Google, Twitter Security Chiefs Leaving Companies
22.3.2018 securityweek Social
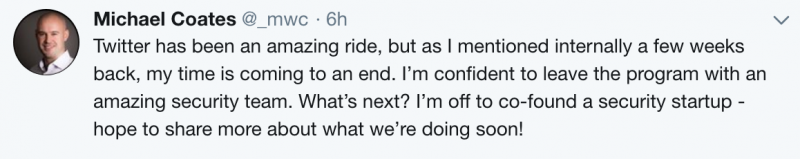
Michael Coates, the chief information security officer (CISO) of Twitter, announced on Wednesday that he has decided to leave the social media giant. Google security chief Gerhard Eschelbeck has also announced his departure.
Coates, who joined Twitter in January 2015, says he will co-found a cybersecurity startup, but has not shared any details.

According to his LinkedIn profile, Coates has been working in cybersecurity since 2004, including at Motorola, Aspect Security and Shape Security. Between March 2010 and October 2013, he led Mozilla's Security Assurance program.
Until recently he was on the global board of directors of the OWASP Foundation, and is presently on the board of several organizations, including Comprehend Systems, Synack, and Vendor Security Alliance.
The Verge reported that Joseph Camilleri, a senior manager for information security and risk, will act as interim CISO at Twitter following Coates’ departure.
Eschelbeck, vice president of security and privacy engineering at Google, also announced his departure on Wednesday, but has not shared his plans for the future.
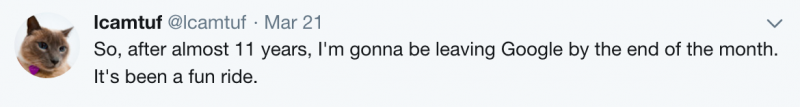
Eschelbeck, known online as lcamtuf, previously held leadership positions at McAfee, Qualys, Webroot and Sophos. He joined Google in October 2014.
The announcements made by Eschelbeck and Coates come just days after reports that Facebook CISO Alex Stamos is leaving the social media giant in the wake of internal clashes over how to deal with the platform being used to spread misinformation.
“Despite the rumors, I'm still fully engaged with my work at Facebook,” Stamos said in response to a New York Times article on his alleged departure from Facebook. “It's true that my role did change. I'm currently spending more time exploring emerging security risks and working on election security.”
Growing Mistrust Threatens Facebook After Data Mining Scandal
22.3.2018 securityweek Social
As Facebook reels from the scandal over hijacked personal data, a movement to quit the social network gathered momentum Wednesday, portending threats to one of the most powerful internet firms.
In a sign of the mood, one of those calling it quits was a high-profile co-founder of the WhatsApp messaging service acquired by Facebook in 2014 for $19 billion.
"It is time. #deletefacebook," Brian Acton said in a tweet, using the hashtag protesting the handling of the crisis by the world's biggest social network.
The WhatsApp co-founder, who now works at the rival messaging application Signal, posted the comment amid a growing uproar over revelations that Facebook data was harvested by a British political consulting firm linked to Donald Trump's presidential campaign.
"Delete and forget. It's time to care about privacy," he said.
The huge social network also faces investigations on both sides of the Atlantic over its data practices, and a handful of lawsuits which could turn into class actions that may prove a costly distraction for Facebook.
It remains to be seen whether the uproar would lead to any significant departures, but the topic was active on social media, including on Facebook itself.
Donella Cohen, a Weather Channel product manager, posted on her Facebook page that she would be off the network by midnight.
"The latest revelations are showing just how corrupt and detrimental to society this particular platform is," she wrote.
"I hope that a new social network emerges. One that isn't so greedy as to corrupt the political process in the name of the almighty dollar."
- Fabric of internet -
Yet analysts noted Facebook is unlikely to fade quickly because of how it is woven into the fabric of the internet, with "like" buttons on websites, comments sections for news articles and an ad network that delivers messages to those who are not Facebook members.
The #deleteFacebook movement "is a social media feedback loop from the public -- we saw the same thing with #deleteUber," said Jennifer Grygiel, a communications professor at Syracuse University.
"Sure, some people will delete Facebook, but to truly delete Facebook would mean that users would need to delete Facebook, Instagram, WhatsApp, and Messenger. This is not realistic for most people given how social media has been integrated into everyday life."
Sandra Proske, head of communications for the Finland-based security firm F-Secure, said it's not easy to break up with Facebook.
"If this (scandal) makes you uncomfortable you can choose to not use the site, of course," Proske wrote in a blog post.
"But given how intertwined in our lives Facebook and the sites it has acquired, including Instagram and WhatsApp, have become, you may not consider this an option. And for some people and even some countries, Facebook is the internet."
Proske and others offer suggestions on how Facebook users can improve privacy by limiting what is shared and which apps have access to their data.
Several websites offered tips on how to quit Facebook, while noting that the process is more complicated than it appears.
Facebook offers users the option to "deactivate" an account for users who want to take a break and return later, or to "delete" the account and its data entirely.
But Facebook noted that some data such as posts on friends' timelines might remain in the system even after an account is deleted.
And longtime Facebook users could face complications on dealing with log-ins and authorizations to other websites and apps through the social network.
The tech website The Verge published a guide to deletion, advising users to download a copy of all personal data including photos and posts before quitting.
The website noted that it could take up to 90 days to fully delete an account, and that data may be inaccessible during that period.
It was unclear how many users were following through on plans to quit Facebook, which has more than two billion users worldwide.
But Roger McNamee, an early investor in Facebook, said the social network was losing the trust of its users.
"The issue is a callous disregard for the privacy rights of users and a lack of care with respect to data that had been entrusted to Facebook," McNamee told National Public Radio.
"I'm not sure exactly what's going on here, but I'm afraid there is a systemic problem with the algorithms and the business model of Facebook that allow bad actors to cause harm to innocent users of Facebook."
Zuckerberg on Cambridge Analytica case: we made mistakes
22.3.2018 securityaffairs Social
Facebook CEO Mark Zuckerberg on Wednesday commented the Cambridge Analytica case, he admitted the company made mistakes.
Finally, Facebook CEO Mark Zuckerberg on Wednesday commented the Cambridge Analytica case, he admitted that his company has failed in protecting its users, but he pointed out that the company has already adopted necessary measures to prevent future abuses.
“we made mistakes” he said. “We have a responsibility to protect your data, and if we can’t then we don’t deserve to serve you,” reads a statement published by Zuckerberg on Facebook.
“I’ve been working to understand exactly what happened and how to make sure this doesn’t happen again. The good news is that the most important actions to prevent this from happening again today we have already taken years ago. But we also made mistakes, there’s more to do, and we need to step up and do it.”
A team of academics had collected a huge amount of user data and shared the information with Cambridge Analytica which is a commercial data analytics company that allegedly used it to target US voters in the 2016 Presidential election.
The news was confirmed by Facebook over the weekend, the researchers used an app developed by the University of Cambridge psychology lecturer Dr. Aleksandr Kogan to collect user data.
The app named “thisisyourdigitallife” is available to users since 2014, it was provided by Global Science Research (GSR) and asked users to take an online survey for $1 or $2. The app requested access to the user’s profile information, and over 270,000 users gave the app permission to use their personal details for academic research.
The app is a powerful tool to profile users by harvesting information on their network of contacts, its code allowed to collect data from over 50 million users.
Facebook confirmed to have “suspended” any business with Cambridge Analytica (CA) and its holding company.
Facebook discovered the activity in 2015 thanks to claims from its users and adopted the necessary measures to force the involved parties in deleting the data from their servers.
Zuckerberg highlighted that he was not aware of the activities conducted by Cambridge Analytica and that his company prompted interrupted business activities with the firm once discovered it has not deleted collected data.
“Last week, we learned from The Guardian, The New York Times and Channel 4 that Cambridge Analytica may not have deleted the data as they had certified. We immediately banned them from using any of our services.”

Mark Zuckerberg said he would take several measures to prevent threat actors from abusing Facebook users’ data.
The company will assess all apps that had access to large amounts of information before 2014, when the social network giant took the most important steps to prevent bad actors from accessing people’s data.
Facebook will restrict developers’ data access even further to prevent such kind of situation and it will show users a tool at the top of their News Feed to show the apps they used and revoke them permissions to access their data.
The company will ban any developer that does not agree to a thorough audit.
“We’ll require developers to not only get approval but also sign a contract in order to ask anyone for access to their posts or other private data. And we’ll have more changes to share in the next few days.” continues Zuckerberg while announcing more changes.
Below the complete statement published by Zuckerberg.
Mark Zuckerberg
před 12 h
I want to share an update on the Cambridge Analytica situation -- including the steps we've already taken and our next steps to address this important issue.
We have a responsibility to protect your data, and if we can't then we don't deserve to serve you. I've been working to understand exactly what happened and how to make sure this doesn't happen again. The good news is that the most important actions to prevent this from happening again today we have already taken years a...
Puerto Rico Electric Power Authority (PREPA) hacked over the weekend
22.3.2018 securityaffairs BigBrothers
Puerto Rico Electric Power Authority (PREPA) power utility confirmed early this week that it has been hacked over the weekend.
A few days ago, the US government issued an alert to warn of cyber attacks powered by Russian state-sponsored hackers against US critical infrastructure.
News of the day is that Puerto Rico power utility, aka Puerto Rico Electric Power Authority or PREPA, confirmed early this week that it has been hacked over the weekend.

Last year, PREPA filed a form of U.S. bankruptcy to shed some $9 billion in debt. Puerto Rico Governor Ricardo Rossello plans to privatize the Puerto Rico Electric Power Authority and to modernize the outdated infrastructure.
The bankrupt power utility confirmed that there is no risk for its customers because their data were not compromised by hackers.
The hackers did not access the customer service system at Puerto Rico power utility.
According to the Executive Director Justo Gonzalez Torres, on Sunday night, the computer infrastructure of PREPA suffered a security breach, he also added that an investigation is ongoing.
“In these moments we are protecting the systems and working to resolve the situation,” said Gonzalez.
At the time there is no evidence for the involvement of Russian hackers in the attack against the Puerto Rico Electric Power Authority.Anyway, the attribution of such kind of cyber attacks is very hard because threat actors adopt sophisticated techniques to remain stealth
“As of Monday evening, there was no indication that Russia was to blame for PREPA’s hack.” reported the Reuters.
“When asked about potential sources of the attack, a spokesman for PREPA said the matter was “being investigated and referred to the relevant authorities,” declining to say who those authorities were.”
In September, the PREPA grid was destroyed when Hurricane Maria that hit Puerto Rico, 3.4 million residents of the U.S. commonwealth went in the dark.
Android Trojan Leverages Telegram for Data Exfiltration
21.3.2018 securityweek Android
A newly discovered Android Trojan is abusing Telegram’s Bot API to communicate with the command and control (C&C) server and to exfiltrate data, Palo Alto Networks security researchers warn.
Dubbed TeleRAT, the malware appears to be originating from and/or to be targeting individuals in Iran. The threat is similar to the previously observed IRRAT Trojan, which uses Telegram’s bot API for C&C communication only.
Still active in the wild, IRRAT masquerades as applications supposedly informing users on the number of views their Telegram profile received (something that Telegram doesn’t actually allow for). After the app’s first launch, the malware creates and populates a series of files on the phone’s SD card, which it then sends to an upload server.
The files contain contact information, a list of Google accounts registered on the phone, SMS history, a picture taken with the front-facing camera, and a picture taken with back-facing camera. The malicious app reports to a Telegram bot, hides its icon from the phone’s app menu, and continues to run in the background, waiting for commands.
TeleRAT, on the other hand, creates two files on the device, one containing various device information (including system bootloader version number, available memory, and number of processor cores), and another containing a Telegram channel and a list of commands, Palo Alto Networks says.
After installation, the RAT informs attackers on this by sending a message to a Telegram bot via the Telegram bot API with the current date and time. It also starts a background service to listen for changes made to the clipboard, and fetches updates from the Telegram bot API every 4.6 seconds, listening for commands.
Based on the received commands, the malware can grab contacts, location, app list, or the content of the clipboard; receive charging information; get file list or root file list; download files, create contacts, set wallpaper, receive or send SMS; take photos; receive or make calls; turn phone to silent or loud; turn off the phone screen; delete apps; cause the phone to vibrate; and get photos from the gallery.
The new malware family is also capable of uploading exfiltrated data using Telegram’s sendDocument API method. By performing all communication via the Telegram bot API, it evades network-based detection.
The use of said API allows for getting updates in two manners, namely the getUpdates method (which exposes a history of all the commands sent to the bot, including the usernames the commands originated from), and the use of a Webhook (bot updates can be redirected to a HTTPS URL specified by means of a Webhook).
The researchers claim to have found an image of the botmaster testing out the RAT, along with exfiltrated messages to confirm it. The malware also appears to contain the developer’s username in the code, which lead researchers to the ‘vahidmail67’ Telegram channel, which advertises applications to help users get likes and followers on Instagram, ransomware, and even the source code for an unnamed RAT.
The researchers also found threads on an Iranian programmers’ forum advertising the sale of a Telegram bot control library and say that code from developers frequenting the forum was found in encountered TeleRAT samples. Although the forum claims all content is in accordance with Iran’s laws, the malicious use for some of the code advertised there is clear.
Because TeleRAT puts together code written by several developers, including freely available source code via Telegram channels and code sold on forums, this makes it difficult to point to one single actor commanding either IRRAT or TeleRAT. Thus, Palo Alto Networks says the malware could be the work of several actors possibly operating inside of Iran.
The malware is distributed via seemingly legitimate applications in third-party Android app stores and also distributed and shared via both legitimate and nefarious Iranian Telegram channels. A total of 2,293 users were apparently infected, based on the analyzed infrastructure, with 82% of the victims having Iranian phone numbers.
Firefox Fails at Keeping Passwords Secure, Developer Claims
21.3.2018 securityweek Safety
Recovering Encrypted Firefox Passwords via Brute Force Attacks is Easy, Developer Says
Firefox does a poor job at securing stored passwords even if the user has set up a master password, a software developer claims.
According to Wladimir Palant, author of the popular Adblock Plus extension, the password manager in Firefox and Thunderbird needs some major improvements in terms of security. The manager can spill out passwords in less than a minute, he says.
The issue, Palant claims, resides in the manner in which the manager converts a password into an encryption key. The operation is performed by the sftkdb_passwordToKey() function, which applies SHA-1 hashing to a string consisting of a random salt and the actual master password.
In the current implementation, the SHA-1 function has a very low iteration count of 1, meaning that it falls way behind what’s considered a minimum value in practice, namely 10,000. In fact, an iteration count of at least 1,000 was considered “modest” decades ago.
Because of that, recovering encrypted passwords via brute force attacks is not difficult at all, Palant says. In fact, he underlines that graphics processing units (GPUs) are great at calculating SHA-1 hashes. With some of them capable of calculating billions of SHA-1 hashes per second, it would not take more than a minute to crack the passwords encrypted and stored in Firefox.
This NSS bug was first reported about nine years ago, but remains unpatched. And it wouldn’t even be that difficult to address the issue, the developer says.
“NSS library implements PBKDF2 algorithm which would slow down bruteforcing attacks considerably if used with at least 100,000 iterations. Of course, it would be nice to see NSS implement a more resilient algorithm like Argon2 but that’s wishful thinking seeing a fundamental bug that didn’t find an owner in nine years,” Palant notes.
Robert Relyea, who has worked for over 20 years on NSS, notes that, while the iteration count could be increased, it would not affect the security of old databases, which would remain readable. Only changing the master password (even to the same password) for them would also increase the iteration count.
The issue was thought resolved in PKCS #12, but it wasn’t fixed for the NSS database password (Firefox Master Password) too. Thus, Relyea reopened the bug, so it could be properly addressed.
Mozilla is also working on a new password manager component for Firefox. Dubbed Lockbox and available as an extension, it might not solve the issue either, Palant says, pointing out that it relies on Firefox Accounts, which could prevent wide adoption.
Even if this issue still exists in Firefox, setting up a master password for Firefox’ manager is still better than using none. Of course, using a password manager that isn’t impacted by such bugs is even better, although cracking firms would say that the security of such tools is debatable.
AMD Chip Flaws Confirmed by More Researchers
21.3.2018 securityweek Vulnerebility
Another cybersecurity firm has independently confirmed some of the AMD processor vulnerabilities discovered by Israel-based CTS Labs, but the controversial disclosure has not had a significant impact on the value of the chip giant’s stock.
CTS Labs last week published a brief description of 13 allegedly critical vulnerabilities and backdoors found in EPYC and Ryzen processors from AMD. The company says the flaws can be exploited for arbitrary code execution, bypassing security features (e.g. Windows Defender Credential Guard, Secure Boot), stealing data, helping malware become resilient against security products, and damaging hardware.
The flaws have been dubbed MASTERKEY, RYZENFALL, FALLOUT and CHIMERA, and exploiting them requires elevated privileges to the targeted machine — physical access is not required. The security firm will not disclose technical details any time soon in order to prevent abuse.
CTS Labs, which no one heard of until last week, came under fire shortly after its disclosure for giving AMD only a 24-hour notice before going public with its findings, and for apparently attempting to short AMD stock. The company later made some clarifications regarding the flaws and its disclosure method.
While initially many doubted CTS Labs’ claims due to the lack of technical information, an increasing number of independent researchers have confirmed that the vulnerabilities do in fact exist. Nevertheless, there are still many industry professionals who believe their severity has been greatly exaggerated.
Trail of Bits was the first to independently review the findings. The company, which has been paid for its services, has confirmed that the proof-of-concept (PoC) exploits developed by CTS Labs work as intended, but believes that there is “no immediate risk of exploitation of these vulnerabilities for most users.”
“Even if the full details were published today, attackers would need to invest significant development efforts to build attack tools that utilize these vulnerabilities. This level of effort is beyond the reach of most attackers,” Trail of Bits said in a blog post.
On Monday, Check Point also confirmed two of the RYZENFALL vulnerabilities following its own review. The security firm says it does not have any relationship with CTS Labs and it has not received any payment for its services. It also noted that it does not agree with the way CTS disclosed its findings, describing it as “very irresponsible.”
“In our opinion the original CTS Labs report might have been problematically phrased in a way that misrepresented the threat model and impact that the RYZENFALL-1 and RYZENFALL-3 vulnerabilities present,” Check Point said in a blog post. “However, problematic phrasing aside, after inspecting the technical details of the above, we can indeed verify that these are valid vulnerabilities and the risks they pose should be taken under consideration.”
Alex Ionescu, a reputable researcher and Windows security expert, also confirmed the findings and warned that “admin-level access and persistence are legitimate threats in multi-tenant IaaS and even things such as VTL0/1 (Credential Guard) when firmware and chipset trust boundaries are broken.”
AMD is investigating the claims, but it has yet to make any statement regarding the impact of the flaws.
Less than an hour after CTS Labs released its report, a controversial company named Viceroy Research published what it described as an “obituary” in hopes of leveraging the findings to short AMD stock. Since CTS’s report also included a disclaimer noting that the company had a financial interest, many assumed the two were working together to short AMD.
While CTS has avoided answering questions regarding its financial interests, Viceroy representatives told Vice’s Motherboard that the company obtained the report describing the vulnerabilities from an “anonymous tipster” and claimed to have no connection to the security firm.
Viceroy’s attempt has had an insignificant impact on AMD stock and experts doubt the situation will change. This is not actually surprising considering that Intel was hit the hardest by Meltdown and Spectre — critical vulnerabilities disclosed by reputable researchers — and still the impact on the company’s stock has been only minor and temporary.
Facebook Rocked by Data breach Scandal as Investigations Loom
21.3.2018 securityweek Social
[UPDATE] Facebook shares plunged Monday as the social media giant was pounded by criticism at home and abroad over revelations that a firm working for Donald Trump's presidential campaign harvested and misused data on 50 million members.
Calls for investigations came on both sides of the Atlantic after Facebook responded to explosive reports of misuse of its data by suspending the account of Cambridge Analytica, a British firm hired by Trump's 2016 campaign.
Democratic Senator Amy Klobuchar and Republican John Kennedy called for Facebook chief Mark Zuckerberg to appear before Congress, along with Google and Twitter's CEOs.
The lawmakers said the companies "have amassed unprecedented amounts of personal data" and that the lack of oversight "raises concerns about the integrity of American elections as well as privacy rights."
Facebook's chief of security Alex Stamos said his role has shifted to focusing on emerging risks and election security at the global social network.
Stamos revealed the change after The New York Times reported that he was leaving Facebook in the wake of internal clashes over how to deal with the platform being used to spread misinformation.
"Despite the rumors, I'm still fully engaged with my work at Facebook," Stamos said in a message posted on his verified Twitter account.
"It's true that my role did change. I'm currently spending more time exploring emerging security risks and working on election security."
Stamos advocated investigating and revealing manipulation of news at the social network by Russian entities, to the chagrin of other top executives, the Times reported, citing unnamed current and former employees.
- Profiles weaponized? -
Senator Ron Wyden asked Facebook to provide more information on what he called a "troubling" misuse of private data that could have been used to sway voters.
Wyden said he wants to know how Cambridge Analytica used Facebook tools "to weaponize detailed psychological profiles against tens of millions of Americans."
In Europe, officials voiced similar outrage.
Vera Jourova, the European commissioner for justice, consumers and gender equality, called the revelations "horrifying, if confirmed," and vowed to address concerns in the United States this week.
According to a joint investigation by The New York Times and Britain's Observer, Cambridge Analytica was able to create psychological profiles on 50 million Facebook users through the use of a personality prediction app that was downloaded by 270,000 people, but also scooped up data from friends.
Cambridge Analytica denied misusing Facebook data for the Trump campaign.
Elizabeth Denham, Britain's Information Commissioner who regulates the sector in the country, announced her office would seek a court warrant on Tuesday to search Cambridge Analytica's computer servers.
She said the company had been "uncooperative" to requests for access to its records and missed a Monday deadline stipulated.
Meanwhile, Facebook said it has hired a digital forensics firm to examine how the data leak occurred and to ensure that any data collected had been destroyed.
Facebook shares skidded 6.8 percent by the close of the Nasdaq on concerns about pressure for new regulations that could hurt its business model.
Shares slipped another percent or so to $170 in after-market trades.
The sell-off spread to other technology giants on Wall Street including Apple, Google-parent Alphabet and Netflix. Asian markets extended the losses, with Tokyo-listed Sony down, Samsung falling in Seoul and Tencent retreating in Hong Kong.
'Self-regulation not working'
Jennifer Grygiel, a Syracuse University professor who studies social media, said the disclosures will increase pressure to regulate Facebook and other social media firms, already under scrutiny for allowing disinformation from Russian-directed sources to propagate.
"Self-regulation is not working," Grygiel said.
Daniel Kreiss, a professor of media and communications at the University of North Carolina, said Facebook failed to live up to its responsibilities on election ads.
"The fact that Facebook seems to make no distinction between selling sneakers and selling a presidential platform is a deep problem," Kreiss said.
Brian Wieser at Pivotal Research maintained that the revelations highlight "systemic problems at Facebook," but that they won't immediately impact the social network's revenues.
David Carroll, a media professor at the Parsons School of Design, said Facebook and others will soon be forced to live with new privacy rules such as those set to take effect in the European Union.
"Facebook and Google will have to ask users a lot more permission to track them," Carroll said. "Most people are going to say no, so I think it's going to have a huge impact on these companies."
Carroll has filed a legal action in Britain calling on Cambridge Analytica to disclose what data was gathered and used on him.
An undercover investigation of Cambridge Analytica by Britain's Channel 4 said executives boasted they could entrap politicians in compromising situations with bribes and Ukrainian sex workers, and spread misinformation online.
The executives claimed to have worked in more 200 elections across the world, including Argentina, the Czech Republic, India, Kenya and Nigeria.
The British firm said it "strongly denies" the claims from Channel 4 as well as reports on misuse of Facebook data.
"Facebook data was not used by Cambridge Analytica as part of the services it provided to the Donald Trump presidential campaign," a statement read.
Frost Bank Says Data Breach Exposed Check Images
21.3.2018 securityweek Incindent
Frost Bank, a subsidiary of Cullen/Frost Bankers, Inc., announced on Friday that it discovered the unauthorized access to images of checks stored electronically.
According to the company, it discovered last week that a third-party lockbox software program had been compromised, resulting in unauthorized users being able to view and copy images of checks stored electronically in the image archive. Frost Bank systems weren’t impacted in the incident, Frost says.
Customers can use lockbox services to send payments to a central post office box. The bank receives the payments and credits them directly to a business’s account.
The information that was accessed as part of the incident could be used to forge checks, the company says.
The company says it stopped the identified unauthorized access immediately after discovering it, and that it also launched an investigation into the matter. Frost says it is working with an unnamed cybersecurity firm to investigate the incident and that the law-enforcement authorities have been informed as well.
“At Frost, we care deeply about taking care of our customers and protecting their information, and we regret that this situation has occurred. We are working very hard to make things right,” Frost Chairman and CEO Phil Green said in a statement.
According to the company, the unauthorized access was limited to a software program serving around 470 commercial customers using the electronic lockbox. The fraction of impacted Frost customer base might experience forgeries on accounts or could be informed of compromised check images.
Facebook Security Chief Changes Role to Focus on Election Fraud
21.3.2018 securityweek Social
Facebook's chief of security late Monday said his role has shifted to focusing on emerging risks and election security at the global social network, which is under fire for letting its platform be used to spread bogus news and manipulate voters.
Alex Stamos revealed the change in his role at work after a New York Times report that he was leaving Facebook in the wake of internal clashes over how to deal with the platform being used to spread misinformation.
"Despite the rumors, I'm still fully engaged with my work at Facebook," Stamos said in a message posted at his verified Twitter account.
"It's true that my role did change. I'm currently spending more time exploring emerging security risks and working on election security."
Stamos advocated investigating and revealing manipulation of news at the social network by Russian entities, to the chagrin of chief operating officer Sheryl Sandberg and other top executives, the Times reported, citing unnamed current and former employees.
Stamos reportedly decided in December he was done with Facebook, but remained at the social network as part of a plan to smoothly hand his job off to a successor. Neither Facebook nor Stamos directly commented on how long he intended to remain at the company, referring to his tweet in response to queries.
Word from Stamos came as the California-based social media giant faced an onslaught of criticism at home and abroad over revelations that a firm working for Donald Trump's presidential campaign harvested and misused data on 50 million members.
Calls for investigations came on both sides of the Atlantic after Facebook responded to the explosive reports of misuse of its data by suspending the account of Cambridge Analytica, a British firm hired by Trump's 2016 campaign.
Vera Jourova, the European commissioner for justice, consumers and gender equality, called the revelations "horrifying, if confirmed," and vowed to address concerns in the United States this week.
In Britain, parliamentary committee chair Damian Collins said both Cambridge Analytica and Facebook had questions to answer.
According to a joint investigation by the Times and Britain's Observer, Cambridge Analytica was able to create psychological profiles on 50 million Facebook users through a personality prediction app downloaded by 270,000 people, but also scooped up data from friends.
A Cambridge Analytica statement denied misusing Facebook data for the Trump campaign.
Facebook said it had hired a digital forensics firm to examine how the data leak occurred and to ensure that any data collected had been destroyed.
An undercover investigation of Cambridge Analytica by Britain's Channel 4 found executives boasted they could entrap politicians in compromising situations with bribes and Ukrainian sex workers, and spread misinformation online.
The executives claimed to have worked in more 200 elections across the world, including Argentina, the Czech Republic, India, Kenya and Nigeria. The British firm said it "strongly denies" the claims from Channel 4 as well as reports on misuse of Facebook data.
Coverity Scan Hacked, Abused for Cryptocurrency Mining
21.3.2018 securityweek Cryptocurrency
Coverity Scan, a free service used by tens of thousands of developers to find and fix bugs in their open source projects, was suspended in February after hackers breached some of its servers and abused them for cryptocurrency mining.
Synopsys, which acquired Coverity in 2014, started notifying Coverity Scan users about the breach on Friday. The company said malicious actors gained access to Coverity Scan systems sometime in February.
“We suspect that the access was to utilize our computing power for cryptocurrency mining,” Synopsys told users. “We have not found evidence that database files or artifacts uploaded by the open source community users of the Coverity Scan service were accessed. We retained a well-known computer forensics company to assist us in our investigation.”
Synopsys says the service is now back online and it believes the point of access leveraged by the attackers has been closed. In order to regain access to Coverity Scan, users will need to reset their passwords.
“Please note that the servers in question were not connected to any other Synopsys computer networks. This should have no impact on customers of our commercial products, and this event did not put any Synopsys corporate data or intellectual property at risk,” users were told.
Cybercriminals have become increasingly interested in making a profit by hacking PCs and servers and abusing them to mine cryptocurrencies. Cryptocurrency mining malware can target a wide range of devices, including industrial systems.
One recent high-profile victim was the carmaker Tesla, whose Kubernetes pods were compromised and used for cryptocurrency mining. According to RedLock, which discovered the breach, hackers gained access to Tesla’s Kubernetes console due to the lack of password protection.
Telegram Must Give FSB Encryption Keys: Russian Court
21.3.2018 securityweek BigBrothers
Moscow - Russia's Supreme Court on Tuesday ruled the popular Telegram messenger app must provide the country's security services with encryption keys to read users' messaging data, agencies reported.
Media watchdog Roskomnadzor instructed Telegram to "provide the FSB with the necessary information to decode electronic messages received, transmitted, or being sent" within 15 days, it said on its website.
Telegram had appealed against an earlier ruling that it must share this information, but this appeal was rejected on Tuesday.
If it does not provide the keys it could be blocked in Russia.
The free instant messaging app, which lets people exchange messages, photos and videos in groups of up to 5,000 people, has attracted more than 100 million users since its launch in 2013.
Telegram's self-exiled Russian founder Pavel Durov said in September 2017 the FSB had demanded backdoor access.
When Telegram did not provide the encryption keys, the FSB launched a formal complaint.
Durov wrote last year that the FSB's demands are "technically impossible to carry out" and violate the Russian Constitution which entitles citizens to privacy of correspondence.
Tuesday's ruling is the latest move in a dispute between Telegram and the Russian authorities as Moscow pushes to increase surveillance of internet activities.
Last June, Russia's state communications watchdog threatened to ban the app for failing to provide registration documents. Although Telegram later registered, it stopped short of agreeing to its data storage demands.
Companies on the register must provide the FSB with information on user interactions.
From this year they must also store all the data of Russian users inside the country, according to controversial anti-terror legislation passed in 2016 which was decried by internet companies and the opposition.
Oil and Gas Sector in Middle East Hit by Serious Security Incidents
21.3.2018 securityweek Incindent
Many oil and gas companies in the Middle East reported suffering at least one serious security incident in the past year, according to a study conducted by Ponemon Institute on behalf of German industrial giant Siemens.
Nearly 200 individuals responsible for overseeing cybersecurity risk in oil and gas companies in the Middle East have taken part in the study and the results show that many organizations are unprepared to address the risks faced by their operational technology (OT) networks.
According to Siemens, three-quarters of respondents said their organizations had suffered at least one security incident that resulted in disruption to operations in their OT environment or loss of confidential information in the past 12 months. Eleven percent of respondents said they had experienced more than 10 OT network intrusions, and nearly half believe they may not be aware of all breaches.Oil and gas industry in Middle East not prepared for cyberattacks
Roughly two-thirds of the individuals who took part in the survey believe the risk of attacks on industrial control systems (ICS) has increased considerably over the past few years, and 60 percent say there is a greater risk to OT environments compared to IT.
Outdated and ageing control systems pose a serious risk, according to 42 percent of respondents. The areas most at risk in Middle Eastern oil and gas companies are believed to be exploratory information, production information, potential partners, financial and organizational reports, operational data, information on drilling sites, and field production data collected by sensors.
While insider threats are the main concern, only 21 percent of respondents are concerned about malicious insiders, while 68 percent are more worried about the cybersecurity impact of careless employees.
Companies appear aware of the risks, but many of them are not prepared to deal with them. Less than half of respondents say they continually monitor their entire infrastructure, and only a quarter are confident in their ability to address security risks and allocate the resources necessary for addressing them. On average, companies have allocated only a third of their cybersecurity budget to protecting OT environments, the report shows.
Siemens says many organizations are still attempting to air gap their ICS environments in an effort to mitigate threats, but only 39 percent plan on hardening endpoints, and 20 percent plan on adopting analytics solutions over the next year.
Cyberattacks on oil and gas and petrochemical companies can have a devastating impact. Researchers discovered recently a piece of malware that leveraged a zero-day vulnerability in Schneider Electric’s Triconex Safety Instrumented System (SIS). The attack is said to have targeted a petrochemical company in Saudi Arabia and one of the main suspects is Iran. According to some reports, the attackers may have been trying to trigger a deadly explosion at the targeted plant.
XM Cyber Unveils Automated Purple-Teaming at Speed and Scale
21.3.2018 securityweek APT
Israeli Cybersecurity Startup Launches Automated Advanced Persistent Threat (APT) Simulation Platform
Penetration testing is the most effective method of testing whether existing security policy stands up against advanced attackers, but it doesn't scale well to large, dynamic networks, and only provides a single conclusion at a specific point in time. The solution is clearly automation.
XM Cyber is an Israeli firm founded in 2016. Its three co-founders are Tamir Pardo (formerly head of Mossad); Boaz Gorodissky (formerly head of technology for the government of Israel); and Noam Erez (who spent 25 years in Israeli intelligence). Its headquarters are in Israel, but with a presence in the U.S. and Australia. It has customers in Israel, the U.S. and Europe.
Its primary product, an automated APT simulation platform called HaXM, is unveiled today. The product simulates the possible behavior of an attacker in order to locate potential weaknesses on the system; and then, using the data gathered, provides recommendations for the remediation of those weaknesses. In this manner it provides automated red teaming with blue teaming to produce purple teaming at speed, continuously, and at scale.
"The problem we solve," VP of Product Adi Ashkenazy told SecurityWeek, "is that when you look at modern organizations and you see the kind of security stack they have in place, you have to wonder if they are actually securing their critical assets. This is something the companies ask themselves as well. They spend a lot of money on different products and vendors; but at the end of the day, if you ask them, 'are your critical assets secure?', they may have hope and some belief, but they have no concrete evidence to support the idea."
Manual penetration testing to prove the hypothesis of security, he continued, makes no sense for the modern organization that may have tens of thousands of endpoints, and hundreds of subsystems; and is continuously evolving and changing.
"This is why we founded XM Cyber," commented Noam Erez: "to equip enterprises with a continuous 360-degree view of which critical assets are at risk, what security issues they should focus on, and how best to harness their resources to resolve them."
HaXM places sensors only on 'endpoints of interest'. "We don't have to map the entire network," said Ashkenazy. "We deploy our sensors on the endpoints of interest within the infrastructure that hackers are able or likely to use. We try to be almost religious in the way we mimic attacks -- we don't put sensors on every endpoint."
Nor does HaXM start with any preconceived idea of a potential attack. "We don't define the attack vectors in advance," he said. "We act like a virtual hacker. We start from points of likely breach -- which could be internet-facing servers, for example; or endpoints that receive external email. We place our virtual hacker in those starting points with a tool box that mimics the capabilities of an advanced attacker; and from that moment on the virtual hacker mimics the steps taken by a real hacker trying to find his way to critical assets. We never know in advance what will be found, but so far the virtual hacker has always eventually managed to compromise the entire network."
This is HaXM's simulation mode, where great care is taken not to trigger any alarms from the customer's existing security stack. It checks for the conditions that could be used by an attacker. "This is what we use for 24/7 testing. But we also have a validation mode," added Ashkenazy. "When you switch to validation mode, this is not continuous, but is a controlled mode, where you specify when and where you want to actually test a specific attack vector -- and then we conduct the malicious activities to their full extent so that you can check the security stack in its entirety."
HaXM provides a visualization of the route an aggressor can take from initial entry point on a network to the company's critical assets. In doing this, it definitively presents the existence or absence of sufficient security, highlighting if and where additional security is necessary. While many security products seek to find indications of actual compromise after an initial breach, XM Cyber's approach is to find routes of potential compromise irrespective of an existing breach. It will not locate an attacker; but it will tell the customer what an attacker could achieve.
XM Cyber has offices in Herzliya, Israel; New York; and Sydney, Australia. It has raised $15 million as initial funding in its first two years. The product will be demonstrated at the RSA Conference in San Francisco, California in April 16-19, 2018.