
European Commission requests IT firms to remove ‘Terror Content’ within an hour
2.3.2018 securityaffairs Cyber
The UE issued new recommendations to tackle illegal content online, it asked internet companies to promptly remove terror content from their platforms within an hour from notification.
On Thursday, the UE issued new recommendations to internet companies to promptly remove “harmful content,” including terror content, from their platforms.
“As a follow-up, the Commission is today recommending a set of operational measures accompanied by the necessary safeguards – to be taken by companies and Member States to further step up this work before it determines whether it will be necessary to propose legislation.” reads the fact sheet published by the European Commission.
“These recommendations apply to all forms of illegal content ranging from terrorist content, incitement to hatred and violence, child sexual abuse material, counterfeit products and copyright infringement.”
It is a call to action for the tech firms and social media giants to take down “terrorist content” within an hour of it being reported, the recommendation is directed to major services including YouTube, Facebook, and Twitter.
These platforms are daily abused by terrorist organizations like Islamic State group, the EU’s recommendations follow the demands of the nations participant at the 2017 G7 Summit held in Taormina, Italy, that urged action from internet service providers and social media giants against extremist content online.

The European Commission is teaming up with a group of US internet giants to adopt additional measures to fight web extremism, but at the same time, it warned it would adopt consider legislation if the Internet firms will not follow the recommendations.
“While several platforms have been removing more illegal content than ever before — showing that self-regulation can work — we still need to react faster against terrorist propaganda and other illegal content,” said the commission’s vice-president for the Digital Single Market Andrus Ansip.
“This content remains “a serious threat to our citizens’ security, safety, and fundamental rights,”

Andrus Ansip
✔
@Ansip_EU
What is illegal offline is also illegal online. Limited liability system under EU's #eCommerce law already works well – it should stay in place. My statement at press conference on fighting illegal content online: http://bit.ly/2oJGgTw
1:07 PM - Mar 1, 2018
11
See Andrus Ansip's other Tweets
Twitter Ads info and privacy
The European Commission recognized the results achieved by internet firms in combatting illegal content, but the adversaries are very active and there is still a lot of work to do.
“significant scope for more effective action, particularly on the most urgent issue of terrorist content, which presents serious security risks”.
The European Commission pretends that terrorist content should be taken down within one hour of being reported by the authorities, it also urges more strictly monitoring and proactive actions against the illegal content.
The EU suggests the adoption of automated detection systems that could support tech firms to rapidly identify harmful content and any attempt to re-upload removed illegal content.
The new recommendations specifically address also other types of harmful illegal content such as hate speech and images of child sexual abuse.
“Illegal content means any information which is not in compliance with EU law or the law of a Member State. This includes terrorist content, child sexual abuse material (Directive on combating sexual abuse of children), illegal hate speech (Framework
Decision on combating certain forms and expressions of racism and xenophobia by means of criminal law), commercial scams and frauds (such as Unfair commercial practices directive or Consumer rights directive) or breaches of intellectual property rights (such as Directive on the harmonisation of certain aspects of copyright and related rights in the information society).” continues the EC.
“Terrorist content is any material which amounts to terrorist offences under the EU Directive on combating terrorism or under national laws — including material produced by, or attributable to, EU or UN listed terrorist organisations.”
According to the commission, internet firms removed 70 percent of illegal content notified to them in the preceding few months.
Apple Moves iCloud Data and Encryption Keys for Chinese Users to China
2.3.2018 thehackernews Apple
Apple has finally agreed to open a new Chinese data center next month to comply with the country's latest controversial data protection law.
Apple will now move the cryptographic keys of its Chinese iCloud users in data centers run by a state-owned company called Cloud Big Data Industrial Development Co, despite concerns from human rights activists.
In 2017, China passed a Cybersecurity Law that requires "critical information infrastructure operators" to store Chinese users' data within the country's borders, which likely forced Apple to partner with the new Chinese data center.
And the icing on the cake is that Chinese government already has legislation called National Security Law, passed in 2015, which gives police the authority to demand companies help them bypass encryption or other security tools to access personal data.
This is the first time when Apple is going to store encryption keys required to unlock iCloud accounts of its users outside the United States.
In theory, Chinese law enforcement agencies won't have to ask US courts for compelling Apple to give them access to the Chinese users’ data.
Instead, they'll simply use their legal system to demand access to cryptographic keys required to unlock iCloud accounts stored within their nation, making it far easier to access users’ data, such as messages, emails, and photos.
However, Apple has said the company alone would have access to the iCloud encryption keys and that Chinese authorities will have no backdoor into its data troves.
Apple said the company had not given any of its customers account information to Chinese authorities despite receiving 176 requests from 2013 to 2017, Reuters reported, though all requests were made before the new cybersecurity laws took effect.
If Apple thinks it would comply with one law, i.e., storing users data in China, but could stand without complying with other stringent Chinese regulations, then the company should reconsider its decision.
The company has severely been implementing various aspects of Chinese laws in recent months for its regional operations in the most populated country.
Last year, Apple controversially removed VPN apps from its official App Store in China to comply with Chinese cyberspace regulations, making it harder for internet users to bypass its Great Firewall.
Earlier last year, Apple removed the New York Times (NYT) app from its Chinese App Store because the app was in "violation of local regulations."
A Simple Bug Revealed Admins of Facebook Pages — Find Out How
2.3.2018 thehackernews Social
Facebook Page admins are publicly displayed only if admins have chosen to feature their profiles.
However, there are some situations where you might want to contact a Facebook page admin or want to find out who is the owner of a Facebook page.
Egyptian security researcher Mohamed A. Baset has discovered a severe information disclosure vulnerability in Facebook that could have allowed anyone to expose Facebook page administrator profiles, which is otherwise not supposed to be public information.
Baset claimed to have discovered the vulnerability in less than 3 minutes without any kind of testing or proof of concepts, or any other type of time-consuming processes.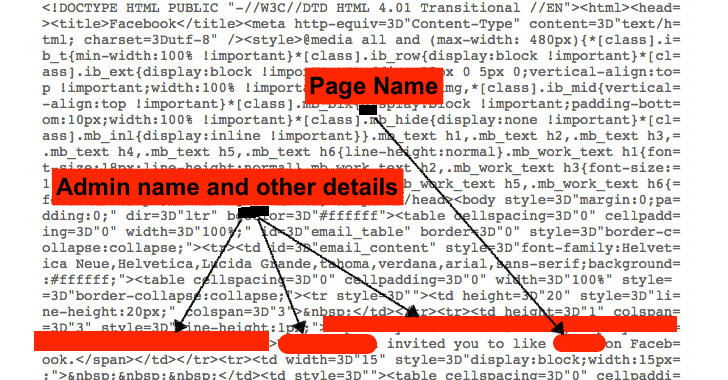
In a blog post, Baset said he found the vulnerability, which he described as a "logical error," after receiving an invitation to like a particular Facebook page on which he had previously liked a post.
Facebook has introduced a feature for page admins wherein they can send Facebook invitations to users asking them if they wished to like their page after liking a post, and a few days later, these interacted users may receive an email reminding them of the invitation.
After Baset received one such email invite, he simply opened "show original" drop-down menu option in email. Looking at the email's source code, he noticed that it included the page administrator's name, admin ID and other details.
The researcher then immediately reported the issue to the Facebook Security Team through its Bugcrowd bug bounty program. The company acknowledged the bug and awarded Baset $2,500 for his findings.
Though Facebook has now patched this information disclosure issue, people who have already received one such page invitation can still find out admin details from the invitation emails.
"We were able to verify that under some circumstances page invitations sent to non-friends would inadvertently reveal the name of the page admin which sent them," Facebook said. "We've address the root cause here, and future emails will not contain that information."
Facebook has now patched this information disclosure issue.
Bugcrowd Raises $26 Million to Expand Vulnerability Hunting Business
2.3.2018 securityweek Vulnerebility
Crowdsourced security testing company Bugcrowd announced today that it has closed $26 million in a Series C funding round led by Triangle Peak Partners.
The new funding brings the total amount raised by the company to $50 million, including $15 million raised in a Series B funding round in 2016.
The company’s flagship “Crowdcontrol” offering is software-as-a-service platform that allows organizations run their own customized bug bounty programs to uncover and resolve security vulnerabilities in their products.
The new funding will be used to support product innovation and program management, the company said.
Bugcrowd currently operates the rewards programs of more than 70 different companiesnincluding security firms BitDefender, Centrify, NETGEAR, 1Password, Okta, Cylance, LastPass. Industry customers include MasterClass, Fiat Chrysler, Square, Fitbit, Mastercard, Tesla and Western Union. A recently announced Samsung Electronics' Mobile Security program rewards security researchers up to $200,000 per vulnerability, depending on its severity.
Existing investors Blackbird Ventures, Costanoa Ventures, Industry Ventures, Paladin Capital Group, Rally Ventures, Salesforce Ventures and Stanford participated in the Series C round, along with new investors Hostplus and First State Super.
Remotely Exploitable Flaws Patched in DHCP
2.3.2018 securityweek Vulnerebility
Updates released by the Internet Systems Consortium (ISC) for the Dynamic Host Configuration Protocol (DHCP) software patch two remotely exploitable vulnerabilities discovered by a researcher at Google.
Felix Wilhelm of the Google Security Team found that the DHCP Client (dhclient), which provides a means for configuring network interfaces, is affected by a buffer overflow vulnerability that allows a malicious server to cause the client to crash.
In some cases, exploitation of the flaw could also lead to remote code execution, ISC said in an advisory. The security hole is tracked as CVE-2018-5732 and rated high severity.
“Where they are present, operating system mitigation strategies such as address space layout randomization (ASLR) should make it difficult to leverage this vulnerability to achieve remote code execution but we can not rule it out as impossible. The safest course is to patch dhclient so that the buffer overflow cannot occur,” ISC said.
The second vulnerability, CVE-2018-5733, is a medium severity issue that can be exploited to exhaust the memory available to the DHCP daemon (dhcpd), resulting in a denial-of-service (DoS) condition to clients.
“A malicious client which is allowed to send very large amounts of traffic (billions of packets) to a DHCP server can eventually overflow a 32-bit reference counter, potentially causing dhcpd to crash,” ISC said.
The flaws affect DHCP versions 4.1.0 through 4.1-ESV-R15, 4.2.0 through 4.2.8, 4.3.0 through 4.3.6, and 4.4.0. Fixes are included in versions 4.1-ESV-R15-P1, 4.3.6-P1 and 4.4.1.
ISC said there was no evidence that the vulnerabilities had been exploited for malicious purposes.
The organization has also informed customers of a vulnerability affecting BIND Supported Preview Edition, which is a customer-only, non-public version of BIND. The flaw, tracked as CVE-2018-5734 and rated high severity, can lead to an assertion failure, which typically causes the software to crash.
23,000 Digital Certificates Revoked in DigiCert-Trustico Spat
2.3.2018 securityweek Security
Digicert vs Trustico
Certificate Authority (CA) DigiCert on Wednesday announced the en-masse revocation of more than 23,000 HTTPS certificates after certificate reseller Trustico sent over the private keys for those certificates.
The keys are supposed to be secret and only in the possession of certificate owners, not in the hands of the certificate authority, the reseller or any other third party. With the private keys exposed, DigiCert was forced to revoke impacted certificates within 24 hours, thus affecting a large number of customers.
The revocation appears to be the result of a one-month feud between Trustico and DigiCert and might evolve into an even larger number of certificates being axed.
This all apparently started on February 2, 2018, when Trustico sent a request to DigiCert “to mass revoke all certificates that had been ordered by end users through Trustico,” Jeremy Rowley, Executive VP of Product at DigiCert, explains. The CA refused, given the large number of certificates it was asked to revoke at once (50,000).
In August last year, DigiCert announced plans to buy Symantec’s website security and related public key infrastructure (PKI) solutions, after Symantec ended up in the crosshairs for wrongfully issuing TLS certificates on several occasions. Since December 1, 2017, Symantec SSL certificates have been issued by DigiCert.
With major browsers already announcing plans to distrust older Symantec certificates, Trustico too decided to abandon those certificates, and announced in mid-February that it would cease to offer Symantec branded SSL Certificates: Symantec, GeoTrust, Thawte and RapidSSL.
“As a valued partner of Comodo, Trustico have updated their systems to minimize disruption to customers with their API and ordering processes by enabling the automatic selection and ordering of equivalent products from the Comodo range,” Trustico said at the time.
A couple of weeks later, on February 27, Trustico sent DigiCert a file with 23,000 private keys matching certificates issued to reseller’s customers, which triggered a 24-hour revocation process.
“Trustico’s CEO indicated that Trustico held the private keys for those certificates, and then emailed us approximately 20,000 certificate private keys. When he sent us those keys, his action gave us no choice but to act in accordance with the CA/Browser Forum Baseline Requirements, which mandate that we revoke a compromised certificate within 24 hours,” DigiCert said in a Wednesday statement.
Because of these actions, starting today, visitors of impacted websites will see in their browsers that the connection to the domain is untrusted, unless the revoked certificates have been replaced in the meantime.
Since the beginning of February, DigiCert and Trustico have been communicating with each other over this, but each company has a different side of the story.
According to DigiCert, Trustico informed them that the certificates had been compromised and that it was in the possession of said private keys. Thus, DigiCert requested proof of compromise and received said keys.
“At this time, Trustico has not provided any information about how these certificates were compromised or how they acquired the private keys. As is standard practice for a Certificate Authority, DigiCert never had possession of these private keys,” Rowley says.
In addition to revoking the certificates, DigiCert decided to email all impacted customers to inform them on its action: “Following our standard revocation process, we gave notice via email to each certificate holder whose private keys had been exposed to us by Trustico, so they could have time to get a replacement certificate.”
Trustico, on the other hand, claims that it never said the certificates had been compromised, but that it informed DigiCert that it believed “Symantec to have operated our account in a manner whereby it had been compromised.”
The reseller also says that it doesn’t believe it to be “ideal to have any active SSL Certificates on the Symantec systems,” especially with Chrome set to distrust of all Symantec SSL certificates.
“The same management team responsible for that situation is duly employed at DigiCert and are fully managing our account, causing grave concern on our part as it appears to be business as usual with a new name. We were also a victim whereby Symantec mis-issued SSL Certificates owned by us, subsequently we were asked to keep the matter quiet, under a confidentially notice,” the company claims.
Moreover, Trustico points out that it never authorized DigiCert to email its customers about the revocation, but adds that it too sent a notice to the impacted clients.
The bottom line here, however, is the fact that DigiCert ended up revoking 23,000 HTTPS certificates because their private keys were compromised. Even if the keys hadn’t been compromised when the spat started, the fact that the reseller sent those keys in an email represented a compromise in itself.
“In communications today, Trustico has suggested that this revocation is due to the upcoming Google Chrome distrust of Symantec roots. That is incorrect. We want to make it clear that the certificates needed to be revoked because Trustico sent us the private keys; this has nothing to do with future potential distrust dates,” DigiCert points out.
The fact that Trustico kept those private keys on their platform is also worrisome.
Both Trustico and DigiCert said they would be working with the impacted customers to replace the axed certificates and that free replacement certificates are available for those clients.
Russia-linked Hackers Directly Targeting Diplomats: Report
2.3.2018 securityweek APT
The Russia-linked cyber espionage group Sofacy has been targeting foreign affairs agencies and ministries worldwide in a recently discovered campaign, Palo Alto Networks warns.
The hacking group, also known as APT28, Fancy Bear, Pawn Storm, Sednit, Tsar Team, and Strontium, has been highly active recently, and new evidence shows activity directly targeting diplomats in North America and Europe, including those at a European embassy in Moscow.
Sofacy was supposedly behind the attacks on the 2016 United States presidential election, but also hit Ukraine and NATO countries. In fact, the group heavily targeted NATO in early 2017, when it even used zero-day exploits, but then started to shift its focus towards the Middle East and Central Asia.
Palo Alto Networks has now uncovered two parallel efforts within a new Sofacy campaign, each using its own set of tools for attacks. One of the efforts was observed in the beginning of February 2018 to use phishing emails as the attack vector, to target an organization in Europe and another in North America.
The message spoofed the sender address of Jane’s by IHSMarkit, a well-known supplier of information and analysis. The email carried an attachment claiming to be a calendar of events relevant to the targeted organizations, but was a Microsoft Excel spreadsheet containing a malicious macro script.
The attackers used a white font color to hide the content of the document to the victim and lure them into enabling macros. Once that happens, the script changes the text color to black.
The macro also retrieves content from several cells to obtain a base64 encoded payload, writes it to a text file in the ProgramData folder, and leverages the command certutil -decode to decode the contents to an .exe file, which it runs after two seconds.
The executable is a loader Trojan that decrypts an embedded payload (DLL) and saves it to a file. Next, it creates a batch file to run the DLL payload, and writes the path to the batch file to a registry key, for persistence.
The installed malware is a variant of SofacyCarberp, which has been extensively used by the threat group in attacks. The malware performs initial reconnaissance by gathering system information, then sends the data to the command and control (C&C) server and fetches additional tools.
Both the loader and the SofacyCarberp variant used in the attack are similar to samples previously analyzed, yet they include several differences, such as a new hashing algorithm to resolve API functions and find browser processes for injection, and modified C&C communication mechanisms.
The security researchers also believe the group may have used the Luckystrike open-source tool to generate the malicious document and/or the macro, as the macro in the document closely resembles those found within the Microsoft PowerShell-based tool. The only difference between the two, besides random function name and random cell values, would be the path to the “.txt” and “.exe” files.
The security researchers also noticed that the Sofacy group registered new domains as part of the campaign, but that it used a default landing page they employed in other attacks as well. The domain used in this attack, cdnverify[.]net was registered on January 30, 2018.
“No other parts of the C&C infrastructure amongst these domains contained any overlapping artifacts. Instead, the actual content within the body of the websites was an exact match in each instance,” Palo Alto notes.
“The Sofacy group should no longer be an unfamiliar threat at this stage. They have been well documented and well researched with much of their attack methodologies exposed. They continue to be persistent in their attack campaigns and continue to use similar tooling as in the past. This leads us to believe that their attack attempts are likely still succeeding, even with the wealth of threat intelligence available in the public domain,” Palo Alto concludes.