Delta Patches Vulnerabilities in HMI, PLC Products
3.3.2018 securityweek Vulnerebility
Taiwan-based Delta Electronics has patched several vulnerabilities in two of the company’s industrial automation products, including flaws that can be exploited for remote code execution.
A researcher who uses the online moniker “Axt” informed Delta via Trend Micro’s Zero Day Initiative (ZDI) and ICS-CERT that its WPLSoft product, a programming software for programmable logic controllers (PLCs), is affected by several types of vulnerabilities.
ICS-CERT’s advisory describes three types of flaws that can allow arbitrary code execution in the context of the current process or denial-of-service (DoS) attacks, specifically stack-based buffer overflow, heap-based buffer overflow, and out-of-bounds write issues. The security holes have been rated high severity and they are tracked as CVE-2018-7494, CVE-2018-7507 and CVE-2018-7509.
ZDI has published a total of nine advisories, one for each variation of these flaws. According to the company, the vulnerabilities are related to how the application parses .dvp files and they can be exploited by getting the targeted user to open a specially crafted file or webpage.
ZDI said it reported the security holes to Delta via ICS-CERT in February 2017. The company’s advisories suggest that the vendor attempted to release some patches last summer, but they did not properly fix the vulnerabilities. ZDI published its advisories in August 2017 with a “0Day” status.
ICS-CERT reported this week that the vulnerabilities were patched by Delta with the release of WPLSoft V2.46.0, which according to the vendor’s site was made available on February 2.
A separate advisory published this week by ICS-CERT describes a medium severity vulnerability found by researcher Ghirmay Desta in Delta’s DOPSoft human-machine interface (HMI) product.
The flaw, a stack-based buffer overflow, is related to the processing of .dop or .dpb files, and it can allow remote code execution. The issue affects DOPSoft 4.00.01 and prior, and it was patched with the release of version 4.00.04 on March 1.
This vulnerability was also reported to Delta via ZDI, but the company has yet to publish advisories. ZDI’s website shows a total of 17 upcoming advisories describing vulnerabilities found by Desta in the DOPSoft product in October 2017. Last year, the expert also found weaknesses in Delta’s PMSoft, a development tool for motion controllers.
ZDI was also recently informed by an anonymous researcher of four high severity flaws in an unnamed Delta product.
It’s not uncommon for ICS vendors to take hundreds of days to patch vulnerabilities. A report published last year by ZDI showed that the average patching time for SCADA flaws had been 150 days.
New Malware Used in Attacks Aimed at Inter-Korean Affairs
3.3.2018 securityweek Virus
A threat actor apparently interested in inter-Korean affairs continues to launch highly targeted attacks using new pieces of malware and decoy documents referencing North Korean political topics.
The cyber espionage group, which experts believe is sponsored by a nation state, has been active for several years, but it managed to stay under the radar until last year, when researchers analyzed two of its main tools, namely SYSCON and KONNI. These pieces of malware had been leveraged in attacks aimed at organizations linked to North Korea.
McAfee’s Advanced Threat Research team recently spotted a new campaign that appears to focus on North Korea, particularly humanitarian aid efforts. The security firm named this operation Honeybee based on the name of the user who created the malicious documents.
Previous research into this group’s activities and a new McAfee report claim the threat actor is likely a Korean speaker. In the past, some even suggested that the attacks may have been launched from South Korea.
However, McAfee told SecurityWeek that South Korea is most likely not behind the attacks. The security firm believes this is the work of an actor interested in inter-Korean affairs, specifically in English-language information.
The attack starts with a spear-phishing email carrying or linking to a malicious document. The document contains a macro designed to drop and execute a new version of the SYSCON backdoor. The malware allows attackers to upload files to a server, and download files to the compromised system and execute them.
The campaign appears to be mainly focused on North Korea, particularly humanitarian aid efforts, with primary targets located in Southeast Asia and the Americas. While many of the targeted entities are located in South Korea, some attacks are also aimed at users in Vietnam, Singapore, Japan, Indonesia, Canada and Argentina.
Some of the malicious documents used to deliver the malware reference North Korea – for example, one is named “International Federation of Red Cross and Red Crescent Societies – DPRK Country Office.”
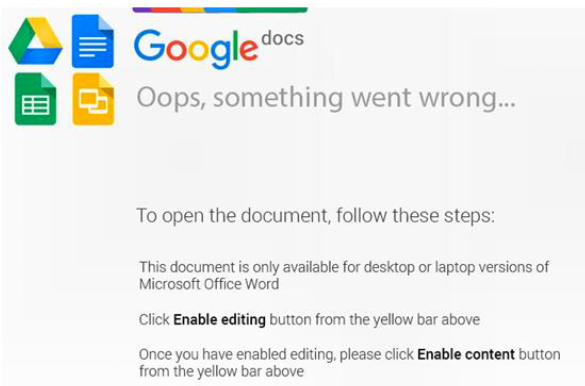
Other documents, however, rely on a different approach. They display fake Google Docs or Microsoft Office messages that instruct recipients to enable editing and content in order to access the information. If users comply, malicious code is executed and malware is downloaded to their device.

Some of the droppers used in the Honeybee campaign are only disguised as documents. One dropper, tracked by McAfee as MaoCheng, has a document icon, but it’s actually an executable file signed with a stolen Adobe certificate. Once executed, MaoCheng opens a decoy document that instructs users to enable content in order to access the information.
McAfee said the MaoCheng dropper was likely created specifically for the Honeybee campaign and it has only been spotted two times. A new variant of the SYSCON backdoor was first seen by researchers on January 17, but the operation has relied on new implants since at least November 2017. Experts say many components are loosely based on previous versions of SYSCON, but they are unique from a code perspective.
“The attacks used simplistic malware, but the speed to put the campaign into production indicates that this is a well-organized group, hence it has the traits of a nation state level group,” Ryan Sherstobitoff, McAfee Senior Analyst of Major Campaigns
Nuance Estimates NotPetya Impact at $90 Million
3.3.2018 securityweek Ransomware
Nuance Communications, one of the companies to have been impacted by the destructive NotPetya attack last year, estimates the financial cost of the attack at over $90 million.
Initially believed to be a ransomware outbreak, NotPetya hit organizations worldwide on June 27, and was found within days to be a destructive wiper instead. Linked to the Russia-linked BlackEnergy/KillDisk malware, NotPetya used a compromised M.E.Doc update server as infection vector.
NotPetya affected major organizations, including Rosneft, AP Moller-Maersk, Merck, FedEx, Mondelez International, Nuance Communications, Reckitt Benckiser, and Saint-Gobain, causing millions in damages to every one of them.
Last year, Nuance estimated that NotPetya impacted its revenue for the third quarter of 2017 by around $15 million, but the total financial losses the attack incurred are of around $100 million, the company now says.
In its latest 10-Q filing with the Securities and Exchange Commission (SEC), Nuance reveals that, for the fiscal year 2017, NotPetya caused losses of around $68.0 million in revenues, and incurred incremental costs of approximately $24.0 million as result of remediation and restoration efforts.
“NotPetya malware affected certain Nuance systems, including systems used by our healthcare customers, primarily for transcription services, as well as systems used by our imaging division to receive and process orders,” Nuance says. The company’s Healthcare segment was hit the most.
The company also notes that, while the direct effects of the attack were remediated during fiscal year 2017, the effects will continue to impact the company for the first quarter of fiscal year 2018 as well. The incident also determined the company to spend more on improving and upgrading information security, during fiscal year 2018 and beyond.
Last month, Danish shipping giant A.P. Moller–Maersk said it had to reinstall software on nearly 50,000 devices following the NotPetya assault. In September 2017, FedEx revealed a negative impact of around $300 million on its profit as result of the attack.
In mid-February 2018, the United Kingdom officially accused the Russian government of being responsible for the NotPetya attack. The next day, United States, Canada, Australia, and New Zealand joined the U.K. and also blamed Russia for the incident.
Biggest-Ever DDoS Attack (1.35 Tbs) Hits Github Website
2.3.2018 thehackernews Attack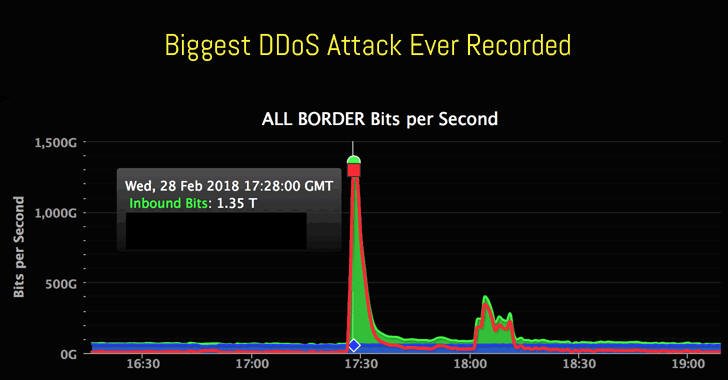
On Wednesday, February 28, 2018, GitHub's code hosting website hit with the largest-ever distributed denial of service (DDoS) attack that peaked at record 1.35 Tbps.
Interestingly, attackers did not use any botnet network, instead weaponized misconfigured Memcached servers to amplify the DDoS attack.
Earlier this week we published a report detailing how attackers could abuse Memcached, popular open-source and easily deployable distributed caching system, to launch over 51,000 times powerful DDoS attack than its original strength.
Dubbed Memcrashed, the amplification DDoS attack works by sending a forged request to the targeted Memcrashed server on port 11211 using a spoofed IP address that matches the victim's IP.
A few bytes of the request sent to the vulnerable server trigger tens of thousands of times bigger response against the targeted IP address.
"This attack was the largest attack seen to date by Akamai, more than twice the size of the September 2016 attacks that announced the Mirai botnet and possibly the largest DDoS attack publicly disclosed," said Akamai, a cloud computing company that helped Github to survive the attack.
In a post on its engineering blog, Github said, "The attack originated from over a thousand different autonomous systems (ASNs) across tens of thousands of unique endpoints. It was an amplification attack using the memcached-based approach described above that peaked at 1.35Tbps via 126.9 million packets per second."
Expect More Record-Breaking DDoS Attacks
Though amplification attacks are not new, this attack vector evolves thousands of misconfigured Memcached servers, many of which are still exposed on the Internet and could be exploited to launch potentially more massive attacks soon against other targets.
To prevent Memcached servers from being abused as reflectors, administrators should consider firewalling, blocking or rate-limiting UDP on source port 11211 or completely disable UDP support if not in use.
Windows Updates Deliver Intel's Spectre Microcode Patches
2.3.2018 securityweek Vulnerebility
Microsoft announced on Thursday that Windows users will receive the microcode updates released by Intel to patch the notorious Spectre vulnerability.
Meltdown and Spectre attacks allow malicious applications to bypass memory isolation and access sensitive data. Meltdown attacks are possible due to a flaw tracked as CVE-2017-5754, while Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). Meltdown and Spectre Variant 1 can be addressed with software updates, but Spectre Variant 2 requires microcode patches.
Microsoft has provided users the necessary software updates and it has now started delivering microcode patches as well.
After the first round of Spectre microcode patches from Intel caused more frequent reboots and other instability problems, the company started releasing new updates. The first patches were for Skylake, then for Kaby Lake and Coffee Lake, and this week for Haswell and Broadwell processors.
Intel has provided the microcode updates to device manufacturers, which are expected to make them available to customers once they have been tested.
For the time being, Microsoft will deliver Intel’s microcode updates to devices with 6th Generation Intel Core (Skylake) processors if they are running Windows 10 version 1709 (Fall Creators Update) or Windows Server version 1709 (Server Core).
“We will offer additional microcode updates from Intel as they become available to Microsoft. We will continue to work with chipset and device makers as they offer more vulnerability mitigations,” said John Cable, director of Program Management, Windows Servicing and Delivery.
When it started releasing software mitigations for Spectre and Meltdown, Microsoft warned that some users may not receive the updates due to antivirus compatibility issues. Cable said a vast majority of Windows devices now have compatible security products installed so they should not experience any problems in getting the patches.
“We will continue to require that an AV compatibility check is made before delivering the latest Windows security updates via Windows Update until we have a sufficient level of AV software compatibility,” Cable explained.
After news broke that Intel’s first round of microcode updates caused instability issues, Microsoft released an update that allowed Windows users to disable the problematic Spectre Variant 2 mitigation.
Cyberattack 'Ongoing' Against German Government Network
2.3.2018 securityweek BigBrothers
The German government's IT network is under an "ongoing" cyberattack", the parliamentary committee on intelligence affairs said Thursday, without confirming a media report that Russian hackers were behind the assault.
"It is a real cyberattack on parts of the government system. It's an ongoing process, an ongoing attack," said Armin Schuster, chairman of the committee, adding that no further details could be given to avoid passing crucial information on to the attackers.
Interior Minister Thomas de Maiziere said the hacking was "a technically sophisticated attack that had been planned for some time", adding that it had been brought under control.
The highly professional assault had been monitored by the security agencies in order to gain insights into the mode of attack and its targets, said de Maiziere.
German news agency DPA, which first reported the attack the previous day, said Thursday, citing unnamed security sources, that the likely authors were the Russian cyber espionage group "Snake".
DPA had earlier pointed at the Russian hacker group APT28, which has been accused of attacks on Hillary Clinton's 2016 presidential campaign as well as on Germany's parliamentary IT system in 2015.
German security authorities had only detected the online spying in December, DPA has reported, adding that it had infiltrated the systems of the foreign and interior ministries. Konstantin von Notz, deputy of the committee, complained it was "completely unacceptable" that members of the oversight body only learnt of the attack through the media.
- Russian hackers -
Top security officials had repeatedly warned during Germany's 2017 general election campaign that Russian hackers may seek to influence or disrupt the polls.
While authorities did not have concrete proof, they have blamed the malware attack that crippled the Bundestag parliamentary network in 2015 for days on the APT28, also known as "Fancy Bear" or "Sofacy".
The attack netted 17 gigabytes of data which, officials feared, could be used to blackmail MPs or discredit them.
In a separate assault, several German political parties were in September 2016 sent fake emails purporting to be from NATO headquarters which contained a link that installed spying software on victims' computers.
The emails affected party operations such as a regional network of Chancellor Angela Merkel's Christian Democratic Union and the federal offices of the far-left Die Linke party.
Amid the rising frequency of attacks, Germany's defence ministry in 2016 set up a cyber department to coordinate the response to online intrusions.
Merkel, seeking to prepare the German public for more online attacks, has said people should "not allow themselves to be irritated" by such rogue operations.
Python-Written CannibalRAT Used in Targeted Attacks
2.3.2018 securityweek Virus
A newly identified remote access Trojan (RAT) that has been written entirely in Python is being used in highly targeted attacks, Cisco Talos researchers say.
Dubbed CannibalRAT, the malware lacks sophistication but exhibits signs of code cannibalization. At least two variants (versions 3.0 and 4.0) have been already used in attacks, both with the usual RAT capabilities, but the latter lacking features to fit a campaign targeting users of a Brazilian public sector management school.
The malicious activity associated with the RAT has increased after the second variant (4.0) emerged on February 5, 2018 (the first variant was spotted on Jan. 8). The newer iteration also uses obfuscation to avoid detection: it was packed with UPX and has a function to generate random strings in memory.
Both variants use base16 encoding scheme to obfuscate command and control (C&C) hostnames and data exchanged with the server. Also, both use the "CurrentVersion\Run" registry key for persistence, along with the service name "Java_Update", Cisco reveals.
Once executed on the infected machine, version 4.0 creates a PDF file with HTML code embedded, designed to load an image hosted at imgur.com, and launches Chrome to open the PDF.
Both versions connect to the same C&C infrastructure, but the older one uses standard web requests, while the newer version uses a REST-based API. The latter method would send username, hostname, and capability related information to the server as part of the initial request.
The credential-stealer modules are copied from the Radium-Keylogger’s source code (available on Github), while the VM detection function was copied from a different Github repository.
This, the researchers say, shows the large amount of code that adversaries share among them, which makes attribution even more difficult.
The malware’s modules have self-explanatory names: runcmd, persistence, download, upload, screenshot, miner, DDoS, driverfind, unzip, ehidden, credentials, file, zip, python, update, and vm. All are present in version 3.0, while version 4.0 lacks the distributed denial of service, miner, Python and update modules, as well as the ability to steal credentials from Firefox (it only works with Chrome).
The latest version also drops the module approach and includes all code in the main script. Furthermore, it includes four possible C&C hostnames (version 3.0 only had two), and randomly chooses one upon execution.
The attackers use the fast flux technique to hide the infrastructure and change name servers with high frequency (120 seconds), but the end points tend to be the same, belonging to a telecom provider in Brazil, the researchers say.
One of the domains associated with the campaign (the malware was hosted on it) is inesapconcurso.webredirect.org, apparently specifically created for these attacks. The actor used social engineering for the name as well: inesapconcurso is the aggregation of inesap and concurso, representing the school name and the Portuguese word for “competition”.
“While the objective of this campaign is unclear, the adversaries went through some work in order to keep their RAT as unnoticed as possible. Both the campaign target and the command-and-control visibility show this campaign is active in Brazil, which our DNS data confirms, reflecting the highly targeted approach of this campaign,” Cisco concludes.
Philips Working on Patches for 35 Flaws in Healthcare Product
2.3.2018 securityweek Vulnerebility
Philips has informed customers that it’s working on patches for dozens of vulnerabilities affecting the company’s IntelliSpace Portal, a visualization and analysis solution designed for healthcare organizations.
According to Philips, versions 7.0.x and 8.0.x of the IntelliSpace Portal are affected by issues related to insecure Windows service permissions, legacy encryption, and remote desktop access functionality. A total of 35 CVE identifiers are associated with the vulnerabilities.
An advisory published by ICS-CERT describes the security holes as input validation flaws that allow remote code execution or denial-of-service (DoS) attacks, information exposure issues that allow unauthorized access to sensitive data, access control weaknesses that can be used for privilege escalation or code execution, local code execution and privilege escalation flaws, a code execution vulnerability that exists due to leftover debugging code, and multiple cryptographic issues. Serious vulnerabilities found in Philips IntelliSpace Portal
While some of these vulnerabilities appear to be specific to Philips’ product, many affect third-party components. For example, there are several remote code execution, information disclosure and DoS flaws related to Windows SMB, including the EternalBlue flaw exploited in the WannaCry ransomware attack.
Other flaws affect the Microsoft Remote Desktop Protocol (RDP) and Microsoft Office. The crypto-related weaknesses include POODLE, BEAST and other vulnerabilities disclosed in the past years, including one from 2004.
While exploits are publicly available for many of these vulnerabilities, they don’t specifically target Philips products, and the vendor claims it’s not aware of any attacks.
Philips will release patches in the coming months. The company says it’s also currently testing operating system updates, which cannot be installed without ensuring that they don’t impact the stability of the product. Until patches become available, customers have been provided a series of workarounds.
In January, Philips informed customers of an authentication issue affecting its IntelliSpace Cardiovascular (ISCV) cardiac image and information management system.
The company learned from a customer that when the ISCV system is used with an Electronic Medical Record (EMR) in Kiosk mode and configured with Windows authentication, users may not be properly logged out once they are done using the software.
The flaw allows a malicious actor that gains access to the system after it has been used by a legitimate EMR user to log in with that user’s credentials and obtain or modify sensitive information.
Philips said the security hole will be addressed with the release of version 3.1.0. In the meantime, users have been advised to close the browser after accessing the system. Changing the configuration so that Windows authentication is not used also addresses the problem.
Iran-Linked Chafer Group Expands Toolset, Targets List
2.3.2018 securityweek APT
The Iran-based targeted attack group known as "Chafer" has been expanding its target list in the Middle East and beyond and adding new tools to its cyberweapon arsenal, Symantec warns.
Last year, the group engaged in a series of ambitious new attacks, hitting a major telecom companies in the Middle East and also attempting to attack a major international travel reservations firm. Active since at least July 2014 and already detailed a couple of years ago, Chafer is mainly focused on surveillance operations and the tracking of individuals.
During 2017, the group used seven new tools, rolled out new infrastructure, and hit nine new organizations in Israel, Jordan, the United Arab Emirates, Saudi Arabia, and Turkey. Targets included airlines, aircraft services, software and IT services firms serving the air and sea transport sectors, telecoms, payroll services, engineering consultancies, and document management software companies.
The group also targeted an African airline and attempted to compromise an international travel reservations firm, Symantec discovered.
Last year, Chafer compromised a telecoms services provider in the Middle East, a company that sells solutions to multiple telecom operators in the region. The compromise could have potentially allowed the attackers to carry out surveillance on a vast pool of end-users.
In attacks observed in 2015, the group was attacking the web servers of organizations, likely through SQL injection attacks. Last year, the group also started using malicious documents to drop malware, likely sent via spear-phishing emails to individuals working in targeted organizations.
Said documents were Excel spreadsheets carrying a malicious VBS file that would run a PowerShell script to execute a dropper on the compromised machine. In turn, the dropper would install an information stealer, a screen capture utility, and an empty executable.
The screen capture tool only had a role in the initial information gathering stage, the information stealer targeted the contents of the clipboard, took screenshots, recorded keystrokes, and stole files and user credentials. Next, the attackers would download additional tools onto the infected computer and attempted lateral movement on the victim’s network.
Recently, Chafer employed seven new tools in addition to the malware already associated with the group. Most of these tools, Symantec points out, are freely available, off-the-shelf tools that have been put to a malicious use.
These include Remcom, an open-source alternative to PsExec; Non-sucking Service Manager (NSSM), an open-source alternative to the Windows Service Manager; a custom screenshot and clipboard capture tool; SMB hacking tools, including the EternalBlue exploit; GNU HTTPTunnel, an open-source tool to create a bidirectional HTTP tunnel on Linux computers; UltraVNC, an open-source remote administration tool for Windows; and NBTScan, a free tool for scanning IP networks for NetBIOS name information.
Additionally, the group continued to use tools such as its own custom backdoor Remexi, PsExec, Mimikatz, Pwdump, and Plink.
Chafer apparently used the tools in concert to traverse targeted networks. NSSM was recently adopted for persistence and to install a service to run Plink, which opens reverse SSH sessions to presumably gain RDP access to the compromised computer. Next, PsExec, Remcom, and SMB hacking tools are leveraged for lateral movement.
The new infrastructure used in recent attacks included the domain win7-updates[.]com as a command and control (C&C) address, along with multiple IP addresses, though it’s unclear whether these were leased or hijacked. On a staging server apparently used by the attackers, the researchers found copies of many of the group’s tools.
According to Symantec, Chafer’s activities have some links to Oilrig, another Iran-based cyberespionage group. Both appear to be using the same IP address for C&C address, as well as a similar infection vector, an Excel document dropping a malicious VBS file referencing to the same misspelled file path.
While this could suggest that the two groups are one and the same, there isn’t enough evidence to support that hypothesis, Symantec says. More likely, the “two groups are known to each other and enjoy access to a shared pool of resources,” the researchers suggest.
Chafer’s recent activities show not only that the group remains highly active, but also that it has become more audacious in its choice of targets. Similar to other targeted attack groups, it has been relying on freely available software tools for malicious activities, and also moved to supply chain attacks, which are more time consuming and more likely to be discovered.
“These attacks are riskier but come with a potentially higher reward and, if successful, could give the attackers access to a vast pool of potential targets,” Symantec concludes.
Equifax Identifies 2.4 Million More Affected by Massive Hack
2.3.2018 securityweek Hacking
US credit bureau Equifax said Thursday it identified an additional 2.4 million American consumers affected by last year's massive data breach that sparked a public outcry and a congressional probe.
The company's forensic investigation revealed the new identities on top of the 146 million affected in the attack that exposed victims' personal details, including names, birth dates and social security numbers.
"This is not about newly discovered stolen data," said Paulino do Rego Barros, who took over as interim chief executive last year at the scandal-hit credit agency.
"It's about sifting through the previously identified stolen data, analyzing other information in our databases that was not taken by the attackers, and making connections that enabled us to identify additional individuals."
Equifax said the newly identified consumers were not previously informed because their social security numbers -- which appeared to be the focus of the hackers -- were not stolen together with their partial driver's license information.
Equifax said it would notify these consumers and will offer identity theft protection and credit file monitoring services.
The Atlanta-based company, which tracks consumer financial data to help establish credit ratings, is now facing state and federal investigations as well as class-action lawsuits over the breach.
While the breach was not the largest in history, it has been considered among the most damaging because of the sensitive information held by Equifax and the potential for that data to be used in identity theft or other crimes.
CannibalRAT, a RAT entirely written in Python observed in targeted attacks
2.3.2018 securityaffairs Virus
Security researchers from Cisco Talos discovered a new remote access Trojan (RAT) dubbed CannibalRAT that has been written entirely in Python.
The CannibalRAT RAT is being used in highly targeted attacks. the experts explained that even if it isn’t very sophisticated it exhibits signs of code cannibalisation from other open-source projects.
“The RAT itself is not very sophisticated, and exhibits signs of code cannibalisation from other open-source projects, which contrasts with the command-and-control, using fast flux to keep hidden, even if the endpoints are not very diversified.” reads the analysis published by Talos.
The researchers observed the involvement of at least two variants (versions 3.0 and 4.0) in targeted attacks.

The two samples were written using Python and packed into an executable using the popular tool py2exe.
According to the researchers, the version 4.0 is a stripped-down version, this means that vxers removed from the main code some features, anyway authors have attempted to add obfuscation techniques in order to avoid detection.
The version 4.0 includes a function that will generate random strings in memory in the attempt to make memory string analysis harder.
“The malware main script bytecode is stored in a portable executable (PE) section called PYTHONSCRIPT, while the Python DLL is stored in a section called PYTHON27.DLL. All the remaining modules’ bytecode is compressed and stored in the executable overlay.” continues the analysis.
The first variant of the malware was spotted on Jan. 8, anyway, Cisco Talos observed a significant increase in the activities of the CannibalRAT after the variant 4.0 appeared in the wild on February 5, 2018
Both variants use base16 encoding scheme to obfuscate command and control (C&C) hostnames and data exchanged with the server, they gain persistence by using “CurrentVersion\Run” registry key with the service name “Java_Update“,
Once executed, the CannibalRAT version 4.0 creates a PDF file with HTML code embedded that loads an image hosted at imgur.com and launches Chrome to open the PDF.
The two versions share the same C&C servers, but while the variant 3.0 uses standard web requests, the newer version uses a REST-based API.
“The command-and-control infrastructure attempts to use the fast flux technique to hide, although the name servers are changing with high frequency, and the end points tend to be the same, all belonging to a telecom provider in Brazil with the autonomous system number AS 7738 and shared among all four command-and-control hostnames.” states Cisco Talos.
CannibalRAT borrows the credential-stealer modules form the Radium-Keylogger, which has the source code published on Github, the experts also noticed that the VM detection feature was copied from a different Github repository.
“The malware’s modules have self-explanatory names: runcmd, persistence, download, upload, screenshot, miner, DDoS, driverfind, unzip, ehidden, credentials, file, zip, python, update, and vm.” continues the analysis.”All are present in version 3.0, while version 4.0 lacks the distributed denial of service, miner, Python and update modules, as well as the ability to steal credentials from Firefox (it only works with Chrome).”
Experts noticed that the version 4.0 doesn’t use modules, instead, all the code is included in the main script. Furthermore.
Talos team provided details of a campaign involving the CannibalRAT Version targeting the INESAP, a Brazilian school for public administration
The campaign is highly targeted at this specific geographic region, attackers targeted only Chrome users.
“the RAT was hosted at inesapconcurso.webredirect.org and filebin.net, while the second domain is a popular file-sharing platform, the first domain was clearly created as part of the campaign.” continues the analysis.
“The subdomain inesapconcurso is the aggregation of two words; inesap and concurso. The first word is the school name, the second can be translated into competition, this is part of the social engineering of this campaign, as this Institute helps the management the application of workers to public sector vacancies.”
Further info about the malware including IoCs are reported in the analysis.