
Google to banish cryptocurrency mining extensions from official Chrome Web Store
3.4.2018 securityaffairs Cryptocurrency
Google will ban cryptocurrency mining extensions from the official Chrome Web Store after finding many of them abusing users’ resources without consent.
The number of malicious extensions is rapidly increased over the past few months, especially those related to mining activities.
The company has introduced a new Web Store policy that bans any Chrome extension submitted to the Web Store that mines cryptocurrency.
“Until now, Chrome Web Store policy has permitted cryptocurrency mining in extensions as long as it is the extension’s single purpose, and the user is adequately informedabout the mining behavior.” reads a blog post published by Google.
“Unfortunately, approximately 90% of all extensions with mining scripts that developers have attempted to upload to Chrome Web Store have failed to comply with these policies, and have been either rejected or removed from the store.”
“Starting today, Chrome Web Store will no longer accept extensions that mine cryptocurrency,”
Until now, Google only allowed those cryptocurrency mining extensions that explicitly informed users about their mining activities.
The Mountain View firm announced it will block all mining extensions that are not in compliance and secretly mine cryptocurrency using devices’ resources.
cryptocurrency mining extensions
Google pointed out that the ban on cryptocurrency mining extensions will not affect blockchain-related extensions such as Bitcoin price checkers and cryptocurrency wallet managers.
“Existing extensions that mine cryptocurrency will be delisted from the Chrome Web Store in late June. Extensions with blockchain-related purposes other than mining will continue to be permitted in the Web Store.” continues the blog post.
Google ban is another step to protect its users from hidden risks, it follows the recent announcement to ban advertisements related to cryptocurrency.
“This policy is another step forward in ensuring that Chrome users can enjoy the benefits of extensions without exposing themselves to hidden risks.” concluded Google.
Google is not the unique media firm that imposed a ban on cryptocurrency-related abuses, Twitter recently announced the ban for cryptocurrency-related ads on its platform, in January, Facebook banned all ads promoting cryptocurrency-related initiatives, including Bitcoin and ICOs.
New Bill in Georgia Could Criminalize Security Research
3.4.2018 securityweek Cyber
A new bill passed by the Georgia State Senate last week deems all forms of unauthorized computer access as illegal, thus potentially criminalizing the finding and reporting of security vulnerabilities.
The new bill, which met fierce opposition from the cybersecurity community ever since it first became public, amends the Georgia code that originally considered only unauthorized computer access with malicious intent to be a crime.
“Any person who intentionally accesses a computer or computer network with knowledge that such access is without authority shall be guilty of the crime of unauthorized computer access,” the bill reads (Senate Bill 315).
“Any person convicted of computer password disclosure or unauthorized computer access shall be fined not more than $5,000.00 or incarcerated for a period not to exceed one year, or both punished for a misdemeanor of a high and aggravated nature,” the bill continues.
The original code only made a crime out of the access of a computer or computer network without authority and with the intention of tampering with applications or data; interfering with the use of a computer program or data; or causing the malfunction of the computer, network, or application.
The main issue with the bill is that it does little to protect security researchers who find and responsibly disclose vulnerabilities.
In fact, it is possible that the new bill was created because a security researcher discovered a vulnerability in the Kennesaw State University election systems last year. The flaw was reported ethically and the researcher came clean after being investigated by the FBI.
However, the breach made it to the news and, because the state felt very embarrassed by the incident, the attorney general’s office apparently asked for law that would criminalize so-called “poking around.”
“Basically, if you’re looking for vulnerabilities in a non-destructive way, even if you’re ethically reporting them—especially if you’re ethically reporting them—suddenly you’re a criminal if this bill passes into law,” Scott M. Jones from Electronic Frontiers Georgia pointed out.
The Electronic Frontier Foundation has already called upon Georgia Gov. Nathan Deal to veto the bill as soon as possible. The foundation also points out that S.B. 315 doesn’t ensure that security researchers aren’t targeted by overzealous prosecutors for finding vulnerabilities in networks or computer programs.
EFF also points out that, while Georgia has been a hub for cybersecurity research until now, that it all might change with the adoption of the new bill. Cyber-security firms and other tech companies might no longer find Georgia welcoming and could consider relocating to states that are less hostile to security research.
“S.B. 315 is a dangerous bill with ramifications far beyond what the legislature imagined, including discouraging researchers from coming forward with vulnerabilities they discover in critical systems. It’s time for Governor Deal to step in and listen to the cybersecurity experts who keep our data safe, rather than lawmakers looking to score political points,” EFF notes.
The infosec community has already reacted to the passing of the bill, calling for a veto and pointing out not only that search engines such as Shodan could become illegal in Georgia, but also that security talent is highly likely to migrate to other states.
Professor Andy Green
@secprofgreen
recruitment of georgia security talent to other states is already starting to happen.@GovernorDeal please veto #sb315#gapol https://twitter.com/alexhutton/status/980116433265987584 …
6:53 PM - Mar 31, 2018
9
See Professor Andy Green's other Tweets
Twitter Ads info and privacy
Stephen Gay
@redpalmetto
@secprofgreen - Will the automated scanning and inventory of vulnerable devices within the State of Georgia be illegal after #SB315 is signed into law? @shodanhq
12:30 PM - Mar 30, 2018
1
See Stephen Gay's other Tweets
Twitter Ads info and privacy
Others, however, suggest that some researchers could turn to “irresponsible disclosure” instead.
Robᵉʳᵗ Graham 🤔
@ErrataRob
30 Mar
So Georgia just passed a bill making unauthorized, but well meaning (no damage or theft) access to a computer illegal, meaning anybody noticing a vuln on a website can be sent to jail for up to a year.
Dodge This Security
@shotgunner101
All this will do is force those living in georgia who would have done responsible disclosure to do irresponsible disclosure under an alternative identity. It will still happen just not in the abobe board well structured way we see now.
8:45 AM - Mar 30, 2018
See Dodge This Security's other Tweets
Saks, Lord & Taylor Stores Hit by Data Breach
3.4.2018 securityweek CyberCrime
A data breach at Saks Fifth Avenue and Lord & Taylor stores in North America exposed customer payment card data, parent company Hudson's Bay Company (HBC) announced on Sunday.
The hack, which also impacted its discount store brand Saks OFF 5TH, did not appear to affect HBC’s e-commerce or other digital platforms.
“We identified the issue, took steps to contain it, and believe it no longer poses a risk to customers shopping at our stores,” the announcement said. “We are working rapidly with leading data security investigators to get our customers the information they need, and our investigation is ongoing. We also are coordinating with law enforcement authorities and the payment card companies,” it added.
According to cybersecurity research and threat intelligence firm Gemini Advisory, a cybercrime marketplace called JokerStash announced that over five million stolen credit and debit cards were for sale, which it says were likely stolen from HBC’s stores.
“In cooperation with several financial organizations, we have confirmed with a high degree of confidence that the compromised records were stolen from customers of Saks Fifth Avenue and Lord & Taylor stores,” Gemini said in a blog post, adding that the window of compromise was estimated to be May 2017 to present.”
As of Sunday, roughly 125,000 records had been released for sale so far, Gemini said, with the “entire cache” expected to become available in the following months.
HBC did not provide details on the number of customers/records impacted in the incident.
“The Company is working rapidly with leading data security investigators to get customers the information they need, and the investigation is ongoing. HBC is also coordinating with law enforcement authorities and the payment card companies,” HBC said.
“The details of how these cards were stolen remains unclear at this time, but it’s important that we learn what happened so that others can work to prevent similar breaches," commented Tim Erlin, VP, product management and strategy at Tripwire. "This appears to be the type of breach, through point-of-sale systems, that EMV is supposed to prevent, so we need to ask what happened here. Was EMV in use, and if so, how did the attackers circumvent it?
News of HBC’s breach comes days after sports gear maker Under Armour said that a data breach of its fitness application was hacked, affecting approximately 150 million user accounts.
njRAT Gets Ransomware, Crypto-Currency Stealing Capabilities
3.4.2018 securityweek Cryptocurrency
An updated version of the njRAT remote access Trojan (RAT) is capable of encrypting files and stealing virtual currencies from crypto-wallets, Zscaler warns.
Also known as Bladabindi, njRAT has been around since at least 2013 and is one of the most prevalent malware families. Built in .NET Framework, the malware provides attackers with remote control over the infected systems, utilizes dynamic DNS for command-and-control (C&C), and uses a custom TCP protocol over a configurable port for communication.
Dubbed njRAT Lime Edition, the new malware variant includes support for ransomware infection, Bitcoin grabber, and distributed denial of service (DDoS), while also being able to log keystrokes, spread via USB drives, steal passwords, and lock the screen.
The malware gets a list of running processes on the victim’s machine and uses it to track crypto wallets. Because these store digital currency and may also be connected to the users’ bank accounts, debit cards, or credit cards, it’s no surprise they are of interest to cybercriminals.
Once it has infected a system, the malware also checks for virtual machines and sandbox environments, Zscaler's researchers say. It also gathers large amounts of system information: system name, user name, Windows version and architecture, presence of a webcam, active window, CPU, video card, memory, volume information, installed antivirus, and infection time.
Additionally, the threat monitors the system for specific security-related processes and attempts to kill them to avoid detection.
The new njRAT iteration can also launch ARME and Slowloris DDoS attacks, the security researchers say. The Slowloris tool allows a single machine to take down a server with minimal bandwidth while attempting to keep many connections to the target web server open. ARME attacks also attempt to exhaust the server memory.
Upon receiving commands from the C&C, the malware can delete Chrome cookies and saved logins, turn off monitor, use TextToSpeech to announce text received from C&C, restore normal mouse button functionality, enable task manager, change wallpaper, log keystrokes from the foreground window, share, download files via torrent software, and start Slowloris attacks.
It can also drop and show a ransom note, restart the computer, disable command prompt, delete event logs, stop Bitcoin monitor thread, start the botkiller thread, send system information (CPU/GPU/RAM), check installed Bitcoin wallets and send the information to C&C, and load a plugin and configure it with the C&C server.
njRAT also includes worm-like spreading capabilities. It can monitor the system for connected USB drives and can copy itself to them, while also creating a shortcut to itself using the folder icon.
The malware’s ransomware functionality encrypts users’ files and adds the .lime extension to them. The malware uses the AES-256 symmetric algorithm for encryption, meaning that the same key can be used for decryption as well.
“When Lime is first launched, it will call a RandomString() function, which will attempt to generate an AES key. It generates a 50-byte array from the input string using a random index, and uses the random() function to fetch one character and stores it to the output string,” Zscaler explains.
The function to decrypt the files encrypted by the Lime ransomware is included in the malware itself, the security researchers have discovered.
HiddenMiner Android Cryptocurrency miner can brick your device
3.4.2018 securityaffairs Cryptocurrency
Researchers at Trend Micro recently discovered a new strain of Android miner dubbed ANDROIDOS HIDDENMINER that can brick infected devices
Crooks are looking with increasing interest cryptocurrency mining malware developed for mobile devices.
Researchers at Trend Micro recently discovered a new strain of Android malware dubbed ANDROIDOS HIDDENMINER that abuse device CPU to mine Monero cryptocurrency.
HiddenMiner also implements evasion techniques, it is able to bypass automated analysis by checking if it’s running in a virtualized environment by abusing an Android emulator detector found on Github.
“We uncovered a new Android malware that can surreptitiously use the infected device’s computing power to mine Monero. Trend Micro detects this as ANDROIDOS_HIDDENMINER.” reads the analysis published by Trend Micro.
“This Monero-mining Android app’s self-protection and persistence mechanisms include hiding itself from the unwitting user and abusing the Device Administrator feature (a technique typically seen in SLockerAndroid ransomware).”
The experts were able to find the Monero mining pools and wallets connected to the HiddenMiner malware, they learned that one of its operators withdrew 26 XMR (or US$5,360 as of March 26, 2018) from one of the wallets. This information suggests that the operators are currently active.

HiddenMiner abuse the device’s CPU power to mine Monero, unfortunately, the computational effort is so important that the CPU can overheat causing the device to lock, fail, and be permanently damaged.
“There is no switch, controller or optimizer in HiddenMiner’s code, which means it will continuously mine Monero until the device’s resources are exhausted.” continues the analysis.
“Given HiddenMiner’s nature, it could cause the affected device to overheat and potentially fail.”
This behavior was already observed in the past, the Loapi Monero-mining malware caused a device’s battery to bloat.
HiddenMiner, like Loapi, uses to lock the device screen after revoking device administration permissions.
The ANDROIDOS HIDDENMINER is currently being delivered through a fake Google Play update app, experts found it on third-party app marketplaces.
The miner is mainly affecting users in India and China, but experts fear it could rapidly target other countries.
Malware developers are abusing Device Administration Permission, experts pointed out that users can’t uninstall an active system admin package until device administrator privileges are removed first.
Victims of the HiddenMiner’s cannot remove the miner from device administrator as it employs a trick to lock the device’s screen when a user wants to deactivate its device administrator privileges. Experts explained that it exploits a vulnerability found in Android operating systems except for Nougat and later versions.
“Indeed, HiddenMiner is yet another example of how cybercriminals are riding the cryptocurrency mining wave.” concluded Trend Micro. “For users and businesses, this reinforces the importance of practicing mobile security hygiene: download only from official app marketplaces, regularly update the device’s OS (or ask the original equipment manufacturer for their availability), and be more prudent with the permissions you grant to applications.”
Would Facebook and Cambridge Analytica be in Breach of GDPR?
2.4.2018 securityweek Privacy
The Cambridge Analytica (CA) and Facebook accusations over the U.S. 2016 presidential election campaign, and to a lesser extent between CA and the UK's Brexit VoteLeave campaign, are -- if proven true -- morally reprehensible. It is not immediately clear, however, whether they are legally reprehensible. The matter is currently under investigation on both sides of the Atlantic.
On March 26, both Apple and IBM called for more regulatory oversight on the use of personal data. "I'm personally not a big fan of regulation because sometimes regulation can have unexpected consequences to it, however I think this certain situation is so dire, and has become so large, that probably some well-crafted regulation is necessary," said Apple chief Tim Cook on March 24, 2018.
"If you're going to use these technologies, you have to tell people you're doing that, and they should never be surprised," IBM chief executive Rometty said on March 26, 2018. "(We have to let) people opt in and opt out, and be clear that ownership of the data does belong to the creator," he said.
GDPR - European Data ProtectionSuch regulatory oversight already exists in Europe under national data protection laws, and this will potenyially become global when the European General Data Protection Regulation (GDPR) comes into effect on May 25, 2018. The question is whether Facebook and/or CA would have been in breach of GDPR were it already operational, and therefore whether GDPR will prevent any future repetitions of this sort.
"From Facebook's perspective," MacRoberts LLP senior partner David Flint told SecurityWeek, "the only good point is that the maximum fine under the [current UK] Data Protection Act is £500,000; after 25 May 2018 it would be 4% of Facebook worldwide turnover ($40bn in 2017) -- a potential $1.6bn fine! That's before damages claims."
Cambridge Analytica is an offshoot or SCL, formerly Strategic Communications Laboratories (a private British behavioral research and strategic communication company); and was specifically formed to target the U.S. presidential elections.
The user profile collection
At this stage we have to stress that everything is just a combination of accusation and denial, with nothing yet proven in a court of law. Nevertheless, the accusation is that a Cambridge University academic, Dr. Aleksandr Kogan, developed a Facebook personality quiz app (called 'thisisyourdigitallife') that collected data from some 270,000 app users on Facebook; and also collected their friends' data. Kogan's firm was known as Global Science Research (GSR).
Concerns about the relationship between Facebook user data, GSR, CA, and the U.S. presidential election are not new. In December 2015, the Guardian reported, "Documents seen by the Guardian have uncovered longstanding ethical and privacy issues about the way academics hoovered up personal data by accessing a vast set of US Facebook profiles, in order to build sophisticated models of users' personalities without their knowledge."
The user profiles were at least partly gathered through the process of 'turking' via the Amazon service, the Mechanical Turk. GSR reportedly paid Turkers $1 or $2 to install an app that would "download some information about you and your network … basic demographics and likes of categories, places, famous people, etc. from you and your friends."
An important element of the evolving story is that while it could be argued that the original turkers and anyone who installed Kogan's app had given implied consent to the collection of their personal data, their friends had almost certainly not; nor it seems did anyone give permission for that personal data to be used for political purposes in the presidential election via a third-party, namely Cambridge Analytica.
The scandal
The scandal did not reach public proportions until March 2018 following new reports from the New York Times and the Guardian, and a video interview between CA whistleblower Christopher Wylie and the Guardian. Wylie revealed that "personal information was taken without authorization in early 2014 to build a system that could profile individual US voters in order to target them with personalized political advertisements."
Public awareness was suddenly so high that Facebook -- the ultimate source of the user profiles -- saw an immediate and dramatic drop in its share value. Since March 16, Facebook has lost approximately $80 billion in value (at the time of writing), the FTC has announced an investigation into Facebook's privacy practices, Mark Zuckerberg, Facebook's co-founder and CEO, agreed to testify before Congress (but declined to appear in person before UK lawmakers), and the UK's data protection regulator (the Information Commissioner's Office) has raided CA's offices.
Incidentally, Facebook and CA are also included in an ongoing but lower profile investigation into possible manipulation of the Brexit referendum vote. Speaking before a UK parliamentary select committee this week, Wylie claimed that CA had been involved in the Brexit referendum and that, in his view, the result had been obtained by 'fraud' and 'cheating'.
Cambridge Analytica's alleged involvement in the U.S. election has been known since at least 2015. Facebook made some minor changes to its policies and requested that Kogan and CA delete all gathered user data. It says it believed that had happened -- but if Wylie's accusations are true, that could not have happened.
It is only in March 2018, following the dramatic drop in share value, that Facebook has responded seriously. On March 16, Facebook VP and deputy general counsel Paul Grewel announced, "We are suspending SCL/Cambridge Analytica, [whistleblower] Wylie and Kogan from Facebook, pending further information." One day later he added, "Aleksandr Kogan requested and gained access to information from users who chose to sign up to his app, and everyone involved gave their consent. People knowingly provided their information, no systems were infiltrated, and no passwords or sensitive pieces of information were stolen or hacked." The claim that 'everyone involved gave their consent' is open to debate.
On March 2, Facebook founder Mark Zuckerberg published a personal apology together with news that Facebook would dramatically rein in the amount of personal data that apps can collect. "We will reduce the data you give an app when you sign in -- to only your name, profile photo, and email address. We'll require developers to not only get approval but also sign a contract in order to ask anyone for access to their posts or other private data. And we'll have more changes to share in the next few days."
Nevertheless, two things stand-out. Facebook, CA and Aleksandr Kogan all claim they have done nothing illegal -- and it is only after the incident affected Facebook's bottom line that it has begun to take serious action. It is against this background that Tim Cook has called for "some well-crafted regulation".
GDPR
The EU's General Data Protection Regulation (GDPR) was drafted precisely to protect personal information from misuse. GDPR, is already enacted and due to come into force on May 25, 2018. The question is whether this regulation would provide the future oversight called for by Apple and IBM.
"Absolutely," says Thycotic's chief security scientist Joseph Carson. "This is exactly why EU GDPR has been put in place to protect EU citizens' personal information and ensure that companies have explicit consent to use personal data. Let's think about this - if only the data breach (aka trust) had occurred after May 25th, 2018, and if any of the 50 million impacted users had been EU citizens, Facebook would have been facing a potential whopping $1.6 billion financial penalty from the EU. I believe that would change Facebook's priority on ensuring data is not being misused. This is going to be an example on what could have been if GDPR was enforced."
It could be claimed that GDPR would still fail as a regulation because the impacted users are, ostensibly, all North American. "GDPR applies to the data for any EU resident," comments Nathan Wenzler, chief security strategist at AsTech. "For example, if a U.S. citizen was residing in an EU country, their data would be governed under GDPR when it goes into effect. Citizenship is not the criteria used to determine application of GDPR. Residency is, though, and that makes it far more complicated for companies to determine which of the individual records they have are or are not under the mandates of GDPR."
Dov Goldman, Vice President, Innovation and Alliances at Opus, is even more forthright. "The GDPR privacy rules do not protect non-EU citizens," he told SecurityWeek. "If Facebook can prove that the data released to Cambridge Analytica only contained PII of US persons, Facebook would likely not face any liability under GDPR. There are U.S. regulations that protect American's financial data, but not their personal data (PII), for now."
It's not that clear cut. While the common perception is that GDPR is designed to protect people within the EU (or perhaps the slightly larger European Economic Area), Recital 14 states: "The processing of personal data is designed to serve man; the principles and rules on the protection of individuals with regard to the processing of their personal data should, whatever the nationality or residence of natural persons, respect their fundamental rights and freedoms, notably their right to the protection of personal data."
GDPR is principal-based legislation. Interpretation of the details will be left to the courts to decide, based on their understanding of the intent of the lawmakers. It is, therefore, not entirely clear at this stage whether 'whatever the nationality' means European nationality or global nationality.
David Flint has no doubts. "GDPR would apply (were it in force) to any processing of data carried out by Cambridge Analytica, even if only of US nationals, by virtue of Article 3.1 of the GDPR (Data Controller / Processor based in EU)," he told SecurityWeek. "Article 2 (processing by automated means) would also be relevant." In this view, GDPR is about the processing of personal data, not the nationality of the data subject.
Under GDPR, responsibility is primarily with the data controller, and that responsibility cannot be off-loaded to the data processor. "It is difficult to see how Facebook would not be considered as a Data Controller (or perhaps Controller in Common with Cambridge Analytica)," continued Flint, "given that it collected the data, and/or permitted CA to do so, provided the platform APIs which allowed the data collection and mining; and carried out automatic mass profiling."
There is little doubt that Cambridge Analytica, as a UK company gathering and processing personal data from a firm (Facebook) that operates within the EU would be considered liable under GDPR. Key to this would be the consent issue. It will be argued that by downloading and installing Kogan's app, users gave consent for their data to be used and shared; and that in allowing their data to be shared among friends on Facebook, the friends also gave consent.
This argument won't pass muster. GDPR says, "'the data subject's consent' shall mean any freely given specific and informed indication of his wishes by which the data subject signifies his agreement to personal data relating to him being processed." It is unlikely that even the app downloaders were giving free and informed consent for their personal data to be profiled for political purposes in the U.S. presidential election.
As at least co-controllers with Cambridge Analytica, it is difficult then to see how Facebook would not also be drawn into the issue.
Will GDPR provide the regulation/oversight sought by Apple and IBM?
In the final analysis, Facebook's liability under GDPR for the misuse of users' personal data by Cambridge Analytica will partly come down to an interpretation of whether the legislation covers non-EU subjects. If a single affected user was living in or passing through the EU at the time, there would be no ambiguity. However, in the end, the interpretation will be done by the courts -- although it is worth noting that the European MEP who drove through GDPR as its rapporteur (Jan Philipp Albrecht) has made it clear that he sees GDPR as changing privacy practices throughout the world for all people.
Where there is little ambiguity, however, is that Facebook's processing and privacy practices fell short of that required by GDPR. These requirements do not rely on the nationality or residency of the data subject.
GDPR could well provide the basis of global oversight of large company privacy practices; but we may have to wait until the courts start to interpret the finer details. In the meantime, all companies should carefully consider what happens to the personal data they collect and share. It is possible that sharing or selling that data to a third-party not specified at the time of collection will prove a breach of GDPR.
Cloudflare Launches Free Secure DNS Service
2.4.2018 securityweek Safety
Cloudflare Launches Globally Available Secure Free DNS Resolver
Cloudflare launched a new free service, designed to improve both the speed and the security of the internet, on April Fool's Day (4/1/2018). But this is no joke. The idea is that 4/1 is geekery four ones, or 1.1.1.1 -- the name and heart of the new service.
1.1.1.1 (and 1.0.0.1) is the address of Cloudflare's new, globally available, free DNS resolver service. It is similar to -- but according to Cloudflare -- faster and more secure than, Google's 8.8.8.8 service. Both address speed and security issues in the standard internet DNS look-up process. The biggest problem is security because DNS lookups are primarily controlled by ISPs; and ISPs are commercial organizations seeking to monetize data; and are often heavily controlled or influenced by governments.
In the U.S., ISPs are allowed to sell customer data -- including website visits -- to marketing firms. In the UK, ISPs are required by law to record and hand over such customer data to law enforcement, intelligence and other government agencies. In Turkey, in 2014, the Turkish government censored Twitter by getting ISPs to block DNS requests for twitter.com -- and activists took to the streets to spray paint Google's 8.8.8.8 DNS service as a workaround. Turkey has a history of using the DNS system for censorship, including a block on Wikipedia in April 2017.
Google's service is good and fast, and bypasses ISP instigated blocks, but user data is still available to Google. Cloudflare wants to provide an even faster service, but one where no commercial entity can easily monetize the user data, nor government gain access without a court order. Since the firm is committed to never writing that data to disk, and to wiping all log records within 24 hours (to be independently audited by KPMG with a published public report) there will be little historical data available anyway.
"Cloudflare's business has never been built around tracking users or selling advertising," blogged Matthew Prince, co-founder and CEO of Cloudflare, on Sunday. "We don't see personal data as an asset; we see it as a toxic asset." Cloudflare retains the log data for a maximum of 24 hours for abuse prevention and debugging issues.
“We think it’s creepy that user data is sold to advertisers and used to target consumers without their knowledge or consent,” said Prince. “Frankly, we don’t want to know what people do on the Internet -- it’s none of our business -- and we’ve designed 1.1.1.1 to ensure that we, along with ISPs around the world, can’t.”
The insecurity of the DNS infrastructure struck the team at Cloudflare, he says, as a bug at the core of the Internet, "so we set out to do something about it." The firm decided to combine a DNS Resolver with its existing Authoritative DNS service across its worldwide network, but still needed some memorable IP addresses.
Little could be more memorable than 1.1.1.1. This address was held by the APNIC research group, which agreed to provide it to the new service. "We began testing and found that a resolver, running across our global network, outperformed any of the other consumer DNS services available (including Google's 8.8.8.8)," says Prince.
1.1.1.1 is primarily a consumer service (the IPv6 numbers are 2602:4700:4700::1111 and 2602:4700:4700::1001). Technical details are provided in a separate blog written by director of engineering, Olafur Gudmundsson. The service uses DNS Query Name Minimization defined in RFC7816 to minimize the data sent, and supports privacy-enabled TLS queries on port 853 (DNS over TLS), "so," he writes, "we can keep queries hidden from snooping networks."
Furthermore, he adds, "by offering the experimental DoH (DNS over HTTPS) protocol, we improve both privacy and a number of future speedups for end users, as browsers and other applications can now mix DNS and HTTPS traffic into one single connection."
Cloudflare is working with major browsers, operating systems, app manufacturers, cloud platforms, and router manufacturers to enable DNS over HTTPS. Mozilla is already working to integrate the standard into its Firefox browser:
“Like Cloudflare, Mozilla cares about making the Internet faster and more privacy-conscious so people have a better experience on the web,” says Selena Deckelmann, senior director of engineering, Firefox Runtime at Mozilla. “We are always looking for new technologies like DNS over HTTPS to ensure Firefox is at the cutting edge of speed, privacy and improving life online.”
The resolver is built on the fairly new open source Knot Resolver from CZ NIC -- whose original main developer has been working with Cloudflare for more than two years.
The service uses Cloudflare's 149 data centers distributed around the world. "In March alone, we enabled thirty-one new data centers globally," as far apart as Pittsburgh and Houston, Reykjavik and Tallinn, and Edinburgh and Bogota, notes Gudmundsson; "and just like every other city in our network, new sites run DNS Resolver, 1.1.1.1 on day-one!"
San Francisco, CA-based Cloudflare was founded in 2009. It has raised a total funding amount of $182,050,000 -- the most recent being $110 million Series D funding led by Fidelity Investments in September 2015. It routes traffic through its own global network, blocking DoS attacks, reducing spam and improving performance.
After Cambridge Analytica scandal Facebook announces Election security Improvements
2.4.2018 securityaffairs Social
After Cambridge Analytica case, Facebook announced security improvements to prevent future interference with elections.
Facebook is under the fire after the revelation of the Cambridge Analytica case and its role in the alleged interference to the 2016 US presidential election.
While the analysts are questioning about the interference with other events, including the Brexit vote, Facebook is now looking to prevent such kind of operations against any kind of election.
Guy Rosen, Facebook VP of Product Management declared that everyone is responsible for preventing the same kind of attack to the democracy and announced the significant effort Facebook will spend to do it.
“By now, everyone knows the story: during the 2016 US election, foreign actors tried to undermine the integrity of the electoral process. Their attack included taking advantage of open online platforms — such as Facebook — to divide Americans, and to spread fear, uncertainty and doubt,” said Guy Rosen.
“Today, we’re going to outline how we’re thinking about elections, and give you an update on a number of initiatives designed to protect and promote civic engagement on Facebook.”
Facebook plans to improve the security of elections in four main areas: combating foreign interference, removing fake accounts, increasing ads transparency, and reducing the spread of false news.
Alex Stamos, Facebook’s Chief Security Officer, added that the company always fight “fake news,” explaining that the term is used to describe many malicious activities including:
Fake identities– this is when an actor conceals their identity or takes on the identity of another group or individual;
Fake audiences– so this is using tricks to artificially expand the audience or the perception of support for a particular message;
False facts – the assertion of false information; and
False narratives– which are intentionally divisive headlines and language that exploit disagreements and sow conflict. This is the most difficult area for us, as different news outlets and consumers can have completely different on what an appropriate narrative is even if they agree on the facts.
“When you tease apart the overall digital misinformation problem, you find multiple types of bad content and many bad actors with different motivations.” said Alex Stamos.
“Once we have an understanding of the various kinds of “fake” we need to deal with, we then need to distinguish between motivations for spreading misinformation. Because our ability to combat different actors is based upon preventing their ability to reach these goals.” said Stamos.
“Each country we operate in and election we are working to support will have a different range of actors with techniques are customized for that specific audience. We are looking ahead, by studying each upcoming election and working with external experts to understand the actors involved and the specific risks in each country.”
Stamos highlighted the importance to profile the attackers, he distinguished profit-motivated organized group, ideologically motivated groups, state-sponsored actors, people that enjoy causing chaos and disruption, and groups having multiple motivations such as ideologically driven groups.
Facebook is working to distinguish between motivations for spreading misinformation and implement the necessary countermeasures.
Currently, Facebook already spends a significant effort in combatting fake news and any interference with elections.
Samidh Chakrabarti, Product Manager, Facebook, explained that the social media giant is currently blocking millions of fake accounts each day with a specific focus on those pages that are created to spread inauthentic civic content.
Chakrabarti explained that pages and domains that are used to share fake news is increasing, in response, Facebook doubles the number of people working on safety issues from 10,000 to 20,000. This hard job is mainly possible due to the involvement of sophisticated machine learning systems.
“Over the past year, we’ve gotten increasingly better at finding and disabling fake accounts. We’re now at the point that we block millions of fake accounts each day at the point of creation before they can do any harm.” said Chakrabarti.
“Rather than wait for reports from our community, we now proactively look for potentially harmful types of election-related activity, such as Pages of foreign origin that are distributing inauthentic civic content. If we find any, we then send these suspicious accounts to be manually reviewed by our security team to see if they violate our Community Standards or our Terms of Service. And if they do, we can quickly remove them from Facebook. “
But we all know that Facebook is a business that needs to increase profits, for this reason ads are very important for it.
Facebook is building a new transparency feature for the ads on the platform, dubbed View Ads, that is currently in testing in Canada. View Ads allows anyone to view all the ads that a Facebook Page is running on the platform.
“you can click on any Facebook Page, and select About, and scroll to View Ads.” explained Rob Leathern, Product Management Director.
“Next we’ll build on our ads review process and begin authorizing US advertisers placing political ads. This spring, in the run up to the US midterm elections, advertisers will have to verify and confirm who they are and where they are located in the US,”
This summer, Facebook will launch a public archive with all the ads that ran with a political label.
VPNs & Privacy Browsers leak users’ IPs via WebRTC
2.4.2018 securityaffairs Safety
The security researcher Dhiraj Mishra (@mishradhiraj_) has studied how VPNs & Privacy Browsers leak users’ IPs via WebRTC
Hi Internet,
You might have heard about VPN’s & Privacy Browsers leaking users’ IPs via WebRTC [1] [2]
Summary:
Got CVE-2018-6849 reserved, wrote a Metasploit Module for this issue which uses WebRTC and collects the leak private IP address, however this module may be implemented as a new library in (browser_exploit_server.rb) in MSF. #cheers What is WebRTC ?
WebRTC (Web Real-Time Communication) provides supports to web browser on a real-time communication via API.So let’s get started….There are “multiple” online services and JavaScript code available which uses WebRTC function. Even if you are using VPN’s or Privacy based browsers it leaks your actual public and private IP address.I think this is more of a privacy issue rather than security if we talk specifically in browser-based bug bounty, however, such information can help an attacker to do further recon/attack if they are in the same network.Most of the browser have WebRTC enabled by default,Mozilla Team says :This is a well-known property of webrtc – see the duplicate bug.
http://tools.ietf.org/html/draft-ietf-rtcweb-security-arch-07#section-5.4
Chrome Team says :
We’ve already done what we plan to do, following the guidelines in https://tools.ietf.org/html/draft-ietf-rtcweb-ip-handling-04. And we offer a “Network Limiter” extension (https://chrome.google.com/webstore/detail/webrtc-network-limiter/npeicpdbkakmehahjeeohfdhnlpdklia?hl=en) to turn on more restrictive modes.
Don’t forget Facebook even they have Webkits and it is vulnerable too.
Facebook Team says :
Hi Dhiraj,
Thank you for your report. We’ve looked into your finding but determined the information being leaked is not sensitive enough to warrant a bounty. We may consider leakage of a victims referrer header, but it would have to display a full and potentially sensitive path. However, we have protections in place which prevent this from happening. Although this finding doesn’t qualify we still appreciate your time and effort sending it in.
Okay if your an android lover, you would be aware with android webkit though, The android webkit also leaks IP address as well, I tested this on Nokia 8 android 8.1.0 and the issue still exists.
Android Team says:
The Android security team has conducted an initial severity assessment on this report. Based on our published severity assessment matrix (1) it was rated as not being a security vulnerability that would meet the severity bar for inclusion in an Android security bulletin.
Pheewww ! then what, I started targeting privacy browser and the very first browser came in my mind was DuckDuck Go which has 1,000,000+download rate in Android market and being an privacy based browser the WebRTC was enabled over there and it leaks your IP address, I reported the same to DD Go Security Team.
Duck Duck Go Team says:
Hi again Dhiraj,
Thank you for trying out the new browser and for sending this report,
including the security team. They’re currently looking into this and
I’ll let you know if any further information is needed.
There’s a similar discussion in the Firefox Focus for Android repository
on GitHub, so we’ll keep an eye on that too:
https://github.com/mozilla-mobile/focus-android/issues/609
Hmmmm cool, then CVE-2018-6849was assign for this issue, However I keep on taking follow up for them but they are taking too long time to patch. #Unpatched
Then I thought of creating module for this, many thanks to Brendan Coles who helped me in this and even suggested this can be used has a functionality to a HTTP library would be more useful, as it could be leveraged by existing exploits and info gathering modules.

Working of my MSF Module on DuckDuck Go Privacy Browser
In between RageLtMan also gave his thoughts that “I could actually see a benefit to this being in lib for use by things like #8648. I can inject the separate script ref in the response via the MITM mechanism, but would be cool to just generate and serve the JS directly (for any script we think will have more than 2 weeks of lifetime in browsers). Thanks for the PR”
Outcome:
So lets see, I started with private IP leak vulnerability which turned to CVE-2018-6849, which gave rise to a Metasploit module, which will in turn became a part of MSF library,
now that’s cool. Hope you like the read……
https://datarift.blogspot.it/p/private-ip-leakage-using-webrtc.html
About the Author: Security Researcher Dhiraj Mishra (@mishradhiraj_)
Philippine central bank has thrown an alert after SWIFT hackers hit Malaysia central bank
2.4.2018 securityaffairs Hacking
The Philippine central bank has thrown an alert to local financial institutions following a cyber attack against the SWIFT servers at the Malaysian central bank.
The Philippine central bank has thrown an alert to local financial institutions following a cyber attack against the Malaysian central bank.
According to Malaysian governor, the hackers attempted to steal money through fraudulent wire transfers, the good news is that the attack failed.
Bank Negara Malaysia confirmed that no funds were lost in the cyber attack, the hackers sent fake wire-transfer requests over the SWIFT bank messaging network to the target bank in order to trick it to transfer the money.
“We issued a general alert reminder as soon as we got BNM advisory to be extra careful over the long holiday. Although banks already do that as SOP (standard operating procedure),”Bangko Sentral ng Pilipinas Governor Nestor Espenilla said in a phone message.
“Information sharing is part of enhanced defensive protocols against cyber-crime,”.
At the time of writing is still unclear who is behind the attack or the way the hacker breached the SWIFT systems used by the bank.
“Bank Negara did not say who was behind the hack or how they accessed its SWIFT servers. The central bank, which supervises 45 commercial banks in Malaysia, said on Thursday there was no disruption to other payment and settlement systems the central bank operates because of the cyber attack.” reported the Straits Times.
SWIFT
Bank Negara said it had taken additional security measures to protect its stakeholders.
“All unauthorised transactions were stopped through prompt action in strong collaboration with SWIFT, other central banks and financial institutions,” it said in a statement.
The Philippine banks were also involved in the clamorous 2016 cyber heist when hackers stole US$81 million from the Bangladesh central bank, at the time the hackers transferred money into several accounts at Manila-based Rizal Commercial Banking Corp (RCBC) and then used them into the local casino industry.
The Philippine central bank fined RCBC a record one billion pesos (US$20 million) in 2016 for the failure to prevent the fraudulent transfers of money.
RCBC sustained that a rogue employee was responsible for the movement.
Mr Abu Hena Mohd. Razee Hassan, deputy governor of Bangladesh Bank, said the latest attack against the Malaysian central bank showed that the SWIFT platform remained vulnerable.
“After the attack on our central bank, SWIFT took several measures to protect the system globally but yet this is happening, meaning criminals have more ability and more capable weapons,” Mr Razee Hassan told Reuters in Dhaka.
“So this is the time to further improve the financial transfer system globally.”
Airbnb China will share hosts information with the government
2.4.2018 securityaffairs BigBrothers
Airbnb China announced that it will share user data belonging to Chinese users with the Government to comply with national laws and regulations.
Airbnb announced that it will share user data belonging to Chinese users with the Government. The company is notifying the Chinese users it will share guest’s information with local authorities to comply with national laws and regulations.
According to an email obtained by TechNode, Airbnb hosts with a listing in China were notified by the company by email that their information could be shared with Chinese authorities without further notice starting from 30 March 2018.
“Online short-term rental services operate in a gray area in China, which has strict regulations for hospitality businesses. Guests must check in with a valid ID such as Chinese identification cards or passports and their information are recorded by hotels in a central register operated by local police bureaus.” reads a blog post published by Technode.com.
“For foreign visitors, the rules are even stricter. They need to be registered within 24 hours of arrival into China. If international visitors are not staying at a hotel or guesthouse, they must report to the police and depending on the local regulation, provide documentation such as rental contracts or property titles.”

Source Technode.com
Previously, the Airbnb hosts were submitting passport and other required traveler information.
Airbnb China implemented a “deactivate my China listing” button to allow hosts to remove their listing.
National laws and regulations require the hotel and lodging industry to share data with the government. The Chinese Government aims to automate the information sharing so that traveler’s data are directly available for government agencies.
“Like all businesses operating in China, Airbnb China must comply with local laws and regulations,” said Airbnb spokesman Jake Wilczynski. “The information we collect is similar to information hotels in China have collected for decades.”
In China, Airbnb faces tough competition from local companies Xiaozhu and Tujia, both complying with government laws.
Russian Hacker Who Allegedly Hacked LinkedIn and Dropbox Extradited to US
1.4.2018 thehackernews Social
A Russian man accused of hacking LinkedIn, Dropbox, and Formspring in 2012 and possibly compromising personal details of over 100 million users, has pleaded not guilty in a U.S. federal court after being extradited from the Czech Republic.
Yevgeniy Aleksandrovich Nikulin, 30, of Moscow was arrested in Prague on October 5, 2016, by Interpol agents working in collaboration with the FBI, but he was recently extradited to the United States from the Czech Republic on Thursday for his first appearance in federal court.
Nikulin's arrest started an extradition battle between the United States and Russia, where he faces significantly lesser criminal charges of stealing $3,450 via Webmoney in 2009. But the Czech Republic ruled in favor of the United States.
In the U.S., Nikulin is facing:
3 counts of computer intrusion
2 counts of intentional transmission of information, code, or command causing damage to a protected computer
2 counts of aggravated identity theft
1 count of trafficking in unauthorized access devices
1 count of conspiracy
According to the maximum penalties for each count, Nikulin faces a maximum of 32 years in prison and a massive fine of more than $1 Million.
The U.S. Justice Department accused Nikulin of allegedly hacking into computers belonging to three American social media firms, including LinkedIn, the online cloud storage platform Dropbox and now-defunct social-networking firm Formspring.
Nikulin reportedly gained access to LinkedIn's network between March 3 and March 4, 2012, Dropbox between May 14 and July 25, 2012, and Formspring between June 13 and June 29, 2012.
The hacker allegedly stole accounts of more than 117 Million LinkedIn users and more than 68 Million Dropbox users. Authorities also say that after stealing data from the three companies, Nikulin worked with unnamed co-conspirators to sell the stolen data.
Besides hacking into the three social media firms, the Justice Department also accused Nikulin of allegedly gaining access to credentials belonging to LinkedIn and Formspring employees, which helped him carry out the computer hacks.
Nikulin appeared in Federal District Court in San Francisco on Friday and pleaded not guilty to the charges against him, the New York times reported.
"This is deeply troubling behavior once again emanating from Russia," said Attorney General Jeff Sessions in a statement. "We will not tolerate criminal cyber-attacks and will make it a priority to investigate and prosecute these crimes, regardless of the country where they originate."
Judge Jacqueline Scott Corley scheduled Nikulin's next court appearance for status on April 2, 2018, and scheduled a detention hearing for April 4, 2018.
Apple macOS Bug Reveals Passwords for APFS Encrypted Volumes in Plaintext
1.4.2018 thehackernews Apple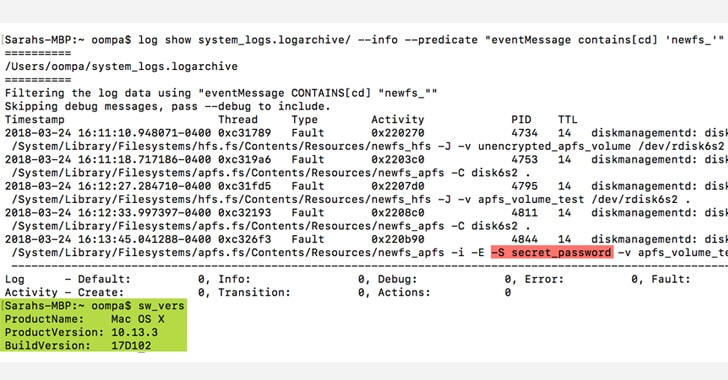
A severe programming bug has been found in APFS file system for macOS High Sierra operating system that exposes passwords of encrypted external drives in plain text.
Introduced two years ago, APFS (Apple File System) is an optimized file system for flash and SSD-based storage solutions running MacOS, iOS, tvOS or WatchOS, and promises strong encryption and better performance.
Discovered by forensic analyst Sarah Edwards, the bug leaves encryption password for a newly created APFS volume (e.g., encrypting USB drive using Disk Utility) in the unified logs in plaintext, as well as while encrypting previously created but unencrypted volumes.
"Why is this a big deal? Well, passwords stored in plaintext can be discovered by anyone with unauthorized access to your machine, and malware can collect log files as well and send them off to someone with malicious intent," Edwards said.
The password for an encrypted APFS volume can easily be retrieved by running following simple 'newfs_apfs' command in the terminal:
log stream --info --predicate 'eventMessage contains "newfs_"'
However, this bug is not as stupid as the previously disclosed root password bug wherein the password hint section was exposing the actual password in the plain text.
Though the exact reason of the programming error is not clear, the researcher believes "it was likely a result of other APFS encryption related bugs (or at least somehow related to it), so perhaps Apple felt it didn't need to provide the additional details."
It should be noted that you would not find the password in the plaintext when converting a non-APFS drive to APFS and then encrypting the drive.
Edwards tested and found the bug affects only macOS 10.13 and 10.13.1, while later versions of macOS High Sierra (including the latest one) have somehow reportedly fixed this loophole.
For more technical details of this bug, you can head on to the original blog post by Edwards.
This issue is the third APFS bug in past six months affecting Apple's latest macOS High Sierra version.
The operating system has seen a number of security issues since its release—from giving away root access to anyone without a password to revealing passwords in plaintext from the password hint feature.
Microsoft's Meltdown Patch Made Windows 7 PCs More Insecure
1.4.2018 thehackernews Vulnerebility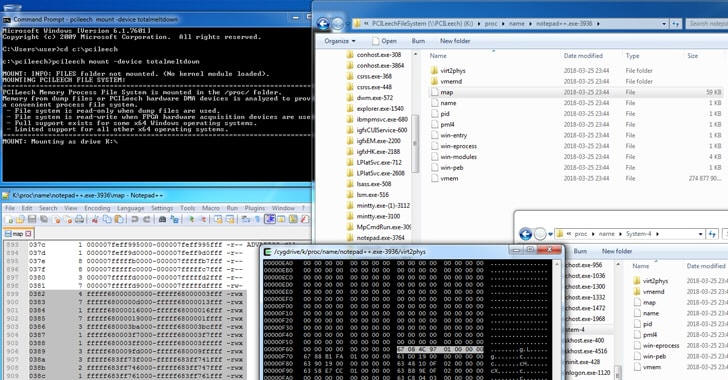
Meltdown CPU vulnerability was bad, and Microsoft somehow made the flaw even worse on its Windows 7, allowing any unprivileged, user-level application to read content from and even write data to the operating system's kernel memory.
For those unaware, Spectre and Meltdown were security flaws disclosed by researchers earlier this year in processors from Intel, ARM, and AMD, leaving nearly every PC, server, and mobile phone on the planet vulnerable to data theft.
Shortly after the researchers disclosed the Spectre and Meltdown exploits, software vendors, including Microsoft, started releasing patches for their systems running a vulnerable version of processors.
However, an independent Swedish security researcher Ulf Frisk found that Microsoft's security fixes to Windows 7 PCs for the Meltdown flaw—which could allow attackers to read kernel memory at a speed of 120 KBps—is now allowing attackers to read the same kernel memory at a speed of Gbps, making the issue even worse on Windows 7 PCs and Server 2008 R2 boxes.
Frisk is the same researcher who previously discovered a way to steal the password from virtually any Mac laptop in just 30 sec by exploiting flaws in Apple's FileVault disk encryption system, allowing attackers to unlock any Mac system and even decrypt files on its hard drive.
The discovery is the latest issue surrounding Meltdown and Spectre patches that were sometimes found incomplete and sometimes broken, making problems such as spontaneous reboots and other 'unpredictable' system behavior on affected PCs.
According to Frisk, the problem with MS' early Meltdown fixes occurs due to a single bit (that controls the permission to access kernel memory) accidentally being flipped from supervisor-only to any-user in a virtual-to-physical-memory translator called PLM4, allowing any user-mode application to access the kernel page tables.
The PML4 is the base of the 4-level in-memory page table hierarchy that Intel's CPU Memory Management Unit (MMU) uses to translate the virtual memory addresses of a process into physical memory addresses in RAM.
The correctly set bit normally ensures the kernel has exclusive access to these tables.
"The User/Supervisor permission bit was set to User in the PML4 self-referencing entry. This made the page tables available to user mode code in every process. The page tables should normally only be accessible by the kernel itself," Frisk explains in his blog post.
To prove his claim, Frisk also provided a detailed breakdown and a proof-of-concept exploit. The issue only affects 64-bit versions of Windows 7 and Windows Server 2008 R2, and not Windows 10 or Windows 8.1 PCs, as they still require attackers to have physical access to a targeted system.
Buggy Patch Allows to Read Gigabytes of Data In a Second
Also since the PML4 page table has been located at a fixed memory address in Windows 7, "no fancy exploits" are needed to exploit the Meltdown vulnerability.
"Windows 7 already did the hard work of mapping in the required memory into every running process," Frisk said. "Exploitation was just a matter of read and write to already mapped in-process virtual memory. No fancy APIs or syscalls required - just standard read and write!"
Once read/write access has been gained to the page tables, it would be "trivially easy" to gain access to the entire physical memory, "unless it is additionally protected by Extended Page Tables (EPTs) used for Virtualization," Frisk said.
All attackers have to do is to write their own Page Table Entries (PTEs) into the page tables in order to access arbitrary physical memory.
Frisk said he has not been able to link the new vulnerability to anything on the public list of Common Vulnerabilities and Exposures. He also invited researchers to test the flaw using an exploit kit he released on GitHub.
UPDATE: Microsoft Releases Emergency Patch
In the wake of the researcher's finding, Microsoft released an emergency patch on Thursday for the vulnerability (CVE-2018-1038) introduced as a Meltdown patch issued by the company earlier this year.
The out-of-band security update for Microsoft Windows 7 and Windows Server 2008 R2 "addresses an elevation of privilege vulnerability in the Windows kernel in the 64-Bit (x64) version of Windows."
According to the Microsoft advisory, the elevation of privilege flaw occurs when the Windows kernel fails to handle objects in memory properly. Successfully exploitation of this flaw could allow an attacker to run arbitrary code in kernel mode.
"An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights," the advisory states.
No other Windows OS version is impacted, except Windows 7 Service Pack 1 (x64) and Windows Server 2008 R2 Service Pack 1 (x64).
So all admins and users of Windows 7 and Windows 2008R2 are strongly recommended to update their systems as soon as possible.