Facebook Flaw Exposed Page Administrators
27.7.2018 securityweek Social
Facebook recently patched an information disclosure vulnerability that exposed page administrators, researcher Mohamed Baset reported this week.
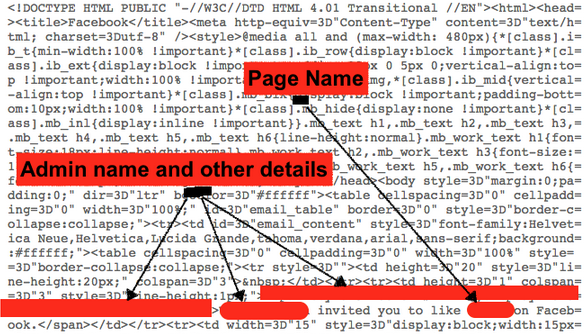
Baset claimed he discovered the issue, which he described as a “logical error,” within a few minutes of receiving an invitation to like a Facebook page on which he had liked a post.
Looking at the email’s source code, the researcher noticed that it included the name of the page’s administrator and other details.

After being notified through its bug bounty program, Facebook acknowledged the vulnerability and decided to award the expert $2,500 for his findings.
Sophos’ Paul Ducklin has provided an explanation on why such an information disclosure flaw can pose a problem to Facebook page administrators.
“For many individual Facebook pages, the administrator and the page will share an identity, so putting the admin’s name in the page’s email isn’t really giving away much,” Ducklin said. “But for business or community pages, which might have a number of co-administrators, you wouldn’t expect Facebook to reveal anything more than the name of the page itself, at least not without asking.”
“If nothing else, this protects individual employees from getting bombarded with comments and questions – whether they’re praises or rants – in place of the account itself,” the expert added.
Baset, founder and lead penetration tester at Seekurity, said this was the second time he reported a vulnerability to Facebook without having to write any code to demonstrate his findings.
Facebook reported recently that last year it paid out more than $880,000 for 400 valid vulnerability reports submitted by white hat hackers.
Splunk to Acquire Security Orchestration Firm Phantom for $350 Million
27.7.2018 securityweek IT
Machine data solutions firm Splunk said on Tuesday that it has agreed to acquire Phantom Cyber, a provider of Security Orchestration, Automation and Response (SOAR) solutions.
Under the terms of the agreement, Splunk will pay approximately $350 million in cash and stock to acquire Palo Alto, Calif.-based Phantom.
Phantom, which has raised more than $23 million in funding, has developed a community-powered security automation and orchestration platform that currently has more than 200 “apps” which integrate with various security products. These apps are available for a wide range of security tools from partners including Cisco, McAfee, Palo Alto Networks, RSA Security, Symantec, Splunk, HPE, IBM and others.
By combining technologies from both companies, Splunk says that IT teams will be able to leverage automation capabilities to “help solve automation challenges in a widening range of use cases, including Artificial Intelligence for IT Operations (AIOps).”
Following the acquisition, Phantom founder and CEO Oliver Friedrichs will report to Haiyan Song, senior vice president and general manager of security markets at Splunk.
The acquisition is expected to close during the first half of 2018, subject to customary closing conditions and regulatory reviews.
“The majority of purchase price consideration will be paid from cash on our balance sheet. Total equity consideration plus Phantom employee retention incentives will result in less than one percent total dilution from this transaction,” said Dave Conte, chief financial officer, Splunk.
Investors in Phantom include, iconic Silicon Valley VC firm Kleiner Perkins, TechOperators Venture Capital, Blackstone, Foundation Capital, In-Q-Tel, Rein Capital, Zach Nelson, and John W. Thompson.
Changes in Apple’s iCloud Security Policies and Argument of China
27.7.2018 securityaffairs BigBrothers
Changes in Apple’s iCloud Security Policies – Apple announced to relocating the encryption key for users data in China; from the United States of America to some country in Asia!
The latest chaos in the digital world regarding Apple has stricken like a bullet, as the iPhone manufacturer announced to relocating the encryption key for users data in China; from the United States of America to some country in Asia!
Well, some security advocates argue that this is incorrect for the corporation itself as well as a privacy threat for users, but according to Apple Company; the codes are secure.
According to the reports, the users of iCloud in China are confused that in what way Apple will manage the confidentiality of their essential data.
Apple too fears that data protection employees have concerns about changing the privacy of iCloud users in China, as per two reports this week.
The classified data such as online emails, photographs, and messages stay protected from hackers by encryption. And now, Apple will store encryption keys in China instead of the United States of America (Reuters and the Wall Street Journal reports).
It means that the Chinese authorities do not need to go to USA law agencies to force Apple to provide the rights to the data. This step in reaction to newly introduced laws in China, according to which iCloud services offered to the citizens, should secure data within premises of the country and can be used by Chinese organizations.
By the end of the coming month, Apple is going to start transmitting coded information to China and will work closely with a Chinese government. Apple did not say when the encryption data keys would move abroad.
Data protection advocates said, “The change can cause problems for political and other dissidents”.
“Given that Apple is going to work in China, it is unlikely that government can get access to Apple’s data from the local community,” said the professor at the Toronto University, studying the actions of the Chinese government carefully.
Apple says, however, that the data keys stored in a secure place, still Apple will control them. Besides, Apple also claimed that it would provide data only on demand to China’s current legislative requirements and did not create loopholes for access.
Apple’s high-level officer said to news agencies that iCloud is a matter of concern for the recently introduced laws.
The spokeswoman also noted that Apple decision to break the service of iCloud in China would lead to reduced client’s interaction with Apple and would reduce the security and confidentiality of data for Chinese users.
Big multinationals like Microsoft and Amazon also work with Chinese companies to provide cloud storage service and use the vast Chinese market. Two technological giants of USA refused to inform the magazine, where the encryption keys of the company’s data store.
Apple informed the news agencies that they sent a warning about the transition to Chinese iCloud users, which will allow them to disable iCloud to avoid data storage in the country. Apple also told that no one will be touched before accepting new terms of use in China.
Users whose configurations allow another nation like Macao and Hong Kong have not registered their data on servers in China.
The Reuters also includes Taiwan in this list; the newspaper does not do this.
Apple Company and Amazon did not respond to our request for additional comments yet. Microsoft also denied giving any further comments.
Israeli mobile forensics firm Cellebrite can unlock every iPhone device on the market
27.7.2018 securityaffairs Apple
The Israeli mobile forensics firm Cellebrite has designed a technology that allows it to unlock almost any iPhone, including the latest iPhone X.
We have debated for a long time the legal dispute between Apple and the FBI for unlocking the San Bernardino shooter’s iPhone 5c.
The tech giant refused to help the US authorities to unlock the mobile device and the FBI paid over a million dollar to a third-party company to access data contained in the San Bernardino’s shooter’s iPhone.

Such kind of dispute would not happen in the future, the Israeli mobile forensics firm Cellebrite has designed a technology that allows it to unlock almost any iPhone, including the latest iPhone X.
The Israeli mobile forensics firm Cellebrite that is one of the leading companies in the world in the field of digital forensics. The company already works with the principal law enforcement and intelligence agencies worldwide.
Cellebrite provides the FBI with decryption technology as part of a contract signed in 2013, its technology allows investigators to extract information from mobile devices.
The company’s Advanced Unlocking and Extraction Services could be used to unlock every iPhone running iOS 11 and older versions.
“Cellebrite, a Petah Tikva, Israel-based vendor that’s become the U.S. government’s company of choice when it comes to unlocking mobile devices, is this month telling customers its engineers currently have the ability to get around the security of devices running iOS 11.” reads a post published by Forbes.
“That includes the iPhone X, a model that Forbes has learned was successfully raided for data by the Department for Homeland Security back in November 2017, most likely with Cellebrite technology.”
Cellebrite says it advanced services can hack into “Apple iOS devices and operating systems, including iPhone, iPad, iPad mini, iPad Pro and iPod touch, running iOS 5 to iOS 11.”
According to Forbes, anonymous sources confirmed that Cellebrite could also unlock the iPhone 8, and likely the iPhone X.
“a source in the police forensics community told Forbes he’d been told by Cellebrite it could unlock the iPhone 8. He believed the same was most probably true for the iPhone X, as security across both of Apple’s newest devices worked in much the same way.” continues Forbes.
Law enforcement agencies that need to unlock a device (iOS or Android) simply need to send it to the company Labs where a pool of experts will do the job, the service costs as little as $1,500 per unlock.
“In its labs, the company then uses whatever secret exploits it has to crack the lock and either hands it back to investigators so they can take data from the device, or Cellebrite can do that for them. As Forbes previously detailed, this can be relatively inexpensive, costing as little as $1,500 per unlock.” states Forbes.
It also appears the FBI has already tried out Cellebrite service on the latest Apple devices, the iPhone X. According to a warrant viewed by Forbes related to a suspect in an arms trafficking (Abdulmajid Saidi), his iPhone X was sent to a Cellebrite specialist at the DHS Homeland Security Investigations Grand Rapids labs and the data extracted on December 5.
Cellebrite hasn’t commented on the latest report.
Flaw in Popular μTorrent Software Lets Hackers Control Your PC Remotely
27.2.2018 thehackernews Vulnerebility

If you have installed world's most popular torrent download software, μTorrent, then you should download its latest version for Windows as soon as possible.
Google's security researcher at Project Zero discovered a serious remote code execution vulnerability in both the 'μTorrent desktop app for Windows' and newly launched 'μTorrent Web' that allows users to download and stream torrents directly into their web browser.
μTorrent Classic and μTorrent Web apps run in the background on the Windows machine and start a locally hosted HTTP RPC server on ports 10000 and 19575, respectively, using which users can access its interfaces over any web browser.
However, Project Zero researcher Tavis Ormandy found that several issues with these RPC servers could allow remote attackers to take control of the torrent download software with little user interaction.
According to Ormandy, uTorrent apps are vulnerable to a hacking technique called the "domain name system rebinding" that could allow any malicious website a user visits to execute malicious code on user's computer remotely.
To execute DNS rebinding attack, one can simply create a malicious website with a DNS name that resolves to the local IP address of the computer running a vulnerable uTorrent app.
"This requires some simple DNS rebinding to attack remotely, but once you have the secret you can just change the directory torrents are saved to, and then download any file anywhere writable," Ormandy explained.
Proof-of-Concept Exploits for uTorrent Software Released Publicly
Ormandy also provided proof-of-concept exploits for μTorrent Web and μTorrent desktop (1 and 2), which are capable of passing malicious commands through the domain in order to get them to execute on the targeted computer.
Last month, Ormandy demonstrated same attack technique against the Transmission BitTorrent app.
Ormandy reported BitTorrent of the issues with the uTorrent client in November 2017 with a 90-days disclosure deadline, but a patch was made public on Tuesday—that's almost 80 days after the initial disclosure.
What's more? The re-issued new security patches the same day after Ormandy found that his exploits continued to work successfully in the default configuration with a small tweak.
"This issue is still exploitable," Ormandy said. "The vulnerability is now public because a patch is available, and BitTorrent have already exhausted their 90 days anyway."
"I see no other option for affected users but to stop using uTorrent Web and contact BitTorrent and request a comprehensive patch."
Patch your uTorrent Software NOW!
The company assured its users that all vulnerabilities reported by Ormandy it two of its products had been addressed with the release of:
μTorrent Stable 3.5.3.44358
BitTorrent Stable 7.10.3.44359
μTorrent Beta 3.5.3.44352
μTorrent Web 0.12.0.502
All users are urged to update their software immediately.
Phone-Cracking Firm Found a Way to Unlock Any iPhone Model
27.2.2018 thehackernews Apple
Remember the infamous encryption fight between Apple and the FBI for unlocking an iPhone belonging to a terrorist behind the San Bernardino mass shooting that took place two years ago?
After Apple refused to help the feds access data on the locked iPhone, the FBI eventually paid over a million dollar to a third-party company for unlocking the shooter's iPhone 5c.
Now, it appears that the federal agency will not have to fight Apple over unlocking iPhones since the Israeli mobile forensics firm Cellebrite has reportedly figured out a way to unlock almost any iPhone in the market, including the latest iPhone X.
Cellebrite, a major security contractor to the United States law enforcement agencies, claims to have a new hacking tool for unlocking pretty much every iPhone running iOS 11 and older versions, Forbes reports.
In its own literature [PDF] "Advanced Unlocking and Extraction Services," Cellebrite says its services can break the security of "Apple iOS devices and operating systems, including iPhone, iPad, iPad mini, iPad Pro and iPod touch, running iOS 5 to iOS 11."
Citing anonymous sources, the publication reported that Cellebrite could also unlock the iPhone 8, and since the security across Apple's newest iPhone devices worked in much the same way, the company can break the security of the iPhone X as well.
Besides Apple's devices, Cellebrite can also break into Google Android-powered smartphones from Samsung (Galaxy and Note series), Alcatel, Google Nexus, HTC, Huawei, LG, Motorola, ZTE and many more.
"Cellebrite Advanced Unlocking Services is the industry's only solution for overcoming many types of complex locks on market-leading devices," Cellebrite literature explains.
"This can determine or disable the PIN, pattern, password screen locks or passcodes on the latest Apple iOS and Google Android devices."
Last November, the Department of Homeland Security reportedly managed to get into an iPhone X owned by a suspect in an arms trafficking case, probably with the help of a Cellebrite-trained specialist.
However, a warrant discovered by Forbes does not mention the method or technology used by law enforcement to hack into the iPhone X.
Founded in 1999, Cellebrite provides digital forensics tools and software for mobile phones to its customers, which also includes the US government.
One of its main products is the Universal Forensic Extraction Device (UFED) that claims to help investigators extract all data and passwords from mobile phones.
While the Cellebrite's iPhone hacking tool has the potential to affect hundreds of millions of Apple users, Apple also rolls out software updates and patches on a regular basis.
So users are advised to keep their devices up-to-date, as its hard to say if the company's hacks work on the latest updates of iOS 11.
Neither Cellebrite nor Apple immediately commented on the latest report.
Android P Will Block Background Apps from Accessing Your Camera, Microphone
27.2.2018 thehackernews Android
Yes, your smartphone is spying on you. But, the real question is, should you care?
We have published thousands of articles on The Hacker News, warning how any mobile app can turn your smartphone into a bugging device—'Facebook is listening to your conversations', 'Stealing Passwords Using SmartPhone Sensors', 'Your Headphones Can Spy On You' and 'Android Malware Found Spying Military Personnel' to name a few.
All these stories have different objectives and targets but have one thing in common, i.e., apps running in the background covertly abuse ‘permissions’ without notifying users.
Installing a single malicious app unknowingly could allow remote attackers to covertly record audio, video, and taking photos in the background.
But, not anymore!
In a boost to user privacy, the next version of Google's mobile operating system, Android P, will apparently block apps idling in the background from accessing your smartphone's camera and microphone.
According to the Android Open Source Project (AOSP) commit, Google is working on two built-in features in Android P to protect its users from malicious apps spying on them using smartphones’ camera or microphone.
First spotted by XDA developers, the source code commit for both the camera and microphone changes notes that apps that are "idle" (aka running in the background) "for more than a certain amount of time" without specifying themselves will not be able to use the microphone or camera.
To do so, the Android P mobile operating system would target something known as an app's User ID (UID)—a unique ID assigned to an app when a user downloads it on his/her Android device that cannot be altered and are permanent until the app is uninstalled.
Android P would keep an eye on the app’s UID and block it from accessing the camera and microphone in any way whenever that UID is idle. Repeated attempts of requesting access to the camera would generate errors.
However, microphone-using apps will not be cut off from the microphone, but will "report empty data (all zeros in the byte array), and once the process goes in an active state, we report the real mic data."
It should also be noted that users talking on the smartphone while using other apps will not have to worry about these new features because the dialer application went into the background while active.
Imposing such limitations on apps would surely alleviate spying fears for Android users as of today when advertisers misuse such features to listen in on app users and Android malware capable of capturing audio, video, and images in the background are out there, for example, Skygofree and Lipizzan.
Android P is still in development and is not yet named. The company seems to release the next major version of Android in this year's Google I/O developer conference that will take place from May 8 to May 10 at the Shoreline Amphitheatre in Mountain View, California.
North Korea's Flash Player Flaw Now Exploited by Cybercriminals
27.2.2018 securityweek BigBrothers
Endpoint security firm Morphisec has spotted a massive campaign that exploits a recently patched Adobe Flash Player vulnerability to deliver malware.
The flaw in question, CVE-2018-4878, is a use-after-free bug that Adobe patched on February 6, following reports that North Korean hackers had been exploiting the vulnerability in attacks aimed at South Korea. The threat group, tracked as APT37, Reaper, Group123 and ScarCruft, has been expanding the scope and sophistication of its campaigns.
After Adobe patched the security hole, which allows remote code execution, other malicious actors started looking into ways to exploit CVE-2018-4878.
Morphisec said it spotted a campaign on February 22, which had been using a version of the exploit similar to the one developed by APT37. However, researchers pointed out that the exploit in the malspam campaign, unlike the one used in the original attacks, did not have a 64-bit version.
The attack starts with a spam email containing a link to a document stored on safe-storage[.]biz. Once downloaded and opened, the document informs users that an online preview is not available and instructs them to enable editing mode in order to view the content.
If users comply, the Flash vulnerability is exploited and the Windows command prompt is executed. The associated cmd.exe file is then injected with malicious shellcode that connects to the attacker’s domain.
A DLL file is then downloaded by the shellcode and executed using the Microsoft Register Server (regsvr32) utility. The legitimate tool is abused in an effort to bypass whitelisting products.
The malicious documents and the Flash exploit were only detected by a few security solutions based on their signature at the time of Morphisec’s analysis.
Since the URLs included in the spam emails were created using Google’s URL shortening service, researchers determined that each of the different links delivered in this campaign had been clicked tens and even hundreds of times within 3-4 days of being created. Users clicked on the links from various browsers and email services, including Outlook, Gmail and Aruba.it.
“As expected and predicted, adversaries have quickly adopted the Flash exploit, which is easily reproducible,” Morphisec’s Michael Gorelik explained in a blog post. “With small variations to the attack, they successfully launched a massive malspam campaign and bypassed most of the existing static scanning solutions once again.”
Evrial: The Latest Malware That Steals Bitcoins Using the Clipboard
27.2.2018 securityaffairs Virus
Evrial is a cryptocoin malware stealer discovered by the researchers at ElevenPaths which takes control of the clipboard to get “easy money”.
Evrial is a cryptocoin malware stealer which takes control of the clipboard to get “easy money”.
ElevenPaths has taken a deep technical dive into the malware itself, to show how it technically works, with a quite self-explanatory video. Aside, we have followed the steps of its Russian creator and found that his scam has been targeting other scammers themselves.

By the end of 2017, CryptoShuffle was a malware sample capable of reading the clipboard and modifying cryptocurrency addresses found there. Later, someone realized that there could be some business on providing these features as a service and started to sell the platform itself calling it “Evrial”. The product was formed by a .NET malware sample capable of stealing passwords from browsers, FTP clients, Pidgin and it could also modify the clipboard on the fly so as to change any copied cryptocurrency address to whatever address he wanted to.
Evrial allows the attacker to control it all from a comfortable panel where the stolen data can be easily explored. When the attacker buys the application, he can set his “name” for logging into the panel which will be hardcoded in the code, so that the shipped Evrial version is unique for him.
When you want to make a Bitcoin transfer, you usually copy and paste the destination address. In this sense, the attacker waits until the user, trusting in the clipboard action, sends a new transaction to the copied cryptocurrency address, without knowing that the recipient’s address has been silently modified to one that belongs to the attacker. The malware performs this task in the background for different types of address including Bitcoin, Litecoin, Ethereum and Monero addresses as well as for Steam identifiers and Webmoney WMR and WMZ units.
The author exposes his username in Telegram: @Qutrachka. The account is in the source code in order to be able to contact him. Using this information and some other analysed samples, it has been possible to identify users in different deep web forums under the name Qutra whose main objective: sell this malicious software. There are also evidences that CryptoSuffer malware was linked to the same threat actor after identifying a publication in Pastebin explaining the functionalities of this family and published under the same user.
We are able to guess how much it is in every wallet. He has received a total of 21 transactions into the Bitcoin wallet, supposedly from his victims, collecting approximately 0.122 BTC. If ransomware wallets usually receive the same amount from its victims, here the range is wider because the legitimate payments that the victim wants to do are, of course, of different amounts.
The attacker has moved all the money to several addresses to try to blur the trail of his payments. The attacker has received 0.0131 Litecoins as well, but this amount is still available in his wallet. On the other hand, it has not been possible to track any payments related to his Monero account because of how this technology works so as to hide the information of which parties have been involved in each operation. At the same time, we could not find out any additional information linked to his various Webmoney accounts (WMR and WMZ). Anyway, what is clear is that this type of malicious behavior is technically viable while it is being used in the wild.
Line Between Nation-State, Criminal Hackers Increasingly Blurred: Report
26.2.2018 securityweek Crime
The line between the level of sophistication typically exhibited by state-sponsored threat groups and cybercriminals became increasingly blurred in the past year, according to CrowdStrike’s 2018 Global Threat Report.
CrowdStrike has analyzed various aspects of the cybersecurity landscape in the past year, including targeted attacks launched by nation state actors, the tools and operations of cybercriminals, hacktivism, law enforcement campaigns, and the effectiveness of attacks and defense mechanisms.
According to the security firm, there are several factors that led to the leveling of the playing field, but one of the most significant is the so-called “trickle-down effect.” This product adoption model states that a product initially too expensive for the masses eventually gets cheap enough for the general public to acquire.
Applying this model to the cybersecurity scene, we have the EternalBlue exploit, which is believed to have been developed by the U.S. National Security Agency (NSA), getting leaked by a group named Shadow Brokers. This has allowed other state-sponsored attackers – including in the WannaCry and NotPetya attacks believed to have been launched by North Korea and Russia – and profit-driven cybercriminals to use the exploit to accomplish their own goals.
On one hand, attacks such as the ones involving NotPetya and WannaCry malware have inspired cybercriminals, giving them ideas on how to maximize profits. On the other hand, state-sponsored actors have also taken inspiration from cybercriminals – both the NotPetya and WannaCry attacks were made to appear as if they were ransomware campaigns launched by profit-driven criminals.
Sophisticated supply chain attacks have been typically used by nation state groups, but last year saw several incidents that did not appear to be the work of state-sponsored cyberspies.
One incident involved rogue Python libraries being uploaded to the Python Package Index (PyPI). While the libraries included malicious code, it actually turned out to be benign, which has led some experts to believe that it may have been the work of a grey hat hacker.
Other incidents involved a piece of macOS malware called ProtonRAT, which attackers managed to deliver last year on at least two occasions after compromising websites hosting popular video conversion and media player apps. Operation WilySupply analyzed by Microsoft also falls into this category.
The list of supply chain attacks attributed to state-sponsored groups last year included the CCleaner and NetSarang incidents, which some linked to China, and the NotPetya campaign, whose initial infection vector was an updater for a Ukrainian tax accounting application.
“CrowdStrike's report is just one more in a long line of publications that demonstrates the increasing futility of technical attribution. The largest detriment of this trend of nation states hiding in the hacking noise is that the security industry no longer can have confidence in its traditional technical attribution models. Relying on code usage and IPs in a world where we know tool kits and techniques are shared, stolen, and sold amongst hackers is a recipe for misattribution,” Ross Rustici, senior director of intelligence services at Cybereason, commented on the CrowdStrike report.
“Hackers, especially the higher tier have proven time and again that they are capable and willing to play on cybersecurity's habit of confirmation bias by using false flags to point the community in the direction of a particular nation state or criminal group that is either: 1) currently the most talked about group making which plays into the self interest of the company of finding something that already garners a lot of media and PR attention; or 2) plays to the nationalism of the victim,” Rustici added.
NanoCore RAT Creator Sentenced to Prison
26.2.2018 securityweek Virus
A Hot Springs, Arkansas man who last year admitted in court to creating the NanoCore RAT (Remote Access Trojan) was sentenced to 33 months in prison.
Taylor Huddleston, 27, was sentenced on Friday for helping and assisting with computer intrusions through the development and marketing of malicious software, the Department of Justice announced. The programs he created were used to steal sensitive data from victims, spy on them, and conduct other illegal intrusions.
In addition to the 33 months in prison, Huddleston was ordered to serve two years of supervised release following his prison sentence.
Accused of developing, marketing, and distributing two malware families, Huddleston pleaded guilty in court in July 2017.
The first malicious program Huddleston developed is the NanoCore RAT, a backdoor that allows attackers to steal information from victim computers, including passwords, emails, instant messages, and other sensitive data. Used to infect and attempt to infect tens of thousands of systems, the RAT allows attackers to activate infected machines’ webcams to spy on victims.
NanoCore RAT was used in attacks targeting the finance departments of small and medium-sized businesses in the U.K., the U.S. and India, as well as in other global infection campaigns. Distribution methods included, among others, fileless tricks to the abuse of free Voice-over-IP (VoIP) service Discord.
Huddleston also admitted to creating Net Seal, licensing software that allowed him to distribute malware for co-conspirators for a fee. Huddleston is said to have used Net Seal to assist Zachary Shames in his attempt to infect 3,000 systems with malware that was in turn used to infect 16,000 computers.
Huddleston built Net Seal in 2012 and created NanoCore in 2014 (he marketed the RAT as a remote desktop management utility.
In his guilty plea last year, Huddleston admitted that he intended the programs to be used maliciously.
PhishMe Acquired at $400 Million Valuation, Rebranded as Cofense
26.2.2018 securityweek Phishing
Private Equity Deal Values Cofense at $400 Million
PhishMe, a security awareness firm that focuses on training employees on how to recognize and report phishing attacks, has been acquired by a private equity consortium in a deal that valued the company at $400 Million.
The company has also re-branded and changed its name to Cofense.
“PhishMe was founded to challenge the cliché - human is the weakest link,” said Rohyt Belani, CEO and Co-Founder of Cofense. “The Cofense solution set leverages internal employee-generated attack intelligence in concert with purpose-built response technologies to break the attack kill chain at delivery. Cofense reflects the full breadth of our portfolio of enterprise-wide attack detection, response, and orchestration solutions.”
Cofense LogoThe company says it currently has more than 1700 customers globally and that its PhishMe Reporter is installed on more 10 million endpoints.
In a recent survey by the Financial Services Information Sharing and Analysis Center (FS-ISAC) that polled more than 100 of its 7,000 global members, thirty-five percent of CISOs in the financial sector consider staff training to be the top priority for cyber defense.
“With cybersecurity a top priority for organizations everywhere, our goal is to continue bringing innovative products to markets around the globe to help stop active attacks faster than ever,” Belani added.
Cofense says it has experienced roughly 80% CAGR over the last four years, and has new offices opening in Australia, Singapore, Dubai, and Saudi Arabia.
The company has previously raised a total of roughly $58 million, including a large $42.5 million funding round in July 2016. The company had raised $2.5 million in July 2012 in a Series A round, followed by $13 Million in a Series B funding round in March 2015.
Security awareness firms have been the subject of significant funding and M&A transactions in recent months.
Earlier this month, security awareness training firm Wombat Security agreed to be acquired by Proofpoint for $225 million in cash. In August 2017, Webroot acquired Securecast, an Oregon-based company that specializes in security awareness training. In October 2017, security awareness training and simulated phishing firm KnowBe4 secured $30 million in Series B financing, which brought the total amounbt raised by KnowBe4 to $44 million. Security awareness training firm PhishMe has raised nearly $58 million in funding, including a $42.5 million series C funding round in July 2016.
Researchers Propose Improved Private Web Browsing System
26.2.2018 securityweek Privacy
A group of researchers from MIT and Harvard have presented a new system designed to make private browsing even more private.
Dubbed Veil, the system proposes additional protections for people who share computers with other people at the office, in hotel business centers, or university computing centers. The new system, the researchers claim, can be used in conjunction with existing private-browsing systems and anonymity networks. The system works even if users don’t visit a page using a browser’s native privacy mode.
In a paper (PDF) describing Veil, Frank Wang – MIT Computer Science and Artificial Intelligence Laboratory (CSAIL), Nickolai Zeldovich – MIT CSAIL, and James Mickens – Harvard, explain that the system is meant to prevent information leaks “through the file system, the browser cache, the DNS cache, and on-disk reflections of RAM such as the swap file.”
The researchers explain that existing private-browsing sessions rely on retrieving data, loading it into memory, and attempting to erase it when the session is over. However, because of a complex memory management process, some data could end up on a hard drive, where it could remain for days, with the browser not knowing what happened to that data.
The newly proposed system keeps all the data that the browse loads into memory encrypted until it is displayed on the screen, the researchers say. Users no longer type a URL into the browser, but access the Veil website and enter the URL there. With the help of a blinding server, the Veil format of the requested page is transmitted.
While the Veil page can be displayed in any browser, there is a bit of code in the page that executes a decryption algorithm and all of the data associated with the page is unreadable until it goes through that algorithm, the researchers say.
The system would also add decoy, meaningless code to every served page, so that the underlying source file is modified without affecting the way the page looks to the user. With no two transmissions of a page by the blinding sever similar, an attacker capable of recovering snippets of decrypted code after a Veil session should not be able to determine what page the user had visited.
“The blinding servers mutate content, making object fingerprinting more difficult; rewritten pages also automatically encrypt client-side persistent storage, and actively walk the heap to reduce the likelihood that in-memory RAM artifacts will swap to disk in cleartext form. In the extreme, Veil transforms a page into a thin client which does not include any page-specific, greppable RAM artifacts,” the paper reads.
One other option would be to have the blinding server opening the requested page itself, taking a picture of it, and sending the picture to the user’s computer. Should the user click anywhere on the image, the browser records the position of the click and sends the data to the server, which processes it and returns an image of the updated page.
Veil uses an opt-in model, meaning that the use of the new private browsing system requires developers to create Veil versions of their sites. To help in this regard, the researchers built a compiler to help admins convert sites automatically and is also capable of uploading the converted version of a site to a blinding server.
“To publish a new page, developers pass their HTML, CSS, and JavaScript files to Veil’s compiler; the compiler transforms the URLs in the content so that, when the page loads on a user’s browser, URLs are derived from a secret user key. The blinding service and the Veil page exchange encrypted data that is also protected by the user’s key. The result is that Veil pages can safely store encrypted content in the browser cache; furthermore, the URLs exposed to system interfaces like the DNS cache are unintelligible to attackers who do not possess the user’s key,” the paper reads.
The blinding servers, however, require maintenance, either by a network of private volunteers or a for-profit company. However, site admins would also have the option to host Veil-enabled versions of their sites themselves.
Ukraine Arrests 'Avalanche' Cybercrime Organizer: Police
26.2.2018 securityweek CyberCrime
Ukraine has detained one of the organizers of the massive Avalanche cybercrime network, police said on Monday, over a year after the global ring was busted in an international raid.
"An organizer of the international crime platform known as 'Avalanche' which infected up to half a million computers in the world daily was detained in Kiev Sunday," Ukraine's cyber police said in a statement.
Avalanche was a criminal network providing infrastructure for malware and DDoS (distributed denial of service) spam attacks across the world before it was busted in an unprecedented global sting operation.
Speaking to AFP, a cyber police spokeswoman confirmed the arrested man was Gennadiy Kapkanov, a Ukrainian citizen who was using a passport with a different identity.
Police also searched his rented flat, seizing a laptop and memory storage devices, it said.
In November 2016, police from more than 25 countries smashed the network and arrested its top bosses following a four-year operation.
Hundreds of servers were shut down or seized and 800,000 internet domains were blocked, Europol said at the time, in one of the biggest takedowns to date.
During the operation, Kapkanov was also detained in the sting at his home in Poltava, a city in central Ukraine, but the local court did not formally arrest him and he disappeared, Ukrainian media said.
Later on Monday, the same court will have to rule again on whether to formally place Kapkanov under arrest.
VISA – The adoption of chip-and-PIN card technology lead to 70% Drop in Counterfeit Fraud
26.2.2018 securityaffairs Crime
VISA – The cases of counterfeit fraud had dropped by 70% in September 2017 compared to December 2015 thanks to the diffusion of the diffusion in the storefronts of payment systems for EMV cards.
The introduction of chip-and-PIN card technology in the United States improved in a significant way the security of merchants and has reduced payment card fraud.
The cases of counterfeit fraud had dropped by 70% in September 2017 compared to December 2015 thanks to the diffusion of the diffusion in the storefronts of payment systems for EMV cards.
“For merchants who have completed the chip upgrade, counterfeit fraud dollars
EMV chip cards and chip-activated merchants combat counterfeit fraud in the U.S.
December 2017 Visa Chip Card Update in September 2017 compared to December 2015″ states VISA.
The process started in 2011 with the introduction of EMV (Europay, MasterCard, Visa) card technology in the United States.
The process was very slow, according to Visa, by September 2015, only roughly 392,000 merchants were accepting payment card using the new technology. at the same period, the number of Visa debit and credit cards using the EMV technology was only at 159 million.
Now Visa has shared data related to the adoption of the EMV technology by December 2017. The number of storefronts that currently accept payments with chip cars has reached 2.7 million in the U.S. (+570%), representing 59% of the total.

The number of Visa payment cards using EMV technology increased passed from 159 million to 481 million (202%), with 67% of Visa payment cards having chips.

It is an excellent result, according to VISA Chip transactions continue to increase in the US. EMV cards accounted for 96% of the overall payment volume in the United States in December 2017, with chip payment volume reaching $78 billion.

Cybercriminals have responded to the adoption of EMV chip cards focusing their efforts on card-not-present (CNP) fraud had that is today a serious concern for merchants.