
Facebook's Sandberg Says Other Cases of Data Misuse Possible
7.4.2018 securityweek Social
Facebook was aware more than two years ago of Cambridge Analytica's harvesting of the personal profiles of up to 87 million users and cannot rule out other cases of abuse of user data, chief operating officer Sheryl Sandberg said.
Sandberg, who joined Facebook in 2008 from Google, has been largely silent since the privacy scandal broke but she gave interviews on Thursday and Friday to National Public Radio and NBC's "Today Show."
"We know that we did not do enough to protect people's data," Sandberg told NPR. "I'm really sorry for that. Mark (Zuckerberg) is really sorry for that, and what we're doing now is taking really firm action."
"Safety and security is never done, it's an arms race," she said. "You build something, someone tries to abuse it."
"But the bigger (question) is, 'Should we have taken these steps years ago anyway?'" Sandberg said. "And the answer to that is yes.
"We really believed in social experiences, we really believed in protecting privacy, but we were way too idealistic," she said.
"We did not think enough about the abuse cases and now we're taking really firm steps across the board."
Facebook has been scrambling for weeks in the face of the disclosure of the hijacking of private data by the British consulting group working for Donald Trump's 2016 presidential campaign.
'That's on us'
Sandberg said Facebook was first aware two and a half years ago that Cambridge Analytica had obtained user data from a researcher who put up a poll on Facebook.
"When we received word that this researcher gave the data to Cambridge Analytica, they assured us it was deleted," she said. "We did not follow up and confirm, and that's on us — and particularly once they were active in the election, we should have done that."
Sandberg was asked by the "Today Show" if other cases of misuse of user data could be expected.
"We're doing an investigation, we're going to do audits and yes, we think it's possible, that's why we're doing the audit," she said.
"That's why this week we shut down a number of use cases in other areas — in groups, in pages, in events — because those are other places where we haven't necessarily found problems, but we think that we should be more protective of people's data," she told NPR.
Sandberg said that starting Monday, the social network will put on top ot its news feed "a place where you can see all the apps you've shared your data with and a really easy way to delete them."
Sandberg said Facebook also should have been more proactive in dealing with Russian interference in the 2016 presidential election.
"That was something we should have caught, we should have known about," she told NPR. "We didn't. Now we've learned."
"We're going after fake accounts," she told the "Today Show." "A lot of it is politically motivated but even more is economically motivated."
Zuckerberg accepted responsibility this week for the failure to protect user data but maintained he was still the best person to lead the network of two billion users.
He is to appear before a US congressional panel next week to address privacy issues.
Facebook shares were down slightly in mid-morning trading in New York on Friday.
Best Buy Impacted by Payment Card Breach
7.4.2018 securityweek Incindent
After Delta Air Lines and Sears Holdings, Best Buy has also come forward to warn customers that their payment card information may have been compromised as a result of a breach suffered by online services provider [24]7.ai.
Similar to Delta and Sears, Best Buy contracted [24]7.ai for online chat/support services. The retailer says it will contact impacted customers and provide free credit monitoring if needed.
Best Buy has not specified exactly how many of its customers are impacted, but noted that “only a small fraction of our overall online customer population could have been caught up in this [24]7.ai incident, whether or not they used the chat function.”
San Jose, CA-based [24]7.ai provides customer acquisition and engagement solutions to organizations in a wide range of sectors and any of them could be impacted by this incident. Its website lists several major firms, but some of them apparently no longer do business with the company.
Delta has set up a dedicated page on its website and it has provided some new information regarding the incident. According to the airline, cybercriminals planted a piece of malware in [24]7.ai software, which captured some payment card data between September 26 and October 12, 2017.
“[The malware] made unauthorized access possible for the following fields of information when manually completing a payment card purchase on any page of the delta.com desktop platform during the same timeframe: name, address, payment card number, CVV number, and expiration date,” Delta explained.
The airline believes the incident may impact hundreds of thousands of customers, but it cannot say definitively whether any information has actually been stolen by the attackers.
It appears that the malware involved in this attack is capable of harvesting payment card information entered on websites that use the [24]7.ai chat software. Consumers may be impacted even if they have not directly used the chat functionality, which has only been leveraged as a point of entry to the websites of major organizations. These types of attacks have been common in the past years.
Sears Holdings, the company that owns the Sears and Kmart retail store brands, says the incident has impacted the credit card information of less than 100,000 customers.
Sears and Delta said they were only notified by [24]7.ai in mid and late March, several months after the breach had been supposedly contained.
Contacted by SecurityWeek, [24]7.ai said it could not provide any additional information about the breach, citing client confidentiality agreements.
New Strain of ATM Jackpotting Malware Discovered
7.4.2018 securityweek Virus
A new type of ATM jackpotting malware has been discovered. Dubbed ATMJackpot, the malware appears to be still under development, and to have originated in Hong Kong. There are no current details of any deployment or use.
ATMJackpot was discovered and analyzed by Netskope Threat Research Labs. It has a smaller footprint than earlier strains of jackpotting malware, but serves the same purpose: to steal money from automated teller machines (ATMs).
ATM jackpotting -- also known as a logical attack -- is the use of malware to control cash dispensing from individual ATMs. The malware can be delivered locally to each ATM via a USB port, or remotely by compromising the ATM operator network.
Jackpotting has become an increasing problem in recent years, originally and primarily in Europe and Asia. In 2017, Europol warned that ATM attacks were increasing. "The malware being used has evolved significantly and the scope and scale of the attacks have grown proportionately," said Steven Wilson, head of Europol's EC3 cybercrime center.
The first attacks against ATMs in the U.S. were discovered in January 2018 following an alert issued by the Secret Service. In March 2018, the alleged leader of the Carbanak group was arrested in Spain. Carbanak is believed to have stolen around $1.24 million over the preceding years. Its method was to compromise the servers controlling ATM networks by spear-phishing bank employers, and then use foot soldiers (mules) to collect money dispensed from specific ATMs at specific times.
It is not clear whether the ATMJackpot malware discovered by Netskope is intended to be manually installed via USB on individual ATMs, or downloaded from a compromised network. Physical installation on an ATM is not always difficult. In July 2017, IOActive described how its researchers could gain access to the Diebold Opteva ATM. It was achieved by inserting a metal rod through a speaker hole and raising a metal locking bar. From there they were able to reverse engineer software to get access to the money vault.
Jackpotting malware is designed to avoid the need to physically break into the vault. It can be transferred via a USB port to the computer part of the ATM that controls the vault. Most ATMs use a version of Windows that is well understood by criminals. ATMJackpot malware first registers the windows class name 'Win' with a procedure for the malware activity.
The malware then populates the options on the window and initiates a connection with the XFS manager. The XFS subsystem provides a common API to access and manipulate the ATM devices from different vendors. The malware then opens a session with the service providers and registers to monitor events. It opens a session with the cash dispenser, the card reader and the PIN pad service providers.
It is then able to monitor events and issue commands. It can read data from the PIN pad, dispense cash, and eject cards.
Whether ATMJackpot will be used in earnest is not yet known. Nevertheless, it is a new example of the malware used in a growing problem -- stealing money from the world's automated teller machines.
Los Altos, CA-based Netskope is a cloud access security broker (CASB). Founded in 2012, it announced an oversubscribed Series E funding round that raised $100 million in June 2017, bringing the total raised by the company to $231.4 million.
Critical Flaws Expose Natus Medical Devices to Remote Attacks
7.4.2018 securityweek Vulnerebility
Researchers at Cisco Talos have identified several critical vulnerabilities that expose Natus medical devices to remote hacker attacks. The vendor has released firmware updates that patch the flaws.
The vulnerabilities allow remote code execution and denial-of-service (DoS) attacks and they impact the Natus NeuroWorks software, which is used by the company’s Xltek electroencephalography (EEG) equipment to monitor and review data over the network.
According to Cisco, an attacker with access to the targeted network can remotely execute arbitrary code on the device or cause a service to crash by sending specially crafted packets. An attack does not require authentication.
“Vulnerable systems are searched for by attackers as points of ingress and persistence within computer networks. A vulnerable system can be compromised by threat actors, used to conduct reconnaissance on the network, and as a platform from which further attacks can be launched,” Talos warned.
Remote code execution on vulnerable Natus devices is possible due to four different functions that can cause a buffer overflow. All of the code execution flaws have been rated “critical” with CVSS scores of 9 or 10. The DoS vulnerability, rated “high severity,” is caused by an out-of-bounds read issue.
Cisco said it reported the vulnerabilities to Natus in July 2017, but the bugs were only confirmed in October. The flaws have been tested on Natus Xltek NeuroWorks 8 and they have been patched with the release of NeuroWorks 8.5 GMA2.
Healthcare facilities that use the affected products have been advised to install the update as soon as possible. The risk of attacks involving these vulnerabilities is relatively high considering that the devices are widely deployed – Natus was recently reported to have a 60 percent share in the global neurodiagnostic market. Furthermore, Cisco has made available technical information for each of the vulnerabilities.
The healthcare industry has been increasingly targeted by malicious actors, including in attacks involving ransomware and theft of sensitive information. The infosec community and authorities have issued numerous warnings, and recent reports show that there are plenty of healthcare product vulnerabilities that hackers could exploit in their operations.
Researchers Link New Android Backdoor to North Korean Hackers
7.4.2018 securityweek Android
The recently discovered KevDroid Android backdoor is tied to the North Korean hacking group APT37, Palo Alto Networks researchers say.
Also tracked as Reaper, Group 123, Red Eyes, and ScarCruft, the threat group was observed earlier this year to be using a Flash Player zero-day vulnerability and has been expanding the scope and sophistication of its campaigns over the past months.
Recently, the group was said to have targeted victims with Android spyware via spear phishing emails. Cisco’s Talos security researchers analyzed the malware, which they called KevDroid, but weren’t able to find a strong connection with the group.
According to Palo Alto Networks, however, KevDroid is indeed part of APT37’s arsenal of mobile tools. Furthermore, the security researchers were able to find a more advanced version of the spyware, as well as Trojanized iterations of legitimate applications that are used as downloaders for the malware.
The Android spyware was initially found to be masquerading as an anti-virus app from Naver, a large search and web portal service provider in South Korea.
One version of the malware, Palo Alto’s Ruchna Nigam discovered, would call home to cgalim[.]com, a domain already associated with the Reaper group’s non-mobile attacks. Artefacts from the original malware variant eventually revealed a more advanced iteration of the malware, the security researcher notes.
The threat actor apparently uses two Trojanized application versions to distribute Android spyware variants. The legitimate applications – Bitcoin Ticker Widget and PyeongChang Winter Games – are distributed through Google Play, but the malicious variants never made it to the official app store.
The two Trojanized applications, which are signed with the same certificate, contact the same URL to fetch payloads, and were observed serving an advanced iteration of the Android spyware. Each of the malicious apps was created to “respectively download and drop one specific variant of Reaper’s Android spyware,” the Nigam says.
Once installed, the apps would display a message asking the user to update them. If the user accepts the update, however, the malicious payload is downloaded instead and saved as AppName.apk. Next, the payload is loaded and the user is asked to confirm the installation.
The spyware can record audio and video, capture screenshots, grab the phone’s file listing, fetch specific files, download a list of commands, get device info, and root the device. Additionally, it can steal voice recordings from incoming and outgoing calls, call logs, SMS history, contact lists, and information on registered accounts on the phone.
Unlike the previously detailed variants of the malware that used an open source library to record calls, the most recent – and more advanced – variant of the malware writes its own call recording library.
“The emergence of a new attack vector, followed by the appearance of new variants disguising themselves as currently relevant applications like the Winter Olympics, indicates expanding operations of the Reaper group that are actively in development,” Nigam concludes.
RSA to Acquire Behavioral Analytics Firm Fortscale
7.4.2018 securityweek IT
RSA on Thursday announced that it has entered an agreement to acquire Fortscale, a company that provides behavioral analytics solutions. Financial terms of the deal have not been disclosed.
Fortscale’s technology is designed to identify threats using a combination of predictive, big data analytics and machine learning. It automatically identifies deviations from normal behavior and warns security teams of potential risks, such as shared user credentials, remote access anomalies, and abuse of privileged user accounts.RSA acquires Fortscale
As a result of the acquisition, RSA wants to provide customers new user and entity behavioral analytics (UEBA) capabilities through its NetWitness Platform.

“RSA NetWitness UEBA directly addresses and overcomes obstacles that standalone solutions have encountered due to their high cost and high touch requirements,” said Idan Tendler, CEO and co-founder of Fortscale. “RSA NetWitness UEBA requires minimal customization and no manual tuning. It is designed to detect unknown threats and to address malicious behavior in which exploits have received elevated permissions.”
Since its launch in 2013, Fortscale has raised a total of $23 million, including $7 million roughly one year ago.
RSA also announced a new version of its NetWitness Platform. Version 11.1 includes not only UEBA Essentials, but also Endpoint Insights, which helps organizations manage endpoints, and Dynamic Log Visibility, which uses dynamic parsing technology to provide instant access to log data.
Later this month, RSA will also make available NetWitness Orchestrator, a product powered by Demisto that should make it easier for security teams to investigate incidents. The NetWitness Orchestrator suggests analyst assignments, enhances playbooks, and identifies the best course of action for investigations, RSA said.
VirusTotal presents its new Android Droidy sandbox
7.4.2018 securityaffairs Android
VirusTotal announced on Thursday the launch of a new Android sandbox, named Droidy sandbox, that will replace the previous one that was designed in 2013.
“Recently we called out Additional crispinness on the MacOS box of apples sandbox, continuing with our effort to improve our malware behavior analysis infrastructure we are happy to announce the deployment of a new Android sandbox that replaces the existing system that was developed back in 2013.” reads the announcement published by Virus Total.
The Droidy sandbox was specifically designed to analyzed mobile threats, it can be used to obtain information on network communications and SMS-related activities, file system interactions, SQLite database usage, permissions, Java reflection calls, process and service actions, registered receivers, and crypto-related activity.
The Droidy sandbox is integrated with other services, such as VirusTotal Graph and VirusTotal Intelligence, the company aims to create a complete environment for malware analysis that helps professionals to analyzed the threats.
If you are interested in more info about the new Droidy sandbox just select it from the drop-down menu in the Behavior section, it also includes the Tencent HABO analysis system.
It is an important improvement for the VirusTotal platform, data from Droidy sandbox are complementary to the Tencent HABO.
The two sandboxes are part of a multisandbox project that aims to aggregate malware analysis sandbox reports.
“VirusTotal is much more than just an antivirus aggregator; we run all sorts of open source/private/in-house tools to further characterize files, URLs, IP addresses and domains in order to highlight suspicious signals.” states VirusTotal.
“Similarly, we execute a variety of backend processes to build relationships between the items that we store in the dataset, for instance, all the URLs from which we have downloaded a given piece of malware.“
Selecting Droidy sandbox from the behavior menu it is possible to see general information about the analyzed sample. Users can also go deeper in their analysis and “dig into the hooked calls and take a look at the screenshots generated when running the apps.”

“To understand the extent to which this is an improvement with respect to the 2013 setup, you can take a look at the following report. It displays by default the output of the old sandbox. Use the selector to see the new report with VirusTotal Droidy:
https://www.virustotal.com/#/file/f1475147b50a2cc868e308d87457cebd35fd6443ef27adce67a6bb3e8b865073/behavior” continues VirusTotal.
“Wrapping up, don’t think of this as just new functionality to dissect individual threats. All of this data contributes to the bigger picture and increases the power of our telescope lens that sheds light into malicious behaviors on the Internet.” concluded VirusTotal.
A Remote Code Execution Vulnerability found in the Spring Framework. Upgrade it now!
7.4.2018 securityaffairs Vulnerebility
Security experts have discovered a vulnerability in the Spring Framework that could be exploited by a remote attacker to execute arbitrary code on applications built with it.
Security researchers have discovered three vulnerabilities in the Spring Development Framework, one of them could be exploited by a remote attacker to execute arbitrary code on applications built with it.
Pivotal’s Spring is widely used open source framework for the development of web applications. Affected Spring Framework versions are 5.0 to 5.0.4, 4.3 to 4.3.14, and older versions.
The security advisory published by Pivotal includes technical details of the following three vulnerabilities;
CVE-2018-1270: Remote Code Execution with spring-messaging, it is rated as “Critical”.
“Spring Framework versions 5.0 to 5.0.4, 4.3 to 4.3.14, and older unsupported versions allow applications to expose STOMP over WebSocket endpoints with a simple, in-memory STOMP broker through the
spring-messaging
module.” reads the advisory.
An attacker can send specially crafted messages to the broker in order to trigger the remote code execution flaw.
CVE-2018-1271: Directory Traversal with Spring MVC on Windows, it is rated as “High”.
“Spring Framework versions 5.0 to 5.0.4, 4.3 to 4.3.14, and older unsupported versions allow applications to configure Spring MVC to serve static resources (e.g. CSS, JS, images).” reads the advisory.
An attacker can use a specially crafted URL to lead a directory traversal attack.
CVE-2018-1272: Multipart Content Pollution with Spring Framework, it is rated as “Low”.
“When Spring MVC or Spring WebFlux server application (server A) receives input from a remote client, and then uses that input to make a multipart request to another server (server B), it can be exposed to an attack, where an extra multipart is inserted in the content of the request from server A, causing server B to use the wrong value for a part it expects. This could to lead privilege escalation, for example, if the part content represents a username or user roles.” reads the advisory.
An attacker that is able to guess the multipart boundary value chosen by server A for the multipart request to server B could successfully exploit the issue. This means that the attacker needs to gain the control of the server or have to find a way to see the HTTP log of server A through a separate attack vector.

The above issued are addressed with the Spring Framework 5.0.5 and 4.3.15. Pivotal also released Spring Boot 2.0.1 and 1.5.11.0.
Development teams need to upgrade their software to the latest versions as soon as possible.
Best Buy Hit by [24]7.ai Payment Card Breach
6.4.2018 securityaffairs Incindent
After Delta Air Lines and Sears Holdings, Best Buy has also come forward to warn customers that their payment card information may have been compromised as a result of a breach suffered by online services provider [24]7.ai.
Similar to Delta and Sears, Best Buy contracted [24]7.ai for online chat/support services. The retailer says it will contact impacted customers and provide free credit monitoring if needed.
Best Buy has not specified exactly how many of its customers are impacted, but noted that “only a small fraction of our overall online customer population could have been caught up in this [24]7.ai incident, whether or not they used the chat function.”
San Jose, CA-based [24]7.ai provides customer acquisition and engagement solutions to organizations in a wide range of sectors and any of them could be impacted by this incident. Its website lists several major firms, but some of them apparently no longer do business with the company.
Delta has set up a dedicated page on its website and it has provided some new information regarding the incident. According to the airline, cybercriminals planted a piece of malware in [24]7.ai software, which captured some payment card data between September 26 and October 12, 2017.
“[The malware] made unauthorized access possible for the following fields of information when manually completing a payment card purchase on any page of the delta.com desktop platform during the same timeframe: name, address, payment card number, CVV number, and expiration date,” Delta explained.
The airline believes the incident may impact hundreds of thousands of customers, but it cannot say definitively whether any information has actually been stolen by the attackers.
It appears that the malware involved in this attack is capable of harvesting payment card information entered on websites that use the [24]7.ai chat software. Consumers may be impacted even if they have not directly used the chat functionality, which has only been leveraged as a point of entry to the websites of major organizations. These types of attacks have been common in the past years.
Sears Holdings, the company that owns the Sears and Kmart retail store brands, says the incident has impacted the credit card information of less than 100,000 customers.
Sears and Delta said they were only notified by [24]7.ai in mid and late March, several months after the breach had been supposedly contained.
Contacted by SecurityWeek, [24]7.ai said it could not provide any additional information about the breach, citing client confidentiality agreements.
Improved Visibility a Top Priority for Security Analysts
6.4.2018 securityweek Security
Security Analysts Require Improved Visibility as well as Improved Threat Detection
Vendors listen to existing and potential customers to understand how to improve their products over time. At the smallest level, they use focus groups. At the largest level they employ market research firms to query thousands or more respondents from relevant employments and industry sectors. Some way in-between, they run their own relatively small-scale surveys primarily for their own benefit.
This is what Boston, MA-based next-gen endpoint protection firm Barkly did, querying some 70 IT and security professionals to understand what mid-market users look for and are not currently getting from their endpoint security controls. Not surprisingly, 60% of the respondents say that adding to or improving protection is their top priority -- possibly because 88% of them consider that there are types of attacks (for example, the growing practice of employing fileless attacks) that current security simply does not block.
More surprising, however, is that 40% of the respondents prioritize improving forensic and response capabilities as their current top priority. This may partly be driven by the new breed of regulations -- and in particular, GDPR -- that demand increasingly rapid incident disclosure, and remediation of the breach vector to prevent repeats.
Alternatively, this may simply be down to a high ratio of alerts (including both true-positives and false-positives) to human-resources with their current products. While the sample size of the survey is small, forty-five percent of the respondents, Barkly says, "admit they currently don’t have enough time to investigate and respond to the incidents they’re already seeing now. Adding to that workload with complex endpoint detection and response (EDR) solutions without considering current limitations is obviously not a productive answer."
The need for improved automation to reduce the time for manual involvement also shows in users' top frustrations with current solutions. Twenty-seven percent of the respondents are concerned with poor visibility into incidents, and 25% are concerned about limited investigative/response features. A further 18% find current solutions difficult and time-consuming to manage.
The need to make incident response faster and simpler is the driving force behind Barkly's new version 3.0 launched today. Rapid response comes from two new features: endpoint isolation; and file quarantine and delete. The first enables an administrator to instantly remove an affected device from the network while the incident is investigated.
This is a one-click operation via the Barkly CommandIQ management portal, and can be enacted from any location, on- or off-site at any time via any remote or mobile device with internet access. As soon as the affected device is cleaned or confirmed to be clean, it can just as easily be returned to the network. It means that both an alert and its response can be handled instantly without requiring the security administrator to be in his office or to return to his office first.
The second feature automatically quarantines a blocked malicious executable. This instantly contains the threat, but maintains administrative access to the file for further investigation before deletion. Again, this can be performed either from the administrator's office desktop, or remotely via a mobile device.
A further two new features help analysts to investigate incidents. The first provides an automated interactive method for users to provide context, which is fed back to the analyst, whenever a file or process is blocked. The second is Incident Path Visualization, enabling analysts to trace malicious processes back to their origins.
Together, these features provide rapid forensic insight into the cause of the incident, allowing the security team to leverage the insights gained to improve their security going forwards.
Barkly version 3.0 adds the ability for automated and rapid response to its existing machine-learning threat detection engine. Its ability to do this via any mobile device means there is no delay if an incident occurs while administrators are off-site. The intention is to enable existing staff levels to handle workloads more efficiently without being stretched too thin, and without requiring additional company manpower.
Intel Discontinues Keyboard App Affected by Critical Flaws
6.4.2018 securityweek Vulnerebility
Serious vulnerabilities have been found in Intel’s Remote Keyboard application, but the company will not release any patches and instead advised users to uninstall the app.
Introduced in June 2015, the Intel Remote Keyboard apps for Android and iOS allow users to wirelessly control their Intel NUC and Compute Stick devices from a smartphone or tablet. The Android application has been installed more than 500,000 times.
Researchers discovered recently that all versions of Intel Remote Keyboard are affected by three severe privilege escalation flaws.
The most serious of them, rated “critical” and identified as CVE-2018-3641, allows a network attacker to inject keystrokes as a local user. The vulnerability was reported to Intel by a UK-based researcher who uses the online moniker trotmaster.
Another vulnerability, tracked as CVE-2018-3645 and rated “high severity,” was reported to Intel by Mark Barnes. The researcher discovered that Intel Remote Keyboard is affected by a privilege escalation flaw that allows a local attacker to inject keystrokes into another keyboard session.
The third security hole is CVE-2018-3638, which allows an authenticated, local attacker to execute arbitrary code with elevated privileges. Intel has credited Marius Gabriel Mihai for finding this vulnerability.
Intel does not plan on releasing patches for these vulnerabilities. The company has decided to discontinue the product and advised users to uninstall the apps at their earliest convenience. Intel Remote Keyboard has been removed from both Google Play and the Apple App Store.
Intel also published a security advisory this week to warn customers of an important denial-of-service (DoS) vulnerability affecting the SPI Flash component in multiple processors. The flaw was discovered by Intel itself and mitigations are available.
The company also informed users of a privilege escalation flaw in 2G modems, including XMM71xx, XMM72xx, XMM73xx, XMM74xx, Sofia 3G, Sofia 3G-R, and Sofia 3G-RW. The issue impacts devices that have the Earthquake Tsunami Warning System (ETWS) feature enabled.
A network attacker can exploit the vulnerability to execute arbitrary code. “Devices equipped with an affected modem, when connected to a rogue 2G base station where non-compliant 3GPP software may be operational, are potentially at risk,” Intel said.
The company says it has developed patches for this vulnerability.
“External researchers reported a potential security vulnerability in the implementation of the Earthquake and Tsunami Warning System (ETWS) in certain Intel 2G modem firmware implementations. Intel has developed firmware updates that address the issue, and we have been working closely with our customers and partners to deploy the updates to affected products as soon as possible,” Intel told SecurityWeek in an emailed statement.
New macOS Backdoor Linked to Cyber-espionage Group
6.4.2018 securityweek Apple CyberSpy
A recently discovered macOS backdoor is believed to be a new version of malware previously associated with the OceanLotus cyber-espionage group, Trend Micro says.
Also known as APT 32, APT-C-00, SeaLotus, and Cobalt Kitty, OceanLotus is believed to be operating out of Vietnam and has been targeting high-profile corporate and government organizations in Southeast Asia. Well-resourced and determined, the group uses custom-built malware and already established techniques.
Some of the group’s targets include human rights organizations, media organizations, research institutes, and maritime construction firms.
The newly discovered macOS backdoor, which Trend Micro detects as OSX_OCEANLOTUS.D, has been observed on machines that have the Perl programming language installed.
The malware is being distributed via malicious documents attached to emails. The document masquerades as the registration form for an event with HDMC, an organization in Vietnam that advertises national independence and democracy.
The document contains malicious, obfuscated macros with a payload written in Perl. The macro extracts an XML file from the Word document. This file is an executable acting as the dropper for the final payload, which is the backdoor.
The dropper, which has all of its strings encrypted using a hardcoded RSA256 key, is also used to establish the backdoor’s persistence on the infected systems. The dropper checks whether it runs as root or not, and uses different path and filename based on that.
The dropper sets the backdoor’s attributes to “hidden” and uses random values for the file date and time, and deletes itself at the end of the process.
The backdoor has two main functions, which collect platform information and sending it to the command and control (C&C) server. It can also receive additional C&C communication information, which is encrypted before being sent.
“Malicious attacks targeting Mac devices are not as common as its counterparts, but the discovery of this new macOS backdoor that is presumably distributed via phishing email calls for every user to adopt best practices for phishing attacks regardless of operating system,” Trend Micro concludes.
Unprotected Switches Expose Critical Infrastructure to Attacks: Cisco
6.4.2018 securityweek Attack
Cisco has advised organizations to ensure that their switches cannot be hacked via the Smart Install protocol. The networking giant has identified hundreds of thousands of exposed devices and warned that critical infrastructure could be at risk.
The Cisco Smart Install Client is a legacy utility that allows no-touch installation of new Cisco switches. Roughly one year ago, the company warned customers about misuse of the Smart Install protocol following a spike in Internet scans attempting to detect unprotected devices that had this feature enabled. It also made available an open source tool for identifying devices that use the protocol.
Attackers can abuse the Smart Install protocol to modify the configuration file on switches running IOS and IOS XE software, force the device to reload, load a new IOS image, and execute high-privilege commands. These attacks rely on the fact that many organizations fail to securely configure their switches, rather than an actual vulnerability.
According to Cisco, sophisticated nation-state groups have also abused Smart Install in their campaigns, including the Russia-linked threat actor tracked as Dragonfly, Crouching Yeti and Energetic Bear, which has been known to target critical infrastructure.
Cisco has decided to once again warn organizations of the risks associated with Smart Install following the disclosure of a critical vulnerability discovered recently by researchers at Embedi.
The flaw, tracked as CVE-2018-0171, allows a remote and unauthenticated attacker to cause a denial-of-service (DoS) condition or execute arbitrary code by sending specially crafted Smart Install messages to an affected device on TCP port 4786. Researchers said they had identified roughly 250,000 vulnerable Cisco devices with TCP port 4786 open.
Cisco’s own Internet scans revealed 168,000 systems potentially exposed due to their use of the Cisco Smart Install Client. The company says the number of impacted devices has decreased considerably since 2016, when security firm Tenable identified more than 250,000 exposed systems.
Throughout the end of 2017 and early 2018, Cisco’s Talos group noticed attackers increasingly looking for misconfigured clients. Now that CVE-2018-0171 has been found, the risk of attacks has increased even more, especially since Embedi has released technical details and proof-of-concept (PoC) code.
There is no evidence that CVE-2018-0171 has been exploited in malicious attacks. Cisco also noted that much of the activity it has seen is likely not malicious, but the company says the sharp increase in scanning is noteworthy.
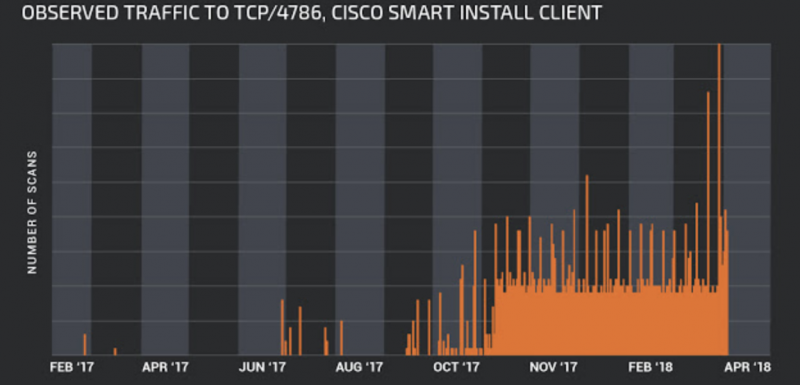
The vendor has provided recommendations for preventing potential attacks and advised customers to remove the Smart Install Client from devices where it’s not needed. Smart Install is enabled by default on switches that have not received a recent update that automatically disables the feature when it’s not in use.
While it’s unclear if Smart Install was involved, Cylance reported recently that the Dragonfly cyberespionage group had hijacked a core Cisco router at a major state-owned energy conglomerate in Vietnam and abused it to obtain credentials that were later leveraged in attacks targeting energy companies in the United Kingdom.
Financial Services DDoS Attacks Tied to Reaper Botnet
6.4.2018 securityweek BotNet
Recorded Future's "Insikt" threat intelligence research group has linked the Mirai variant IoTroop (aka Reaper) botnet with attacks on the Netherlands financial sector in January 2018.
The existence of IoTroop was first noted by Check Point in October 2017. At that point the botnet had not been used to deliver any known DDoS attacks, and its size was disputed. What was clear, however, was its potential for growth.
In January 2018, the financial services sector in the Netherlands was hit by a number of DDoS attacks. Targets included ABN Amro, Rabobank and Ing; but at that time the source of the attack was unknown.
Insikt researchers now report that at least one these financial services attacks -- and possibly more -- was the first known use of IoTroop to deliver a DDoS attack. "IoTroop is a powerful internet of things (IoT) botnet," reports Insikt, "primarily comprised of compromised home routers, TVs, DVRs, and IP cameras exploiting vulnerabilities in products from major vendors including MikroTik, Ubiquity and GoAhead."
The attack itself was not excessively high by modern standards. "The initial attack was a DNS amplification attack with traffic volumes peaking at 30Gb/s," reports Insikt -- far short of the 1.7Tb/s attack that occurred in February.
If the IoTroop assumption is correct, it is clear the botnet has evolved extensively since its discovery last year. Fortinet's SVP products and solutions reported last month, "the Reaper [IoTroop] exploit was built using a flexible Lua engine and scripts, which means that instead of being limited to the static, pre-programmed attacks of previous exploits, its code can be easily updated on the fly, allowing massive, in-place botnets to run new and more malicious attacks as soon as they become available."
Insikt reports that the malware can use at least a dozen vulnerabilities and can be updated by the attackers as new vulnerabilities are exposed. "Our analysis," it says, "shows the botnet involved in the first company attack was 80% comprised of compromised MikroTik routers with the remaining 20% composed of various IoT devices ranging from vulnerable Apache and IIS web servers to routers from Ubiquity, Cisco and ZyXEL. We also discovered Webcams, TVs and DVRs among the 20% of IoT devices, which included products from major vendors such as MikroTik, GoAhead, Ubiquity, Linksys, TP-Link and Dahua."
This list adds new devices now vulnerable to IoTroop in addition to those noted in the original October 2017 research -- which suggests, says Insikt, "a widespread and rapidly evolving botnet that appears to be leveraging publicly disclosed vulnerabilities in many IoT devices."
Insikt's research shows the January attack was delivered from 139 different countries, showing a widespread targeting of vulnerable IoT devices around the world. More than half of the attacking clients are located in the Russian Federation, Brazil, Ukraine, China and the U.S.; but this probably has no relevance other than popularity of MikroTik devices in those countries.
Insikt believes that its analysis of the January DDoS attacks makes it almost certain that at least one and probably more were delivered by IoTroop; but that the new devices included within the botnet show its continuing evolution. "The similarity in device composition with the IoTroop/Reaper botnet," it says, "suggest IoTroop has evolved to exploit vulnerabilities in additional IoT devices and is likely to continue to do so in the future in order to build up the botnet to facilitate larger DDoS attacks against the financial sector."
The research also found seven IP addresses that it believes are likely to be controllers for the botnet. Insikt urges industry to monitor these addresses for malicious activity since they "are likely to be engaged in aggressive scanning for new vulnerable IoT infrastructure to commandeer as well as be responsible for any Denial of Service, attack commands issued to the botnet clients."
Protecting consumer IoT devices is less simple, since consumers notoriously adopt an unpack, plug and play approach to new devices. Nevertheless, Recorded Future urges all users to immediately change default manufacturer passwords, to patch firmware wherever possible and required, to invest in a VPN for devices that have remote access (such as IP cameras), and -- perhaps less easily for consumers -- to disable unnecessary services such as Telnet.
Microsoft Adds New Security Features to Office 365
6.4.2018 securityweek Safety
Microsoft today announced new protections for Office 365 Home and Office 365 Personal subscribers, aimed at helping them recover files, protect data, and defend against malware.
Courtesy of the newly announced protections, Office 365 Home and Office 365 Personal users can now recover their files after a malicious attack like ransomware, Kirk Koenigsbauer, Corporate Vice President for Office at Microsoft, says.
The new functionality is available through a Files Restore option that has been long available for OneDrive for Business customers. The feature is now available for personal OneDrive accounts and is enabled for both work and personal files.
With the help of Files Restore, users can restore their entire OneDrive to a previous point in time within the last 30 days. The feature should prove highly useful in a variety of situations, ranging from an accidental mass delete to file corruption, ransomware encryption, or another catastrophic event.
To further protect users, Microsoft is bringing ransomware detection and recovery features to Office 365. This feature ensures that ransomware attacks are detected and also helps users restore their OneDrive to a point before files were compromised.
“If an attack is detected, you will be alerted through an email, mobile, or desktop notification and guided through a recovery process where you’ll find the date and time of attack preselected in Files Restore, making the process simple and easy to use. As these threats evolve, we are continuously improving detection capabilities to help keep you safe from the most advanced ransomware,” Koenigsbauer notes.
Microsoft is also retrofitting Office 365 with adding three new capabilities meant to help users keep their data secure and private when sending confidential or personal information online, regardless of whether via email or through sharing a link.
For starters, the software giant is allowing users to set and require a password to access a shared file or folder in OneDrive, thus preventing unauthorized access to their files, provided that the link is accidentally shared with a third-party.
Microsoft is also providing email encryption in Outlook.com, for an added layer of protection. Through end-to-end encryption of messages, the company aims at preventing hackers from intercepting and reading users’ communication.
“Encryption is particularly useful in cases where it is unclear what level of security your intended recipients’ email providers offer. Recipients receive a link to a trusted Office 365 webpage where they can choose to receive a one-time passcode or re-authenticate with a trusted provider before viewing the email,” Koenigsbauer says.
Recipients viewing encrypted emails in Outlook.com, the Outlook for iOS and Android app, or the Windows Mail app do not need to engage in extra steps to read and reply to messages. Outlook.com can also detect sensitive information like social security numbers when a new email is composed, and can provide a suggestion to send with encryption.
Additionally, users can now restrict email recipients from forwarding or copying emails sent from Outlook.com. Moreover, all Office documents attached to these emails are now encrypted even after downloading, meaning that, if they are forwarded to a third party, the recipient won’t be able to open the attachment.
Later this year, Office 365 Home and Office 365 Personal subscribers will also be able to take advantage of advanced link checking in Word, Excel, and PowerPoint. The functionality follows the advanced link checking and attachment scanning added to Outlook.com in October last year in an attempt to keep users protected from previously unseen viruses and phishing scams in real-time.
“Starting later this year, links you click in Word, Excel, and PowerPoint will also be checked in real-time to determine if the destination website is likely to download malware onto your computer or if it’s related to a phishing scam. If the link is suspicious, you will be redirected to a warning screen recommending you don’t access the site,” Koenigsbauer notes.
Cisco Smart Install Protocol misuse could expose critical infrastructure to attacks
6.4.2018 securityaffairs Attack
Cisco PSIRT has published a new security advisory for abuse of the Smart Install protocol, the IT giant has identified hundreds of thousands of exposed devices online.
Cisco is advising organizations that hackers could target its switches via the Smart Install protocol. The IT giant has identified hundreds of thousands of exposed devices and warned critical infrastructure using them of potential risks.
Smart Install is a legacy plug-and-play configuration and image-management feature that provides zero-touch deployment for new switches.
In February 2017, researchers from Cisco Talos observed a spike in Internet scans attempting to discover unprotected Cisco devices that had Smart Install feature enabled.
“Research has indicated that malicious actors may be leveraging detailed knowledge of the Smart Install Protocol to obtain copies of customer configurations from affected devices.” reported Cisco Talos last year.
“The attack leverages a known issue with the Smart Install protocol. Cisco PSIRT has published a security response to this activity. Abuse of the Smart Install protocol can lead to modification of the TFTP server setting, exfiltration of configuration files via TFTP, replacement of IOS image and potentially execution of IOS commands.”
The researchers also reported that attackers were using an open source tool to scan for affected systems, called the Smart Install Exploitation Tool (SIET),
Now Cisco PSIRT has published a new security advisory for abuse of the protocol.
“Cisco is aware of a significant increase in Internet scans attempting to detect devices where, after completing setup, the Smart Install feature remains enabled and without proper security controls. This could leave the involved devices susceptible to misuse of the feature. ” reads the new security advisory.
“Several researchers have reported on the use of Smart Install (SMI) protocol messages toward Smart Install clients, also known as integrated branch clients (IBC), allowing an unauthenticated, remote attacker to change the startup-config file and force a reload of the device, load a new IOS image on the device, and execute high-privilege CLI commands on switches running Cisco IOS and IOS XE Software.”
At the end of March, Cisco patched more than 30 vulnerabilities in its IOS software, including the CVE-2018-0171 flaw that affects the Smart Install feature of Cisco IOS Software and Cisco IOS XE Software. The flaw could be exploited by an unauthenticated, remote attacker to cause a reload of a vulnerable device or to execute arbitrary code on an affected device.
“The vulnerability is due to improper validation of packet data. An attacker could exploit this vulnerability by sending a crafted Smart Install message to an affected device on TCP port 4786.” reads the security advisory published by Cisco.
Cisco experts revealed they had identified roughly 250,000 vulnerable Cisco devices with TCP port 4786 open. A recent scan performed by Cisco revealed 168,000 systems are exposed online.

Since Embedi has released technical details and proof-of-concept (PoC) code for the exploitation of the CVE-2018-0171 vulnerability, risk of attacks has dramatically increased.
At the time, there is no evidence that CVE-2018-0171 has been exploited in attacks.
Cisco published recommendations for preventing such kind of attacks and urged customers to disable the feature if not needed.
Zuckerberg admitted public data of its 2.2 billion users has been scraped by Third-party entities
6.4.2018 securityaffairs Social
Third-party scrapers have exploited an issue in the Facebook ’s search function that allows anyone to look up users via their email address or phone numbers.
Facebook revealed on Wednesday that 87 million users have been affected by the Cambridge Analytica case, much more than 50 million users initially thought.
Facebook is the middle of a storm, Mark Zuckerberg admitted public data of its 2.2 billion users has been compromised over the course of several years by third-party actors that gathered information on its users.
Third-party scrapers have exploited an issue in the Facebook’s search function that allows anyone to look up users via their email address or phone numbers.
Users name come up in Facebook searches is they don’t explicitly disable this security setting.
“Until today, people could enter another person’s phone number or email address into Facebook search to help find them. This has been especially useful for finding your friends in languages which take more effort to type out a full name, or where many people have the same name.” reads a blog post published by CTO Mike Schroepfer.
“However, malicious actors have also abused these features to scrape public profile information by submitting phone numbers or email addresses they already have through search and account recovery. Given the scale and sophistication of the activity we’ve seen, we believe most people on Facebook could have had their public profile scraped in this way. “
Schroepfer announced that Facebook has now disabled this feature and is changing the account recovery procedure to reduce the scraping activities.
Zuckerberg confirmed the extent of the scraping activity during a call with the press:
“I would assume if you had that setting turned on that someone at some point has access to your public information in some way.” explained Zuckerberg.
Zuckerberg blamed himself for what has happened to his company and promtly announced further improvements in term of privacy and security.
When asked if he still considered himself the best person to run the company, he said, “Yes.”
OSX_OCEANLOTUS.D, a new macOS backdoor linked to APT 32 group
6.4.2018 securityaffairs APT Apple
Security experts at Trend Micro have discovered a new macOS backdoor that they linked to the APT 32 (OceanLotus, APT-C-00, SeaLotus, and Cobalt Kitty) cyber espionage group.
The APT32 group has been active since at least 2013, according to the experts it is a state-sponsored hacking group. The hackers hit organizations across multiple industries and have also targeted foreign governments, dissidents, and journalists.
Since at least 2014, experts at FireEye have observed APT32 targeting foreign corporations with an interest in Vietnam’s manufacturing, consumer products, and hospitality sectors. The APT32 is also targeting peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors.
The APT32 group uses custom-built malware for its attacks, the newly discovered macOS backdoor was tracked by experts at Trend Micro as OSX_OCEANLOTUS.D.
The researchers found the backdoor on macOS systems that have the Perl programming language installed.
“We identified a MacOS backdoor (detected by Trend Micro as OSX_OCEANLOTUS.D) that we believe is the latest version of a threat used by OceanLotus (a.k.a. APT 32, APT-C-00, SeaLotus, and Cobalt Kitty).” reads the analysis published by Trend Micro.
“The attackers behind OSX_OCEANLOTUS.D target MacOS computers which have the Perl programming language installed.”
The hackers used spear-phishing messages as attack vectors, the backdoor is distributed via weaponized documents attached to emails. The bait document masquerades as the registration form for an event with HDMC, an organization in Vietnam that advertises national independence and democracy.

The malicious document contains an obfuscated macros with a Perl payload. The macro extracts an XML file (theme0.xml) from the document, it is a Mach-O 32-bit executable with a 0xFEEDFACE signature that acts as a dropper for the final OSX_OCEANLOTUS.D backdoor.
“All strings within the dropper, as well as the backdoor, are encrypted using a hardcoded RSA256 key. There are two forms of encrypted strings: an RSA256-encrypted string, and custom base64-encoded and RSA256-encrypted string.” continues the report.
“Using the setStartup() method, the dropper first checks if it is running as a root or not. Based on that, the GET_PROCESSPATH and GET_PROCESSNAME methods will decrypt the hardcoded path and filename where the backdoor should be installed.”
Once the dropper has installed the backdoor, it will set its attributes to “hidden” and set file date and time to random values using the touch command:
touch –t YYMMDDMM “/path/filename” > /dev/null.
It also changes the permissions to 0x1ed = 755, which is equal to u=rwx,go=rx.
The backdoor loops on two main functions, infoClient and runHandle; infoClient is used to collect platform information and send them to the command and control (C&C) server, meanwhile runHandle implements backdoor capabilities.
The discovery of a new backdoor linked to the APT32 group confirms that the state-sponsored crew was very active in the last months.
1.5 Billion Sensitive Documents on Open Internet: Researchers
5.4.2018 securityweek Incindent
Some 1.5 billion sensitive online files, from pay stubs to medical scans to patent applications, are visible on the open internet, security researchers said Thursday.
Researchers from the cybersecurity firm Digital Shadows said a scanning tool used in the first three months of 2018 found mountains of private data online from people and companies across the world.
The unprotected data amounted to some 12 petabytes, or four thousand times larger than the "Panama Papers" document trove which exposed potential corruption in dozens of countries.
"These are files that are freely available" to anyone with minimal technical knowledge, said Rick Holland, a vice president at Digital Shadows.
Holland told AFP his team scanned the web and found unsecured files, adding "we didn't authenticate to anything."
The availability of open data makes it easier for hackers, nation-states or rival companies to steal sensitive information, Holland said.
"It makes attackers' jobs much easier. It shortens the reconnaissance phase," he added.
The researchers said in the report that even amid growing concerns about hackers attacking sensitive data, "we aren't focusing on our external digital footprints and the data that is already publicly available via misconfigured cloud storage, file exchange protocols, and file sharing services."
A significant amount of the data left open was from payroll and tax return files, which accounted for 700,000 and 60,000 files respectively, Digital Shadows said.
It noted medical files and lists were also weakly protected, with some 2.2 million body scans open to inspection.
Many corporate secrets were also out in the open including designs, patent summaries and details of yet-to-be-released products.
"While organizations may consider insiders, network intrusions and phishing campaigns as sources of corporate espionage, these findings demonstrate that there is already a large amount of sensitive data publicly available," the report said.
The researchers said about 36 percent of the files were located in the European Union. The United States had the largest amount for a single country at 16 percent, but exposed files were also seen around the world including in Asia and the Middle East.
About seven percent of the data was in "misconfigured" cloud Amazon cloud computing storage. Holland said the main problem was not in the cloud computing itself but how users manage their data.
In some cases, users "are backing up their data to the (open) web without knowing it," Holland said.
The majority of the files found by Digital Shadows were exposed by poor security practices in servers and file-sharing protocols.
"Third parties and contractors were among the most common sources of sensitive data exposure," the report said.