Samsung Smartphones Get Encrypted Communications
28.7.2018 securityweek Krypto
KoolSpan this week announced a partnership with Samsung to implement secure communications on Samsung smartphones.
KoolSpan, a provider of encrypted secure voice and messaging solutions for mobiles, is already offering secure communications to enterprises. With support for mainstream phones, which are normally used within organizations, the solutions bring end-to-end encryption to all internal calls and texts within a company.
The end result of the partnership between KoolSpan and Samsung is TrustCall Native for Samsung, which provides native dialer integration on Samsung devices and which is being demonstrated at the Mobile World Congress in Barcelona.
The solution is aimed at tackling the rise in attacks on mobile communications, which normally consist of calls and messages being intercepted through the exploitation of vulnerabilities in mobile internetworking protocols.
Last year, the U.S. Department of Homeland Security (DHS) issued a report to underline some of the issues plaguing mobile communications, suggesting that both deliberate and accidental threats to mobile security continue to exist.
TrustCall Native for Samsung is focused on addressing such concerns by offering more secure communications on Samsung smartphones. To ensure ease-of-use, it integrates with Samsung native functionality for phone, messaging and contacts and applies encryption automatically.
KoolSpan’s solution is managed, deployed and configured across all smartphones within an organization by the IT department and is integrated with the phone’s native dialer and messenger. TrustCall Native Secure Communications for Samsung is available for customers with a Samsung Enterprise Alliance Program (SEAP) account and a subscription to KNOX Configure.
“We’re excited to partner with KoolSpan, which enables us to implement secure communications on Samsung smartphones. TrustCall Native, one of KoolSpan’s flagship products, is the best example of the universal understanding that security is only as good as it is easy to use,” Mike Kazmierczak, Samsung B2B Business Development Manager, Mobile B2B Team, EMEA, said.
Thanatos Ransomware Makes Data Recovery Impossible
28.7.2018 securityweek Ransomware
A newly discovered ransomware family is generating a different encryption key for each of the encrypted files but saves none of them, thus making data recovery impossible.
Dubbed Thanatos, the malware was discovered by MalwareHunterTeam and already analyzed by several other security researchers.
When encrypting files on a computer, the malware appends the .THANATOS extension to them. After completing the encryption, the malware connects to a specific URL to report back, thus allowing attackers to keep track of the number of infected victims.
The malware also generates an autorun key to open the ransom note every time the user logs in. In that note, the victim is instructed to send $200 to a listed crypto-coin address. Victims are also instructed to contact the attackers via email to receive a decryption program.
Thanatos’ operators allow victims to pay the ransom in Bitcoin, Ethereum, or Bitcoin Cash, thus becoming the first ransomware to accept Bitcoin Cash payments, Bleeping Computer’s Lawrence Abrams points out.
The issue with the new ransomware is that it, because it doesn’t save the encryption keys, files cannot be decrypted normally. However, victims don’t know that and might end up paying the ransom in the hope they can recover their files.
The good news regarding Thanatos, however, is that there might be a way to brute force the encryption keys, at least this is what security researcher Francesco Muroni suggests. However, this process would take a long time and would require for it to be a common file type with a known magic header.
Because of the botched encryption process, it is recommended to avoid paying the ransom if infected with Thanatos. Of course, this applies to every ransomware infection. It is also recommended to always keep applications up to date, and to use a security program capable of preventing this type of malware from compromising your systems.
Memcached Abused for DDoS Amplification Attacks
28.7.2018 securityweek Attack
Malicious actors have started abusing the memcached protocol to launch distributed denial-of-service (DDoS) attacks, Cloudflare and Arbor Networks warned on Tuesday.
Memcached is a free and open source distributed memory caching system designed to work with a large number of open connections. Clients can communicate with memcached servers via TCP or UDP on port 11211.
Cloudflare noticed in recent days that memcached has been abused for DDoS amplification attacks, and so have Arbor Networks and Chinese security firm Qihoo 360. Cloudflare has dubbed this type of attack Memcrashed.
Attackers are apparently abusing unprotected memcached servers that have UDP enabled. Similar to other amplification methods, the attacker sends a request to the targeted server on port 11211 using a spoofed IP address that matches the IP of the victim. The request sent to the server is just a few bytes, but the response can be tens of thousands of times bigger, resulting in a significant attack.
The largest memcached DDoS attack observed by Cloudflare peaked at 260 Gbps, but Arbor Networks reported seeing attacks that peaked at 500 Gbps and even more.
“I was surprised to learn that memcached does UDP, but there you go!” said CloudFlare’s Marek Majkowski. “The protocol specification shows that it's one of the best protocols to use for amplification ever! There are absolutely zero checks, and the data WILL be delivered to the client, with blazing speed! Furthermore, the request can be tiny and the response huge (up to 1MB).”
Arbor Networks noted that the type of queries used in these attacks can also be directed at TCP port 11211, but since TCP queries cannot be reliably spoofed, this protocol is less likely to be abused. The company pointed out that Chinese researchers warned about the possibility of attacks abusing memcached in November.
In the attacks seen by Cloudflare, attackers abused servers from all around the world, but mostly from North America and Europe. A majority of the servers are hosted by OVH, DigitalOcean and Sakura.
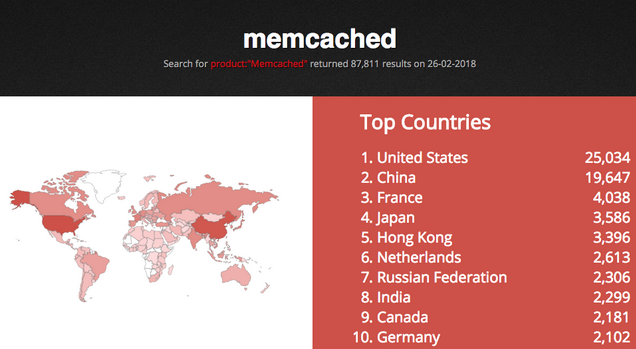
The attacks monitored by the content delivery network (CDN) came from roughly 5,700 unique IPs associated with memcached servers, but experts expect to see much larger attacks in the future considering that Shodan shows nearly 88,000 open servers. A majority of the exposed systems are in the United States, followed by China and France.

“Arbor’s current assessment is that, as with most other DDoS attack methodologies, memcached DDoS attacks were initially – and for a very brief interval – employed manually by skilled attackers; they have subsequently been weaponized and made available to attackers of all skill levels via so-called ‘booter/stresser’ DDoS-for-hire botnets,” Arbor Networks researchers said in a blog post. “The rapid increase in the prevalence of these attacks indicates that this relatively new attack vector was weaponized and broadly leveraged by attackers within a relatively short interval.”
Cloudflare recommends disabling UDP support unless it’s needed, and advised system administrators to ensure that their servers are not accessible from the Web. Internet service providers (ISPs) can also contribute to mitigating these and other types of amplification attacks by fixing vulnerable protocols and preventing IP spoofing.
Ad Network Performs In-Browser Cryptojacking
28.7.2018 securityweek CoinMine
An ad network provider is performing in-browser Coinhive cryptojacking on websites that use its service, 360 Netlab security researchers warn.
The practice has been ongoing since December 2017, several months after the ad network provider, a company called PopAds Publisher, started using domain generation algorithm (DGA) technology to bypass ad blockers, claiming it would allow customers to “monetize traffic that wasn’t monetized before.”
In mid-2017, the provider started to generate seemingly random domains that would ensure ads can reach end users. By the end of the year, however, these domains, which 360 Netlab refers to as DGA.popad, started participating in cryptojacking activities, all without end-users’ acknowledgement.
Given that many people use ad blockers to prevent sites from displaying ads to them, ad networks often attempt to bypass blockers, and this provider decided to use DGA domains to host its advertisements. With these domains changing daily, it becomes difficult to block the ads, the researchers point out.
What’s more, the ad network provider recently started using the DGA.popad domains to perform cryptojacking. These domains, the researchers discovered, have a strong connection with Coinhive family domains in DNS traffic and serve the coinhive.min.js web miner.
Some of the DGA.popad domains have a high ranking, with one of them found in the top 2000 sites on Alexa and several others in the top 3000 list.
Once a user accesses such a site, their computer’s CPU starts being used to the full. According to 360 Netlab, the favicon.ico on the DGA.popad sites was found to run as a web miner. Most of the sites that would redirect users to DGA.popad domains are providing adult content and downloading services.
Because the impacted sites contain advertisements from this ad network, the cryptojacking activities are performed regardless of whether the user has an ad blocker installed or not.
Normally, users would be sent to a standard domain (serve.popads.net) hosted by the provider. If an ad blocker is used, the standard domain is blocked, and the visitor is sent to one of the DGA.popad domains. Regardless of the delivery mechanism, both the ad and the cryptojacking script are served.
“We are not able to make a detailed assessment. This is because only part of all the traffic passing DGA.popad and serve.popads.net will be inserted a web miner, but we are not sure which part will be selected, for now,” the researchers note.
Trump Yet to Order Spies to Retaliate Against Russia: NSA Chief
28.7.2018 securityweek BigBrothers
President Donald Trump has not yet ordered his spy chiefs to retaliate against Russian interference in US elections, the head of the National Security Agency told lawmakers Tuesday.
"We have not opted to engage in some of the same behaviors we are seeing," said Admiral Michael Rogers, who heads both the NSA -- the leading US electronic eavesdropping agency -- and the new US Cyber Command, the military body charged with online combat.
Asked in a Senate Intelligence Committee hearing if he had received orders from Trump to fight back against Moscow's meddling, Rogers said: "No, I have not."
Rogers denied claims that the agency is doing nothing to push back against Russian hacking, theft of US cyber secrets and other activities.
However, he acknowledged: "They have not paid a price that is sufficient to change their behavior."
Rogers echoed the comments he and five other US intelligence chiefs made two weeks ago at the House Intelligence Committee, where all said they had not been ordered by Trump to counter the Russians.
The US has accused Russia of actively interfering in the 2016 presidential election, stealing Democratic party communications and pushing out disinformation through social media.
It also accuses Moscow of stealing hacking secrets of the US intelligence community.
Rogers said an order for Trump is needed before the US intelligence community and military can undertake offensive online operations against the Russians.
"What I see on the Cyber Command side leads me to believe that if we don't change the dynamic here, that this is going to continue, and 2016 won't be viewed as isolated," he said.
But he said that at a lower level, the NSA and Cyber Command could take some unspecified actions to rebuff attackers.
Asked about the exchange in Congress, White House spokeswoman Sarah Sanders suggested the president does not need to act.
"Nobody is denying him the authority," she said of Rogers.
A vulnerability in Facebook exposed email and details of page administrator
28.7.2018 securityaffairs Social
The security researcher Mohamed Baset discovered a vulnerability in Facebook that exposed email and other details of a page administrator.
Facebook has recently addressed an information disclosure vulnerability discovered by the security researcher Mohamed Baset that exposed page administrator.
According to Baset, the flaw is a “logical error” that he discovered after receiving an invitation to like a Facebook page on which he had liked a post.

“One day i liked one of the posts of a specific page but i didn’t liked or followed the page itself after a few days i got an email notification from facebook regarding an invitation to like the page that i did already liked one of its posts, I was amazed by the feature but i realized that this is a feature to target non-fans and i was wondering what could go wrong since this is a new feature ?” state the blog post published by the expert.
“From the investigations that i’m doing sometimes in the office of the fraud and phishing emails i’m always and blindly showing the “Original” of the message (that can be achieved by clicking on the little drop-down menu arrow beside the message reply button)”
The researchers analyzed the source code of the email sent by the social network and discovered it includes the name of the administrator of the page and other info.

The researcher reported the issue to Facebook that acknowledged it and decided to award the expert $2,500 as part of its bug bounty program.
Facebook announced to have paid out more than $880,000 for 400 vulnerability reports submitted by hackers.
Many of you may consider that the issue is not so serious, but this isn’t true because under certain circumstance the data exposure could represent a threat to the users’ privacy
In the case of business or community pages, revealing the identities of the administrators could get them targeted by messages and comments.
“For many individual Facebook pages, the administrator and the page will share an identity, so putting the admin’s name in the page’s email isn’t really giving away much. But for business or community pages, which might have a number of co-administrators, you wouldn’t expect Facebook to reveal anything more than the name of the page itself, at least not without asking.” reads the blog post published by Sophos. “If nothing else, this protects individual employees from getting bombarded with comments and questions – whether they’re praises or rants – in place of the account itself.”
Recently patched CVE-2018-4878 Adobe Flash Player flaw now exploited by cybercriminals
28.7.2018 securityaffairs Vulnerebility
Security researchers at Morphisec have uncovered a massive hacking campaign that is exploiting the recently patched CVE-2018-4878 Adobe Flash Player vulnerability.
Threat actors are exploiting the use-after-free flaw to deliver malware.
The CVE-2018-4878 vulnerability was fixed by Adobe on February 6, after security experts discovered it was used by North Korea-linked APT37 group in targeted attacks against South Korea.
Now the same vulnerability has been exploited by other threat actors in the wild as confirmed by Morphisec. The company spotted a campaign on February 22, the attackers were using a version of the exploit similar to the one used by the APT37 group.
The campaign is attributed to a financially motivated threat actor that exploited the CVE-2018-4878 in a malspam campaign, another thing highlighted by the researchers is that this exploit did not have a 64-bit version like the original one.
The attackers used spam emails containing a link to a document stored on safe-storage[.]biz. Once downloaded and opened, the document tries to trick victims with social engineering. It notifies users that an online preview is not available and instructs them to enable editing mode in order to view the content.
If the user enables the editing mode, the CVE-2018-4878 Adobe vulnerability is exploited and the Windows command prompt is executed. The associated cmd[.]exe file is then injected with malicious shellcode that connects to the attacker’s domain.
Security researchers at Morphisec have uncovered a massive hacking campaign that is exploiting the recently patched CVE-2018-4878 Adobe Flash Player vulnerability.
Threat actors are exploiting the use-after-free flaw to deliver malware.
The CVE-2018-4878 vulnerability was fixed by Adobe on February 6, after security experts discovered it was used by North Korea-linked APT37 group in targeted attacks against South Korea.
Now the same vulnerability has been exploited by other threat actors in the wild as confirmed by Morphisec. The company spotted a campaign on February 22, the attackers were using a version of the exploit similar to the one used by the APT37 group.
The campaign is attributed to a financially motivated threat actor that exploited the CVE-2018-4878 in a malspam campaign, another thing highlighted by the researchers is that this exploit did not have a 64-bit version like the original one.
The attackers used spam emails containing a link to a document stored on safe-storage[.]biz.
The URLs included in the emails is generated with Google’s URL shortening service, this circumstance allowed the researchers to determine the number of victims that clicked it. According to Morphisec each of the different links used in this campaign had been clicked tens and even hundreds of times within 3-4 days of being created.
Once downloaded and opened, the document tries to trick victims with social engineering. It notifies users that an online preview is not available and instructs them to enable editing mode in order to view the content.

If the user enables the editing mode, the CVE-2018-4878 Adobe vulnerability is exploited and the Windows command prompt is executed. The associated cmd[.]exe file is then injected with malicious shellcode that connects to the attacker’s domain.
“On February 22, 2018, Morphisec Labs spotted several malicious word documents exploiting the latest Flash vulnerability CVE-2018-4878 in the wild in a massive malspam campaign.” states the analysis published by Morphisec.
“After downloading and opening the Word document, the attack exploits the Flash vulnerability 2018-4878 and opens a cmd[.]exe which is later remotely injected with a malicious shellcode that connects back to the malicious domain.”
Then the shellcode downloads a dll from the same domain, which is executed using Microsoft Register Server utility to bypass whitelisting solutions.
According to the experts, only a limited number of security solutions flag the bait documents as malicious.
“As expected and predicted, adversaries have quickly adopted the Flash exploit, which is easily reproducible. With small variations to the attack, they successfully launched a massive malspam campaign and bypassed most of the existing static scanning solutions once again.” concluded Morphisec.
Widespread Vulnerability Found in Single-Sign-On Products
27.7.2018 securityweek Vulnerebility
A behavioral quirk in SAML libraries has left many single-sign-on (SSO) implementations vulnerable to abuse. It allows an attacker that has gained any authenticated access to trick the system into granting further access as a different user without knowledge of that user's password.
This could be used by an attacker who has compromised a low level limited access account to acquire access to third-party cloud services -- or it could be used by a malicious insider seeking access to reserved network areas (such as the payroll databases, or HR records).
The vulnerability was discovered by the research team of Duo Security, itself an SSO provider; and is described in a blog posted today. It affects many of the leading SSO providers, and probably affects the majority of proprietary company SSO developments.
Duo has confirmed the flaw in OneLogin - python-saml (CVE-2017-11427); OneLogin - ruby-saml (CVE-2017-11428); Clever - saml2-js (CVE-2017-11429); OmniAuth-SAML (CVE-2017-11430); Shibboleth (CVE-2018-0489); and Duo Network Gateway (CVE-2018-7340).
Security Assertion Markup Language (SAML) is the underlying protocol used by most SSO implementations. It is what allows authentication to be passed between a company's identity store and, for example, a third-party service. Typically, a user will log onto the identity store. This contains the credentials that will allow the same user to access other services.
SAML is used to pass authentication, via the browser, from the identity provider to the third-party service, granting access. The flaw lies in how authentication is encoded by SAML in the provider's 'response'.
The SAML authentication response contains two primary elements: the assertion and the signature. The assertion element says this NameID is authenticated. The signature element is designed to prevent the authenticated user NameID being changed at any point between the identity provider and the service being accessed. "If the attacker can modify the 'NameID' without invalidating the signature, that would be bad," suggest the Duo researchers; and then proceed to explain how it can be done.
"One of the causes of this vulnerability is a subtle and arguably unexpected behavior of XML libraries like Python’s 'lxml' or Ruby’s 'REXML'," write the blog's authors. Comments can be included in the signature, but the canonicalization process of the SAML libraries tend to drop all text after the first text node to isolate the NameID.
"So," explain the researchers, "as an attacker with access to the account 'user@user.com.evil.com', I can modify *my own* SAML assertions to change the NameID to 'user@user.com' when processed by the SP." The seven characters are <!----> inserted before .evil.com. This causes the canonicalization process to drop '.evil.com', leaving the authenticated account as 'user@user.com'.
Not all SSO implementations are vulnerable to this glitch; but Duo has demonstrated that many are. All that is required from the attacker is a genuine account that he can 'modify' to his attack target, plus the relatively minor technical savvy to intercept and edit the SAML authentication as it passes through the browser.
"Remediation of this issue," notes the report, "somewhat depends on what relationship you have with SAML." It gets a bit complicated. "Duo has released updates for the Duo Network Gateway in version? ?1.2.10?. If you use the DNG as a SAML Service Provider and are not at version 1.2.10 or higher (at the time of writing this, 1.2.10 is the latest version), we recommend upgrading."
Different affected SSOs will have different specific recommendations, and it would be best to refer to them for guidance. Similarly, there are different recommendations for maintainers of identity or service providers, maintainers of SAML processing libraries, and maintainers of XML parsing libraries. One thing that would help, suggest the authors, is the ability to enforce multi-factor authentication, "because this vulnerability would only allow a bypass of a user’s first factor of authentication." But the authors also warn, "if your IdP is responsible for both first factor and second factor authentication, it’s likely that this vulnerability bypasses both!"
Because multiple vendors are affected by this vulnerability, Duo Security worked with CERT/CC to co-ordinate disclosure. It provided the vulnerability information to CERT/CC on 18 December 2017. By 20 February 2018, all notified affected vendors had confirmed they were ready for disclosure; and Duo Security has disclosed the vulnerability details today.
Ann Arbor, Michigan-based Duo Security, a cloud-based provider of identity and access management solutions, announced a $70 million Series D funding round led by Meritech Capital Partners and Lead Edge Capital in October 2017. This brought the total amount raised to $119 million, and valued the company at $1.17 billion.
Industrial Cybersecurity Firm CyberX Raises $18 Million
27.7.2018 securityweek IT
Industrial cybersecurity startup CyberX announced today that it has raised $18 million in a Series B funding round, bringing the total amount received to date by the company to $30 million.
The latest funding round was led by Norwest Venture Partners, which also invested in FireEye and Symantec-acquired Fireglass, with participation from previous investors Glilot Capital Partners, Flint Capital, ff Venture Capital, and OurCrow.
CyberX says it plans on using the additional funding to continue its expansion in Europe and the United States, drive international growth, and expand its product development, research, and threat intelligence teams.
Founded in 2013 by military cyber experts Nir Giller and Omer Schneider, CyberX offers a platform that continuously monitors networks and collects data to help detect potentially malicious activity. The company also recently unveiled simulation technology designed to help predict breach and attack vectors.
CyberX says its product has been used by Global 2000 organizations across the energy and utilities, chemical, oil and gas, manufacturing, and other critical infrastructure sectors.
“There is a growing need in many enterprises to connect their IIoT and ICS networks to corporate IT networks for performance, monitoring, and manageability reasons. This trend creates a new security risk which requires a modern, IIoT-optimized, security solution.” said Dror Nahumi, general partner at Norwest Venture Partners. “We are extremely impressed with CyberX’s solution and its successful adoption with top-tier enterprise customers across multiple verticals.”
“We’re proud that our team has delivered a series of industry-firsts, including the first anomaly detection platform to incorporate ICS-specific threat intelligence, risk and vulnerability assessments, and automated threat modeling, as well as native integration with SOC tools,” said Giller. “By providing SOC teams with deeper visibility into Operational Technology (OT) assets, behaviors, and threats, we’re helping organizations implement a unified approach across IT and OT security and remove silos between IT and OT -- thereby improving their combined IT/OT risk posture.”
CyberX previously raised $20,000 in 2013, $2 million in 2014, and another $9 million in 2016, which, along with some add-on investments to the Series A round brought the total raised so far to $30 million. The company noted that its latest funding is the largest B round to date in industrial cybersecurity.