
RCE flaw in Exim MTA affects half of the email servers online
7.3.2018 securityaffairs Vulnerebility
A critical RCE vulnerability in the Exim mail transfer agent (MTA), tracked as CVE-2018-6789, affects most of the email servers online.
A critical remote code vulnerability in the Exim mail transfer agent (MTA), tracked as CVE-2018-6789, affects most of the email servers online. It has been estimated that as in March 2017, the total number of Internet’s email servers running Exim was over 560,000, that corresponds to 56% of all Mail (MX) Server online.
“We reported an overflow vulnerability in the base64 decode function of Exim on 5 February, 2018, identified as CVE-2018-6789. This bug exists since the first commit of exim, hence ALL versions are affected.” reads the blog post published by security firm Devcore.
“According to our research, it can be leveraged to gain Pre-auth Remote Code Execution and at least 400k servers are at risk. Patched version 4.90.1 is already released and we suggest to upgrade exim immediately.”
According to Shodan, the number of Exim Servers exposed online is more than 4 million, most of them in the US.

The flaw was discovered by the security researcher Meh Chang, which reported it to the Exim maintainers on February 2.
On February 10, the Exim team released Exim version 4.90.1 that addresses the flaw.
The researchers developed an exploit targeting SMTP daemon of Exim leverages a one-byte buffer overflow in the base64 decode function of Exim by tricking memory management mechanism.
“There is a buffer overflow in base64d(), if some pre-conditions are met. Using a handcrafted message, remote code execution seems to be possible. A patch exists already and is being tested.” reads the security advisory published by the Exim team.
Exim server owners should install the Exim 4.90.1 update as soon as possible.
Below the vulnerability timeline (UTC)
2018-02-05 Report from Meh Chang <meh@devco.re> via exim-security mailing list
2018-02-06 Request CVE on https://cveform.mitre.org/ (heiko) CVE-2018-6789
2018-02-07 Announcement to the public via exim-users, exim-maintainers mailing lists and on oss-security mailing list
2018-02-08 16:50 Grant restricted access to the security repo for distro maintainers
2018-02-09 One distro breaks the embargo
2018-02-10 18:00 Grant public access to the our official git repo.
In November the Exim team warned of other flaws through the public bug tracker.
Leaked NSA Dump Also Contains Tools Agency Used to Track Other Hackers
7.3.2018 thehackernews BigBrothers
A years ago when the mysterious hacking group 'The Shadow Brokers' dumped a massive trove of sensitive data stolen from the US intelligence agency NSA, everyone started looking for secret hacking tools and zero-day exploits.
A group of Hungarian security researchers from CrySyS Lab and Ukatemi has now revealed that the NSA dump doesn't just contain zero-day exploits used to take control of targeted systems, but also include a collection of scripts and scanning tools the agency uses to track operations of hackers from other countries.
According to a report published today by the Intercept, NSA's specialized team known as Territorial Dispute (TeDi) developed some scripts and scanning tools that help the agency to detect other nation-state hackers on the targeted machines it infects.
NSA hackers used these tools to scan targeted systems for 'indicators of compromise' (IoC) in order to protect its own operations from getting exposed, as well as to find out what foreign threat actors are stealing and which hacking techniques they are using.
"When the NSA hacks machines in Iran, Russia, China and elsewhere, its operators want to know if foreign spies are in the same machines because these hackers can steal NSA tools or spy on NSA activity in the machines," the publication reports.
"If the other hackers are noisy and reckless, they can also cause the NSA's own operations to get exposed. So based on who else is on a machine, the NSA might decide to withdraw or proceed with extra caution."
NSA's Territorial Dispute team maintains a database of digital signatures, like fingerprints for file and snippets from various hacking groups, to track APT operations for attribution.
According to the researchers, when the Shadow Brokers managed to hack the NSA networks and stole a collection of sensitive files in 2013, the agency was tracking at least 45 different state-sponsored APT groups.
It also appears that the NSA hackers were tracking some of the tools from Dark Hotel in 2011—that's about 3 years prior to the wider security community discovered the hacking group.
Dark Hotel is a sophisticated cyber espionage group believed to be from South Korea, well known for targeting hotel Wi-Fi networks to spy on senior-level executives at organisations in manufacturing, defense, investment capital, private equity, automotive and other industries.
The group of researchers has planned to release its findings of the NSA scripts and scanning tools this week at the Kaspersky Security Summit in Cancun, which would help other researchers to dig through the data and identify more of the APT groups the NSA is hunting.
"The team also hopes the information will help the community classify some malware samples and signatures that have previously been uncovered by the security community but remain unattributed to a specific threat group because researchers don’t know to which advanced hacking group they belong," the Intercept says.
Cryptography and System Security (CrySyS Lab) is best known for uncovering an Israeli spying tool called Duqu in 2011, which was believed to be developed by the same Israeli hackers who took the U.S. help to develop the infamous Stuxnet malware for sabotaging Iranian nuclear program.
600 Powerful Bitcoin-Mining Computers Worth $2 Million Stolen In Iceland
7.3.2018 thehackernews Cryptocurrency
Around 600 powerful devices specifically designed for mining bitcoin and other cryptocurrencies have been stolen from Icelandic data centers in what has been dubbed the "Big Bitcoin Heist."
To make a profit, so far criminals have hacked cryptocurrency exchanges, spread mining malware, and ransomware—and even kidnapped cryptocurrency investors for ransom and tried to rob a bitcoin exchange, but now the greed has reached another level.
The powerful computers are estimated to be worth around $2 million, Associated Press reports, and are used to generate cryptocurrency that at the time of this writing are worth $11,500 each.
The theft, which took place between late December and early January, is one of the biggest series of robberies Iceland has ever experienced, according to law enforcement.
"This is grand theft on a scale unseen before," said Police Commissioner Olafur Helgi Kjartansson of the southwestern Reykjanes peninsula.
There were four different burglaries (three in December and one in January) in total that took place at various locations, two of which went down on the southwestern Reykjanes peninsula.
The thefts, which also included burglary of 600 graphics cards, 100 processors, 100 power supplies, 100 motherboards and 100 sets of computer memory, were captured on CCTV cameras by Advania, the server company reportedly hit by two of the three thefts.
Although the stolen computers have not yet been found, police arrested 11 suspects as part of the investigation of the incident, one of whom worked as a security guard.
On Friday, the Reykjanes District Court expressed restraint, releasing nine people on bail and leaving only two people under arrest.
Iceland is home to the data centers of a number of the cryptocurrency mining companies because the mining process is extremely energy-intensive, and renewable energy is cheap there. Almost 100 percent of the power generated in the country comes from renewable sources.
The police are currently tracking high energy consumption areas across Iceland in hopes the thieves will turn the stolen servers on, which could potentially lead them back to the stolen servers' location.
The authorities are also contacting internet service providers (ISPs), electricians and storage units, asking them to report any sudden spike in power usage or other signs the stolen servers had been reconnected.
The police have currently held off from telling the public about the incident for a while, in order not to compromise their investigation.
1.7 Tbps DDoS Attack — Memcached UDP Reflections Set New Record
7.3.2018 thehackernews Attack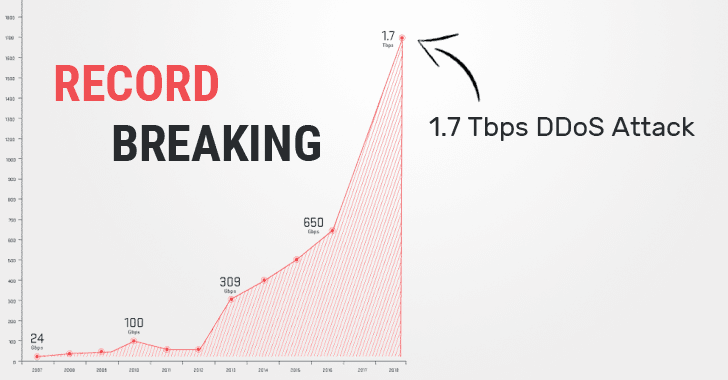
The bar has been raised.
As more amplified attacks were expected following the record-breaking 1.35 Tbps Github DDoS attack, someone has just set a new record after only four days — 1.7 Tbps DDoS attack.
Network security and monitoring company Arbor Networks claims that its ATLAS global traffic and DDoS threat data system have recorded a 1.7Tbps reflection/amplification attack against one of its unnamed US-based customer's website.
Similar to the last week's DDoS attack on GitHub, the massive bandwidth of the latest attack was amplified by a factor of 51,000 using thousands of misconfigured Memcached servers exposed on the Internet.
Memcached, a popular open source distributed memory caching system, came into news earlier last week when researchers detailed how attackers could abuse it to launch amplification DDoS attack by sending a forged request to the targeted Memcached server on port 11211 using a spoofed IP address that matches the victim's IP.
A few bytes of the request sent to the vulnerable server can trigger tens of thousands of times bigger response against the targeted IP address, resulting in a powerful DDoS attack.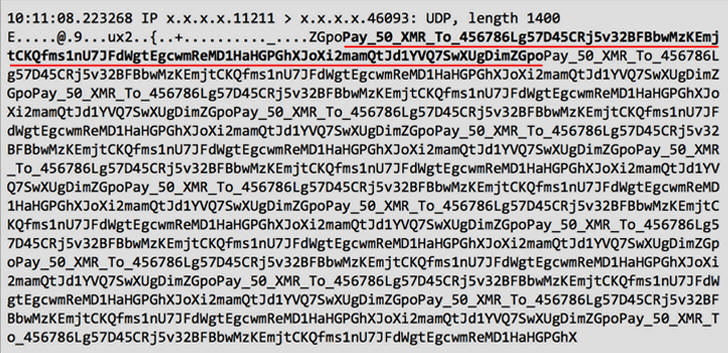
Meanwhile, researchers also noted that cybercriminals have started weaponizing the DDoS attacks through vulnerable memcached servers to extort money from victims.
Following last week's 1.3 Tbps DDoS attack against GitHub, Akamai said its customers have been receiving extortion messages delivered alongside the typically "junk-filled" attack payloads, asking them for 50 XMR (Monero coins), valued at over $15,000.
"While the internet community is coming together to shut down access to the many open memcached servers out there, the sheer number of servers running memcached openly will make this a lasting vulnerability that attackers will exploit," Arbor Networks said in a blog post.
Reflection/amplification attacks are not new. Attackers have previously used reflection/amplification DDoS attack techniques to exploit flaws in DNS, NTP, SNMP, SSDP, CLDAP, Chargen and other protocols in an attempt to maximize the scale of their cyber attacks.
However, the latest attack vector evolves thousands of misconfigured Memcached servers, many of which are still exposed on the Internet and could be exploited to launch potentially more massive attacks soon against other targets. So expect to see more such attacks in coming days.
To prevent Memcached servers from being abused as reflectors, we urge users to install a firewall that should provide access to memcached servers only from the local network.
Administrators should also consider avoiding external traffic to the ports used by memcached (for example 11211 port used by default), and block or rate-limiting UDP or completely disable UDP support if not in use
New 4G LTE Network Attacks Let Hackers Spy, Track, Spoof and Spam
7.3.2018 thehackernews Mobil Attack
Security researchers have discovered a set of severe vulnerabilities in 4G LTE protocol that could be exploited to spy on user phone calls and text messages, send fake emergency alerts, spoof location of the device and even knock devices entirely offline.
A new research paper [PDF] recently published by researchers at Purdue University and the University of Iowa details 10 new cyber attacks against the 4G LTE wireless data communications technology for mobile devices and data terminals.
The attacks exploit design weaknesses in three key protocol procedures of the 4G LTE network known as attach, detach, and paging.
Unlike many previous research, these aren't just theoretical attacks. The researchers employed a systematic model-based adversarial testing approach, which they called LTEInspector, and were able to test 8 of the 10 attacks in a real testbed using SIM cards from four large US carriers.
Authentication Synchronization Failure Attack
Traceability Attack
Numb Attack
Authentication Relay Attack
Detach/Downgrade Attack
Paging Channel Hijacking Attack
Stealthy Kicking-off Attack
Panic Attack
Energy Depletion Attack
Linkability Attack
Among the above-listed attacks, researchers consider an authentication relay attack is particularly worrying, as it lets an attacker connect to a 4G LTE network by impersonating a victim's phone number without any legitimate credentials.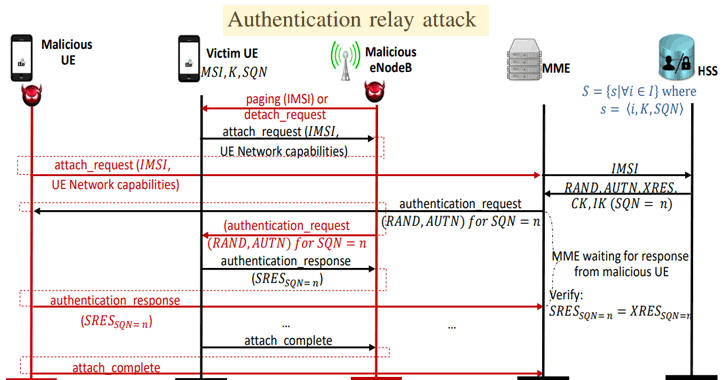
This attack could not only allow a hacker to compromise the cellular network to read incoming and outgoing messages of the victims but also frame someone else for the crime.
"Through this attack the adversary can poison the location of the victim device in the core networks, thus allowing setting up a false alibi or planting fake evidence during a criminal investigation," the report said.
Other notable attacks reported by the researchers could allow attackers to obtain victim’s coarse-grained location information (linkability attack) and launch denial of service (DoS) attack against the device and take it offline (detach attack).
"Using LTEInspector, we obtained the intuition of an attack which enables an adversary to possibly hijack a cellular device’s paging channel with which it can not only stop notifications (e.g., call, SMS) to reach the device but also can inject fabricated messages resulting in multiple implications including energy depletion and activity profiling," the paper reads.
Using panic attack, attackers can create artificial chaos by broadcasting fake emergency messages about life-threatening attacks or riots to a large number of users in an area.
What's interesting about these attacks is that many of these can be carried out for $1,300 to $3,900 using relatively low-cost USRP devices available in the market.
Researchers have no plans to release the proof-of-concept code for these attacks until the flaws are fixed.
Although there are some possible defenses against these observed attacks, the researchers refrained from discussing one.
The paper reads: "retrospectively adding security into an existing protocol without breaking backward compatibility often yields band-aid-like-solutions which do not hold up under extreme scrutiny."
"It is also not clear, especially, for the authentication relay attack whether a defense exists that does not require major infrastructural or protocol overhaul," it adds. "A possibility is to employ a distance-bounding protocol; realization of such protocol is, however, rare in practice."
The vulnerabilities are most worrying that once again raise concerns about the security of the cell standards in the real world, potentially having an industry-wide impact.
Funny? Useful? Cool? Kali Linux natively on Windows 10
7.3.2018 securityaffairs Safety
It’s funny, but it is true, the popular Kali Linux hacking distro is available for download on the official Microsoft App Store on Windows 10.
Kali Linux is now natively available on Windows 10, without requiring dual boot or virtualization.
Kali Linux isn’t the unique Linux distribution available on the Windows App Store, Windows users can download other popular distros, including as Ubuntu, Fedora, and OpenSUSE.
The Linux distribution can be used directly on Windows by exploiting the feature called Windows Subsystem for Linux (WSL)
“For the past few weeks, we’ve been working with the Microsoft WSL team to get Kali Linux introduced into the Microsoft App Store as an official WSL distribution, and today we’re happy to announce the availability of the ‘Kali Linux’ Windows application,” reads the announcement published on the Kali Linux website.
“For Windows 10 users, this means you can simply enable WSL, search for Kali in the Windows store, and install it with a single click. This is especially exciting news for penetration testers and security professionals who have limited toolsets due to enterprise compliance standards.”
To enable the WSL follow these steps:
Access the “Apps and features” menù item under the Control Panel
Select “Programs and Features” from the right panel
Click the “Turn Windows features on or off” from the left menu
Check the “Windows Subsystem for Linux”
Save the operation and Reboot the system
Alternatively, users can open PowerShell as Administrator and run the following command before restarting the machine.
Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Windows-Subsystem-Linux
At this point, you can search for Kali Linux on Windows Store and download it.
Offensive Security has published a video to show how to use the distribution on Windows 10.
It is important to remind that the Kali Linux on Windows does not come with any hacking testing tools pre-installed, this means that you need to download them when needed.
Experts noticed that Antivirus software, including Windows Defender, can flag the distro’s packages as a malware.
BlackBerry Sues Facebook Over Messaging Apps
6.3.2018 securityweek Social
Canadian telecommunications firm BlackBerry sued Facebook on Tuesday, accusing the American social media company of infringing on its patents for messaging apps.
BlackBerry is claiming infringement on patents it holds for message encryption and notifications, and is seeking an injunction as well as damages for lost profits, although no figure was given.
Facebook and its wholly-owned services Instagram and WhatsApp are named as defendants in the lawsuit.
"We have a lot of respect for Facebook and the value they've placed on messaging capabilities, some of which were invented by BlackBerry," BlackBerry spokeswoman Sarah McKinney said in a statement.
She said BlackBerry would like to partner with Facebrook "in our drive toward a securely connected future, and we continue to hold this door open to them."
"However, we have a strong claim that Facebook has infringed on our intellectual property, and after several years of dialogue, we also have an obligation to our shareholders to pursue appropriate legal remedies," McKinney added.
BlackBerry, after abandoning the manufacture of its once-popular smartphones, has refocused its core business on cybersecurity software and services.
World Economic Forum Announces New Fintech Cybersecurity Consortium
6.3.2018 securityweek Cyber
Following the announcement of a new Global Centre for Cybersecurity, the World Economic Forum (WEF) has today launched a new fintech-focused initiative: WEF's Fintech Cybersecurity Consortium. Its aim is to create a framework for the assessment of cybersecurity in financial technology firms and data aggregators.
The founding members of the new consortium include global bank Citigroup, insurance company Zurich Insurance Group, fintech lender Kabbage and financial infrastructure provider DTCC. Their intention is to develop common principles for cybersecurity assessments, guidance for implementation, a point-based scoring framework, and guidance on improving an organization's score.
"Cyber breaches recorded by businesses have almost doubled since 2013 and the estimated cost of cybercrime is $8 trillion over the next five years," said Mario Greco, Chief Executive Officer of Zurich Insurance Group, Switzerland, a participant in the consortium. "We expect the consortium to help adopt best cybersecurity practices and reduce the complexity of diverging cyber regulation around the world."
The $8 trillion figure comes from a May 2017 report from Juniper Research. More recently, McAfee reported that the cost of global cybercrime is $600 billion.
The new consortium will commence immediately, working closely with WEF's Global Centre for Cybersecurity being established in Geneva. It expects to draw upon a similar, domestic-focused project undertaken in 2017 by the US Chamber of Commerce on Critical Infrastructure Protection, Information Sharing and Cybersecurity. A detailed description is found in a separate whitepaper, Innovation-Driven Cyber-Risk to Customer Data in Financial Services (PDF).This paper makes it clear that the work will draw upon existing frameworks, with particular reference to NIST.
WEF spokesperson Georg Schmitt told SecurityWeek that the consortium is "doing this to step in where regulators might not (yet)." The paper makes it clear that recent cyber developments are considered to be a major threat to the financial sector. Two of these are the evolution of open banking driven by European finance legislation such as PSD2 ; and the customer privacy regulations, led perhaps by GDPR. The former increases fintech's attack surface, while rapid growth in the IoT and use of AI algorithms increases the amount of PII collected and stored.
"It's a smart move to highlight data aggregators as a point of cyber vulnerability," David Shrier, CEO of Distilled Analytics told SecurityWeek. "You have only to look at the Equifax hack to understand why this is important. And classically they are not considered fintechs, so it's worthwhile to call them out separately.
"Unknowingly," he adds, "in our race to adopt new technology over the past 20 years, we have ceded a massive amount of personal information to these third parties (data aggregator and fintech alike), and it has created gigantic cyber vulnerabilities."
Kabbage CEO Rob Frohwein explained: "Kabbage is joining the World Economic Forum consortium because cybersecurity is a never-ending, age-long issue that requires a long-lasting solution for tomorrow and not a Band-Aid for today. We need a living global standard that allows financial services companies to compete and work with incumbent institutions across borders and industries."
The Fintech Cybersecurity Consortium will develop a cybersecurity assessment framework for fintechs and data aggregators. This will, in theory, enable new firms to interconnect with fintech and aggregator firms with greater confidence.
Some firms will likely balk at yet another fintech framework-come-regulation, particularly since it will evolve from existing frameworks. "Unfortunately, this really doesn't change the game in any way (that I can tell)," comments Nathan Wenzler, chief security strategist at AsTech. "It is likely to get a, 'it's yet another regulation for us financial companies' kind of reaction. Yes, some financial firms might be interested. If this was any other industry besides finance, it might be something more significant. As it stands, they're pretty numb to all the regulatory requirements they deal with everywhere."
Shrier is more optimistic. "We have seen the WEF tackle other areas with paradigm-shifting thought leadership, so, provided they get the right experts in their working group, this could be additive to improving cybersecurity. While this new effort is not guaranteed to succeed, our problem today is too many headlines about cyber breaches and not enough systems thinking about cyber solutions. The WEF group has a chance to raise serious cyberthinking in the C-suite and board room proactively, instead of reactively after an incursion."
Two Scammers, Five Mules Arrested in BEC Bust
6.3.2018 securityweek Spam
A criminal investigation commenced by the French National Gendarmerie in June 2016 led to the arrest of one French and one Belgian national on February 20, 2018 for their part in large scale CEO fraud (also known as business email compromise -- BEC).
According to Europol, "The criminals belonged to an organized crime group involved in at least 24 cases of CEO fraud causing €4.6 million worth of damage."
The investigation was launched when French law enforcement was informed that two companies had fallen victim to BEC fraud, with a total estimated cost of €1.2 million. Since then, the investigation has identified 15 alleged Romanian company managers living in France and Belgian involved in orchestrating BEC fraud and Forex scams. Money obtained from the BEC scams was sent via the Romanian company accounts to Hong Kong.
The two suspects arrested in France are thought to be recruiters and facilitators for the criminal gang; but not the masterminds. "The suspects arrested in Paris and Lille seem to be closely linked to the ring leader(s) most probably hiding in Israel, where computers and mobile phones have also been seized," announced Europol on Friday.
A further five individuals were arrested in Belgium, suspected of acting as money mules for the gang.
BEC fraud has become a major problem over the last few years. According to figures from the FBI, worldwide BEC fraud netted $2.3 billion from 17,642 victims in at least 79 countries from October 2013 through February 2016.
A typical BEC scam will persuade an authorized employee to wire money to an external account. It is a sophisticated version -- with much higher stakes -- of the pre-internet fax directory scam where a fake invoice is sent to a company because it often just gets paid. It is similar in operation to targeted spear-phishing using a disguised sender and social engineering to trick the target. Typically, it is an email disguised to appear as if it comes from the CEO (hence its common description as CEO fraud), asking the finance director to urgently mail funds to or for a supplier or partner.
In this instance, the two arrested in France helped people to establish firms with Romanian bank accounts. According to Europol these included law firms and notaries. An apparent email from the CEO asking for funds to be sent to a law firm in France acting on behalf of a known or fictitious supplier could appear both safe and compelling.
Unlike phishing, BEC carries no payload in the form of a malicious link or weaponized attachment. Without such a payload to detect, BEC emails are very difficult to flag with technology.
In February, Agari published a trends analysis (PDF) of BEC. It found that in the second half of 2017, an average of 45 BEC attacks per company bypassed secure email gateways (SEG), advanced threat protection systems (APT), and targeted attack protection (TAP); 96% or organizations had experienced BEC attacks; and one company had experienced 369 attacks.
DMARC can help prevent BEC, but is not foolproof. Furthermore, Agari points out that 67% of the Fortune 500 do not have a DMARC policy, and only 5% have a Reject (or “blocking”) policy on their corporate domain.
Because of the difficulties in detecting BEC attacks, there have been several major successful examples during 2017. In April 2017, the Justice Department disclosed that Google and Facebook lost a combined $100 million to BEC attacks impersonating their server hardware supplier Quanta. In June 2017, New York Judge Lori Sattler was duped into sending $1,057,500 to a scammer posing as her lawyer in a real estate deal. In August 2017, MacEwan University in Alberta, Canada was defrauded of $11.8 million in a BEC attack impersonating a vendor of the university.
Android's March 2018 Patches Fix Critical, High Risk Flaws
6.3.2018 securityweek Android
Google has released its March 2018 set of security updates for Android to address numerous Critical and High severity vulnerabilities in the popular mobile operating system.
The majority of the Critical vulnerabilities addressed this month could allow an attacker to execute code remotely on affected devices. Impacted components include media framework, system, and kernel, Nvidia, and Qualcomm components.
A total of 16 vulnerabilities were addressed as part of the 2018-03-01 security patch level: 8 rated Critical severity and 8 considered High risk. The most severe of these vulnerabilities could allow a remote attacker using a specially crafted file to run arbitrary code with high privileges.
Four of the Critical flaws (three remote code execution bugs and one elevation of privilege issue) and two High risk bugs (elevation of privilege) were addressed in media framework. The remaining four Critical vulnerabilities (all remote code execution) and six High risk issues (information disclosure bugs) were resolved in system.
The 2018-03-05 security patch level addressed 21 vulnerabilities, only three of which were rated Critical severity. All of the remaining bugs were assessed High risk, Google notes in an advisory.
The flaws affect Kernel components (two elevation of privilege and four information disclosure High risk issues), NVIDIA components (two High risk elevation of privilege bugs), Qualcomm components (two Critical – remote code execution – and nine High risk – six elevation of privilege, two information disclosure, and one denial of service – vulnerabilities), and Qualcomm closed-source components (one Critical and one High risk).
Google also addressed over 40 vulnerabilities impacting its Pixel / Nexus devices this month, most of them rated Moderate severity.
A Moderate risk elevation of privilege issue was patched in framework, 2 High severity denial of service bugs were resolved in Media framework, and 2 elevation of privilege and 2 information disclosure vulnerabilities were fixed in system, all four Medium risk.
Google also addressed 1 High risk information disclosure and 5 Moderate elevation of privilege issues in kernel components, 3 moderate information disclosure bugs in Nvidia components, and 18 elevation of privilege and 9 information disclosure issues in Qualcomm components (all Moderate severity).
Pixel 2 and Pixel 2 XL devices also received fixes for several functionality issues that were not related to the security of these devices. Instead, they improved screen wake performance with fingerprint unlock, audio performance when recording video, and crash reporting.
Kaspersky Lab Offers $100,000 for Critical Vulnerabilities
6.3.2018 securityweek Vulnerebility
Just days before its annual Security Analyst Summit kicks off in Cancun, Mexico, Kaspersky Lab this week announced an extension to its bug bounty program and plans to pay rewards of up to $100,000 for severe vulnerabilities in some of its products.
Launched in August 2016, the HackerOne-powered bug bounty program initially promised a total of $50,000 in bounties and resulted in the discovery of more than 20 flaws in the first six months. To date, the program allowed Kaspersky to address more than 70 bugs in its products and services.
In April last year, the Moscow-based security firm announced the addition of Kaspersky Password Manager 8 to the bounty program, along with an increase in the maximum reward for remote code execution vulnerabilities from $2,000 to $5,000.
The newly announced larger payouts represent a 20-fold increase on existing rewards available to researchers who participate in the company’s bug bounty program, which is available to all members of the HackerOne platform.
The largest rewards will be offered for the discovery and coordinated disclosure of bugs that enable remote code execution via the product database update channel, Kaspersky says. Another requirement is that the launch of the code takes place in the product’s high privilege process and silently from the user, and that persistence is also achieved.
Security flaws leading to other types of remote code execution will receive rewards ranging from $5,000 to $20,000, depending on their complexity level. The company also announced it is willing to pay researchers who discover bugs allowing local privilege escalation or leading to sensitive data disclosure.
Only previously unknown vulnerabilities discovered in Kaspersky Internet Security 2019 (the most recent beta) and Kaspersky Endpoint Security 11 (the most recent beta) qualify for the bug bounties. Supported platforms include desktop Windows 8.1 and higher, with the most recent updates installed.
“Finding and fixing bugs is a priority for us as a software company. We invite security researchers to make sure there are no vulnerabilities in our products. The immunity of our code and highest levels of protection that we offer customers is a core principal of our business – and a fundamental pillar of our Global Transparency Initiative,” Eugene Kaspersky, CEO of Kaspersky Lab, said.
Announced in October 2017, the Global Transparency Initiative was meant to clear Kaspersky’s name after reports suggested it had ties to the Russian government and the Department of Homeland Security (DHS) ordered all government agencies to stop using the company’s products.
"ComboJack" Malware Steals Multiple Virtual Currencies
6.3.2018 securityweek Cryptocurrency
A newly discovered piece of malware is capable of stealing a variety of crypto-coins from its victims by replacing legitimate wallet addresses with that of the attacker.
Dubbed ComboJack, the malware performs its nefarious activity by monitoring the user clipboard and replacing targeted addresses there. This is the same technique that was recently observed being used by the Evrial Trojan and the CryptoShuffler malware, but the new threat targets multiple virtual currencies.
ComboJack, Palo Alto Networks has discovered, is targeting multiple crypto-currencies at the moment, including Bitcoin, Litecoin, Monero, and Ethereum.
The malware is being distributed through spam emails targeting users in Japan and America, carrying a malicious PDF that contains an embedded document. This is a RTF file attempting to exploit CVE-2017-8579, a vulnerability addressed in September 2017 after it was abused to spread the FinFisher spyware.
The RTF document references to an embedded remote object, an HTA file that contains encoded PowerShell commands. Once fetched from the remote server, the file executes the PowerShell to download and execute the final payload.
The downloaded file is an initial stage self-extracting executable (SFX) that extracts the second stage, a password protected SFX that has the password supplied by the first stage. Only after the second stage is executed, the ComboJack is extracted.
First, the malware copies itself to the ProgramData folder, and then leverages the attrib.exe built-in Windows tool to set the hidden and system attributes to itself. Next, the malware sets a registry key to achieve persistence.
Once the steps have been completed, ComboJack starts checking the contents of the clipboard every half second to determine if wallet information for different digital currencies has been copied there. When that happens, the malware replaces the information with hardcoded data in an attempt to divert funds to a presumably attacker-owned wallet.
“This tactic relies on the fact that wallet addresses are typically long and complex and to prevent errors, most users will opt to copy an exact string in order to prevent potential errors,” Palo Alto points out.
The malware can detect addresses of crypto-currencies such as Ethereum, Monero (erroneously, the replacement address is shorter), Bitcoin, Litecoin, Qiwi, WebMoney (Rubles), WebMoney (USD), Yandex Money, and a currently unknown virtual coin.
The fact that ComboJack is targeting WebMoney (USD, EUR, and RUB) and Yandex Money, which are popular digital payment systems, also sets the malware apart from other Trojans capable of stealing crypto-currencies by replacing wallet addresses that have been copied to the clipboard.
“By targeting multiple cryptocurrencies and web based wallets, the author of ComboJack appears to be hedging his or her bets on which currency will boom and which will bust. As the prices of cryptocurrencies continue to rise it is likely we will see more and more malware targeting cryptocurrencies, as it presents the fastest way to the highest profit,” Palo Alto concludes.
Researchers Devise New Attacks Against 4G LTE Mobile Networks
6.3.2018 securityweek Mobil Attack
A team of researchers from Purdue University and the University of Iowa have discovered 10 new attacks against the 4G LTE protocol, which could allow adversaries snoop on messages, deny service, and even track the location of users.
In a whitepaper (PDF), the team provides information on LTEInspector, the adversarial model-based testing approach they decided to adopt in this quest, and on the 10 new vulnerabilities they discovered in the protocol, alongside 9 previously known attacks.
LTEInspector, the researchers explain, was designed to analyze three critical procedures in the 4G LTE network, namely attach, detach, and paging. Designed to be tool-agnostic, the new approach can be “instantiated through any generic symbolic model checker and cryptographic protocol verifier,” the researchers say.
Using the new approach, the researchers discovered undocumented attacks on each of the critical procedures in the protocol. Four of the attacks affect the attach procedure, one affects the detach procedure, and five affect paging.
The first such attack is called Authentication Synchronization Failure and could disrupt the attach procedure, thus resulting in the victim experiencing service disruption.
A Traceability Attack can be abused to track a particular victim user equipment. “This attack can also be performed for a specific user with only the knowledge of victim’s phone number,” the researchers say.
The Numb Attack allows the adversary to inject an out-of-sequence control-plane protocol message and disrupt the service of a victim user device until restart. This issue can be chained with other types of assaults to impersonate the victim.
A Paging Channel Hijacking attack enables an adversary to hijack the victim device’s paging channel, thus preventing it from receiving legitimate paging messages, meaning that the victim does not receive service notifications such as incoming phone calls or SMS.
A Stealthy kicking-off Attack results in the user device disconnecting from the Evolved Packet Core (EPC) and can be used as a prerequisite of the Authentication Relay Attack.
As part of a Panic Attack, an adversary injects fake emergency paging messages to a large number of user devices, thus creating artificial emergency.
An adversary could also launch Energy Depletion Attacks to make user devices “perform expensive cryptographic operations,” by forcing them to repeatedly carry out the expensive attach procedure.
The Linkability Attack, the researchers say, would allow an adversary to trace a victim device in a cell area by broadcasting a paging with the victim’s IMSI and observing the received attach request.
The only attack against the detach procedure is the Detach/Downgrade Attack, where the adversary injects network initiated detach requests to disrupt the victim’s service.
The researchers also point out that it is possible to chain some of these attacks with previously known assault methods, as well as among them, which could have wider implications. One such attack is the Authentication Relay Attack, where the victim device is disconnected from the EPC and the adversary connects instead, impersonating it, despite the lack of proper credentials.
“In this attack the adversary, however, cannot decrypt or inject valid encrypted messages unless the operator uses a weak or no security context,” the researchers explain.
ComboJack Malware alters Windows clipboards to steal cryptocurrencies and payments
6.3.2018 securityweek Cryptocurrency
Palo Alto Networks discovered a malware dubbed ComboJack that is able of detecting when users copy a cryptocurrency address and alter clipboards to steal cryptocurrencies and payments.
Crooks continue to focus their interest in cryptocurrencies, security researchers at Palo Alto Networks have spotted a strain of malware dubbed ComboJack that is able of detecting when users copy a cryptocurrency address to the Windows clipboard. The malicious code then replaces the address in the clipboard with the author’s one.
“Unit 42 researchers have discovered a new currency stealer which targets cryptocurrencies and online wallets. “CryptoJack” functions by replacing clipboard addresses with an attacker-controlled address which sends funds into the attacker’s wallet.” reads the analysis published by PaloAlto. “This technique relies on victims not checking the destination wallet prior to finalizing a transaction.”
Unlike other similar threats, ComboJack supports multiple cryptocurrencies, including Bitcoin, Litecoin, Monero, and Ethereum and it is also able to target other digital payment systems such as Qiwi, Yandex Money, and WebMoney (USD and ruble payments).
In 2017, CryptoShuffler was the first malware to implement this technique to targets online Bitcoin wallets, in February 2018 researchers at ElevenPaths discovered a crypto coin malware stealer called Evrial which takes control of the clipboard to get “easy money”.
Experts from PaloAlto Networks, along with Proofpoint experts, were investigating a malspam campaign targeting Japanese and American users.
The spam messages attempt to trick victims into opening the PDF attachment by claiming a passport was lost and that the attached PDF contained a scanned copy of the document.
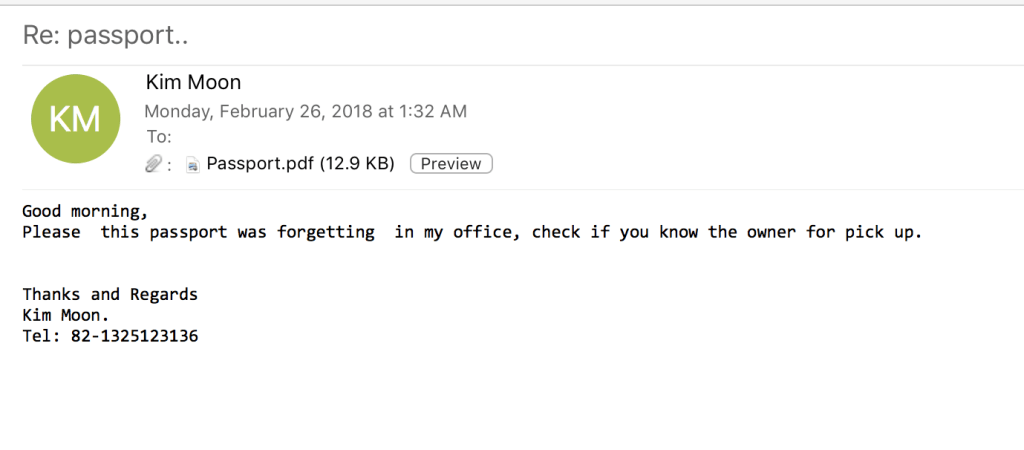
Attackers implemented an attack chain already observed for the distribution of the Dridex banking trojan and Locky ransomware in 2017.
When the user opens the PDF document, the file opens an RTF file that contains an embedded HTA object that attempts to exploit the CVE-2017-8579 DirectX flaw.
“This embedded remote object is an HTA file which was located at hXXps://a.doko[.]moe/tnejln which contains encoded PowerShell commands.” continues the analysis.
The SFX file downloads and runs a password-protected SFX that then finally delivers ComboJack.
Finally, the payload sets a registry key to ensure persistence.

ComboJack checks the Windows clipboard every half-a-second for new content that matches a known pattern for a cryptocurrency or payment system address, then it replaces the address with one from an internal list.
The malicious code exploits the fact that walled addresses are difficult to remind and most users opt to copy an exact string in order to prevent potential errors.
Users are advised to carefully check that the cryptocurrency payment addresses they copy-pasted are identical in the source and destination locations.
“By targeting multiple cryptocurrencies and web based wallets, the author of ComboJack appears to be hedging his or her bets on which currency will boom and which will bust.” concludes PaloAlto Networks.
“As the prices of cryptocurrencies continue to rise it is likely we will see more and more malware targeting cryptocurrencies, as it presents the fastest way to the highest profit.”
Further details, including IOCs are available in the analysis.
World’s largest DDoS attack record broken by a new memcached DDoS attack
6.3.2018 securityweek Attack
World’s largest DDoS attack record lasted just a few days, Arbor Networks reported that earlier this month a US service provider suffered a 1.7Tbps memcached DDoS attack.
On February 28, 2018, the code hosting website GitHub was hit by the largest-ever DDoS attack that peaked at 1.3Tbps. The powerful attack was abusing the memcached protocol to power so-called memcached DDoS attacks.
Memcached is a free and open source, high-performance, distributed memory caching system designed to speed up dynamic web applications by alleviating database load.
Clients communicate with memcached servers via TCP or UDP on port 11211.
Researchers from Cloudflare, Arbor Networks and security firm Qihoo 360 discovered that recently attackers are abusing the memcached for DDoS amplification attacks.
The abuse of memcached servers in DDoS Attacks is quite simple, the attacker sends a request to the targeted server on port 11211 spoofing the IP address of the victim. In a memcached DDoS attack, the request sent to the server is composed of a few bytes, while the response can be tens of thousands of times bigger, resulting in an amplification attack.
Experts at Cloudflare dubbed this type of attack Memcrashed, according to the researcher the amplification technique could allow attackers to obtain an amplification factor of 51,200.
Researchers predicted then that threat actors in the wild would abuse misconfigured Memcached servers in future attacks, and it is exactly what is happening.
Experts at Arbor Networks reported that earlier this month a US service provider suffered a 1.7Tbps DDoS attack. The service provider was able to repel the attack thanks to adequate countermeasures, but we can consider it an exception because a so huge volume of traffic is able to take off the majority of websites online.
The experts confirmed that also in this case attackers exploited unsecured memcached database servers to amplify attacks.
“Today, NETSCOUT Arbor can confirm a 1.7Tbps reflection/amplification attack targeted at a customer of a U.S. based Service Provider has been recorded by our ATLAS global traffic and DDoS threat data system.” reported Arbor Networks. “The attack was based on the same memcached reflection/amplification attack vector that made up the Github attack”

The previous record DDoS attack was observed by ATLAS in 2016, it was a 650Gbps attack towards a target in Brazil.
Unfortunately the availability online of unsecured memcached servers will allow threat actors to power similar attacks in the future.
“While the internet community is coming together to shut down access to the many open mecached servers out there, the sheer number of servers running memcached openly will make this a lasting vulnerability that attackers will exploit,” continues the post published by Arbor Networks.
“It is critically important for companies to take the necessary steps to protect themselves.”
Cloudflare recommends disabling UDP support unless it’s needed and isolating memcached servers from the Internet. Internet service providers have to fix vulnerable protocols and prevent IP spoofing.
“Internet Service Providers – In order to defeat such attacks in future, we need to fix vulnerable protocols and also IP spoofing. As long as IP spoofing is permissible on the internet, we’ll be in trouble.” concluded Cloudflare.
“Developers – Please please please: Stop using UDP. If you must, please don’t enable it by default. If you do not know what an amplification attack is I hereby forbid you from ever typing SOCK_DGRAM into your editor.”
The fear for this new kind of attack represents a good opportunity for cyber criminals, crooks already started to blackmail companies asking for a ransom demand in Monero cryptocurrency to avoid being attacked via Memcached servers.
Let’s see how long the 1.7Tbps attack will remain the largest-ever DDoS attack …
Mobile Banking Trojans Targeting Crypto-Currencies
6.3.2018 securityweek Mobil Android
Mobile malware is now targeting crypto-currencies with the intent of stealing victims’ funds, IBM says.
The immediate result of the massive increase in value that crypto-currencies have registered over the past year was the growth of malicious attacks attempting to steal coins from unsuspecting users. While most of these assaults involved PC malware so far, recent incidents have shown that mobile threats are picking up the pace as well.
Several weeks ago, IBM observed that the TrickBot Trojan was using webinjections to steal virtual coins from its victims by replacing legitimate addresses with those of the attacker. Working in a similar manner, mobile malware is now using screen overlays to trick victims into sending funds to the attacker instead, IBM's security researchers discovered.
According to IBM, mobile malware targeting crypto-coins usually leverages malicious miners to collect coins, but the practice isn’t that profitable, given the limited processing power a mobile device has. Furthermore, users are more likely to discover a mining operation on a mobile device when observing overheating, low performance and faster battery drain.
“Crooks operating mobile banking Trojans don’t install miners on the device. Rather, they typically steal existing coins from unsuspecting owners using mobile malware that creates the same effect as webinjections: cybercriminals trick users with fake on-screen information, steal their access credentials and take over accounts to empty coins into their own wallets,” IBM notes.
Some of the mobile malware families capable of detecting the application opened on a mobile device include ExoBot, BankBot, Marcher, and Mazar. Based on the launched application, these Trojans can display a hardcoded or dynamically fetched overlay and hide the legitimate app screen behind a fake one.
Thus, users end up revealing their credentials to the malware operators, which can then abuse them to access the victim’s account. If a second-factor authorization is required, the malware can hijack it from the compromised device without alerting the victim.
Usually employed in attacks targeting bank accounts, the method has been adapted for the theft of crypto-coins as well, the researchers discovered. Trojans such as BankBot and Marcher have been already packed with the necessary functionality to overlay a fake screen when the user opens relevant wallet apps.
The malware, IBM says, targets multiple virtual currencies, including Bitcoin, Bitcoin Cash, Ethereum, Litecoin, Monero, and other. Although basic-looking, the overlay screens are convincing and can trick users into unknowingly sending their access credentials to an attacker.
“The mobile malware arena already strives to emulate the success of PC banking Trojans and facilitate cross-channel fraud and identity theft. Cryptocurrency is just another target for malware operators looking to get in on the action. Given the rapid evolution of this threat, organizations should invest in mobile threat protection tools to minimize the risk posed by mobile banking Trojans,” IBM concludes.