
Hundreds of Tim Hortons outlets across Canada closed after malware attack
2.3.2018 securityaffairs Attack
Tim Hortons restaurants across Canada have been hit by a computer malware that forced some locations to shut down over the past week.
When dealing with cyber threats for the retail sector, Target in most prominent case of potential damages from a cyber attack.
Today I want to report you the case of a malware-based attack that hit payment systems of hundreds of Tim Hortons restaurants across Canada forcing many of them to close.
“The company told the Globe and Mail that the virus hit fewer than 100 locations, attacking the Panasonic cash registers that the chain uses.” reported the Huffington Post Canada.
“But a source close to the issue told HuffPost Canada that as many as 1,000 Tim Hortons locations may have been impacted, amounting to roughly a quarter of all Canadian locations. Some locations were forced to close, while others had to shut down their drive-throughs.”
At the time of writing, there are no details about the type of malware that infected the systems at Tim Hortons restaurants, CTVNews quoting sources close to the incident reported that the malicious code was specifically designed to target cash registers making them unusable.
“The cash registers just plain don’t work,” the source told the news station “Many or the stores had to close totally.”
The Great White North Franchisee Association (GWNFA) which represents Tim Hortons franchisees is expected to take legal action against the Restaurant Brands International (RBI), the operator of Tim Hortons.
GWNFA accuses them of loss of revenue and of course reputational damage.

In a letter obtained by the Globe and the Canadian Press, Tim Hortons franchisees belonging to the Great White North Franchisee Association asked head office for compensation for losses due to the virus.
“The business interruption includes inability to use some or all of the … issued cash registers and [point-of-sale] terminals, causing partial and complete store closures, franchisees paying employees not to work, lost sales and product spoilage,” the letter from law firm Himelfarb Proszanski reportedly stated.
The letter defined the incident “a failure” and noted that it comes “on the heels of the public relations debacle” from January when two Cobourg, Ont. franchises owned by Ron Joyce Jr. and Jeri Horton-Joyce, the children of the company’s billionaire co-founders, moved to offset the province’s minimum wage hike by cutting paid breaks and forcing workers to cover a bigger share of their benefits.
According to the CTVNews, RBI has declared that no financial (i.e. data credit card information) and sensitive data was stolen by hackers.
Financial Cyberthreats in 2017
2.3.2018 Kaspersky FINANCIAL CYBERTHREATS IN 2017 Cyber
In 2017, we saw a number of changes to the world of financial threats and new actors emerging. As we have previously noted, fraud attacks in financial services have become increasingly account-centric. User data is a key enabler for large-scale fraud attacks, and frequent data breaches – among other successful attack types – have provided cybercriminals with valuable sources of personal information to use in account takeovers or false identity attacks. These account-centric attacks can result in many other losses, including those of further customer data and trust, so mitigation is as important as ever for both businesses and financial services customers.
Attacks on ATMs continued to rise in 2017, attracting the attention of many cybercriminals, with attackers targeting bank infrastructure and payment systems using sophisticated fileless malware, as well as the more rudimentary methods of taping over CCTVs and drilling holes. In 2017, Kaspersky Lab researchers uncovered, among other things, attacks on ATM systems that involved new malware, remote operations, and an ATM-targeting malware called ‘Cutlet Maker’ that was being sold openly on the DarkNet market for a few thousand dollars, along with a step-by-step user guide. Kaspersky Lab has published a report outlining possible future ATM attack scenarios targeting ATM authentication systems.
It is also worth mentioning that major cyber incidents continue to take place. In September 2017, Kaspersky Lab researchers identified a new series of targeted attacks against at least 10 financial organizations in multiple regions, including Russia, Armenia, and Malaysia. The hits were performed by a new group called Silence. While stealing funds from its victims, Silence implemented specific techniques similar to the infamous threat actor, Carbanak.
Thus, Silence joins the ranks of the most devastating and complex cyber-robbery operations like Metel, GCMAN and Carbanak/Cobalt, which have succeeded in stealing millions of dollars from financial organizations. The interesting point to note with this actor is that the criminals exploit the infrastructure of already infected financial institutions for new attacks: sending emails from real employee addresses to a new victim, along with a request to open a bank account. Using this trick, criminals make sure the recipient doesn’t suspect the infection vector.
Small and medium-sized businesses didn’t escape financial threats either. Last year Kaspersky Lab’s researchers discovered a new botnet that cashes-in on aggressive advertising, mostly in Germany and the US. Criminals infect their victims’ computers with the Magala Trojan Clicker, generating fake ad views, and making up to $350 from each machine. Small enterprises lose out most because they end up doing business with unscrupulous advertisers, without even knowing it.
Moving down one more step – from SMEs to individual users – we can say that 2017 didn’t give the latter much respite from financial threats. Kaspersky Lab researchers detected NukeBot – a new malware designed to steal the credentials of online banking customers. Earlier versions of the Trojan were known to the security industry as TinyNuke, but they lacked the features necessary to launch attacks. The latest versions however, are fully operable, and contain code to target the users of specific banks.
This report summarizes a series of Kaspersky Lab reports that between them provide an overview of how the financial threat landscape has evolved over the years. It covers the common phishing threats that users encounter, along with Windows-based and Android-based financial malware.
The key findings of the report are:
Phishing:
In 2017, the share of financial phishing increased from 47.5% to almost 54% of all phishing detections. This is an all-time high, according to Kaspersky Lab statistics for financial phishing.
More than one in four attempts to load a phishing page blocked by Kaspersky Lab products is related to banking phishing.
The share of phishing related to payment systems and online shops accounted for almost 16% and 11% respectively in 2017. This is slightly more (single percentage points) than in 2016.
The share of financial phishing encountered by Mac users nearly doubled, accounting for almost 56%.
Banking malware:
In 2017, the number of users attacked with banking Trojans was 767,072, a decrease of 30% on 2016 (1,088,900).
19% of users attacked with banking malware were corporate users.
Users in Germany, Russia, China, India, Vietnam, Brazil and the US were the most often attacked by banking malware.
Zbot is still the most widespread banking malware family (almost 33% of attacked users), but is now being challenged by the Gozi family (27.8%).
Android banking malware:
In 2017, the number of users that encountered Android banking malware decreased by almost 15% to 259,828 worldwide.
Just three banking malware families accounted for attacks on the vast majority of users (over 70%).
Russia, Australia and Turkmenistan were the countries with the highest percentage of users attacked by Android banking malware.
SecOps: The Roadkill Victim of DevOps' Need for Speed
1.3.2018 securityweek Security
DevSecOps Remains a Theory Not Often Implemented in Practice
DevOps was born from the understanding that greater efficiency comes from breaking down business silos (in this case, development and operations) and working as a single unit. With the increasing understanding and regulatory demands that security should be baked into new products during their development, the logical extension is that security should be included in a new combined working model: DevSecOps.
The potential advantages of DevSecOps are well understand and frequently urged -- but not so commonly implemented. A new survey and report (PDF) from threat detection firm Threat Stack demonstrates that DevSecOps remains a theory not often implemented in practice.
Threat Stack questioned more than 200 security, development and operations professionals working for firms ranging from SMBs to large corporations in North America, across multiple industry sectors. The response shows that DevSecOps is well-understood and frequently lauded by firms, but not so often enacted.
The primary reason appears to be not just a lack of support from the highest levels, but actual discouragement from business leaders. More than half of companies (52%) admit to cutting back on security measures to meet a business deadline or objective. "Since the directive for speed starts at the very top, it's hard to ignore;" comment the report's authors; "even if it means that security becomes roadkill in the process."
The demand for development speed from the business leaders then transfers to the existing DevOps team. Sixty-two percent of the responders said that DevOps push back against demands to deploy secure technology, and 57% push back on security best practices -- presumably because implementing security is seen as incompatible with the overriding need for speed.
This is a common perception. Mike Smart, security strategist at Forcepoint, believes security is like the brake on a car. Business leaders think its purpose is to slow down the car; that is, security slows down business and business development. "Innovators will tell you the opposite," he says. "It's there to give the driver the confidence to go as fast as possible." In this view, security is the enabler of agile business -- but the implication is that security leaders have failed to adequately explain this function to the business leaders.
Surprisingly, however, the theory of DevSecOps is well received. Eighty-five percent of the responding organizations claim that bridging the gap between DevOps and security is an important goal, while 62% of developer and operations professionals say it has become a bigger priority.
Threat Stack has isolated three key factors at play in this apparent contradiction. The first is that security is still siloed and considered a separate function. "A security specialist," notes the report, "is assigned to the operations team at only 27% of the organizations we surveyed, and security pros are on board with development teams in just 18% of cases. At 38% of organizations, security is a completely separate team that is only brought in 'when needed'."
The second is that development is separate from security. "Forty-four percent of developers aren't trained to code securely. Without this basic knowledge, coding is often done without security in mind. This forces security to become a bottleneck when they must inevitably step in and intervene."
Thirdly, operations is little different. "A full 42% of operations staff admit that they are not trained in basic security practices, which means that they can't configure servers securely. It also means that they don't see deploying security as part of the configuration management process, which allows security best practices to fall by the wayside. When ops pros aren't trained in security, there's no way SecOps can succeed."
At the same time, security cannot be absolved from all responsibility for the lack of progress in DevSecOps. Just as developers can't code securely, security teams can rarely code at all. Security teams, suggests Threat Stack, "need to learn how to code and integrate their efforts into continuous deployment cycles. Don't wait for this process to happen organically; you must make a conscious investment in alignment and education across teams."
"Businesses have grappled with the 'Speed or Security' problem for years but the emergence of SecOps practices really means that companies can achieve both," said Brian Ahern, Threat Stack chairman and CEO. "The survey findings show that the vast majority of companies are bought-in, but, unfortunately, a major gap exists between intent of practicing SecOps and the reality of their fast-growing businesses. It's important that stakeholders across every enterprise prioritize the alignment of DevOps and security."
The key to developing an efficient DevSecOps regime is to break down silos -- but that includes breaking down self-imposed as well as organizationally-imposed silos.
Boston, Mass.-based intrusion detection firm Threat Stack raised $45 million in a Series C funding in September 2017, bringing the total raised by the company to more than $70 million.
Fortinet Enhances Network Security OS, Adds AI-based Threat Detection
1.3.2018 securityweek Security
Two major new product announcements were made at Fortinet’s Accelerate 18 conference this week, including a new machine learning (ML) threat intelligence and detection offering, along with a major upgrade to the Fortinet Security Fabric (FortiOS).
Accelerate 18, held in Las Vegas, Nevada, is Fortinet's annual global partner and user conference, attended by around 2,000 Fortinet partners, customers, and industry and technical experts.
The new ML product is called FortiGuard AI. It emerges from five years of analyses by FortiGuard Labs' 215 researchers in 31 countries analyzing the threat data from a global network of more than 3 million security sensors. The analyses have been used, employing supervised learning techniques, to train the FortiGuard AI automatic detection engine.
Fortinet LogoMachine learning threat detection is currently the best option for detecting new and unknown malware. But the accuracy of machine learning detection systems depends on the volume and accuracy of the data from which it learns. By spending five years in the process, and using supervised learning (that is, under the control of human analysts), rather than unsupervised learning, the quality and accuracy of Fortinet's ML system should be high.
The system now analyzes millions of threat samples every week. More than 5 billion processing nodes identify both the clean and malicious features of the threat samples to generate threat intelligence. That intelligence then automatically updates defensive signatures across the entire Fortinet Security Fabric.
"Fortinet Labs' five-year investment in automated analysis and detection of polymorphic threats," comments CISO Phil Quade, "has resulted in FortiGuard AI, a giant leap towards [automatically detecting polymorphic and zero-day threats]. FortiGuard AI analyzes and identifies threats with speed, agility, and accuracy to provide proactive threat detection at machine speed and scale. This frees threat analysts and network operators to focus on critical threat research and higher-order problems, reduces exposure to zero-day attacks, and minimizes the risk to Fortinet customers while increasing the attacker's costs."
The firm also announced the inclusion ML-based User and Entity Behavior Analysis (UEBA) capabilities into its SIEM product (FortiSIEM). The solution 'learns' patterns of normal user or entity behavior, and will then automatically detect anomalies. Concurrent logins from separate locations, users accessing corporate data in the middle of the night, and excessive logins to rarely used servers will all send alerts to the security team for relevant action.
Fortinet has also announced version 6 of its Security Fabric. "FortiOS 6.0," says founder, president and CTO Michael Xie, "delivers hundreds of new features and capabilities that were designed to provide the broad visibility, integrated threat intelligence and automated response required for digital business."
The Security Fabric is based on the world's most deployed network security operating system. It was launched in 2016 to allow different segments of network security to integrate seamlessly and to cooperate actively under the management of a central control. FortiOS 6.0 is expected to be available before the end of March 2018.
Example enhancements include multi-cloud visibility, where cloud connectors provide visibility spanning private clouds (with support for VMware NSX, Cisco ACI and Nokia Nuage); public clouds (supporting AWS, Azure, Google Cloud and Oracle Cloud); and SaaS clouds with CASB connectors (supporting Salesforce.com, Office 365, Dropbox, Box, AWS and more).
FortiClient 6.0 includes expanded OS support for Linux, providing IoT endpoint security. Actionable insights from the IoT devices can be shared with the Security Fabric, while telemetry can provide a deeper insight on what is running on a network's endpoint devices to quickly identify vulnerabilities.
Other enhancements involve network security, advanced threat protection, email and web applications, security management and analytics, and unified access.
"Using a single partner for integrated protection across multiple threat vectors, from public cloud workloads to email SaaS applications, is a key priority for ShipServ," says Dominic Aslan, VP of IT operations at the online marketplace for the marine industry. "Fortinet is an all-in-one cyber security company with a common, intuitive security management interface across all the Fortinet Security Fabric solutions, making it much easier to support."
Russian Hackers Infiltrated German Ministries' Network: Report
1.3.2018 securityweek BigBrothers
Berlin - Russian hackers have infiltrated Germany's foreign and interior ministries' online networks, German news agency DPA reported Wednesday quoting unnamed security sources.
The hacker group known as APT28 -- which has been linked to Russia's GRU military intelligence and accused of attacks on Hillary Clinton's 2016 presidential campaign -- managed to plant malware in the ministries' networks for possibly as long as a year, the news agency said.
German security authorities only detected the online spying in December, it said, adding that an isolated government IT network had also been hit.
If confirmed, the attack would be the biggest to hit the German government.
Top security officials had repeatedly warned during Germany's 2017 general elections that Russia hackers may seek to disrupt the polls.
While authorities did not have concrete proof, they have pinned the malware attack that crippled the Bundestag parliamentary network in 2015 for days on the APT28, also known as "Fancy Bear" or "Sofacy".
The attack netted 17 gigabytes of data which, officials feared, could be used to blackmail MPs or discredit them.
Amid the rising frequency of attacks, Germany's defence ministry in 2016 set up a cyber department to coordinate a response to online intrusions.
"RedDrop" Mobile Malware Records Ambient Audio
1.3.2018 securityweek Android
A newly detailed mobile malware can do more than steal data from infected devices: it can also record ambient audio and send the recordings to cloud storage accounts controlled by attackers.
Dubbed RedDrop, the malware can also inflict financial costs on victims by sending SMS messages to premium services, security firm Wandera says. The U.K.-based company has discovered 53 malware-ridden apps that are exfiltrating sensitive data from infected devices.
RedDrop-infected applications are being distributed through a network of more than 4,000 domains and range from tools such as image editors and calculators to recreational apps. Every observed application offers the expected functionality, thus hiding the malicious content stored within.
Once the user installs an application from the RedDrop family, invasive permissions are requested, so that the next steps of the attack would be performed without additional user interaction, the security researchers reveal. The malware even asks for permissions that allow it to persist between reboots and to continuously communicate with its command and control (C&C) servers.
To lure victims to their malicious network, the attackers even display ads on the popular Chinese search engine Baidu. One such ad would take the user to huxiawang.cn, the primary distribution site for the attack, which encourages users to download one of the 53 malicious apps.
Once the user installs a RedDrop-infected application, 7 additional APKs are silently downloaded and executed on the device, each meant to enable additional malicious functionality. The downloaded components are stored dynamically into the device’s memory.
One of the observed applications (CuteActress) was designed to send an SMS message to a premium service each time the user would touch the screen to interact with the app’s legitimate functionality. The threat would also delete all of these messages, thus erasing any evidence of these premium SMS.
The RedDrop malware family also includes a set of spyware tools capable of extracting valuable and damaging data from the victim’s device. The Wandera researchers associated encrypted and unencrypted data, encoded data and TCP streams to RedDrop’s exfiltration activities.
Stolen data includes locally saved files (such as photos and contacts), device-related information (IMEI, IMSI, etc), SIM info (MNC, MCC, etc), application data, and information on nearby Wi-Fi networks. More disturbing is the fact that RedDrop can also record an audio of device’s surroundings.
According to Wandera, RedDrop is one of the most sophisticated Android malware families, given the range of functioning malicious applications it hides behind and its complex distribution network. The malware is expected to remain active even after the applications are flagged as malicious, and new variants are expected to emerge in the coming months.
“This multifaceted hybrid attack is entirely unique. The malicious actor cleverly uses a seemingly helpful app to front an incredibly complex operation with malicious intent. This is one of the more persistent malware variants we’ve seen,” Dr Michael Covington, VP of Product Strategy at Wandera, says.
According to Craig Young, computer security researcher for Tripwire, this is not the first time Android malware that includes such extensive spyware capabilities has been discovered and the research appears exaggerated.
“This looks more like a very amateur trial run of Android malware rather than “one of the most sophisticated pieces of Android malware” as claimed by Wandera,” Young told SecurityWeek in an emailed comment.
He also pointed out that the malware’s ability to record and upload calls “provides minimal value outside of targeted attacks and potentially makes the malware more apparent by draining a victim’s battery quickly.”
Young recommends paying extra attention to the permissions applications may request, as this is a great means to stay safe from infections.
“With Android 6 (released 2015), apps will request permissions at runtime which should make it abundantly obvious when a malicious app wants to do something like sending SMS or recording audio. Users of older Android releases must rely instead on reviewing the requested permissions at install time to confirm that they are appropriate for the app,” Young concluded.
Five Threat Groups Target Industrial Systems: Dragos
1.3.2018 securityweek ICS
There are at least five sophisticated threat groups whose activities focus on industrial control systems (ICS), according to a report published on Thursday by industrial cybersecurity firm Dragos.
While it’s not uncommon for non-targeted malware to make its way onto industrial systems, targeted attacks have also become increasingly common. Dragos currently tracks five threat actors that have either attacked ICS directly or have shown an interest in gathering information on these types of systems.
One of these groups is tracked by the security firm as Electrum. This is the actor behind the CRASHOVERRIDE/Industroyer malware used in December 2016 to cause a power outage in Ukraine. Electrum has been linked to Sandworm Team, which is believed to be responsible for a 2015 power outage in Ukraine. Russia has been accused for both attacks.
While it apparently hasn’t launched any major attacks since the 2016 campaign targeting Ukraine’s energy sector, Dragos says Electrum continues to be active, and evidence suggests it has expanded targets.Five threat groups target ICS
“While past ELECTRUM activity has focused exclusively on Ukraine, information from low- level ongoing events and the group’s link to SANDWORM Dragos assesses that ELECTRUM could be ‘re-tasked’ to other areas depending on the focus of their sponsor,” Dragos said in its report.
Another gang tracked by Dragos is Covellite, which has been linked to North Korea’s Lazarus group. Researchers started observing Covellite in September 2017, when it launched a highly targeted phishing campaign against a U.S. electric grid company. They later spotted attacks that may have been conducted by this group aimed at organizations in Europe, North America and East Asia.
Unlike Electrum, Covellite has yet to use malware specifically designed to target industrial systems in its campaigns.
Dragos’ report also summarizes the activities of Dymalloy, a group whose attacks came to light during an investigation into Dragonfly, an actor that is also known as Crouching Yeti and Energetic Bear. Dragonfly, which is believed to be operating out of Russia, is known for its sophisticated Havex malware, and it was recently observed targeting control systems in U.S. energy firms.
Dragos believes Dymalloy is not linked – at least not directly – to Dragonfly and its tools are not as advanced as Havex. However, the hackers did manage to breach ICS organizations in Turkey, Europe and North America, gaining access to HMI devices.
Experts say Dymalloy appears to have become less active since early 2017, possibly in response to attention from the media and security researchers.
Since mid-2017, Dragos has been tracking a group it has named Chrysene, whose activity focuses on North America, Western Europe, Israel and Iraq, particularly organizations in the electricity generation and oil&gas sectors.
Chrysene, which continues to be active, has used a unique variation of a framework associated with the Iran-linked cyber espionage groups known as OilRig and Greenbug.
“While CHRYSENE’s malware features notable enhancements over related threat groups using similar tools, Dragos has not yet observed an ICS-specific capability employed by this activity group. Instead, all activity thus far appears to focus on IT penetration and espionage, with all targets being ICS-related organizations,” Dragos said.
It’s worth noting that the recently uncovered piece of malware known as Trisis/Triton, which is the first threat specifically designed to disrupt safety instrumented systems (SIS), has also been linked by some researchers to Iran.
The last ICS-focused threat group monitored by Dragos is Magnallium, which has also been linked to Iran. The security firm started tracking this actor following a report from FireEye on the activities of APT33.
While some media reports portrayed APT33 as a serious threat to ICS and critical infrastructure, Dragos’ investigation showed that the group does not appear to possess any ICS-specific capabilities.
“While only one [of these groups] has demonstrated an apparent capability to impact ICS networks through ICS-specific malware directly, all have engaged in at least reconnaissance and intelligence gathering surrounding the ICS environment,” Dragos said.
“These groups have remained relatively constant regarding overall activity throughout the year, and Dragos is confident that additional unknown events have occurred,” the company added.
Public Advisories Fail to Convey True Impact of ICS Flaws
1.3.2018 securityweek ICS
Public advisories describing vulnerabilities in industrial control systems (ICS) often fail to convey the true impact of the flaws, according to a report published today by ICS cybersecurity firm Dragos.
An analysis of 163 advisories published last year by ICS-CERT and others – excluding reports on medical device flaws, which ICS-CERT regularly covers – allowed Dragos to compile some useful statistics.
The company determined that patches for nearly two-thirds of the security holes disclosed last year don’t fully eliminate the risk due to the fact that the affected systems had been insecure by design.
Another interesting point made by Dragos in its report is that 85% of the vulnerabilities can be exploited late in the kill chain and they are not useful for getting an initial foothold in the targeted organization’s network. This means that an attacker who manages to exploit the flaws has had access to the target’s network for some time.
Once exploited, one-third of the vulnerabilities lead to what Dragos describes as “loss of view,” which results in the victim not being able to monitor or read the state of the compromised system.
In 29% of cases, exploitation of the bugs leads to “loss of control,” preventing any modifications to the state of the system. In roughly the same percentage of cases, exploitation of a flaw leads to both loss of control and loss of view.
“Vulnerabilities which lead to both a loss of view and control occur in the core of traditional control networks affecting both field devices (PLCs, RTUs, etc.) as well as management such as human-machine interface (HMI) systems and engineering workstation (EWS) software,” Dragos explained in its report. “This means that a large percentage (61%) of ICS-related vulnerabilities will cause severe operational impact if exploited.”
Learn More at SecurityWeek’s ICS Cyber Security Conference
Many of the flaws covered by the advisories analyzed by Dragos affect products that are further away from the perimeter of the operational technology (OT) network, which makes them less likely to be exploited.
However, 15% of advisories describe vulnerabilities in components located very close to the network perimeter. Systems such as historians, OPC servers, firewalls, VPN products, and cellular gateways are often directly accessible from the business network and even from the Internet, which makes them more likely to be attacked.
Nearly one-quarter of the weaknesses impact field devices, while 31% affect HMIs.
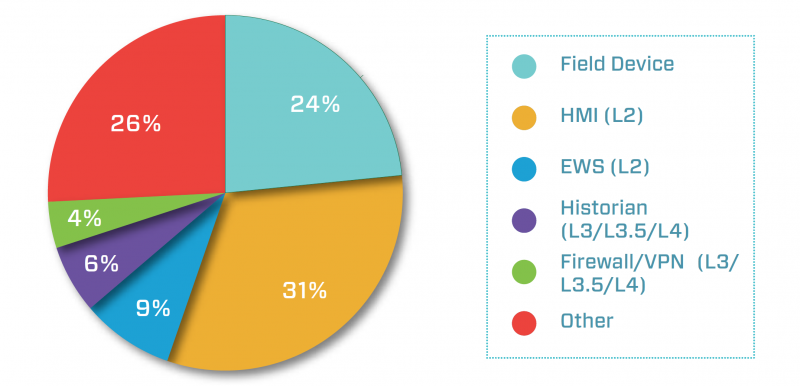
“Most of the control system vulnerability patching focus should be placed on the 30% of vulnerabilities which impact exterior-facing systems,” Dragos said. “Since so many assets and interior control elements are nowhere near a network border, applying patches in the 85% of interior and none-to-medium proximity cases would likely have little to no reduction in risk for impact against attack.”
Dragos also busted a common myth claiming that most ICS vulnerabilities are found in demo or free software rather than actual control systems. However, the company found that 63% of all ICS-related flaws disclosed last year impacted software or hardware that could not have been obtained for free.
The security firm’s analysis also revealed that 72% of public advisories describing ICS flaws did not provide any alternative mitigations. According to Dragos, recommending the use of VPNs and trusted networks, which is included in most advisories, does not count as alternative mitigations.
RedDrop, a new Android Malware records ambient Audio and exfiltrate user’s data
1.3.2018 securityaffairs Android
RedDrop malware is a recently discovered mobile threat that can steal data from infected devices and also record ambient audio.
Security researchers at Wandera have spotted a new sophisticated family of mobile malware dubbed RedDrop that can steal data, record audio, and intercept SMS. All data stolen from infected systems is uploaded to remote file storage systems.
The malicious code was found in dozens of apparently innocuous apps, the researchers discovered RedDrop hidden in 53 Android applications, including image editors, calculators, language learning apps and space exploration apps.
The applications work as expected and the RedDrop malware is executed in the background.
“The latest zero-day threat to be discovered by Wandera’s mobile threat research team is RedDrop, a family of mobile malware inflicting financial cost and critical data loss on infected devices.” reads the analysis published by Wandera. “The most worrying part? The 53 malware-ridden apps are exfiltrating sensitive data – including ambient audio recordings – and dumping it in the attackers’ Dropbox accounts to prepare for further attacks and extortion purposes.”
Once an infected app is installed, it downloads at least seven more Android Application Packages (APKs) from a different command and control server, each of them implements a malicious functionality. The APKs are stored in the memory of the device, this trick allows to execute them without including the feature in the original malware sample.
The RedDrop malware could also send SMS message to a premium service and then instantly deletes the message to avoid detection by the user.
The researchers discovered that the malicious Apps are distributed from a complex network composed of more than 4,000 domains registered to the same underground group that might be operating out of China.
“Wandera’s machine learning detections first uncovered one of the RedDrop apps when a user clicked on an ad displaying on popular Chinese search engine Baidu.” continues the analysis. “The user was then taken to huxiawang.cn, the primary distribution site for the attack. The landing pages that follow host various content to encourage and incite the user to download one of the 53 apps within the RedDrop family of malicious apps.”
One of the applications observed by the researchers (CuteActress) was designed to send an SMS message to a premium service every time the user would use a functionality of the app. The threat would also delete all of these messages, thus erasing any evidence of these premium SMS.

Currently, most of the infections were observed are in China, followed by Europe and America.
Android users that download apps from third-party sources and websites are most exposed to this threat, no instance of the RedDrop malware have been yet found on the Google Play store neither other official stores.
Hundreds of sites based on WordPress, Joomla and CodeIgniter infected by ionCube Malware
1.3.2018 securityaffairs Virus
Security researchers at the firm SiteLock have discovered that hundreds of websites have been infected with the ionCube malware.
Security researchers at SiteLock have discovered that hundreds of websites have been infected with malware that masquerades as legitimate ionCube-encoded files.
ionCube is an encoding technology used to protect PHP software from being viewed, changed, and run on unlicensed computers.
The experts were analyzing an infected WordPress website when discovered a number of suspicious obfuscated files – such as “diff98.php” and “wrgcduzk.php” – appearing almost identical to legitimate ionCube-encoded files. Further analysis conducted revealed that hundreds of websites were infected by the same ionCube Malware.
“While reviewing an infected site, the SiteLock Research team found a number of suspiciously named, obfuscated files that appear almost identical to legitimate ionCube-encoded files. We determined the suspicious ionCube files were malicious, and found that hundreds of sites and thousands of files were affected.” reads the analysis published by SiteLock.
“Overall, our investigation found over 700 infected sites, totalling over 7,000 infected files.”
Further analysis revealed that attackers also compromised Joomla and CodeIgniter websites. Threat actors packed their malware in a manner that appears ionCube-encoded files.
The malicious code could theoretically infect any website based on a web server running PHP, once decoded, the fake ionCube files compose the ionCube malware.
“While there’s still some degree of obfuscation, the presence of the $_POST and $_COOKIE superglobals and the eval request at the end of the file reveal its true purpose: to accept and execute remotely supplied code.” continues the analysis. “It looks like the remote code supplied to this file is further obfuscated and there may be some sort of access control implemented, judging by the GUID-formatted string present.”

The researchers also provided recommendations to mitigate the ionCube Malware, they suggest administrators check the presence of ionCube-encoded files as an indicator of compromise.
If an infection is detected, the scanning of the entire site is recommended, to completely eliminate the threat, the researchers also suggest the adoption of a web application firewall (WAF).
“If you find indicators of this infection, we strongly recommend having your site scanned for malware as soon as possible, as this malware seldom appears on its own.” concluded the analysis.
“This is especially important if you are using an ionCube-encoded application, as manually differentiating the malicious files from the legitimate ones is difficult, and it is common to see up to 100 slightly different variants of this malware on a single site. “