softwares
Terrorist groups and jihadists were already making use of – and developing – secure communications software like:
1. Asrar al-Mujahideen (Message and File Encryption Software): Developed in 2007, Asrar al-Mujahideen is a Jihadi-themed encryption software package that encrypts messages and files between users and is promoted as a trusted and secure avenue for terrorist groups to communicate with one another.
2. Asrar Al-Dardashah (Encryption for Instant-messaging Services): Approximately four months before the Snowden's first revelation, GIMF introduced a new software package on February 7, 2013, that allows jihadi users to encrypt live conversations over instant messaging platform including Google Chat, Yahoo, MSN and Paltalk with the multi-platform instant messaging software Pidgin.
3. Tashfeer Al-Jawwal (Mobile Encryption Program): Developed on September 4, 2013, Tashfeer Al-Jawwal provides encryption for SMS messages and files sent on Android as well as Symbian-based mobile phones.
4. Amn al-Mujahid (Android-based Message Encryption software): Launched in late 2013 by Al-Qaida’s al-Fajr Media Center, Amn al-Mujahid is an encryption software for online communication with support for Android.
Don't Mess With Encryption
These examples are enough to provide you an overview that forcing companies to install backdoor will only leave us all vulnerable to the same type of surveillance from unauthorized entities, including hackers and spies from China, Russia, and other countries.
So, backdooring encryption software will never be a complete solution.
However, the FBI and NSA will continue their fight for gaining access to encrypted communications through backdoors, and possibly they will try their luck with the next presidential administration in 2017.
Meanwhile, in the wake of the Paris attacks, UK is willing to pass the Investigatory Powers Bill (IPB) that will grant intelligence agencies more powers to collect private communications in bulk.
Discovered an ISIL Bitcoin Address containing 3 Million dollars
17.11.2015
Hackers of the anti-Terrorism group Ghost Security Group have discovered ISIL militants had a bitcoin address containing 3 Million Dollars.
We have been dismayed by the recent Paris attacks, fear, disgust and anger are the emotions that many of us have felt seeing the images from the France.
While the Islamic State (ISIS) was claiming the responsibility for the attack, the collective of hackers Anonymous declared war on the terrorist organization by launching the operation #opParis.
The investigators are collecting every information regarding the Paris attacks trying to discover when and how the terrorist attacks were organized.
One of the principal problems for the authorities is to discover who is fundings the terrorists, which are the channels used by the ISIL to transfer money to the cells operating in various European countries.
The experts of the Anti-terrorism group of ethical hackers, Ghost Security Group (GSG), speculate that members of the ISIL regularly uses cryptocurrencies to fund the operations of its cells.
To proof their thesis, the hackers of the Ghost Security Group have searched for Bitcoin wallets used by the ISIL organization, and finally they have discovered them.
Members of the Ghost Security Group have uncovered several Bitcoin addresses that might be used by the ISIL to fund its operations. They also made a disconcerting discovery, one of the wallets they have analyzed contains $3 Million in US dollars worth of Bitcoins.
paris attacks
“Yes, we did detect several indicators of an attack impending and are currently in the process of collecting valuable evidence for United States government officials. I cannot go into more detail at the moment on current investigations.” a member of Ghost Security Group explained in an interview with NewsBTC.
“The Islamic State does use cryptocurrencies as a form of income to fund their ongoing operations, and we have managed to uncover several Bitcoin addresses used by them,” “We had discovered a BtC address linked to a known Islamic State deep website approximately three months ago and provided it to dw.com. They hired a team of blockchain analysts to trace the cryptocurrency to the estimated 3 million in BtC the discovered.”
The Ghost Security Group has identified several websites used by the ISIL on the darkweb and gathered information about the amount of money contained in the wallets the addresses of which are present on these sites.
“Most of the Bitcoin funding sites utilized by the Islamic State are on the deep web and we have managed to uncover several and successfully shut them down in order to limit the funding extremists receive through the use of cryptocurrencies.” continues the Ghost Security Group.
Although there are no proofs that these wallets were used to fund the cells involved in the Paris attacks, the Ghost Security Group linked it to the ISIL organization demonstrating the use of cryptocurrencies.
The hackers Ghost Security Group believe that Bitcoin is their prime form of cryptocurrency for the ISIL, but they have no information regarding the mining abilities of the group. It is likely that the ISIL receives donations on a regular basis by its sympathizers.
Anyone can assist the Ghost Security Group by reporting any tips they may receive to http://reportonlineterrorism.com. The group also accepts donations to purchase computer equipment for its activities.
GHOST SECURITY GROUP BITCOIN ADDRESS:
1MfUH1ThpU1dMjBAc5jcewLToE2efQxu7K
Windows Bitlocker disk encryption could be easily bypassed
17.11.2015
Microsoft recently fixed the a vulnerability in the Bitlocker disk encryption feature that could be exploited to easily bypassed it is a few seconds.
A disk encryption tool is a very important software for the protection of our data, million machines rely on them to protect user data, but we have to consider that also these applications could be affected by serious flaws.
In September, the security expert James Forshaw, a member of Google’s Project Zero team, has discovered two critical flaws in the driver that the popular disk encryption tool TrueCrypt installs on Windows systems. The vulnerabilities could be exploited by attackers to access protected data.
BitLocker is another popular disk encryption tool, it was designed by Microsoft and an amazing number of Windows users rely on its feature to protect their data.
The news in the headlines is that the BitLocker disk encryption tool could be easily bypassed prior to last week’s update.

According to a recent research conducted by the expert Ian Haken from the security firm Synopsys, the security feature implemented in BitLocker could be bypassed, and “does not require a sophisticated attacker.”
Prior to BitLocker, an attacker could simply boot up a live Linux distribution, mount the disk containing the user data and access his document. The full-disk encryption feature starts at the boot of the machine protecting data with unbreakable encryption.
One researcher, Ian Haken, a researcher at security firm Synopsys, said in a paper published late last week that the security feature could be bypassed, and “does not require a sophisticated attacker.”
Haken explained that PCs connected to domains were most exposed to the attack if the attacker is able to disconnect the machine from the network and the domain server couldn’t be reached. In this attack scenario the Windows machine uses a local username and password stored in the cache.
The researcher has discovered a method to access the cached password and modify it. In this way the attacker is able to bypass the full-disk encryption feature.
The researcher has demonstrated that by setting up a fake domain server with an identical name, the attacker only had to create a user account with a password created in the past by the user. This trick triggers a policy-based password change, at this point it is enough to change the password and log into the PC using the password that is set in its cache.
“Once logged in, the attacker now has access to all of the user’s data, such as emails, intellectual property, saved passwords, cached credentials, etc. If the user is a local administrator, the attacker could even dump the BitLocker key from kernel memory” wrote the researcher.
Microsoft has already fixed the bug, the last monthly security updates contain the fix for the flaw. Microsoft gave low priority to the flaw because its exploitation requests specific conditions, as reported in the MS15-122 security bulletin.
Clearly the classic attack scenario sees the attackers with access to a lost or stolen laptop, a circumstance not rare in an enterprise context.
The researcher excluded that the flaw has been exploited in the wild.
“As usual, the most important security procedure is to make sure you have applied all security updates to your effected systems,” the researcher wrote.
Hackers claim ISIS Militants linked to Paris Attacks had a Bitcoin Wallet worth $3 Million
16.11.2015
The world watched in horror as coordinate attacks in Paris Friday night killed more than 130 people and left over 352 injured.
Over 20 attackers have so far been part of the terrorist cell that planned the deadly Paris attacks, with seven suicide bombers dead, seven attackers under arrest and a total of six people on the run.
The attacks were carried out by Islamic State (ISIS), who later claimed responsibility for targeting innocent people at 'soft' locations that lack police or military protection, including Bataclan concert venue where at least 89 people lost their lives.
Following the bloody terror attacks, the hacktivist collective Anonymous declared war on the Islamic State (IS, formerly ISIS/ISIL) saying, "We will launch the biggest operation ever against you."
But the Question here is:
From Where did the terrorist cell that planned the brutal terrorist attacks in Paris get Fundings?
The Anti-terrorism group of ethical hackers, Ghost Security Group (GSG), said that ISIS regularly uses cryptocurrencies to fund its terrorist operations.
The anonymous member of GSG has uncovered several Bitcoin addresses that they said, might be used by ISIS. One of the accounts they analyzed was found to contain $3 Million in US dollars worth of Bitcoins.
Also Read: Anonymous Just Leaked list of 1000 ISIS Twitter Accounts.
"The Islamic State does use cryptocurrencies as a form of income to fund their ongoing operations, and we have managed to uncover several Bitcoin addresses used by them," a member of Ghost Security Group said in an interview with NewsBTC.
"We had discovered a BtC address linked to a known Islamic State deep website approximately three months ago and provided it to dw.com. They hired a team of blockchain analysts to trace the cryptocurrency to the estimated 3 million in BtC the discovered."
Although there are no actual proofs that cryptocurrencies were used to support the terrorist attacks in Paris, GSG claimed…
…it had uncovered several Bitcoin funding sites utilized by the ISIS on the dark web and successfully shut them down to limit the funding extremists receive through the use of cryptocurrencies.
Putin: ISIS Financed by 40 Countries, Including G20 Member States
At the recent G20 summit, Russian President Vladimir Putin said that ISIS is financed by individual businessmen from 40 countries, including some G20 members.
However, Putin hopes that the work with the G20 members in the fight against terrorism will continue. "I think that cooperation in fighting terrorism is very important," Putin told reporters.
Putin also calls out Obama for arming and training Fighters for ISIS, saying U.S.-trained rebels were leaving to join ISIS with weapons supplied by Washington.
“In my opinion, provision of military support to illegal structures runs counter to the principles of modern international law and the United Nations Charter,” Putin told reporters.
#ParisAttacks — Anonymous declares War on ISIS: 'We will Hunt you Down!'
16.11.2015
Following the bloody terror attacks in Paris where over 130 people were killed, the hacktivist collective Anonymous has declared total war against the Islamic State (IS, formerly ISIS/ISIL).
Anonymous released a video message, posted in French, on YouTube Sunday announcing the beginning of #OpParis, a coordinated campaign to hunt down ISIS's social media channels and every single supporter of the jihadist group online.
The combat mission #OpParis was announced as revenge for the recent ISIS terror attacks that took place in Paris on Friday, November 13, 2015.
Behind its signature Guy Fawkes mask, the group’s spokesperson speaking in French said, "Anonymous from all over the world will hunt you down. Expect massive cyber attacks. War is declared. Get prepared."
"You should know that we will find you, and we will not let you go. We will launch the biggest operation ever against you," the Anonymous spokesperson added. "The French people are stronger than you and will come out of this atrocity even stronger."
Under the #OpISIS online campaign, Anonymous members have been defending French cyber-borders following the Charlie Hebdo massacre in January. In #OpISIS, the group hacked, defaced, unmasked, and reported thousands of ISIS Twitter accounts.
Now, expect the same thing to happen again. In a separate tweet, the group posted a video message saying:
"We are upping our game, you will now be hit by major cyber attacks, I will be speaking to all the most prominent #OpIceISIS teams and supporters such as @TheBinarySec, @CtrlSec, @OpIceISIS and we will work together to take down all ISIS cyber communications and your accounts, haha good luck with keeping them."
More interestingly, the group has allegedly leaked a list of almost 1000 ISIS Twitter accounts in #OpParis.
The social network giant Facebook on Friday the 13th deleted an Anonymous group page, which has been exposing and reporting social media accounts linked to pro-ISIS, as well as banned all its administrators, without giving any prior warning.
The company said that the existence of the group was a "violation of Facebook Terms of Service and Community Standards."
How does the ISIS control the Internet?
16.11.2015
The ISIS, exactly as any other government, has adopted measures to control the access to the Internet in the territories occupied.
In these hours we are discussing the tragic Paris attacks, we are trying to collect the greatest amount of information as possible about the organization of the ISIS. How does the ISIS conduct its propaganda? Which are the communication channels they use? Which will be the next target?
Researching the topic on the web I have found an interesting post published by the Israel homeland Security website. We all know that the Western intelligence run Internet surveillance program and many governments apply a strict censorship on the online activities of their population. Probably the majority of you has read about the “The Great Firewall of China,” one of the most sophisticated surveillance system that is used by the Chinese Government to monitor the online activities of the population and block all the content not aligned with the policy of Beijing.
The Russian government has its surveillance system known as SORM exactly like the British government that manage a network of systems used to screen internet activities, experts refer it with the term “Hadrian’s Firewall.”
The question is … does the ISIS block online activities in the territories it has occupied? How does it do?
Paris attack ISIS darknet hub screenshot-from-2015-11-15-174423 2
The response is affirmative, the ISIS also controls and block Internet access from its region, it monitors the flow of information in and out of the provinces it occupies.
The mechanism is simple and effective, the self-proclaimed caliphate has banned every private access to the Internet.
“Since earlier in the year, ISIL has been monitoring access to the internet – quite literally, access to the internet itself. Previously, in cities likes Raqqa, Syria, “people would go to the cafes and pay money for internet and have a password or a username,” said Abu Ibrahim al-Raqqawi – an activist with the group Raqqa is Being Slaughtered Silently. “They were sitting in their homes and could access the internet” connecting to WiFi extenders operated by many neighbourhood internet cafes.” states the post published on the Israel homeland Security.
Basically every individual that wants to go online need to use a computer in an Internet cafè where he is tracked. The members of the ISIS in an unpredictable way inspect internet cafes and the machine used by the local people to check none has violated its rules.
Now, private internet access in banned. To go online, “you need to go to the internet cafe and you need to have your ID and they will register your name, the time you enter, and the time you’re out,” says Raqqawi, who uses a pseudonym.
Each offender is punished, and we all know the methods of ISIS.
Zaznamenali jsme podezřelou platbu, piráti zkouší nový trik
16.11.2015 Phishing
S důmyslným phishingovým podvodem přišli v posledních dnech počítačoví piráti. Vydávají se za zaměstnance České spořitelny a příjemcům nevyžádaného e-mailu tvrdí, že z jejich účtu byla provedena podezřelá transakce. Z uživatele se touto cestou snaží vylákat informace o platební kartě, díky kterým pak budou schopni odčerpat finanční prostředky z účtu.
„Tímto Vám oznamuji, že jsme zaznamenali podezřelou platební transakci na Vašem bankovním účtu, který máte vedený v České spořitelně. Tímto elektronickým dopisem Vás vyzývám o zaslání níže vyplněných parametrů, které potvrdí Vaši totožnost a disponenční právo k Vašemu účtu,“ tvrdí kyberzločinci v podvodném e-mailu.
Kromě jména a příjmení požadují zadat také rodné číslo i bydliště. Hlavní problém je v tom, že důvěřiví uživatelé by mohli vyplnit i poslední tři okénka tabulky, tedy informace o platební kartě. Ty mohou útočníkům sloužit k provádění plateb na internetu.

„Podvodník žádá po držiteli platební karty citlivé údaje - číslo platební karty, platnost karty a kód CVV2/CVC2 – trojčíslí uvedené na zadní straně platební karty VISA/MasterCard,“ uvedli zástupci České spořitelny.
Podvodná zpráva se objevuje v různých obměnách. Zatím vždy ale obsahovala hlavičku České spořitelny a byla psána bez pravopisných chyb.
„Podvodné zprávy navíc obsahují fotografie skutečných zaměstnankyň naší banky,“ konstatovali zástupci banky. Uživatelé se tak mohou nechat relativně snadno napálit.

Banka informace o platební kartě kvůli ověření platby nikdy nepožaduje. „Česká spořitelna žádné takové zprávy klientům nerozesílá a prostřednictvím e-mailu žádné bezpečnostní údaje nikdy nepožaduje,“ stojí v prohlášení banky.
„V případě, že takovou či podobnou zprávu obdržíte, v žádném případě na ni nereagujte. Pokud jste již požadované údaje vyplnili a zaslali odesílateli, doporučujeme se co nejrychleji obrátit na Klientské centrum České spořitelny na bezplatné telefonní lince 800 207 207,“ uzavřeli zástupci banky.
Není vyloučeno, že se v budoucnu objeví také zprávy, které budou cílit na uživatele dalších finančních domů v Česku. V případě, že uživatelé citlivé informace o platební kartě někomu sdělili, měli by se co nejdříve obrátit na zástupce své banky.
Twittor tool uses Twitter direct messages to control botnets
16.11.2015
Twittor is a tool open source that was designed by the London-based researchers Paul Amar to control botnets via Direct Messages.
The expert has developed the Twittor tool to make life easier for botnet masters, allowing them to control their malicious architectute by sending out commands via Twitter accounts.
“I mostly wanted to create a PoC after Twitter decided to remove the 140 characters limit for Direct Messages,” wrote the security researcher.
The use of Twitter as a communication channel to control a botnet is not a novelty, any botmasters use social networks such as Facebook and Twitter as C&C. This is a winner’s choice because the technique makes it hard to detect botnet activities.
The interactions with social networking sites can be easily automated and “malicious” traffic directed to social media platforms is hard to identify due to large volumes. Attackers can set up a network of fake profiles on a social network and use them to post a specific set of encrypted commands to the malware. The infected machine queries the “bootmaster” profile for new commands, summarizing a botnet a using C&C in social media is extremely resilient and allows malware to run for long periods of time.
The attackers have improved their control techniques over time. Some malicious agents, in fact, don’t limit their activity to just interpreting messages from social networking but also receive commands hidden inside a picture posted by a profile related to the bootmaster.

The Twittor tool is open source and it is available on GitHub, and the researcher Amar is inviting developers to contribute to the project.
“A stealthy Python based backdoor that uses Twitter (Direct Messages) as a command and control server This project has been inspired by Gcat which does the same but using a Gmail account.” Amar wrote.
“fork the project, contribute, submit pull requests, and have fun.”
The Twittor tool is a Python-based backdoor, the attacker just needs a Twitter account, set up a Twitter app, and get Twitter API credentials.
Among the features already implemented by the twitter tool there is the listing of active boys, execution of commands on it, refreshing of the C&C control. All via features rely on the Direct Messages.
Amar explained that Twittor tool has been inspired by gcat, another open source backdoor that exploits Gmail as a command and control server.
A few hours the Paris attacks, a new ISIS propaganda hub appeared on the Darknet
16.11.2015
The popular security expert Scot Terban (aka @krypt3ia ) discovered a few hours after the Paris attacks, a new ISIS propaganda hub appeared on the Darknet.
The Paris attacks shocked the world, the war is overwhelmingly coming into our homes and the intelligence experts fear that this is just the beginning. The ISIS knows how to spread his message, none in the past was able to organize a so effective propaganda. Each media is masterfully handled by terrorists, social networks, instant messaging app, gaming platforms and forums course in the darknet.
In June, the Europol announced the creation of a team that aims to find key figures in propaganda campaigns run by ISIS members seeking to recruit foreign fighters. The Isis‘s machine propaganda is scaring as efficient, it generates something like 100.000 daily tweets, and it’s used to recruit foreign fighters to support the group.
The Isis is gaining a lot of power in the last years, for the first time a terrorist organization has resources and capabilities to proclaim itself a State.
For this reason, the Europol announced the creation of a new Europe-wide police unit to search for the core leaders of Isis’s social media propaganda campaign. The police unit will track the leaders responsible for an average of 100.000 tweets a day.
isis paris attacks post propaganda
The Paris attacks have raised the level of attention on the organizations that could have supported the terrorist operations from the inside. What are the channels used by terrorists to communicate and what technologies they used?
Many intelligence experts point to the revelations of Snowden as an element that has greatly benefited the terrorists to escape the control exercised by the police. Terrorists are aware that intelligence agencies are carefully monitoring telecom communications, emails, instant messaging apps and much more.
That’s why groups like the ISIS are looking for new channels to reach wider audiences, such as the gaming consoles and the Dark Web, two environments where it is necessary a significant effort to track and identify the source of the messages.
paris attacks
A few hours after the cruel Paris attack, Daesh (al-dowla al-islaamiyya fii-il-i’raaq wa-ash-shaam, a.k.a. ISIS/ISIL) launched his propaganda on the Dark Web.
The website contains translations in English, Turkish, and Russian from the recent statement issued by Daesh claiming credit for the Paris attacks.
The new propaganda center was discovered by the popular researcher Scot Terban (aka @krypt3ia ), who reported it to the colleagues at Salted HASH.
The expert noticed a post that explained the need to create a new hub for propaganda, this is the response to the numerous operations against other websites used by the ISIS that were seized by law enforcement of targeted by hacktivists online. The terrorists decided to move on the Darknet to make the Daesh more resilient to take over attempts.
“Terban came across the new Al-Hayat hub while performing jihadi research over the weekend.” states Salted HASH. “In a post on the Shamikh forum (a known jihadi bulletin board), someone posted the new address and instructions for reaching it.”
The new website includes a collection of propaganda video and images produced by Al-Hayat Media Center, the media division of Daesh. It is known to the intelligence because it is used to spread content glorifying the jihad against the infidel West, including poems for mujahids and songs (Nasheeds).
In the past, Daesh already had propaganda and recruitment hubs on the Darknet, but as explained by the expert it is the first time ever it published proof of those claims.
Terban has mirrored the website and its files, the intention of the expert is to analyze them and publish more details in the coming days. The site is a mine of information , it includes data from various sources, including standard bulletin boards used by the ISIS terrorists.
“The site mirrors many of the other standard bulletin boards that the jihadi’s have had over the years replete with videos and sections in all languages. Given that this site has popped up today in the Darknet just post the attacks in Paris, one has to assume that an all out media blitz is spinning up by Al-Hayat to capitalize on the situation,” Terban wrote.
The new Daesh hub demonstrates that even if the ISIS is aware of the Internet surveillance of western government, it considers the use of technology as strategical.
The Dark Web is a privileged environment for cyber criminals and state-sponsored hackers due to the anonymity offered by its services. The Dark Web is difficult to monitor for intelligence agencies and it is not so easy to locate members of terrorist organizations like the ISIS that share propaganda content. In the principal black markets hosted on the deep web it is possible to purchase any kind of illegal product and service, but in the dark part of the web it is possible to find propaganda videos and images. Hidden services in the Deep Web also offer the possibility to download the mobile apps used by the jihadists to communicate securely and to transfer Bitcoins to terrorist cells in every place of the world.
The new Daesh hub also suggests ISIS sympathizer the use of Telegram, a secret encrypted messaging platform that is largely adopted by terrorists.
Telegram is “A Secret Chat is a one-on-one chat wherein all messages are encrypted with a key held only by the chat’s participants.” It is an essential tool for all the individuals that need to protect their communication from prying eyes.
Telegram’s Channels used by the terrorists allow them to reach tens of thousand followers instantly.
Beaches, carnivals and cybercrime: a look inside the Brazilian underground
15.11.2015 Zdroj: Kaspersky
The Brazilian criminal underground includes some of the world’s most active and creative perpetrators of cybercrime. Like their counterparts in China and Russia, their cyberattacks have a strong local flavor. To fully understand them you need spend time in the country and understand its language and culture.
The Brazilian underground generates quite a lot of cyberthreats – mainly banking Trojans and phishing campaigns. These attacks can be quite creative and are designed to reflect the local landscape. In 2014, Brazil was ranked the most dangerous country for financial attacks, and the Brazilian banking Trojan, the ChePro family, was ranked the second most widespread Trojan after ZeuS.

Countries most affected by banking Trojans in 2014
The picture for phishing attacks is not that different, with Brazil also ranked in first place worldwide. Not surprisingly, quite a number of the brands and companies that feature in the most frequently attacked list are Brazilian.
Beaches, carnivals and cybercrime: a look inside the Brazilian underground

Countries most attacked by phishing attacks in 2014
Brazilian cybercriminals are adopting techniques that they have imported from Eastern Europe, inserting it into local malware to launch a series of geo-distributed attacks. These can include massive attacks against ISPs and modems and network devices or against popular, nationwide payment systems such as Boletos.
To understand what is going on in the Brazilian cybercriminal underground, we would like to take you on a journey into their world, to explore their attack strategy and their state of mind. We will look at the underworld market for stolen credit cards and personal data, the new techniques used in local malware and the ways in which they are cooperating with criminal in other countries.
For many people, Brazil is a country famous for its culture, beaches, samba and carnivals. For security professionals, it is equally renown as a prominent source of Banking Trojans.
Like Bonnie and Clyde: living the crazy life
The first impression you get is that Brazilian criminals like to flaunt how much money they have stolen and the high life they lead as a result of this. They compare themselves to Robin Hood: stealing from the ‘rich’ (in their eyes the banks, the financial systems and the government), in favor of the ‘poor’ (themselves). This is a widely-held conviction: they don’t regard themselves as stealing from individuals who bank online, but from the banks, since, according to local laws financial institutions are obliged to reimburse the victim for any money lost through theft.
There is a widespread sense of impunity, especially because, until recently cyber-crime was not legally defined as criminal activity under Brazilian law. The Carolina Dieckman law (named after a famous actress whose nude pictures were stolen from her computer) was approved in 2013, but the law is not very effective in punishing cybercriminals as the penalties are too lenient and the judicial system is very slow. It is very common for attackers to be arrested three or four times only to be released again without charge. The lack of effective legislation to combat cybercrime and high levels of police corruption provide the icing on the cake.
A strong indicator of just how immune to prosecution the cyber-criminals feel can be seen in the fact that it’s very easy to find videos and pictures of them online or to access their profiles on social networking sites. Invariably, they can be seen flaunting what appears to be stolen money, celebrating the high life, paying for prostitutes in Rio during the carnival, and more.

Brazil has achieved worldwide notoriety as a place where many ‘Bonnie and Clyde’ types are living decadent lives. How much do they steal? Quite a lot. According to the Brazilian Federation of Banks (FEBRABAN), in 2012 local banks lost 1.4 billion of reais (around US$500 million) paying for fraud perpetrated via Internet banking, by telephone, or through credit card cloning.
The target audience for cybercrime in Brazil is significant: the country has more than 100 million Internet users, 141 million citizens eligible to use Brazil’s e-voting system and more than 50 million people who use Internet banking services daily.
There are online videos celebrating the criminal life, like this song, the “Hacker’s Rap”. The lyrics celebrate the life of the criminals who use their knowledge to steal bank accounts and passwords:
The lyrics say: “I’m a virtual terrorist, a criminal; on the internet I spread terror, have nervous fingers; I’ll invade your PC, so heads up; you lose ‘playboy’, now your passwords are mine”.
Card-skimmers also celebrate and flaunt their profits in the “Cloned credit card rap”, also available on Youtube:
The lyrics include the words: “You work or you steal, we cloned the cards, I’m a 171, a professional fraudster and cloner, we steal from the rich, like Robin Hood, I’m a Raul…”
Recently the Brazilian Federal Police arrested the owner of a three million reais luxury mansion bought with funds stolen using Boleto malware. In Brazil, cybercrime pays, and pays very well.
C2C: Cybercrime to Cybercrime
As is the case with other underground fraternities, Brazilian cybercriminals are organized in small or medium-sized groups, each with their own expertise, selling their services to each other or working together. ‘Independent’ criminals are also common, but in general, most need to collaborate to do business.
The most common channels used by the Brazilian underworld to negotiate, buy and sell services or malware are Internet Relay Chat (IRC) channels. Some of them also use social networks such as Twitter and Facebook, but most of the juicy content is hidden inside IRC channels and closed forums that you can only join by invitation or with endorsement from an existing member. In these IRC chats criminals exchange data about attacks, hire out services among themselves, and sell personal data from hacked websites, while coders sell their malware and spammers sell their databases and services. These are true C2C (Cybercrime to Cybercrime) operations. The two most popular IRC networks used for such activity are FullNetwork and SilverLords.
However, a very common problem among the criminal fraternity is what it calls “calote” or deadbeats – those people who steal from the thieves, who buy criminal services or software underground without paying the seller. Revenge is taken quickly and in one of two ways. Firstly, the bad player may be “doxed”: their real identity published with the aim of alerting Law Enforcement. Secondly, they may find their name added to a big reputation database of bad and good debtors. This ‘black’ and ‘white’ list enables the ‘community’ to protect itself by checking out the reputation of a customer before doing business with them.

An underground reputation system from Fullnetwork.org: protection against deadbeats
“Doxing” and other attacks on competing gangs are common among the Brazilian underground – some groups even celebrate the arrest of other cyber-crooks. That’s what happened with Alexandre Pereira Barros, responsible for the SilverLords network. He and three other cybercriminals were arrested by the Brazilian Federal Police in April 2013 after a series of fraud attacks against financial systems, credit card cloning, hacktivism attacks, and more. The group owned a lottery retailer in the state of Goias, responsible for theft of $250.000. To ‘celebrate’ their arrest, other criminals posted a video on Youtube, in revenge for unpaid debts:

Brazilian cybercriminals arrested in 2013 – unfortunately, they did not end up in jail after all
A typical Brazilian cybercrime group include four or five members, but some groups can be bigger than that. Each member has their own role. The main character in this scenario is the “coder”, the person responsible for developing the malware, buying exploits, creating a quality assurance system for the malware and building a statistical system that will be used by the group to count victims; and then putting everything in a package that can be easily negotiated and used by other criminals. Some coders don’t limit themselves to a single group and may work with several, and most prefer to not get their hands dirty with any stolen money. Their earnings come from selling their creations to other criminals. A coder could be a leader of a group, but this is not common. They are rarely arrested.
Every group has one or two spammers, responsible for buying mailing lists, buying VPSs and designing the “engenharia” (the social engineering used in the mail messages sent to the victims). Their role also involves spreading the infection as widely as possible. It´s common to find spammers with experience in the defacement of web servers that then allow them to insert a malicious iframe into infected websites. Spammers don’t have a fixed salary: their earnings come from the number of people infected. That is why the coder needs to build a victim-counter into the malware, as this information is used to calculate how much the spammer will receive.
The group also has a recruiter, responsible for hiring the money mules (also known as “laranjas”). This is a very important task because this person will be in direct contact with people or hold responsibility for external activities, such as for coordinating the things necessary for transferring the money or withdrawing it from ATMs, paying the bills (generally at a lottery house) or receiving the products bought online with the stolen credit cards – do the “correria” (foray). It´s common for the people in this role to recruit their own family members to work as money mules, as they can earn up to 30% of the sums stolen and distributed among the money mule accounts. Generally, the money mules are the first to be arrested in police operations, followed by the recruiter.
The real leader of the group is responsible for coordinating the other members and all the activites, negotiating new “KLs” (keyloggers) with a coder, requesting a new “engenharia” from the spammers, or do the “correria” with recruiters. They are also responsible for recruiting new members to the group and negotiating their wares in with other criminal groups. Roles are not fixed; some members may perform a number of functions and work with more than one group, and their earnings may vary. Some criminals prefer to work independently, selling their services and goodies to several groups.
And some criminals have opened web stores to sell their goods and promote their services in a better and more user-friendly way. In these stores one can buy cryptors, hosting services, coding services for new Trojans, etc. That was the purpose of the “BlackStore” (now offline). Let’s check the prices of their ‘goodies’:
| A “crypter” 100% undetected, R$ 100 (U$ 30.00)
|
| Hosting: US$17
|
| Coding services: US$170 |
| Tester of stolen credit cards: US$130
Check out the pictures of the application on our database!” |
| DNS Network US$1500
|
| Malicious Java applet: US$25
|
| Viral Facebook: US$20 |
| VPS Spam sender: US$20
|
| SPAM PHP system: US$10
|
| KL (Keylogger): US$ 300 Targeted banks:
|
As a “professional” store, they also offer a receipt for your purchases:

Honest thieves: proof of your underground purchases
The professionalization of organized cybercrime, as observed in Eastern Europe, is now adopted by the Brazilian crime underground. Investment in technology and marketing is aimed at increasing their profits. In some closed forums criminals have even started advertising their services in a clear attempt to attract newcomers not used to developing their own tools:

The text says: “Buying any social engineering kit you also earn kits for banker, credit card and frequent flyer miles. 1 million free spam messages, from Bruno Dias smart solutions”. Other services that are increasingly offered include websites offering “malware as service”, cryptors, FUDs (fully undetected malware) and a complete system to manage information about stolen banking accounts:

“FUD as a service”, encryption service for already detected trojans
An “admin panel” manages the complete system that allow attackers to control infected machines, collect banking data, and bypass two-factor authentication (2FA) in any form (SMS, token, OTPs (one-time password cards) and more). Some systems also allow for the control of websites and domains used to spread the malware and to send spam and manage mail lists, all in a single solution.

Remote access tool sold on the underground intended to bypass the 2FA of Brazilian banks
The goods on offer also include DDoS attacks. Using the power of thousands of infected computers it’s not difficult to perform a distributed denial of service for other criminals, using SYN flood, amplified UDP, and more. The prices are listed below: 300 seconds: $8.3; 450 seconds: $13; 1000 seconds: $28; 3600 seconds: $40.

DDoS for hire: takedown your target paying by seconds of attacks
How much does your credit card cost?
Credit card dumps are among the most valuable data exchanged among criminals. These have often been cloned in different ways, including chupa cabras (skimmers) on ATMs and point-of-sale terminals, phishing pages, keyloggers installed on victims’ PCs, and more.
Brazil has one of the highest concentrations of ATM terminals, according to the World Bank. There are more than 160,000 opportunities for fraudsters to install a skimmer (also known as a “Chupa Cabra device”), and they do this all the time. Even during the day you can see them hanging about, wearing flip-flops and beachwear and in a very relaxed mood, installing skimmers in a crowded bank:
When it comes to credit card cloning, Brazil has some of the most creative and active criminals. Fortunately, most of the cards in use have CHIP and PIN technology built in. Despite recent news revealing some security flaws in this protocol, CHIP and PIN cards are still more secure and harder to clone than magnetic swipe cards. Because these EMV chips are used all over the country, most of the cloning activity happens online, using phishing attacks, fake bank pages, fake giveaways and compromised e-commerce portals, offering an expensive product for very attractive price. If you are engaged in any type of online business, sooner or later your card will be attacked: via phishing or through compromise of the e-commerce portal.
These highly sought-after dumps are sold online through specialized websites or even through IRC channels. And it’s not just carders and cybercriminals who are involved in this underground business, but many ‘traditional’ criminals connected to drug trafficking and other illegal activities.
The price of a cloned credit card depends in the bank, the country of origin, etc.
Infinity: flags such as American Express or international cards are sold at $42 apiece
Platinum: cards from multinational banks, $40 apiece
Black: cards by $30 apiece
Gold/ Premier: $25 apiece
Classic: from national banks, $22 apiece
Ad of a criminal selling dumps of stolen credit cards: you can even pay for it with your own credit card
Data breach incidents fueling cyberattacks
The Brazilian underground is hungry for personal data – and this allows cybercriminals to monetize identity theft, offering opportunities to buy products using “laranjas” or money mules, or even collect this data to empty your bank account, as several online services ask for personal data to confirm a customer’s identity.
Unfortunately, the country does not yet have specific laws in place to protect personal data – at this time politicians are still evaluating their options. As a result, data breaches in government organizations and private companies are widespread. Affected businesses currently are not obligated by law to contact customers affected by the breach or even to inform them that an incident has taken place.
Recently, we observed some very serious data breach incidents affecting major websites, and involving databases from the government, Receita Federal (IRS) and other institutions. It is common to find leaked databases being sold underground, such as the database of DETRAN (Traffic Department), with data on five million citizens costing only US$50:

Flaws on government websites are critical. In 2011 two very serious flaws in the Labor Ministry website exposed an entire database with six months’ worth of data on every citizen in the country. A flaw in the website’s security left sensitive data out in the open, with only a CPF number (Brazilian SSN) required to obtain further information about a person.

The CPF is one of the most important documents for anyone living in Brazil. The number is unique and is a prerequisite for a series of tasks like opening bank accounts, to get or renew a driver’s license, buy or sell real estate, obtain loans, apply for a jobs (especially in the public sector), and to get a passport or credit cards. Leaked data makes it possible for a cybercriminal to impersonate the victim and to steal their identity in order to, for example, get a loan from a bank.
This is a case of where a data leak meets the phishers. Information of such quality can only be obtained through data leak incidents. Not surprisingly, it is common for the Brazilian media to spot criminals selling CDs carrying data from the Brazilian IRS system which includes a lot of sensitive data, including the CPF numbers. You can find criminals selling CDs full of leaked database from several sources for a mere $100. As a result of such data breaches, Brazilian phishers have created attacks with messages displaying the complete name and the CPF number of the victim in an attempt to add legitimacy to a fake message. Attacks such this one have happened regularly since 2011:

A phishing message displaying the complete name of the victim and their CPF number
The abundance of personal data leaked from several sources has allowed Brazilian criminals to establish online services offering a searchable database with personal data from millions of citizens. Despite the efforts of the authorities to take down such websites, new services are created every month.

Having the CPF number is enough to find all your personal data
The problem of data brokers
Another problem related to the bad management of personal data is “Data brokers”, companies that collect information and then sell it on to companies that use it to target advertising and marketing at specific groups; or to verify a person’s identity for the purpose of fraud detection; or to sell to individuals and organizations so they can research particular individuals.
Local companies such as Serasa (now acquired by Experian) are a common target of phishers and malware authors. As they offer the biggest database in the country regarding fraud protection, and carry a complete profile of personal data for every citizen, the stolen credentials to access this database are valuable among fraudsters.
So, not surprisingly many fraudsters resell the results of their access to data broker services using stolen customer credentials, in packs that cost US$30 per 15 days or US$50 for 30 days of full access:

Other criminals go further, and build their own data broker services. Owners of these services market them to other fraudsters, offering a comprehensive package to search databases leaked from the government as well as those obtained from private sources. Such widespread activity gives the impression that in Brazil cybercrime will always be able to reach you, one way or another.

Govern and Data broker’s database together in the same underground service
To advertise their services, fraudsters use all channels, even social networks like Facebook. In a dossier published by Tecmundo they found evidence of public employees involved in the scheme, selling databases and credentials.

Access to stolen data service advertised on Facebook
How phishing attack compromised the Amazon forest
Could you imagine a phishing attack compromising the biggest rainforest in the world? That is what happened with IBAMA, the Brazilian Institute of Environment and Renewable Natural Resources. IBAMA is responsible for limiting the cutting of hardwood trees in the Amazon region, ensuring that only authorized companies are able to do that.
In a series of attacks against IBAMA’s employees (probably using phishing emails like the one below), Brazilian criminals were able to steal credentials and break into IBAMA’s online system. Then they unlocked 23 companies previously suspended for environmental crimes, allowing them to resume extracting wood from the forest. In just 10 days these companies extracted $11million in wood. The number of trees cut illegally was enough to fill 1,400 trucks.

Phishing page of IBAMA: to steal credentials and cut woods in the forest
Underground cooperation with Eastern Europe
We have sufficient evidence that Brazilian criminals are cooperating with the Eastern European gangs involved with ZeuS, SpyEye and other banking Trojans created in the region. This collaboration directly affects the quality and threat-level of local Brazilian malware, as its authors are adding new techniques to their creations.
It’s not unusual to find Brazilian criminals on Russian underground forums looking for samples, buying new crimeware and ATM/PoS malware, or negotiating and offering their services. The first result of this cooperation can be seen in the development of new attacks such the one affecting Boletos payments in Brazil.

Brazilian bad guy writing in (very bad) Russian, selling access to 400 infected PoS devices
They have also started to use the infrastructure of Eastern European criminals, sometimes buying bulletproof hosting or renting it. “João de Santo Cristo” (a fictional character that appears in a popular Brazilian tune) was one of them, buying and hosting 14 Boleto malware domains in Russia:

Not surprisingly we have started to see Russian websites hacked into and hosting fake Boleto websites:

These facts show how Brazilian cybercriminals are adopting new techniques as a result of collaboration with their European counterparts. We believe this is only the tip of the iceberg, as this kind of exchange tends to increase over the years as Brazilian crime develops and looks for new ways to attack businesses and regular people.
Advances in local malware
The contact with Eastern European cybercrime affects the quality of Brazilian malware. For example, we found in Boleto malware exactly the same encryption scheme that is used in payloads by ZeuS Gameover.

Encrypted payload of Boleto malware: the same encryption used by ZeuS
We also saw, for the first time, Brazilian malware using DGA (Domain Generation Algorithm). Trojan-Downloader.Win32.Crishi was one of them, distributed in messages like this one:

Further evidence of advances in Brazilian malware due to the cooperation with Eastern European criminals can be seen in the use of fast flux domains in Boleto attacks.
Conclusion
Brazil is one of the most dynamic and challenging markets in the world due to its particular characteristics and its important position in Latin America. The constant monitoring of Brazilian cybercriminals’ malicious activities provides IT security companies with a good opportunity to discover new attacks related to financial malware. In some cases these attacks are very unique as happened with the usage of malicious PAC files.

Message from bad guys in a malicious PAC file to yours truly: reaction due a good detection
To have a complete understanding of the Brazilian cybercrime scene, antimalware companies need to pay close attention to the reality of the country, collect files locally, build local honeypots, and retain local analysts to monitor the attacks, mostly because it’s common for criminals to restrict the reach of the infection and distribution of their creations to Brazilian users. As happens in Russia and China, Brazilian criminals have created their own, unique reality that’s very hard to understand from the outside.
Did terrorists use PlayStation 4 for communications in Paris attacks?
15.11.2015
Rumors circulating on the Internet sustain that terrorists behind the Paris attacks have used PlayStation 4 for their communications.
The Paris attacks have shocked the world, the ruthless terrorists of the ISIS killed defenseless people. The days after atrocity law enforcement are conducting an investigation on a large range to identify the logistic base of the group and the network of ISIS members that supported the men involved in the Paris attacks.
The roots of the Paris Attacks lie partly in Syria and Iraq, but we investigators have no doubt, they have deep ramifications in the principal European cities.
At the time I’m writing, 3 people suspected of having links with Paris Attacks have been arrested in Belgium, the countries that intelligence agencies consider the lair from which they started terrorists ISIS.
The ISIS has brought the terror in our cities, for the first time a group of terrorist has men, resources and money to proclaim itself a state.
The Paris attacks demonstrate the ISIS had high-level logistical organization, they coordinated such a mass terrorist attack avoiding being detected by the intelligence, despite the level of alert was high due to the alleged terrorist attack in Sinai and the tragedy of the Charlie Hebdo.
Such kind of attack needs a significant effort in communicating among members which remained hidden from the law enforcement and intelligence agencies despite the numerous surveillance programs of many governments.
Authorities are monitoring in every instant the communications, even messages exchanged over the Internet and probably among ISIS members crowding the Deep Web.
New of the last hours is that the IS terrorists involved in the Paris attacks may have used the most popular Sony PlayStation 4 gaming console as the platform to exchange messages.
A raid in nearby Brussels provided evidence that terrorists were using at least one PlayStation 4 console.
The Belgian federal home affairs minister Jan Jambon explained that the PS4 is used by ISIS members for their communications.
The choice is not casual, despite the effort of the intelligence agencies in monitoring communications over Gaming console, the ISIS members were aware of the difficulties to conduct a large-scale surveillance on the PlayStation 4 channels.
“The thing that keeps me awake at night is the guy behind his computer, looking for messages from [the Islamic State]and other hate preachers,” Jambon said last Friday, according to Brussels weekly, the Bulletin. “PlayStation 4 is even more difficult to keep track of than WhatsApp.”
ISIS Paris attacks PlayStation 4
The PlayStation’s IP-based voice systems are difficult to monitor and terrorists could send messages to each other within PlayStation games without speaking or typing a word.
At the time I’m writing there is no certainly, the investigators have no clear idea about a possible use of the Sony Play Station 4, anyway we cannot underestimate this option in the hand of terrorists that have significant technological abilities. A few days ago the popular Cyber security expert Mikko Hypponen, Chief Research Officer for F-Secure, said he worries about cyber extremists that could penetrate critical infrastructure and cause serious damages. The expert explained that the ISIS is probably the first group of terrorist that has hacking capabilities to manage a major attack against a government infrastructure, and the situation is getting worse because this group is gaining greater awareness of the effectiveness of an offensive launched by the cyberspace.
We have already discussed in the past the possibility that terrorist groups could exploit gaming console for internal communications. In 2013, I published a post describing the activities of the NSA and the British GCHQ to infiltrate the virtual world of online games considered as an attractive environment for cyber terrorists and hackers.
The Guardian published documents leaked by Snowden on the surveillance program in partnership with the New York Times and ProPublica, according the files the intelligence agencies have operated in virtual worlds and gaming communities to conduct intelligence operation and try to recruit informants.
Last documents published by the Guardian titled “Exploiting Terrorist Use of Games & Virtual Environments” are dated 2008 and remarked the necessity to monitor online gaming communities describing them as a “target-rich communications network” where intelligence targets could “hide in plain sight”.
The documents just provide a warning on the possible abuse of online gaming communities, but don’t contain an indication on real case discovered by the intelligence agencies.
The Secret Services have infiltrated the principal online game communities including Second Life to monitor users’ habits and snoop their communications, NSA and GCHQ have created human avatars to explore virtual reality and prevent terrorist initiatives.
Yes, but at that time there was no automatic system to monitor such kind of communication, what about today abilities?
Paris attacks must lead us to reflect seriously on the subject, the ISIS has skills and resources and it is not surprising that its members can exploit gaming console as communication channels.
Russia has a new anti wiretapping System
15.11.2015
A Russian manufacturer has built an advanced system for the protection of any channels of telephone communication against wiretapping.
The Russian Government has a new system for the protection of communication channels against the wiretapping, the news was disclosed by the director general of the Interstate Corporation of Development (ICD), Ivan Polyakov, and it was reported by the Russian News agency Tass.
The protection of telephone communication against wiretapping is strategic for any governments, the new system protecting any channels of telephone communication against espionage activities has been designed by a Russian manufacturer.
“The solution has been found that makes it possible to guarantee confidentiality of conversations irrespective of what systems and standards of communications you use,” Polyakov said.
“This is a very interesting solution, we believe it will be in demand on the market,” he said without providing further details on the solution.
surveillance wiretapping
The Russian authorities decided to develop a system for the protection of communication channels because the solution available on the don’t match the requirements of the Government.
“The options existing on the market could not satisfy us as a corporation. That is why we started with ourselves, and then decided to offer the product to the market,” he added.
Polyakov explained that components for the protection system were designed and produced directly at enterprises of the ICD.
As reported in the official website of the ICD, the purpose of Corporation establishment is the development of scientific, industrial and high-tech cooperation in Collective Security Treaty Organization (CSTO) countries.
The ICD was established on January 15, 2011, its is considered of the biggest Russian designers and producers of solution that could protect communication systems.
The Collective Security Treaty Organization is an military alliance, acting as counterpart to the NATO alliance, which was signed on 15 May 1992 and that includes Armenia, Belarus, Kazakhstan, Kyrgyzstan, Russia, Tajikistan and Uzbekistan.
Flaw in the Android Gmail app opens to email spoofing attacks
14.11.2015
A security loophole in the official Gmail Android app opens the email spoofing attacks allowing anyone to change the sender email name.
The independent security researcher Yan Zhu has discovered a serious security issue in the Gmail Android app allows ill-intentioned to send an email pretending to be someone else. Clearly a similar loophole could represent a gift for phishers and scammers, the issue dubbed Email Spoofing, enable the forgery of an e-mail header so that the email appears to have originated from someone else than the legitimate sender.
In a classic email spoofing attack, threat actors need an SMTP (Simple Mail Transfer Protocol) server to send the email and a mailing application.
The researchers Yan Zhu, discovered a flaw in the Gmail Android app that allowed her to change her display name in the account settings so that the final recipient will not be able to know the identity of the email sender.
Zhu provided a PoC of her attack by sending an email to someone by changing her display name to yan “”security@google.com,” as it visible in the following image.
“[This] extra quotes [in the display name] triggers a parsing bug in the Gmail app, which causes the real email to be invisible,” Zhu told Motherboard. “It’s always been possible to spoof email envelope addresses, but spoofed emails now usually get caught by spam filters or get displayed with a warning in Gmail, With this bug, a hacker can get around these protections.”
Wait! Now is arriving the interesting part of the story.
Zhu reported the issue to the Google Security team at the end of October, but unfortunately the experts rejected the bug report saying it is not a security vulnerability.
“Thanks for your note, we do not consider this [bug] to be a security vulnerability,” a Google Security Team member told Zhu.
“Filed a Gmail Android bug that lets me fake sender email address. [Google] said it’s not a security issue. ¯\_(ツ)_/¯.” Zhu tweeted.
You got it right! The security team of Google does not consider a security issue the e-mail spoofing.
Users that want to protect themselves from email spoofing attacks can read the following suggestions:
Enable antispam feature provided by your email service.
Analyze the Email message headers and search for the legitimate IP addresses of the sender. Every time you suspect an email spoofing give a look to the header and search for the real source.
Never Click on a Suspicious Link or open suspicious attachment. Be aware of any unsolicited email.
Keep your PC’s Antimalware Up-to-Date.
Bug in Gmail app for Android Allows anyone to Send Spoofed Emails
14.11.2015
A security researcher has discovered an interesting loophole in Gmail Android app that lets anyone send an email that looks like it was sent by someone else, potentially opening doors for Phishers.
This is something that we call E-mail Spoofing – the forgery of an e-mail header so that the email appears to have originated from someone other than the actual source.
Generally, to spoof email addresses, an attacker needs:
A working SMTP (Simple Mail Transfer Protocol) server to send email
A Mailing Software
However, an independent security researcher, Yan Zhu, discovered a similar bug in official Gmail Android app that allowed her to hide her real email address and change her display name in the account settings so that the receiver will not be able to know the actual sender.
How to Send Spoofed Emails via Gmail Android App?
To demonstrate her finding, Zhu sent an email to someone by changing her display name to yan ""security@google.com" (with an additional quote). You can see the below screenshot posted by Zhu on her Twitter timeline.
"[This] extra quotes [in the display name] triggers a parsing bug in the Gmail app, which causes the real email to be invisible," Zhu told Motherboard.
Gmail Android App Bug Allows anyone to Send Spoofed Emails
Once received, the email address could trick the receiver into believing that the mail has arrived from a legitimate Gmail security team, which is not.
Google – 'The Bug isn't a Security Vulnerability'
Zhu reported the loophole to Google's Security team at the end of October, but the team disapproved her bug report, saying the bug is not a security vulnerability.
"Thanks for your note, we do not consider this [bug] to be a security vulnerability," a Google Security Team member told Zhu.
"Filed a Gmail Android bug that lets me fake sender email address. [Google] said it's not a security issue. ¯\_(ツ)_/¯." Zhu tweeted.
Email spoofing can be used legitimately, but because spoofing an email address is surprisingly easy, spammers and phishers take advantage of it to harm people or organisation.
Here's How to Protect Yourself from Spoofed Emails
So, if you want to protect yourself from spoof messages, you can follow the given couple of things:
Turn on your Spam Filters – Almost every email service offers spam filters and junk boxes that dump spoof emails to your junk mail.
Learn to Read Email message headers, and Trace IP addresses – Tracking down the source of spam is a good practice. When you receive a suspicious email, open the header, and see if the IP address of the sender matches up with previous emails from the same person.
Never Click on a Suspicious Link or Download an Unfamiliar Attachment – Always pay attention to the emails you receive and avoid clicking links in email or downloading email attachments. Go to your bank's official website, or other websites directly from the browser and log into your account to find what they want you to see.
Keep your PC's Antimalware Up-to-Date.
FBI denies paying $1 MILLION to Unmask Tor Users
14.11.2015
Just day before yesterday, the Tor Project Director Roger Dingledine accused the FBI of paying the Carnegie Mellon University (CMU) at least $1 Million to disclose the technique they had discovered to unmask Tor users and reveal their IP addresses.
However, the Federal Bureau of Investigation has denied the claims.
In a statement, the FBI spokeswoman said, "The allegation that we paid [CMU] $1 Million to hack into Tor is inaccurate."
The Tor Project team discovered more than hundred new Tor relays that modified Tor protocol headers to track online people who were looking for Hidden Services, and the team believes that it belongs to the FBI in order to reveal the identity of Tor-masked IP addresses.
One such IP address belongs to Brian Richard Farrell, an alleged Silk Road 2 lieutenant who was arrested in January 2014.
The attack on Tor reportedly began in February 2014 and ran until July 2014, when the Tor Project discovered the flaw. Within few days, the team patched the vulnerability and updated its software, thereby rolling out new versions of code to block similar attacks in the future.
This week, Motherboard reviewed a new court filing in Farrell's case that proved the FBI had indeed recruited a "university-based research institute" to uncover the identity of Farrell by running systems on the Tor network.
The FBI spokeswoman didn't provide any further statement on the Tor Project claims, and it's still unclear which part of the FBI's statement is inaccurate – The Payment Amount or The FBI's Involvement Entirely.
What do you think? Hit the comments below.
You can buy a Cryptolocker/Cryptowall Ransomware Kit for $3,000
14.11.2015
Experts at BitDefender have discovered a Cryptolocker/Cryptowall Ransomware Kit offered for sale at $3,000, source code included.
Yesterday I wrote about a new Ransomware-as-a-service, the FAKBEN, surfaced from the criminal underground, requesting customers 10 percent profit cut. In the previous days I reported other cases involving ransomware, such as a malicious code that infected the UK Parliament, an off-line ransomware and a Linux.Encoder1 ransomware revealing the decryption key.
The cybercrime is looking with increasing interest to ransomware, today I want to write about the availability of the source code of Cryptolocker/Cryptowall in the underground.
According to Bitdefender, a Cryptolocker/Cryptowall Ransomware Kit is offered for sale for $3,000, including its source code.
The experts consider this offer for the Cryptolocker/Cryptowall Ransomware Kit not that expensive for the features it implements. We have seen that the return on investment for ransomware like Cryptowall could be very high.
Security researchers of the Cyber Threat Alliance have conducted an investigation into the cybercriminal operations leveraging CryptoWall 3.0 ransomware.
A Pastebin post also claims that the manual and free support is included along with Cryptolocker/Cryptowall Ransomware Kit source code, of course, buyers can pay it in Bitcoin.

The sellers also offer for sale ransomware binaries, a bundle of 8 goes for $400. However, the developer is opening to various models of sales, including the affiliate program in which he would share 50/50 the revenue with potential buyers.
“This is your chance to become a partner and join or buy build individual to you and use and to generate income and to convert and monetization,” reads the post. “If you are interested then contact i need a partnership and also iselling build to you.”
This is one of the few times when we can take a look at how the underground market works, the types of services offered, and maybe estimate the amount of money made from selling custom-made malware.

Cryptolocker/Cryptowall Ransomware Kit Sold for $3,000 - Source Code Included
Liviu Arsene, Security Researcher at Bitdefender, explained that buyers of Cryptolocker/Cryptowall Ransomware Kit will allegedly not only gain access to full support but paying an additional fee they fully customize their ransomware.
“Those who actually want to purchase the Cryptolocker/Cryptowall Ransomware Kit will allegedly not only gain access to full support, but can also ask for additional modules or customizations, such as preferred language interfaces for the access panel or custom deployments on VPS servers.” said Arsene.
Below the information provided by the seller, including the list of features implemented in the Cryptolocker/Cryptowall Ransomware Kit. It is interesting to note that the developer claims the ability of its ransomware of communicating with Command and Control servers over Tor without losing any connections, a unique technique that will only be disclosed once contacting support.
“Information for customers:
JID: whiterocks@richim.org
Price of binary: $400 (8/1 customers)
Price of source code and manual how edit code wallet btc i give you: $3000 (1 customer)
You keep 100% of payments
Free recompiles and support
Escrow accepted
Bitcoin (BTC) only!”
“Features:
Encryption algoritm BlowFish 448 bit (stronger then AES).
448 bit key is generated on computer and sent to C&C. Each computer generates unique key. Key is not stored on computer and is purged from RAM.
All C&C decryption keys are encrypted with the RSA-alg (1024 or 2048 Bit Keys). The Password used to decrypt the private key is not stored and only temporary used(conclusion: even if the server is raided or compromised the User-Passwords cannot be decrypted).
Locker can communicate with C&C over Tor, without losing any connections (contact support for more information – we are using a different technique).
Files in all locations (external media and network) are encrypted.
Encrypted extensions: odt, ods, odp, odm, odc, odb, doc, docx, docm, wps, xls, xlsx, xlsm, xlsb, xlk, ppt, pptx, pptm, mdb, accdb, pst, dwg, xf, dxg, wpd, rtf, wb2, mdf, dbf, psd, pdd, pdf, eps, ai, indd, cdr, jpg, jpe, dng, 3fr, arw, srf, sr2, bay, crw, cr2, dcr, kdc, erf, mef, mrwref, nrw, orf, raf, raw, rwl, rw2, r3d, ptx, pef, srw, x3f, der, cer, crt, pem, pfx, p12, p7b, p7c, c, cpp, txt, jpeg, png, gif, mp3, html, css, js, sql, mp4, flv, m3u, py, desc, con, htm, bin, wotreplay, unity3d , big, pak, rgss3a, epk , bik , slm , lbf, sav , lng ttarch2 , mpq, re4, apk, bsa , cab, ltx , forge ,asset , litemod, iwi, das , upk, bar, hkx, rofl, DayZProfile, db0, mpqge, vfs0 , mcmeta , m2, lrf , vpp_pc , ff , cfr, snx, lvl , arch00, ntl, fsh, w3x, rim ,psk , tor, vpk , iwd, kf, mlx, fpk , dazip, vtf, 001, esm , blob , dmp, layout, menu, ncf, sid, sis, ztmp, vdf, mcgame, fos, sb, itm , wmo , itm, map, wmo, sb, svg, cas, gho,iso ,rar, syncdb ,mdbackup , hkdb , hplg, hvpl, icxs, itdb, itl, mddata, sidd, sidn, bkf , qic, bkp , bc7 , bc6 ,pkpass, tax, gdb, qdf, t12,t13, ibank, sum, sie, sc2save ,d3dbsp, wmv, avi, wma, m4a, 7z, torrent, csv
AV software cannot decrypt files (Panda Ransomware Decrypt Tool, BitDefender Decrypt, Kaspersky).
Secure file erase (7 passes).
Message is displayed on GUI and inside of .txt files created in all folders. This message is configured on C&C, unique by country.
Compatible with crypters (no EOF).
Empty recycle bin (all drives).”
Unfortunately is even simpler for wannabe cyber criminals to arrange a ransomware campaign, they don’t need specific technical know-how to start developing and spreading their custom malware.
Chrome exploit leaves million Android devices open to attack
14.11.2015
At the MobilePwn2Own, a Chinese expert has demonstrated how to hijack an Android smartphone by exploiting a zero-day flaw in the Chrome browser.
The Chinese expert Guang Gong from Qihoo 360 has demonstrated how to hijack an Android smartphone by exploiting a flaw in the Chrome browser. The researcher demonstrated the hack at the MobilePwn2Own at the PacSec conference in Tokyo, the compromised device was running the latest version of the Android OS and the hacker exploited a JavaScript v8 flaw through the Chrome browser.
Gong hijacked a Google Project Fi Nexus 6 running the Android 6.0 Marshmallow and with all applications up-to-date gaining complete control of the smartphone.
The JavaScript v8 flaw allowed Gong to install an arbitrary application (he installed a BMX Bike game) on the targeted smartphone without requiring any user interaction. The attacker just needs to trick victims into visiting a bogus website he set up to compromise the device.
“PacSec speaker Guang Gong from Qihoo 360 just pwned my Google Project Fi Nexus 6 (which was fresh out of the box and only updated to the latest OS and apps) by having the Chrome browser visit the web server he set up on his laptop. As soon as the phone accessed the website the JavaScript v8 vulnerability in Chrome was used to install an arbitrary application (in this case a BMX Bike game) without any user interaction to demonstrate complete control of the phone. Interestingly, this was a one shot exploit that did everything in one go instead of chaining multiple vulnerabilities.” wrote the PacSec organizer Dragos Ruiu in a post on Google+.
The vulnerability did not reside in the Android OS but affects mobile devices running on the popular OS. Ruiu added that the exploit works also on some other mobile devices because it exploits the flaw in the JavaScript engine in Chrome this mean it could potentially affect all Android versions with the latest version of the Google browser installed.
“Off line we also tested his exploit on some other phones and it looks like it works on many targets – so I guess the three months he put into developing it delivered results. Since we don’t have any lavish prizes for him, I’m bringing him to Canada next year for some skiing/snowboarding at CanSecWest.” said Ruiu.
PWN2OWN Mobile: the information about the vulnerability in JavaScript v8 in latest Chrome is being given to Chrome security engineer here
Kancelářský open space jako bezpečnostní riziko? Větší, než se zdá
14.11.2015 Hrozby
Jaké hrozby zabezpečení dat otevřený prostor přináší a jak tento problém se zabezpečením mohou bezpečnostní profesionálové vyřešit?
Stále více firem v současné době opouští tradiční rozvržení místností a uzavřených kanceláří ve prospěch otevřeného prostoru (open space). Společnosti jako Facebook nebo Google před potenciálními zaměstnanci propagují svá řešení otevřeného prostoru a vychvalují, že tyto konstrukce umožňují pracovat více pohromadě a podporují kulturu spolupráce.
Trend open space se v dohledné době nezmění: podle asociace IMFA (International Management Facility Association) nyní pracuje 70 procent zaměstnanců v USA v prostředí otevřeného prostoru.
Facebook pdole svých slov pracuje na dalším rozšíření, které navrhl Frank Gehry. Po jeho dokončení na jaře 2015 tak bude v centrále v Menlo Parku tohoto tvůrce sociální sítě největší pracoviště s otevřeným prostorem na světě.
Jedna věc je jistá – otevřený prostor se snaží najít rovnováhu mezi udržením soukromí a veřejným přístupem, a to významně mění způsob ochrany důvěrných a citlivých informací společností.
Vyvolává to ale otázku: jaké hrozby zabezpečení dat otevřený prostor přináší a jak tento problém se zabezpečením mohou bezpečnostní profesionálové vyřešit?
Hrozba vizuálního hackingu
Vizuální hacking, neboli akt sledování či zachycování citlivých, tajných a soukromých informací pro neoprávněné použití, je hlavním rizikem bezpečnosti dat v epoše otevřeného prostoru.
Se zaměstnanci, kteří pravidelně mění pracoviště, je pro dodavatele, třetí strany a dokonce pro zločinné pracovníky relativně snadné spatřit tajné informace nebo získat přihlašovací údaje k dalšímu průniku do databází společnosti z obrazovky nebo kopie souboru.
S pomůckami, jako jsou brýle Google Glass a vysoká kvalita kamer chytrých fotoaparátů, je poměrně snadné skrytě pořizovat snímky dat nebo přihlašovacích údajů.
Možná řešení: Týmy zabezpečení dat a ochrany osobních údajů by měly přezkoumat jak zásady společnosti, tak i fyzická řešení pro boj s vizuálním hackingem:
Použít ochranu před vizuálním únikem informací prakticky z každého úhlu pomocí spojení tradičních filtrů pro zachování soukromí s technologiemi jako 3M ePrivacy Filter a softwaru, který upozorní uživatele, že mu někdo hledí přes rameno, a rozmaže obrazovku, když se uživatel dívá jinam nebo odejde.
Podporovat pracovníky, aby si uvědomovali své okolí a pootáčeli si obrazovky zařízení pryč od míst s vysokým provozem.
Poučit zaměstnance, aby byly všechny počítačové monitory a displeje zařízení vypnuté a chráněné heslem, když se nepoužívají.
Zavést zásadu čistého pracovního stolu a zajistit, aby zamětnanci hned po použití odstranili všechny dokumenty obsahující důvěrné informace.
Nedostatek soukromí na hovory
Stejně jako riziko, že v otevřeném kancelářském prostoru zaměstnanci uvidí informace, které by neměli, existuje i možnost, že zaslechnou hovory, jež nejsou určené pro ně.
Možná řešení: Kromě vzdělávání zaměstnanců, jaké druhy rozhovorů by se měly vést na uzavřeném místě, mohou bezpečnostní týmy chránit soukromí hovorů pomocí následujících opatření:
Využívat technologie maskovacího zvuku, jako jsou například generátory tzv. bílého a růžového šumu, aby se přehlušily rozhovory pracovníků.
Vyčlenit prostor pro pracovníky k použití pro telefonní hovory a konverzace malých skupin.
Zavést profesionální systém rychlých zpráv, jako je například Spark, aby mohli zaměstnanci rychle získat informace, aniž by verbálně rušili ostatní.
Zvýšené riziko krádeže zařízení a dokumentů
Když společnosti používají prostředí s otevřeným prostorem, bude tam samozřejmě každý den přicházet a odcházet velké množství jedinců. I když to může přinášet užitek ohledně spolupráce v organizaci, znamená to také vyšší počet jedinců v blízkosti zařízení a dokumentů, které obsahují důvěrné informace.
Když dojde k jejich zmizení, způsobí to velké problémy se zabezpečením dat. Institut Ponemon a Intel udělaly v roce 2010 studii, která zkoumala náklady firem na ztracené nebo ukradené notebooky.
Zjistilo se, že ačkoliv se většina notebooků ztratila mimo pracoviště a při cestování, došlo u 12 procent případů ke ztrátám či krádežím přímo na pracovišti.
Možná řešení: Týmy zabezpečení by měly přijmout taková opatření, aby se zajistila nejen ochrana proti fyzickému odcizení privátních informací, ale aby v případě krádeže řešení se škoda zmírnila dalšími bezpečnostními opatřeními:
Nařiďte, aby zařízení, brašny, kufříky, složky apod., které obsahují důvěrné dokumenty, nebyly ponechávané za žádných okolností bez dozoru.
Vybavte kancelářské prostory bezpečnými zásuvkami nebo jinými místy pro ukládání, kde lze důvěrné dokumenty a zařízení uložit.
Dejte na pracoviště uzamykací kabely pro notebooky.
Vybavte všechny přístroje s přístupem k podnikovým informacím funkcemi ochrany proti krádeži, jako jsou šifrování dat a vzdálené vymazání.
Nainstalujte kamery pro sledování otevřeného pracoviště, abyste udrželi odpovědné chování zaměstnanců a v nejhorším případě abyste mohli identifikovat pracovníky nebo dodavatele, kteří by z pracoviště zařízení nebo dokumenty odnesli.
Další opatření
Ve věku pracovišť s otevřeným prostorem by měly zásady a postupy firem definovat, k jakým informacím lze přistupovat, kde a kdy, a přispět tak k ochraně před těmito novými hrozbami pro bezpečnost dat, které spolu s tímto trendem přicházejí.
Vytvoření kontinuálního plánu informování a vzdělávání zaměstnanců, který by upozorňoval na potenciální rizika zabezpečení dat, spojená s otevřeným prostorem, zase může pomoci, aby se na tuto tematiku nezapomínalo.
Další spojení s fyzickými opatřeními a softwarem může pomoci udržet ochranu pracovního prostředí. Zejména ve větších společnostech mohou pracovníci zjistit, že denně spolupracují na úkolech s různými jedinci, a je na týmech zabezpečení dat, aby zajistily, že důvěrné a citlivé informace zůstanou v tomto novém prostředí v bezpečí.
Hackers Can Remotely Record and Listen Calls from Your Samsung Galaxy Phones
13.11.2015
Hackers Can Remotely Record and Listen Calls from Your Samsung Galaxy Phones
If you own a Samsung Galaxy Phone – S6, S6 Edge or Note 4, in particular – there are chances that a skilled hacker could remotely intercept your voice calls to listen in and even record all your voice conversations.
Two security researchers, Daniel Komaromy of San Francisco and Nico Golde of Berlin, have demonstrated exactly the same during a security conference in Tokyo.
The duo demonstrated a man-in-the-middle (MITM) attack on an out-of-the-box and most updated Samsung handset that allowed them to intercept voice calls by connecting the device to fake cellular base stations.
The issue actually resides in the Samsung's baseband chip, which comes in Samsung handsets, that handles voice calls but is not directly accessible to the end user.
How to Intercept Voice Calls?
The researchers set up a bogus OpenBTS base station that nearby Samsung devices, including the latest Samsung S6 and S6 Edge, think is a legitimate cellular tower.
Once connected to it, the bogus base station remotely tinkers with the phone's baseband processor even without any knowledge of the user.
This gives an attacker ability to intercept, listen, and even record your phone calls. In short, the hack attack is a cellular MITM attack, and users have no idea what's happening
Must Read: Chrome Zero-day Exploit leaves MILLIONS of Android devices vulnerable to Remote Hacking
However, given the requirements to make such an attack possible, an everyday hacker can not be able to execute the hack.
"Our example of modifying the baseband to hijack calls is just an example," Komaromy told the Reg. "The idea with hijacking would be that you can redirect calls to a proxy and that way you can man-in-the-middle the call. So that means the caller sees her original call connected – but it can be recorded in the proxy [which is how] it is like a wiretap implant."
The pair has reported their findings to Samsung and kept the details of the attack out of the reach of the public. Hopefully, the company will address the security hole promptly.
The Website of the Norwich airport hacked, a cue to reflect
13.11.2015
A hacker shut down the website of the Norwich airport in just a few minutes to demonstrate the importance of a proper approach to the cyber security.
A few days ago the website of the Norwich Airport was shut down by a hacker managed, the attack was conducted in a few minutes revealing serious problems of cyber security.
The hacker explained to the BBC that it was too easy to hack the website, he discovered a serious vulnerability by using sqlmap, the popular SQL injection and database takeover tool.
The hacker posted the following Video PoC on YouTtube to demonstrate that could be very easy to hack a vulnerable website just using the online material to identify a target, discover a security flaw and exploit it. In a few minutes the website of the Norwich Airport was shut down by the expert.
“In a world where computers rule nearly every aspect of our lives, privacy and security are now more important than ever before and failure to take basic steps is inexcusable even for the most basic websites,” he said. “With online guides and wiki pages detailing step by step, free and secure patch fixes to most hacks and an entire worldwide compendium of knowledge on every single aspect of the computer sciences this is not acceptable.”
Why did he hack the website?
The hacker explained that he decided to hack the website because a friend belonging the “Muslim Electronic Army” confided that he was “planning on having fun” with the security flaw in the website around Christmas time. During that period, an attack would have major repercussions causing many hardships, “alarm or disruption.”
The hacker raises the question about the security posture of a critical infrastructure such as an airport.
“Do you want to fly from an airport that may not have control of their own computers?” he added.
Sure, you can question me that no critical system has been impacted, but we cannot underestimate that a similar attack could have also serious consequences. Let think to a data breach, stolen data could be used by an attacker to extend the damage to other systems with lateral movement within a targeted network. Another possible attack scenario sees threat actors that use the compromised website to deliver malware to a huge number of visitors that could be a victim of more or less sophisticated fraud scheme.
“Imagine if the ‘official’ airport website is hacked and easily defaced with something designed specifically to cause public concern, or worse—panic. Or what if the site started delivering malware to visitors? Just because the site doesn’t store confidential information, it doesn’t mean its security can be ignored.” observed the WhiteHat Security founder, Jeremiah Grossman.
Chrome Zero-day Exploit leaves MILLIONS of Android devices vulnerable to Remote Hacking
13.11.2015
Hackers have found a new way to hack your Android smartphone and remotely gain total control of it, even if your device is running the most up-to-date version of the Android operating system.
Security researcher Guang Gong recently discovered a critical zero-day exploit in the latest version of Chrome for Android that allows an attacker to gain full administrative access to the victim's phone and works on every version of Android OS.
The exploit leverages a vulnerability in JavaScript v8 engine, which comes pre-installed on almost all (Millions) modern and updated Android phones.
All the attacker needs to do is tricking a victim to visit a website that contains malicious exploit code from Chrome browser.
Once the victim accessed the site, the vulnerability in Chrome is exploited to install any malware application without user interaction, allowing hackers to gain remotely full control of the victim’s phone.
Also Read: This Malware Can Delete and Replace Your Entire Chrome Browser with a lookalike
This Chrome for Android zero-day exploit was practically demonstrated by Gong in a hacking contest MobilePwn2Own during the 2015 PacSec conference in Tokyo.
Complete technical details on the exploit are not available yet, but the researcher has already alerted Google to the bug, and the company is expected to pay out a sizeable bug bounty for the exploit.
Just to be on the safer side, Android users are advised to use alternative browsers until Google patches the vulnerability.
USA a Británie zkoušely reakci finančního sektoru na útok hackerů
13.11.2015 Zabezpečení
Británie, Spojené státy a přední světové firmy uskutečnily dnes plánované cvičení, které mělo prověřit jejich reakci na případný kybernetický útok ve finančním sektoru. S odvoláním na sdělení britského ministra financí o tom informovala agentura Reuters.
Test měl ukázat, jak by New York a Londýn, coby dvě největší světová finanční střediska, dokázaly zvládat případný hackerský útok, sdílet informace a komunikovat s veřejností.
„Připravujeme se na hrozbu kybernetického incidentu ve finančnictví,” uvedl v prohlášení britský ministr financí George Osborne. „A budeme nadále spolupracovat s našimi partnery ve Spojených státech, abychom zlepšili naši kybernetickou spolupráci,” uvedl také.
Uskutečnění testu během roku avizovali britský premiér David Cameron a americký prezident Barack Obama.
Americká prokuratura tento týden obvinila tři muže v souvislosti s hackerskými útoky na finanční instituce a úřady, včetně největší americké banky JPMorgan Chase. Podle agentury Reuters se obvinění vztahují také na nedávno odhalené krádeže dat ve vydavatelství Dow Jones, které vydává například ekonomický deník The Wall Street Journal.
Známý server Ammyy nabízí software s malwarem, tvrdí Eset
13.11.2015 Viry
Eset detekoval několik případů škodlivého softwaru distribuovaného prostřednictvím oblíbené webové stránky ammyy.com. Například na přelomu října a listopadu byl k dispozici nakažený legitimní Remote Desktop Software.
Výzkumníci Esetu si podle svých slov koncem října všimli, že po dobu asi jednoho týdne všichni návštěvníci ammyy.com, kteří stahovali z této stránky programy, zároveň s těmito produkty stáhli i malware.
I když je Ammyy Admin legitimním softwarem, má za sebou i dlouholetou historii zneužívání různými podvodníky, a proto jej poskytovatelé bezpečnostních řešení považují za potenciálně nebezpečnou aplikaci.
Přesto je program Ammyy Admin stále ještě široce používaný: webová stránka ammyy.com uvádí mezi svými klienty společnosti, které jsou zahrnuty v žebříčku TOP 500 Fortune, nebo ruské banky.
Podle zjištění Esetu bylo během nedávné doby distribuováno prostřednictvím stránek ammyy.com pět různých skupin malwarů. Prvním je Lurk downloader, který byl distribuován 26. října, dále šlo 29. října o Corebot, poté 30. října o Buhtrap a konečně 3. listopadu o Ranbyus a Netwire RAT.
Ačkoli tyto skupiny malwarů nejsou vzájemně propojené, v každém případě mohly být z webové stránky ammyy.com stažené. Je docela možné, že počítačoví hackeři odpovědní za útok na tyto internetové stránky prodávali dál přístup k různým skupinám využívajícím software Ammyy.
Ze škodlivého softwaru šířeného prostřednictvím internetových stránek ammyy.com zasluhuje zvláštní pozornost instalační balíček zneužívaný hackery při jejich malwarové kampani Operation Buhtrap.
„To, že počítačoví zločinci nyní používají metodu kompromitování klíčových webů, ukazuje, že se zmenšuje rozdíl mezi tradiční kyberkriminalitou a sofistikovanými útoky s využitím takzvaných pokročilých perzistentních hrozeb," říká Jean-Ian Boutin, specialista Esetu na malwary.
Facebook is testing Self-Destructing Messages for Messenger App
13.11.2015
Facebook is testing a Self-Destructing Messages for its Messenger, at the moment the feature is available for some users in France.
This is the silent war of the social media, now Facebook is planning to offer its users a Snapchat-like feature in its Messenger app, the company is implementing the Self-Destructing Messages.
The new feature will allow Facebook users to send self-destructing messages.
Snapchat is a video messaging application that allows sending videos and messages, dubbed “Snaps,” that recipients can view for a limited time, it has been estimated that in May 2015 the app’s users were sending 2 billion photos and videos per day.
Facebook Self-Destructing messages
Now some Facebook users in France have discovered this new feature in the Messenger app that lets them send messages that Self-Destruct after an hour.
“Facebook is testing a disappearing message option within its Messenger app in France, giving users the option to have their messages self destruct one hour after sending them. The feature will bring ephemeral messaging to Facebook Messenger for the first time, taking a shot at Snapchat, the company’s biggest messaging competitor.” states Buzzfeed.
Users can enable the self-destructing message by tapping the hourglass icon on the top-right corner of the Messenger conversation. Enabling this mode Facebook sets the messages to self-destruct after an hour. To restore Facebook Messenger normal behavior user has to tap again the hourglass icon.
“We’re excited to announce the latest in an engaging line of optional product features geared towards making Messenger the best way to communicate with the people that matter most.” states Facebook.“Starting today, we’re conducting a small test in France of a feature that allows people to send messages that disappear an hour after they’re sent. Disappearing messages gives people another fun option to choose from when they communicate on Messenger. We look forward to hearing people’s feedback as they give it a try.”
Last year, Facebook has tested a similar self-destructing message feature, Slingshot, but without success.
At the time I’m writing, the feature is only available to a limited number of French users.
FAKBEN Ransomware-as-a-service emerges from the underground
13.11.2015
FAKBEN is offering a professional Ransomware-as-a-service that relies on a new CryptoLocker ransomware which can be downloaded through the executable file.
Ransomware is probably the most popular category of malicious code in this period, this week we have discussed a malicious code that infected the UK Parliament, an off-line ransomware and a Linux.Encoder1 ransomware revealing the decryption key.
News of the day is that a new Ransomware-as-a-service surfaces from the criminal underground, requesting customers 10 percent profit cut.
The FAKBEN Team is offering a professional Ransomware-as-a-service that relies on a new CryptoLocker ransomware which can be downloaded through the executable file. Users can customize their CryptoLocker variant and manage the campaign by using the CryptoLocker service developed by FAKBEN.
The service allows users to send the ransomware to a specific victim to ask for ransom money, the CryptoLocker service exploits the Tor Network to host a Hidden Service (https://24fkxhnr3cdtvwmy.onion/).
Customers can choose the total amount of victim to pay and the BTC wallet of destination.
“A new service launched this week is offering a new Ransomware product under the name CryptoLocker to anyone willing to pay ten percent of the collected ransom. In addition to the core Ransomware product, the ultimate goal of the business owner is to implement additional functions to the malware including linking it to recently produced exploits.” states a post published by Salted Hash. “Called CryptoLocker Service, the new venture launched this week on a standalone Darknet website. The new venture is being run by a person using the handle Fakben.”
Customers of the FAKBEN ransomware-as-a-service have to US$50 to download the CryptoLocker executable file, when one of the victims pay the ransom, the VXers keep 10 percent of the sum.
“You can download CryptoLocker executable file for $50 . When you have done the payment you will immediately be enabled to the building source of the ransomware so you can specify the amount of money you want to receive and the address destination for BTC. When crytpolocker file is executed to the victim’s machine it crypts all files. ” states FAKBEN.
“Then an automatic window is opened and is asked to the victim to pay in order to get the key for the decryption of the files. When the person pays for files decryption is important to be loyal and give him/her the key for the decryption. When money is payed we will take 10% for the service and then the other amount will be sent to the address you specified before.”
FAKBEN ransomware-as-a-service included a user-friendly interface that will show the number of infected machines and ransoms paid. This specific Ransomware-as-a-service surfaces is still not active, it will be launched in the coming days.
FAKBEN explained that the code used by the platform is completely different from the one of the original Cryptolocker, the malware actually only runs on Windows machines but there are plans to make it multiplatform.
Fakben explained that the ransomware cold be customized by adding a number of exploits targeting vulnerabilities in products such as Adobe and Java.
“Those additional services are not part of the core product. If they’re used, the customer would still pay the opening $50 USD fee, plus the exploit cost and development cost, as well as the ten percent commission on each ransom paid.” states Salted Hash.

Ransomware-as-a-service is not a novelty in the criminal ecosystem, recently crooks launched a similar service, the Tox ransomware-as-a-service, that anyway had no success and its creators decided to offer it for sale in the underground.
How to Build a Successful Incident Response Plan
13.11.2015
The fight to protect your company’s data isn’t for the faint of heart.
As an embattled IT warrior, with more systems, apps, and users to support than ever before, keeping everything up and running is a battle in itself.
When it comes to preventing the worst-case scenario from happening, you need all the help you can get, despite your super-hero status.
According to SANS, there are 6 key phases of an incident response plan.
Preparation - Preparing users and IT to handle potential incidents in case they happen
Identification - Figuring out what we mean by a “security incident” (which events can we ignore vs. which we must act on right now?)
Containment - Isolating affected systems to prevent further damage
Eradication - Finding and eliminating the root cause (removing affected systems from production)
Recovery - Permitting affected systems back into the production environment (and watching them closely)
Lessons Learned - Writing everything down and reviewing and analyzing with all team members so you can improve future incident response efforts
Here are three examples from the front lines of incident response that can help you at each phase as you build out your plan.
On Defining Success Incident Response Success
There are many levels of success in defensive work… the common wisdom is that the attacker only has to be right once, but the defender has to be right every time, but that’s not always true.
Attacks are not all-or-nothing affairs - they happen over time, with multiple stages before final success.
To remain undetected against an attentive defender, it is the attacker who must make every move correctly; if an astute defender detects them even once, they have the possibility to locate and stop the whole attack.
You aren't going to immediately detect everything that happens during an attack - but as long as you detect (and correctly identify) enough of an attack to stop it in its tracks, that’s success.
Don’t Panic. Stay Focused.
Execution is key - the range of ways to attack a target can seem limitless - expecting to be an expert on all of them is pointlessly unrealistic.
The most important part of incident response is to handle every situation in a way that limits damage, and reduces recovery time and costs.
At the end of the day, that’s how you’ll be measured on a job well done… not that you’ve covered every angle of every potential vulnerability.
Start with Simple Steps. Attackers are Lazy.
Attackers have technical and economic imperatives to use the minimum amount of effort and resources to breach their targets - the more you remove the low-hanging fruit on your network, the more you raise the actual level of work an attacker has to expend to successfully infiltrate it.
AlienVault has recently created a 5 chapter eBook titled the Insider’s Guide to Incident Response that goes further into fundamental strategies that can help you create an efficient and effective incident response plan.
The eBook covers:
Arming & Aiming Your Incident Response Team
Incident Response Process and Procedures
Types of Security Incidents
Incident Response Tools
Incident Response Training
You can download the entire eBook at AlienVault’s website here.
Learn more about AlienVault USM:
Download a free 30-day trial
Watch a demo on-demand
Play with USM in our product sandbox (no download required)
Facebook will Let You Send Self-Destructing Messages with Messenger App
13.11.2015
Facebook is planning to offer you the popular Snapchat feature in its Messenger app – 'Self-Destructing' Messages.
Yes, Facebook is testing a new feature within its Messenger app that will allow its users to send self-destructing messages.
Some Facebook users in France have spotted this new feature in the Messenger app that lets them send messages that only last for an hour.
How to Turn ON the Feature?
Users can turn on the self-destructing message feature within Messenger through an hourglass icon on the top-right corner of the conversation. The icon, when tapped, sets the messages to self-destruct after an hour of sending it.
Tapping the hourglass icon again will turn off the feature, with everything going back to normal.
Here's what Facebook says about the feature:
"We're excited to announce the latest in an engaging line of optional product features geared towards making Messenger the best way to communicate with the people that matter most."
"Starting today, we're conducting a small test in France of a feature that allows people to send messages that disappear an hour after they're sent. Disappearing messages gives people another fun option to choose from when they communicate on Messenger. We look forward to hearing people's feedback as they give it a try."
Snapchat has been offering similar feature since 2011 that allows its users to send images that self-destruct itself.
This is not the very first time Facebook has experimented with the self-destructing message feature. Last year, the social network giant tested a similar feature with Slingshot, a standalone app that allows users to send self-destructing messages, but it didn’t work.
Hopefully, by integrating self-destructing messages in its Messenger app with 700 Million users already, the company gets success this time.
So far the feature is only available to some users in France, but Facebook may roll out the feature outside of France if it's successful.
What do you think of this new feature? Hit the comments below.
Cherry Picker, a PoS Malware even more threatening
13.11.2015
Researchers at Trustwave have published the analysis of the Cherry Picker threat, a point-of-sale (PoS) malware that went undetected over the years.
A point-of-sale (PoS) malware that went largely undetected for the past several years has been analyzed by researchers at Trustwave.
Security experts at Trustwave have analyzed an insidious point-of-sale (PoS) malware dubbed Cherry Picker that threat has been around since at least 2011. The threat implements sophisticated evasion techniques that allowed it to remain under the radar across the years.
Cherry Picker Pos malware was detected for the first time in 2011 by experts at Trustwave, the researchers analyzed several samples and discovered that they were designed to inject processes managing cardholder data. One of the pieces of code analyzed by Trustwave consisted of two components, a command line interface (sr.exe), and the searcher.dll that is a code which is directly injected into targeted processes bysr.exe.
Cherry Picker Pos malware poseidon
Cherry Picker belongs to the family of the memory scrapers and uses a file infector for persistence.
“Cherry Picker’s use of configuration files, encryption, obfuscation, and command line arguments have allowed the malware to remain under the radar of many security companies and AV’s,” Trustwave researchers said. “The introduction of new way to parse memory and find CHD, a sophisticated file infector, and a targeted cleaner program have allowed this malware family to go largely unnoticed in the security community.”
The threat includes a cleaner module that allows it to remove all traces of the infection from the system.
The latest version of the Cherry Picker PoS malware uses the a set of API called QueryWorkingSet to scrape the memory and gather card data. The card data are then written into a file that is sent to the control servers.
“Once the data is exfiltrated, the cleaning process begins. The malware developers created a targeted cleaner tool designed to restore the infected system to a clean state. The threat relies on the popular remote control software TeamViewer to overwrite and remove files, logs and registry entries.” reported SecurityWeek.
The experts noticed that the presence of Cherry Picker was always accompanied to other threats, such as AutoIt PoS malware, and the Rdasrv that is one of the earliest PoS RAM scrapers.
Trustwave researchers reported spotting three different strains of the Cherry Picker PoS malware, the different versions account for the evolution of the other.
The researchers have noticed an evolution in the mechanism for persistence, earlier versions used a registry entry, in more recent instances, it uses an updated version of sr.exe, srf.exe, which has been used to install the malware and inject a DLL into processes.
The Cherry Picker PoS, different from similar threats focuses only on the process that manage card data, this process is reported in the configuration file. If the malware doesn’t find the process to inject on the machine it exits.
Central Shop, the evolution of credit card black markets
13.11.2015
Central Shop is a web portal dedicated to the sale of stolen credit card data that captures the attention of the experts due to its amazing interface.
The sale of stolen credit card data is one of the most prolific activities in the criminal ecosystem, in many black markets it is quite easy to acquire the precious commodities.
Today I desire to present you the Central Shop website, a portal dedicated to the sale of credit card data that captures the attention of the experts due to its amazing interface.
The first thing that immediately obvious when we access the site is an interactive map that allows visitors to chose the origins of stolen data they are searching for.
The possibility to choose the country for the stolen card data is very important for cyber criminals, by acquiring cards related to a specific region and operating the cash out activities in the same area could allow them to circumvent some of the controls implemented by identifying the ongoing fraudulent activities.
The same feature has been implemented by other actors in the underground, the popular expert Brian Krebs a couple of years ago reported the commercialization of the card information on the location of stores and point of sales where cards were used.
The financial security experts consider the information very precious for the arrangement of scams, the knowledge of the places where the cards were used allows the attackers to choose the points where to use the cards to reduce the risk of detection for the ongoing scam.
Location information included in the stolen card data allows buyers to use cloned versions of cards issued to people in their immediate vicinity.
“Later, I learned from a fraud expert that this feature is included because it allows customers of the shop to buy cards issued to cardholders that live nearby. This lets crooks who want to use the cards for in-store fraud avoid any knee-jerk fraud defenses in which a financial institution might block transactions that occur outside the legitimate cardholder’s immediate geographic region.” explained Brian Krebs.
The same feature was also implemented by operators of the AlphaBay black market, the recently announced a credit card “autoshop.”
By looking in the map it is possible to note that only a small number of countries are not covered, including Russia, Central Asia and Central and East Africa.

The site is available in several languages, such as Russian, English, Spanish and Chinese.
Researchers at Motherboard have tested the search function discovering that most of the cards come from the United States (nearly 50,000 cards).
Top 10 countries include also the United Kingdom (48,424 cards), Canada (34,048 cards), and Brazil (22,370 cards).

The domain was registered in June, but it’s not clear when operators behind Central Shop website started their activities.
At the time I’m writing it is no possible to register with the website …. stay tuned
Windows 10 verze Threshold 2 je venku – co přináší?
13.11.2015 Bezpečnost
Windows 10 verze Threshold 2 je venku – co přináší?Včera, Michal Hala, aktualitaDnes (12. listopadu) Microsoft vypustil do oběhu první velkou aktualizaci pro Windows 10 nazvanou November Update známou už dříve spíše pod kódovým jménem Threshold 2. Pojďme se podívat, co přináší pro všechny uživatele a speciálně pak pro podniky.
Windows 10 byla uvolněna 29. července letos v létě a zatím dostávala jen drobné aktualizace. Teď tedy nadešel čas na větší upgrade. Číselně jde o verzi 1511, sestavení 10586, která už byla dříve uvolněna Insiderům v rámci testování. Upgrade je dostupný prostřednictvím Windows Update, nebo je možné stáhnout ISO.
Aktualizace přináší řadu vylepšení systému Windows 10 a to zejména tato, která se týkají všech uživatelů:
Vyšší rychlost systému – například bootování má být o 30 % rychlejší než ve Windows 7 na stejném zařízení (nekamenujte mě v diskusi).
Vyšší stabilita systému – na základě rozšiřující se uživatelské základny Windows 10 bylo možno odladit chyby na exotičtějších zařízeních.
Virtuální asistentka Cortana – rozpozná ručně psané poznámky (tedy pokud máte elektronické pero), nově je podporována japonština a kanadská, australská a indická angličtina.
Prohlížeč Edge – má být rychlejší a bezpečnější, přibyly náhledy stránek v záložkách, funguje synchronizace oblíbených položek mezi různými zařízeními. Bohužel původně slíbená rozšíření Microsoft nestihl implementovat a budou (snad) až v příštím upgradu příští rok v červnu.
Změny rozhraní (GUI) systému – jde nastavit barva titulku, změnil se vzhled kontextových menu a pár dalších změn, které ovšem nejsou nijak zásadní.
Logo Windows
Vylepšení pro podniky se týká:
Windows Store for Business – je zpřístupněno tržiště aplikací určené pro podniky, které by mělo vyhovovat potřebám podnikových uživatelů i administrátorů podnikových IS.
Windows Update for Business – týká se edic Pro, Enterprise a Education a nabízí vylepšený mechanismus aktualizací pro podniky, kterému se budeme věnovat podrobněji dále.
Windows Update for Business dělí updaty to tří skupin a podle toho je možné je spravovat:
Upgrady OS - mohou být odloženy až o osm měsíců v intervalech po měsíci.
Updaty (Security updates, Critical updates) - mohou být odloženy až o čtyři týdny v intervalech po týdnu.
Updaty definic (Definition updates) - nemohou být odloženy.
Zatím není implementována funkce Enterprise Data Protection, které bude umožňovat v rámci režimu Bring Your Own Device (tj. využití vlastního zařízení v práci) zašifrovat podniková data na takovém zařízení, bez dopadu na osobní aplikace a data. Na druhou stranu Windows 10 Enterprise v aktualizační větvi Long Term Servicing Branch teď mohou kompletně vypnout telemetrii, byť to Microsoft nedoporučuje.
Když už mluvíme o novinkách pro podniky, tak prý ze 120 miliónů (Mary Jo Foleyová v původním článku uvádí 110 miliónů) je 12 miliónů podnikových PC. To není úplně málo, ale ani to nesignalizuje bůhvíjakou ochotu podniků přecházet na nový systém. A je otázka jestli to aktualizace Threshold 2 nějak výrazně změní. Já bych spíš sázel až na příští upgrade Redstone. A i to je možná příliš optimistický odhad.
Redstone má být k dispozici počátkem června příští rok. Zatím se neví, co přesně přinese, kromě odložených rozšíření pro prohlížeč Edge a vylepšení mechanismu spolupráce mezi PC a mobilními zařízeními s Windows 10, které se inspirovalo u Applu a jeho funkce Continuity.
První linuxový ransomware prolomen
13.11.2015 Viry
Antivirová společnost Bitdefender našla způsob, jak obnovit data zašifrovaná prvním v Linuxu šifrujícím ransomwarem Linux.Encoder.1. Napadení uživatelé si můžou její nástroj stáhnout zdarma.
Administrátoři webových serverů, které byly v uplynulých dnech napadeny prvním v Linuxu šifrujícím ransomwarem mají štěstí. K dispozici už je bezplatný nástroj, který dokáže zašifrované soubory zase dešifrovat. A uživatelé tak nemusí platit výkupné stanovené na 1 bitcoin, tedy víc než osm tisíc korun.
Děkovat za něj mohou vývojářům z antivirové společnosti Bitdefender, kteří objevili trhlinu ve způsobu, jakým ransomware s označením Linux.Encoder.1 šifruje soubory v napadených adresářích.
Využívá k tomu takzvaný Advanced Encryption Standard (AES), na jehož bázi lze soubory jak zašifrovat, tak dešifrovat, v kombinaci s asymetrickým šifrovacím algoritmem RSA. Ten používá veřejný i soukromý klíč, přičemž veřejný pro šifrování, soukromý pro dešifrování.
V případě Linux.Encoder.1 je pár těchto klíčů generován na serveru útočníků a jen veřejný je zaslán do napadeného počítače a využit k zašifrování AES klíče. V takovém případě pak napadený uživatel těžko může soubory dešifrovat bez získání soukromého klíče. V Bitfenderu však v procesu našli slabinu, díky které obešli nutnost získat tento soukromý klíč.
Jejich nástroj je v podstatě v Pythonu napsaný skript, který po analýze šifrovacícho proesu dokáže obnovit zašifrovaná data jeho převrácením.
„Jestliže jste schopni nabootovat napadený systém, stáhněte si skript a spusťte ho jako superuživatel,“ radí Bitfender v příspěvku, v němž použití nástroje detailně popisují.
Nejde o první případ, kdy tvůrci ransomwaru zapomněli na mezery v šifrovacích algoritmech, což vedlo k snadnému prolomení šifer a záchraně napadených programů. Ve většině takových případů se však pučili a další verze svých škodlivých programů už vypustili zdokonalené.
Dá se tedy předpokládat, že i Linux.Encoder se dočká svých vylepšených verzí anebo že se objeví zcela nové červy šifrující v Linuxu.
FBI reportedly Paid $1 Million to University Researchers for UnMasking Tor Users
12.11.2015
The non-profit Tor Project has accused the FBI of paying the security researchers of Carnegie Mellon University (CMU) at least $1 Million to disclose the technique they had discovered that could help them…
…Unmask Tor users as well as Reveal their IP addresses as part of a criminal investigation.
As evidence, the Tor Project points to the cyber attack that it discovered last year in July.
The team discovered more than hundred new Tor relays that modified Tor protocol headers to track people who were looking for Hidden Services – web servers hosted on Tor that offers more privacy.
The Evidence
The unknown attackers used a combination of nodes and exit relays, along with some vulnerabilities in the Tor network protocol that let them uncovered users' real IP addresses.
The attack reportedly began in February 2014 and ran until July 2014, when the Tor Project discovered the vulnerability. Within few days, the team updated its software and rolled out new versions of code to block similar attacks in the future.
But who was behind this serious ethical breach was a mystery until the talk from Carnegie Mellon University's Michael McCord and Alexander Volynkin on de-anonymizing Tor users was cancelled at last year’s Black Hat hacking conference with no explanation.
UnMasking Tor Using Just $3,000 of Hardware
The Carnegie Mellon talk detailed a new way to "de-anonymize hundreds of thousands of Tor [users] and thousands of Hidden Services [underground sites] within a couple of months" using just $3,000 of hardware.
The researchers were going to prove their technique with examples of their own workaround identifying "suspected child pornographers and drug dealers."
However, after the ongoing attack on Tor network was discovered in July last year, the talk was abruptly canceled and suspicions were aroused that their techniques were used in the attacks discovered by the Tor Project.
The Tor Project also says the researchers stopped answering their emails, which made them more convinced of who was behind the attack – Carnegie Mellon's Computer Emergency Response Team (CERT).
"Such action is a violation of our trust and basic guidelines for ethical research. We strongly support independent research on our software and network, but this attack crosses the crucial line between research and endangering innocent users," The Tor Project Director Roger Dingledine wrote in a blog post published Wednesday.
However, the team is more confident that the Federal Bureau of Investigation (FBI) used the researchers of Carnegie Mellon University to circumvent federal hacking laws.
The FBI Paid $1 MILLLLLION to Unmask Tor Users
hack-tor-users
This week, Motherboard reviewed a court filing in the case of Brian Richard Farrell, an alleged Silk Road 2 lieutenant who was arrested in January 2014, that proved the FBI had indeed recruited a "university-based research institute" that was running systems on the Tor network to uncover the identity of Farrell.
"Apparently these researchers were paid by the FBI to attack hidden services users in a broad sweep, and then sift through their data to find people whom they could accuse of crimes," Dingledine wrote. "We have been told that the payment to CMU was at least $1 million."
Neither the FBI nor the Carnegie Mellon officials immediately responded to the Tor Project’s claims. If true, this incident would really make us think that…
Are these research by computer security researchers meant to help "identify vulnerabilities in the software" Or "endanger innocent people?"
What do you think? Let us know by hitting the comments below.
Did FBI pay the Carnegie Mellon to hack Tor?
12.11.2015
The Director of the Tor Project Roger Dingledine has accused the FBI of commissioning to the Carnegie Mellon boffins a study on methods to de-anonymize Tor users.
The experts at the Tor Project have collected more information about the attack launched last year by Carnegie Mellon researchers on the popular anonymizing system.
The Director of the Tor Project Roger Dingledine has accused the FBI of commissioning to the Carnegie Mellon boffins a study on methods to de-anonymize Tor users. The FBI has paid at least $1 million track Tor users and to reveal their IP addresses as part of a large criminal investigation.
“Apparently these researchers were paid by the FBI to attack hidden services users in a broad sweep, and then sift through their data to find people whom they could accuse of crimes. We publicized the attack last year, along with the steps we took to slow down or stop such an attack in the future:
https://blog.torproject.org/blog/tor-security-advisory-relay-early-traffic-confirmation-attack/
Here is the link to their (since withdrawn) submission to the Black Hat conference:
https://web.archive.org/web/20140705114447/http://blackhat.com/us-14/briefings.html#you-dont-have-to-be-the-nsa-to-break-tor-deanonymizing-users-on-a-budget
along with Ed Felten’s analysis at the time:
https://freedom-to-tinker.com/blog/felten/why-were-cert-researchers-attacking-tor/
We have been told that the payment to CMU was at least $1 million.” reads a blog post published by the Tor Project.
In 2014, researchers from Carnegie Mellon University’s computer emergency response team (Cert), Alexander Volynkin and Michael McCord, announced that they were able to de-anonymise Tor users and planned to reveal their discovery during the next Black Hat Conference in August.
A few weeks later the organization of the BlackHat had been contacted by the university’s lawyers which informed it that the researchers will not participate in the event.
“Unfortunately, Mr Volynkin will not be able to speak at the conference since the materials that he would be speaking about have not yet [been] approved by Carnegie Mellon University/Software Engineering Institute for public release,” states the message posted on the official website of the event.
The experts at the Tor Project are accusing the FBI of an attack on a large scale, the researchers confirmed that the offensive launched by the experts at the Carnegie Mellow University was not narrowly tailored to target specific individuals charged of criminal activity.
The attack represented a clear violation of trust and basic guidelines for ethical research.
“We strongly support independent research on our software and network, but this attack crosses the crucial line between research and endangering innocent users.” continues the post.
Neither the FBI not Carnegie Mellon representatives commented the accusation, Ed Desautels, a spokesman for Carnegie Mellon’s Software Engineering Institute only told Wired that he was not aware of any research activity commissioned to his institute.
“I’d like to see the substantiation for their claim,” said Ed Desautels. “I’m not aware of any payment.”
The evidence of the collaborations between the FBI and the Carnegie Mellon University has emerged also in a stand trial in federal court in Seattle later this month. The court was discussing the case of Brian Farrell, an alleged Silk Road 2 lieutenant, the law enforcement discovered the IP addresses belong to the suspect. A new filing in Farrell’s case states that a “university-based research institute” supported the investigation and helped the feds to de-anonymize Farrell.

According to a Homeland Security search warrant, between January 2014 and July 2014 a “source of information” provided law enforcement “with particular IP addresses” that had accessed the vendor side of Silk Road 2.
In July, the researchers at the Tor Project discovered a sustained attack against the Tor Network based on the technique described by the team of Carnegie Mellon University researchers.
“We think it’s unlikely they could have gotten a valid warrant for CMU’s attack as conducted, since it was not narrowly tailored to target criminals or criminal activity, but instead appears to have indiscriminately targeted many users at once. Such action is a violation of our trust and basic guidelines for ethical research. We strongly support independent research on our software and network, but this attack crosses the crucial line between research and endangering innocent users. This attack also sets a troubling precedent: Civil liberties are under attack if law enforcement believes it can circumvent the rules of evidence by outsourcing police work to universities. If academia uses “research” as a stalking horse for privacy invasion, the entire enterprise of security research will fall into disrepute. Legitimate privacy researchers study many online systems, including social networks — If this kind of FBI attack by university proxy is accepted, no one will have meaningful 4th Amendment protections online and everyone is at risk.”continues the post.
Snooping Samsung S6 calls with bogus base stations
12.11.2015
A duo of security researchers, Daniel Komaromy of San Francisco and Nico Golde of Berlin, demonstrated how to intercept calls using bogus base stations.
PacSec Modern Samsung devices, including the last generation Samsung S6, S6 Edge and Note 4, are vulnerable to phone eavesdropping. A duo of experts, Daniel Komaromy of San Francisco and Nico Golde of Berlin, demonstrated that is possible to intercept calls using malicious base stations.
The duo demonstrated the attacks on Samsung’s ‘Shannon’ line of baseband chips at the Mobile Pwn2Own competition at PacSec held in Toyko. Obviously the researchers haven’t publicly disclosed the details of their attack, they reported it to Samsung instead.
base stations MITM hack Samsung S6
Nico Golde and Daniel Komaromy at Pwn2Own today. (Drago Ruiu)
The experts targeted Samsung devices, including the Samsung S6, with a man-in-the-middle attack relying on an OpenBTS base station, tricking the handsets and forcing it to connect to the bogus station. Once connected to the bogus base station, the handset receives the baseband processor firmware, the module which is responsible handling voice calls.
“Our example of modifying the baseband to hijack calls is just an example,” Komaromy told Vulture South. “The idea with hijacking would be that you can redirect calls to a proxy (like a SIP proxy) and that way you can man-in-the-middle the call.” “So that means the caller sees her original call connected – but it can be recorded in the proxy [which is how] it’s like a wiretap implant.”
The attack works on Samsung S6 Edge running up updated software.
“I turned it on next to their radio and then dialled myself,” said PacSec organiser Dragos Ruiu. “And instead of ringing on my phone it rang on theirs.”
Android Tablets with Pre-loaded Cloudsota malware sold on Amazon
12.11.2015
Experts at Cheetah Mobile are warning about Android Tablet pre-loaded with Cloudsota Trojan sold on Amazon and other online stores.
Once again electronics equipment from China was offered for sale with pre-installed Trojan. This time, several models of Android tablets sold on Amazon and other online stores are sold with pre-loaded the Cloudsota malware.
Cheetah Mobile has identified more than 30 Android tablet brands pre-loaded with the Cloudsota malware, the majority of them are generic brand tablets equipped with Allwinner chips.
“Recently, researchers from the Cheetah Mobile Security Lab have found a dangerous Trojan, dubbed Cloudsota, pre-installed on certain Android tablets. Tablets infected with this Trojan are still on the shelves of Amazon, ready to be shipped to customers around the world.” states the post published by Cheetah Mobile.
The list of infected devices includes JYJ 7, JEJA 7 Zoll, FUSION5, Alldaymall Tablet, Yuntab SZ Wave, and Tagital. All the infected Android tablets are manufafured by Chinese companies.
The experts at Cheetah Mobile noticed several online reviews from customers who have purchased Android tablets infected with the malware.

It seems that the Cloudsota Trojan was deployed on several Android Tablet for many months, hackers used it to conduct several illegal activities, including install adware and hijack search results.
The researchers highlighted that the malware is able to restore itself after a reboot if the user attempts to remove it, this is possible because it runs with root permissions.
According to data collected by security products installed by the Cheetah Mobile, more than 17,000 infected tablets have been purchased in more than 150 countries.
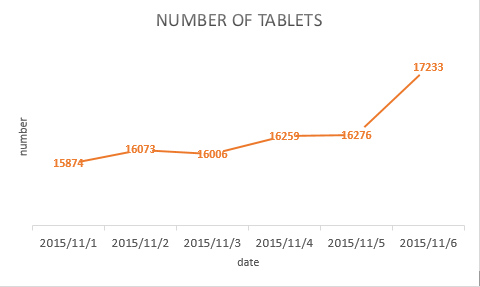
The highest number of infections was observed in Mexico, the United States and Turkey. Unfortunately, it is impossible to have a reliable estimation of the number of infected devices because there are many Android Tablets that comes without Cheetah Mobile security products.
Tablets infected with Cloudsota have been traced to over 150 countries, with the highest number of infections in Mexico, the United States and Turkey.
The worst aspect of the story is that despite Cheetah Mobile has reported the issue to the affected manufacturers, none of them responded.
The experts at Cheetah Mobile who analyzed the malware code and the C&C servers suspect that the threat actors behind the Cloudsota Trojan are from China.
Mobile devices shipped with pre-loaded malware are not a novelty, in September experts from G Data revealed that malware had been found on over two dozen smartphone models from China.
Microsoft vydal tucet záplat. Kritické chyby mají Windows i Explorer
11.11.2015 Zranitelnosti
Tucet bezpečnostních záplat vydala tento týden společnost Microsoft. Americký softwarový gigant jimi opravuje trhliny ve Windows, Internet Exploreru, Skypu, ale také v dalších softwarových produktech. S ohledem na závažnost chyb by lidé s instalací aktualizací neměli otálet.
Čtvrtina z vydaných záplat dostala nálepku „kritická“, to znamená, že trhliny představují pro uživatele nejvyšší možné nebezpečí. Upozornil na to server Krebs on Security.
Zranitelnosti mohou počítačoví piráti zneužít k tomu, aby propašovali prakticky libovolného záškodníka na cizí počítač. S jeho pomocí pak budou schopni přistupovat k uloženým datům, odposlouchávat internetovou komunikaci či počítač úplně zotročit.
Sítě zotročených počítačů
Takový stroj se pak klidně i bez vědomí uživatele může stát součástí botnetu (síť zotročených počítačů), který kyberzločinci zpravidla zneužívají k rozesílání spamu nebo k DDoS útokům.
Kritické zranitelnosti byly kromě platformy Windows objeveny také ve webovém browseru Internet Explorer. Útočníci je mohou také zneužít ke vzdálenému spuštění libovolného kódu. Stejně závažnou trhlinu obsahuje také nový prohlížeč Microsoft Edge.
Stahovat všechny záplaty pro kritické trhliny, které vyšly společně s balíkem pravidelných běžných aktualizací, je možné prostřednictvím služby Windows Update.
Ransomware infected the UK Parliament’s computer networks
11.11.2015
A ransomware infected several PC at the UK Parliament, for the first time a threat hit the internal computer network, the Parliamentary Digital Service.
Ransomware is once again in the headlines, this time the attention of the media was caught due to the nature of the victim, the UK Parliament. Cyber criminals have infected the computers at the UK parliament’s network and demand ransom money from an MP.
In the first successful cyber-attack, the attackers infected a number of computers and raked sensitive data relating to Labour Party’s Shadow Digital Minister Chi Onwurah and her employees.
The IT staff detected the ransomware in May when the threat locked several files stored in a shared drive.
UK Government
The incident appeared serious due to a large number of users accessing the drive. Nearly 8,500 people in the UK Parliament were exposed to the threat, including MPs, lords and the internal employees.
The RT.com reported that ransomware rapidly spread within the UK Parliament’s computer network, but it was halted before encrypting highly confidential files.
“The hackers compromised several computer systems that held confidential documents relating to parliamentary work by Chi Onwurah, the shadow digital minister, and files containing information about her employees.The attack, which occurred in May, is the first report of a successful hack against the parliamentary network. It comes amid heightened fears that hackers are winning a cyber-arms race against companies and public bodies” reported The Times.
You can imagine the surprise when the MP for Newcastle-upon-Tyne Central was requested to pay a ransom to recover encrypted files.
Onwurah reported the incident to the IT staff which seized all of her computers, disconnected the machine from the internal network and wiped and replaced the hard disks.
“It’s important that everyone realizes how susceptible we all are to these attacks,” Onwurah told The Times newspaper. “There are reports that foreign intelligence agencies have targeted MPs’ computers, so the time has come to find out how well we are being protected, especially now we know what cyber-attackers can do,” “A lot of what I deal with is very confidential to the person concerned. They should expect a high level of confidentiality and a high level of security.”
Onwurah is determined to learn more about malware and risks of exposure to cyber-attacks on MPs.
Microsoft Security Updates November 2015
11.11.2015
Microsoft posted four critical bulletins today, along with another eight rated Important and lesser. Microsoft’s summary is at the Technet site. All in all, the software maker is patching a large number of vulnerabilities this month, with 37 CVE listed vulnerabilities being fixed with the four critical Bulletins alone. On the bright side, Microsoft claims that none of these exploits are being publicly exploited at the time of notification.
Software affected with Bulletins rated critical are listed here (MS15-112, MS15-113, MS15-114, MS15-115):
Web browsers Microsoft Edge and Internet Explorer
Windows Journal
Windows’ font handing code
Software affected with Bulletins rated important are listed here (MS15-116, MS15-117, MS15-118, MS15-119, MS15-120, MS15-121, MS15-122, MS15-123):
Microsoft Office
Windows NDIS, IPSEC, Schannel, and winsock (network software)
Microsoft .NET Framework
Kerberos
Services on Sharepoint and Office Web Apps
Skype for Business and Microsoft Lync
Of the Bulletins rated “Important”, 16 CVE listed vulnerabilities were being fixed.
For you travelers aware of your own operational security and shunners of pgp, it’s interesting that Bulletin MS15-122 provides fixes against BitLocker-encrypted drive attacks.
According to Microsoft, “Kerberos fails to check the password change of a user signing into a workstation. An attacker could bypass Kerberos authentication on a target machine and decrypt drives protected by BitLocker.
An attacker who has physical access to a target machine could bypass Kerberos authentication by connecting a workstation to a malicious Kerberos Key Distribution Center (KDC).
The following mitigating factors may be helpful in your situation:
This bypass can be exploited only if the target system has BitLocker enabled without a PIN or USB key.
A domain user must be logged on to the target machine for the attack to succeed.”
Its reporter, Ian Haken, will be presenting the attack in a couple of days at BlackHat EU in Amsterdam. Perhaps this is another indication that hardware assisted drive encryption is the way to go.
Significant updates today also include Google announcing their deprecation of support for the Chrome browser on Windows XP and Windows Vista, along with Mac OS X 10.6, 10.7, and 10.8. While some organizations in the ICS or health care space may want to continue running their investment into these systems on their plant floors or facilities, this deprecation is another reason to upgrade those systems.
What You Should Know about Triangulation Fraud and eBay
11.11.2015
The increasing phenomenon of triangulation fraud on eBay has led to a published analysis on behalf of the company, as to how buyers should get informed and what they should pay attention to.
Over the past few months, a new phenomenon has risen and its proportions have been growing exponentially. It seems that, even if you have ordered something on eBay from a legitimate seller, you can never be sure of having avoided fraud altogether. To be more specific, with the help of the triangulation fraud, somebody might be taking advantage of you and your desire to purchase something via this platform.
If you are not familiar with the exact process that takes place in the triangulation fraud, think of it like that:
You, as a carefree customer, order something and pay for it to be shipped to you
The seller uses stolen credit card data, in order to purchase what you have been searching for in the first place
He sends it to you, after having bought it from a legitimate e-Commerce site
You are happy, since you’ve got what you have ordered
The e-Commerce site is happy, because they have sold their goods
The seller is happy, as they have scammed everyone
The only one who’s left unhappy is the person, whose credit card data has been stolen
So, you get the picture! This is why most of the times there is no dispute filed as to any parties that are left discontent – in fact, they aren’t!
Elaborating more on that, eBay has published an analysis on triangulation fraud and the extent that it can take. Indeed, there may be more than a few scammers. In other words, the seller might employ someone to do all the hard work for them and ship the goods, so as not to raise any suspicions.
According to Ebay, the seller is normally an individual engaged in a “work at home” job, in some cases he doesn’t realize he is involved in a fraud scheme, and some do have a respectable selling history.
“Postings for seller positions are easily found on the web, and typically advertise the seller keeps a significant percentage of the sale − typically 30%.” states the analysis.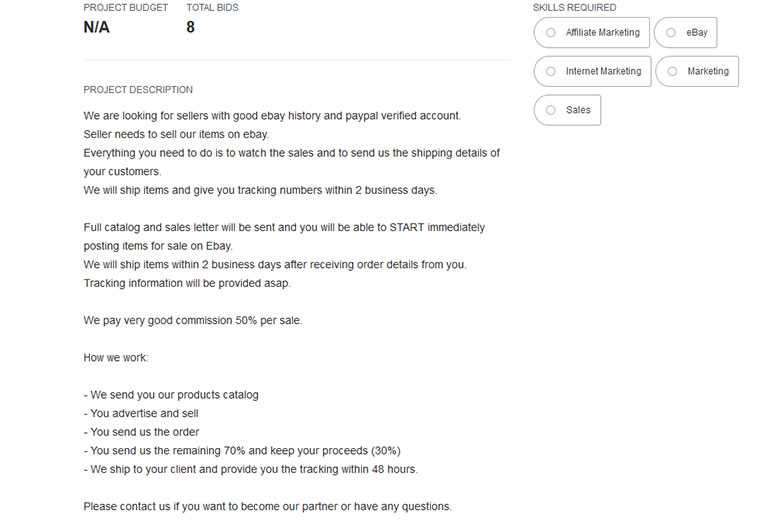

According to Ryan Moore, senior manager of global corporate affairs for eBay, working together is the key preventing such a mess.
“We believe collaboration and cooperation is the best way to combat fraud and organized retail crime of this nature, working in partnership with retailers and law enforcement”, he has stated. As he has added, this type of online crime “relies heavily on the tools that merchants use themselves, which includes understanding their customers and implementing the correct credit card authorization protocols”. explained Moore.
It is important to highlight just how crucial it can be for potential buyers to evaluate the offers on eBay and other platforms, prior to completing their order. If something sounds too good to be true moneywise, then it most probably is!
88 percent of company networks vulnerable to privileged account hacks
11.11.2015
A research published by CyberArk Labs focuses on targeted attacks against organizational networks, analyzing hackers’ methods, tools and techniques.
Bad news for network administrators, according to the security company CyberArk, 88 percent of networks are susceptible to privileged account hacks.
The report published by CyberArk entitled “Analyzing Real-World Exposure to Windows Credential Theft Attacks” reveals that corporate Windows networks are most of the times poorly configured and expose credentials for privileged user accounts. The analysis analyzes various credential abuse methods, including Kerberos attacks, Overpass-the-Hash and Pass-the-Hash attacks, providing suggestions for their mitigation.
The experts have searched for vulnerabilities and configuration issued that exposed credentials to hackers. They focused the investigation on the theft attacks, events that cause the exposure of the user’s credentials that could be used to log in impersonating the victim to exfiltrate data from the targeted machine.
The researchers at CyberArk assessed 51 corporate networks relying on Windows systems and discovered in over 88% of the cases “highly threatening machines” in the network’s architecture. The experts highlighted that 40 percent of Windows hosts could lead to a complete compromise if they were hacked.
“Every Windows network, no matter how large or small, could potentially be compromised by attackers through theft or privileged credentials,” states the report. 
The worst scenario occurs when the attacker access credentials for privileged accounts, let us think to network administrators, and use them to lateral movement within the targeted organization.
Each machine is a mine of information for attackers that could gather them to penetrate more deeply targeted networks. Only 12 percent of the networks analyzed by the experts were classified at a“low exposure,” which are networks where less than 10 percent of the hosts had a high risk of being compromised.
Similar techniques were adopted by threat actors in the wild, such as the notorious cases of the giants of the retail industry, Target and Home Depot.
The report also mentions the abuse of privileged service accounts ordinary used to execute a number of functions implemented by the operating system.
“We’ve seen similar credential theft methods as the basis for major attacks across a number of organization,” said Andrey Dulkin, director of cyber innovation at CyberArk Labs. “Identifying these machines and securing the associated privileged credentials against theft and exploitation is a critical step in securing against advanced cyber attacks.”
Nový firewall Sophosu synchronizovaně chrání síť i koncové body
11.11.2015 Ochrany
Firewall Sophos XG přichází, podle výrobce jako vůbec první, se synchronizovanou ochranou koncových bodů a sítí, která v případě hrozby dokáže izolovat koncové zařízení od sítě.
Synchronizovanou ochranu před sofistikovanými hrozbami založenou na bezpečnostním mechanismu Heartbeat představil Sophos. Tento mechanismus je zahrnutý ve firewallech nové generace série Sophos XG a v zařízeních pro jednotnou správu hrozeb (UTM).
Jde o novou technologii, která umožňuje přímé propojení zařízení a následné sdílení bezpečnostních informací o jednotlivých hrozbách. Vedle rychlejší detekce hrozeb patří mezi přínosy nové technologie také automatická izolace infikovaných zařízení nebo možnost bezprostřední a cílené reakce i přijetí adekvátních opatření.
Heartbeat pravidelně a v reálném čase informuje o podezřelém chování nebo nežádoucí aktivitě mezi koncovými body a síťovým firewalem nebo zařízením pro jednotnou správu hrozeb. Díky možnostem přímého sdílení důležitých informací mezi tradičně nezávislými produkty může okamžitě hrozbu eliminovat, případně pomoci s bojem proti nákaze malwarem i proti kompromitaci dat.
Firewall Sophos XG využívá pro izolaci napadených zařízení a omezení přístupu k nim data poskytovaná řešeními Sophos pro ochranu koncových bodů, která mohou současně pracovat na řešení bezpečnostního problému.
IT firmy tak nemusí nasazovat další agenty, zavádět nové vrstvy komplexních nástrojů pro správu, využívat logovací a analytické nástroje nebo zvyšovat své náklady spojené s bezpečností. Mechanismus Heartbeat je plně funkční součástí firewallu Sophos XG i cloudového řešení Sophos pro ochranu koncových bodů.
K dispozici je přitom řada modelů XG od desktopových zařízení s integrovanou podporou Wi-Fi až po zařízení určená pro datová centra a umožňující instalaci do racku.
Jak bezpečnostní mechanismu Heartbeat funguje?
Ve chvíli, kdy je do sítě přidán nový koncový bod chráněný technologiemi Sophos, se mechanismus Heartbeat automaticky spojí s lokálním firewallem Sophos XG a koncový bod začne okamžitě sdílet informace o svém bezpečnostním stavu.
Pokud firewall identifikuje podezřelou komunikaci nebo je na koncovém bodu detekován malware, jsou bezpečnostní informace včetně podrobností o hrozbě poskytnuty druhé straně okamžitě, a to bezpečným způsobem.
Koncový bod poskytuje podrobné kontextové informace, jako je název počítače, uživatelské jméno a informace o procesech spojených s identifikovanou hrozbou.
Firewall může automaticky přijmout potřebná opatření k izolaci koncového bodu z pohledu interních i externích sítí a vyvolat další akce na koncovém bodu, které minimalizují riziko a předejdou ztrátě dat.
Po odstranění hrozby využije koncový bod mechanismus Heartbeat k informování o změně svého bezpečnostního stavu a firewall opětovně povolí běžnou síťovou komunikaci.
Three men charged for the attack on the JPMorgan Chase
11.11.2015
U.S. Authorities have charged other three men in huge cyber fraud targeting JPMorgan, and at least another nine financial institutions.
The US authorities have charged three individuals over the hack of the JPMorgan Chase and other financial institutions. The data breach suffered by the JPMorgan Chase is considered the largest ever hacking case in financial history, data related nearly 76 million households and seven million small business accounts were exposed in the hack.
According to Bloomberg, the cyber thieves have stolen details of “over 100 Million customers,” meanwhile the spokeswoman for JPMorgan Chase Patricia Wexler confirmed the number of affected customers was around 80 Million.
“We appreciate the strong partnership with law enforcement in bringing the criminals to justice,” Wexler said in an email statement. “As we did here, we continue to cooperate with law enforcement in fighting cybercrime.” explained Wexler.
Now the US Court of the Southern District of New York has charged three men, Gery Shalon, Ziv Orenstein, and Joshua Samuel Aaron, accusing them of hacking into a number of financial institutions, including JPMorgan Chase.
The three hackers are added to another alleged criminal, Anthony Murgio, which was subjected to a separate indictment. Murgio was previously arrested for a cyber attack on JPMorgan as well as for operating an illegal Bitcoin exchange.
The Israeli Shalon, 31, and Orenstein, 40 were arrested in July, meanwhile American Murgio was arrested in the same period. Aaron, 31, is a U.S. citizen who has lived in Moscow and Tel Aviv.
“The new charges portray Shalon as the ringleader, having orchestrated hackings since 2012 against nine companies in which personal information for more than 100 million customers was stolen. He and Orenstein were accused of having since 2007 run at least 12 illegal Internet casinos, generating millions of dollars of profit each month.” states the Reuters.
“They allegedly also ran IDPay and Todur, through which they collected $18 million of fees to process hundreds of millions of dollars of transactions for criminals. According to the indictment, the illegal proceeds included tens of millions of dollars from manipulating the prices of stocks sold to customers whose information had been stolen.”
jpmorgan
The three alleged cyber criminals targeted at least nine financial organizations between 2012 and mid-2015, they were charged with 23 counts, including hacking, identity theft, securities fraud, and money laundering, among others.
Authorities said Shalon and Aaron exploited server located in Egypt to launch the attacks. The machines were rented under an alias that Shalon in all the hacking attacks.
E*Trade Financial Corp, TD Ameritrade Holding Corp and News Corp’s Dow Jones unit were among the victims of the hackers, a long list that includes also the Fidelity Investments and Scotttrade Inc.
The U.S. Attorney Preet Bharara explained at a press conference that “By any measure, the data breaches at these firms were breathtaking in scope and in size.”
GCHQ and NCA hunting criminals in the dark web
11.11.2015
The GCHQ and NCA join forces to fight online criminals in the Dark Web and formed a new unit called the Joint Operations Cell (JOC).
The dark web is a privileged environment for cyber criminals, the marketplaces hosted in this hidden part of the web are the right places where to buy and sell any kind of illegal service and product.
In the dark markets, it is possible to to find drugs, weapons, stolen data, and unfortunately also child pornography. British law enforcement and intelligence agencies, including the GCHQ and the National Crime Agency (NCA), have created a new unit, the JOC, that will specifically address the cyber crime.
The newborn unit will be initially focused on tackling online child sexual exploitation
“An NCA and GCHQ co-located Joint Operations Cell (JOC) opens officially today. The unit brings together officers from the two agencies to focus initially on tackling online child sexual exploitation.” states the press release published by the NSA.
In fact, the British Government is always in the forefront in the fight to online child sexual exploitation, in December 2014 the UK Prime Minister David Cameron announced the plan for the creation of a unit of cyber experts that will be involved in the investigation of crimes exploiting the dark web.
Prime Minister David Cameron revealed that national intelligence agencies will join the efforts to track and arrest online abusers and pedophiles. The British Prime Minister anticipated that the British Intelligence will have greater powers for online monitoring of suspects.
British authorities warned that up to 1,300 children are exposed to online abuse from pedophiles, it is a moral and social obligation to fight this social evil.
Cameron explained the strategy of the British Government at the #WeProtectChildren online global summit in London, announcing the creation of a new unit composed by members from the GCHQ and the National Crime Agency (NCA).
GCHQ against pedophilies Cameron
One of the most difficult goals of law enforcement that operate against online pedophiles, is to track this category of criminals that makes large use of anonymizing networks like Tor.
“The so-called ‘dark-net’ is increasingly used by paedophiles to view sickening images. I want them to hear loud and clear: we are shining a light on the web’s darkest corners; if you are thinking of offending, there will be nowhere for you to hide.” Cameron said.
The JOC will have the ambitious plan to fight any kind of online criminal activity.
“The Joint Operations Cell will increase our ability to identify and stop serious criminals, as well as those involved in child sexual exploitation and abuse online. This is a challenging task as we must detect them while they attempt to hide in the mass of data. We are committed to ensuring no part of the internet, including the dark web, can be used with impunity by criminals to conduct their illegal acts.” explained the GCHQ Director Robert Hannigan.
The GCHQ and the NCA have a long story of collaboration since the creation of the NCA in 2013. The NCA Director General Keith Bristow explained that the Joint Operations Cell wants to be the response to the significant increase in online illegal activities.
“The explosion in online communication channels has brought huge benefits for society. It has also significantly expanded the means by which criminals can share information, plan crimes including the sexual exploitation of children, and target victims. The JOC is a genuinely innovative development, using the best of our respective agencies’ skills to tackle the most complex cases and the most dangerous offenders online.” said the NCA Director General Keith Bristow.
I have no doubt, the Joint Operations Cell will give a hard time to criminals.
JPMorgan Hack — Three Men Charged in Biggest Bank Hack in History
10.11.2015
The US government has charged hackers over the largest ever hacking case in financial history.
The US Court of the Southern District of New York has charged three men accused of hacking into many financial institutions, including JPMorgan Chase that, according to the officials, was "the largest theft of user data from a U.S. financial institution in history."
JPMorgan Chase is one of the world's biggest banks that controls total assets worth more than $2.59 Trillion.
The Hackers targeted at least nine financial institutions between 2012 and mid-2015, including JPMorgan Chase, brokerages and a major business news publication, and stolen information of "over 100 Million customers," Bloomberg reported Tuesday.
The three men, including Gery Shalon, Ziv Orenstein, and Joshua Samuel Aaron were charged with 23 counts, including hacking, identity theft, securities fraud, and money laundering, among others.
A separate indictment was also filed against an alleged hacker, Anthony Murgio, who was previously arrested for a cyber attack on JPMorgan as well as for operating an illegal Bitcoin exchange.
The spokeswoman for JPMorgan Chase Patricia Wexler confirmed the bank's 2014 data breach hack that affected around 80 Million households.
"We appreciate the strong partnership with law enforcement in bringing the criminals to justice," Wexler said in an email statement. "As we did here, we continue to cooperate with law enforcement in fighting cybercrime."
U.S. Attorney Preet Bharara in Manhattan will announce the details of the indictments in a press conference that has been scheduled for later today at 1 St. Andrew's Plaza.
Disbanding the ‘Zoo’
10.11.2015
Two approaches to protecting virtualized data centers
Virtualized environments are exceptionally flexible, manageable, fault-tolerant and cost-effective. However, a number of difficulties have to be overcome to protect them from external threats. If this is not done successfully, problems will inevitably arise. This is true of individual virtual machines, as well as the data center as a whole.
Unfortunately, malware infections are a common occurrence in virtualized systems, particularly in VDI environments: customers’ employees do whatever they like on their virtual workstations without worrying about cyber-hygiene, believing that both their own IT department and the service provider will effectively block any malware.
It should be noted that, in most cases, the provider is not allowed access to customer machines and has to demand that customers use their own protection. Many customers, though not all, take a responsible approach and install endpoint protection solutions of their choice on their machines.
Sometimes, however, in spite of the provider’s recurring requests, customers resign themselves to the risk and do absolutely nothing about protection. There is no doubt that the provider will ultimately have to deal with all the problems arising from this approach. As a result, this turns into a major undertaking for the provider, who will have to change its protection strategy completely. (More information about security-related business problems faced by data centers can be found here.)
In virtualized data centers, information is stored and processed on virtual machines and in data storage systems. These are completely different technologies that require different approaches to protection, each having many subtle aspects.
The nuances of protecting virtualized environments
As mentioned above, if the service provider does not provide protection for customers’ virtual machines, customers will do it on their own, each in their own individual way. On the one hand, this is not a bad thing; each customer can choose a security solution that suits their needs. However, in practice, this approach is not only inefficient; the resulting chaotic ‘zoo’ of solutions on customer machines creates numerous problems of its own:
Excessive use of hardware resources. The security system on each machine includes a complete set of components: an antivirus engine, a signature database, a firewall, etc. Each takes up its share of CPU time, RAM and disk space.
‘Storms’. If scanning for malware is performed or antivirus databases are updated on several virtual machines at the same time, this leads to a surge in resource consumption, which can result in degradation of the entire platform’s performance or even in denial of service. Security software can of course be manually configured to avoid storms, but the time required to do this for hundreds of virtual machines will be very significant.
Panic attacks. A security system is often configured to step up protection when malware is detected on a machine. A ‘paranoid’ set of security rules is activated and out-of-schedule scans are launched. This can increase the load on the host machine’s hardware and negatively affect the performance of neighboring virtual machines.
‘Instant-on’ security gap. Virtual machines often remain inactive until they are started up when the need arises. While a machine is inactive, none of the security system components on it are updated and the machine remains vulnerable during the period from startup until an anti-malware solution update is completed.
Incompatibility. Virtual machines are similar to physical computers in many ways, but they are also different in some significant aspects of their operation. For example, they use dynamic hard disks and can migrate from one server to another without shutting down. Standard security systems for physical machines are not designed with virtualized systems in mind. This can lead to delays, faulty operation or even complete inability to operate.
All these issues will ultimately have to be addressed by the service provider – and on a regular basis. There is only one way to avoid this – prevent this ‘zoo’ from being created in the first place by putting customers in a situation where they have to choose between several proven dedicated security solutions for virtualized environments.
With or without an agent?
The key advantage of virtualization security systems like Kaspersky Security for Virtualization lies in the fact that the engine and the anti-malware databases are hosted on a separate virtual machine (Security Virtual Appliance, SVA) which provides protection for all machines running on the hypervisor.
This solution has obvious advantages: hundreds of machines can be protected by just one anti-malware engine running on the SVA, which operates all the time and receives timely updates. This means all machines receive a high level of protection, while the VM scanning schedule is designed to preclude any excess load on the environment.
Virtualization security software can be implemented in two substantially different ways: agent-based (light agent) or agentless. Customers have the freedom to choose the one that best suits their needs, or even combine the two.
The agentless security solution has all of its components running on the SVA, and has a number of serious limitations. It is only designed to operate in environments based on VMware products, and is not capable of working with processes running in virtual machine memories, so it only scans the file system and incoming network traffic. In other words, it can only scan files and block network attacks. In some cases, this is sufficient. An agentless solution also provides almost instant protection of virtual machines immediately after they are launched. No software needs to be installed on the customer’s machines.

Disbanding the 'Zoo': Two Approaches to Protecting Virtualized Data Centers
The agentless approach to securing virtual environments, based on the solution Kaspersky Security for Virtualization | Agentless
The light agent-based security system provides the entire range of security technologies (working with memory processes, application control, web browser protection, etc.) without using up lots of resources, as the scan engine and the databases are hosted on the SVA. Such an approach provides the functionality similar to Endpoint Protection-class solutions, while also being optimized and tested for virtual environments. However, a lightweight agent needs to be installed on each virtual machine so that the security solution has full access to the system. This can be seen as inconvenience, but many virtualization scenarios allow the use VM templates; in this case, the agent can be pre-installed into the template, so every VM spawned from it would have the agent as well, receiving instant protection right after being started.

The light agent-based approach to securing virtual environments, based on the solution Kaspersky Security for Virtualization | Light Agent
The choice between these two types of solutions depends on the accompanying circumstances.
Often the provider cannot guarantee the presence of a security solution at the customer’s facility, which potentially creates a gap in data center security. The customer may also have reasons for not allowing any third-party software to be installed on their machines. In this case, the agentless security solution is the optimal choice.
In other cases, the provider and the customer agree from the outset that a security solution will be installed on the virtual machines from a shortlist of tested and approved solutions. In this case, it is best to use specialized light agent-based security systems for virtual environments. This will provide the maximum level of security with minimum collateral problems.
A special case is that of a virtual desktop infrastructure (VDI) hosted in a data center. When virtual machines are used as workstations, each of them is exposed to a multitude of threats during everyday operations. An employee may pick up a malware program when visiting a dangerous website or receive an email with a malicious attachment, while it is not uncommon for malware to spread from a removable media device that has passed between other users.
When such a broad range of potential infection vectors is present, an agentless solution will be insufficient: with its limited functionality, the risk of infection is much higher. If an infection is detected, it will most probably happen too late to prevent any damage. On the other hand, a light agent-based security system is capable of protecting against a much broader range of threats by checking programs that are launched, preemptively blocking a user’s access to dangerous websites, and controlling the processes running in the system.
A third, more resource-intensive, protection option for virtual machines also exists – a ‘regular’, full-agent endpoint protection-class security product. This is a viable choice if there is no access to the hypervisor (e.g. in public clouds such as Amazon or Azure), or if a more obscure hypervisor is used at the data center that is incompatible with specialized security solutions. And finally, these ‘regular’ security systems are developed for a broader range of operating systems. For instance, they can be used to protect virtual machines running under Mac OS.
It should be noted that a security system that is not designed to work in a virtual environment may not be fully compatible with specific virtual machines and may not work properly or may not work at all. Solving these types of issues can take considerable time.
Taking care of data storages
An infected network data storage puts the entire data center at risk, and if anything requires anti-malware protection, it is data storage systems. If this need is not fulfilled, an epidemic may break out, especially if not all the machines located at the data center are connected to a security solution for virtual environments.
Storage Area Networks (SAN) are very easy to protect – all it takes is a security system on the server. This is no different from protecting any other server; in this case, a server solution is implemented, such as Kaspersky Security for File Servers. Things are different with Network Attached Storage (NAS), which all machines in the network are granted instant access to. In this case, a specialized NAS security solution is required.

Network data storage types
Data stored on NAS needs to be protected before it is available to customer machines, meaning support on the NAS side is required. Luckily, most NAS support a number of special protocols and are able to work with external security solutions.

Diagram showing how a NAS protection solution works
When a customer requests a file from NAS (1), the storage sends it to the security system’s server (2). The server scans the file and reports the result to the storage (3). Depending on the security solution’s verdict, NAS provides the file to the customer or denies access (4). For greater reliability, more than one security server can be present in a network. During normal operation, the data storage itself will balance the load between them.
Conclusion
When it comes to securing virtualized data centers, there is no silver bullet solution, nor can there be one, that would ideally solve all problems. What is possible is to choose the optimum security system based on all the relevant factors.
An agentless solution is best for protecting database servers, intranet web servers and machines that are not allowed to host any software besides a fixed set of applications.
If the customer has a choice of several specialized security solutions pre-approved by the provider, a light agent solution is the best option. This will meet the needs of protecting web servers, virtual workstations, and sensitive data processing servers.
Flexibility is particularly relevant when protecting virtual environments, so Kaspersky Lab provides both solutions – the agentless solution and the light agent solution – under one license. This gives the customer a choice between these two variants, and the capability to combine them when necessary, e.g. in environments with different hypervisors, or to address a variety of tasks more efficiently. More detailed information is available here.
The most important thing is to ensure that protection issues are addressed before any annoying and costly problems arise.
Zapomnětlivý vyděrač: Power Worm zašifruje, vydírá, ale zapomene klíč
10.11.2015 Viry
Ransomware je škodlivý software, který v počítači oběti šifruje data, dokud uživatel nezaplatí „výkupné“. Někdy však ani zaplacení nemusí pomoci. Příkladem je nová verze ransomwaru s názvem Power Worm, ve kterém se tvůrce dopustil banální chyby. Jak totiž upozornil web Neowin, software po zablokování dat zapomene dešifrovací klíč.
Na chybu v kódu škodlivého nástroje upozornil bezpečnostní výzkumník Nathan Scott. Power Worm se dosud specializoval na dokumenty Word a Excel kancelářského balíku Office, po poslední aktualizaci však záběr zacílených typů souborů k zašifrování rozšířil.
Zároveň se však při poslední aktualizaci změnil způsob, jakým se soubory po zaplacení odblokují. Vývojář ransomwaru chtěl zjevně proces dešifrování zjednodušit za pomoci využití stejného ID a kódu pro všechny uživatele. Nahrazeny tak měly být unikátní identifikátory. Při odblokování souborů však aktuálně dochází k chybě v jednom ze skriptů, která celý proces znemožní. Postižení uživatelé tak zůstanou natrvalo bez možnosti obnovy svých dat, přičemž zároveň přijdou o peníze.
Jediným způsobem, jakým složitou situaci vyřešit, je využití bodu obnovení systému. Ale nejlepší ochranou je pochopitelně prevence, která vniknutí škodlivého softwaru do počítače vůbec neumožní.
Flaw in Linux.Encoder1 ransomware reveals the decryption key
10.11.2015
Experts at Bitdefender have discovered a flaw in Linux Encryption Ransomware Linux.Encoder1 that exposes the decryption Key used to lock the files.
Last week security experts at Russian antivirus firm Doctor Web reported the discovery of a new Linux ransomware dubbed Linux.Encoder1 that is targeting Linux systems. It has been estimated that tens of users have already fallen victim to this Linux ransomware. The Linux.Encoder1 ransomware encrypts files present on the systems, once a machine is infected it downloads the files containing attackers’ demands and a file containing the path to a public RSA key. The Linux ransomware is launched as a daemon and deletes the original files, subsequently, the RSA key is used to store AES keys used to encrypt files.
“First, Linux.Encoder.1 encrypts all files in home directories and directories related to website administration. Then the Trojan recursively traverses the whole file system starting with the directory from which it is launched; next time, starting with a root directory (“/”). At that, the Trojan encrypts only files with specified extensions and only if a directory name starts with one of the strings indicated by cybercriminals.” states the post published by Dr Web last week.
The Encoder.1 , reportedly distributed via a vulnerability in eBay’s Magento ecommerce platform, demands the payment of one Bitcoin ($380) in exchange for the key needed to recover the files.
Linux.Encoder1 was spread by exploiting a vulnerability in the popular eBay’ Magento e-commerce platform, in order to recover the encrypted files, victims are asked to pay one Bitcoin (roughly $380 at today’s rate), once the ransom is paid the files are decrypted using a private RSA key that retrieves the AES key from encrypted files.
Despite the above algorithms are totally secure and impossible to crack, the researchers at Bitdefender discovered a flaw in the process for the generation of the AES key used by the ransomware.
“We mentioned that the AES key is generated locally on the victim’s computer. We looked into the way the key and initialization vector are generated by reverse-engineering the Linux.Encoder.1 sample in our lab. We realized that, rather than generating secure random keys and [initialization vectors], the sample would derive these two pieces of information from the libc rand() function seeded with the current system timestamp at the moment of encryption.” states the post published by BitDefender.
“This information can be easily retrieved by looking at the file’s timestamp,” Bitdefender said. “This is a huge design flaw that allows retrieval of the AES key without having to decrypt it with the RSA public key sold by the Trojan’s operator(s).”
The flaw allowed the experts at Bitdefender to develop a decryption tool that automatically recovers files encrypted by the Linux.Encoder1. The company also provided a script and the procedure to follow to restore the encrypted files. Given the complexity of the procedure, Bitdefender provides free support to any user in need of assistance.
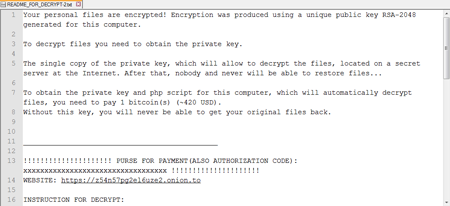
Linux users are advised never to execute untrusted applications with root privileges, and it is important to perform regular backups that could allow them to recover encrypted file sin case of ransomware infections.
“Never run applications that you don’t completely trust as root user. This is a great security risk that will likely compromise your machine or the integrity of the data on it;
Backup early, backup often. If your computer falls victim to ransomware, it would be better to simply restore the affected files from an earlier backup than to pay the decryption fee. “
Yesterday I wrote about another useful tool released by Bitdefender to vaccine users against the CryptoWall 4.0 threat.
New insight on the Rocket Kitten Iranian hacking crew
10.11.2015
Experts from Check Point firm published a new report on the Rocket Kitten APT that include more insight into the activities of the group.
Do you remember the Rocket Kitten ATP?
The Rocket Kitten group has been suspected to be active since 2011 and have been increasing their activity since 2014. The main targets are based in the Middle East, and it seems that their targets are involved in policy research, diplomacy and international affairs like policy research, diplomacy and international affairs.
Several security firms have analyzed the operations conducted by the Rocket Kitten, experts have used different names to reference the hacking crew. FireEye linked the group to the cyber espionage campaign “Operation Saffron Rose“, the experts at iSIGHT Partners discovered the group was using a network of fake accounts on principal social media to spy on US officials and political staff worldwide, the NEWSCASTER network. Again, the experts from ClearSky uncovered the Thamar Reservoir operation that is targeting entities in the Middle East, meanwhile researchers at Trend Micro in March a new hacking campaign dubbed Operation Woolen GoldFish likely run by a threat actor group Rocket Kitten.
The Rocket Kitten group is very active and despite the numerous investigations of security firms it is continuing to conduct cyber espionage operations by using different tools in their arsenal for each hacking campaign.
The Rocket Kitten hackers are now in the headlines thanks to a new report published by the Check Point security firm. Check Point was investigating a phishing attack against one of its customers when discovered a server used by the Rocket Kitten group.
According to the report “Rocket Kitten: A Campaign with 9 Lives,” the hackers used a common XAMPP web server that was poorly configured, allowing the investigators to gain root access without authentication.
The experts at Check Point discovered that more than 1,800 victims were already successfully targeted by Rocket Kitten, their information was stored in the database present on the server.
The analysis of the logs from the phishing server revealed the most visitors came from Saudi Arabia (18%), the United States (17%), Iran (16%), the Netherlands (8%) and Israel (5%).
“This list was analyzed to confirm a strong alignment with nation-state political interests, with specific victims known as adversarial or of intelligence value to Iran.” states the report.

It is curious to note that nearly 26 percent of visitors provided their credentials.
Each victim was associated with a particular Rocket Kitten operator, in one case a single operator harvested details of nearly 700 victims. Another operator phished 522 users as part of a campaign targeting human rights activists, company executives and ministry officials in Saudi Arabia.
“Looking at user names, we can spot some potentially Persian names or aliases such as merah, kaveh, ahzab or amirhosein. These were potentially the campaign ‘operators’—tasked with social engineering and tailoring a phishing page per target.” states the report.
A third operator collected information belonging to 233 individuals in organizations operating in the defense sector, including in NATO countries, the United Arab Emirates, Afghanistan, Thailand, and Turkey.
The hackers also targeted Iranians living abroad, Israeli nuclear scientists, former military officials, national security and foreign policy researchers and Venezuelan entities.

The analysis of the phishing server allowed the investigators to reveal the identity of the main developer of the hacking crew, an individual using the nickname “Wool3n.H4T.”
“In this case, as in other previously reported cases, it can be assumed that an official body recruited local hackers and diverted them from defacing web sites to targeted espionage at the service of their country. As is often the case with such inexperienced personnel, their limited training reflects in lack of operational security awareness, leaving a myriad of traces to the origin of the attack and their true identities,” Check Point said in its report.
If you want to do deeper on the investigation give a look to the excellent “Rocket Kitten: A Campaign with 9 Lives” report published by Check Point.