
Russian hacker Yevgeni Nikulin was extradited to the United States
31.3.2018 securityaffairs BigBrothers
Last week, the Czech Republic announced it had extradited the Russian hacker Yevgeni Nikulin (29) to the United States.
Yevgeni Nikulin was requested by the US for alleged cyber attacks on social networks and by the Russian authorities that charged him with frauds. According to US authorities, the man targeted LinkedIn and Formspring and hacked into the file hosting service Dropbox.
The Russian criminal was arrested in Prague in October 2016 in an international joint operation with the FBI.
The case is in the middle of an arm wrestling between Moscow and Washington, the US Government are accusing Russia to have interfered with 2016 Presidential election through hacking.

Source: US Defense Watch.com
In May 2017, a Czech court ruled that Nikulin can be extradited to either Russia or the United States, leaving the final decision to the Justice Minister Robert Pelikan.
The Czech justice ministry confirmed “the extradition of Russian citizen Yevgeni Nikulin to the United States,” ministry spokeswoman Tereza Schejbalova said on Twitter.
The extradition “took place overnight,” she added.
Nikulin was transferred via plane after midnight Thursday.
“We confirm extradition to the United States,” a spokeswoman said in a text message. “He has already flown out.”
Tens of thousands of misconfigured Django apps leak sensitive data
31.3.2018 securityaffairs Security
The security researcher Fábio Castro discovered tens of thousands of Django apps that expose sensitive data because developers forget to disable the debug mode.
Security researchers have discovered misconfigured Django applications that are exposing sensitive information, including passwords, API keys, or AWS access tokens.
Django is a very popular high-level Python Web framework that allows rapid development of Python-based web applications.
The researcher Fábio Castro explained that installs expose data because developers forget to disable the debug mode for the Django app.



@6IX7ine
28,165 thousand django running servers are exposed on the internet, many are showing secret API keys, database passwords, amazon AWS keys.
A small line http GET http://54.251.149.60:8081/ --body | grep 'DATABASE_URL\|Mysql\|AWS'#Shodan #django #hacking #cybersecurity #infosec
1:43 PM - Mar 27, 2018
278
226 people are talking about this
Twitter Ads info and privacy
Castro found 28,165 apps querying Shodan for Django installs that have debug mode enabled.
I made the same query a few hours later and I obtained 28,911 results.

Many servers with debug mode enabled expose very, the experts discovered server passwords and AWS access tokens that could be used by hackers to gain full control of the systems.
“I found this as I was working with the Django framework on a small project,” Castro told Bleeping Computer “I noticed some error exception and then went searching on Shodan.”
“The main reason [for all the exposures] is the debug mode enabled,” Castro says. “This is not a failure from Django’s side. My recommendation is to disable debugging mode when deploying the application to production.”
Facebook Details Election Security Improvements
31.3.2018 securityweek Social
While under heavy fire for the user privacy blunder involving U.K. firm Cambridge Analytica, Facebook took its time this week to present some of the steps it is taking to protect elections from abuse and exploitation on its platform.
The United States this month announced sanctions against Russia for supposed attempts to influence the 2016 US presidential election, after it charged 13 Russians for their role in a campaign supposedly aimed at tilting the vote.
The United States, however, wasn’t the only country hit by such attacks: Canada, France, and Germany (and possibly other countries too) were hit as well. These cyber-attacks prompted the launch of Google's election security solutions, but Facebook is now looking to strengthen protections against other types of election meddling.
“By now, everyone knows the story: during the 2016 US election, foreign actors tried to undermine the integrity of the electoral process. Their attack included taking advantage of open online platforms — such as Facebook — to divide Americans, and to spread fear, uncertainty and doubt,” Guy Rosen, VP of Product Management, notes.
There are four main election security areas Facebook plans to improve: combating foreign interference, removing fake accounts, increasing ads transparency, and reducing the spread of false news.
According to Alex Stamos, Facebook’s Chief Security Officer, the social platform will focus on tackling four major issues related to fake news, namely the use of false identities, fake audiences, false facts, and false narratives.
After understanding the various kinds of fake news the platform has to deal with, the next step is to distinguish between motivations for spreading misinformation, Stamos also points out. Successfully combating actors requires the ability to prevent them from reaching those goals.
Organized, professional groups are usually after the money, and the misinformation Facebook has encountered so far came from groups looking to gain financially by driving traffic to their sites. Thus, the goal is to increase the cost of such operations and decrease profitability.
Other organized actors focus on artificially influencing public debates. Ranging from private groups to state intelligence services, these actors have both foreign and domestic targets, meaning that an eye should be kept on domestic manipulation as well.
Less organized groups and individuals might spread misinformation as well, either because they like causing chaos and disruption (the so called Internet “trolls”) or because they don’t realize they are sharing false stories.
“Each country we operate in and election we are working to support will have a different range of actors with techniques are customized for that specific audience. We are looking ahead, by studying each upcoming election and working with external experts to understand the actors involved and the specific risks in each country,” Stamos says.
According to Samidh Chakrabarti, Product Manager, Facebook is currently blocking millions of fake accounts each day straight from the creation point, before they can do harm.
The platform looks into pages that attempt to distribute inauthentic civic content and removes them when that is the case, takes against Pages and domains that repeatedly share false news, is doubling the number of people working on safety issues from 10,000 to 20,000, and is partnering with third-party fact-checking organizations to prevent the spreading of fake news.
Facebook is also building a new transparency feature for the ads on the platform. Now in testing in Canada, a feature called View Ads allows anyone to view all the ads that a Facebook Page is running across the platform.
“Next we’ll build on our ads review process and begin authorizing US advertisers placing political ads. This spring, in the run up to the US midterm elections, advertisers will have to verify and confirm who they are and where they are located in the US,” Rob Leathern, Product Management Director, explains.
The process will involve a number of checks and steps and election-related ads will be clearly marked in people’s Facebook and Instagram feeds. The social network also plans the launch of a public archive with all the ads that ran with a political label.
20 Arrested in Italy and Romania for Spear Phishing Scam
31.3.2018 securityweek Crime
Authorities this week arrested 20 individuals in Italy and Romania for their role in a banking phishing scam that defrauded bank customers of €1 million ($1.23 million).
The arrests were the result of a two-year long cybercrime investigation conducted by the Romanian National Police and the Italian National Police, with support from Europol, the Joint Cybercrime Action Taskforce (J-CAT), and Eurojust.
The arrests were made on March 28, following a series of coordinated raids. 9 of the individuals were arrested in Romania and 11 in Italy. The Romanian Police raided 3 houses, while the Italian authorities conducted 10 home and computer searches.
The hackers, Europol reveals, engaged in a banking fraud scheme that netted €1 million from hundreds of customers of 2 major banking institutions.
The group, mainly comprised of Italian nationals, sent spear phishing emails impersonating tax authorities to victims, in an attempt to harvest their online banking credentials.
Unlike common phishing scams, where millions of generic emails are sent to potential victims, spear phishing emails are highly personalized, featuring content that makes them appear as coming from a reputable source, such as the bank.
Since 2016, the investigators have been tracking the manner in which the arrested individuals have been using the stolen online banking credentials to log into their victims’ accounts and transfer funds to the attacker-controlled accounts.
Next, they would withdraw the funds from Automated Teller Machines (ATMs) in Romania, using credit/debit cards linked to the criminal accounts.
The highly organized hackers pursued their criminal activities using encrypted chat applications. They also used intimidating and punitive methods towards affiliates and competitors to establish power, Europol says.
Furthermore, authorities suspect the group of money laundering, as well as drug and human trafficking, prostitution, and participation in a criminal organization.
During the investigation, Eurojust ensured the coordination between the prosecuting and investigating authorities in Italy and Romania, while Europol provided tailored intelligence analysis and expertise.
Earlier this week, Europol announced that a Ukrainian national believed to be the leader of a hacking group that used Carbanak malware to steal money from banks worldwide was arrested in Spain. The cybercriminal group has caused losses totaling over €1 billion ($1.23 billion).
Apple Patches Dozens of Vulnerabilities Across Product Lines
31.3.2018 securityweek Apple
Apple this week released a new set of security patches to address tens of vulnerabilities impacting macOS, iOS, watchOS, and tvOS, as well as Windows software.
Over 40 security bugs were fixed with the release of iOS 11.3 on Thursday. The bugs affect iPhone 5s and later, iPad Air and later, and iPod touch 6th generation.
WebKit was affected the most, with a total of 19 issues resolved. Components such as CoreFoundation, CoreText, File System Events, iCloud Drive, Kernel, Mail, PluginKit, Safari, Security, and Storage were impacted as well.
Exploitation of these flaws could result in an attacker being able to run arbitrary code on the vulnerable device, in malicious applications elevating their privileges, user interface spoofing, data exfiltration, interception of encrypted email contents, denial of service, keylogging, the disabling of features on the device, or in causing device restarts.
Multiple memory corruption issues discovered in WebKit could lead to arbitrary code execution when processing maliciously crafted web content. The bugs, 16 in total, were addressed with improved memory handling.
Apple resolved 35 vulnerabilities with the release of macOS High Sierra 10.13.4, Security Update 2018-002 Sierra, and Security Update 2018-002 El Capitan. The issues impact OS X El Capitan 10.11.6, macOS Sierra 10.12.6, and macOS High Sierra 10.13.3.
Affected components include Admin Framework, APFS, CoreFoundation, CoreText, CoreTypes, Disk Images, Disk Management, File System Events, iCloud Drive, Intel Graphics Driver, Kernel, LaunchServices, Mail, Notes, PluginKit, Security, System Preferences, and Terminal.
Exploitation of these issues could lead to exposed passwords, disclosed user information, elevation of privilege, denial of service, arbitrary code execution, reading of restricted memory, code signing enforcement bypass, interception and exfiltration of encrypted email contents, arbitrary command execution spoofing, and keylogging.
Released on Thursday for OS X El Capitan 10.11.6, macOS Sierra 10.12.6, and macOS High Sierra 10.13.4, Safari 11.1 patches 23 flaws that could lead to address bar spoofing, exfiltration of autofilled data without explicit user interaction, arbitrary code execution, cross-site scripting, ASSERT failure, denial of service, and websites exfiltrating data cross-origin.
Of the 23 vulnerabilities, 2 were found in Safari, 1 in Safari Login AutoFill, while the remaining 20 impact WebKit.
A total of 28 bugs were resolved with the release of tvOS 11.3, impacting Apple TV 4K and Apple TV (4th generation). Affected components include WebKit, Kernel, CoreFoundation, CoreText, File System Events, NSURLSession, Quick Look, Security, and System Preferences.
watchOS 4.3 fixes 22 vulnerabilities in CoreFoundation, CoreText, File System Events, Kernel, NSURLSession, Quick Look, Security, System Preferences, and WebKit. All Apple Watch models are impacted by the bugs.
The tech giant also addressed multiple issues in LLVM with the release of Xcode 9.3. The bugs impact macOS High Sierra 10.13.2 or later.
iCloud for Windows 7.4 patches 20 vulnerabilities, 19 of which impact WebKit, the same as iTunes 12.7.4 for Windows does. The bugs could lead to arbitrary code execution, elevation of privileges, ASSERT failure, denial of service, or malicious websites exfiltrating data cross-origin.
VMware Acquires Threat Detection and Response Firm E8 Security
31.3.2018 securityweek IT
VMware announced this week that it has acquired threat detection and response company E8 Security, whose technology will be used to improve the Workspace ONE digital workspace platform. This is the third acquisition made by VMware in less than two months.
California-based E8 Security emerged from stealth mode in March 2015 and it has raised a total of nearly $22 million – more than $23 million if you count seed funding.
E8 Security has developed a platform that helps organizations detect malicious activity by monitoring user and device behavior. The product also improves incident response by providing the data needed to analyze threats.VMware acquires E8 Security
VMware plans on using E8 Security’s technology to improve its Workspace ONE product, specifically a recently announced intelligence feature that provides actionable information and recommendations, and automation for remediation tasks.
“By adding E8 Security’s user and entity behavior analytics capabilities to insights from VMware Workspace ONE Intelligence, our customers will be able to streamline management, remediation, and automation to improve the employee experience and the security of their digital workspace,” explained Sumit Dhawan, senior vice president and general manager of VMware’s End-User Computing (EUC) business.
VMware announced in February the acquisition of CloudCoreo, a Seattle-based cloud security startup launched less than two years ago. The company has created a product that allows organizations to identify public cloud risks and continuously monitor cloud infrastructure to ensure that applications and data are safe.
The virtualization giant plans on using the CloudCoreo technology and team to help customers secure their applications in the cloud.
Also in February, VMware announced its intent to buy CloudVelox, a company that specializes in providing workload mobility between the data center and public clouds. CloudVelox’s solutions also include data, system and application security capabilities.
Financial terms have not been disclosed for these recent acquisitions.
Prague Extradites Russian Hacker to US for Alleged Cyberattacks
31.3.2018 securityweek BigBrothers
The Czech Republic on Friday said it had extradited a Russian hacker to the United States where he is wanted for alleged cyberattacks on social networks.
Yevgeni Nikulin, who is also sought by his native Russsia on fraud charges, had been in a Prague prison since he was arrested in the Czech capital in 2016 in a joint operation with the FBI.
The case comes amid accusations by Washington that Russia tried to "interfere" through hacking in the 2016 US election won by Donald Trump, charges the Kremlin has dismissed.
The Czech justice ministry "confirms the extradition of Russian citizen Y. Nikulin to the United States," ministry spokeswoman Tereza Schejbalova said on Twitter.
The extradition "took place overnight," she added.
A US government plane left Prague soon after midnight Thursday and landed nine hours later near Washington, according to the website flightaware.com.
Following Nikulin's arrest, Moscow accused Washington of harassing its citizens and vowed to fight Nikulin's extradition.
It then issued a separate arrest warrant for him over alleged theft from the WebMoney settlement system.
The US has charged Nikulin with hacking into social networks LinkedIn and Formspring and into the file hosting service Dropbox, Nikulin's lawyer Martin Sadilek told AFP at the time.
He also said Nikulin alleges that FBI investigators had tried twice to persuade him to confess to cyberattacks on the US Democratic Party.
Last year, a Prague court ruled that Nikulin could be extradited to either Russia or the United States, with the final say left to the Czech justice minister.
Ensuring best website security through SSL Certificate updates.
31.3.2018 securityaffairs Safety
What are the advantages for adopting an SSL Certificates and why is it important to discover and analyze SSL Certificates online?
Secure Socket Layer (SSL) has gained weight with the increasing concern of security for all sensitive data online. In fact, it is the only reliable source for secure business and data handling. The entire information that travels between the computers all over the world is kept fully safe from potential dangers with the help of SSL. The business portals need high-level security to keep their own and their customers’ data away from malicious intentions.
Advantages of SSL Certificates
The safety of the data traveling across the World Wide Web is encrypted by SSL. Only the intended users like sender and receiver can understand it. Any third person involved in data handling cannot pick any of its information. Credit card details, usernames, passwords etc. stay secured identity thieves and hackers. Here are some vital benefits of using SSL:
SSL for Promoting Customers Trust and Business Dealings
A business thrives with its customers. That is why the valuable companies and entrepreneurs priorities to keep their customers satisfied and happy. One top important thing for a customer is his security and privacy. He does not want his sensitive personal details and data to get exposed to any other third person. Once a company ensures its customers that all their dealings are secured and data saved through proper encryption, the business prospers between the contractors.
Improving SEO with SSL Certificates
Google has a strict stance policy for keeping the security and privacy of its consumers intact. To implement this modern security measure for consumers, Google has set HTTPS a ranking tool. The secure HTTPS/SSL version promises the business websites to operate securely and exchange the data between its partners and customers without any fear of loss, hacking or theft.
Meeting the Standards of Payment Card Industry with SSL
Online monetary dealings take place through credit cards and these cards carry highly sensitive and important information. The Credit Card Industry ensures the full protection of this valuable information through a setup standard. The companies can meet this standard of security by using SSL certificates only. A website passes some audits that declare that it is using SSL and complying with the Payment Card Industry standards.
SSL Certificates for Guarding against Scams

SSL certificates are actually procedures that encode a message between two parties: sender and receiver. No third party can snoop in. This cryptographic technology secures the link between a remote browser and a web server. This encrypted message is a hard nut for phishing proxies and hackers. They cannot make any use of the message in case they intercept it which is impossible for them. The coded message shows just like a string of random hash.
Importance of Discovering SSL Certificates
Most of the e-commerce websites operate through the main domain and several subdomains. Each of these is involved in a heavy online business. IT professionals manage these portals through a number of intricate jobs. This leaves the website vulnerable to threats, thus SSL certificates need to be renewed.
Analyzing and discovering SSL certificates at a website is highly important at this stage. There are many companies that provide discovery tools. There is Comodo Certificate Manager. This finds the location, expiry date, and other information on an SSL certificate. Another service is DigiCert which discovers SSL certificates in use, finds neglected or expired certificates and identifies vulnerabilities.
What is CertDB
CertDB, however, is a more comprehensive SSL and TLS certificate discovery service. It is a search engine which can operate throughout the internet and analyze the certificates in real time. This service helps the users to discover the modern information and historical data because it scans the most common ports of the entire IPv4 range. Here are the salient features of CertDB:
Absolutely Free
CertDB is absolutely free for users. Companies and websites owners need not worry about extra expenses for discovering certificates with the help of CertDB.
Comprehensive
CertDB is comprehensive in its search and findings. The different types of SSL certificates and their latest info are fully discovered by CertDB. Experts can find recently registered domains, geographic location, soon to expire certificates, company names and many more
Modern
CertDB scans the internet regularly for certificate-driven data about websites, organizations and certificate issuers. It is accurate and continuously updated. CertDB generates big amounts of data for analysis and discovery of statistical and detailed information about specific companies, their business objectives and integration between them.
Best UI
User-friendly interface makes CertDB easy and favorite for companies and organizations. Entrepreneurs, marketers, and business analysts prefer CertDB because it is trouble-free and does not need IT specialists only for working on it. Developed by skilled, IT specialists and analysts SP*SE team, CertDB is the latest forever-free tool for organizations, students, entrepreneurs, tech geeks and e-commerce owners.
European police agencies coordinated by Europol arrested 20 people for Spear Phishing scam
31.3.2018 securityaffairs Phishing
An international operation conducted by the Romanian National Police and the Italian National Police, with support from Europol, the Joint Cybercrime Action Taskforce (J-CAT), and Eurojust. led to the arrest of 20 individuals involved in a banking spear phishing scam.
According to the investigators, the banking phishing scam allowed crooks to defrauded bank customers of €1 million ($1.23 million).
The international investigation lasted two years, the police conducted a series of coordinated raids. 9 of the individuals were arrested in Romania and 11 in Italy.
The Romanian Police raided 3 houses in the country, while the Italian police raided 10 houses and conducted several computer searches.
“A two-year long cybercrime investigation between the Romanian National Police and the Italian National Police, with the support of Europol, its Joint Cybercrime Action Taskforce (J-CAT) and Eurojust, has led to the arrest of 20 suspects in a series of coordinated raids on 28 March. 9 individuals in Romania and 11 in Italy remain in custody over a banking fraud netted EUR 1 million from hundreds of customers of 2 major banking institutions.” reads the press release published by the Europol.
“The Romanian authorities have conducted 3 house searches, while the Italian National Police ordered the execution of 10 home and computer searches, involving more than 100 Italian policemen.”
According to the Europol, the banking fraud scheme netted €1 million from hundreds of customers of targeted 2 major banks.
Most of the members of the gang are Italians, they were using with spear phishing messages posing as tax authorities, in an attempt to harvest their online banking credentials.
“While the most common phishing scams blast out millions of generic e-mails, spear phishing emails are personally addressed to targeted stakeholders with content to make it appear from a reputable source, such as a bank. Recipients are encouraged to click on a link, which will lead to a fake version of a legitimate website where their account or contact details can be stolen.” continues the press release.
The authorities are monitoring the activity of the crime gang since 2016, once the attackers stole credentials through spear phishing message they log into their victims’ accounts and drained funds.
The gang made the cash out through ATMs in Romania, using payment cards associated with criminal accounts.
The crime gang was using encrypted chat applications for the communication and according to the police they also used intimidating and punitive methods towards affiliates and competitors to establish power.
The authorities suspect the group of other illegal activities, including money laundering, as well as drug and human trafficking, prostitution, and participation in a criminal organization.
This is the second successfully operation announced by the Europol in a few days, earlier this week, the agency announced the arrest of the head of the crime ring behind the Carbanak gang that since 2013 targeted banks worldwide.
Systems at a Power Company in India infected by a ransomware
31.3.2018 securityaffairs Ransomware
A ransomware infected systems at the Uttar Haryana Bijli Vitran Nigam power company in India, crooks demanded 10 million Rupees to get the data back.
The Uttar Haryana Bijli Vitran Nigam power company in India was hacked last week, attackers breached into its computer systems and stole the billing data of their customers.
The hackers demanded 10 million Rupees to get the data back (roughly $152,000 USD).
cerber ransomware
The intrusion occurred on March 21 night, a ransomware infected the systems and the day after the employees discovered that their data were encrypted.
“In a first of the kind of a case in the country, the hackers have stolen the billing data of the Uttar Haryana Bijli Vitran Nigam (UHBVN), one of the two power discoms of Haryana and have demanded Rs One crore in form of bitcoins from the state government to retrieve the data.” states the New Indian Express.
“Sources said that UHBVN which is monitoring electricity billings of nine districts of the state came under cyber attack at 12.17 AM after midnight on March 21 and thus the billing data of thousands of consumers had been hacked as the IT wing of the nigam was target.”
The Haryana Police launched an investigation trying to trace the IP address from where the attack was originated.
The officials at the company are uploading the billing data from the log books, anyway the incident could have a significant impact on the billing activities due to the difficulties to estimate current consumption in absence of data. The good news is that the billing of about 4,000 consumers has already started functioning normally.
“The Nigam had already taken steps much before to phase out the said system and to be replaced by latest, robust and technologically advanced system on cloud services which would be operational by the end of May 2018. The billing of about 4,000 consumers has already started functioning normally” added an official of the Nigam.
Fauxpersky Keylogger masqueraded as Kaspersky Antivirus and spreads via USB drives
31.3.2018 securityaffairs Virus
Security researchers at Cybereason recently discovered a credential-stealing malware dubbed Fauxpersky, that is masquerading as Kaspersky Antivirus and spreading via infected USB drives.
Fauxpersky was written in AutoIT or AutoHotKey, which respectively are a freeware BASIC-like scripting language designed for automating the Windows GUI and general scripting and a free keyboard macro program to send keystrokes to other applications.
The analysis of infected systems revealed the existence of four dropped files, attackers named them as Windows system files: Explorers.exe, Spoolsvc.exe, Svhost.exe, and Taskhosts.exe.
After initial execution, the Fauxpersky keylogger gathers the listed drives on the machine and starts replicating itself to them.
“This AHK keylogger utilizes a fairly straightforward method of self propagation to spread. After the initial execution, the keylogger gathers the listed drives on the machine and begins to replicate itself to them. Let’s examine the process:” reads the analysis.
“This allows the keylogger to spread from a host machine to any connected external drives. If the keylogger is propagating to an external drive, it will rename the drive to match it’s naming scheme.”
The malware renames the external drives to match its naming scheme, the new name is composed of the following convention:
original name:size:”Secured by Kaspersky Internet Security 2017”
it also creates an autorun.inf file to point to a batch script.
One of the dropper files, Explorers.exe, includes a function called CheckRPath() designed creates the files if they are not already present on the drive.
The keylogger created the files with attributes System and Hidden and also creates the necessary directories, with parameters of Read-Only, System, and Hidden.
“When starting the process of creating the component files (HideRFiles()) we begin by starting a loop. This loop allows the keylogger to iterate over the various output files it needs to write to disk in a structured way.” continues the analysis. “We can see that the link (a .lnk shourtcut file), text, and batch files will all be created for each disk to start. Then the value passed to the function gets incremented to allow the created directory to be moved as a whole once the files have been placed there. “
The files are stored in the source directory named Kaspersky Internet Security 2017 when it is copied to the new destination. The folder included a Kaspersky image named Logo.png and a text file containing instructions for users to disable their antivirus if execution fails. The instructions also include a list of security tools “incompatible with Kaspersky Internet Security 2017” (Kaspersky Internet Security included).
Fauxpersky monitors the currently active window using the AHK functions WinGetActiveTitle() and input(), Keystrokes are appended to the file Log.txt that is stored in %APPDATA%\Kaspersky Internet Security 2017.
The malware gains persistence by changing the working directory of the malware to %APPDATA% and creating the Kaspersky Internet Security 2017 folder. It checks that all the necessary files are created in %APPDATA% and copies them there if they aren’t.
The files Spoolsvc.exe is used to change the values of registry keys to prevent the system from displaying hidden files and to hide system files, then it verifies if explorers.exe is running and launches it if not.

Fauxpersky exfiltrates the keylogged data using a Google form.
“Exfiltrating data to a Google form is a very simple and clever way to overcome a lot of the “logistics” involved in data exfiltration. Using this technique means there’s no need to maintain an anonymized command and control server plus data transmissions to docs.google.com is encrypted and doesn’t look suspicious in various traffic monitoring solutions.” Cybereason concluded.
Grindr gay-dating app exposed millions of users’ private data, messages, locations
31.3.2018 securityaffairs Incindent
According to an NBC report, the Grindr gay-dating app was affected by 2 security issues (now patched) that could expose the information of its more than 3 million daily users.
Every day we read of a new data breach, in some cases, exposed data could have a severe impact on the victim.
According to an NBC report, the Grindr gay-dating app was affected by 2 security issues (now patched) that could expose the information of its more than 3 million daily users.
An attacker could have exploited the feature to access location data, private messages to other users, and profile information, even if they’d opted out of sharing such information.
The security issues were identified by Trever Faden, CEO of the property management startup Atlas Lane, while he was working at his website C*ckblocked that allowed users to see who blocked them on Grindr.
Faden discovered that once a Grindr logged in his service, it was possible to access to a huge quantity of data related to their Grindr account, including unread messages, email addresses, and deleted photos.
NBC noted that C*ckblocked exploited a “similar security loophole” to one that was recently used by Cambridge Analytica to create a profile of more than 50 million Facebook users.
“Grindr makes public the location of many of its users, but allows for users to opt out of this feature. Faden found that he could find the location of users who had opted out if they connected their Grindr profiles through his third-party website.” reported NBC.
“One could, without too much difficulty or even a huge amount of technological skill, easily pinpoint a user’s exact location,” Faden explained.

Grindr confirmed it was aware of the issue discovered by Faden and it had addressed them. Faden shut down his service after Grindr changed its policy on access to data on which users had blocked other users.
Grindr recommends its users to avoid using Grindr logins for other apps or web services.
“Grindr moved quickly to make changes to its platform to resolve this issue,” the company said in the statement. “Grindr reminds all users that they should never give away their username and password to any third parties claiming to provide a benefit, as they are not authorized by Grindr and could potentially have malicious intent.”
The company published the following statement on its official Twitter account:
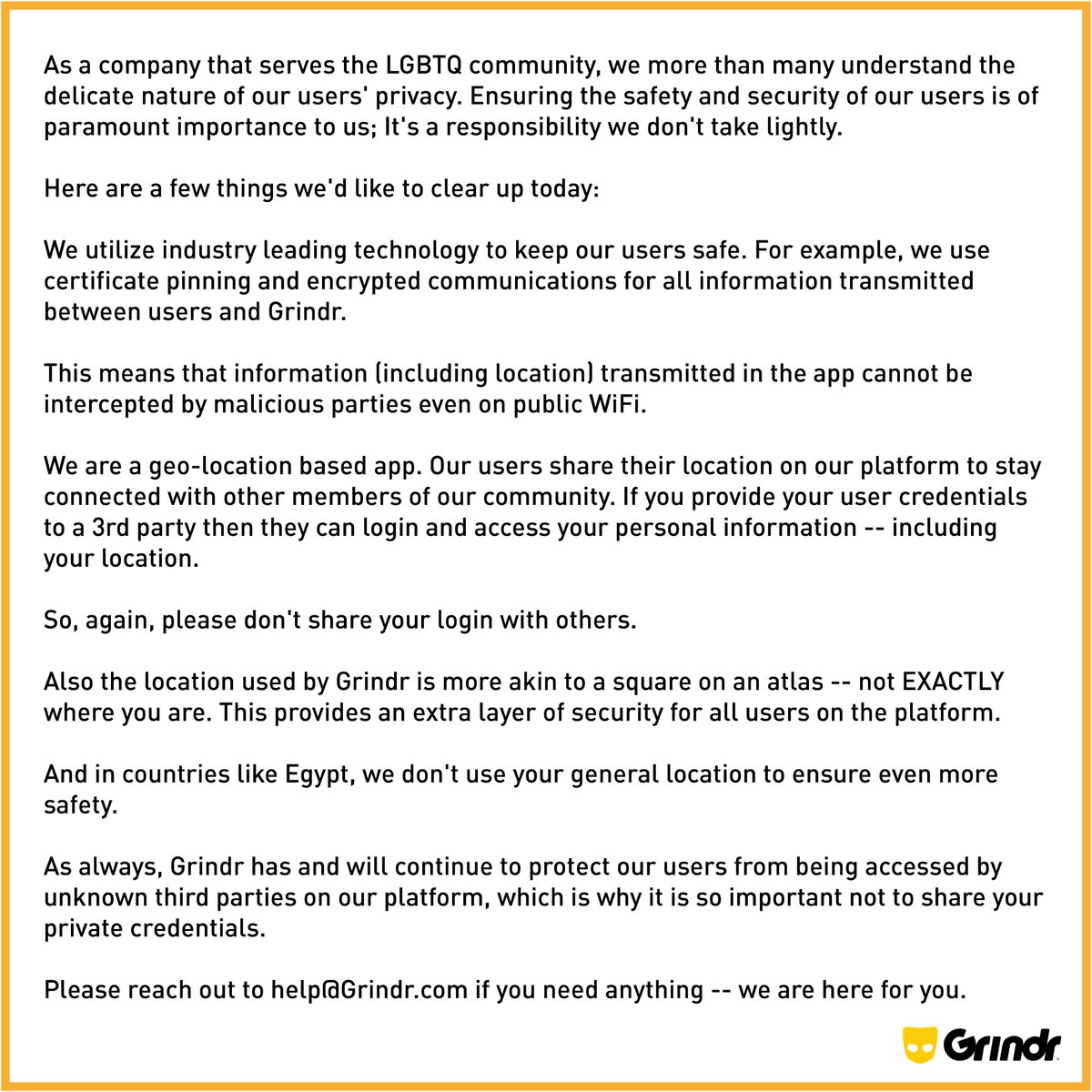
Grindr
✔
@Grindr
As a company that serves the LGBTQ community, we understand the delicate nature of our users’ privacy. Ensuring safety and security of our users is of paramount importance to us and will continue to be our top priority.
5:40 AM - Mar 29, 2018
88
23 people are talking about this
Twitter Ads info and privacy
In the past, other experts found similar issues in the Grindr service, in 2014 researchers at cybersecurity firm Synack found that it allowed any user see the profiles and locations of people. Unfortunately, the problems were not completely fixed and two years after Wired published an interesting article about the experiments of experts that were still able to figure out users’ locations.